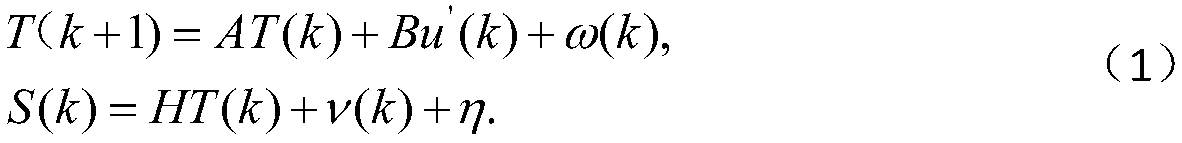Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
64results about How to "Troubleshoot deployment issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
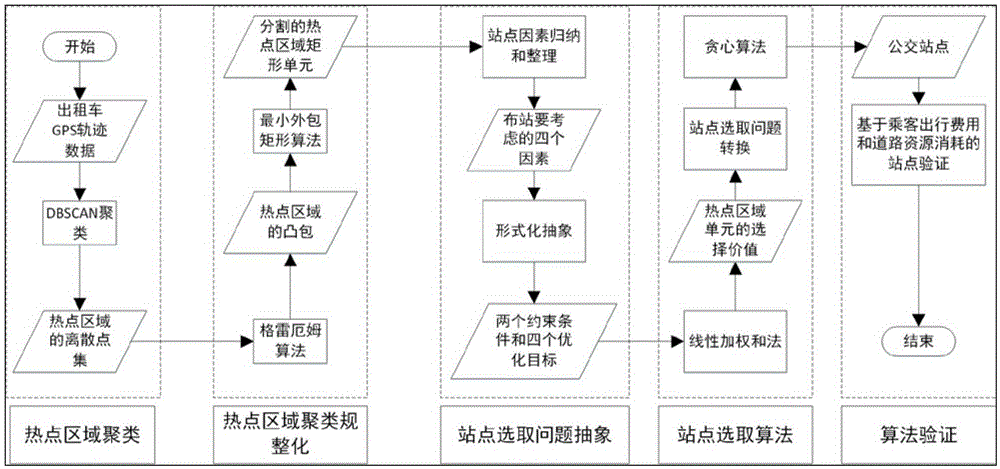
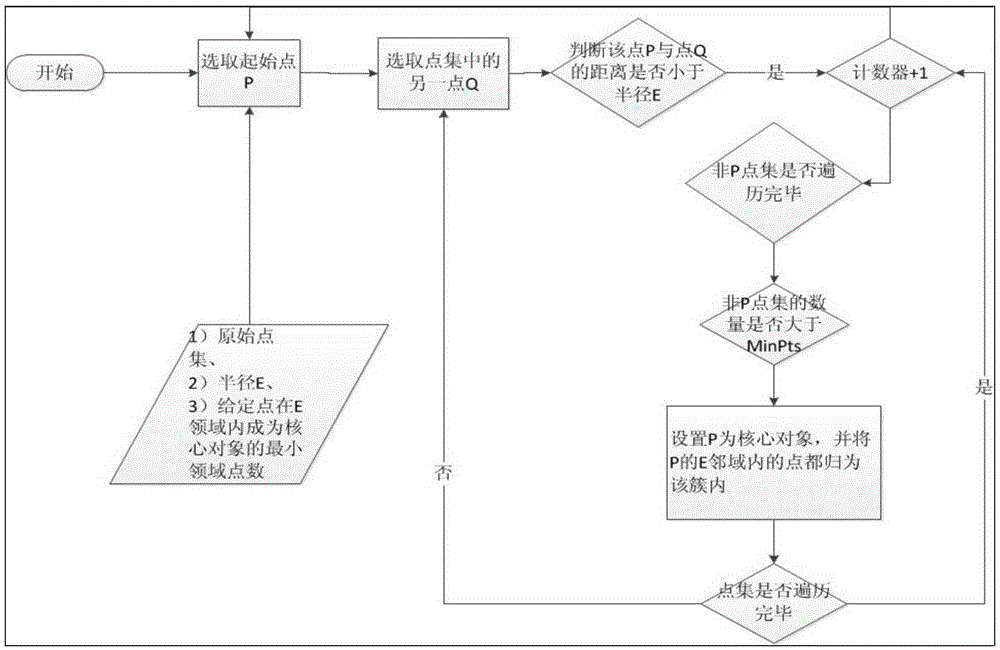
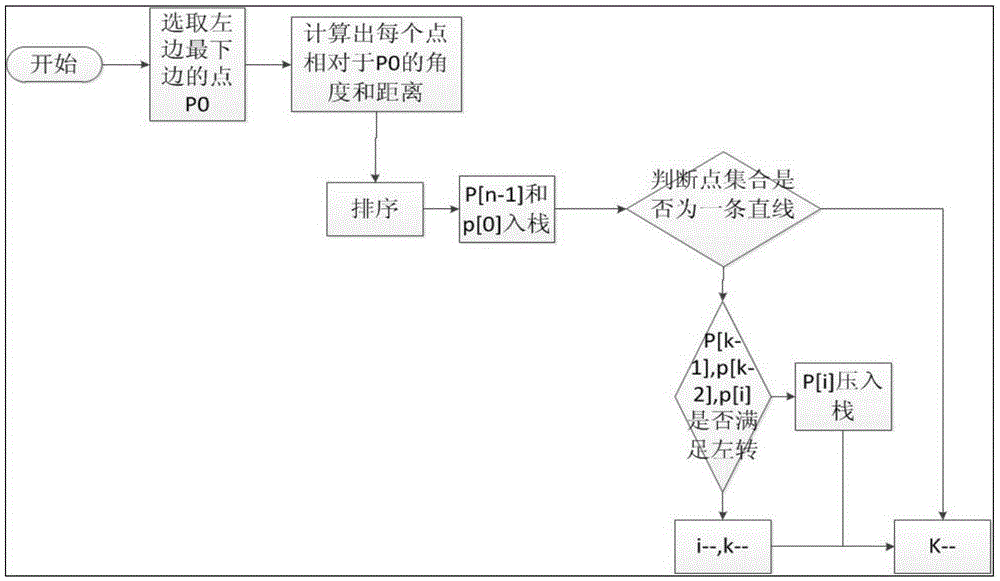
Travel demand analysis-based bus station point deployment method
InactiveCN105427003AImprove traffic efficiencyTroubleshoot deployment issuesForecastingGeographical information databasesGreedy algorithmResource consumption
The invention relates to a travel demand analysis-based bus station point deployment method. According to the travel demand analysis-based bus station point deployment method, travel demand characteristics of Beijing are analyzed based on massive taxi data; passenger hot areas are obtained through trajectory data; data such as road traffic congestion conditions, road types, road width and the number of roads are obtained through GIS map data extraction, and the data are adopted as consideration factors for station site deployment; and station site deployment optimization targets are processed, and a greedy algorithm is adopted to solve problems in station site deployment. Bus station sites obtained through adopting the method is the basis of intelligent bus line design; and routes can be arranged between the bus station sites, so that travel cost of passengers and road resource consumption can be effectively reduced.
Owner:BEIHANG UNIV
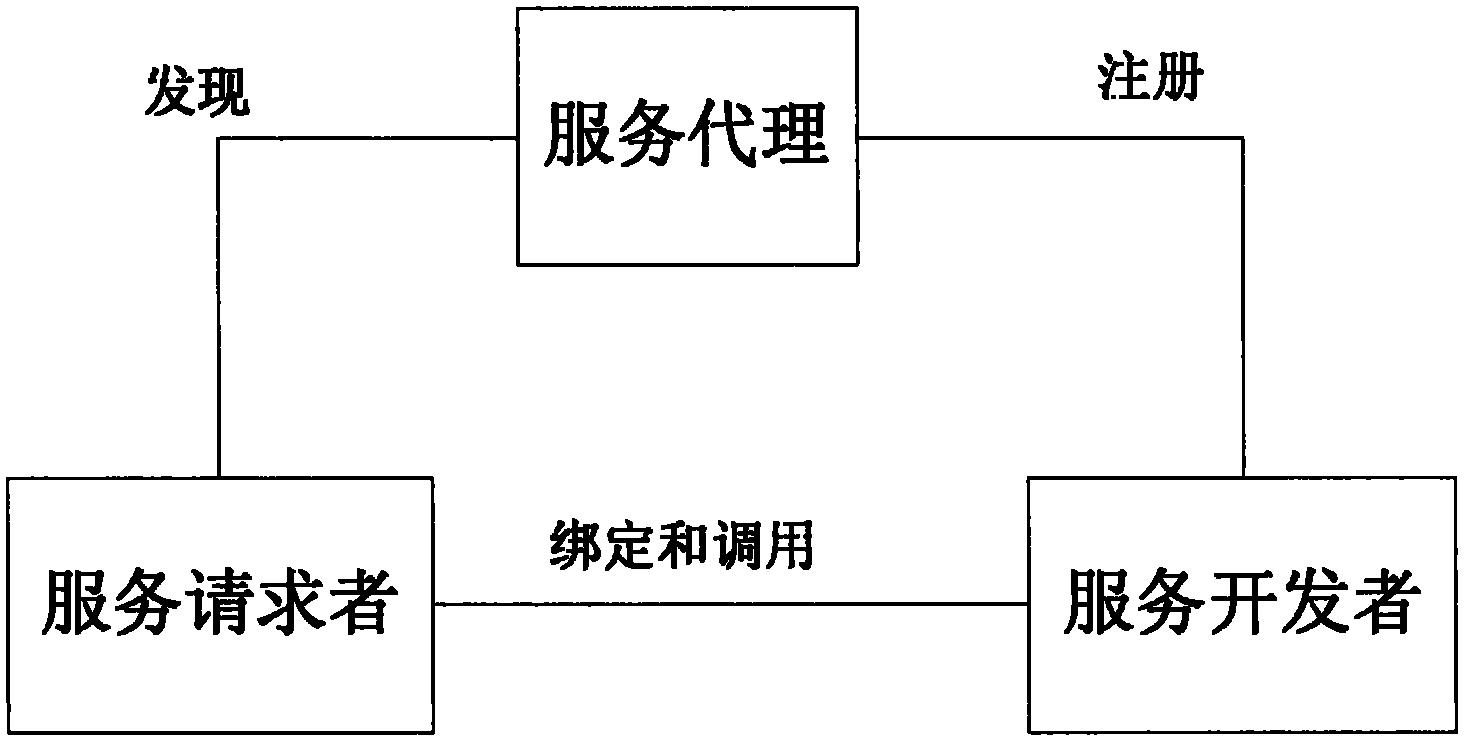
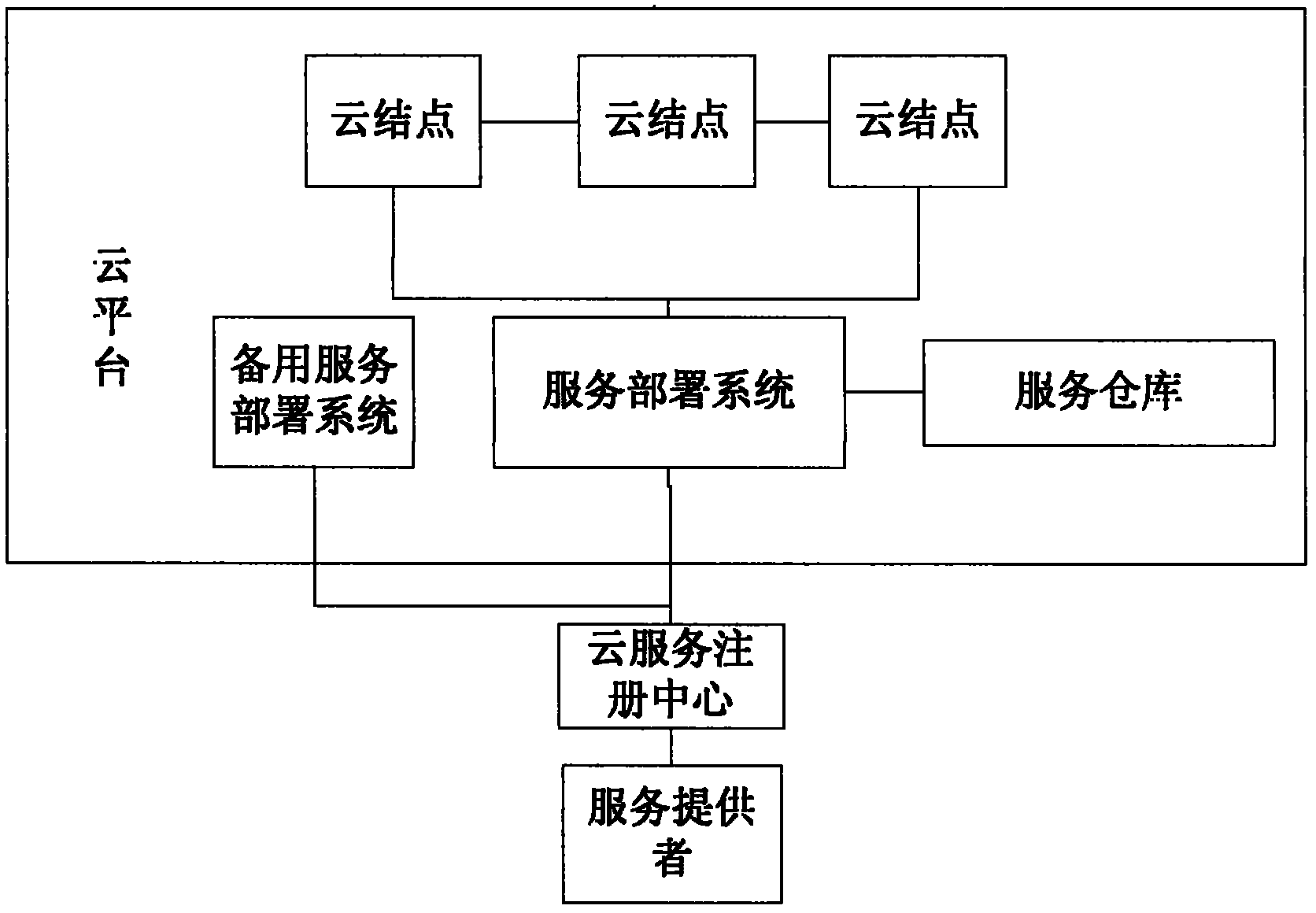
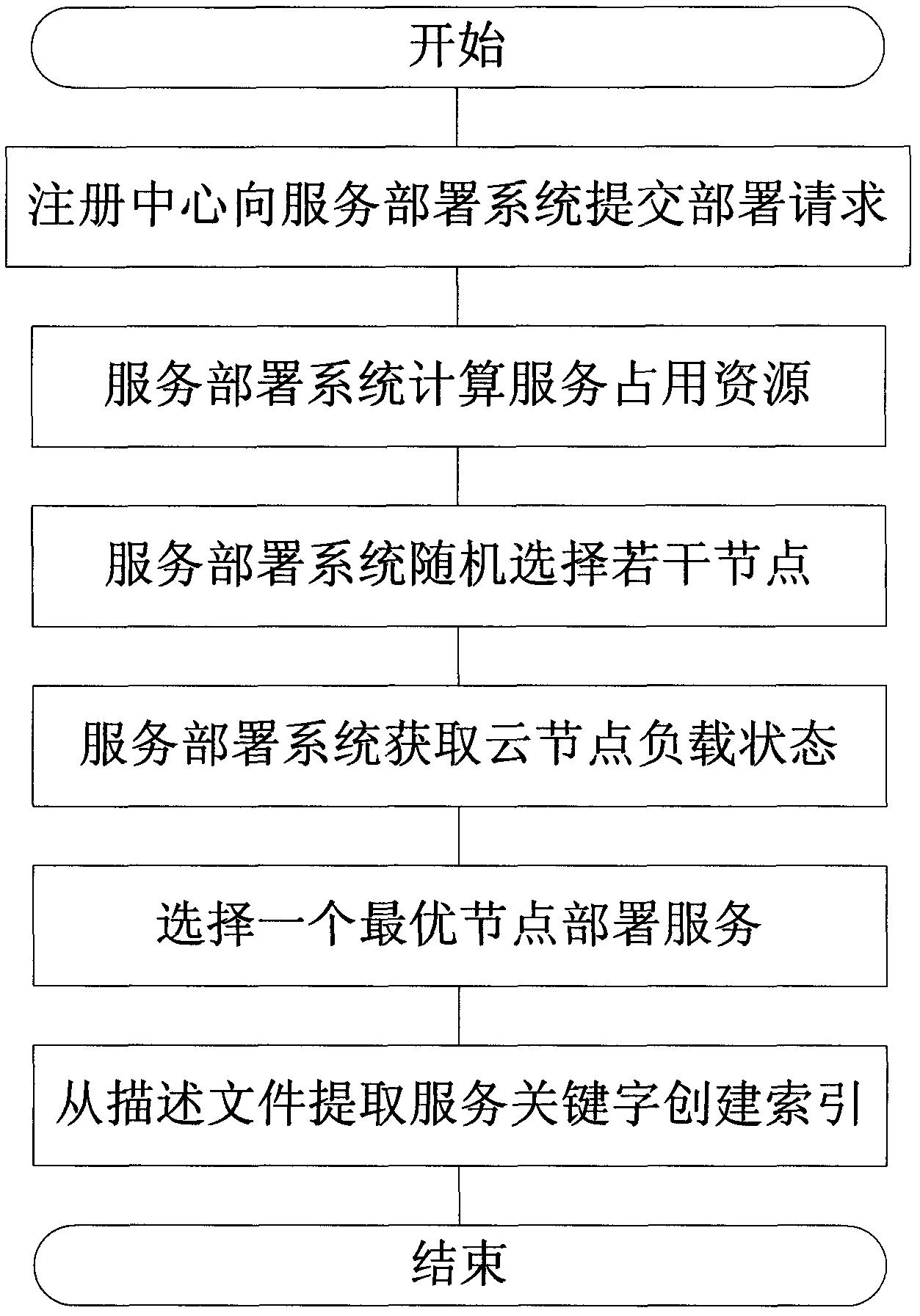
Method for deploying services in cloud computing environment
ActiveCN102223398ATroubleshoot deployment issuesTransmissionSpecial data processing applicationsFault toleranceNode deployment
The invention discloses a method for deploying services in cloud computing environment. The method the following steps: a developer describes the provided service through using a cloud platform service definition language conceptual schema definition language (CSDL) defined by the invention, submits the service to a cloud platform; the cloud platform selects an optimal node deployment server according to the cloud node and the load of the service, and generates a search rule according to the CSDL; and a service user searches available services and calls the available services through accessing a cloud service warehouse. The system also provides a standby deployment system for ensuring the robustness, and periodically inspects the operation condition of the cloud node; the redeployment service reaches optimization; and by utilizing the method, the cloud platform is enabled to have higher service efficiency and fault tolerance; and in the cloud environment, the service provider does notneed maintain the environment of service operation by self, and submits the service to the cloud environment.
Owner:慧之安信息技术股份有限公司
Method for measuring multimedia multicast service quality based on client
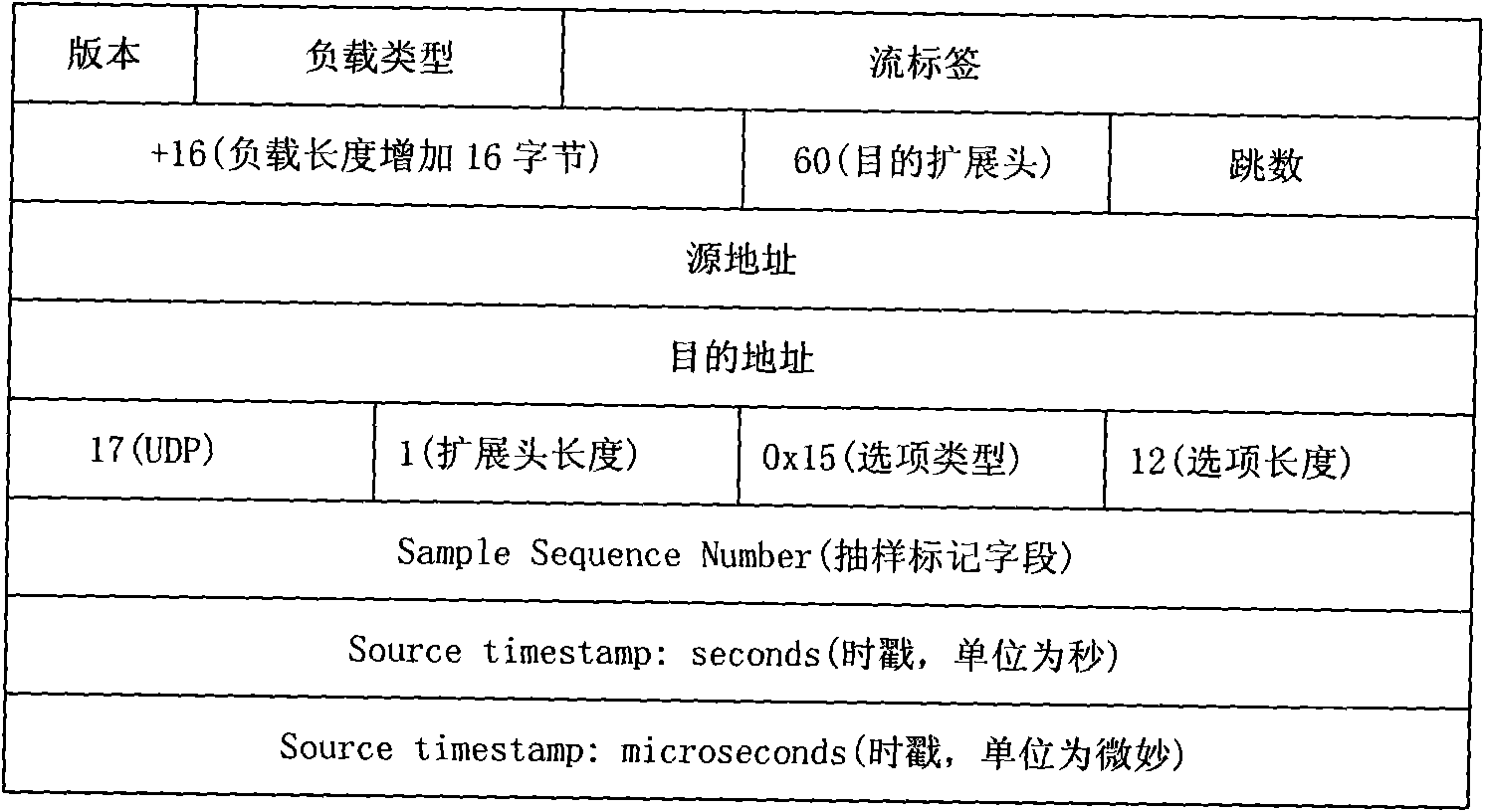
InactiveCN101674204ATimely measurementImprove friendlinessData switching networksActive measurementIPv6
The invention discloses a method for measuring the multimedia multicast service quality based on a client under a large-scale IPv6 network environment. The method provides a whole set of schemes to solve the multimedia multicast service quality measurement, comprising the time synchronization of a closed system, the message sampling and time stamp adding of a multicast source end system, the selection of a dynamic measurement point, the measurement of multicast service quality parameters of a single measurement point, and the assessment and control of a multicast control server to the access network multimedia multicast service quality. The method not only can overcome the invasion and non-reliability of active measurement as well as the locality of passive measurement, but also can timelyand truly measure the multimedia multicast service quality, and has the advantages of convenient deployment, good expansibility and the like.
Owner:SOUTHEAST UNIV
Container-based block chain deployment method
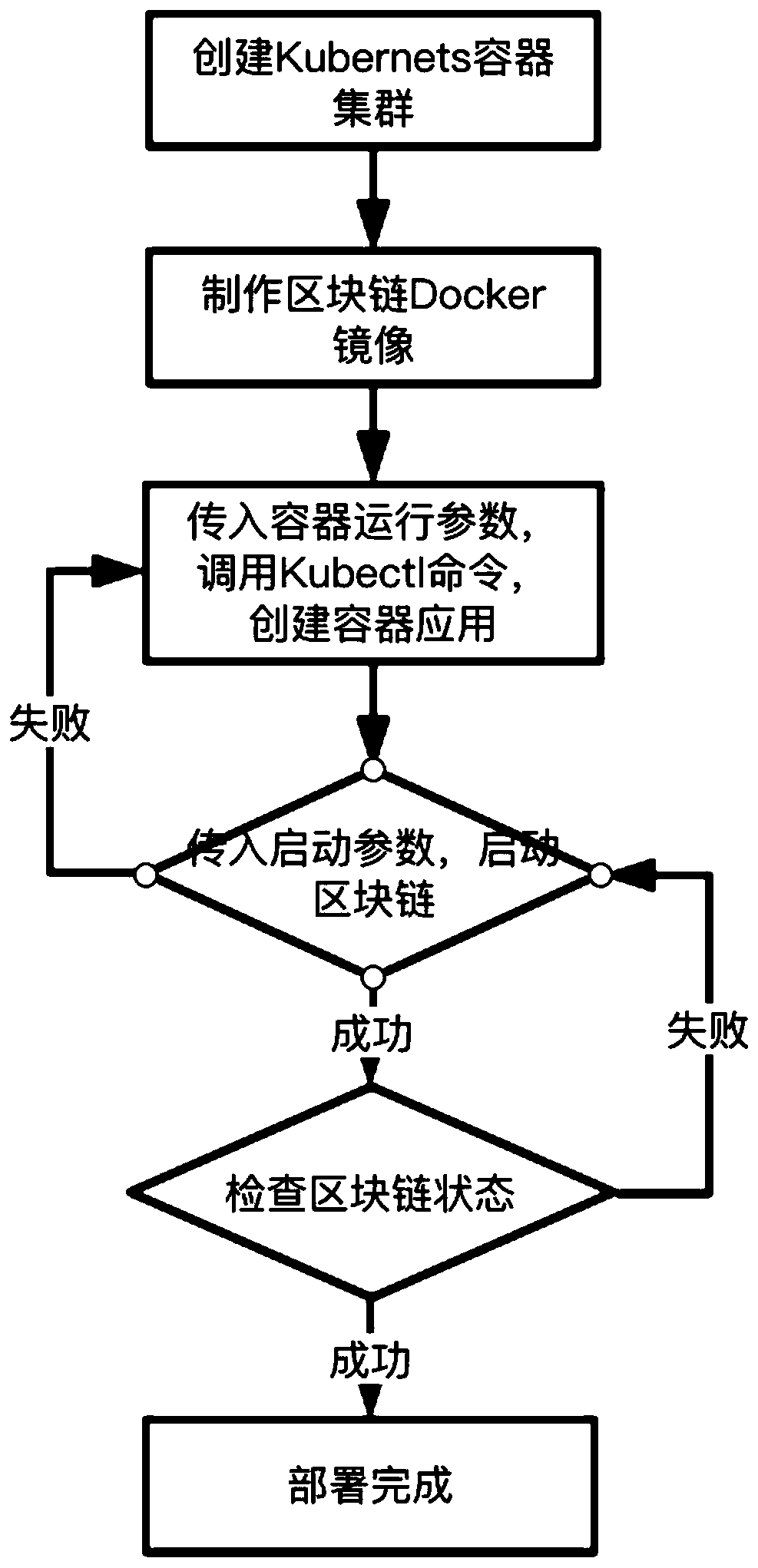
InactiveCN109800056ASimplify the deployment processTroubleshoot deployment issuesSoftware simulation/interpretation/emulationOperational systemLow speed
The invention discloses a container-based block chain deployment method. The method comprises the following steps: 1) establishing a kubernetes container cluster; 2) manufacturing a Docker mirror image comprising an operating system, a block chain installation package, a daemon process and a startup script; 3) creating a container arrangement file, and defining the number of container instances, aused mirror image ID, a running port, an NAT gateway ID and an elastic IP; 4) calling a Kubectl command line tool, connecting the container cluster created in the step 1), loading the docker image produced in the step 2) by using the container arrangement file created in the step 3), and creating a blockchain container application; 5) communicating with a daemon process in the container through the GRPC, calling a command for starting the block chain, transmitting a starting parameter, and starting the block chain; And calling a command for checking the block chain state, checking whether theblock chain is successfully started or not, and completing the deployment of the block chain. According to the invention, the container-based block chain deployment method is realized, and the problems of complex operation and low speed of block chain deployment are solved.
Owner:HANGZHOU QULIAN TECH CO LTD
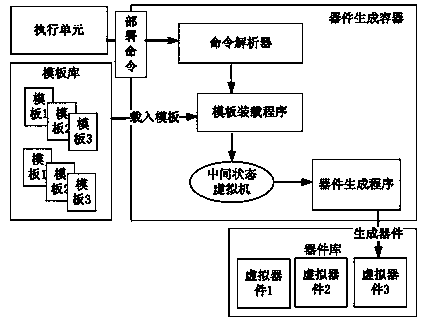
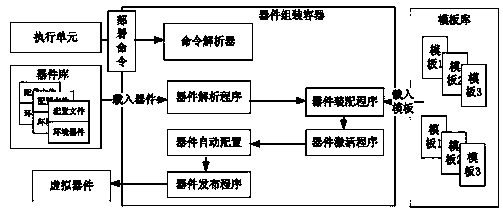
Virtual device generating and deploying method
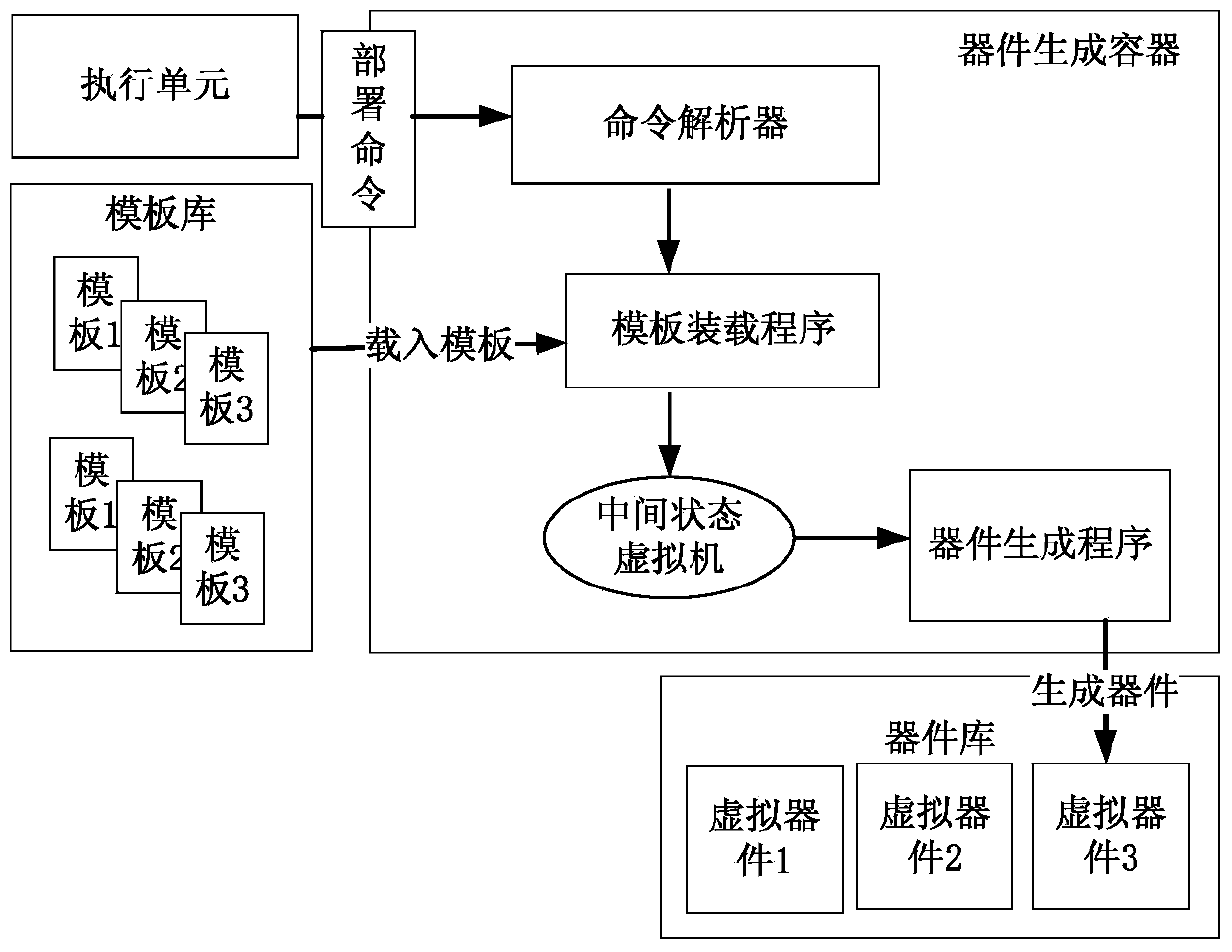
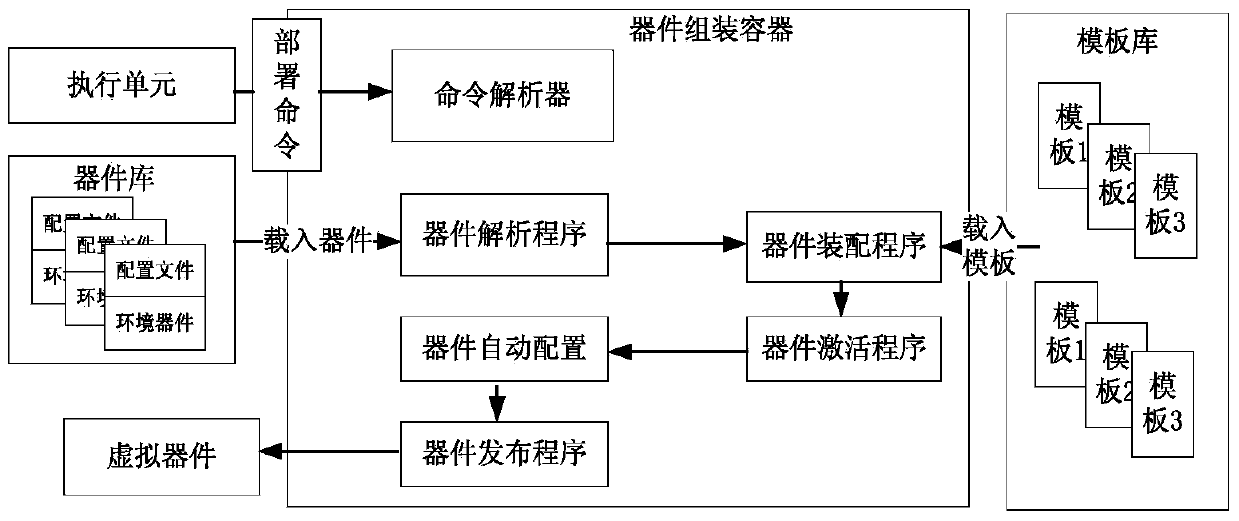
ActiveCN103793259ASolve the problem that the volume is too large and the distribution is difficultResolve commitProgram loading/initiatingSoftware simulation/interpretation/emulationApplication softwareVirtual computing
The invention belongs to the technical field of virtual computer environments and particularly relates to a virtual device generating and deploying method. Automatic virtual device generating and deploying are achieved by disintegrating the complete virtual machine image used by a virtual device into a basic substrate and a business device. The method includes the steps of firstly, deploying a virtual computing environment, deploying a physical host, and deploying a management server; secondly, under the support of the virtual computing environment, realizing virtual device generating and deploying through virtual device modules, and respectively setting virtual device modules including a universal template database, a device library, a device generating container, a device assembling container and an executing unit; thirdly, using a front-end user interface to create and generating the virtual device; fourthly, when the virtual device saved in the virtual device library is applied in the virtual computing environment, deploying the virtual device through the front-end user interface. The method has the advantages that the problems that application software submitting, deploying and configuring are difficult and time consuming are solved, the problem that the virtual device in the existing commercial technology is excessively large in size and difficult in issuing, and centralized application issuing, zero configuration deploying and fast issuing can be achieved.
Owner:INST OF CHINA ELECTRONICS SYST ENG CO +1
Method, system and device for detecting virtual private LAN loop
ActiveCN101562552ATroubleshoot deployment issuesData switching networksNetwork deploymentLocal area network
The embodiment of the invention provides a method for detecting a virtual private LAN loop, which comprises the following steps that: a first operator edge PE of a virtual private LAN generates a loop detection message carrying the sending interval of the loop detection message and the blocking priority of a link between a first PE and a user edge CE; the first PE sends the loop detection message to the CE according to the sending interval; and if the first PE receives the loop detection message, the link between the first PE and the CE is blocked. The embodiment of the invention also provides a system and a device for detecting the virtual private LAN loop. Through the proposal provided by the embodiment, the problem that a loop detection technique for a VPLS network depends on the deployment of a user side network is solved; and simultaneously, the loop is effectively prevented from appearing in the network of an operator.
Owner:HUAWEI TECH CO LTD
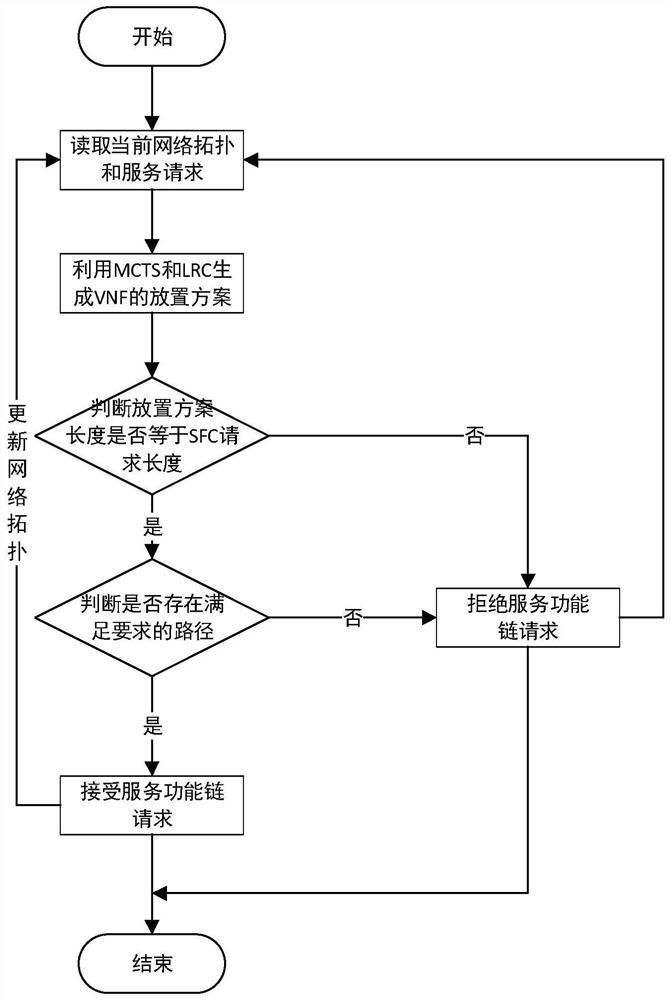
Service function chain deployment method based on reinforcement learning
ActiveCN112083933ATroubleshoot deployment issuesImplement deploymentMachine learningSoftware simulation/interpretation/emulationNetwork topologyPhysical network
The invention discloses a service function chain deployment method based on reinforcement learning. The method comprises the following steps: 1) reading a current physical network topology and a service function chain request; 2) generating a placement scheme of the virtual network function set on the physical network; 3) judging whether each virtual network function in the virtual network function set has a server for placing the virtual network function or not, if so, entering the step 4), and otherwise, entering the step 6); 4) judging whether a link meeting the requirement of the placementscheme exists in the physical network or not, if so, forming a link mapping scheme of the service function chain request, and entering a step 5), otherwise, entering a step 6); 5) receiving a servicefunction chain request, deploying the service function chain request according to the placement scheme and the link mapping scheme, updating the physical network topology, and returning to the step 1); and 6) rejecting the service function chain request, and returning to the step 1). According to the invention, the problem of online service function chain deployment in a scene with a known VNF sequence is solved.
Owner:CHONGQING UNIV +1
Flood disaster emergency material distribution analysis method
InactiveCN108288120ATroubleshoot deployment issuesClimate change adaptationForecastingDisaster areaMaterial distribution
The invention discloses a flood disaster emergency material distribution analysis method, and relates to a network analysis method. The method comprises the following steps of: carrying out real-timedemand point estimation on disaster area material demands by utilizing initial data obtained by an execution layer of an emergency relief distribution center; carrying out unsupervised cluster analysis according to five flood disaster area-related attributes such as a relief frequency, a casualty rate, a vulnerable group rate, a rainfall capacity and a building damage degree, so as to obtain divided disaster areas; determining emergency degree priorities of material distribution areas; distributing residual relief materials in an emergency inventory to the disaster areas according to weight sequences; updating the disaster area material demands in real time until the disaster area demands achieve a preset satisfaction degree; and realizing dynamic interaction between a decision making layer and the execution layer. According to the method, the emergency material deployment problems of flood disaster areas are solved, and golden relief periods are effectively utilized to complete humanitarian relief.
Owner:SHENYANG UNIV
Delay-based SDN multi-controller deployment method
ActiveCN109286528AIncrease profitReduce latencyData switching networksAlgorithm SelectionNetwork topology
The invention discloses a delay-based SDN multi-controller deployment method. According to the method, the delay and structure of network topology are analyzed; delay between each switch in the network and the degree of each node are calculated; the number of switches that can be deployed by each controller is determined, and a qualified node is selected according to a customization algorithm so as to be adopted as the deployment location of each controller, all switches in the management area of the controller are determined; a minimum average delay quantity and a worst case-oriented minimumdelay quantity are obtained according to a minimum average delay model and a worst case-oriented minimum delay model; then the same method is used to calculate a remaining qualified node, the remaining qualified node is adopted as the deployment position of another controller, so that a minimum average delay quantity and a worst case-oriented minimum delay quantity are obtained; and the above process is repeated until controller location deployment is completed. The method of the invention can be applied to algorithms for multi-controller location deployment of various network scales. With themethod adopted, a controller location deployment problem can be systematically solved.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
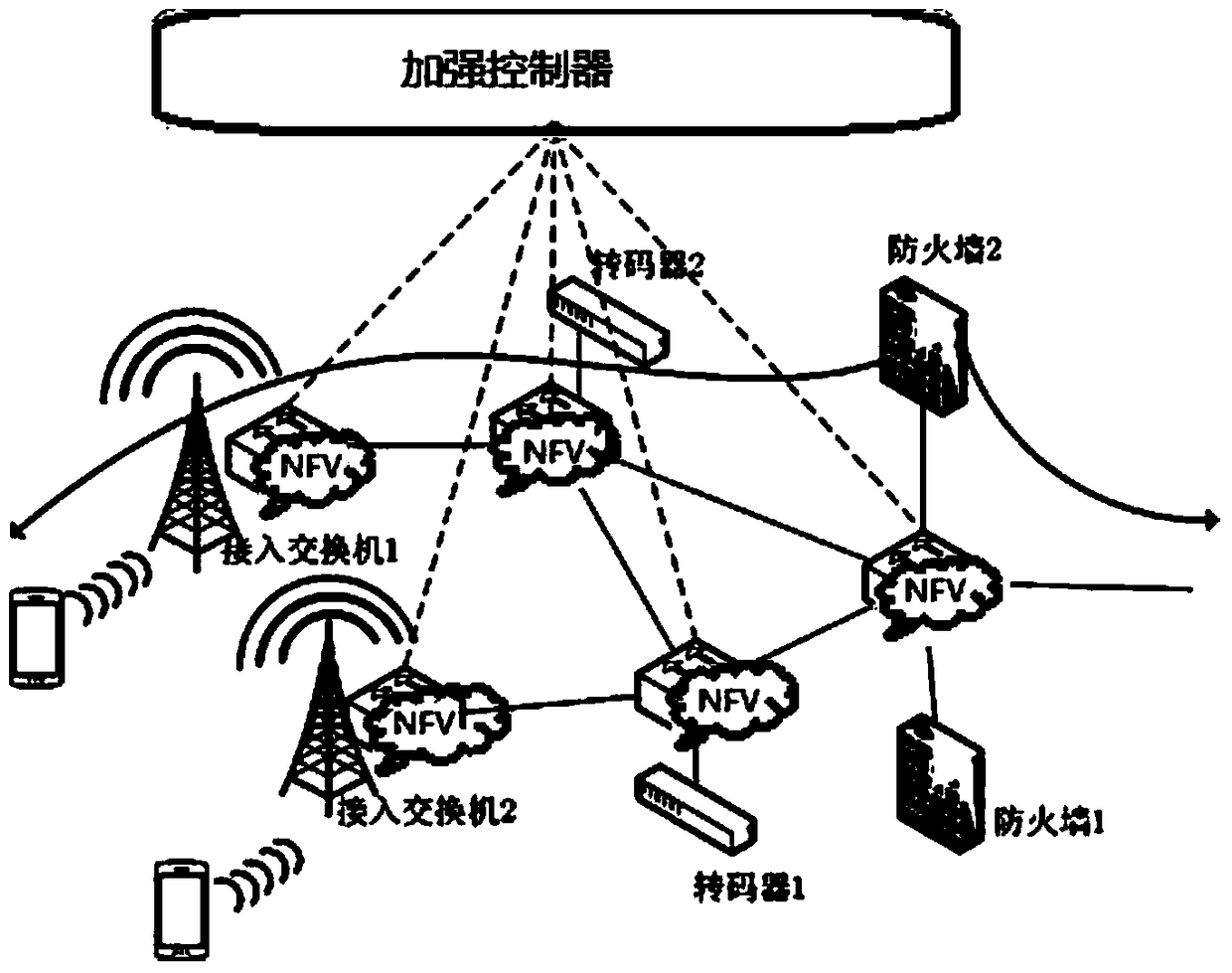
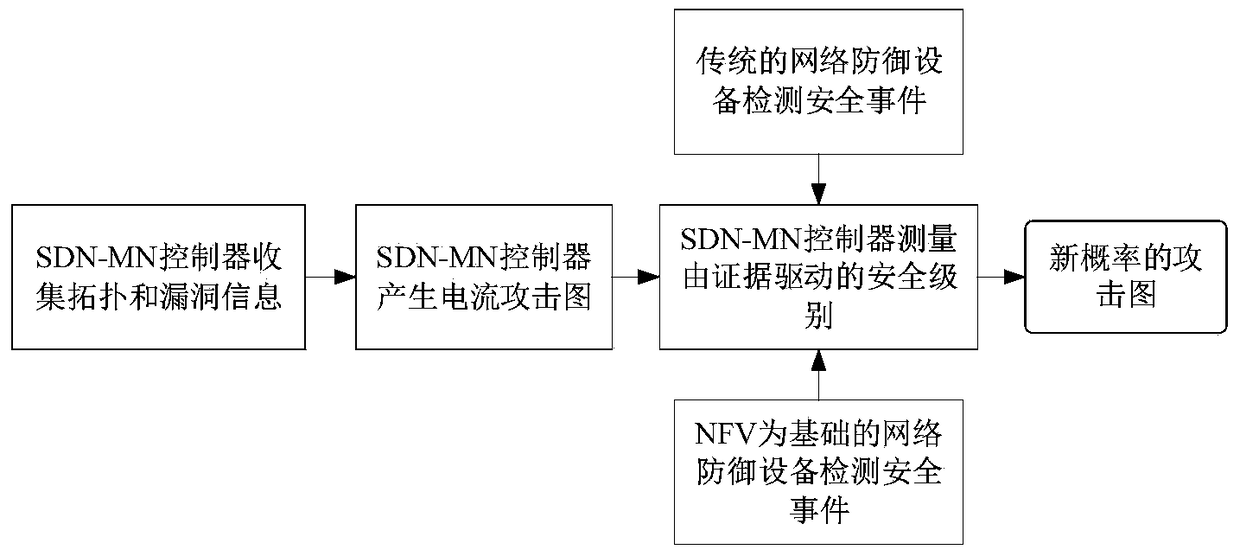
5G network multistage attack mitigation method based on software defined network (SDN) and network function virtualization (NFV)
ActiveCN105516177ATroubleshoot deployment issuesTransmissionSecurity arrangementEvaluation algorithmNetwork Functions Virtualization
The invention provides a 5G network multistage attack mitigation method based on SDN and FNV. The 5G network multistage attack mitigation method comprises the following steps of a first step, expanding an SDN-MN architecture; a second step, according to the expanded SDN-MN architecture, obtaining a proof driving security evaluation mechanism in which a software defined network-mobile network (SDN-MN) based on NFV detection; a third step, measuring the security level of a static network through the proof driving security evaluation mechanism and a generated new-probability proof driving attack graph; a fourth step, calculating a state node probability, an action node probability and a posterior probability in the attack graph through a security evaluation algorithm in the proof driving security evaluation mechanism; and a fifth step, disposing an attack mitigation mechanism by means of SDN control and NFV, and disposing a corresponding attack mitigation plan through a security level which is obtained from the proof driving attack graph. The 5G network multistage attack mitigation method can be directly used in a 5G network and can perform strategy decision according to a current network environment and settles an attack mitigation strategy disposition problem.
Owner:SHANGHAI JIAO TONG UNIV
Wireless sensor network gateway optimization deployment method
ActiveCN104883702ATroubleshoot deployment issuesImprove service qualityNetwork topologiesWireless sensor networkingAlgorithm convergence
A wireless sensor network gateway optimization deployment method relates to a gateway optimization deployment method. In order to solve a wireless sensor network gateway deployment problem under a geometry K center, a covering radius is reduced and network service quality is increased. The method comprises the following steps of carrying out gateway position vector initialization, gateway position vector variation operation, interlace operation and selection operation; repeating the above steps till that iterations reach the following equation: P=500; in a 500th generation group, calculating an adaptation value corresponding to each target vector (img file=' DDA0000724768830000011. TIF' wi=' 369' he=' 74' / ) respectively, wherein the target vector corresponding to a minimum adaptation value is an optimal deployment position coordinate of the gateway in the wireless sensor network. An experiment result shows that through using a differential evolution algorithm to solve the deployment position of the gateway in the wireless sensor network, a convergence speed is increased by about 50% and the covering radius is decreased by 20% compared to the convergence speed generated by using an existing algorithm based on a particle swarm. Therefore, through using the method, the network service quality can be obviously increased.
Owner:HARBIN INST OF TECH
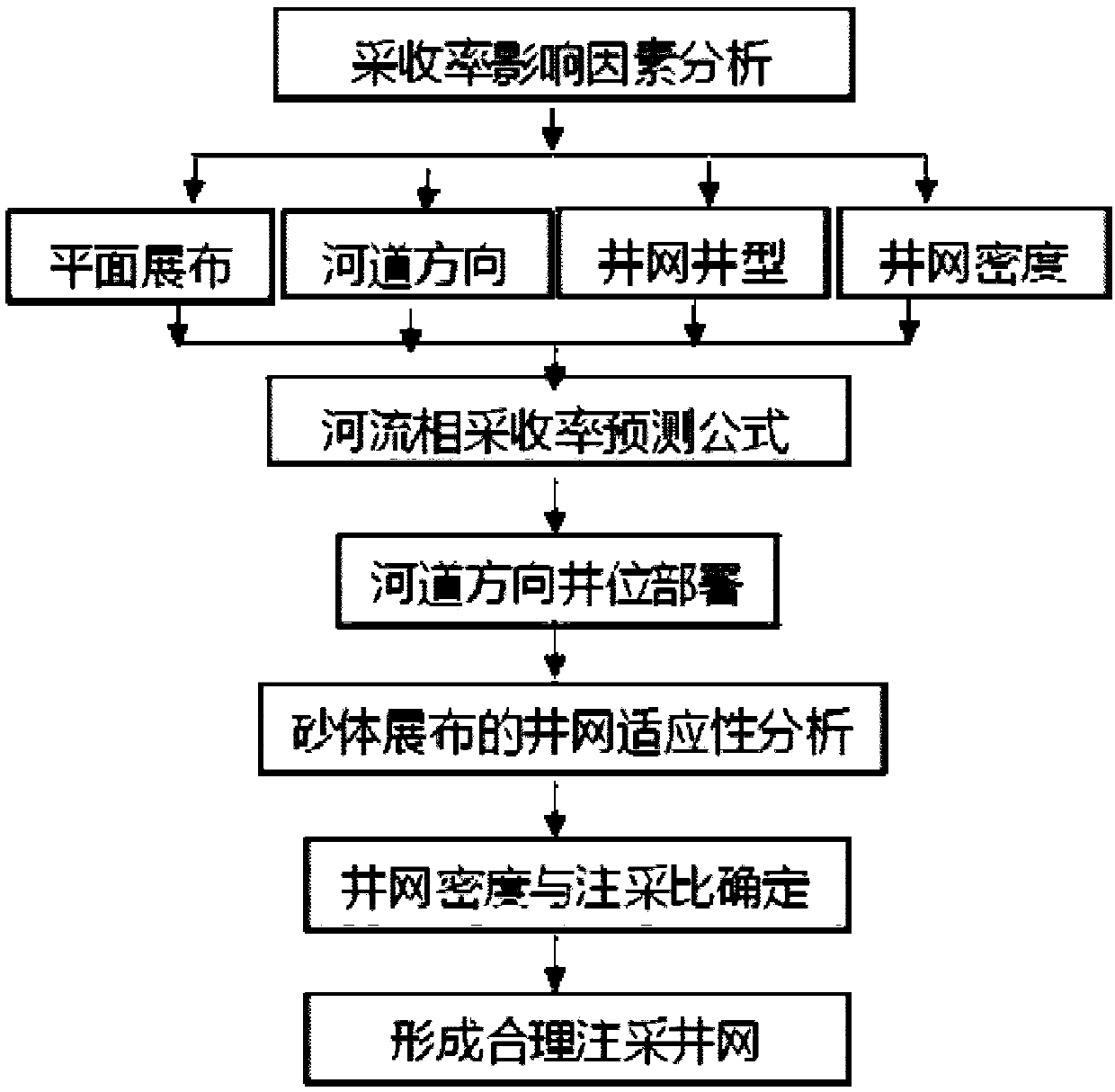
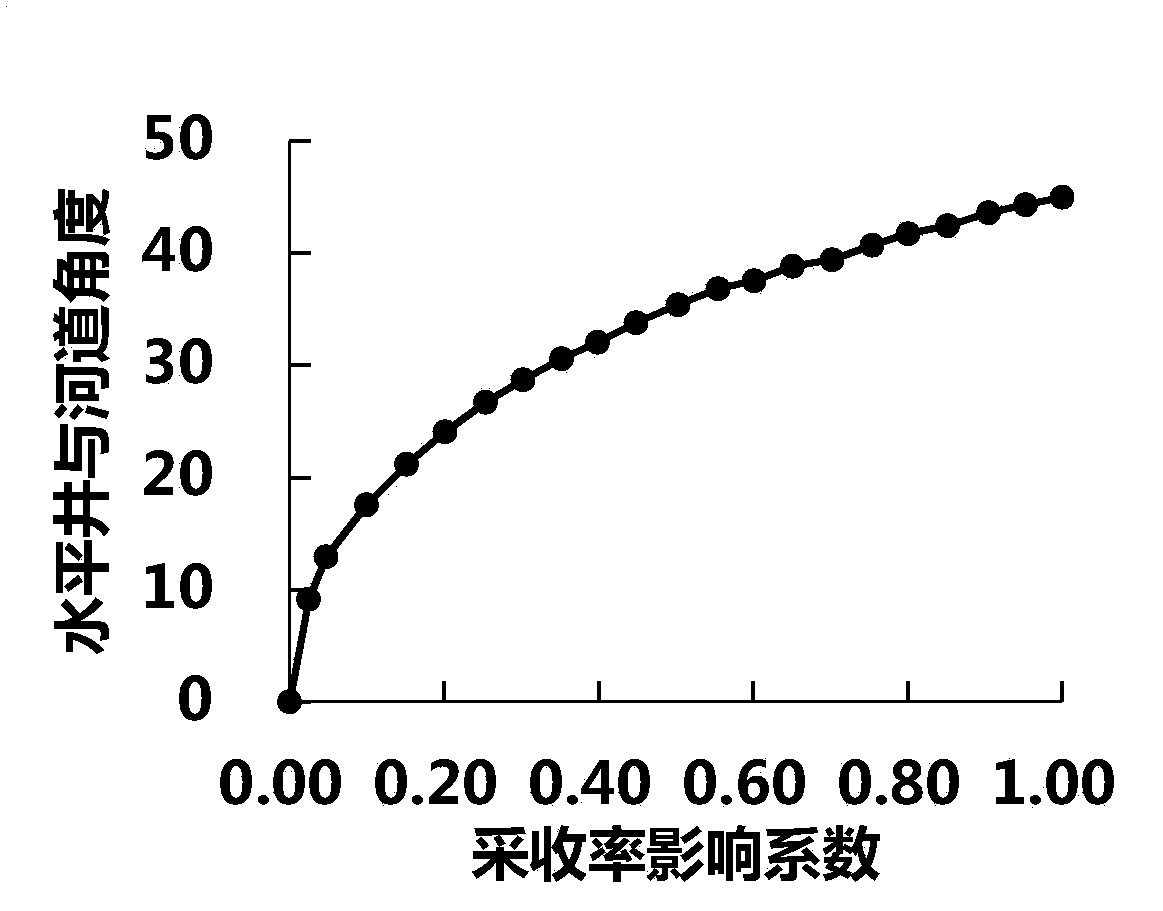
Deployment method of offshore oilfield well pattern on basis of equilibrium displacement
ActiveCN107701167ATroubleshoot deployment issuesSolve the problem of difficult adjustmentFluid removalWell controlTechnical support
The invention discloses a deployment method of an offshore oilfield well pattern on the basis of equilibrium displacement. The deployment method comprises the following steps that 1, the reservoir displacement effect is maximized, and as for anisotropic medium reservoirs, the well distances in a certain direction can be adjusted according to the characteristic of the permeability to achieve the purpose of equilibrium displacement of an injected fluid; 2, adaptability of sand body distribution and the well pattern is determined; and 3, the well control reserve volume and injection-to-productionwell ratio are determined. According to the deployment method, the recovery efficiency of the reservoirs under different development scheme deployment is established, and the problem of oilfield wellpattern development is solved; and in addition, the technical support is provided for offshore complex river-phase oilfields to achieve equilibrium displacement and well pattern one-time forming, andthe problem that due to limitation of the platform space and the service life, the oilfield well pattern later-period adjusting is difficult is solved.
Owner:CHINA NAT OFFSHORE OIL CORP +1
System and method for constructing sponge city based on Internet and microcirculation systems
ActiveCN106971352AReduce drainage loadDrain load noData processing applicationsSewerage structuresThe InternetStormwater
One aspect of the invention discloses a system for constructing a sponge city based on the Internet and microcirculation systems. The system comprises a drainage pipeline monitoring module which is used for monitoring the operation state of the drainage pipelines of a sponge city, a rainwater scheduling management module which is used for receiving and processing weather forecast information, drainage pipeline operation information and microcirculation system information to get a regional drainage plan and a rainwater scheduling plan, multiple regional management modules which are used for decomposing the plans to get a microcirculation drainage plan and a microcirculation scheduling plan, and multiple microcirculation systems which are used for recycling rainwater, draining water according to the microcirculation drainage plan and the microcirculation scheduling plan, and sending water shortage state information. The invention further discloses a method for constructing a sponge city based on the Internet and microcirculation systems. Weather information is received via the Internet, and a water-logging prevention plan is made. Thus, water drainage can be pre-planned. The drainage load of the pipe network can be reduced during rainstorm. The problem that the pipeline capacity is limited in the process of sponge city construction is solved.
Owner:HENGSHUI YITONG PIPE IND CO LTD +1
File format conversion method and device
InactiveCN110018984AEasy to convertTroubleshoot deployment issuesFile system administrationSpecial data processing applicationsDocument preparationWeb page
The invention discloses a file format conversion method and device, relates to the technical field of computers, and mainly aims to solve the problem of Office component interface deployment in the file format conversion process, and the main technical scheme of the invention is as follows: obtaining a to-be-converted text document; converting the to-be-converted text document into a webpage fileby calling a document tool set; and processing the webpage file, and converting the webpage file into a file in a preset format. The method is mainly used for converting the file format.
Owner:BEIJING GRIDSUM TECH CO LTD
Robot software testing method, device and storage medium
InactiveCN111813676AImprove test efficiencyTroubleshoot deployment issuesSoftware testing/debuggingSoftware systemSimulation
The invention discloses a robot software test method, a device, and a storage medium. The method comprises the steps: obtaining a robot software test target, and splitting the software test target, and obtaining a plurality of split test targets; publishing the plurality of split test targets in a task mode, so that a robot test service cluster subscribes the plurality of test targets and executescorresponding test tasks based on the subscribed test targets; receiving a test result fed back by the robot test service cluster after executing the test task in parallel; the purpose of testing therobot software by adopting a distributed testing method is achieved, and the complex robot software system is tested by utilizing a distributed technology.
Owner:JUXING TECH SHENZHEN CO LTD
Intelligent video content server deployment method and system
ActiveCN108616401ATroubleshoot deployment issuesHigh speed computingData switching networksArray data structureNetwork topology
The invention provides an intelligent video content server deployment method and system; the method comprises the following steps: obtaining network topology information; encoding evolution algorithmchromosomes according to the network topology information, wherein each chromosome array represents a feasible solution; forming a multi-source multi-sink network topology model according to the feasible solutions, and using same as an initial server deployment solution; converting the multi-source multi-sink network topology model into a single-source single-sink network topology model; using a minimum cost maximum flow algorithm to determine an adaption value of each network topology model in the evolution algorithm; using the evolution algorithm to carry out multiple iterations, continuously evolving, keeping the individual with the minimum adaptation in each generation, and finally obtaining the video content server deployment optimum scheme. The method and system can intelligently deploy video content servers, thus ensuring user bandwidth demands, and minimizing the video content server deployment cost and bandwidth rental fee.
Owner:SOUTH CHINA UNIV OF TECH
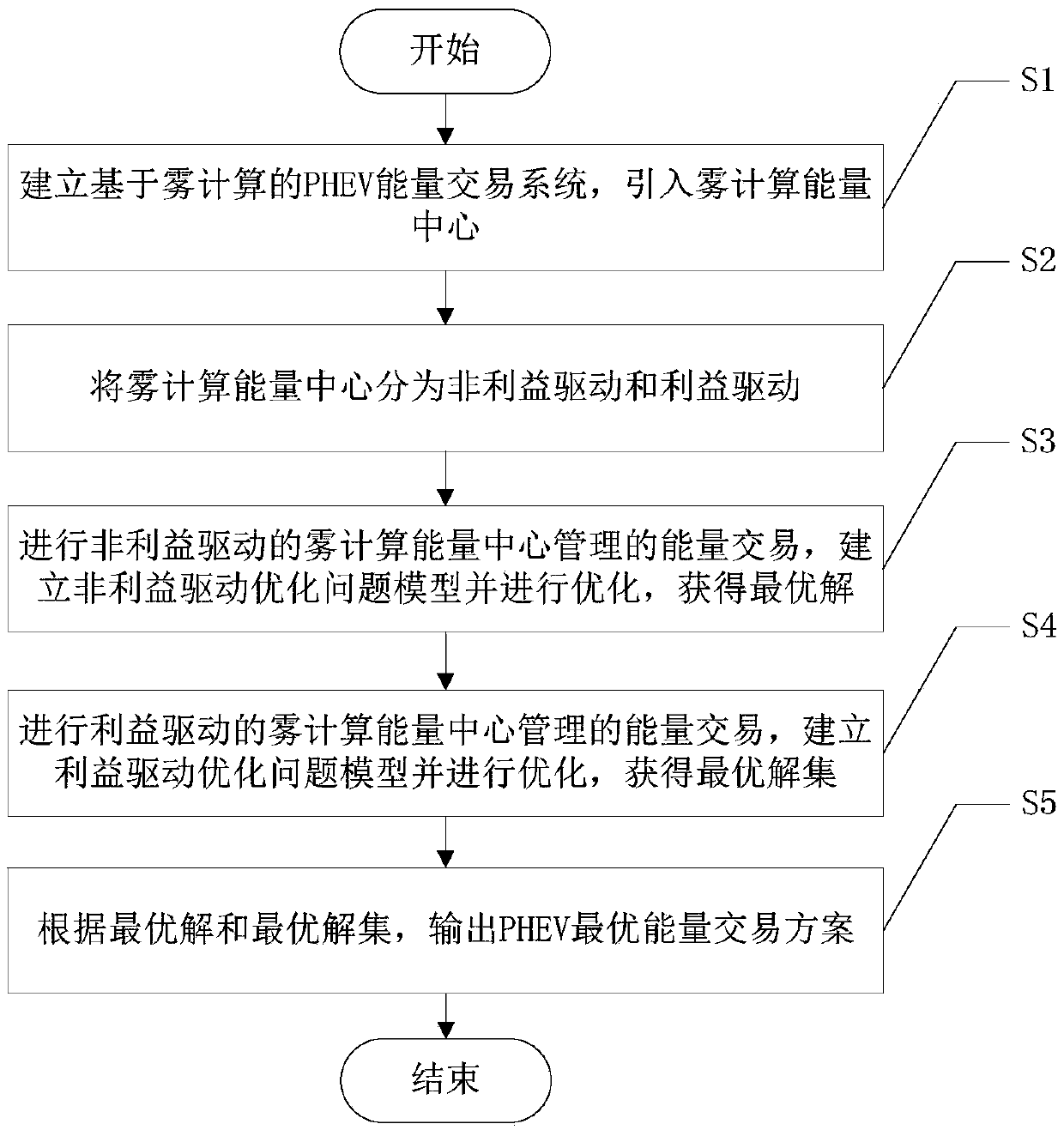
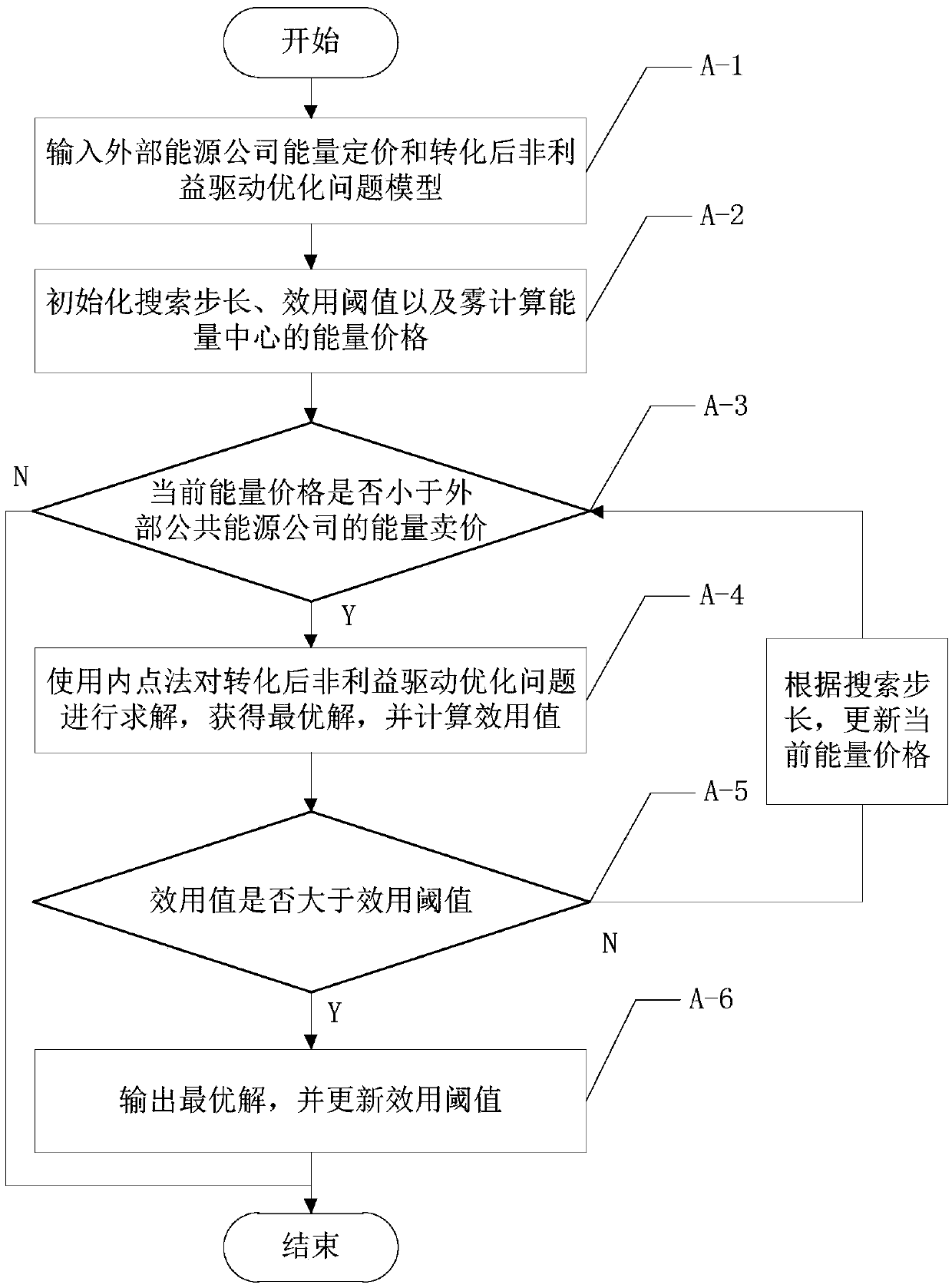
A method for obtaining the optimal energy trading scheme of PHEV based on fog calculation
InactiveCN109034472AEnable direct interactionReduce investmentForecastingBuying/selling/leasing transactionsNon profitSimulation
The invention discloses a method for obtaining the optimal energy trading scheme of PHEV based on fog calculation, comprising the following steps: S1, establishing an energy trading system of PHEV based on fog calculation, and introducing an energy center of fog calculation; S2, dividing the energy center of fog calculation into non-profit driving and profit driving; S3, carrying out the energy transaction managed by the non-profit-driven fog computing energy center, establishing a non-profit-driven optimization problem model and optimizing, and obtaining the optimal solution; S4, carrying outthe energy transaction managed by the benefit-driven fog computing energy center, establishing the benefit-driven optimization problem model and optimizing, and obtaining the optimal solution set; S5, according to the optimal solution and the optimal solution set, outputting the PHEV optimal energy trading scheme. The invention solves the problems of low practicability, large capital investment,low optimization of energy transaction between PHEV and power network, low real-time performance and low efficiency existing in the prior art.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Tunnel restraint information sending, receiving method and device
InactiveCN105681190AImplement deploymentMeet the requirements of the deploymentNetworks interconnectionNetwork communicationReal-time computing
The invention discloses a tunnel restraint information sending, receiving method and device and relates to the field of data network communication. The tunnel restraint information sending method disclosed by the invention comprises following steps of when there are loose points in building a tunnel, setting the restraint condition between every two loose points in the tunnel by a head node; calculating a route from the head node to a first loose point; transmitting the calculated route information from the head node to the first loose point and the restraint condition between every two loose points to each follow-up node through protocol messages, wherein the restraint condition between every two loose points is used for route exclusion in calculating the loose point route. The invention also discloses a tunnel restraint information receiving method and tunnel restraint information sending and receiving device. According to the technical solution provided by the invention, the restraint of each segment of route can be deployed through extending a new sub-object; and the calculated tunnel route conforms to the deployment demand better.
Owner:ZTE CORP
Railway shunting signal lamp detection method and system based on binary convolutional neural network
PendingCN110633668AAccurate detectionSolve the problem of manual identification of shunting lightsCharacter and pattern recognitionNeural architecturesData setAlgorithm
The invention provides a railway shunting signal lamp detection method and system based on a binary convolutional neural network, and the method comprises the following steps: S1, data set preparation: collecting a train head front video obtained during the running of a train, cutting the video into pictures with a set size, and manually screening pictures containing a target, thereby obtaining atarget picture; dividing the target picture into a training set and a test set according to a set proportion of a blue lamp and a white lamp; S2, network construction: constructing a binary convolutional neural network framework by utilizing the training set; S3, network training: training a binarized convolutional neural network by using a binarizing method through the test set to obtain a targetnetwork; and S4, performing network operation, and performing real-time target detection on the railway shunting signal lamp by using the target network. Binaryzation is carried out on the neural network weight to accelerate neural network operation and reduce memory consumption of the weight. The invention is high in accuracy, high in reliability and capable of accurately detecting the signal lamp in front of the train.
Owner:HEFEI LOCOMOTIVE DEPOT SHANGHAI RAILWAY BUREAU +1
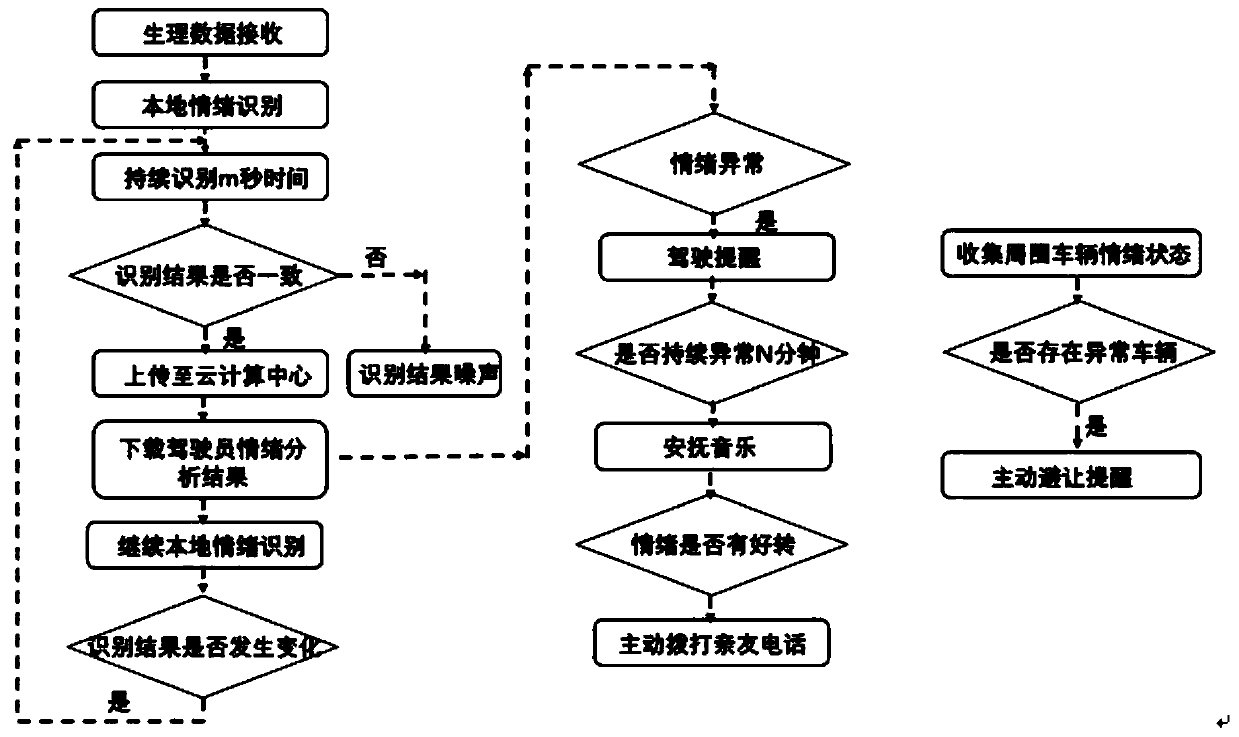
Vehicle-mounted emotion communication interacting system
InactiveCN111568444ATroubleshoot deployment issuesAddressing non-portability issuesSensorsPsychotechnic devicesComputer hardwareIn vehicle
The invention discloses a vehicle-mounted emotion communication interacting system. The system comprises a wearable intelligent device, an intelligent mobile terminal device and a cloud side server, wherein the intelligent mobile terminal device are separately in communicating connection with the wearable intelligent device and the cloud side server. According to the system, the problem in deployment of physiological sensors is solved, a clothes main body is used as a physiological data acquisition unit, the sensors are accurately arranged at optimum positions for detecting physiological signals of a human body, and the signals are accurate and sustained. The problem that other systems need additional embedding of a vehicle-mounted processor at present and generated emotion services are not transportable is solved, and the intelligent mobile terminal device and the cloud side server serve as a controlling and processing center in a coordinated manner. The intelligent mobile terminal device and the cloud side server can provide processing capacity more powerful than that of a vehicle-mounted processor, the system has transportability, and thus, the cost of service is reduced.
Owner:武汉艾瓦客机器人有限公司
Heterogeneous wireless network resource allocating method for processing emergency businesses
InactiveCN105517062ATroubleshoot bandwidth resource allocation issuesTroubleshoot deployment issuesNetwork traffic/resource managementMaximum efficiencyBusiness requirements
The invention belongs to the technical field of wireless networks, and particularly relates to a heterogeneous wireless network resource allocating method for processing emergency businesses. The method includes that in the process of distributing bandwidth resources, services different in quality are provided for different businesses, especially for emergency business needs for access to wireless networks, requirements are met preferably, and access services are provided; in the process of allocating bandwidth resources, if the emergency businesses are CBR (constant bit rate) businesses, fixed bandwidth need values must be distributed to the CBR businesses; if the emergency businesses are VBR (variable bit rate) businesses, bandwidth resources distributed to the VBR businesses need to be within a bandwidth need range. On the premise that emergency business needs are guaranteed, corresponding guarantee mechanisms are adopted for bandwidth resource allocating of common businesses. By using the method, the emergency businesses are ensured to acquire bandwidth resource allocating preferably, and more common business bandwidth requests can be contained, so that a heterogeneous wireless network system realizes maximum efficiency.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
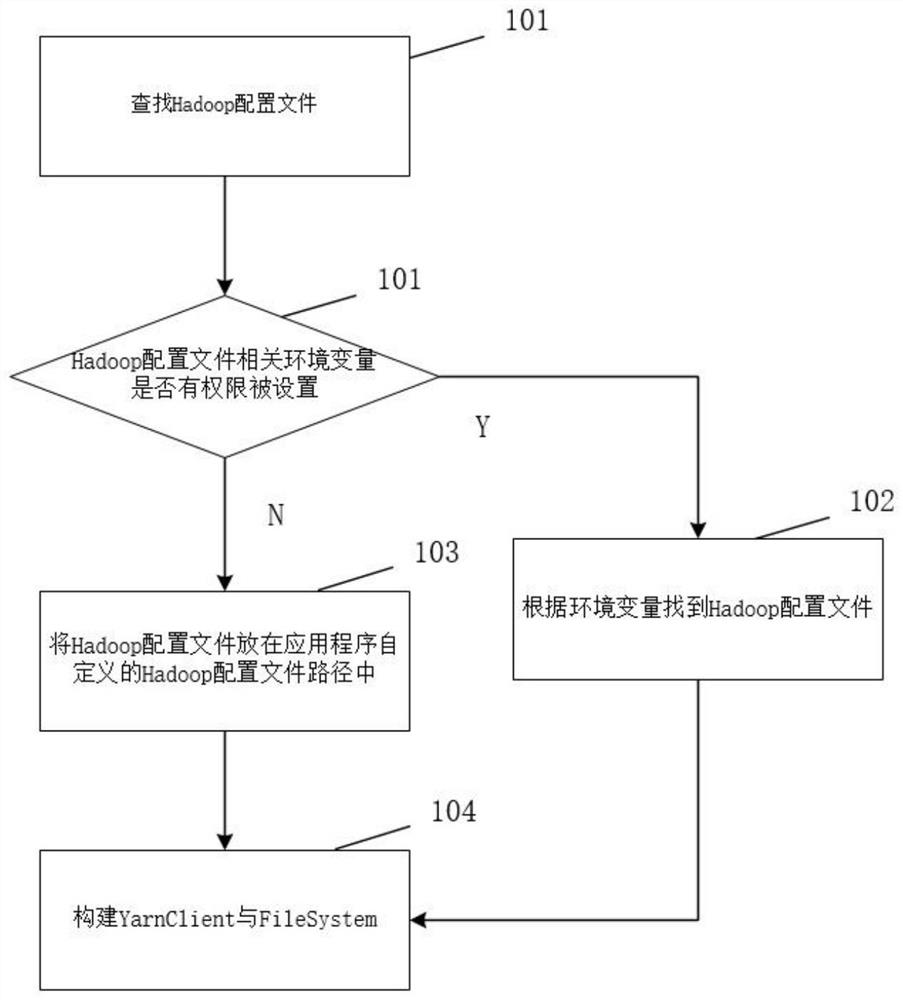
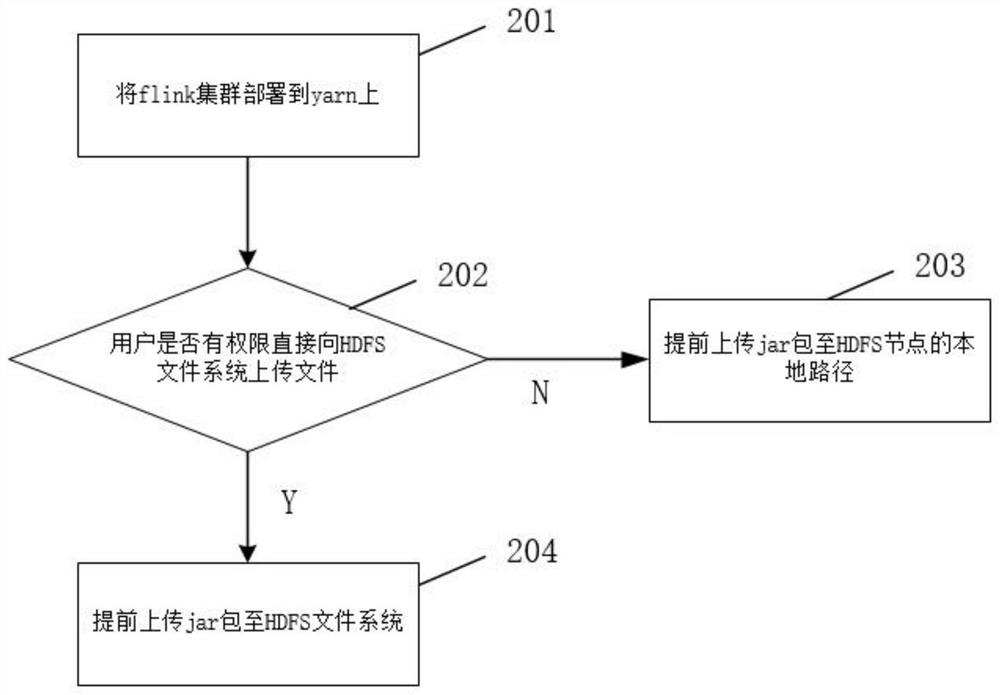
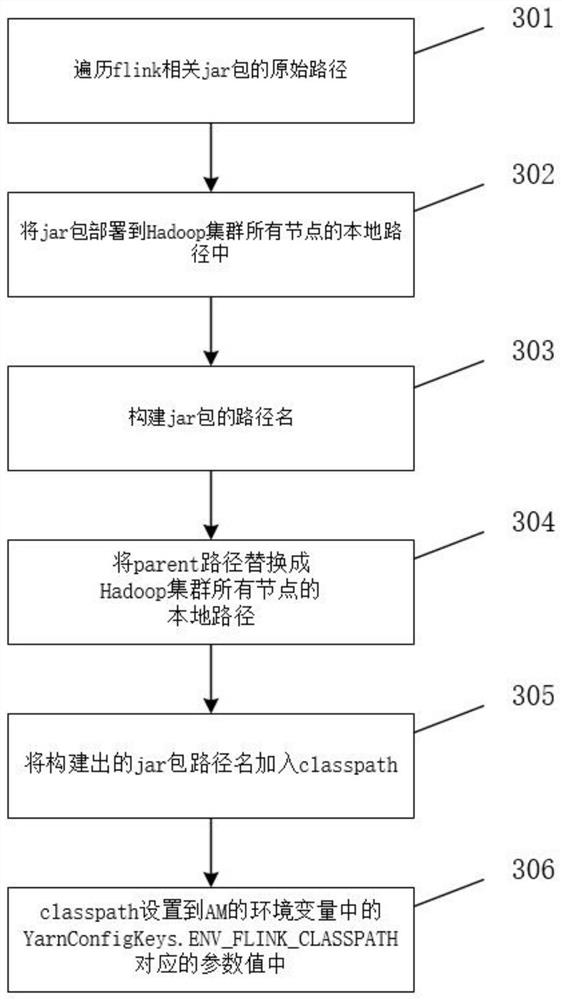
Implementation method and device for submitting flink job to yarn cluster in application program
ActiveCN114489833AImprove deployment flexibilityImprove convenienceDigital data information retrievalVersion controlThird partyYarn
The invention relates to the technical field of big data computing, discloses an implementation method and device for submitting an flink job to a Yarn cluster in an application program, solves the deployment problem of a Hadoop configuration file and a third-party dependent jar package, and realizes self-defined deployment of the Hadoop configuration file and the third-party dependent jar package by rewriting a part of functions in an flink system class. The deployment flexibility, convenience and operation efficiency of the application programs are improved, the degree of dependence on the environment is reduced, and mutual interference possibly existing between different application programs is avoided.
Owner:WUHAN DAMENG DATABASE
Micro-service optimization deployment control method, system and cluster based on cloud-side environment
ActiveCN113064712AMeet QoS requirementsEfficient task schedulingProgram initiation/switchingResource allocationEngineeringCluster based
The invention provides a micro-service optimization deployment control method and system based on a cloud-side environment and a cluster. The micro-service optimization deployment control method comprises the following steps: dividing a micro-service application into a plurality of sub-structures and mapping each sub-structure into the same node of a cloud-side continuum; allocating computing resources for each micro-service fine granularity based on the constraint of the optimization target; and monitoring the resource use condition of each node, and migrating the micro-service from a congested node to other idle nodes when discovering that the resource use is unbalanced during operation. According to the method, the problem of deployment of the micro-service in the cloud-side continuum environment can be solved, so that the resource use of the micro-service is minimized under the condition that the end-to-end delay requirement of a user request is ensured.
Owner:SHANGHAI JIAO TONG UNIV
Mobile user-oriented 5G network edge server deployment method
PendingCN114423023ATroubleshoot deployment issuesMeet needsNetwork traffic/resource managementEdge serverEngineering
The invention discloses a 5G network edge server deployment method for mobile users. The 5G network edge server deployment method comprises the following main steps: S1, dividing mobile user data in one day into a plurality of network snapshots in different time periods; s2, taking user delay and edge server deployment cost as optimization objectives, and obtaining edge server deployment schemes of different network snapshots through an improved discrete binary particle swarm optimization algorithm and a recent association algorithm; s3, obtaining a set C containing all network snapshot edge server positions; s4, calculating the position numbers of the edge servers of different network snapshots, and obtaining the maximum value K of the position numbers of the edge servers in all the network snapshots; and S5, selecting an edge server deployment position meeting the movement requirement of the user by adopting an alternate replacement mode to obtain an edge server deployment scheme. According to the method, the user delay is reduced, the mobility of the user is effectively considered, and the overall performance of the system is improved; the method is simple, and an edge server deployment scheme can be obtained more quickly.
Owner:广州大鱼创福科技有限公司
PC hierarchy-based real-time high definition video communication terminal
InactiveCN102387336ALow costMeet the technical performanceClosed circuit television systemsTwo-way working systemsMedium enterprisesHigh-definition video
The invention discloses a PC hierarchy-based real-time high definition video communication terminal. The communication terminal is easy in arrangement and high in flexibility, can be applicable to mini-medium enterprises, families and mobile users, and is characterized in that the PC comprises a PC main board supporting a USB3.0 interface; a high definition video image process, code stream control and communication scheduling unit is arranged on the PC main board, is connected with a USB 3.0 interface-based high definition camera through the USB 3.0 interface, and is further connected with a high definition video coder supporting the USB 3.0 interface or a PCI-E interface through the USB 3.0 interface or the PCI-E interface.
Owner:北京华纬讯电信技术有限公司
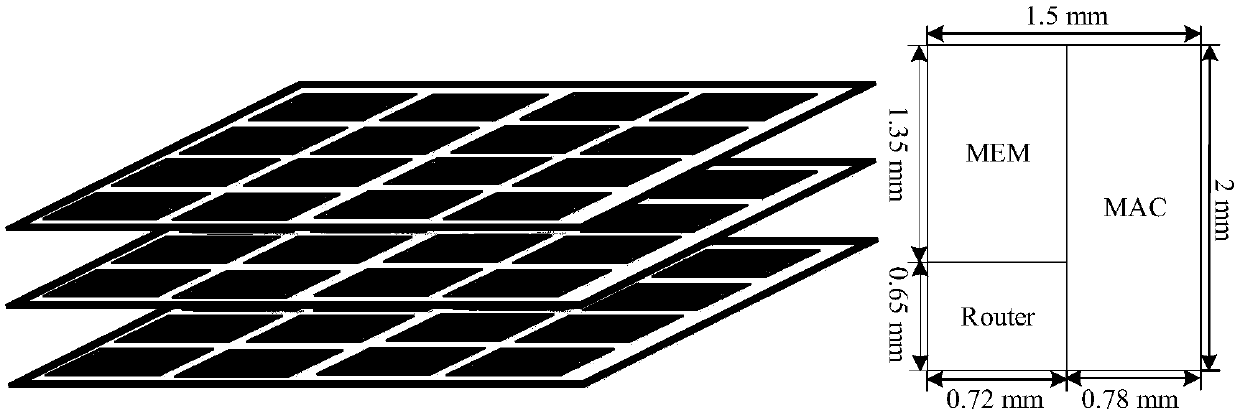
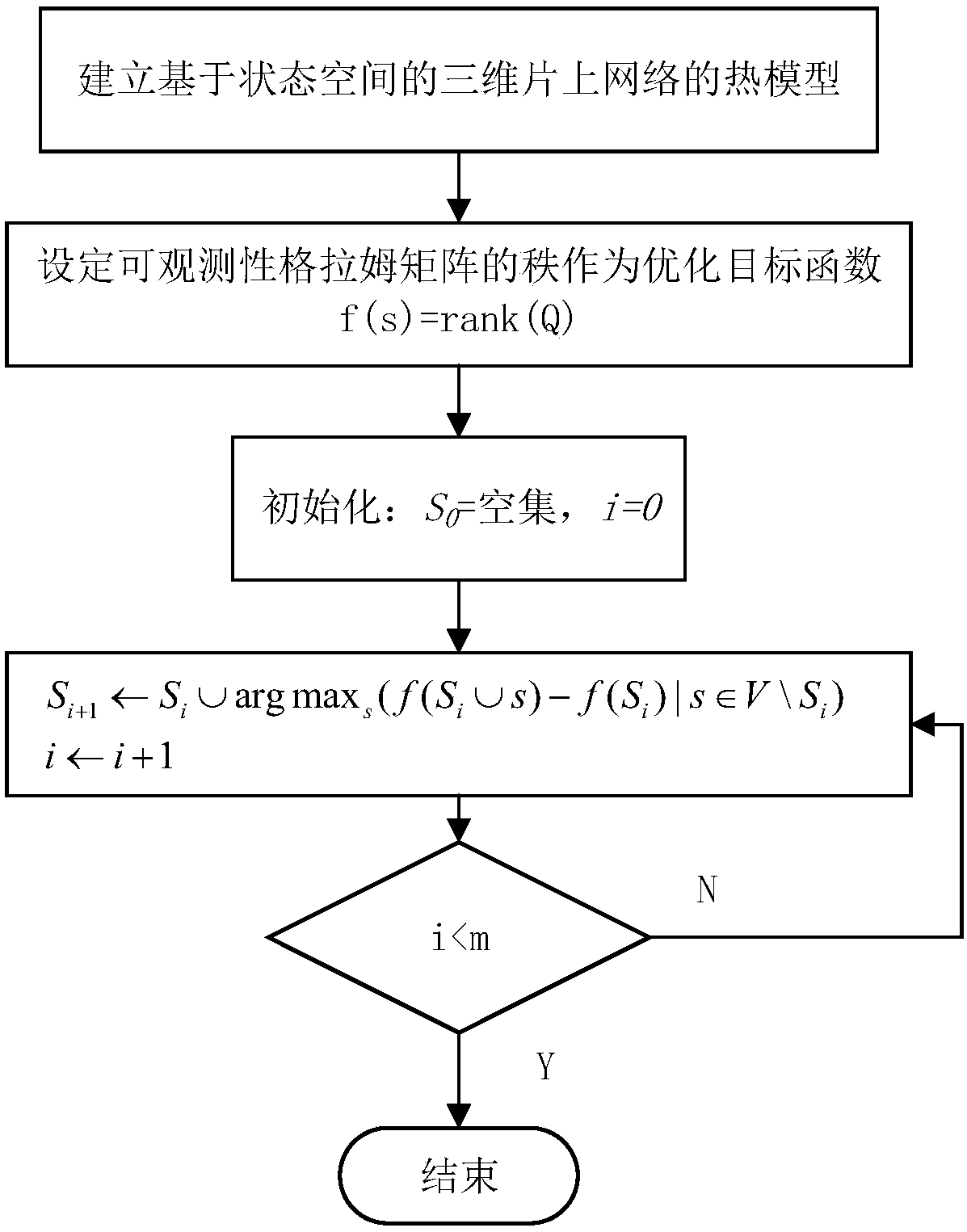
Method for deploying temperature sensors in three-dimensional network-on-chip based on greedy algorithm
ActiveCN108536931ATemperature controlTroubleshoot deployment issuesDesign optimisation/simulationSpecial data processing applicationsGreedy algorithmState space
The invention discloses a method for deploying temperature sensors in three-dimensional network-on-chip based on greedy algorithm. The method comprises the following steps: firstly establishing a thermal model of a three-dimensional network-on-chip based on a state space, and then setting an rank of an observability Gramian matrix as an optimal target function; selecting a subset S which is m in size from an available position set V of a temperature sensor for deploying the temperature sensor, the target function is maximized through the subset. By adopting the method, a second best solution is found in a polynomial time, a certain error interface is met. Compared with the conventional method, the method has the advantages that in the presence of measuring noise and under the condition oflimited sensor quantity, high-accuracy full-chip temperature rebuilding can be realized by combining Kalman filtering.
Owner:NANJING UNIV
Multi-level attack mitigation method for 5G network based on SDN and NFV
ActiveCN105516177BTroubleshoot deployment issuesTransmissionSecurity arrangementAttack graphSecurity level
The present invention provides a 5G network multi-level attack mitigation method based on SDN and NFV, including the following steps: Step 1: Extend the SDN-MN architecture; Step 2: According to the extended SDN-MN architecture, obtain the application of SDN-MN and the Evidence-driven security assessment mechanism for NFV detection; Step 3: measure the security level of the static network through the evidence-driven security assessment mechanism and the generated new probability evidence-driven attack graph; Step 4: Security in the evidence-driven security assessment mechanism The evaluation algorithm calculates the state node probability, action node probability and posterior probability in the attack graph; step 5: use SDN control and NFV to deploy the attack mitigation mechanism, and deploy the corresponding attack mitigation plan based on the security level obtained from the evidence-driven attack graph. The present invention can be directly applied to the 5G network, and can make policy judgment according to the current network environment in time, and solve the deployment problem of the attack mitigation policy.
Owner:SHANGHAI JIAOTONG UNIV
Simplified generation and deployment method of virtual device
InactiveCN108874509ASolve the problem that the volume is too large and the distribution is difficultResolve commitSoftware simulation/interpretation/emulationSoftware engineeringApplication software
The invention provides a simplified generation and deployment method of virtual device. The generation and deployment method realizes the automatic generation and deployment of the virtual device by dividing a complete virtual machine image used by the virtual device into two parts of a base template and a business device. The generation and deployment method solves the problems that submission, deployment and configuration of application software is difficult and time consuming, and solves the problems that the virtual device is too large in volume and difficult to deliver in the prior commercial technology, so that can realize centralized delivering, zero configuration deployment and going online rapidly of the application.
Owner:HEFEI LANGJIN ANTI COUNTERFEITING TECH CO LTD
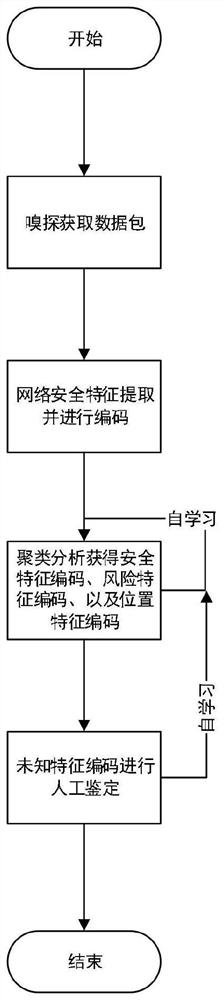
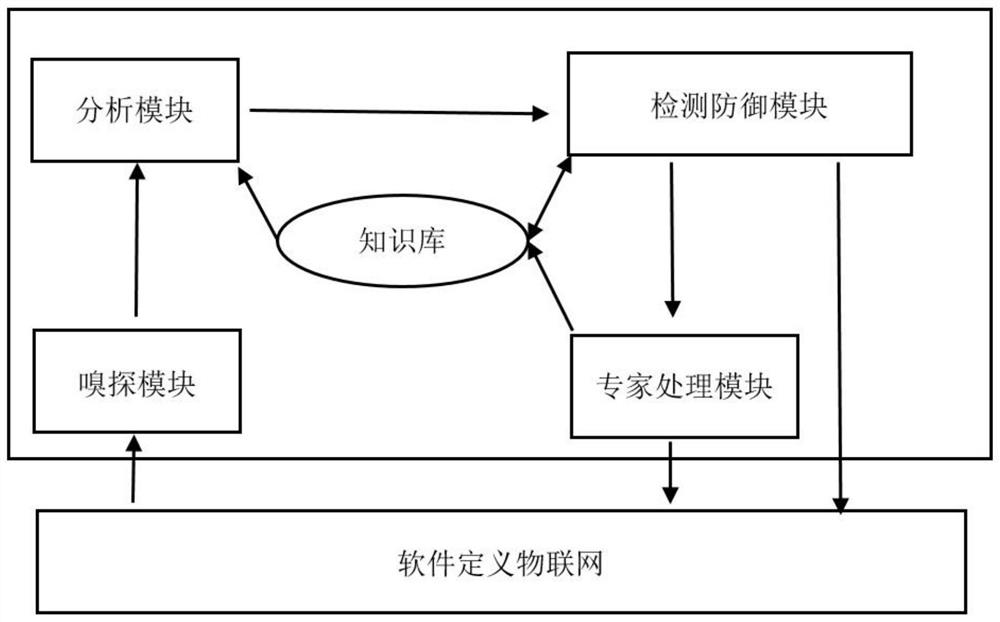
Software-defined Internet of Things self-learning security defense method and system
ActiveCN111669396AEase node configuration managementSelf-learning abilityCharacter and pattern recognitionNeural architecturesData packThe Internet
The invention discloses a software-defined Internet of Things self-learning security defense method and system. The method comprises the following steps: (1) sniffing and obain a data packet which issent by a software-defined Internet of Things node and is contained between a medium access control layer and a network layer; (2) performing network security feature extraction and encoding; (3) clustering the codes of the network security feature values; (4) comparing each category with elements in a known security network security feature code set and elements in a known risk network security feature value code set, automatically performing judging and updating; and (5) identifying and updating unknown network security feature codes by network security expert group members. The system comprises a sniffing module, an analysis module, a detection defense module and a knowledge base; according to the invention, the Internet of Things node configuration management work of an Internet of Things administrator is effectively reduced, the software-defined Internet of Things security defense system is automatically updated, and the self-adaption to the dynamic change of the software-definedInternet of Things network environment is realized.
Owner:SHAOXING UNIVERSITY
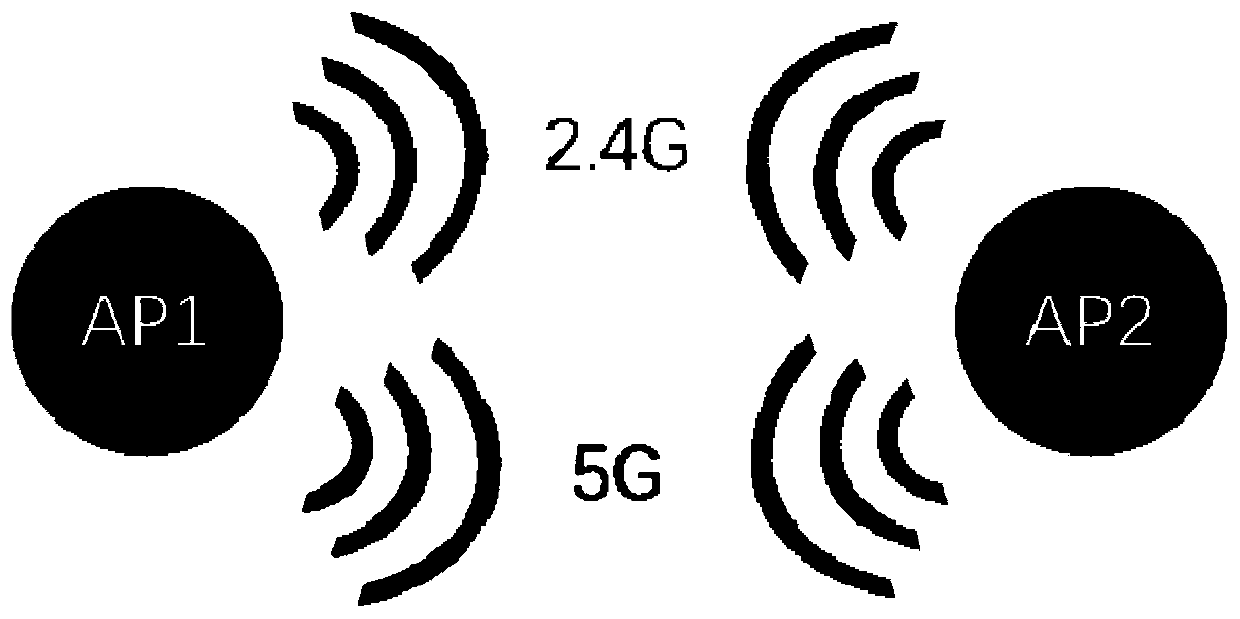
Channel deployment method and device, wireless access point and computer storage medium
ActiveCN111447022AImplement deploymentTroubleshoot deployment issuesTransmission monitoringWireless communicationWireless access pointBandwidth utilization
The invention discloses a channel deployment method and device, a wireless access point and a computer storage medium, and the method is applied to any wireless access point in a wireless networking system, and comprises the steps: obtaining the wireless state information of each frequency band of the wireless access point, wherein the wireless state information of each frequency band comprises acurrent value negotiated by a 2.4 G frequency band and a front end and a current channel utilization rate of a 5G frequency band; judging whether a preset bridging pause condition is met or not according to the wireless state information of each frequency band; and when judging that the preset pause bridging condition is met, switching the current working mode of the 2.4 G frequency band of the wireless access point into an access point mode, and carrying out channel deployment on the 2.4 G frequency band of the wireless access point. By adopting the embodiment of the invention, the channel deployment in the wireless networking system can be realized so as to reduce the channel competition and increase the bandwidth utilization rate.
Owner:TP-LINK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com