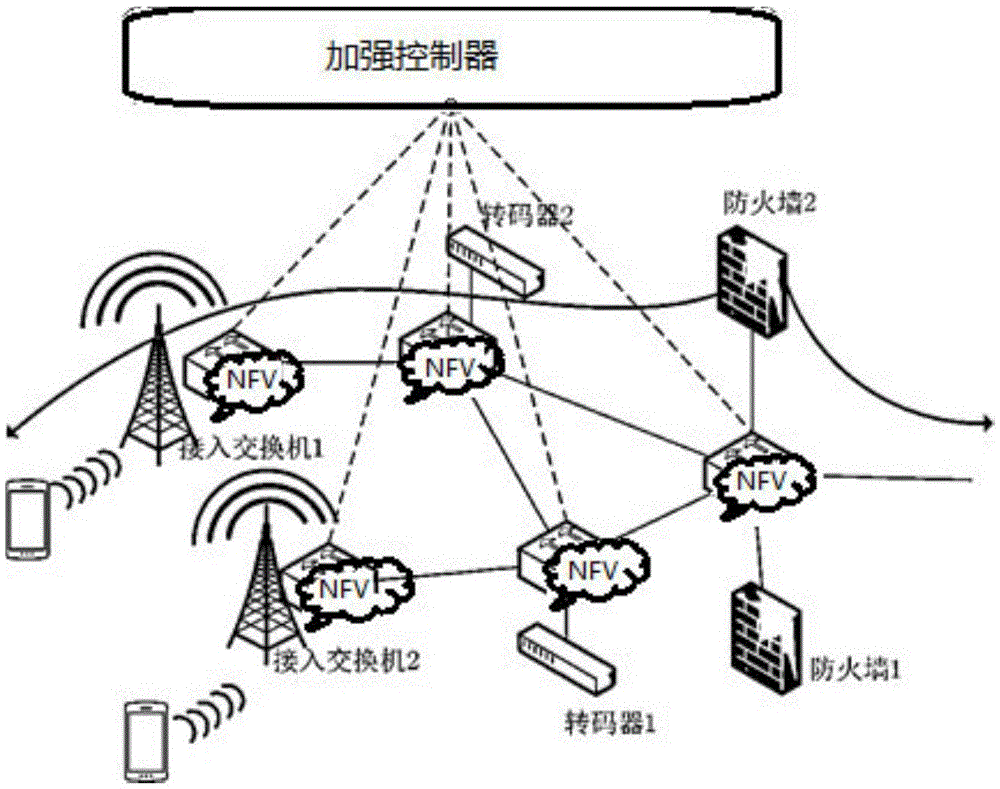
5G network multistage attack mitigation method based on software defined network (SDN) and network function virtualization (NFV)
A network and 5G technology, applied in the field of 5G network multi-level attack mitigation based on SDN and NFV, can solve the problems that cannot be directly applied to SDN-MN, and cannot be directly used in 5G networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] The present invention will be described in detail below in conjunction with specific embodiments. The following examples will help those skilled in the art to further understand the present invention, but do not limit the present invention in any form. It should be noted that those skilled in the art can make several modifications and improvements without departing from the concept of the present invention. These all belong to the protection scope of the present invention.
[0085] The present invention first extends the definition of SDN-MN architecture in 5G to improve system capabilities and monitor comprehensive network events and deploy network security functions in a timely manner, and then proposes an evidence-driven security assessment mechanism using SDN-MN factors and NFV detection, Finally, a mechanism for attack mitigation using SDN control and NFV deployment is proposed.
[0086] Concrete steps of the present invention include:
[0087] Step S1: Extend t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com