Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Security as a service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security as a service (SECaaS or SaaS) is a business model in which a service provider integrates their security services into a corporate infrastructure on a subscription basis more cost effectively than most individuals or corporations can provide on their own, when total cost of ownership is considered. SECaaS is inspired by the "software as a service" model as applied to information security type services and does not require on-premises hardware, avoiding substantial capital outlays . These security services often include authentication, anti-virus, anti-malware/spyware, intrusion detection, Penetration testing and security event management, among others.
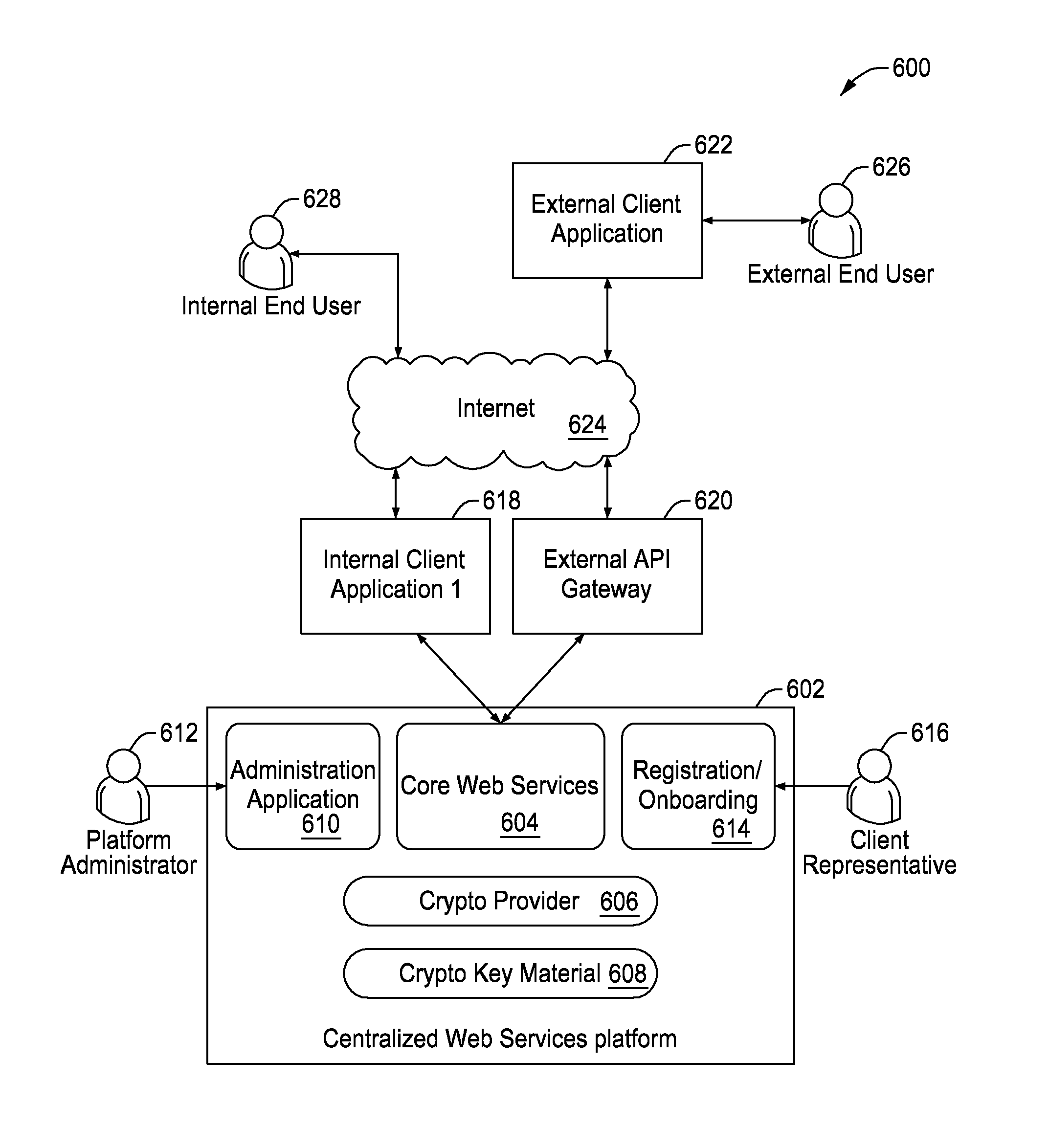
Systems and methods for cryptographic security as a service
A system and a computer-based method for providing bundled services to a client application in a service call to a service system in a service provider computer system includes receiving a message defining an API service request comprising at least a parameter portion and a payload portion, determining at the gateway system an identity of an application transmitting the received message using identity information that has been established within the service provider computer system, providing, by a services platform, at least one of encryption services and decryption services for data contained in the payload portion using the parameters received in the parameter portion, managing key material for security of the data, and transmitting the encrypted data back to the calling application.
Owner:MASTERCARD INT INC
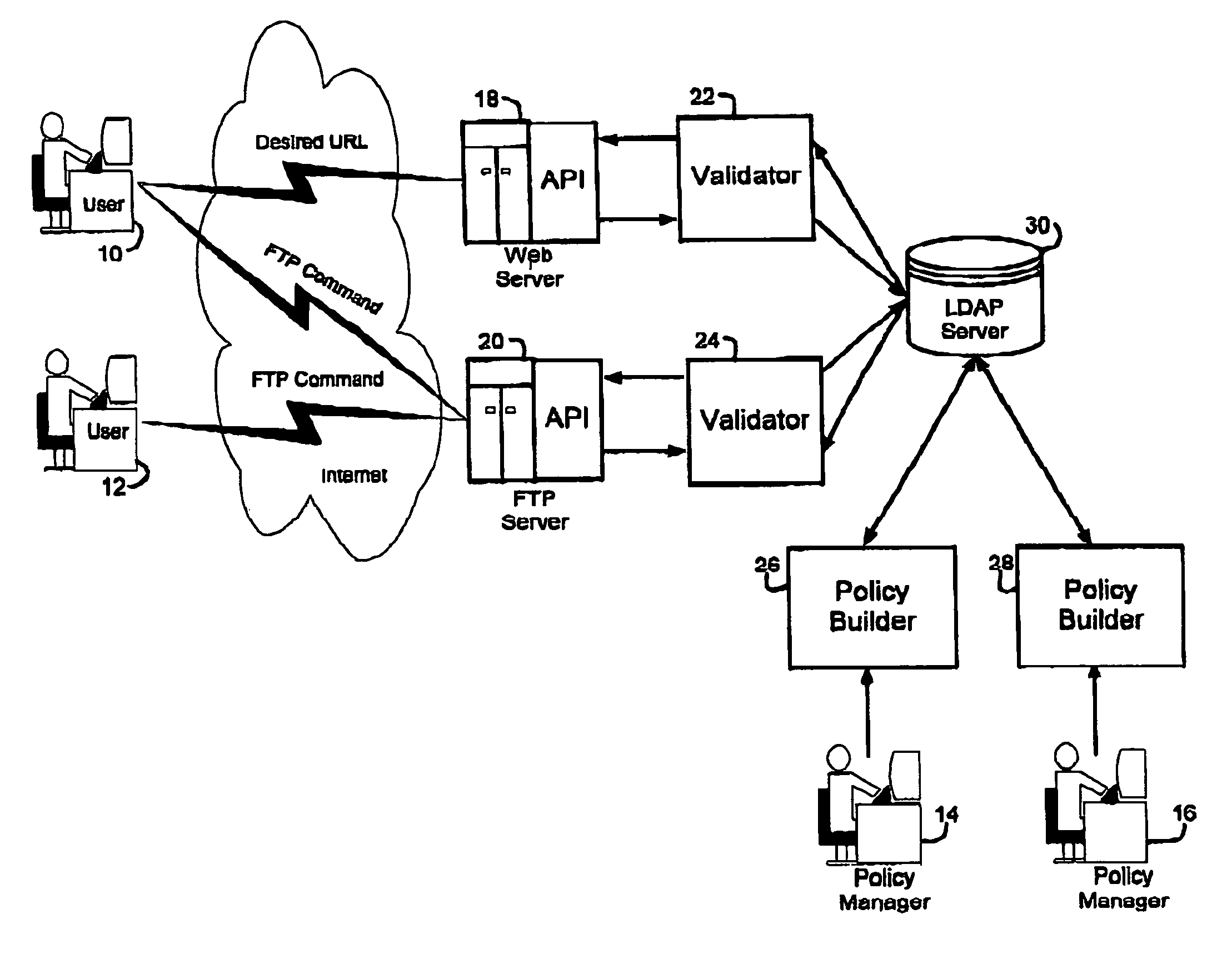
Computer system security service
InactiveUS7757271B2Digital data processing detailsComputer security arrangementsAccess networkGraphics
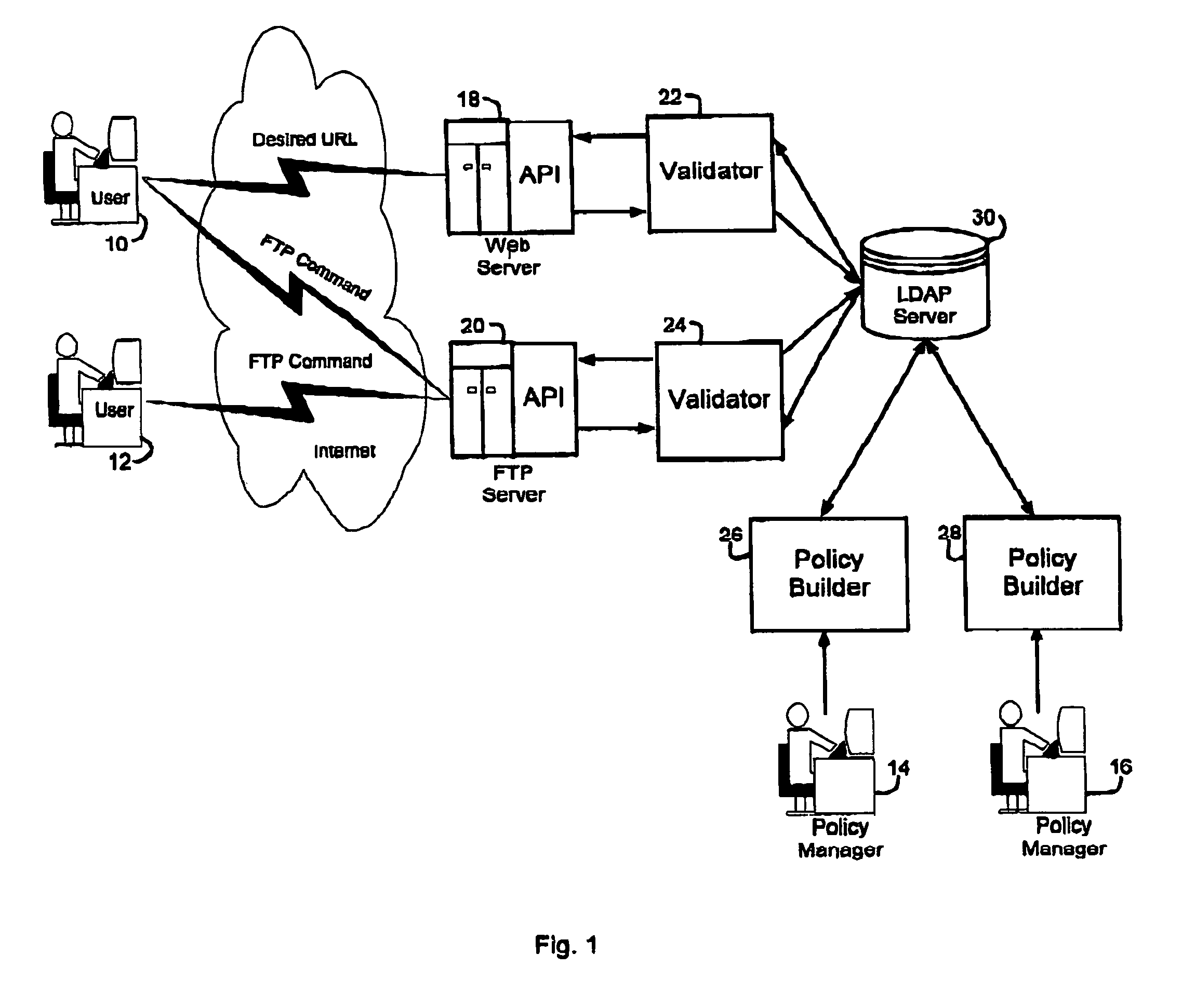
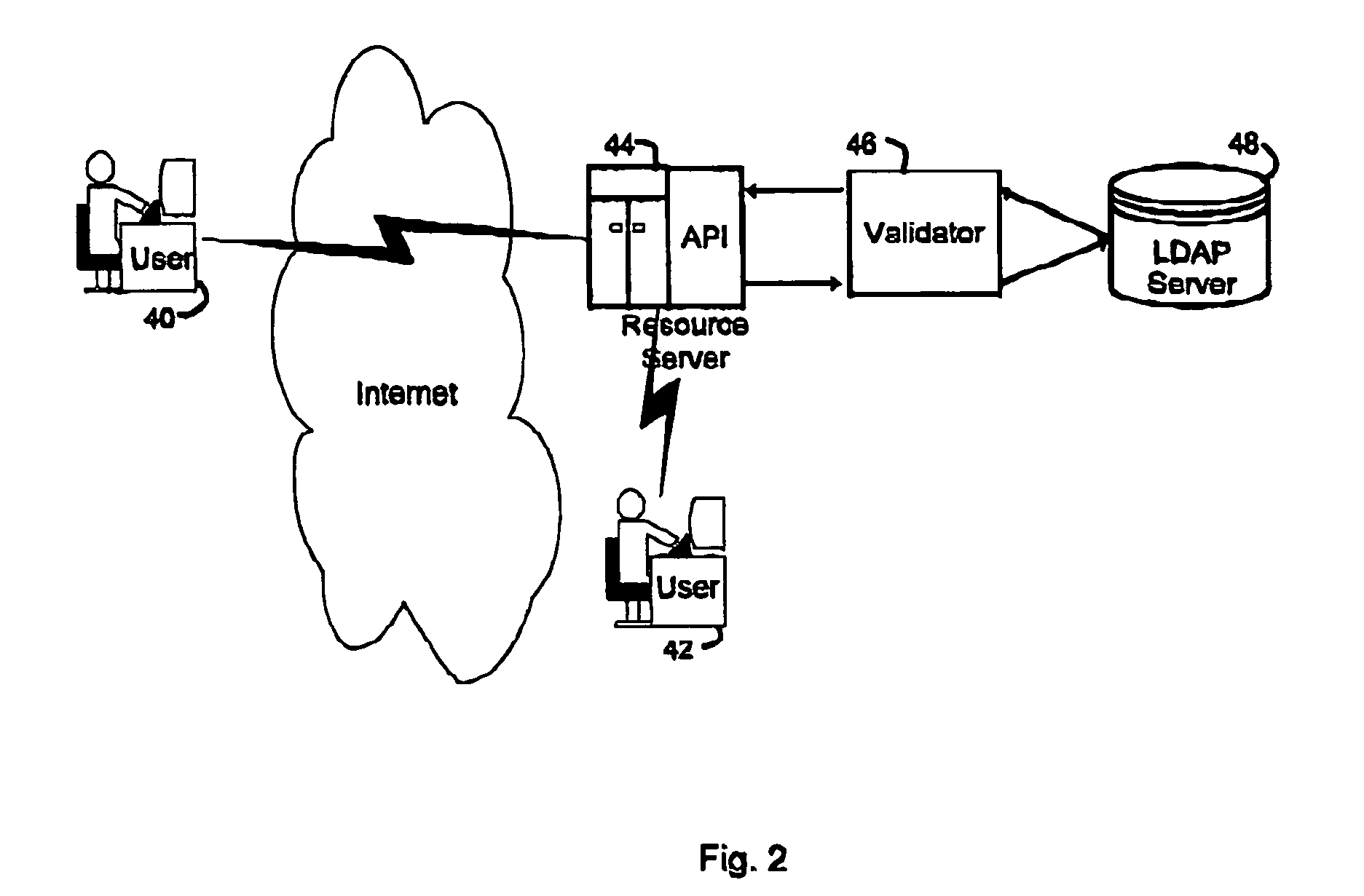
A security service of computer networks having a policy builder, an LDAP-compliant database, a validator and an API. The policy builder component provides a graphical user interface to be used by a policy manager to define access policies for users seeking to access network services and resources. The graphical user interface has a grid of nodes representing access policies. The grid is arranged to correspond to a defined tree structure representing services and resources and a business relationship tree structure representing users. The graphical user interface permits the policy manager to define policy builder plug-ins for access policy customization. The LDAP-compliant database maintains the policy builder plug-ins. The validator component receives requests from users and queries the LDAP-compliant database to obtain relevant access policies as defined by the policy manager. The system provides for double inheritance of access policies such that where there is no express definition of an access policy for a node, the access policies are propagated according to the hierarchical structures of the data. The validator includes validator plug-ins for carrying out access policies corresponding to the access policies defined by policy builder plug-ins.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method of providing cyber security as a service
InactiveUS20140259095A1Memory loss protectionError detection/correctionChange managementNetworked system
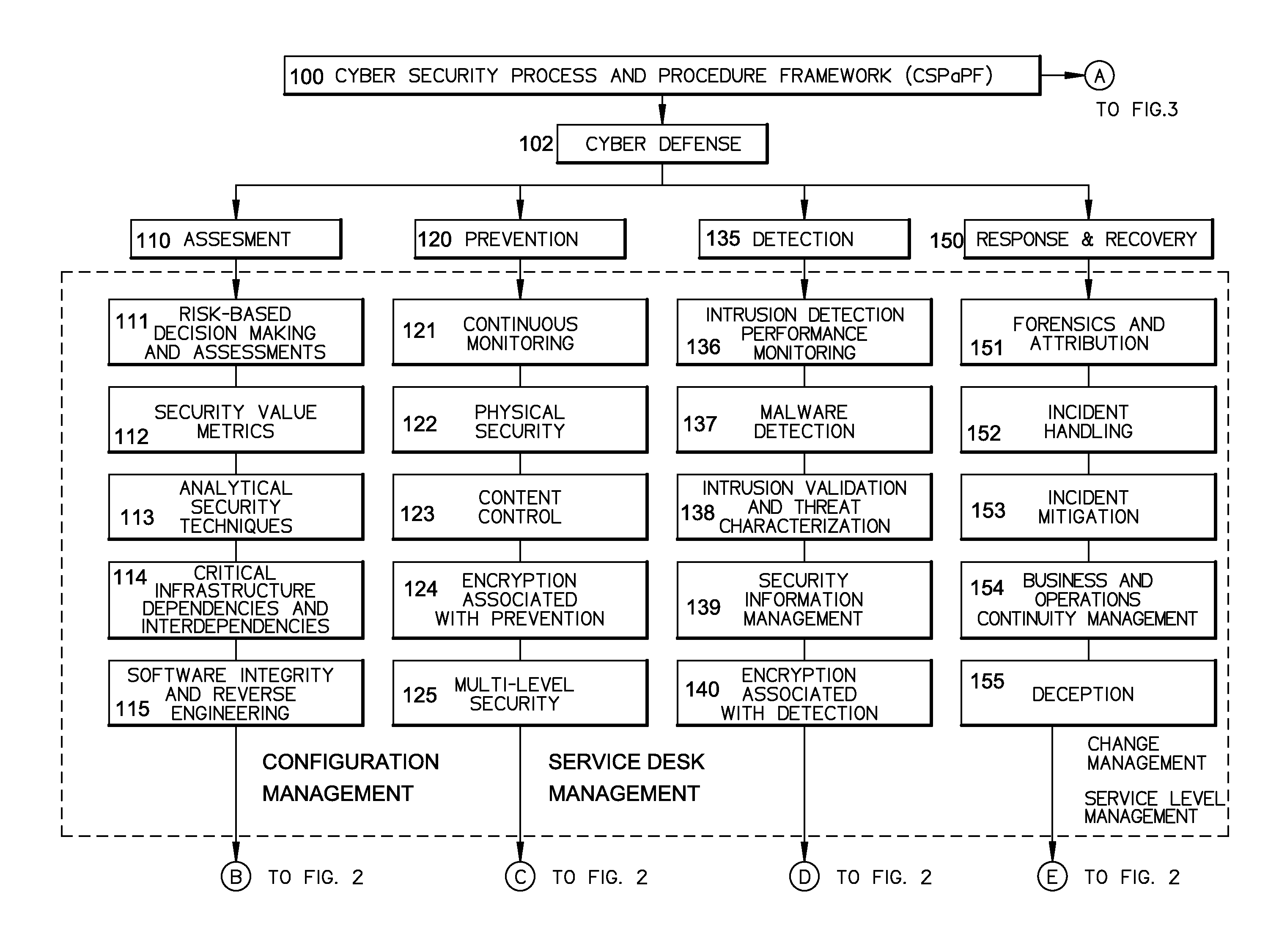
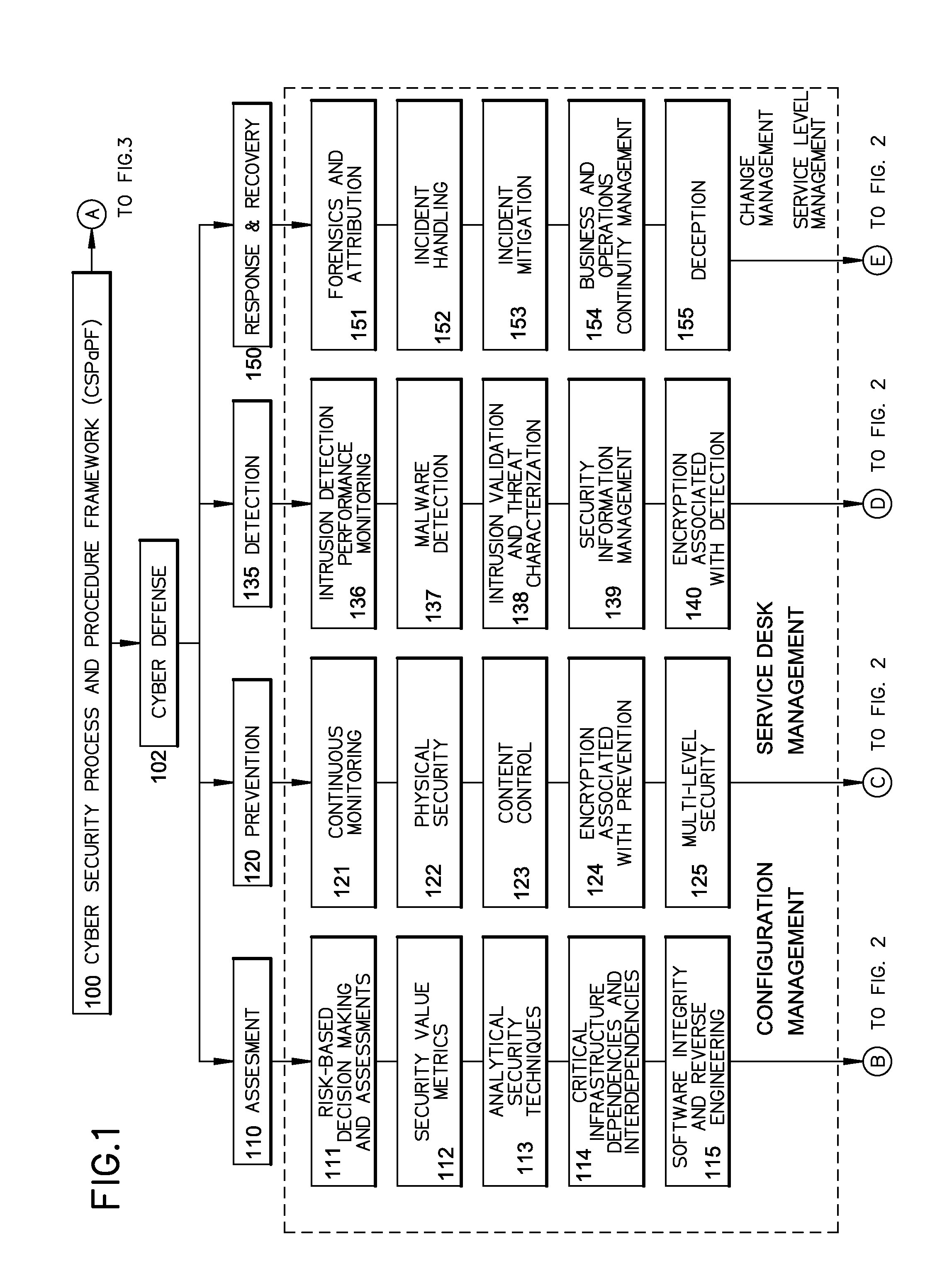
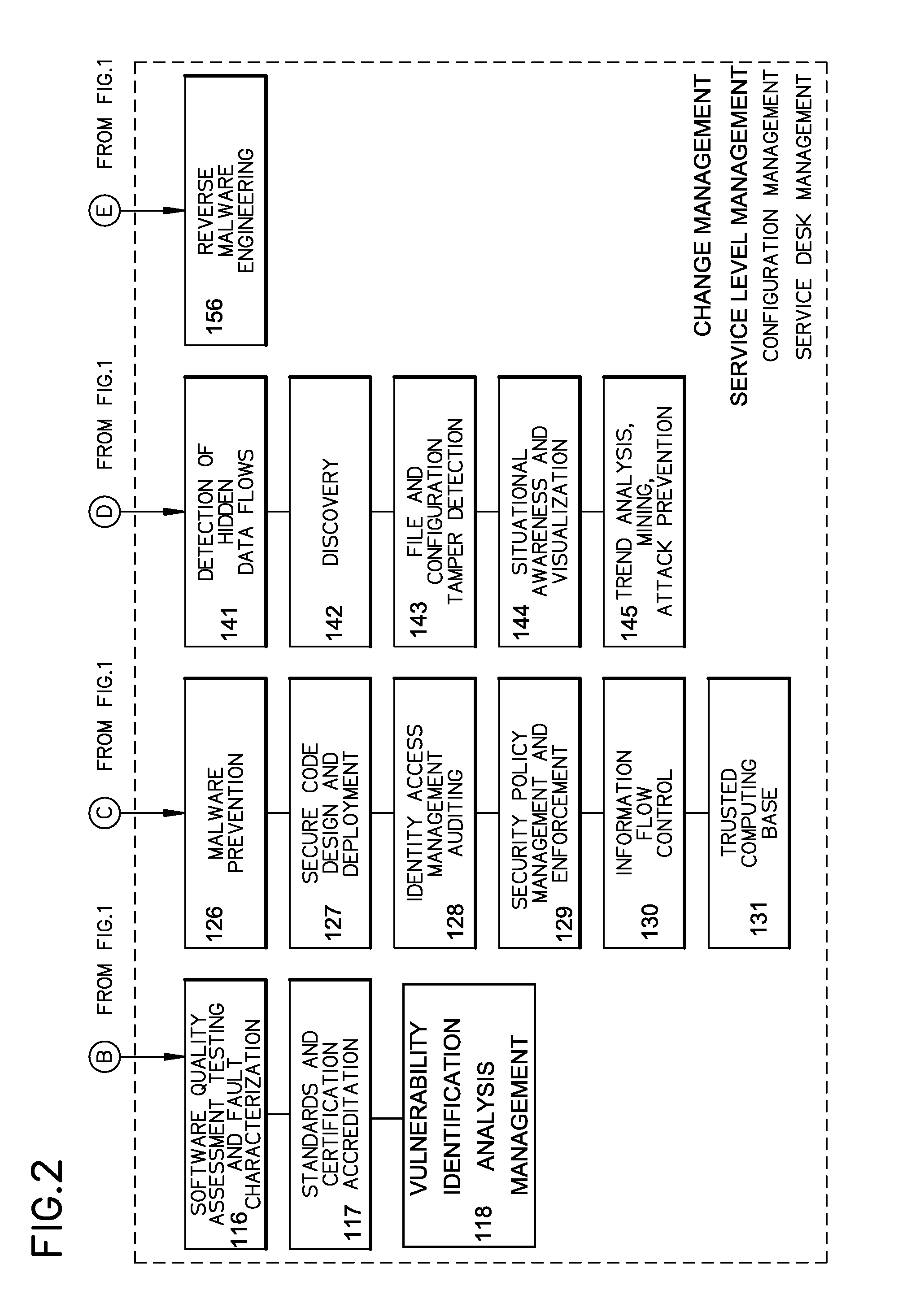
A cyber system including a method of providing cyber security as a service is provided. The cyber system may include an integrated architecture of defensive and offensive security procedures and processes that enable enterprises to practice safe, holistic security techniques. The plurality of cyber defense procedures may include a plurality of risk-based assessment procedures, a plurality of attack-prevention procedures, a plurality of detection procedures and a plurality of response and recovery procedures. The plurality of cyber offense procedures may include a plurality of cyber weapon procedures, a plurality of cyber Intelligence, surveillance and reconnaissance procedures, a plurality of information operations target exploitation procedures and a plurality of information operations attack procedures. The cyber system may also include a plurality of overlapping processes interconnecting the plurality of cyber offense procedures and plurality of cyber defense procedures. The plurality of overlapping processes may include a change management, a configuration management, a service desk and a service-level management. The change management may be structured within an enterprise for ensuring that changes in people, facilities, technology and / or processes are smoothly and successfully implemented to achieve lasting benefits. The configuration management may establish and maintain the consistency of a product's performance, functional and physical attributes with its requirements, design and operational information throughout its life. The service desk may provide the communication needs of the users, employees and customers. Service-level management may assess the impact of change on service quality and establish performance metrics and benchmarks.
Owner:BRYANT JAMES ALVIN
Offloaded Security as a Service
ActiveUS20140105103A1Network traffic/resource managementBroadcast service distributionTraffic flowMalware
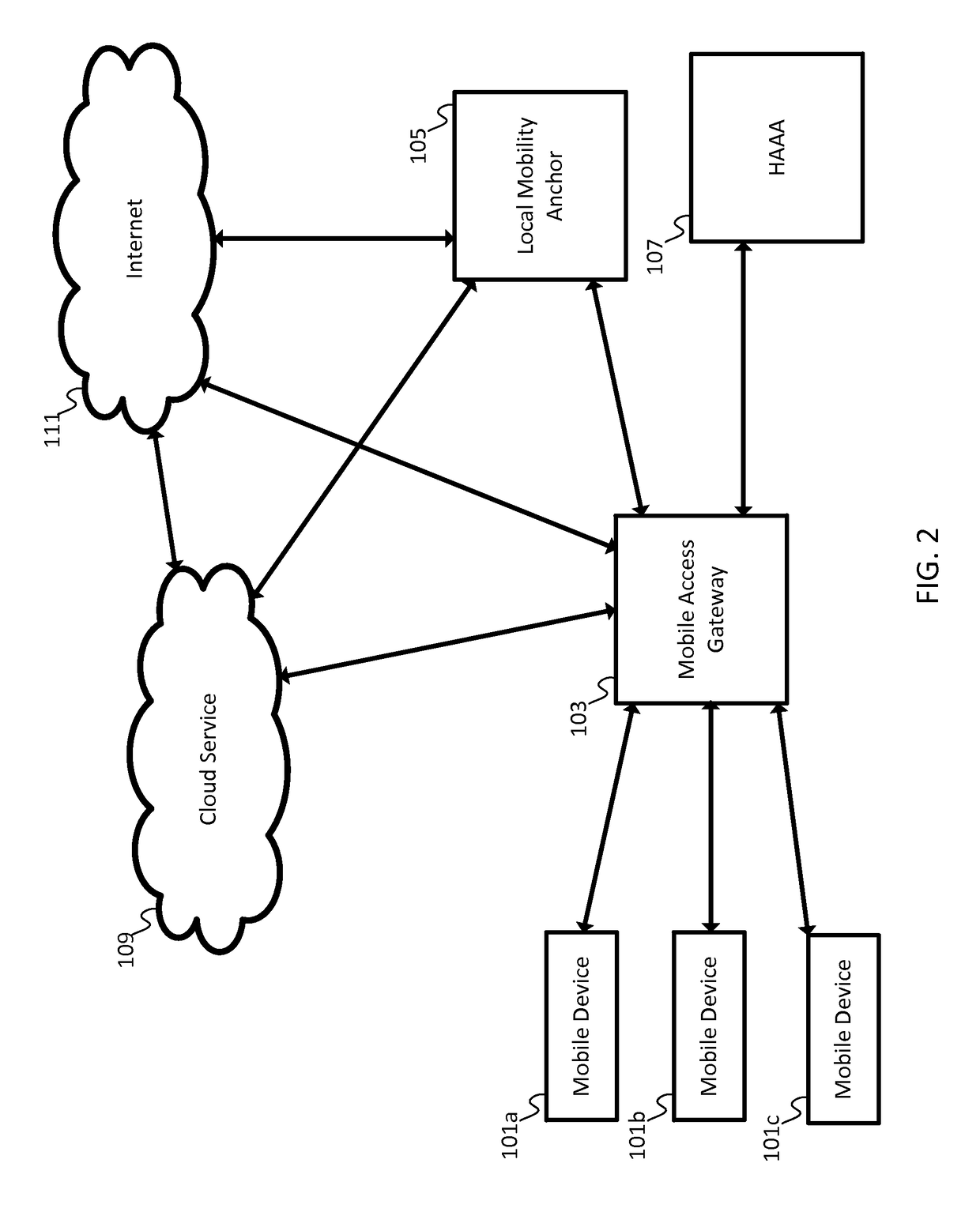
In one implementation, traffic in a mobile network is offloaded to a security as a service server or a cloud server. A mobile access gateway (MAG) in the mobile network identifies one or more mobile nodes that are configured for communication on the mobile network. The MAG receives a message that includes an address of a mobile node and sends a request based on the message to the security as a service server. The MAG forwards traffic flows to the security as a service server according to the message, which is configured to detect an indication of malicious software in the traffic flows and / or filter content of the traffic flows according to a user profile.
Owner:CISCO TECH INC
Method and system for administration of security services within a virtual execution environment (VEE) infrastructure
ActiveUS8074276B1Eliminate disadvantagesMemory loss protectionDigital data processing detailsManaged security serviceAnti virus
A system and method for managing administration of security services provided to users includes a computer system and an operating system running on the computer system. A plurality of Virtual Execution Environments (VEEs) are executed on the computer system. The VEEs can be any of a Virtual Private Server, a Virtual Machine, a Hypervisor-based Virtual Machine, and a Lightweight Hypervisor-based Virtual Machine, a session of Terminal Server and a session of Presentation Server, Lightweight Hypervisor-based Virtual Machines, VMM-based VMs or hypervisor-based VMs. Each VEE provides a set of services to remote users. One or more designated VEE(s) provide security services to each of the VEEs based on the needs of the remote users of the particular VEEs. The security services provided by the designated VEE can be firewall services, spam filtering and anti-virus protection. The security services are controlled and administered by each of the VEEs requesting a particular service via control means of the designated VEE(s).
Owner:MIDCAP FINANCIAL TRUST
Implementing method and system for could security service
InactiveCN104601530ARespond quicklyEasy to handleTransmissionSecurity operations centerSecurity as a service
The invention discloses an implementing method and an implementing system for cloud security service. The method includes the steps that: security middleware receives an executing message from a cloud security operating center, wherein the security middleware is preset in a security engine layer, and the cloud security operating center is preset in a managing layer; the security middleware executes corresponding dynamic security operation according to the executing message, and thereby obtaining an execution result; the security middleware dynamically regulate a cloud security strategy according to the execution result. According to the implementing method and system for cloud security service, the efficiency for quickly responding to security threat and dealing with security events in the case of no manual intervention can be improved.
Owner:ZTE CORP
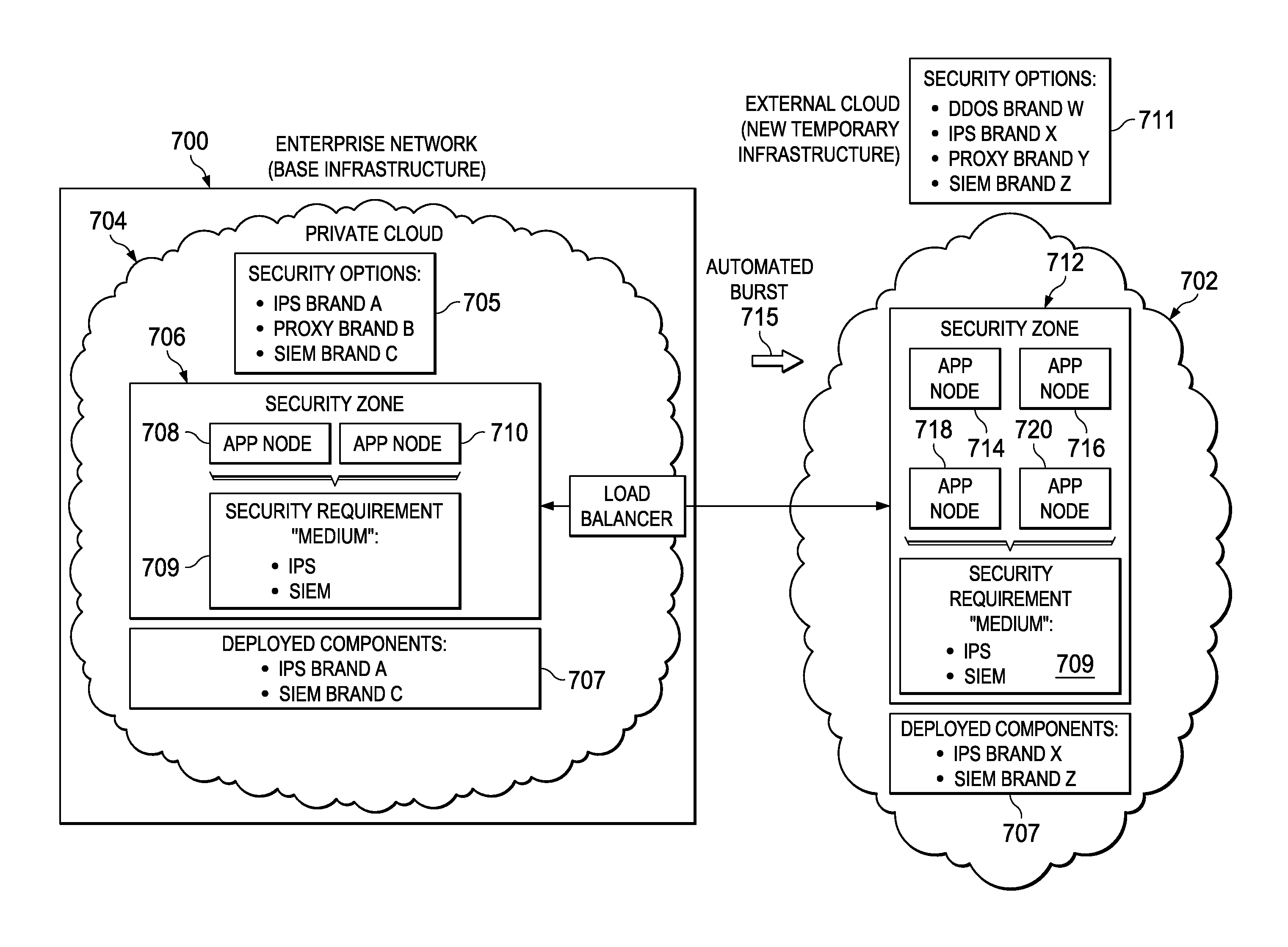
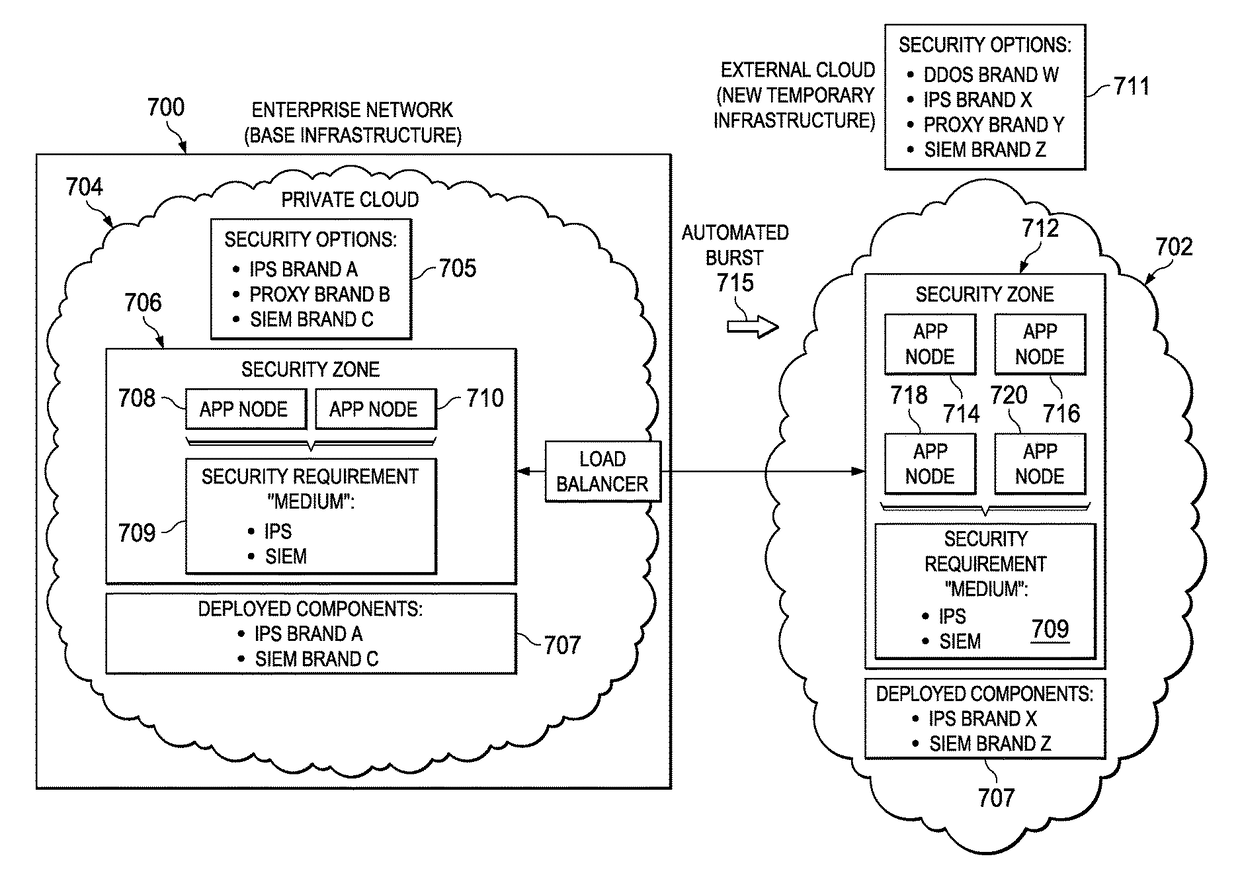
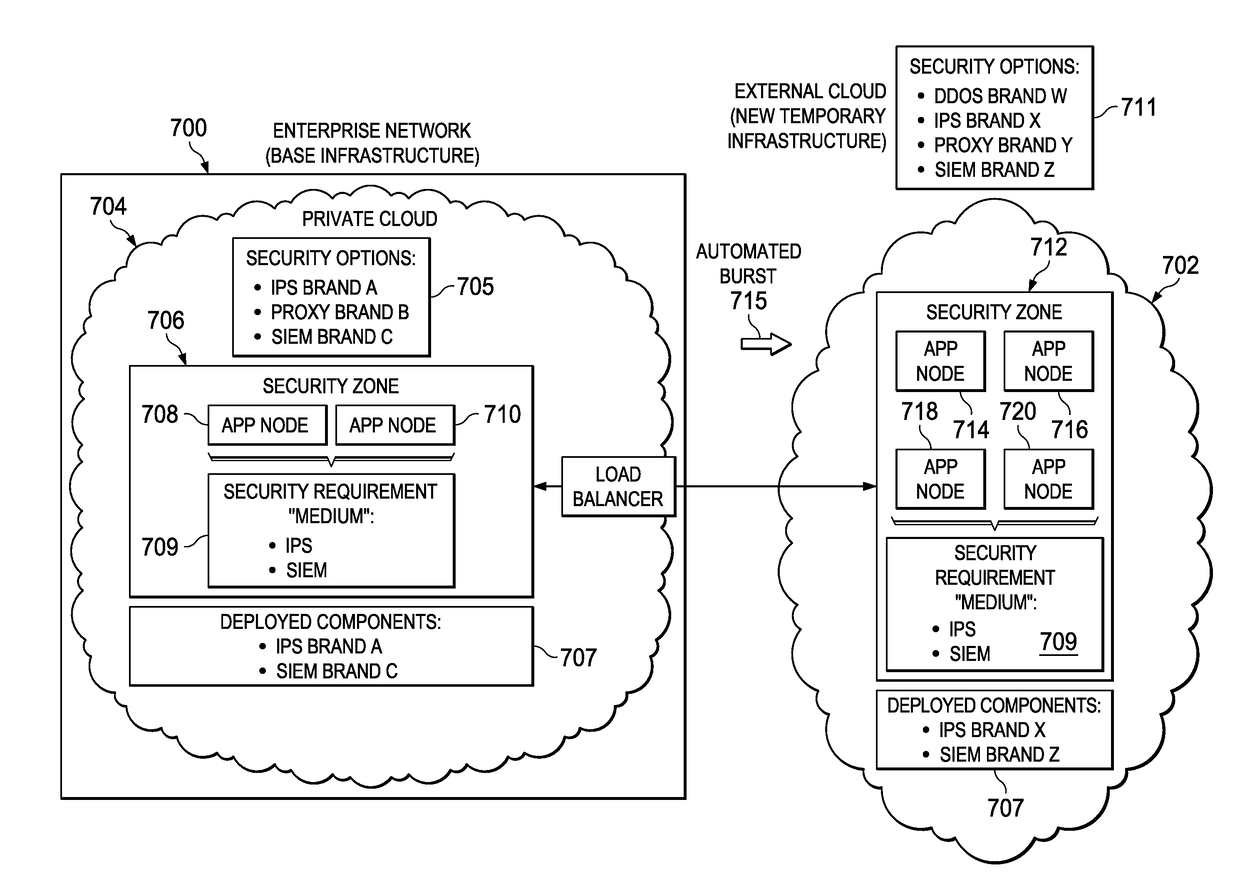
Secure application zones for cloud burst environments
A cloud infrastructure security assurance service is enhanced to facilitate bursting of cloud applications into other cloud infrastructures. The security assurance service provides a mechanism to enable creation and management of secure application zones within a cloud infrastructure. When the security assurance service receives an indication that a workload associated with a cloud application triggers a cloud burst, the service is extended into a new cloud infrastructure. Once the security assurance service is instantiated in the new cloud infrastructure, it identifies the broad security requirements of the application, as well as the security capabilities of the new environment. Using this information, the security assurance service computes a minimal security environment needed by the cloud application for the burst operation. The security assurance service then configures the necessary topology in the new cloud environment, and the burst operation is then completed by having the cloud application deployed in that topology.
Owner:IBM CORP
Coordination of multipath traffic
ActiveUS20150026756A1Digital data processing detailsMultiple digital computer combinationsData streamNetwork connection
In one implementation, traffic in a mobile network is directed across multiple paths to a single cloud server or security server (e.g., a security as a service). The mobile device detects a cloud connector through a primary connection based on an attachment or connection via a first interface of a mobile device. The mobile device sends a request to the cloud connector for an identification of a cloud security server associated with the cloud connector. After receiving the identification of the cloud security server, the mobile device directs one or more subsequent data flows or subflows for a second interface or another interface of the mobile device to the cloud server or security server. The second data flow and the second interface are associated with another network that is external to the enterprise network and trusted network connection or not associated with the enterprise network and the trusted network connection.
Owner:CISCO TECH INC
Providing security services on the cloud
ActiveUS8479008B2User identity/authority verificationComputer security arrangementsComputer usersComputerized system
Owner:MICROSOFT TECH LICENSING LLC
System and Method For Cryptographic Keys Security in the Cloud
ActiveUS20200250318A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesSecurity solutionThird party
There is provided an improved method or security solution for securing cryptographic keys in a virtual machine RAM. A security solution is proposed to hide cryptographic keys in the cloud, without the necessity of any architectural modifications. The present solution only requires the availability of a Trusted Platform Module (TPM) capable of creating and holding a protected public / private key pair. It lends itself to security-as-a-service scenarios where third parties perform encryption or decryption on behalf of data owners. This allows the present solution to be easily integrated and coupled with other existing cloud architectures. A decrypt-scatter or gather-decrypt solution which allows users to carry out encryption or decryption while protecting keys from unauthorized peeks by the cloud administrators is proposed.
Owner:AL BELOOSHI BUSHRA ABBAS MOHAMMED
Internet risk management method and system based security as service
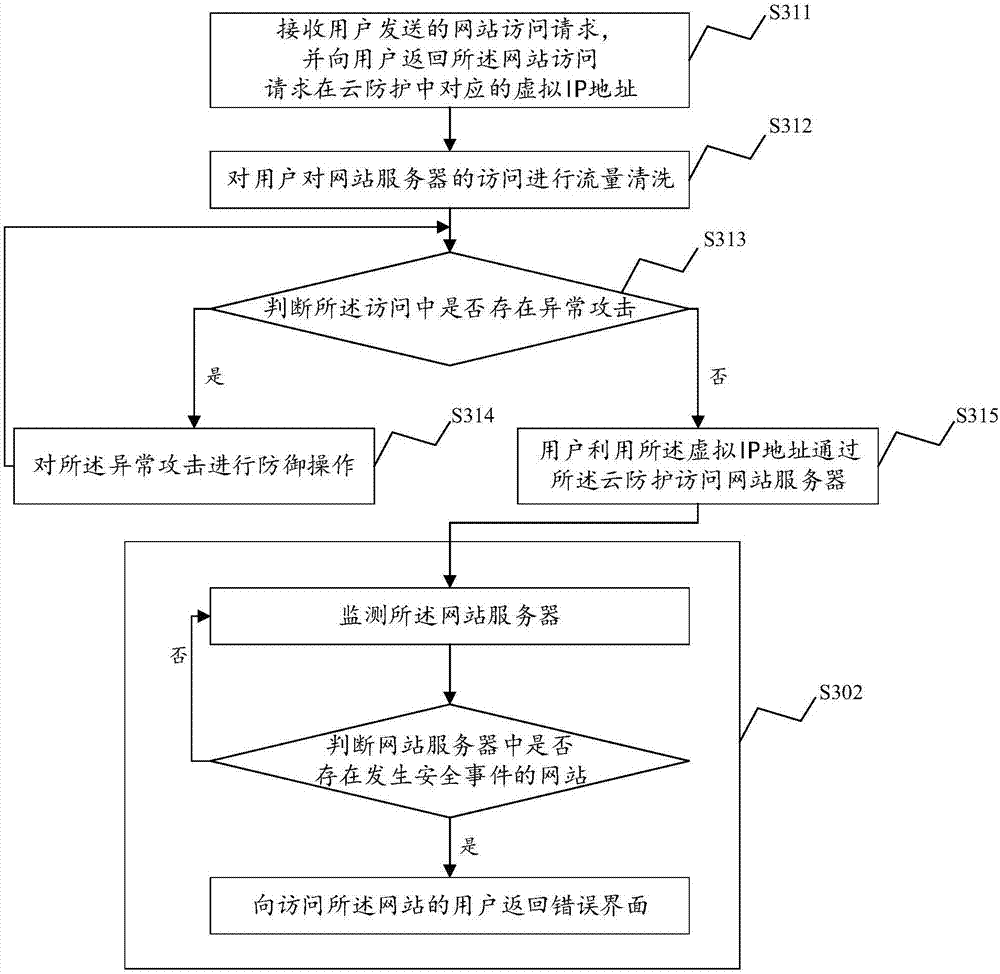
InactiveCN107277080AImprove protectionQuick Control Range of InfluenceTransmissionIp addressCloud detection
The invention discloses an internet risk management method based on security as service. The method comprises the following steps: receiving a website access request transmitted from a user, and returning an IP address which corresponds to the website access request to the user so that the user can visit a website server through the IP address; and monitoring the website server, and returning a mistaken interface to the user who visits the website when a website in which security events occur in the website server. According to the internet risk management method provided by an embodiment, the website server is detected through cloud detection; when the security events occur, website access operation of the user is intercepted automatically, and response is in time; and steps of deployment of security equipment such as a firewall are omitted, and the running and maintenance cost is low. Meanwhile, only the ability of cloud detection and monitoring of the security events needs to be updated, and the protecting ability of the system to a website server can be improved. The invention further discloses an internet risk management system, and the technical effect can also be achieved.
Owner:SANGFOR TECH INC
Coordination of multipath traffic
ActiveUS9185562B2Multiple digital computer combinationsSecurity arrangementTraffic capacityData stream
In one implementation, traffic in a mobile network is directed across multiple paths to a single cloud server or security server (e.g., a security as a service). The mobile device detects a cloud connector through a primary connection based on an attachment or connection via a first interface of a mobile device. The mobile device sends a request to the cloud connector for an identification of a cloud security server associated with the cloud connector. After receiving the identification of the cloud security server, the mobile device directs one or more subsequent data flows or subflows for a second interface or another interface of the mobile device to the cloud server or security server. The second data flow and the second interface are associated with another network that is external to the enterprise network and trusted network connection or not associated with the enterprise network and the trusted network connection.
Owner:CISCO TECH INC
Distributed encrypted service gateway and implementation method thereof
ActiveCN106850549AEasy to implementMeet application security requirementsNetwork connectionsTTEthernetApplication server
The invention provides a distributed encrypted service gateway and an implementation method thereof. The gateway comprises a basic network service sub-system, a security service sub-system and a communication service sub-system communicating with each other, wherein both the basic network service sub-system and the security service sub-system communicate with a user application via the communication service sub-system. The method comprises the steps of providing a basic gateway; configuring the basic network service sub-system and the communication service sub-system on the basic gateway; and configuring the security service sub-system on the basic gateway, thus acquiring the distributed encrypted service gateway, wherein the security service sub-system provides security service for the basic gateway via an encrypted server cluster can be accesses remotely. According to the gateway and the implementation method thereof provided by the invention, security service, network service and reliable and flexible gateway of application server for the user application via the distributed software and hardware system module, extremely high redundancy and expansibility are provided, the Internet application security requirement in the age of big data can be met, and a reliable path is provided for secure utilization and flexible control of the network.
Owner:北京江南博仁科技有限公司
Offloaded security as a service
ActiveUS10231120B2Network traffic/resource managementBroadcast service distributionMalwareTraffic flow
Owner:CISCO TECH INC
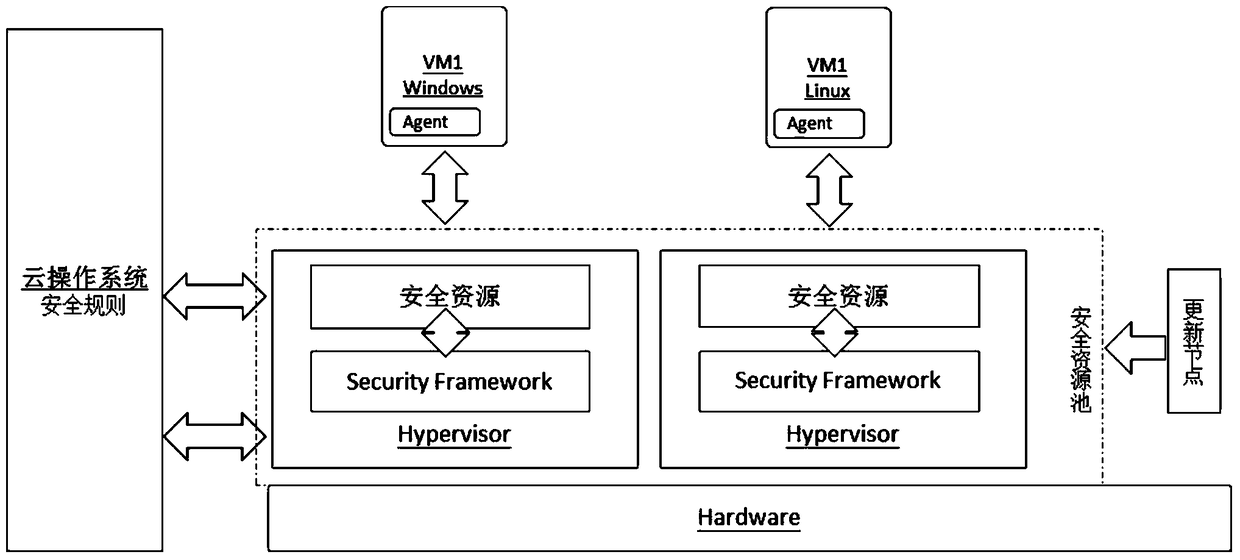
System and method for providing SaaS (Security as a Service) in cloud operating system
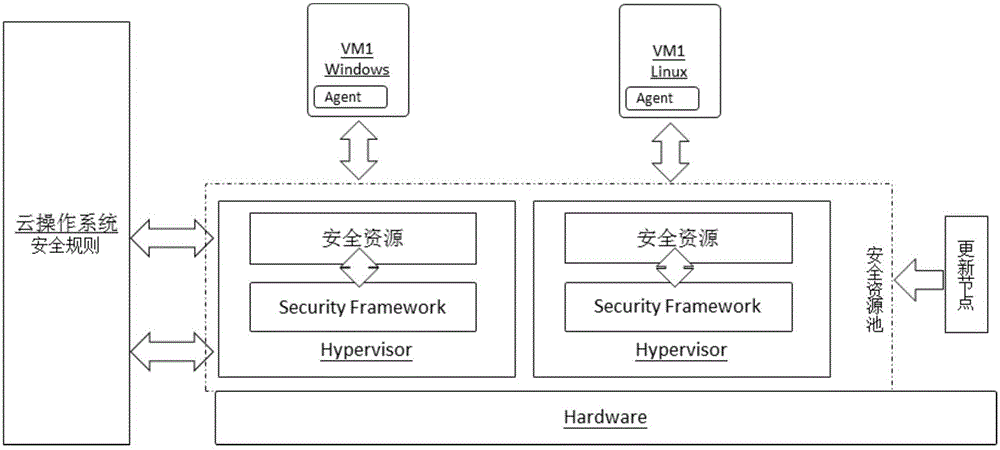
The invention discloses a system and a method for providing SaaS (Security as a Service) in a cloud operating system. The system comprises a security resource pool used for centralizing security resources for pooling and providing security service for a virtual machine; an updating node used for linking to a security updating library and updating resources in the security resource pool; and a security terminal agent used for deploying a security agent program in the virtual machine and carrying out safety protection on the virtual machine through interacting with the security resource pool. According to the system and the method, the operation and maintenance efficiency of a cloud data center is improved and the operation and maintenance cost is reduced. A comprehensive and timely security protection is provided for the virtual machine in the cloud operating system, and the network storm of a computational node, which is caused by updating of security features under the conventional security protection mode, is avoided.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Secure application zones for cloud burst environments
Owner:INT BUSINESS MASCH CORP
Providing scalable cloud-based security services
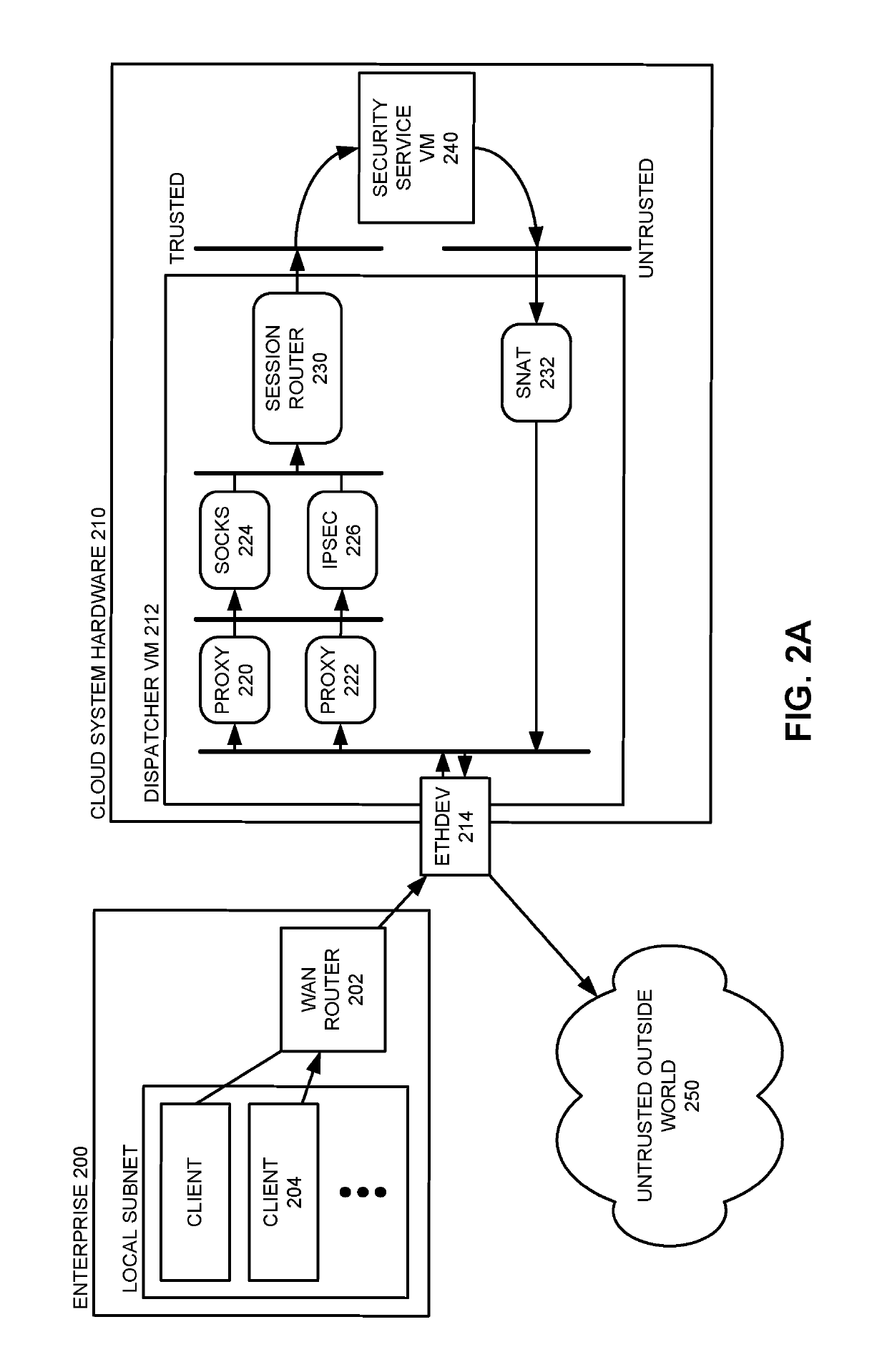
ActiveUS10419394B2Cost of financingReduce financial costsPlatform integrity maintainanceTransmissionCloud data centerClient-side
The disclosed embodiments disclose techniques for providing a cloud-based security service. During operation, a dispatcher virtual machine (VM) executing in a cloud data center receives a network request from a remote enterprise client. The dispatcher VM executes multiple docker containers, including a set of ingress docker containers that decode the request and then forward it to a session router docker container that in turn forwards the request to a set of security service VMs. After these security service VMs have analyzed the contents of the request and determined that the request is valid and permitted, a SNAT docker container then sends the request out to an untrusted network to be serviced.
Owner:NUBEVA INC
Hardware architecture based on hardware security isolation execution environment and measurement method applying context integrity
ActiveCN108595983AAccurate acquisitionReduce overheadInternal/peripheral component protectionContextual integrityHardware architecture
The present invention provides a hardware architecture based on a hardware security isolation execution environment and a measurement method applying context integrity. The hardware architecture comprises security isolation hardware, a security manager, a security service driver layer, and a security service interface layer, wherein the security isolation hardware provides a configurable hardwareisolation environment; the security manager can configure the security isolation hardware to work in a normal domain or a security domain; the security service driver layer is located in a kernel space of the normal domain for providing security services for a user space; and the security service interface layer is located in the kernel space of the security domain for providing security servicesfor the user space in the security domain. The security manager can perform conversion between the normal domain and the security domain, the security service driver layer calls the security manager to switch from the normal domain to the security domain, and the security service interface layer calls the security manager to switch from the security domain to the normal domain. The hardware architecture based on the hardware security isolation execution environment and the measurement method applying context integrity in the invention support both the measurement of the integrity of the code and the dynamic measurement to detect whether the code is tampered with by a malicious program.
Owner:XUCHANG UNIV
Providing security in a cloud storage environment
InactiveUS20140137214A1Digital data processing detailsMultiple digital computer combinationsControl storeSecurity level
A method of providing security as a service in a cloud storage environment includes storing, through a cloud manager of the cloud storage environment, a security level of access of a storage controller associated with a customer of the security as a service, and receiving a request from the customer to access security information of the storage controller associated therewith. The method also includes providing, through the cloud manager, security information of the storage controller associated with the customer in accordance with the request and the stored security level of access of the storage controller associated with the customer.
Owner:NETWORK APPLIANCE INC
Methods and systems for 5g slicing based on dynamic security properties
ActiveUS20220217540A1Network traffic/resource managementTransmissionSecurity propertiesSecurity parameter
Systems and methods enable the provisioning of security as a service for network slices. A network device stores definitions of multiple security assurance levels for network slices based on security parameters of assets used in the network slices. The network device stores multiple network slice templates, wherein the multiple network slice templates have different security assurance levels, of the multiple security assurance levels, for a Network Service Descriptor (NSD). The network device receives a request for a network slice with a requested security assurance level, of the multiple security assurance levels, for the NSD, and deploys the network slice using one of the network slice templates that has a security assurance level that corresponds to the requested security assurance level. The network device monitors the security parameters of the assets of the network slice for changes to the security assurance level of the deployed network slice.
Owner:VERIZON PATENT & LICENSING INC
Web caching with security as a service
In one implementation, Web-Cache deployed in the Enterprise premises and cloud-based SecaaS are combined such that similar identity-based polices are enforced on both the SecaaS and content delivered from the Web-Cache. This identity-based policy implementation outside the network using SecaaS and within the network for web-cached content provides consistent identity-based security while still providing content to end-users with high performance. Content inspected and / or modified by SecaaS may be cached in the enterprise premises so that requests for content from an origin server decreases, freeing Internet bandwidth and reducing access time. Local caching of streaming content may decrease latency while local implementation of identity-based policy continues to limit the streamed content as appropriate. Local implementation of identity-based policy may reduce the load on SecaaS. Rather than using content delivery networks provided by a service provider for web-content, a cache server within the enterprise is used.
Owner:CISCO TECH INC
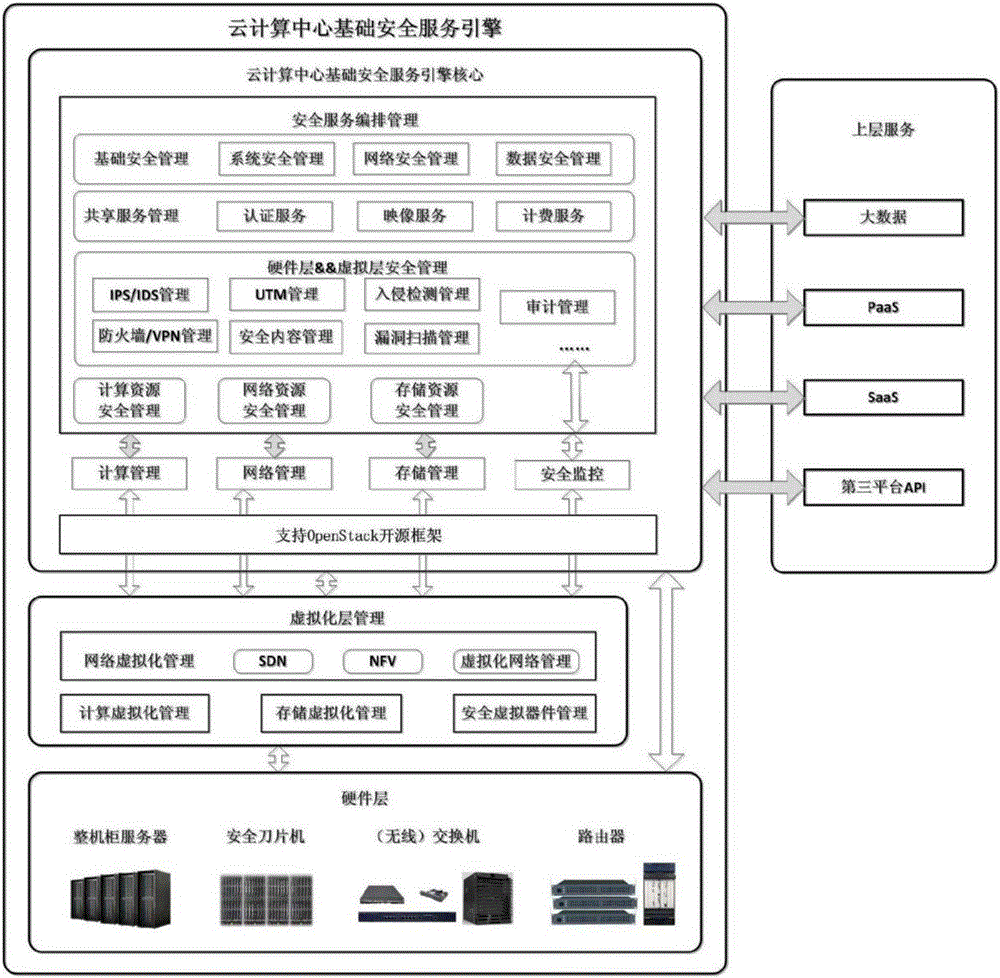
Security service system for cloud computation center
InactiveCN106453484AFlexible and customizable managementRealize full virtualizationTransmissionVirtualizationNetwork resource management
The invention discloses a security service system for a cloud computation center. The system comprises a cloud computation center basic security service engine core module, a virtualization layer management module, an upper layer service open interface and a third-party platform open API (Application Program Interface), wherein the cloud computation center basic security service engine core module is used for managing security service arrangement, managing calculation resources, network resources and storage resources of basic resources, and performing continuous security monitoring on the basic resources; and the cloud computation center basic security service engine core module is connected with the virtualization layer security management module, the upper layer service open interface and the third-party platform open API.
Owner:CHINA SOUTHERN POWER GRID COMPANY
System for distributing cloud security resources
PendingCN114386944ASecurity as a ServiceActive connectionOffice automationResource poolSecurity as a service
The invention discloses a system for distributing cloud security resources, which is connected with a cloud service platform for providing user business application computing storage resources, and comprises a cloud security resource pool of a plurality of security service components, a user-oriented user platform, an operator-oriented operation platform and a security service provider-oriented security ecological platform. A selectable cloud security resource adaptation service and a visual channel are provided for a user, so that the user can effectively configure and use the cloud security resources as required, a cloud security resource operator can operate and create the security ecology, the security requirements of all parties are met, the cloud security resource ecological operation capability for continuously resisting new security threats is created, and the user experience is improved. The method has the characteristics of safety as a service, visual full threat, complete decoupling, clear safety responsibility, operable platform, ecological sustainability and the like.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD
Dynamic migration access control technology design method based on heterogeneous network
InactiveCN107920065AReal-time understanding of fault statusReal-time understanding of abnormal statusUser identity/authority verificationSecurity arrangementAccess methodModel method
The invention discloses a dynamic migration access control technology design method based on a heterogeneous network. The method includes the following steps: establishing a system architecture of a mutual trust system and judging a mobile node; establishing a security access model of a heterogeneous mobile network; and authenticating security access of the heterogeneous mobile network. The architecture disclosed by the invention consists of a client and a security service system installed on a trusted user node, and thus the security service system can acquire the real-time state of the mobile node, filter the credibility of the node, know the failure or abnormal state of the mobile node in real time, and further terminate the provision of services for the node; through modeling methods,various security access methods are analyzed and compared to find a more secure and more efficient access method; and meanwhile, a trust update algorithm of the system can be optimized, the system information can be periodically updated, and the security threats actually operated in environments can be mitigated.
Owner:中山大学新华学院
Method for building desktop cloud virtual trust safety wall
ActiveCN103279703AImprove securityImprove real-time performancePlatform integrity maintainanceTrusted ComputingTrust relationship
The invention provides a method for building a desktop cloud virtual trust safety wall. A TCM serves as a trust root, a safety wall trust chain and a basic trust chain together form a two-dimensional trust chain, the virtual trust safety wall can move along with virtual desktops synchronously, the two-dimensional trust chain is built, and a trust relationship can be expanded to a whole desktop cloud system from the trust root through the two-dimensional trust chain. By means of a virtual trust safety wall system structure, on the basis of a trust computing basis platform, a virtual trust safety wall is built for each virtual desktop, and a desktop visit method high in safety and instantaneity is provided for business application. For enhancing the safety of desktop cloud, the two-dimensional trust chain is formed by the safety wall trust chain and the basis trust chain, and the trust relationship is expanded to the whole desktop cloud system from the trust root. Aiming at dynamic characteristics of the cloud environment, the virtual trust safety wall has the capability of moving along with the virtual desktops dynamically, and the aim of 'safe service' can be achieved.
Owner:INFORMATION & COMMNUNICATION BRANCH STATE GRID JIANGXI ELECTRIC POWER CO +1
Systems and methods for providing security services during power management mode
ActiveUS9516040B2Digital data processing detailsPlatform integrity maintainanceManaged security serviceHard disc drive
Systems and methods for providing security services during a power management mode are disclosed. In some embodiments, a method comprises detecting with a mobile security system a wake event on a mobile device, providing from the mobile security system a wake signal, the providing being in response to the wake event to wake a mobile device from a power management mode, and managing with the mobile security system security services of the mobile device. Managing security services may comprise scanning a hard drive of the mobile devices for viruses and / or other malware. Managing security services may also comprise updating security applications or scanning the mobile device for unauthorized data.
Owner:CUPP COMPUTING
Secure application zones for cloud burst environments
A cloud infrastructure security assurance service is enhanced to facilitate bursting of cloud applications into other cloud infrastructures. The security assurance service provides a mechanism to enable creation and management of secure application zones within a cloud infrastructure. When the security assurance service receives an indication that a workload associated with a cloud application triggers a cloud burst, the service is extended into a new cloud infrastructure. Once the security assurance service is instantiated in the new cloud infrastructure, it identifies the broad security requirements of the application, as well as the security capabilities of the new environment. Using this information, the security assurance service computes a minimal security environment needed by the cloud application for the burst operation. The security assurance service then configures the necessary topology in the new cloud environment, and the burst operation is then completed by having the cloud application deployed in that topology.
Owner:INT BUSINESS MASCH CORP
System and method using dedicated computer security services
ActiveCN105721461APlatform integrity maintainanceTransmissionManaged security serviceComputer network
The invention discloses a system and a method using dedicated computer security services. The exemplary method includes the steps of: storing a rule indicating when a first cloud service or a second cloud service is used in the security services in an electronic database; receiving a request visiting the security services from a client computer; determining parameters relevant to the received request; applying the parameters to multiple rules to determine to indicate an instruction whether a request is transferred to the first cloud service or the second cloud service; and transmitting the request to the first cloud service or the second cloud service to use at least a security service based on the instruction.
Owner:AO KASPERSKY LAB
A security service providing method and server
The present invention provides a server and method for security service providing, wherein a basic platform is used for verifying the call request after receiving the call request of the user for any application, forwarding the call request to the application it calls after the call request is verified and configuring the resources for the run of the called application. Every application is used to receive the forwarded call request of the basic platform and provides the user with the business of the security class according to the call request. The basic platform provides unified services of request verifying and resources configuring for all the applications. And because each application is independent of other applications in the running process, numerous applications can be built based on the basic platform theoretically, which can improve the scalability of the security service providing server.
Owner:ALIBABA GRP HLDG LTD
System and method for providing security as a service in a cloud operating system
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com