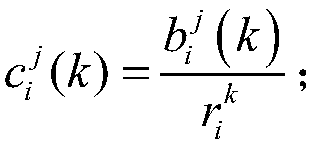Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
308results about How to "Implement deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
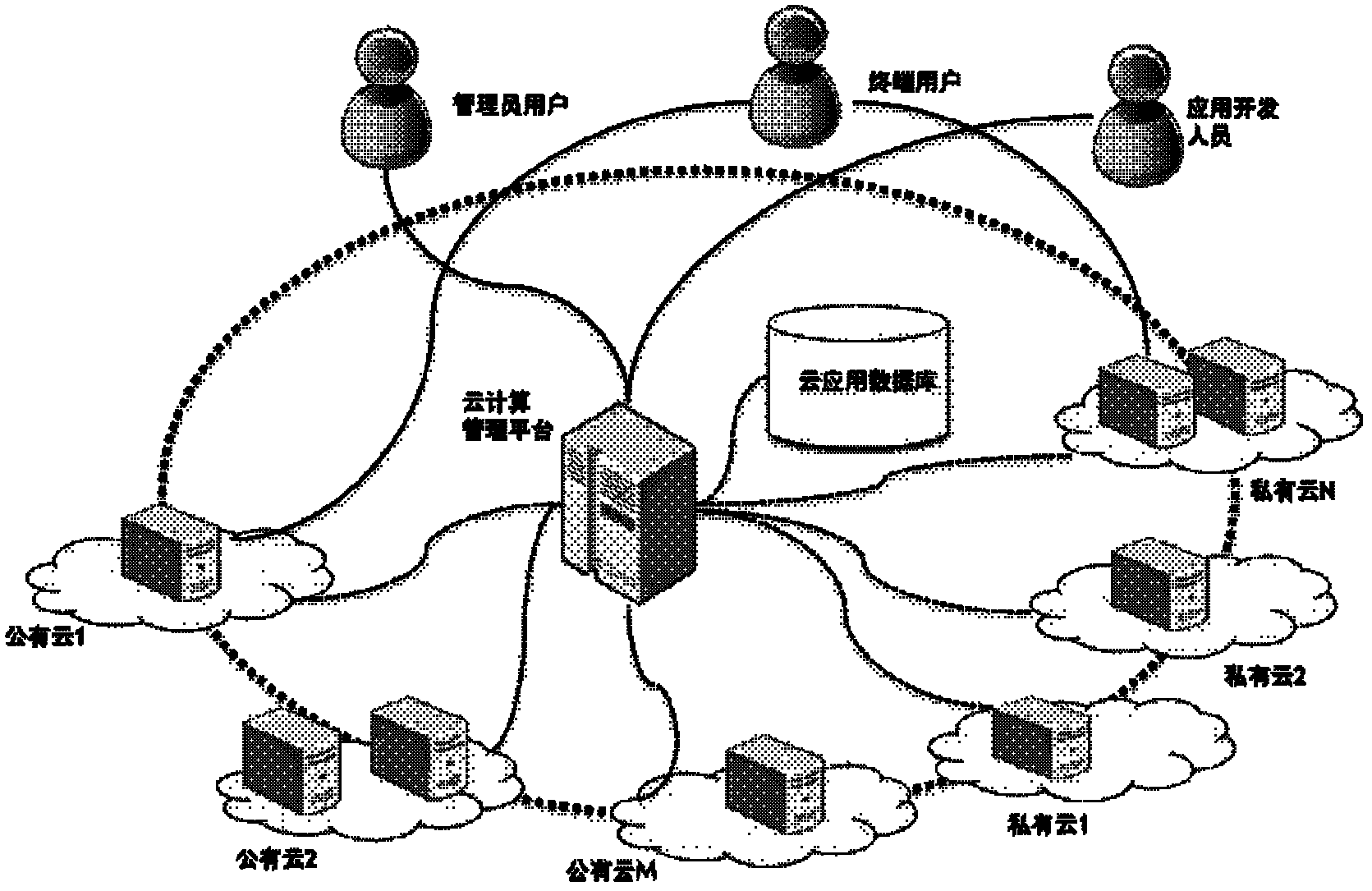
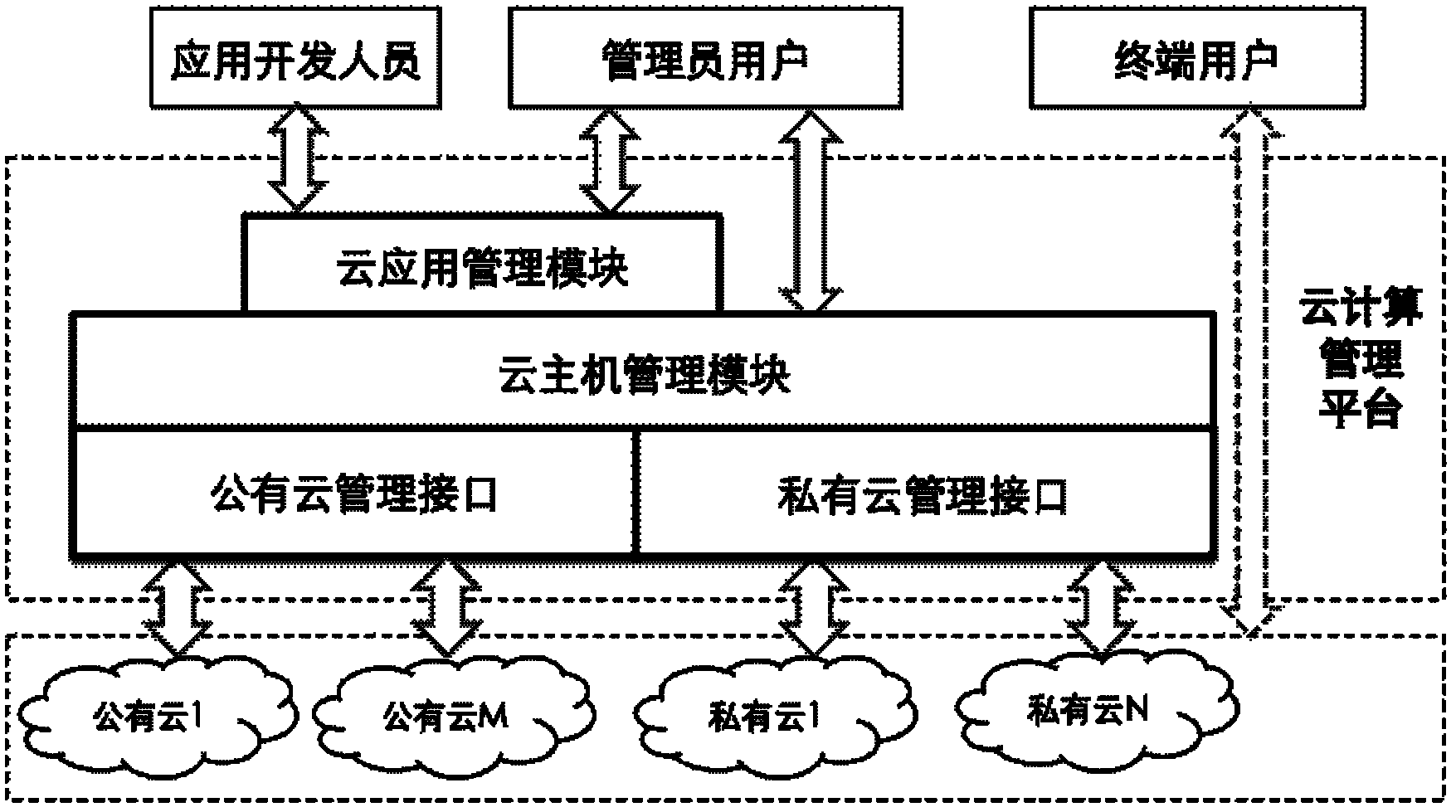
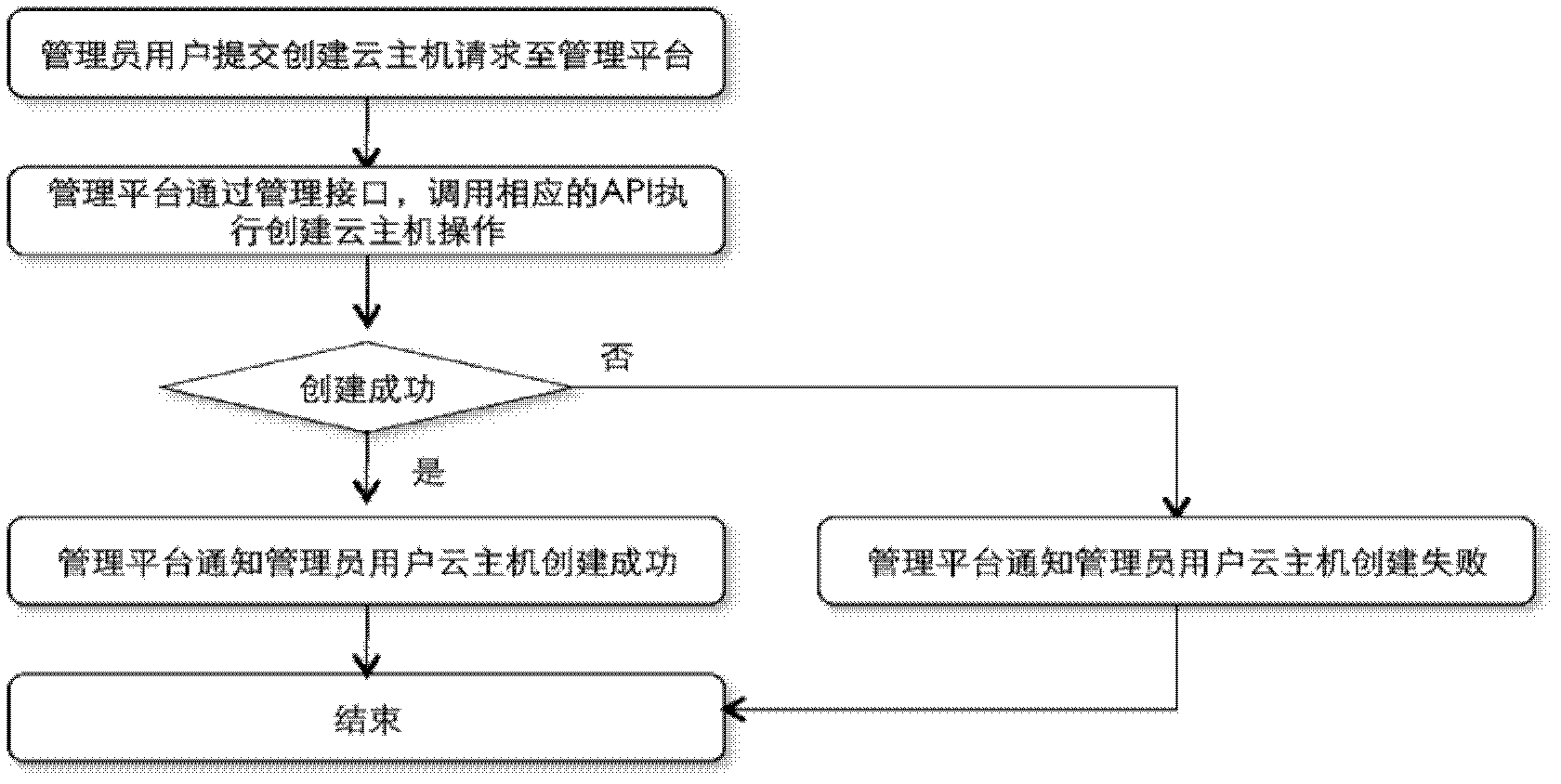
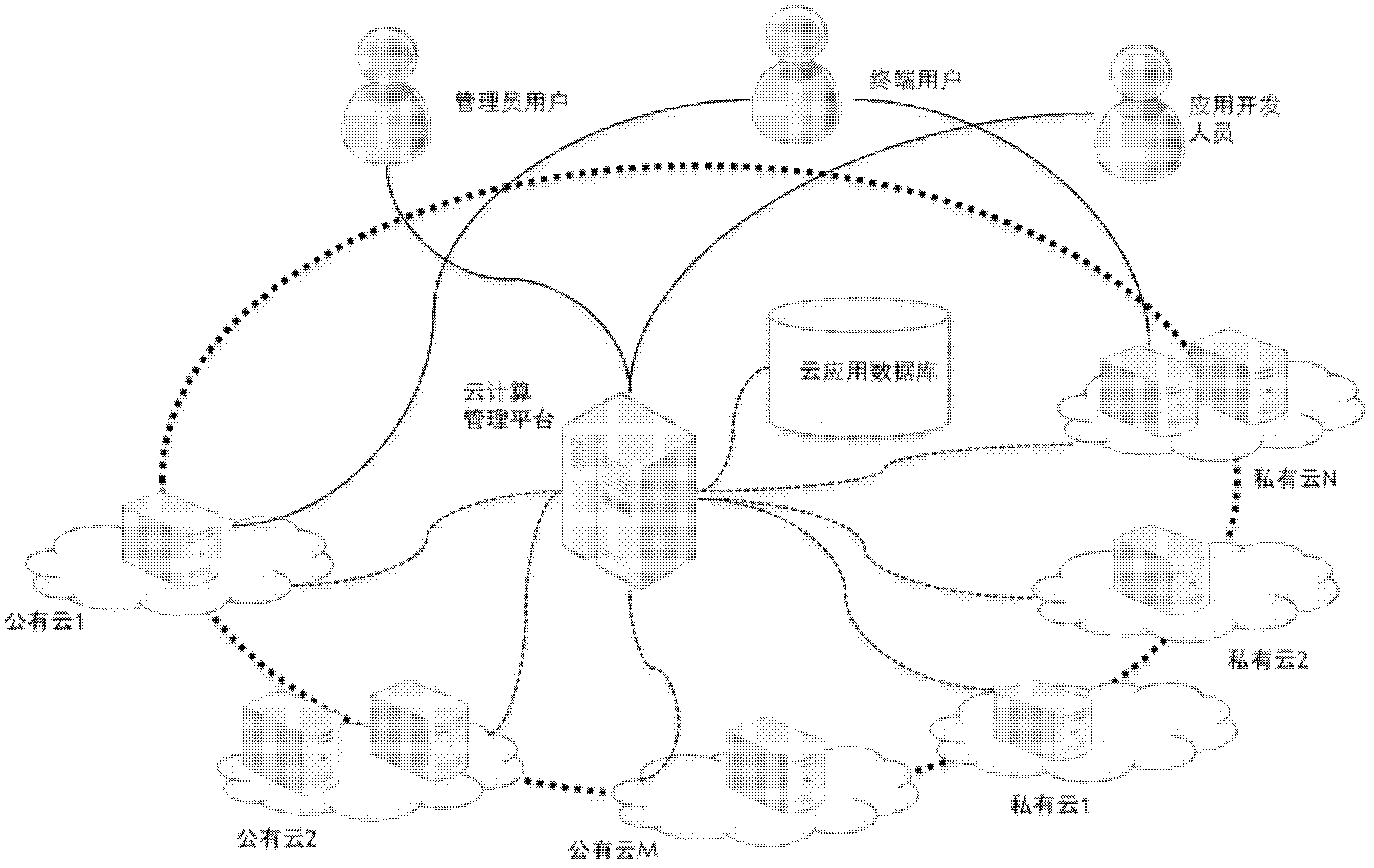
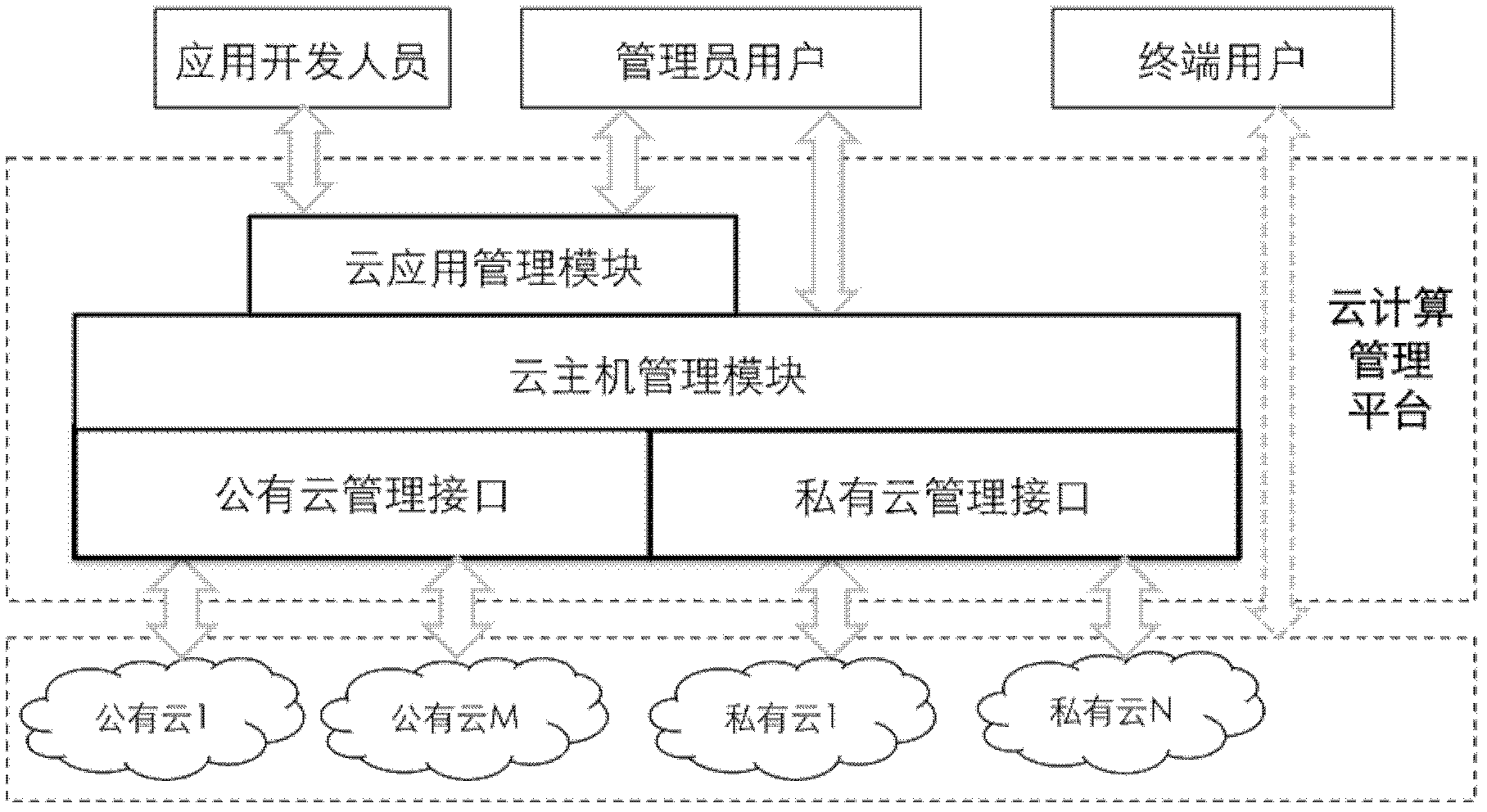
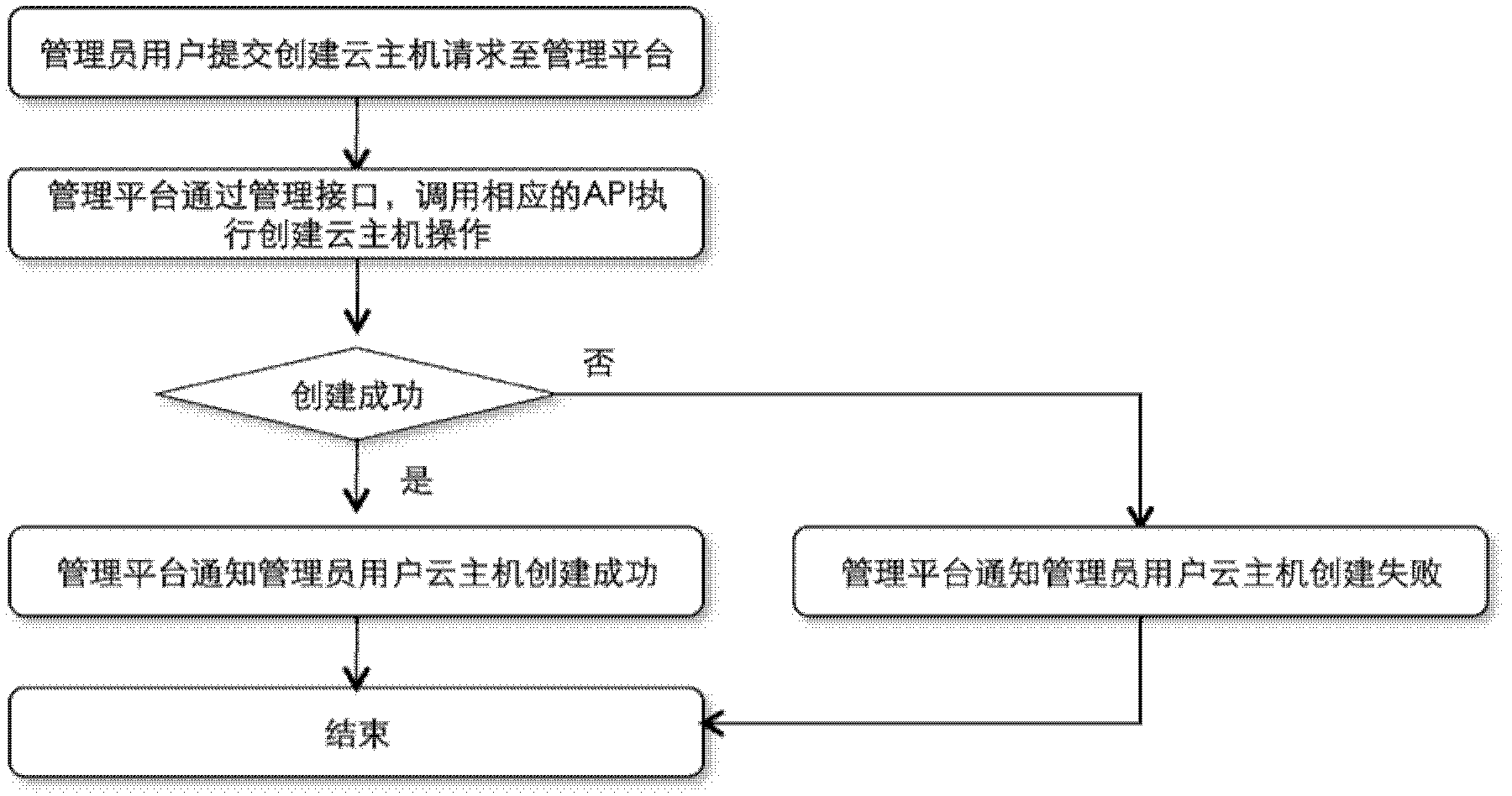
System for managing cloud computing service and cloud computing management method
ActiveCN102427481ARealize unified managementAutomate deploymentTransmissionManagement systemCloud management
The invention discloses a system for managing cloud computing service, which comprises a cloud computing management platform and a cloud application database, wherein the cloud application database is connected with the cloud computing management platform, and the cloud computing management platform is connected with public clouds or private clouds through a network; and the cloud application database comprises all installation packages for cloud application; and the cloud computing management platform is used for helping customers to realize managing a cloud host in the public clouds or private clouds and cloud application in the cloud host. The cloud computing management system provided by the invention realizes the unified management of multiple public clouds and multiple private clouds through a public cloud management interface and a private cloud management interface, so that great convenience is provided for users.
Owner:EAYUN INC
Self-contained technology for installing application software based on ITRON
InactiveCN1959631ADynamic installationImprove refactoring effectSpecific program execution arrangementsSoftware engineeringCore component
An autonomous assembling technique of application software based on ITRON includes container in charging of interaction between software application component and operation environment and in charging of setting up application component according to design policy, domain configuration file for describing hardware unit and software component in system, automatic assembly / disposal tool for providing visualized editor of domain configuration file and automatic assembly / disposed tool being used to generate domain configuration file as required by container.
Owner:上海启明软件股份有限公司 +1
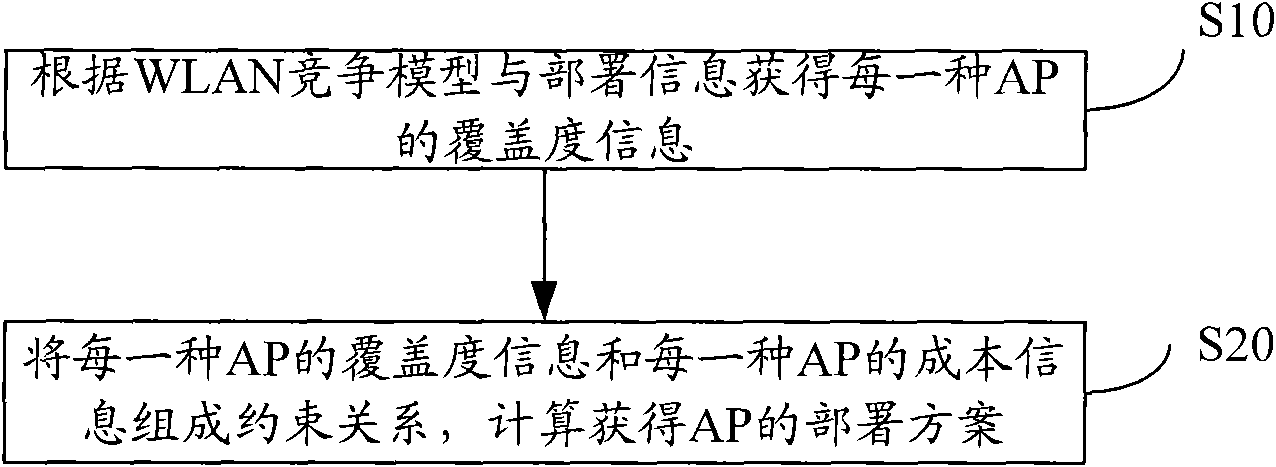
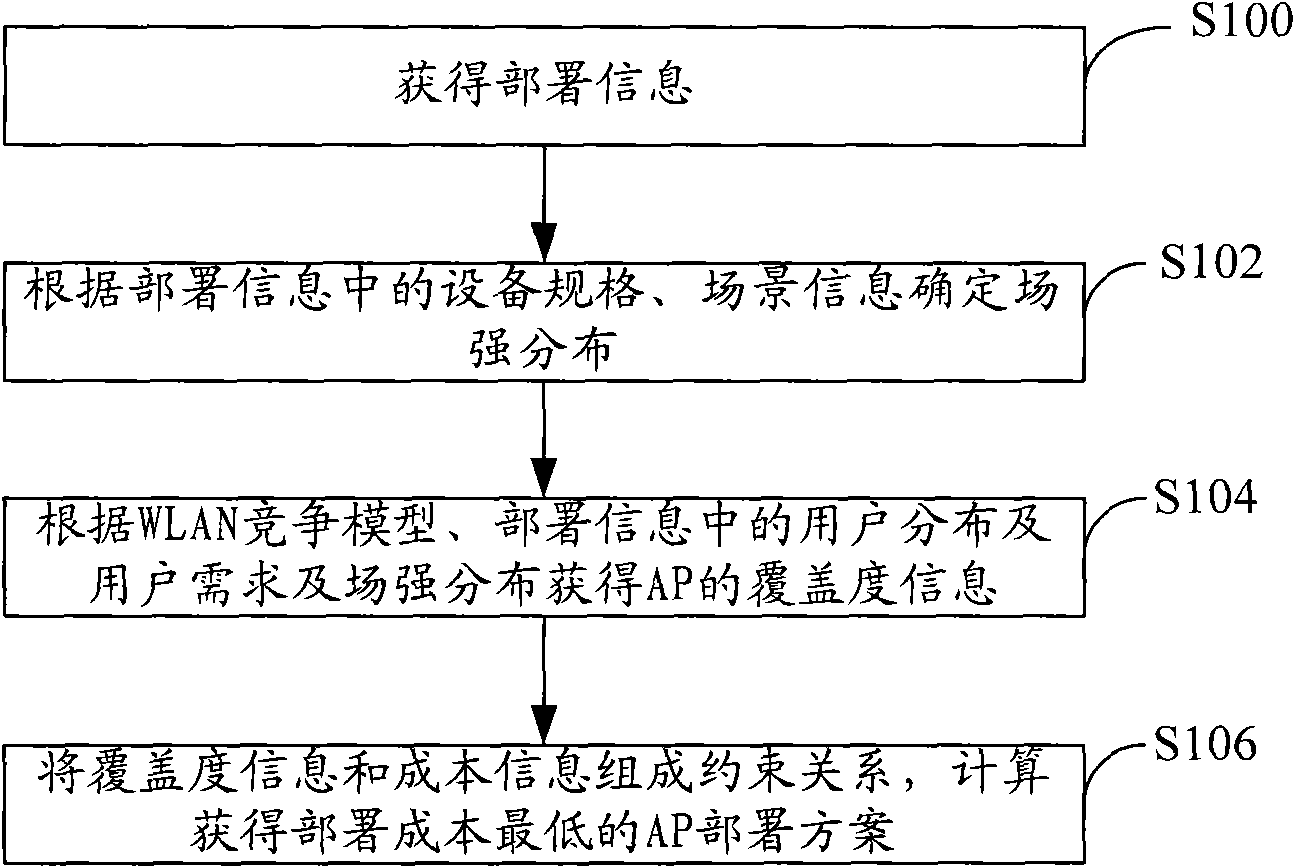
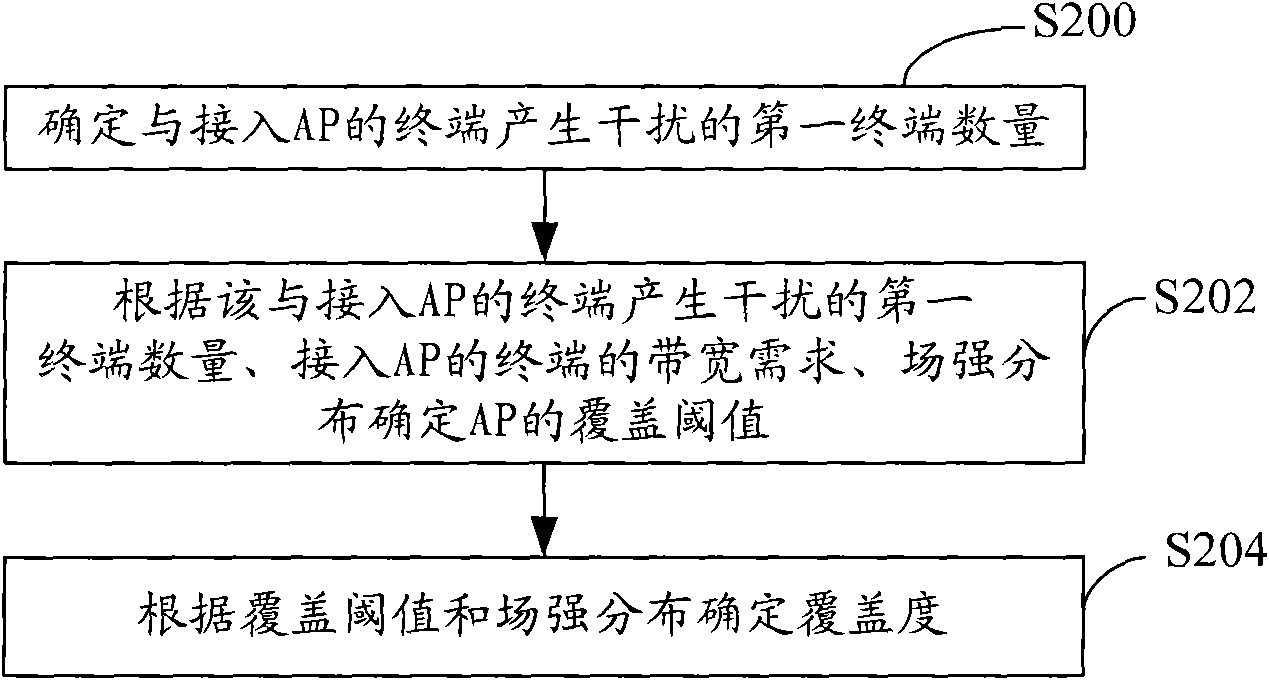
Method and system for acquiring deployment scheme of wireless local area network (WLAN) access point (AP)
ActiveCN102056180AImplement deploymentNetwork topologiesNetwork planningEngineeringReal-time computing
The embodiment of the invention discloses a method for acquiring a deployment scheme of a wireless local area network (WLAN) access point (AP). The method comprises the following steps of: acquiring coverage information of each AP according to a WLAN competition model and deployment information; and forming a constraint relationship between the coverage information of each AP and cost information of each AP and calculating to acquire the deployment scheme of the AP. The embodiment of the invention also provides a device and a system. The device and the system can automatically acquire the deployment scheme of the AP and control cost.
Owner:HUAWEI TECH CO LTD
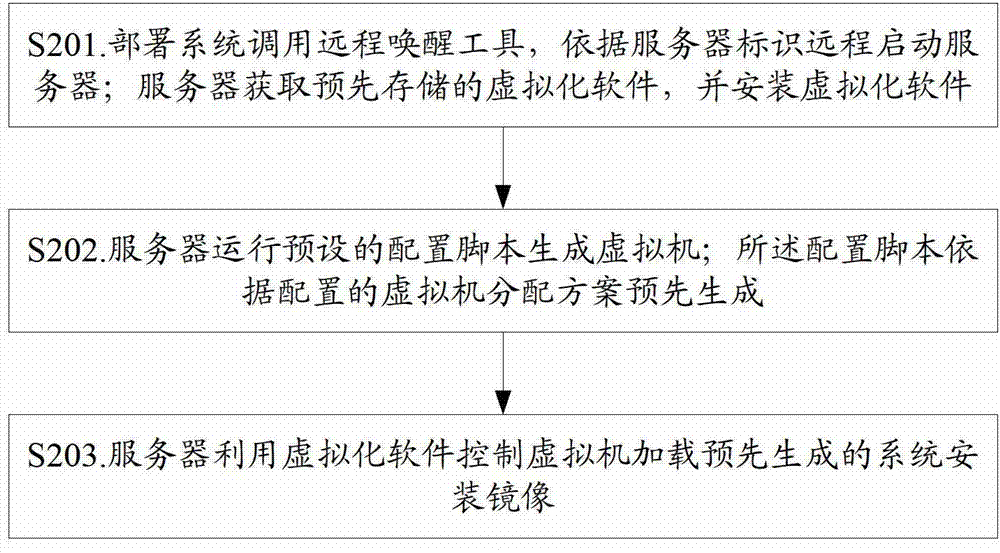
Management method and platform of server cluster
ActiveCN102932408AImplement deploymentImplement configurationProgram loading/initiatingTransmissionVirtualizationSystem call
The invention provides a management method and platform of a server cluster. The method comprises the following steps of: calling a long-distance wakening tool by a deployment system; starting a server according to server identifications in a long-distance manner; acquiring pre-stored virtualization software by the server; arranging the virtualization software; running a pre-set configuration script by the server so as to generate a virtual machine, wherein the configuration script is per-generated according to a configured virtual machine allocation plan; and controlling the virtual machine by the sever through using the virtualization software to load pre-generated system installation mirror images. According to the management method and platform of the server cluster, the development and the configuration of a virtual environment of the server cluster can be automatically realized.
Owner:CHINA TELECOM CLOUD TECH CO LTD
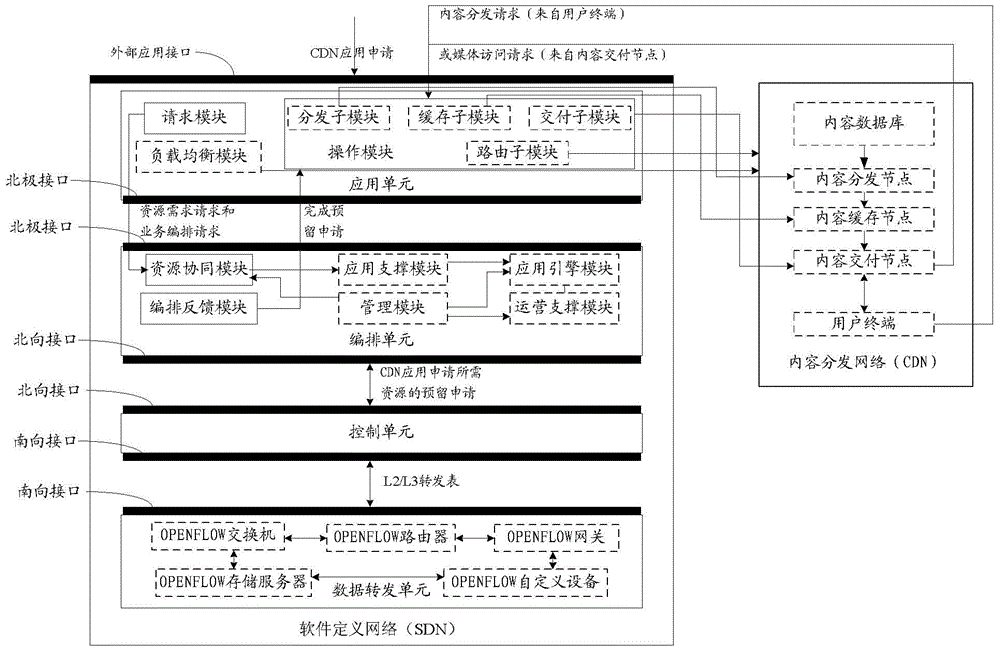
Method and system for realizing content delivery network based on software defined network
ActiveCN105577714ARealize the planSolve the closing problemTransmissionContent distributionOrchestration
The invention discloses a system and a method for realizing a content delivery network (CDN) based on a software defined network (SDN). The method comprises the steps of adding a complete business logic function of the CDN into a SDN application layer; when an application unit receives a CDN application request, transmitting a resource requirement and a business orchestration request to an orchestration unit; performing business orchestration by the orchestration unit according to related information of the SDN, transmitting the reserved application of the required resource to a control unit for acquiring the required resource, and afterwards determining a content distributing / delivery path according to network load balance and router condition; establishing an L2 / L3 forwarding table according to an SDN control surface forwarding related strategy and transmitting the L2 / L3 forwarding table to a data forwarding unit; and performing related operation by the application unit according to a content distributing or media accessing request, and performing data forwarding by the data forwarding unit. The method and the system realize DCN based on the SDN and effectively settle the problems of CDN bearing network closeness, hardware specificity and management complexity. Furthermore the system and the method realize reasonable selection for resources, engines and paths required by the CDN.
Owner:ZTE CORP
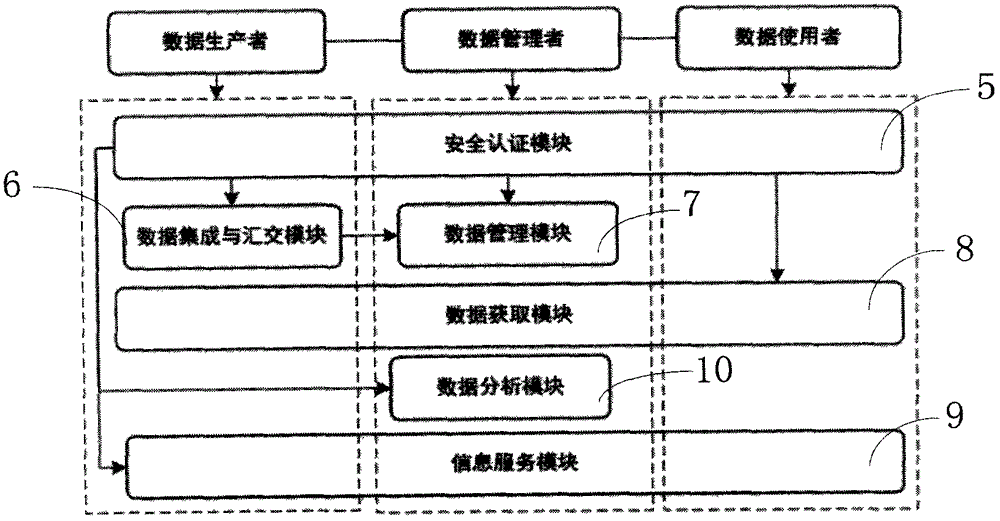
Service-oriented intelligent residential area real-time database system and working method thereof
ActiveCN107122422AImprove data exchange efficiencyReduce software development cycle and application costData processing applicationsSpecial data processing applicationsData conversionCondition monitoring
The invention discloses a service-oriented intelligent residential area real-time database system and a working method thereof. The system comprises a data interface layer, a data persistence layer, a call service layer, a data model layer and a service layer, wherein the data interface layer is used for performing classified collection on sensor information of a safety protection system or a building automation system of a residual area, packaging data according to a unified communication protocol and transmitting the packaged data into a memory of the data persistence layer in a binary data stream form; the data persistence layer is used for unified storage of the data collected by the data interface layer; the call service layer performs data analysis and storage; the data model layer is used for providing measurement points and an internet-of-things device and performing data associative analysis and prediction; and the service layer is used for providing core services including data analysis, data cleaning, data compression, data decompression, data conversion, real-time data access, historical data access, state monitoring, business management, log recording and alarm services. A real-time database has the characteristics of loose coupling, service reusability and the like.
Owner:SHANDONG JIANZHU UNIV
Network service intelligent deployment method and system
ActiveCN108762768AGuaranteed uptimeImplement deploymentTransmissionPhysical realisationVirtualizationTransfer probability
The invention discloses a network service intelligent deployment method and a system, which relates to the field of network function virtualization. The method comprises the following steps: describing virtual resources in a tensor-based formal description mode of virtual resources; based on artificial intelligence technology and historical sample data, calculating the transfer probability of eachvirtual resource, generating a transfer tensor model, and predicting the change trend of the virtual resource utilization rate according to the transfer tensor model; according to the change trend prediction result, allocating the most suitable virtual resources to the virtual network function to ensure the normal operation of the virtual network function. The invention intelligently realizes thedeployment and resource allocation of the virtual network function in the telecommunication cloud platform.
Owner:FENGHUO COMM SCI & TECH CO LTD
Cloud computing management system and cloud computing management method
InactiveCN102882908ARealize unified managementImprove efficiencyData switching networksCloud managementManagement system
The invention discloses a cloud computing management system. The system comprises a cloud computing management platform and a cloud application database, wherein the cloud application database is connected to the cloud computing management platform; the cloud computing management platform is connected with public clouds or private clouds through networks; the cloud application database comprises installation packages of all cloud applications; and the cloud computing management platform is used for helping a client to manage cloud hosts in the public clouds or private clouds and the cloud applications in the cloud hosts. By the cloud computing management system, various public clouds or private clouds are managed in a unified mode through a public cloud management interface and a private cloud management interface, and great convenience is brought to a user.
Owner:EAYUN INC
Regional resource environmental data sharing and comprehensive service platform
InactiveCN104657918AImplement deploymentAchieve runnabilityData processing applicationsWeb serviceMathematical model
The invention discloses a regional resource environmental data sharing and comprehensive service platform. A data resource layer, a business logic layer, a Web service layer and a Web layer are arranged. The problems that applicability conditions cannot meet requirements of modern social resource environment administrative decisions to resource environmental mathematic models and structures are complex gradually are solved; the sharing and comprehensive service platform has compatibility of isomerous integration, realizes deployment and operation of a trans-department and cross-operating system, and ensures sharing and application of a plurality of metadata standards under a platform, so as to meet requirements of intersection of multidisciplinary data resources; besides, the sharing and comprehensive service platform is simple in structure, and convenient to operate, and injects novel vitality into development of resource environmental system modeling.
Owner:胡宝清
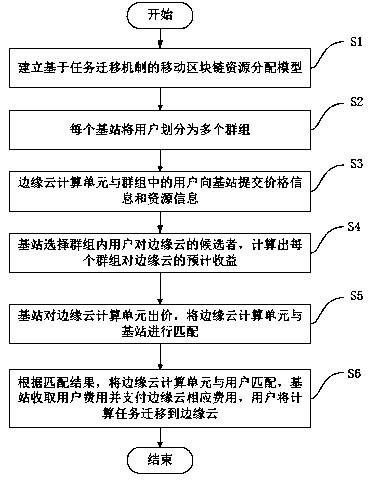
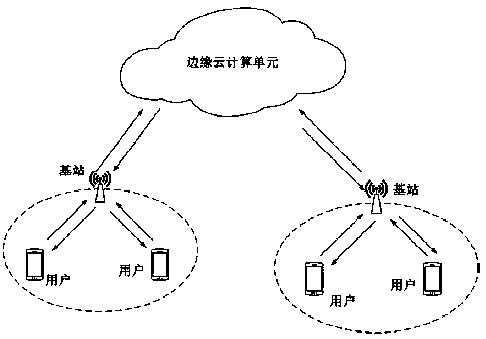
A mobile block chain resource allocation method based on a task migration mechanism
InactiveCN109165972AImprove computing efficiencyNo energy consumptionFinanceMarketingResource informationDistribution method
The present invention relates to the technical field of mobile block chain cloud computing, and more particularly relates to a mobile block chain resource allocation method based on task migration. The invention provides a three-layer matching method, comprising the following steps: in a mobile block chain resource allocation model, a base station divides users into a plurality of groups; the userin the group submits the computing resource demand and bidding information to the base station, and the edge cloud computing unit submits the self-allocatable resources to the base station; the basestation completes the matching between the user and the edge cloud computing unit according to the resource information of the user and the edge cloud, and loads the computing task of the user into the corresponding edge cloud, and the base station collects the user fee and pays the fee to the edge cloud. The method does not consume too much energy and computational power in the transaction process, can realize the deployment of the block chain at the mobile end, meets the needs of the user for mining on the mobile phone, increases the income of the user with resource surplus, and enables users to have higher personal income and overall income.
Owner:GUANGDONG UNIV OF TECH
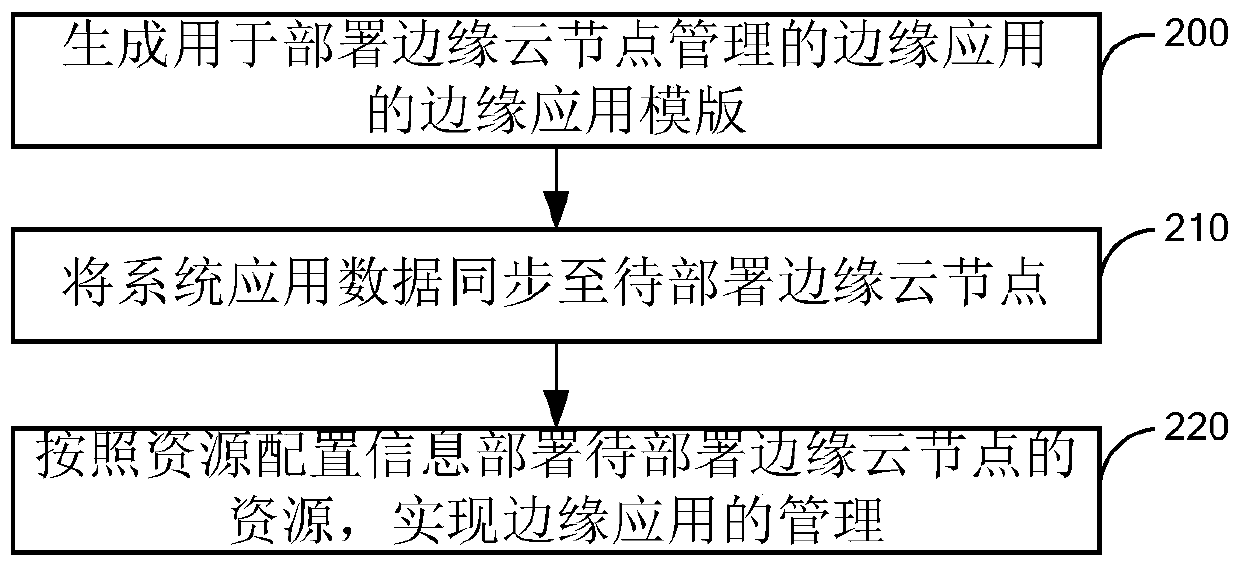
Edge application management method and system
ActiveCN110737442ARealize managementReduce management difficultyVersion controlProgram controlData synchronizationCloud data center
The invention provides an edge application management method and system, and the method comprises the steps: generating an edge application template for deploying an edge application managed by an edge cloud node, and enabling the edge application template to comprise the resource configuration information for deploying edge cloud node resources and the system application data of an elastic cloudserver in a cloud data center; synchronizing the system application data to an edge cloud node to be deployed; and deploying resources of the to-be-deployed edge cloud node according to the resource configuration information to realize management of the edge application. By applying the scheme provided by the embodiment of the invention, the unified deployment of the edge applications managed by the edge cloud node can be realized through the edge application template, and the deployment workload of a user and the management difficulty of the edge applications are reduced.
Owner:XIAMEN WANGSU CO LTD
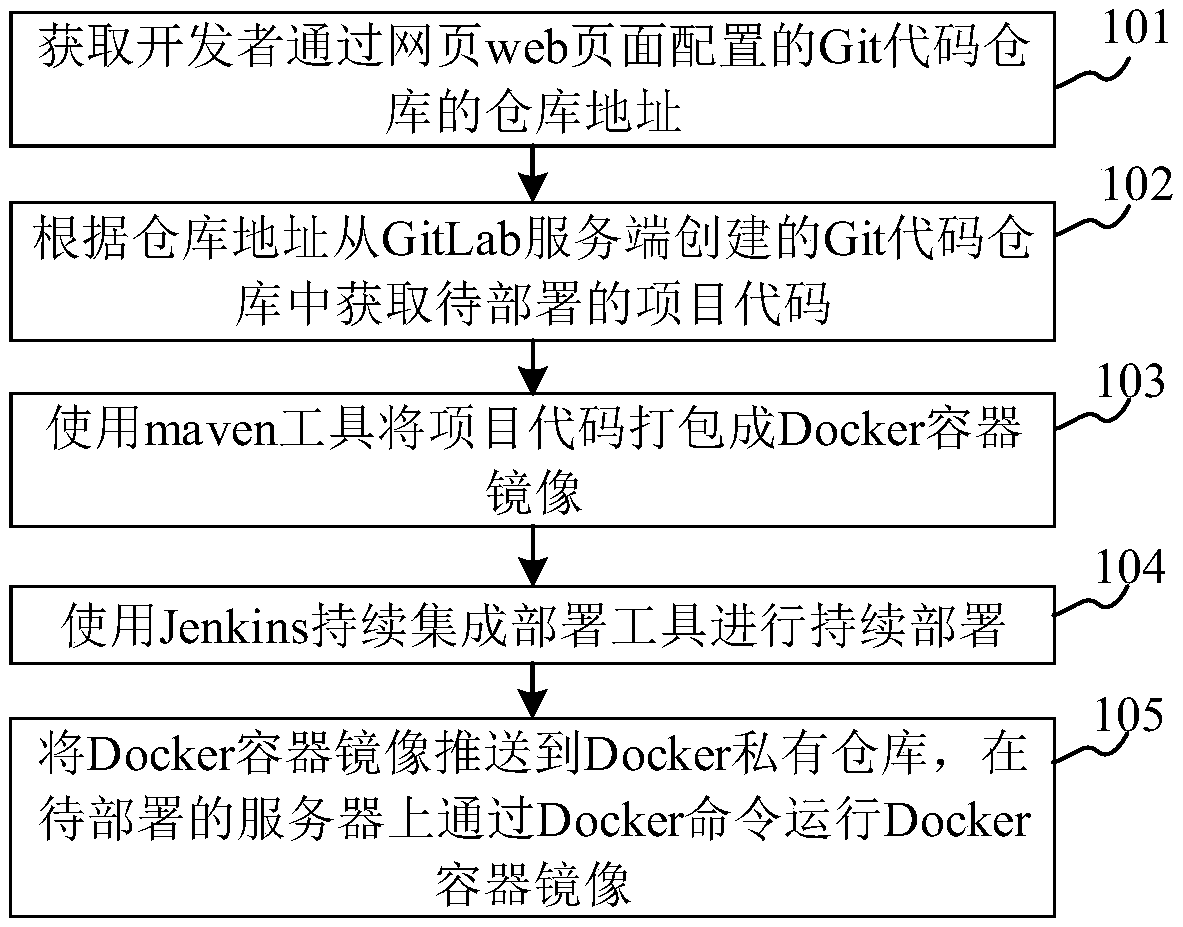
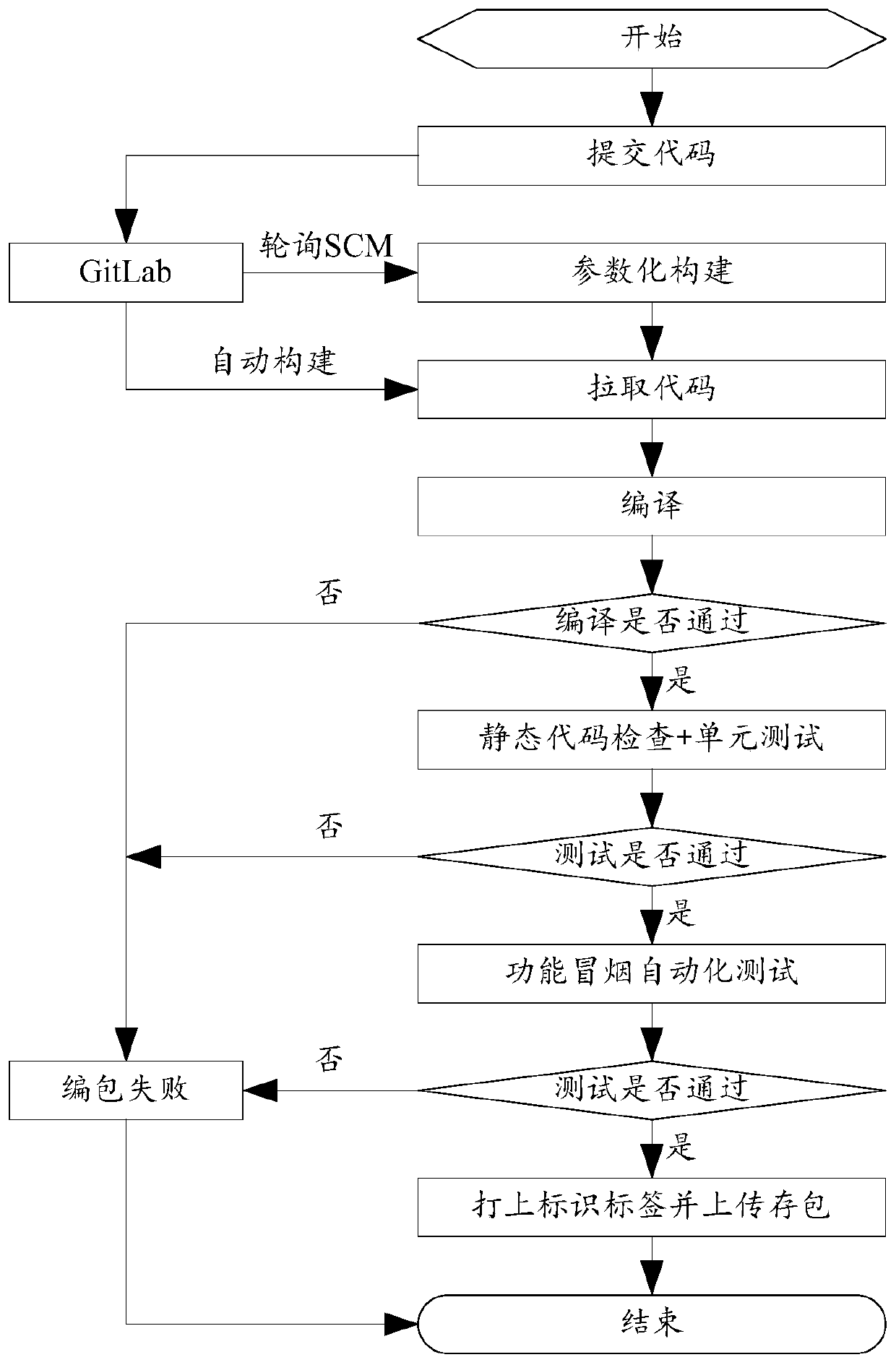
Project deployment method and device
InactiveCN109597644ASolve manual packaging and compilationSolve efficiency problemsVersion controlSoftware deploymentContinuous integrationSoftware engineering
The invention relates to a project deployment method and device, and belongs to the technical field of project development. The method comprises the steps: obtaining a warehouse address of a Git codewarehouse configured by a developer through a web page; Obtaining a to-be-deployed project code from a Git code warehouse created by the GitLab server according to the warehouse address; Packaging theproject code into a Docker container mirror image by using a mavene tool; using A Jenkins continuous integration deployment tool to perform continuous deployment; Pushing the Docker container mirrorimage to a Docker private warehouse, and operating the Docker container mirror image on a to-be-deployed server through a Docker command; The problem that the efficiency of manual packaging, compilingand code deploying is low can be solved; Automatic application service deployment is realized, and the project deployment efficiency is improved.
Owner:JIANGSU FENGYUN TECH SERVICE CO LTD
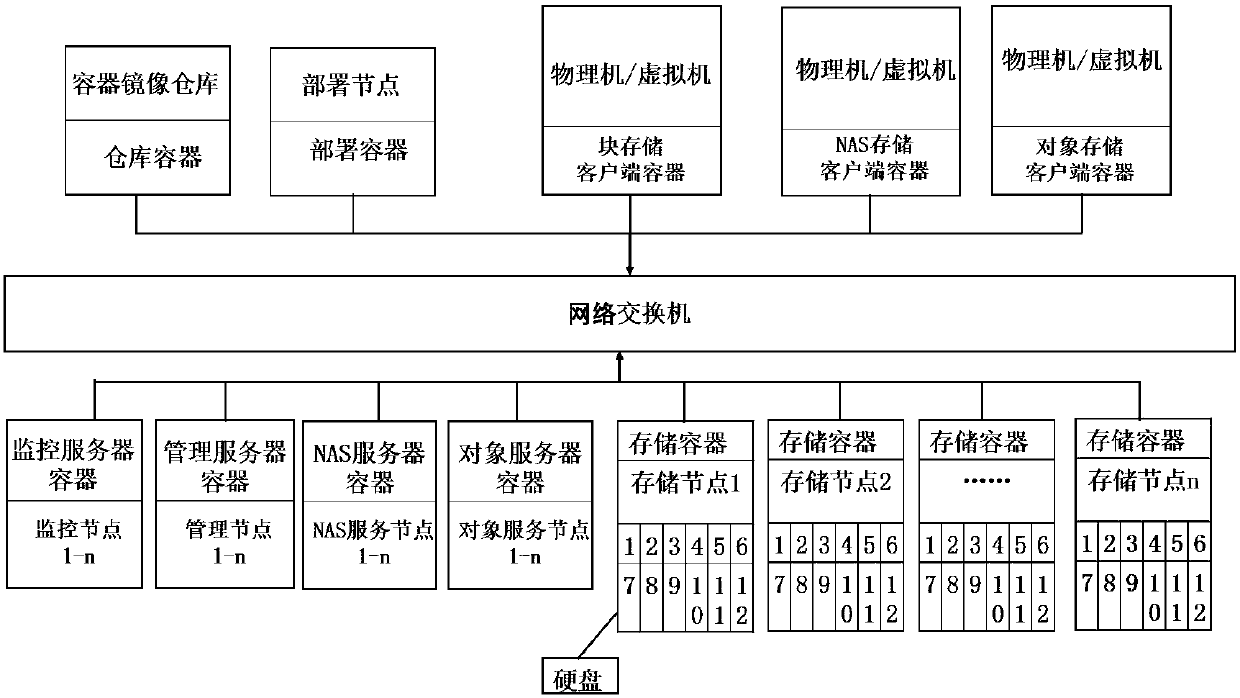
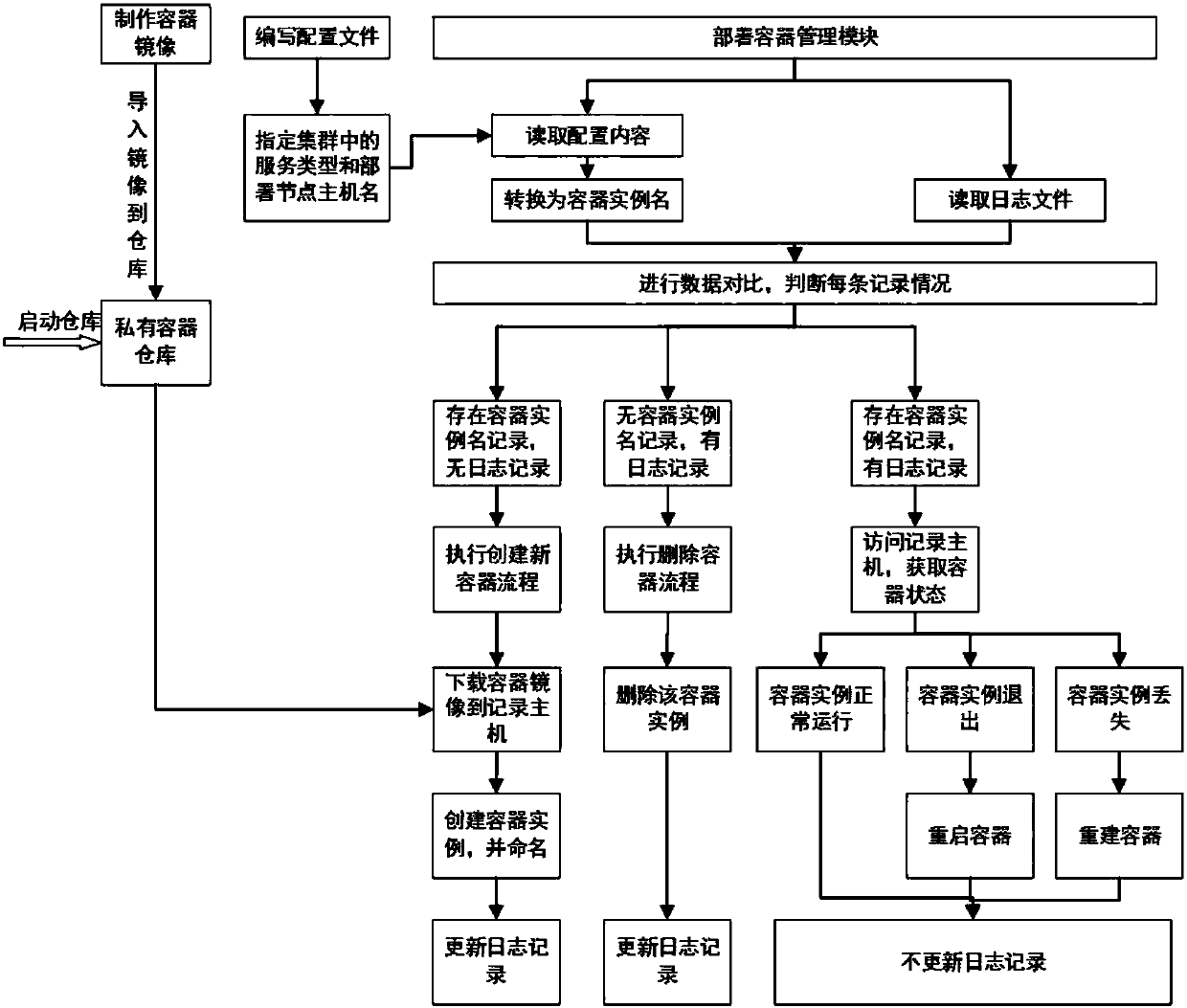
Distributed storage system deployed on the basis of container technology and storage method thereof
ActiveCN107797767ASimplify the deployment processImplement deploymentInput/output to record carriersLogfileDistributed memory systems
The invention discloses a distributed storage system deployed on the basis of container technology. The system includes a plurality of nodes connected with a network switch. The nodes are divided intoa deployment node, a container mirror image warehouse node and a plurality of service end nodes and client nodes used for deploying distributed storage. A storage method of the above storage system includes the steps of: (1) making a container mirror images of various services to establish a private container warehouse; (2) specifying all service types in a cluster and node host names, which needto be used for deployment, to save the same to a configuration file; (3) reading configuration file contents and log file contents through a deployment container management module; (4) obtaining instance names of all containers by conversion according to the read configuration file contents; (5) carrying out data comparison according to the container instance names, which are obtained by conversion, and a read log file to judge status of all records; and (6) carrying out distinguishing according to comparison results of all the records, and carrying out different operations. The system and the method realize simple and highly efficient automated management.
Owner:南京卓盛云信息科技有限公司
Method and device of wireless sensor network interaction deployment based on three-dimensional scene
InactiveCN103200581ARealize a realistic simulationImplement deploymentNetwork topologiesNetwork planningInteraction designWireless sensor networking
The invention discloses a construction method and a construction device of a wireless sensor network interaction deployment platform. According to the construction method and the construction device of the wireless sensor network interaction deployment platform, the deployment and the design of a wireless sensor network are digitalized, firstly a virtual environment is built through a digital modeling mode, then modeling is conducted to different types of nodes such as wireless sensors and routers, further, an interaction design approach based on multi-point touch control is offered to a user, in the period, a designer can use certain mature algorithms or conduct manual deployment, and the connectivity of the wireless sensor network and the coverage of the wireless sensor network are verified in real time in a deployment process. The construction method and the construction device of the wireless sensor network interaction deployment platform can be directly used for various occasions which need to be built with wireless sensor networks and include environment monitoring and biological monitoring, intelligent factories, intelligent communities, and the like.
Owner:SHANDONG UNIV
Cloud automated deployment system and method
InactiveCN106878334AImplement deploymentImprove good performanceTransmissionSoftware deploymentOperational systemExecution unit
The invention provides a cloud automated deployment system and method. The system comprises an interaction unit used for receiving cloud deployment information from a user; a deployment management unit used for determining the type of a cloud platform, the type of an operating system, a server which needs to deploy a cloud, the node type of the server under the cloud platform type based on the cloud deployment information, and determining a cloud component that is adapted to the node type under the cloud platform type as the cloud component needed to be deployed by the server; a server management unit used for pushing an installation file and a configuration file of the operating system that is adapted to the determined operating system type to the server which needs to deploy the cloud, so as to install and configure the operating system on the server which needs to deploy the cloud; and a deployment task execution unit used for deploying the determined cloud component on the server on which the operating system is installed and configured.
Owner:西安三星电子研究有限公司 +1
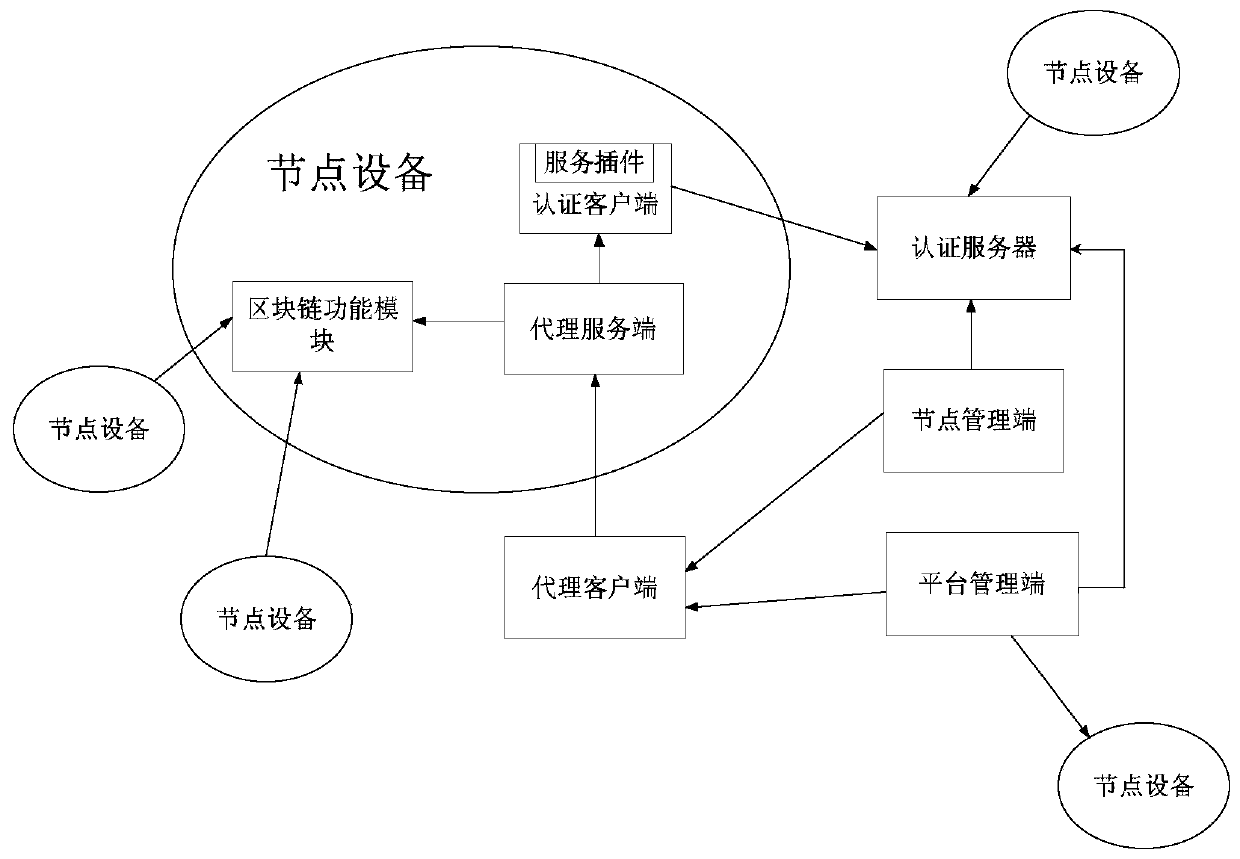
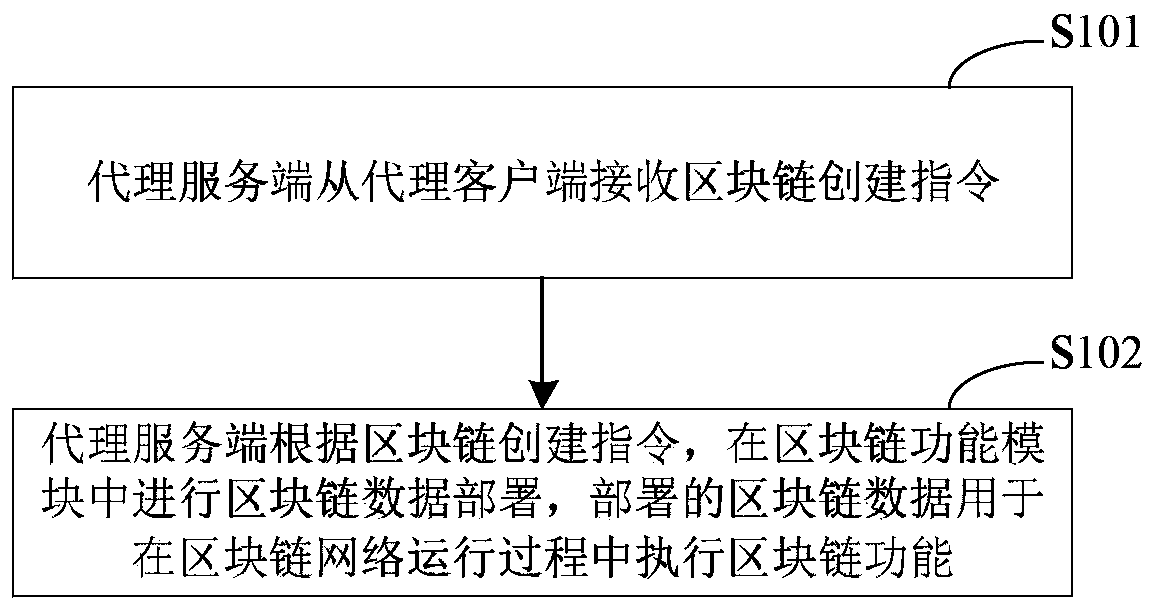
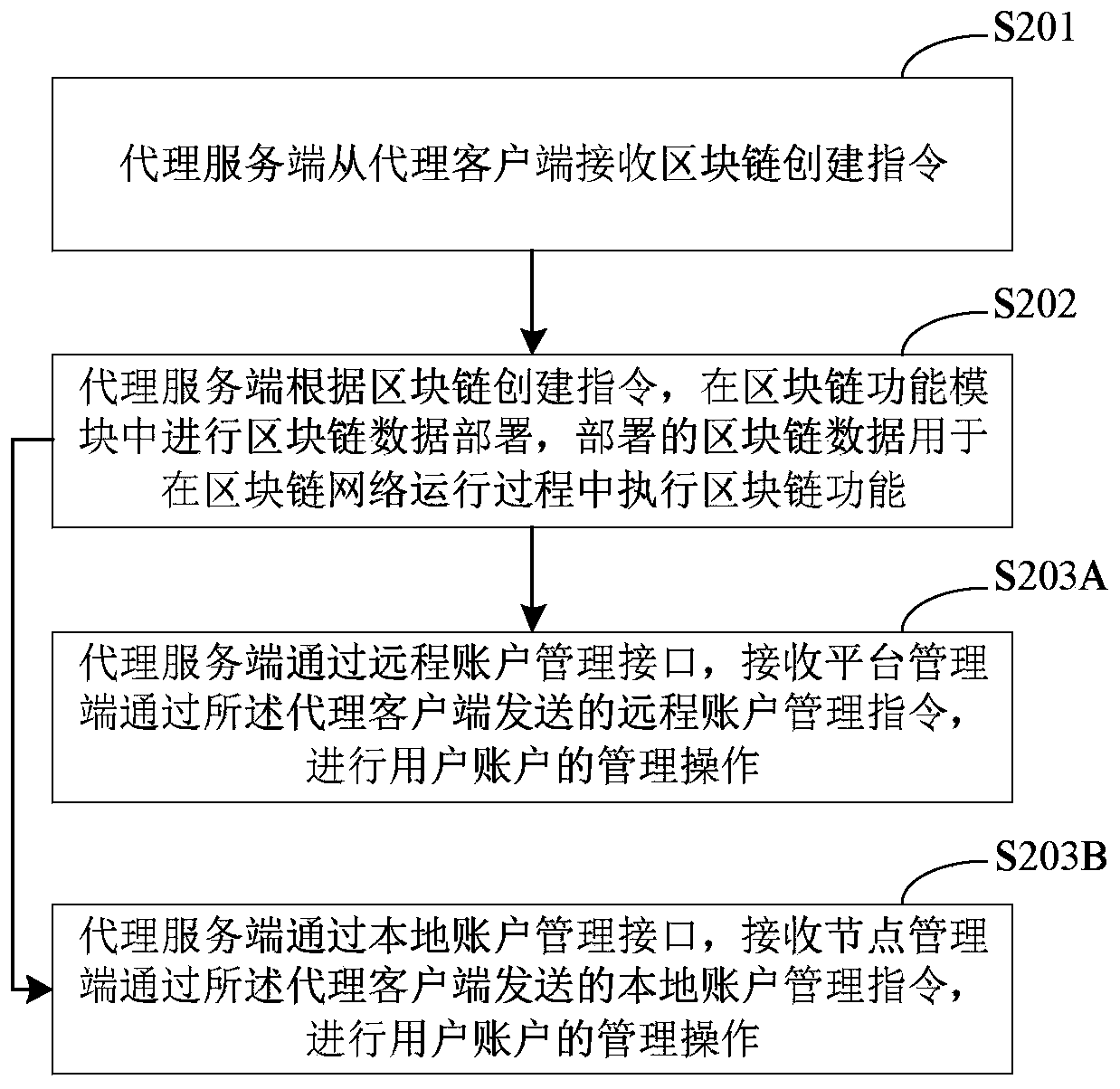
Block chain network deployment control method and device, equipment and medium
ActiveCN110516007AHighly configurableImplement deploymentResource allocationDatabase distribution/replicationClient-sideChain network
The invention discloses a block chain network deployment control method and device, equipment and a medium, and relates to the technical field of block chains. The method comprises the following steps: configuring a block chain function module and a proxy server on node equipment; receiving a block chain creation instruction from the proxy client through the proxy server; and performing block chain data deployment in the block chain function module through the proxy server according to the block chain creation instruction, wherein the deployed block chain data is used for executing a block chain function in a block chain network operation process. According to the technical scheme of the embodiment of the invention, the proxy server is configured in the node equipment; according to the invention, the proxy server receives and processes the block chain creation instruction to realize the deployment of the block chain data for the block chain function module in the node device, so that the configurability of the node device is enhanced, and the effective control of the block chain network deployment process is realized.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
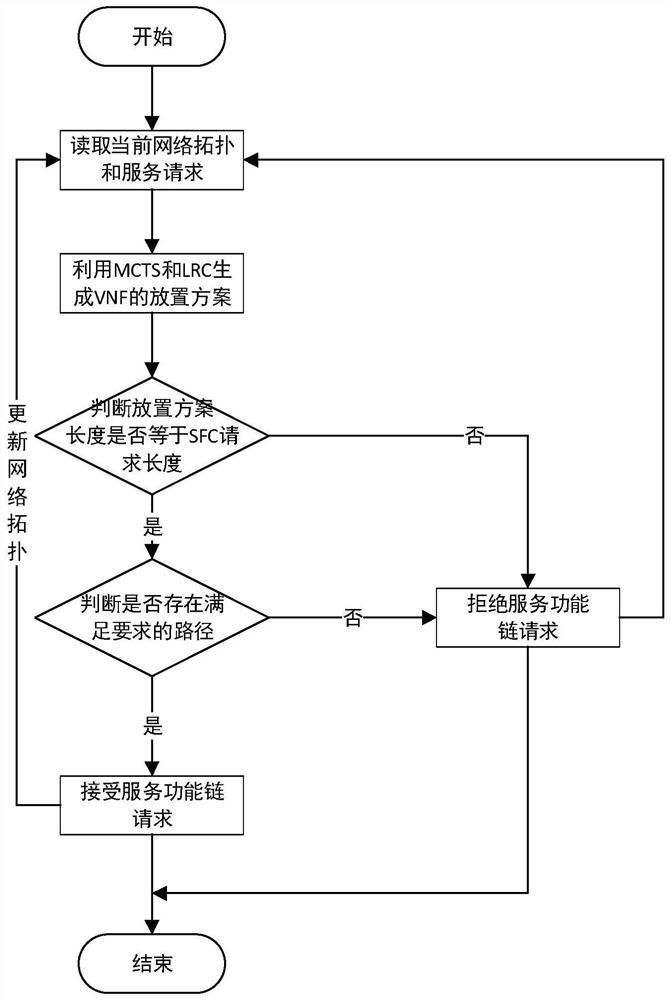
Service function chain deployment method based on reinforcement learning
ActiveCN112083933ATroubleshoot deployment issuesImplement deploymentMachine learningSoftware simulation/interpretation/emulationNetwork topologyPhysical network
The invention discloses a service function chain deployment method based on reinforcement learning. The method comprises the following steps: 1) reading a current physical network topology and a service function chain request; 2) generating a placement scheme of the virtual network function set on the physical network; 3) judging whether each virtual network function in the virtual network function set has a server for placing the virtual network function or not, if so, entering the step 4), and otherwise, entering the step 6); 4) judging whether a link meeting the requirement of the placementscheme exists in the physical network or not, if so, forming a link mapping scheme of the service function chain request, and entering a step 5), otherwise, entering a step 6); 5) receiving a servicefunction chain request, deploying the service function chain request according to the placement scheme and the link mapping scheme, updating the physical network topology, and returning to the step 1); and 6) rejecting the service function chain request, and returning to the step 1). According to the invention, the problem of online service function chain deployment in a scene with a known VNF sequence is solved.
Owner:CHONGQING UNIV +1
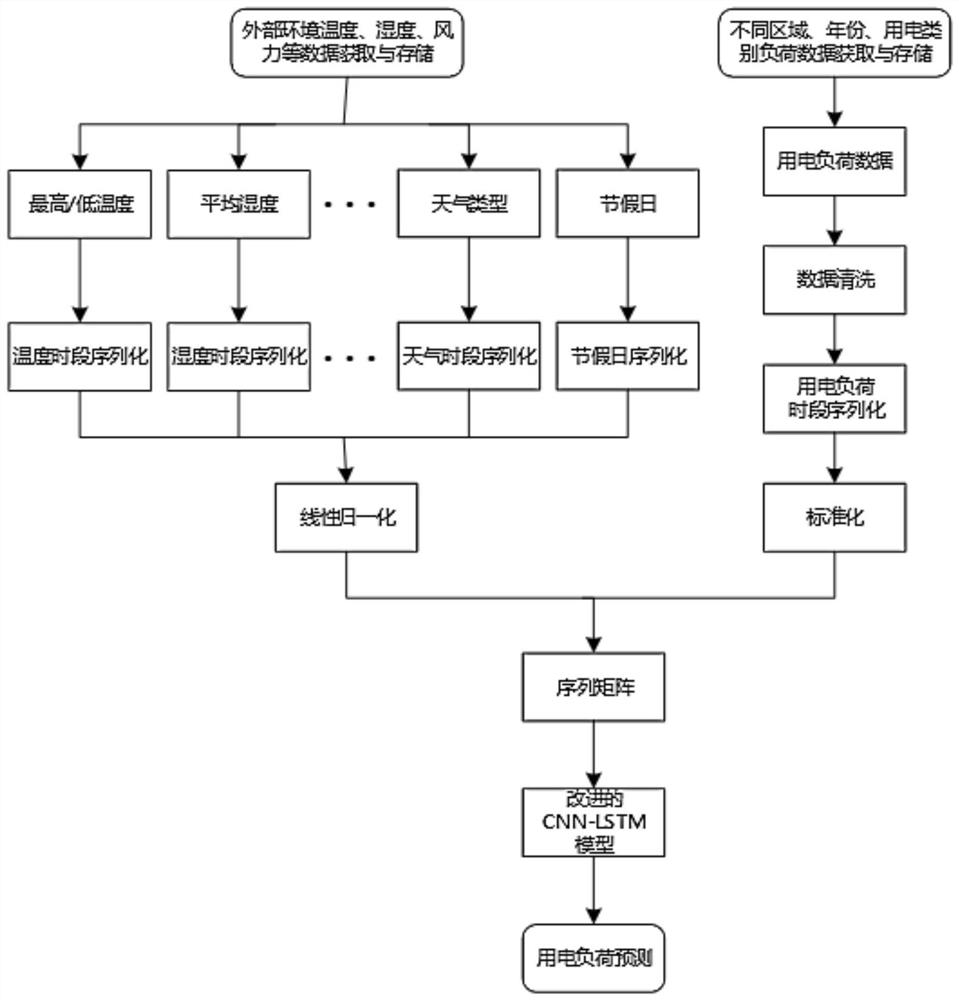
Multi-factor electrical load prediction method based on deep learning
ActiveCN113962364AImprove forecast accuracyReduce the impactLoad forecast in ac networkEnergy industryImproved algorithmPower grid
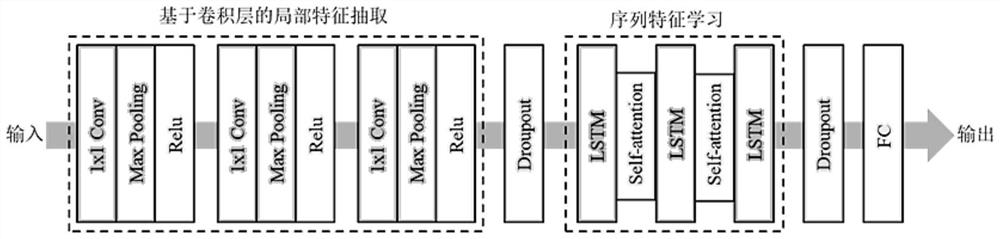
The invention discloses a multi-factor electrical load prediction method based on deep learning, and the method comprises the steps: firstly completing the acquisition and storage of data, including electrical load data and environmental influence data; preprocessing and standardizing the data based on abnormal data detection, autoregression interpolation and sequence data normalization of a k-proximity algorithm and an improved DBSCAN algorithm; then, propsing an improved CNN-LSTM electrical load prediction model, and firstly using a CNN feature extraction module to learn local features of input data; inputting the input data into an LSTM sequence learning model, and extracting sequence feature information of the input data; meanwhile, introducing a self-attention mechanism into the LSTM for learning features of a hidden layer of the LSTM, and extracting key features by distributing different attention weights, so that the final prediction precision is improved; and finally, predicting the electrical load. According to the invention, digital upgrading of a power grid can be promoted, personalized requirements of users are met, and industry correlation analysis, power generation dispatching, power consumption trend prediction, work and production resumption guidance and the like are realized.
Owner:SICHUAN UNIV
Block chain all-in-one machine, multi-node deployment method and device thereof and storage medium
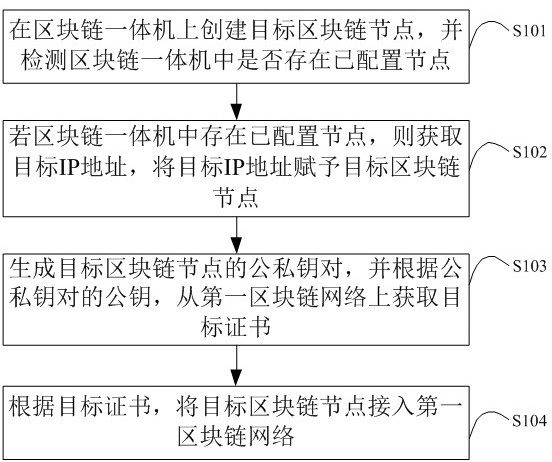
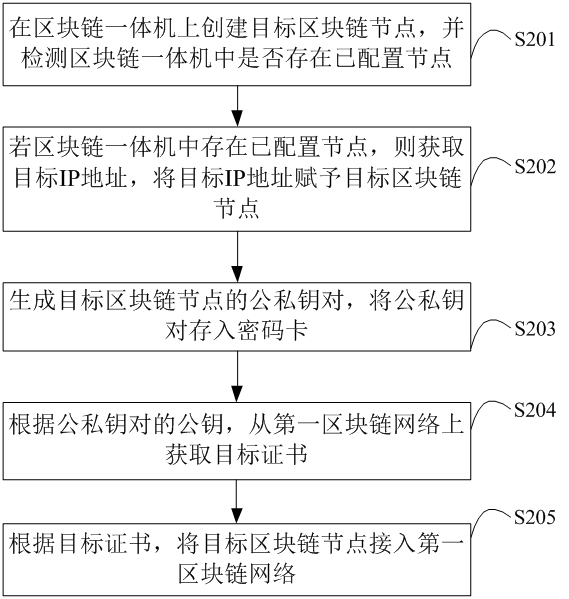
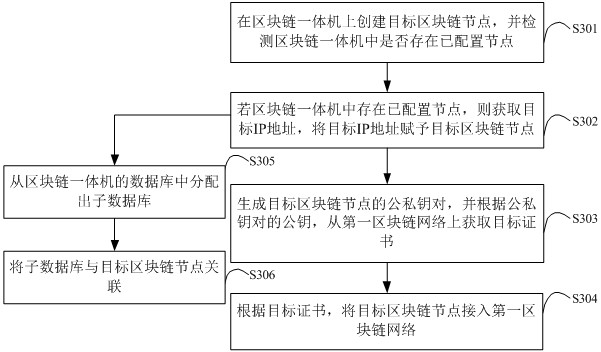
ActiveCN112887160AImplement deploymentImprove deployment efficiencyData switching networksIp addressNode deployment
The invention is suitable for the technical field of block chains, and particularly relates to a block chain all-in-one machine, a multi-node deployment method and device thereof, and a storage medium. The multi-node deployment method comprises: a target block chain node is created in a block chain all-in-one machine, and when it is detected that a configured node exists in the block chain all-in-one machine, the target block chain node is endowed with an IP address which is not used by the configured node, and the corresponding public and private key pair is generated for the target block chain node; the target certificate is acquired from the to-be-added first block chain network according to the public key of the public-private key pair, the target block chain node is accessed to the first block chain network through the target certificate, deployment of the newly added node is realized, the target block chain node and the configured node are isolated on a network transmission channel due to different IP addresses, and the deployment efficiency of the newly added node is improved. The target block chain node is independent of the configured node, a virtual machine does not need to be installed in the block chain all-in-one machine, and the deployment efficiency of the newly added block chain node is improved.
Owner:杭州链城数字科技有限公司
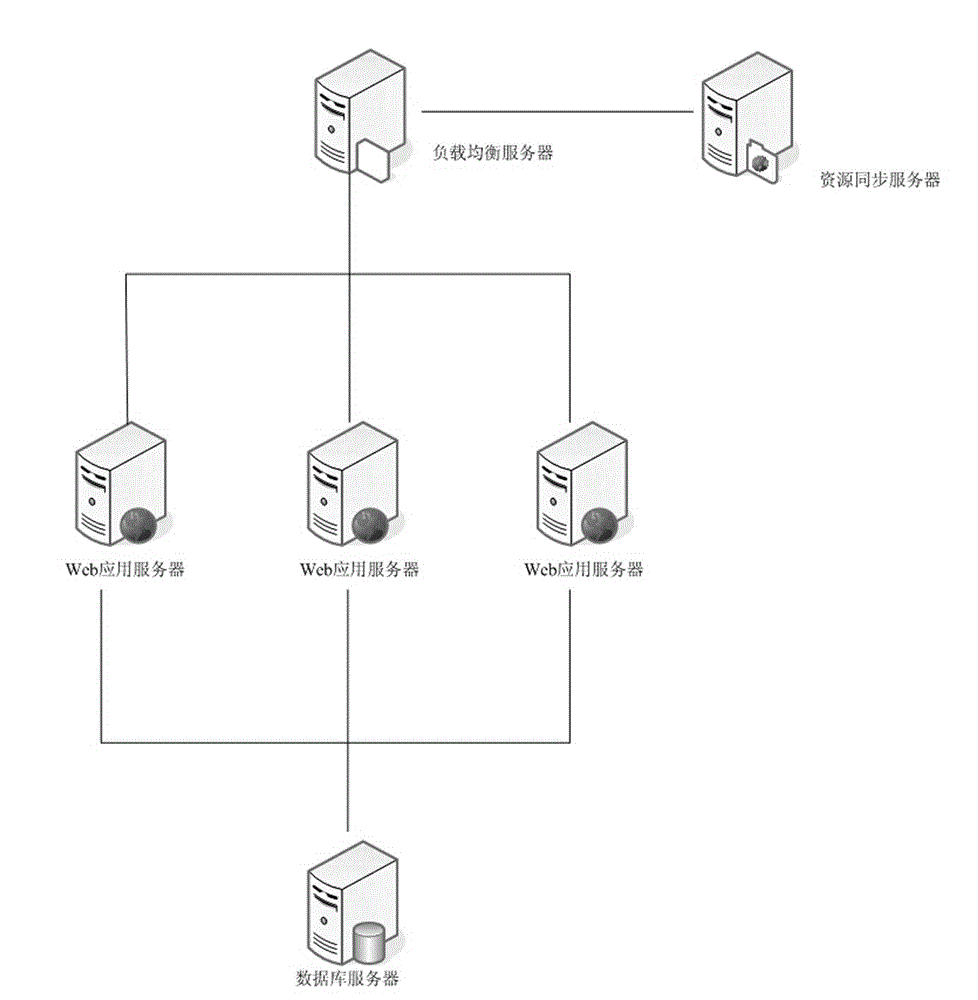
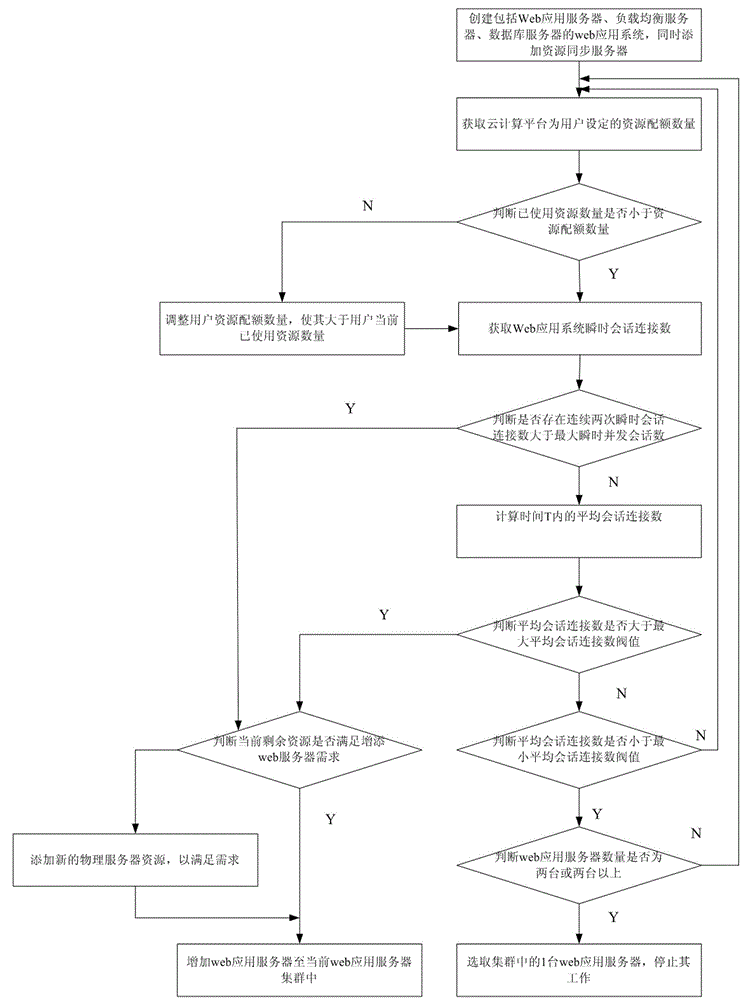
Web application automatic elastic extension method under cloud computing environment based on sessions
ActiveCN103561055ARealize dynamic adjustmentImprove adaptabilityTransmissionWeb applicationApplication server
The invention discloses a Web application automatic elastic extension method under a cloud computing environment based on sessions. The Web application automatic elastic extension method includes the steps of deploying a Web application system, judging the number of resources which are used, increasing resource quota quantities, acquiring the linking number of the instant sessions, comparing the linking number of the instant sessions, calculating the mean session linking number, comparing the mean session linking number, judging residual resources, adding Web application servers, judging the number of the application servers and deleting the Web application servers. According to the Web application automatic elastic extension method, dynamic extension and reduction are conducted on the high-concurrency Web application system and a Web application system cluster with multiple or few sessions at a certain time interval through the linking numbers of the instant sessions and the mean session linking number, dynamic adjustment of the Web application system based on the sessions is achieved, and adaptability of the Web application system is improved.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
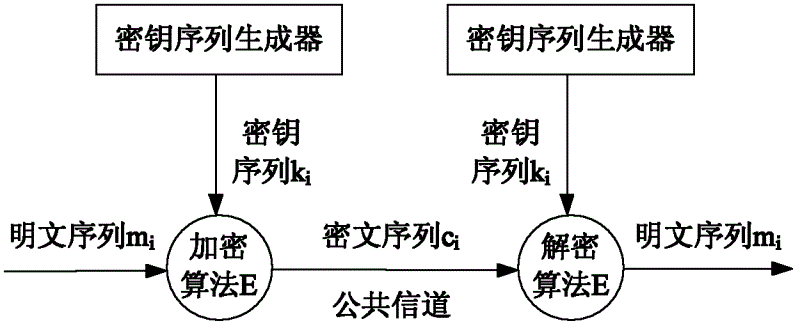
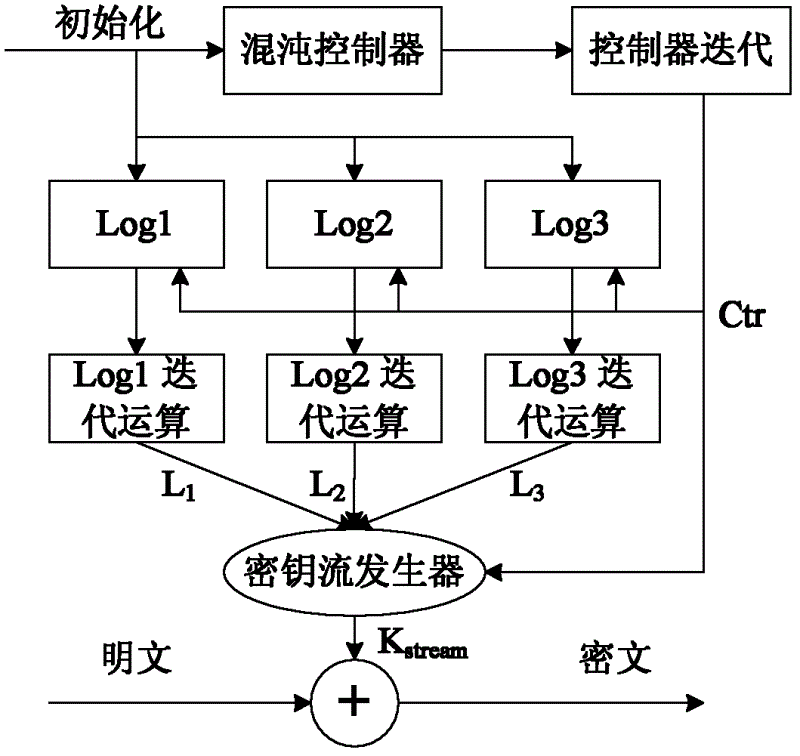
Wireless sensor network-oriented mutual interference compound chaos stream cipher implementation method
ActiveCN102624519AImprove safety and practicalitySolve the degradation problemSecurity arrangementSecuring communicationWireless mesh networkWireless sensor networking
The invention relates to a wireless sensor network-oriented mutual inference compound chaos stream cipher implementation method, which comprises the following steps of: (1) converting typical Logistic mappings and Tent mapping into a discrete function on an integer field and enabling a chaos sequence integer model to be implemented on a sensing node of a wireless sensor network which supports integer computation; (2) on the basis of an integer chaos function, establishing three Logistic chaos mappings with different initial values as a main chaos system, and then establishing a Tent chaos mapping as a chaos controller; and (3) enabling the chaos controller to mutually interfere with the three Logistic mappings, and simultaneously, enabling the Tent chaos controller to be compounded with the three Logistic chaos mappings to form a safer random cipher stream with longer period to further form a complete chaos stream cipher. The wireless sensor network-oriented mutual interference compound chaos stream cipher implementation method has favorable chaos characteristic and enhanced safety and practicability.
Owner:ZHEJIANG UNIV OF TECH
Software continuous integration method based on micro-service architecture
PendingCN111552644AImprove work efficiencyEliminate hidden dangersSoftware testing/debuggingSoftware deploymentContinuous integrationSoftware engineering
The invention discloses a software continuous integration method based on a micro-service architecture. The invention discloses a software delivery test method and system, belongs to the field of internet software development, and is used for delivery from software development to software test, and solves the problems that in the existing software project development process, the continuous integration efficiency of software is poor, compiling failure occurs easily before project delivery test, and project publishing deployment is affected due to no automatic test function. The method comprises the following steps: firstly, constructing and configuring a Jenkins CI platform; then, a micro-service engineering package Job1 is constructed on a Jenkins CI platform; marking an identification label on the packaged micro-service installation package and uploading the micro-service installation package to an installation package warehouse; arranging and storing the micro-service installation package according to the dimension of the project version, performing digital verification through an MD5 algorithm, constructing a package fetching deployment test environment Job2 with parameters ona Jenkins CI platform, and finally outputting a test environment publishing list. Therefore, high continuous integration can be achieved during project delivery testing, and the working efficiency ofsoftware development and testing is improved.
Owner:成都库珀创新科技有限公司
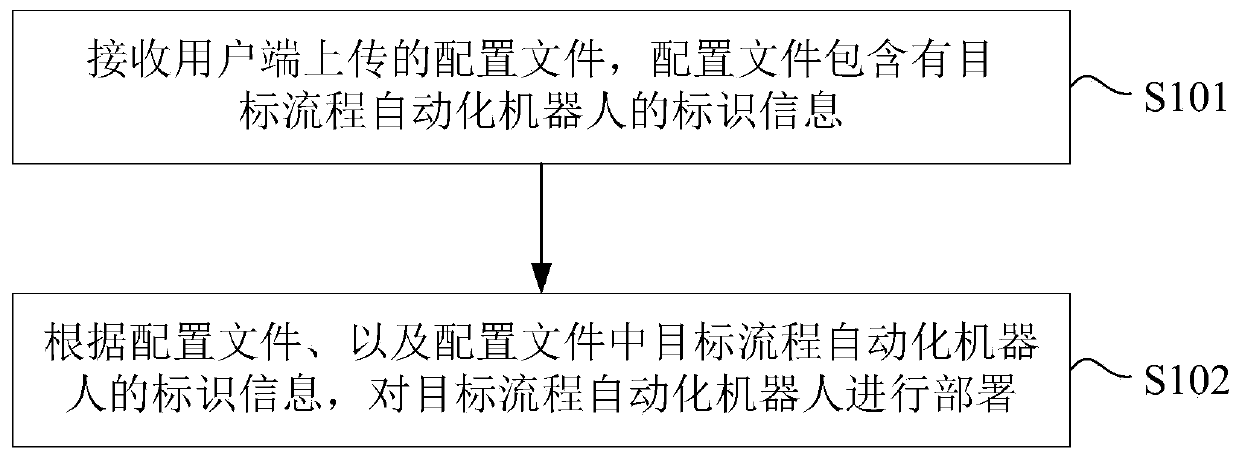
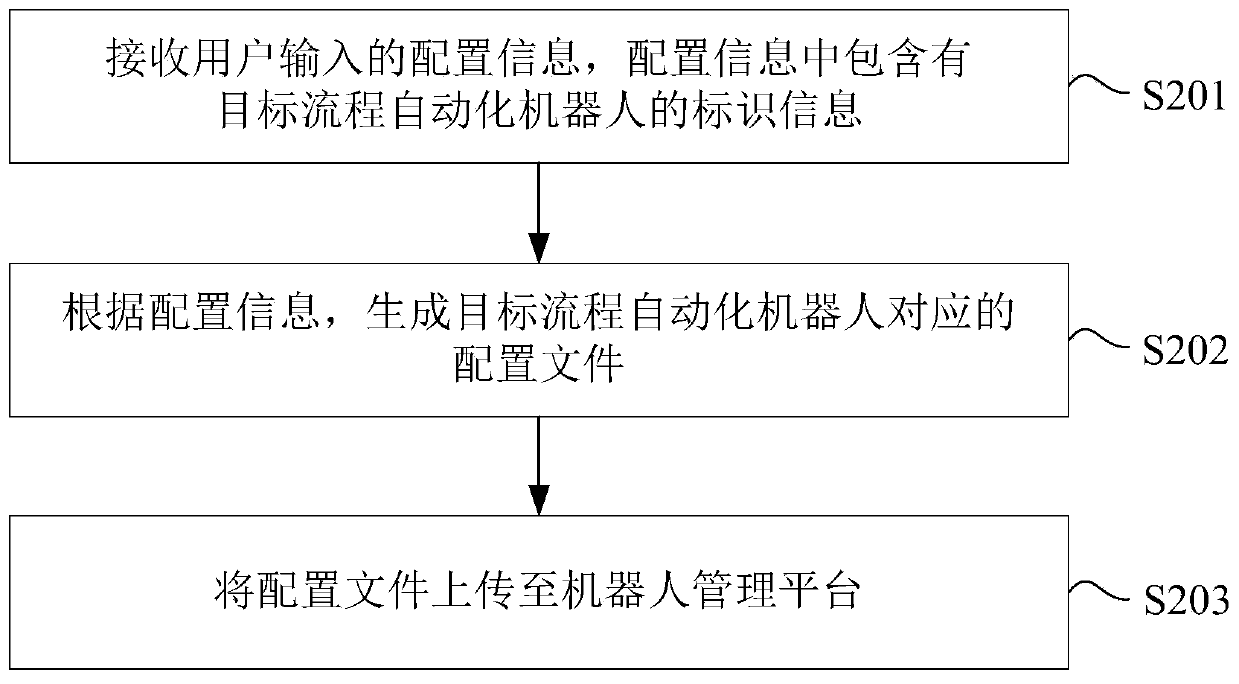
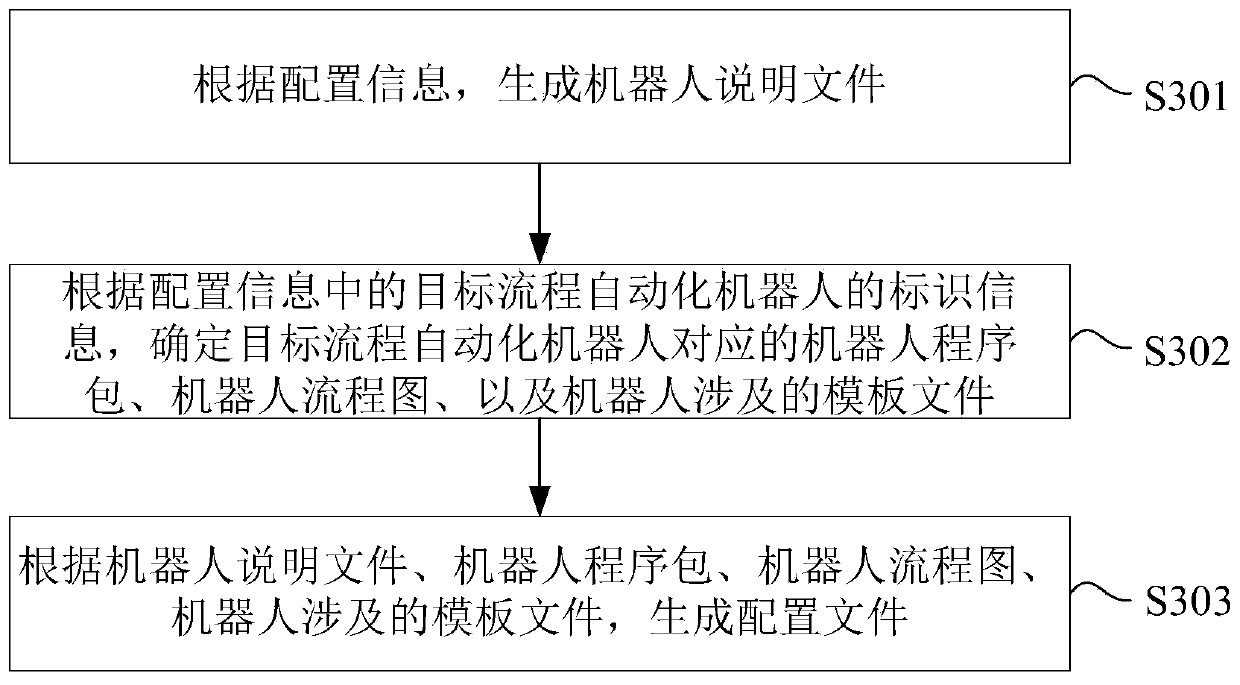
RPA process automation robot deployment method and device and electronic equipment
PendingCN111242577AEnsure deployment efficiencyReduce incompatibilityOffice automationDeployment environmentOperating system
The invention provides an RPA process automation robot deployment method and device and electronic equipment, which relate to the technical field of process automation.A user side can generate a configuration file containing identification information of a target process automation robot according to configuration information input by a user; the configuration file is updated to a robot managementplatform; the robot management platform can deploy the target process automation robot according to the received configuration file and the identification information of the target process automationrobot in the configuration file, so that large-scale deployment of the RPA process automation robot is realized, and the deployment efficiency of the RPA process automation robot is ensured. Meanwhile, the configuration file is generated by the user side according to the configuration information input by the user, and when the configuration file is generated, the user can adjust the deployment environment according to the RPA process of the target process automation robot, so that the problem that the deployment environment of the target process automation robot is incompatible with the RPAprocess can be reduced.
Owner:CHINA CONSTRUCTION BANK
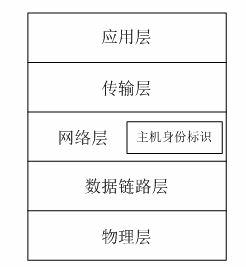
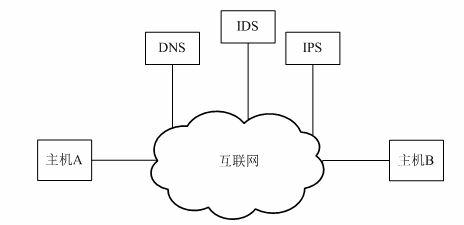
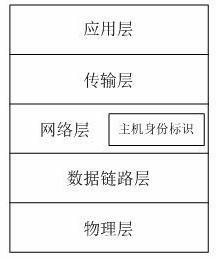
Method for separating host identifier (HID) mark from locator based on IPV6 (Internet Protocol Version 6) address
The invention relates to a method for separating a host identifier (HID) from a locator based on an IPV6 (Internet Protocol Version 6) address, wherein the method is simple in operation, good in compatibility and capable of supporting the network mobility preferably. The method comprises the following steps: adding the HID onto a network layer in a TCP / IP (Transmission Control Protocol / Internet Protocol) architecture at a host end, wherein the identifier is of an IPV6 address and can be formed into prefixes of 0000011+domain domain identifier and stand-alone identifier, and the address indicated by the prefix belongs to an address which is not distributed for use by the IPV6; disposing a mapping server at a position parallel to a DNS (domain name system) server on the network to manage the mapping of the HID and the locator, wherein the mapping server comprises an identifier management domain server IDS (Intrusion Detection System) and an identity-position mapping server IPS (Intrusion Prevention System); and comparing the address at the host end in order to distinguish a protocol provided by the method so as to determine the communication mode of the host.
Owner:SHANDONG NORMAL UNIV
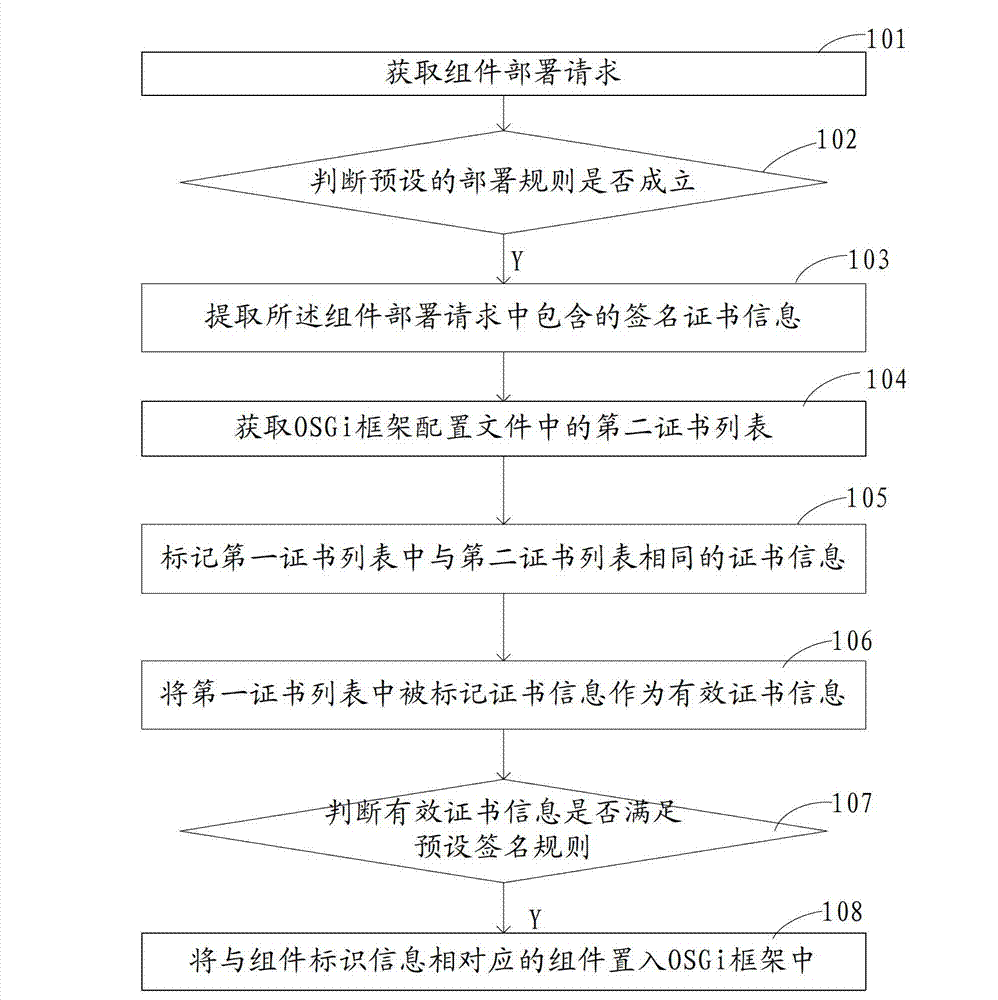
Bundle deployment methodnd device and security framework
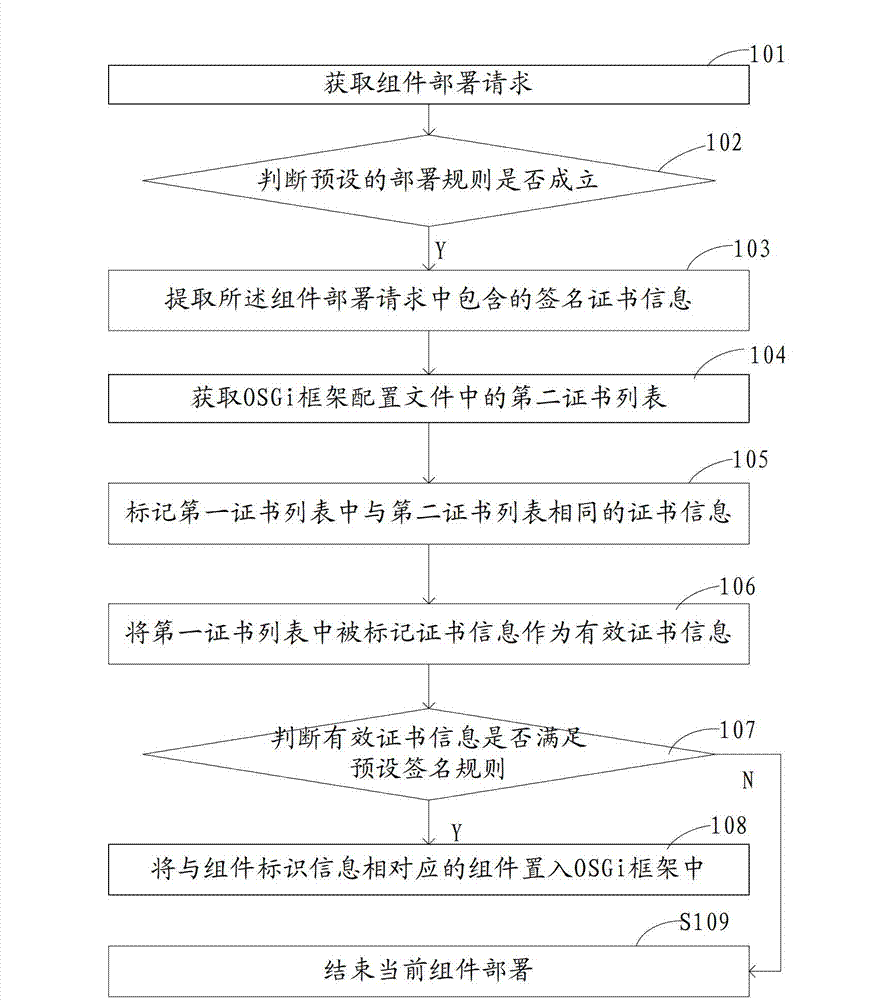
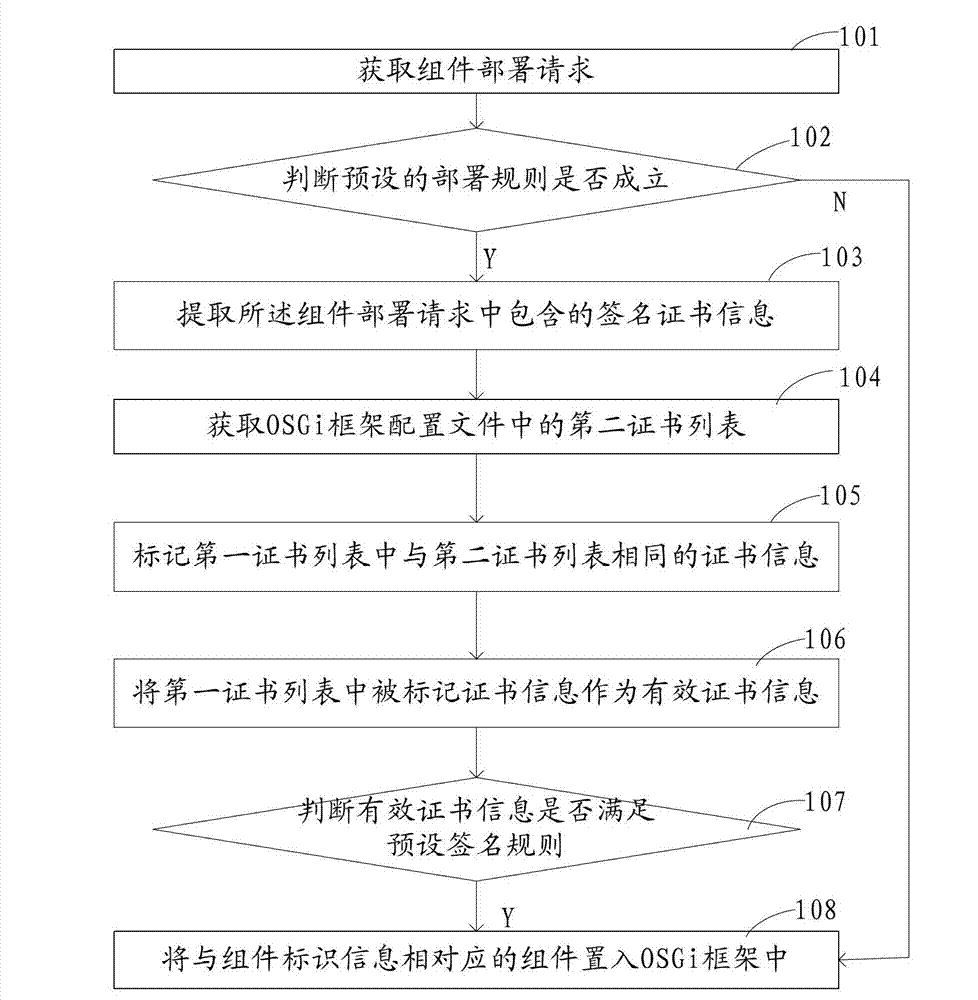
ActiveCN103034789AImprove efficiencyImplement deploymentProgram/content distribution protectionService gatewaySecurity framework
The invention discloses a bundle deployment method and device and a security framework. The method comprises the following steps of: obtaining a bundle deployment request comprising bundle identification information; if the preset deployment rule is established, extracting signature certificate information contained in the bundle deployment request; the signature certificate information comprising a first certificate list, and the first certificate list comprising at least one certificate information; obtaining a second certificate list in an OSGi (Open Service Gateway initiative) framework configuration file; marking the certificate information same as that of the second certificate list in the first certificate list; the marked certificate information in the first certificate list being used as effective certificate information; and if the effective certificate information meets the preset signature rule, placing a bundle corresponding to the bundle identification information into the OSGi framework. According to the embodiment of the application, the signature of the bundle is certified to realize security deployment, so that the efficiency of bundle deployment is obviously improved under the premise of ensuring the security deployment of the bundle.
Owner:山东中创软件商用中间件股份有限公司
Full-memory operation system which supports container running
InactiveCN107391141AReal-time loadingImplementation supportSoftware designProgram loading/initiatingOperational systemContainer status
The invention discloses a full-memory operation system which supports container running. The full-memory operation system comprises a full-memory operation system body, and the full-memory operation system body comprises a generating unit and an operation system loading unit; the full-memory operation system generating unit is used for establishing a Linux customizing operation system, compiling tool package software and a container engine and establishing a Linux memory operation system mirror image; the operation system loading unit is used for achieving core module loading, storage driving loading, container mirror image configuration loading and container storage driving loading of the operation system. The invention provides a memory operation system and an achieving method thereof which support container application deployment, and are high in practicability and efficiency. According to the operating system, a state-free container can totally run in a memory, therefore the bottleneck of hardware reading and writing is avoided, reading of the container mirror image is accelerated, the situation that the container state is stored in persistent data is supported, the situation that a host machine or the network stores persistent data is further supported, and the data safety is guaranteed.
Owner:INSPUR QILU SOFTWARE IND
Point-to-multipoint multicast realization method, network nodes and system
ActiveCN103716169AAvoid excessive copyingReduce processing burdenSpecial service provision for substationNetworks interconnectionMulticast
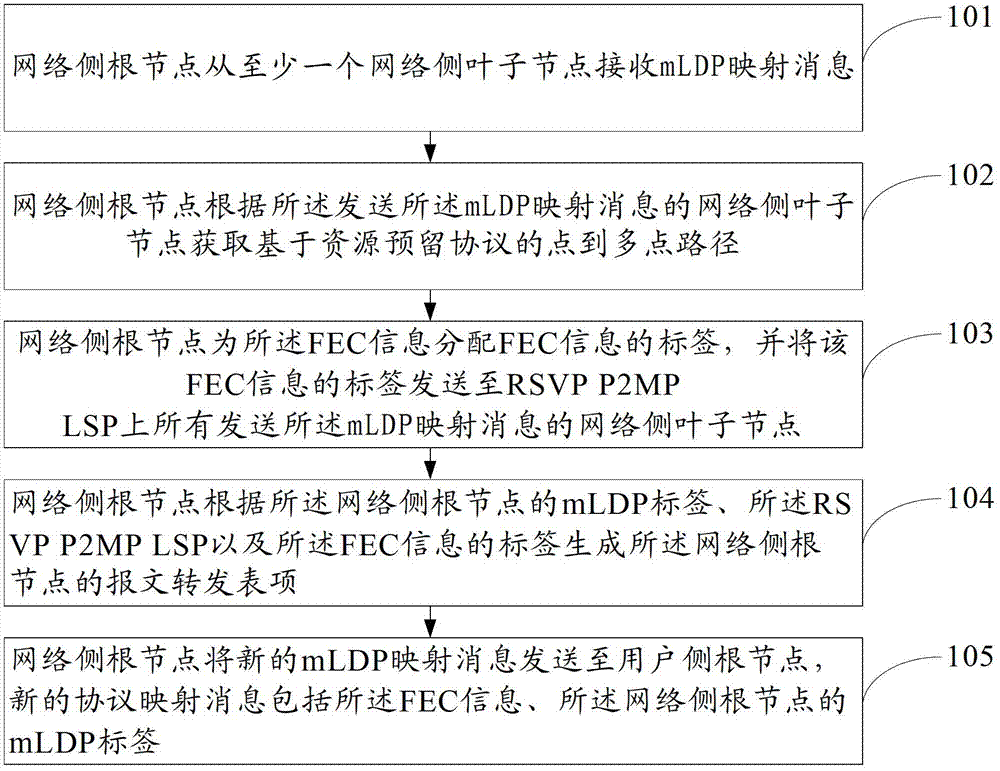
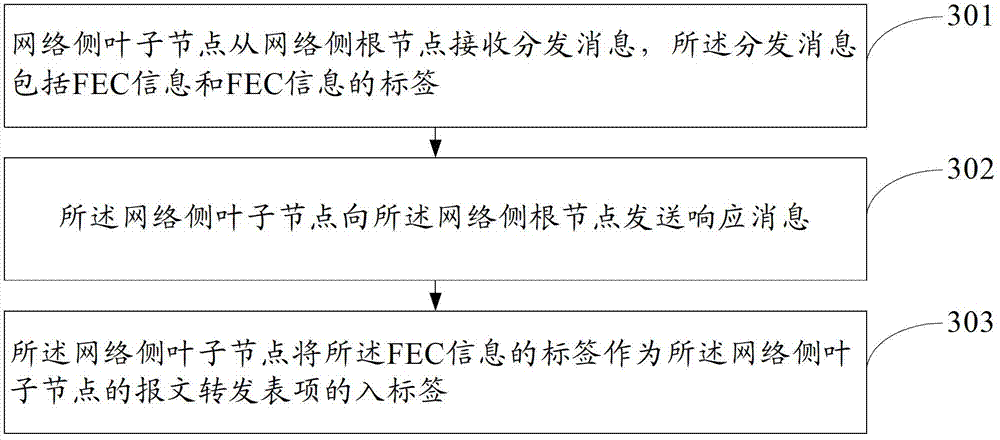
The embodiment of the invention provides a point-to-multipoint multicast realization method, network nodes and a system, which are applicable to P2MP multicast under a non-VPN scenario and capable of realizing deployment when a PE device does not support an mLDP. The method is that: network-side leaf nodes acquire mLDP labels and FEC information of downstream user-side leaf nodes through mLDP mapping messages of the downstream user-side leaf nodes and then the mLDP mapping messages which include the mLDP labels and the FEC information are sent to upstream network-side root nodes and then forwarding table items are generated; the network-side root nodes search for or establish an RSVP P2MP LSP and distribute label values for the received FEC information; forwarding table items of the different network-side leaf nodes are associated with the label values of the FEC information and at the same time, the network-side root nodes send the mLDP labels and the FEC information of the network-side root nodes to the upstream user-side leaf nodes through the mLDP mapping messages and associate the mLDP labels of the network-side root nodes with the RSVP P2MP LSP and the FEC information. The point-to-multipoint multicast realization method, the network nodes and the system are used for realizing P2MP multicast.
Owner:HUAWEI TECH CO LTD
Facial recognition based mobile phone secure payment system and payment method thereof
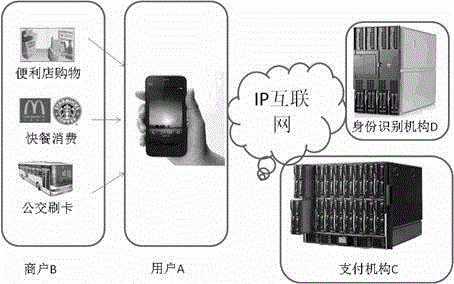
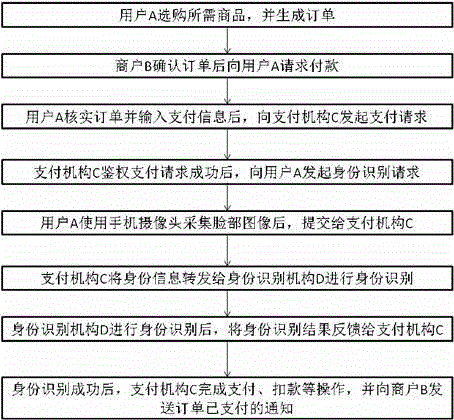
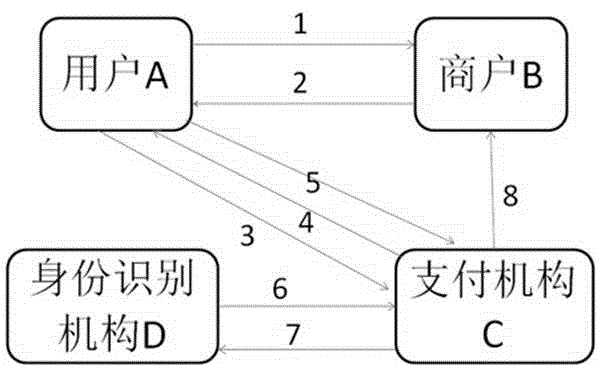
InactiveCN104537534AWide application of patentsWide applicabilityProtocol authorisationIdentity recognitionComputer module
The invention relates to a facial recognition based mobile phone secure payment system, which comprises four modules including a user A, a merchant B, a payment mechanism C, and an identity recognition mechanism D, wherein the modules are loosely coupled and interact via information. A payment method using the mobile phone secure payment system provided by the invention differs from the traditional face payment method in that the face authentication and the mobile phone payment are organically integrated in the flow, the identity recognition mechanism D is added in the existing mobile phone payment flow, and the secure flow of mobile phone payment is expanded among the user A, the payment mechanism C and the identity recognition mechanism D. In addition, the existing phone payment system is reused to a large extent, the deployment and the upgrading can be quickly realized, the construction cost is low, the risk of payment caused by the pavement of mobile phone non-users can be effectively reduced, and an important role in mobile internet e-commerce is played.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
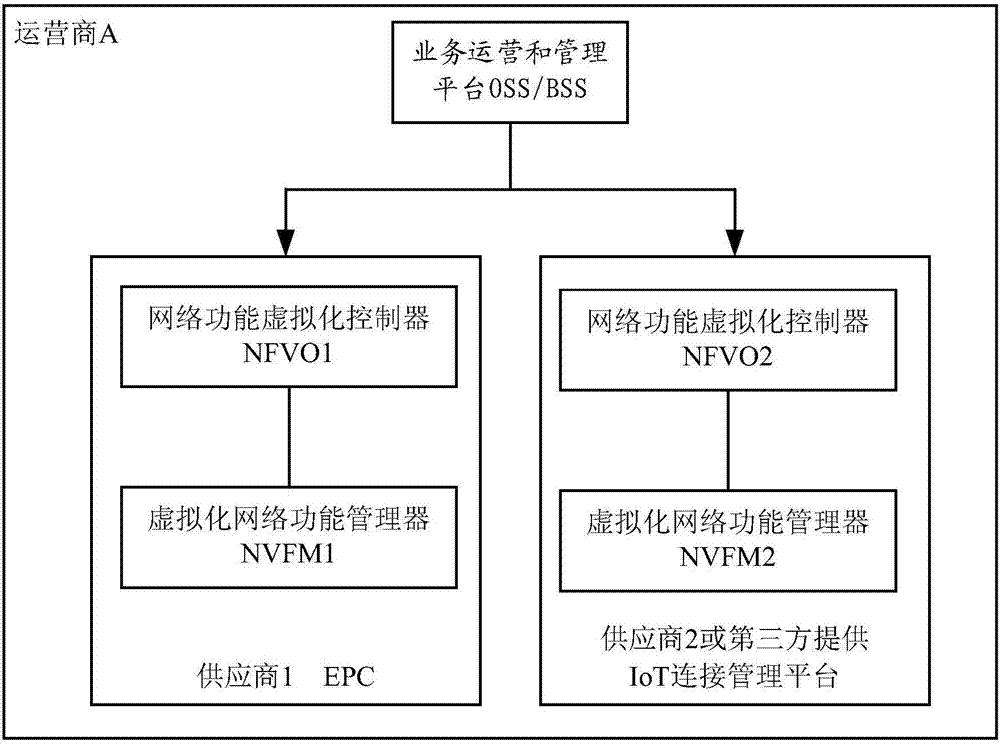
Deployment method and deployment system of virtualized network
InactiveCN107306201AImplement deploymentIncrease flexibilityNetworks interconnectionNetwork deploymentVirtualization
The invention relates to a deployment method and deployment system of a virtualized network. The virtualized network is formed by a plurality of parts. The method comprises: a first network function virtualization orchestrator (NFVO) receives a first-part deployment request sent by a service operation and management platform, wherein the first-part deployment request includes resource reservation indication; a second NFVO receives a second-part deployment request; the second NFVO obtains orchestrating information of a first part and carries out orchestrating on a second part based on the orchestrating information of the first part; and when the orchestrating information of the first part meets the deployment request of the second part, the first NFVO and the second NFVO request resource allocation. Resource reservation is carried out on the part needing deployment and no resource allocation is performed after resource reservation; and after orchestrating planning of all deployment parts is completed, resource allocation is carried out. Therefore, when a virtual network service is formed by a plurality of parts and virtualized network deployment is performed, mutual coordinate of all parts is realized, so that flexibility and universality of network deployment are improved.
Owner:HUAWEI TECH CO LTD
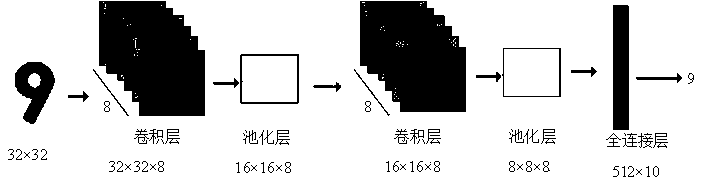
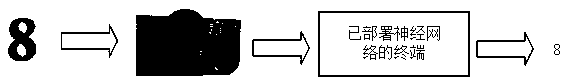
Implementation method of small neural network oriented to programmable logic device mobile terminal
InactiveCN110782022AReduce storage space requirementsImplement deploymentNeural architecturesPhysical realisationActivation functionConcurrent computation
The invention relates to an implementation method of a small neural network oriented to a programmable logic device mobile terminal. The implementation method comprises the following steps of S1, obtaining a feature map after an input image passes through two convolution layers; S2, performing nonlinear mapping on the feature map after each convolution through an activation function; performing maximum pooling operation between different convolution layers by adopting a filter with a step length of 2, selecting main features in the feature map, and reducing the dimension of the feature map toobtain a pooling layer output image; and S3, tiling the pooling layer output image obtained in the step S2 into one dimension, and obtaining an output result after the image passes through the full connection layer. According to the method, the model parameters are reduced by about 4 times, the requirement of the parameters for the storage space is reduced, and the calculation requirement is alsoreduced through the 1-bit input data and the 8-bit weight parameters. When the neural network is deployed at a terminal, a lookup table and pipeline parallel computing method can be adopted to improvethe computing speed.
Owner:FUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com