Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
180 results about "CIPURSE" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
CIPURSE is an open security standard for transit fare collection systems. It makes use of smart card technologies and additional security measures.
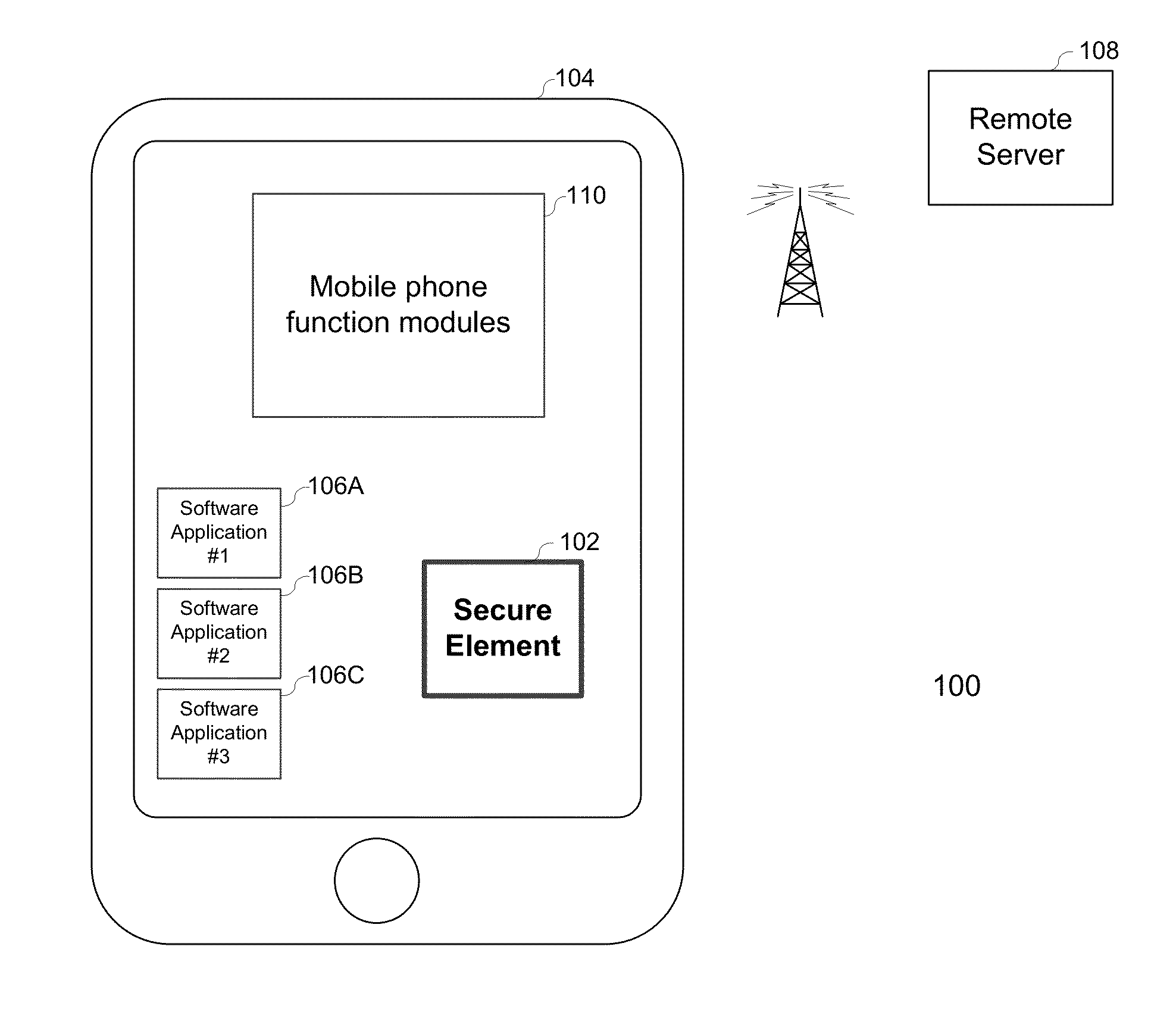
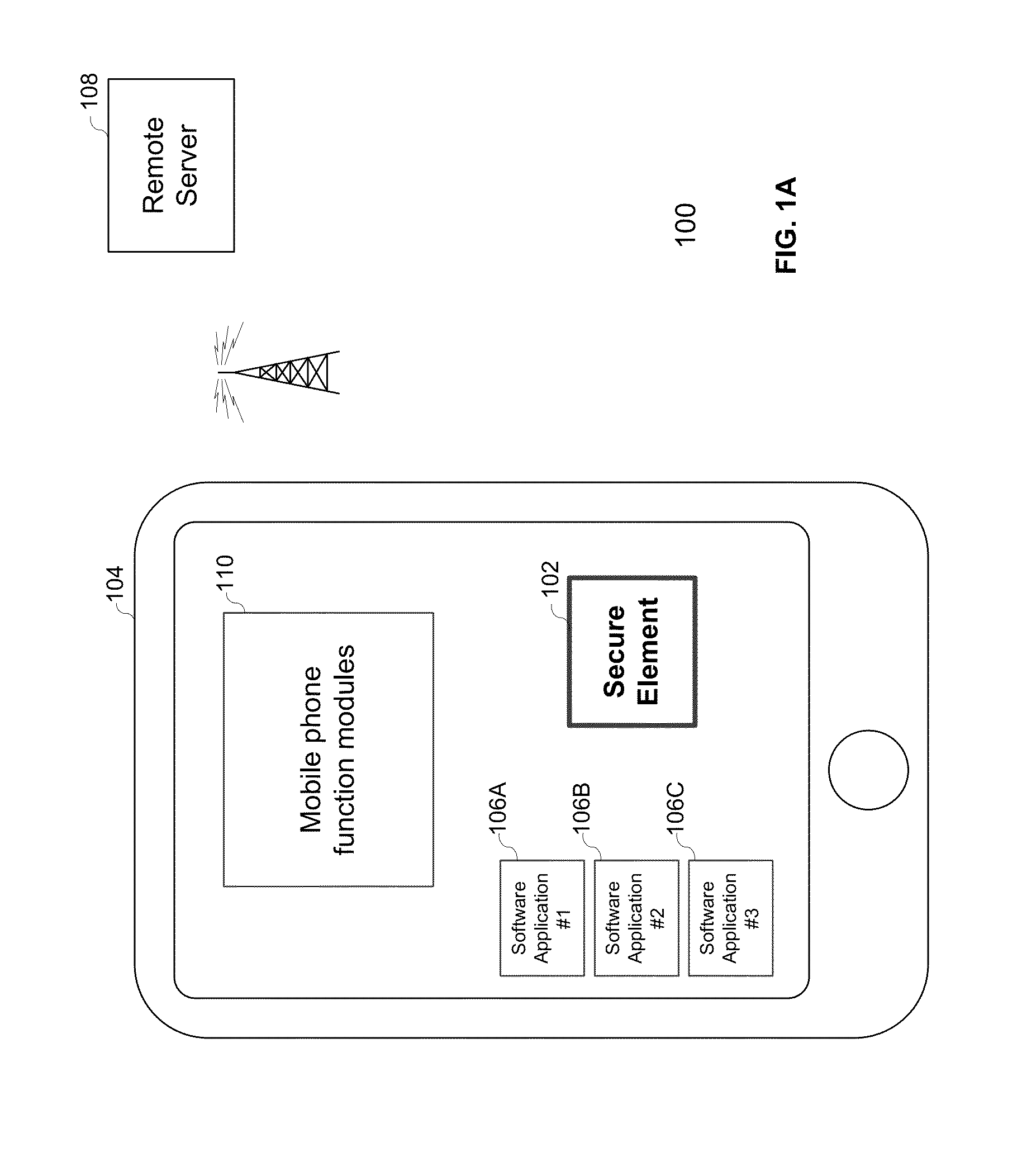
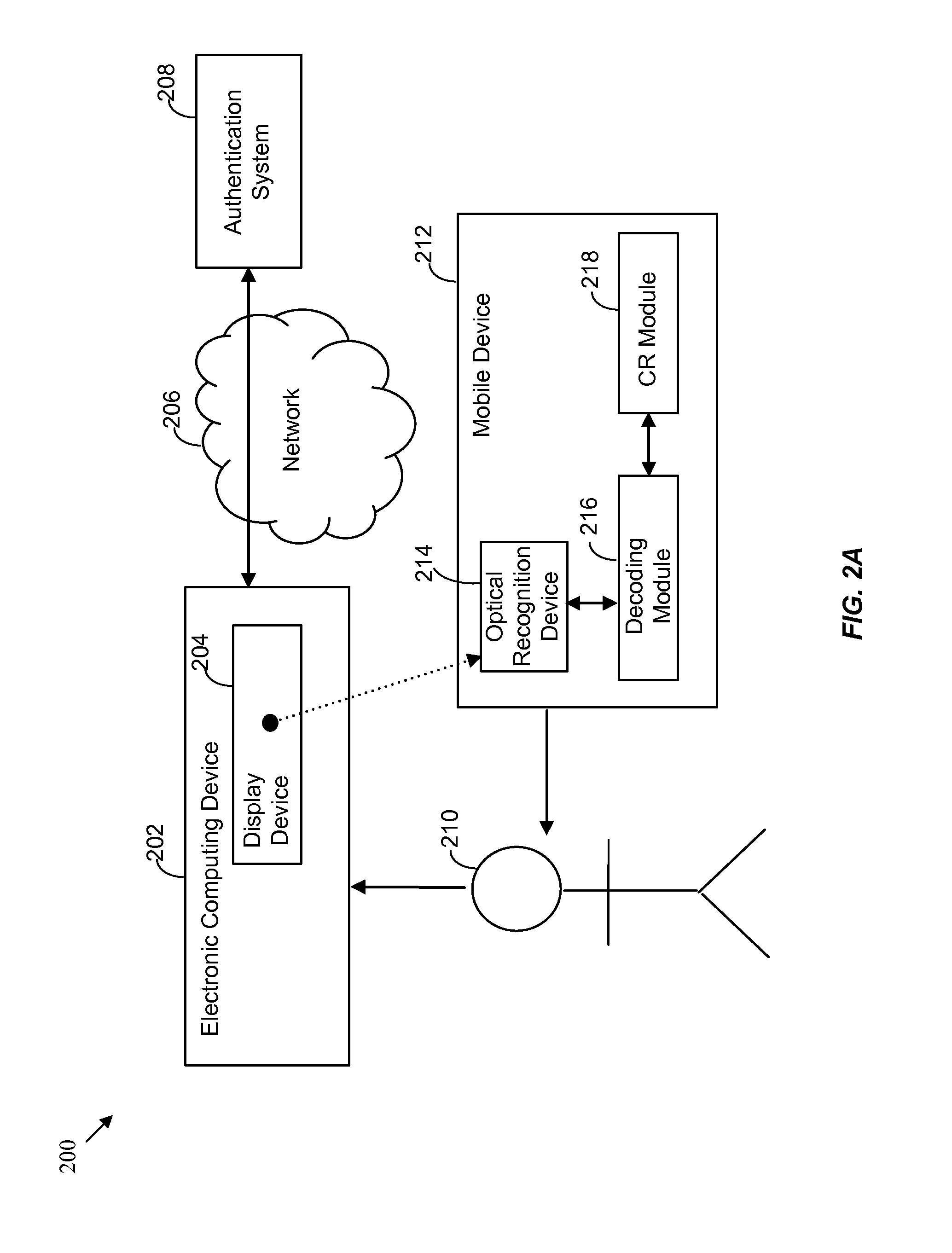
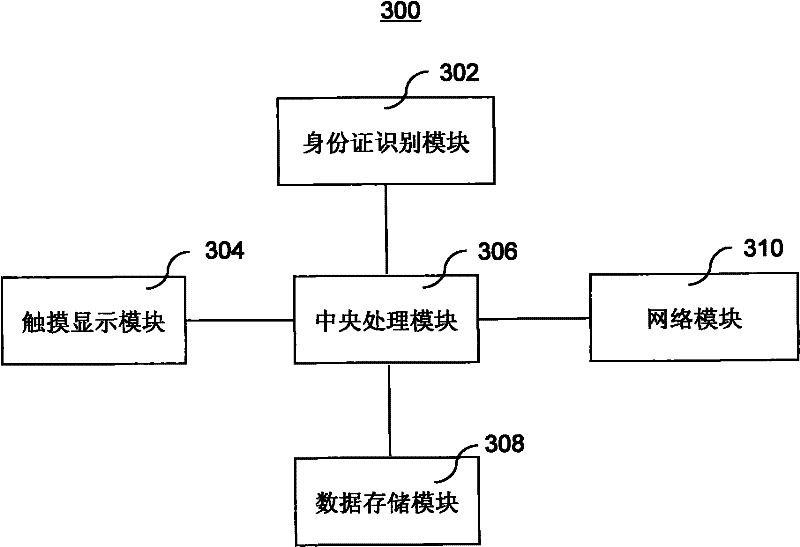
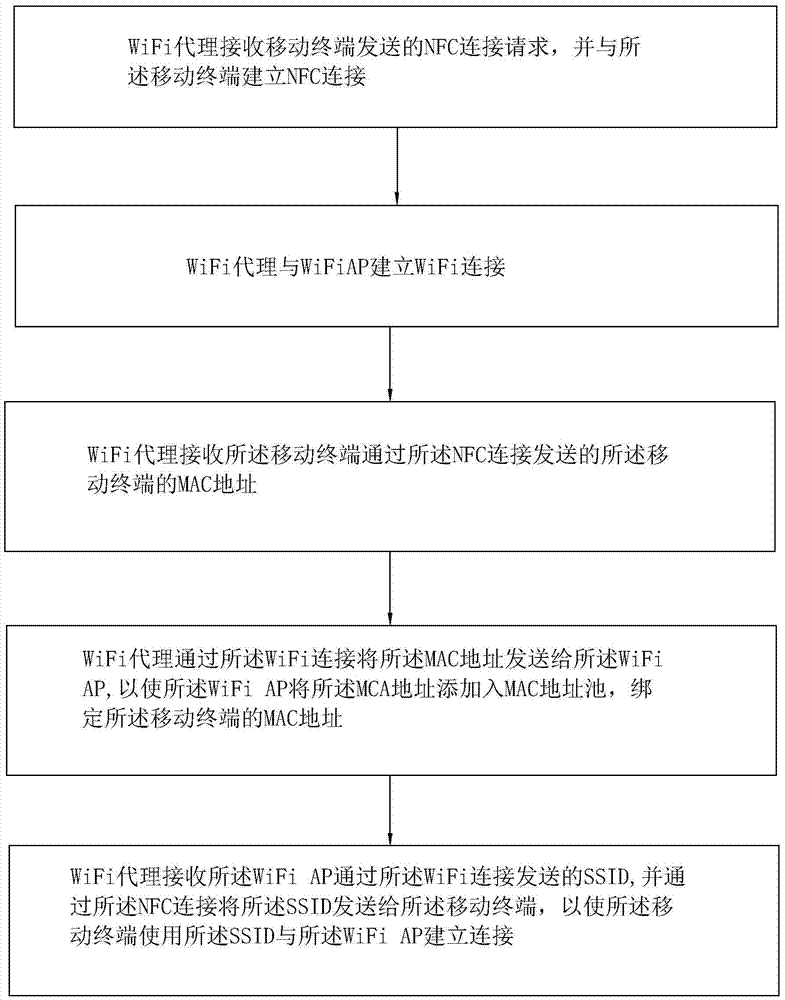
Embedded secure element for authentication, storage and transaction within a mobile terminal
ActiveUS20140013406A1Improve security levelImprove securityNear-field transmissionDigital data processing detailsEmbedded securityApplication software
Various embodiments of the present invention relate to incorporating an embedded secure element into a mobile device, and more particularly, to systems, devices and methods of incorporating the embedded secure element into a mobile device for identity authentication, data storage and processing in trusted transactions. These trusted transactions require a high security level to protect sensitive data or programs in bank account management, purchasing orders, contactless payment, passport verification, and many other high-security applications. The secure element will provide a root of trust such that that applications running on the mobile device are executed in a controlled and trusted environment. In addition to conventional password or encryption protection, alternative security features are introduced from both software and hardware levels based on the embedded secure element. Therefore, the security level of the mobile device is not only enhanced, but also may potentially exceed that of the conventional POS terminals.
Owner:MAXIM INTEGRATED PROD INC
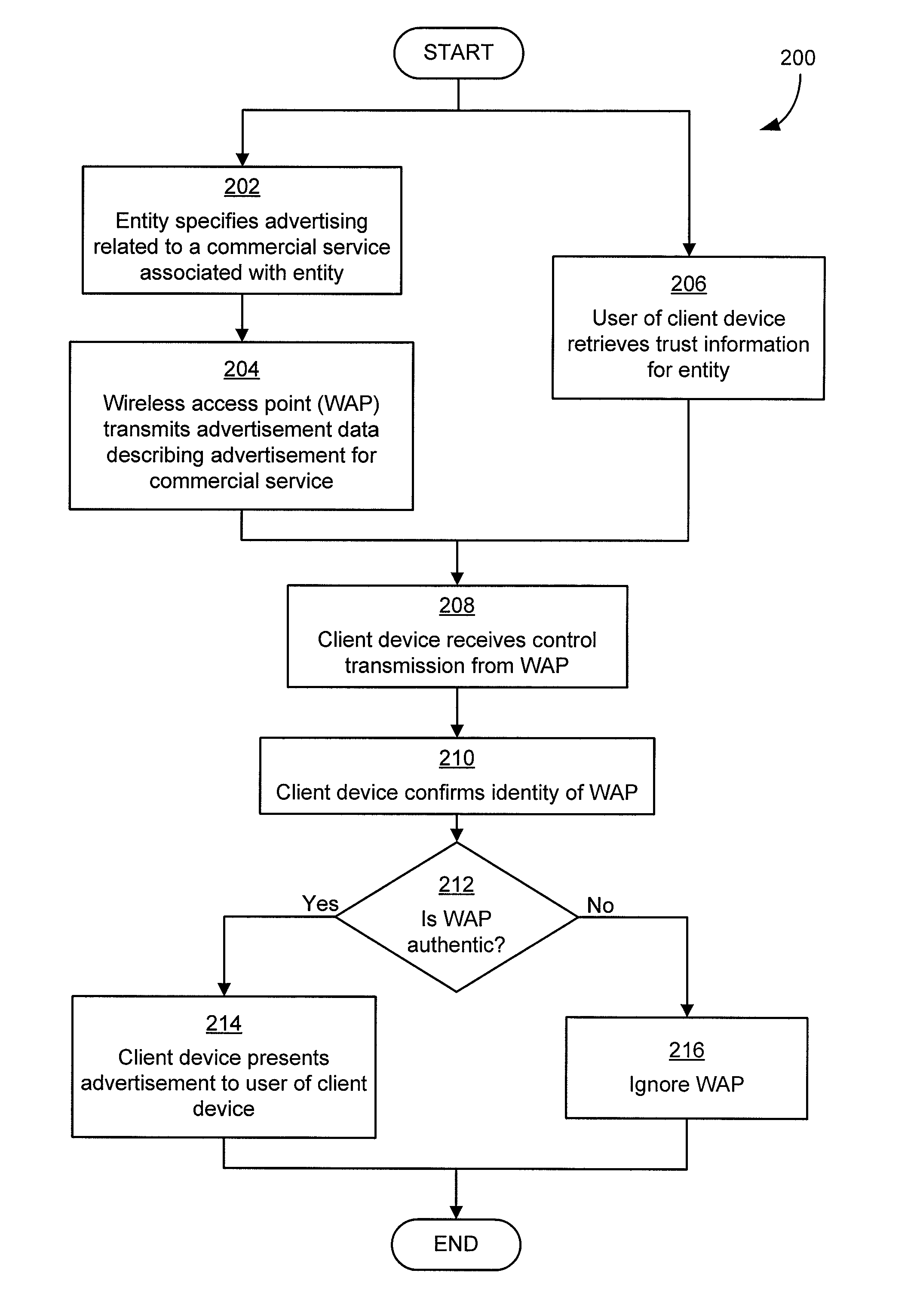
Authentication mechanisms for wireless networks
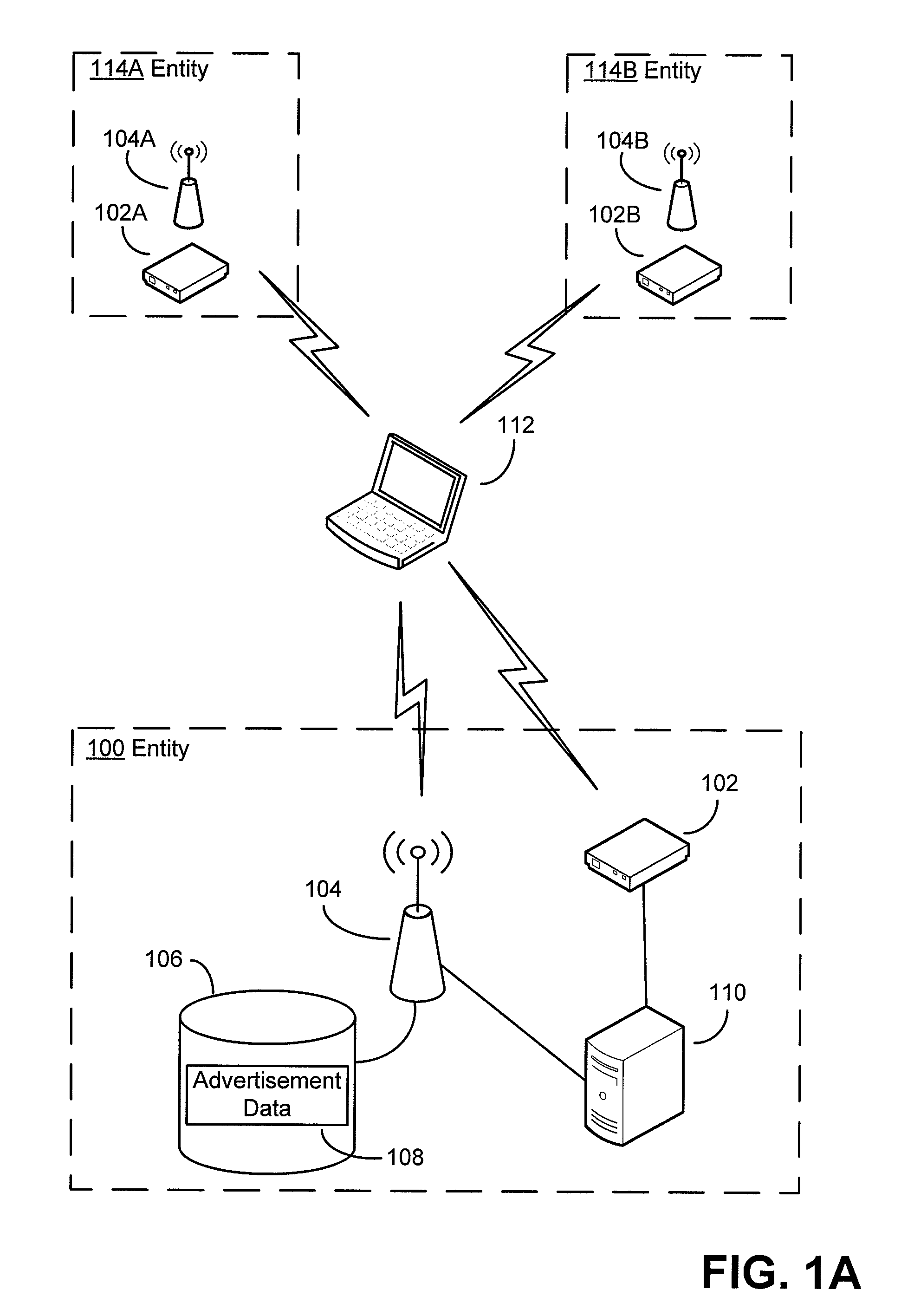
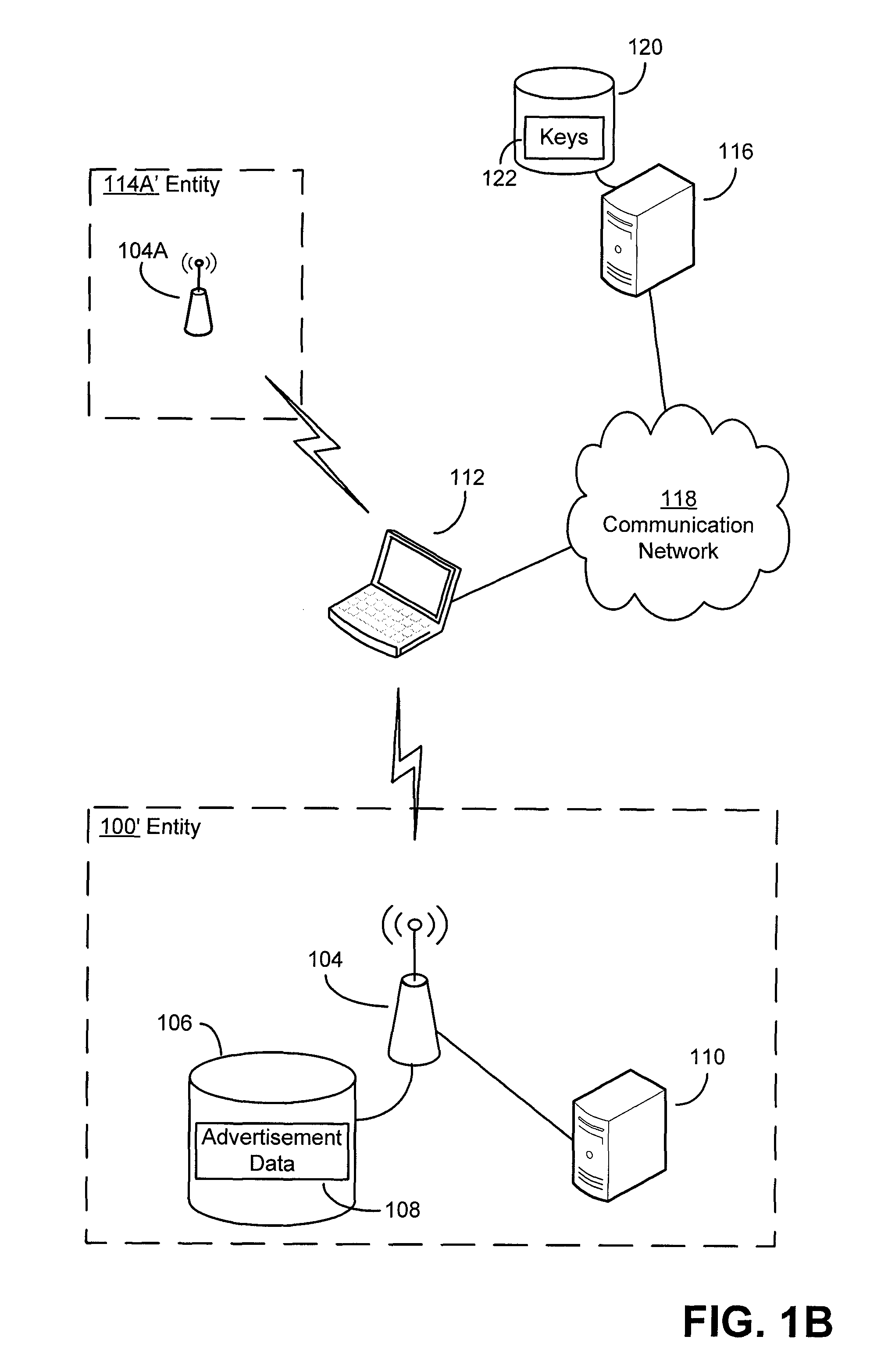
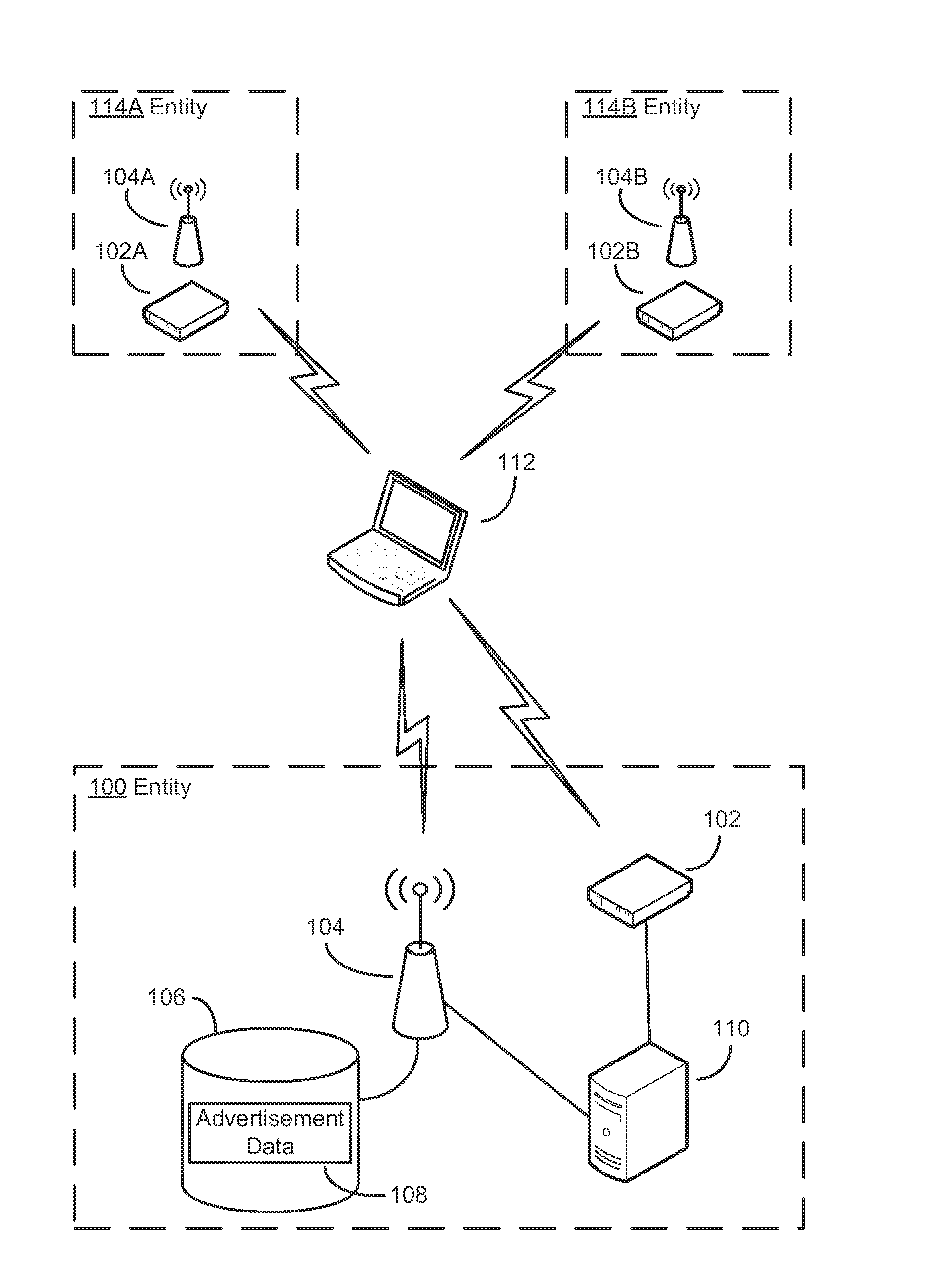
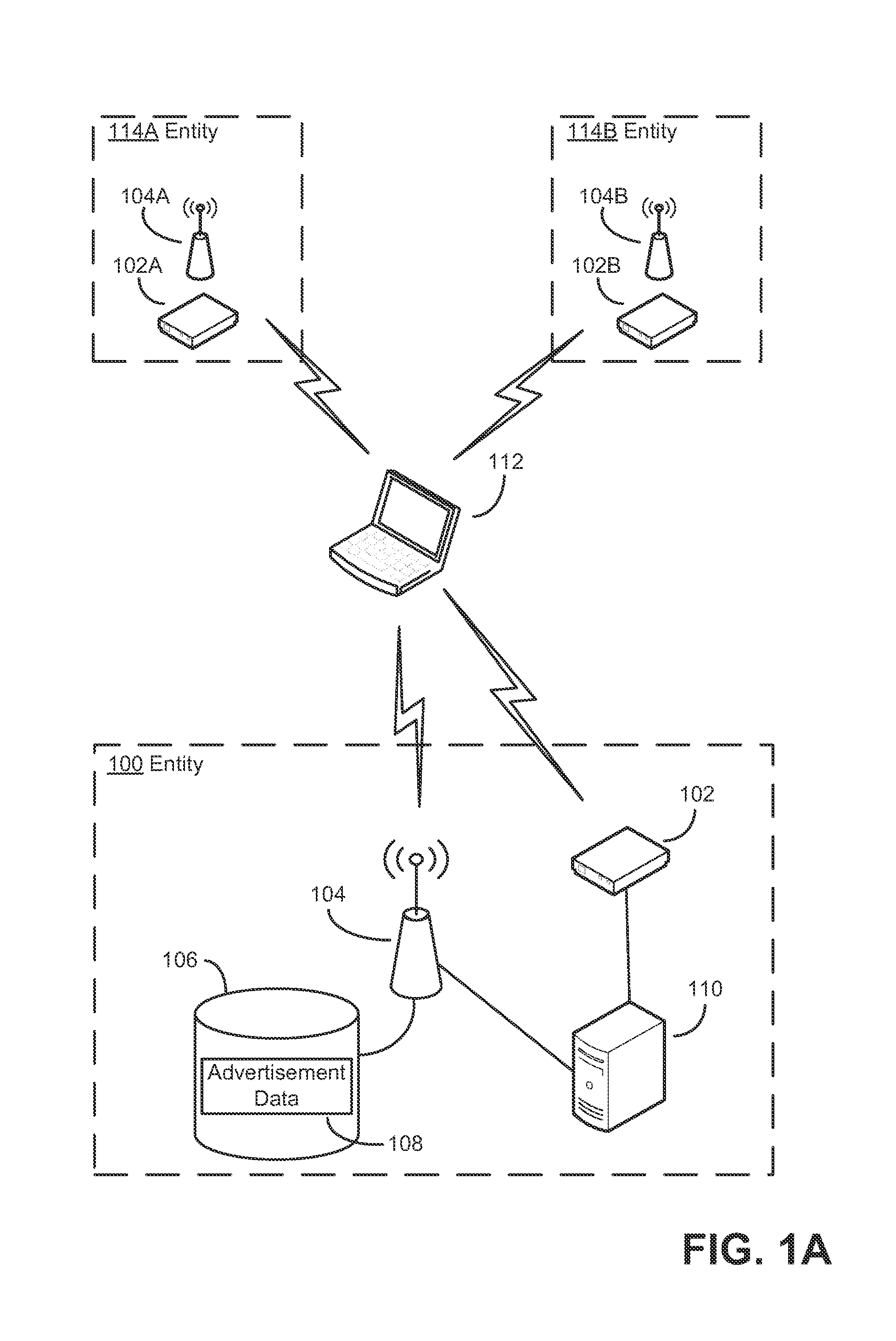
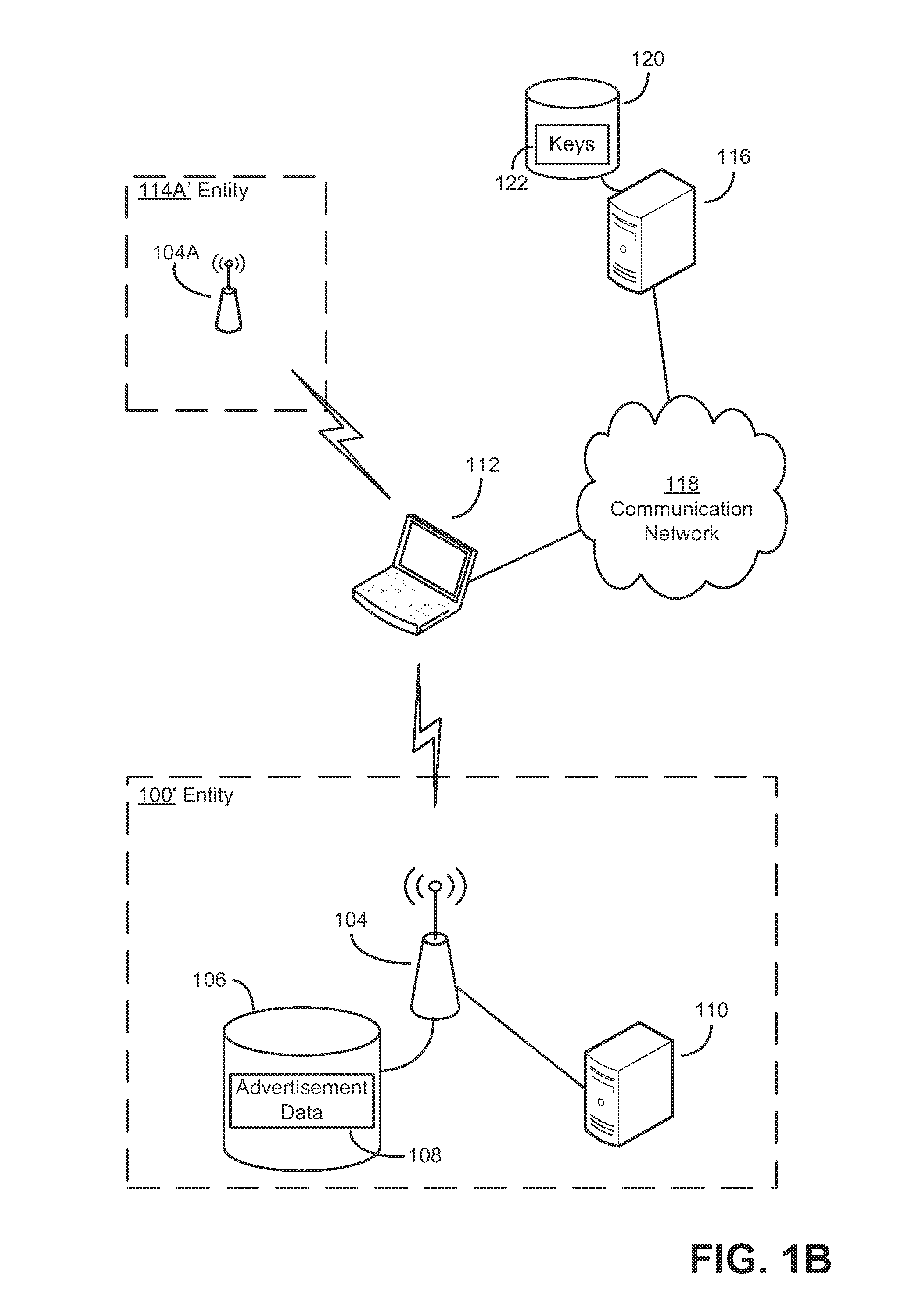
Security techniques and security mechanisms for wireless networks that transmit content such as advertisements. According to exemplary techniques, control messages comprising unrequested content (e.g., advertisement data) may be transmitted in response to a request from a client device, while in other exemplary techniques the control messages may be transmitted without any request from a client device. In some exemplary implementations, security mechanisms such as public key cryptography algorithms may be used to secure transmissions. In some of these techniques which implement public key cryptography, a user may be required to retrieve a public key from a source other than the wireless access point transmitting encrypted advertisements (e.g., a sign or terminal in a commercial entity transmitting such advertisements, or from a web service), such that the user may confirm that the encrypted content is from a source matching the retrieved public key and thus confirm the authenticity of a wireless access point.
Owner:MICROSOFT TECH LICENSING LLC
Authentication of a client using a mobile device and an optical link
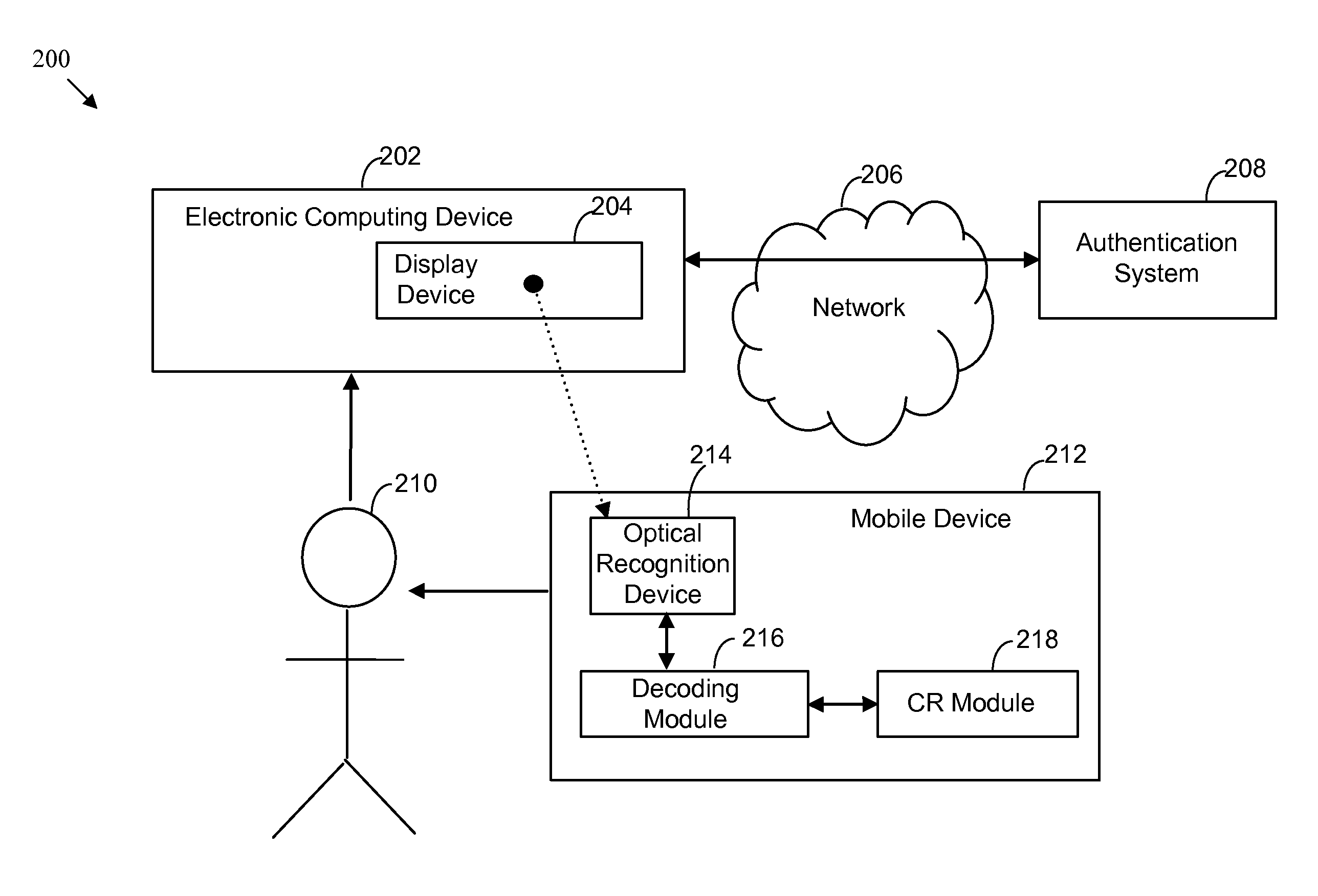
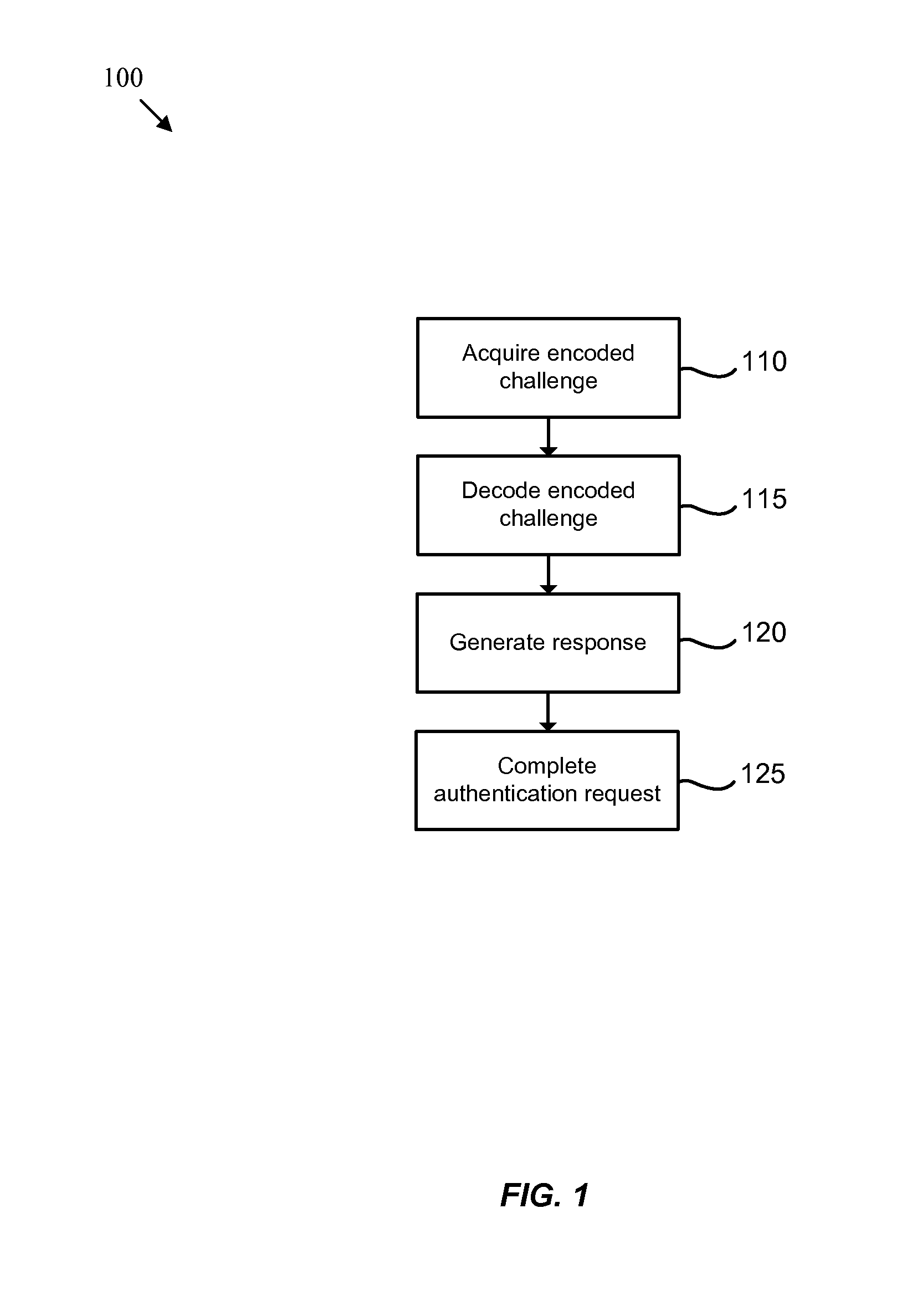
ActiveUS8661254B1Digital data processing detailsUser identity/authority verificationAuthentication serverApplication software
Systems and methods for enhancing the convenience, reliability and security of transactions are provided. In authenticating a user attempting to engage in a transaction, a machine-readable indicia may be optically acquired and a challenge derived therefrom sent to a one-time password (OTP) application running on a mobile or other device. The device may then generate a response OTP using, at least in part, the derived challenge. The response may be read by a user and used in-band or may alternatively be sent by the mobile device out-of-band to an authentication server, which may respond with an authentication response operable to authenticate the user.
Owner:CA TECH INC
Intelligent locking system, and system and method for renting public bike based on same
InactiveCN105243752ARealize intelligent controlMake an appointment in advanceApparatus for meter-controlled dispensingIndividual entry/exit registersPasswordComputer module
The invention discloses an intelligent locking system, and a system and a method for renting public bikes based on the system, and belongs to the field of intelligent electronic locks. The intelligent electronic lock system comprises an intelligent lock, an intelligent lock master control platform, and a mobile terminal. The intelligent lock comprises a power module and an intelligent lock body. The intelligent lock body is internally provided with a control master control chip. The surface of the intelligent lock is provided with an intelligent two-dimension code label used to uniquely identify the intelligent lock. The intelligent lock body is also internally provided with a mobile communication module and a controller module used to control password generation of the intelligent lock. The intelligent lock master control platform comprises a background monitoring server. The intelligent lock is connected with the background monitoring server through the mobile communication module, and the mobile terminal is connected with the background monitoring server in a communication manner. Using the intelligent locking system can realize non-contact intelligent control on an intelligent lock. The system and method for renting public bikes based on the intelligent locking system make bike renting of users no longer limited in fixed bike piles, one-key bike renting and returning can be realized at any time, and requirement of users is preferably satisfied.
Owner:北京骑思妙享科技有限公司
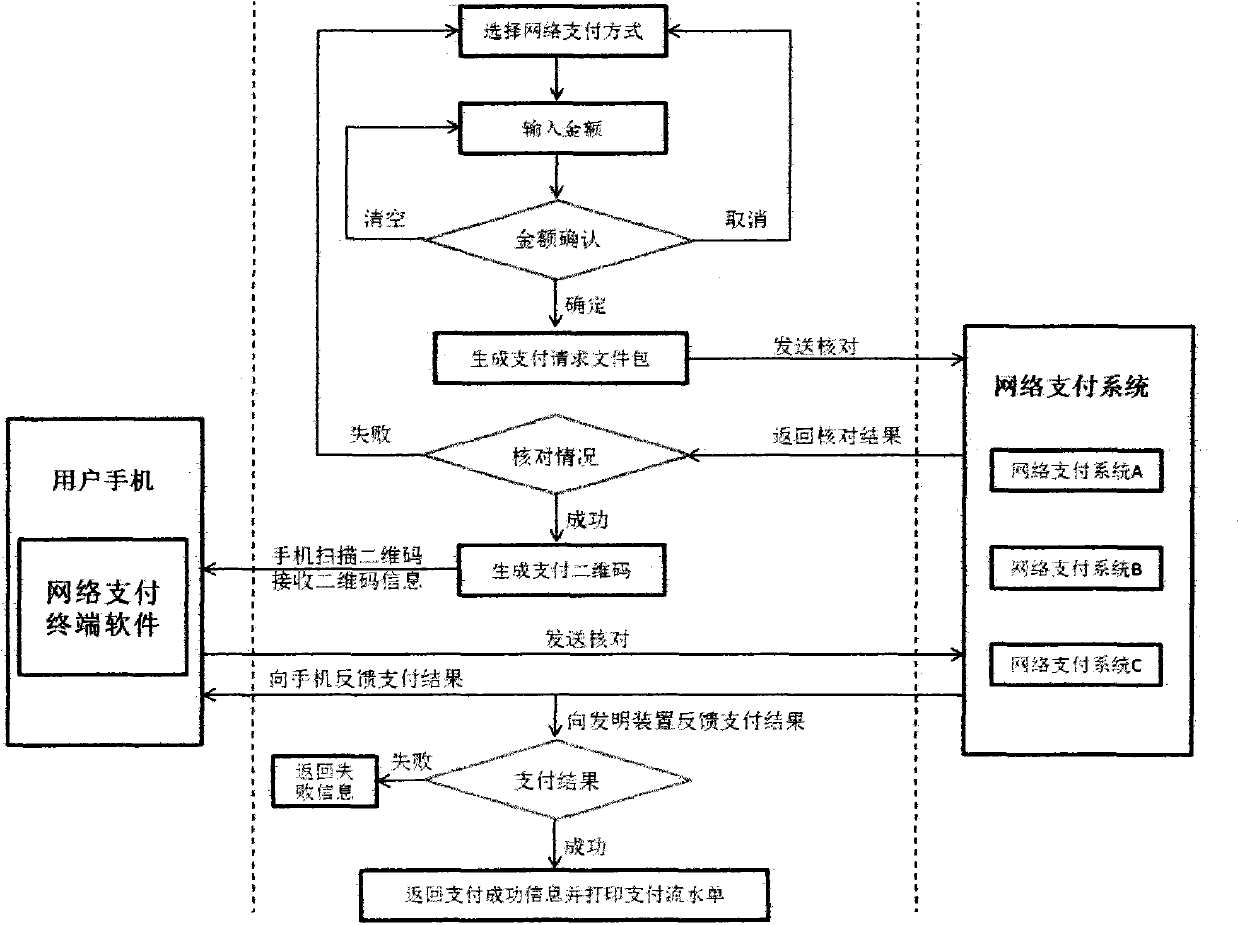
Online payment method and system thereof
ActiveCN103679445ARealization of card-not-present paymentGood application basisPayment architectureUser inputPassword
The invention discloses an online payment method. The online payment method is characterized by comprising steps of: (1) being associated with a plurality of online payments accounts of businesses; (2) allowing the businesses to select a method of payment and enter an amount according to an online payment system selected by users; (3) generating a two-dimension code; (4) allowing the users to scan the two-dimension code and pay by an online payment software on a mobile phone and enabling the online payment system to feed back results of completed payments to a terminal system when the users enter a password and complete the payments; (5) printing out the running information of the results of the completed payments, wherein a payment request comprises a payment amount, a product name and a payment account. The invention further discloses an online payment system. The online payment method and the system thereof has the advantages of being available to card-not-present payments, safe and convenient in operation and capable of using two-dimension codes scanned by mobile phones to achieve online payments.
Owner:YUNNEX TECH
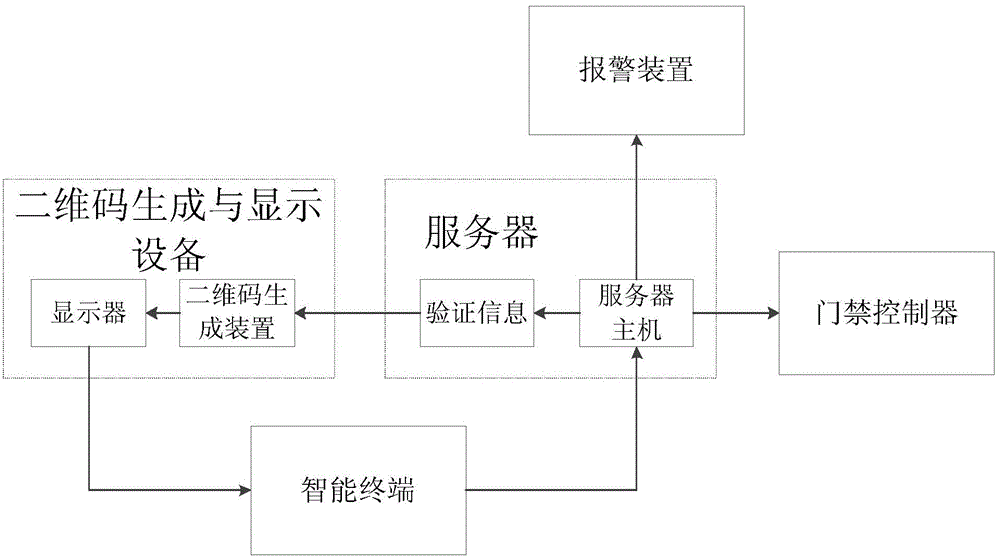
Access control system based on intelligent terminal and control method of access control system
InactiveCN104318647AReduce forgetting to carryReduce the use effectIndividual entry/exit registersPasswordDisplay device
The invention discloses an access control system based on an intelligent terminal and a control method of the access control system. The system sends verification information to a two-dimension code generation and display device by use of a server host; the intelligent terminal scans a two-dimension code generated by the two-dimension code generation and display device and a user performs validation; after validation, the validated information is sent to the server host for comparison validation; after the comparison validation is successful, the server host sends a door opening signal code to an access control controller to open the door; and if the comparison validation fails, the server host sends validation failure information to a display. The access control system based on the intelligent terminal has the advantages that a key, an access control card or other articles cannot be required so that the trouble caused by forgetting carrying or wrong use can be reduced, such input devices as a coded lock or a fingerprint lock do not need to be arranged and the functions can be completed by use of the carried intelligent terminal, and therefore, the instability or damage of the existing coded lock or fingerprint lock device due to long-term touch is avoided, and the trouble of manual password change of the existing coded lock is avoided.
Owner:CHANGAN UNIV
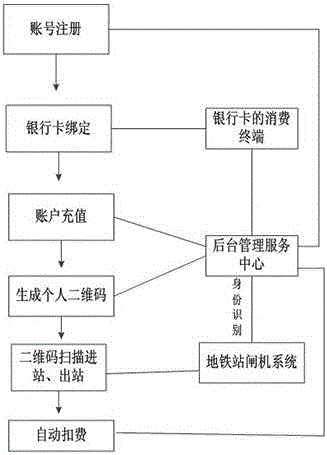
Subway taking method based on electronic purse
InactiveCN106296293ASave time buying ticketsNo congestionPayment architectureMarketingBarcodeCIPURSE
The invention discloses a subway taking method based on an electronic purse. The subway taking method based on the electronic purse comprises the following steps: (1) account number registration, to be specific, registering an account number in electronic purse application software and setting payment codes by a passenger; (2) bank card binding, to be specific, logging into the electronic purse by the passenger according to the login account number to bind the bank card; (3) account number recharging, to be specific, confirming the recharging amount of money in the electronic purse by the passenger after binding the bank card successfully; (4) generating a personal two-dimensional barcode, to be specific, generating the personal two-dimensional barcode by the electronic purse application software after successful recharging; (5) getting in a station and leaving the station by scanning the two-dimensional barcode, to be specific, finding the two-dimensional barcode in the electronic purse application software of a mobile device by the passenger, and scanning the personal two-dimensional barcode at the entrance and exit gates of subways; and (6) automatic fee deduction, to be specific, automatically deducting fee according to disbursement calculated by a payment and settlement center after verifying the identity of the passenger by using a backstage management service center.
Owner:仁通融合(南京)信息技术有限公司
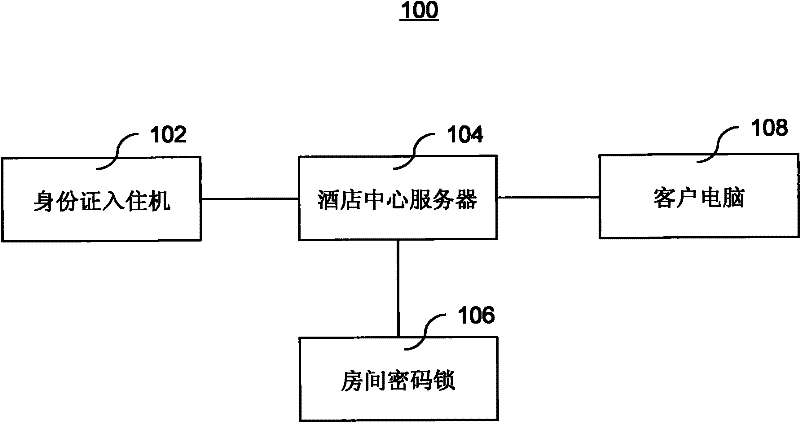
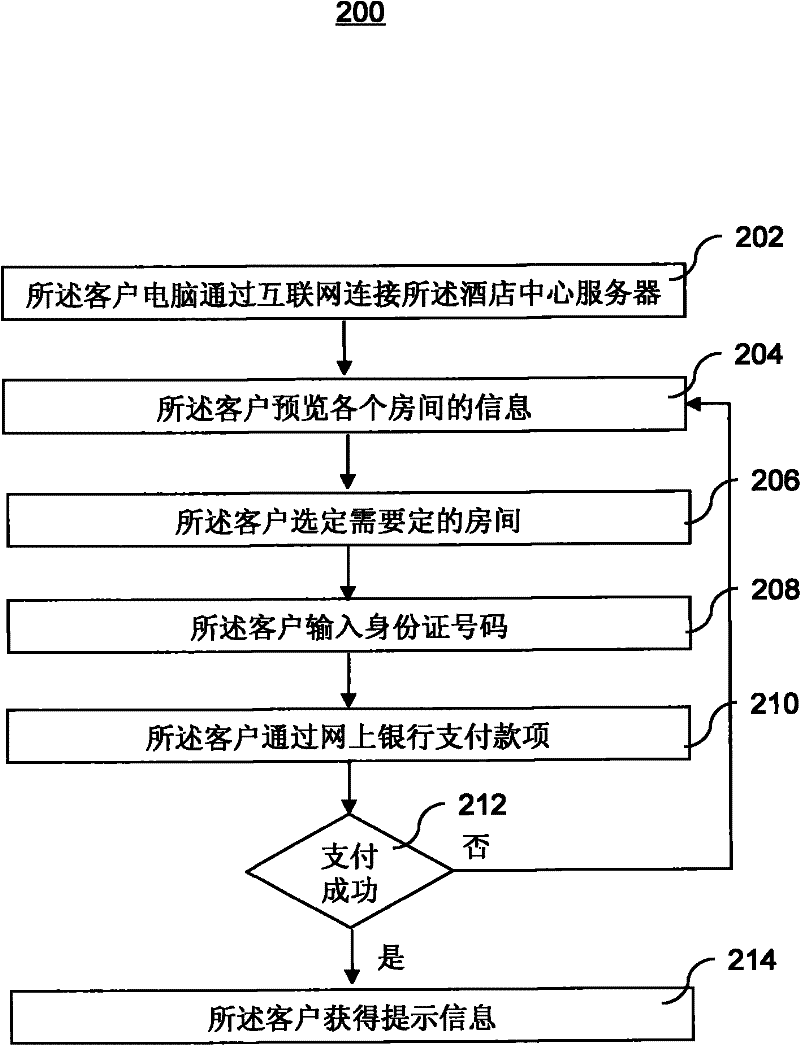
A hotel self-check-in system
InactiveCN102262801ASimple technologyEasy to implementApparatus for meter-controlled dispensingSensing record carriersPasswordControl room
The invention discloses a hotel self-check-in system. The system comprises: an ID card check-in machine, which completes self-check-in according to the customer's ID card information and the reservation information associated with the ID card; After the customer makes a successful reservation, save the customer's ID card information and reservation information and share it with the ID card check-in machine; and the room password lock, which is set by the hotel center server, and the customer can use the password to open the room during the reservation time period. For the reserved room, compared with the prior art, the present invention uses the ID card as the identification medium, and controls the opening of the room through the room code lock. The technology is simple, the cost is low, and the specific use effect is good.
Owner:无锡市美普索特电子科技有限公司
Control system of smart lock of mobile internet and control method thereof
InactiveCN103813142AQuick access to valid evidenceEasy networkingTransmission systemsClosed circuit television systemsData acquisitionEmbedded system
The invention relates to a smart lock, in particular to a control system and method of the smart lock having remote control, alarm receiving and monitoring functions, and discloses a control system of the smart lock of a mobile internet and a control method thereof. The control system comprises a fingerprint coded lock module, a photographing and data collection server module and a smart terminal processing module. Communication between the fingerprint coded lock module and the smart terminal processing module is achieved through connection via a data line or through wireless transmission via a wireless communication module. Communication between the photographing and data collection server module and the smart terminal processing module is achieved by accessing the internet via a wired or wireless connection module. Accordingly, a both-way communication system is built through communication connection between the smart terminal processing module with the photographing and data collection server module and the fingerprint coded lock module, and the use status of the smart lock can be monitored in real time and the smart lock can be operated in a long distance. The invention further discloses the control method of the control system. The smart lock is enabled to have various functions such as movement and remote alarming, and is simple and convenient to operate and easy to popularize.
Owner:劳海鹏
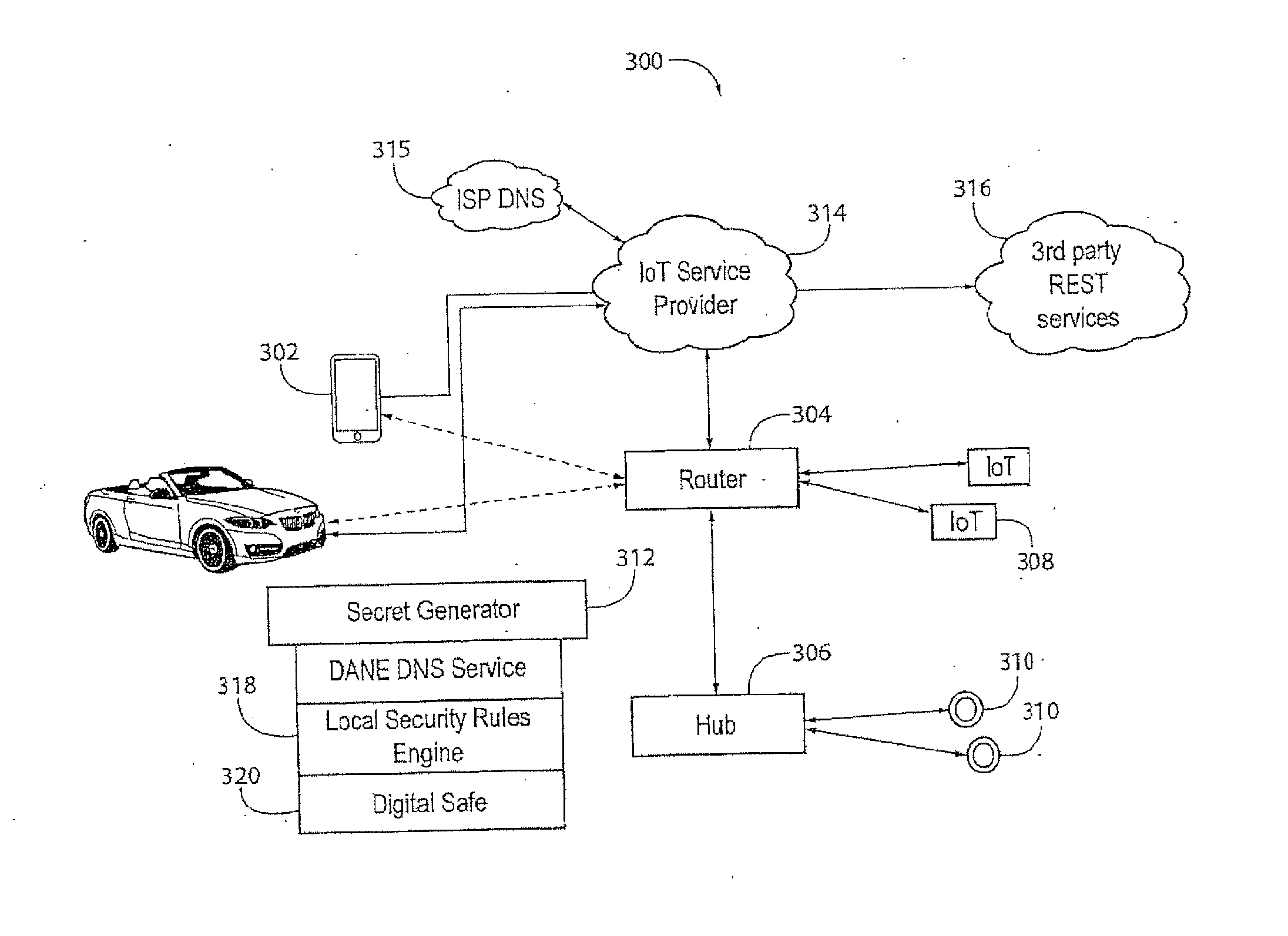
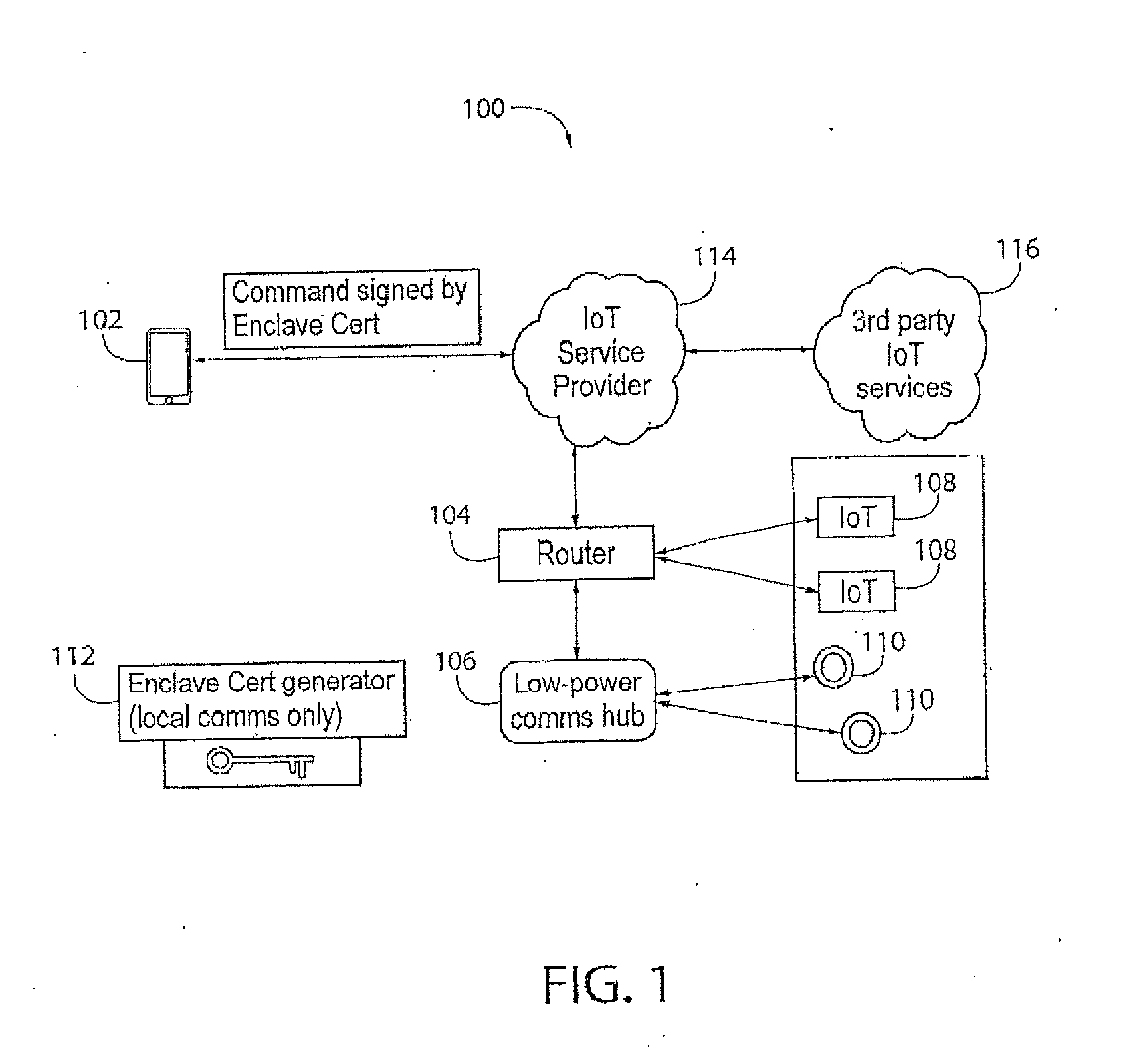
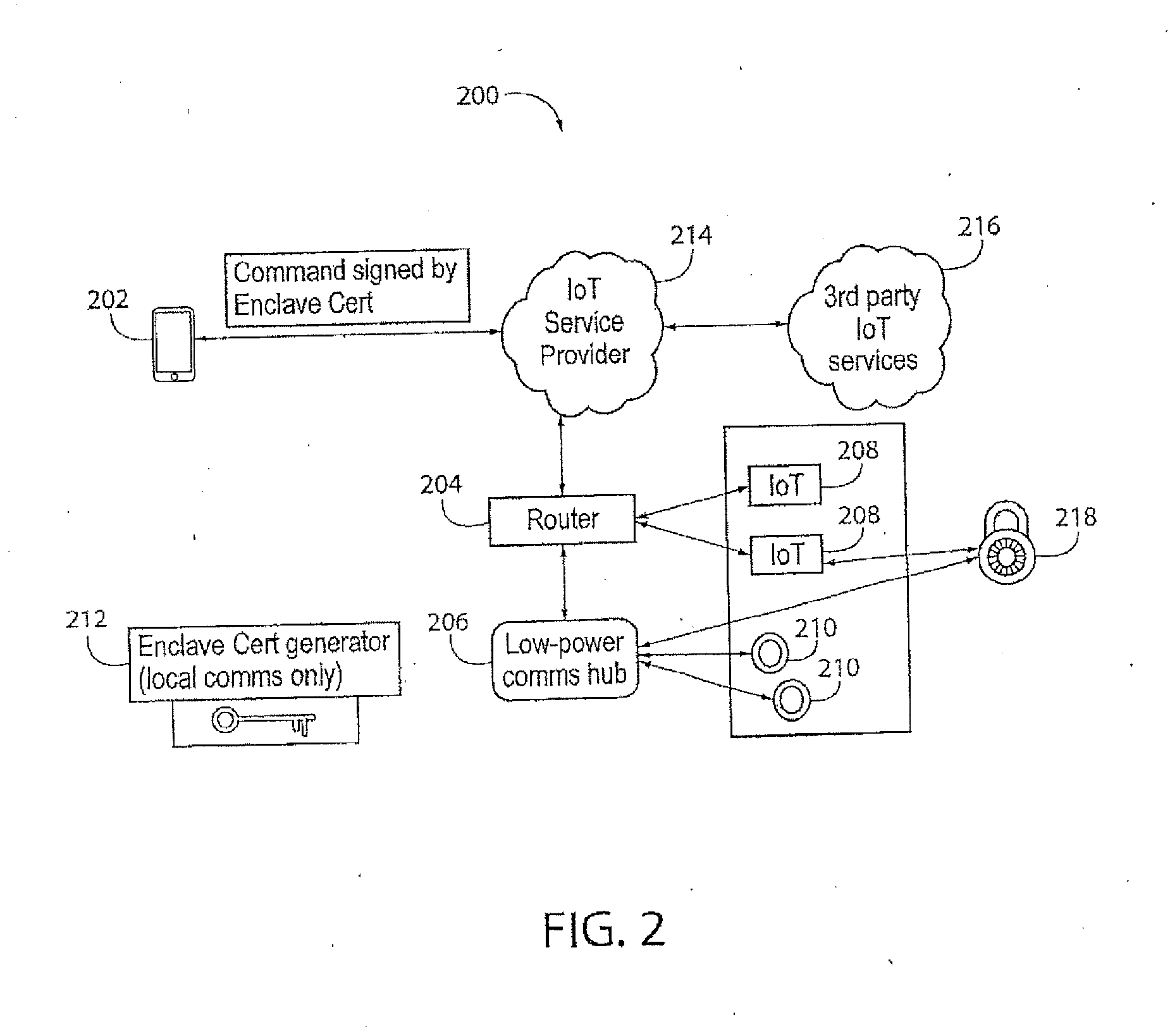
System, Method and Device for Consistently Configuring and Securing Devices Installed in Close Physical Proximity
InactiveUS20170034700A1Trust between devices is enhancedImprove trustUser identity/authority verificationSecurity arrangementWeb serviceThe Internet
It is an object of the present invention that trust between devices is enhanced by distributing a shared secret (e.g. an X.509 certificate or other cryptographic or shared secret mechanisms), utilizing a short range communication mechanism, thereby permitting those devices to securely authenticate and authorize sensitive commands to each other in communication over the Internet or an untrusted network. A system, method and device are also provided for securely and consistently configuring multiple networked devices with network credentials, server addresses, and web service credentials, and standardizing and enforcing any inventory, device management, or other policies desired by a user / operator at the time of installation, utilizing a short range communication mechanism.
Owner:ZUUL INC
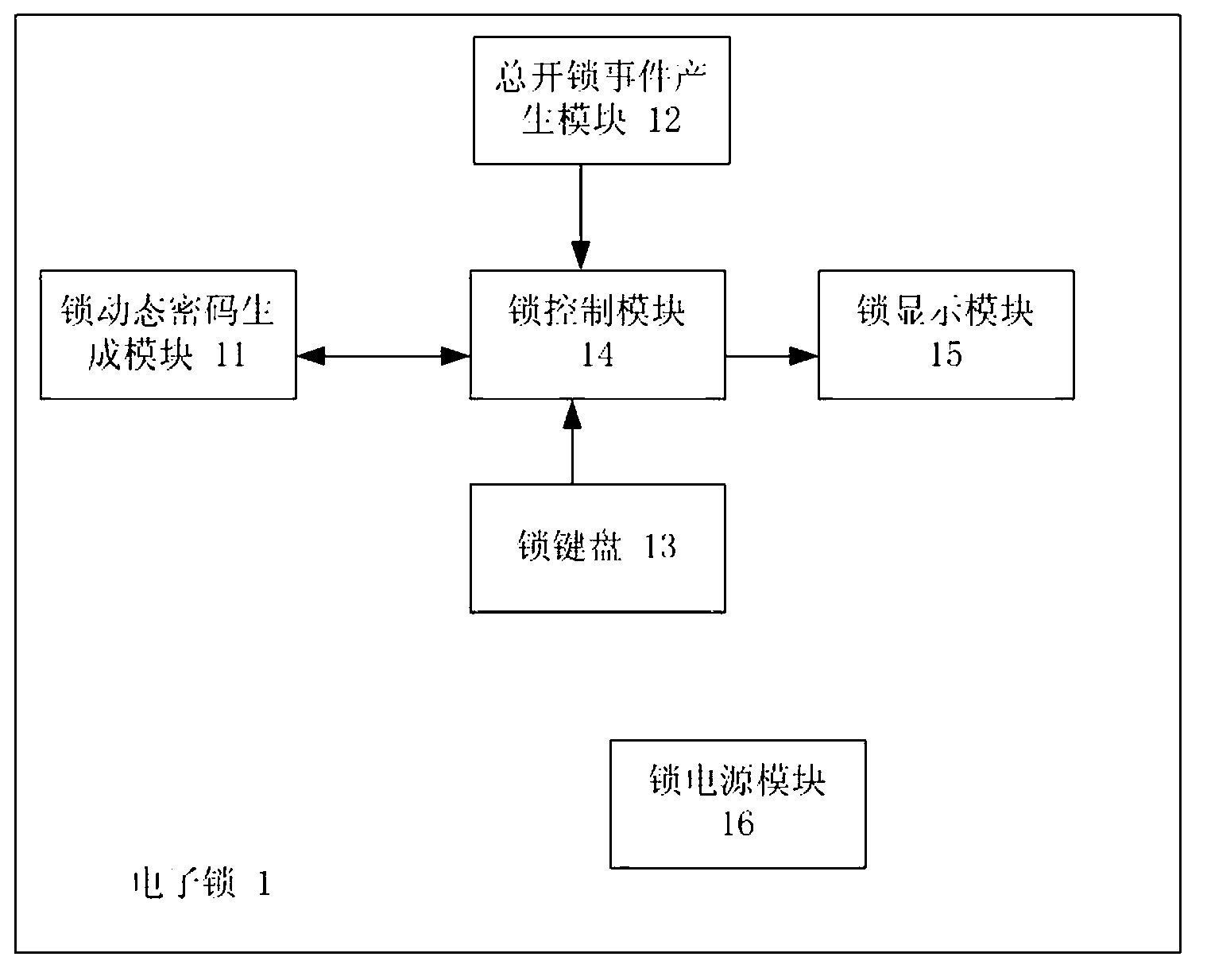
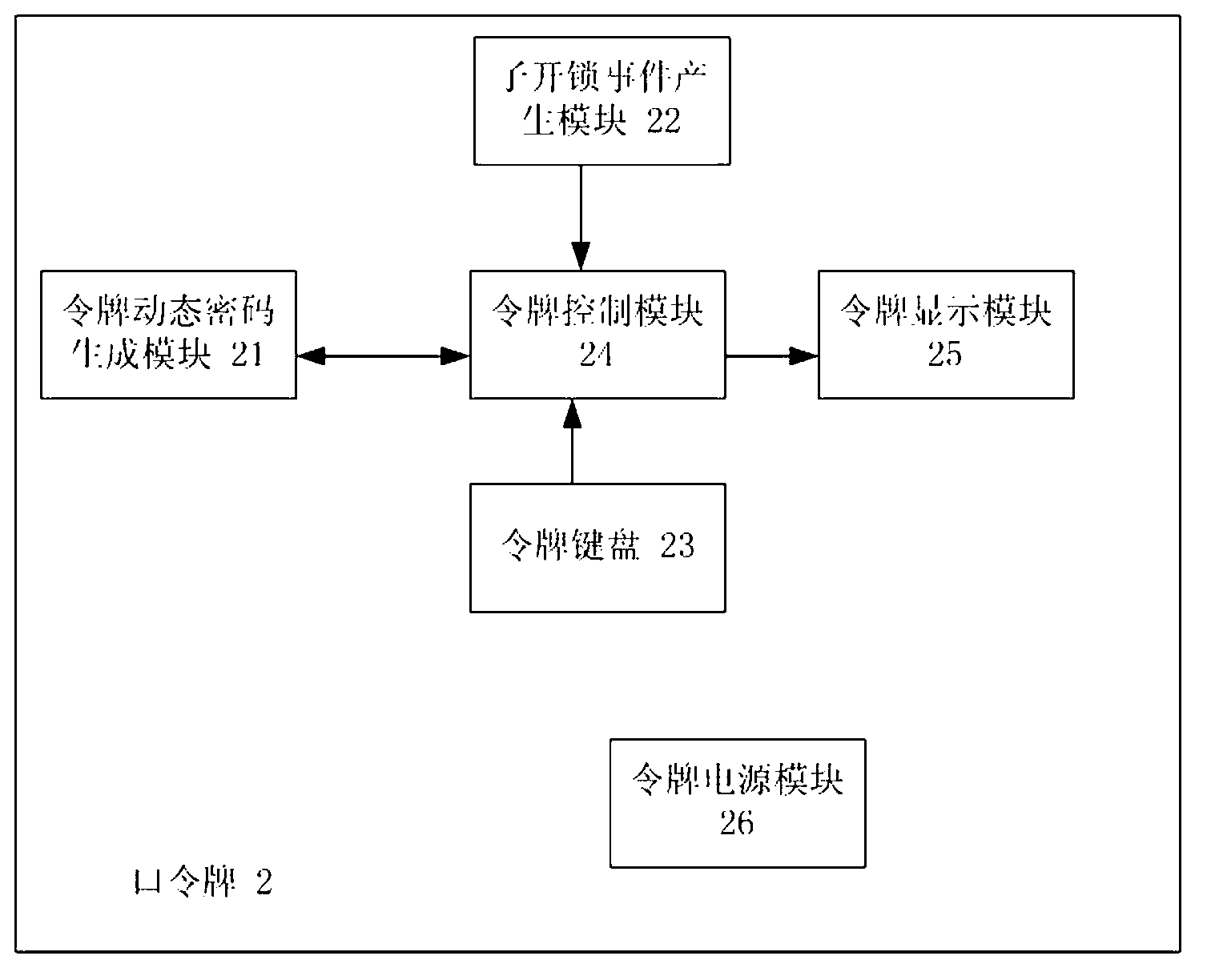
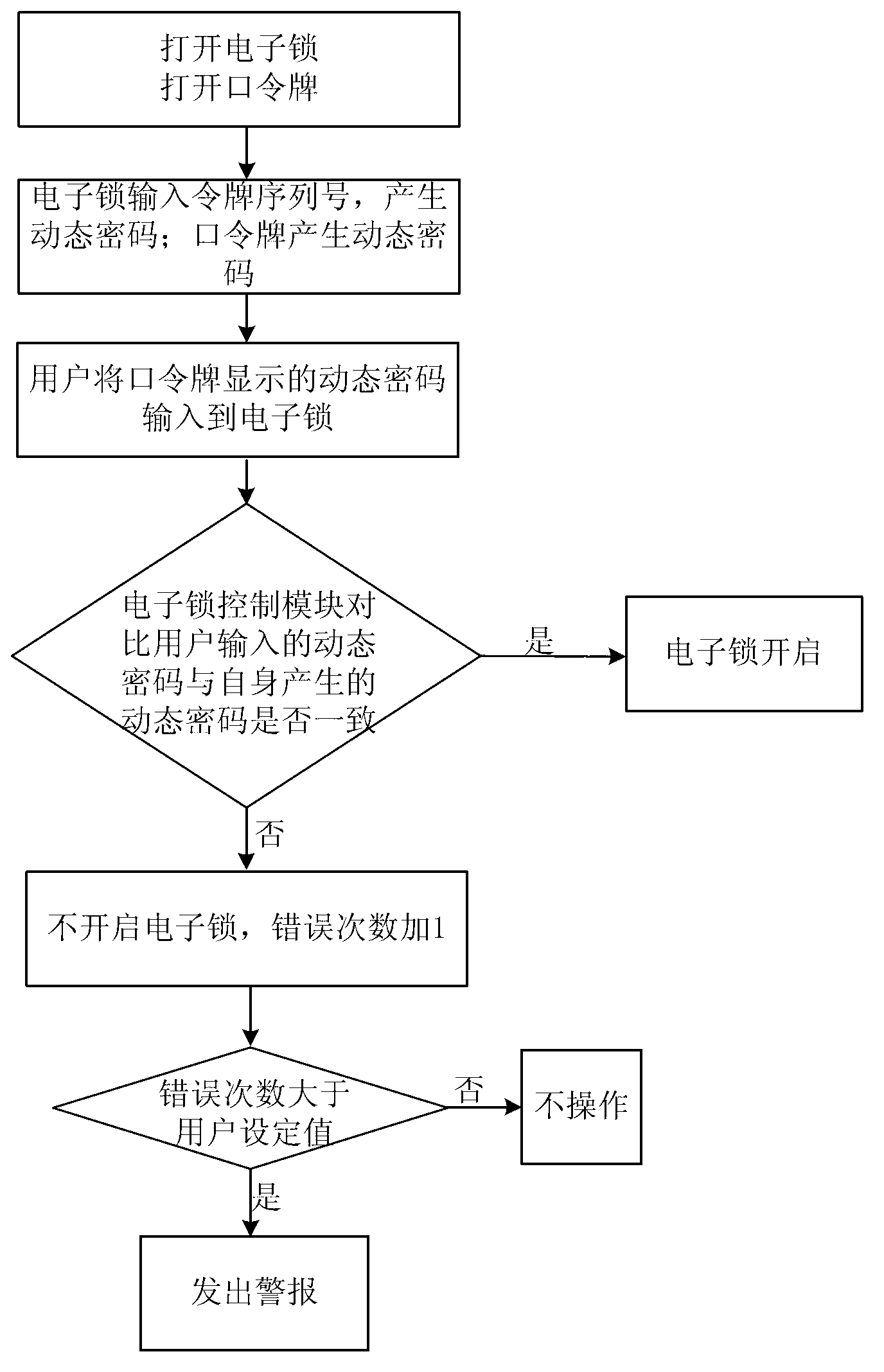
Dynamic electronic coded lock system and authentication method thereof
ActiveCN103218865AExtended service lifeImprove securityIndividual entry/exit registersPasswordUser input
The invention relates to a dynamic electronic coded lock system and an authentication method thereof. The system is composed of an electronic lock (1) and a plurality of password tokens (2) with different equipment sequence numbers. The authentication method comprises the following steps that: the electronic lock respectively accumulates and stores the application times of the password tokens according to the equipment sequence numbers; each password token accumulates and stores own application time; a dynamic password is calculated according to certain rules at the password token end on the basis of the equipment sequence numbers and the accumulated application times, and then is displayed; a dynamic password set is calculated according to the same rules of the password token end at the electronic lock end on the basis of the equipment sequence number corresponding to the password token in use and the allowable error range of the accumulated application times corresponding to the equipment sequence number, and a password input by a user is received; and an unlocking command is executed if the password input by the user is in the selectable dynamic password set, otherwise, the unlocking operation is ineffective. The system and method need no time benchmark, the service life and the security of the system can be prolonged and improved, and a hardware design is simplified.
Owner:孙添平
Intelligent safe box lease sharing system and control method thereof
InactiveCN107195123AImprove securityRealization of leasing and sharingPayment architectureApparatus for meter-controlled dispensingPaymentElectricity
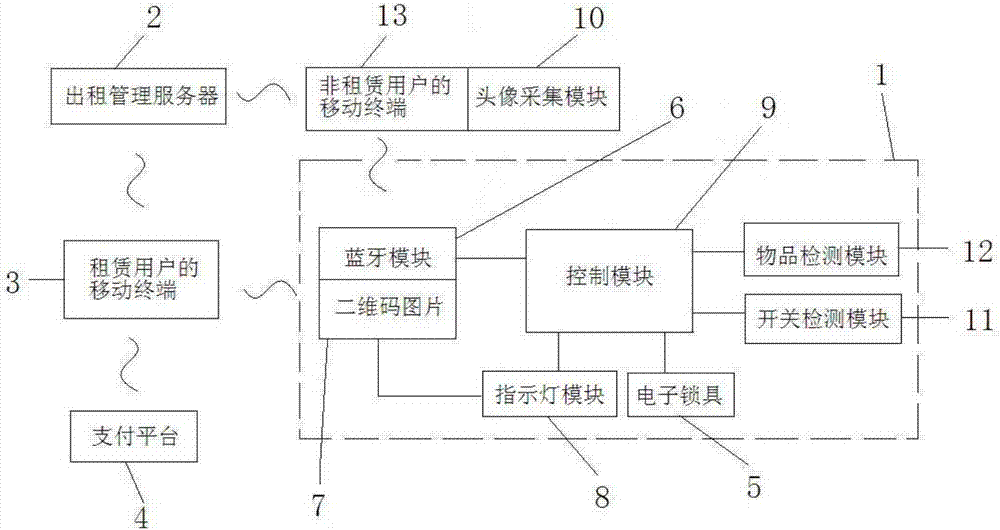
The invention relates to an intelligent safe box lease sharing system which comprises a mobile terminal of a lease user, a rental management server, multiple safe boxes and a payment platform, each safe box comprises a cabinet, a control module and an electronic lock, the mobile terminal of the lease user is networked with the rental management server to be used for submitting a lease application and receiving a box opening password, and the mobile terminal of the lease user is networked with the payment platform to be used for completing payment; the system is characterized in that the cabinets of the safe boxes are internally provided with short-distance wireless communication modules electrically connected with the control module, and the mobile terminal of the lease user can be in communication connection with the control module through the short-distance wireless communication modules and the safe boxes to be used for transmitting the box opening password to the safe boxes. According to the intelligent safe box lease sharing system, networking is not needed, and the safety is high. In addition, the invention further provides a control method of the lease sharing system of the intelligent safe boxes which are free of networking, capable of achieving multi-person sharing and high in safety.
Owner:宁波青大智能安防科技有限公司
Auto-induction door access system and implementation method thereof
InactiveCN102831687ADoes not increase geometric spaceReduce quality problemsIndividual entry/exit registersSystems managementPassword
The invention relates to an auto-induction door access system and an implementation method of the system, which is used in the fields of bank, hotel, machine room, armory, confidential room, office room, intelligent community, factory, high-way toll station and so on. The auto-induction door access system mainly comprises a mobile device, application program, a door access, a computer and a management background, which form the basic conditions for performing the door access function. The mobile device is used as the carrier having the access right of the door access system; the door access system management background provides an account and a password to a user; and the user can communicate with the door access system based on the short-distance wireless communication function of the mobile device, then logs in the door access system by using the account and the password, finally uses the function of the door access system after identity authentication by the two parts. The auto-induction door access system provided by the invention does not need to carry, and has the advantages of zero use cost, high safety, high convenience in operation, and so on.
Owner:李凯
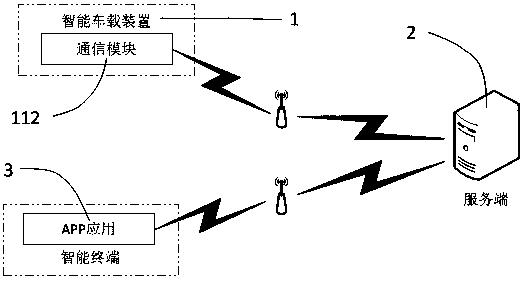
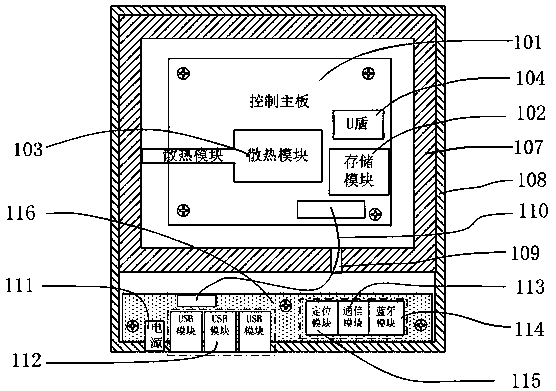
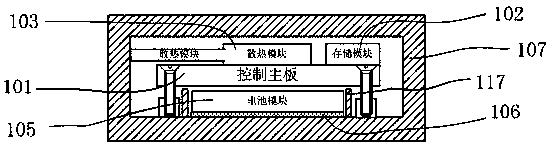
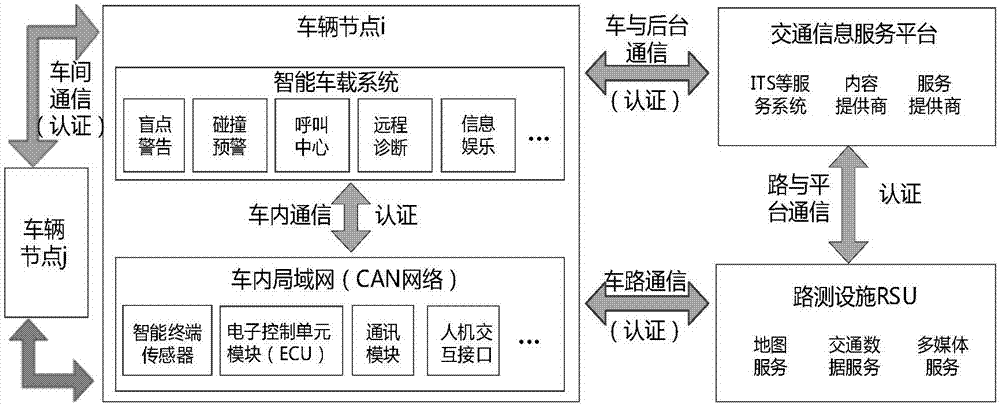
Intelligent vehicle mounted device and secure communication method based on Internet of Vehicles
ActiveCN107948307APlay a protective effectAvoid damageParticular environment based servicesUser identity/authority verificationSecure communicationMicrocomputer
The invention relates to the field of intelligent vehicle and information security, in particular to an intelligent vehicle mounted device and a secure communication method based on Internet of Vehicles. The intelligent vehicle mounted device comprises a microcomputer with large data mining capabilities based on the Linux system, a U shield, various vehicle mounted sensor modules, a communicationmodule, a extension motherboard, and an internal protection shell, and also comprises a matched communication authentication server and APP application; the microcomputer based on the Linux system isinserted with the U shield, and identity authentication operation is performed through the communication module and the communication authentication server. The authentication operation is performed by a cryptography standard signcryption scheme and a customizable signcryption scheme, therefore, the whole intelligent vehicle mounted device is in a highly secure communication environment, and the high security of the communication and data between the intelligent vehicle mounted device and the server is ensured.
Owner:EAST CHINA JIAOTONG UNIVERSITY
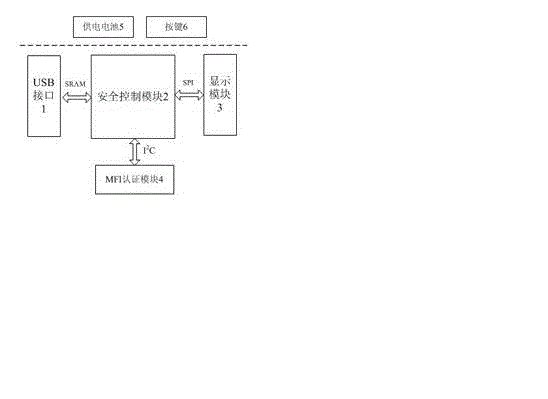
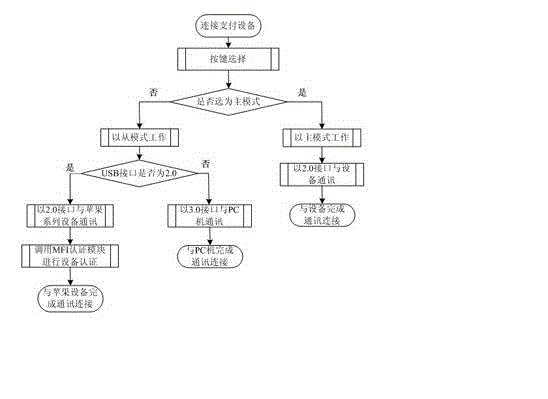
Multi-operating system platform and mobile payment equipment E-bank USB key and working method thereof
InactiveCN102867255AAdd supportSolve the problem that the security of the online banking application cannot be protected based on the USB shieldPayment protocolsKey pressingMoney flow index
The invention relates to a multi-operating system platform and mobile payment equipment E-bank USB key as a second-generation E-bank active USB key for use, and a working method of the USB key. The USB key comprises a miniUSB3.0 interface, a security control module, a display module, an MFI (Money Flow Index) authentication module, a 5V lithium battery and a button part, wherein the miniUSB3.0 interface and a corresponding data connecting line are mated for use so as to realize physical connection with various mobile equipment and PCs (Personal Computers); the security control module is used for providing code service for upper E-bank application; the MFI authentication module is used for completing the equipment authentication of iOS serial equipment to the USB key; and an active USB key is provided with the battery, supports the working mode of main equipment, and can adapt to diversification of the mobile equipment and operating system platforms in the field of security mobile payment, so that the problems that an iOS system, an Android system and other mobile equipment can not protect the security of the USB key-based E-bank application can be thoroughly solved, thus providing uniform, effective and reliable security service for the mobile payment.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
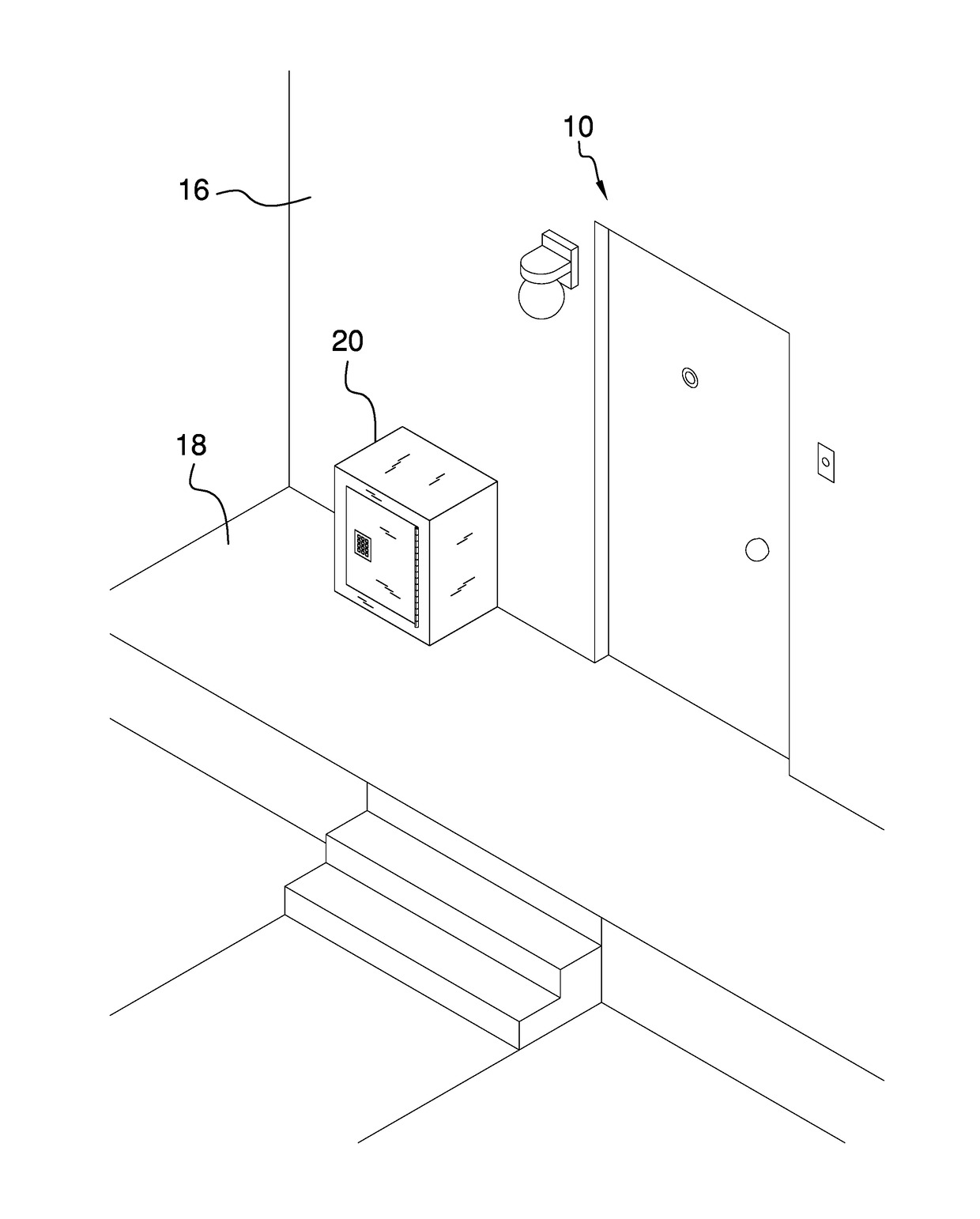
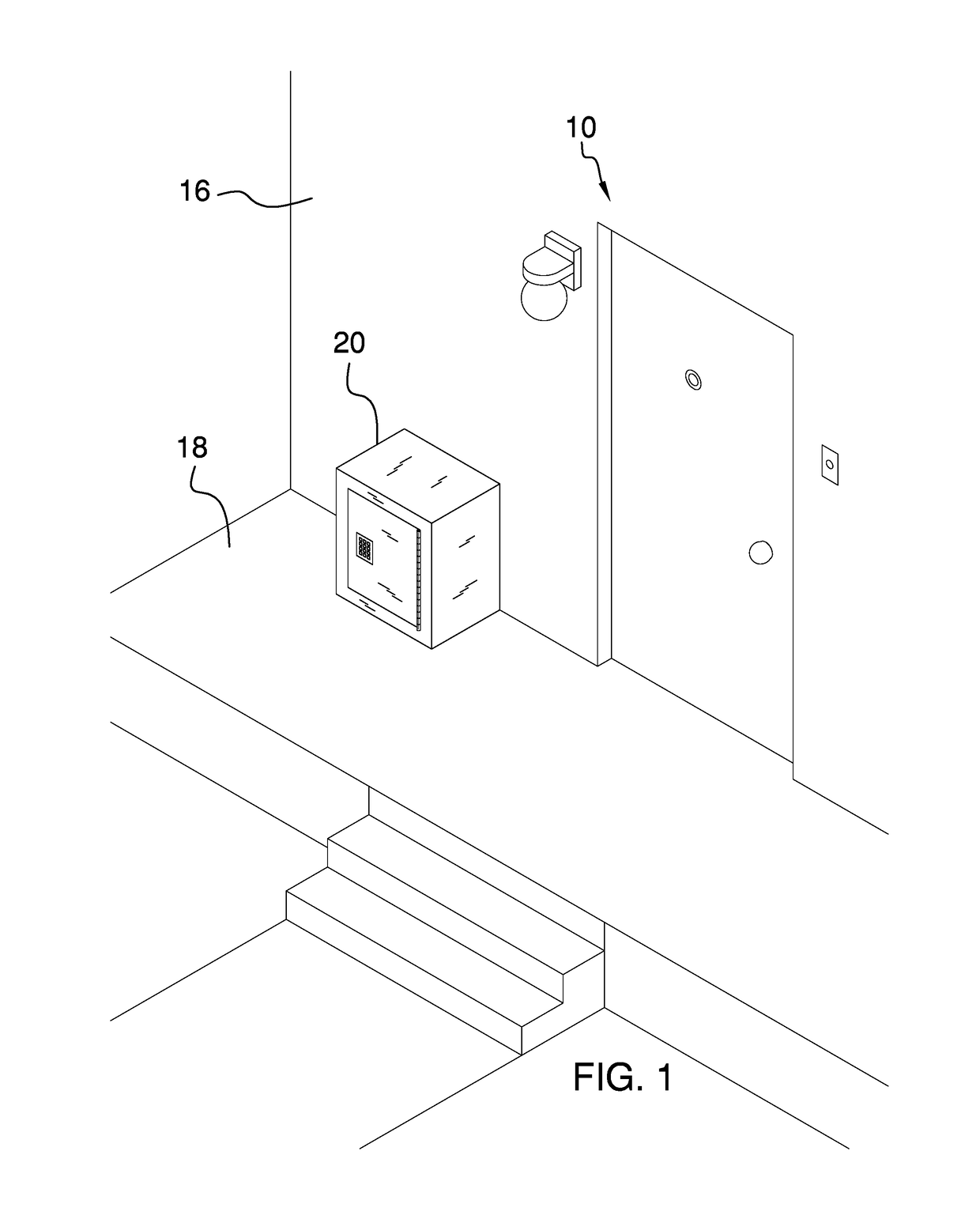
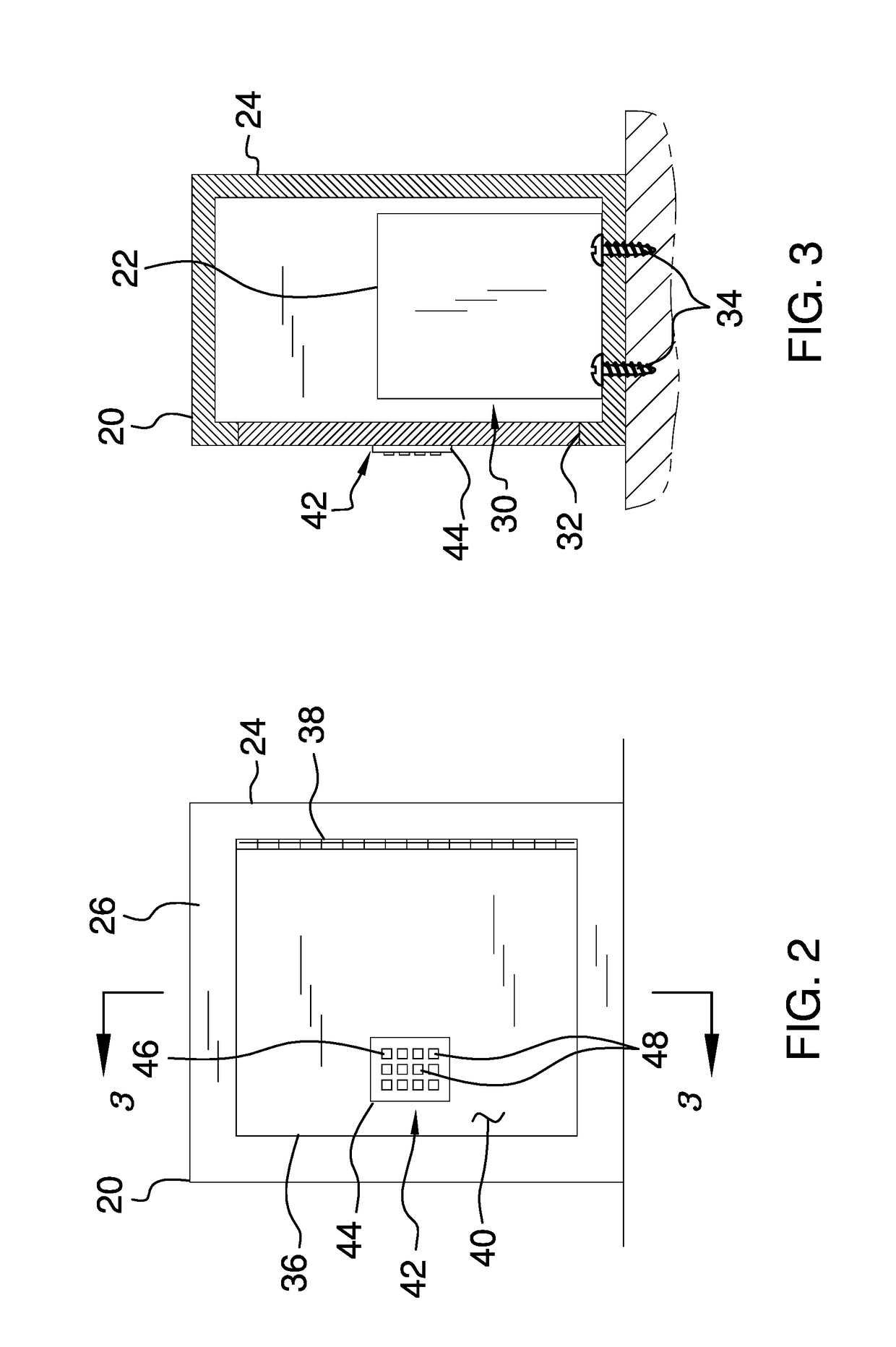
Package Security System
A package security system includes an extrinsic communications network in communication with a parcel delivery company. The extrinsic communications network communicates a predetermined pass code to the parcel delivery company. A building is has an entry and a security box is coupled to the entry. A parcel may be placed within the security box when the parcel delivery company delivers the parcel to the building. A door is hingedly coupled to the security box and an electronic lock is coupled to the door. The electronic lock selectively locks the door in a closed position. Thus, the electronic lock inhibits the parcel from being removed from the security box by an unauthorized user. The electronic lock selectively unlocks the door when the predetermined pass code is entered into the electronic lock. Thus, the parcel may be removed from the security box.
Owner:SCHAIBLE RICHARD
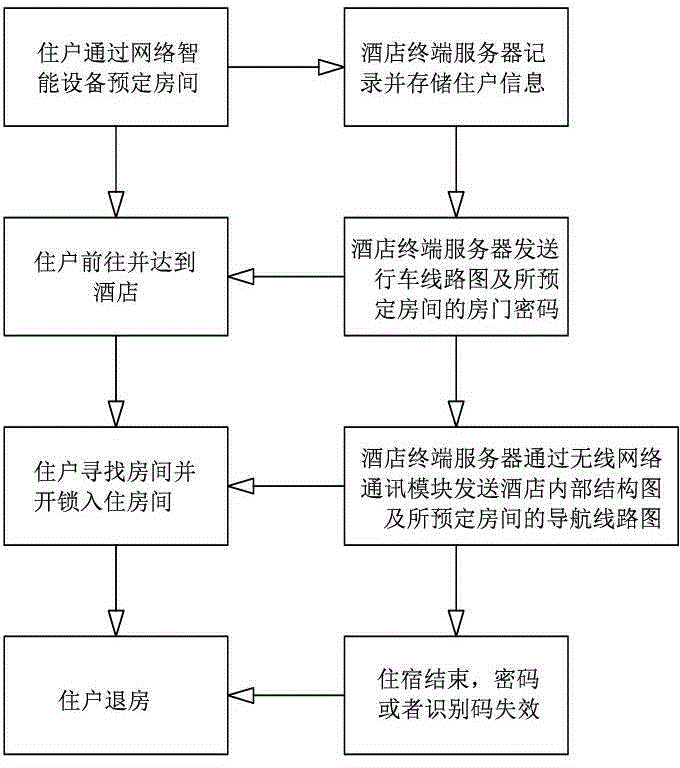
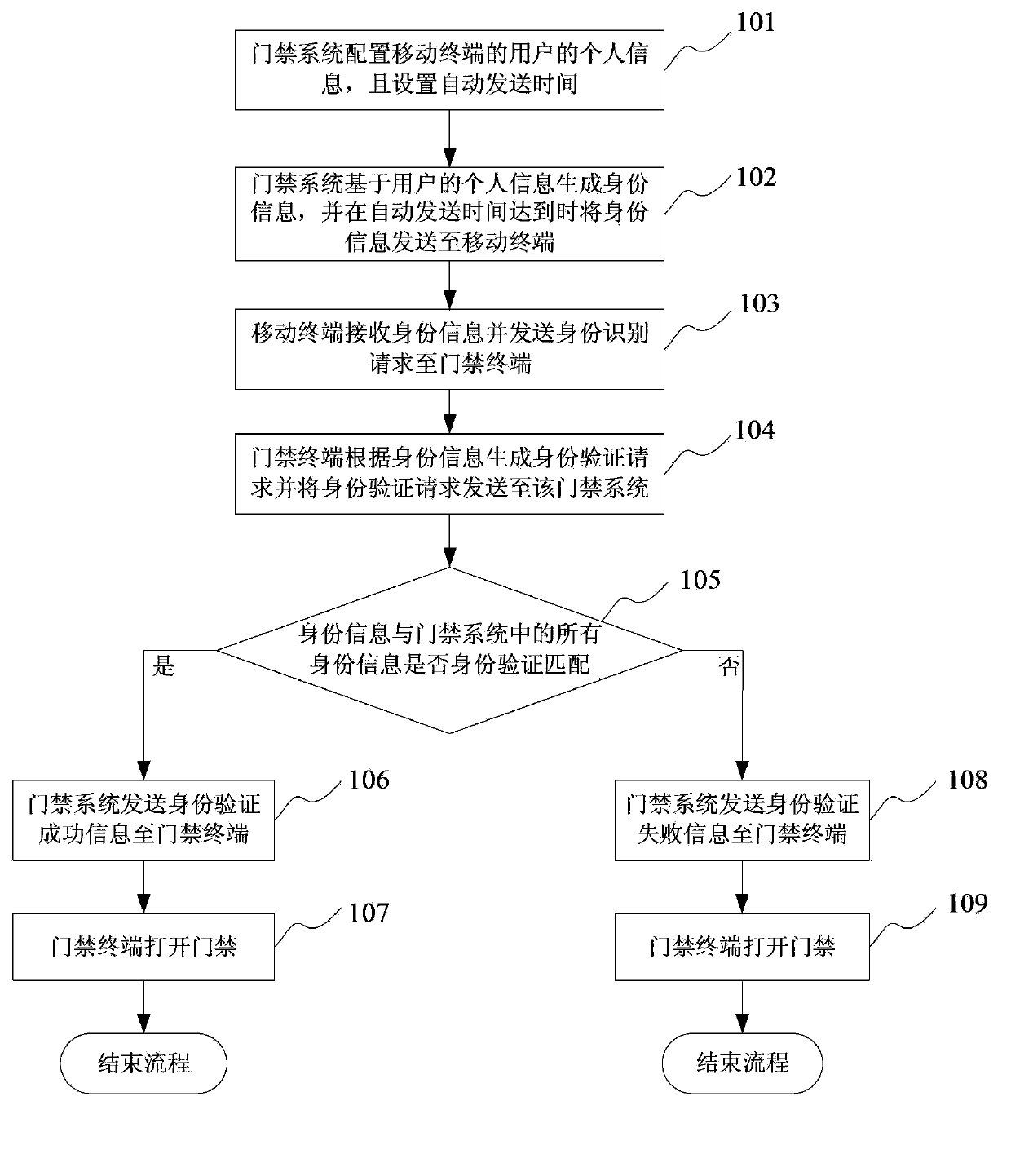
Hotel automatic check-in management control method
InactiveCN104156771AReduce operating costsImprove experienceReservationsOperational costsTerminal server
The invention discloses a hotel automatic check-in management control method, comprising a step of a tenant booking a room through a network smart device and a hotel terminal server recording and storing information of the tenant, a step of the hotel terminal server sending a driving map from a tenant position to a reserved hotel and a door password of the booked room to the network smart device of the tenant, a step of the hotel terminal server sending a hotel inner structure picture and a navigation route picture to the network smart device of the tenant through a network communication module, and a step of the tenant unlocking a door by inputting the door password received by the network smart device. By means of the abovementioned steps, the hotel automatic check-in management control method provided by the invention provides a system flow covering check-in to check-out to the tenant through the Internet technology while manual service is not required, so that tenant experience is improved and operation cost of a hotel is reduced.
Owner:SHENZHEN SAIYI TECH DEV
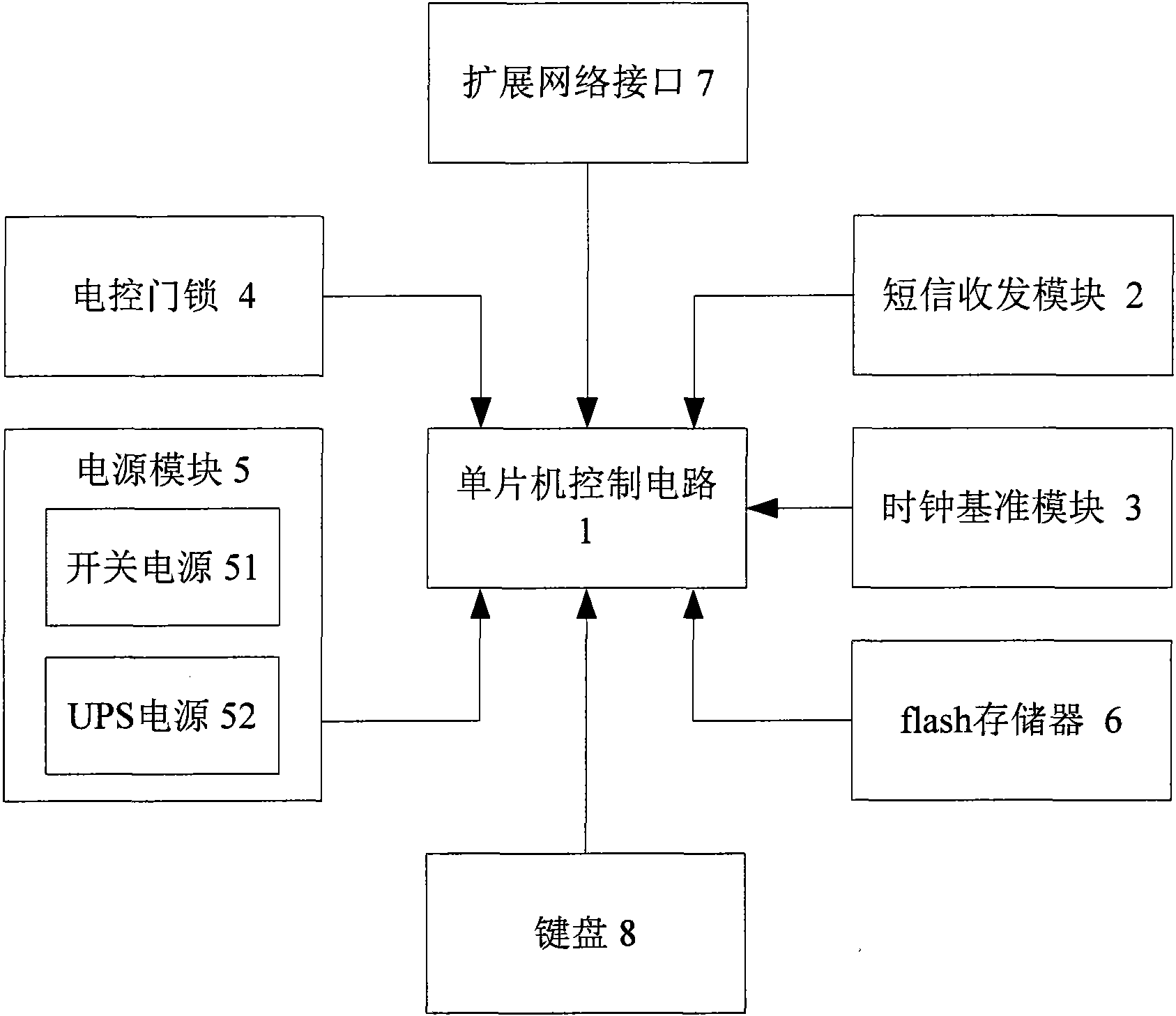
Intelligent electronic access control system
InactiveCN101630422ALow costImprove confidentialityIndividual entry/exit registersMicrocontrollerTransceiver
Owner:TIANJIN POLYTECHNIC UNIV
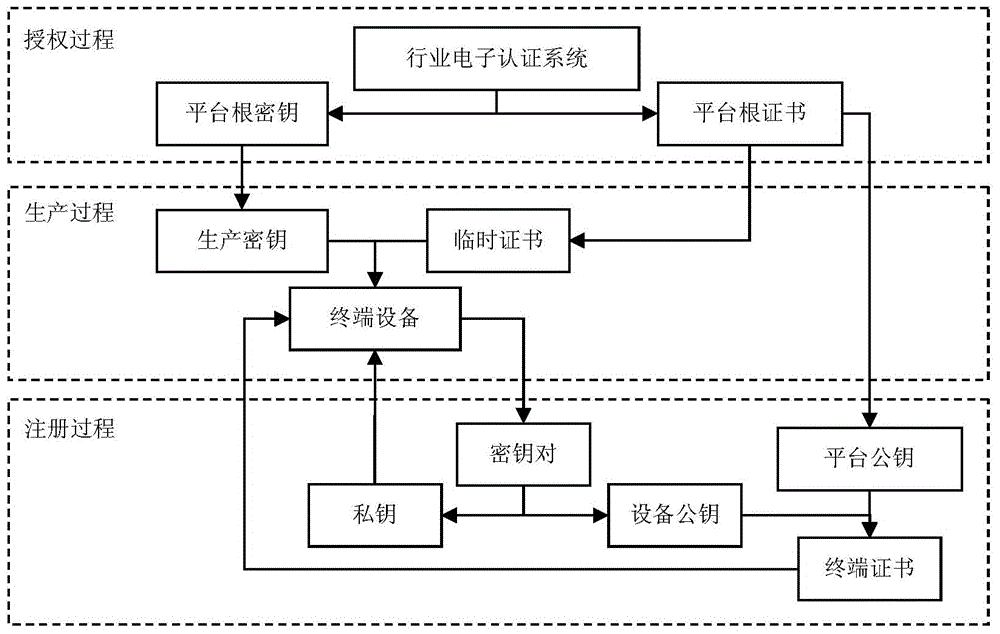
Issuing method of IC card internet terminal and management system
The invention discloses an issuing method of an IC card internet terminal. The method comprises following steps: A, an authorization process: applying a platform root key and a platform root certificate to an industrial electronic authentication system based on an Internet platform; B, a production process: producing a key and writing in a temporary certificate and initialization to terminal equipment; C, a login process: the management system of the IC card internet terminal is used for automatically starting the login process of the terminal equipment.The issuing method of the IC card internet terminal and the management system have following beneficial effects: by means of factorized configuration of industrial temporary certificates and on-line update of formal certificates, issuing regulation and industrial application support of the IC card internet terminal are achieved in support of hardware realization of domestic password algorithms; the working environment for a personal client is provided for application of industrial IC cards; security technology integration and issuing management difficulties of large-scale industrial application based on financial standard equipment are solved; and the issuing method of the IC card internet terminal and the management system help to fill the gap of management work.
Owner:GUANGDONG HUADA INTERNET CO LTD
Internet of vehicles security authentication device and method
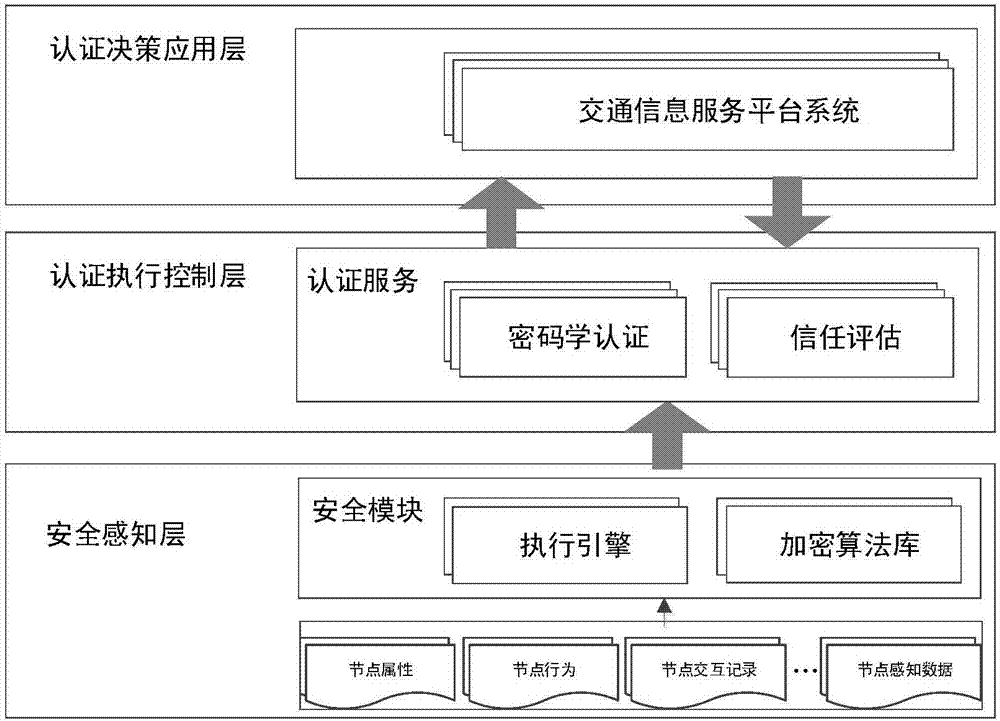
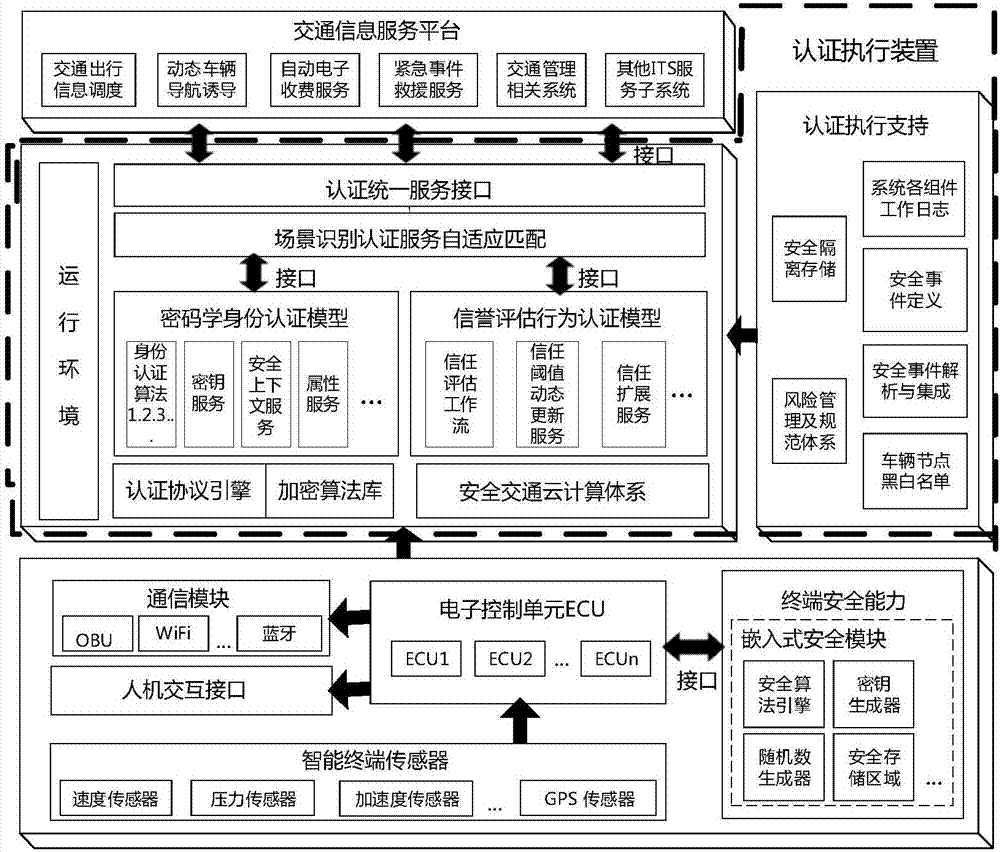
The invention discloses an Internet of vehicles security authentication device and method. The method comprises the following steps of organically combining traditional cryptography authentication service with a trust evaluation mechanism, realizing the traditional cryptography authentication service and the trust evaluation mechanism according to an interface provided by an authentication performance device, mounting the traditional cryptography authentication service and the trust evaluation mechanism to the device, externally providing call service through a uniform interface of the device, and shielding realization details of various complex authentication algorithms; deploying a trusted embedded security module on a vehicle node in a sensing layer, thereby providing security capability, and modularizing an encryption algorithm of the sensing layer; establishing an authentication system integrated with a trusted terminal, a cryptography authentication method and the trust evaluation system; and matching and evaluating a high-security trusted evidence factor provided by a bottom sensing layer and providing authentication decision basis for an upper traffic information service platform.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
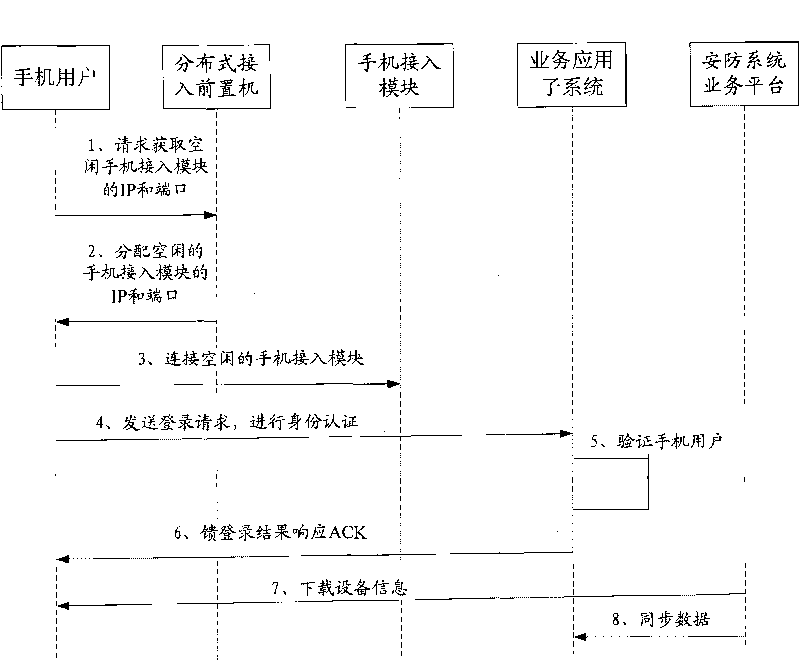
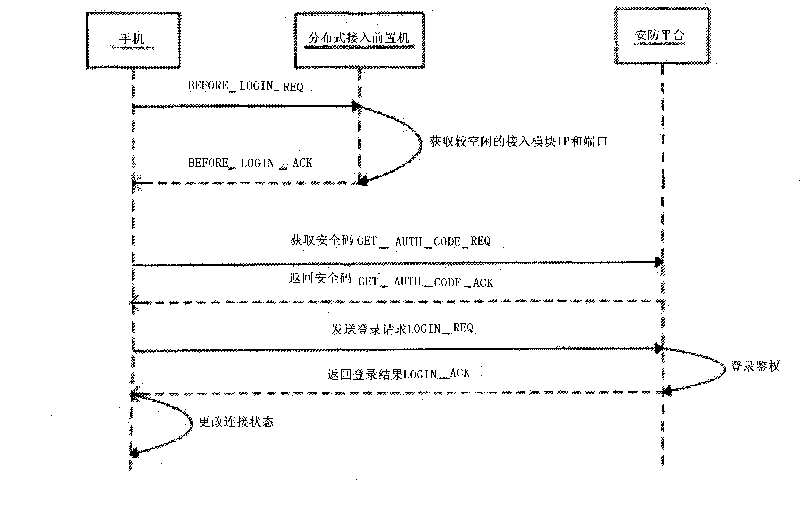
Method for accessing terminal equipment to service platform of security system and transmitting information
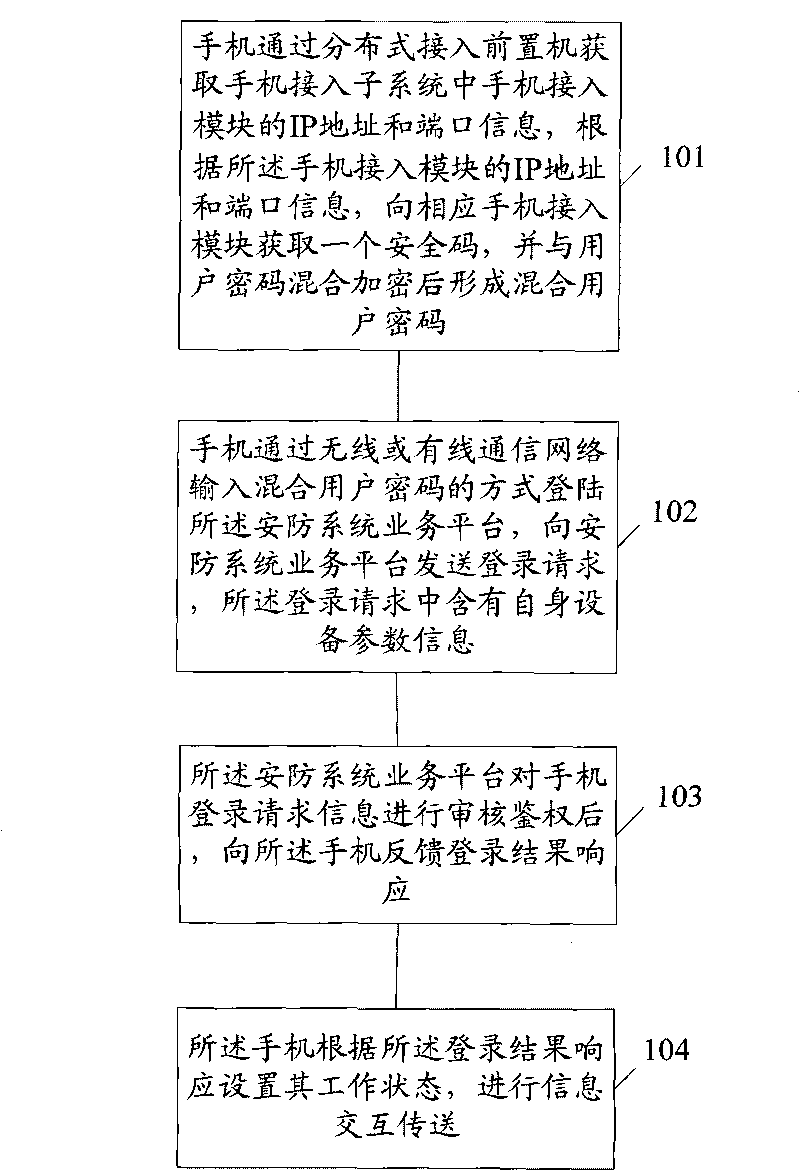
ActiveCN101730094AEasy accessEasy to controlTransmissionSecurity arrangementWired communicationIp address
The invention discloses a method for accessing terminal equipment to a service platform of a security system and transmitting information, which comprises the steps: A. the terminal equipment obtains the IP address and the terminal information of an access module of idle terminal equipment through a distribution type access front-end processor, obtains a safety code for the access module of the corresponding terminal equipment according to the IP address and the terminal information of the access module of the terminal equipment, and encrypts in a mixing way with a user password to be formed into a mixed user password; B. the terminal equipment logins the service platform of the security system by inputting the mixed user password with a wire or wireless communication network, and sends alogin request, wherein the login request comprises parameter information of own equipment; C. the service platform of the security system feeds back a login result response to the terminal equipment after verifying and authenticating the login request information of the terminal equipment; and D. the terminal equipment sets a work status thereof according to the login result response to perform information exchange transmission. Therefore, terminal equipment users can conveniently access the service platform of the security system at any time to call the software of the security system in a remote way.
Owner:GUANGDONG TRI SUN ELECTRONICS TECH
Operating system for managing public parking lot
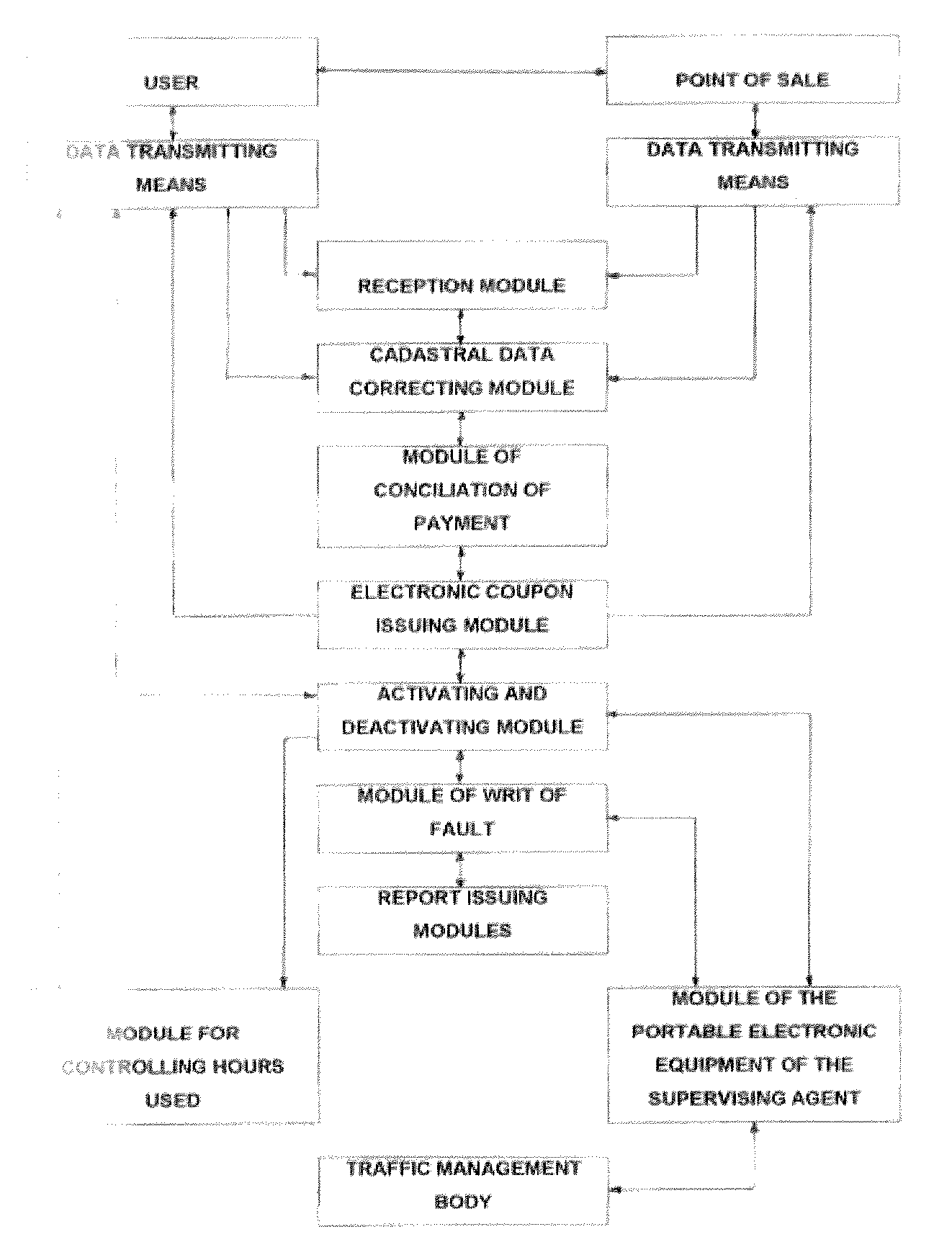
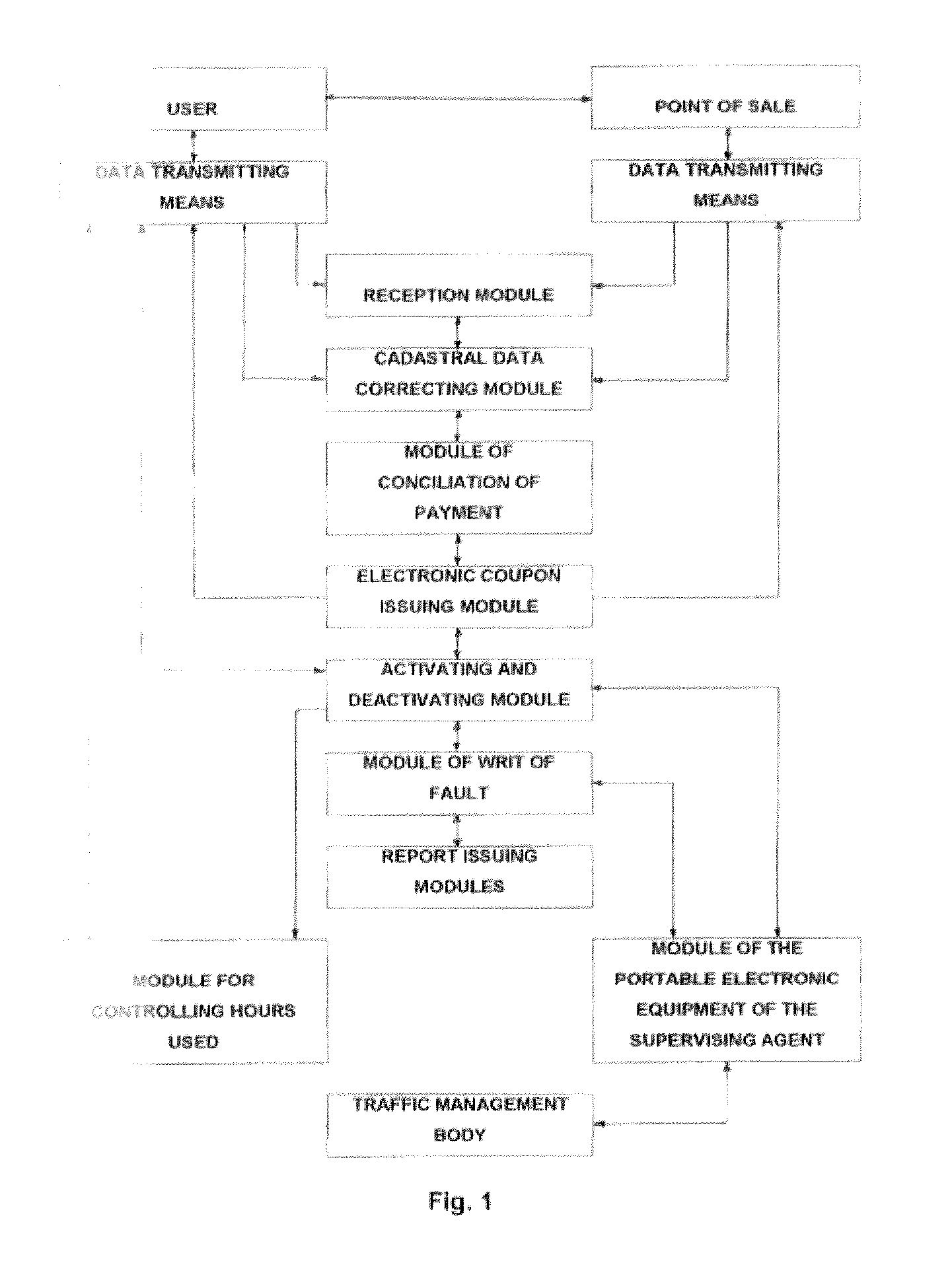
InactiveUS20080203145A1Prevent fraudTicket-issuing apparatusRoad vehicles traffic controlPaymentOperational system
Operating system for managing public parking lot which provides a solution for controlling public parking lots, by using for telecommunications technology which, in combination with mobile devices, allows interconnection of sales terminals with a supervisory program in order to make the process electronic and automated. A reception module receives information about the vehicle, an electronic coupon issuing module generates the electronic coupon based on the provided information and payment, which data is stored in together, and an activation and deactivation module enables activation and deactivation of each electronic coupon upon entry of the number of the electronic coupon and the password of that electronic coupon. The activation and deactivation module provides a confirmation of activation or deactivation of the electronic coupon to a telephone number associated with the electronic coupon.
Owner:MARTINS DOMINGOS NELSON
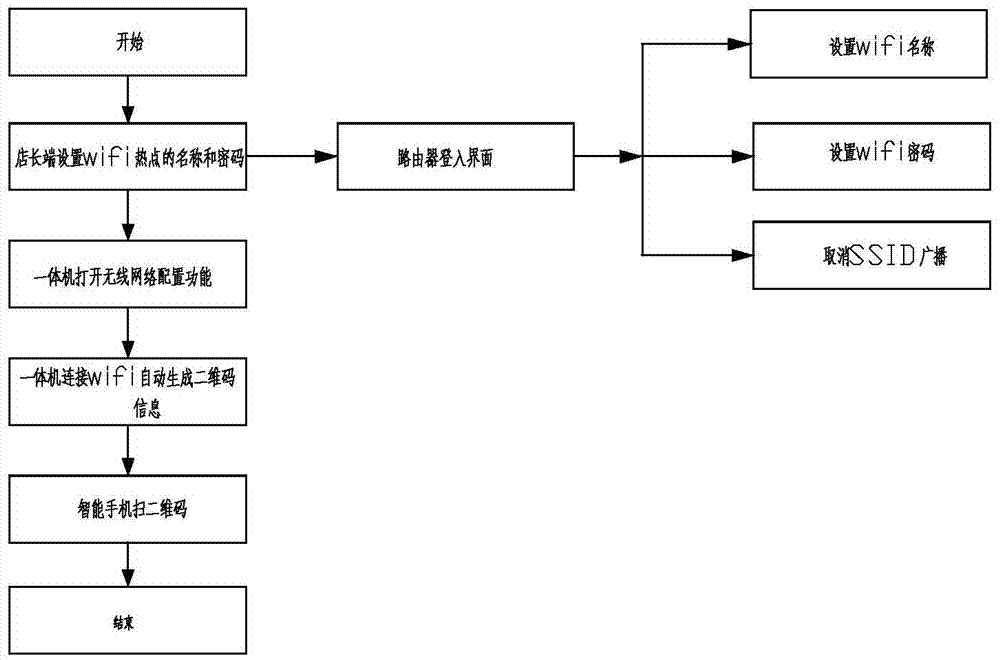
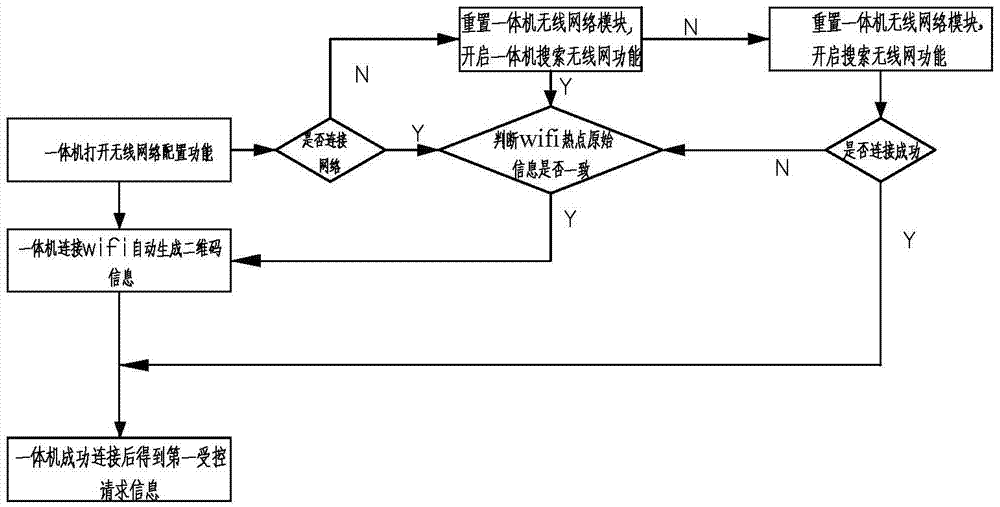
Automatic wifi connection method of advertisement injecting machine
InactiveCN105451306AGuaranteed stabilityImprove experienceAssess restrictionNetwork topologiesPasswordComputer module
The invention relates to an automatic wifi connection method of an advertisement injecting machine. A traditional advertisement injecting machine can not automatically connect wifi and steps for a client to connect the wifi are tedious and are not stable. By using the method in the invention, the above problems are solved. The method comprises the following steps that 1) a shop manager end sets a name and a password of a wifi hotspot, an AES encryption algorithm is used to carry out encryption when the shop manager end sets a wifi instruction, and a wifi module uses an integration module of wifi and bluetooth integration; 2) a wireless network configuration function in the advertisement injecting machine is opened, a hidden wifi name is manually added and input and the wifi set by the shop manager end is connected; 3) the advertisement injecting machine automatically generates two-dimension code information after connecting the wifi and the two-dimension code information comprises a name corresponding to a shop owner end wifi, a password and an encryption mode; 4) an intelligent mobile phone scans a two-dimension code and acquires two-dimension code information to automatically connect the wifi. By using the method in the invention, time for a user to connect the wifi is greatly reduced, linking steps are simple and stability is high.
Owner:GUANGZHOU MICH INFORMATION TECH
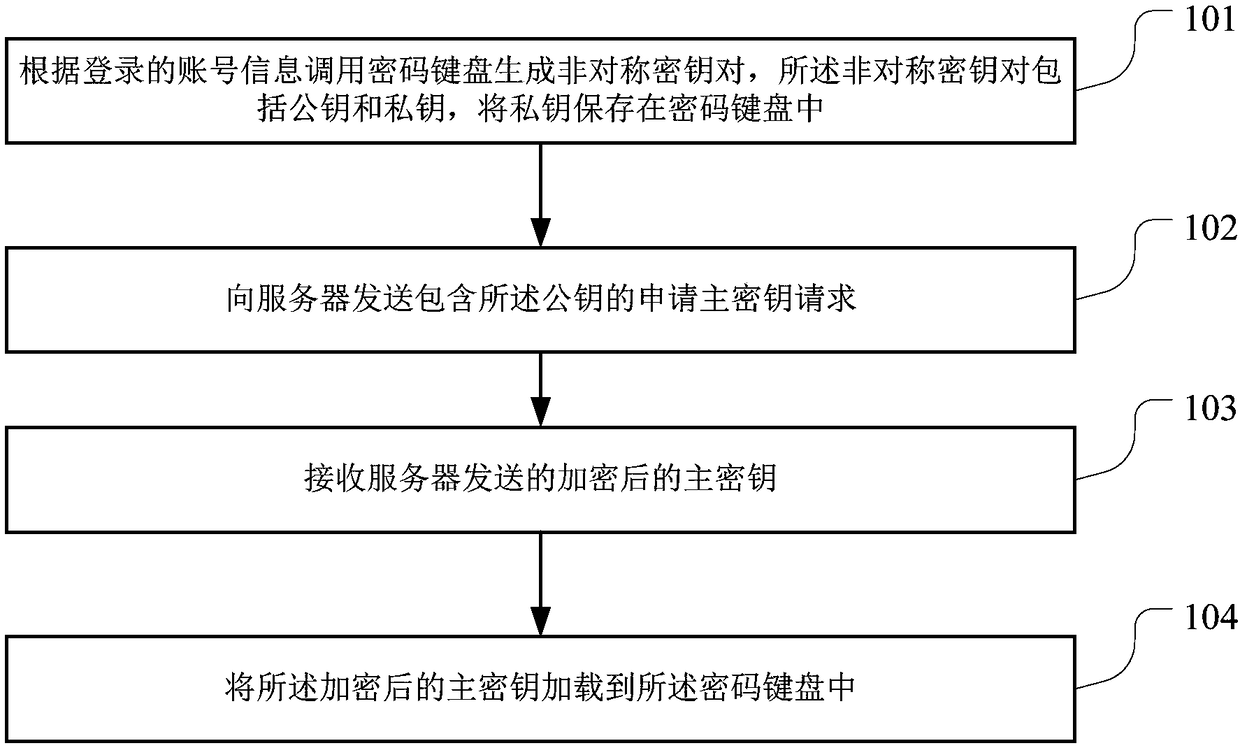
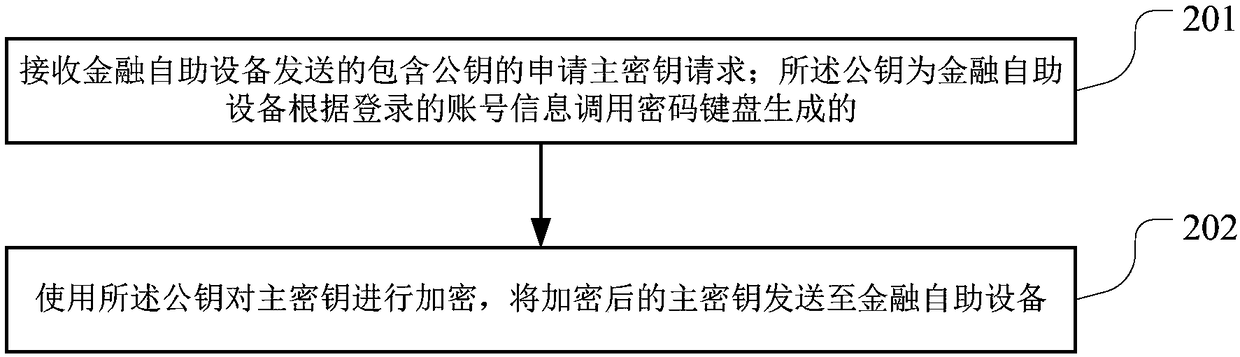
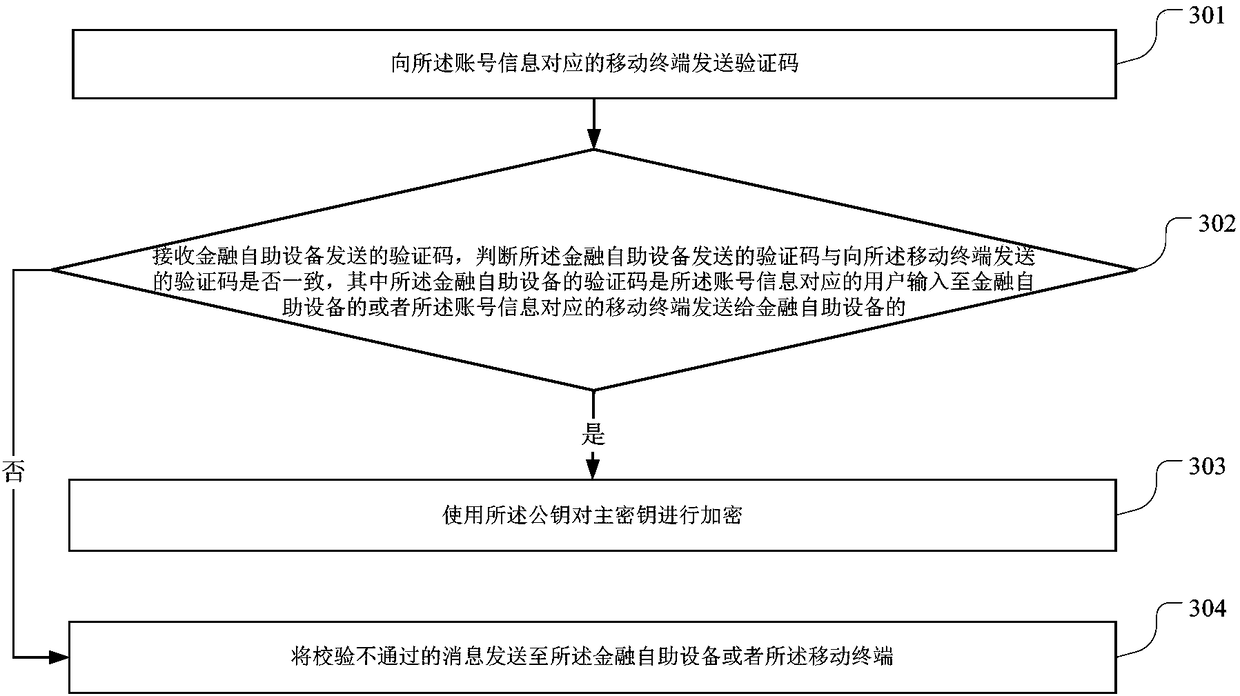
Key generation method and device for financial self-service equipment
InactiveCN108365950AEnsure safetyAvoid safety hazardsKey distribution for secure communicationPayment protocolsUsabilityMaster key
The invention is suitable for the technical field of financial self-service equipment, and provides a key loading method and device for the financial self-service equipment, financial self-service equipment and a server. The method comprises the following steps: calling a cryptographic keyboard to generate an asymmetric key pair according to logged-in account information, wherein the asymmetric key pair includes a public key and a private key; storing the private key in the cryptographic keyboard; sending an application master key request including the public key to the server; receiving an encrypted master key sent by the server; and loading the encrypted master key into the cryptographic keyboard. Through adoption of the key loading method and device for the financial self-service equipment, the financial self-service equipment and the server, the function of automatically encrypting the master key is realized; the hidden danger caused by manual import is avoided; and the security ofthe master key is ensured. The key loading method and device have relatively high practicability and usability.
Owner:SHENZHEN YIHUA COMP +2
Authentication mechanisms for wireless networks
ActiveUS20150327067A1AdvertisementsPublic key for secure communicationWireless mesh networkWeb service
Owner:MICROSOFT TECH LICENSING LLC
Automatic version deployment method and device, computer equipment and storage medium
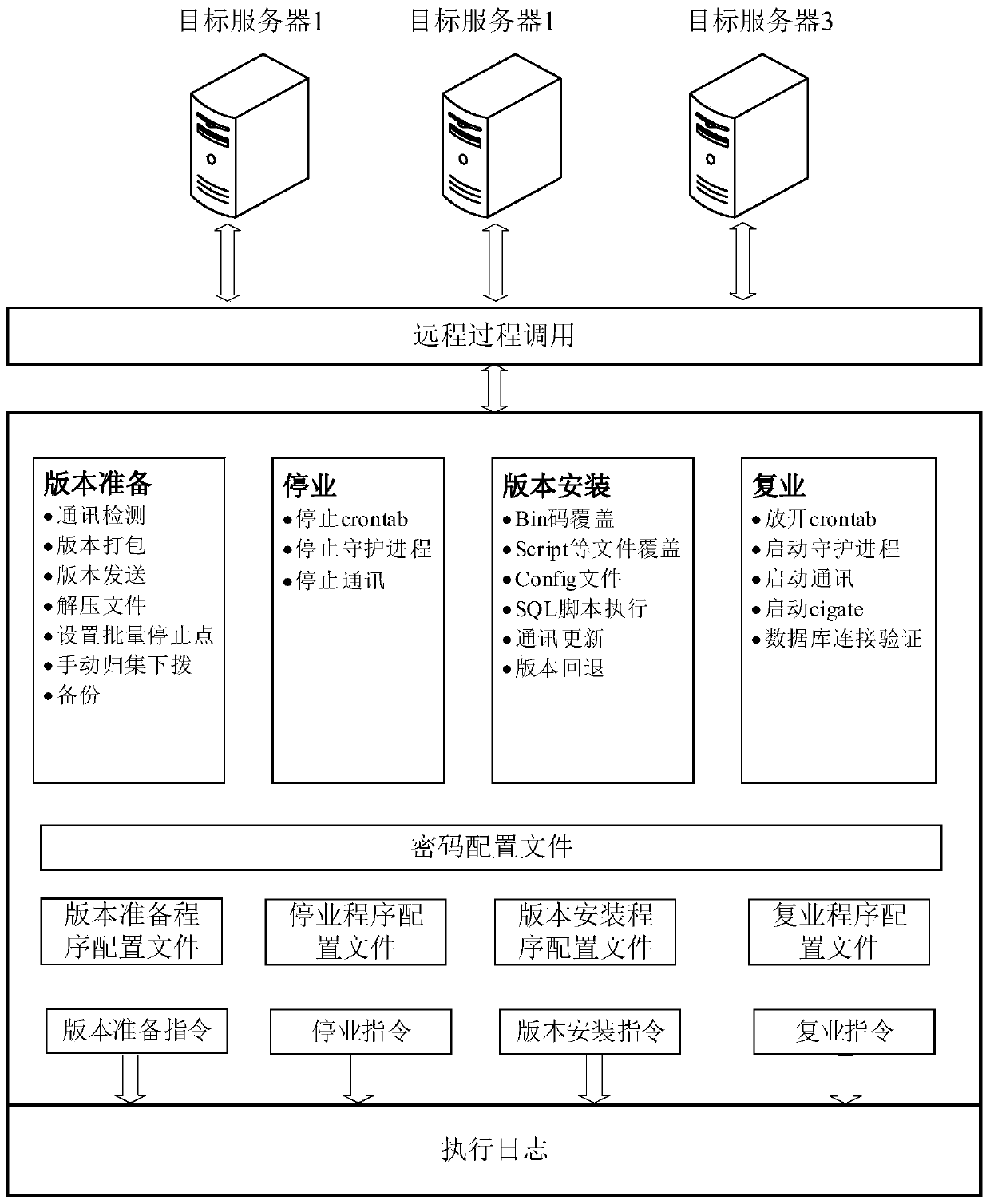
InactiveCN110275872AEasy accessImplement automatic deploymentTransmissionSpecial data processing applicationsPasswordProgram profile
The invention provides an automatic version deployment method and device, computer equipment and a storage medium, and the method comprises the steps: responding to a version deployment instruction, and obtaining a program configuration file and a password configuration file; reading the target command and the server name for executing the target command from the program configuration file, and reading the login information of the target server corresponding to the server name and the identification information of the target command from the password configuration file; logging in the target server according to the login information, and sending the target command to the target server so as to call the target server to execute the target command through the remote procedure call; and receiving execution result information returned by the target server, and matching the identification information with the execution result information to determine whether the target command is successfully executed. According to the scheme, the version deployment efficiency can be effectively improved, and operation errors are reduced.
Owner:BANK OF CHINA
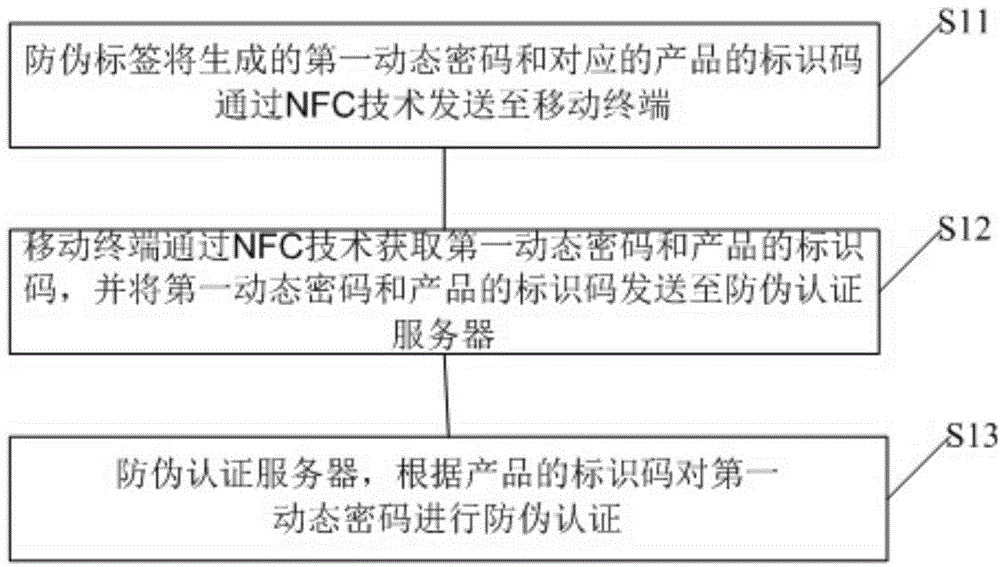
Security label, security method and security system based on dynamic ciphers
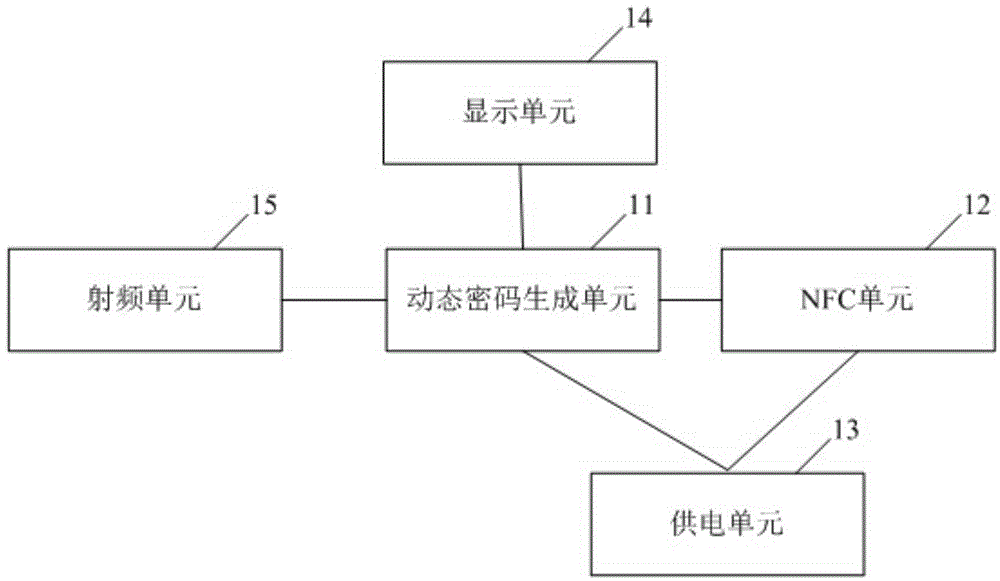
InactiveCN105654170AAvoid the problems caused by manual inputUser identity/authority verificationCommerceComputer terminalCIPURSE
The invention provides a security label, a security method and a security system based on dynamic ciphers. The security label comprises a dynamic cipher generation unit, a near field communication unit and a power supply unit, wherein the dynamic cipher generation unit is used for generating dynamic ciphers, the near field communication unit is used for sending the dynamic ciphers and an identification code of a product corresponding to the security label to a mobile terminal through the near field communication technology to carry out security authentication for the product, and the power supply unit is used for supplying power for the dynamic cipher generation unit and the near field communication unit. According to the security label, the dynamic ciphers are for security authentication, the multiple dynamic ciphers can be generated for one same product so that information disclosure of the dynamic ciphers and forgery can be avoided, so one same product can be authenticated for multiple times, a problem of single authentication caused by authentication failure after one time authentication because of information disclosure of a fixed authentication cipher in the prior art can be solved.
Owner:HIERSTAR SUZHOU
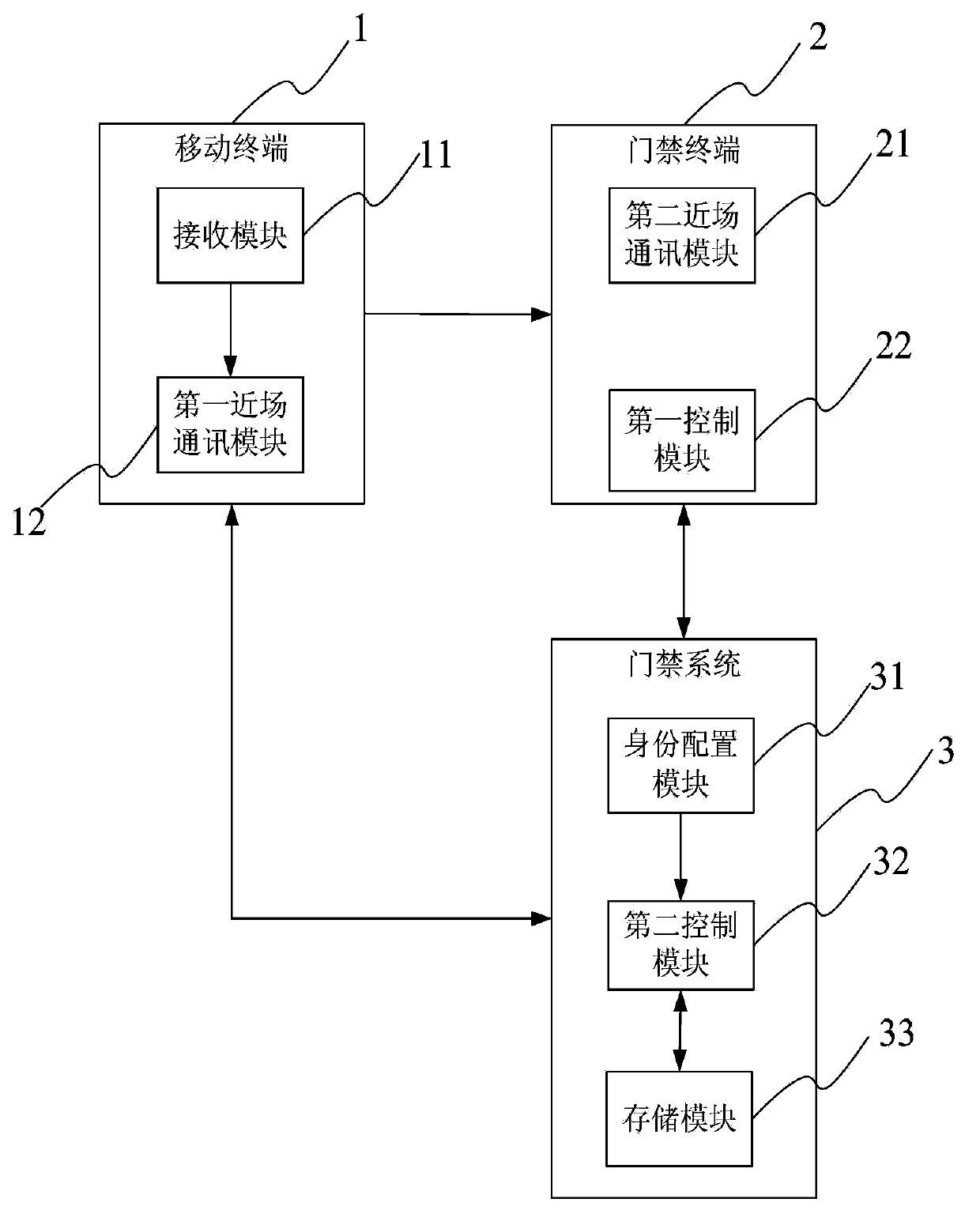
Mobile terminal, entrance guard terminal, entrance guard system, security system and verification method
InactiveCN103971427AImprove securityPrevent theftIndividual entry/exit registersValidation methodsIdentity recognition
The invention discloses a mobile terminal, an entrance guard terminal, an entrance guard system, a security system and a verification method. The mobile terminal comprises a receiving module and a communication module; the receiving module is used to receive dynamic identifying information sent by the entrance guard system and transmit the identifying information to the communication module; and the communication module is used to send an identity recognition request to the entrance guard terminal for requesting the entrance guard terminal to open an entrance guard, wherein the identity recognition request comprises the identifying information. The mobile terminal is capable of dynamically acquiring the identifying information, the mobile terminal sends the identifying information to the entrance guard terminal through near field communication, identity verification is performed through information interaction between the entrance guard terminal and the entrance guard system, the safety of the security system is improved, a user does not need to manually enter password, so that the problems are avoided that an entrance guard card is lost, forgotten and copied and entrance guard password is stolen, and the possibility is also avoided that entrance guard password is peered.
Owner:SHANGHAI SIMCOM LTD
System and method for identification management and real time monitoring of automobile personal
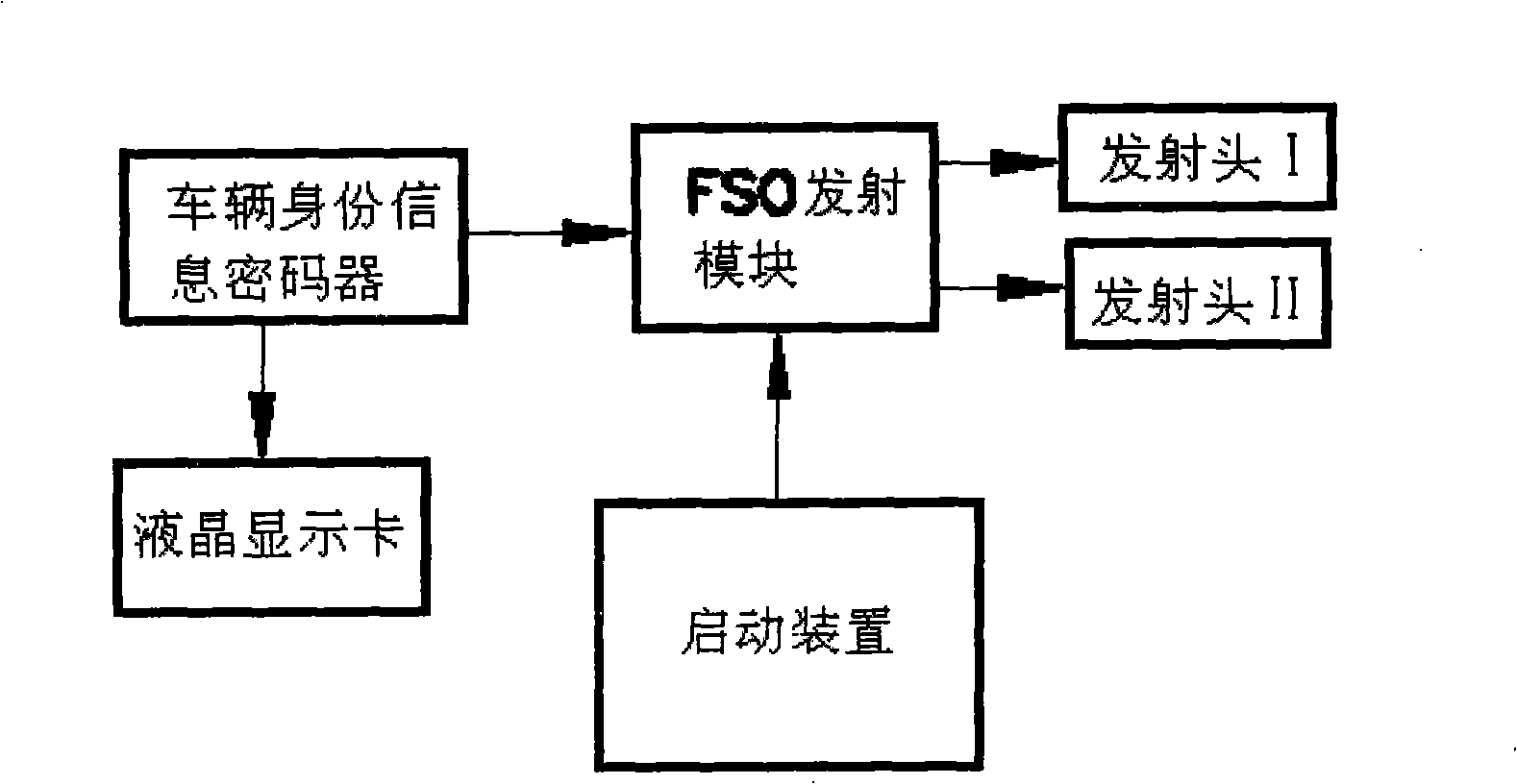
InactiveCN101329816AReduce hardware costsLow costNon-electrical signal transmission systemsRoad vehicles traffic controlEngineeringRadio frequency
The invention discloses an identification management and real-time monitoring system of a motor vehicle, and a method thereof, wherein, atmosphere laser communication is adopted to carry out the information communication of the motor vehicle and a time synchronization password is attached to the identification information codes of the vehicle; a limit device is arranged in a monitoring area; the emission part of an atmosphere laser communication machine is arranged on the motor vehicle as an FSO vehicle-bone device; an FSO receiving device is arranged in the monitoring area and is provided with not only a receiving antenna and a receiving array, but also a high-definition machine vision device which simultaneously captures and collects identification information of the monitored motor vehicle, cooperates with processing software to carry out real-time processing, displays the real-time monitoring results on a monitoring device and sends the real-time monitoring results to relevant traffic management departments. The system and the method of the invention can identify counterfeit license plates and vehicles with illegal identities, provide quick, real time and precise information for effectively cracking down the vehicle robbery and false registration and have the advantages of good transmission security, no occupation of radio frequency, no restriction on communication protocol, massive sending amount, low hardware cost and laying construction expense, high upgrading potential and good compatibility.
Owner:张永刚 +1
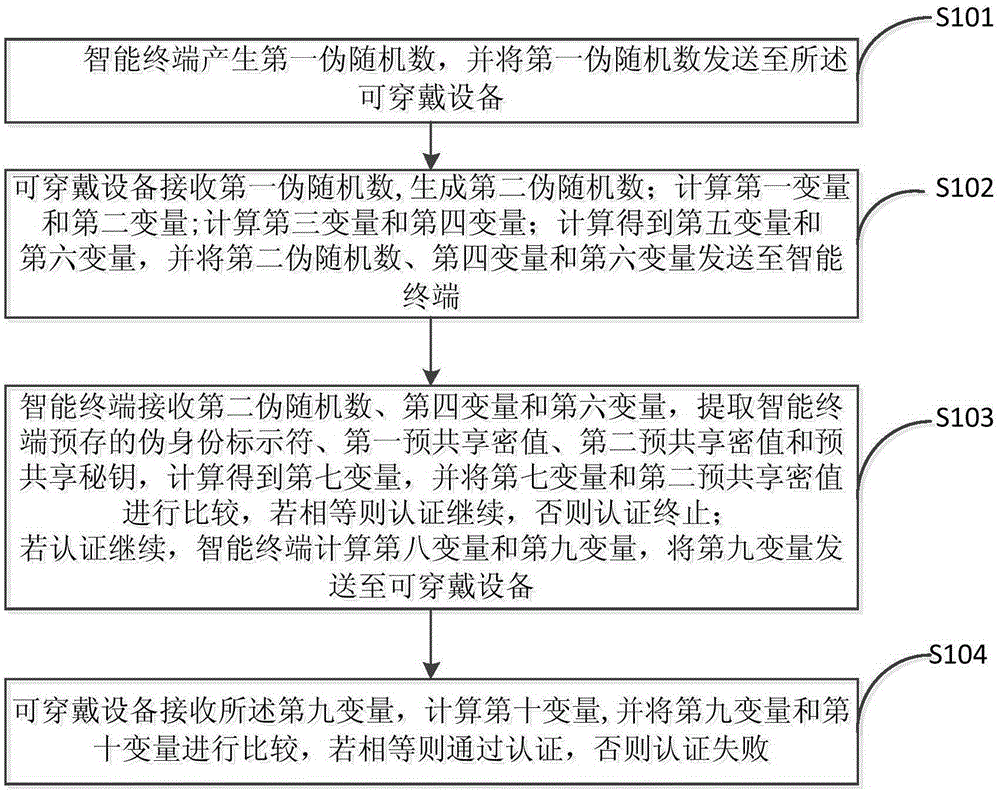
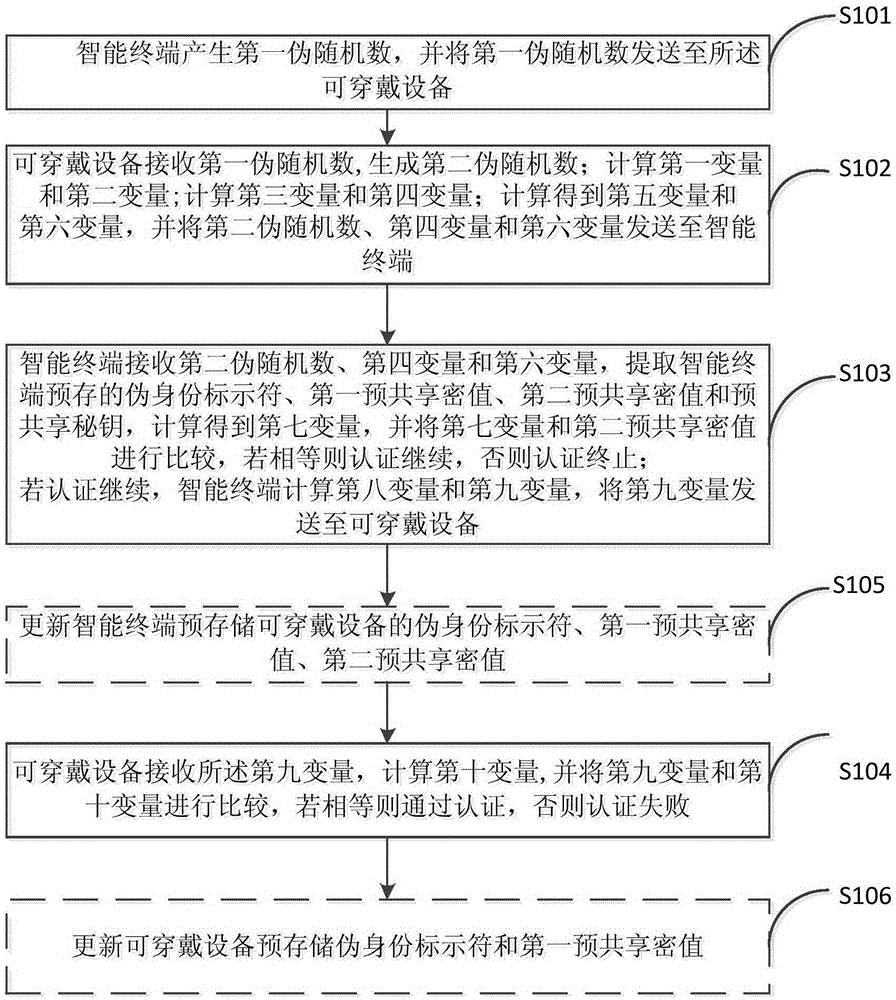
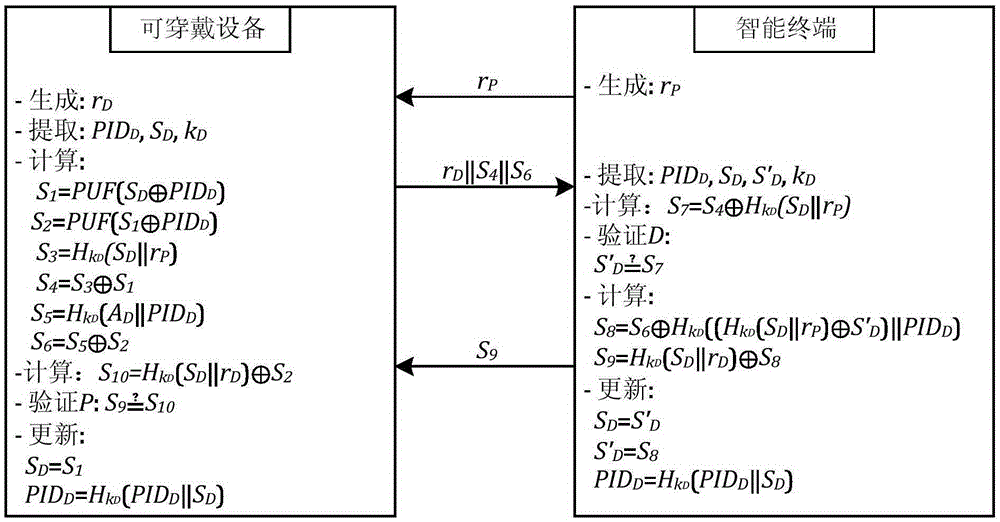
Authentication method for wearable device
ActiveCN105307164AAvoid the problem of increased design costSecurity arrangementComputer hardwareExclusive or
The invention discloses an authentication method for a wearable device. The method uses the excitation-response randomness of a physical unclonable function and introduces lightweight operators like a pseudorandom function, exclusive-or operation and a one-way authentication function and so on, so as to realize mutual authentication of a smart phone and the wearable device. In interaction of the smart phone and the wearable device, a pseudo-identifier of the wearable device and sensitive data like a pre-share private value and so on are transmitted in an anonymous manner, thereby guaranteeing the security of interactive data. In addition, a dynamic update mechanism is introduced, so that freshness and randomness of a session period are improved, and malicious attackers are prevented from replaying and counterfeiting. The method realizes mutual authentication of the smart phone and the wearable device by use of the lightweight cryptology operators, and is applicable to wearable device application scenes with the resource constrained.
Owner:RUN TECH CO LTD BEIJING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com