Security protection method and device for domain name system (DNS) and DNS
A security protection and DNS server technology, applied in the field of communication, can solve the problems of single anti-DDoS protection and poor security protection, and achieve the effect of avoiding manslaughter and improving the response rate and efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
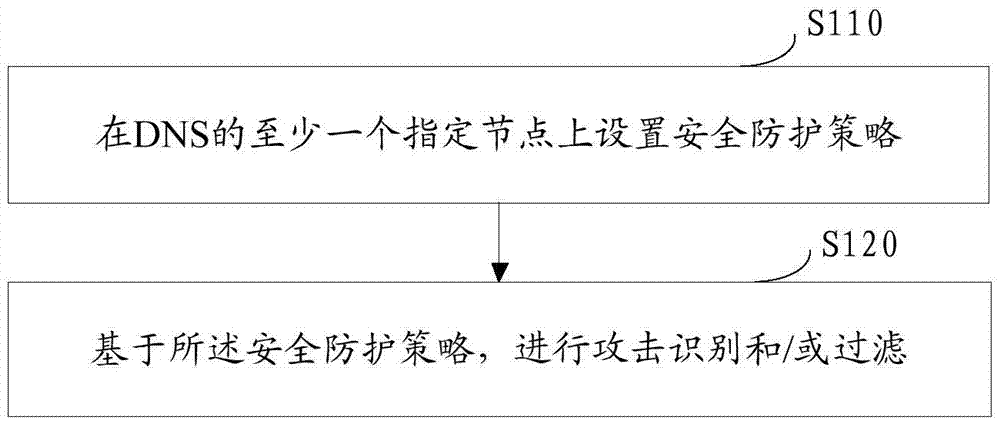
[0081] Such as figure 1 As shown, this embodiment provides a domain name system DNS security protection method, the method includes:
[0082] Step S110: Set a security protection strategy on at least one designated node of the DNS;
[0083] Step S120: Perform attack identification and / or filtering based on the security protection strategy.
[0084] At least one designated node of the DNS in this embodiment, where the designated node is a constituent node of the DNS. DNS usually includes DNS servers, network access nodes that access the DNS server, user access nodes, firewalls, and other nodes.
[0085] In this embodiment, a corresponding security protection policy is set on at least one designated node of the DNS, so that the designated node will perform attack identification and / or attack filtering based on the security protection policy to improve security. For example, by setting up security protection strategies on 2 or more nodes, not only can there be special attack detection n...
Embodiment 2
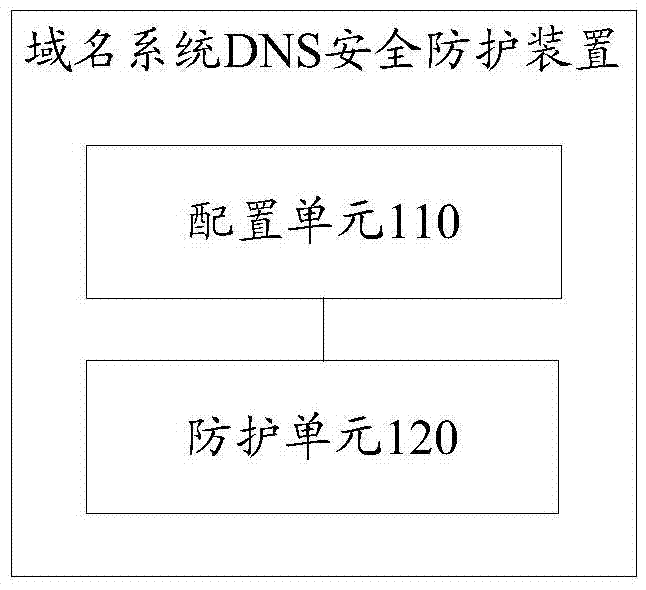
[0111] Such as image 3 As shown, this embodiment provides a domain name system DNS security protection device, which includes:
[0112] The configuration unit 110 is configured to set a security protection strategy on at least one designated node of the DNS;
[0113] The protection unit 120 is configured to perform attack identification and / or filtering based on the security protection strategy.
[0114] The device in this embodiment may be a DNS device that can configure information for each node in the DNS and control these nodes for security protection.
[0115] In this embodiment, the configuration unit 110 and the protection unit 120 can each correspond to a processor or a processing circuit, and the processing can include information processing such as a central processing unit, a digital signal processor, a microprocessor, or a programmable array. structure. The processing circuit may include an application specific integrated circuit or the like. The configuration unit 110 ...
example 1
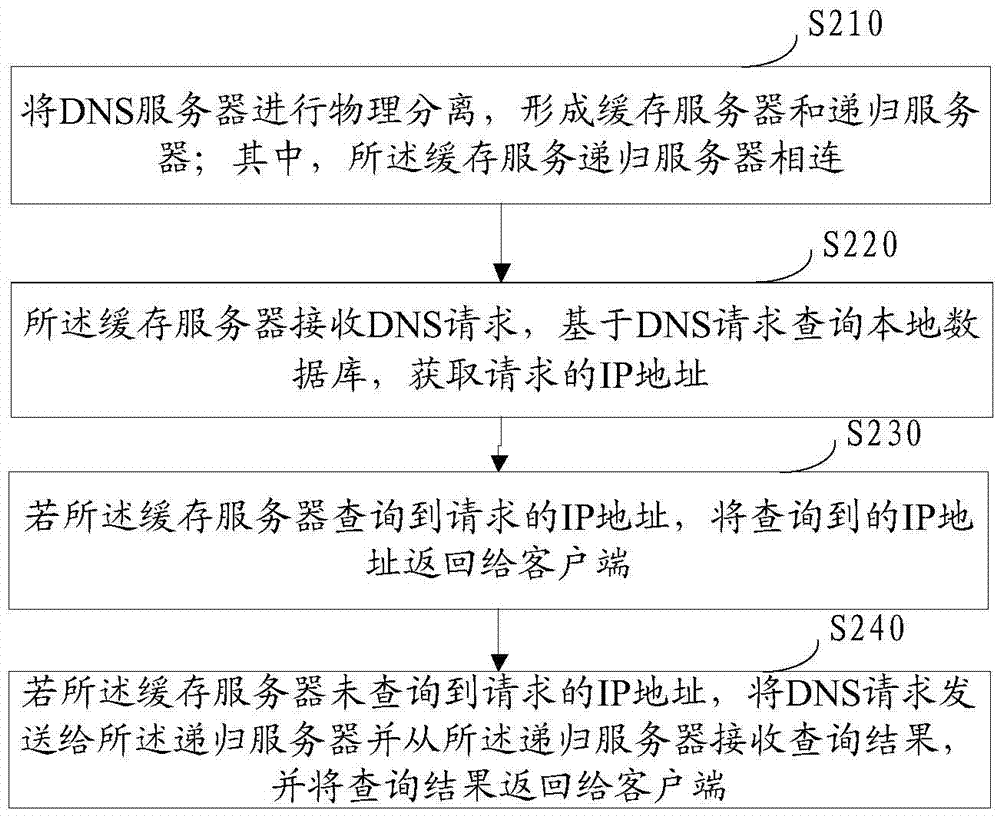
[0118] Example 1: The configuration unit 110 is specifically configured to set a first protection strategy on the access node of the external network; the protection unit 120 is specifically configured to allow the DNS server response to carry a legal external network based on the first protection policy Protocols DNS requests for IP addresses, and prohibits the DNS server from responding to DNS requests that carry illegal external network IP addresses; wherein, the legal IP address is an external network IP address that has passed security confirmation in advance. In this embodiment, by setting a protection strategy on the access nodes of the external network, the access nodes of the external network are used to filter or identify attacks from the external network.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com