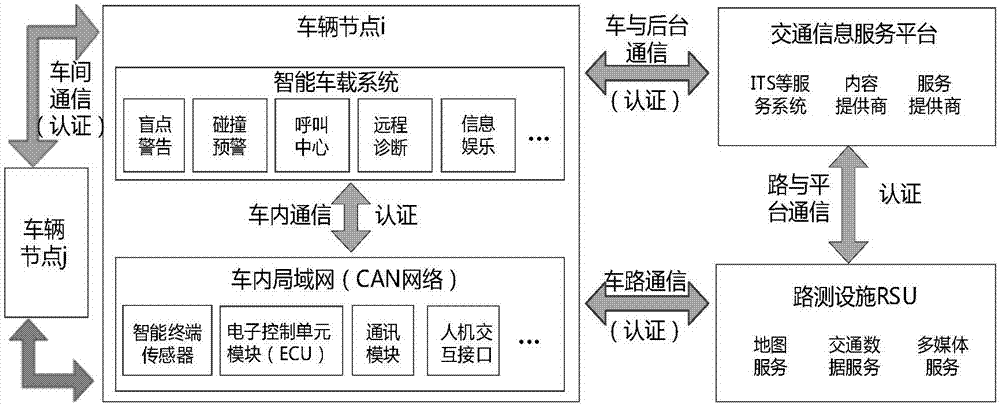
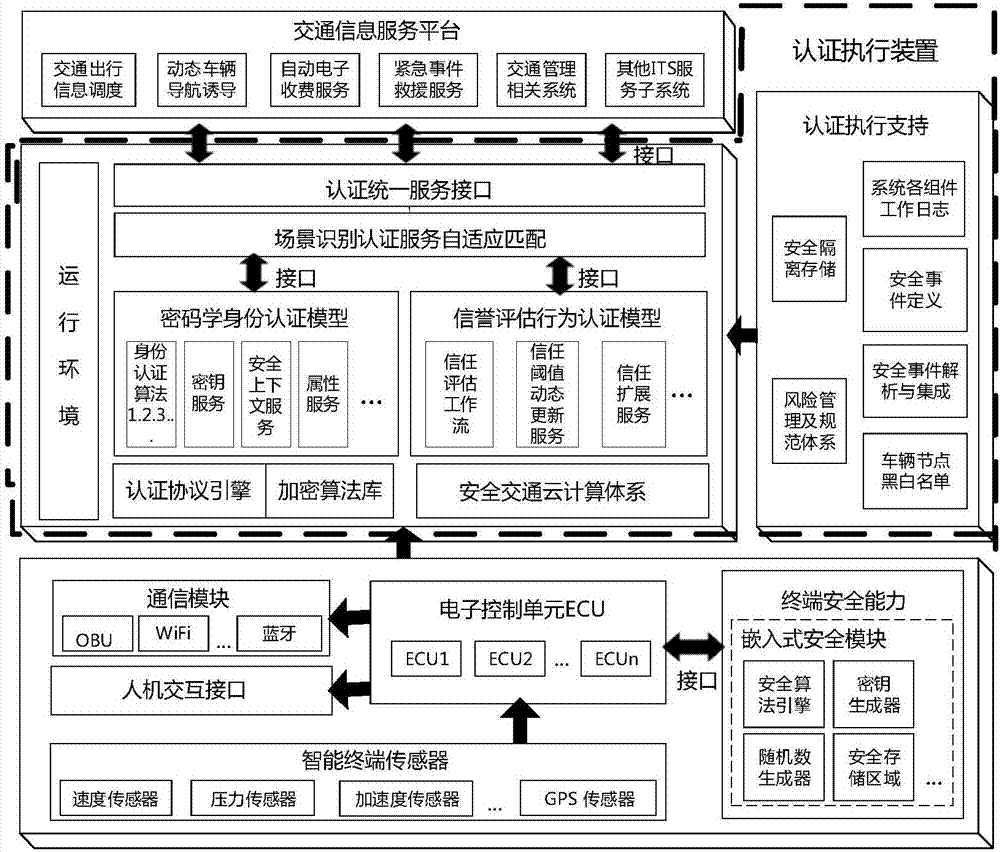
Internet of vehicles security authentication device and method
A security authentication and Internet of Vehicles technology, applied in electrical components, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0033] The technical scheme that the present invention solves the problems of the technologies described above is:
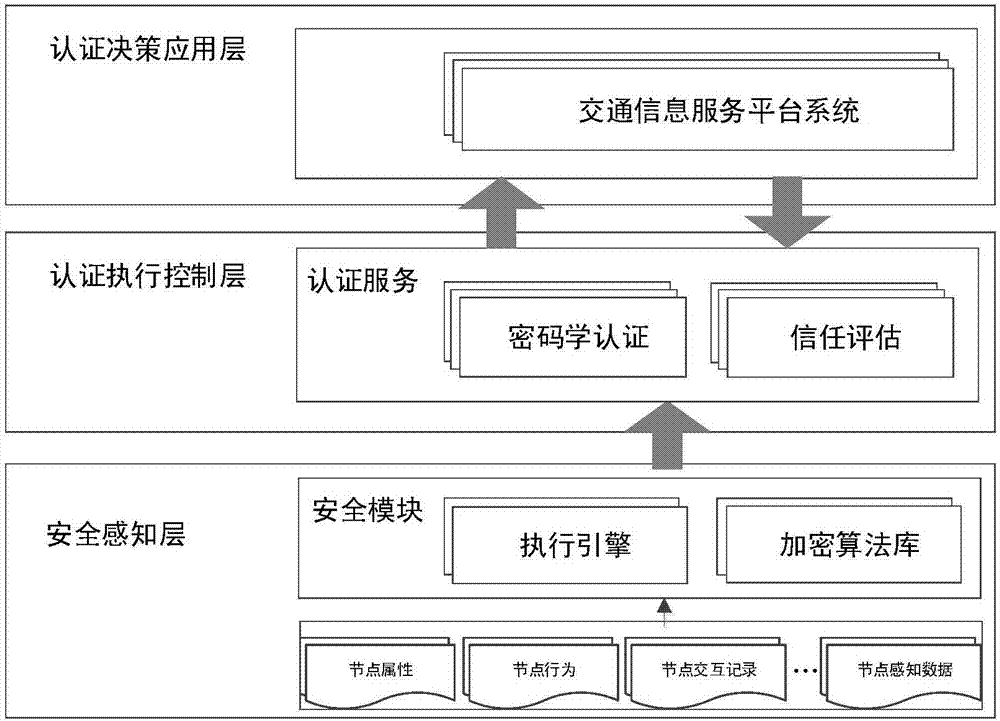
[0034] Such as figure 2 Shown is a hierarchical diagram of the authentication strategy design in the Internet of Vehicles divided by the present invention. The authentication strategy design layers defined in the present invention are: security perception layer, authentication execution control layer, and authentication decision-making application layer, wherein:
[0035] Security-aware layer: the bottom layer of the three-layer structure of authentication policy design. Done by embedded security developers. The trusted security module that encapsulates the encryption algorithm component...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com