Method and system for security detection and repair of wireless network
A wireless network and security detection technology, applied in the field of security detection and repair systems, can solve problems such as home routers are easy to intrude, wireless network security is low, router firmware security loopholes, etc., and achieve the effect of curbing phishing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
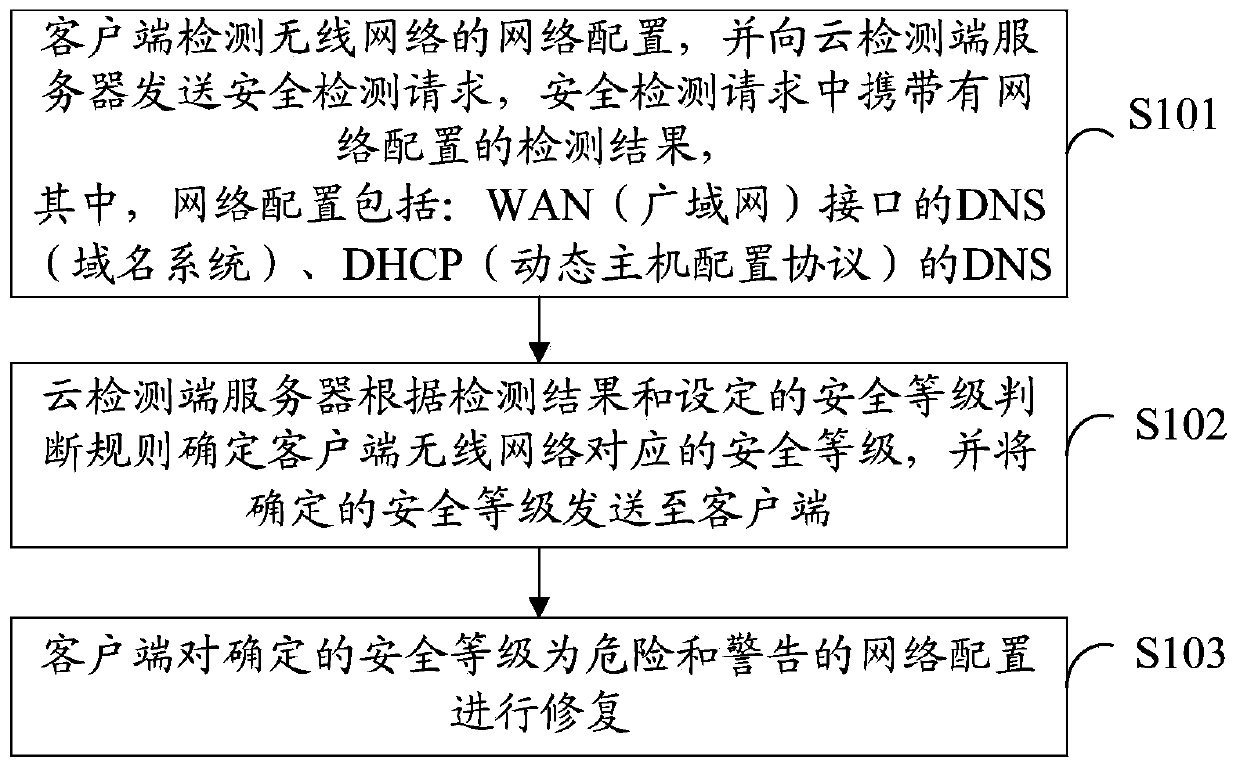
[0042] refer to figure 1 , shows a flow chart of steps of a method for security detection and repair of a wireless network according to an embodiment of the present invention, the method for security detection and repair of a wireless network may specifically include the following steps:
[0043] Step S101, the client detects the network configuration of the wireless network, and sends a security detection request to the cloud detection server. The security detection request carries the detection result of the network configuration, wherein the network configuration includes: DNS (domain name) of the WAN (wide area network) interface system), DNS for DHCP (Dynamic Host Configuration Protocol).
[0044] The WAN (Wide Area Network, wide area network) interface is the port where the network device connects to the external network. Hackers often change the DNS of the WAN interface of the network connection device to malicious DNS. Malicious DNS resolves normal URLs to phishing web...
Embodiment 2
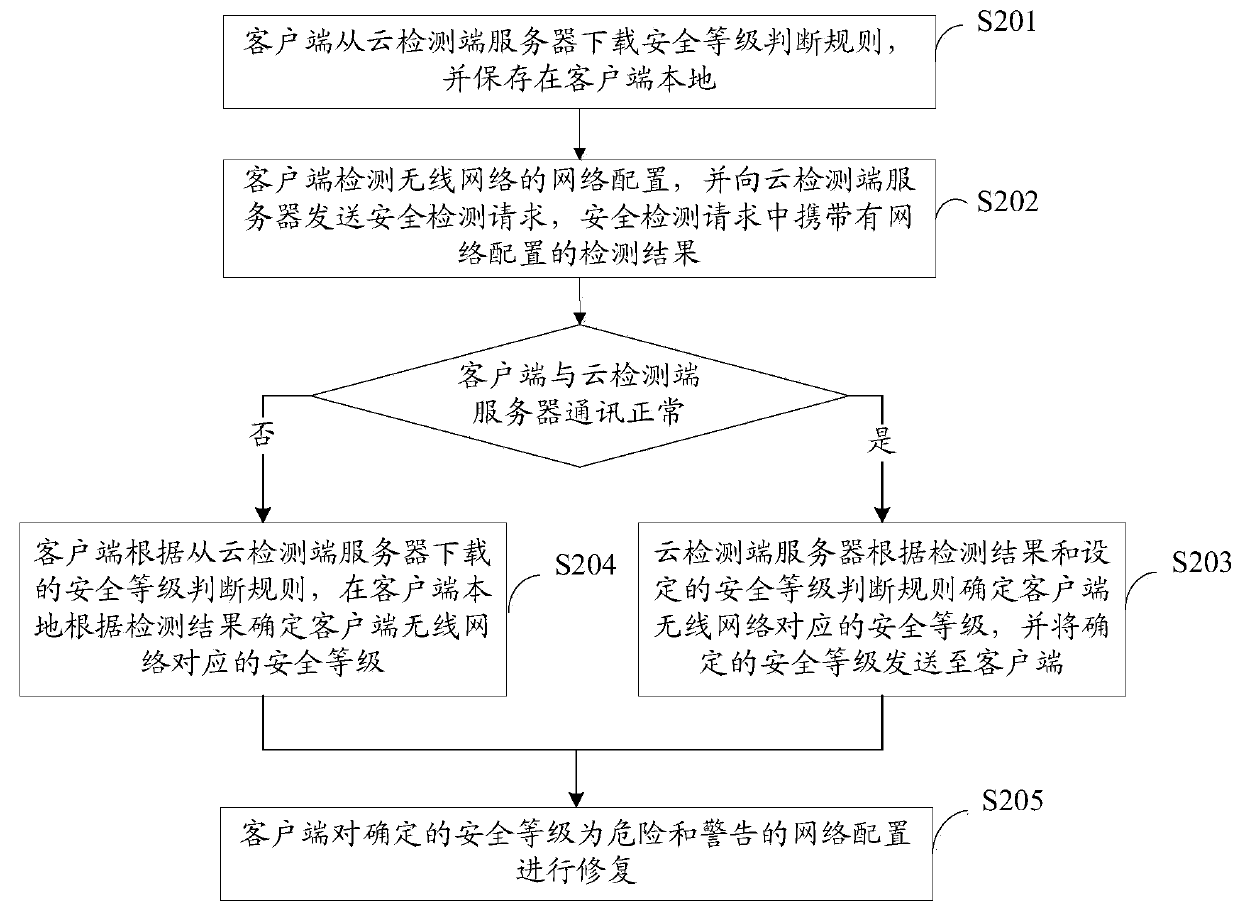
[0053] refer to figure 2 , shows a flow chart of steps of a method for security detection and repair of a wireless network according to an embodiment of the present invention, the method for security detection and repair of a wireless network may specifically include the following steps:
[0054] Step S201, the client downloads the security level judgment rules from the cloud detection server, and saves them locally on the client.
[0055] Step S202, the client detects the network configuration of the wireless network, and sends a security detection request to the cloud detection server. The security detection request carries the detection result of the network configuration. If the communication between the client and the cloud detection server is normal, step S203 is executed. ; If the communication between the client and the cloud detection server is abnormal, execute step S204.
[0056] Wherein, the network configuration includes: the DNS of the WAN interface, the DNS of...
Embodiment 3
[0111] The following assumptions are only for describing the present invention more clearly, and do not constitute undue limitation to the protection scope of the present invention.
[0112] Assumption: the client is a Windows client, the wireless network connection device used is a TP-LINK router, the model is R860, the TP-LINK router uses the DHCP service, and the TP-LINK router uses the default management username and password , that is, the management user name and management password are both admin, the hacker tampered with the DNS of the router’s WAN interface to a malicious DNS (184.105.175.69, 66.102.253.29), and the TP-LINK router adopted WEP encrypted password authentication.
[0113] When a Windows client connects to the above router, the IP address is automatically obtained: 192.168.1.100, and the DNS server is also automatically set to (184.105.175.69, 66.102.253.29).
[0114] To ensure wireless network security, refer to Figure 4 , shows a flow chart of steps o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com