Electronic document safety distribution controlling method based on task stream
A technology of safe distribution and workflow, applied in data processing applications, instruments, computing, etc., can solve the problems of unauthorized use of information without strict control of sensitive information, lack of digital content rights management, enterprise losses, etc., to achieve high security, The effect of preventing leakage and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0017] Example 1 The user of the client is a system analyst
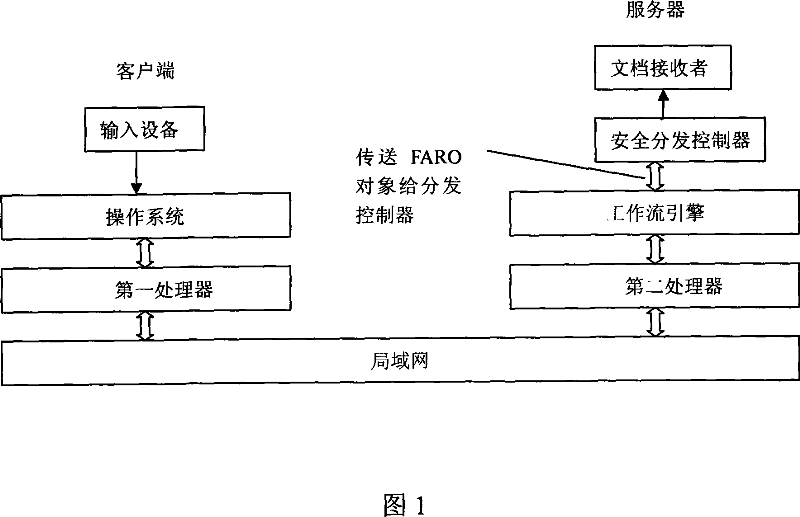
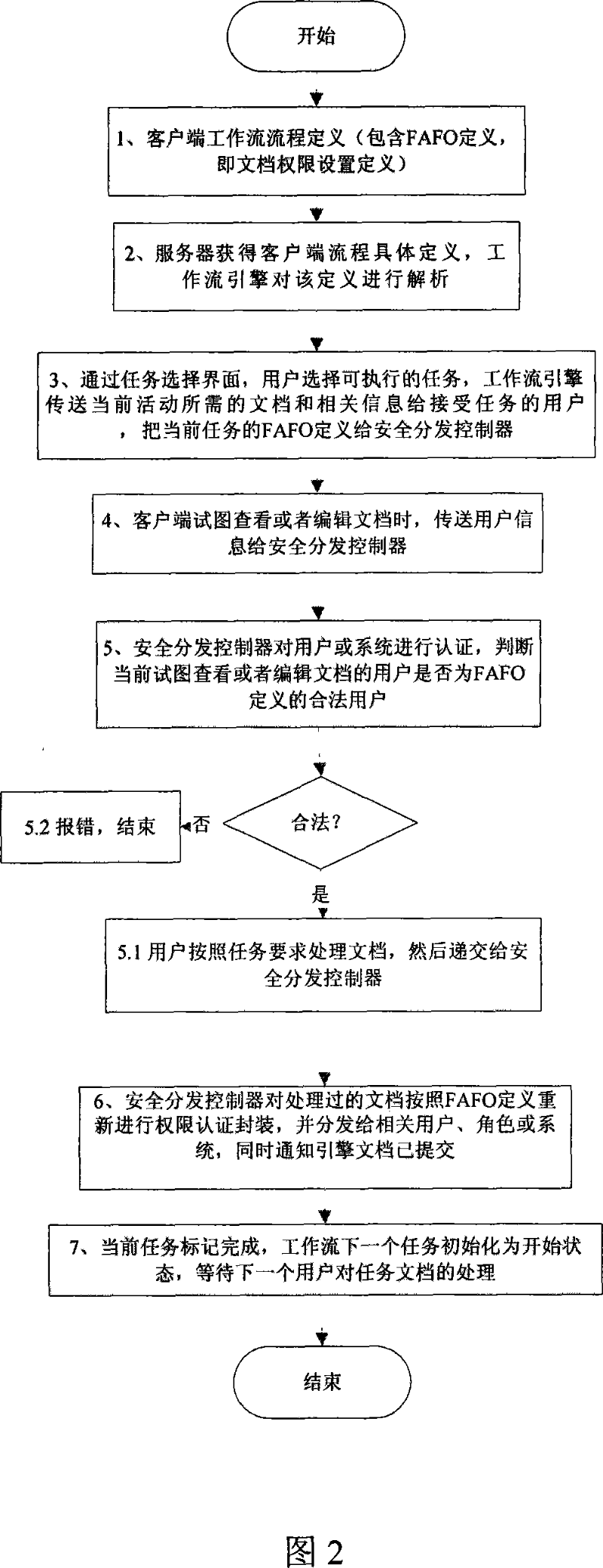
[0018] The method of this embodiment requires a workflow-based electronic document resource security distribution control system composed of an input device, an operating system, a first processor, a local area network, a second processor, a workflow engine, a security distribution controller and an output device In the implementation, the input device is a keyboard, the operating system is a commonly used Windows XP desktop system, the first processor and the second processor are PC terminal devices with computing capabilities, and the workflow engine is able to analyze the workflow definition and execute the work. Flow management system, input device, operating system and the first processor constitute the client, the second processor, workflow engine, security distribution controller and output device constitute the server, the client is connected to the server through the local area network, its characteristics ...
Embodiment 2
[0026] Embodiment 2 The user of the client is a software designer
[0027] Except for the following differences, the remaining parts are identical to Example 1.
[0028] In the third step and the fourth step, the user logs in to the system and tries to open the downloaded "needs analysis document". In the fifth step, the secure distribution controller authenticates the user information, and judges that the "software designer" is indeed a legitimate user, and the user can only perform the operation of "viewing" the document, and cannot Perform other permissions on the document, such as "modify", "print", "comment" or "copy", so as to effectively prevent the leakage of information during the workflow process and ensure that this document is within the process security.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com