Container security system based on cloud computing
A security system and cloud computing technology, applied in the field of communication, can solve problems such as data confidentiality, integrity, usability damage, multi-tenant security threats, and difficulty in handling, so as to improve the security level, realize security isolation, and reduce the scope of influence Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
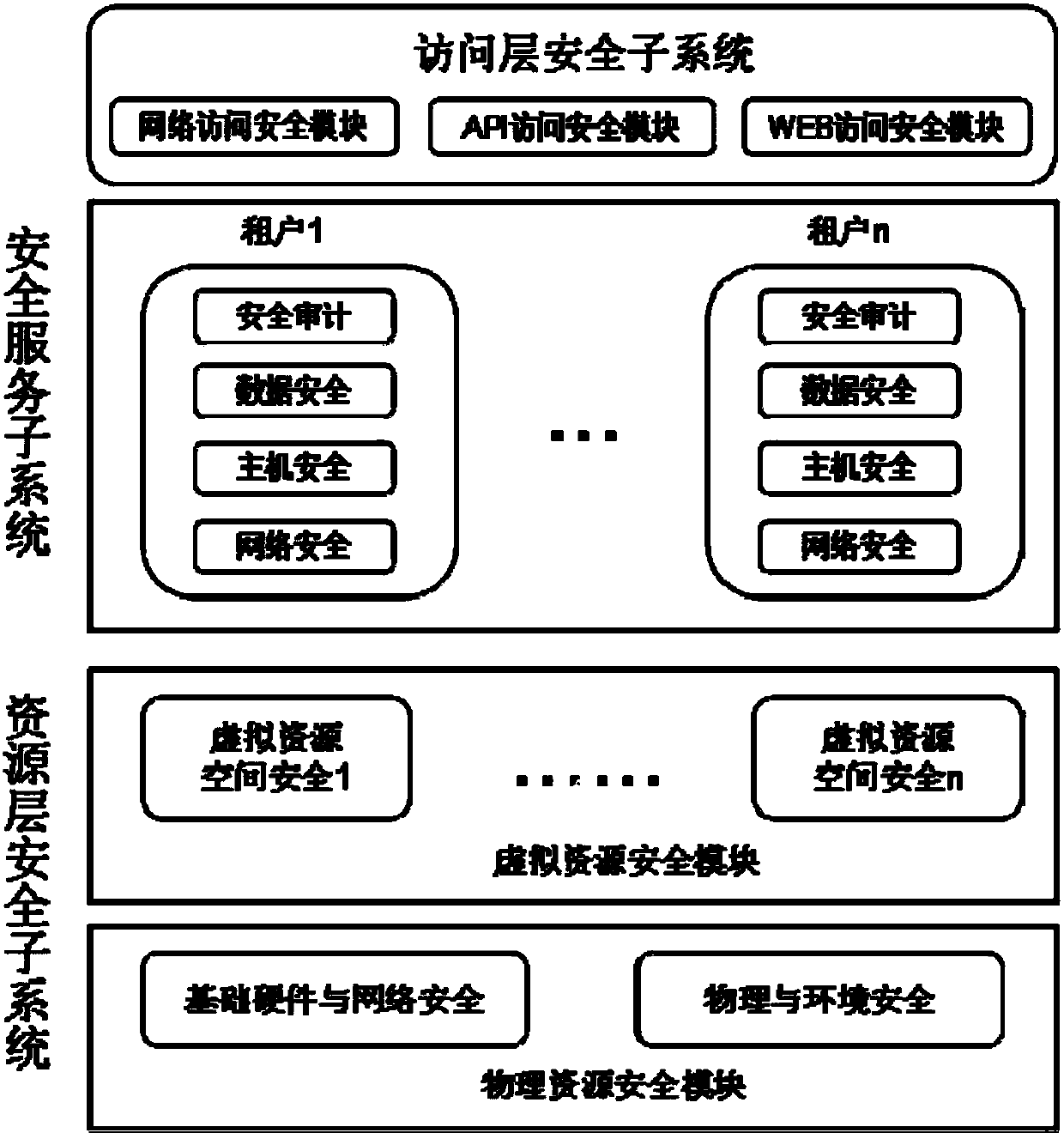
[0035] Embodiment 1 of the present invention provides a cloud computing-based container security system that utilizes cloud computing multi-tenancy, computing virtualization, storage virtualization, and network virtualization technologies to deploy containerized applications in a cloud computing environment. The container can be perfectly matched with the virtualization technology that can protect the virtual machine itself, and provide defense in depth for the host. Specifically, the implementation process of the cloud computing-based container security system provided in this embodiment depends on a cloud computing environment or an environment with a similar architecture, and provides security protection measures for container platform applications. Containerized applications are deployed in a cloud computing environment. All container applications and container resource interface APIs that provide external services are subject to the detection and control of the access layer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com