Data resource security control method in thin client mode
A data resource and thin client technology, applied in the field of network security, can solve problems such as data loss, leakage or tampering, and achieve the effect of ensuring legality and authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
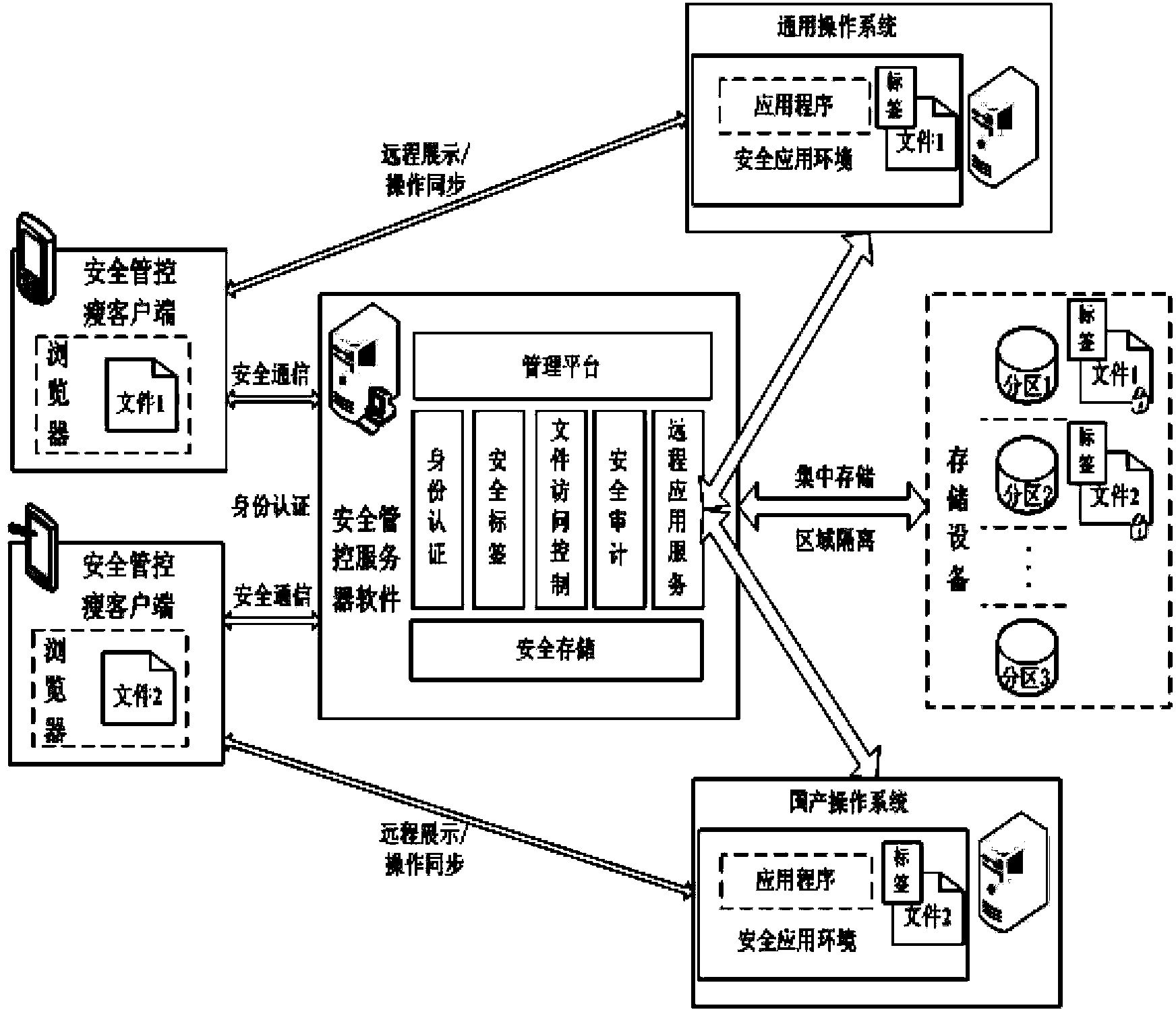
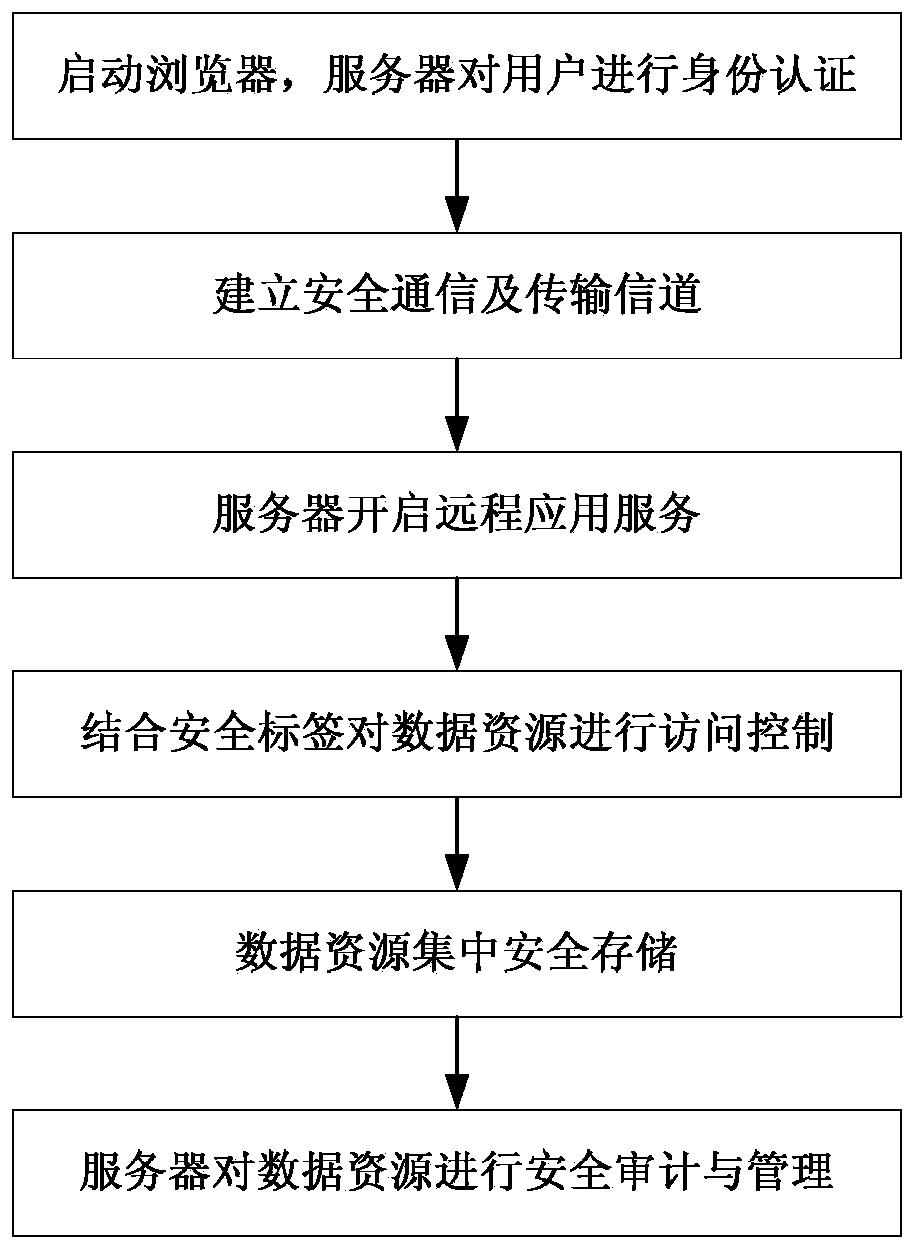
[0060] The method of the present invention will be described in detail below in conjunction with the flow chart.
[0061] Step 1: Start the browser, the user logs in to the server through the USBKEY and user name and password, and the server completes the user's identity authentication through the identity authentication subsystem.
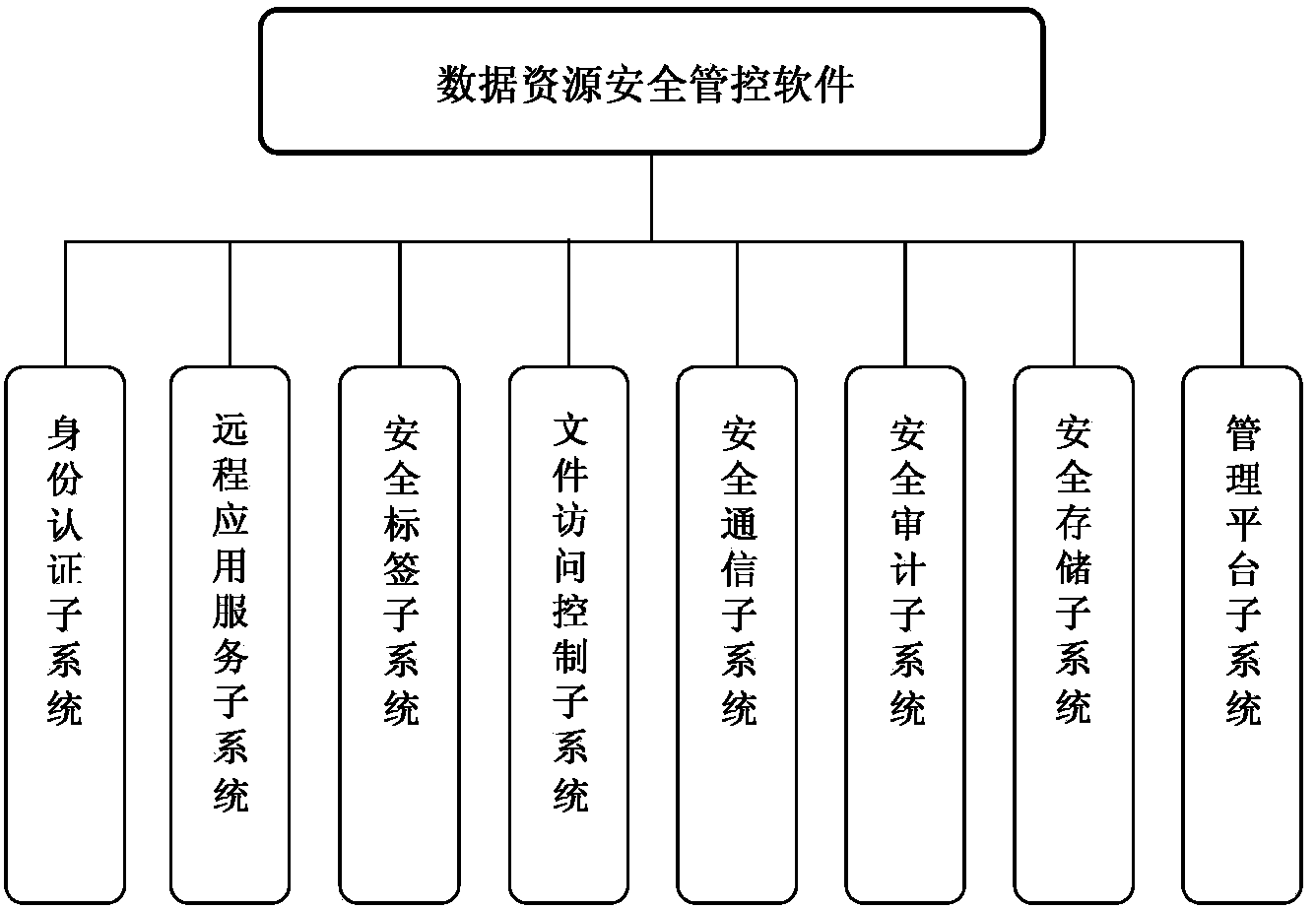
[0062] Server security management and control software supports multiple identity authentication methods: user name + password, USBKey + PIN code, CA digital certificate. At the same time, it supports custom configuration of password strength policy, account lock policy, pull KEY lock screen, terminal binding and other auxiliary functions.
[0063] Considering that the CA digital certificate system has been widely used and has been used as the basic condition of informatization, the identity authentication is completed by using the bottom library of the authentication device, authentication client and authentication server that has provided the CA...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com