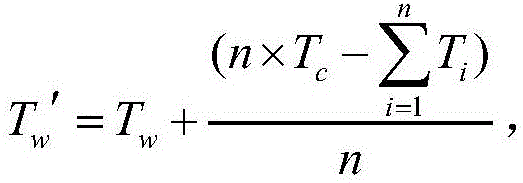Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
83 results about "Resource security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Resource Security. Access to minerals means a more secure America. Minerals are among the most important components in the technologies protecting our nation. Minerals, Supply Chain and National Defense. Access to minerals is crucial for a more secure America. Minerals are the basic components that make up the technologies protecting our nation.
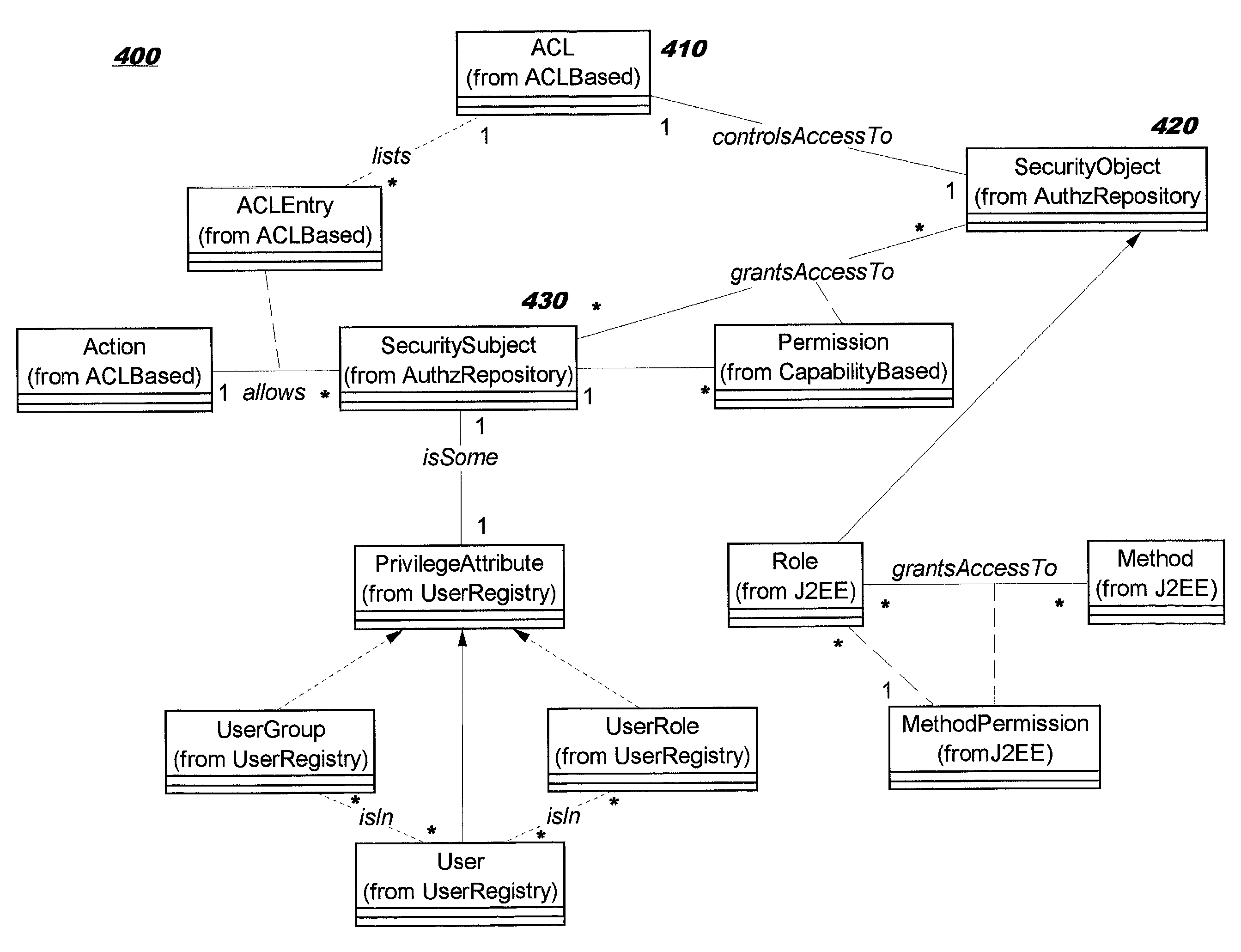
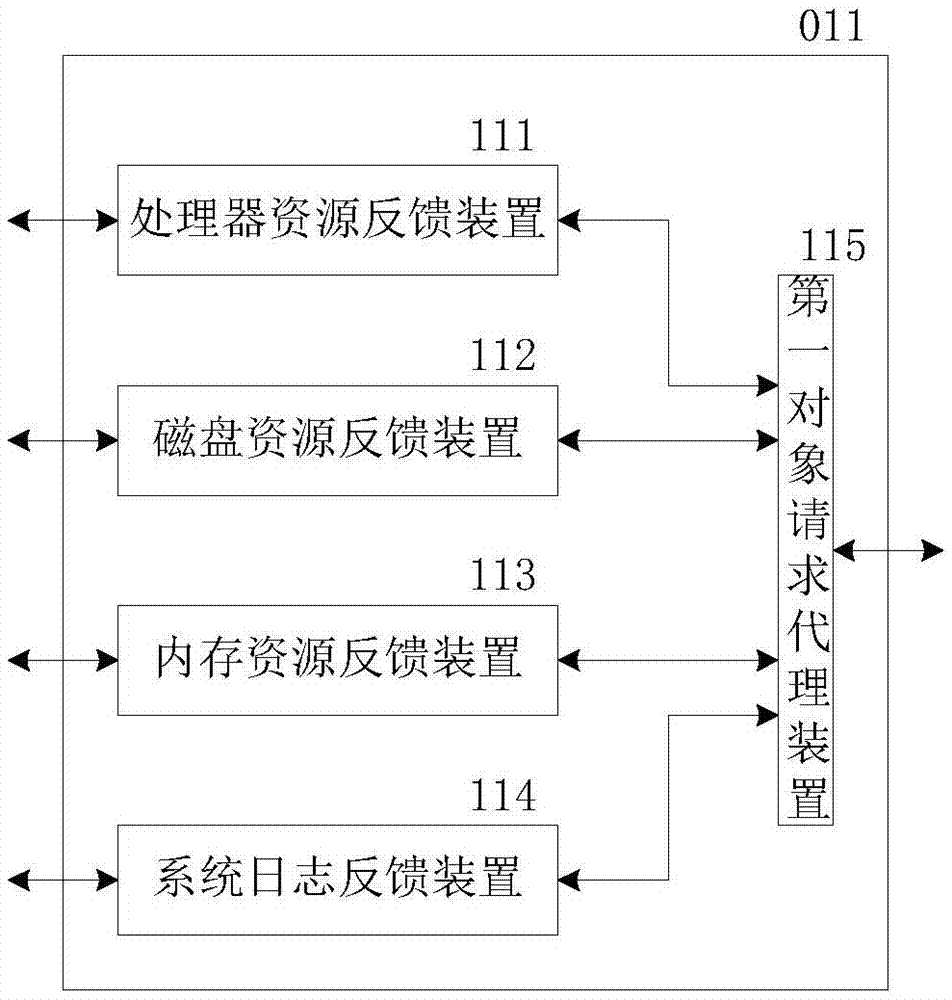
Role-permission model for security policy administration and enforcement
InactiveUS20030046576A1Efficient and more manageableData processing applicationsMultiple digital computer combinationsDistributed Computing EnvironmentInternet privacy
Methods, systems, and computer program products are disclosed for protecting the security of resources in distributed computing environments. The disclosed techniques improve administration and enforcement of security policies. Allowed actions on resources, also called permissions, (such as invocations of particular methods, read or write access of a particular row or perhaps a particular column in a database table, and so forth) are grouped, and each group of permissions is associated with a role name. A particular action on a particular resource may be specified in more than one group, and therefore may be associated with more than one role. Each role is administered as a security object. Users and / or user groups may be associated with one or more roles. At run-time, access to a resource is protected by determining whether the invoking user has been associated with (granted) at least one of the roles required for this type of access on this resource.
Owner:IBM CORP
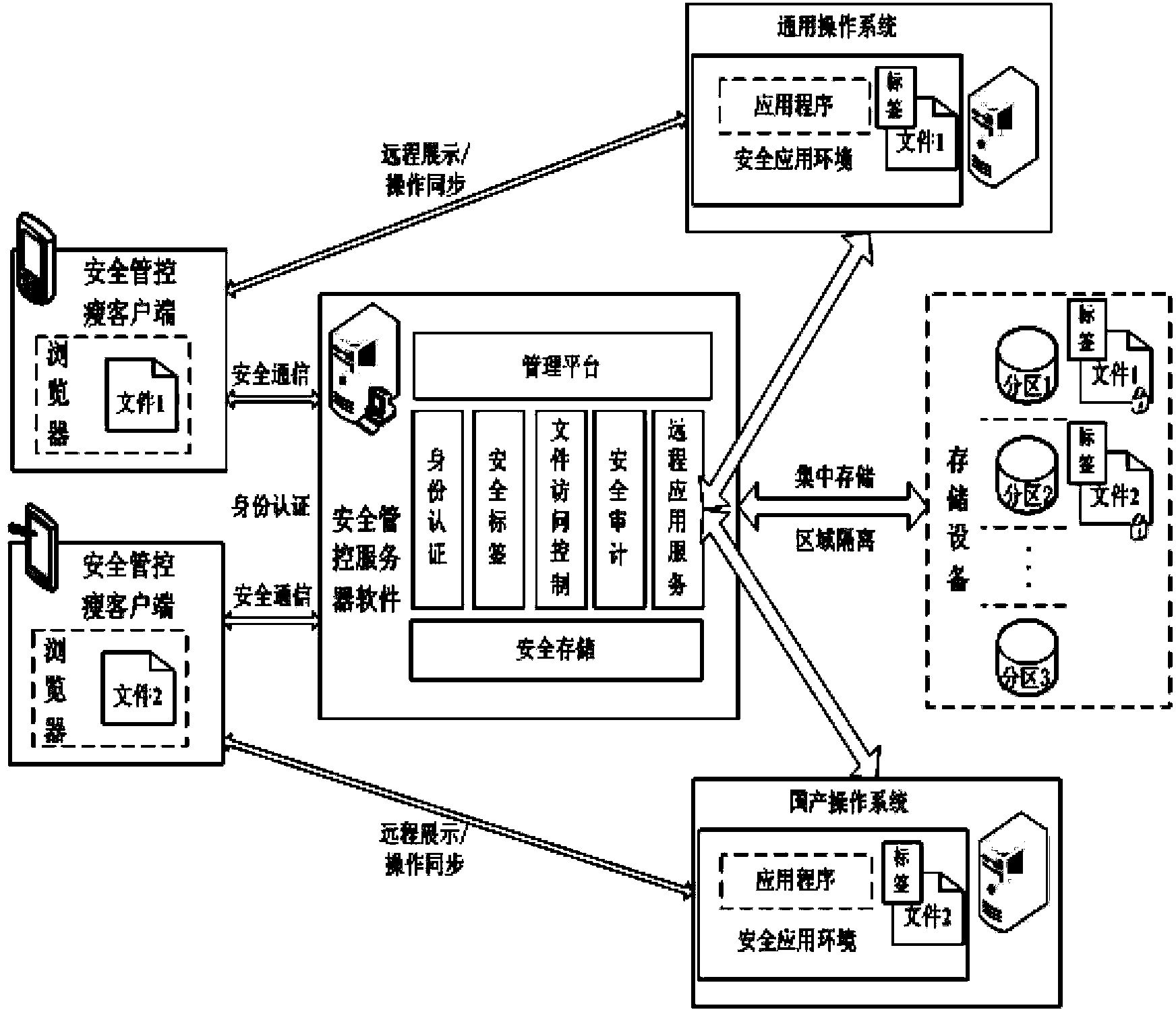
Data resource security control method in thin client mode
ActiveCN103441986AEfficient identificationEnsure authenticityDigital data protectionTransmissionThin clientServer-side
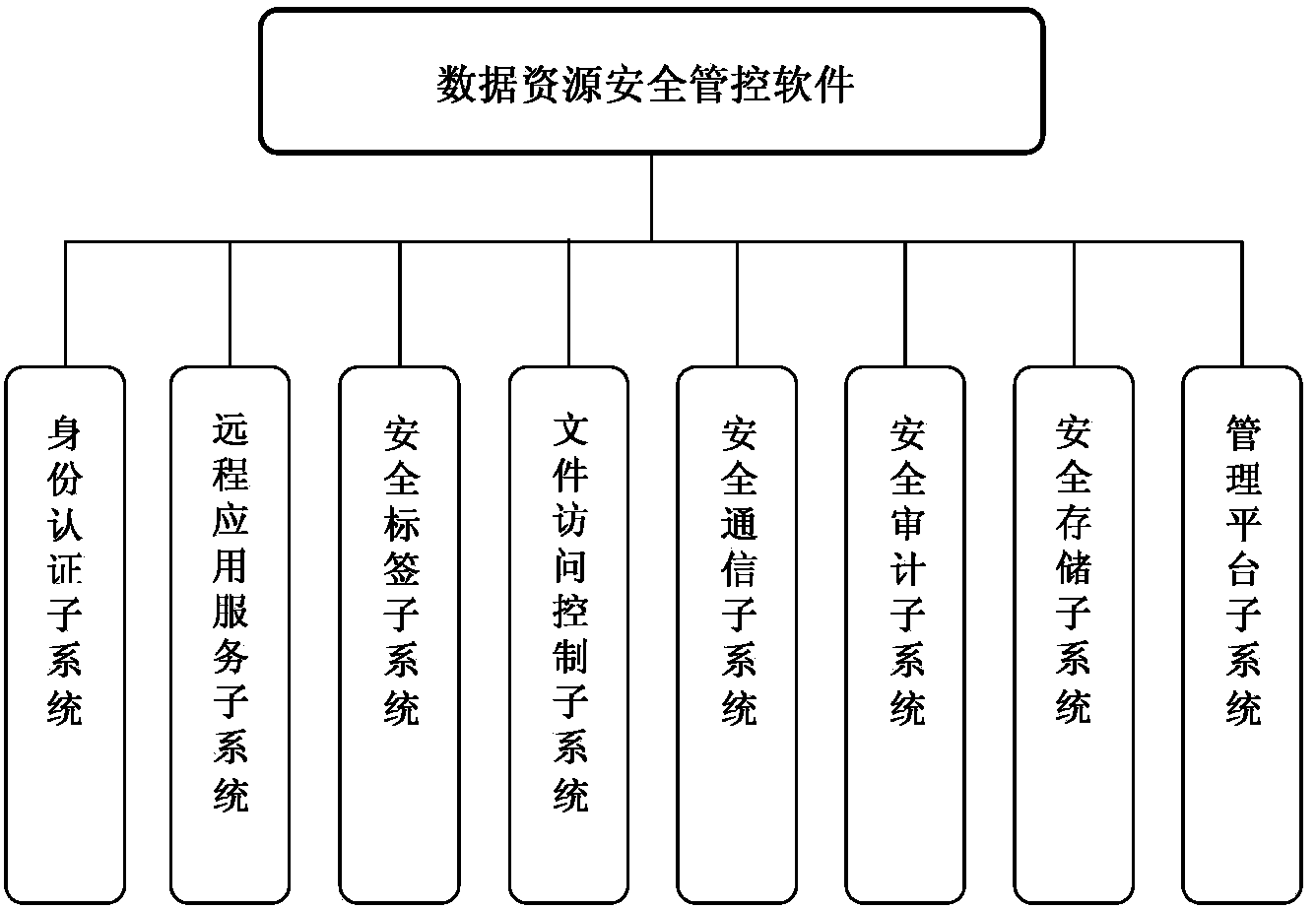
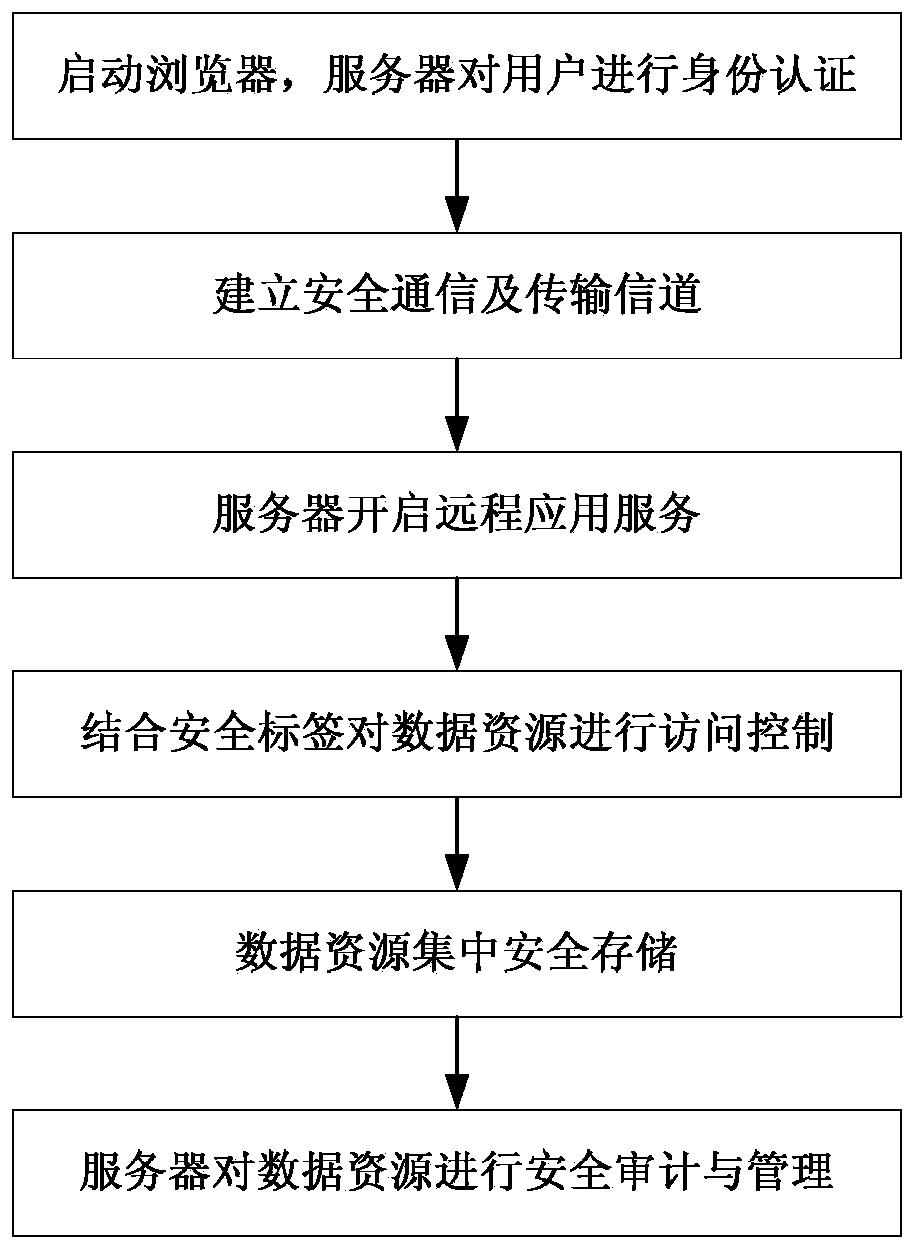
The invention belongs to the field of network security, and particularly relates to a data resource security control method in a thin client mode. The data resource security control method in the thin client mode comprises eight subsystems, namely the identity authentication subsystem, the remote application service subsystem, the security label subsystem, the file access control subsystem, the security communication subsystem, the security audit subsystem, the security storage subsystem and the management platform subsystem. Storage and control of files are mainly performed on a background server, the files are stored in different partitions according to user types or security levels of the files, the files are stored and protected, and a server side can not recognize the content of the files. When a user needs to have access to and process the files, the user logs in on a browser, identity authentication is conducted between the user and a server, and then file access connection is established. The files of a thin client are processed on the server side (provided by a physical application server or a virtual application server), no application or agent needs to be installed on the thin client, and interface interoperability is supported by related services released by remote application services.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
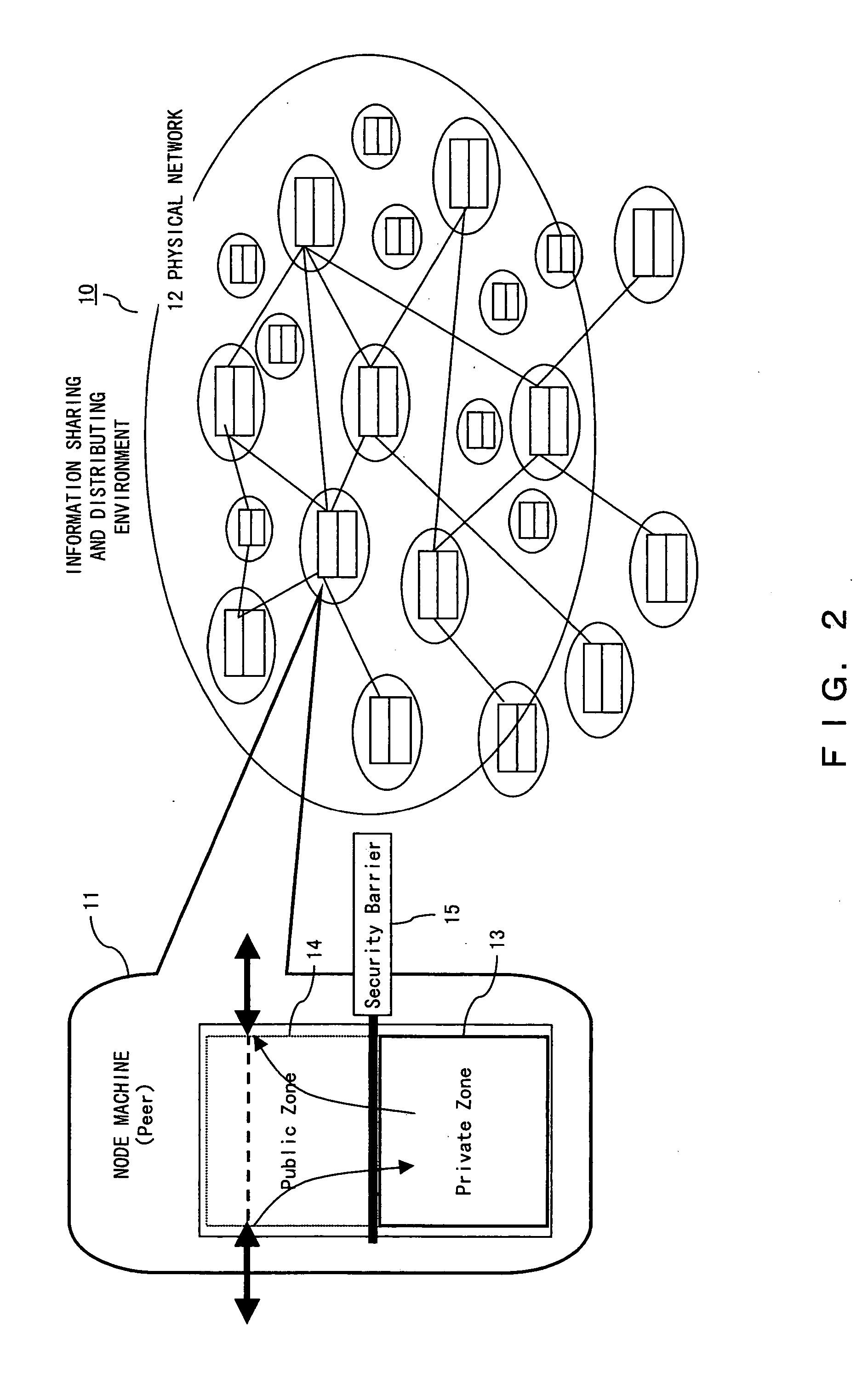
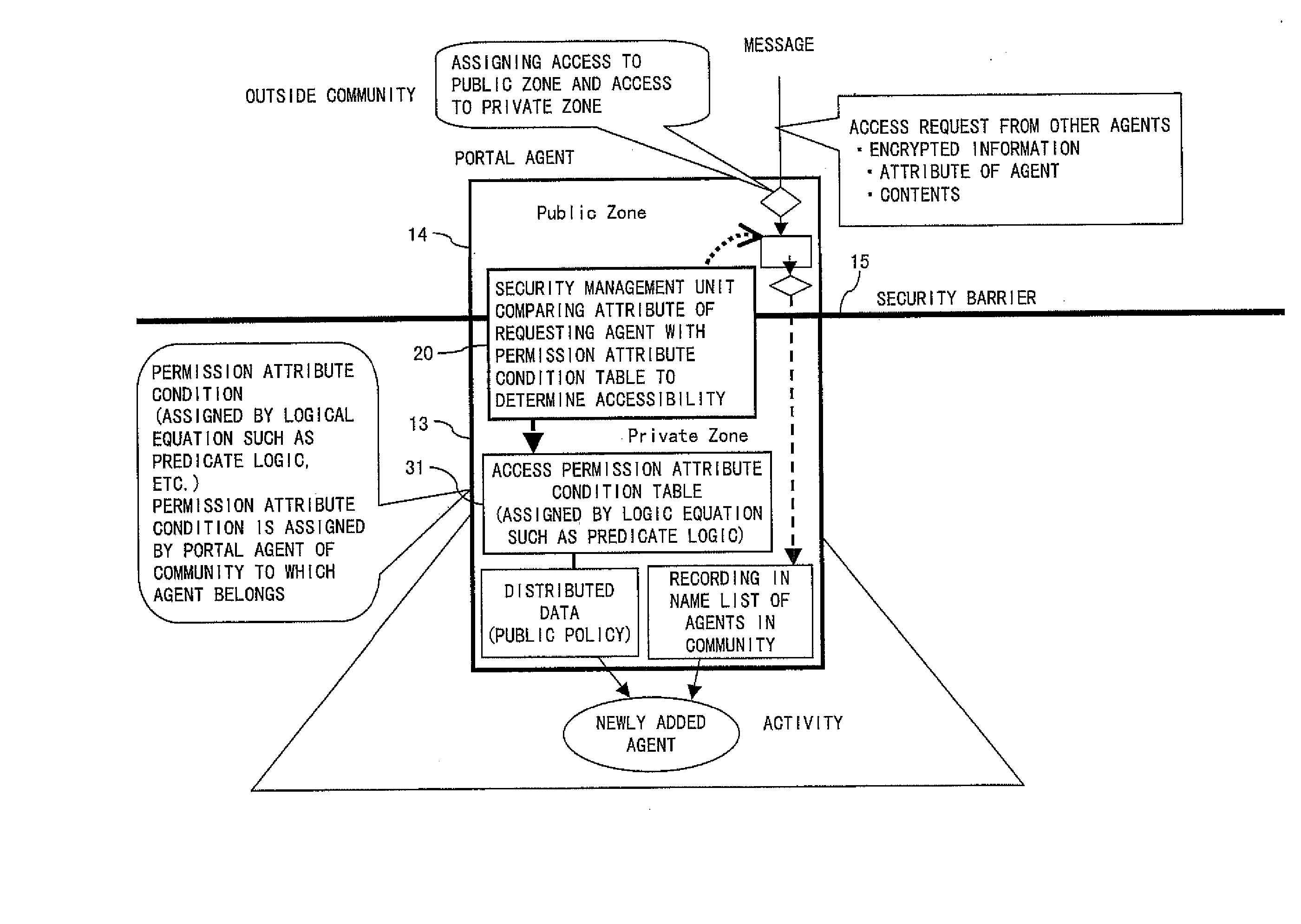
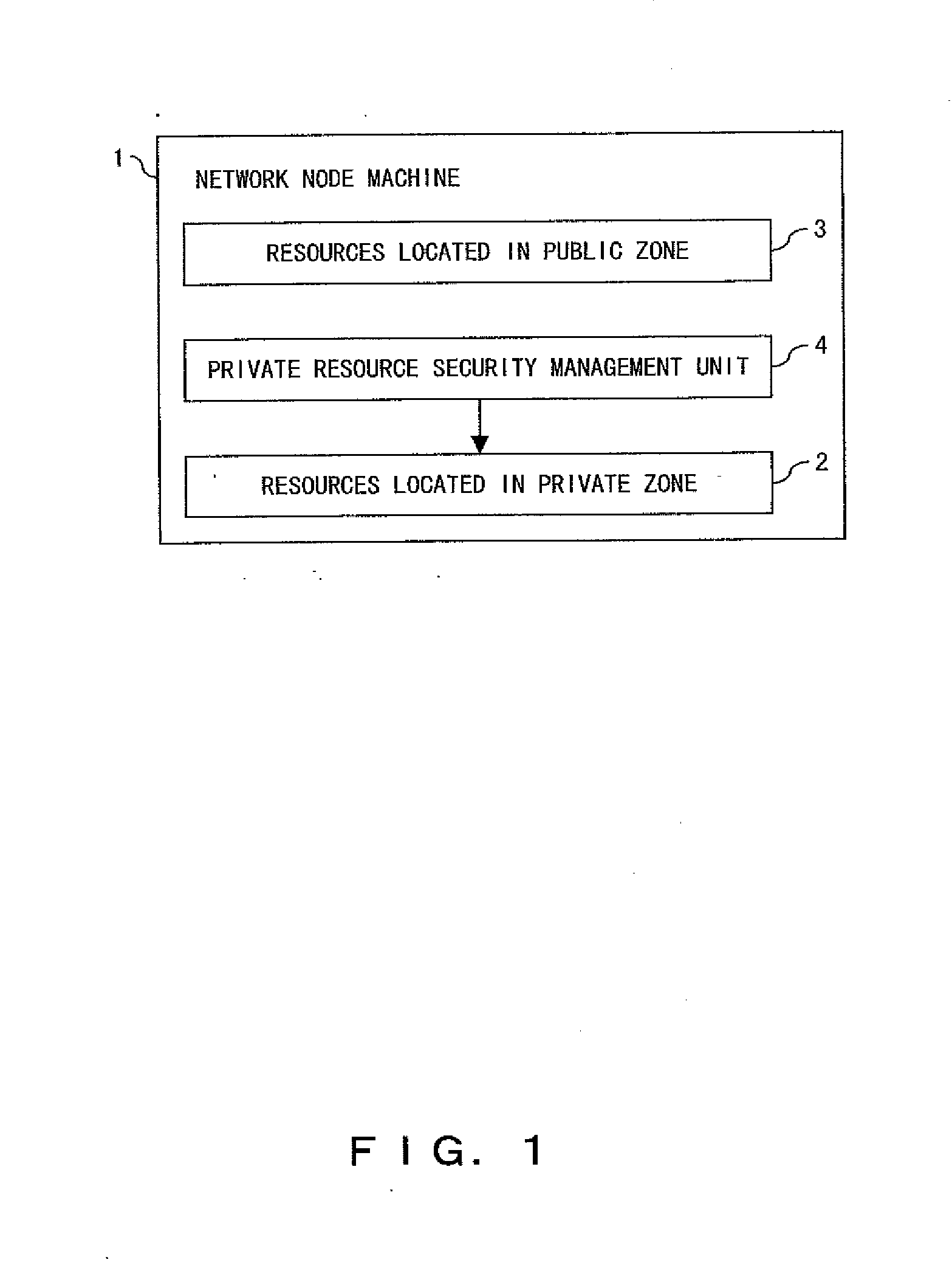
Network node machine and information network system
InactiveUS20050028012A1Easy to usePropelling public useDigital data processing detailsUnauthorized memory use protectionManagement unitResource security
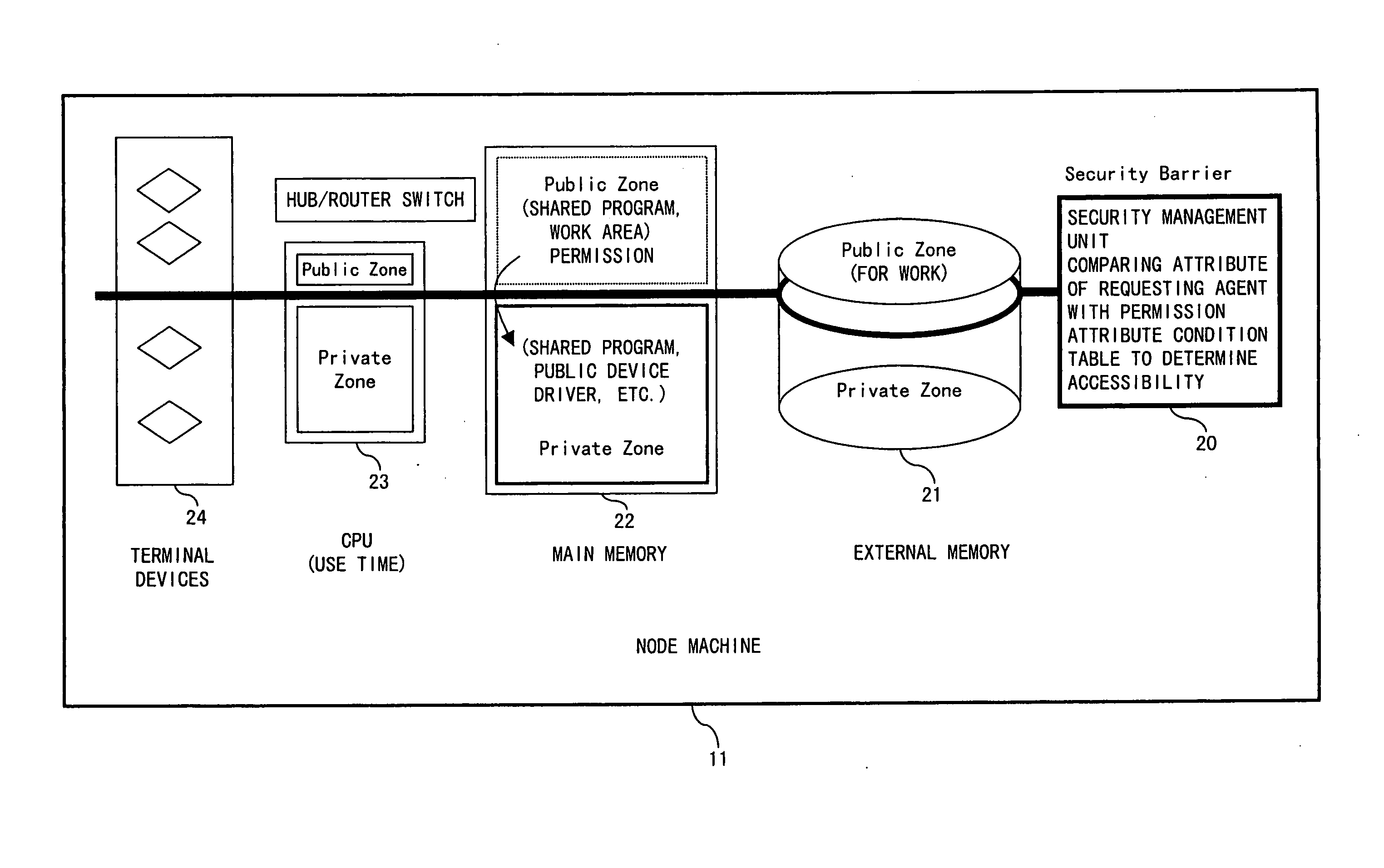
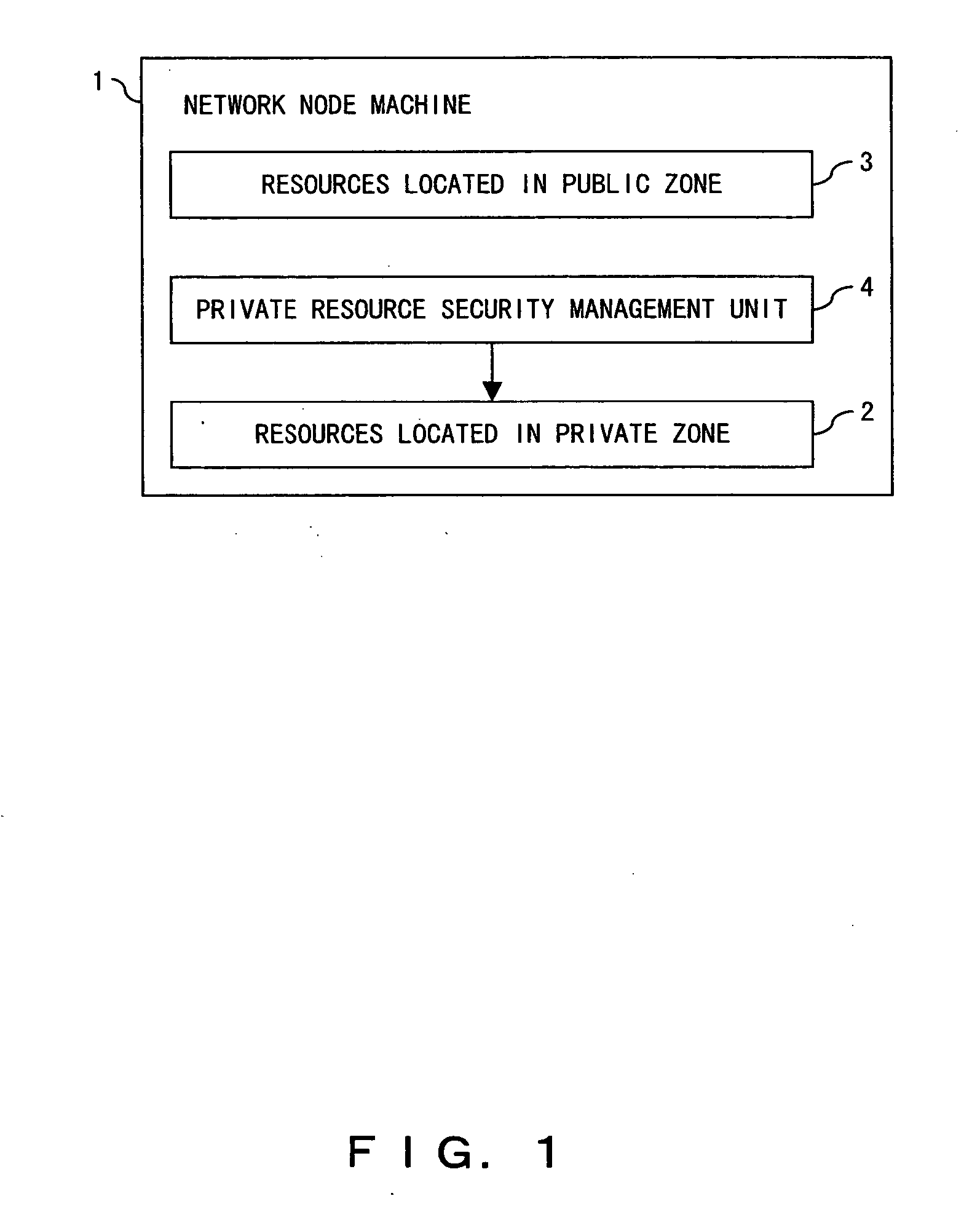
In the global information sharing and distributing service system, the public use of idle resources can be propelled and sufficient security can be guaranteed on the resources for private use. A node machine configuring an information network includes resources located in a private zone available to private use, resources located in a public zone for public service use, and a private resource security management unit for management of the security of the resources located in the private zone.
Owner:FUJITSU LTD +1
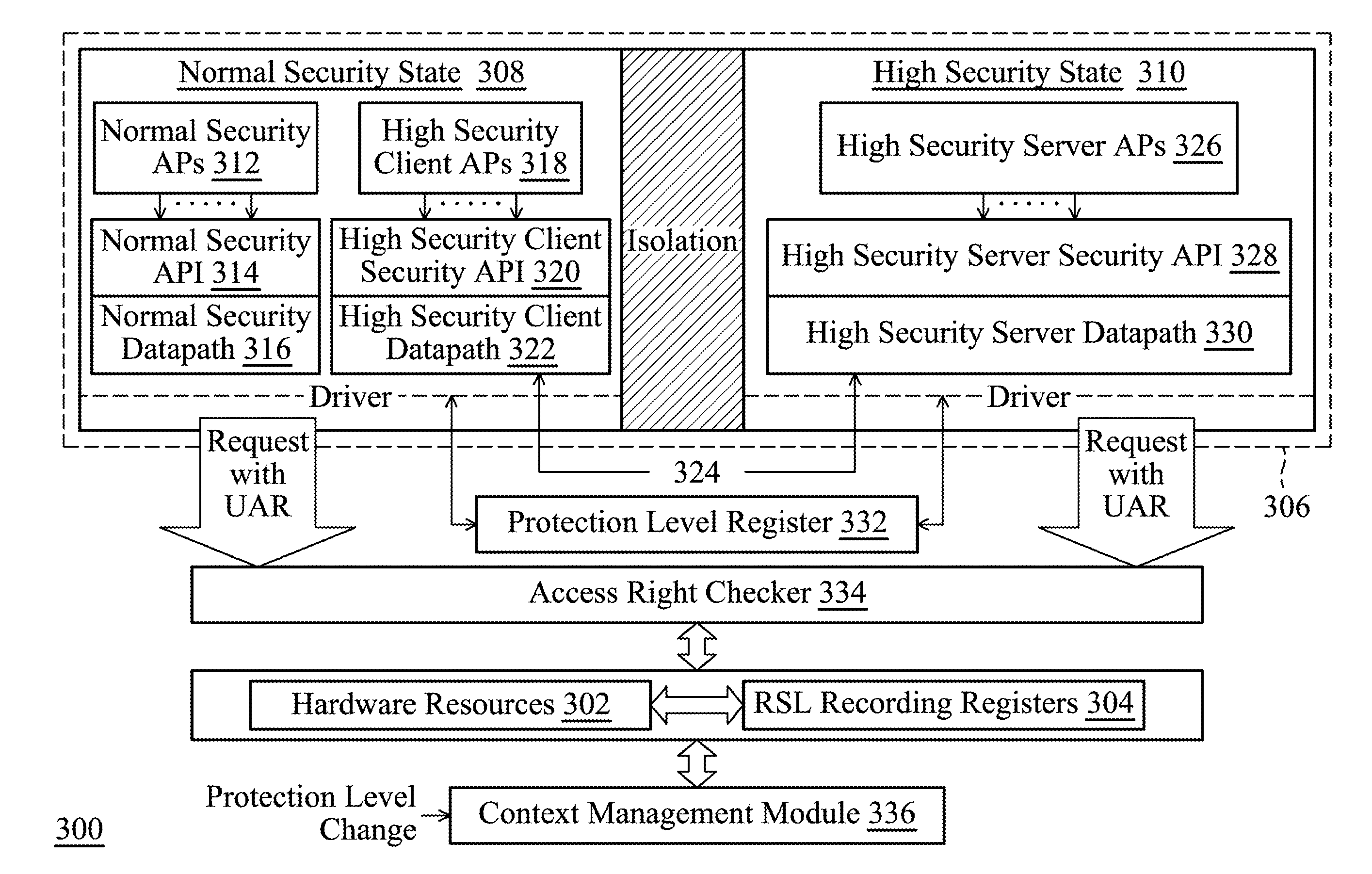
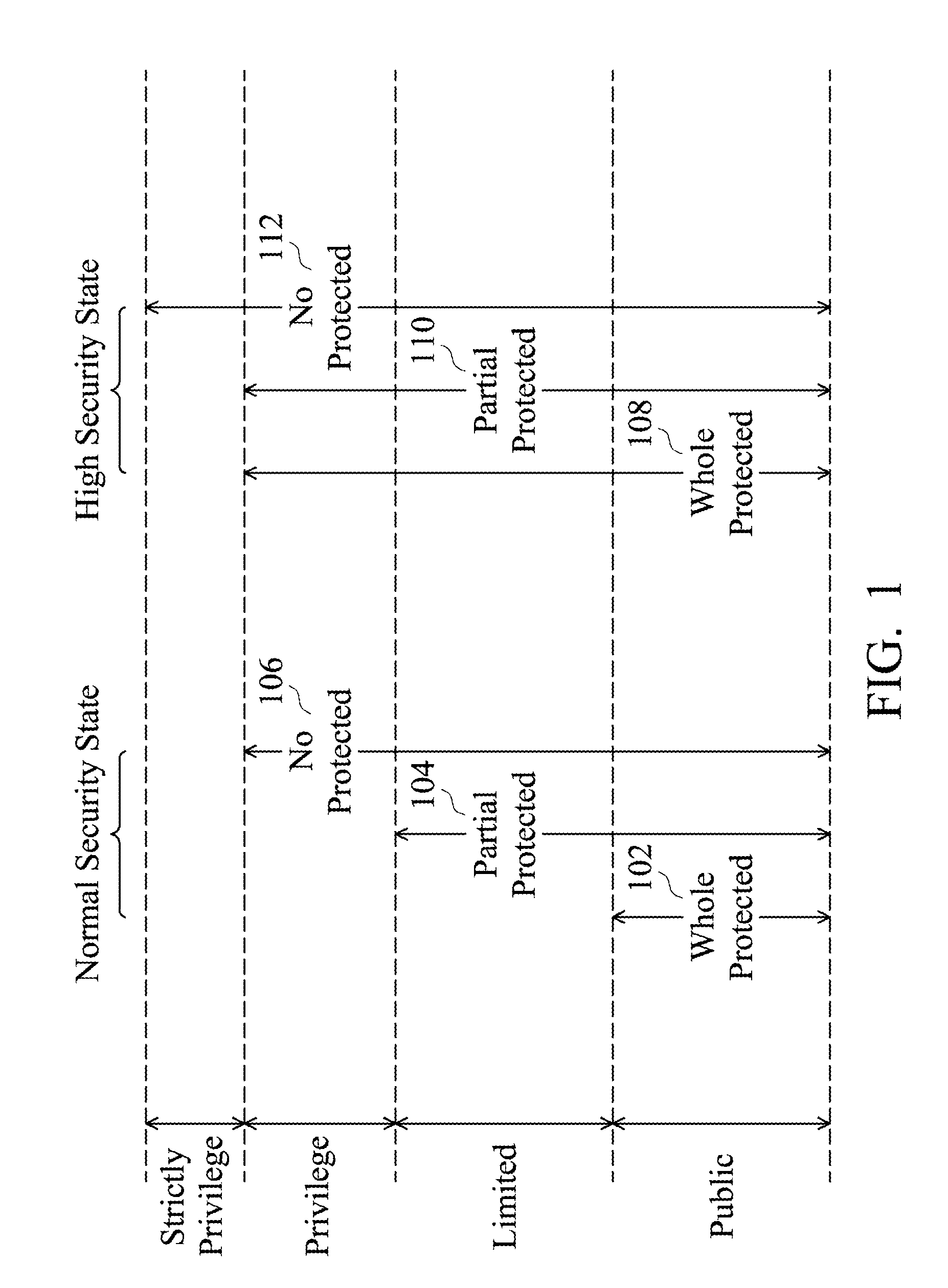
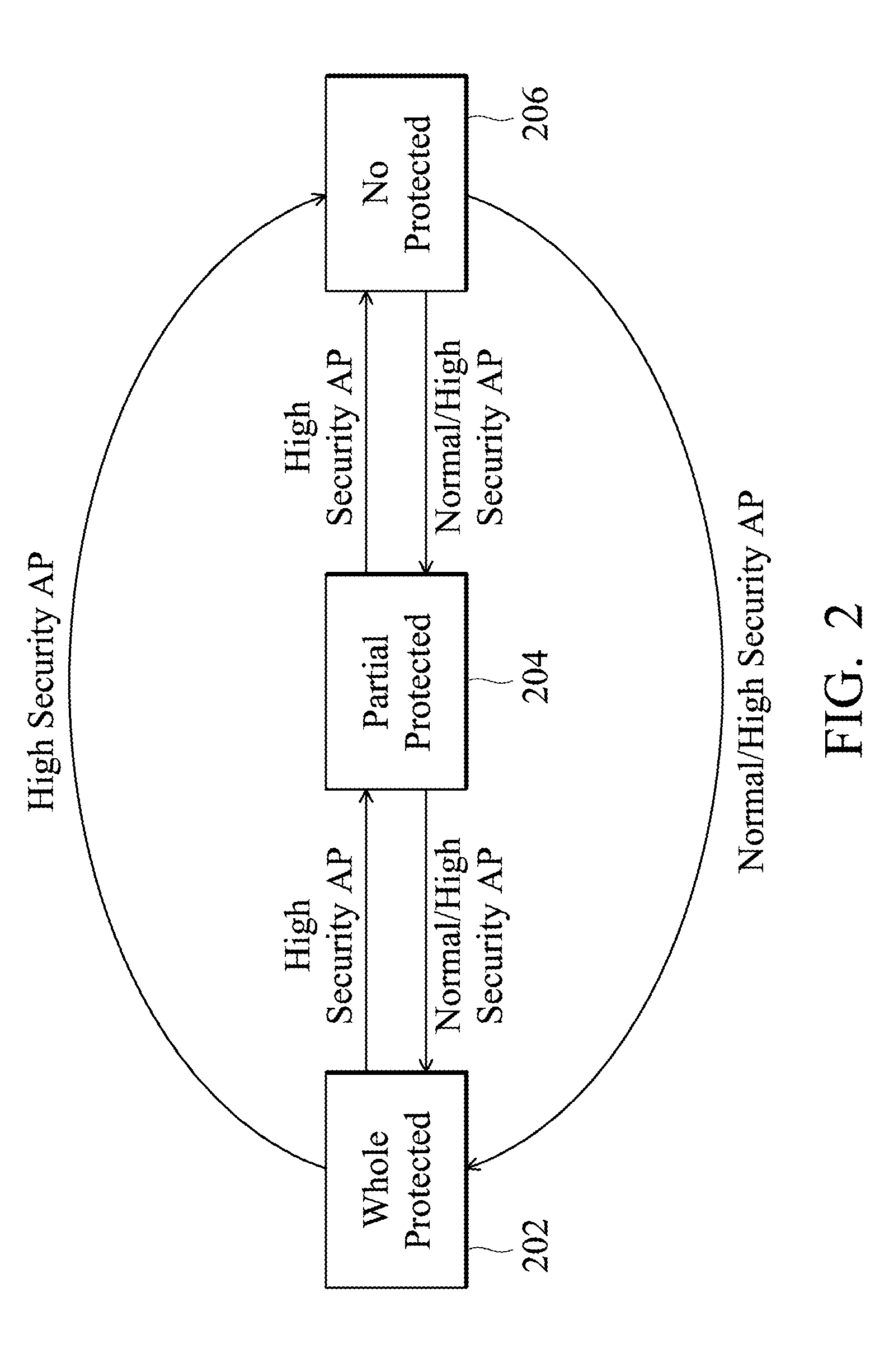
Computing System Providing Normal Security and High Security Services
ActiveUS20110314538A1Improve securityReduce switchingDigital data processing detailsUser identity/authority verificationInternet privacyResource security
A computing system and method providing normal security services and high security services are disclosed. The computing system includes hardware resources, a processor core and an access right checker. The hardware resources are grouped into resource security levels. The processor, switching between a normal security and a high security state, assigns a user access right to a request. In comparison with the normal security state, user access right assigned in the high security state further allows the request to use the hardware resources of a higher resource security level. According to the assigned user access right and the resource security levels of required hardware resources of the request, the access right checker determines whether the request has the authority to use the hardware resources, and thereby, the access right checker executes the request or responds the issued request with an exception.
Owner:HAMILCAR BARCA IP LLC
System and method for dynamic security access
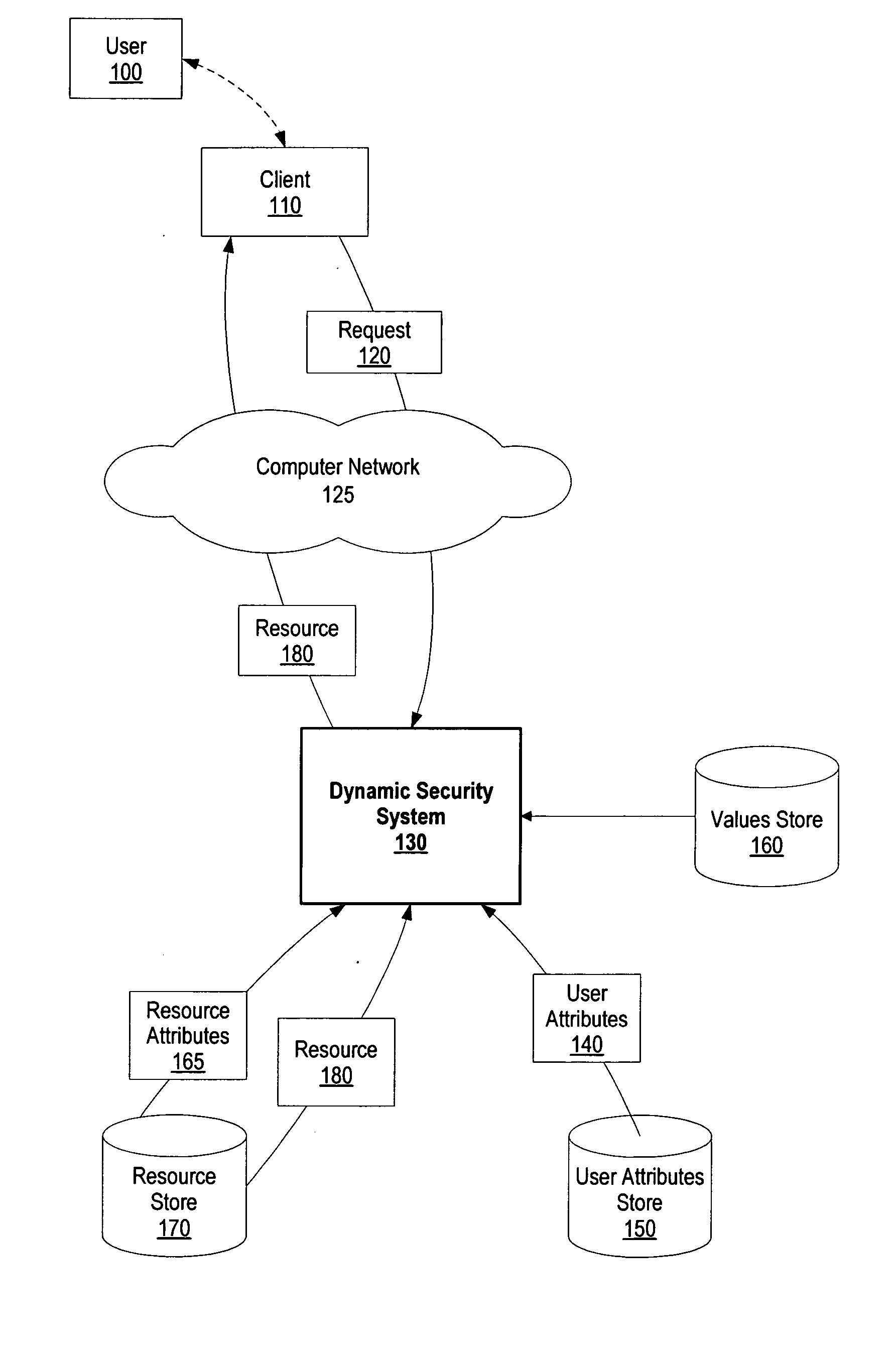
InactiveUS20070169204A1Random number generatorsUser identity/authority verificationResource securitySystem usage
A system and method for dynamic security access. A dynamic security system receives a resource request from a user. The dynamic security system computes a dynamic user security value using a user security formula and user attribute values corresponding to the user. In addition, the dynamic security system computes a resource security value using a resource security formula and resource attribute values corresponding to the resource. Once computed, the dynamic security system compares the dynamic user security value with the resource security value and, if the dynamic user security value is greater than or equal to the resource security value, the dynamic security system grants resource to the user.
Owner:IBM CORP
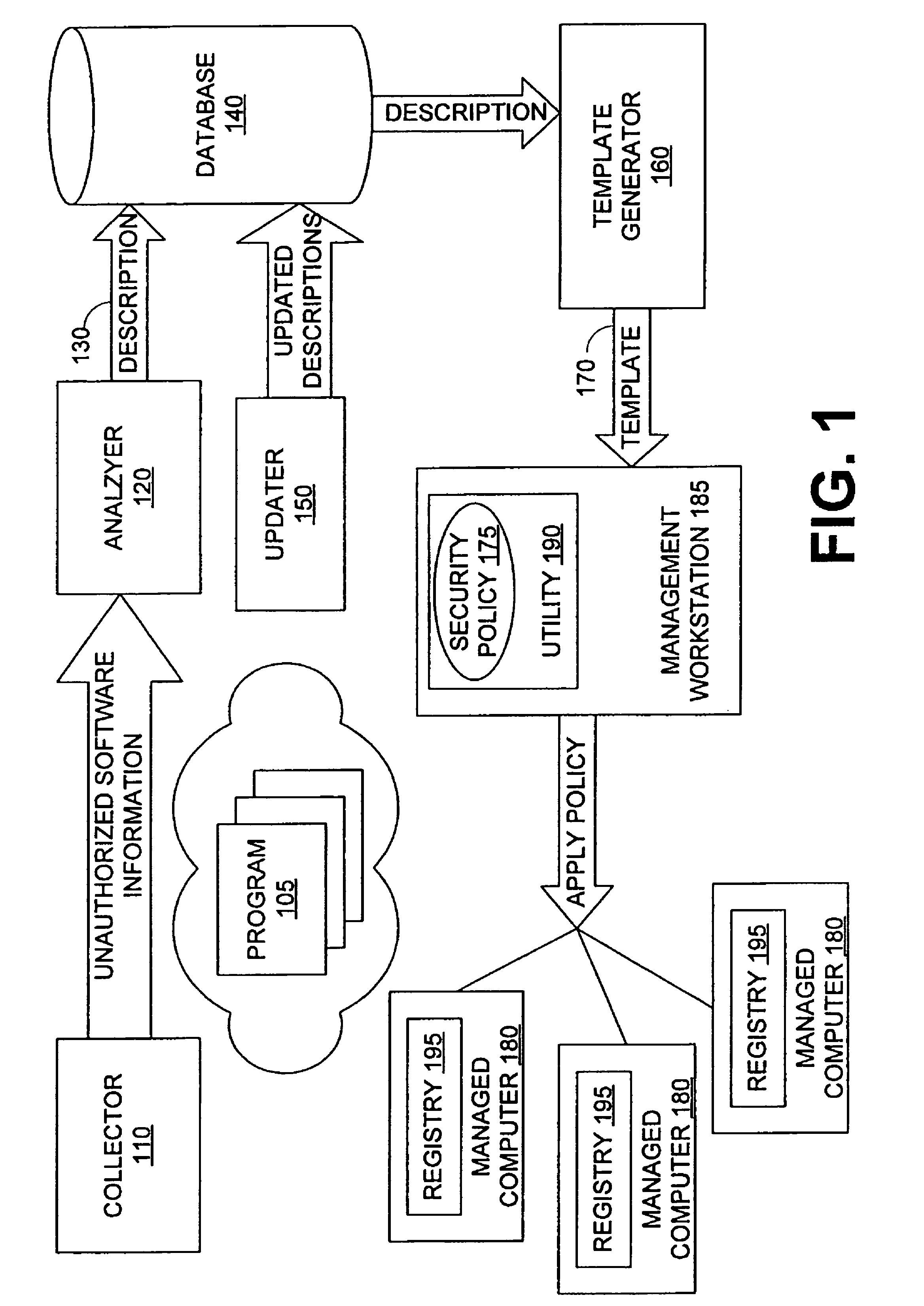
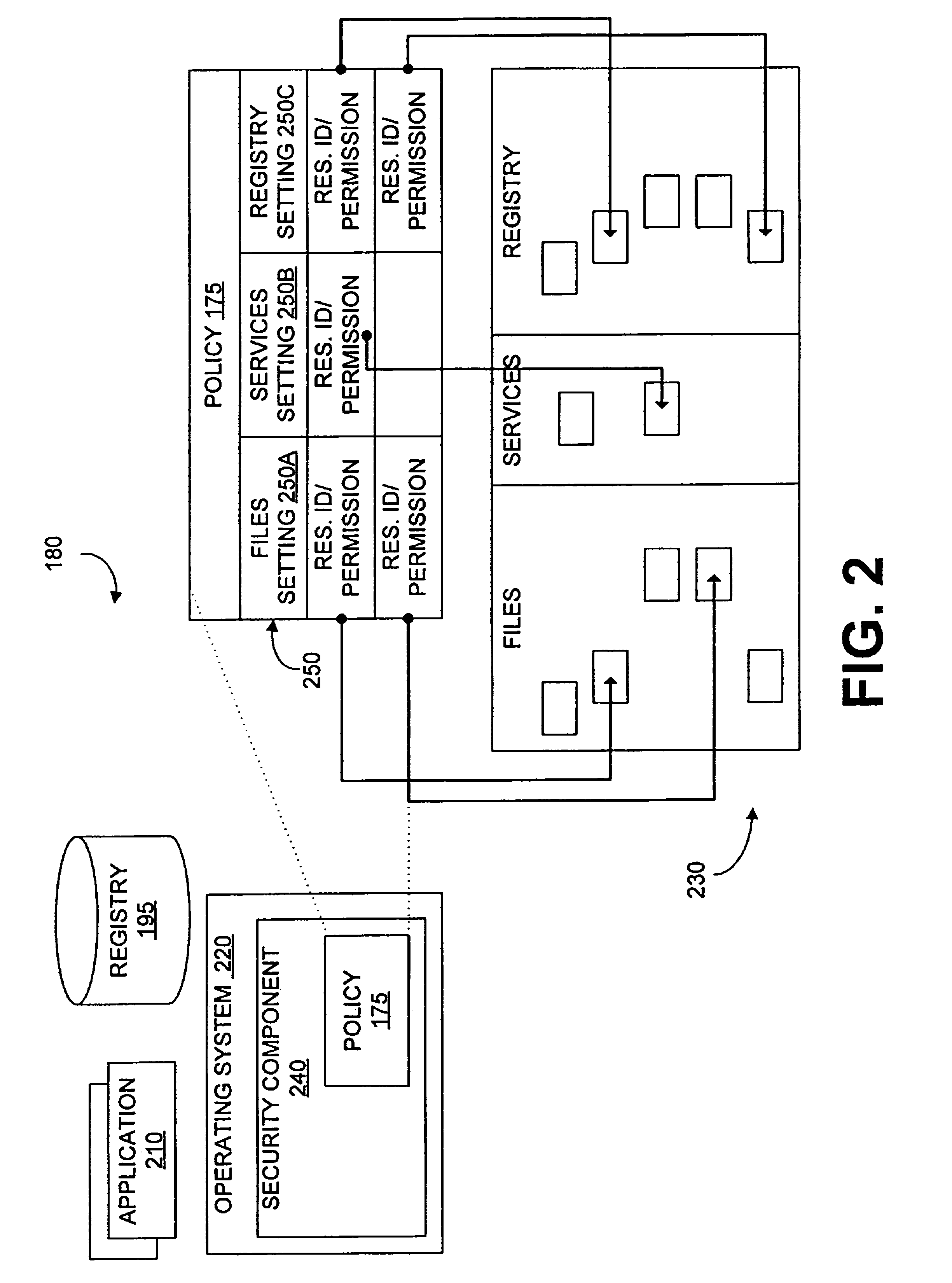
Automating software security restrictions on system resources
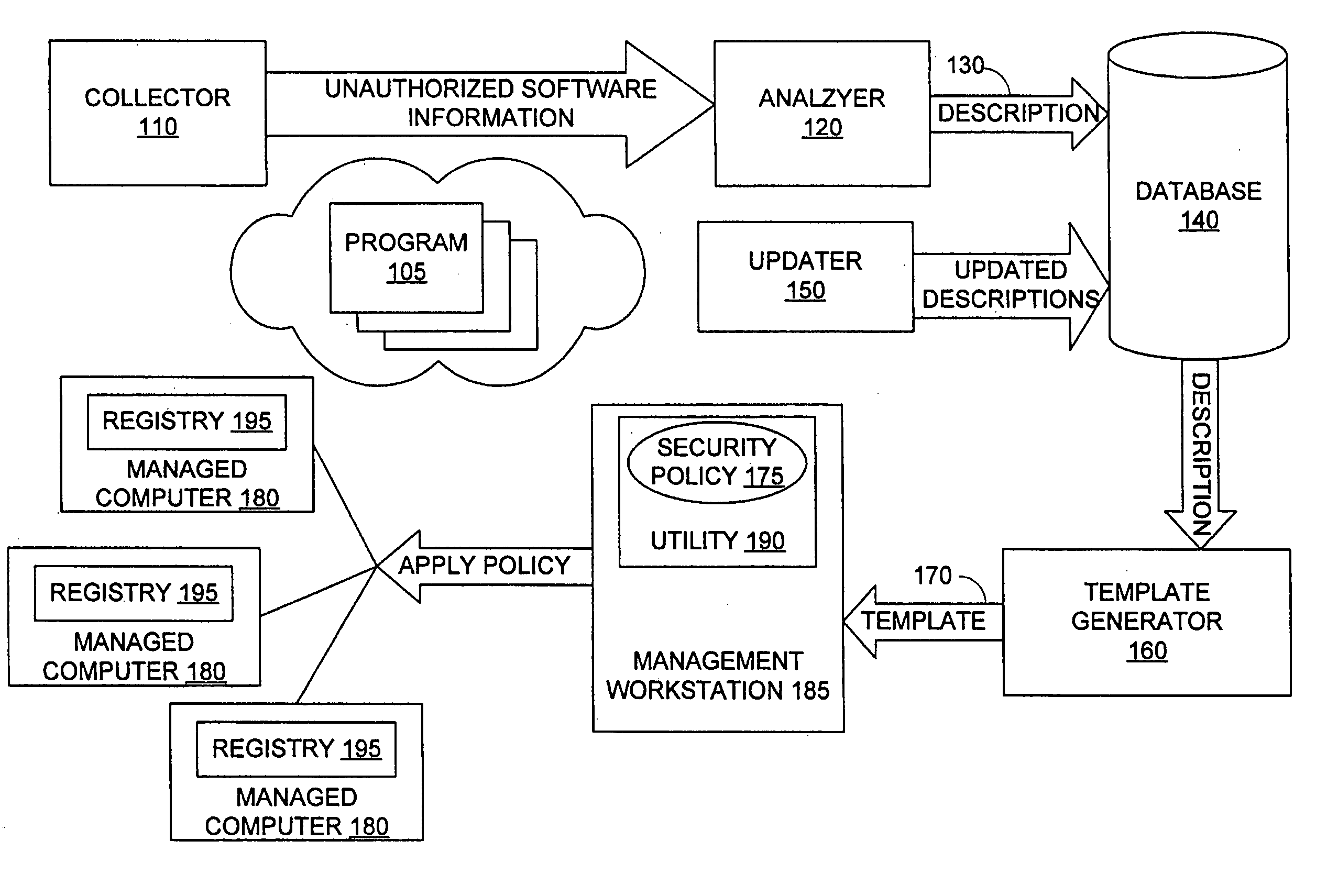
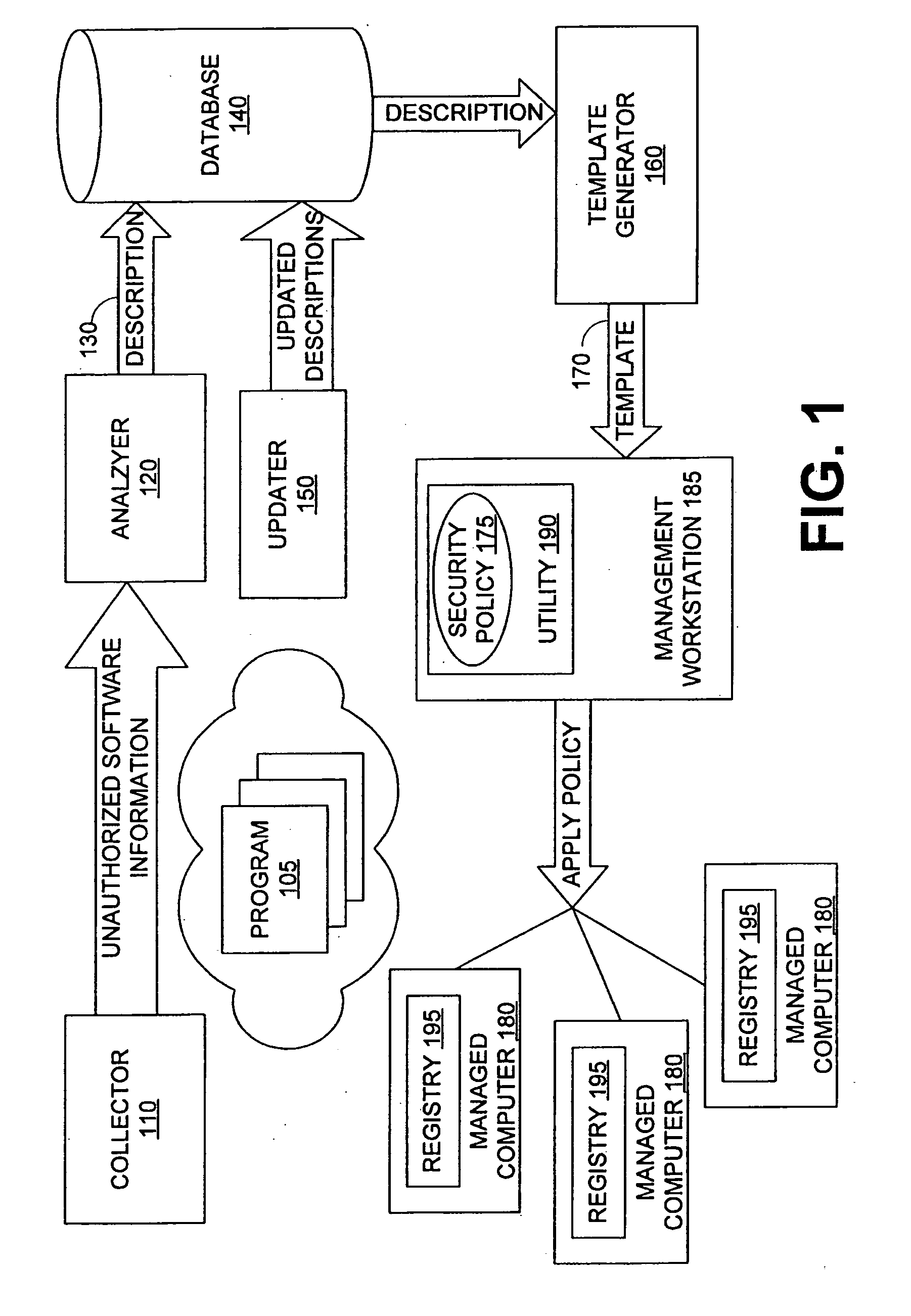
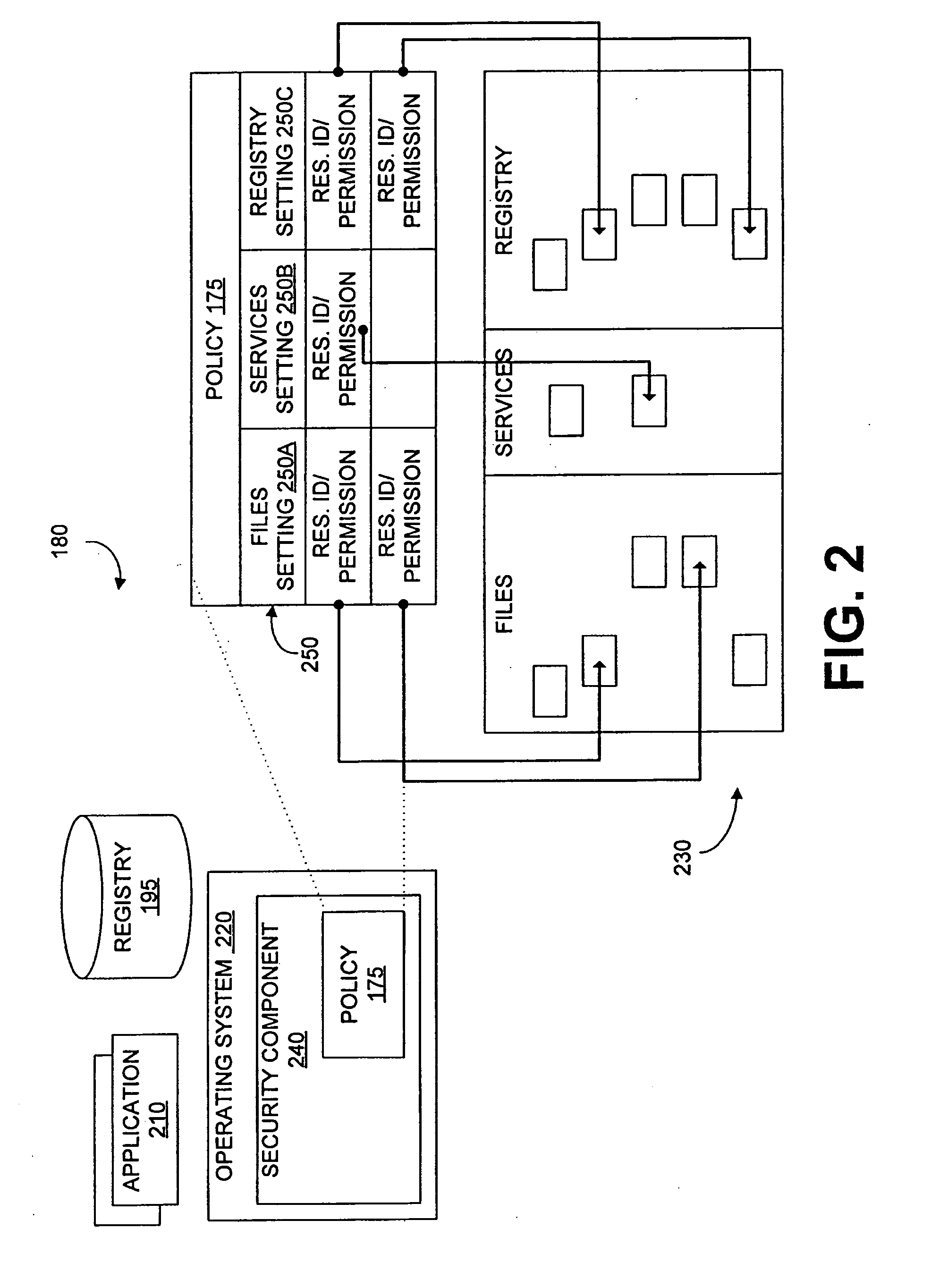
ActiveUS20070209076A1Access be denyMemory loss protectionDigital data processing detailsResource securityData provider
Security components of managed computers are configured using inoculation data. Inoculation data can be retrieved from an inoculation data provider. The inoculation data provider analyzes unauthorized software applications to develop inoculation data. The inoculation data configures the security component to deny access to resources to unauthorized software applications. Inoculation data can be embedded into a script, which is distributed via a management protocol to one or more managed computers from a management computer. Resources can include files, storage paths, memory, registry keys, processor priority, services, dynamic link libraries, archives, browser cookies, and / or ActiveX controls, Java applets, or classes thereof.
Owner:ACTIANCE
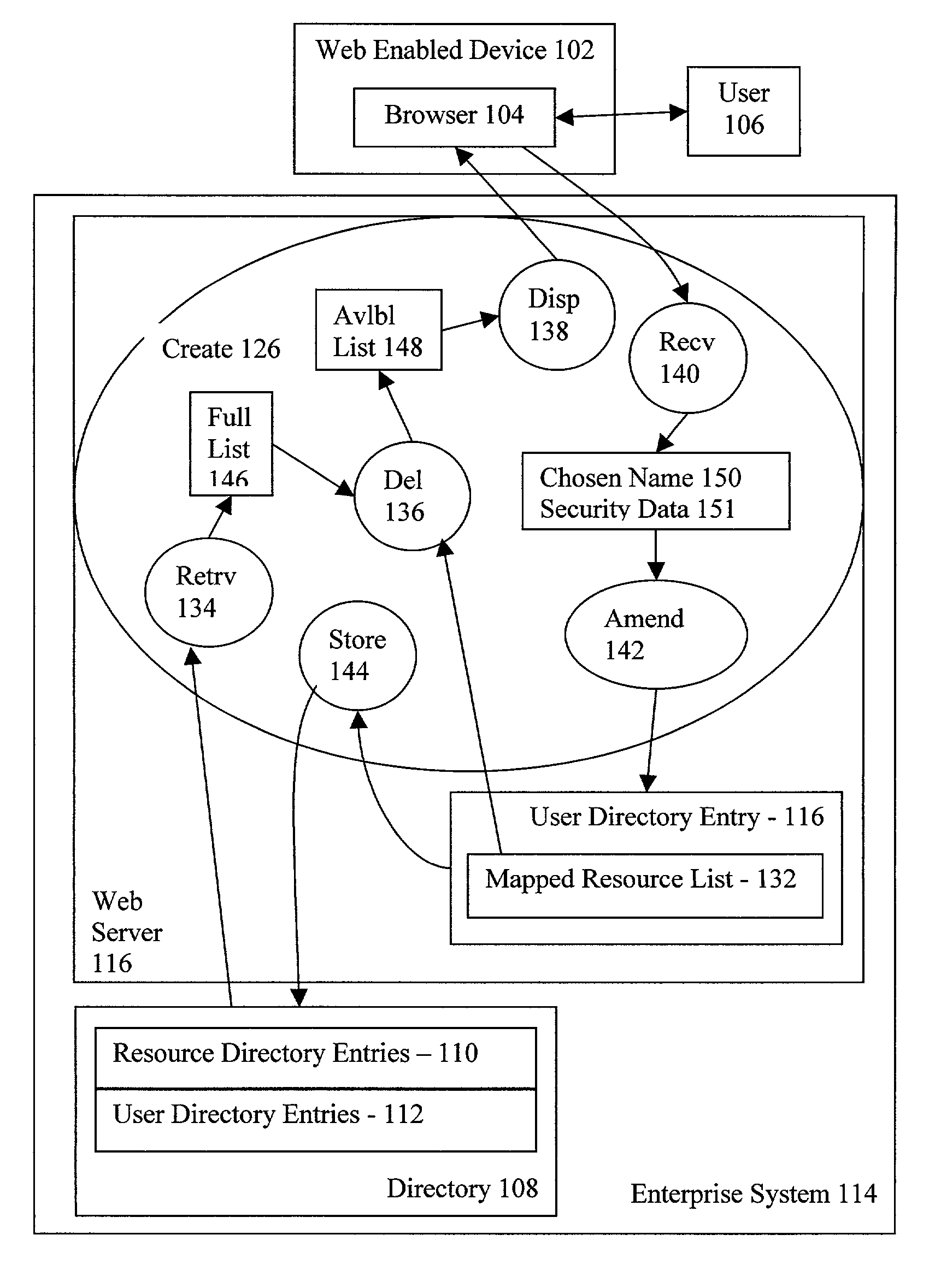
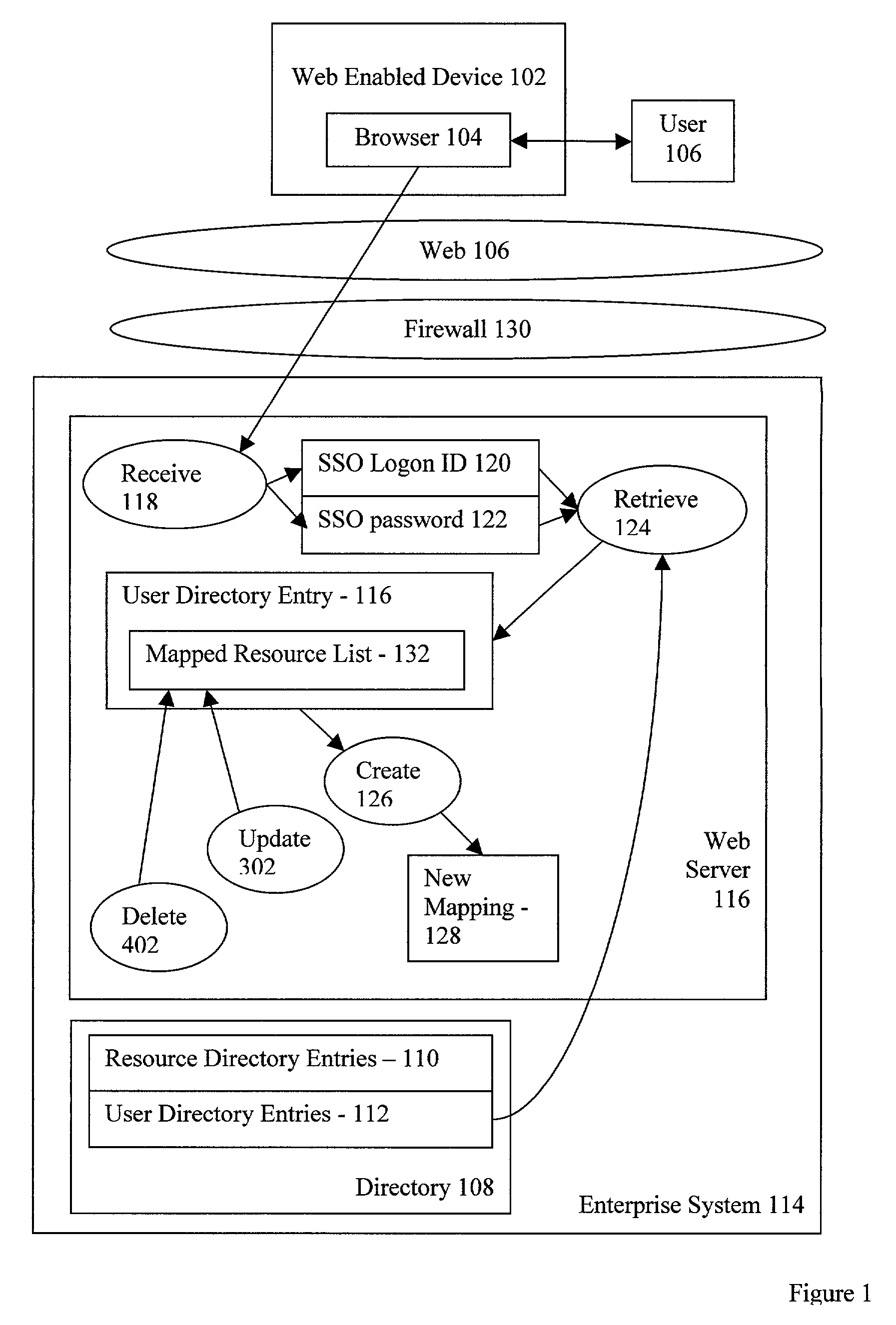
Self service single sign on management system allowing user to amend user directory to include user chosen resource name and resource security data
InactiveUS7016959B2Computer security arrangementsMultiple digital computer combinationsPasswordResource security
A method for directory enabled, self service, single sign on user account management, the method implemented in conjunction with a directory, the directory comprising resource directory entries and user directory entries. Exemplary embodiments include receiving, from a user through a browser, an SSO user ID and SSO password of the user, the SSO password being known only to the user, retrieving from the directory, in dependence upon the SSO user ID and SSO password, a user directory entry for the user, and creating, in dependence upon the user directory entry, a new mapping of a resource to the SSO user ID.
Owner:INT BUSINESS MASCH CORP
Open platform authorization and authentication system and method based on OAuth protocol
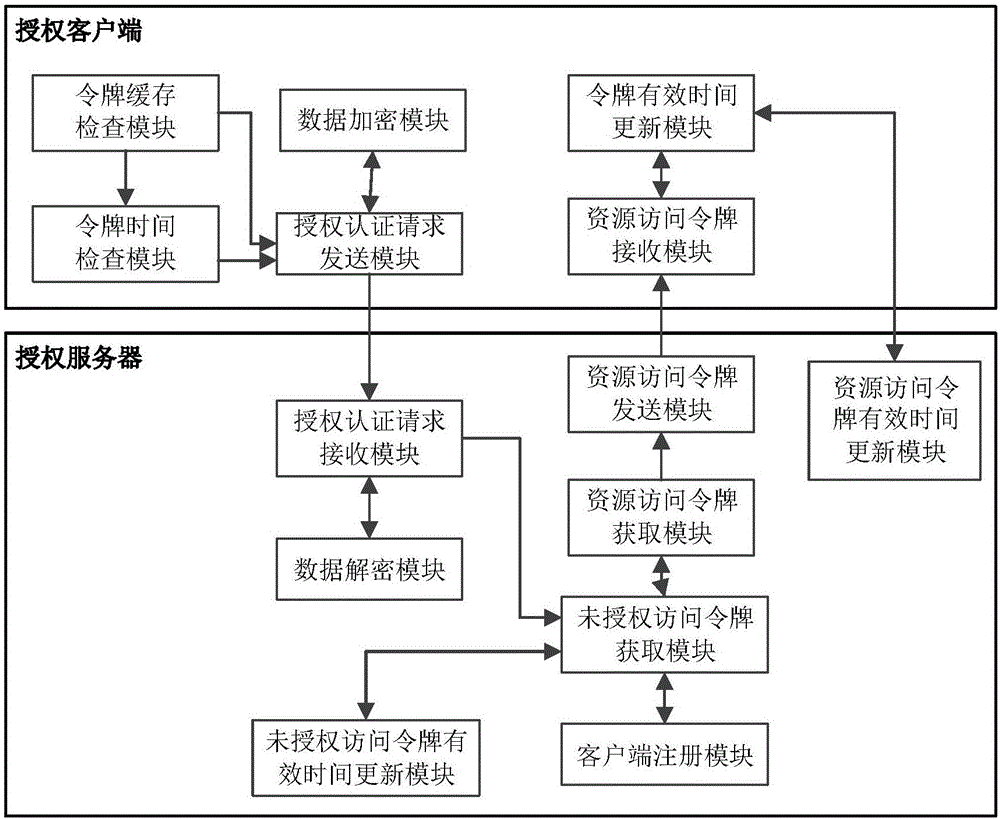
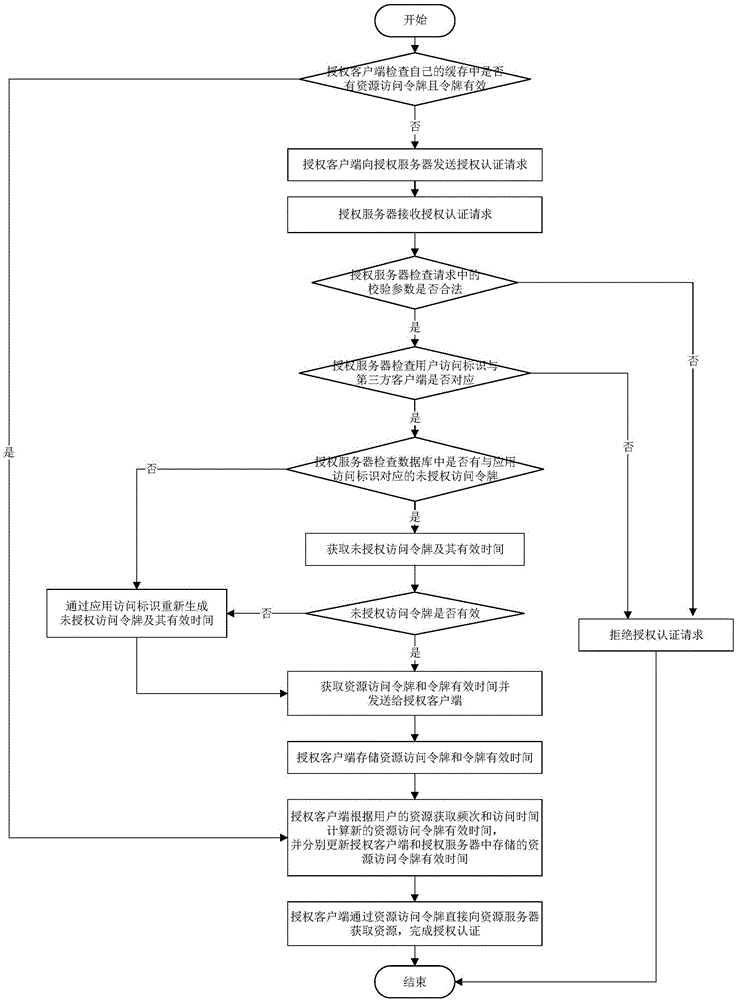
ActiveCN106534175AConvenient authorization and authentication operationsAvoid Repeated Authorization and AuthenticationTransmissionAcquisition timeOpen platform
The invention discloses an open platform authorization and authentication system and method based on an OAuth protocol, and mainly aims to solve the problem of misuse of a resource access token since the valid time of the resource access token is not optimized or limited reasonably in the prior art. The system comprises an authorization client and an authorization server, wherein the authorization client is used for transmitting an authorization and authentication request, receiving the resource access token and the valid time of the token through function modules inside the authorization client, and resetting the valid time of the token according to acquisition times and time of user resources; and the authorization server is used for receiving and checking the authorization and authentication request, acquiring an unauthorized access token and the valid of the token through function modules inside the authorization server, generating a resource access token and the valid time of the token, and transmitting the resource access token and the valid time of the token to the authorization client. Through adoption of the open platform authorization and authentication system and method, an authorization and authentication process is simplified, and the resource security is improved. The open platform authorization and authentication system and method can be applied to an authentication and authorization process during acquisition of open platform resources.
Owner:XIDIAN UNIV
Resource provisioning based on logical profiles and objective functions
Described are techniques for selecting resources for provisioning. A usage definition, including an objective function, and first set of logical profiles based on core criteria are selected. Each of the logical profiles in the first set represents a resource set characterized by a core criteria value set that specifies values for the core criteria. A second set of resulting objective function values are determined by evaluating the objective function for each of the logical profiles in the first set. A highest ranked one of the resulting objective function values in the second set is selected having a corresponding first logical profile of the first set and a corresponding core criteria value set. A third set of resources is selected which is characterized by the corresponding core criteria value set for the first logical profile. The third set of resources is any of recommended or selected for provisioning.
Owner:EMC IP HLDG CO LLC
Multimodal concierge for secure and convenient access to a home or building
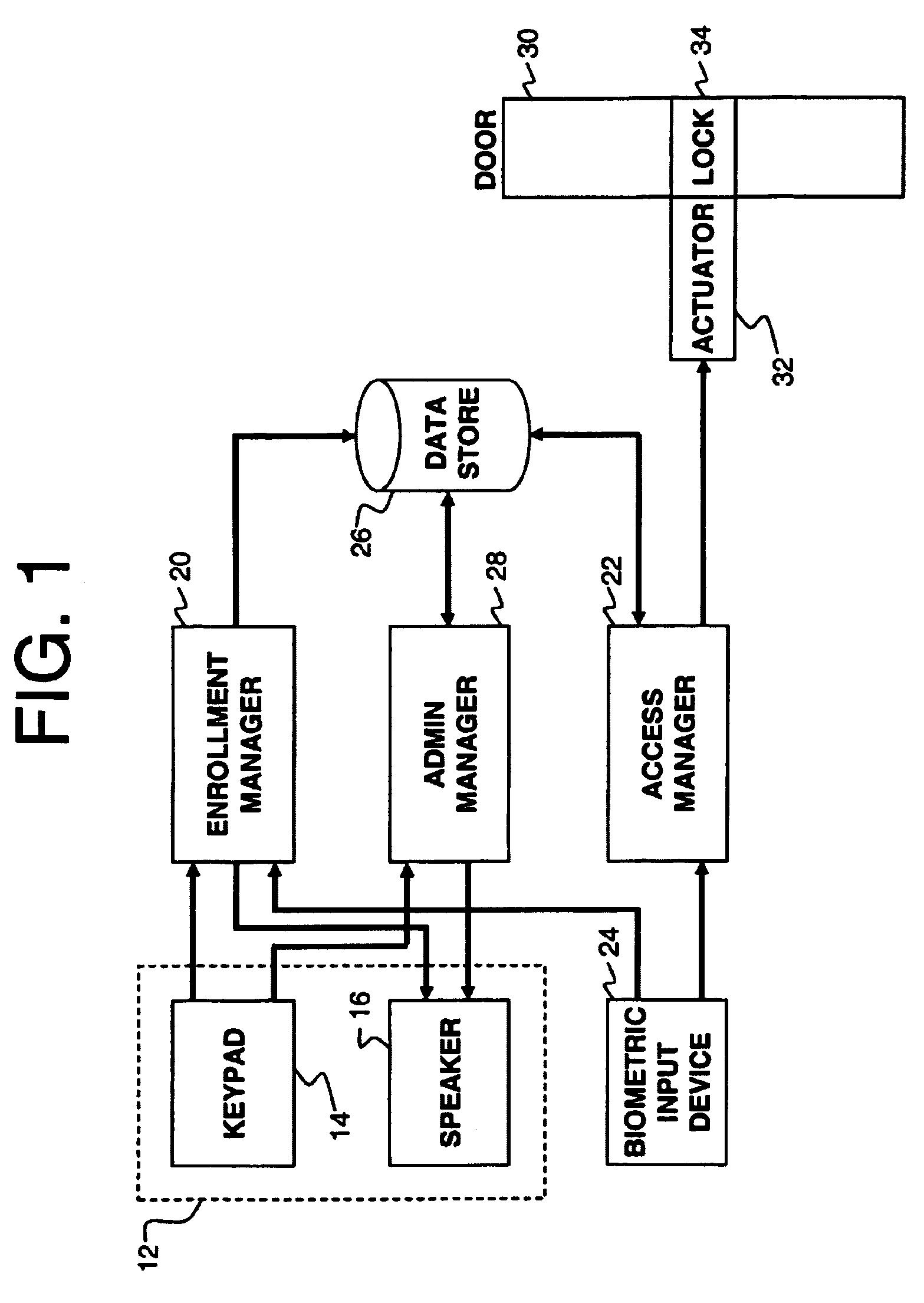
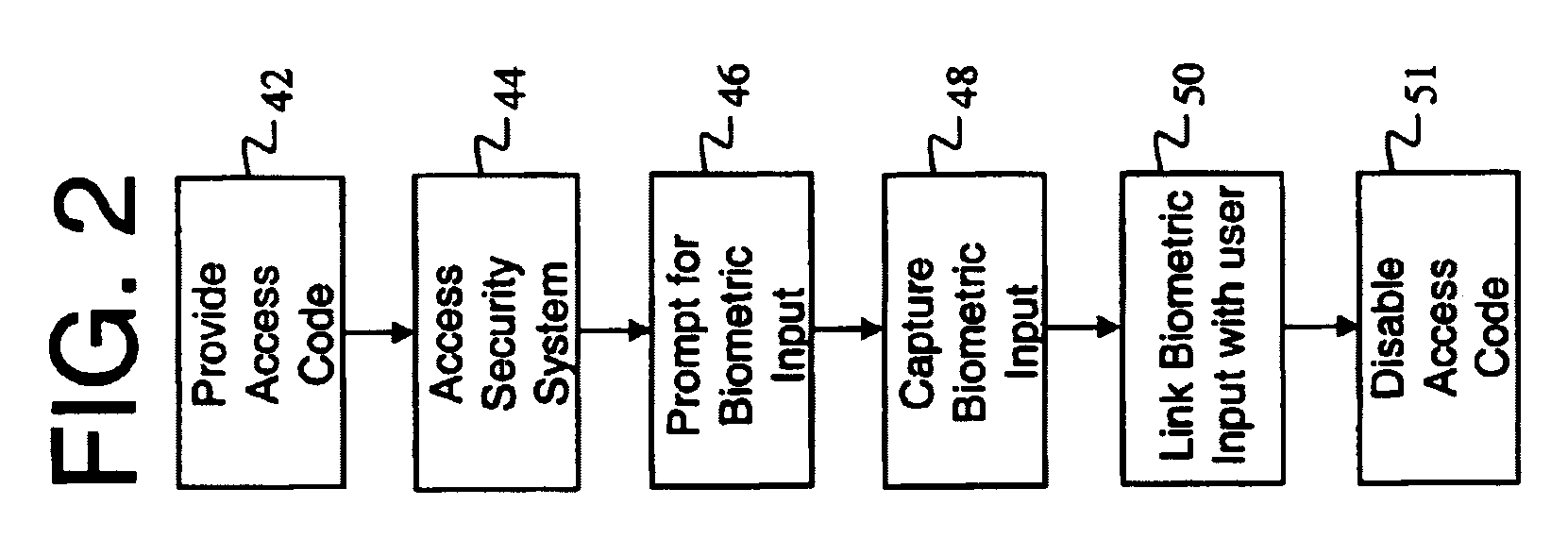
InactiveUS7064652B2Simple methodProgramme controlElectric signal transmission systemsBiometric dataInternet privacy
An improved method is provided for enrolling with a resource security system. The method includes: providing an access code to a system user; accessing the resource security system using the access code; prompting the user to input a biometric feature which identifies the user; capturing a biometric feature associated with the user; and associating the captured biometric feature with the identity of the user for subsequent verification. The method further includes subsequently granting access to the secured resource based on biometric feature data input by the user.
Owner:SOVEREIGN PEAK VENTURES LLC
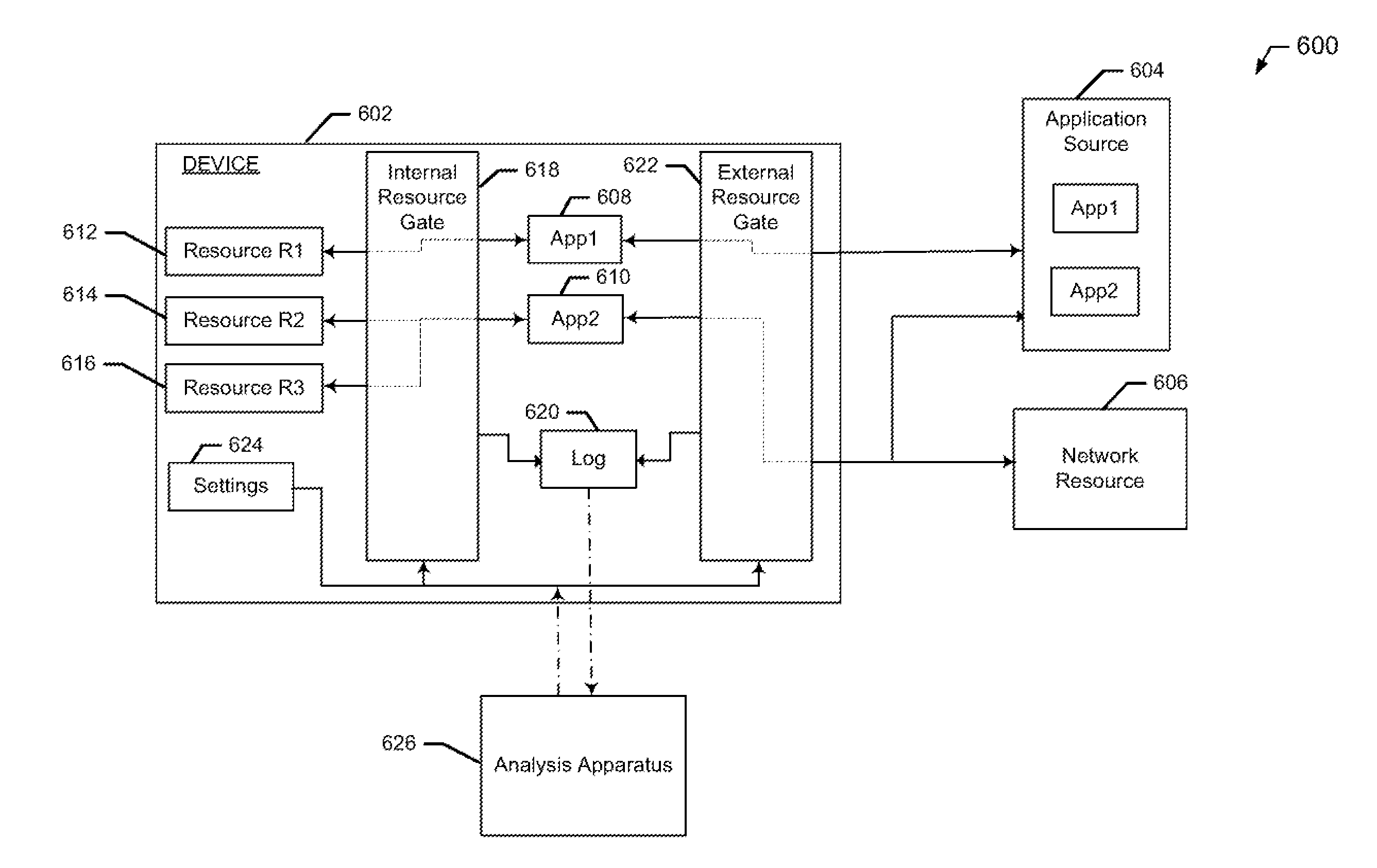
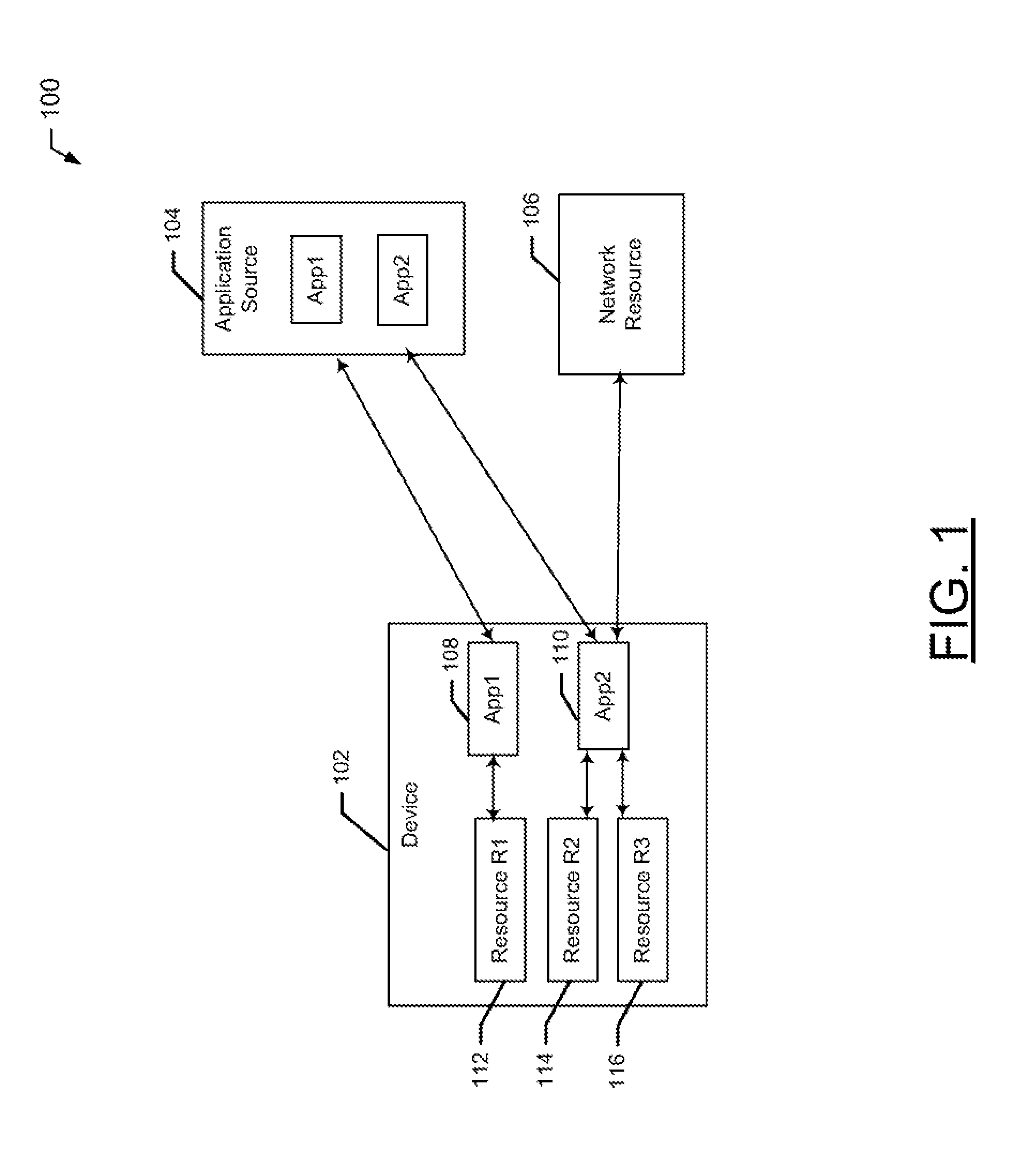
System, Method and Apparatus For Facilitating Resource Security
InactiveUS20140123319A1Facilitating resource securityFacilitate resource securityError detection/correctionDigital data processing detailsResource securityMultiple applications
A method and apparatus are provided for facilitating resource security. A method may include monitoring for resource requests by one or more applications on a device. The method may further include determining, based at least in part on the monitoring, that one of the one or more applications has requested access to a resource. The method may additionally include causing the determined resource request to be logged in a log of resource requests by the one or more applications. A corresponding apparatus is also provided.
Owner:NOKIA TECHNOLOGLES OY
Dynamic Security Access
InactiveUS20080163339A1Digital data processing detailsComputer security arrangementsResource securitySystem usage
An approach for providing dynamic security access is presented. A dynamic security system receives a resource request from a user. The dynamic security system computes a dynamic user security value using a user security formula and user attribute values corresponding to the user. In addition, the dynamic security system computes a resource security value using a resource security formula and resource attribute values corresponding to the resource. Once computed, the dynamic security system compares the dynamic user security value with the resource security value and, if the dynamic user security value is greater than or equal to the resource security value, the dynamic security system grants resource access to the user.
Owner:JANAKIRAMAN JANANI +1
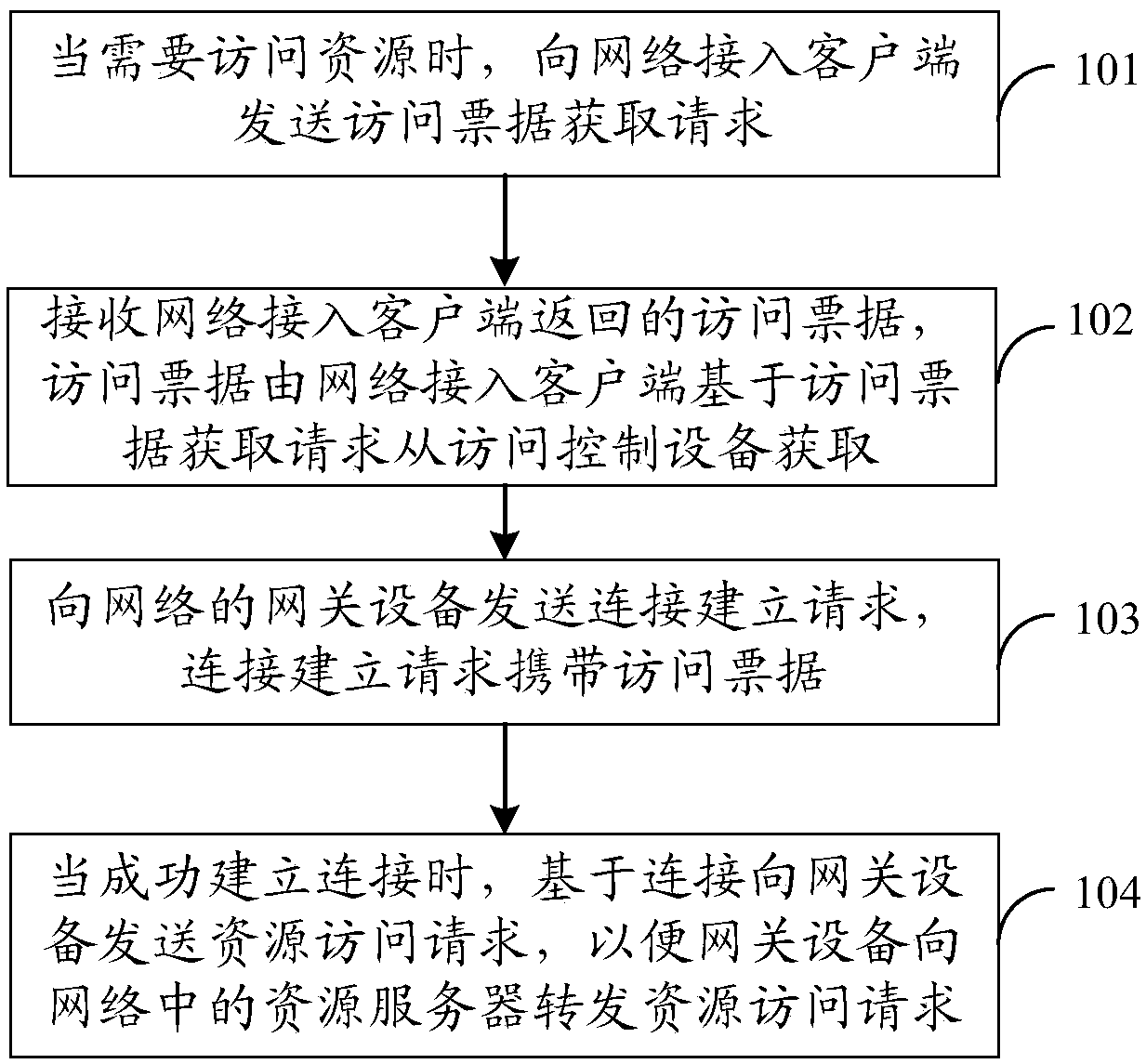
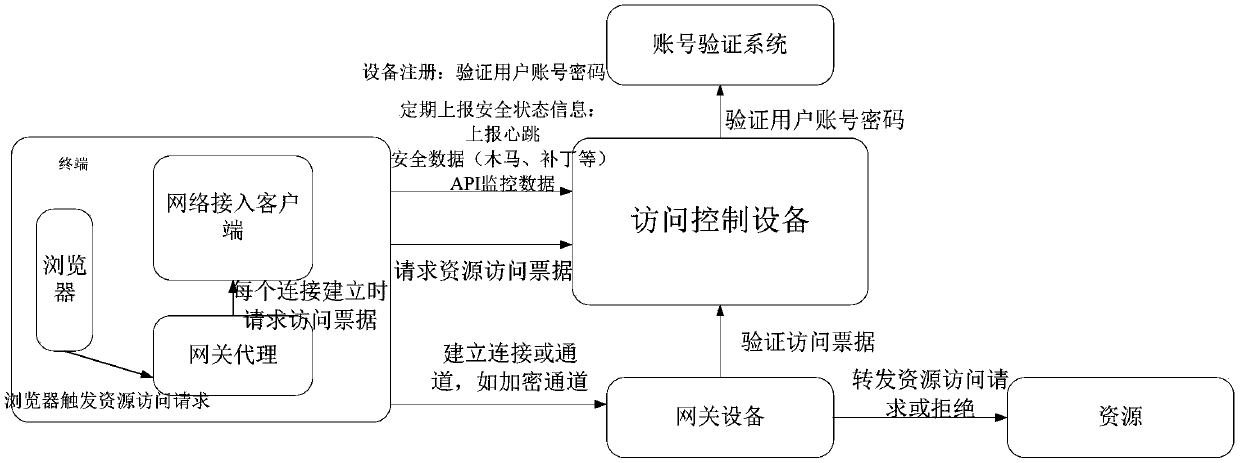
Resource access method and device, terminal and storage medium
The embodiment of the invention discloses a resource access method and device, a terminal and a storage medium. According to the embodiment of the invention, when resources need to be accessed, an access bill acquisition request is sent to a network access client, an access bill returned by the network access client is received, wherein the access bill is acquired by the network access client fromthe access control equipment based on the access bill acquisition request; a connection establishment request is sent to a gateway device of the network, wherein the connection establishment requestcarries the access bill; when the connection is successfully established, a resource access request is sent to the gateway equipment based on the connection, so that the gateway equipment forwards theresource access request to a resource server in the network; according to the scheme, the resource security can be improved.
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
Virtual resource management method and device and electronic equipment
InactiveCN109993530AImprove reliabilityImprove securityDigital data protectionPayment protocolsResource securityResource transfer
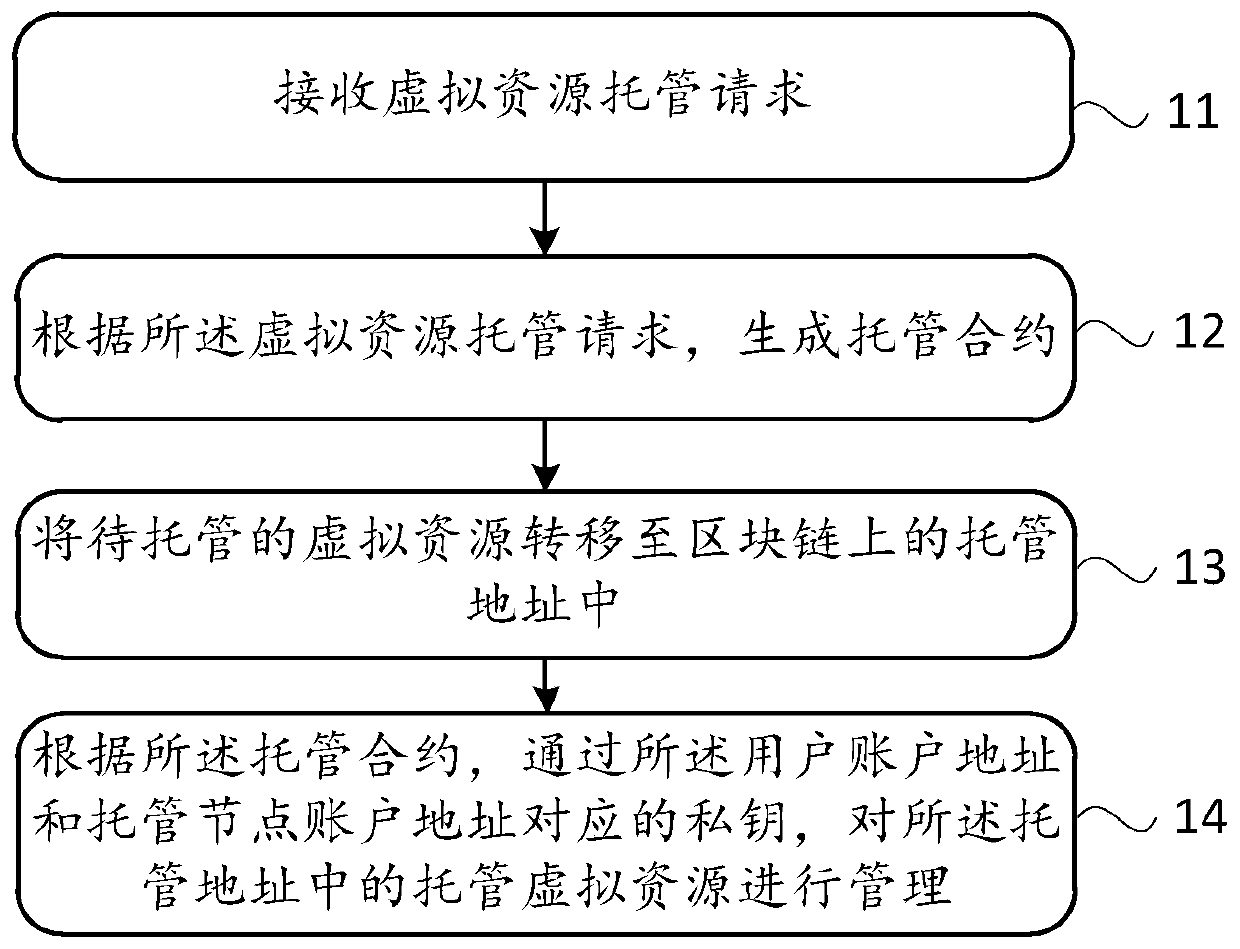
The invention discloses a virtual resource management method, which is used for solving the problem of low virtual resource security in the prior art. The method comprises the following steps: receiving a virtual resource hosting request; wherein the virtual resource hosting request is used for requesting hosting of virtual resources; generating a hosting contract according to the virtual resourcehosting request; wherein the hosting contract comprises at least one user account address and at least one hosting node account address; transferring the virtual resources to be hosted to a hosting address on a block chain, wherein the hosting address is generated according to the hosting contract; and according to the hosting contract, managing hosting virtual resources in the hosting address through the user account address and a private key corresponding to the hosting node account address. The invention further discloses a virtual resource management device, electronic equipment and a computer readable storage medium.
Owner:北京柏链基石科技有限公司
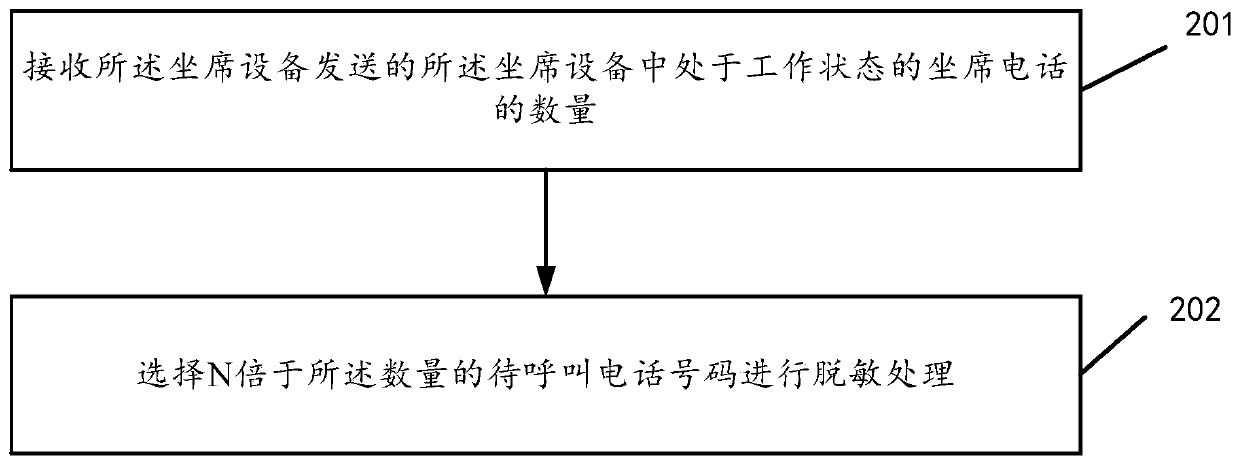
Call method, desensitization server, agent device and computer readable storage medium
InactiveCN109788145AEnsure resource securityLess restraintSpecial service for subscribersResource securitySpeech sound
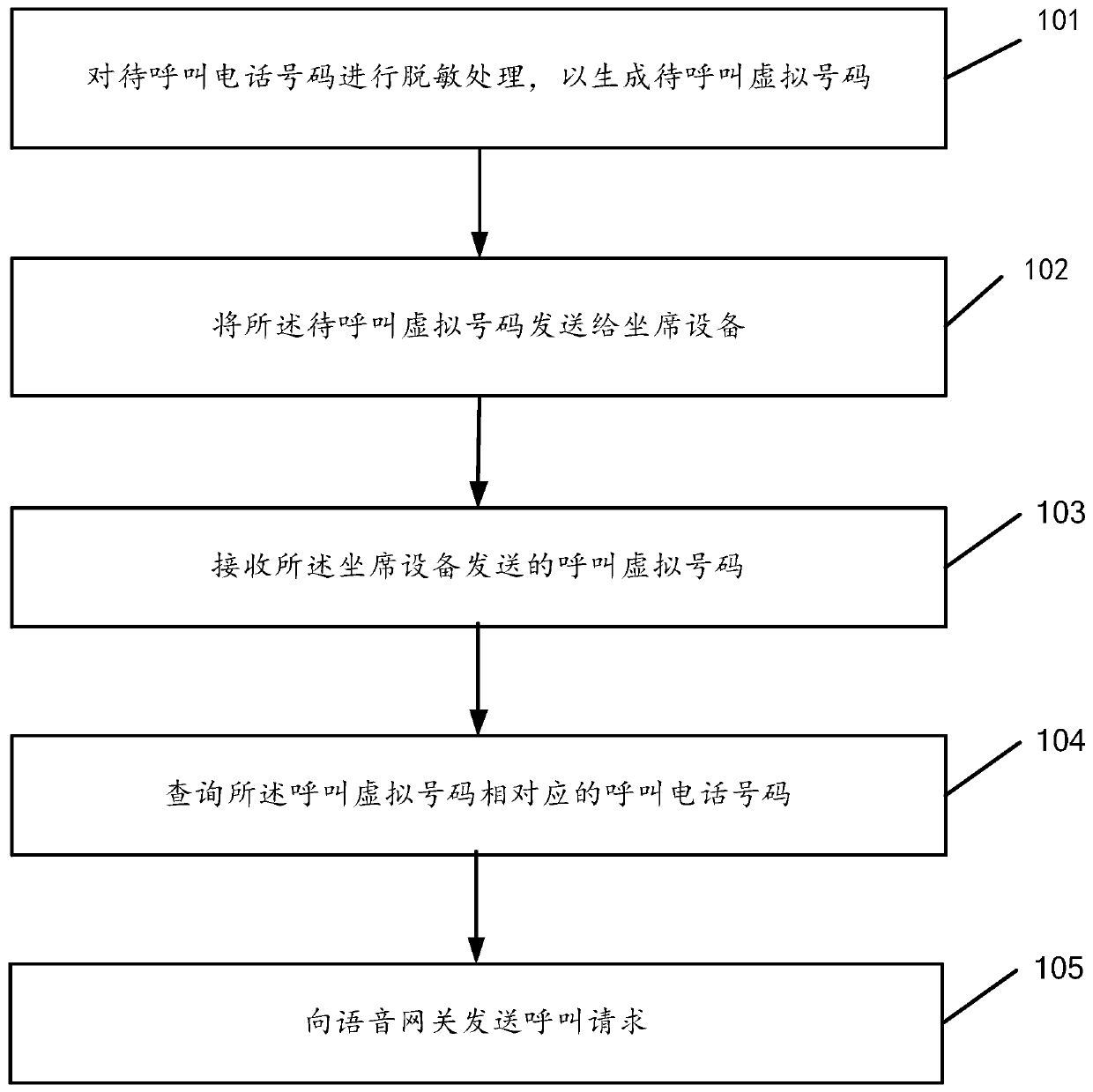
The invention discloses a calling method, a desensitization server, seat equipment and a computer readable storage medium. When the method is executed in a desensitization server, the method comprisesthe following steps: carrying out desensitization processing on a to-be-called telephone number to generate a to-be-called virtual number; Sending the virtual number to be called to seat equipment; Receiving a calling virtual number sent by the agent device, wherein the calling virtual number is determined by the agent device according to the selection of the agent to the to-be-called virtual number; Inquiring a calling telephone number corresponding to the calling virtual number; By means of the method, on the premise that the client resource safety is guaranteed, the constraint of the worksite on the work personnel of the party B can be reduced, and therefore the work personnel of the party B can work better.
Owner:西安天钥科技有限公司
A method and system for implementing resource personalized security access control
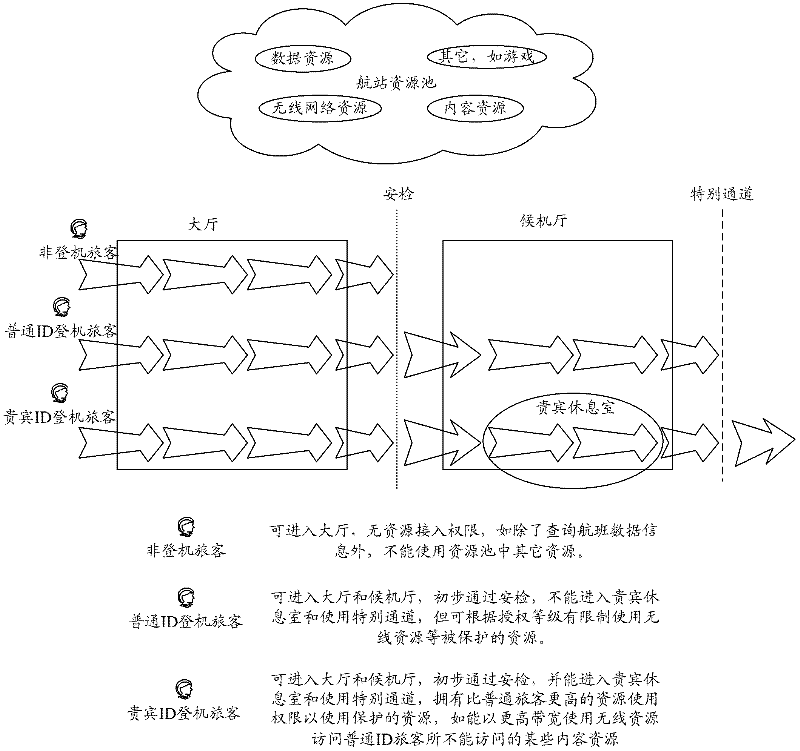
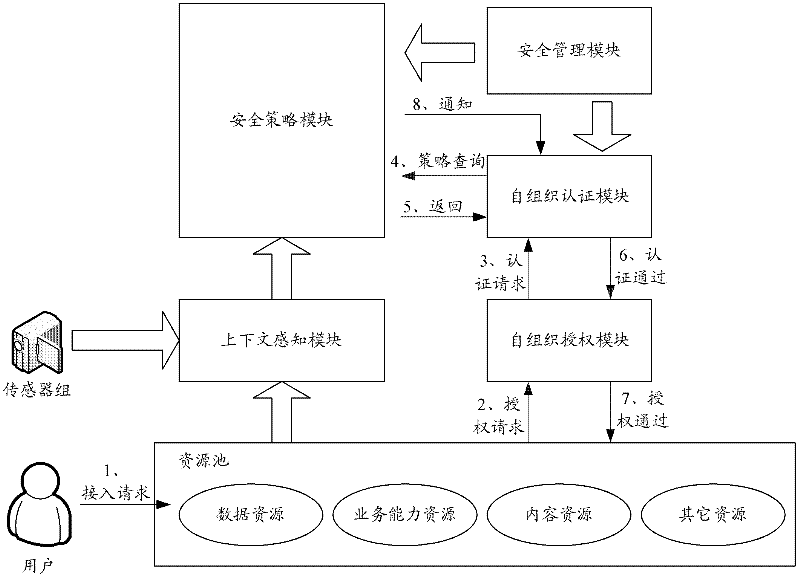
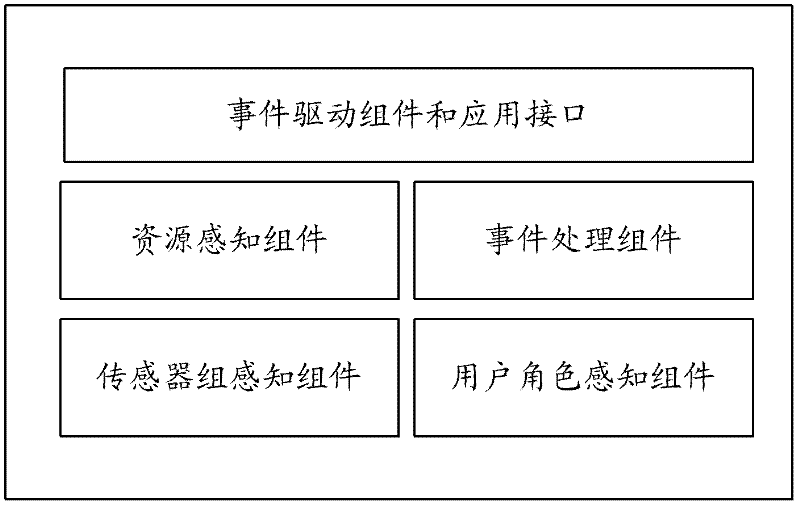
InactiveCN102300212AImprove satisfactionSupport continuitySecurity arrangementPersonalizationResource security
The present invention discloses a method and system for realizing resource individualized security access control, which can obtain the characteristic identity information associated with the user by the context awareness module, as well as the environment and resource capability characteristic information associated with the identity information; the change of the characteristic information After the situation is filtered and processed by the context awareness module, a corresponding event is formed and notified to the security policy module. The security policy module determines the real-time security policy of the user based on the change of the user context and the set of basic security policies; During the configurable life cycle of the policy, the authentication module and the authorization module obtain the user's real-time security policy from the security policy module, and dynamically update the user's authentication mechanism and authorization mechanism accordingly. The method and system of the present invention combine user context awareness technology with corresponding user real-time security policies, and can effectively support the continuity and dynamics of Internet of Things resource security services.
Owner:ZTE CORP
Network node machine and information network system
InactiveUS20080086763A1Propelling public useEnsure safetyDigital data processing detailsUnauthorized memory use protectionManagement unitResource security
Owner:FUJITSU LTD
Play control method and device for smart televisions
InactiveCN103686385AImplement playback controlSelective content distributionResource informationResource security
The invention discloses a play control method and device for smart televisions. The method comprises receiving play instructions, and determining program resource information that users want to watch; comparing the corresponding program resource information of the play instructions with preset program resource information with security levels, and determining security levels of the program resource information corresponding to the play instructions; comparing the security levels of the program resource information corresponding to the play instructions with security levels set for current play environments, and rejecting the play instructions if the security levels fail to meet the security levels set for current play environments. According to the method and the device, play control can be performed on program resources to be played according to the preset program resource security level information and the current play environment security level information, and program play control based on security levels for smart televisions is achieved.
Owner:LE SHI ZHI ZIN ELECTRONIC TECHNOLOGY (TIANJIN) LTD
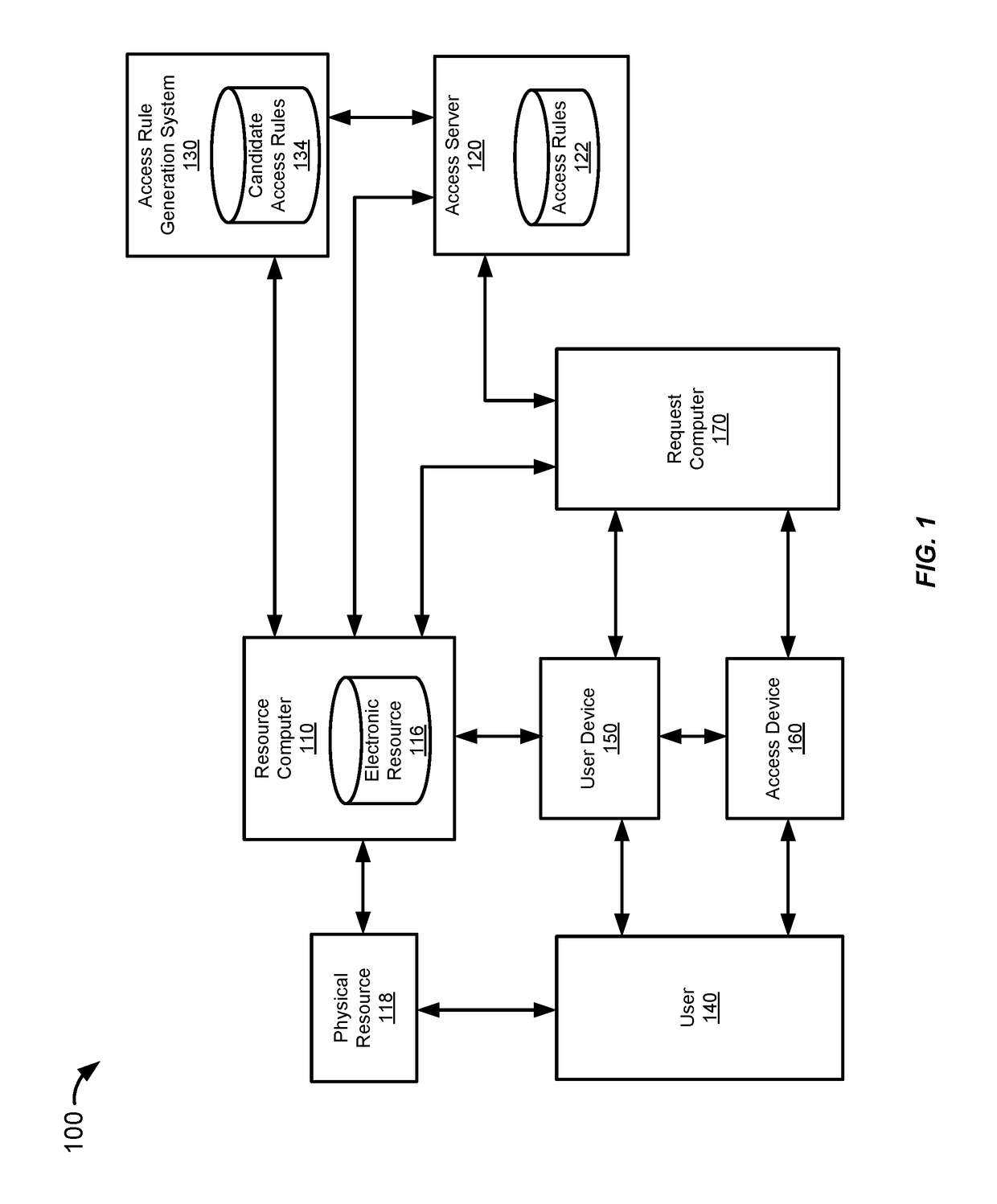
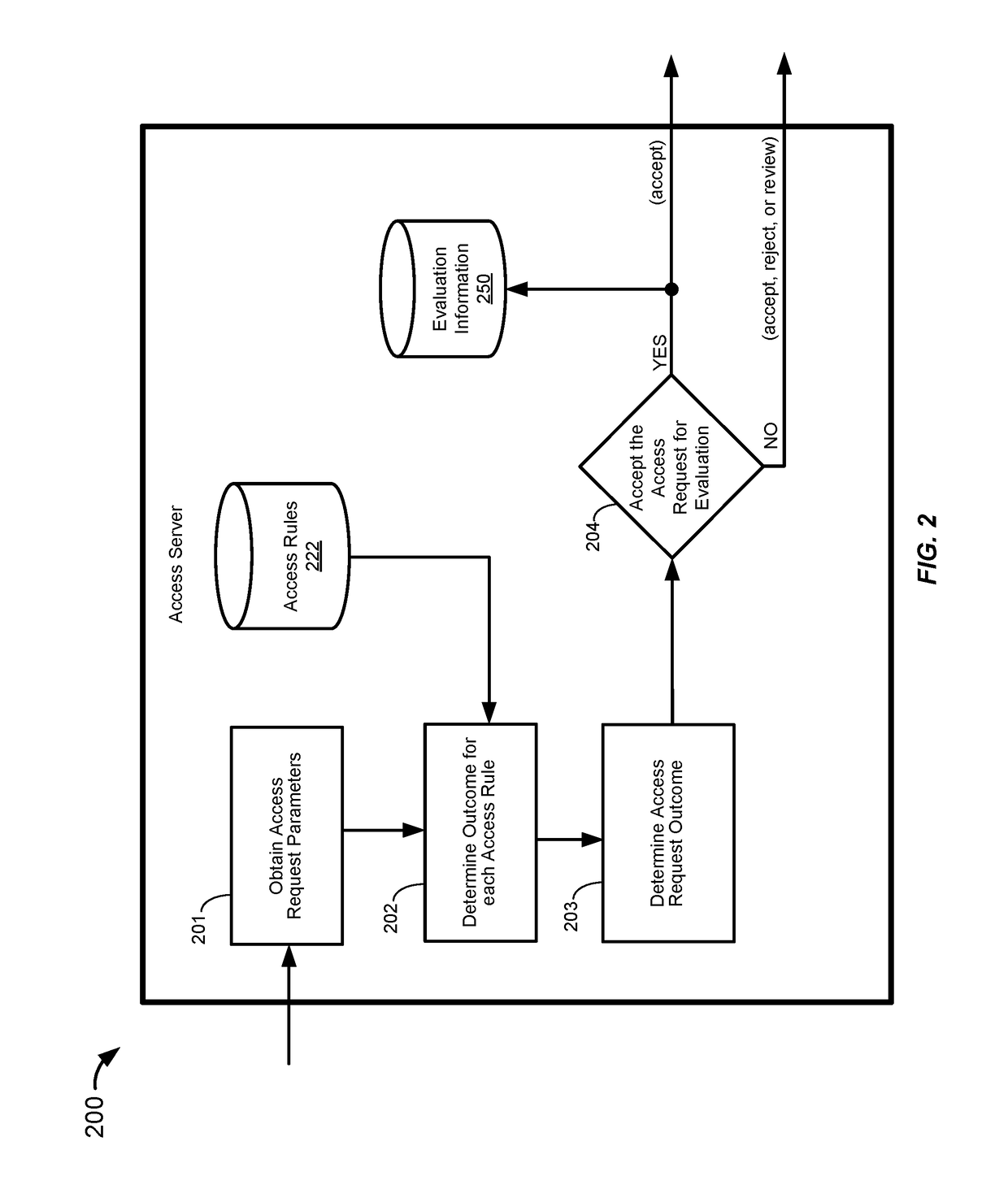
Systems and methods for generation and selection of access rules
A resource security system may generate access rules for use in determining whether to grant or deny a request for access to a resource. In order to generate the access rules, the resource security system may select certain access request parameters and determine conditions associated with those parameters. The resource security system may generate mutually exclusive segments associated with a condition of each of the parameters. The resource security system may generate independent access rules based on the segments. The resource security system may then evaluate the performance of each of the access rules based on validity information corresponding to previously received access requests that satisfy the conditions of a particular access rule.
Owner:VISA INT SERVICE ASSOC
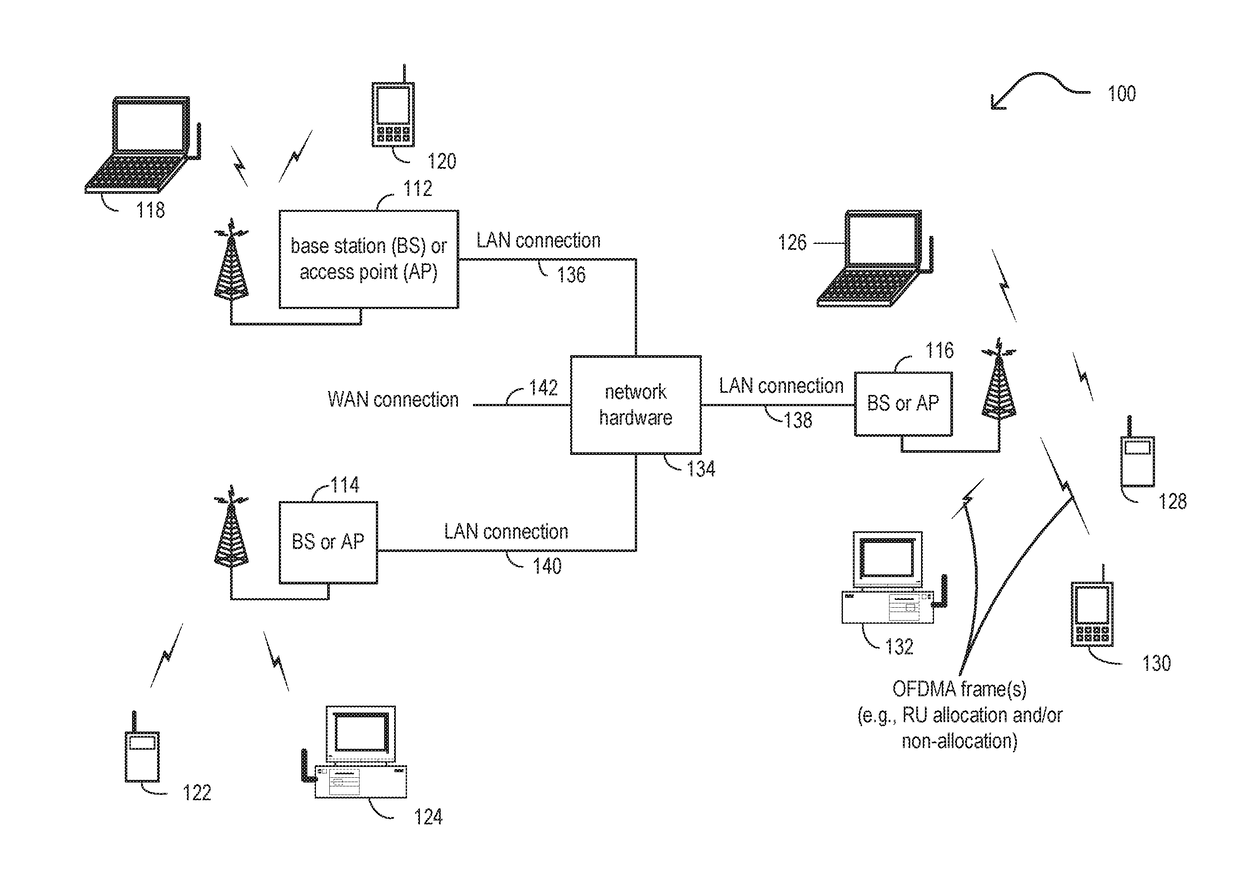
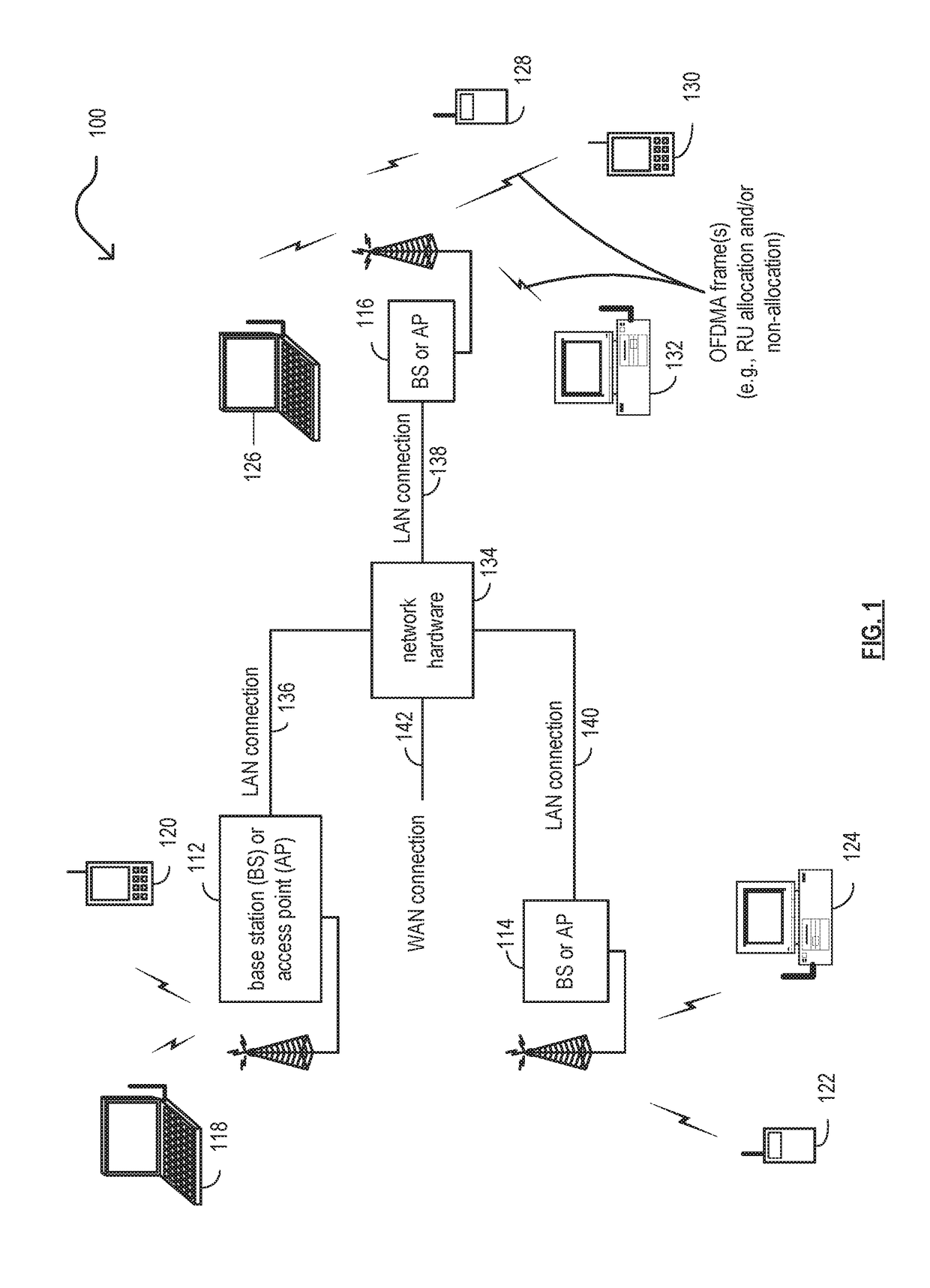
Resource unit (RU) allocation within wireless communications
ActiveUS20170126453A1Transmission path divisionMulti-frequency code systemsCommunication interfaceTelecommunications
A wireless communication device (alternatively, device, WDEV, etc.) includes at least one processing circuitry configured to support communications with other WDEV(s) and to generate and process signals for such communications. In some examples, the device includes a communication interface and a processing circuitry, among other possible circuitries, components, elements, etc. to support communications with other WDEV(s) and to generate and process signals for such communications. A WDEV generates an orthogonal frequency division multiple access (OFDMA) frame that includes a preamble that specifies allocation and / or non-allocation of at least one resource unit (RU) for a communication channel and transmits the OFDMA frame to at least one other wireless communication device to be processed by the at least one other wireless communication device to determine the allocation of the at least one RU for the communication channel or the non-allocation of the at least one RU for the communication channel.
Owner:AVAGO TECH INT SALES PTE LTD
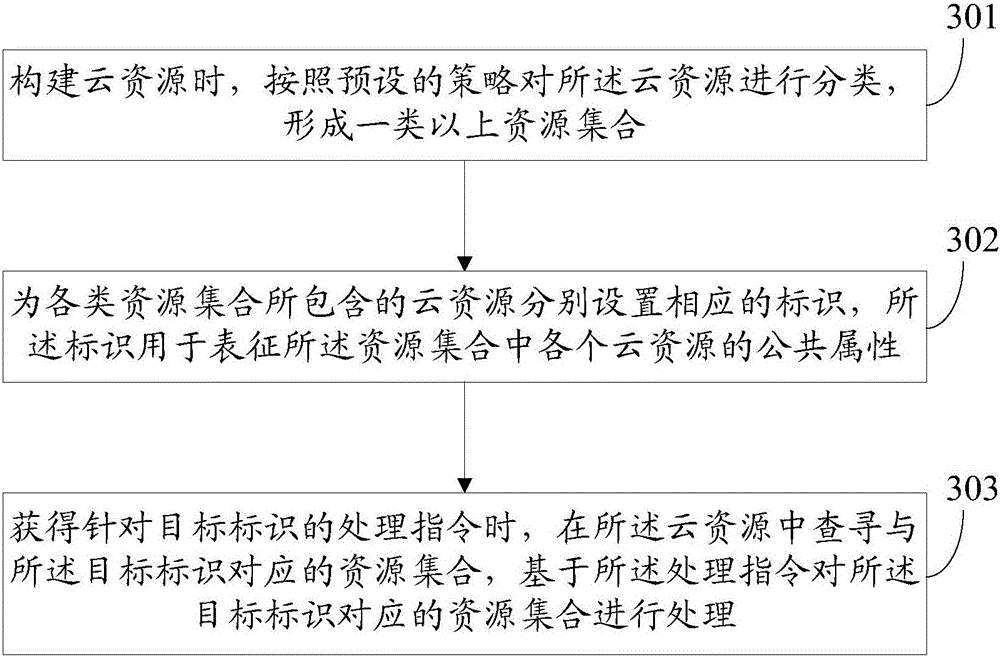
Resource management method and resource management device
ActiveCN105812175AManagement Convenience and AutomationEasy to manageData switching networksResource securityResource management
The invention discloses a resource management method and a resource management device. The method includes classifying cloud resource according to a predetermined strategy when constructing the cloud resource so as to form more than one type of resource sets; setting the cloud resources contained in different types of resource sets with corresponding marks which are used for indicating the public attributes of the cloud resources in the resource sets; managing the cloud resource according to the marks.
Owner:LENOVO (BEIJING) CO LTD
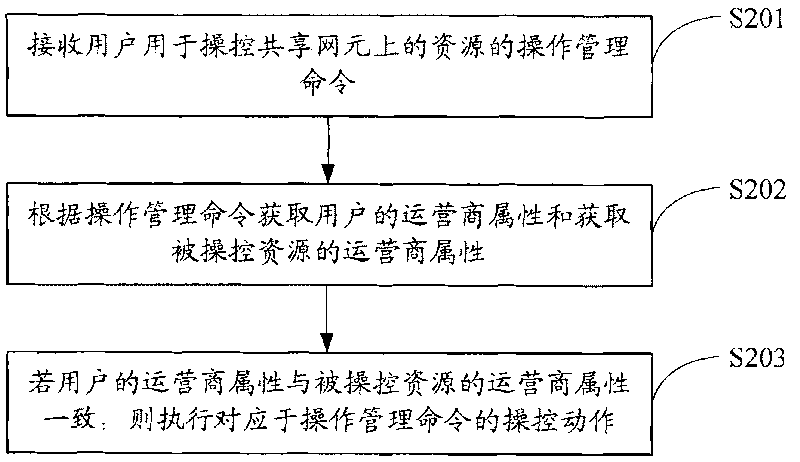
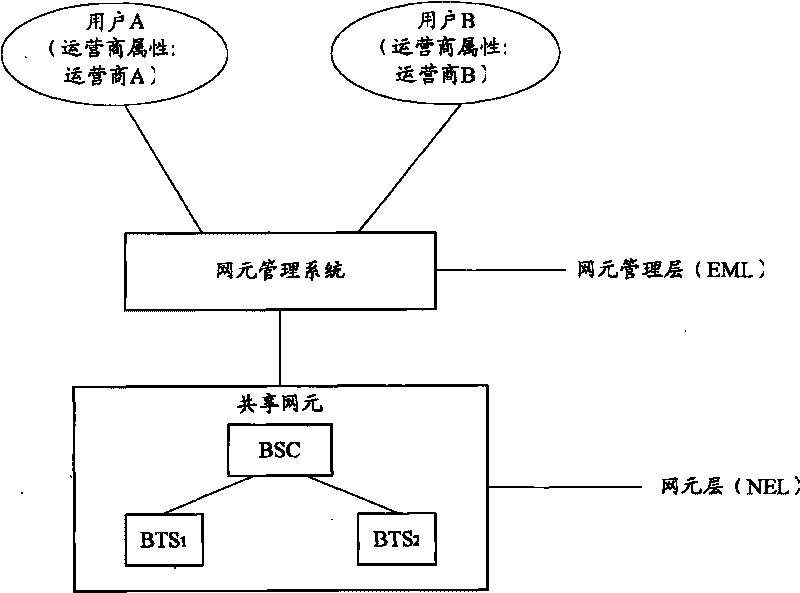
Resource control method on sharing network element, sharing network element and relevant equipment
The embodiment of the invention provides a resource control method on a sharing network element, a sharing network element and relevant equipment, so as to solve the resource safety problem when the sharing network element with telecommunication merging is managed by a webmaster proposal in the prior art; the method comprises the following steps: an operational management command for controlling the resources on the sharing network element by a user is received; operator attribute of controlled resource is obtained and operator attribute of the user is obtained according to the operational management command; if the operator attribute of the user is consistent to the operator attribute of the controlled resource, the control action corresponding to the operational management command is carried out. The method solves the webmaster safety problem when a plurality of operator webmasters are merged under the telecommunication merging.
Owner:SHANGHAI HUAWEI TECH CO LTD
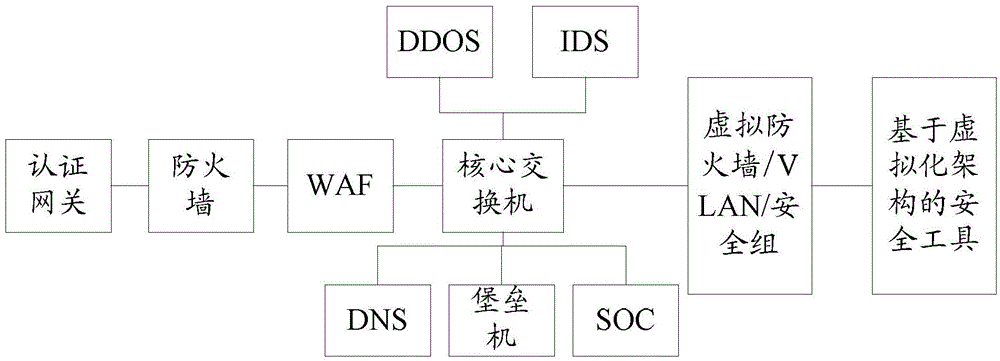
Security system for cloud data center
The invention discloses a security system for a cloud data center, which is applied to security protection of the cloud data center. The security system comprises a conventional security layer, which is used for carrying out security protection on the periphery of the cloud data center through a boundary security reinforcing method; a virtual resource security layer, which is used for carrying out security protection on virtual resources in the cloud data center through isolating the virtual resources; and a virtual resource platform security layer, which is used for a security tool based on a virtual architecture to monitor a virtual machine to carry out security protection on a virtual resource platform in the cloud data center. According to the security system, security protection is fully carried out on the cloud data center from protection of the conventional security layer to protection of the virtual platform layer to the security protection of the virtual resource layer.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
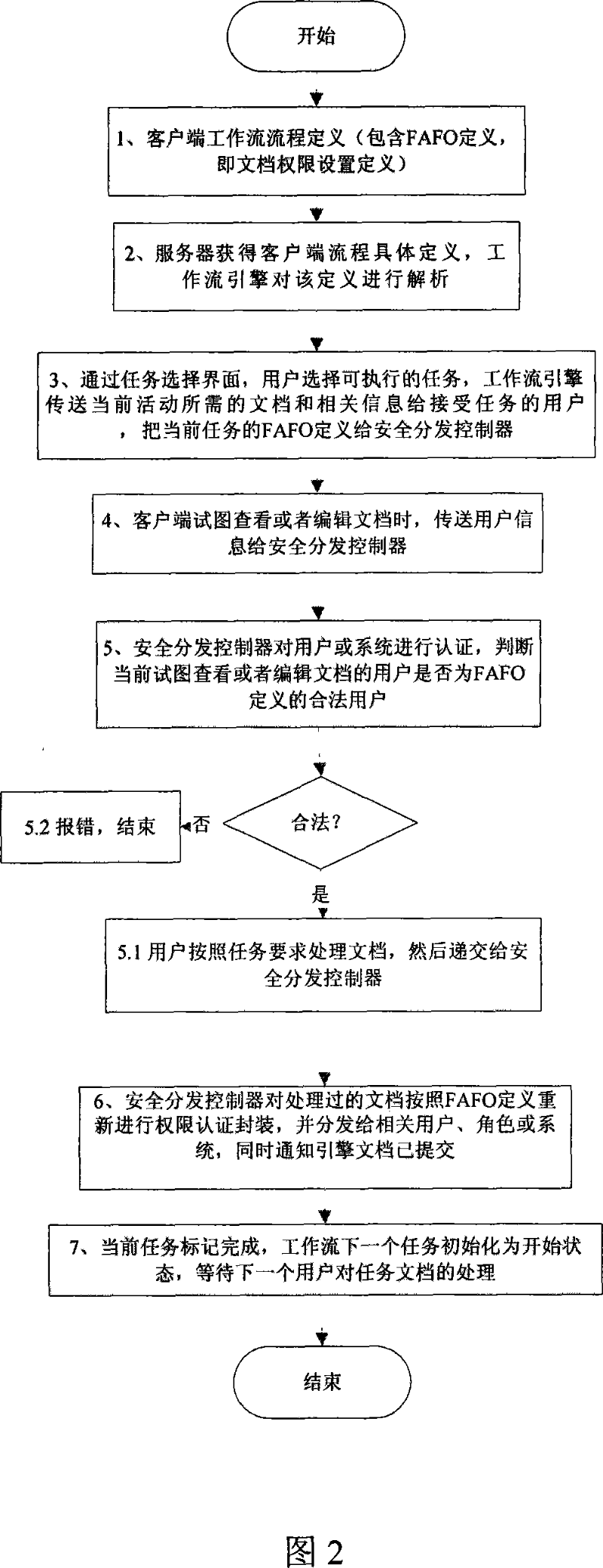
Electronic document safety distribution controlling method based on task stream
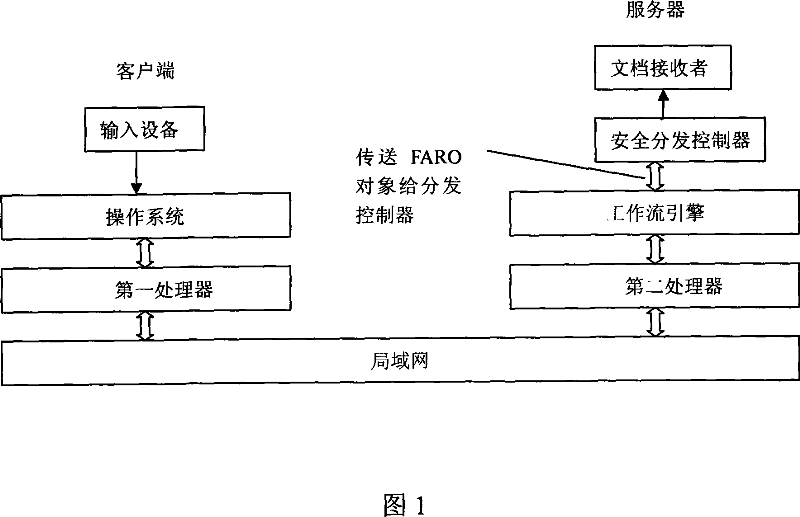
InactiveCN101038637AImprove securityEnsure safetyOffice automationElectronic documentDistribution control
A workflow-bases electronic file resource security distribution control method, belonging to the technical field of the workflow information security, the method refers to the ODRL standard, brings forward the FARO circulation resource right object under the workflow environment, introducing the definition concerning the digital content protection in ODRL to the flow definition language XPDL into the workflow for expanding the XPDL, thereby the expanded XPDL supports the copyright protection on the digital content in the workflow, and supports the safety control of the circulatory file resource by encapsulating the right, in this way, the security of the digital content circulated in the workflow is ensured. The invention has the advantage of that the circulatory file in the workflow has a high security.
Owner:EAST CHINA NORMAL UNIV
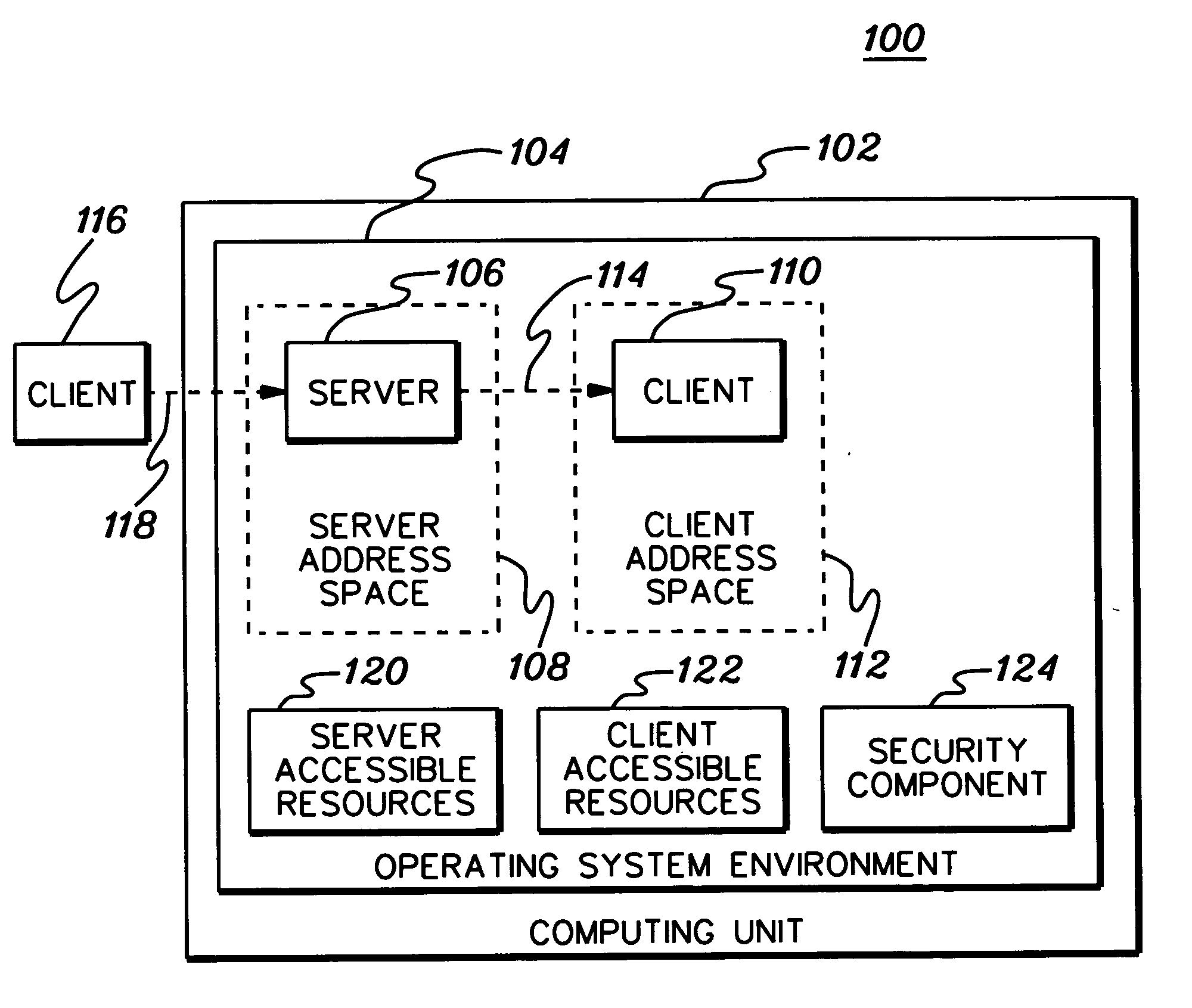
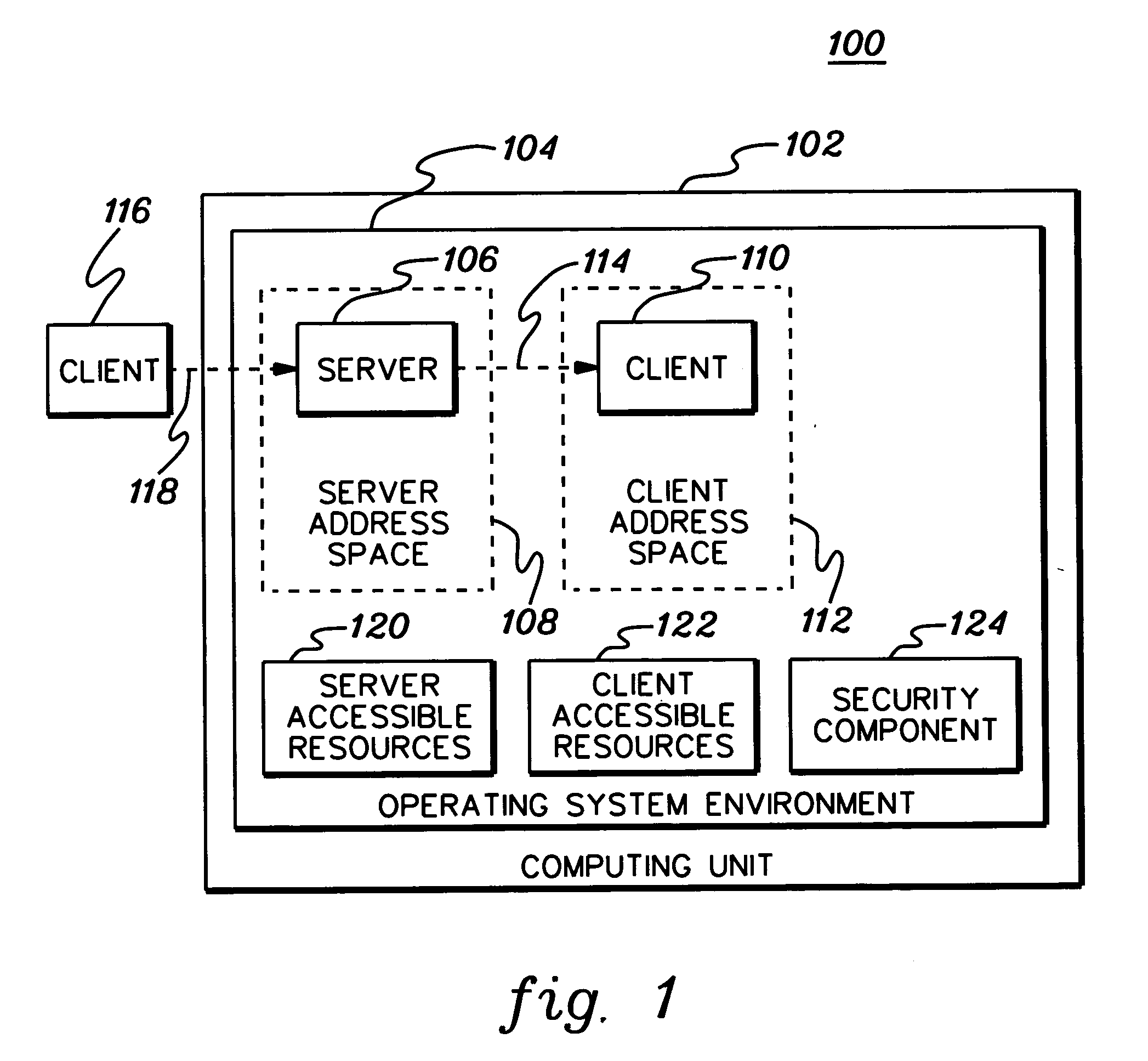
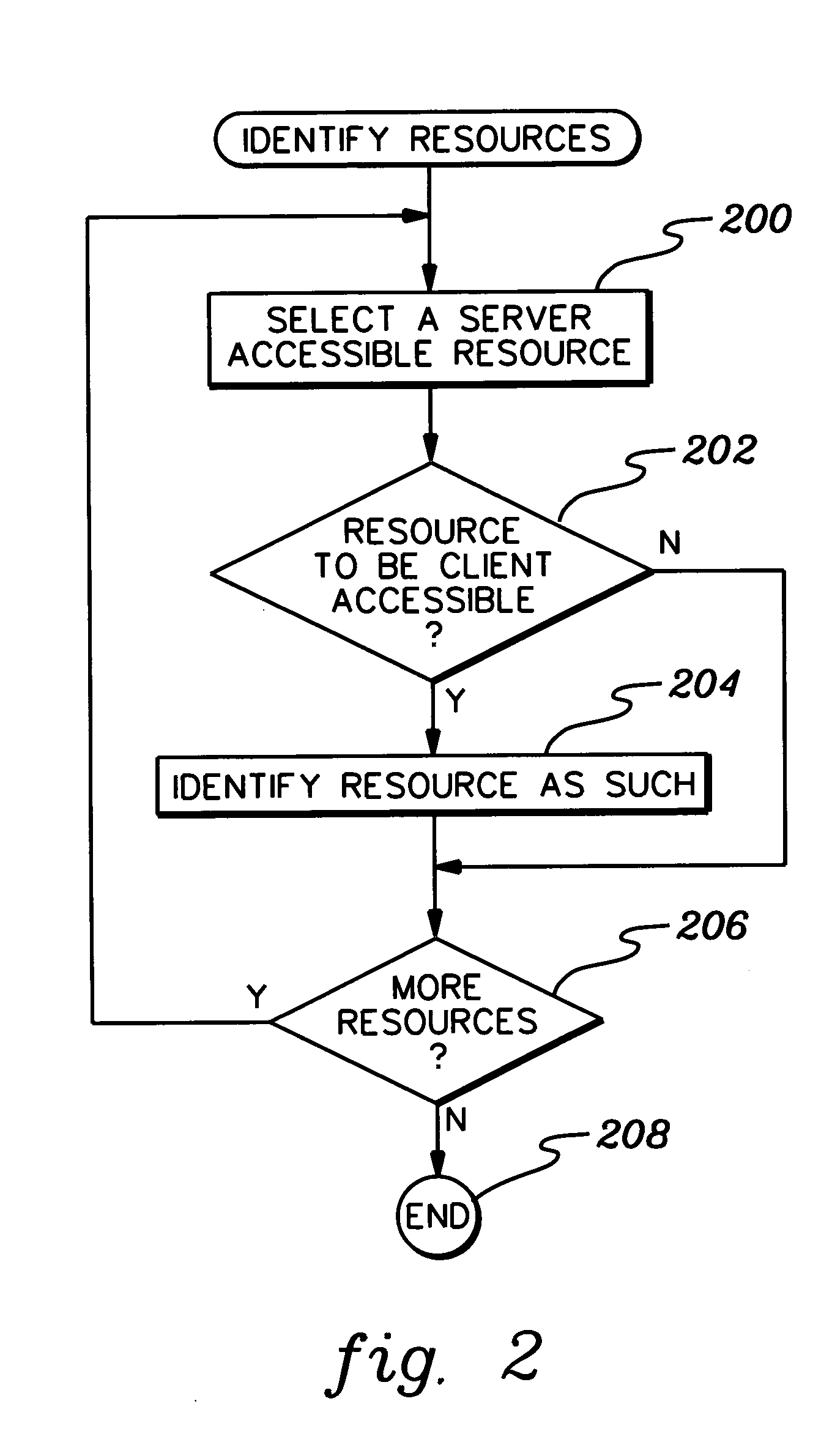
Accessing protected resources via multi-identity security environments
ActiveUS20060137021A1Digital data processing detailsUser identity/authority verificationResource securityComputer science
Owner:IBM CORP
Object and resource security system
InactiveUS20060053439A1Safety is assuredTelevision system detailsKey distribution for secure communicationPlaintextResource security
According to the invention, a method for securing a plaintext object within a content receiver is disclosed. In one step, a secure portion of a secure object and a plaintext remainder of the secure object are received. Which portion of the secure object is the secure portion is determined. The secure portion is decrypted to provide a plaintext portion. The plaintext object that comprises the plaintext portion and the plaintext remainder is formed. The plaintext object is stored including authentication and authorization.
Owner:GOOGLE TECH HLDG LLC
Container security system based on cloud computing
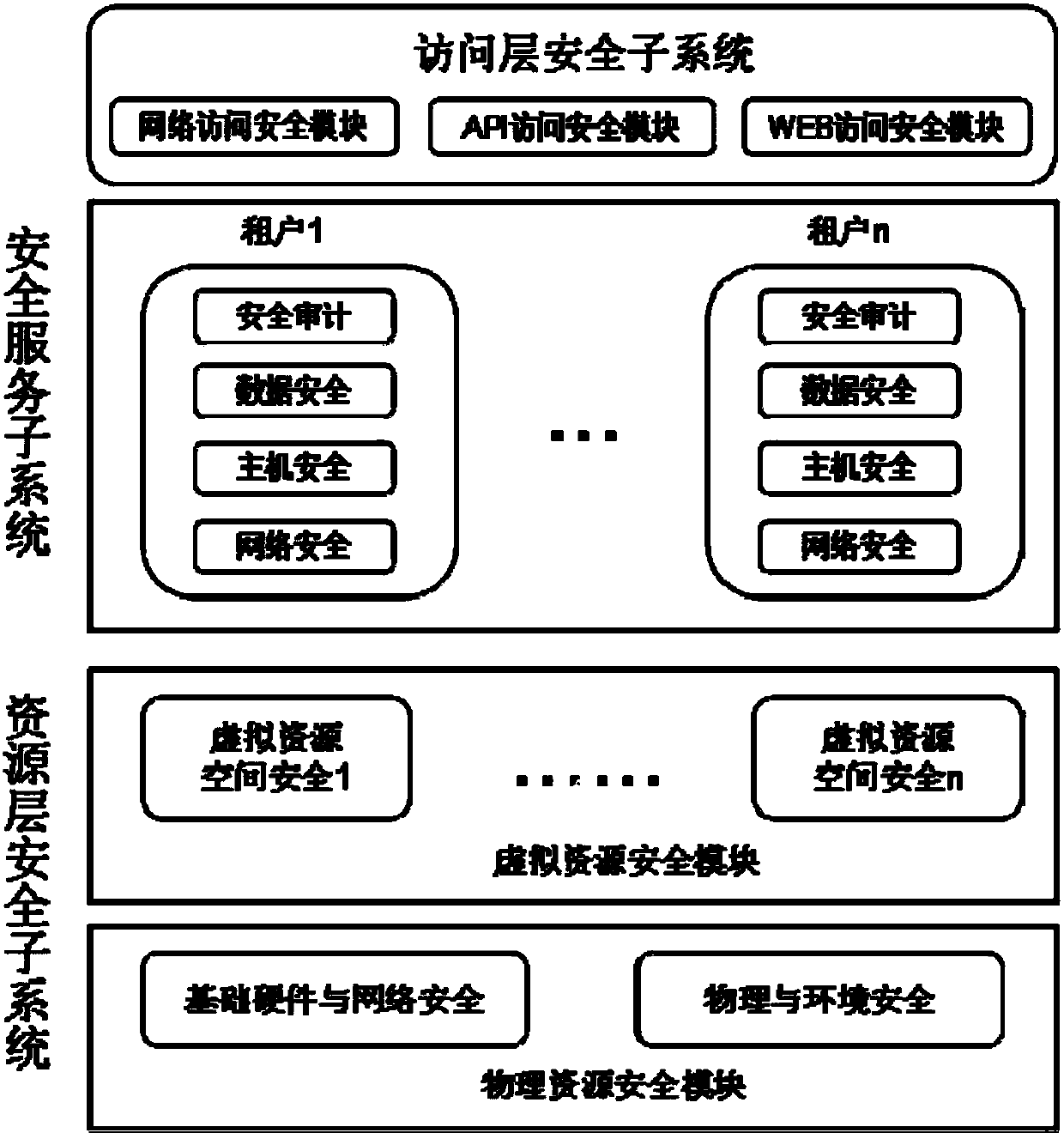
ActiveCN110233817AAchieve securitySolve security problems with poor isolationTransmissionResource securitySecurity question
The invention provides a container security system based on cloud computing, and belongs to the technical field of communication. An access layer security subsystem of the system comprises a network access security module, an API access security module and a WEB access security module. The security service subsystem comprises a host security service module, a network security service module, a data security module and an auditing module, and the resource layer security subsystem comprises a physical resource security module and a virtual resource security module. The system adopts network access security, API access security and WEB access security to realize multi-dimensional access security detection and control. Container deployment is transferred from a physical server to a virtual machine of cloud computing, so that the security problem of poor isolation of the container is solved, the influence range when the risk of the container occurs is reduced, and the security level of thecontainer is improved. Secure isolation of the container is achieved through multi-tenant isolation of cloud computing. Various security mechanisms are adopted, and the security of the container is realized by utilizing multiple tenants of cloud computing.
Owner:GUANGZHOU VCMY TECH CO LTD
Business resource security control system
InactiveCN105450660ASingle sign-on implementationDigital data authenticationTransmissionControl systemInternet privacy
The invention provides a business resource security control system, comprising a security warning device, an access control device and a log management device, wherein the security warning device is used for providing a differential level authentication way, matching or combining the authentication way according to an application level, providing corresponding security strength for corresponding business and continuously storing the corresponding security strength in a corresponding security information database; the access control device is used for controlling the permissions of resources with different categories or levels in a business procedure according to a security policy and continuously storing permission control data in the corresponding security information database; and the log management device is used for recording operations of related permissions in the system and the business procedure and continuously storing the operations in the corresponding security information database. Single sign-on of unified users is formed, a platform business norm is integrated according to the applications and the business system, the users and the permissions are uniformly managed, other mutually integrated systems are accessed online within the permission range, and single sign-on is realized.
Owner:BEIJING ANTUO SOFTWARE TECH CO LTD
Automating software security restrictions on system resources
ActiveUS8046831B2Memory loss protectionDigital data processing detailsResource securityData provider
Security components of managed computers are configured using inoculation data. Inoculation data can be retrieved from an inoculation data provider. The inoculation data provider analyzes unauthorized software applications to develop inoculation data. The inoculation data configures the security component to deny access to resources to unauthorized software applications. Inoculation data can be embedded into a script, which is distributed via a management protocol to one or more managed computers from a management computer. Resources can include files, storage paths, memory, registry keys, processor priority, services, dynamic link libraries, archives, browser cookies, and / or ActiveX controls, Java applets, or classes thereof.
Owner:ACTIANCE
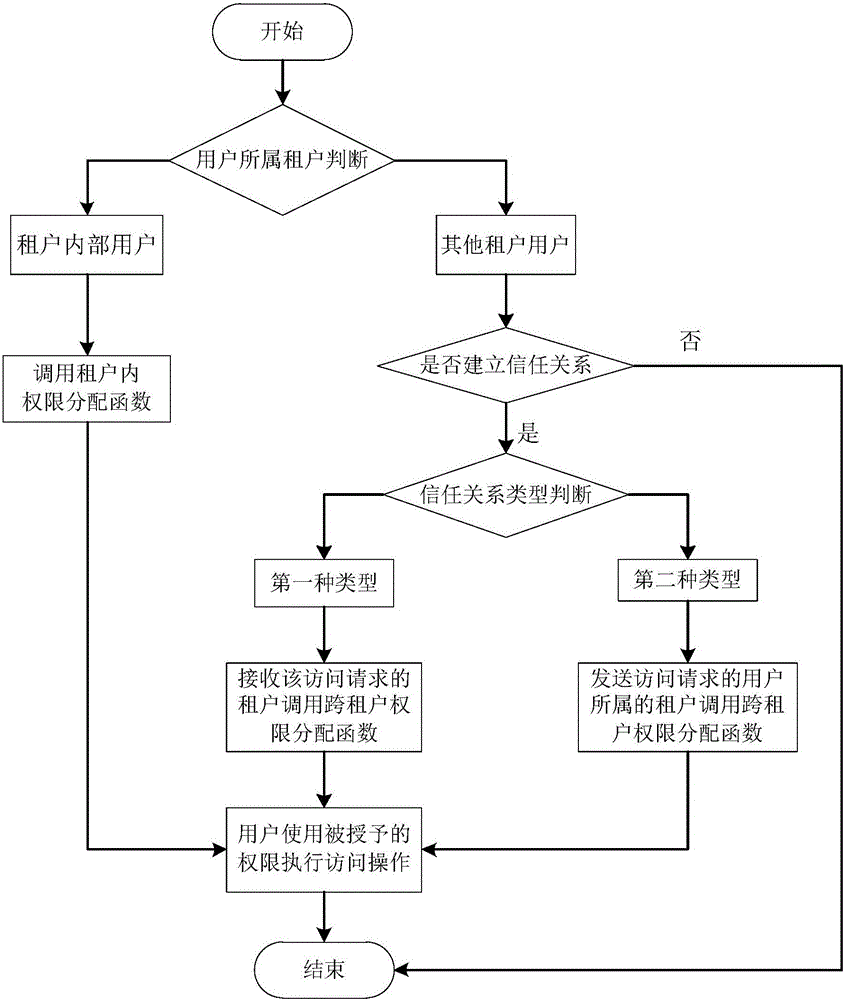
Cross-tenant access control method based on trust model in cloud environment
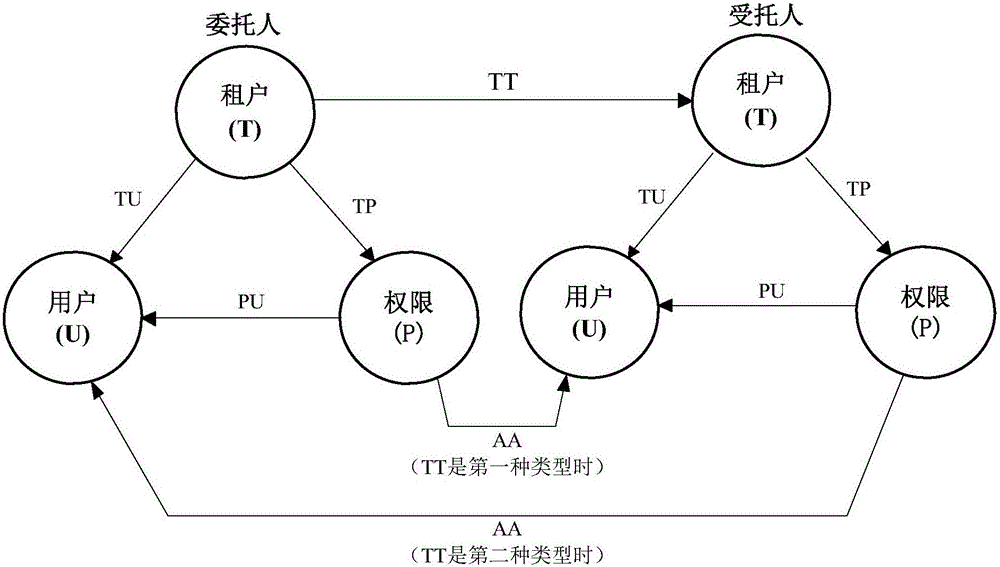
ActiveCN105871880AMeet diverse needsFix security issuesTransmissionResource securityTrust relationship
The invention discloses a cross-tenant access control method based on a trust model in a cloud environment. Based on the characteristics of a cloud computing multi-tenant architecture, a user of a tenant can have access to resources of other tenants after being authorized, so that the problems related to resource security and privacy caused during tenant cooperation are solved. By designing two types of tenant trust relationships, the tenant trust relationship concept is introduced to an access control model to reflect the access control requirement between two tenants. Through the definition of model elements and the formal description of a model function, a tenant trust model is built to adapt to the multi-tenant characteristic of cloud computing, and then cross-tenant access control is achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com