Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52 results about "IMG" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
IMG, in computing, refers to binary files with the .img filename extension that store raw disk images of floppy disks, hard drives, and optical discs or a vector image – .img.
Shunted interleave for accessing plural memory banks, particularly those having partially accessed cells containing data for cache lines
A bank select device has a plurality of addressable locations and a plurality of storage locations correlated to each other so that each storage location is correlated to plural addressable locations and each addressable location is correlated to one storage location. Each storage location contains a respective bank select. The addressable locations and storage locations are grouped into interleave patterns such that, for each pattern, there are Q storage locations and 2A addressable locations arranged in L sequential loops each containing Q sequentially addressable locations and a remainder loop containing R sequentially addressable locations, where L·Q+R=2A. A shunt defines a non-zero offset for each interleave so that each interleave commences with a different bank select and a complete rotation of all of the interleaves addresses each of the memory banks an equal number of times. The shunt (S) may be selected as mod(2A,Q), −Q+mod(2A,Q), ±1 or ±prime to , where −<S<+. The bank select is particularly useful for partially accessing rows of memory data to access data as cache lines.
Owner:EFFICIENT MEMORY TECH
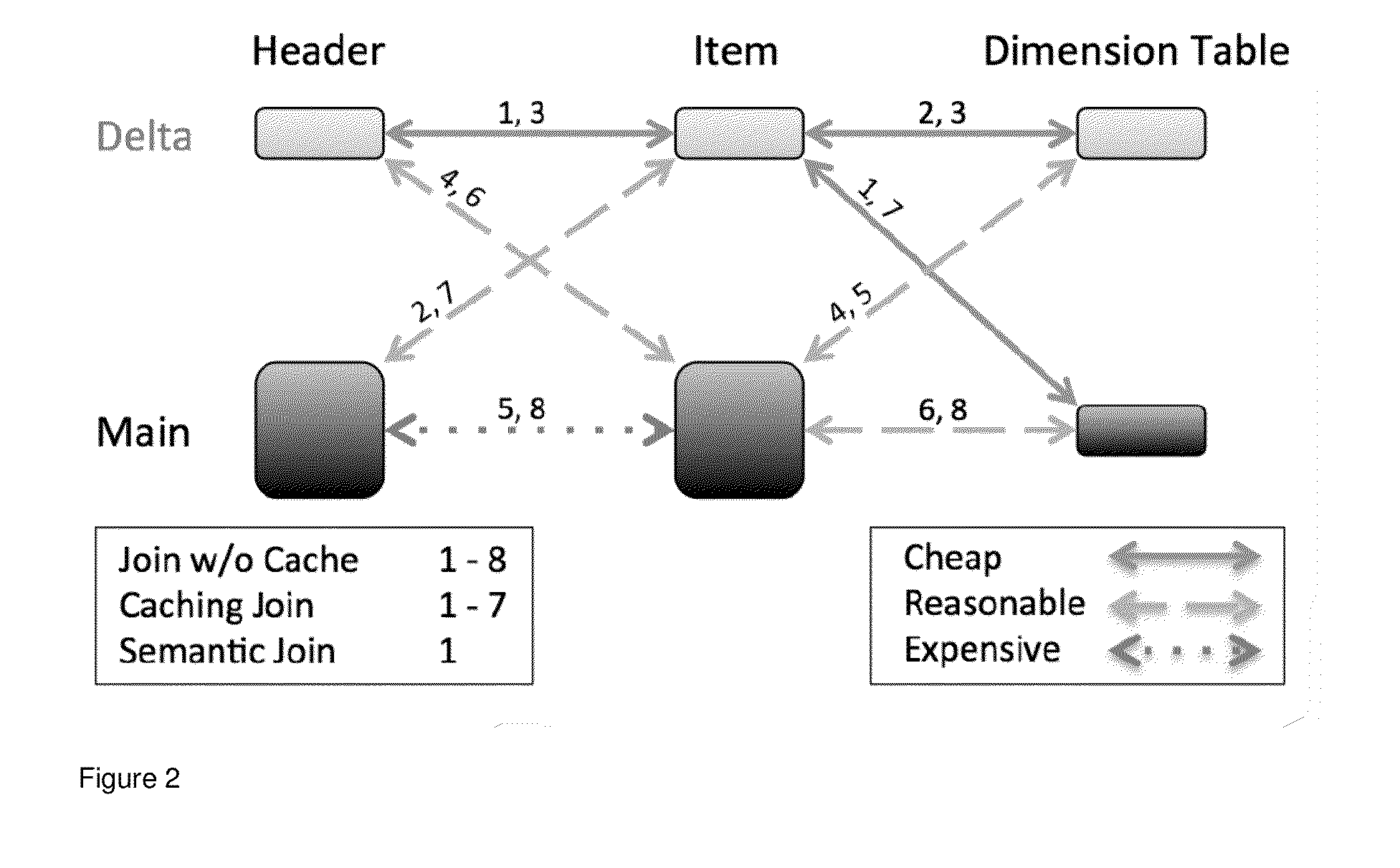
Using object awareness for a join pruning mechanism
ActiveUS20150120698A1Quick searchEasy Connection HandlingDigital data processing detailsMulti-dimensional databasesTable (database)Algorithm
The invention relates to a computer system and a corresponding method and a corresponding computer-readable medium according to the invention. The computer system is suitable for determining the result of a join. The computer system may be distributed system. The computer system comprises: a processing unit; a database coupled to the processing unit, the database comprising: a first table (R), and a second table (S), each of the first and second table being partitioned into at least two partitions, namely a respective first (R1, S1) and a respective second partition (R2, S2), the database being coupled to an application that, in operation, accesses the database according to an access pattern; and a database engine executable by the processor and communicatively coupled to the database, the database engine being configured for determining a join (R R[A]=S[A]S) between the first and the second table by: determining the results for a plurality of subjoins (R1 R[A]=S[A]S1, R2R[A]=S[A]S2, R1 R[A]=S[A]S2, R2 R[A]=S[A]S1); and combining (U) at least those determined results that are not empty(Ø). The database engine is further configured for determining the result of at least one of the plurality of subjoins by inferring from the access pattern of the application that this result is empty (Ø).
Owner:HASSO PLATTNER INSTITUT FUR SOFTWARESYSTTECHN
Decoding method of multi-cell, multi-user and multi-antenna system
InactiveCN104333406AAchieve estimatesSpatial transmit diversityError preventionChannel state informationDecoding methods
The invention relates to a decoding method of multi-cell, multi-user and multi-antenna system. The decoding method includes two steps. The first step is to design a training sequence header: a line (img file='dest_path_image 004.TIF' wi='13' he='16' / ) in front of (img file='2014106135712100004 dest_path_image 002.TIF' wi='24' he='24' / ) is set as the training sequence header, elements in the first line of (img file=' 53509 dest_path_image 002.TIF' wi='24' he='24' / ) are (img file=' dest_path_image 006.TIF' wi='8' he='16' / ) respectively, the lines from the second line of (img file=' 908332 dest_path_image 002. TIF' wi='24' he='24' / ) to (img file=' 688070 dest_path_image 004.TIF' wi='13' he='16' / ) are marked as (img file=' dest_path_image 008.TIF' wi='22' he='24' / ), wherein elements in (img file=' 270230 dest_path_image 008.TIF' wi='22' he='24' / ) can be (img file=' 22285 dest_path_image 006.TIF' wi='8' he='16' / ) or (img file=' dest_path_image 010.TIF' wi='21' he='16' / ), and vectors in all rows of (img file=' 844747 dest_path_image 008. TIF' wi='22' he='24' / ) are different from each other. The second step is to estimate a sent signal matrix (img file=' dest_path_image 014. TIF' wi='18' he='18' / ) through a received signal matrix (img file=' dest_path_image 012. TIF' wi='18' he='18' / ) on the basis of a system model. The decoding method achieves estimation of sent signals in the multi-cell, multi-user and multi-antenna system by aid of a few pilot signals on the condition that the receiving party does not know the channel state information.
Owner:HANGZHOU DIANZI UNIV
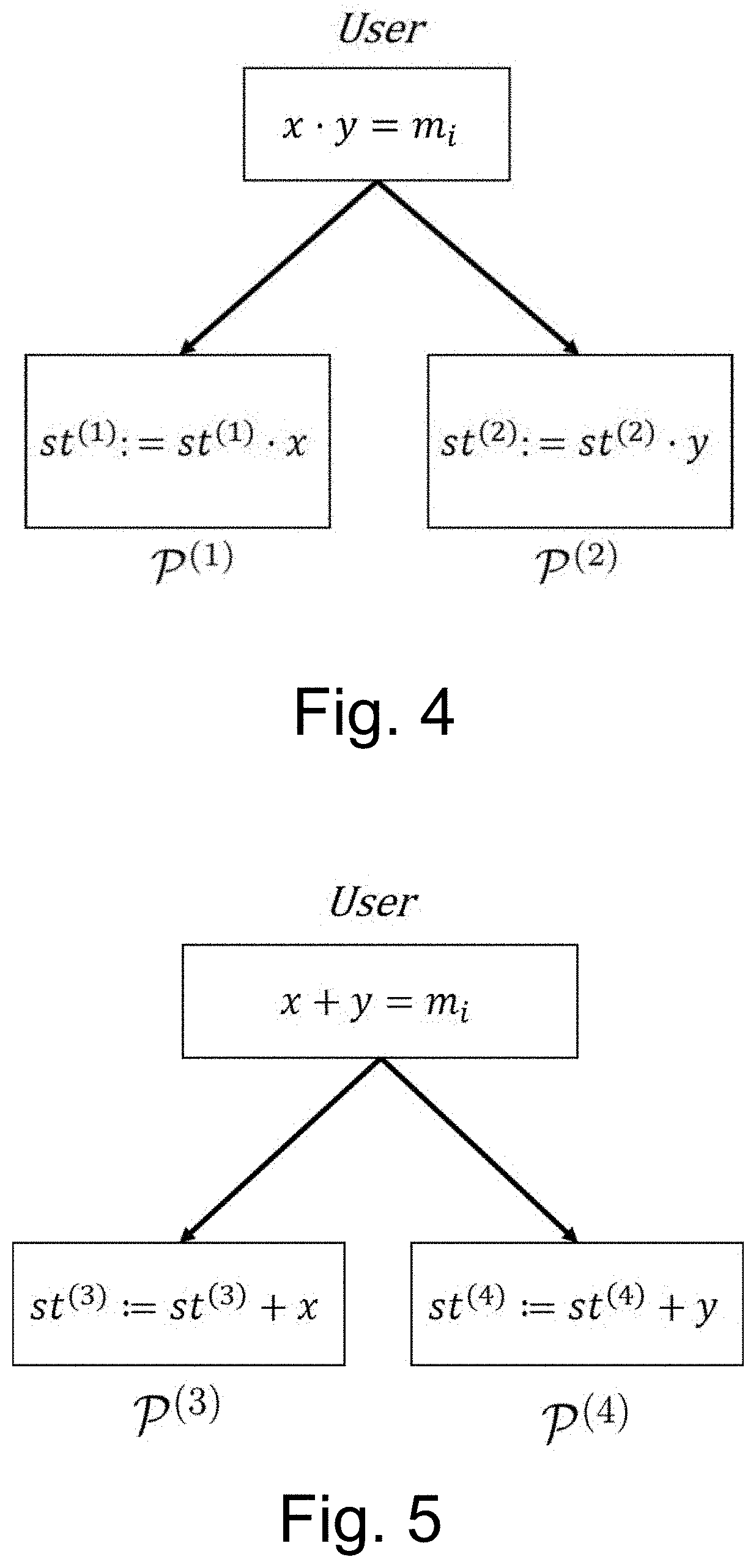
One-Round Secure Multiparty Computation of Arithmetic Streams and Evaluation of Functions
InactiveUS20210167946A1Key distribution for secure communicationCommunication with homomorphic encryptionSecret shareTheoretical computer science
A method for performing, in a single round of communication and by a distributed computational system, Secure MultiParty Computation (SMPC) of an arithmetic function ƒ:pk→p represented as a multivariate polynomial over secret shares for a user, comprising the steps of sharing secrets among participants being distributed computerized systems, using multiplicative shares, the product of which is the secret, or additive shares, that sum up to the secret by partitioning secrets to sums or products of random elements of the field; implementing sequences of additions of secrets locally by addition of local shares or sequences of multiplications of secrets locally by multiplication of local shares; separately evaluating the monomials of ƒ by the participants; adding the monomials to obtain secret shares of ƒ.
Owner:B G NEGEV TECH & APPL LTD AT BEN GURION UNIV 907553
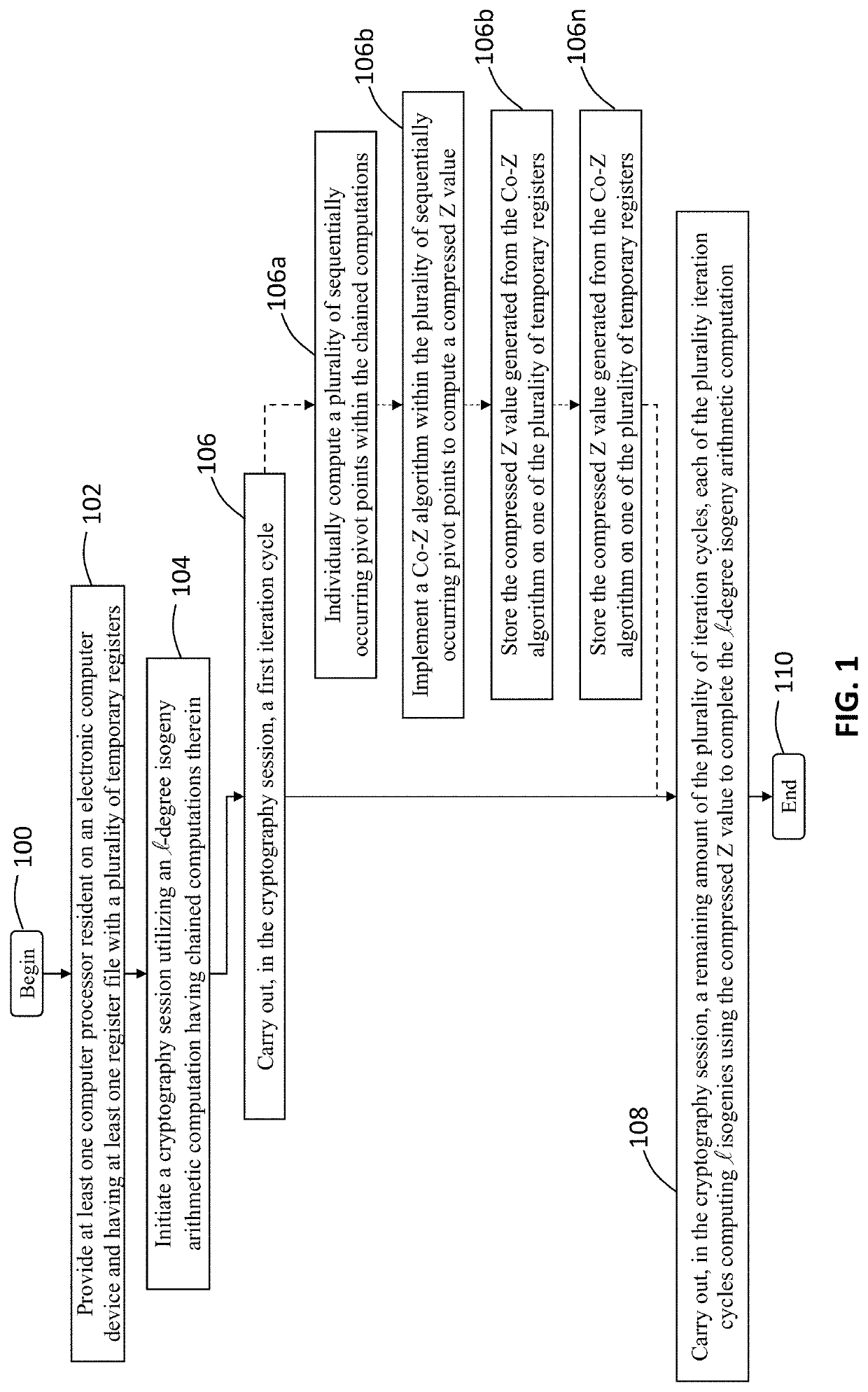
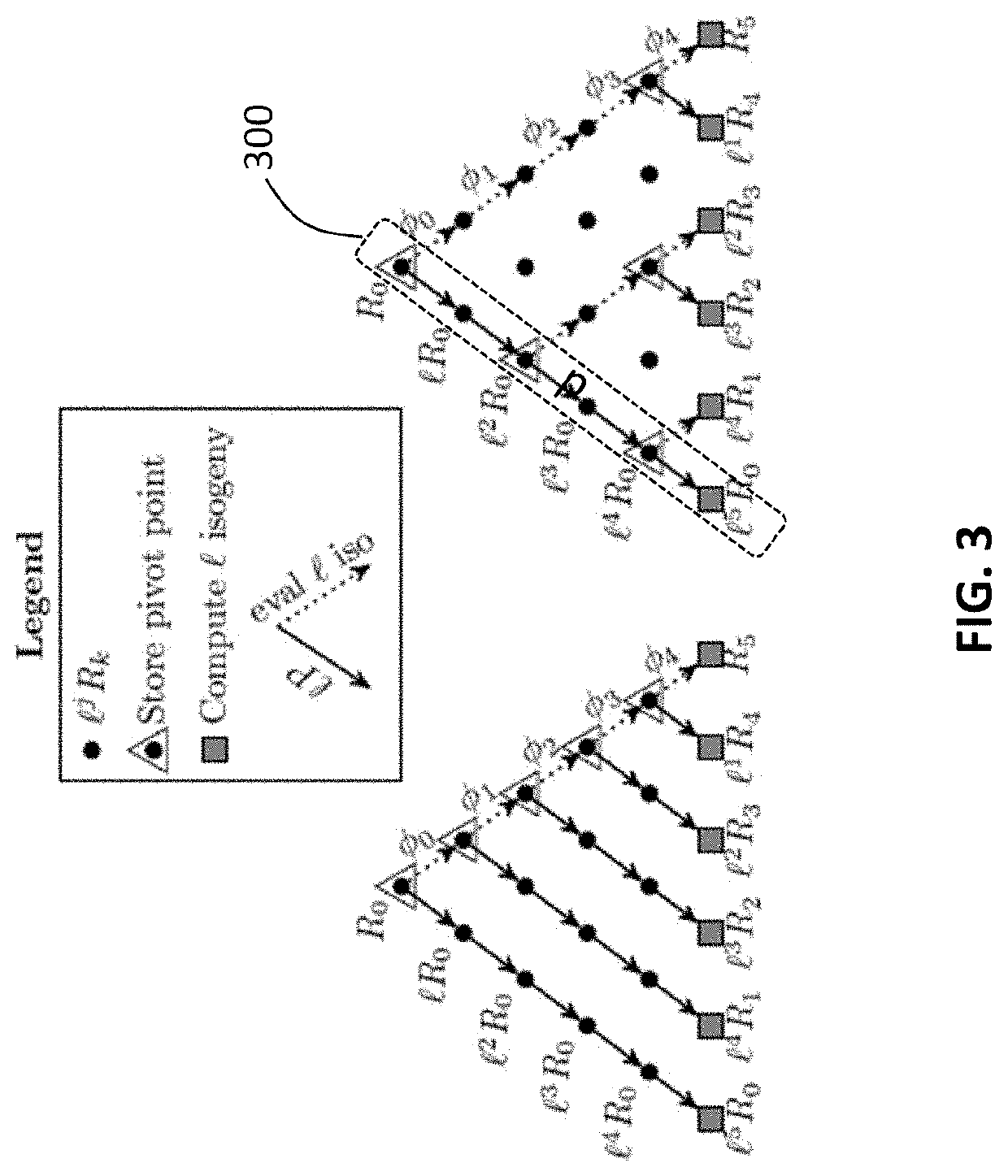
Cryptosystem and method using isogeny-based computations to reduce a memory footprint
ActiveUS20200259648A1Reduced footprintEfficient executionEncryption apparatus with shift registers/memoriesPublic key for secure communicationMemory footprintParallel computing
A computer processing system and method for reducing memory footprint that includes initiating, through at least one computer processor, a cryptography session utilizing an -degree isogeny arithmetic computation having chained computations therein. The cryptography session includes implementing a first iteration cycle, of a plurality of iteration cycles, and a implementing a remaining amount of the plurality of iteration cycles, each of the plurality iteration cycles computing isogenies using a compressed Z value to complete the -degree isogeny arithmetic computation. The first iteration cycle includes individually computing a plurality of sequentially occurring pivot points within the chained computations, implementing a Co-Z algorithm within the plurality of sequentially occurring pivot points to compute and store the compressed Z value on one of the plurality of temporary registers and computing a first isogeny of the -degree isogeny arithmetic computations using the compressed Z value.
Owner:PQSECURE TECH LLC
Efficient hardware implementation of tweakable block cipher
InactiveUS20080270505A1Efficient architectureDigital data processing detailsDigital computer detailsHardware implementationsComputer science
A combination of an infrequently-called tiny multiplication unit and a “differential” unit that quickly computes T (n+1) basing on known T n. The schedule (how often the multiplication unit is called) can be considered as a parameter of the algorithm. The proposed architecture of the “differential” unit is efficient both in terms of speed (delay) and area (gate count).
Owner:BROADCOM INT PTE LTD
Threshold cryptosystem, corresponding electronic devices and computer program products
InactiveUS20150381350A1Encryption apparatus with shift registers/memoriesPublic key for secure communicationTheoretical computer scienceComputer program
In one embodiment, it is proposed a method for encrypting a plaintext M ∈, where is a DDH-hard group of prime order p. The method is executed by an electronic device, and is remarkable in that it comprises:obtaining a public key PK=(, N, g, h, X, H, G) where N is a RSA module, elements g, h are random elements belonging to said group , X=gxhy ∈, where elements x, y are random values from a ring p, and H, G are hash functions;obtaining two random elements r, s, each element belonging to the ring p;determining a vector being (C0, C1, C2)=(M.Xr, gr, hr);determining a proof π that logg(C1)=logh(C2), said proof comprising two components c, t′, with c=H(C0, C1, C2, gs, hs) and t′=s+c.r mod p;delivering a ciphertext C=(C0, C1, C2, π)=(C0, C1, C2, c, t′) ∈3×p2.
Owner:THOMSON LICENSING SA
Image defogging method and system
InactiveCN106251296AMeet real-time requirementsGuaranteed filtering effectImage enhancementTransmittanceComputer science
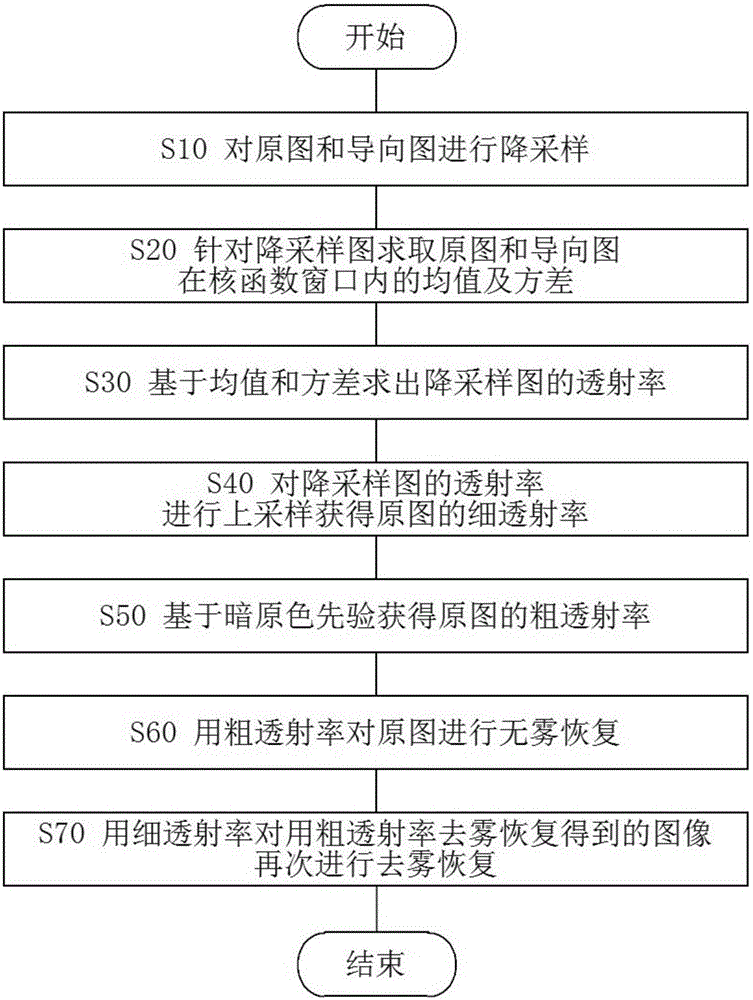
The invention discloses an image defogging method and a system. The method comprises steps that downsampling of a to-be-defogged original image I and a guiding image p is carried out; on the basis of a downsampling image, mean values muk and Pk<-> of the original image I and the guiding image p in a kernel function window, and a variance Qk<2> are resolved; on the basis of the mean values and the variance, a guiding filtering image qi of the downsampling image is resolved, namely transmissivity of the downsampling image; rising-sampling of the transmissivity of the downsampling image is carried out to acqurie fine transmissivity t of the original image; no-fog image recovery of the to-be-defogged image is carried out on the basis of the fine transmissivity. Through the method, not only can image details be guaranteed, but also efficiency is improved, and thereby practicality of the defogging technology is guaranteed especially in a mobile terminal.
Owner:BEIJING YUANXIN SCI & TECH
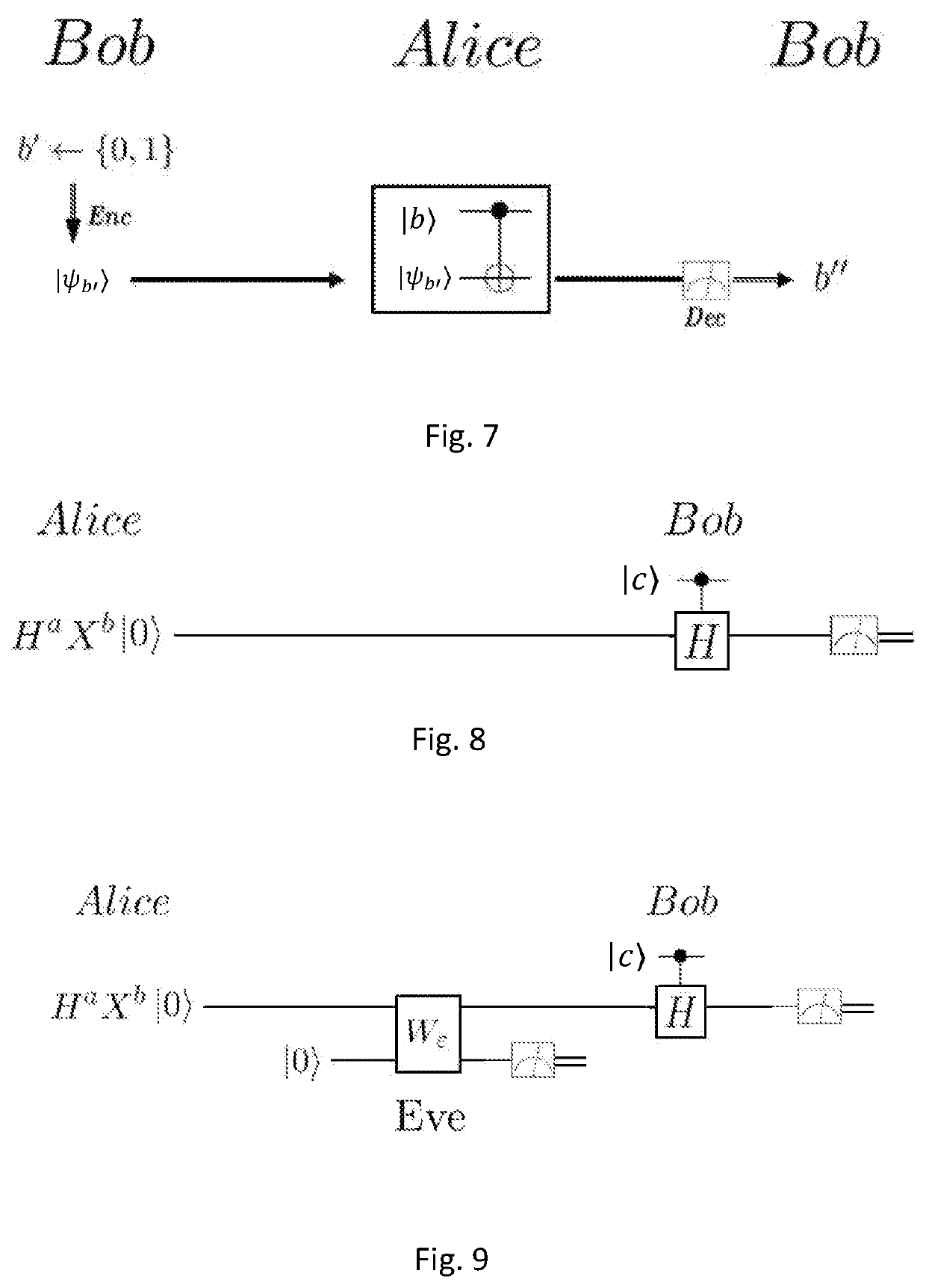
System and Method for Performing Information-Theoretically Secure Quantum Gate Computation and Quantum Key Distribution, Based on Random Rotation of Qubits
PendingUS20220231844A1Quantum computersKey distribution for secure communicationParticle physicsQuantum gate
A computer implemented method for encoding bits by qubits to perform information-theoretically secure quantum gate computation, according to which pairs of quantum bits consisting of a first qubit as an encoding of “0” and a second qubit as an encoding of “1” are randomly selected, such that the first and second qubits are orthogonal to each other as quantum states and are interchanged by a NOT gate. Each qubit rotating to a desired initial direction and then each rotated qubit is further rotated to its antipodal direction by applying a quantum NOT or CNOT gate to the each rotated qubit, without any knowledge about the desired direction. A unitary gate is further applied over the qubits, using an ancillary |0 qubit that creates an equally weighted superposition of the qubits.
Owner:B G NEGEV TECH & APPL LTD
System and method for mobile proactive secret sharing
Described is a system for mobile proactive secret sharing. The system utilizes a Secret-Share protocol to share, by server Pj, a secret s among a set of servers , such that a degree of polynomials used to share the secret s is d and a shared secret is denoted as [s]. A GenPoly protocol is used to cause the servers in the set of servers to generate l random polynomials of degree D. A Secret-Redistribute protocol is used to redistribute the shared secret [s] to a set of new servers ′. Finally, a Secret-Open protocol is used to open the shared secret [s].
Owner:HRL LAB
Two-server privacy-preserving clustering
ActiveUS20210133587A1Improve efficiencyImprove scalabilityMathematical modelsRandom number generatorsExtensibilityEngineering
Described herein are systems and techniques for privacy-preserving unsupervised learning. The disclosed system and methods can enable separate computers, operated by separate entities, to perform unsupervised learning jointly based on a pool of their respective data, while preserving privacy. The system improves efficiency and scalability, while preserving privacy and avoids leaking a cluster identification. The system can jointly compute a secure distance via privacy-preserving multiplication of respective data values x and y from the computers based on a 1-out-of-N oblivious transfer (OT). In various embodiments, N may be 2, 4, or some other number of shares. A first computer can express its data value x in base-N. A second computer can form an ×N matrix comprising random numbers mi,0 and the remaining elements mi,j=(yjNi-mi,0) mod . The first computer can receive an output vector from the OT, having components mi=(yxi Ni-mi,0) mod .
Owner:VISA INT SERVICE ASSOC
Feedback-based network code TCP (Transmission Control Protocol) decoding method and device
InactiveCN106027208AMeet real-time requirementsReduce decoding latencyError prevention/detection by using return channelNetwork traffic/resource managementDecoding methodsNetwork code
The present invention provides a network coding TCP decoding method and device based on feedback. The method includes: when receiving a TCP data packet sent by the TCP layer, the sending end performs the encoding packet that needs to be sent currently according to the packet loss rate of the current link. The number Sn is updated; according to the feedback information carried in the response message sent by the receiving end received at the current moment, the current number of encoding window locks Ln is determined; if the current number of encoding window locks Ln is not 0, the encoding window is fixed , and the W TCP data packets in the encoding window will be encoded according to the number of packets Perform preset encoding, and encode the encoded packets are sent to the receiver. The present invention can not only generate active compensation according to the network environment, but also make corresponding adjustments based on the feedback to speed up the full rank of the decoding matrix and reduce the decoding waiting time delay.
Owner:INST OF INFORMATION ENG CAS
Device and method for calculating conversion parameter of montgomery modular multiplication and program therefor
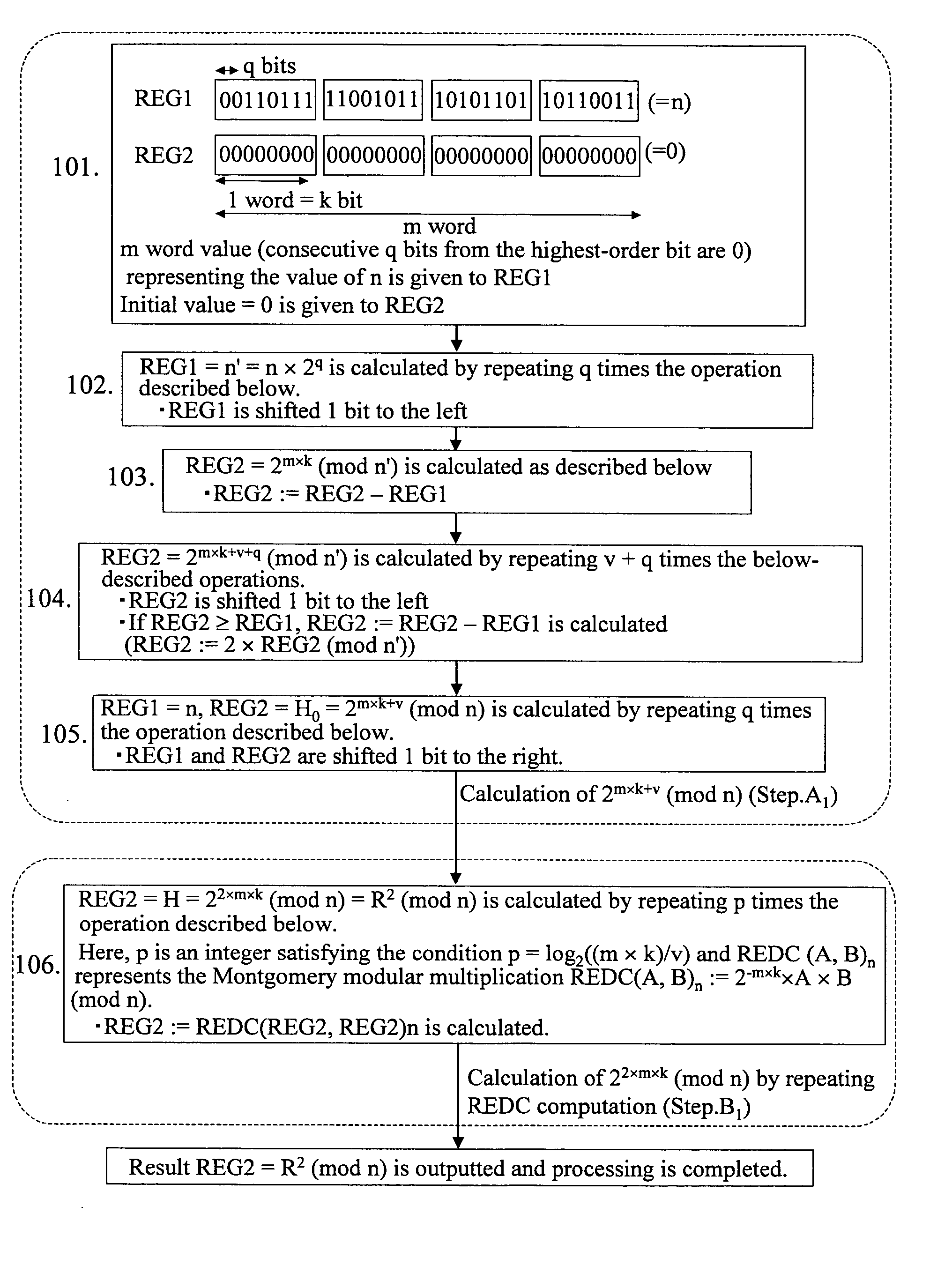
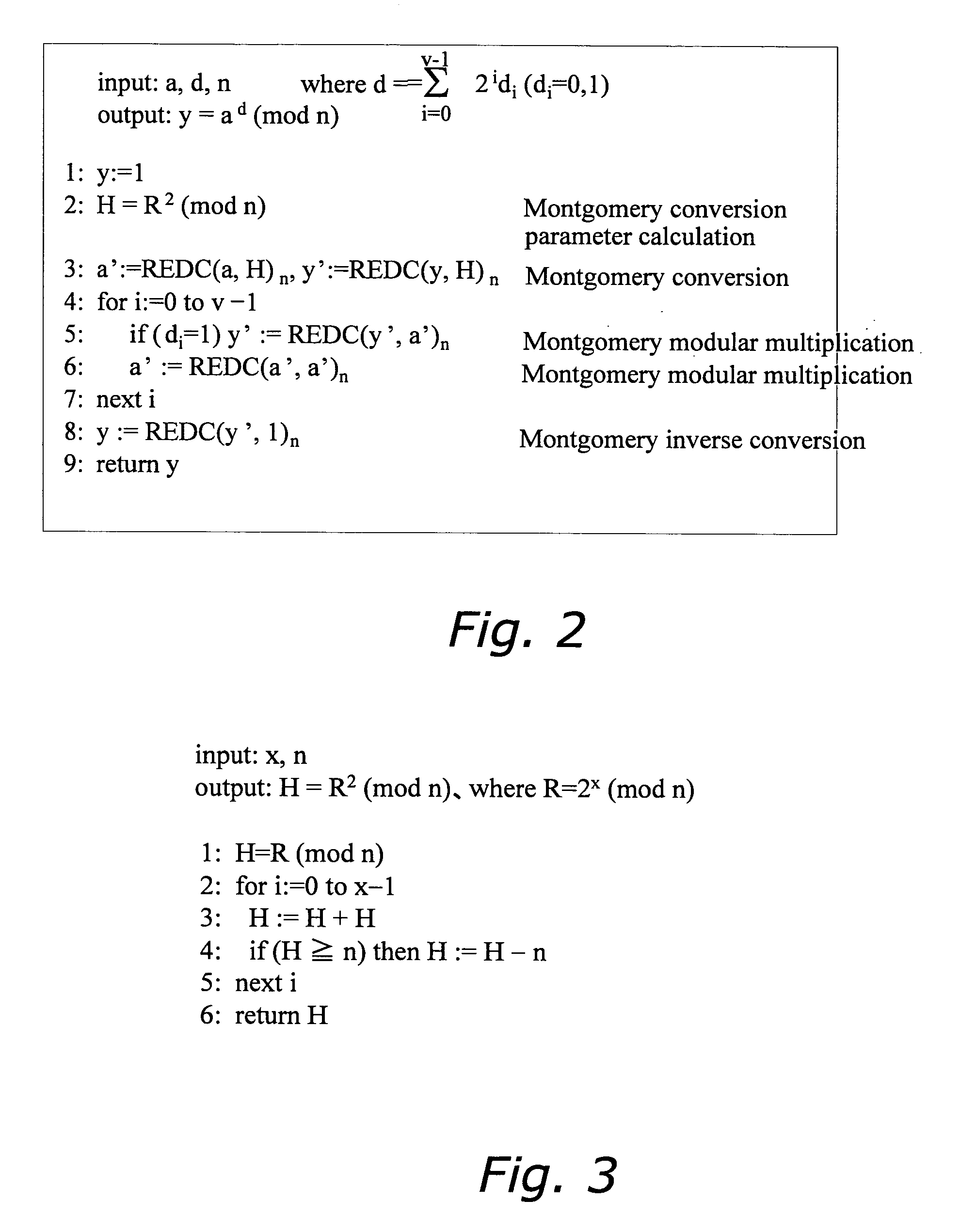
InactiveUS20060235921A1Promote generationIncrease speedDigital computer detailsComputations using residue arithmeticMontgomery reductionComputer science
A method for calculating a conversion parameter of the Montgomery modular multiplication to improve the efficiency of software installation, comprising a first step for calculating H0=2v×R (mod n) (where v is an integer, v≧1, and (m×k) / v is an integer), a second step for calculating Hp=2v×2<?img id="custom-character-00001" he="3.13mm" wi="2.12mm" file="US20060235921A1-20061019-P00900.TIF" alt="custom character" img-content="character" img-format="tif" ?>p×R (mod n) from H0=2v×R (mod n) by repeating Hi=REDC(Hi-1, Hi-1)n with respect to i=1, 2, . . . , p (where p represents an integer satisfying the condition 2p≧(m×k) / v>2p−1, REDC represents the Montgomery modular multiplication REDC(a, b)n=a×b×R−1 (mod n), and xˆi represents exponential computation xi); and a third step for calculating Hp=R2 (mod n) by calculating Hp=REDC(Hp, g)n with respect to Hp obtained in the second step when 2p>(m×k) / v (where g=2k×E(p,m,k), E(p, m, k)=2×m−(v×2p) / k) and finally outputting Hp as R2 (mod n).
Owner:FUJITSU LTD
Cryptographic method on binary edwards elliptic curves
ActiveUS20190081786A1Simple calculationEasy to operatePublic key for secure communicationEdwards curveSecurity level
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Method for judging convex figure shape similarity in digital image
ActiveCN105678336AReduce time complexityEasy to implementCharacter and pattern recognitionTime complexityOmega
The invention provides a method for judging the convex figure shape similarity in a digital image. The method comprises the steps of S1, for any two convex figure shapes omega 1 and omega 2 that are subjected to similarity judgment, respectively figuring out the complex plane feature vectors of the two convex figure shapes based on GCT transformation and recording the complex plane feature vectors thereof as F1 and F2; calculating the intensity sequences and the phase sequences thereof and respectively recording the intensity sequences and the phase sequences as M1, S1, M2 and S2; judging the similarity between the phase sequence S1 and the phase sequence S2; calculating according to img file='DDA0000901986470000011.TIF' wi='131' he='65', img file='DDA0000901986470000012.TIF' wi='1938' he='99', and img file='DDA0000901986470000013.TIF' wi='1123' he='98'; when delta is larger than 0.2, judging that the two convex figure shapes are not similar; S3, judging the similarity between the intensity sequence M1 and the intensity sequence M2; calculating according to img file='DDA0000901986470000014.TIF' wi='918' he='94', img file='DDA0000901986470000015.TIF' wi='1907' he='99', and img file='DDA0000901986470000016.TIF' wi='579' he='97'; when eta is larger than 0.2, judging that the two convex figure shapes are not similar; otherwise, judging that the two convex figure shapes are similar. The method is simple to realize and low in time complexity. The identification accuracy of the method is up to more than 90%.
Owner:珠海金智维信息科技有限公司
Manufacturing method and device of eMMC burning file and computer equipment
PendingCN112486514ALow costRedundant data error correctionSoftware deploymentFile systemSoftware engineering
The invention relates to the technical field of burning file manufacturing, and discloses a manufacturing method of an Android eMMC burning file. The manufacturing method comprises the following stepsof creating an initial eMMC burning file, wherein the initial eMMC burning file is an empty file; after compiling of the Android system is completed, generating an img mirror image file needed by each partition; obtaining the partition size size size of the img mirror image file of each partition, and calculating the offset address of the img mirror image of each partition in the burning file according to the partition size size size; converting the img mirror image file in the simg format into an img mirror image file in a raw format; and copying the img mirror image file of each partition to a corresponding initial position of the initial eMMC burning file according to the offset address by using a Linux dd command to obtain a final eMMC burning file. According to the method provided bythe invention, the technical problems that in the prior art, an eMMC burning file needs to be manufactured by a hardware platform, and the manufacturing mode is low in efficiency, high in cost and low in stability are solved.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD +1
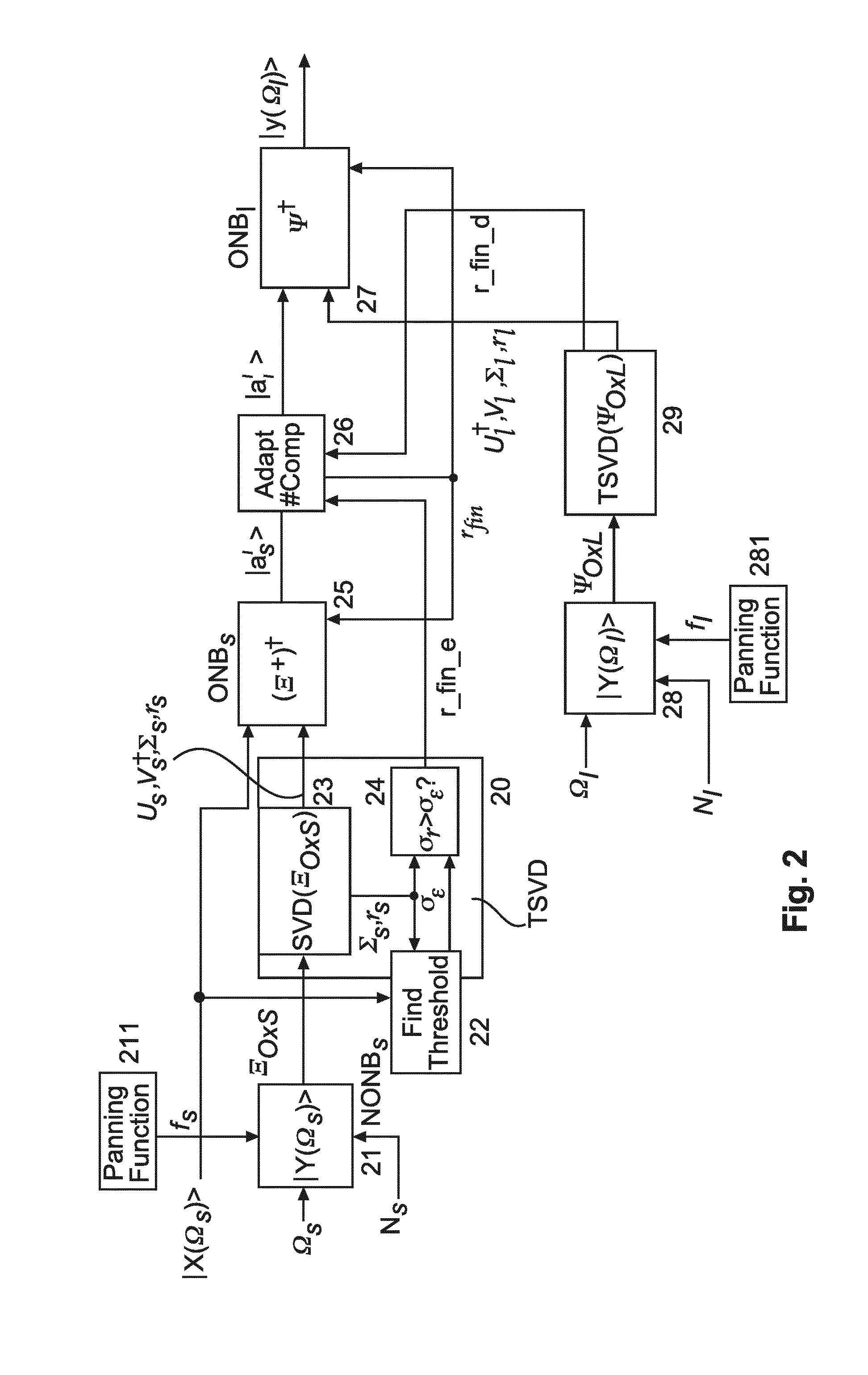
Method and apparatus for higher order ambisonics encoding and decoding using singular value decomposition
ActiveUS20170006401A1Energy balanceReduce component countSpeech analysisStereophonic systemsSingular value decompositionSound sources
The encoding and decoding of HOA signals using Singular Value Decomposition includes forming (11) based on sound source direction values and an Ambisonics order corresponding ket vectors (|(Ω5))) of spherical harmonics and an encoder mode matrix (Ξ0χs). From the audio input signal (|χ(Ωs))) a singular threshold value (σε) determined. On the encoder mode matrix a Singular Value Decomposition (13) is carried out in order to get related singular values which are compared with the threshold value, leading to a final encoder mode matrix rank (rfine). Based on direction values (Ωι) of loudspeakers and a decoder Ambisonics order (Nι), corresponding ket vectors (IY(Ωι)) and a decoder mode matrix (Ψ0χL) are formed (18). On the decoder mode matrix a Singular Value Decomposition (19) is carried out, providing a final decoder mode matrix rank (r find). From the final encoder and decoder mode matrix ranks a final mode matrix rank is determined, and from this final mode matrix rank and the encoder side Singular Value Decomposition an adjoint pseudo inverse (Ξ+)† of the encoder mode matrix (Ξ0χs) and an Ambisonics ket vector (Ia′s) are calculated. The number of components of the Ambisonics ket vector is reduced (16) according to the final mode matrix rank so as to provide an adapted Ambisonics ket vector (|a′ι). From the adapted Ambisonics ket vector, the output values of the decoder side Singular Value Decomposition and the final mode matrix rank an adjoint decoder mode matrix (Ψ)† is calculated (15), resulting in a ket vector (|y(Ωι)) of output signals for all loudspeakers.
Owner:DOLBY INT AB
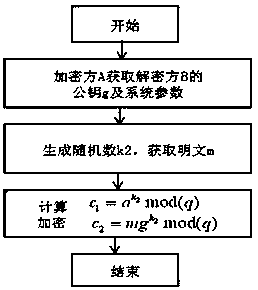
public key encryption and decryption method of a finite field multiplication group with a Meisen prime number
ActiveCN109756335AReduce length requirementsEasy to implementPublic key for secure communicationPlaintextCiphertext
The invention relates to a public key encryption method based on a finite field (shown in the formula in the specification) multiplication group, in particular to a public key encryption method basedon the finite field ( shown in the formula in the specification) multiplication group. wherein p is a prime number, and the formula (1) is shown in the specification, and p is a prime number and is made to be a Mesene number. Finite field isomorphism and polynomial field (img field RE-482803DEST _ PATH _ IMAGE001. TIF) isomorphism and polynomial field (img field RE-637709DEST _ PATH _ IM wherein the structural formula of the polynomial is as shown in the specification, the structural formula of the polynomial is as shown in the specification, and the structural formula of the polynomial is asshown in the specification, wherein the structural formula of the polynomial is as shown in the specification, and the structural formula of the polynomial is as shown in the specification. In the Finite field multiplication group wherein the order of the formula (I) is shown in the specification, the order of the formula (I) is shown in the specification, and the order of the formula (I) is shownin the specification. The order of the formula (II) is shown in the specification. Therefore, the order of the element a of any non-unit element is shown in the specification, wherein the order of the element a of any non-unit element is shown in the specification; the order of the element b of any non-unit element is shown in the specification; The invention discloses a public key cryptosystem.the receiver B discloses a random element a; the primitive polynomial q is used as a system parameter; the k1 is seen as a private key by the random number; A public key g (shown in the specification)is disclosed. An encryption party A generates a random number k2, and the random number k2 is smaller than or equal to 1 and smaller than or equal to 1. carrying out a modular exponentiation operation (shown in the formula in the specification), carrying out a modular exponentiation operation (shown in the formula in the specification), and carrying out a modular exponentiation operation (shown in the formula in the specification), carrying out modular multiplication on the encrypted plaintext m (shown in the formula in the specification), and carrying out modular multiplication on the encrypted plaintext m, The method comprises the following steps that: a decryption party receives a ciphertext, generates a ciphertext according to the ciphertext, and generates the ciphertext according tothe ciphertext. The decryption party receives the ciphertext and generates the ciphertext according to the ciphertext. and decrypting by using the private key k1 to obtain a plaintext m. The method disclosed by the invention can be applied to the aspects of symmetric passwords, public key passwords, digital signatures and the like. The method disclosed by the invention can be applied to the fieldsof the symmetric passwords, the public key passwords, the digital signatures and the like.
Owner:江宝安
Firmware tamper-proofing method and equipment based on Android system
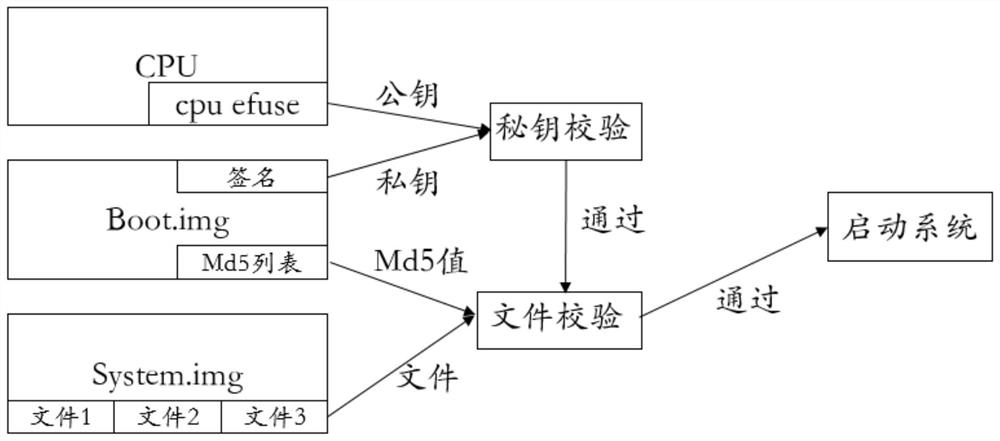
InactiveCN112464243APrevent tamperingProtection securityDigital data protectionPlatform integrity maintainanceSoftware engineeringIMG
The invention discloses a firmware tamper-proofing method and device based on an Android system, and relates to the security technology, and the method comprises the following steps: reading a publickey from a CPU efuse; obtaining a signature of the boot.img file; obtaining a private key from the boot.img file according to the signature of the boot.img file; carrying out secret key matching on the public key and the private key, and reading an integrity check value of a preset file in the system. Im.img file from the boot. Img file under the condition that the secret key matching is successful; and performing integrity check on a preset file in the system. Img file according to the integrity check value, and starting the system under the condition that the integrity check is successful. According to the invention, the system firmware can be effectively prevented from being illegally tampered, and the user information security is ensured.
Owner:微讯智造(广州)电子有限公司
Method, system and device for installing virtual machine operating system
ActiveCN111880818AAchieve installationSoftware simulation/interpretation/emulationSoftware deploymentPathPingOperational system
The invention discloses a method, system and device for installing a virtual machine operating system. The method comprises the following steps: obtaining a vmlinuz temporary file and an initrd.img temporary file; adding a kickstart configuration file and a configuration script file to an initrd.img temporary file; configuring paths of the vmlinuz temporary file and the initrd.img temporary file to a metadata configuration file of the virtual machine; when the virtual machine is started to enter an installation operation system, configuring a system kernel based on the vmlinuz temporary file in the metadata configuration file of the virtual machine, and configuring corresponding hardware equipment based on the kickstart configuration file and the configuration script file in the initrd.imgtemporary file to complete system installation. Therefore, according to the virtual machine operating system installation mode, a PXE server does not need to be deployed, installation of the virtualmachine operating system can be achieved only through a file configuration mode, and the application range is wide.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Operating system deployment method and device, electronic equipment and storage medium
The invention discloses an operating system deployment method and device, electronic equipment and a computer readable storage medium. The method comprises the steps: determining a target operating system type and a target version which need to be deployed, and obtaining a target optical disc mirror image file of the target operating system corresponding to the target operating system type and the target version; determining all devices needing to be deployed, and storing driving information corresponding to the devices which are not supported by the target optical disc mirror image file into a temporary directory; and generating a universal initrd.img file based on the driving information in the temporary directory, so as to deploy the target operating system by using the universal initrd.img file. According to the operating system deployment method provided by the invention, the deployment of the equipment can be completed when the equipment lacks the support of a kernel driver.
Owner:INSPUR BUSINESS MACHINE CO LTD
Power-down protection method based on universal computer operating system
PendingCN110837437AAchieve protectionFlexible data protectionRedundant operation error correctionOperational systemFile system
The invention relates to a power-down protection method based on a universal computer operating system. The power-down protection method comprises the following steps: S1, acquiring an aufs file corresponding to an operating system version; S2, creating a folder to be downloaded; S3, adding the support of the kernel to aufs; S4, manufacturing initrd; and S5, generating a mirror image file initrd.img of the initrd. According to the power-down protection method based on the universal computer operating system, the data protection mode is flexible, system file safety is protected, and system fileprotection under the problems of instantaneous undervoltage, file system damage, accidental outage and the like can be achieved.
Owner:CHINA STANDARD SOFTWARE +1
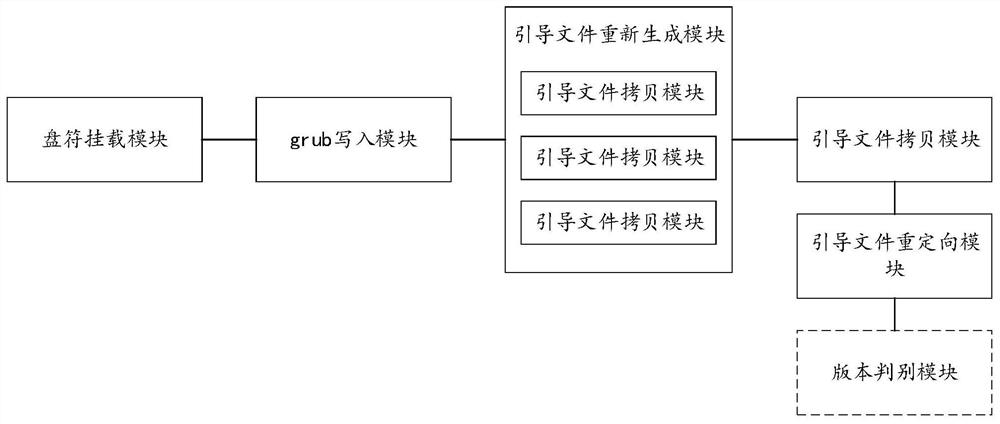
A method and system for resetting passwords based on linux
ActiveCN108984230BReduce memory loadSimplify the process of resetting your passwordDigital data authenticationProgram loading/initiatingPasswordEngineering
The present invention provides a password reset method and system based on Linux, comprising: S1, mounting the drive letter of the mobile device to / mnt; S2, writing grub into the mobile device; S3, resetting the password Write the script into the initramfs.img file to generate a new initramfs.img file; S4, copy the initramfs.img file containing the password reset script into the mobile device. S5. Modify the initramfs boot file of the grub.cfg file in the mobile device to be a newly generated initramfs.img file. In the present invention, a password reset script is built into a mobile device such as a U disk. When the user forgets the system password and needs to reset the password, he or she chooses to boot from the U disk mobile device, and the built-in password reset script automatically runs to complete reset Password. Users do not need to remember the complex operation of repeatedly trying or modifying the grub kernel startup parameters to enter the shell interface to reset the password. They only need to start the reset from the preset U disk mobile device, which reduces the memory burden of the user and simplifies the heavy operation. The process of setting a password is convenient for the user to reset the password.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method for establishing secure public-key cryptography against quantum computing attacks
ActiveCN107911209BKey distribution for secure communicationCryptographic attack countermeasuresPlaintextKey (cryptography)
The present invention relates to the field of information safety, and discloses a method for establishing public key cryptogram against quantum computing attack. The method comprises the following steps of: (11) a protocol first party selects a braid group Bn with an index n of being not small than 7, and selects a subgroup A generated by employing a1, a2, ..., ak in the Bn and a subgroup B generated by employing b1, b2, ..., bm in the Bn; (12) the protocol first party selects [Theta], wherein Bn maps to {0, 1}k is an Hash function from Bn to plaintext space {0, 1}k collision resistance; (13)the protocol first party selects an element x as a private key, wherein x=x(a1, a2, ..., ak) belonging to A, and selects (Bn, A, B, [Theta], X-1b1x, x-1b2x, ..., x-1bmx) as a public key; (14) a protocol second party selects an element y, wherein y=y(b1, b2, ..., bm) belonging to B, calculates KB=(y< 1>y(x< 1>b1x, x< 1>b2x, ..., x< 1>bmx))< 1>=(y< 1>x< 1>yx)< 1>=x< 1>y< 1>xy, performs encryption calculation of a plaintext p to obtain a ciphertext (img file='DDA0001531187730000011. TIF' wi='286' he='71' / ) and sends t to the protocol first party; and (15) the protocol first party calculates KA=x<1>x(y< 1>a1y,y< 1>a2y, ...,y< 1>aky)=x< 1>y< 1>xy, performs decryption calculation to obtain a plaintext (img file='DDA0001531187730000012. TIF' wi='283' he='70' / )(img file='DDA0001531187730000013. TIF' wi='510' he='63' / ). The method provided by the invention can resist all the known attacks comprising quantum computing attack.
Owner:SHENZHEN UNIV
System and method for natural language processing with a multinominal topic model
ActiveUS11416689B2Improve topic modellingIncrease probabilityNatural language translationNatural language analysisAlgorithmTheoretical computer science
The invention refers to a natural language processing system configured for receiving an input sequence ci of input words (v1, v2, . . . vN) representing a first sequence of words in a natural language of a first text and generating an output sequence of output words (, , . . . ) representing a second sequence of words in a natural language of a second text and modeled by a multinominal topic model, wherein the multinominal topic model is extended by an incorporation of language structures using a deep contextualized Long-Short-Term Memory model.
Owner:SIEMENS AG
SPL rollback method and device based on UBOOT, storage medium and terminal
The invention provides an SPL rollback method and device based on UBOOT, a storage medium and a terminal. The SPL rollback method comprises the steps that: an MISC partition of the terminal is read, and OTA upgrading information of the terminal is obtained; the obtained OTA upgrading information is analyzed, and whether OTA upgrading is completed or not is judged; if the judgment result is that the OTA upgrade fails, the data in the SPL main partition is replaced with the data in the SPL standby partition, and the terminal is restarted to complete SPL rollback; and if the judgment result is that OTA upgrading is successful, SPL rollback does not need to be carried out. Whether normal startup can be carried out or not is detected in time after OTA upgrade by using the recognition characteristic of UBOOT on an A / B partition of an MISC partition, and after OTA upgrade failure is detected, the SPL main partition and the SPL standby partition are read and written in time, the data in the SPL main partition is replaced with the data in the SPL standby partition, and a terminal is restarted, so that the purpose of rollback of the SPL is achieved. The situation that the terminal fails to start due to the fact that the SPL main partition and the SPL standby partition are inconsistent is prevented, and then the situation that the terminal cannot be started due to the fact that the IMG is incompatible is prevented.
Owner:XIAMEN UNISOC TECH CO LTD
A Distance Protection Method for Fail-Open Components in Oscillating Blocking
ActiveCN103545798BHigh sensitivityImprove transition resistanceEmergency protective circuit arrangementsElectrical resistance and conductancePhase currents
The invention relates to a distance protection method for a fault-opening element in oscillation locking, comprising the following steps: collecting three-phase current and three-phase voltage at the installation place of the protection; judging whether to enter the oscillation locking state; if and Go to the penultimate step, otherwise, go to the next step; if the current asymmetry m≥0.65, open the distance protection; otherwise, go to the next step; if the oscillation center voltage Either one satisfies Delay 200ms to open the distance protection section I, and open the distance protection section II instantaneously; otherwise, go to the next step; if Either one satisfies Delay 200ms to open distance protection stage I, and instantaneously open distance protection stage II; otherwise, block distance protection; if Either one satisfies , open the distance protection with a delay of 150ms; otherwise, go to the next step; if Either one satisfies , delay 150ms to open the distance protection; otherwise, block the distance protection. The method improves the sensitivity of the fault-opening element in the oscillation blocking, so that the distance protection can operate correctly when the fault passes through a relatively large transition resistance.
Owner:STATE GRID CORP OF CHINA +1
Multi-reservoir water scheduling method, terminal, storage medium and heterogeneous computing system
ActiveCN109214726BImprove timelinessImprove computing efficiencyClimate change adaptationResourcesScheduling (computing)IMG
A method for dispatching water quantity of multiple reservoir is disclosed in an embodiment of the present application, terminal, storage medium and heterogeneous computing system, in accordance withthat present invention, since the present embodiment can control the calculation and output of the individual optimum fitness among the Q complexes in parallel, then the population optimum fitness (img file = 'DDA0001882304610000011. TIF' wi= '91' he= '79' / ) is output according to the individual optimum fitness, and the population optimum fitness (img file = 'DDA 0001882304610000012. TIF 'wi=' 72'he=' 79 ' / ) When the iteration termination condition is satisfied, the parameters corresponding to the optimal fitness (img file = 'DDA0001882304610000013. TIF' wi= '72' he= '79' / ) of the populationare used to regulate the water quantity of the reservoir group, the parallelization technology improves the efficiency of calculating the water dispatching of reservoir group, and has higher computational efficiency for high-dimensional, non-linear and strongly constrained flood control problems.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
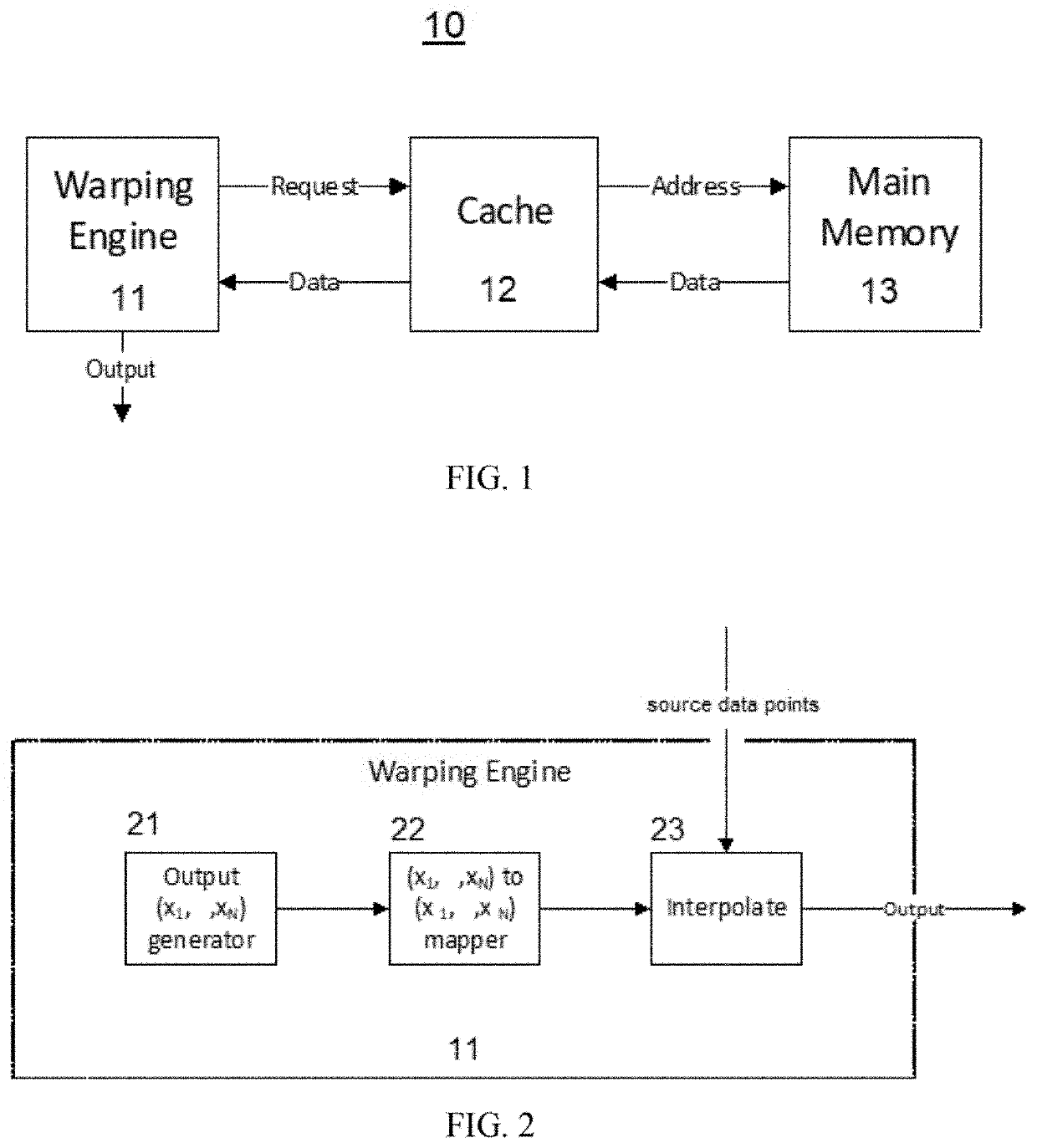
Warping data
ActiveUS11508031B2Minimize impactImprove performanceMemory architecture accessing/allocationGeometric image transformationEngineeringData mining
Owner:SAMSUNG ELECTRONICS CO LTD
Method for decoding inertia-effect bit-flip LDPC codes
ActiveUS11469775B2Error correction/detection using multiple parity bitsCode conversionInertial effectLow-density parity-check code
A method for decoding a Low Density Parity Check code. At each decoding iteration, as long as the syndrome of the estimated word indicates an error, a set ({tilde over (F)}) of the least reliable bits of the word is determined as those where the value of a local energy function ({tilde over (E)}n) is less than a threshold value. The local energy value of a bit includes a first component proportional to the correlation between this bit and a sample corresponding to the observed signal, a second component representing the number of non-satisfied constraints wherein the bit acts, and a third component decreasing with the number (n) of iterations made since the last flipping of this bit. The bits of the estimated word belonging to this set are flipped, where applicable with a predetermined probability, to provide a new estimated word at the following iteration.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com