Authentication method for wearable device
A technology of wearable devices and authentication methods, applied in electrical components, wireless communications, security devices, etc., can solve problems such as increased chip design costs and difficulty in device integration, and achieve the effect of avoiding the increase in design difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
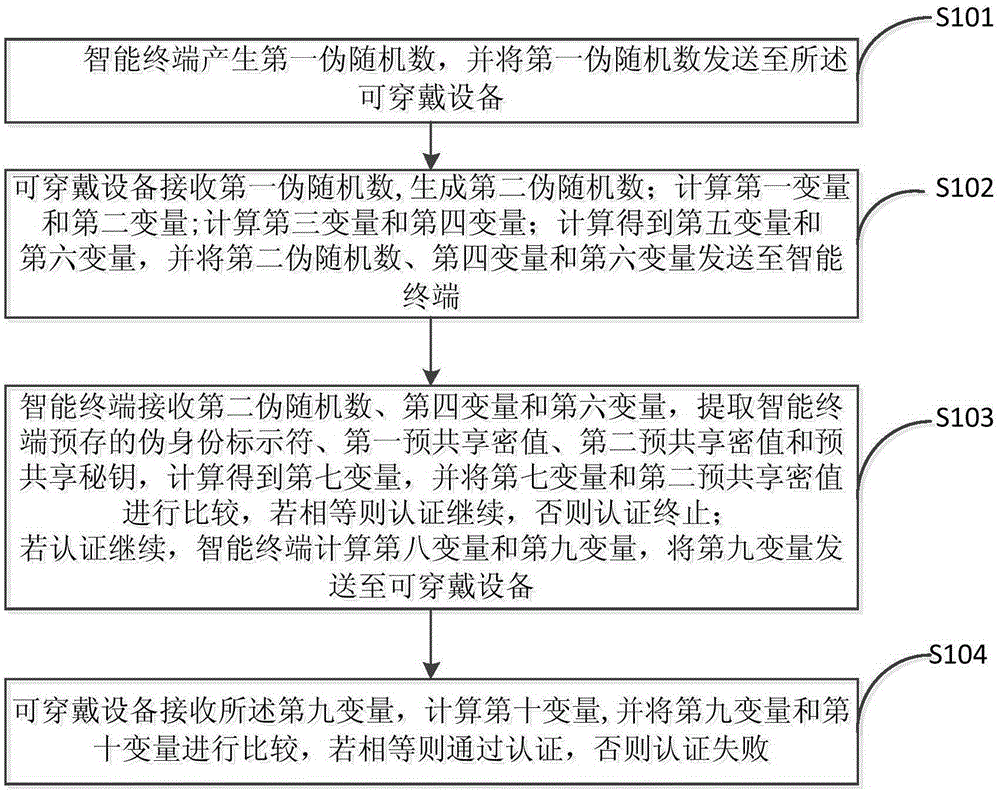
[0020] figure 1 A flow chart of the authentication method for the wearable device provided in the first embodiment is given.
[0021] Such as figure 1 , the authentication method of the wearable device provided in the first embodiment includes:
[0022] S101. The smart terminal generates a first pseudo-random number r p , and the first pseudorandom number r p sent to the wearable device.
[0023] It should be noted that the smart terminal generates the first pseudo-random number r through its internal random function generator p . Among them, the role of the random function generator is to generate a random number within a given range.
[0024] The smart terminal sends the first pseudo-random number r p Send it to the wearable device and use it as an access request to start a new session cycle.
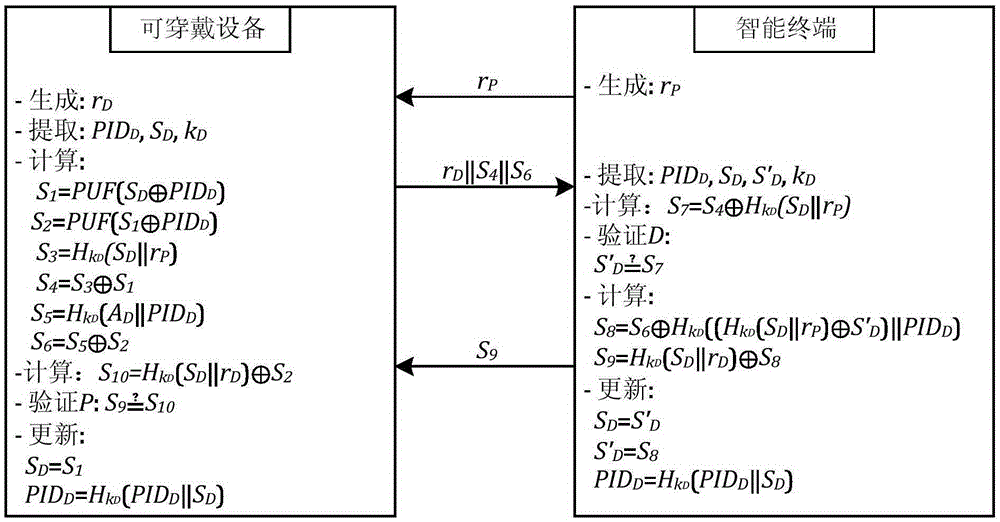
[0025] S102. The wearable device receives the first pseudo-random number r p , to generate the second pseudo-random number r D ;calculate the first variable ...
Embodiment 2
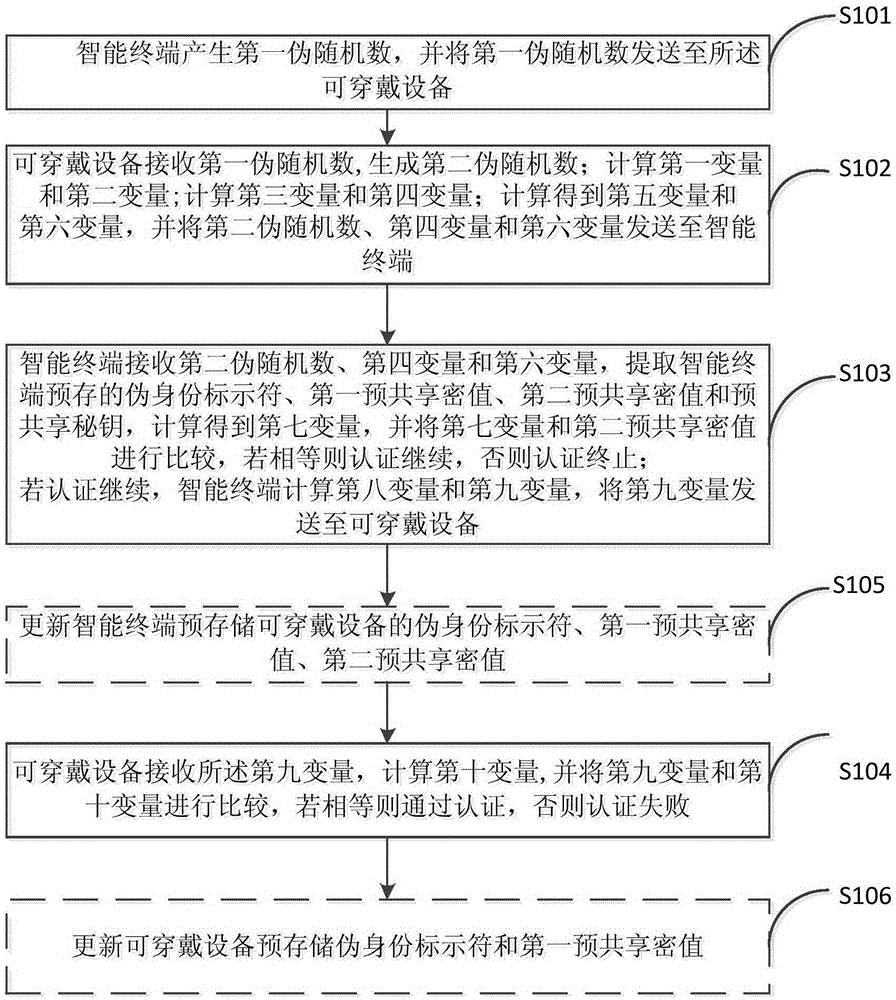
[0072] figure 2 It is a flow chart of the authentication method of the wearable device provided in Embodiment 2 of the present invention.
[0073] Depend on figure 2 As shown, an authentication method for a wearable device includes: Step S101 to Step S106. Wherein, steps S101-S104 have been described in Embodiment 1, and will not be repeated here. In addition, there are:
[0074] S105. Update the smart terminal to pre-store the pseudo-identity identifier PID of the wearable device D , the first pre-shared secret value S D and the second pre-shared secret value S' D .
[0075] After step S103 ends, the smart terminal will check the pre-stored pseudo-identity identifier PID D , the first pre-shared secret value S D and the second pre-shared secret value S' D To update, the update process is as follows:
[0076] The existing second pre-shared secret value S' D Assign the first pre-shared secret value: S D =S' D ;
[0077] The eighth variable S calculated in step S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com