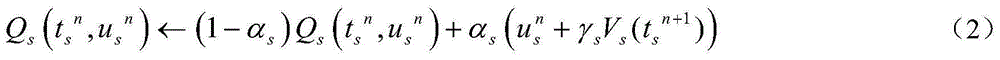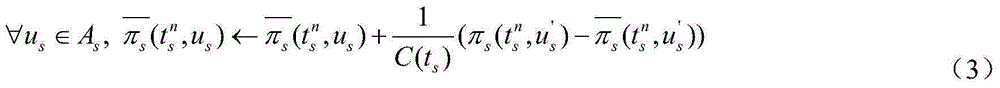Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
173 results about "Wireless network security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
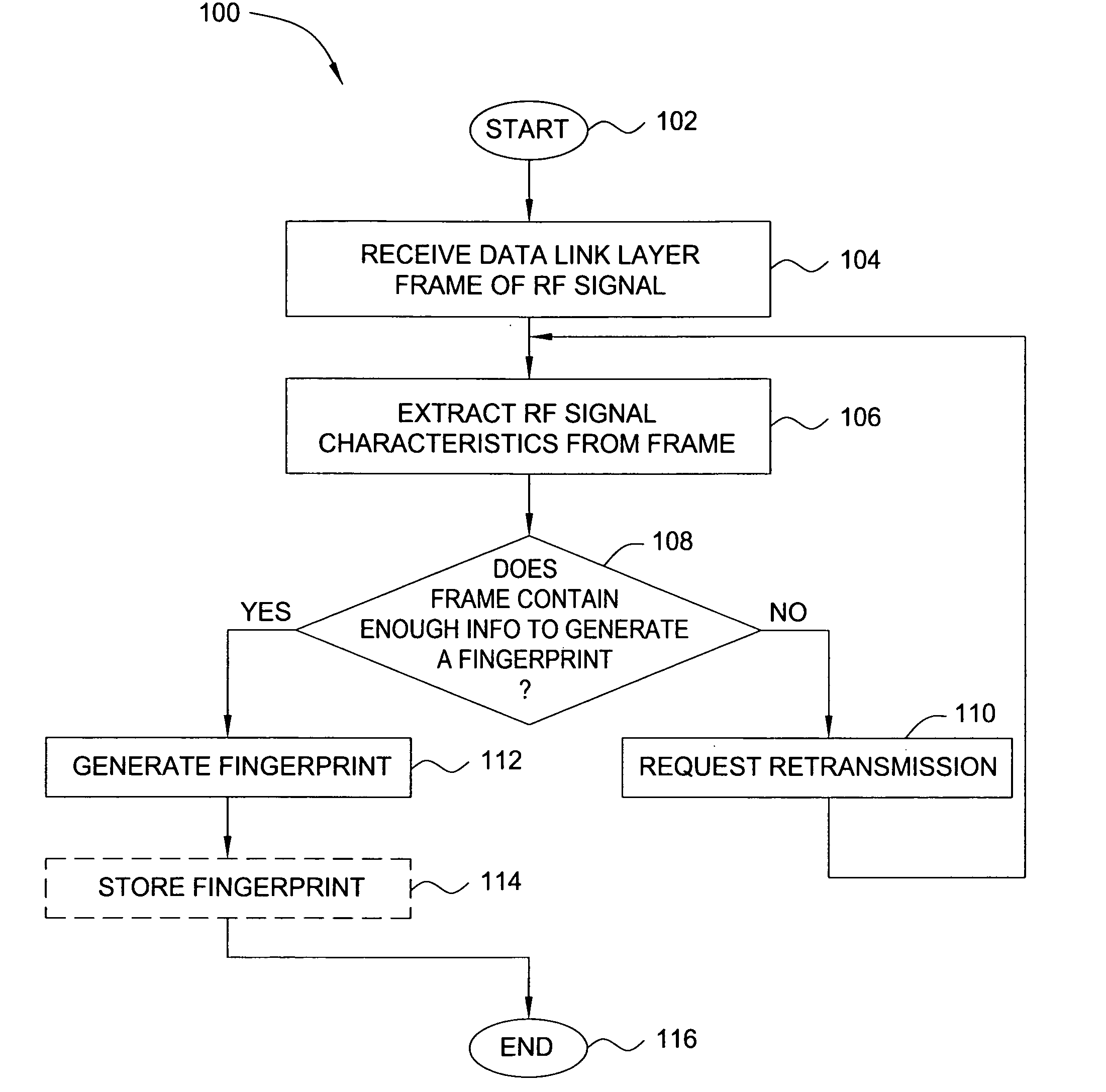
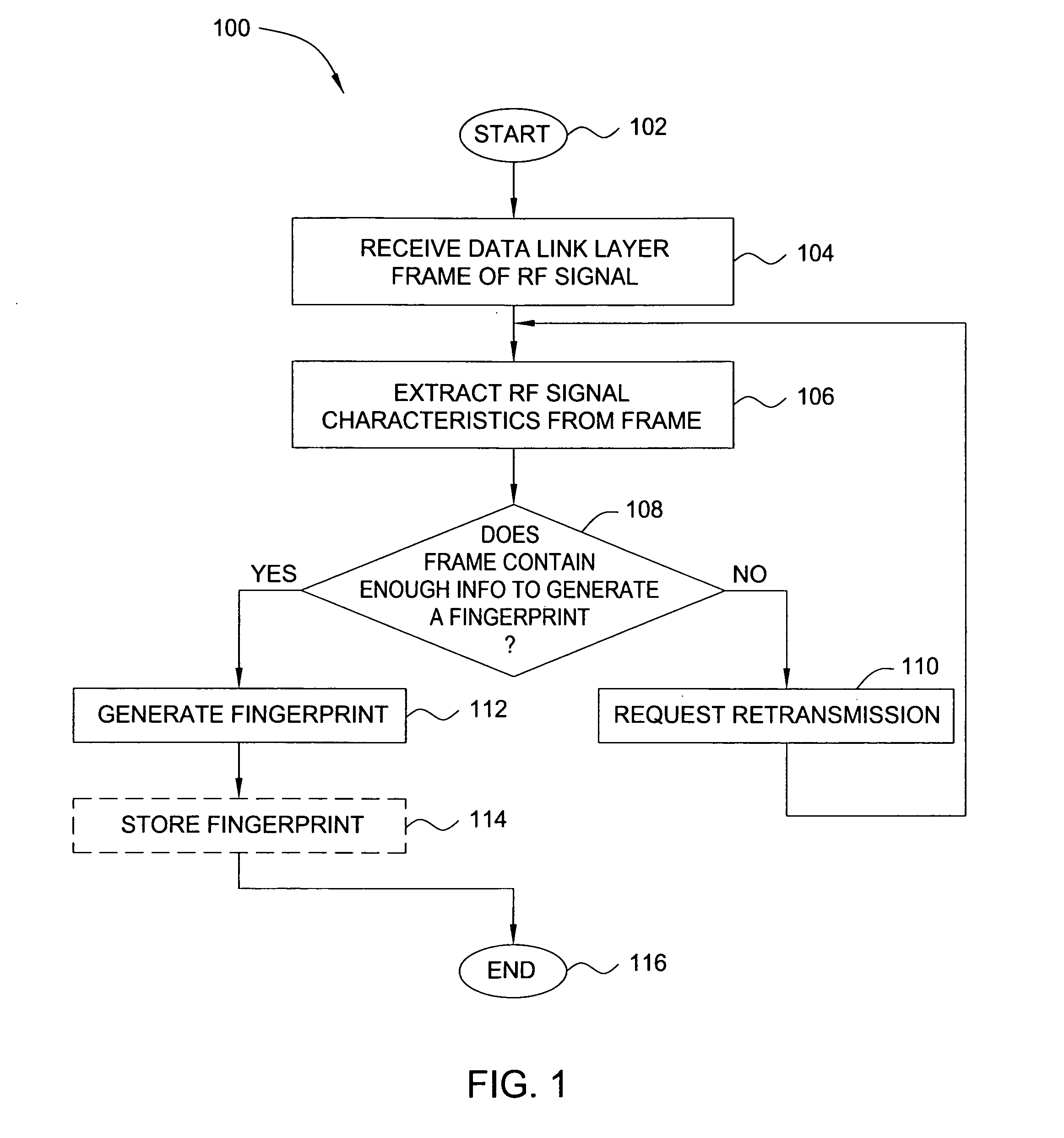
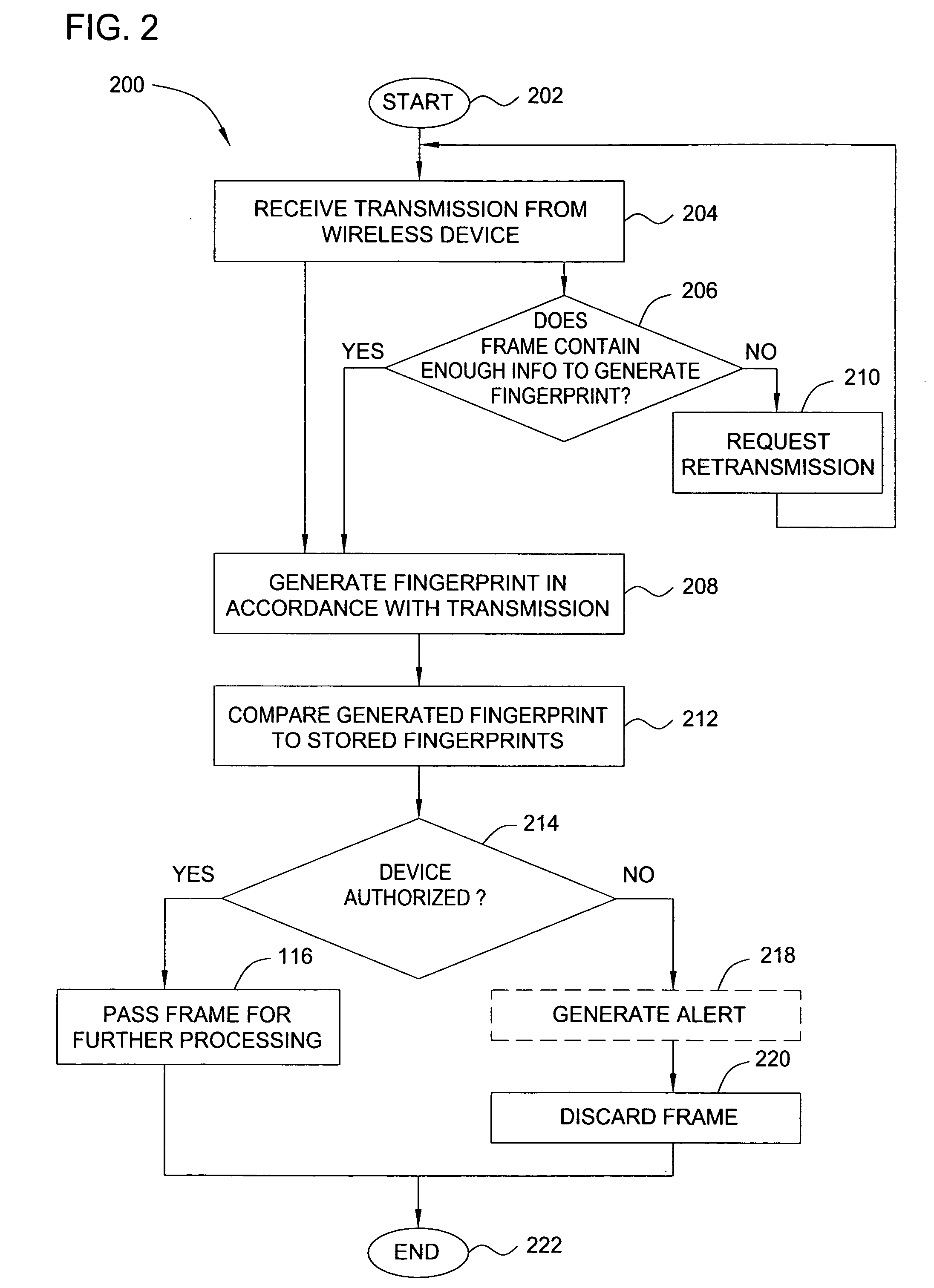
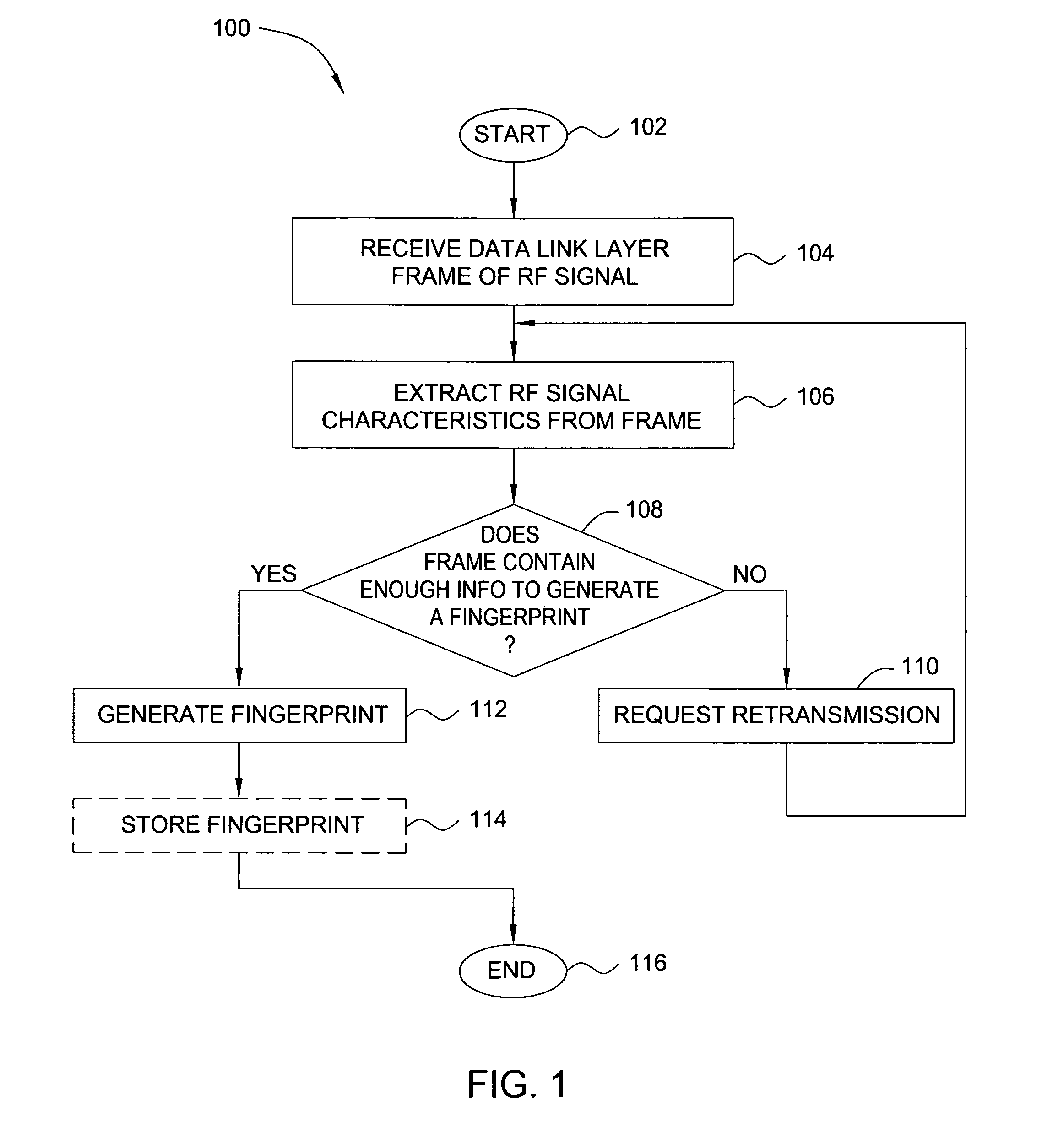
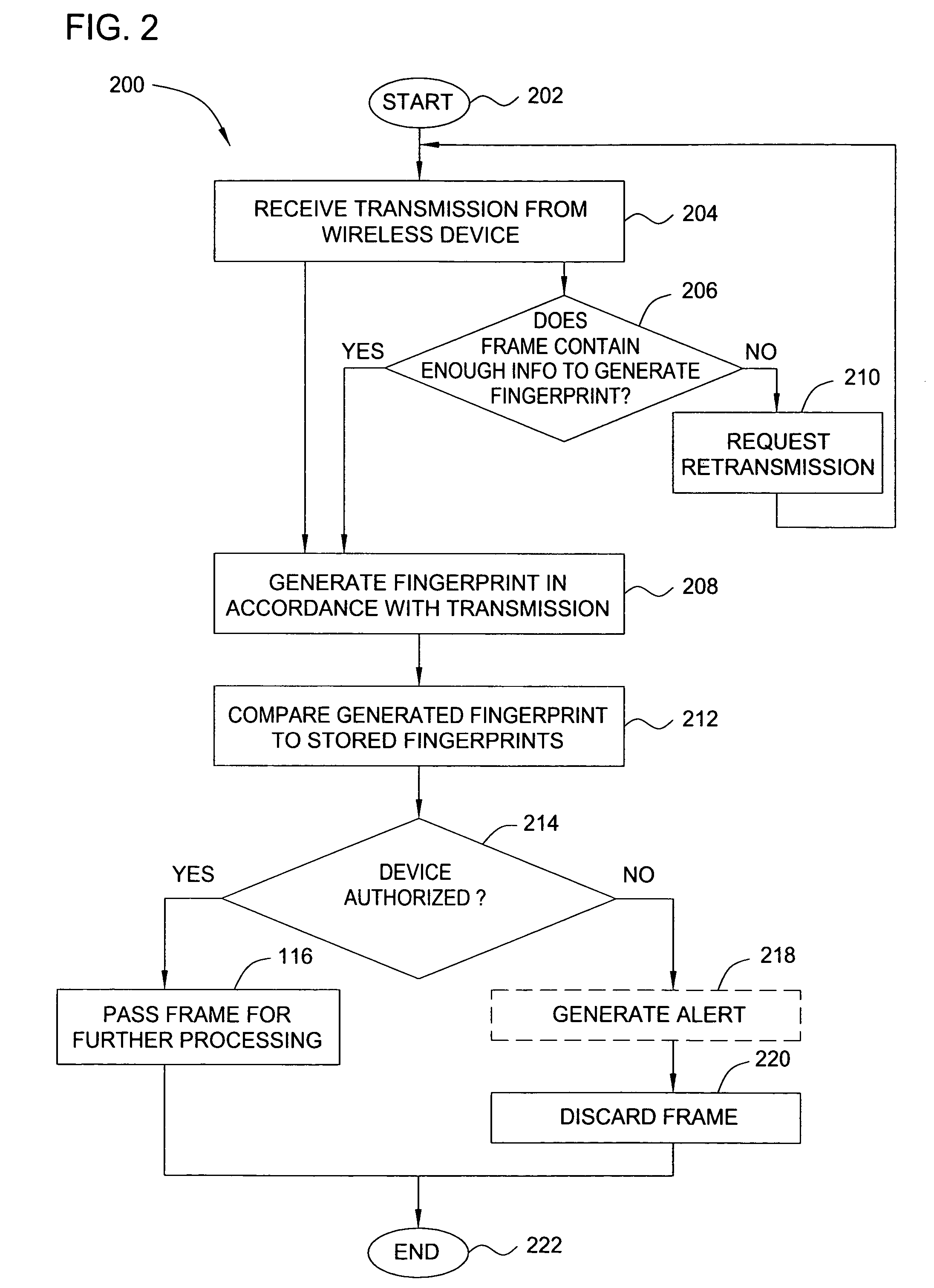
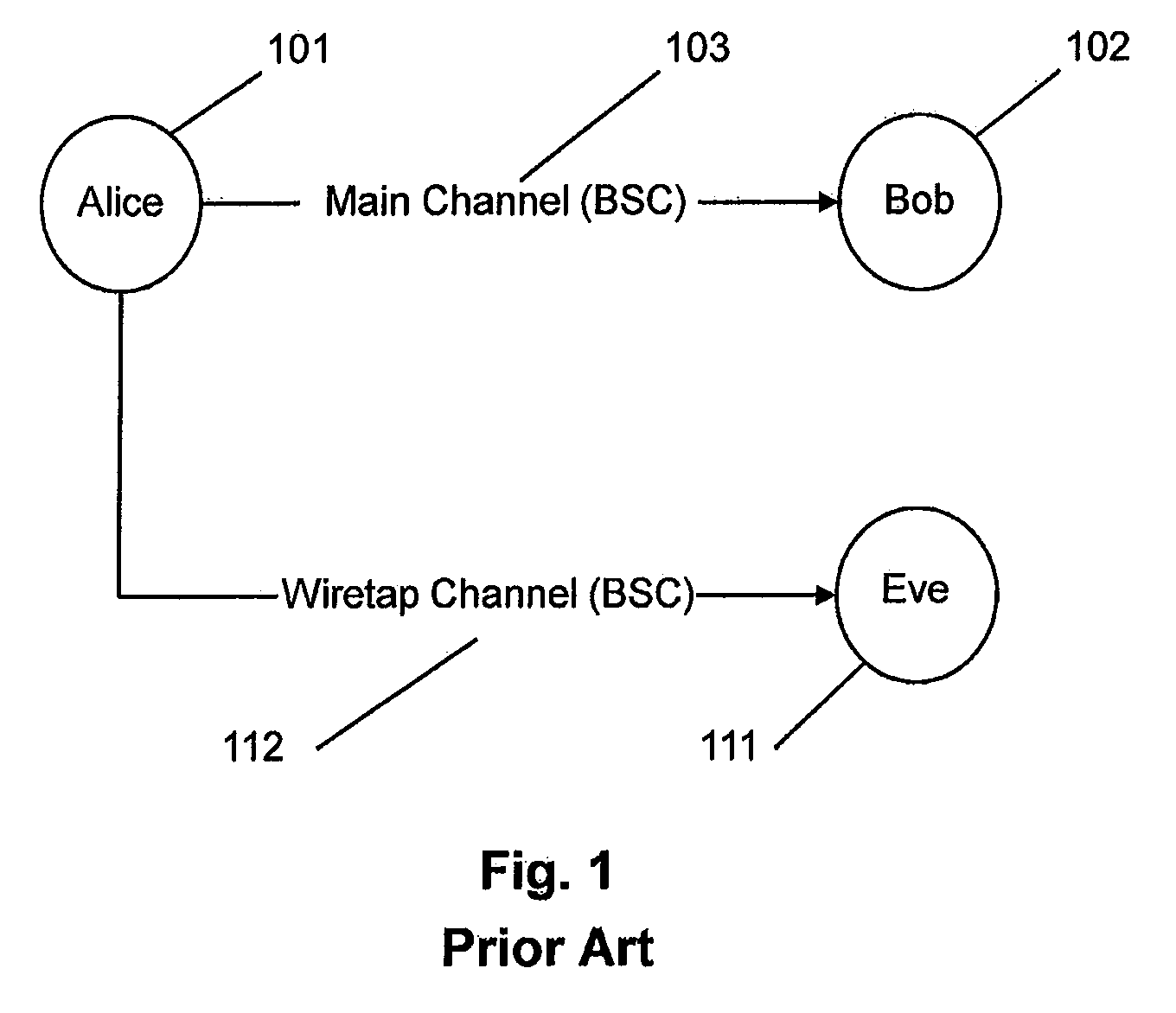
Method and apparatus for wireless network security
ActiveUS20070025265A1Error preventionFrequency-division multiplex detailsRadio frequency signalEngineering
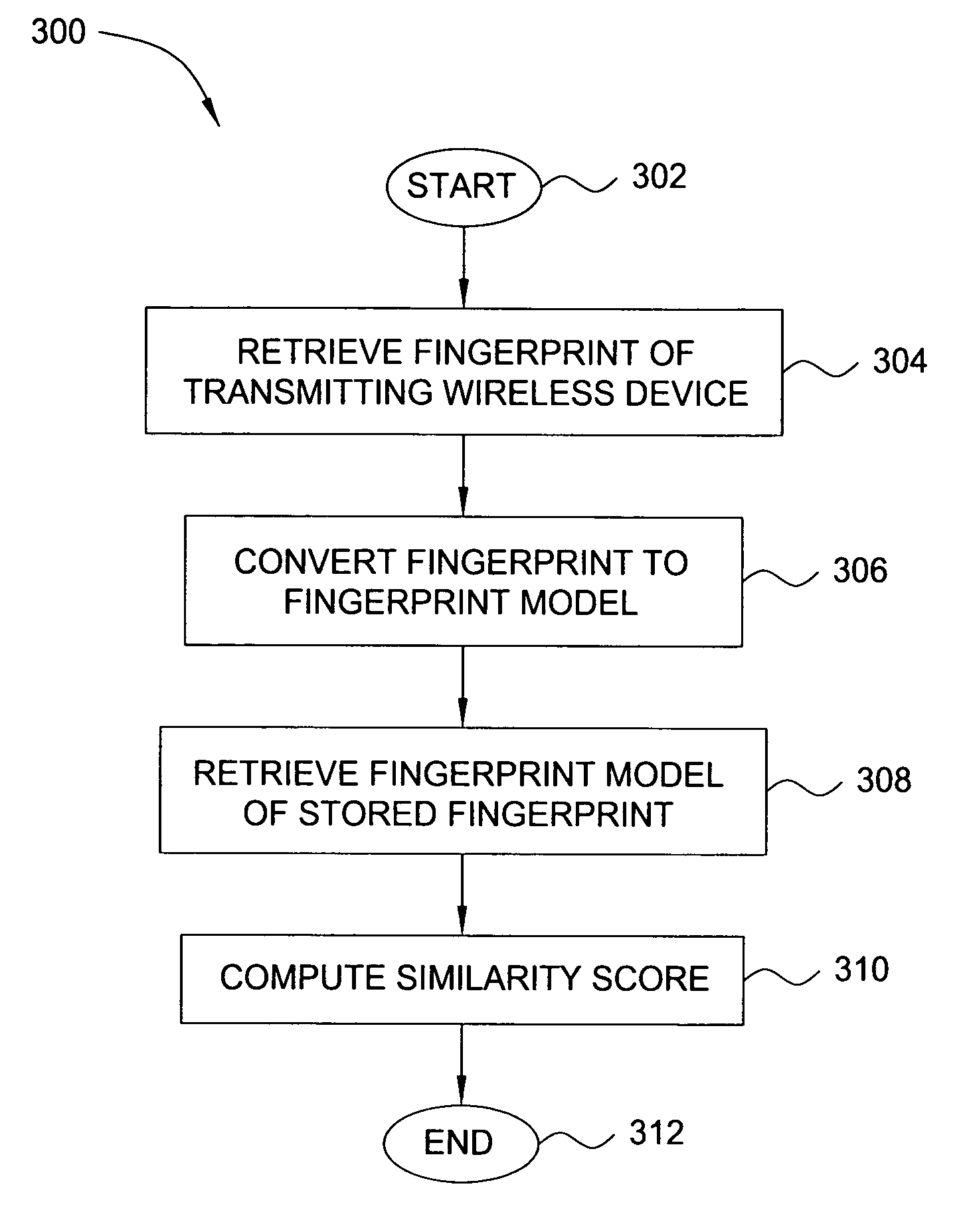
In one embodiment, the present invention is a method and apparatus for wireless network security. In one embodiment, a method for securing a wireless computing network includes receiving a communication from an unidentified transmitter, identifying the transmitter in accordance with a fingerprint generated from one or more radio frequency signal characteristics extracted from the communication, and taking action in response to an identity of the transmitter.
Owner:SRI INTERNATIONAL
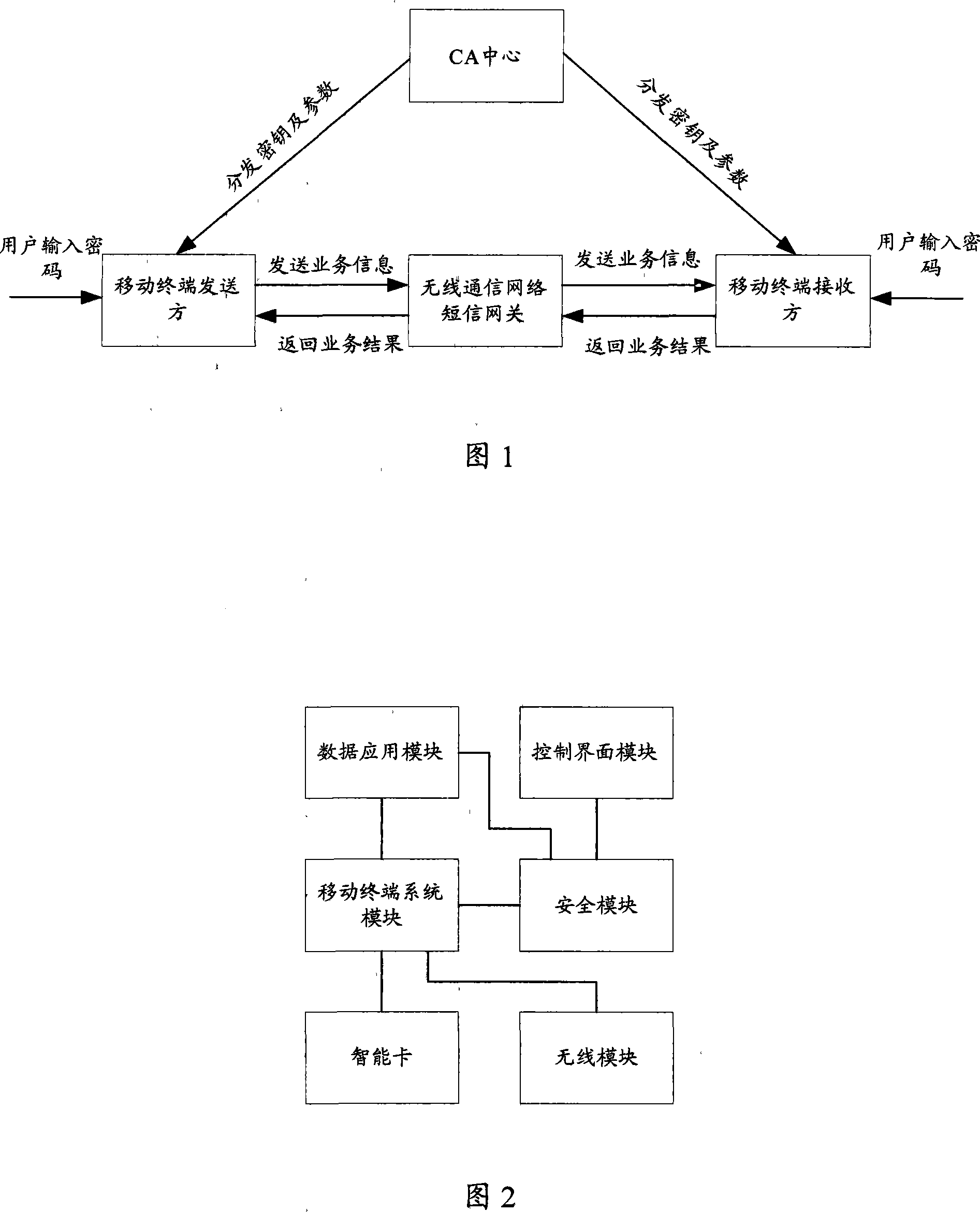
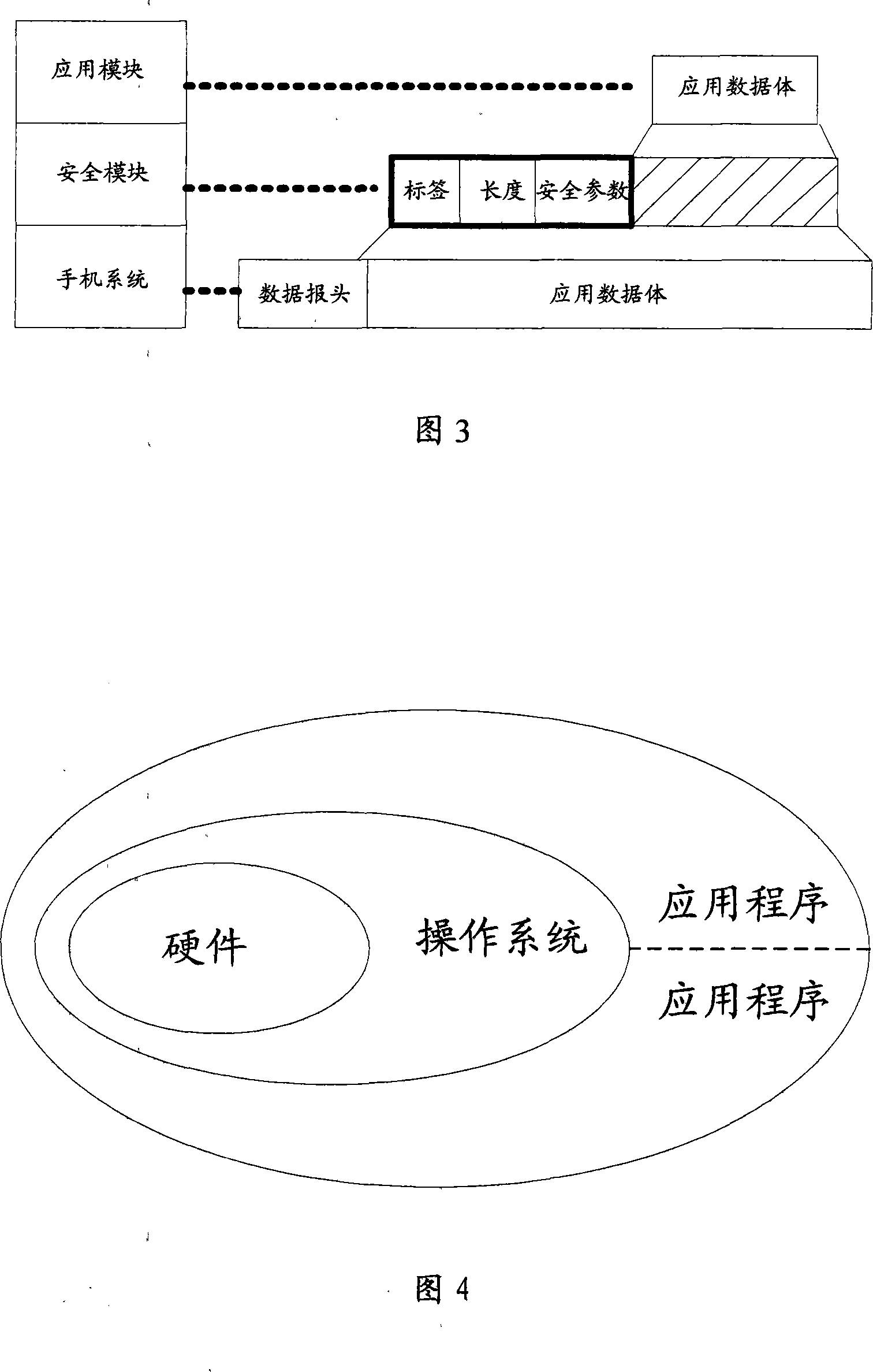
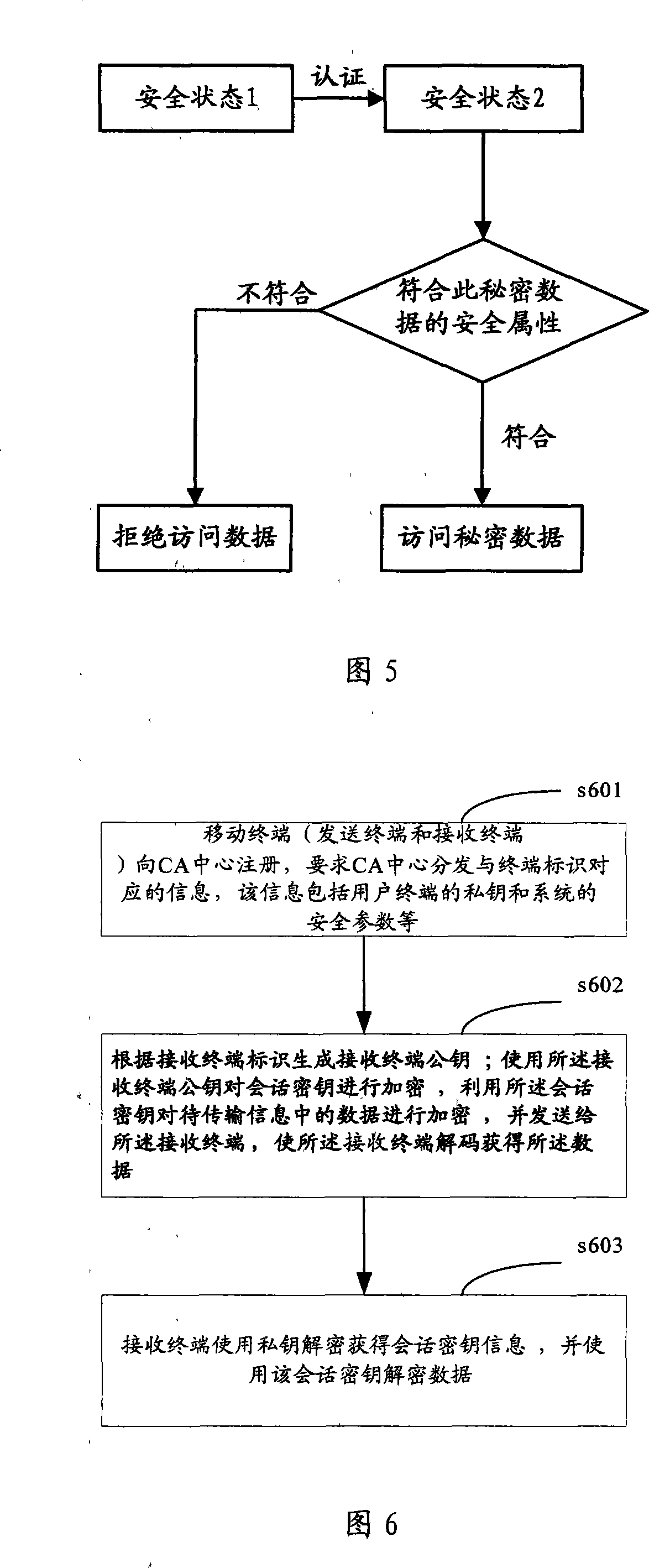
Wireless network security transmission method, system and equipment
ActiveCN101183938APublic key for secure communicationUser identity/authority verificationSecure transmissionData information
The invention discloses a wireless network sending terminal secure transmission method, comprising the following steps: generating a receiving terminal public key according to the receiving terminal identifier; using the receiving terminal public key to encrypt a session key, using the session key to be transmitted The data in the information is encrypted and sent to the receiving terminal, so that the receiving terminal decodes to obtain the data. The invention discloses a wireless network receiving terminal safe transmission method, an authentication center, a receiver device and a sender device. In the embodiment of the present invention, a set of key system is established, so that the mobile terminals participating in this session can obtain the public key information of the other party without information interaction, but directly according to the identification information of each mobile terminal participating in this communication. Get its public key information.
Owner:HUAZHONG UNIV OF SCI & TECH +1
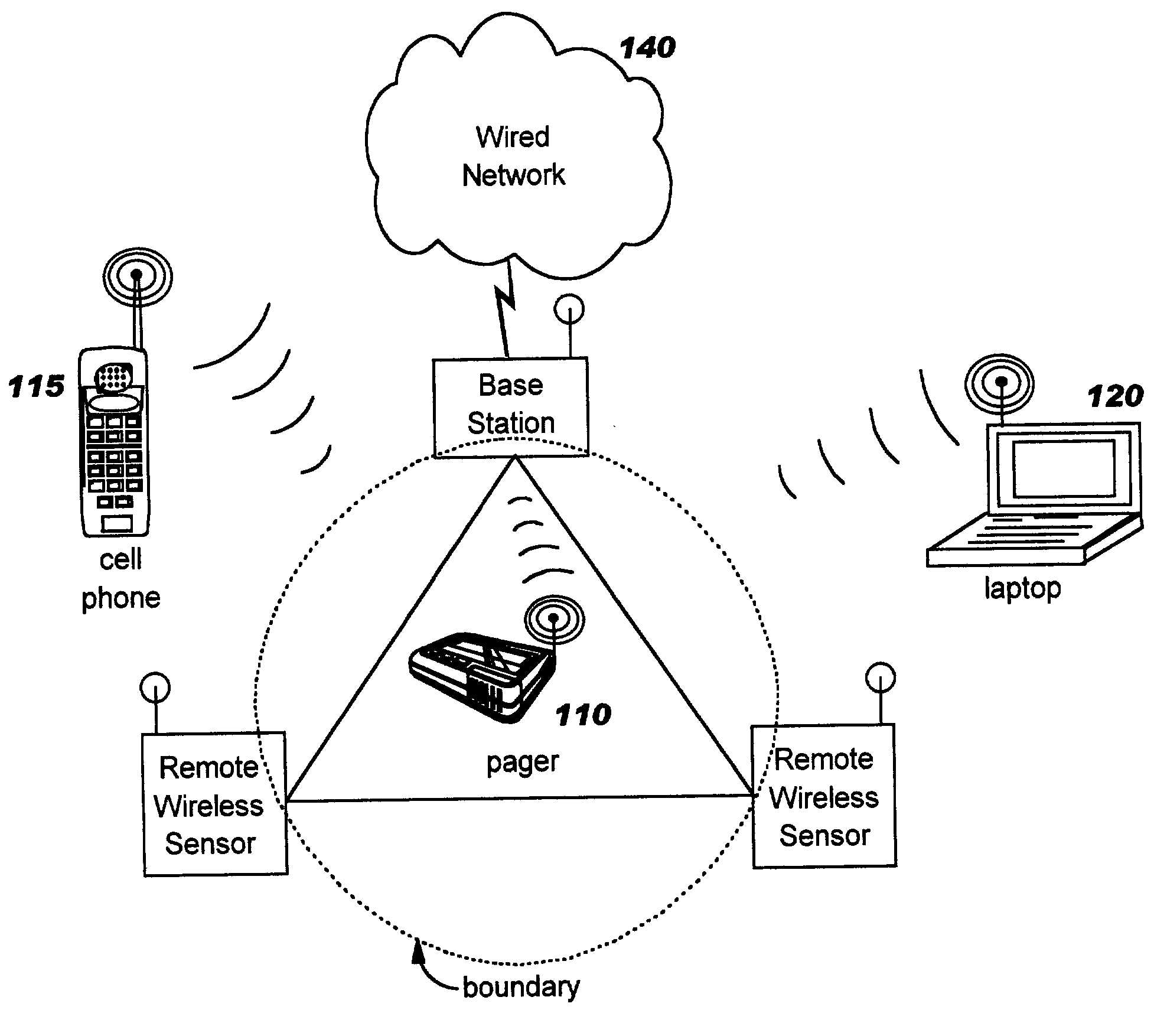
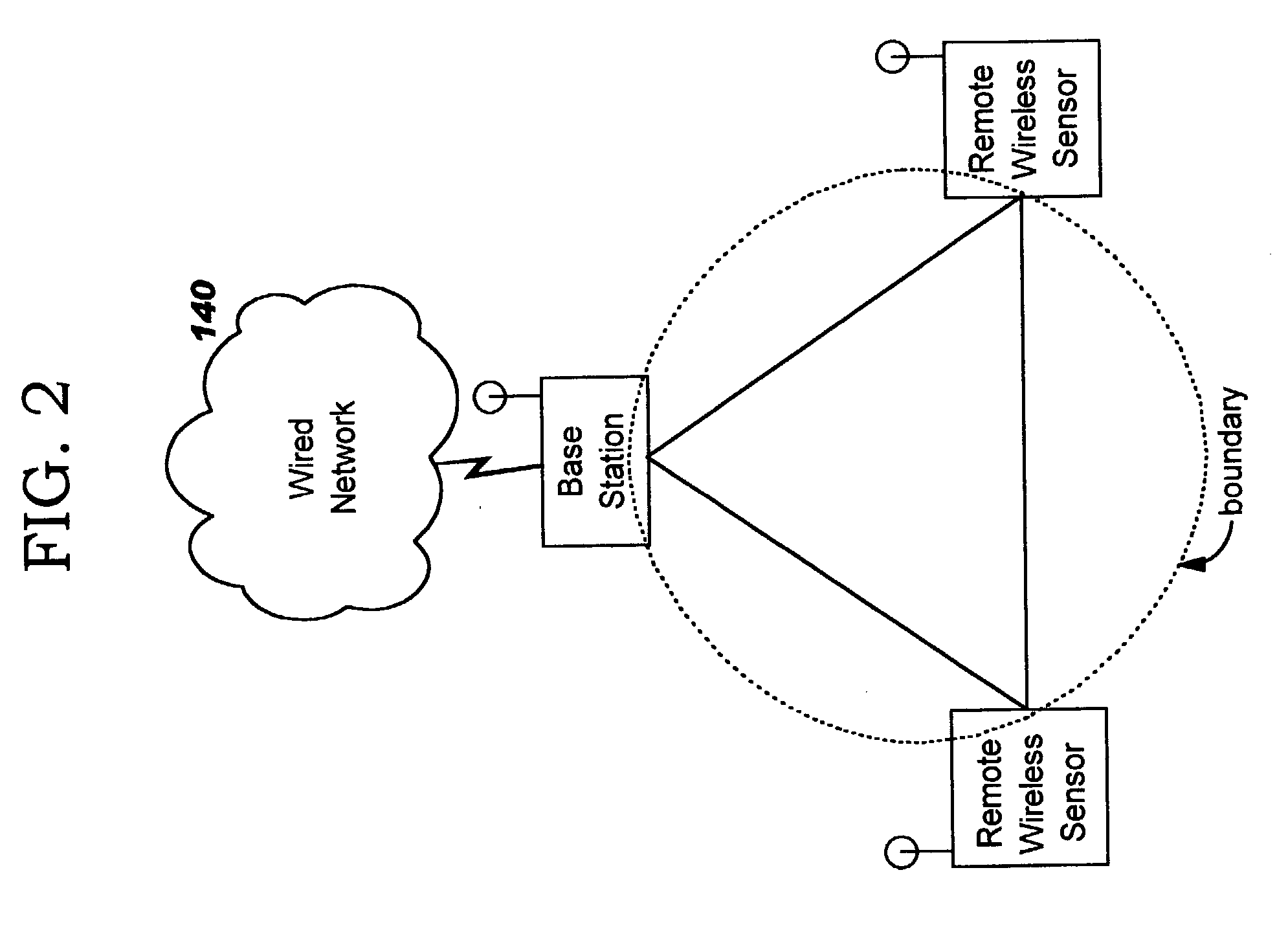
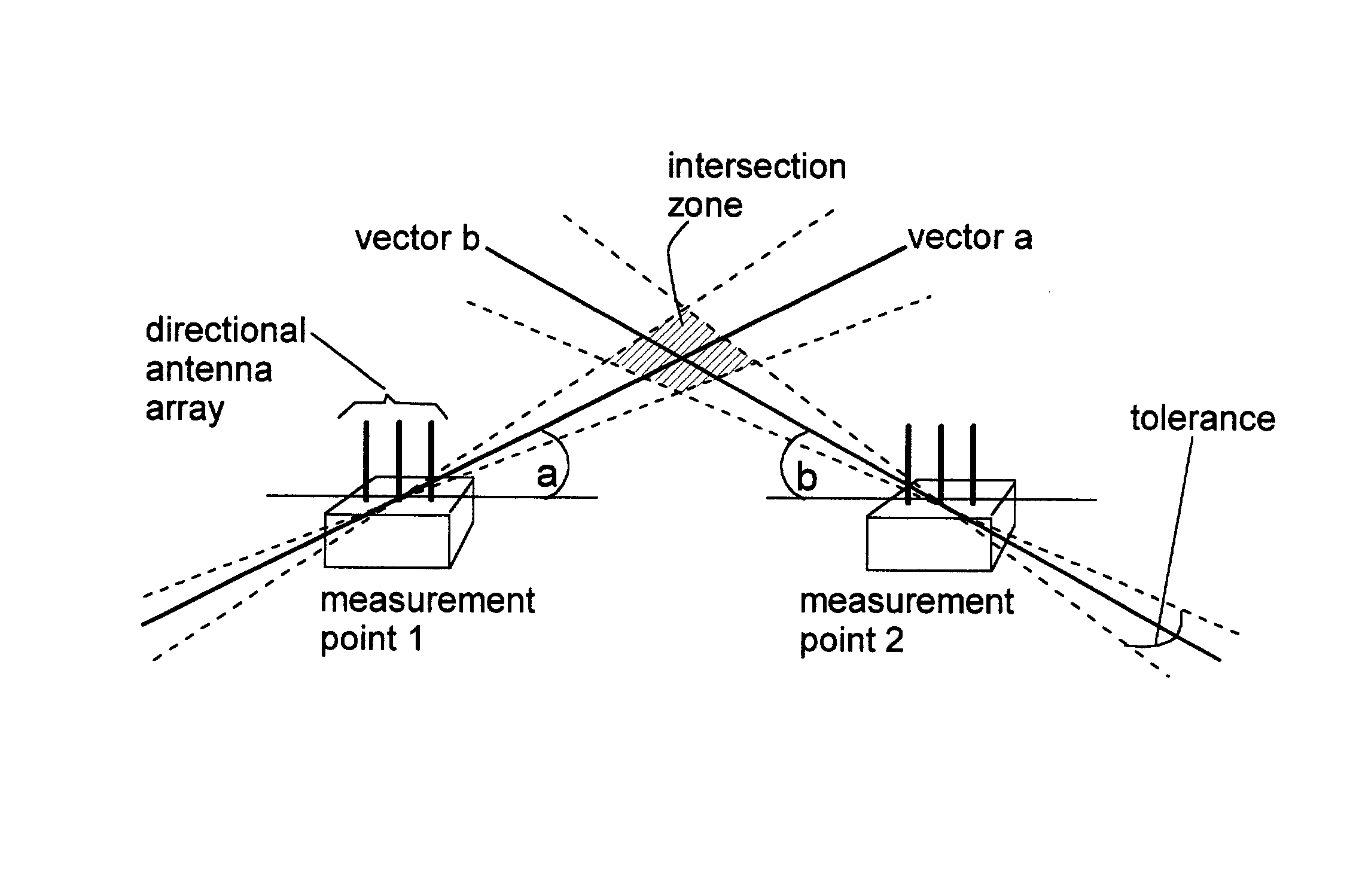
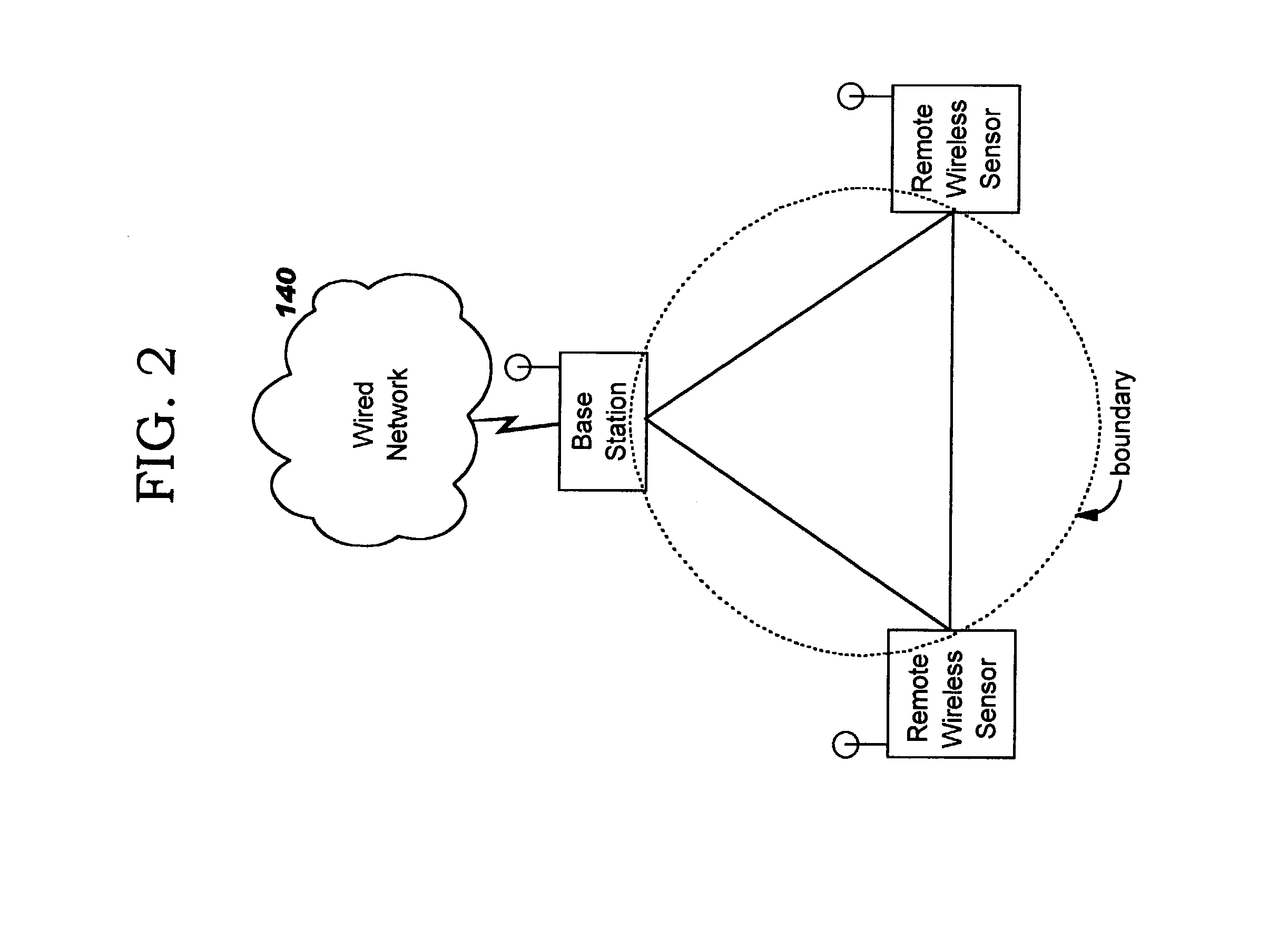
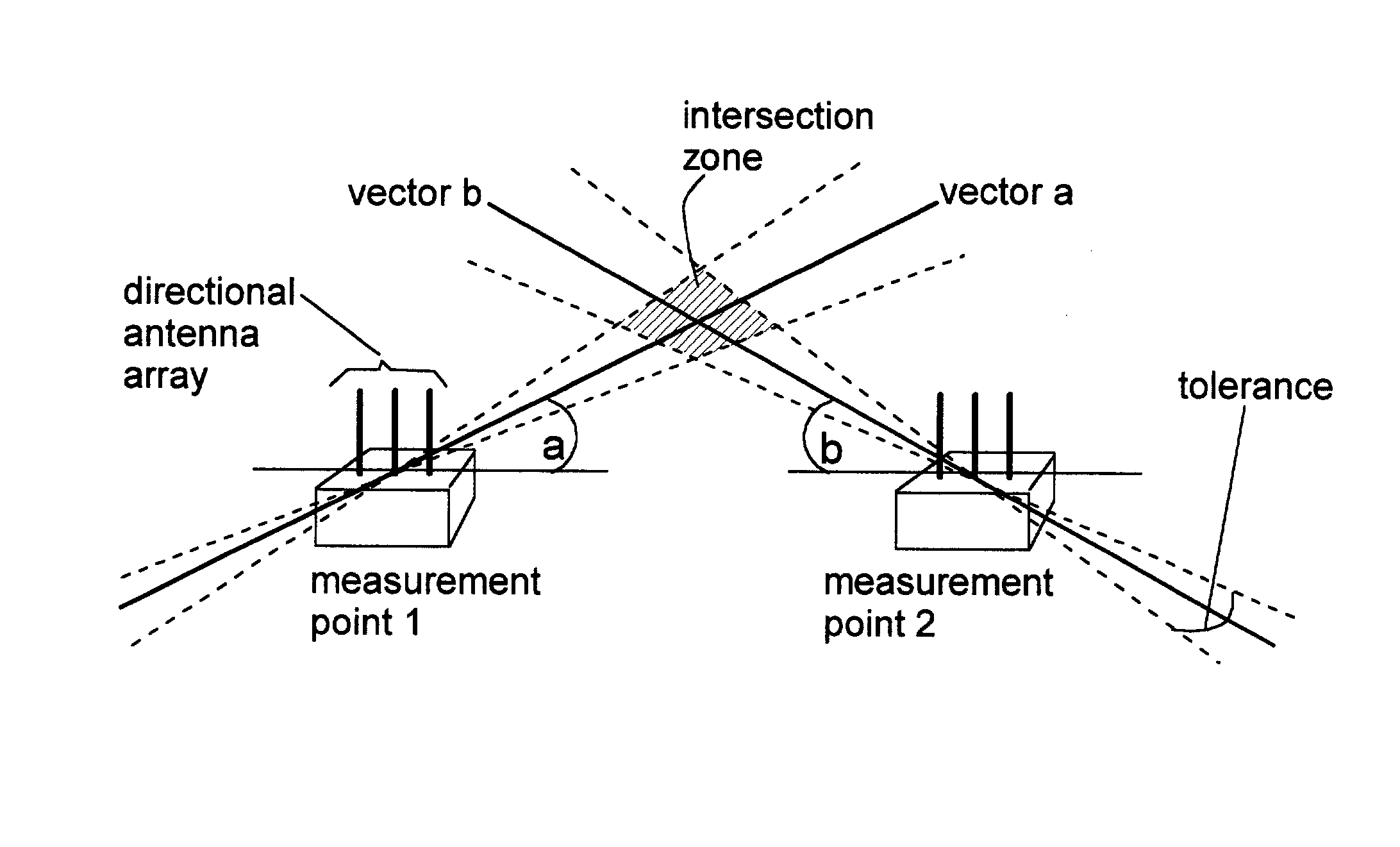
Spatial boundary admission control for wireless networks
InactiveUS20040203910A1Easy to set upDirection finders using radio wavesAssess restrictionTelecommunicationsMeasurement point
Security of wireless networks is improved by rejecting traffic from a wireless device located outside a defined spatial boundary. The device's spatial position with respect to the boundary is determined using directional antenna arrays on a plurality of measurement points, and calculating where the vectors intersect. Having thus determined a device's location, access to a wireless network can be denied if the device is outside a predetermined spatial boundary. Or, the device's location inside or outside of the spatial boundary can be used for other purposes, such as theft detection.
Owner:IBM CORP
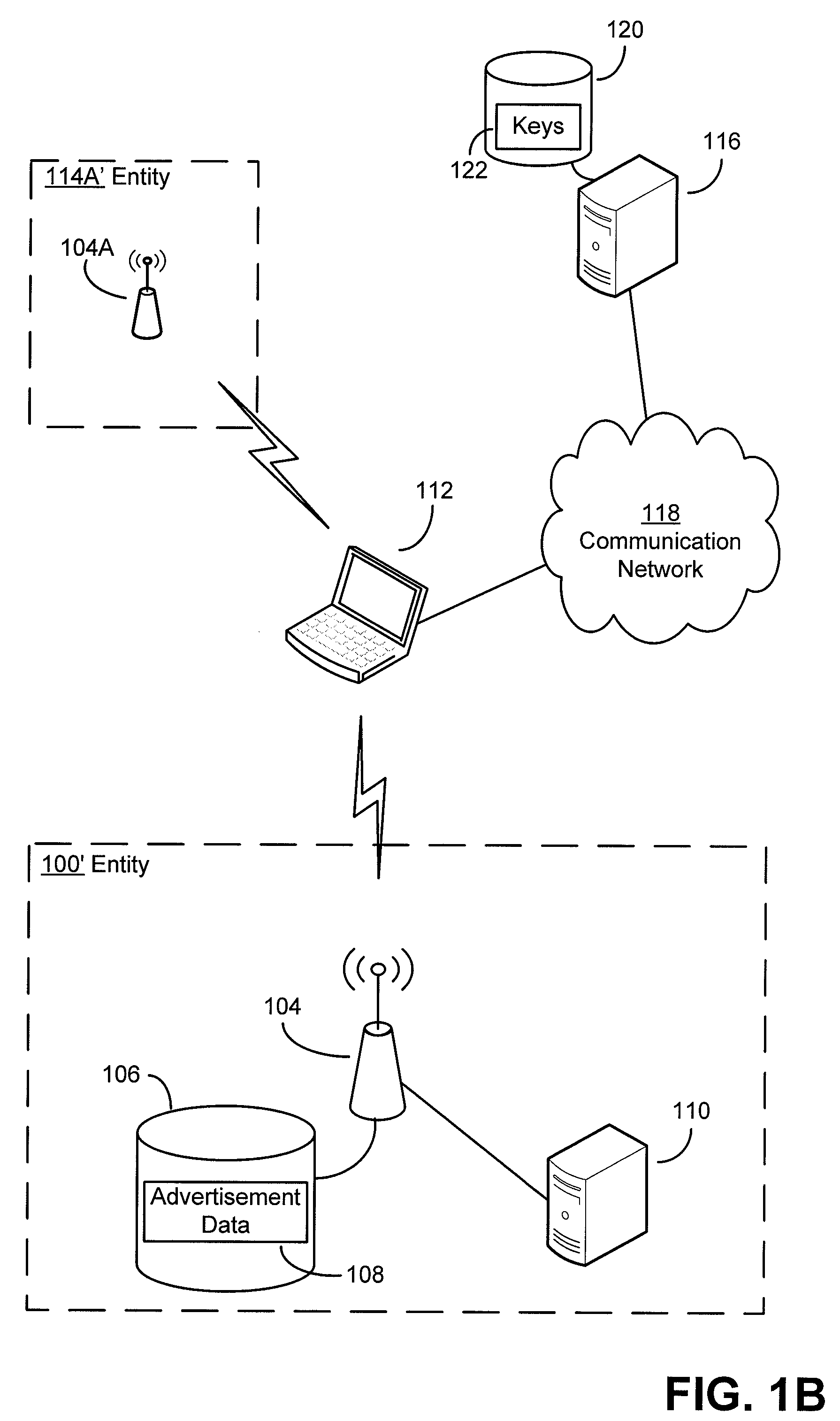
Authentication mechanisms for wireless networks
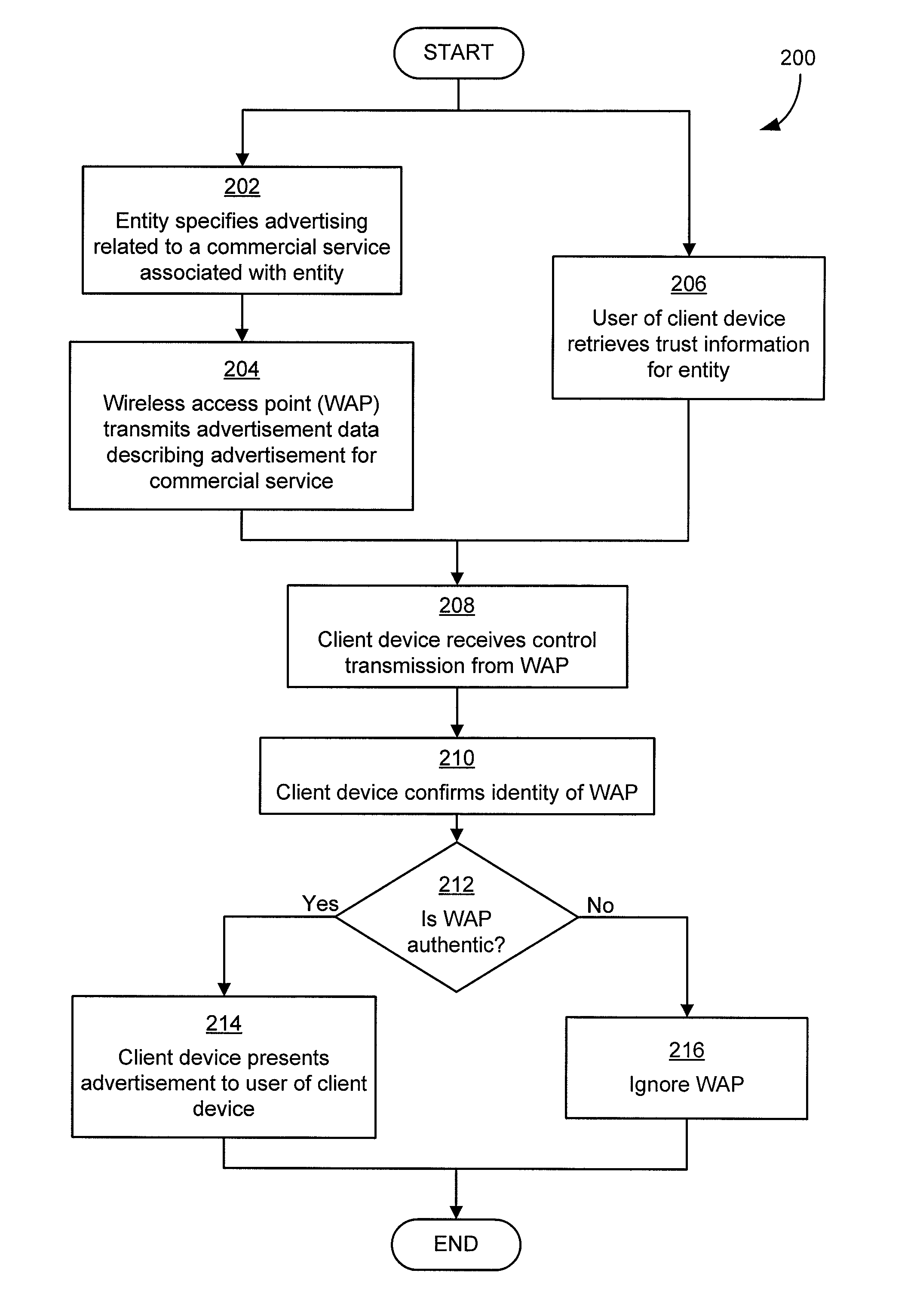
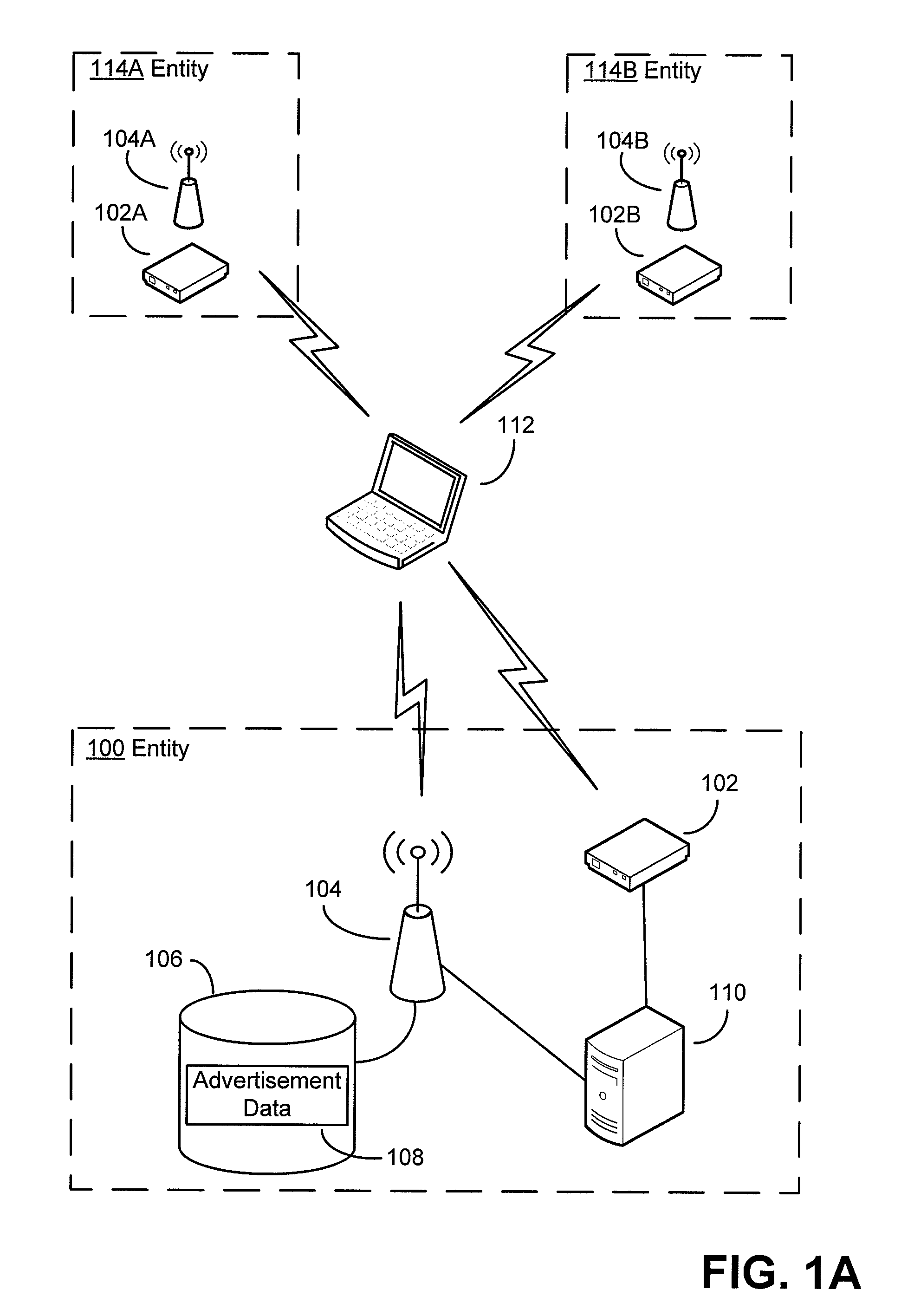
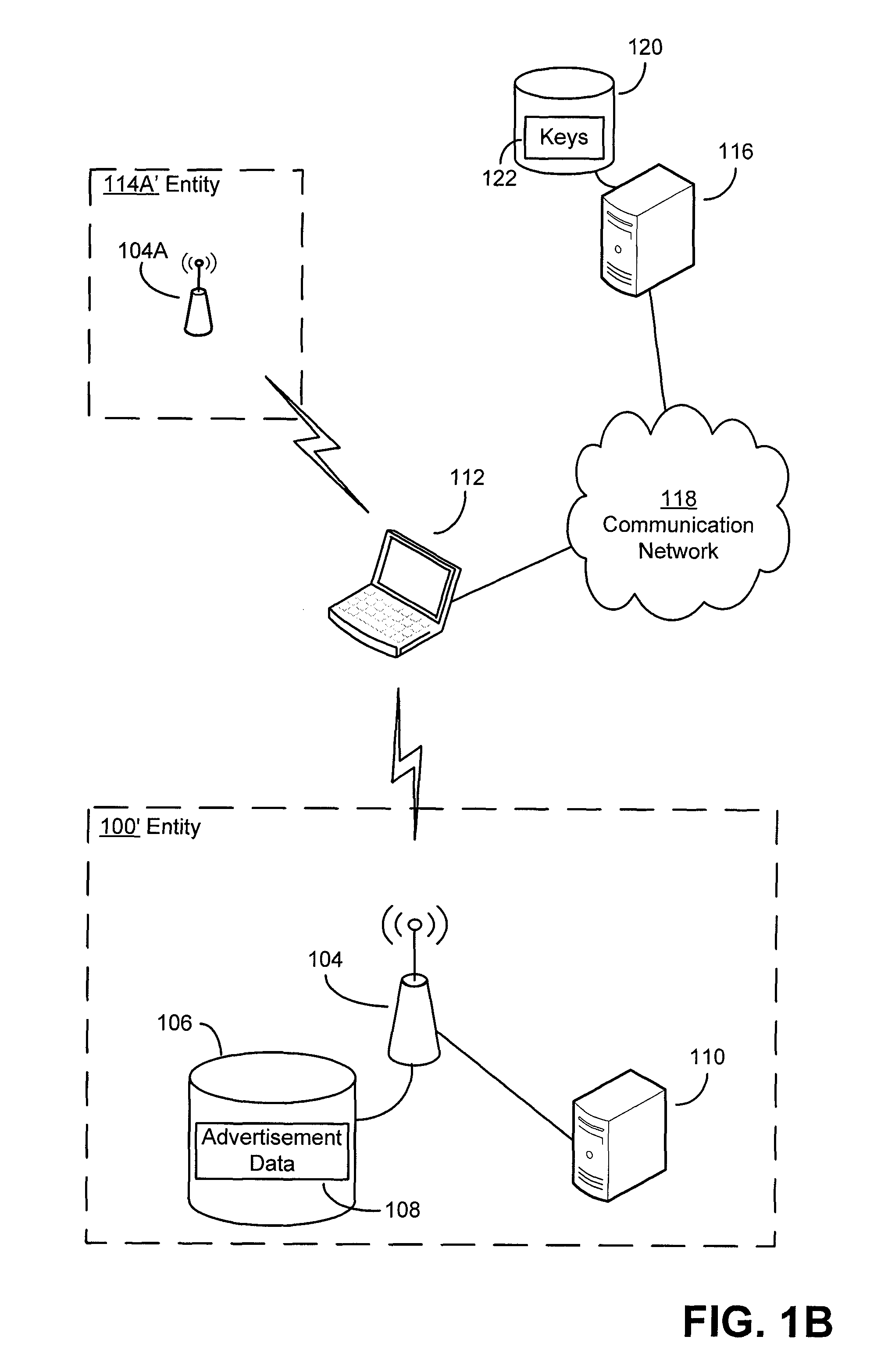
Security techniques and security mechanisms for wireless networks that transmit content such as advertisements. According to exemplary techniques, control messages comprising unrequested content (e.g., advertisement data) may be transmitted in response to a request from a client device, while in other exemplary techniques the control messages may be transmitted without any request from a client device. In some exemplary implementations, security mechanisms such as public key cryptography algorithms may be used to secure transmissions. In some of these techniques which implement public key cryptography, a user may be required to retrieve a public key from a source other than the wireless access point transmitting encrypted advertisements (e.g., a sign or terminal in a commercial entity transmitting such advertisements, or from a web service), such that the user may confirm that the encrypted content is from a source matching the retrieved public key and thus confirm the authenticity of a wireless access point.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for wireless network security
ActiveUS7724717B2Error preventionFrequency-division multiplex detailsRadio frequency signalWireless computing
In one embodiment, the present invention is a method and apparatus for wireless network security. In one embodiment, a method for securing a wireless computing network includes receiving a communication from an unidentified transmitter, identifying the transmitter in accordance with a fingerprint generated from one or more radio frequency signal characteristics extracted from the communication, and taking action in response to an identity of the transmitter.
Owner:SRI INTERNATIONAL
System and method for wireless network security
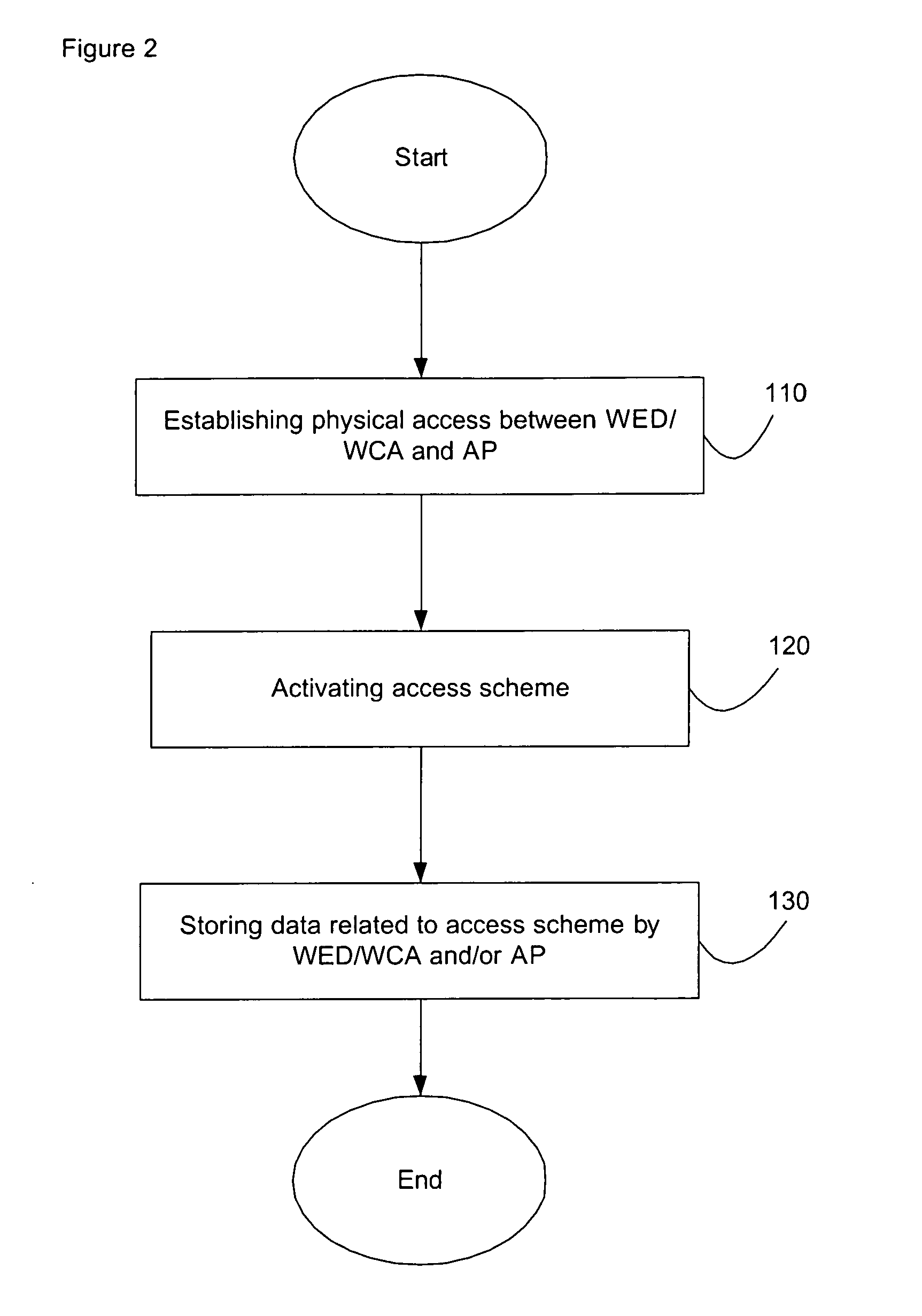
InactiveUS20050245235A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPhysical accessWireless access point
Described are a system and method for a wireless network security. The system may include a wireless electronic device and a wireless access point. The access point includes a memory and is capable of wirelessly communicating with the device. The memory stores an access scheme which defines an authentication procedure for allowing the wireless communications between the electronic device and the further asset. The authentication procedure utilizes data as defined by the access scheme. The access point is situated in a location accessible to an authorized user and provides access for the electronic device to a further asset. The access point allows the wireless communications between the electronic device and the further asset only when the authentication procedure is successful. Before the authentication procedure, the data is transferred between the device and the access point via a physical access to at least one of the access point and the electronic device.
Owner:SYMBOL TECH INC
Authentication mechanisms for wireless networks
ActiveUS20090214036A1More revenueLimited abilityAdvertisementsPublic key for secure communicationWireless mesh networkWeb service
Security techniques and security mechanisms for wireless networks that transmit content such as advertisements. According to exemplary techniques, control messages comprising unrequested content (e.g., advertisement data) may be transmitted in response to a request from a client device, while in other exemplary techniques the control messages may be transmitted without any request from a client device. In some exemplary implementations, security mechanisms such as public key cryptography algorithms may be used to secure transmissions. In some of these techniques which implement public key cryptography, a user may be required to retrieve a public key from a source other than the wireless access point transmitting encrypted advertisements (e.g., a sign or terminal in a commercial entity transmitting such advertisements, or from a web service), such that the user may confirm that the encrypted content is from a source matching the retrieved public key and thus confirm the authenticity of a wireless access point.
Owner:MICROSOFT TECH LICENSING LLC
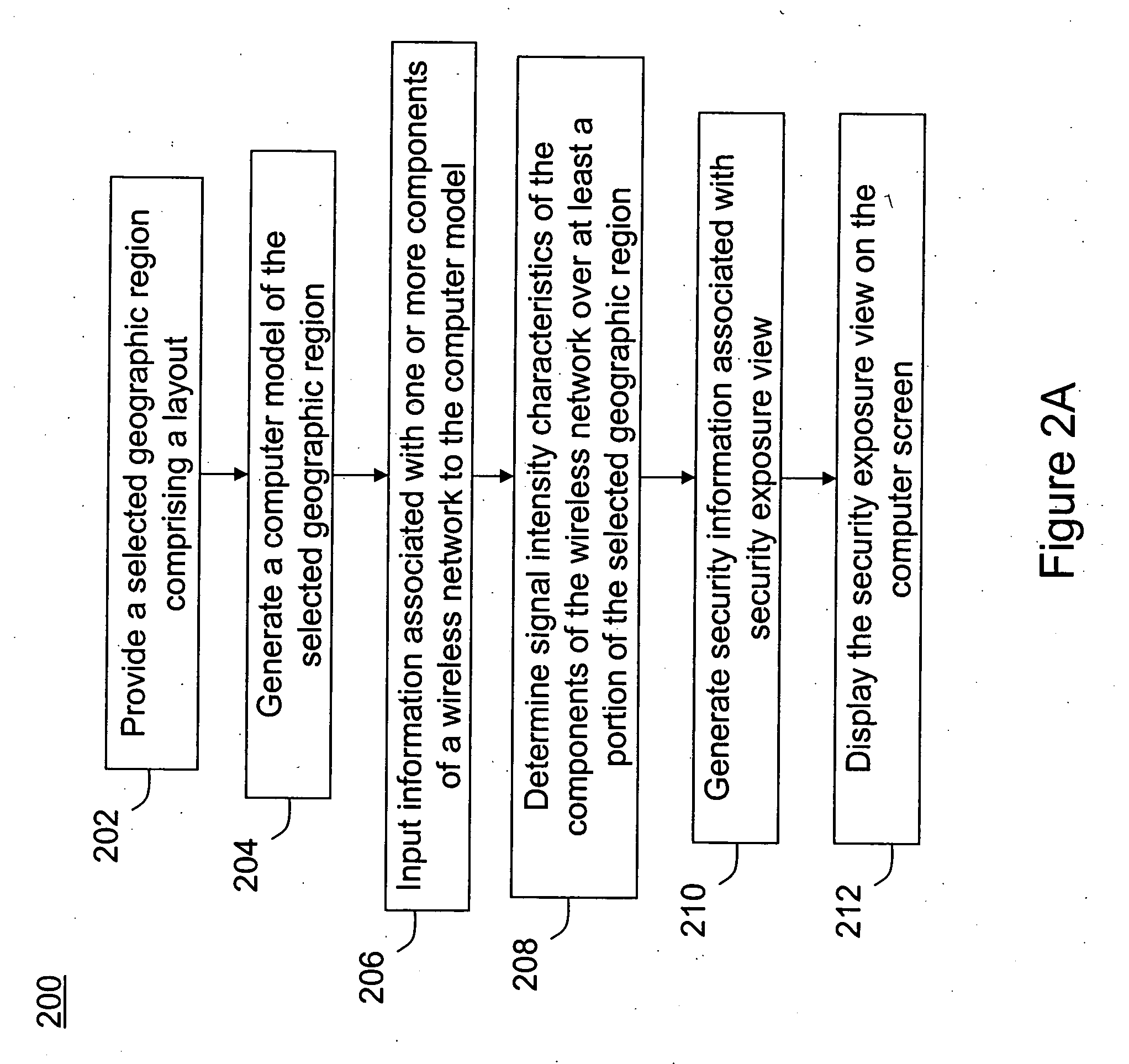
Method for wireless network security exposure visualization and scenario analysis
InactiveUS20060070113A1Facilitates security exposure analysisEasy to readUnauthorised/fraudulent call preventionDigital data processing detailsGraphicsVulnerability
According to an embodiment of the present invention, security exposure analysis of wireless network within a selected local geographic area is provided. A computer model of the selected local geographic region comprising a layout is generated. Information regarding wireless network components is provided to the computer model. Using the computer model, signal intensity characteristics of at least one of the wireless network components are determined over at least a portion of the selected geographic region. Based at least on the signal intensity characteristics, security exposure information associated with the wireless network is determined. The security exposure information is graphically displayed on the computer screen in relation to the layout of the selected geographic region. The security exposure information includes sniffer detection and prevention coverage, access point vulnerability regions, and signal uncertainty and variability views.
Owner:AIRTIGHT NETWORKS
Method and device for detecting access right of wireless network and router
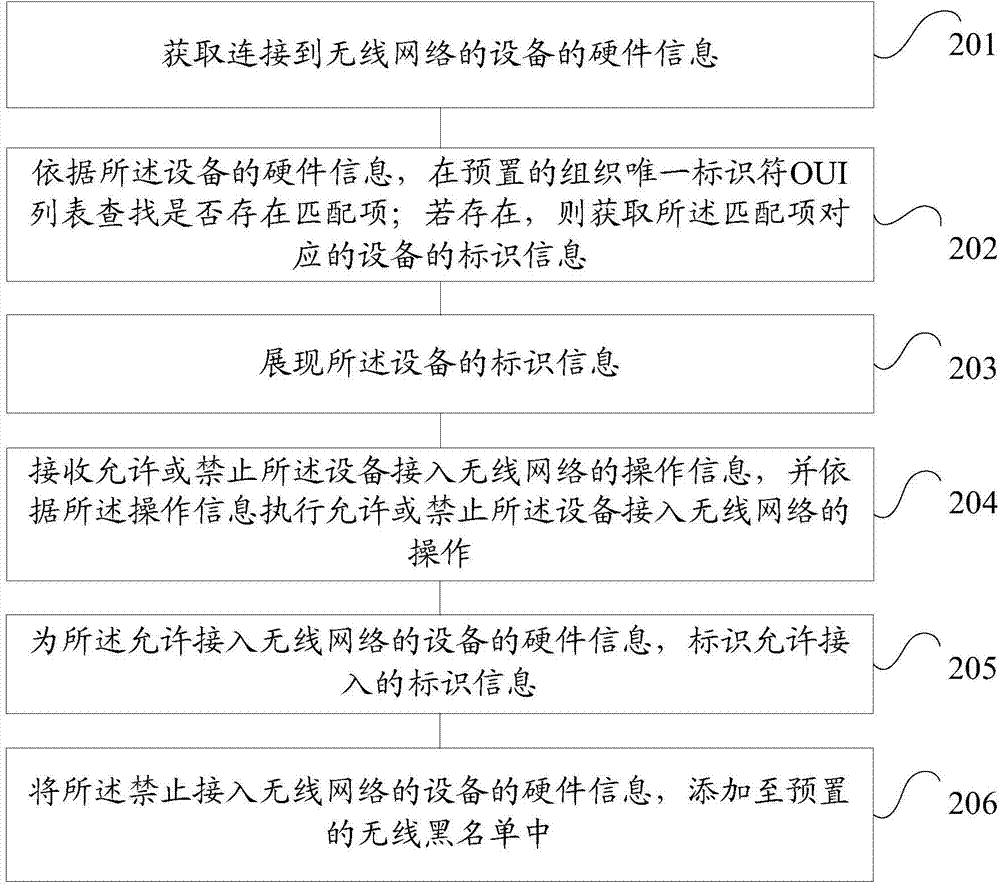
InactiveCN103619018AImprove securityPrevent leakageSecurity arrangementSpecial data processing applicationsWireless mesh networkWireless network coding
The invention discloses a method and device for detecting the access right of a wireless network and a router. The method for detecting the access right of the wireless network comprises the steps that hardware information of a device having access to the wireless network is obtained; whether a matching item exists in a preset OUI list is judged through searching according to the hardware information of the device; the identification information, corresponding to the matching item, of the device is obtained if the matching item exists in the preset OUI list; the identification information of the device is presented; operation information allowing the device to have access to the wireless network or preventing the device from having access to the wireless network is received, and the device is allowed to have access to the wireless network or is prevented from having access to the network according to the operation information. The method and device for detecting the access right of the wireless network and the router are used for preventing data from being leaked, protecting personal information of users and improving the safety performance of the wireless network.
Owner:BEIJING QIHOO TECH CO LTD +1
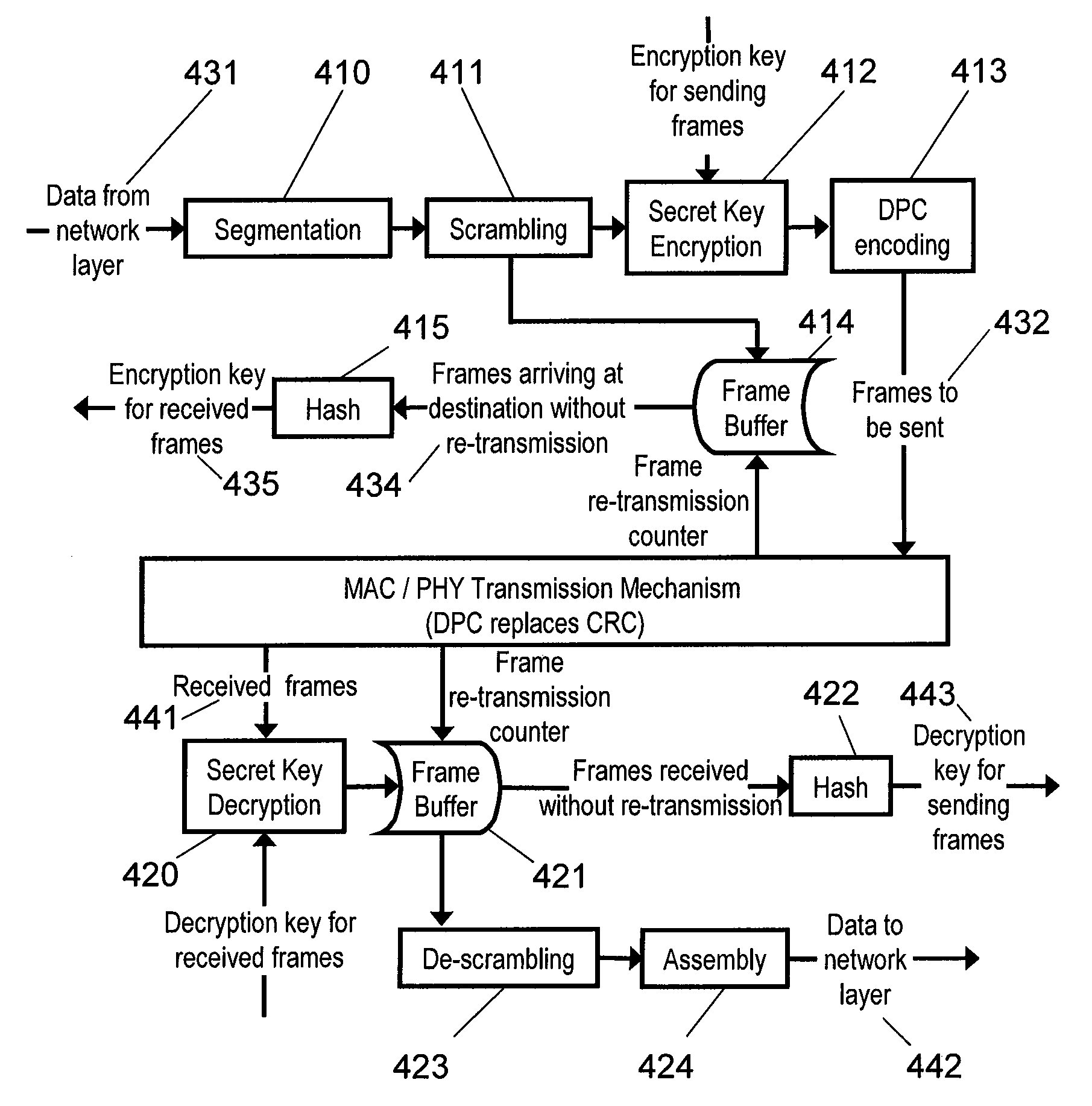
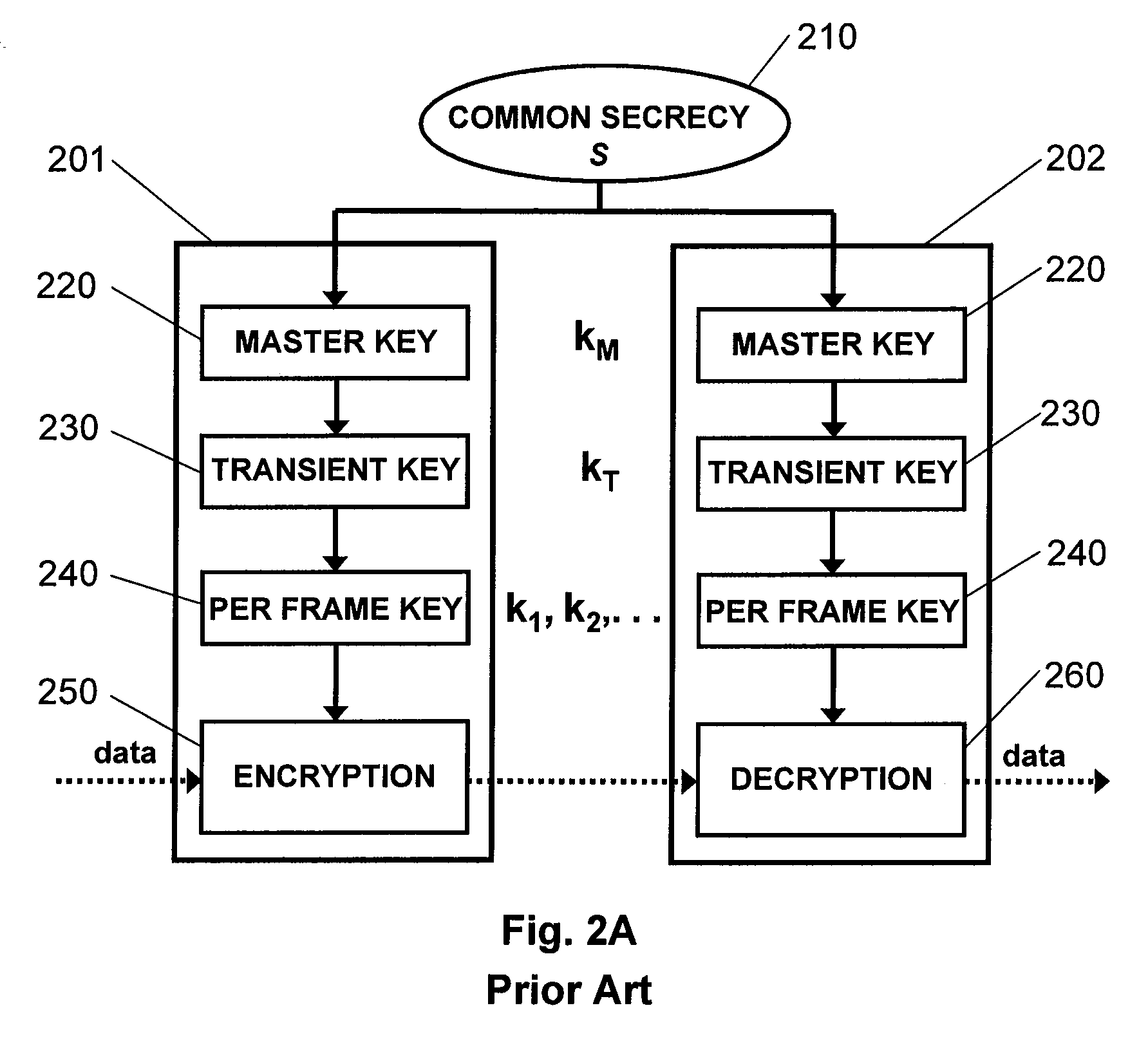
Wireless network security using randomness
InactiveUS20090138715A1Improve performanceUser identity/authority verificationSecure communicationWireless network security
The present invention provides systems and methods for securing communications in a wireless network by utilizing the inherent randomness of propagation errors to enable legitimate users to dynamically create a shared symmetric secret key. In one embodiment, the invention provides a system with two computers each having a wireless network adapter. The sending node encodes the frames, transmits the frames, determines if the frames were correctly received, retransmits the frames if they were not correctly received, stores the frames that were not retransmitted, and applies a uses the stored frames to generate a secret key. The receiving node receives the encoded frames, determines if the frames were retransmitted, stores at least one of the frames that was not retransmitted, and uses the stored frames to generate the same secret key as the receiving node.
Owner:UNIV OF MASSACHUSETTS
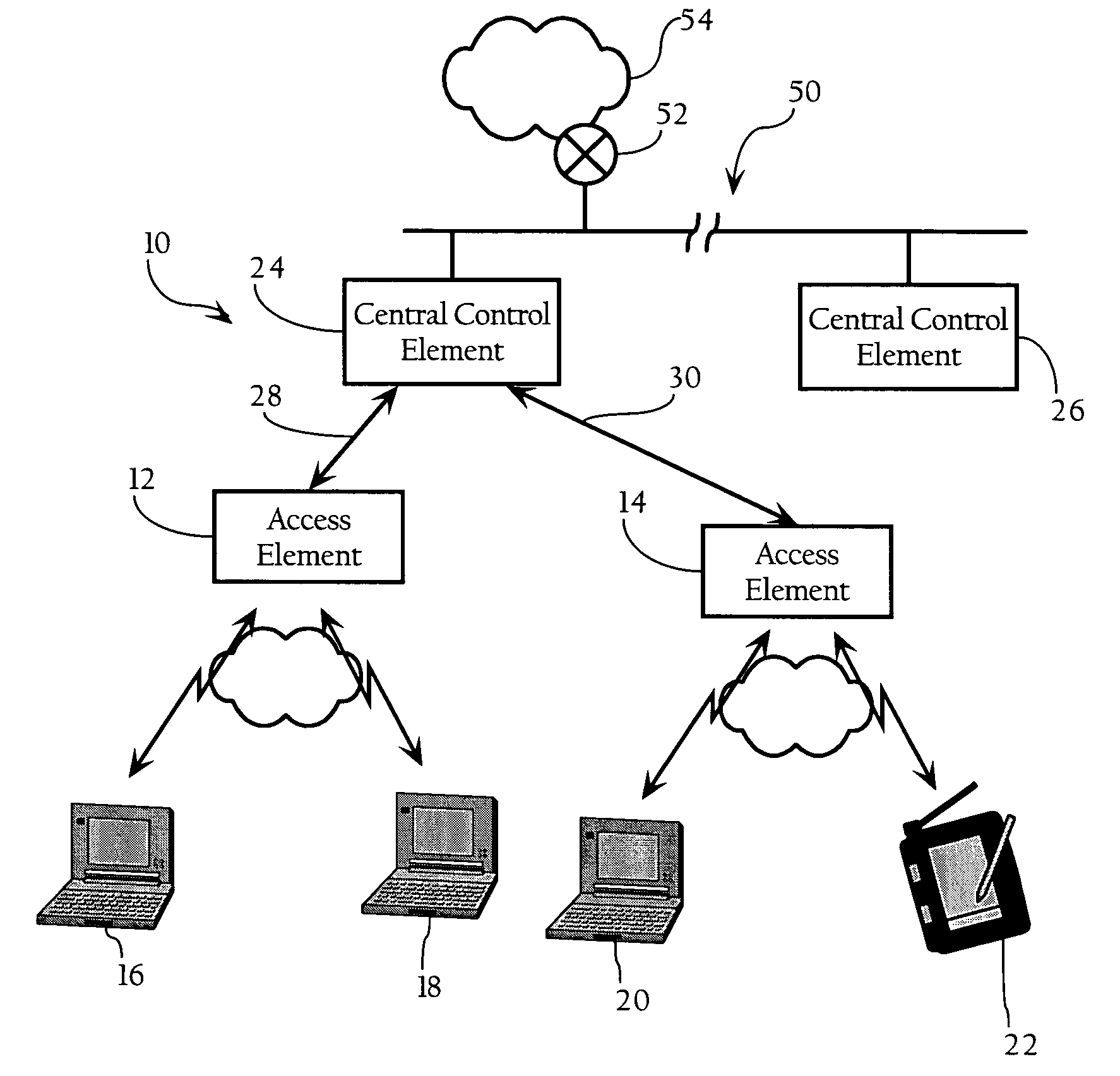
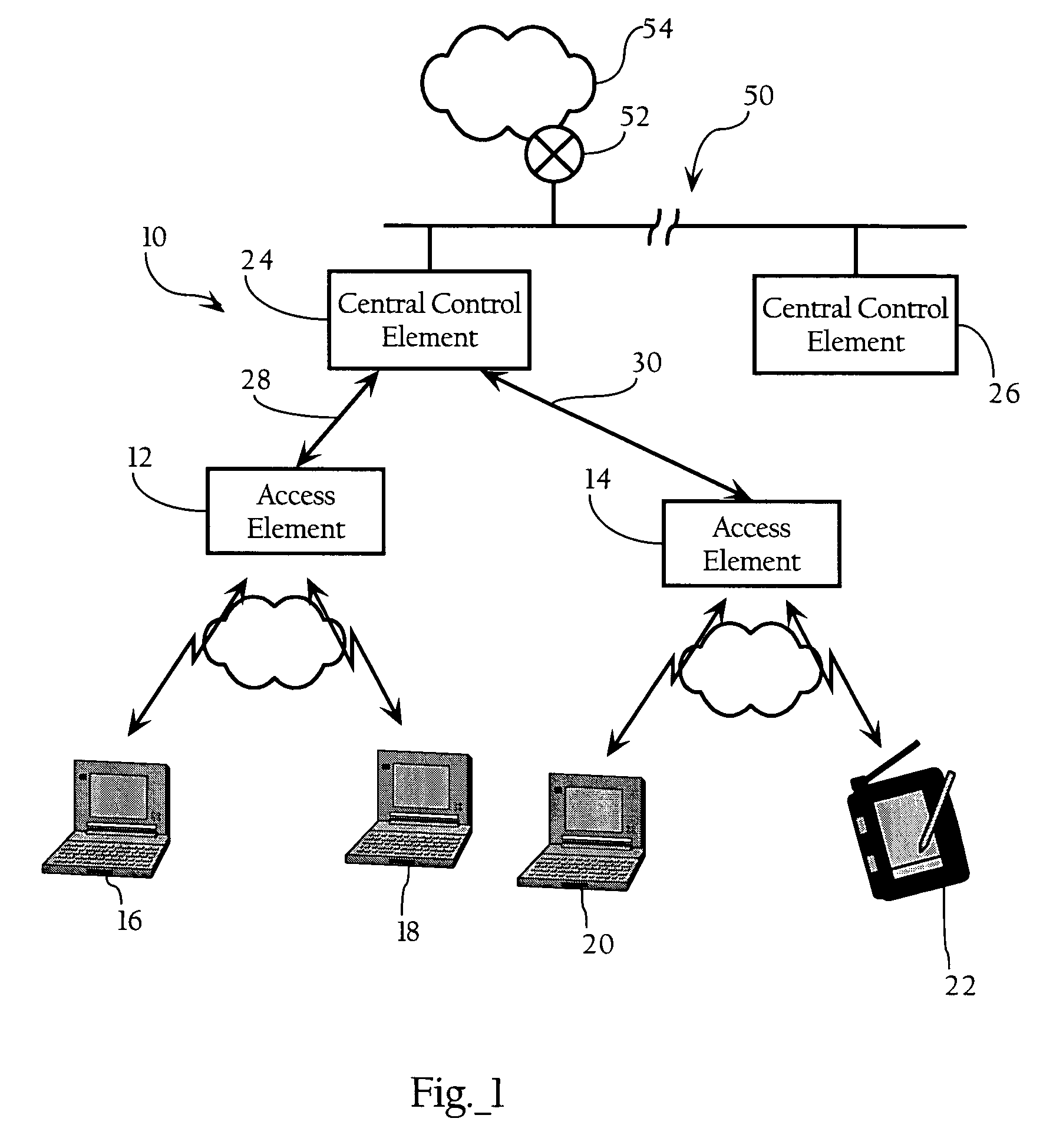
Monitoring changeable locations of client devices in wireless networks
InactiveUS7212828B2Improve securityEasy to set upUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTraffic capacityTelecommunications
Owner:INT BUSINESS MASCH CORP
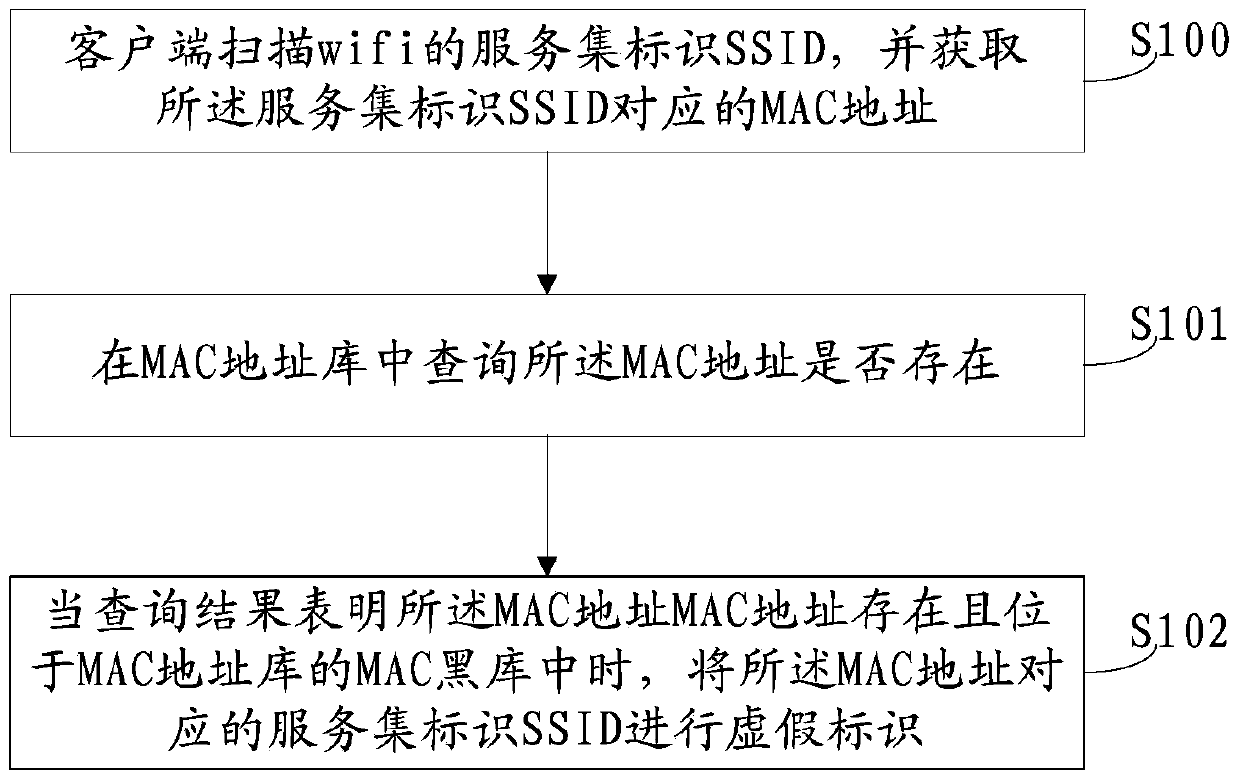
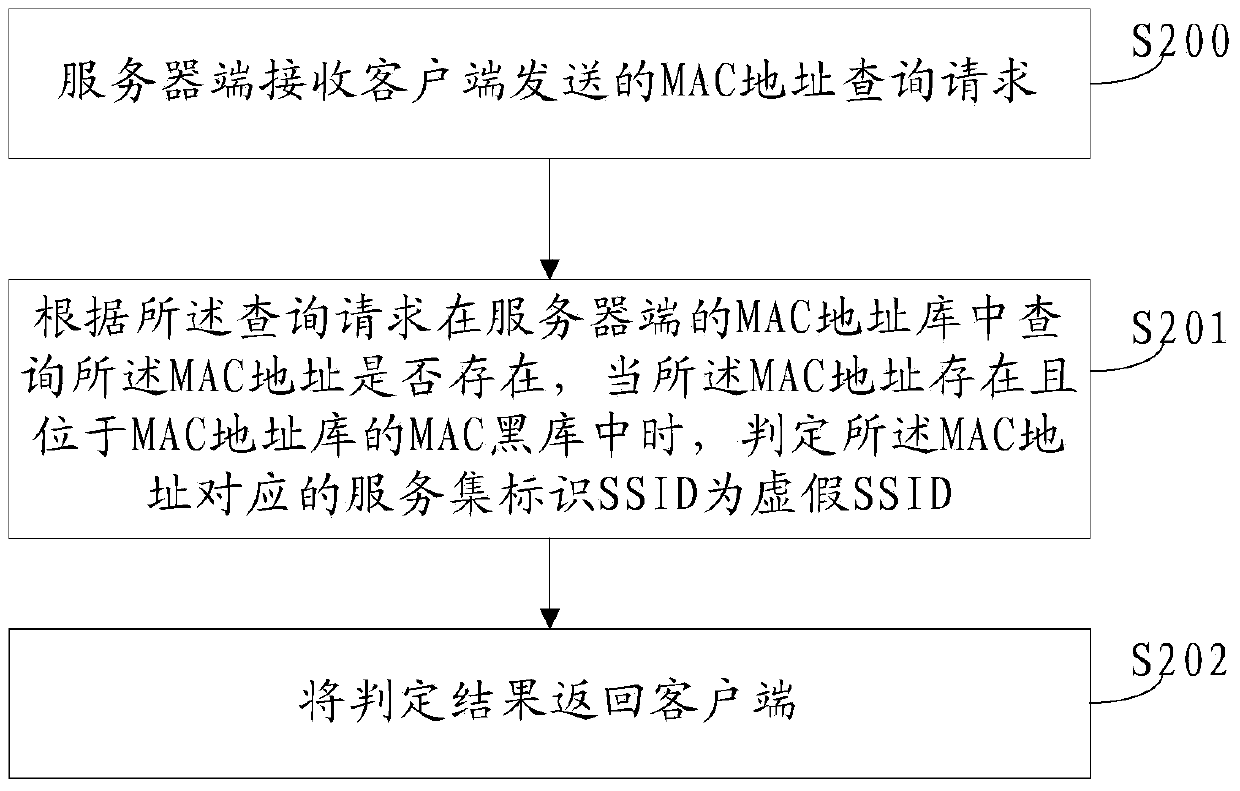
Method and system for identifying false wifi (wireless fidelity), client side and server side
ActiveCN104219670AEffective automatic identificationSecurity arrangementSoftware engineeringClient-side
The invention provides a method and a system for identifying false wifi (wireless fidelity), a client side and a server side and belongs to the field of wireless network security. The method includes: scanning SSID (service set identifier) of the wifi on the client side and acquiring an MAC (media access control) address corresponding to the SSID; searching whether or not the MAC address exists in an MAC address library, and performing false identification on the SSID corresponding to the MAC address when search results show that the MAC address exists and is located in an MAC black library of the MAC address library. The false wifi can be automatically and effectively identified, users are prompted by warning, and the problem that the false wifi cannot be identified in the prior art is solved.
Owner:ZHUHAI BAOQU TECH CO LTD
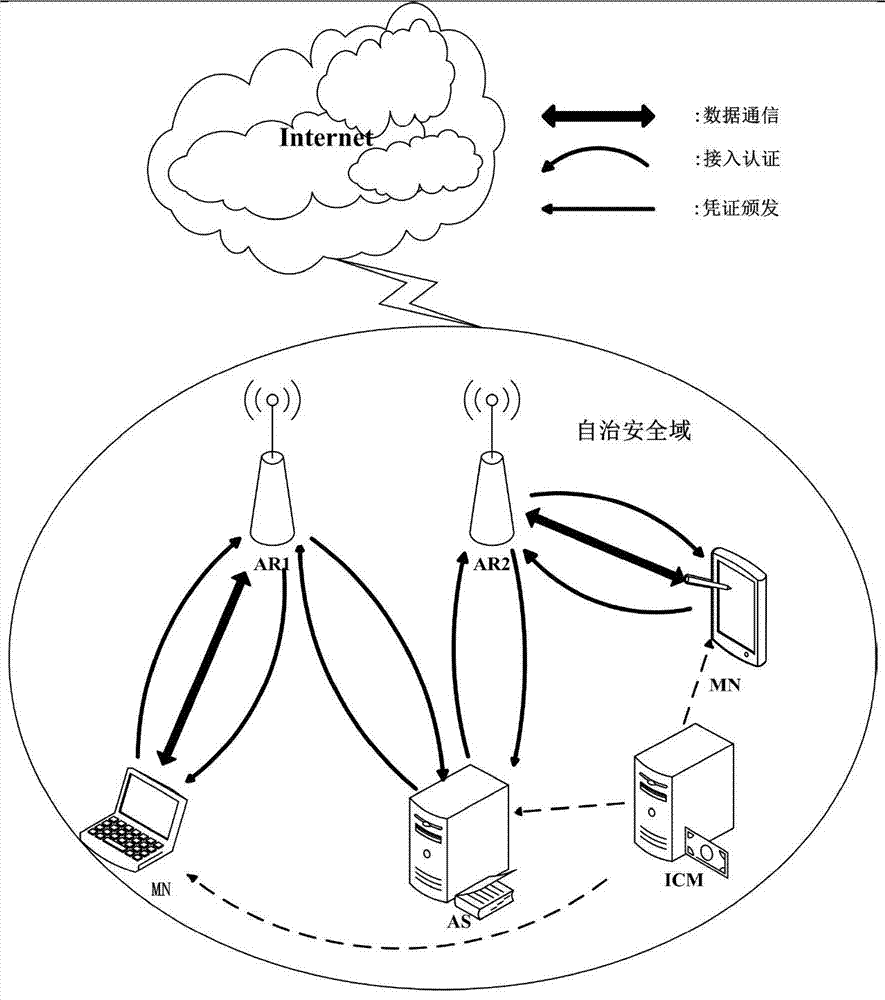
Wireless local area network two-way access authentication system and method based on identity certificates
ActiveCN103491540AEfficient access authenticationImprove access authentication efficiencySecurity arrangementAccess networkDigest access authentication
The invention discloses a wireless local area network two-way access authentication system and method based on identity certificates. The wireless local area network two-way access authentication system comprises access routers arranged in a safety area and further comprises an identity certificate management server and an authentication server. The identity certificate management server is used for managing the identity certificates of entities in the safety area, namely, issuing the identity certificates and maintaining the identity certificates. The authentication server is used for authenticating access certification application of mobile subscribers and completing shared key negotiation with the mobile subscribers. The access routers are used for controlling whether the mobile subscribers have access to the wireless local area network or not according to the authentication result fed back from the authentication server and receiving and forwarding authentication information between the mobile subscribers and the authentication server. According to the wireless local area network two-way access authentication system and method, in an autonomous security domain, two-way access authentication and secret key negotiation between the mobile subscribers and the accessed network can be achieved, efficient access authentication conducted when the mobile subscribers switch between the different access routers is supported, and the access authentication efficiency is improved.
Owner:NORTHEASTERN UNIV
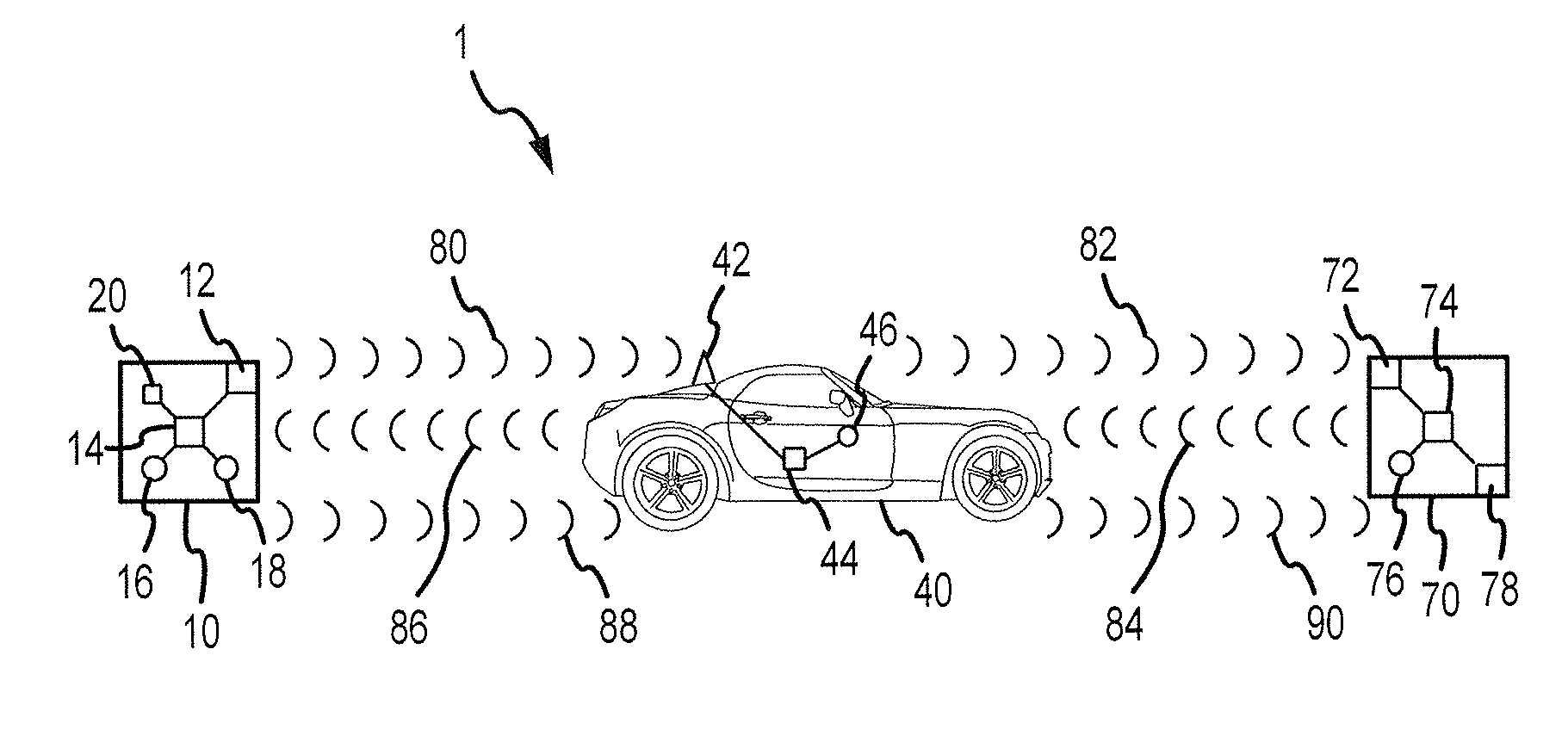
Secure wireless communication initialization system and method
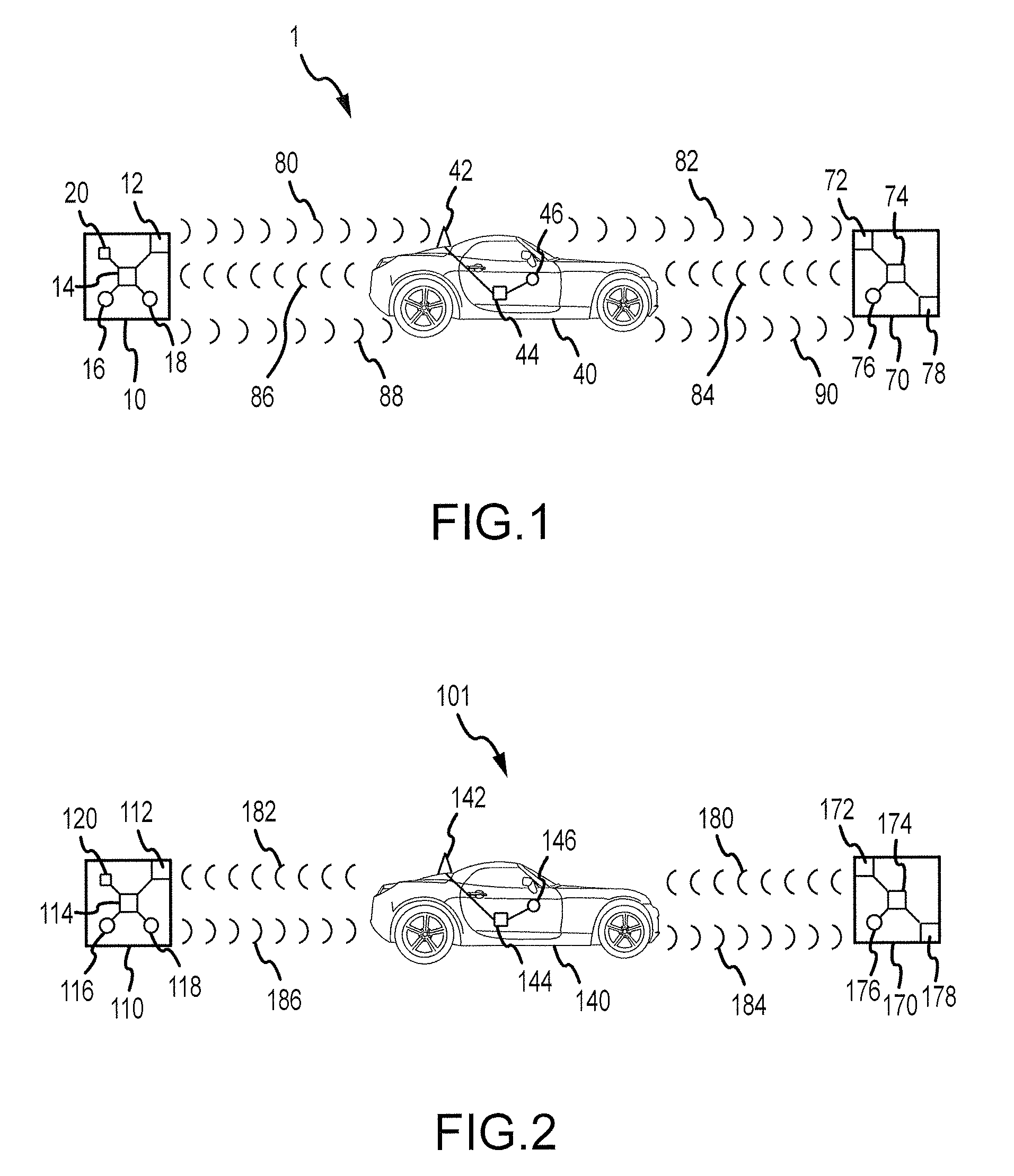
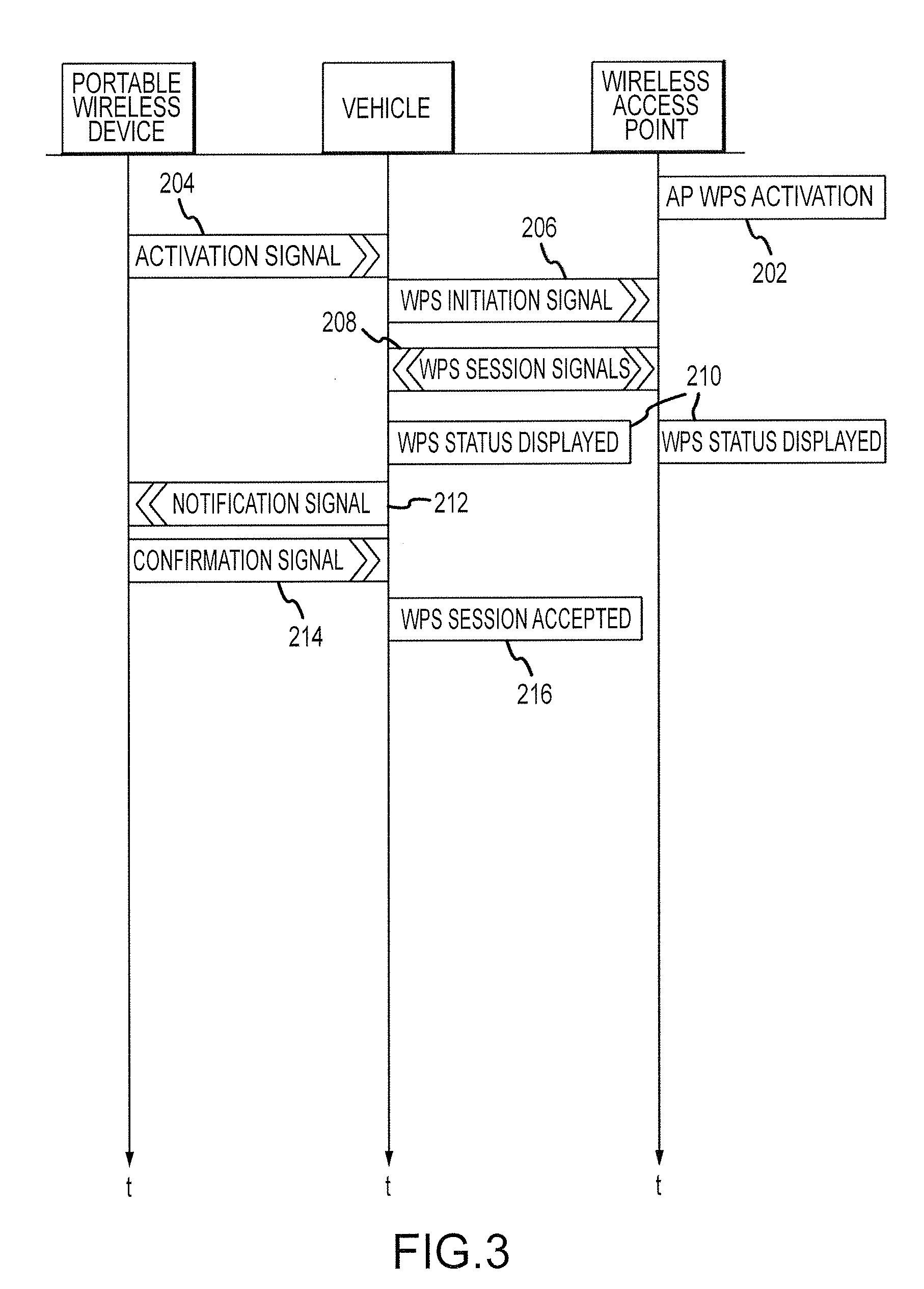
InactiveUS20090291637A1Secure wireless communicationWell formedRadio transmissionSecurity arrangementCommunications systemCommunication device
A wireless communication system for a vehicle is provided. The system comprises a portable wireless device comprising first and second manual interface devices and adapted to transmit a wireless network security protocol confirmation signal in response to manipulation of the first and second manual interface devices, and an onboard wireless communication device for the vehicle, adapted to accept a Wi-Fi Protected Setup (WPS) session outcome in response to receiving the wireless network security protocol confirmation signal.
Owner:GM GLOBAL TECH OPERATIONS LLC
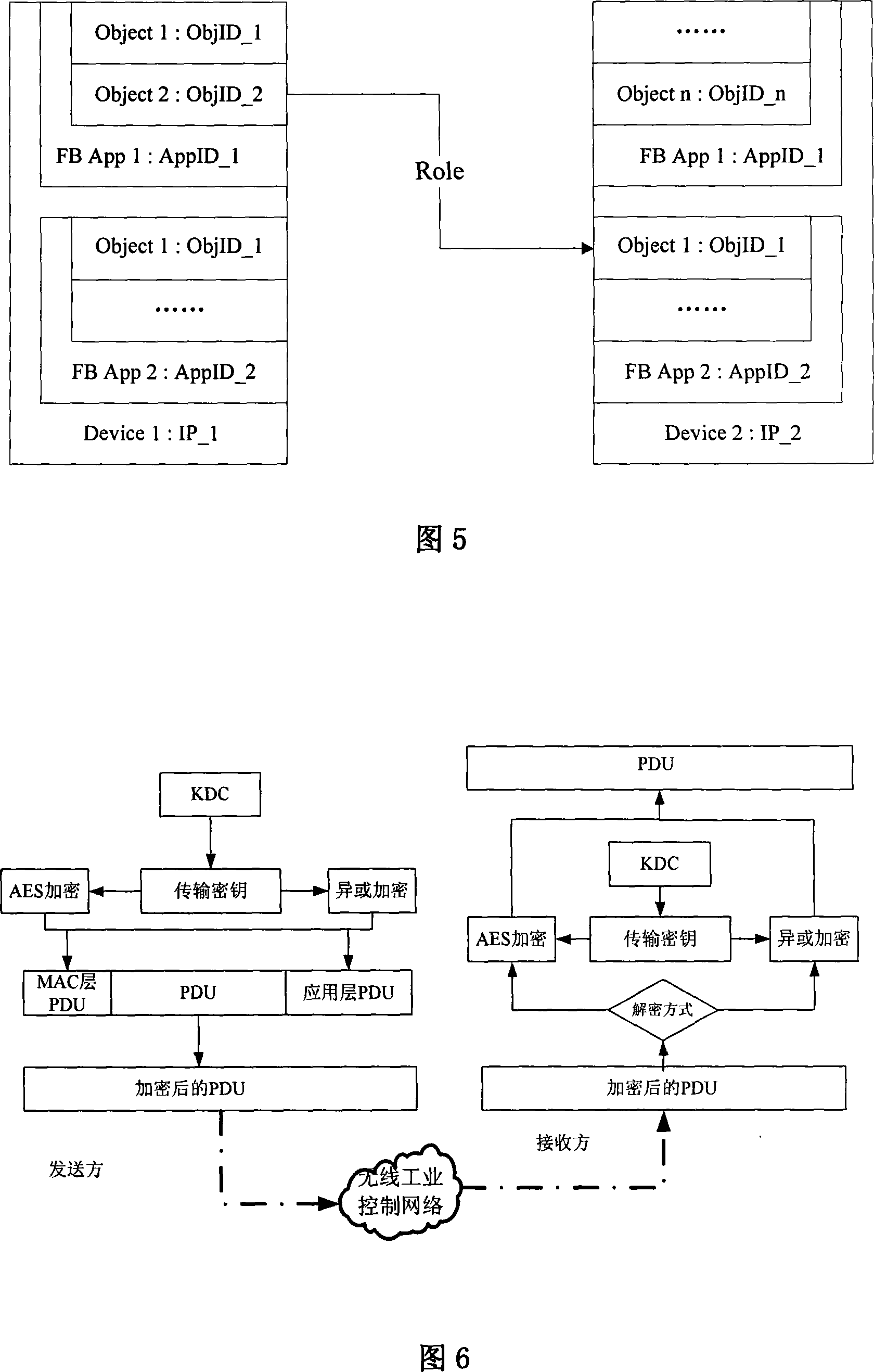
Security system of wireless industrial control network, and method for implementing security policy
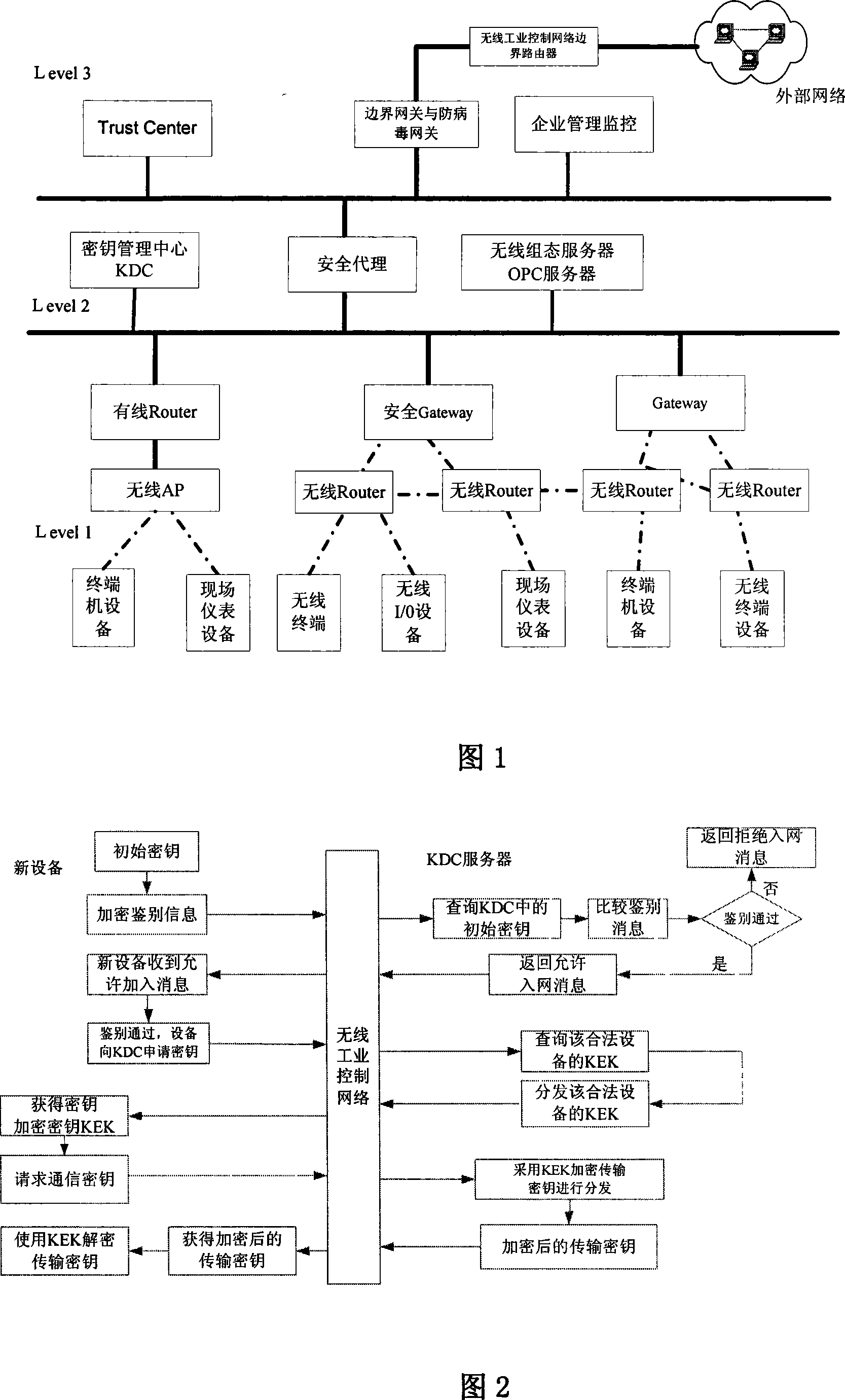
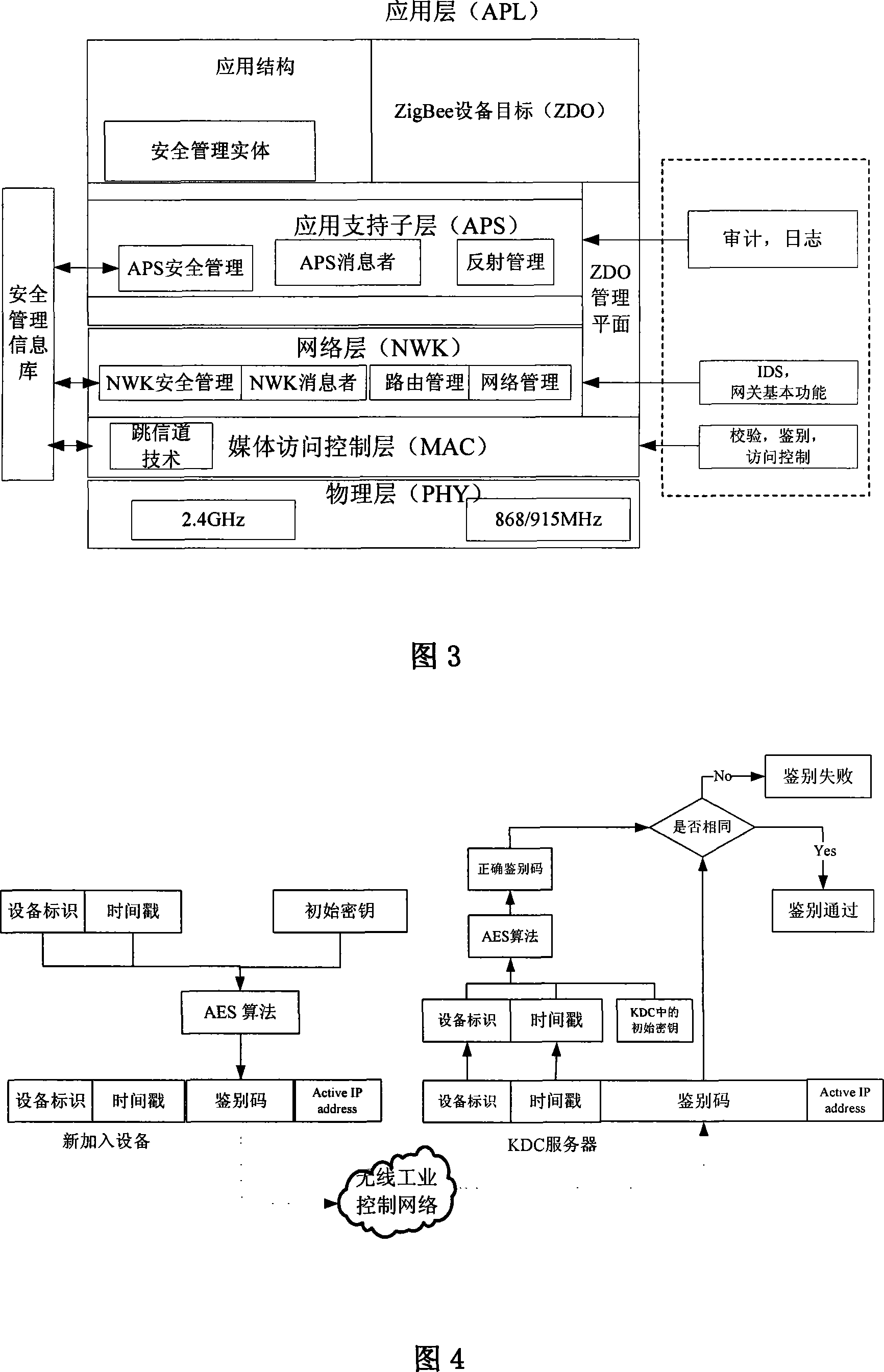
InactiveCN101094056AGuaranteed uptimeNormal production orderKey distribution for secure communicationData switching by path configurationInformation repositoryStructure of Management Information
The technical scheme of this invention is that dividing the wireless industry control net (WICN) into three net sections: a enterprise managing layer, a process controlling layer and field equipment layer. According to the hiberarchy of WICN, a WICN safety managing system is built. This system defines the built WICN into 4 safety levels. According to the access control list in the sever pool of the key administration center KDC, via the mechanism of key managing and the equipment verifying basis on KDC, the wireless safety gateway, the wireless net safety application managing entity and the wireless safety managing info database, different safety precautions are applied on the various layers and various safety levels of nets. This invention suits the industry field control to solve effectively the safety problems of resource and data comm. within the WICN and ensures the normal system running.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Monitoring changeable locations of client devices in wireless networks
InactiveUS20040203908A1Easy to set upUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTraffic capacityTelecommunications
Security of wireless networks is improved by rejecting traffic from a wireless device located outside a defined spatial boundary. The device's spatial position with respect to the boundary is determined using directional antenna arrays on a plurality of measurement points, and calculating where the vectors intersect. Having thus determined a device's location, access to a wireless network can be denied if the device is outside a predetermined spatial boundary. Or, the device's location inside or outside of the spatial boundary can be used for monitoring a changeable location of one or more client devices in a wireless network, for example as a theft detection or theft deterrent mechanism.
Owner:IBM CORP
Security authentication method for wireless network
ActiveCN102547695AImplement Live BindingAvoid the possibility of leakageConnection managementSecurity arrangementBrute forceIp address
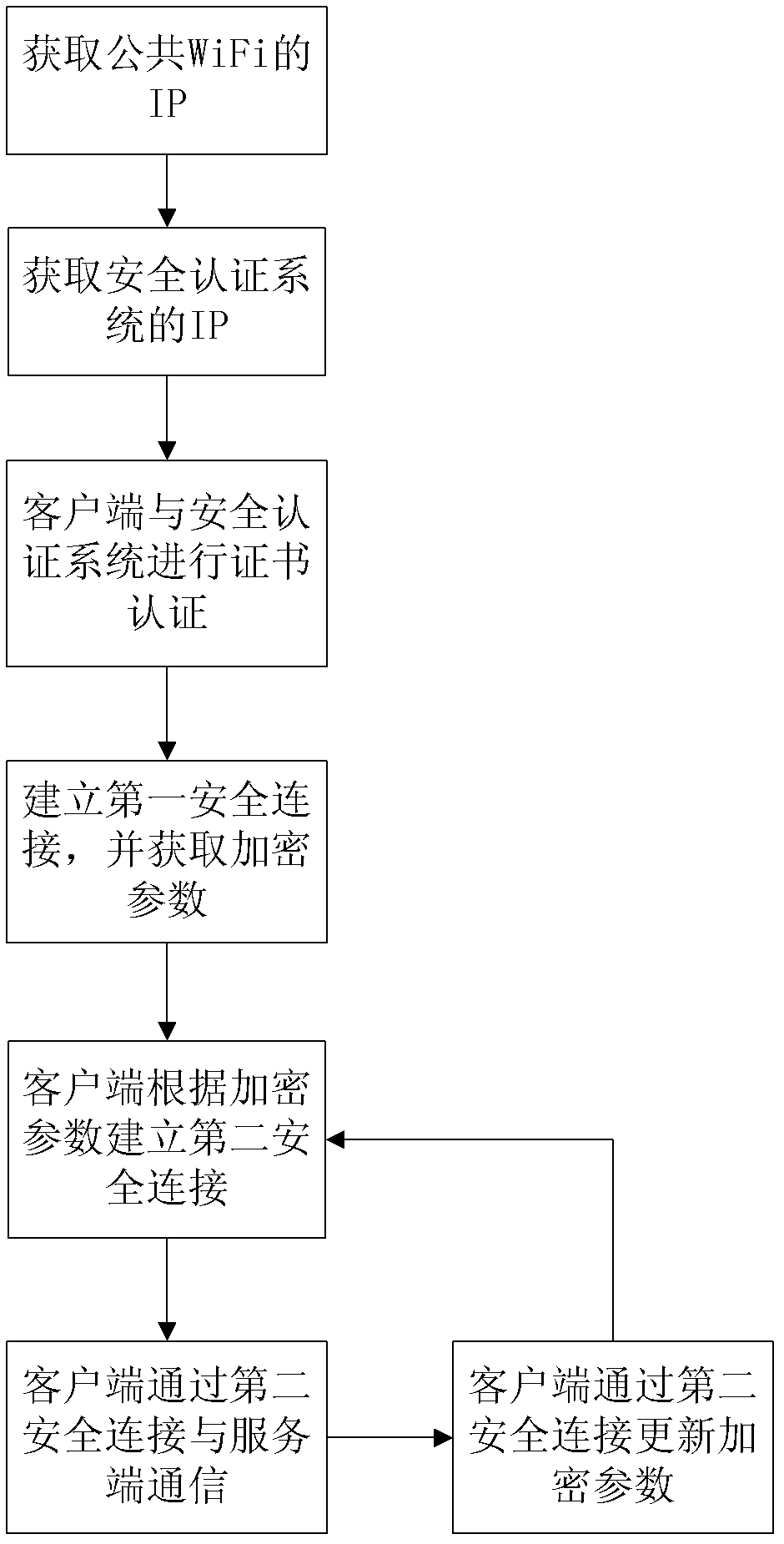
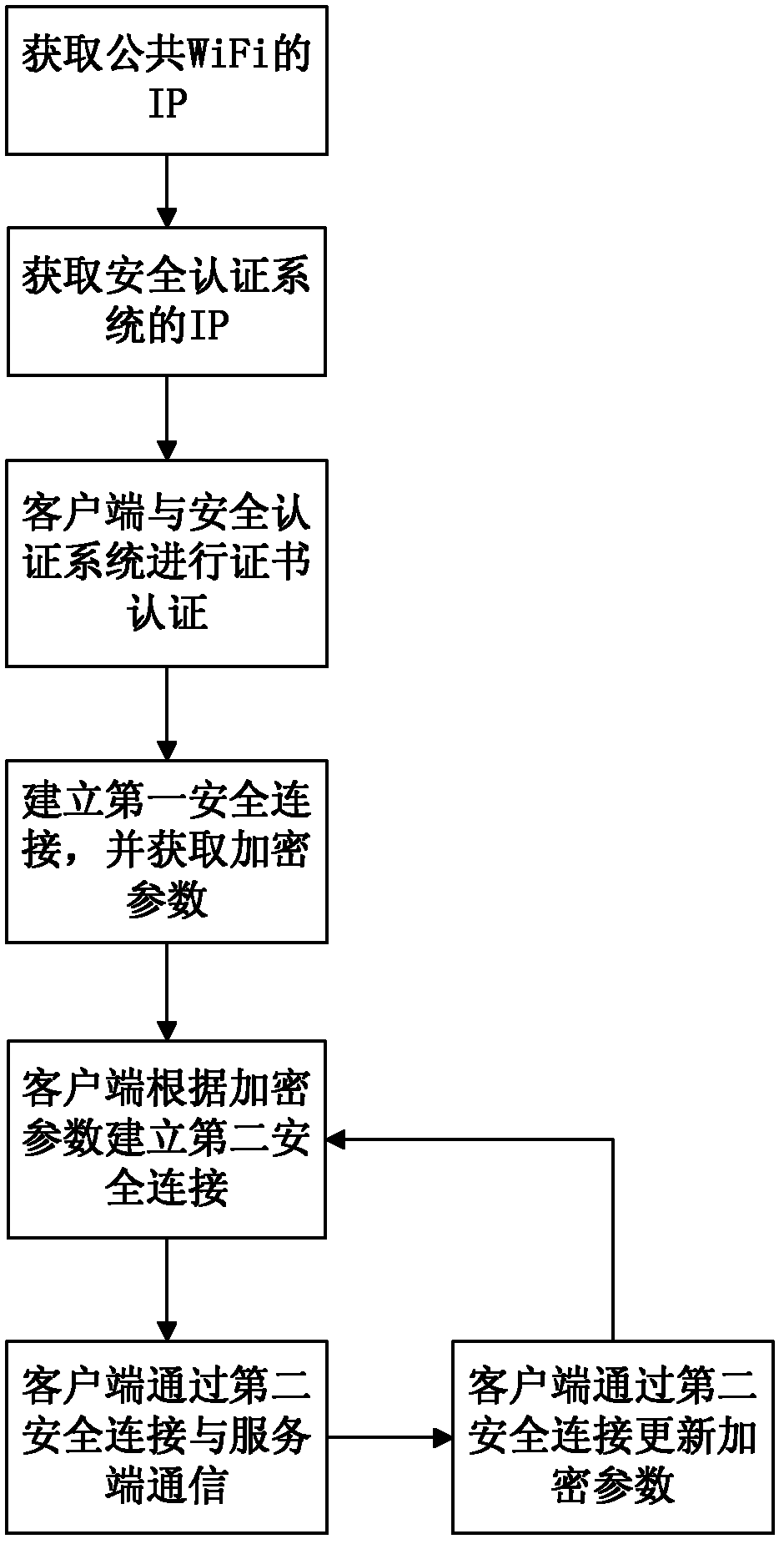
The invention relates to a security authentication method for a wireless network. A wireless fidelity (WiFi) server and a client are involved, and the security authentication method comprises the following steps that: a, an authentication service program is deployed in the client, and the client is connected to a public open system of the WiFi server to acquire a corresponding internet protocol (IP) address; b, according to the IP address, the client acquires and accesses an IP address of a security authentication system of the WiFi server; c, the WiFi server authenticates a client certificate; d, the client which passes the authentication establishes first security connection with the WiFi server and acquires encryption parameters; e, the client establishes a second security connection with the security authentication system of the WiFi server according to the encryption parameters; and f, the client and the WiFi server communicate and are updated through the second security connection. By the security authentication method, the client and the WiFi server can be connected easily and quickly by using a complex key and a complex encryption way; and meanwhile, the security during connecting can be guaranteed by using a method of updating the key regularly to ensure that brute force-based cracking and possibility of key leakage are avoided.
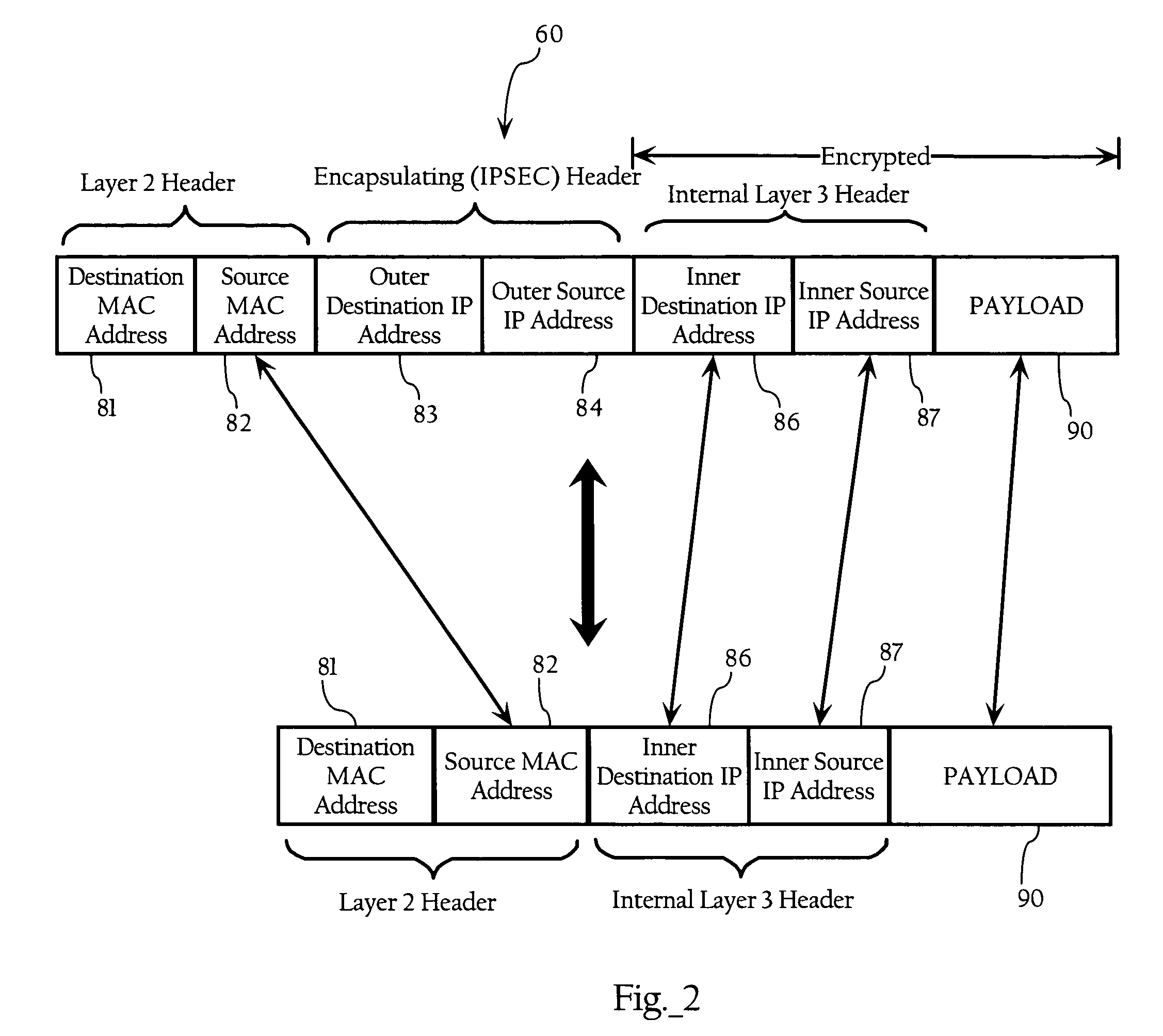
Owner:成都飞鱼星科技股份有限公司
Wireless network security mechanism including reverse network address translation
ActiveUS7516174B1Prevent unauthorized accessAvoid accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPrivate networkNetwork address translation
Methods, apparatuses and systems directed to preventing unauthorized access to internal network addresses transmitted across wireless networks. According to the invention, mobile stations are assigned virtual client network addresses that are used as the outer network addresses in a Virtual Private Network (VPN) infrastructure, as well as unique internal network addresses used as the inner network addresses. In one implementation, the virtual client network addresses have little to no relation to the internal network addressing scheme implemented on the network domain. In one implementation, all clients or mobile stations are assigned the same virtual client network address. A translation layer, in one implementation, intermediates the VPN session between the mobile stations and a VPN server to translate the virtual client network addresses to the internal network addresses based on the medium access control (MAC) address corresponding to the mobile stations. In this manner, the encryption inherent in the VPN infrastructure prevents access to the internal network addresses assigned to the mobile stations.
Owner:CISCO TECH INC
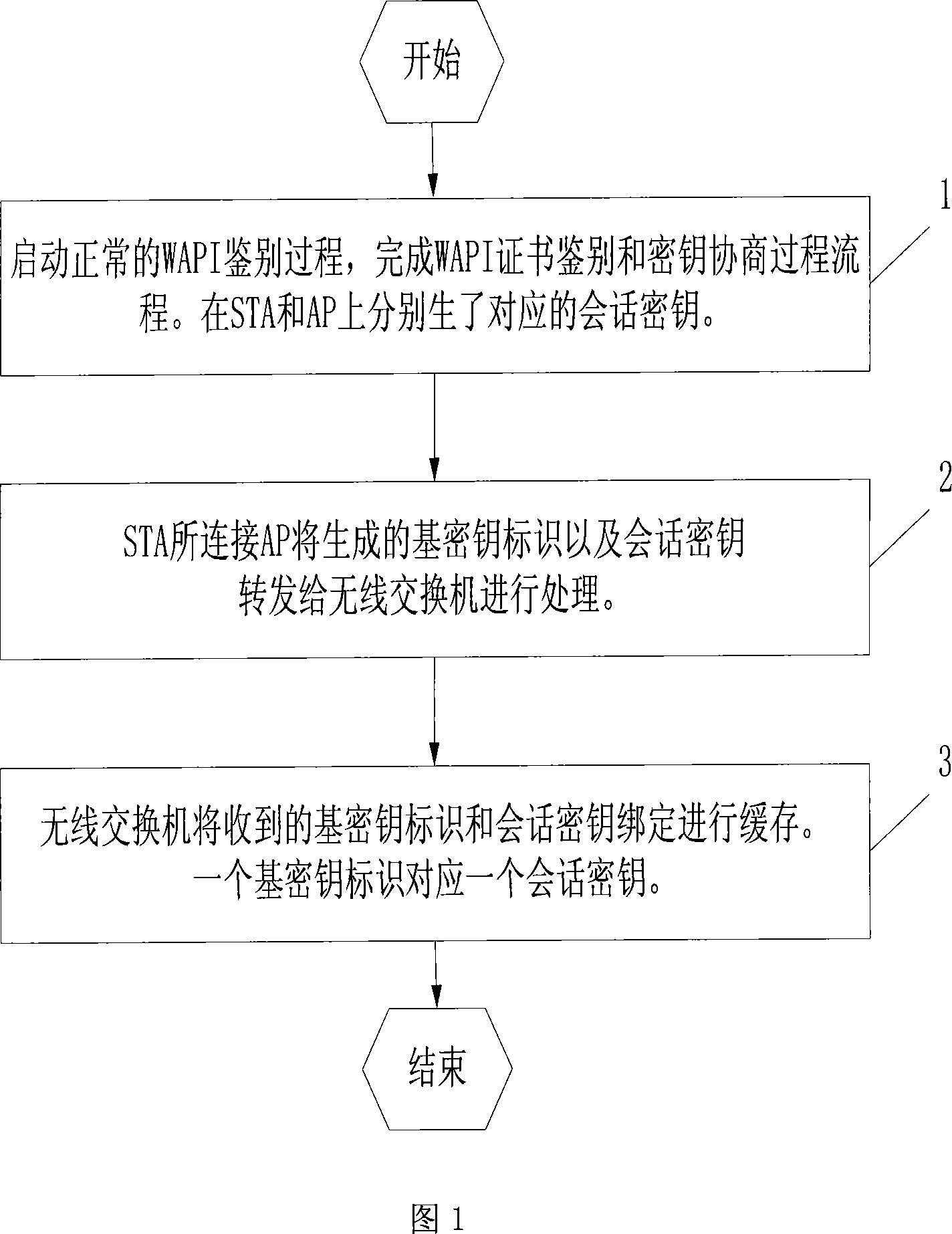
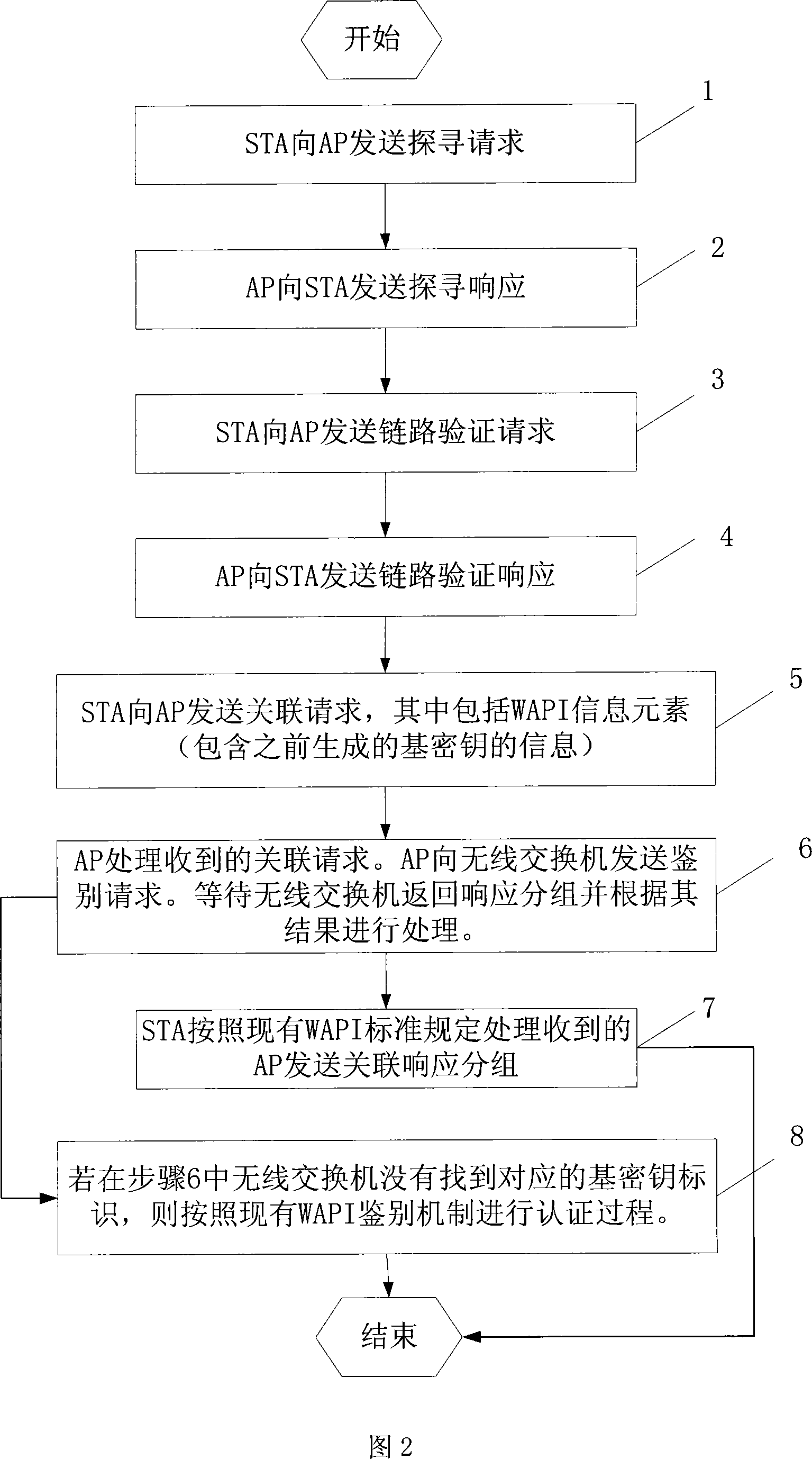
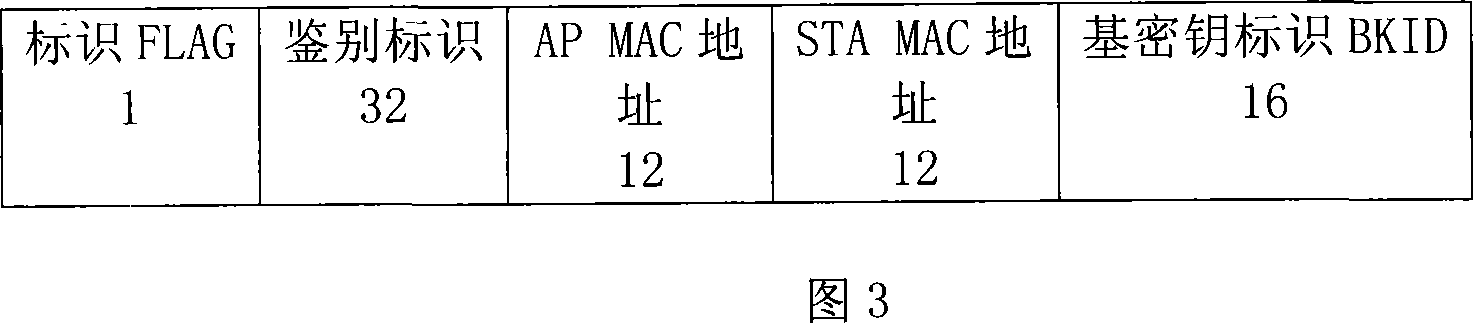
Wireless switching network re-authentication method based on wireless LAN secure standard WAPI
ActiveCN101079891AReduce latencyMove quicklyData switching by path configurationExchange networkWireless lan
This invention relates to a re-authentication method for radio exchange network based on wireless LAN safety standard WAPI characterizing in transmitting basic key identification and session key generated by the access point connected to the terminal to a wireless exchange after applying WAPI for discrimination for the first time, which lists the identification and the session key to lists corresponding to each other and buffer-stores them, when the terminal roams to the next access point and sends an associated request including the basic key identification, said new access point sends a discrimination request and the wireless exchange audits that there is the basic key identification and sends the response packets including corresponding session key to it to communicate with the terminal with the session key, if the identification does not exist, then authentication will be done again.
Owner:TSINGHUA UNIV
Wireless network security
ActiveUS20140143536A1Enhanced informationConvenient wireless communicationNetwork topologiesTransmissionEncryptionWireless network security
A method includes identifying a suspect node of a network. The method also includes initiating formation of a sub-network of the network by identifying neighbor nodes of the suspect node and sending an invitation message to a first neighbor node to invite the first neighbor node to the sub-network. The invitation message is encrypted using a first encryption key associated with the first neighbor node. The invitation message is not sent to a second node that is identified as a neighbor node only by the suspect node. The sub-network is configured to enable first communications between members of the sub-network. The first communications are communicated in a manner that is secured against access by the suspect node. Subsequent to formation of the sub-network, second communications between the suspect node and a device of the network are routed to or through at least one of the members of the sub-network.
Owner:THE BOEING CO
Initial point detection algorithm of transient signal in radio frequency fingerprint identification technology
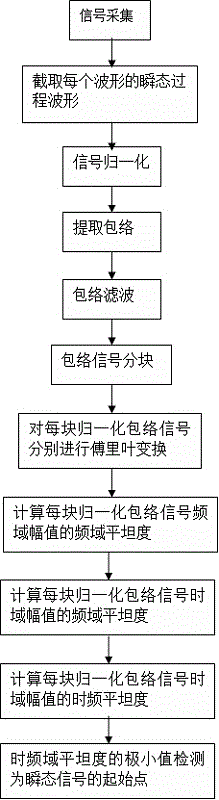
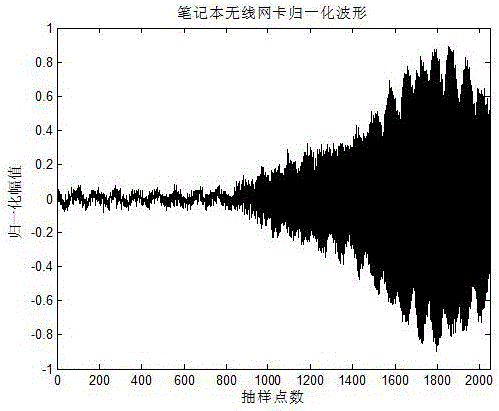
InactiveCN105678273AEfficient extractionCharacter and pattern recognitionTime domainRadio frequency signal
The invention discloses an initial point detection algorithm of a transient part of a radio frequency signal in a radio frequency fingerprint identification technology. The detection algorithm includes the steps of signal acquisition, interception of transient process waveform of each waveform, signal normalization, envelope extraction, envelope filtering, envelope partitioning, Fourier transform of each block of normalized envelope signal, calculation of frequency domain flatness of frequency domain amplitude, time domain flatness and time frequency flatness of each normalized envelop signal, and detection of minimal values of the time and frequency domain flatness as an initial pint of a transient signal. Based on time frequency and frequency domain characteristics, the transient initial point of a radio frequency signal of a transmitter is detected, thereby effectively extracting fingerprint features, and then a classifier is utilized to classify wireless devices, thereby enabling the radio frequency fingerprint identification technology to be better applied to the field of wireless network security. The initial point detection algorithm of the transient part of the radio frequency signal in the radio frequency fingerprint identification technology has a relatively high identification accuracy rate and relatively short classification time.
Owner:SHANGHAI UNIV
Wireless WIFI network quality analysis evaluation method
InactiveCN104301925AEvaluate the overall quality levelTake complexity into accountTransmissionWireless communicationQuality levelWireless connectivity
A wireless WIFI network quality analysis evaluation method comprises the steps of detecting WIFI signal strength and WIFI connection rate; analyzing wireless frequency point information through a wireless frequency point detection engine; analyzing packet loss rate during network transmission through a network transmission error packet loss rate detection engine; analyzing network transmission delay information through a network transmission delay detection engine; analyzing network rate through a wireless connection mode detection engine; analyzing network security level through a wireless network security level detection engine; allocating weight values for the indexes analyzed in the steps (1-6) according to the influence degree of wireless WIFI network quality, respectively evaluating the values of data collected in the steps (1-6) one by one according to the weight values of the corresponding indexes, and then synthesizing all values to evaluate the WIFI network quality. The wireless WIFI network quality analysis evaluation method gives sufficient consideration to the complexity of a wireless network environment and can well evaluate the comprehensive quality level of a wireless WIFI network.
Owner:中电福富信息科技有限公司
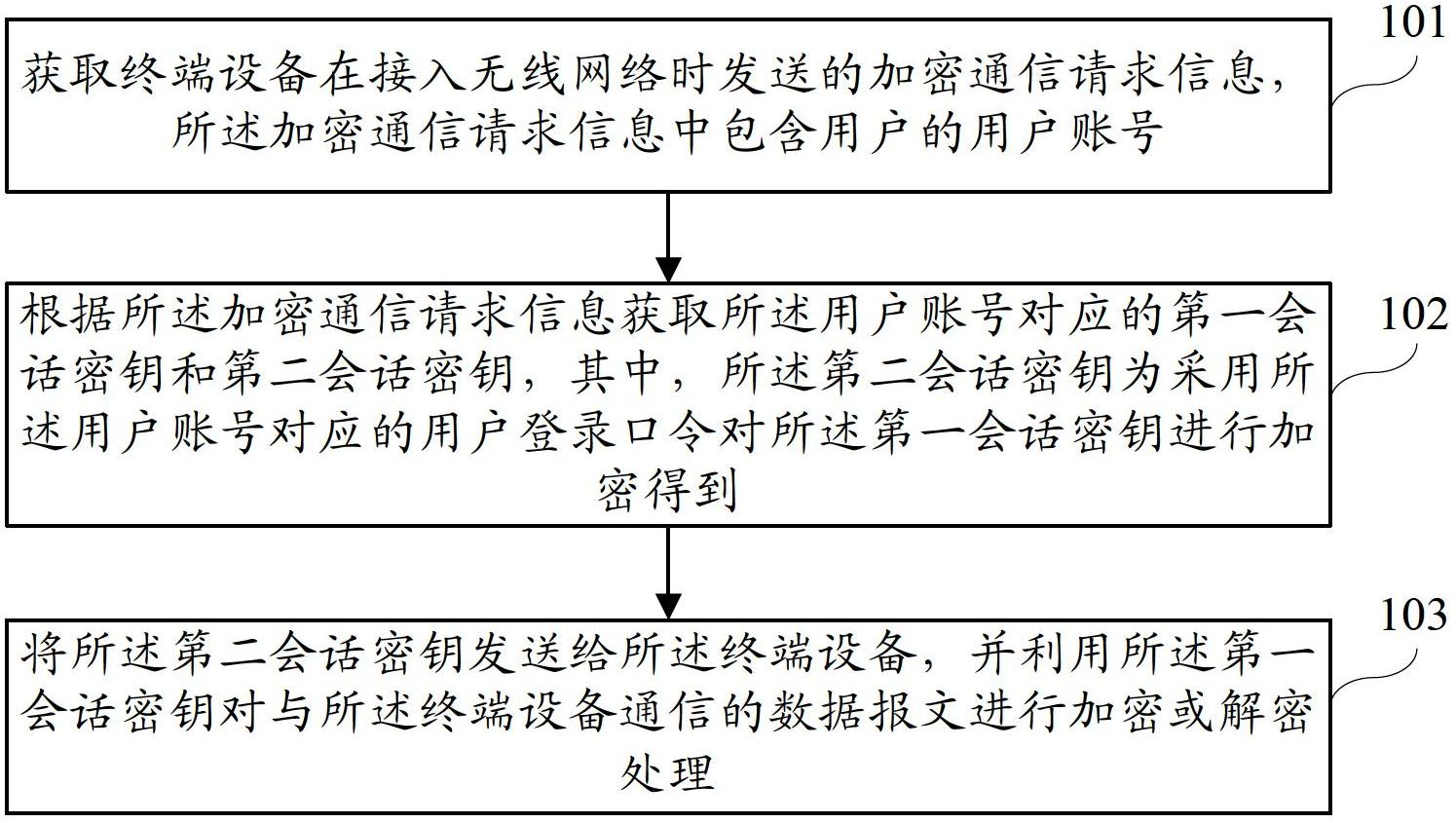
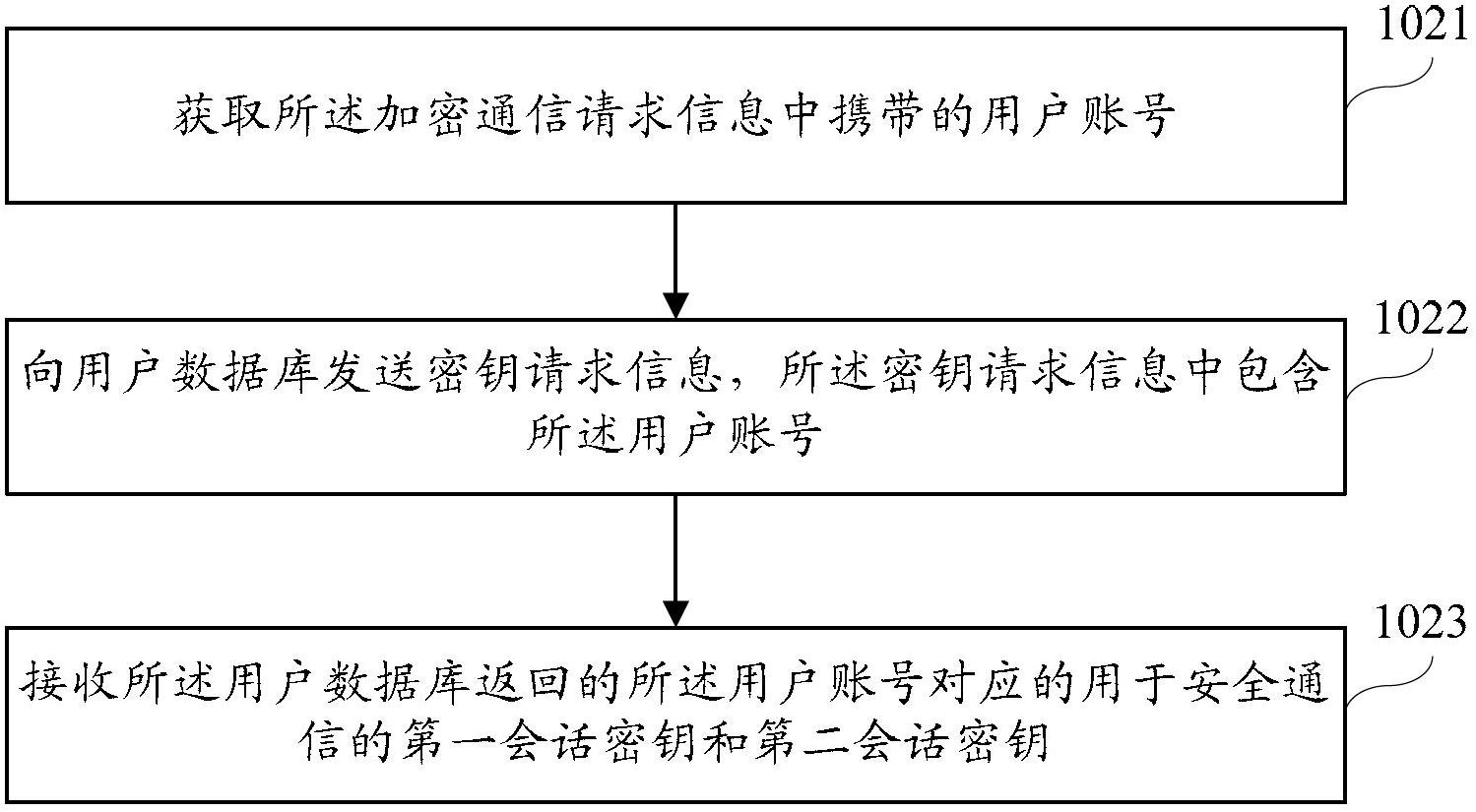
Terminal equipment, encrypted gateway and method and system for wireless network safety communication
ActiveCN102695168AAvoid safety hazardsImprove securityMultiple keys/algorithms usageSecurity arrangementPasswordTerminal equipment
The invention provides terminal equipment, an encrypted gateway and a method and a system for wireless network safety communication. The method for wireless network safety communication includes: acquiring encryption communication request information transmitted by the terminal equipment when the terminal equipment is accessed to a wireless network, wherein the encryption communication request information includes a user account of a user; acquiring a first session key and a second session key corresponding to the user account according to the encryption communication request information, wherein the second session key is obtained by encrypting the first session key by a user login password corresponding to the user account; and transmitting the second session key to the terminal equipment, and using the first session key to encrypt or decrypt data messages communicated with the terminal equipment. By the aid of the terminal equipment, the encrypted gateway, the method and the system, potential safety hazard in existing wireless network communication can be effectively avoided.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
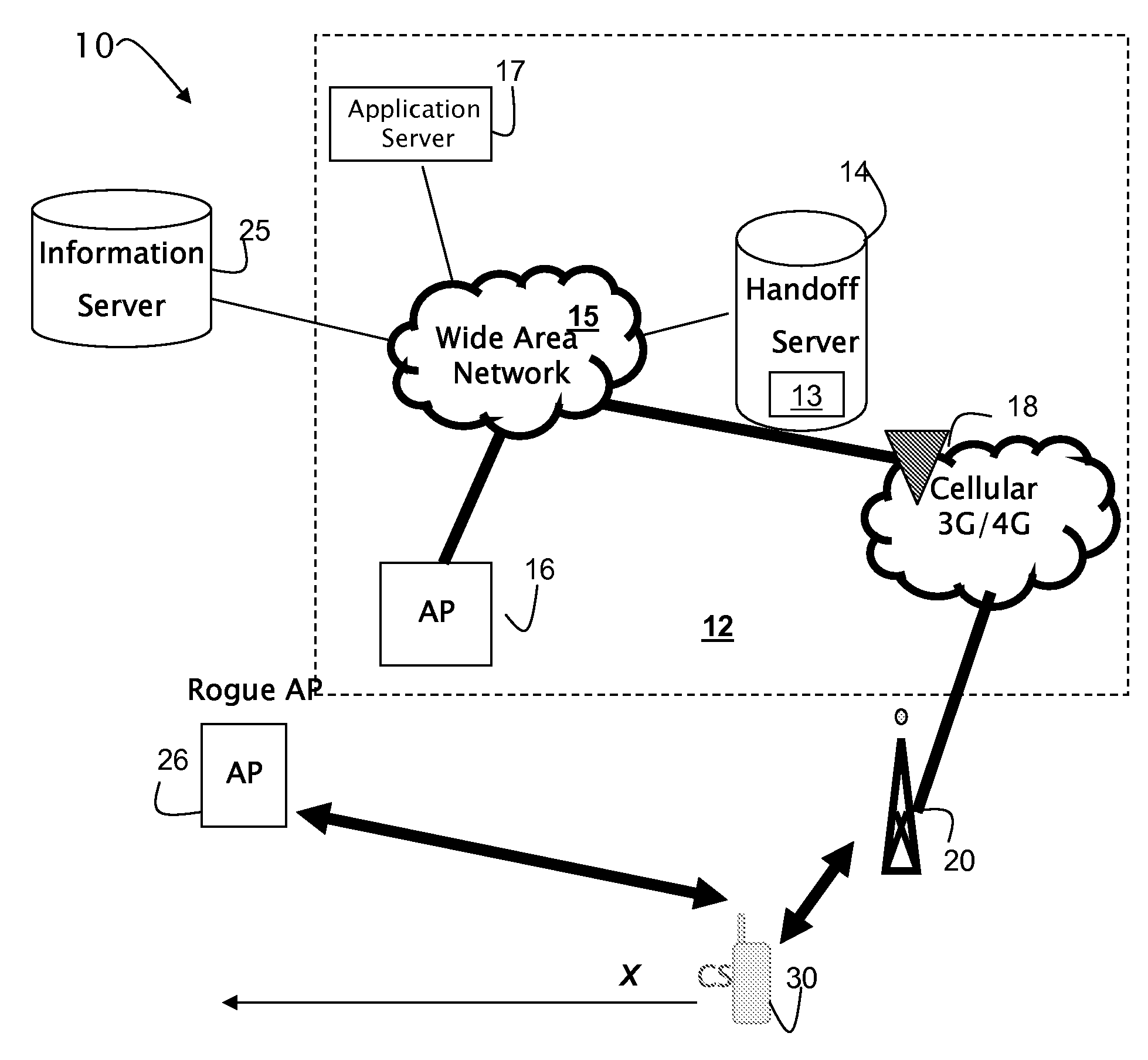
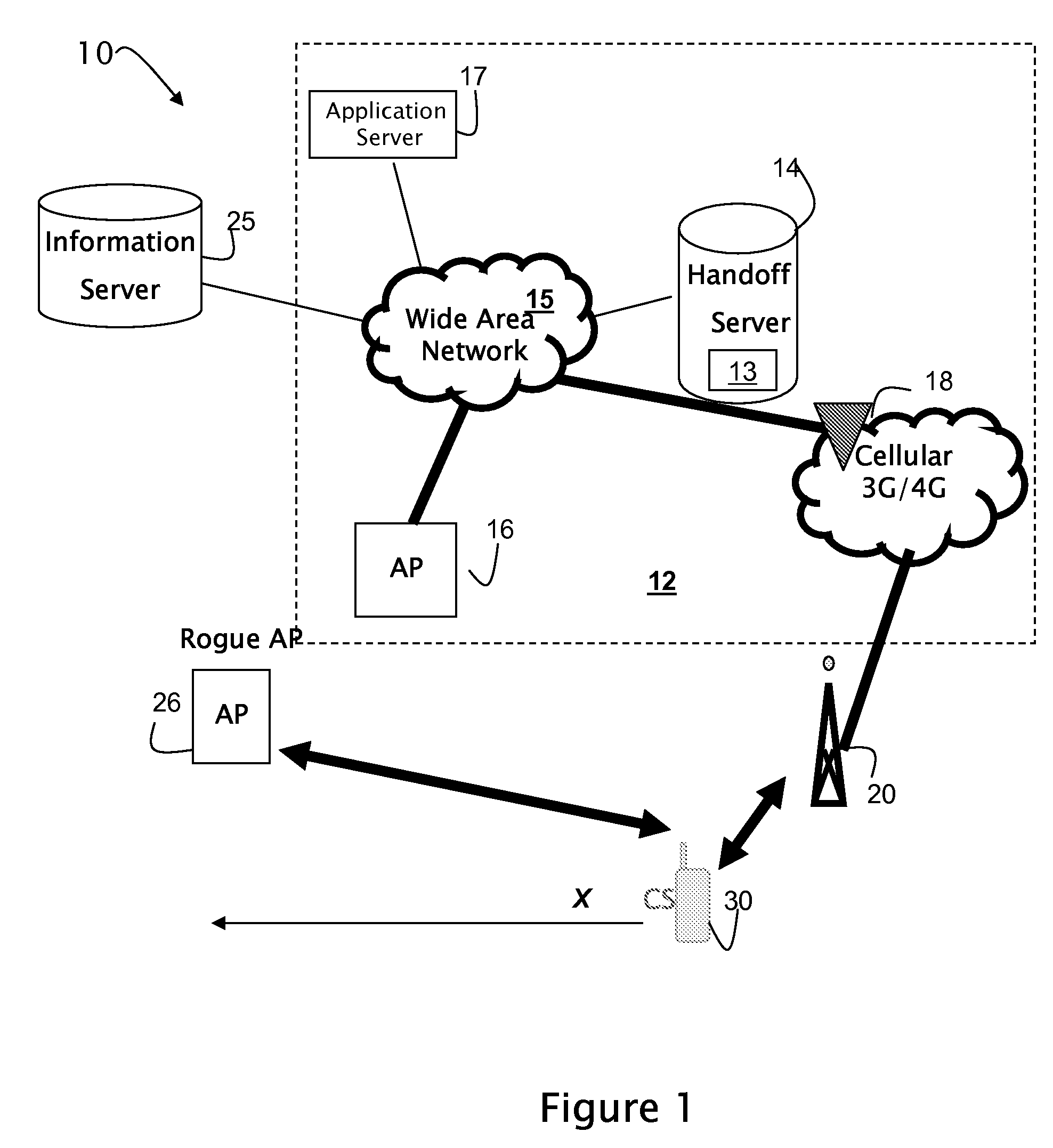
Method and apparatus for security configuration and verification of wireless devices in a fixed/mobile convergence environment
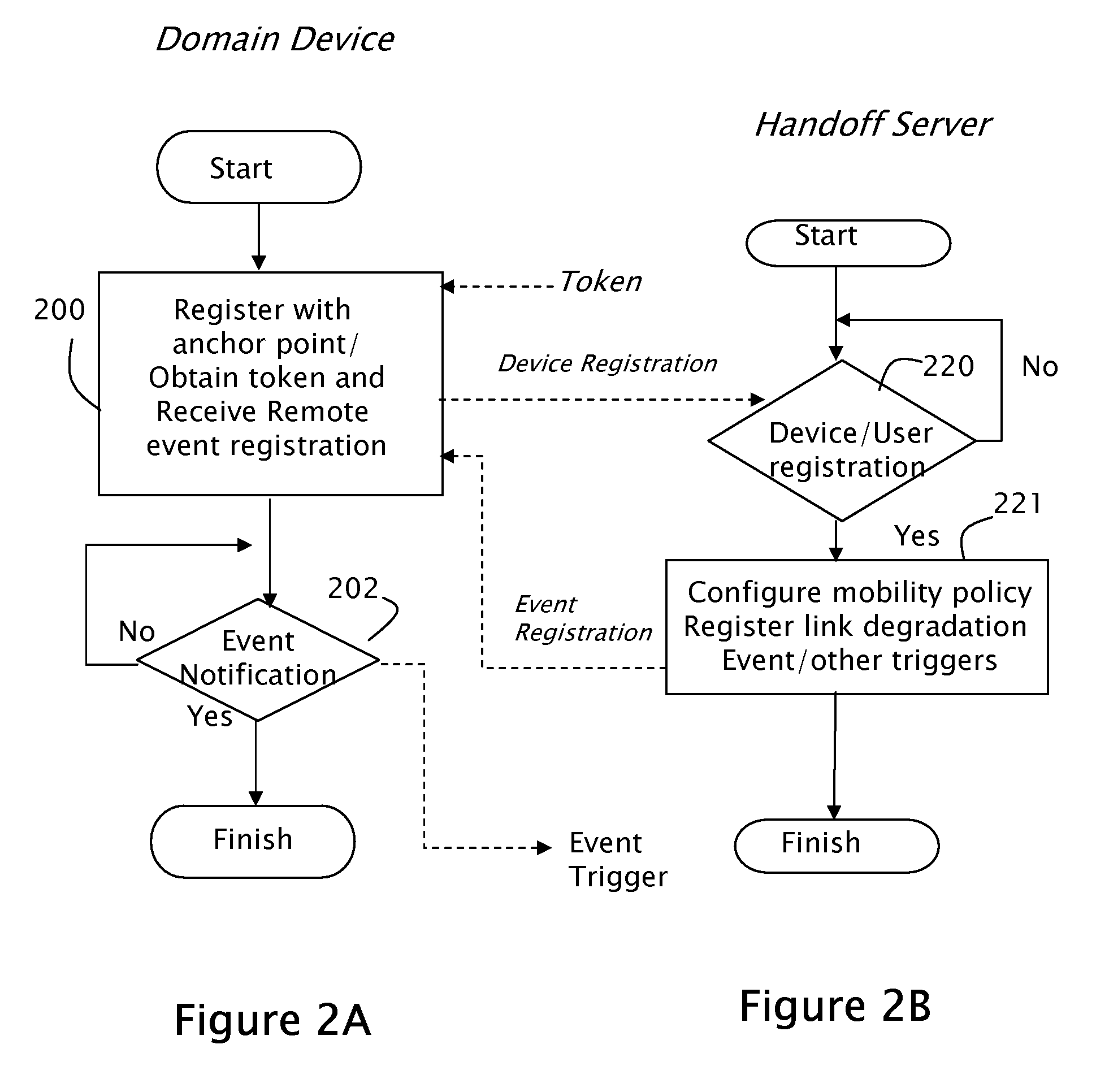
InactiveUS20080301773A1Security of network is notIncrease speedDigital data processing detailsMultiple digital computer combinationsReachabilityRogue access point
A system and method is described that enables autonomic discovery of wireless network security mechanisms by mobile devices. Stateful monitoring of wireless devices facilitates identification of pending network connectivity loss, enabling a handoff server to proactively advertise new points of access and their associated security mechanisms to devices before connectivity is lost. As a result, devices may seamlessly transition between secure networks. Stateful monitoring of device reachability may be used together with device certificates and / or tokens to decrease the potential of MAC spoofing and further secure the network. Stateful monitoring of device connectivity status during network transitions facilitates the identification of rogue access points. The token or certificate on the device may be used to authenticate the device while transitioning between networks by a centralized entity, managing the initiation and the execution of the handover for the device.
Owner:APPLE INC
Secure access control method and device for wireless network
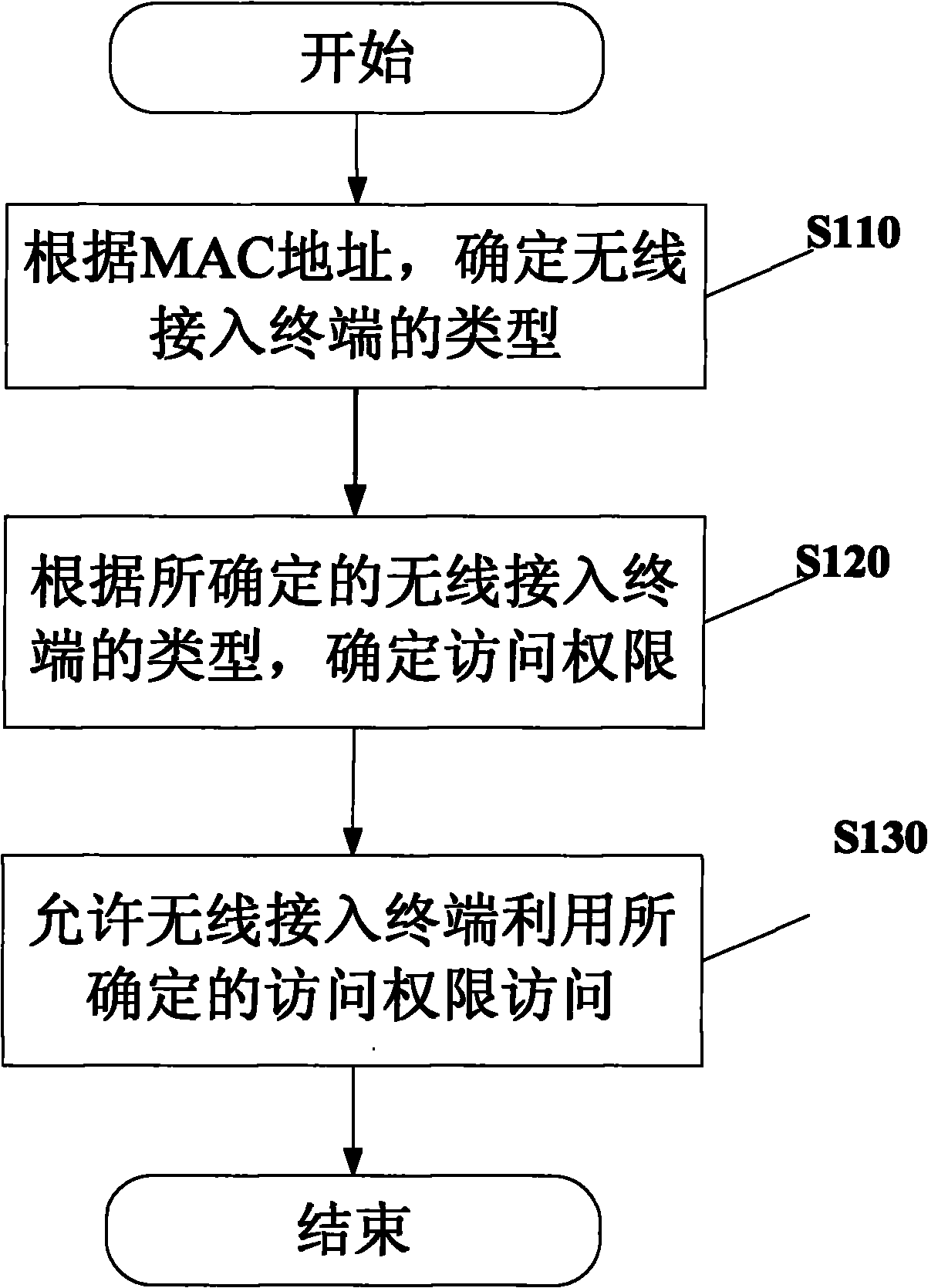
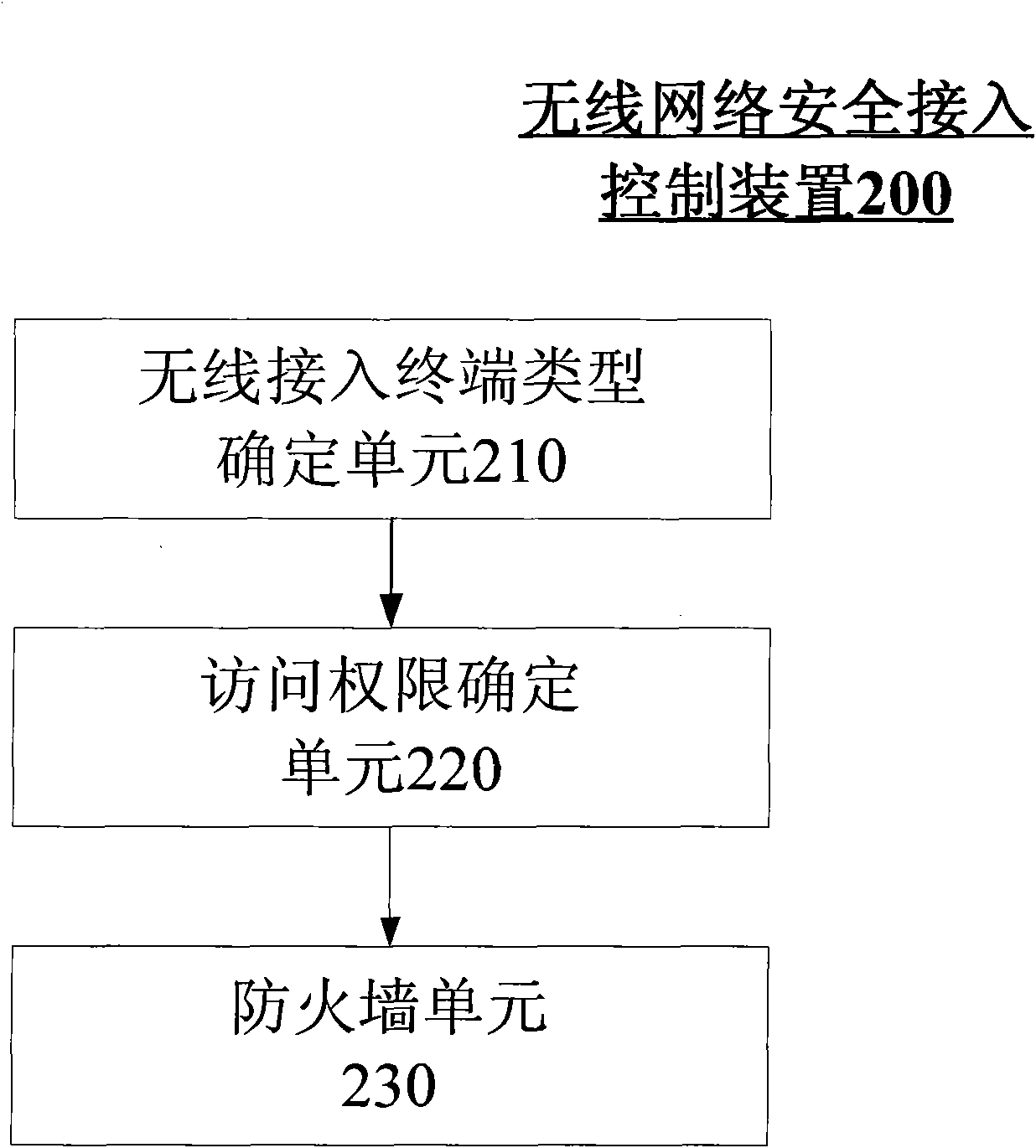
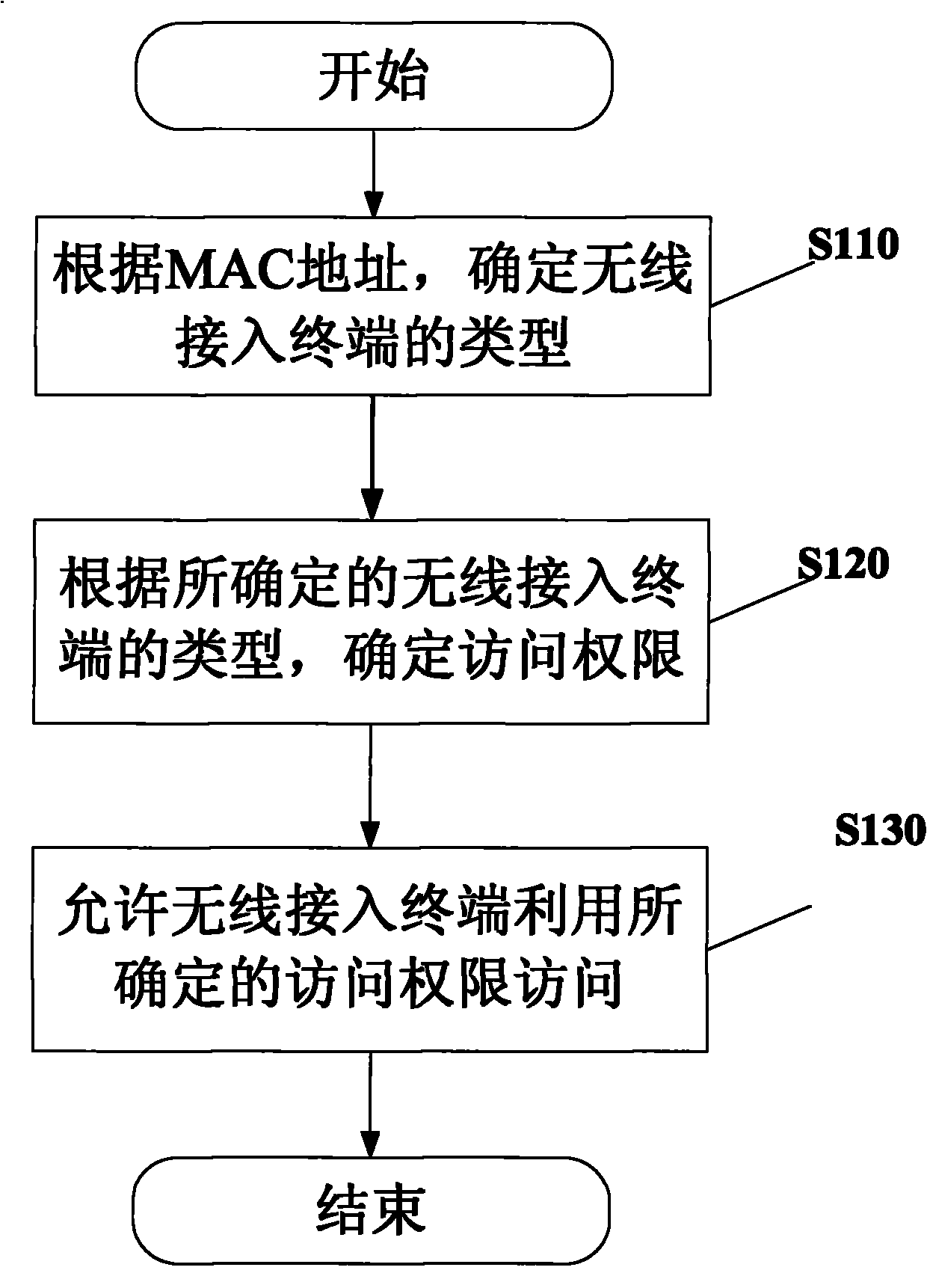
ActiveCN101909298AGuaranteed to be trustedFlexible Access RightsSecurity arrangementMedia access controlClient-side
The invention provides a secure access control method for a wireless network, which comprises the following steps of: confirming the type of a wireless access terminal according to an MAC (Media Access Control) address of the wireless access terminal; confirming the access permission of the wireless access terminal by utilizing a preset firewall policy according to the type of the confirmed wireless access terminal; and allowing the wireless access terminal to access a network with access permission by utilizing the confirmed access permission. The secure access control method for a wireless network can ensure that the client ends carry out access by the wireless network are trusty and can be used for establishing more flexible access permission according to a role of the client end, thereby meeting the legal access requirements of various roles in different environments and filtering and blocking an illegal unauthorized access request.
Owner:UCWEB
Multi-channel high-speed data processor and processing method
InactiveCN1889503AReduce the burden onImprove efficiencyNetwork traffic/resource managementStore-and-forward switching systemsProgrammable read-only memoryData information
A method for processing multichannel high-speed data includes issuing read / write information and data information by network processor and obtaining said information by queue dispatch module, carrying out relevant write operation on buffer area by receiving module after it receives write command from queue dispatch module then sending processed data to frame calibration-sequence module and sending calibrated data to data buffer storage module, writing data in buffer area and outputting data by operating buffer area. The processor of multichannel high-speed data is also disclosed.
Owner:SOUTHEAST UNIV
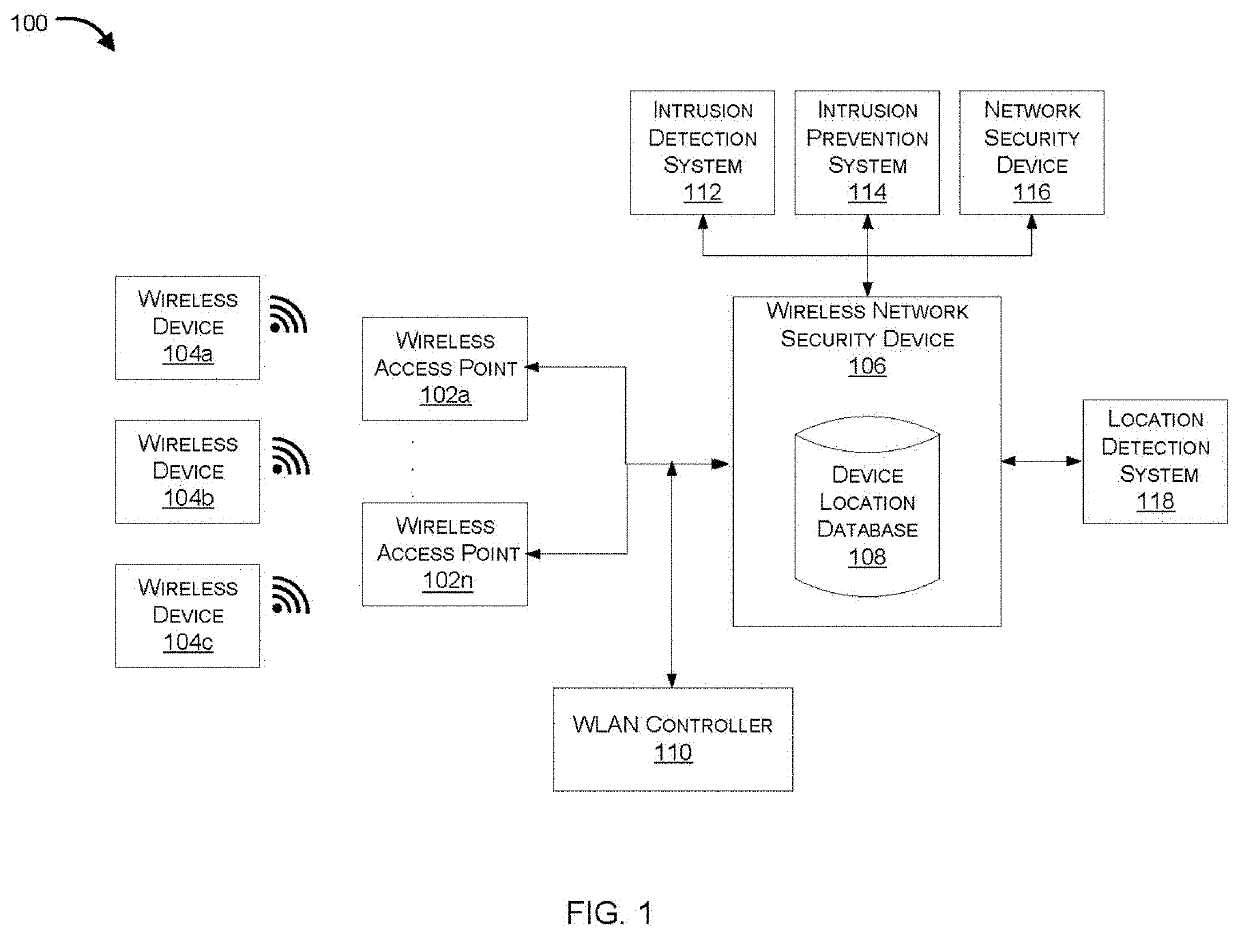
Intrusion detection in a wireless network using location information of wireless devices
Systems and methods for detecting and / or preventing intrusions in a wireless network based on location information of wireless devices are provided. According to one embodiment, a database is maintained by a wireless network security system that includes historical location information and a media access control (MAC) address for multiple wireless devices observed by wireless access points (APs) of a wireless network of an enterprise. Information regarding one or more probe signals originated by a wireless device of the multiple wireless devices is received by the wireless network security system from the multiple APs. A location of the wireless device is determined by the wireless network security system based on the information. A potential attack being conducted by the wireless device or in which the wireless device is involved is identified based on one or more of behavior exhibited by the wireless device, the location and the database.
Owner:FORTINET
Multi-user reinforcement learning-based cognitive wireless network anti-hostile interference method
ActiveCN104994569AImprove communication efficiencyImprove signal to interference ratioPower managementTransmitted powerNetwork packet
The invention relates to wireless network security, particularly to a multi-user reinforcement learning-based cognitive wireless network anti-hostile interference method. Cognitive source nodes adopt a multi-user reinforcement learning strategy to automatically select transmitted power by observation of status information of a master user working condition, self-adaptive jammer transmitted power and the like. Learning of multiple cognitive source nodes is performed at the same time, and each time transmission of a data packet is finished, according to obtained immediate returned report and a state of the next moment, an update state, a behavior and a mapping relation, and according to feedback information, the learning rate of the multi-user reinforcement learning algorithm is replaced, thereby improving the signal to interference ratio of a receiving end, and finally obtaining the optimal transmitted power. Each cognitive source node can assist forwarding of the data packet or transmit data by itself. The method utilizes a multi-user reinforcement learning mechanism, and through a method of attempting and comparison, improves communication efficiency of a cognitive wireless network in a scene of an intelligent hostile jammer.
Owner:XIAMEN UNIV
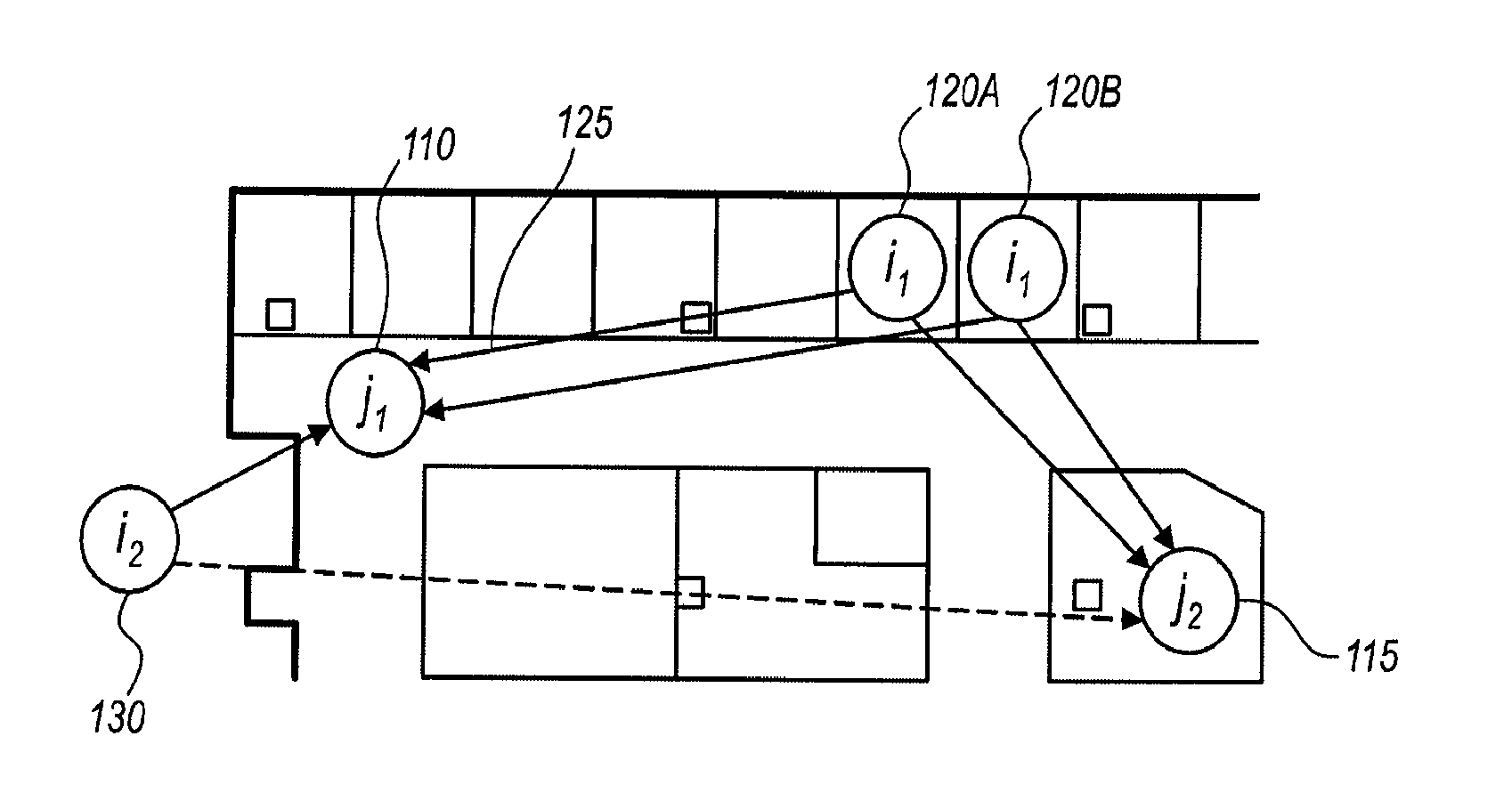
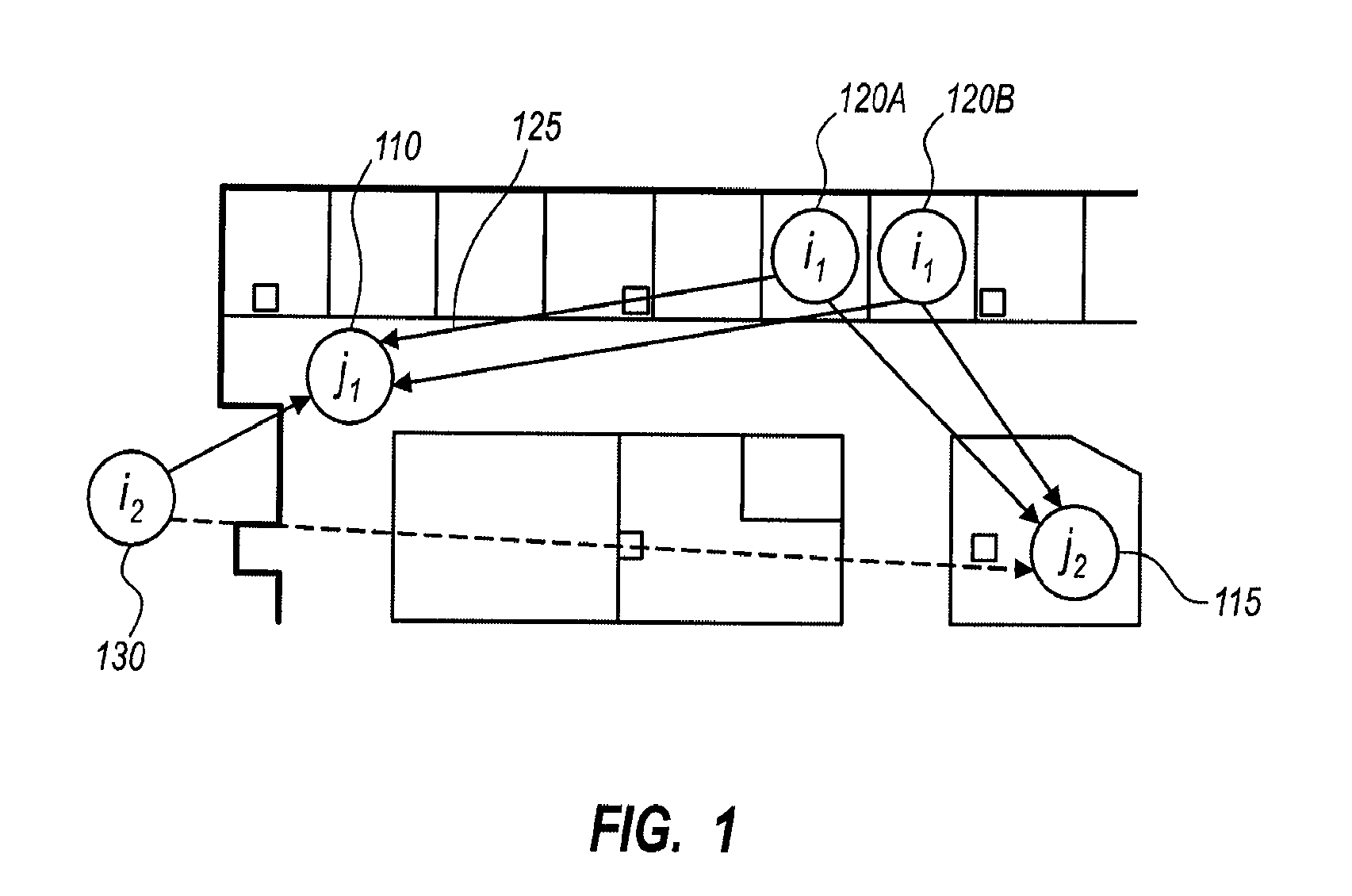
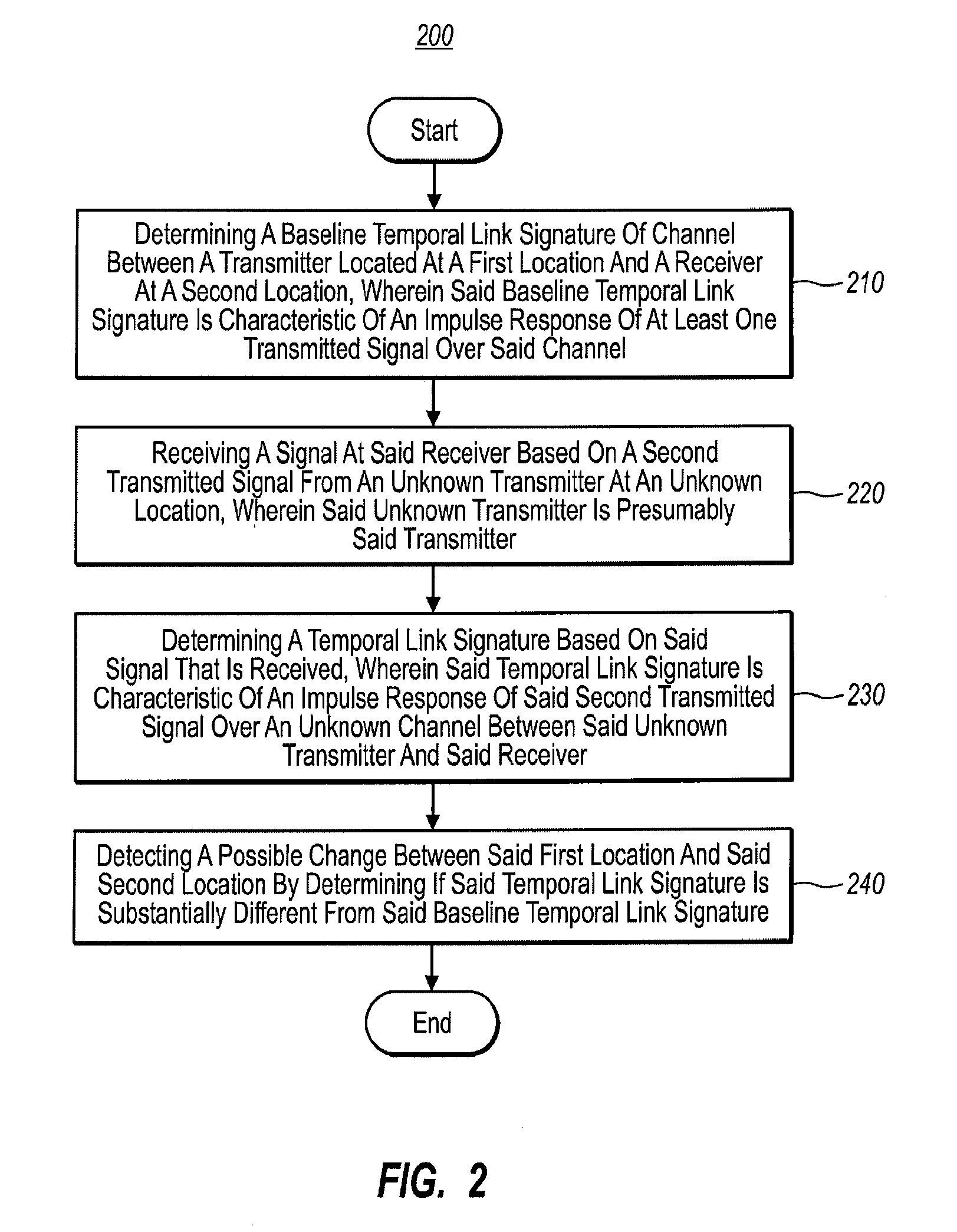
Robust Location Distinction Using Temporal Link Signatures
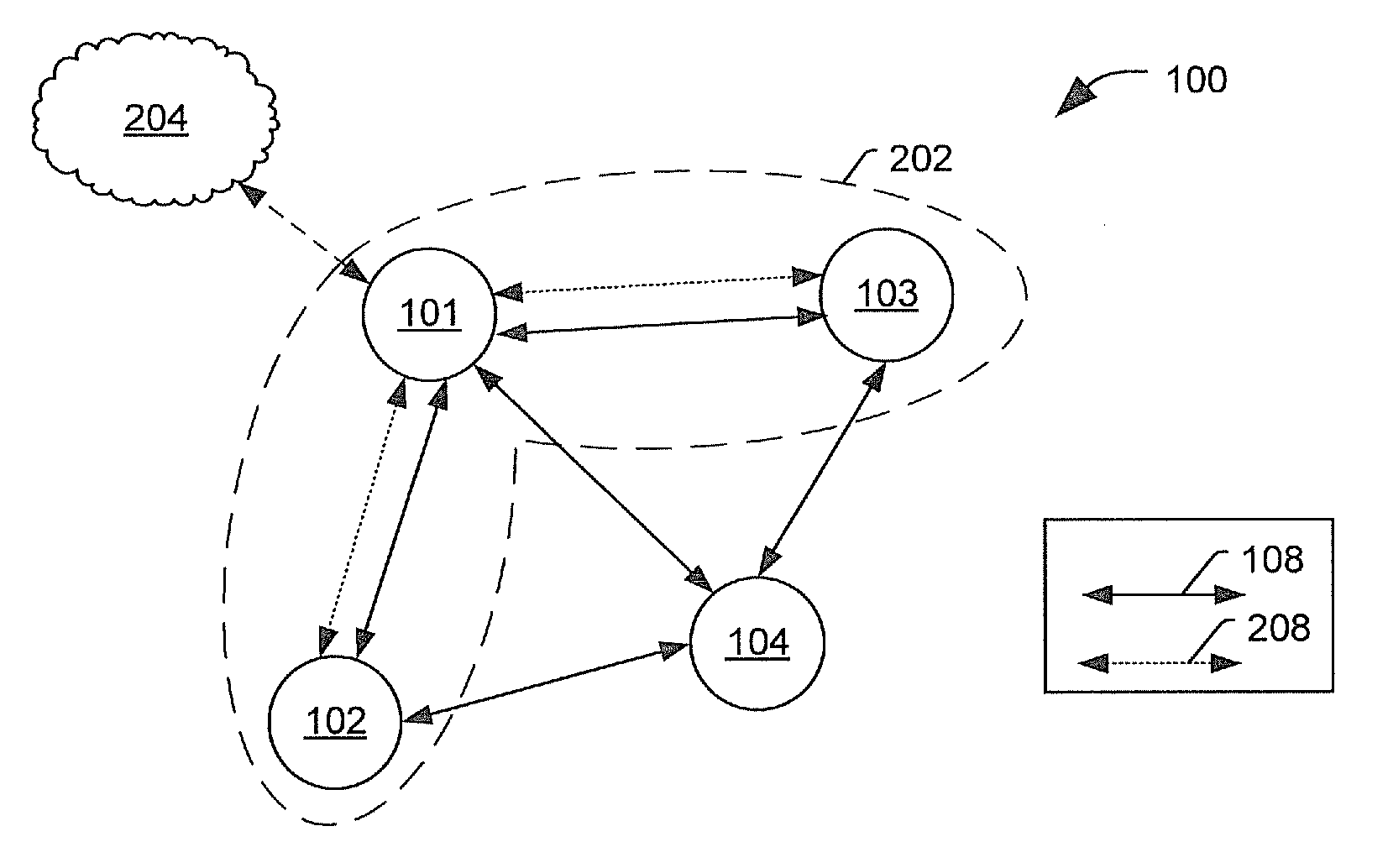
The ability of a receiver to determine when a transmitter has changed location is important for energy conservation in wireless sensor networks, for physical security of radio tagged objects, and for wireless network security in detection of replication attacks. In embodiments of the present invention, a measured temporal link signature is determined to uniquely identify the link between a transmitter and a receiver. The temporal link signature is an impulse response of a transmitted signal from the transmitter over a channel between the transmitter and a receiver over a channel. When the transmitter changes location, or if an attacker at a different location assumes the identity of the transmitter, the proposed link distinction methodology reliably detects the change in the physical channel. This detection can be performed at a single receiver or collaboratively by multiple receivers.
Owner:UNIV OF UTAH RES FOUND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com