Authentication identification method, electronic device, and computer-readable storage medium
A technology of identity verification and identification method, applied in the field of blockchain, can solve the problems of poor controllability and generality, and achieve the effect of improving generality, security reliability, and controllability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0060] The identity verification and identification method provided by the present invention will be described below in conjunction with the accompanying drawings.
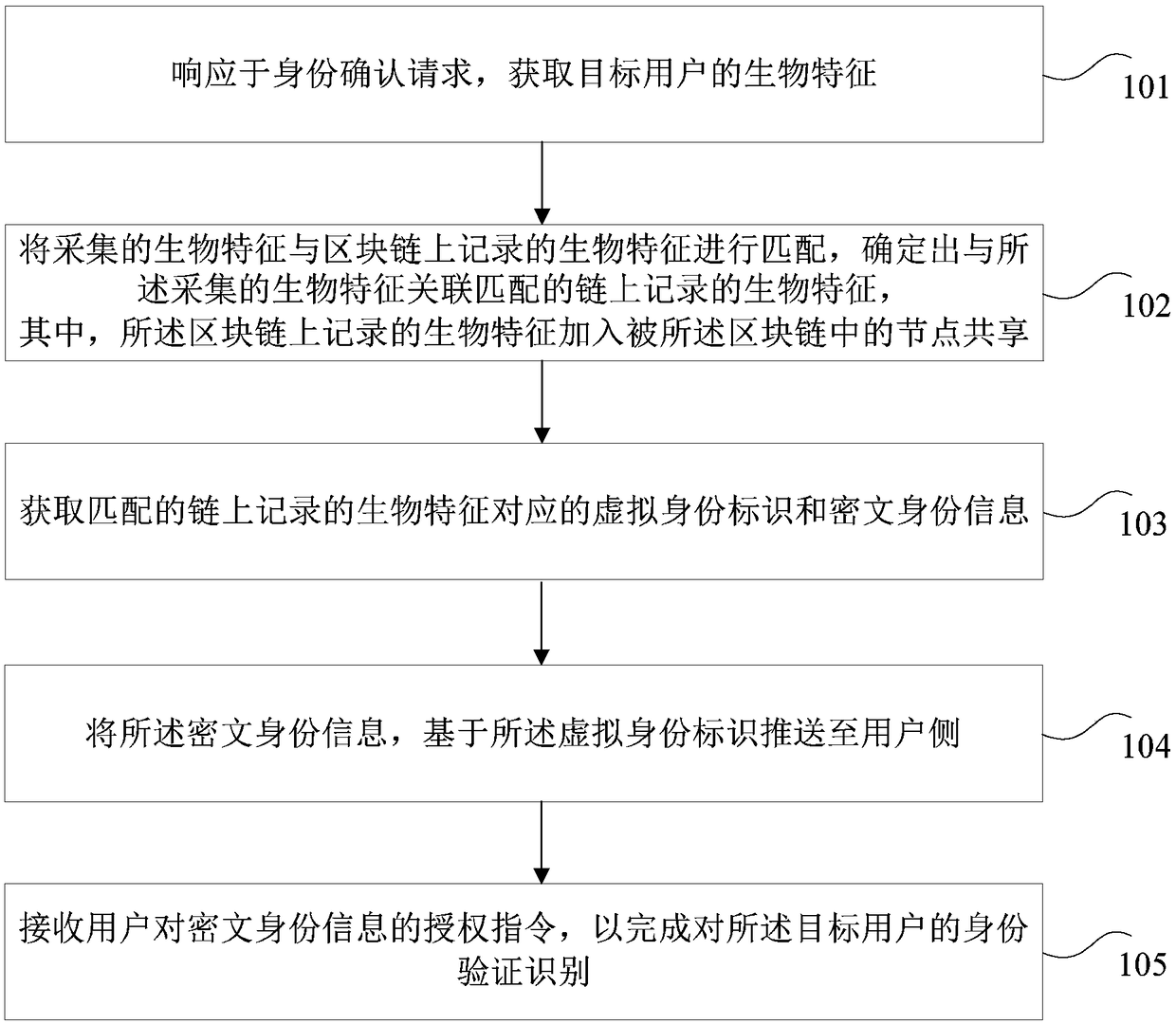
[0061] figure 1 It is an optional schematic flow chart of the identity verification and identification method of the present invention, such as figure 1 As shown, the method may include the following steps:
[0062] Step 101: Obtain the biological characteristics of the target user in response to the identity confirmation request;
[0063] That is, when the user uses the system for feature recognition through the front-end device integrated with SDK, the system can collect the user's biometric features through the front-end, and use them to perform algorithmic matching with the biometric features recorded on the chain, and find the identity and password corresponding to the biometric features. text identity information.
[0064] Step 102: Match the collected biometrics with the biometrics recorded on the blockc...
Embodiment 2
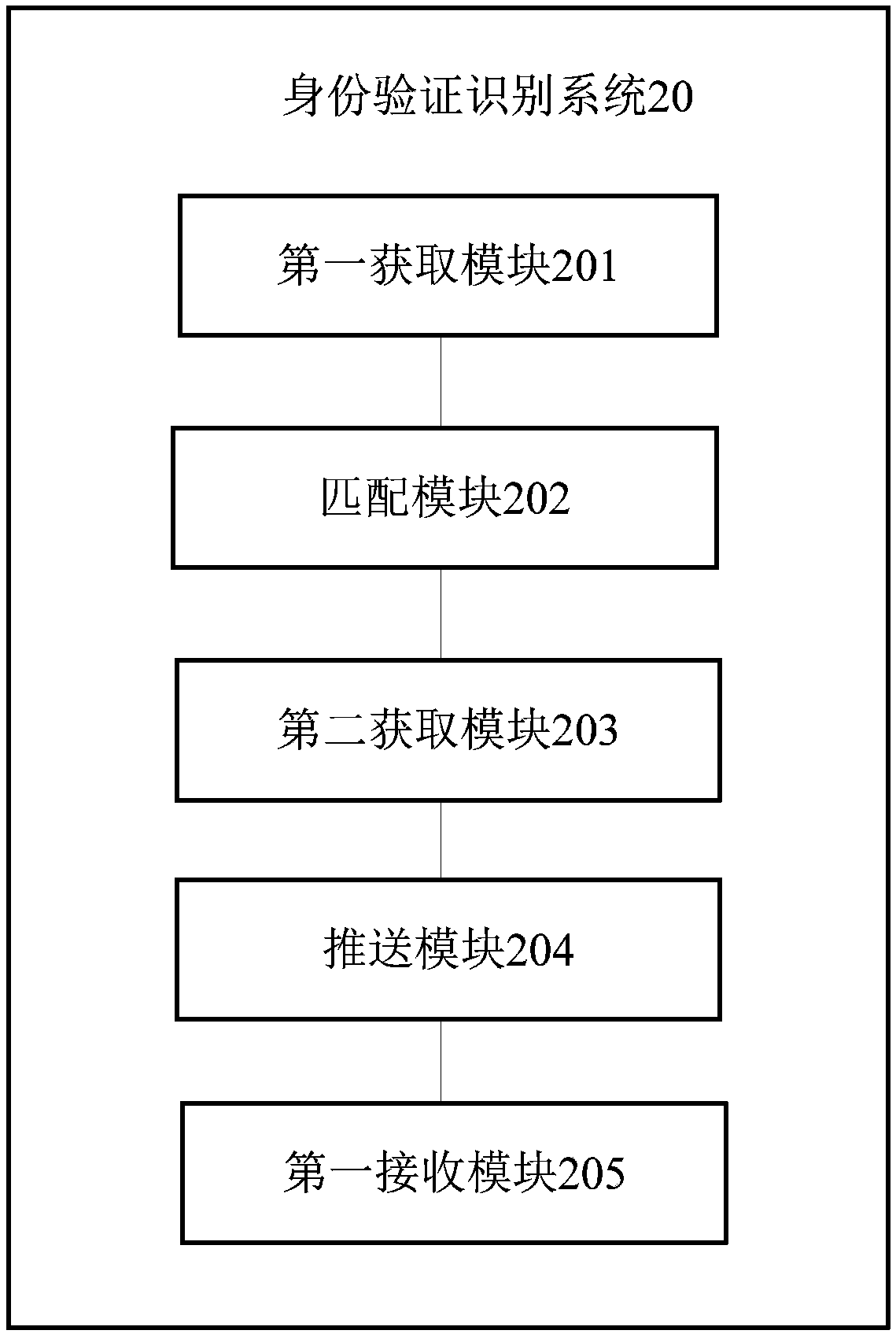
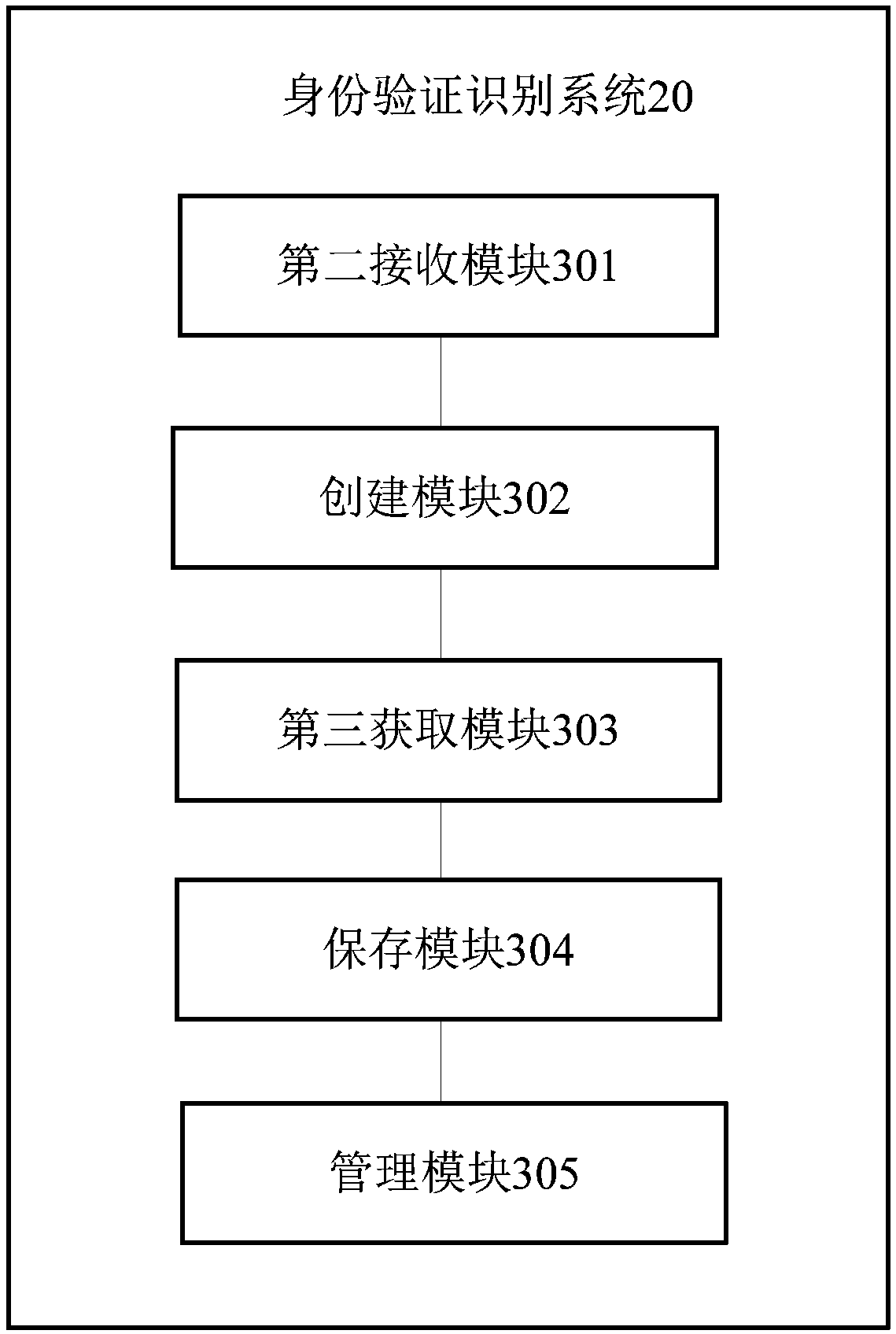
[0103] Based on the identity verification and recognition method provided in the first embodiment above, this embodiment provides an identity verification and recognition system, specifically, figure 2 and image 3 An optional structural block diagram of the identity verification and recognition system is shown, the identity verification and recognition system is divided into one or more program modules, one or more program modules are stored in a storage medium, and processed by one or more implemented by the device to complete the present invention. The program module referred to in the present invention refers to a series of computer program instruction segments capable of completing specific functions, which is more suitable than the program itself to describe the execution process of the identity verification and identification system in the storage medium. The following description will specifically introduce each program module of this embodiment The function:
[010...
Embodiment 3
[0117] An electronic device is provided in the third preferred embodiment of the present invention. Figure 4 It is a schematic diagram of the hardware architecture of an embodiment of the electronic device according to the present invention. In this embodiment, the electronic device 2 is a device capable of automatically performing numerical calculation and / or information processing according to preset or stored instructions. For example, it may be a smart phone, a tablet computer, a notebook computer, a desktop computer, a rack server, a blade server, a tower server, or a cabinet server (including an independent server, or a server cluster composed of multiple servers), etc. As shown in the figure, the electronic device 2 at least includes but is not limited to: a memory 21 , a processor 22 , a network interface 23 , and an identity verification system 20 that can communicate with each other via a system bus. in:
[0118] Memory 21 includes at least one type of computer-re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com