Personnel security management system and method in mining areas
A technology for personnel safety and mining area, which is applied in the field of mining area personnel safety management system, can solve the problems of adding non-safety factors in mining area production, wasting manpower and material resources, and difficult to identify illegal personnel in mining area personnel, achieving fine user authority auditing and facilitating remote monitoring , Conducive to the effect of safe production
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
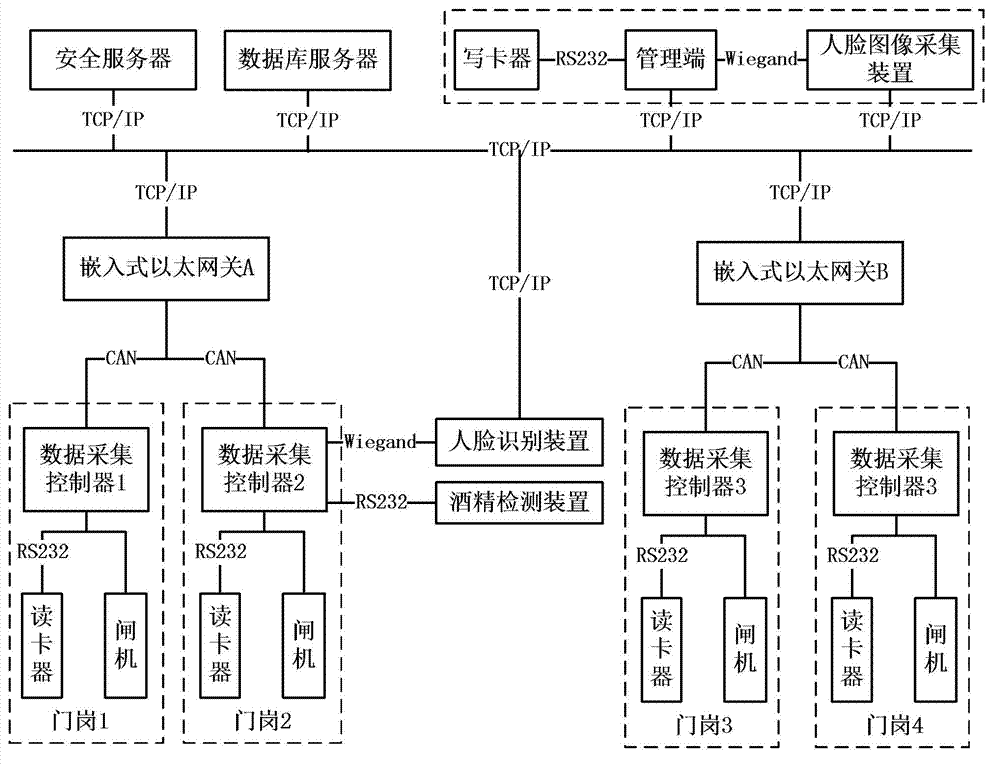
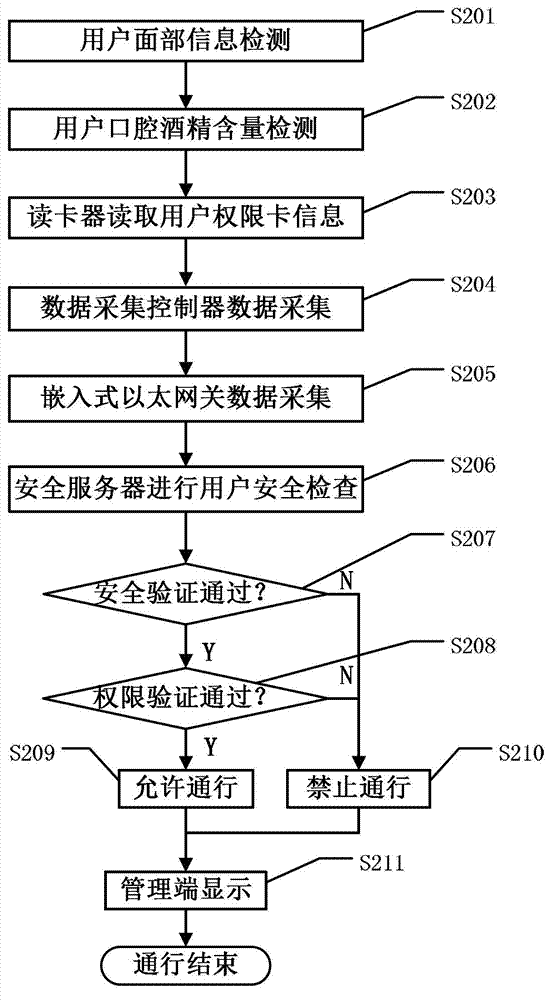
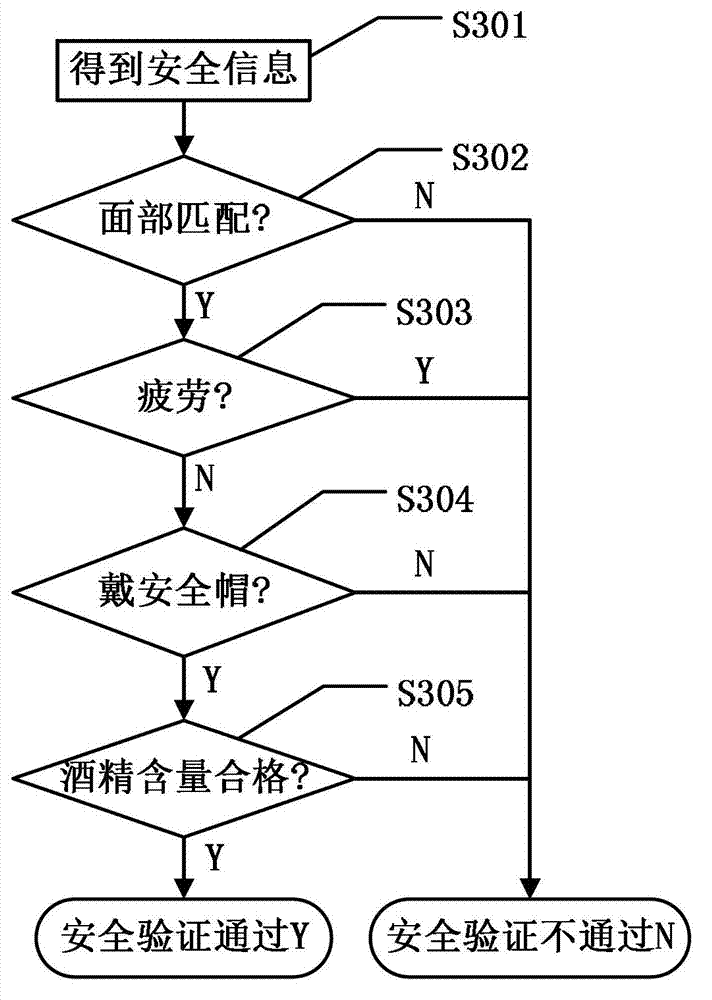
[0116] The administrator of the mining area assigns permissions to the user "Zhang San" through the management terminal: "Zhang San" belongs to the "common group", and the personal permission information of "Zhang San" does not have the access permission of Gate 2 at any time, but the "common group" Users can pass Gate 2 in the mining area from 8:00 to 10:00 on October 1, 2012. The management terminal stores the authority into the database server, issues the authority card through the card reader according to the authority sign in the database server, and encodes the personnel information corresponding to the authority information and writes it into the authority card. The management end uses the face recognition device to collect the facial image information of "Zhang San", and sends it to the face recognition device of Gate 2 through Ethernet. "Zhang San" will pass Gate 2 at 8:30 on October 1, 2012. At this time, he did not drink alcohol, wear a safety helmet as required, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com