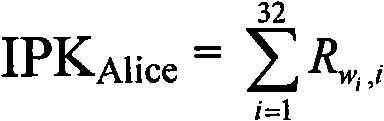Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
73 results about "Anonymous identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
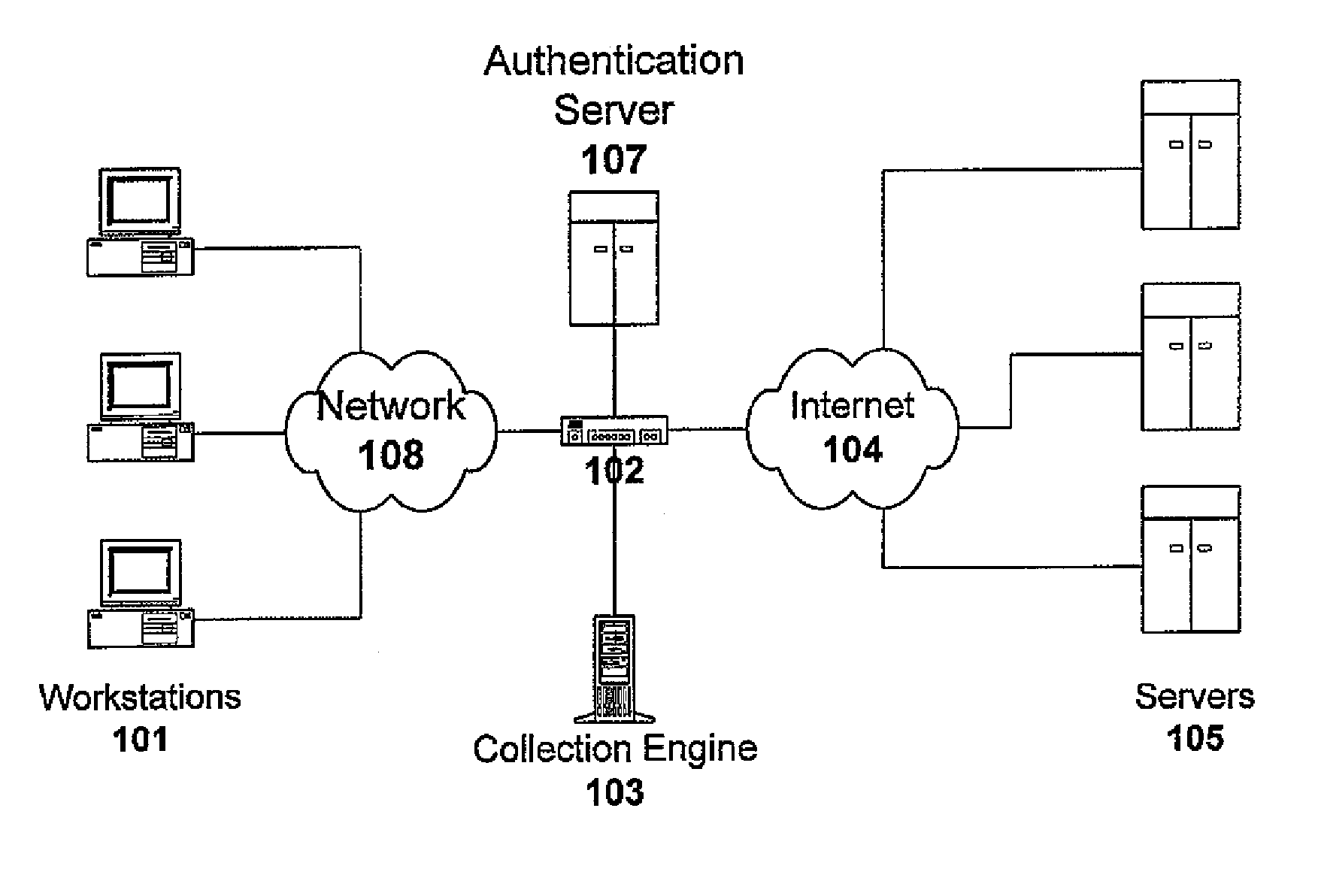
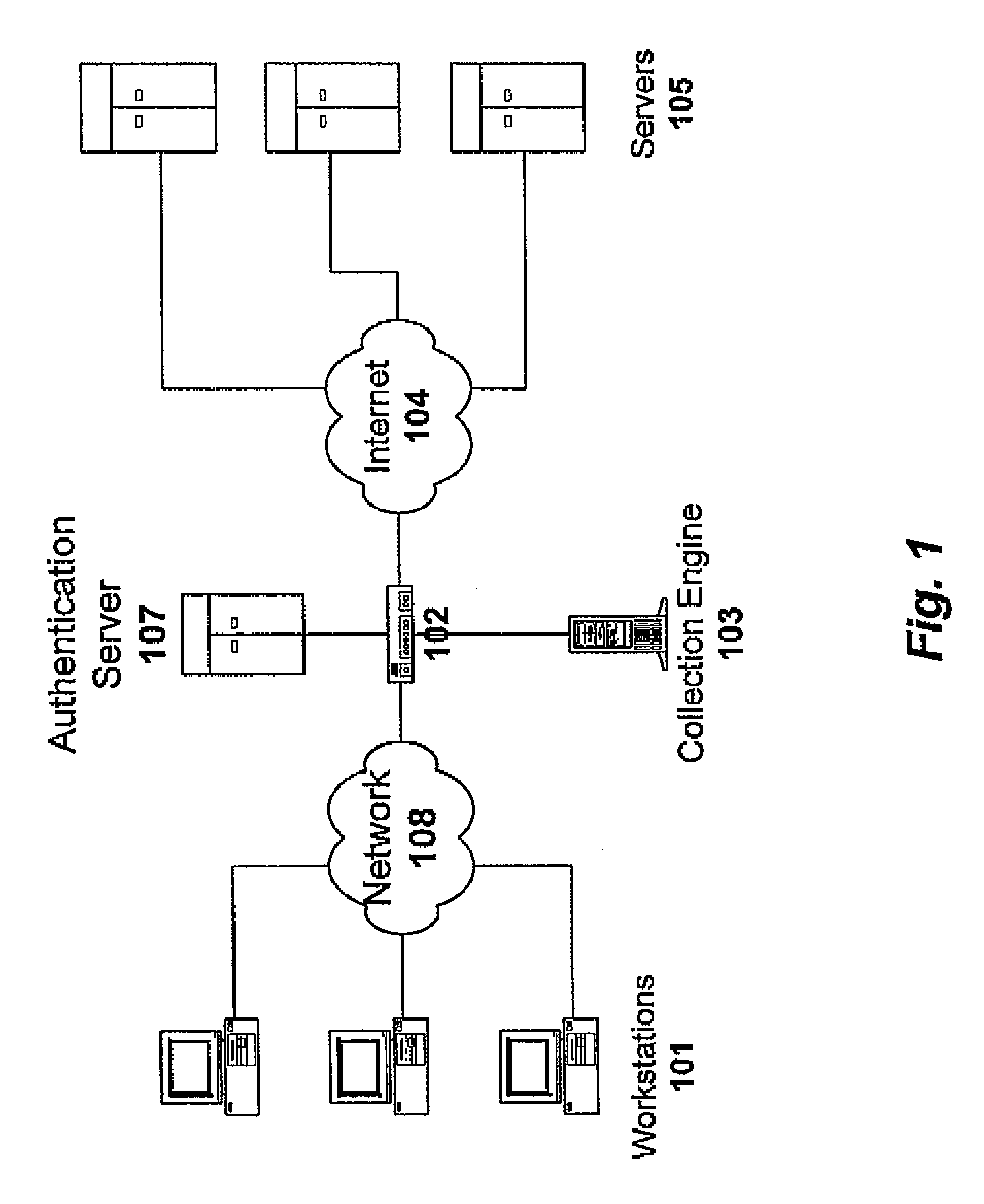
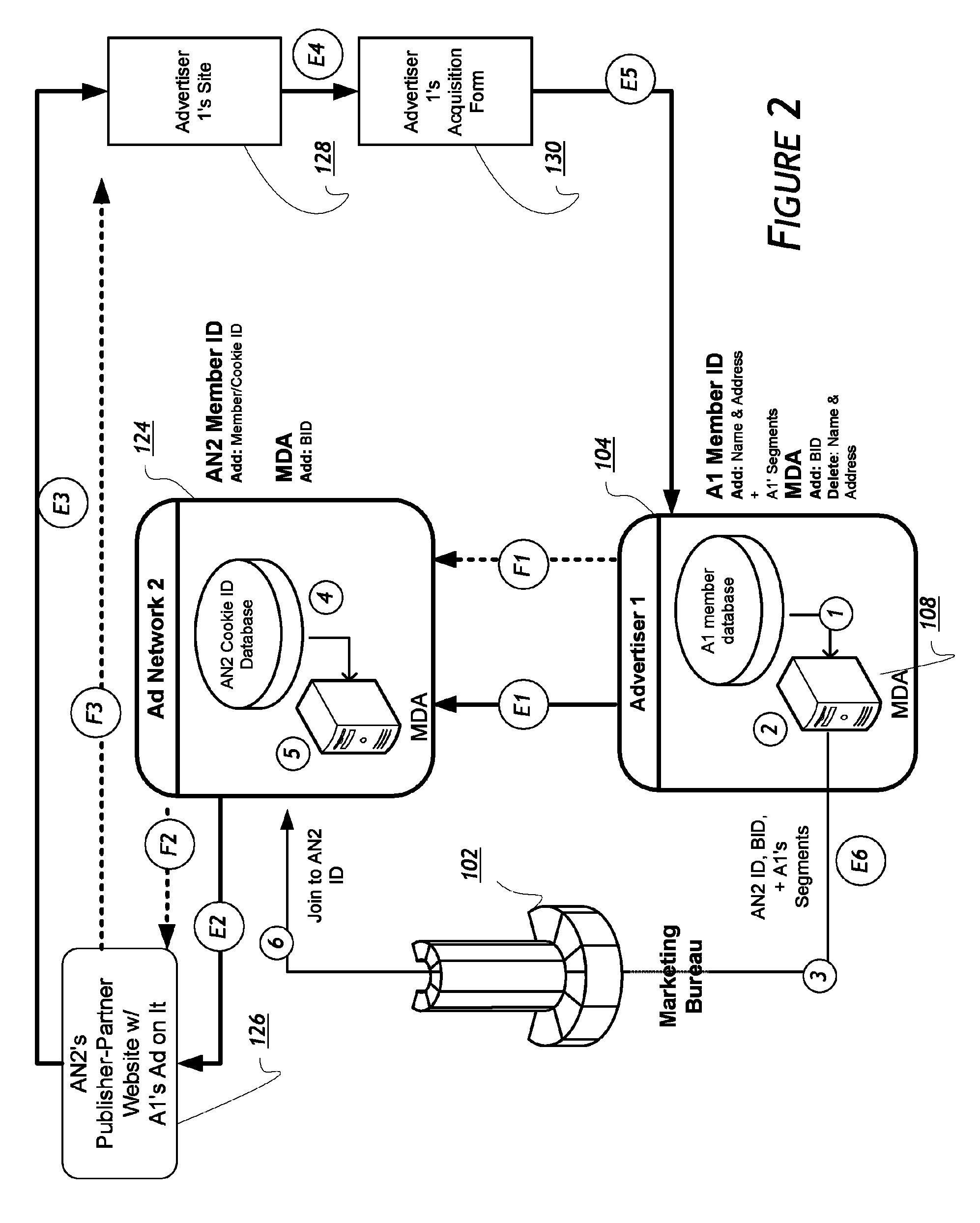
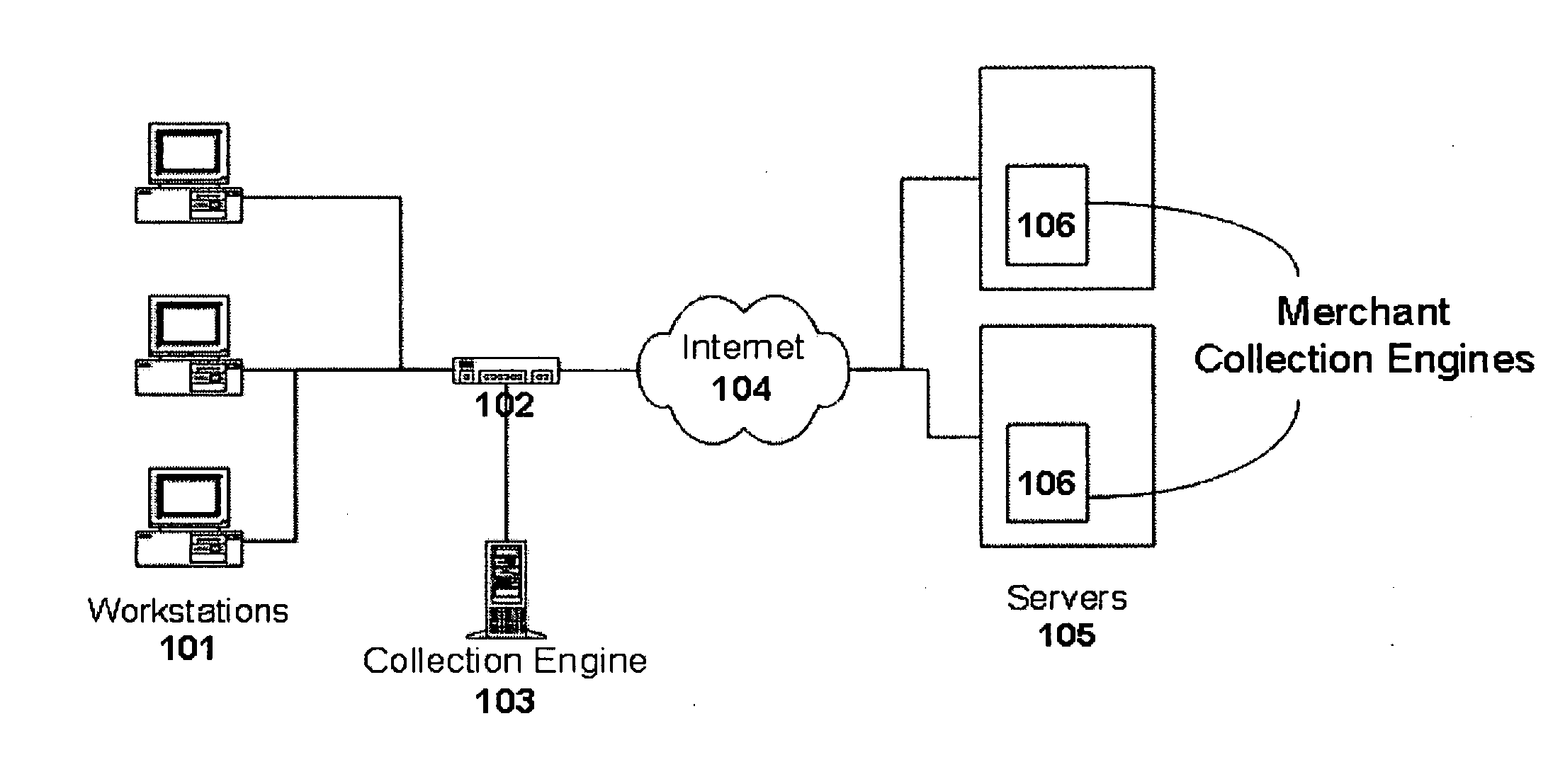
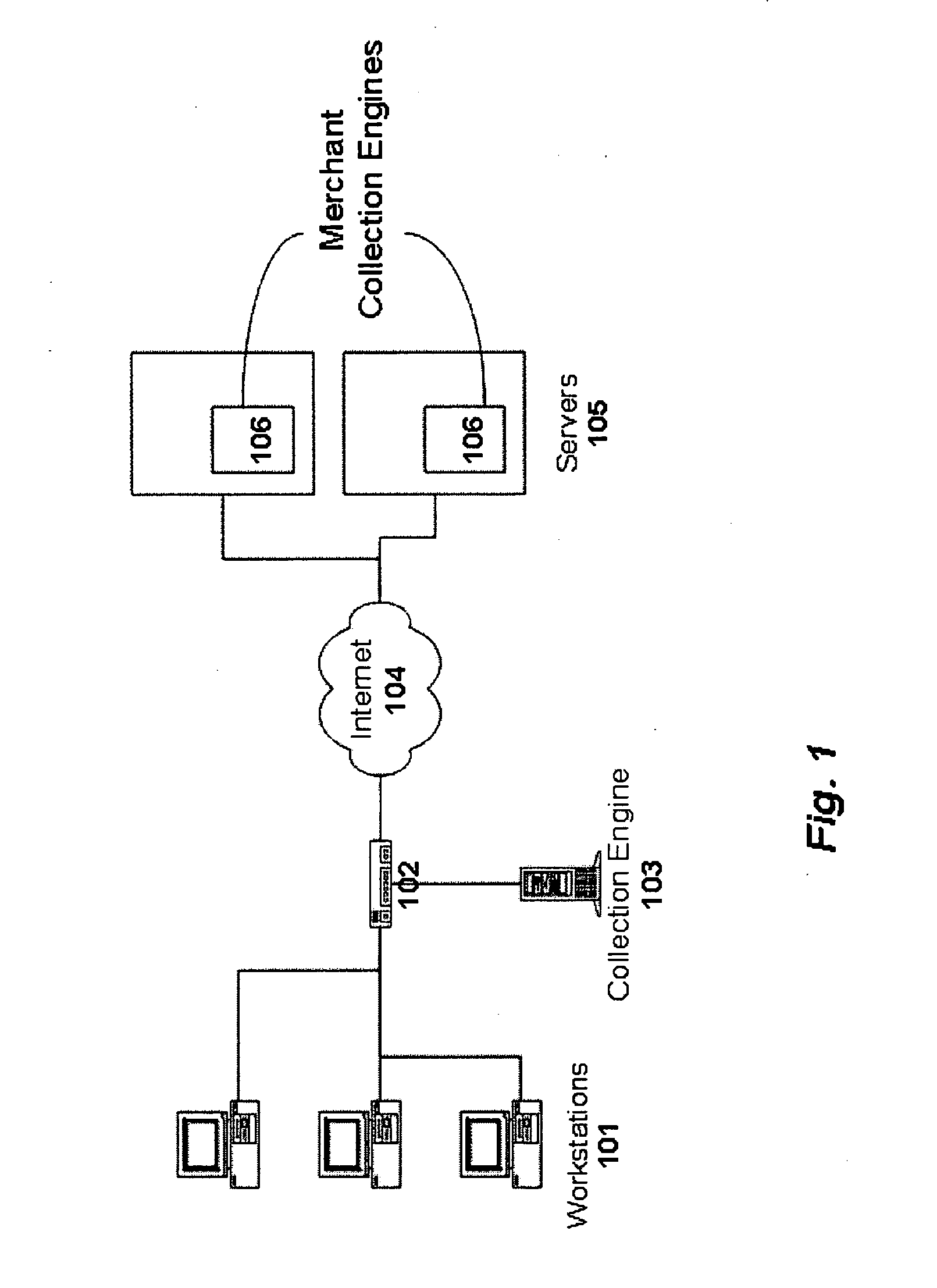
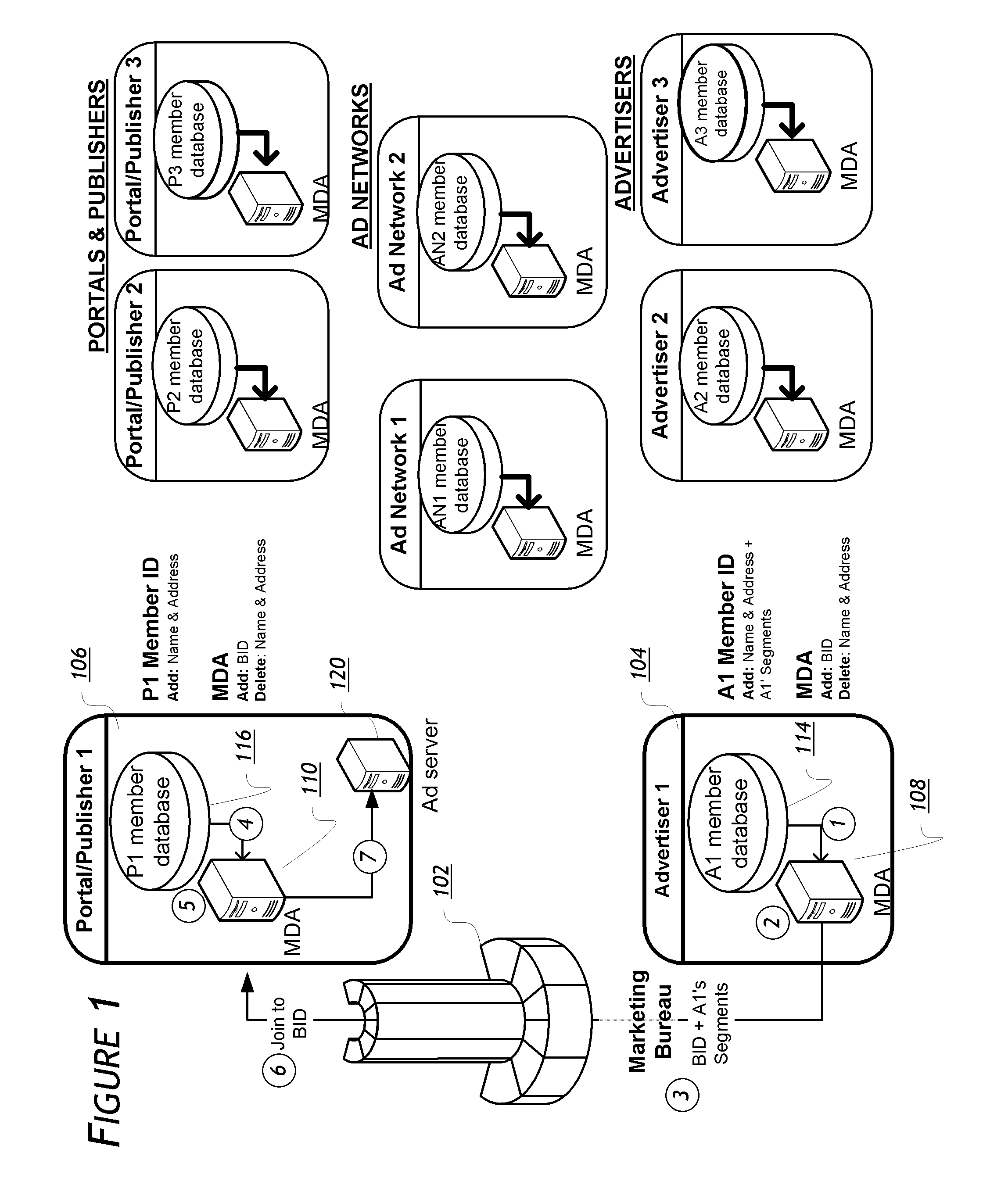
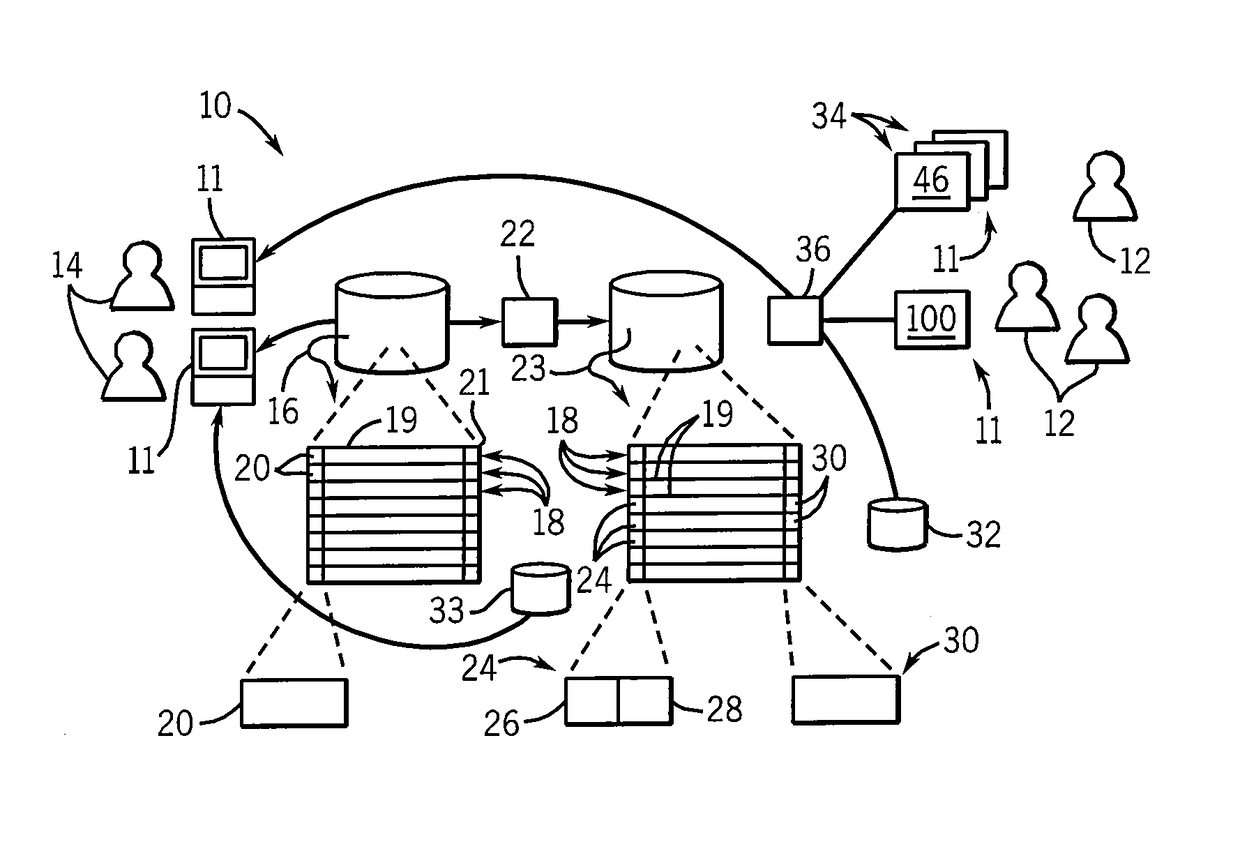
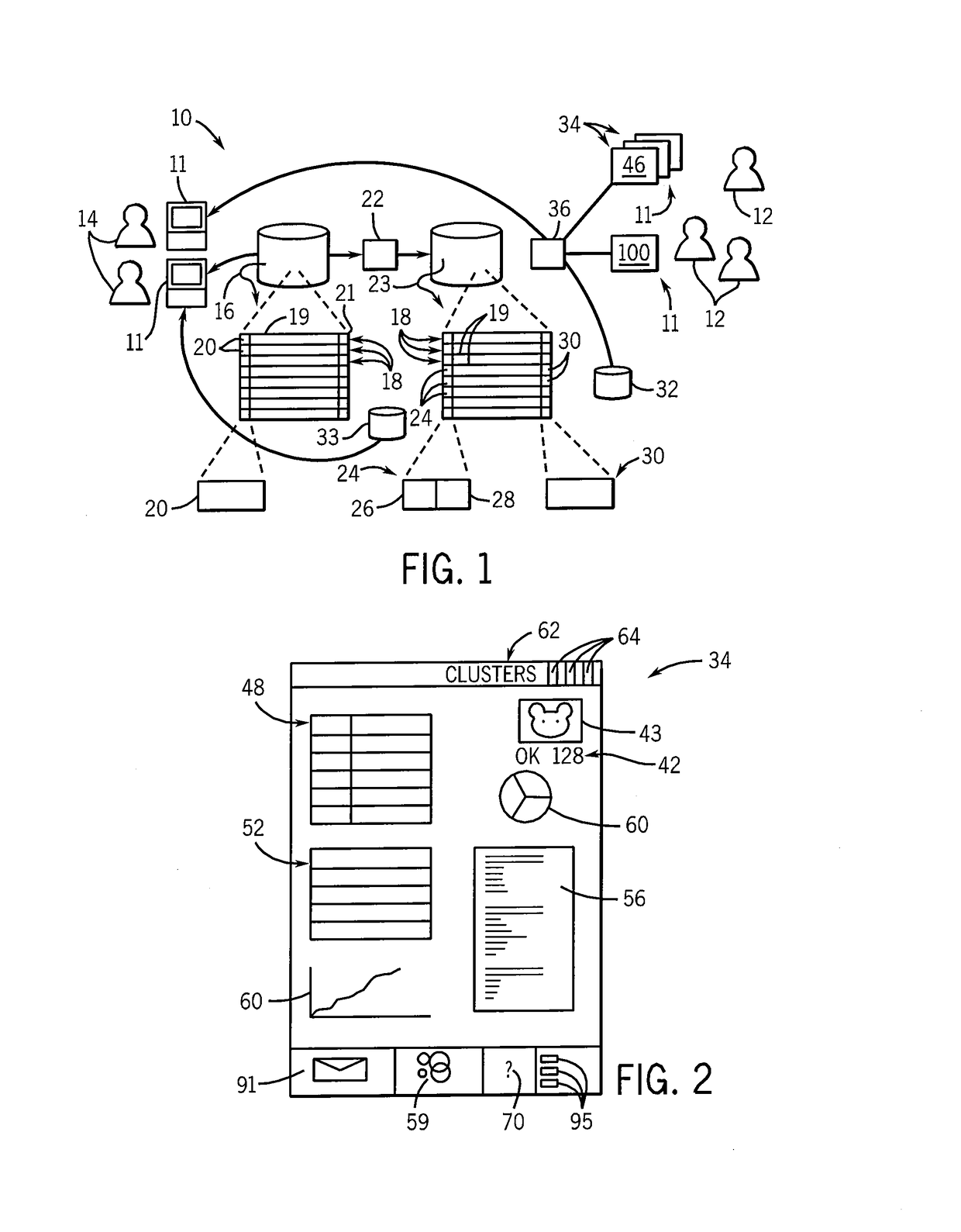
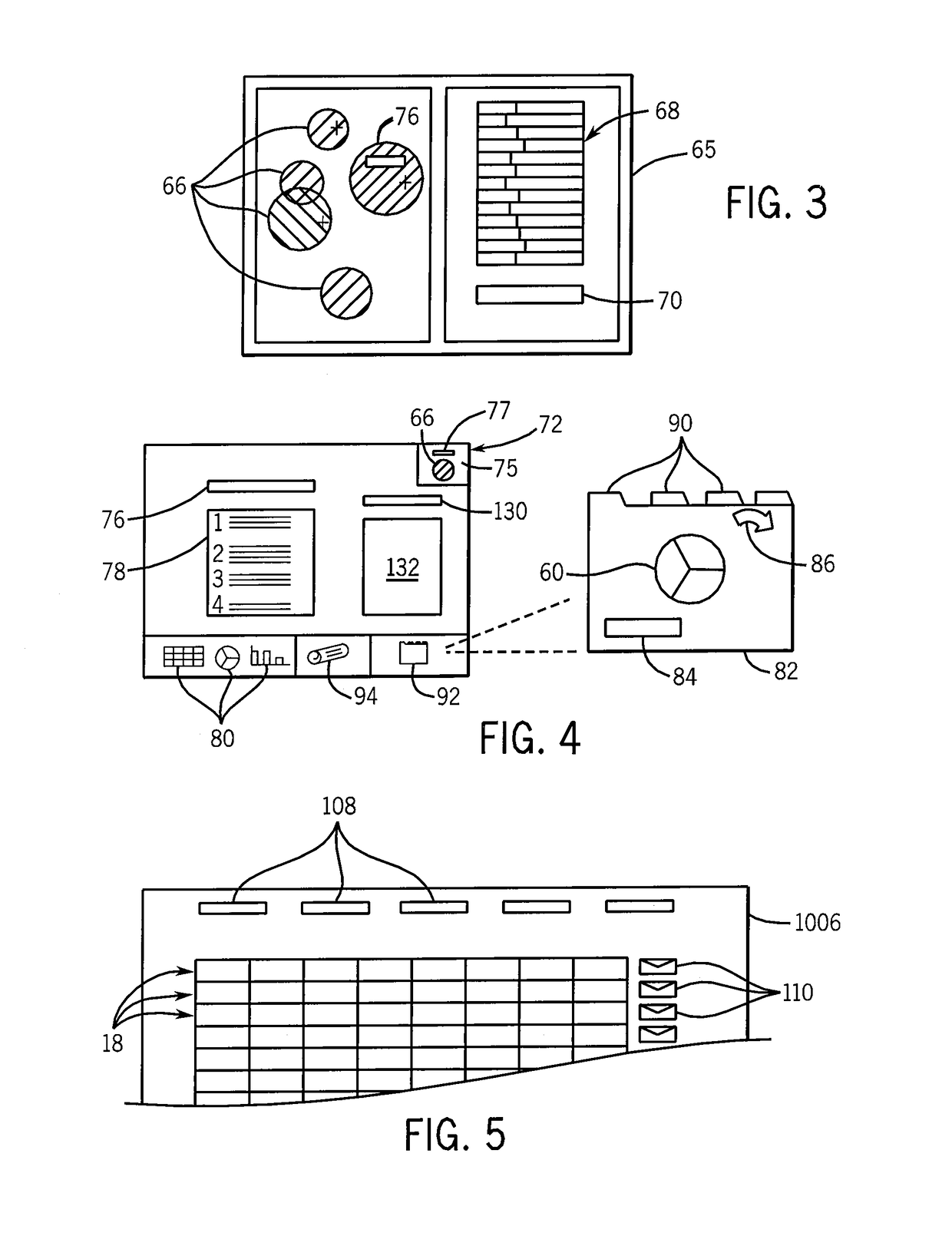
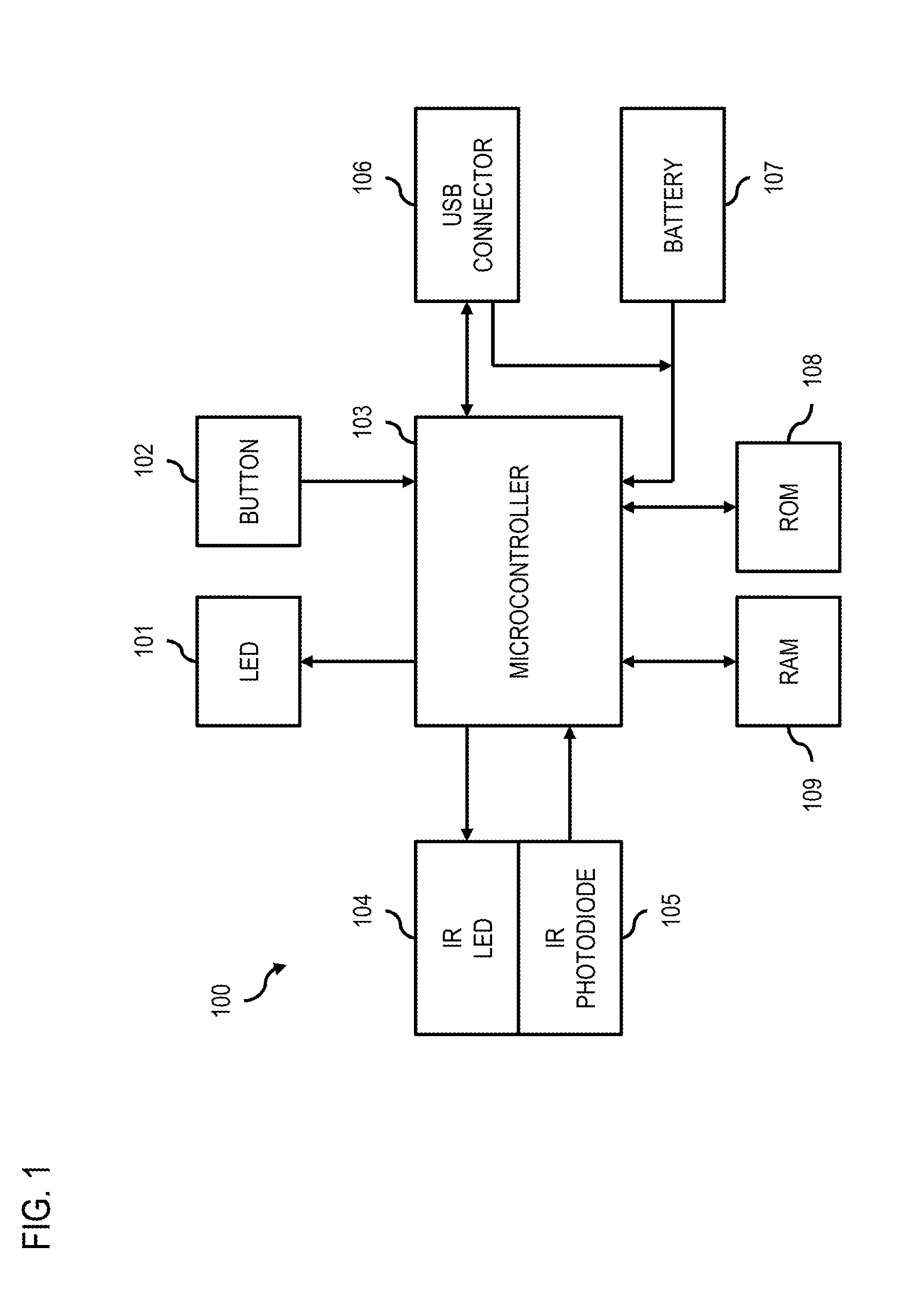
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
InactiveUS6983379B1Amount of timeHardware monitoringComputer security arrangementsInternet privacyTransaction data
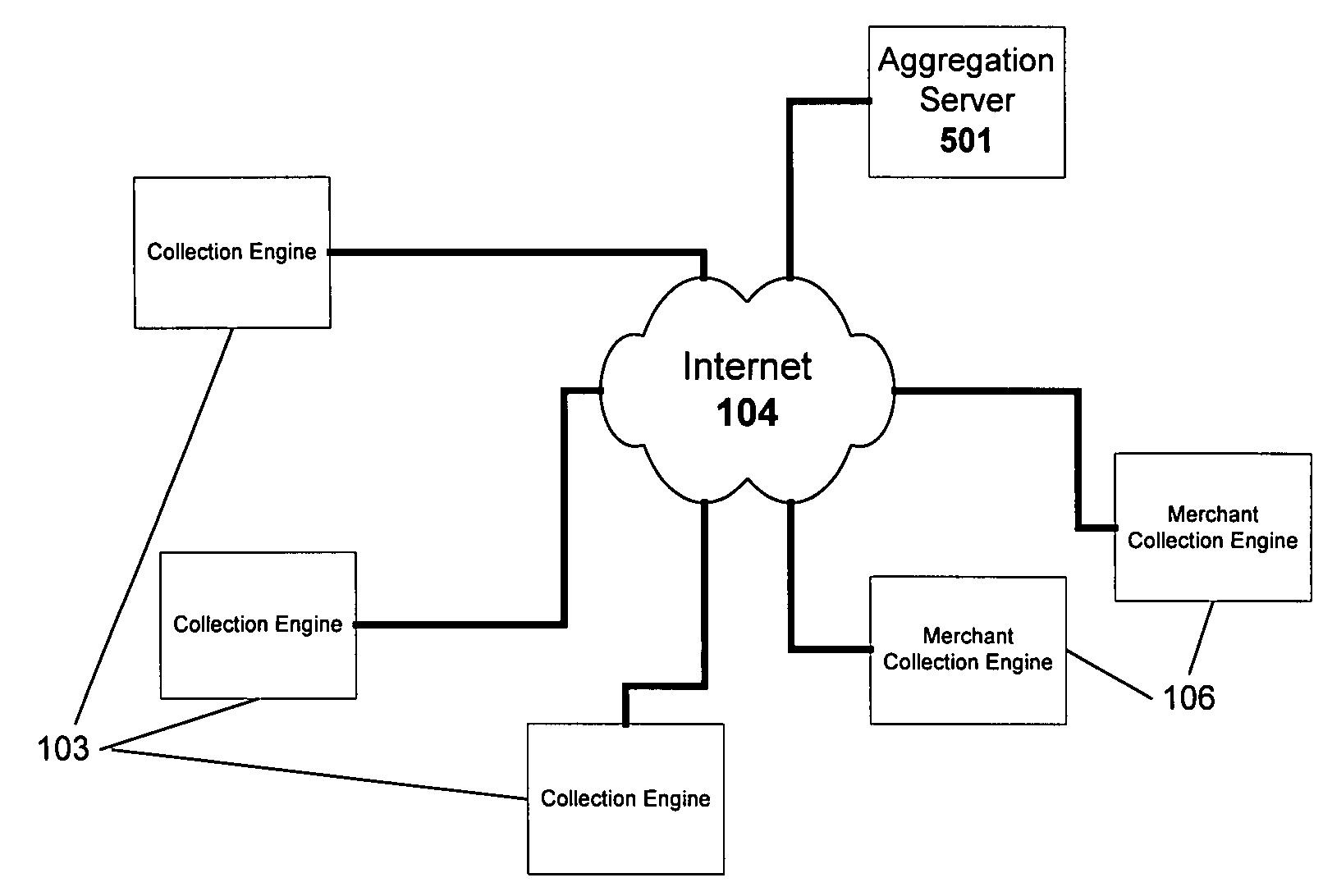
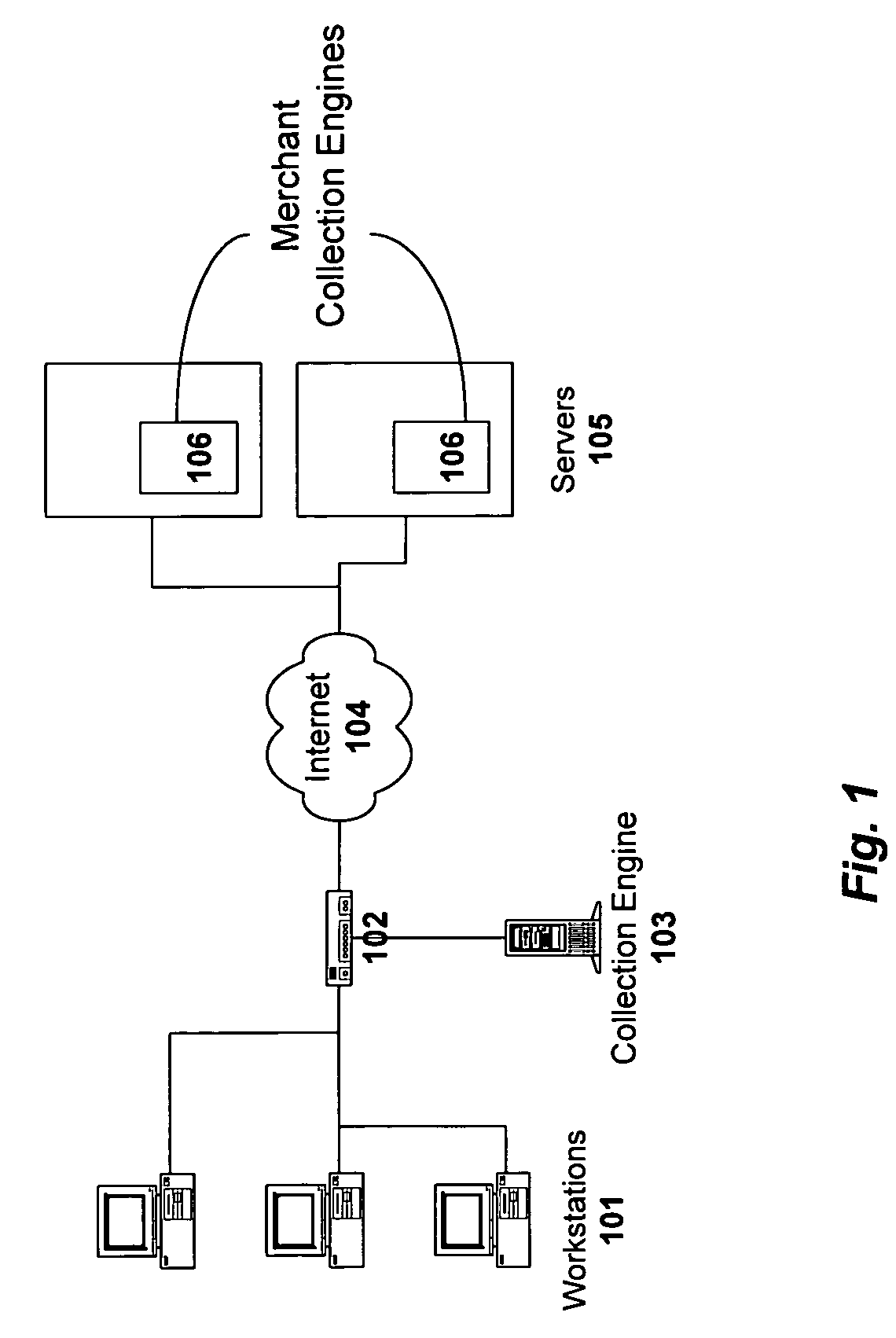
A method and system for monitoring users on one or more computer networks, disassociating personally identifiable information from the collected data, and storing it in a database so that the privacy of the users is protected. The system includes monitoring transactions at both a client and at a server, collecting network transaction data, and aggregating the data collected at the client and at the server. The system receives a user identifier and uses it to create an anonymized identifier. The anonymized identifier is then associated with one or more users' computer network transactions. The data is stored by a collection engine and then aggregated to a central database server across a computer network.
Owner:PLURIMUS CORP +1
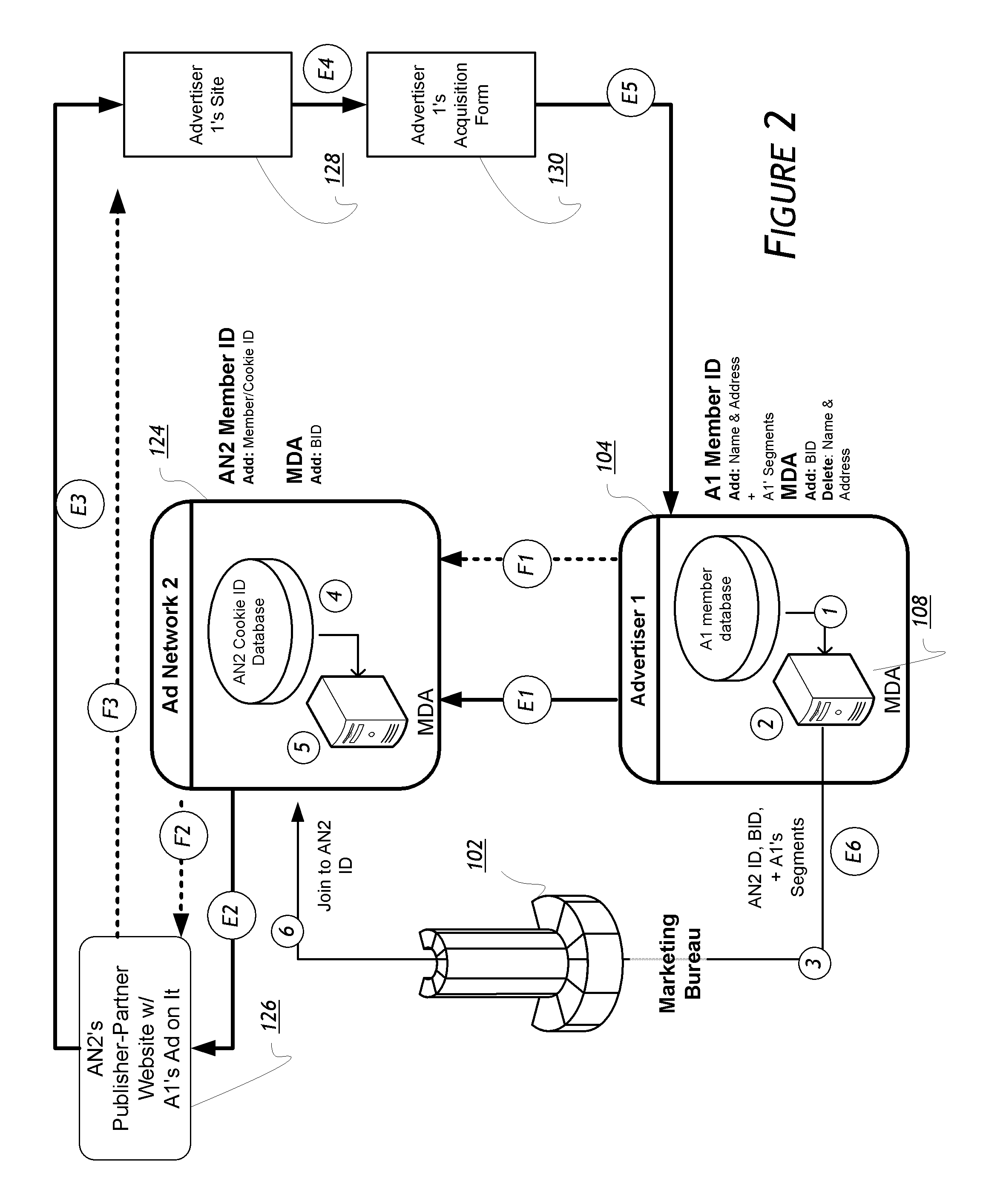
Real-Time Frame Authentication Using ID Anonymization In Automotive Networks
ActiveUS20150089236A1Reduce message authentication delay tmReduce delaysKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkData integrity
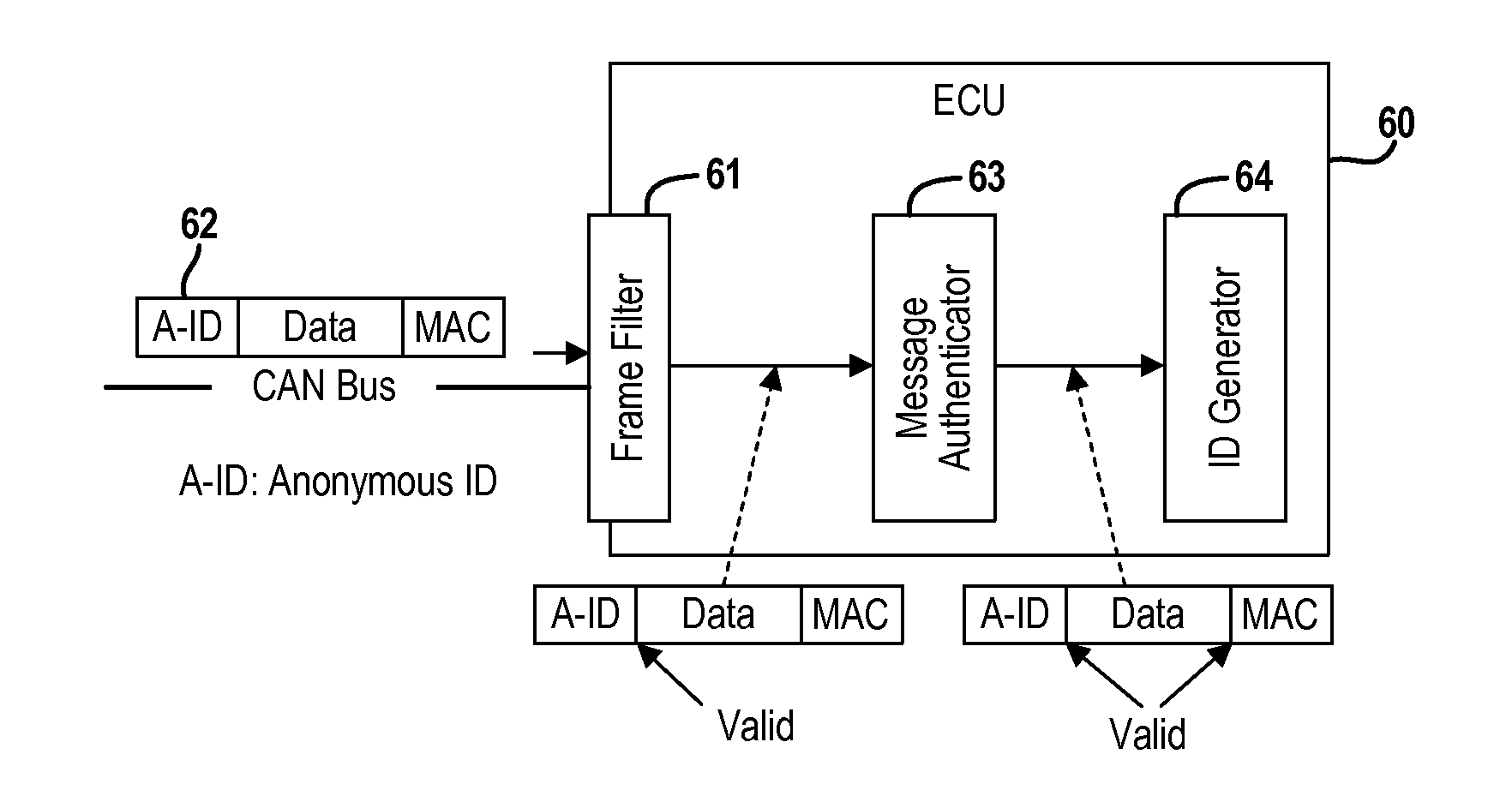
A real-time frame authentication protocol is presented for in-vehicle networks. A frame identifier is made anonymous to unauthorized entities but identifiable by the authorized entities. Anonymous identifiers are generated on a per-frame basis and embedded into each data frame transmitted by a sending ECU. Receiving ECUs use the anonymous identifiers to filter incoming data frames before verifying data integrity. Invalid data frame are filtered without requiring any additional run-time computations.
Owner:RGT UNIV OF MICHIGAN
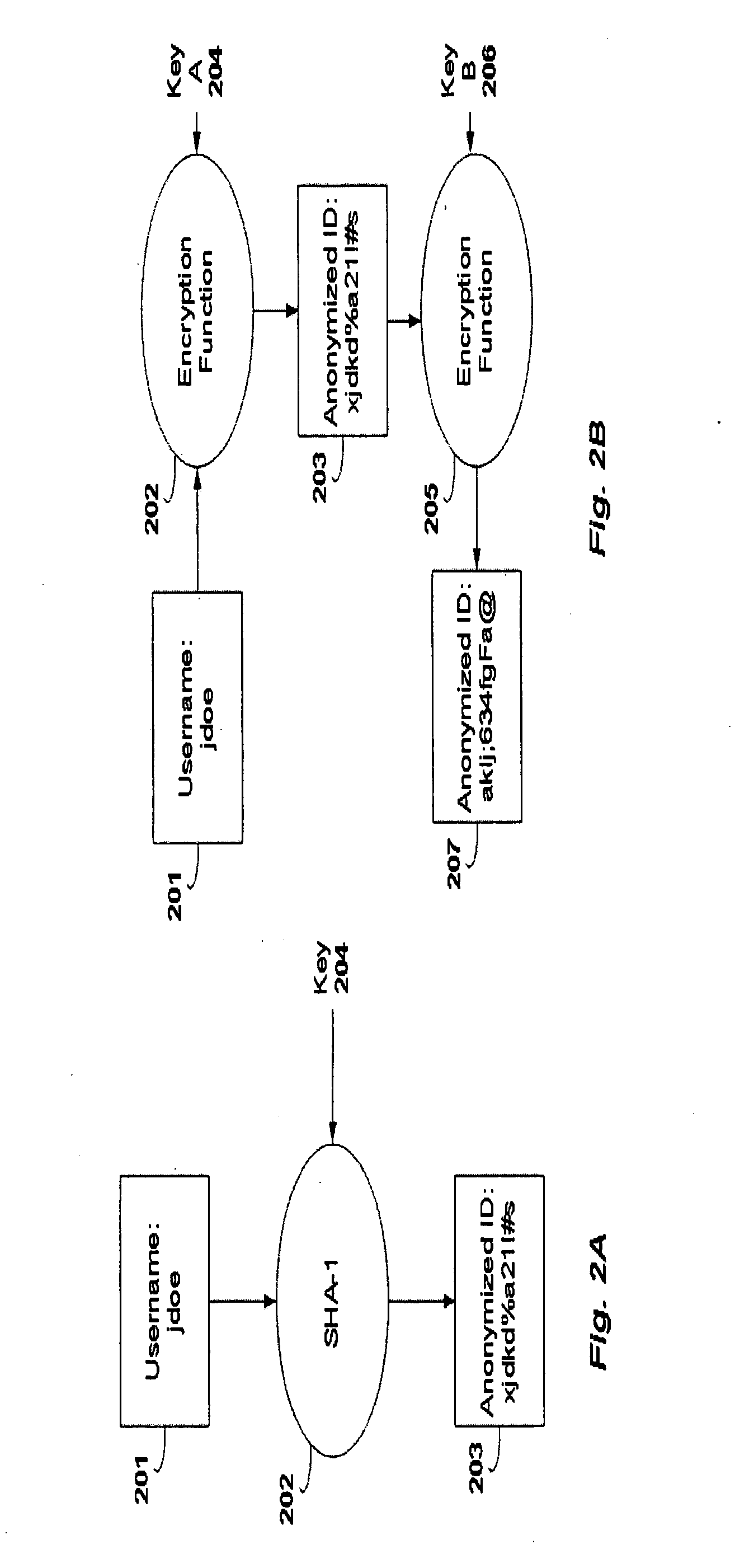
Systems and methods for providing anonymized user profile data
ActiveUS20110060905A1Reduce deliveryIncrease contentCryptography processingOffice automationData transformationInternet privacy
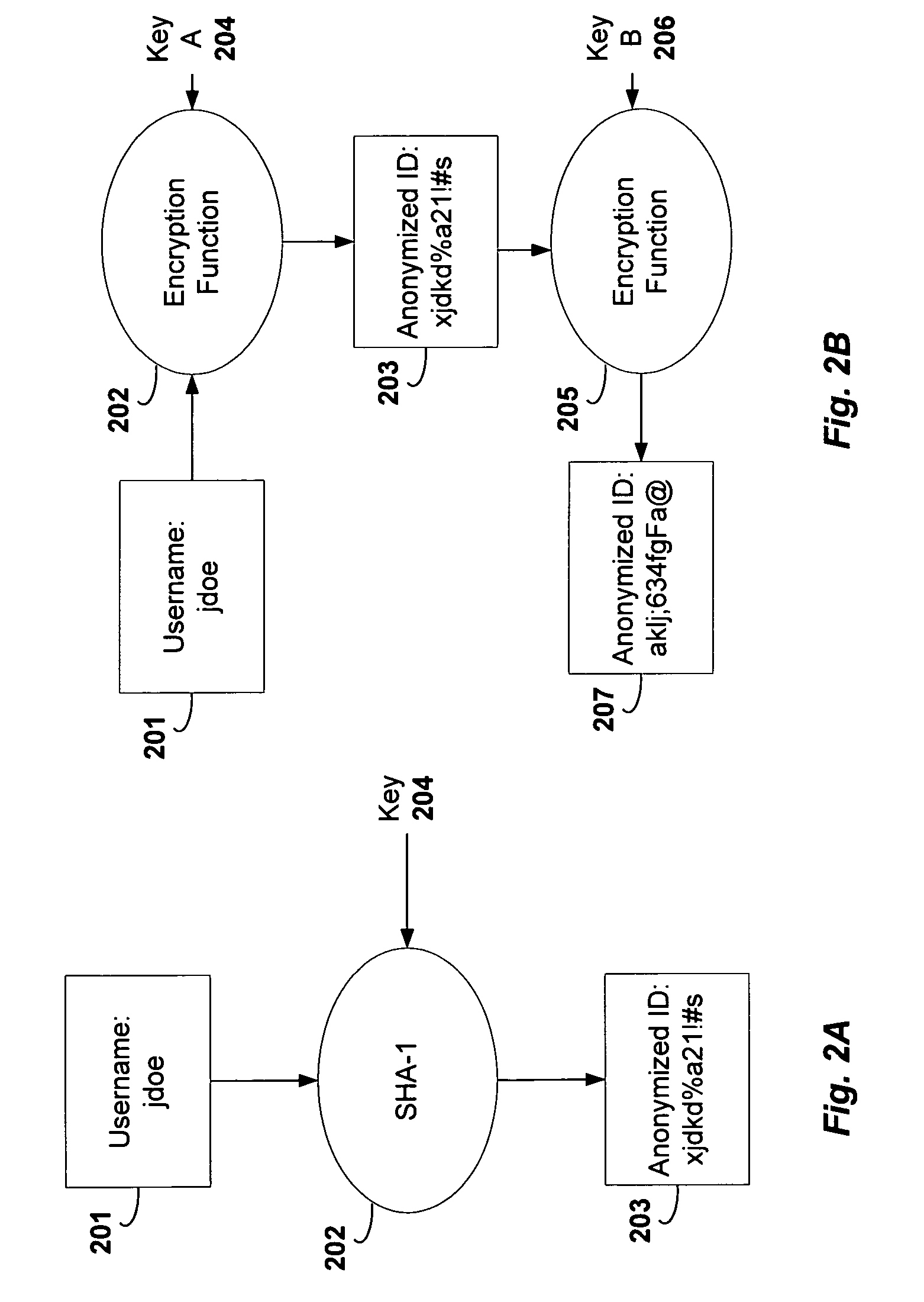
Embodiments facilitate confidential and secure sharing of anonymous user profile data to improve the delivery of customized content. Embodiments of the invention provide a data appliance to an entity such as a business to convert profile data about the business's customers into anonymous identifiers. A similar data appliance is provided to a content provider in one embodiment to generate identifiers for its user profile data. Because the anonymous identifiers are generated with the same anonymization method, identical identifiers are likely generated from profile data of the same users. Therefore, the identifiers can be used to anonymously match the customers of the business to the users of the content provider. Therefore, data can be shared to improve customized content such as advertisements that the business wishes to place with the content provider without requiring the business to disclose customer data in an unencrypted form, and any non-matched data can remain confidential.
Owner:FRITZ SCHAFER +1
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS7996912B2Digital data processing detailsAnalogue secracy/subscription systemsNetwork behaviorInternet privacy
Owner:CONNEXITY AUDIENCE INC
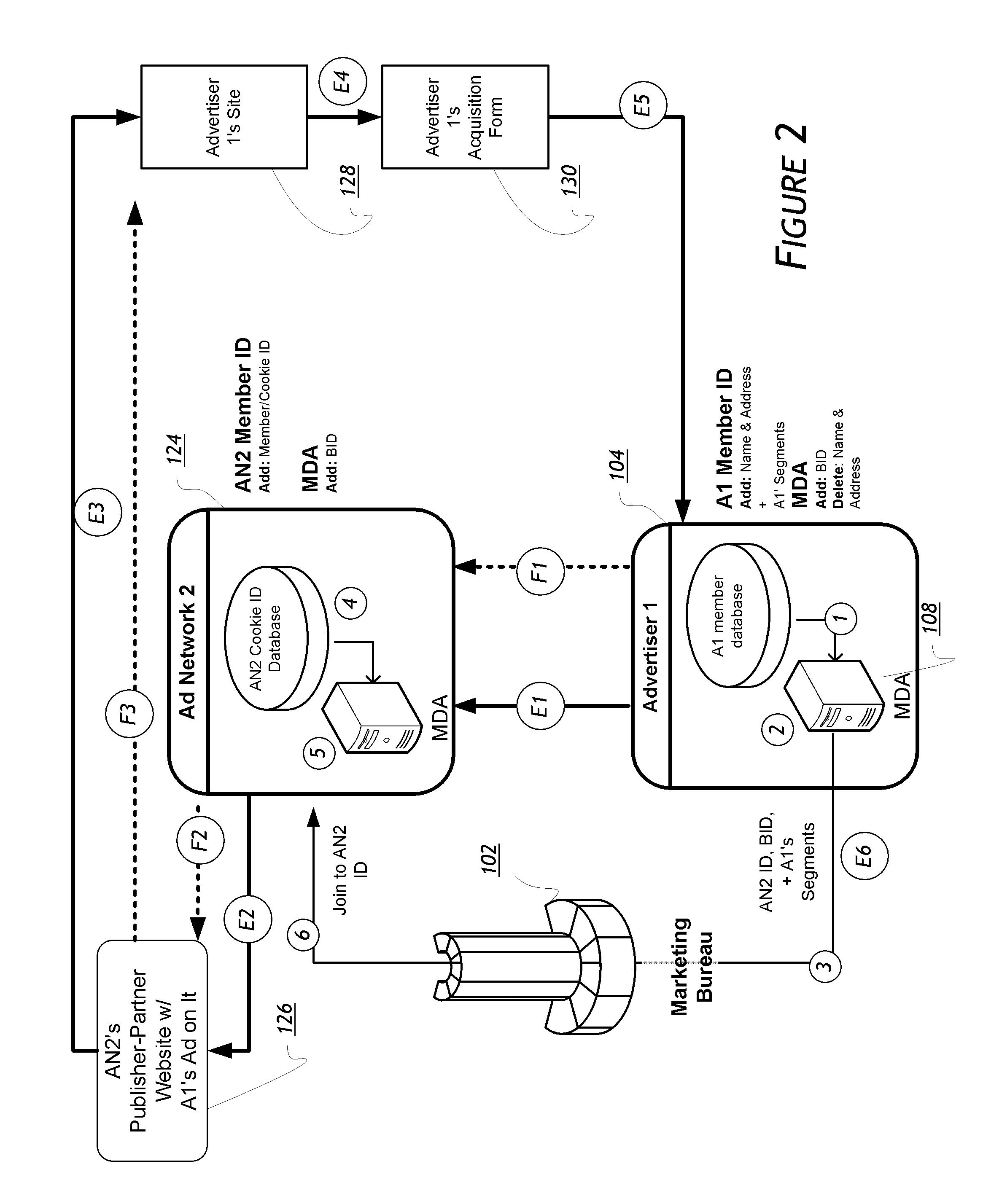
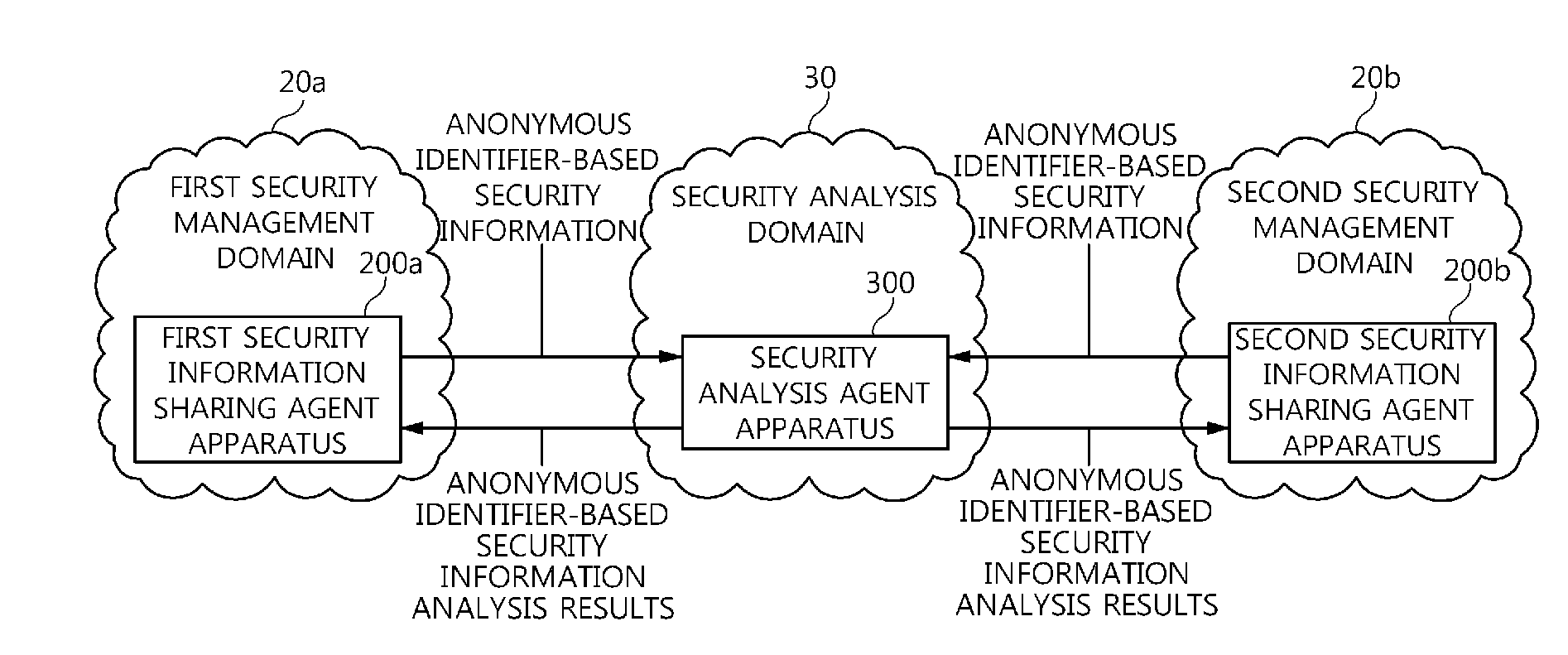
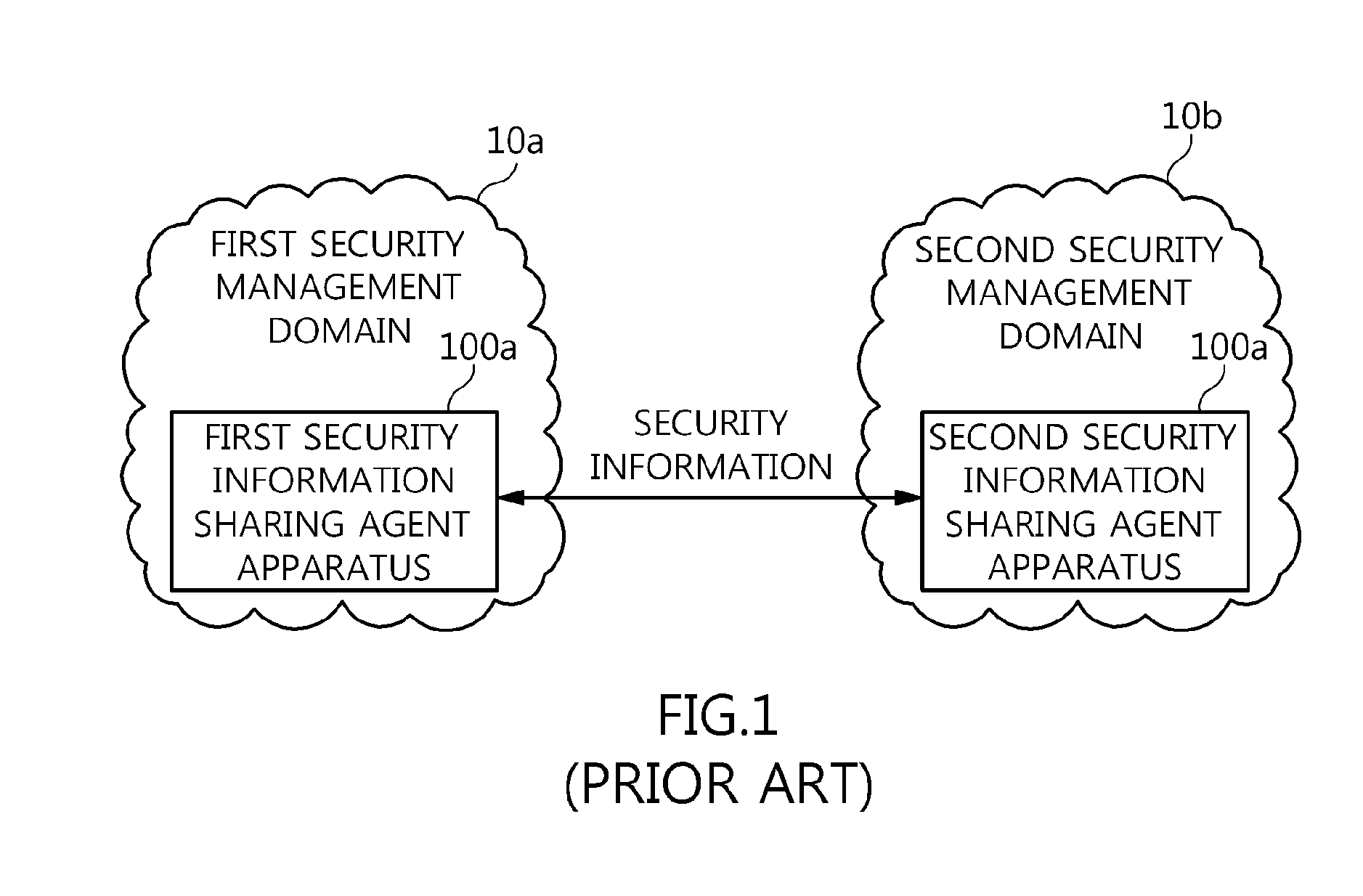
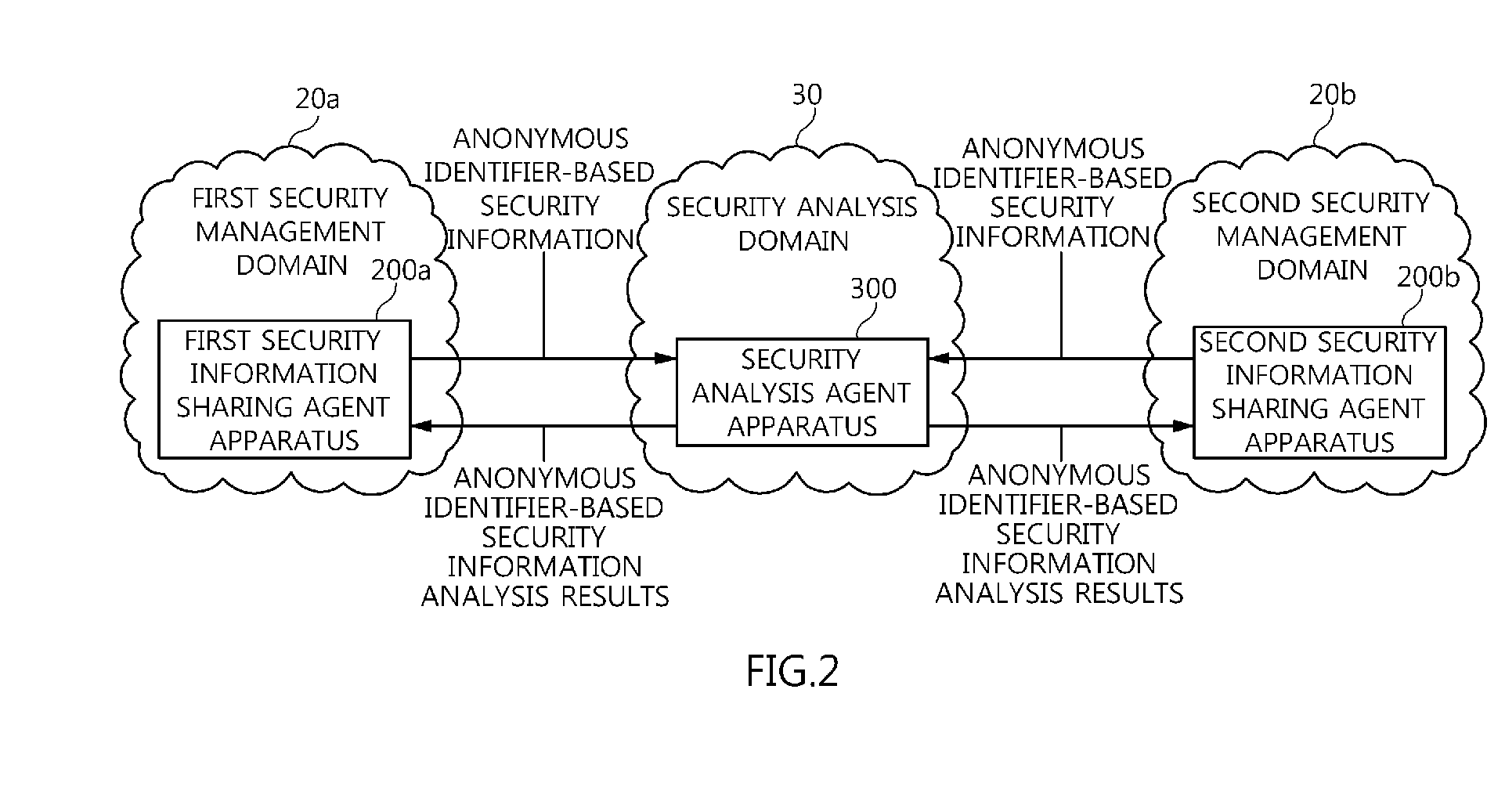
Agent apparatus and method for sharing anonymous identifier-based security information among security management domains
ActiveUS20130139268A1Prevent leakageProtection of personal informationDigital data processing detailsAnalogue secracy/subscription systemsCommunication unitPicocell
The present invention relates to an agent apparatus and method for sharing anonymous identifier-based security information among security management domains. A plurality of security information sharing agent apparatuses respectively located in a plurality of security management domains and configured to collect security information and transmit collected security information to outside of the security management domains. Each security information sharing agent apparatus includes an identifier conversion unit for converting real name identifier-based security information into anonymous identifier-based security information by converting a real name identifier included in the security information into an anonymous identifier, and a security information communication unit for transmitting the anonymous identifier-based security information obtained by the identifier conversion unit to outside of a corresponding security management domain so that security information is shared among the plurality of security management domains.
Owner:ELECTRONICS & TELECOMM RES INST
Systems and methods for providing anonymized user profile data
ActiveUS8639920B2Reduce deliveryEasy to shareCryptography processingDigital data processing detailsData transformationInternet privacy
Embodiments facilitate confidential and secure sharing of anonymous user profile data to improve the delivery of customized content. Embodiments of the invention provide a data appliance to an entity such as a business to convert profile data about the business's customers into anonymous identifiers. A similar data appliance is provided to a content provider in one embodiment to generate identifiers for its user profile data. Because the anonymous identifiers are generated with the same anonymization method, identical identifiers are likely generated from profile data of the same users. Therefore, the identifiers can be used to anonymously match the customers of the business to the users of the content provider. Therefore, data can be shared to improve customized content such as advertisements that the business wishes to place with the content provider without requiring the business to disclose customer data in an unencrypted form, and any non-matched data can remain confidential.
Owner:FRITZ SCHAFER +1
Methods and systems for sharing or presenting member information
InactiveUS20070220611A1Digital data processing detailsUser identity/authority verificationUnique identifierWorld Wide Web
Methods of sharing or presenting members' information without identifying the members are provided. The method comprises receiving a request from a requesting party wherein the requesting party specifies at least one characteristic of members it seeks to target or search in the request; generating a list of members that match the specified characteristic or characteristics in response to the request; substituting information related to members on the list with an anonymous identifier and providing such identifier to the requesting party. Preferably, each member is assigned a unique identifier. The method for supplementing information collected from different organizations is also provided. Additionally, the system and computer program for carrying out these methods are disclosed.
Owner:WIPROX
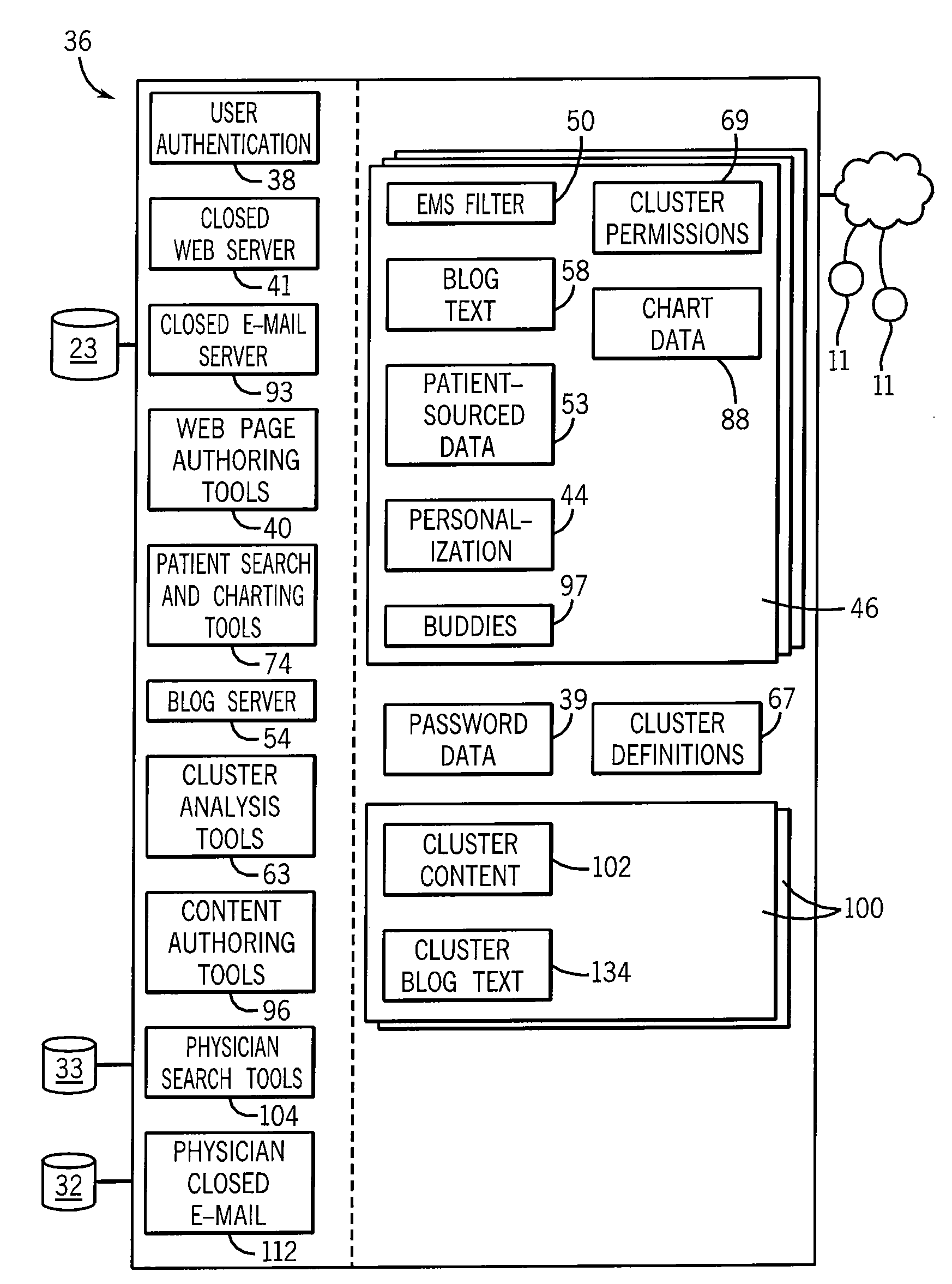
Patient Community System With Anonymized Electronic Medical Data
ActiveUS20100070306A1Quality improvementInterestingMedical communicationMedical data miningMedical recordCommunity system
A computerized system allows intercommunication of patients with respect to the treatment of their diseases. This system includes an electronic medical record database providing electronic medical records of a given set of patients as developed by healthcare professionals and linked to an anonymous identifier for each patient and a set of terminal devices accessible to the patients allowing for the electronic exchange of information through a display and data input device. A server system connects the anonymous medical record database and the terminal devices and executes a stored program to: (1) allow an authenticated connection by a given patient to the server system through a terminal device and associate the connection with an anonymous identifier; (2) permit authoring by the given patient of a patient site viewable on a terminal device incorporating medical records from the anonymous medical record database associated with the anonymous identifier; and (3) identify to the given patient other patient sites for other patients having shared medical conditions according to a predetermined clustering of data of the anonymous medical record database.
Owner:EPIC SYST CORP (US)
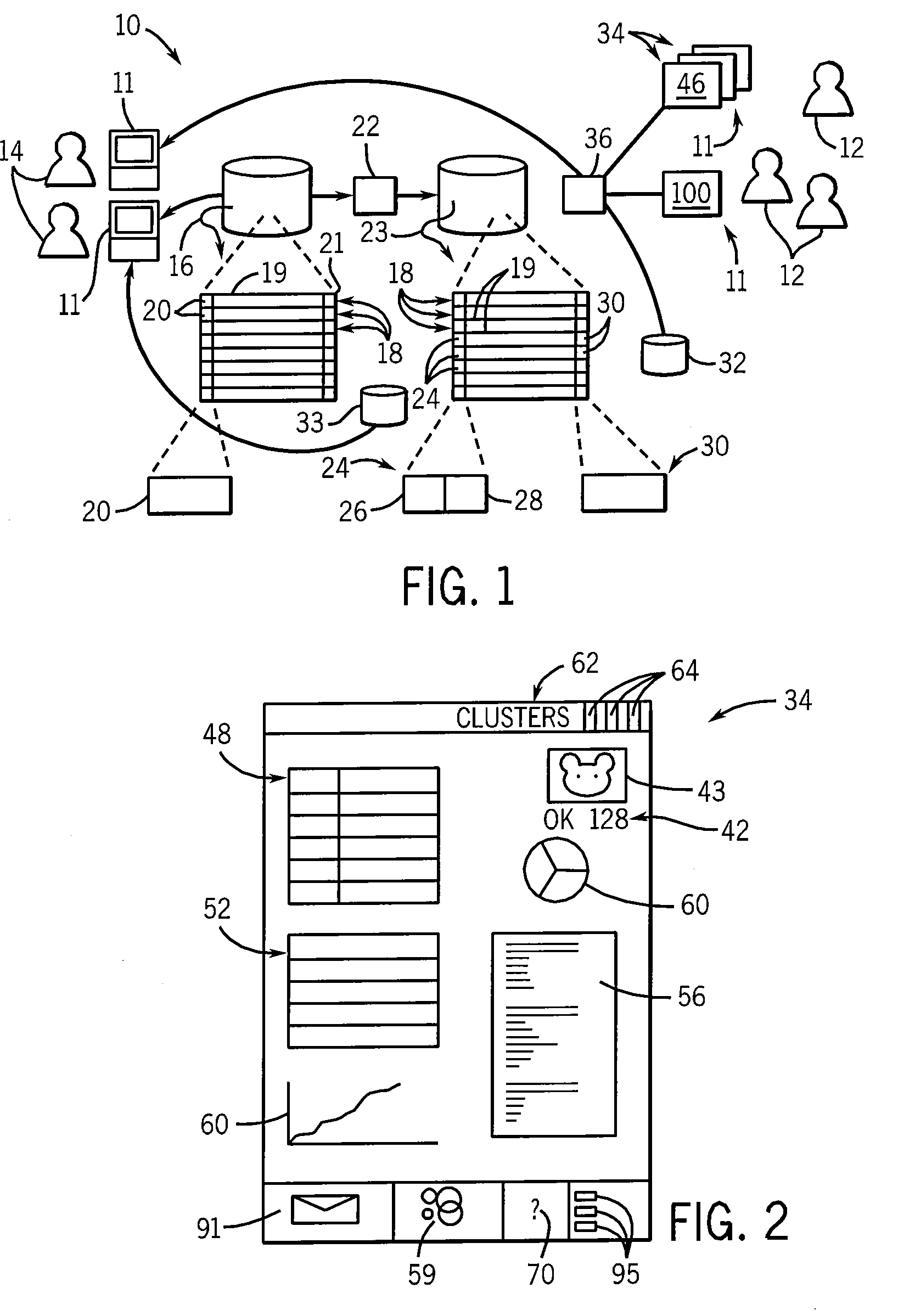
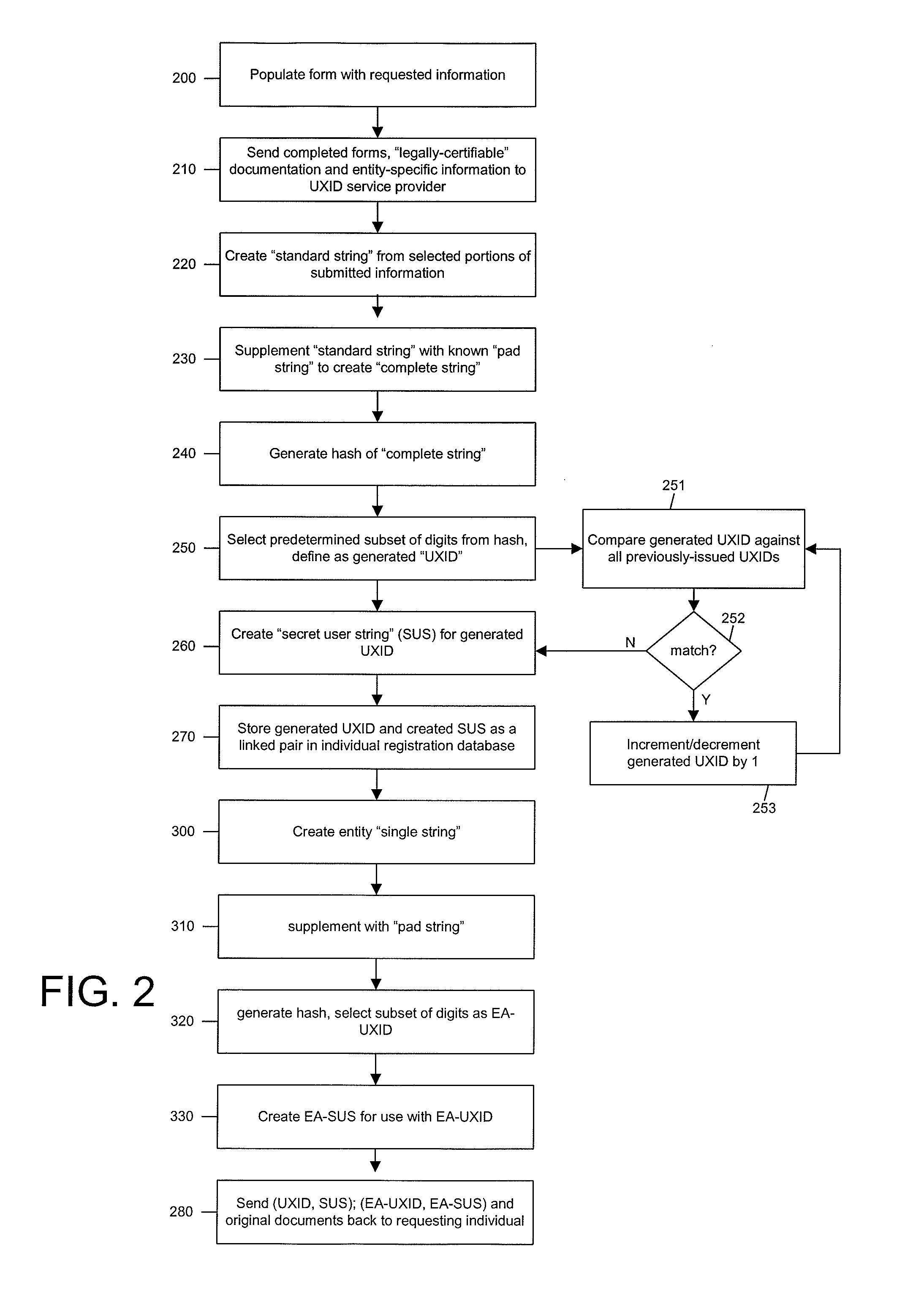
Systems and methods for controlling data access by use of a universal anonymous identifier
ActiveUS8042193B1Digital data processing detailsUser identity/authority verificationDocumentation procedureHash function
A universal anonymous data collection and exchange service is provided where individuals and entities initially register with the service utilizing “legally authentic” identity documentation to obtain a “universal ID” (UXID). The UXID consists of a sting of alphanumeric digits selected from a hash function that is performed on a string of personally identifying information. Once registered, the individual and entity UXIDs are used as a means by the service to engage in a pre-defined confidential data collection and exchange protocol between participating, registered UXID holders. The service is designed for use across many applications, individuals and entities, and may support one-time or recurring collection of data.
Owner:ALBRIGHT ASSOCS
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
InactiveUS20060070117A1Digital data processing detailsUser identity/authority verificationInternet privacyTransaction data
Owner:CONNEXITY AUDIENCE INC
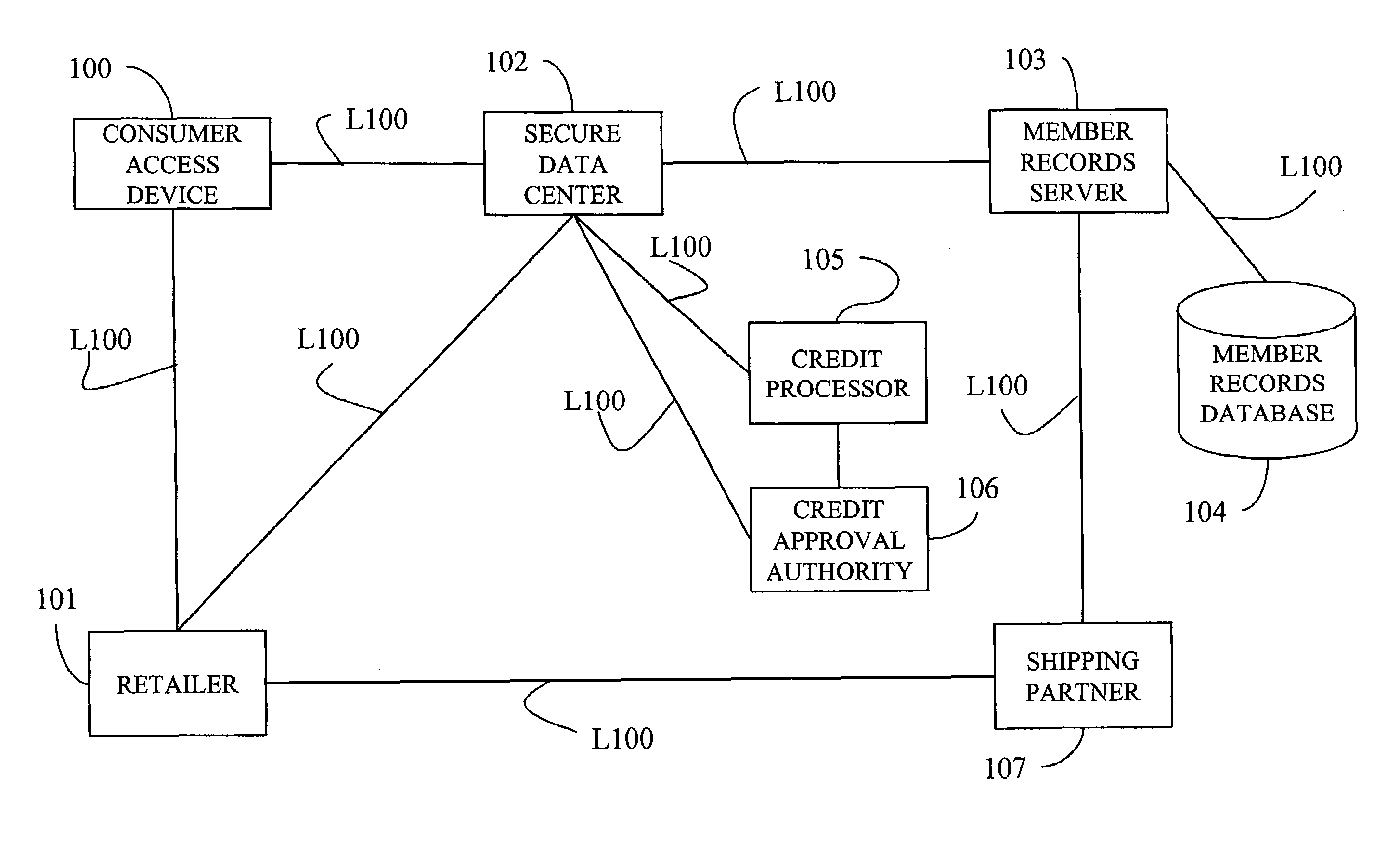
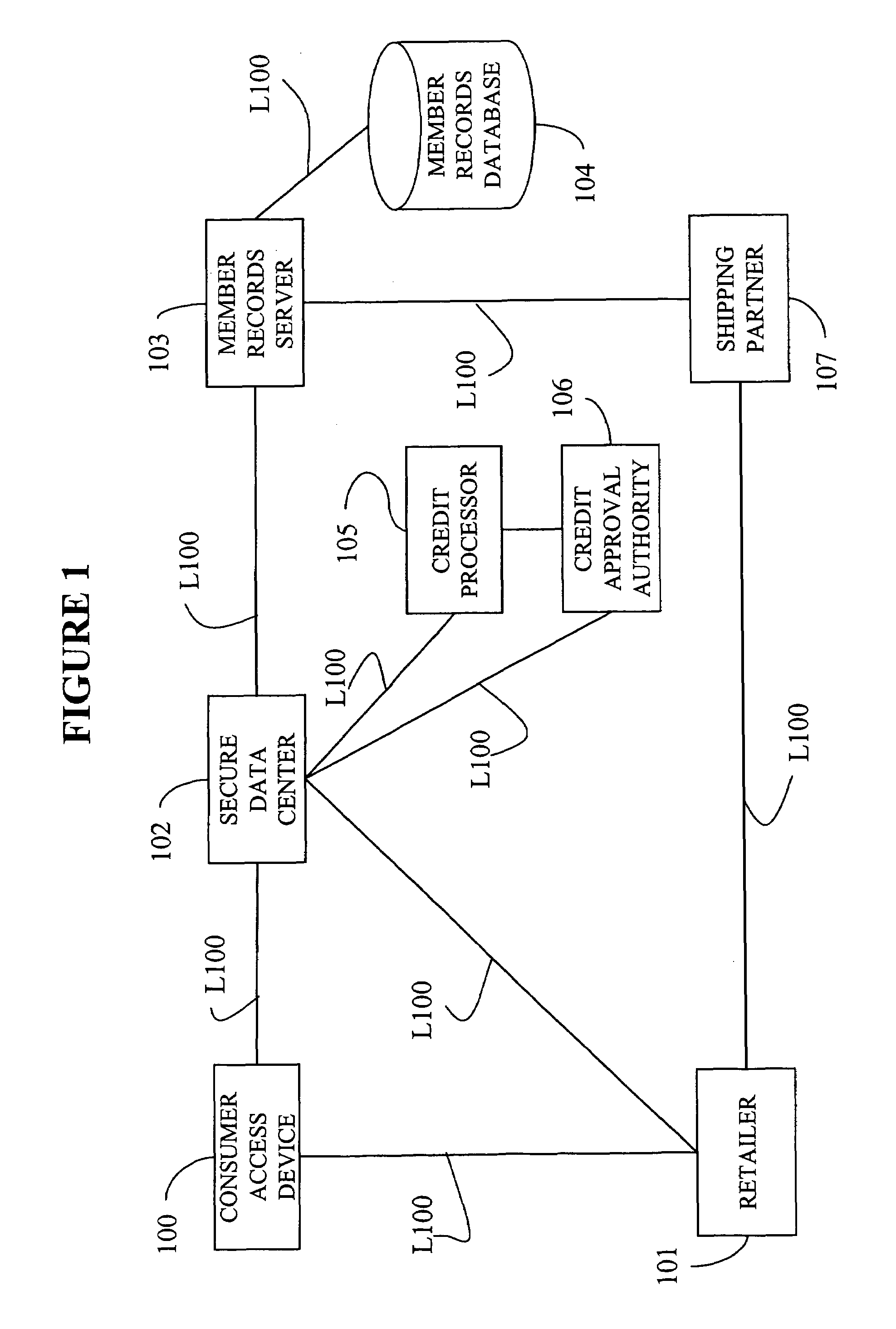
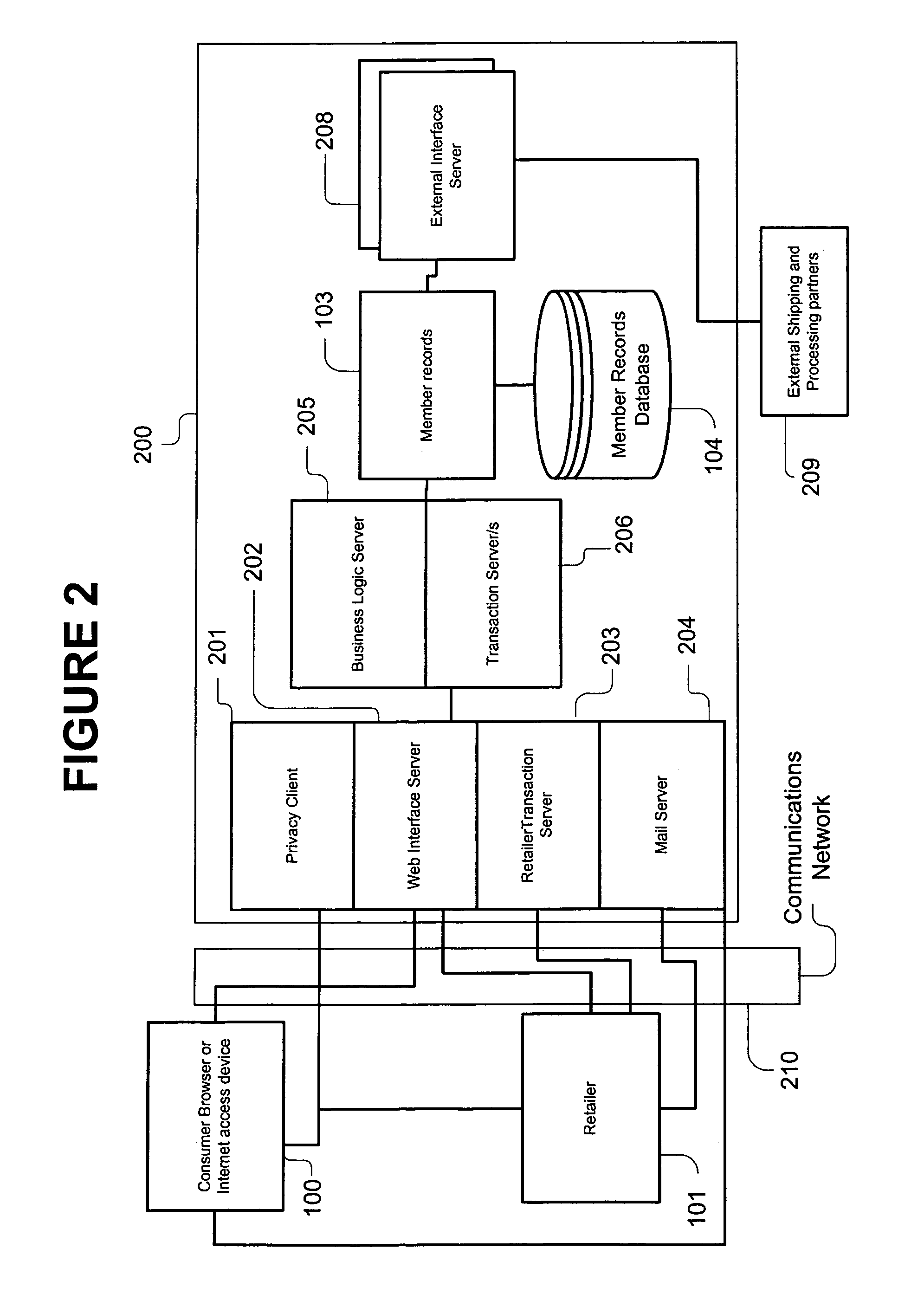
System, method, and computer program product for maintaining consumer privacy and security in electronic commerce transactions
InactiveUS7636696B1Keep it privateDisclosure is limitedComputer security arrangementsBuying/selling/leasing transactionsPaymentInternet privacy
A system, method, and computer program product for maintaining the anonymity of a consumer in a transaction with a retailer. The consumer provides payment method information and ship-to address information to a trusted third party. The consumer purchases products from a retailer by providing the trusted third party anonymous identifiers (e.g., nicknames, unique codes, or one time use codes either supplied by the consumer or by the trusted third party) corresponding to the selected payment methods and ship-to addresses. The retailer requests payment approval from the trusted third party. The trusted third party receives payment approval from a payment partner using the payment method information determined from the anonymous identifier received from the consumer. The trusted third party provides payment approval to the retailer along a transaction unique shipment identifier to place on the parcel. The trusted third party sends the same transaction unique shipment identifier and the actual shipping address determined from the anonymous identifier received from the consumer to a shipping partner who re-labels the package and delivers it to the consumer. The trusted third party acts as an e-mail conduit for messages sent to member consumers.
Owner:MEGASOFT
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS20090182873A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyNetwork behavior
Owner:CONNEXITY AUDIENCE INC
Anonymous Preservation of a Relationship and Its Application in Account System Management
InactiveUS20110078779A1Improve security levelDigital data processing detailsAnalogue secracy/subscription systemsHash functionInternet privacy
Disclosed is a system or method of using hash functions to preserve a relationship. A relationship is anonymously preserved by storing the hash result of a relationship token that comprises a finite set of values of a plurality of objects. Specifically, an account anonymous identifier of an account can be produced by hashing a relationship token that comprises identity information of an owner of said account. A party that has enough knowledge of an account owner can independently produces said account anonymous identifier and therefore, securely communicates with a specific account without prior communication or a password. An account owner can further prove his / her ownership of an account by submitting related documents and a relationship token that comprises his / her identity information to an account system.
Owner:LIU SONG +1
Systems and methods for providing anonymized user profile data
ActiveUS20140201007A1Reduce deliveryEasy to shareCryptography processingOffice automationData transformationInternet privacy
Embodiments facilitate confidential and secure sharing of anonymous user profile data to improve the delivery of customized content. Embodiments of the invention provide a data appliance to an entity such as a business to convert profile data about the business's customers into anonymous identifiers. A similar data appliance is provided to a content provider in one embodiment to generate identifiers for its user profile data. Because the anonymous identifiers are generated with the same anonymization method, identical identifiers are likely generated from profile data of the same users. Therefore, the identifiers can be used to anonymously match the customers of the business to the users of the content provider. Therefore, data can be shared to improve customized content such as advertisements that the business wishes to place with the content provider without requiring the business to disclose customer data in an unencrypted form, and any non-matched data can remain confidential.
Owner:EXPERIAN MARKETING SOLUTIONS
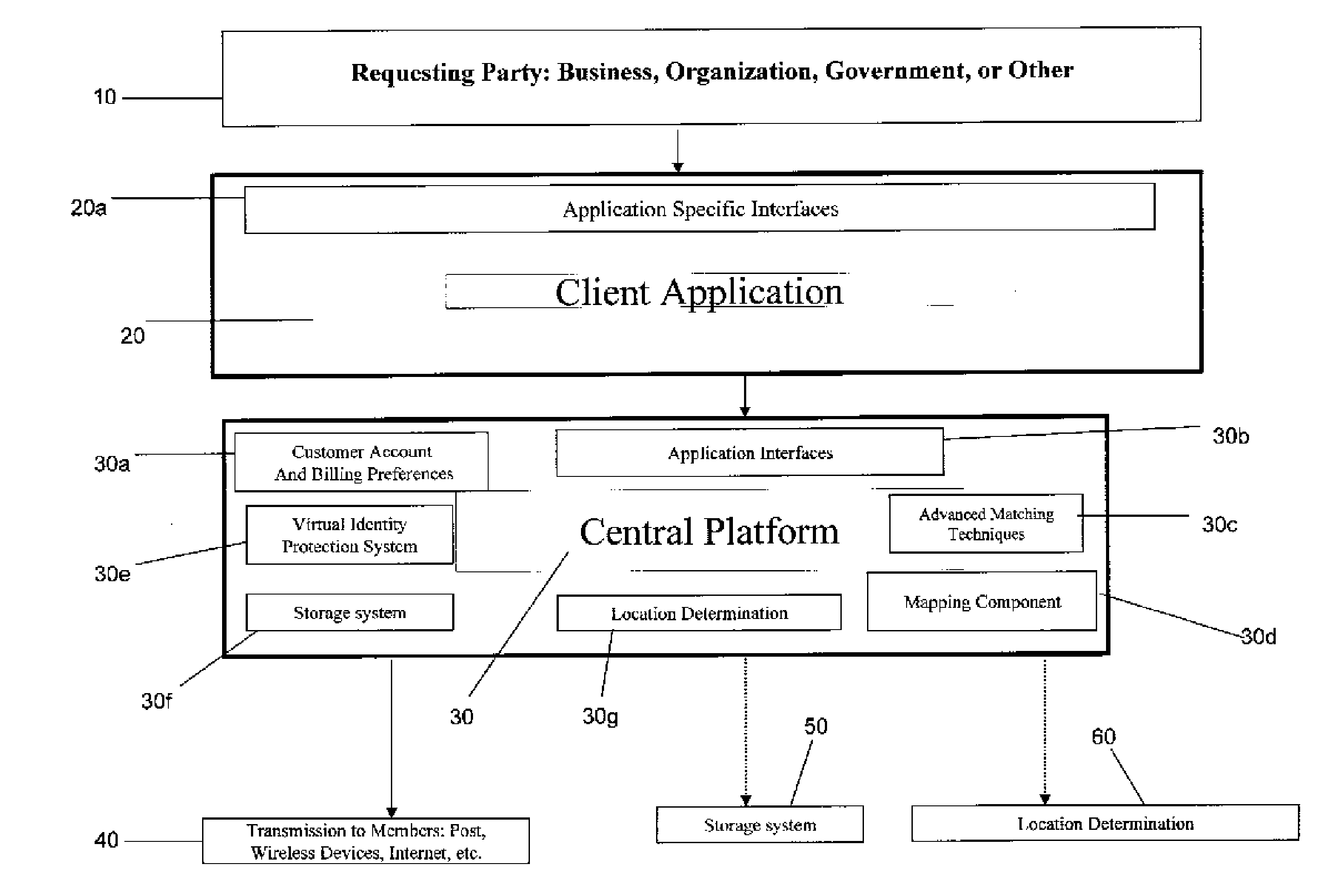
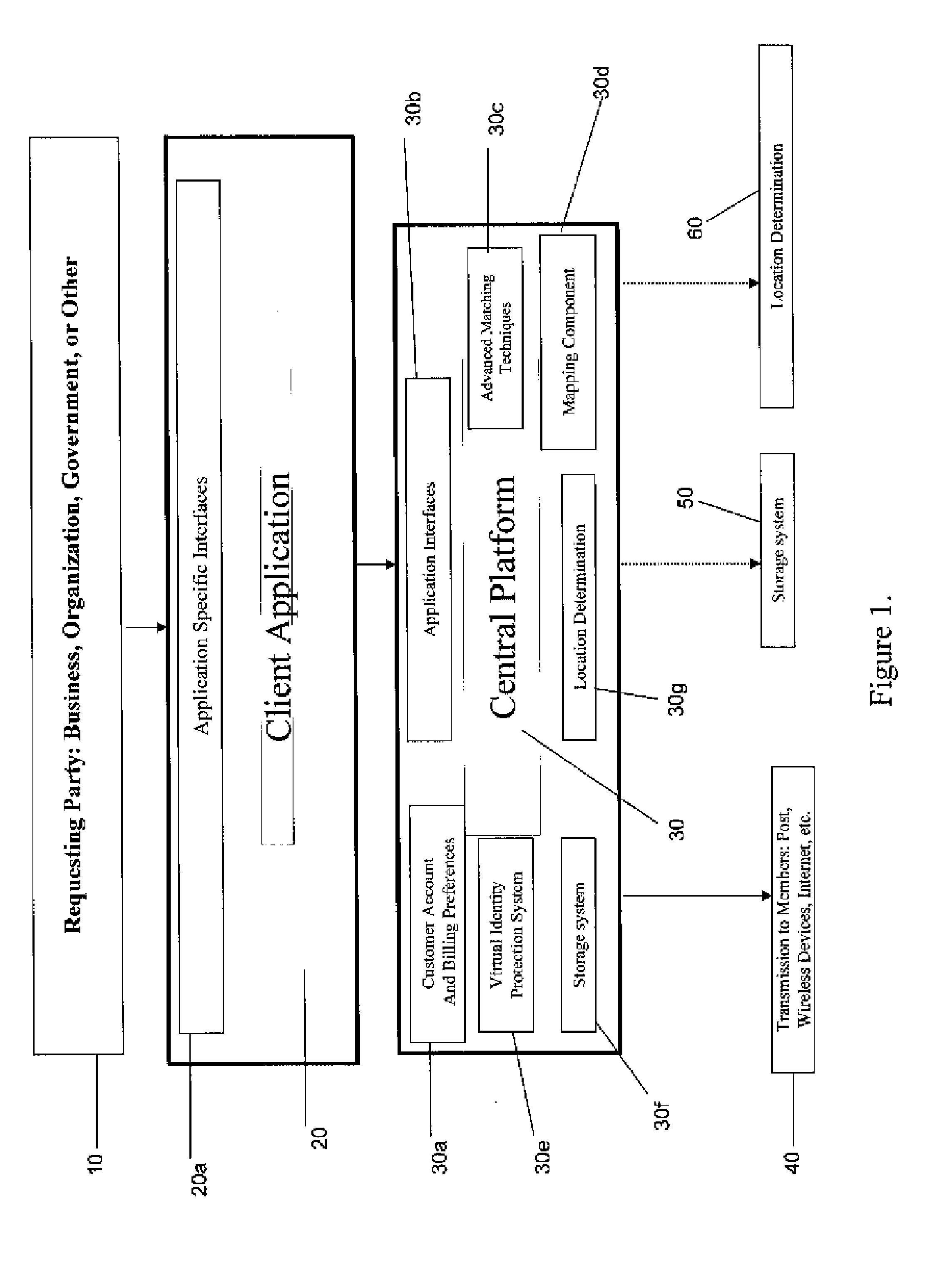
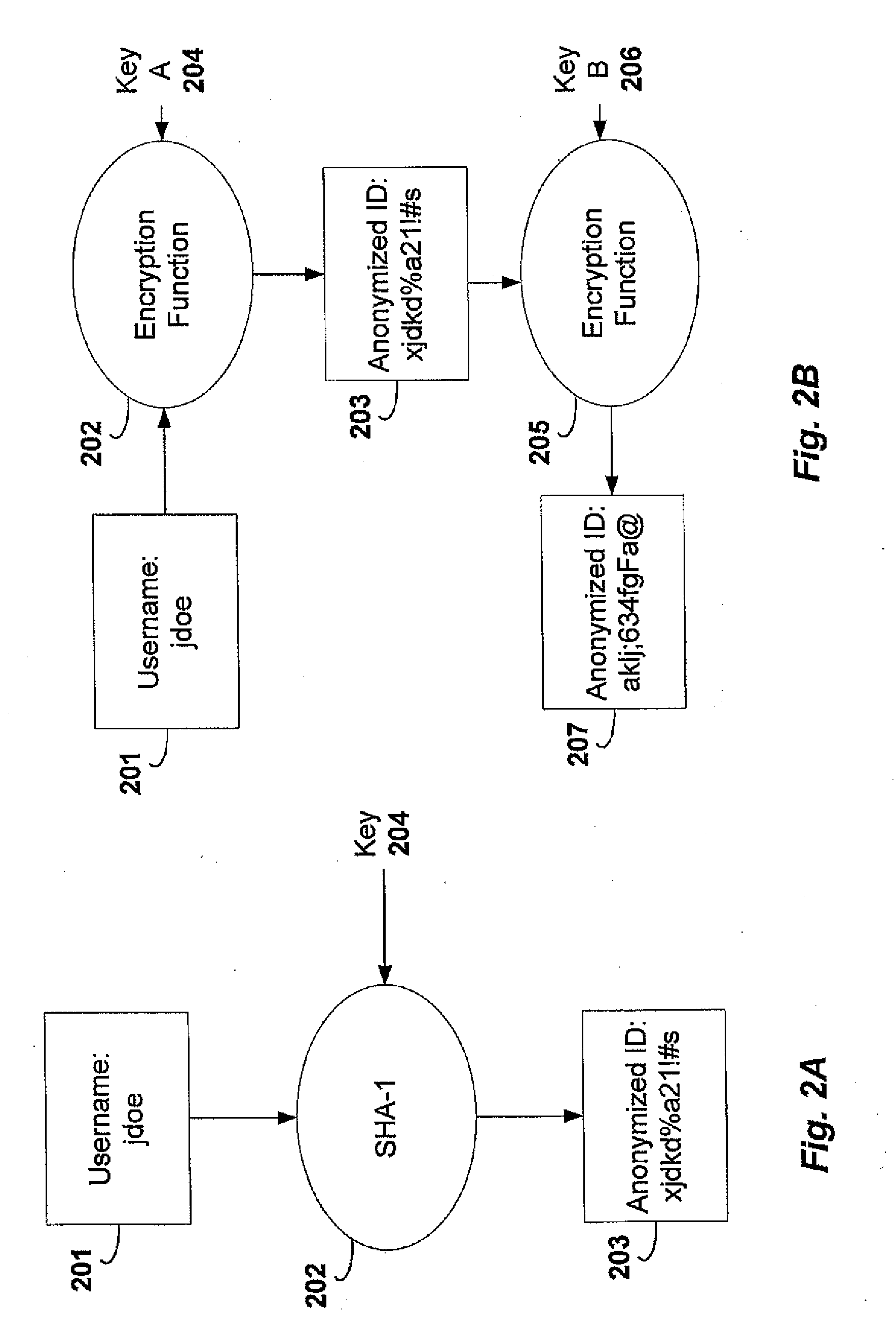
Method of customizing a user's browsing experience on a World-Wide-Web site
In accordance with a first aspect of the present invention, a method of customizing the browsing experience of a user of a Web site comprised of a plurality of Web pages is provided. Each Web page is indexed using at least one coding system. A user record for each user is maintained on the Web site, which contains personal information of the user coded in accordance with said coding system. The user's browsing experience on the site may thus be readily customized using the user's personal information via code comparison. In accordance with a second aspect of the present invention, a method of ensuring the privacy of the user's personal information is provided through use of a unique Universal Anonymous Identifier (UAI) assigned to each user by a third party registration authority.
Owner:PERSONALPATH SYST
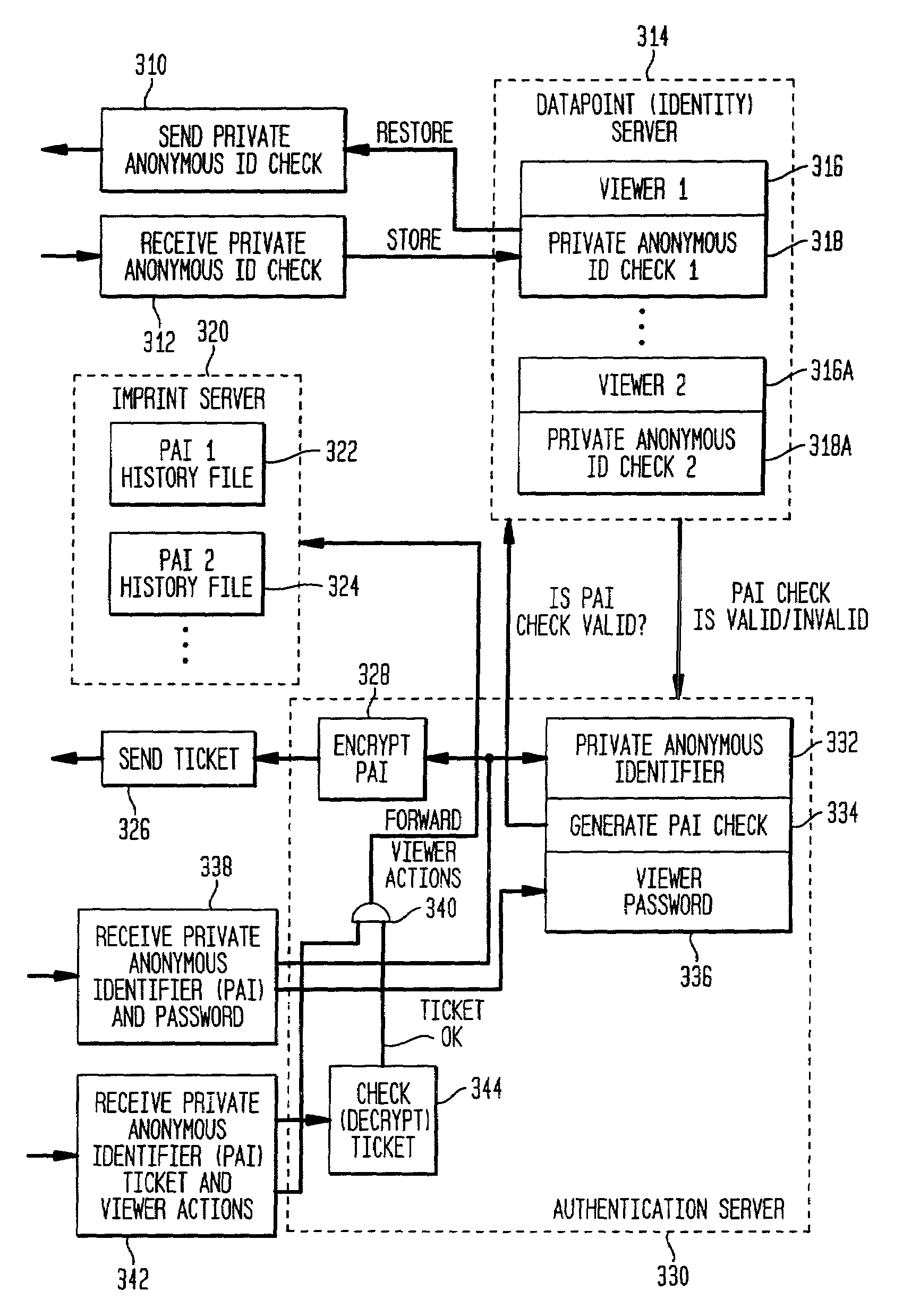
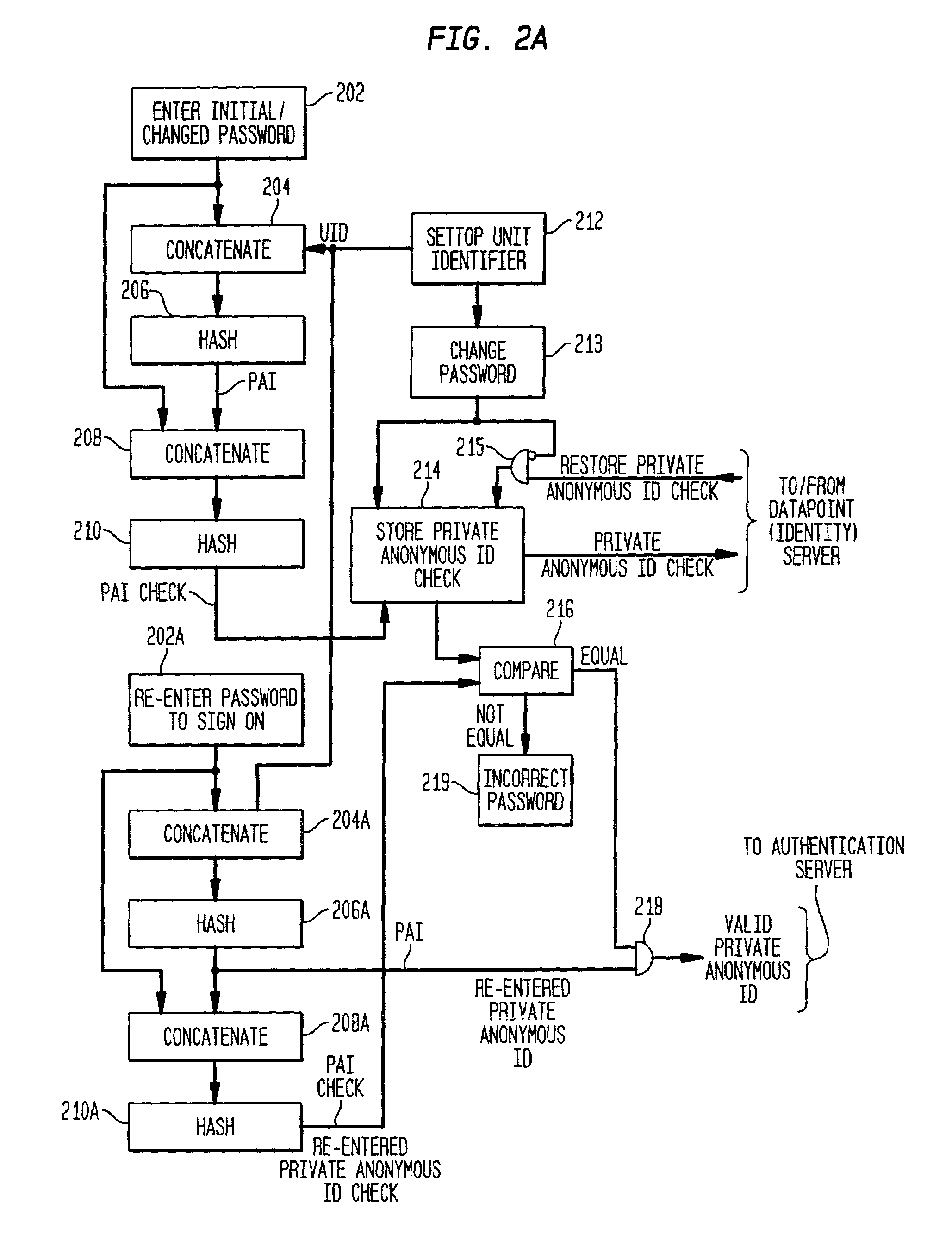
Method and apparatus for anonymously tracking TV and internet usage
ActiveUS7472423B2Improve privacyAvoid dataDigital data processing detailsUser identity/authority verificationUser inputPassword
A system provides for tracking the behavior of television viewers and Internet browsers while protecting the privacy of the user. The level of privacy is under control of the user. In one embodiment, an arbitrary anonymous identifier is assigned to the user. The selection of a new arbitrary anonymous identifier is under the control of the user. In a second embodiment, a private anonymous identifier is based on a user entered password. The user history data is stored on a history server using the private anonymous identifier. An authentication server is provided to validate the private anonymous identifier before transferring the user history data to the history server.
Owner:COMCAST CABLE COMM MANAGEMENT LLC
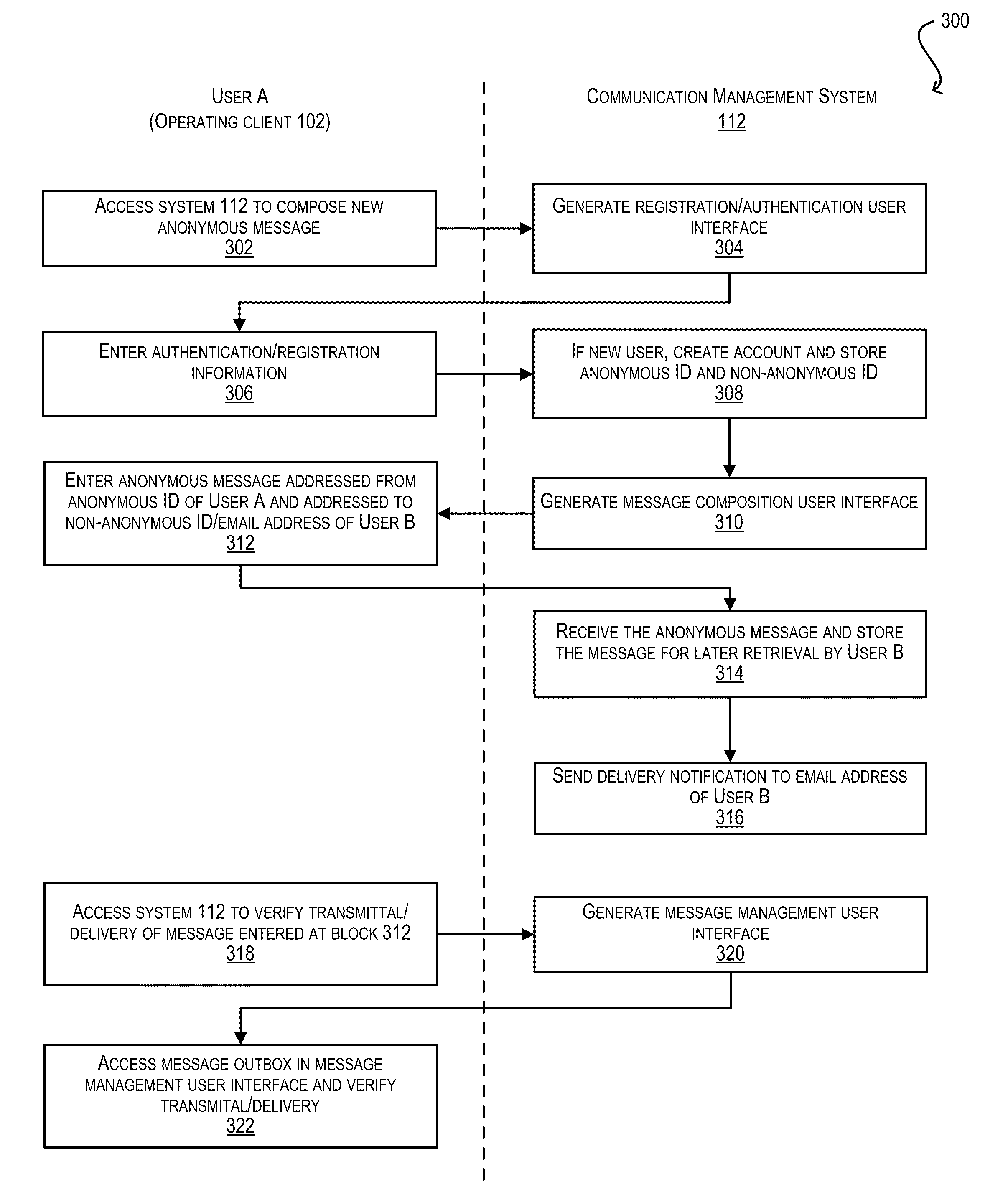
Techniques for enabling anonymous interactive communication
InactiveUS20110010425A1Maintaining anonymityMultiple digital computer combinationsTransmissionElectronic communicationComputer science
Techniques for enabling interactive (e.g., two-way) electronic communication between parties where one party remains anonymous. In one set of embodiments, a system is provided that can store anonymous and non-anonymous identifiers for a group of users. The system can receive, from a first user, an anonymous message addressed from the anonymous identifier of the first user and addressed to the non-anonymous identifier of a second user. The system can then deliver the anonymous message to the second user. The system can further receive, from the second user, a reply message in response to the anonymous message that is addressed from the non-anonymous identifier of the second user and addressed to the anonymous identifier of the first user. The system can then deliver the reply message to the first user. In this manner, the first and second users can communicate interactively while maintaining the anonymity of the first user.
Owner:VOXOPOLIS
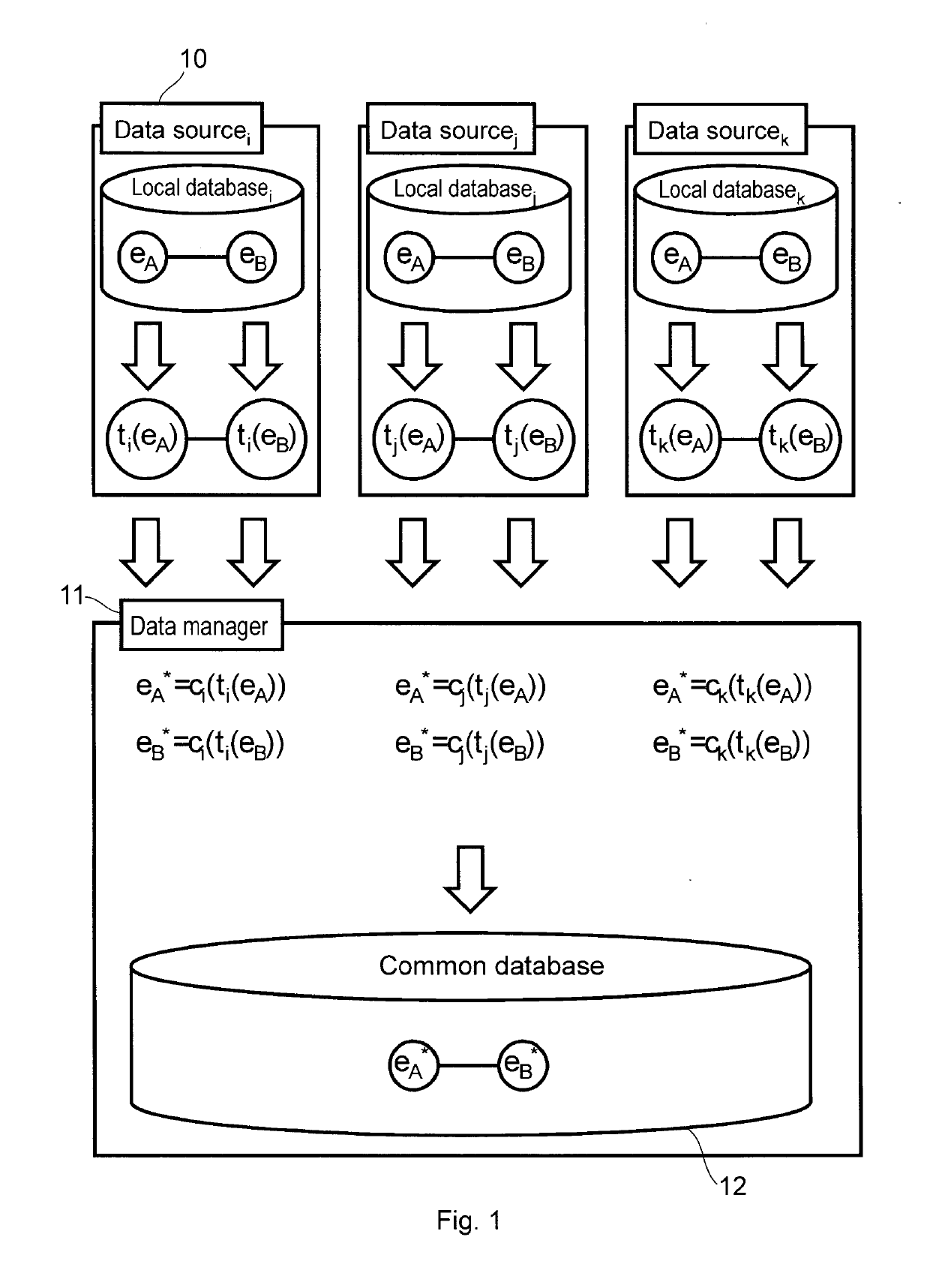
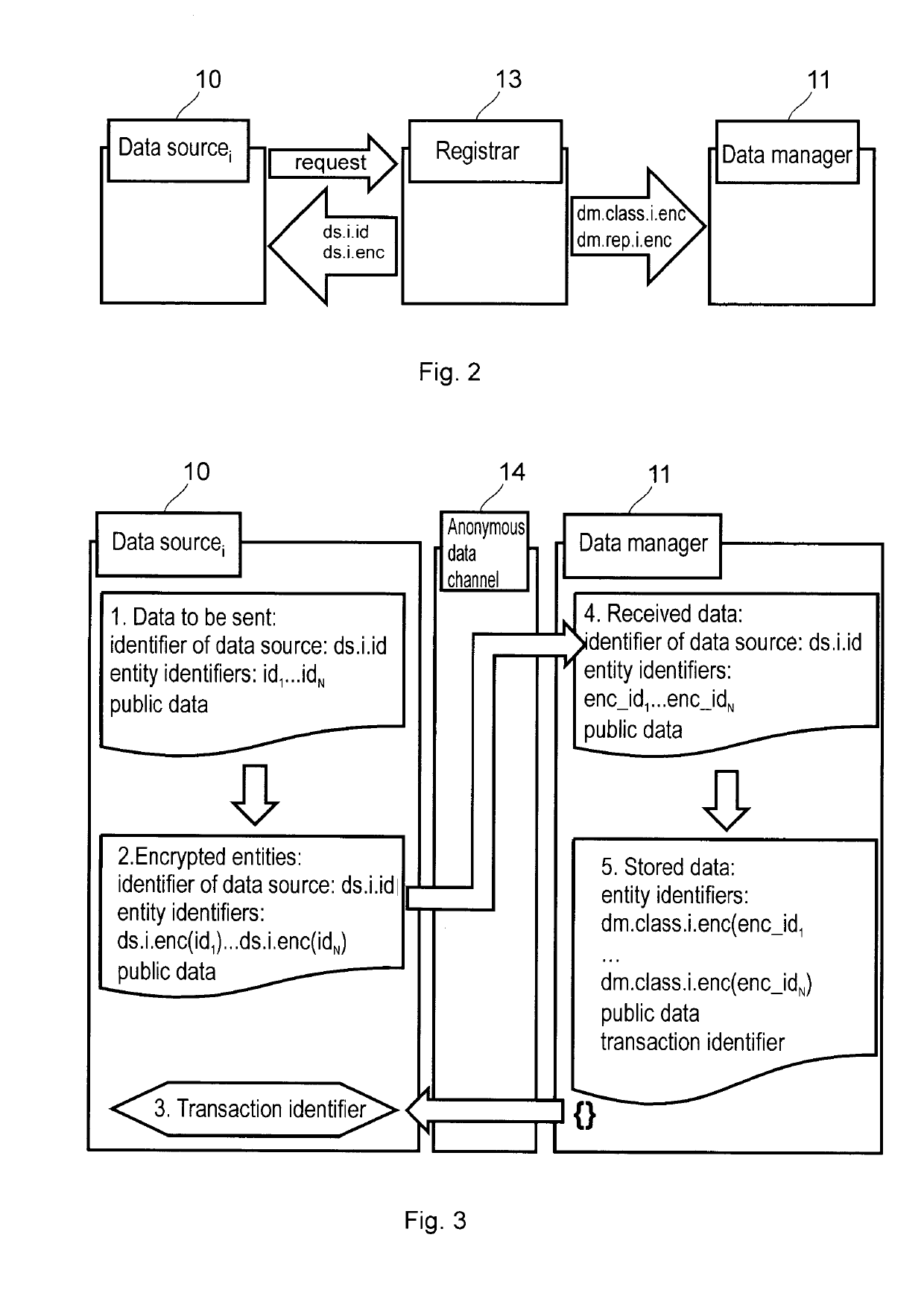
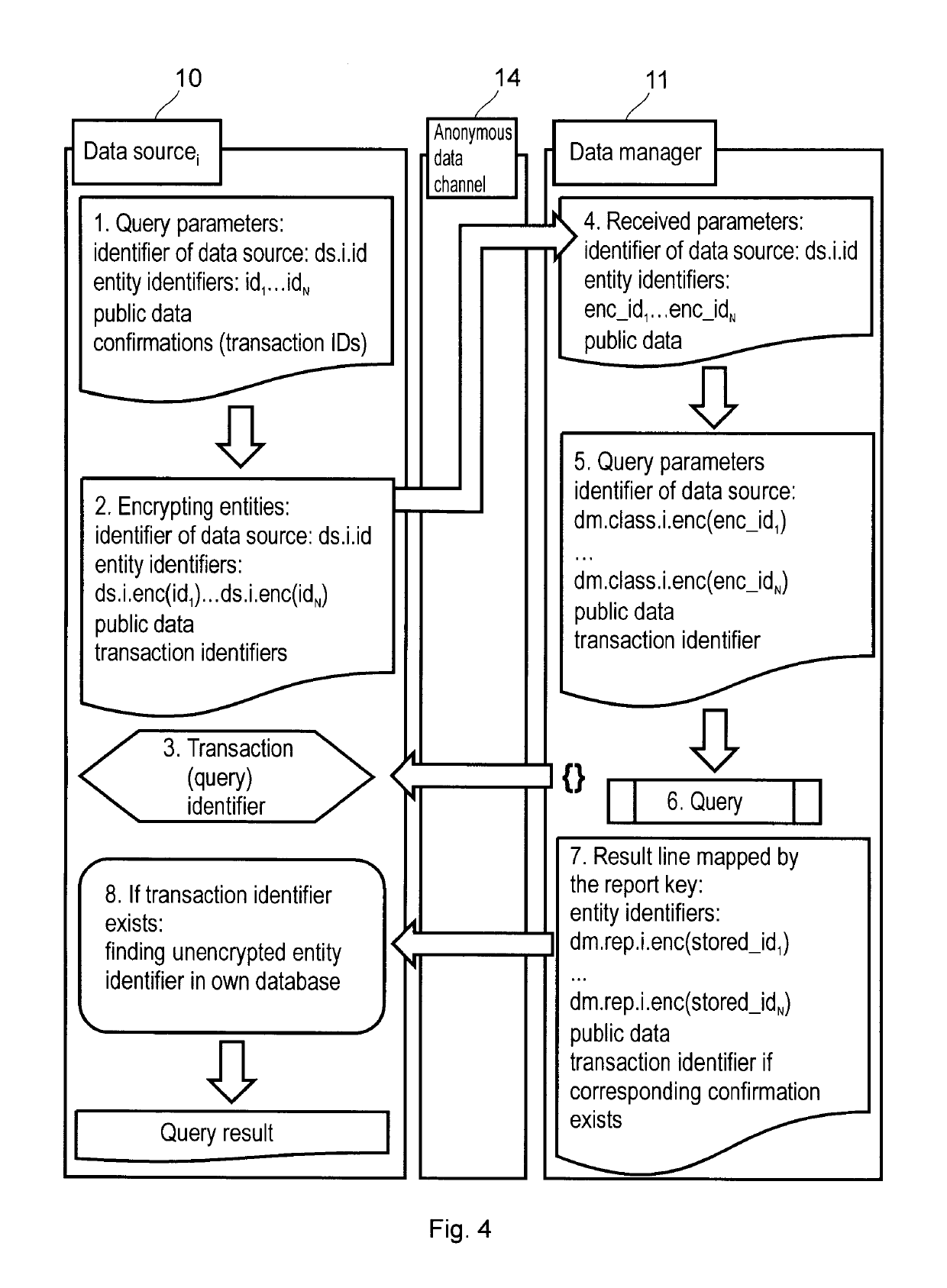
Data management method and registration method for an anonymous data sharing system, as well as data manager and anonymous data sharing system
ActiveUS20190213356A1Maintaining anonymityKey distribution for secure communicationMultiple keys/algorithms usageEntity identifierData source
The invention is a data management method for an anonymous data sharing system, comprising the steps of receiving a data supply from a data source (10), the data supply comprising an anonymous data source identifier, an entity identifier encrypted with the private encryption key of the data source (10), and data associated with the entity. The method further comprises mapping the encrypted entity identifier to a common anonymous entity identifier by applying a classifier key associated with the data source identifier in such a manner that for every entity identifier the following applies: by encrypting said entity identifier with the private encryption key of any data source (10) and by mapping it using the classifier key associated with the identifier of the data source, the same common anonymous entity identifier is obtained, wherein the data associated with the entity are stored in a database (12) in a manner that said data are assigned to the common anonymous identifier. The invention also relates to a registration method, to a data manager, and to an anonymous data sharing system comprising same.
Owner:XTENDR ZRT
Storing identification data as virtual personally identifiable information
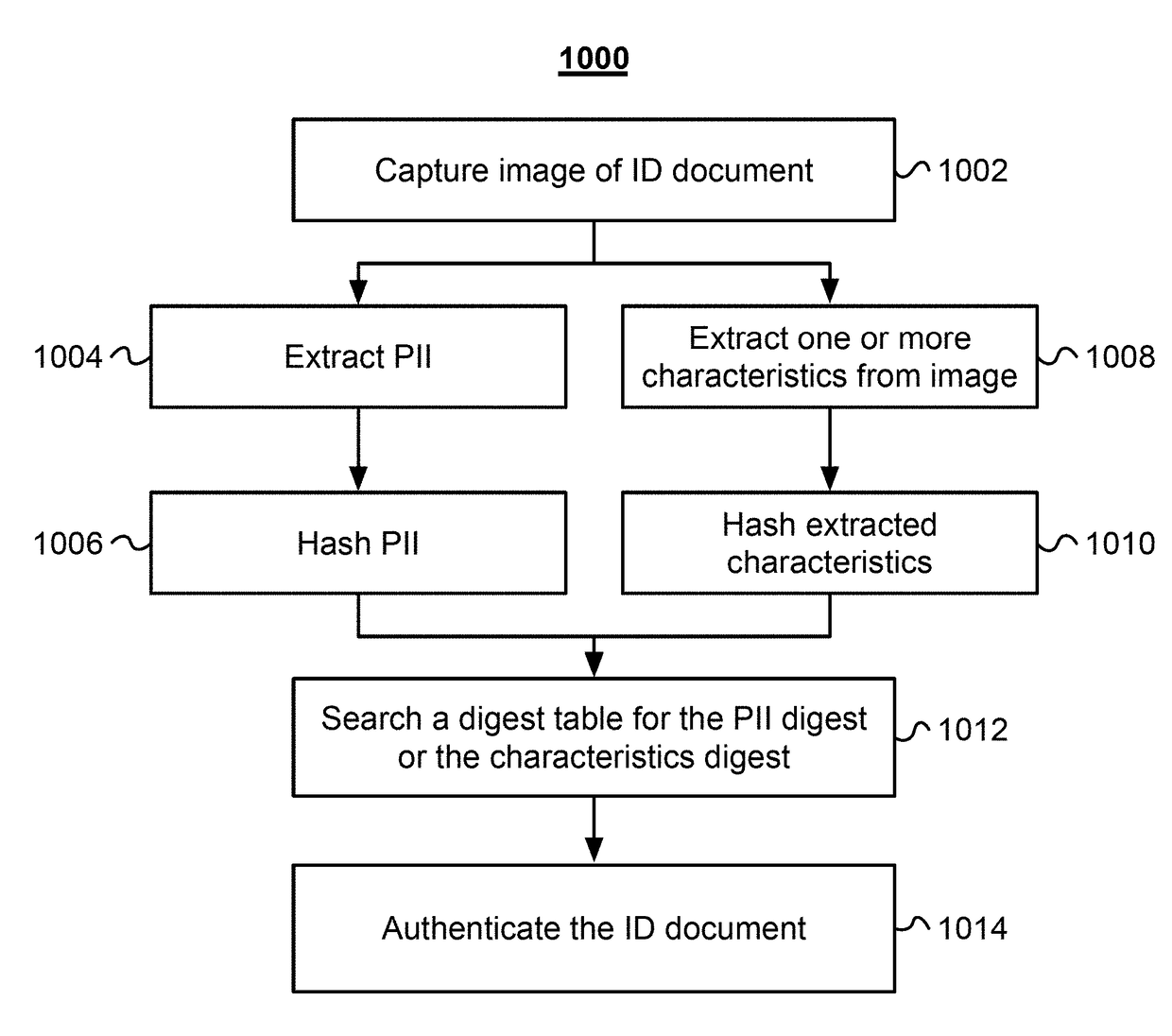
ActiveUS20170286765A1Safe storageProcess can be usedSecuring communicationCharacter recognitionDocumentation procedureHash function
Owner:META PLATFORMS INC
Secret key devices for supporting anonymous authentication, generation method and unlocking method thereof
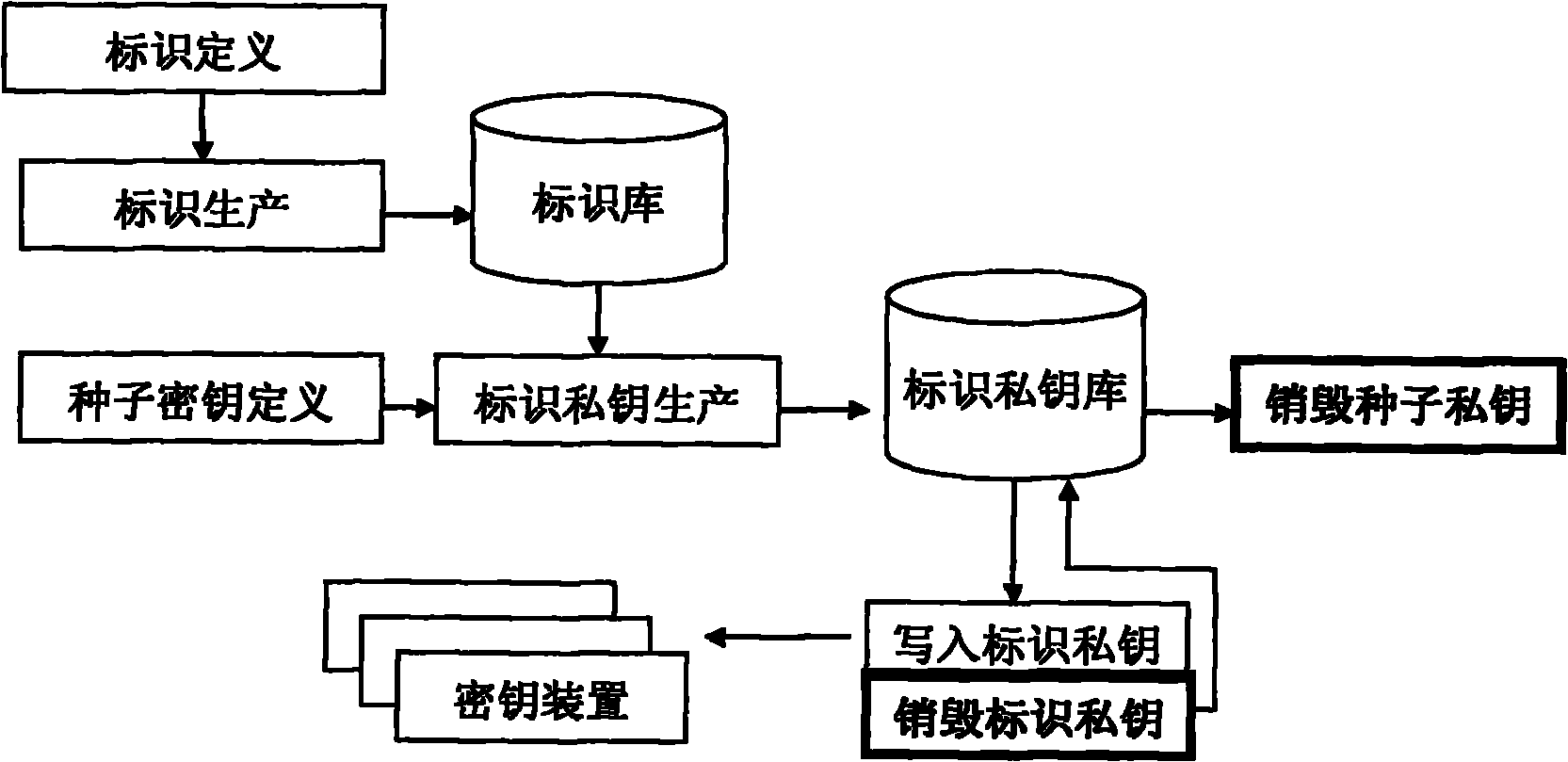
ActiveCN101958796ABreak through application bottlenecksEnable secure interactionsKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationAnonymous identifier
The invention provides identification authentication-based technology, and relates to secret key devices for supporting anonymous authentication. Identification secret keys generated by anonymous identifiers are stored in the secret key devices. The generation method of the secret key devices for supporting the anonymous authentication comprises the following steps of: defining and generating at least one anonymous identifier; defining a seed secret key pair, wherein the seed secret key pair consists of a seed public key and a seed private key; allowing the anonymous identifiers to generate identification private keys corresponding to the anonymous identifiers respectively through the seed private key; and writing the generated identification private keys into each secret key device. The invention also provides a back-up unlocking method of the dual secret key devices. The devices and the method can support requirements of social and publics on anonymous safety service, and reduce theapplication threshold of the authentication technology greatly.
Owner:北京联合智华微电子科技有限公司
Real-time frame authentication using ID anonymization in automotive networks
ActiveCN105745862ASynchronising transmission/receiving encryption devicesPublic key for secure communicationComputer networkData integrity
A real-time frame authentication protocol is presented for in-vehicle networks. A frame identifier is made anonymous to unauthorized entities but identifiable by the authorized entities. Anonymous identifiers are generated on a per-frame basis and embedded into each data frame transmitted by a sending ECU. Receiving ECUs use the anonymous identifiers to filter incoming data frames before verifying data integrity. Invalid data frame are filtered without requiring any additional run-time computations.
Owner:RGT UNIV OF MICHIGAN
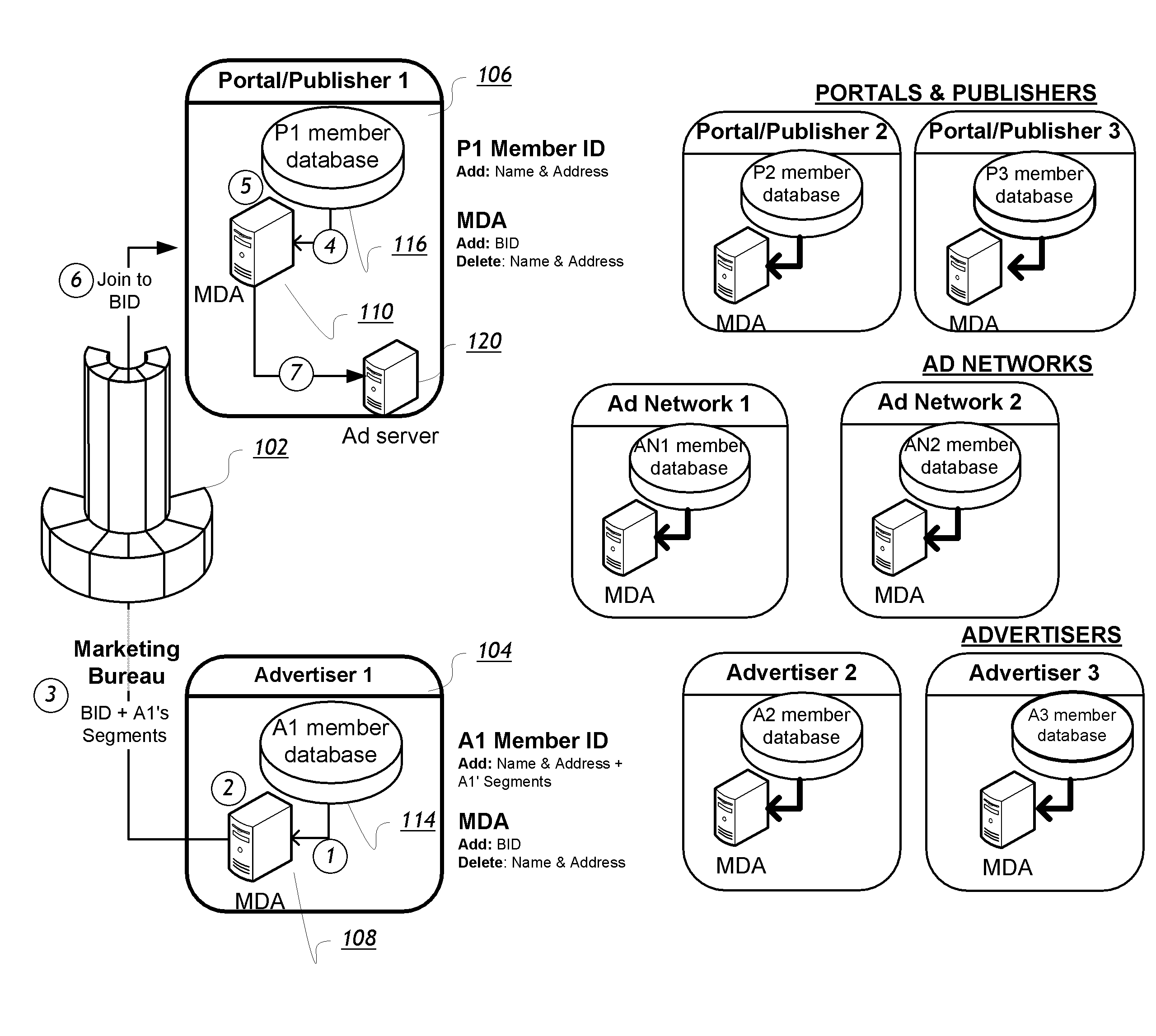
Method, system and apparatus for effecting targeted access to anonymous users of a network
InactiveUS20150095104A1Guaranteed privacy and securityComputer security arrangementsMarket data gatheringNetwork connectionWorld Wide Web
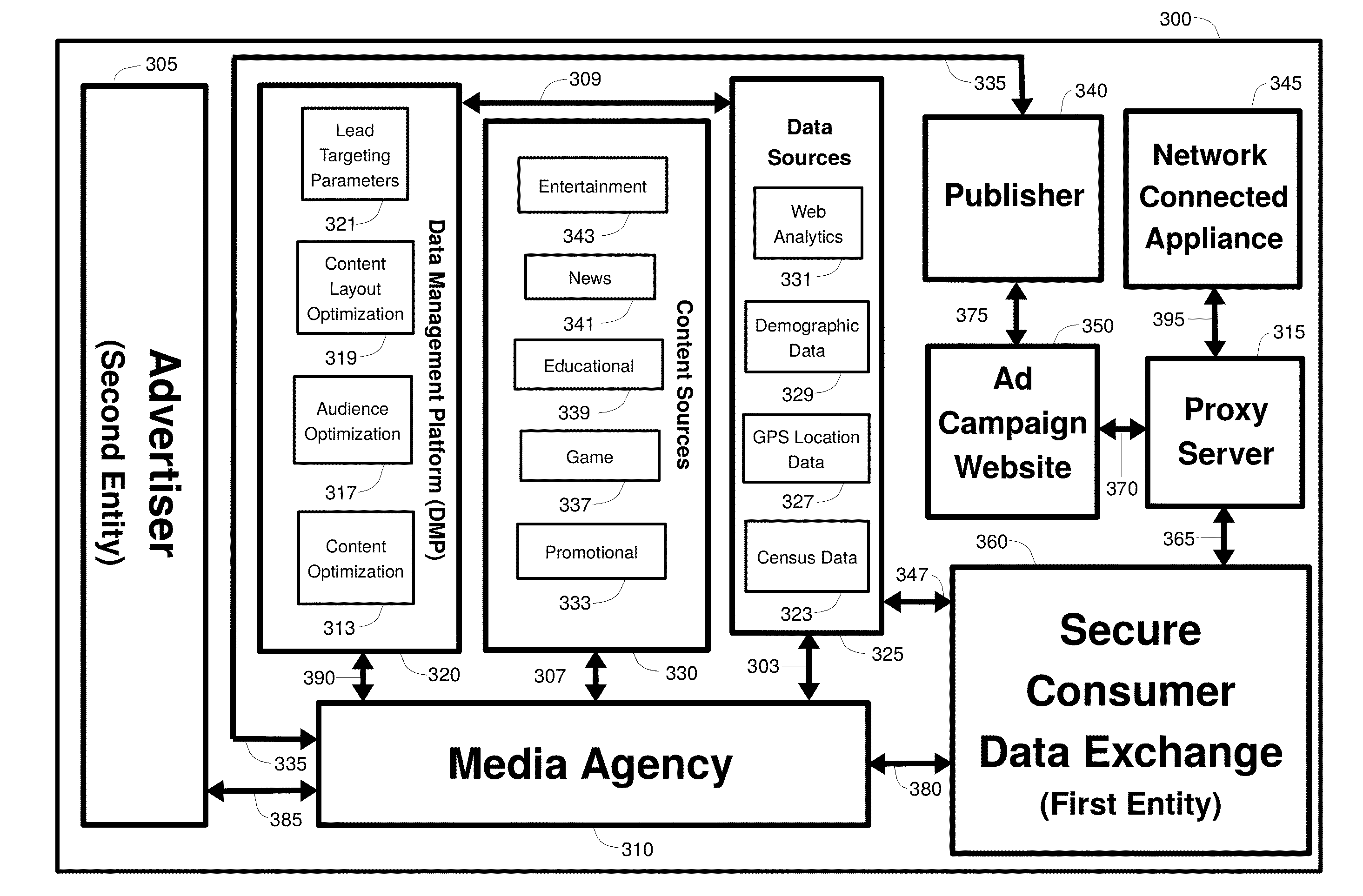
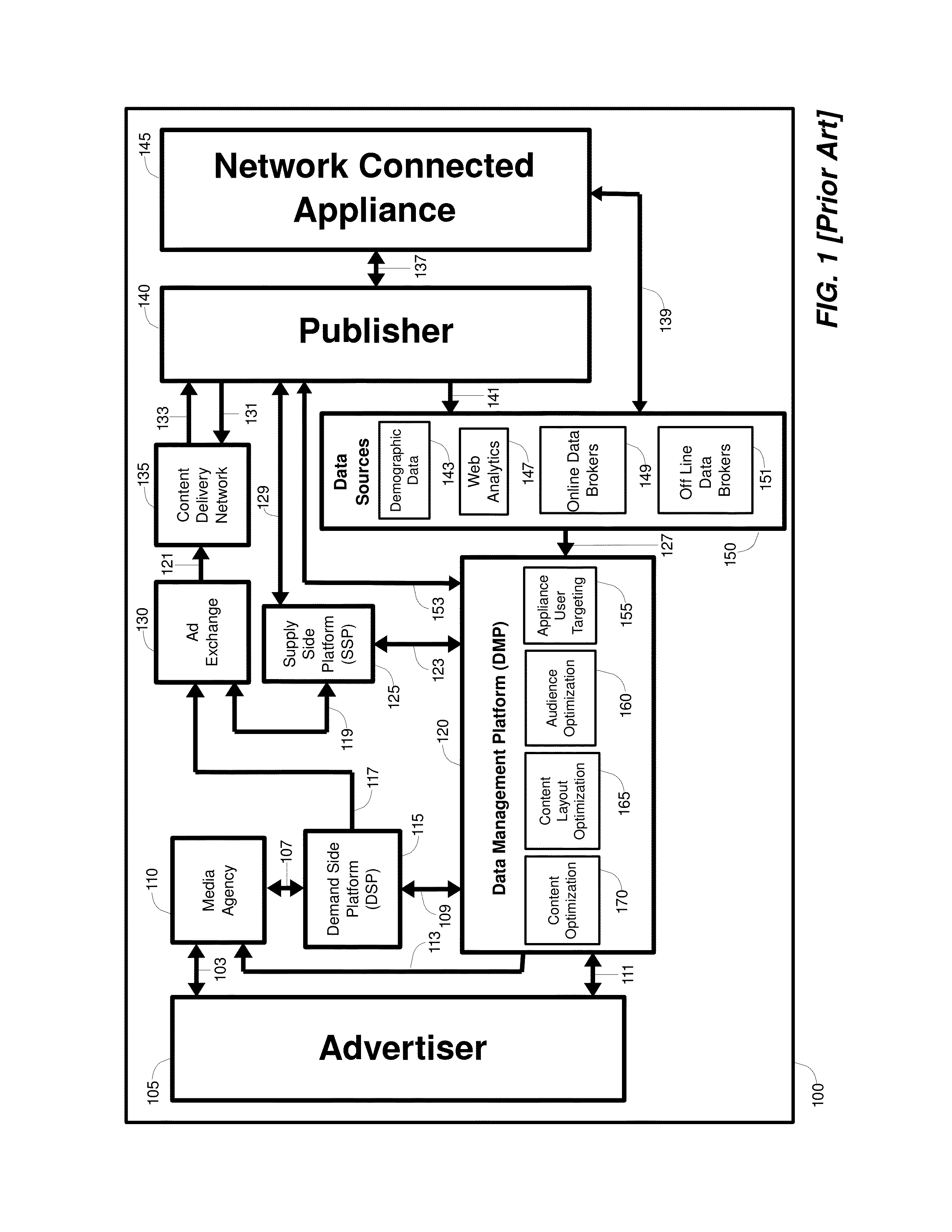
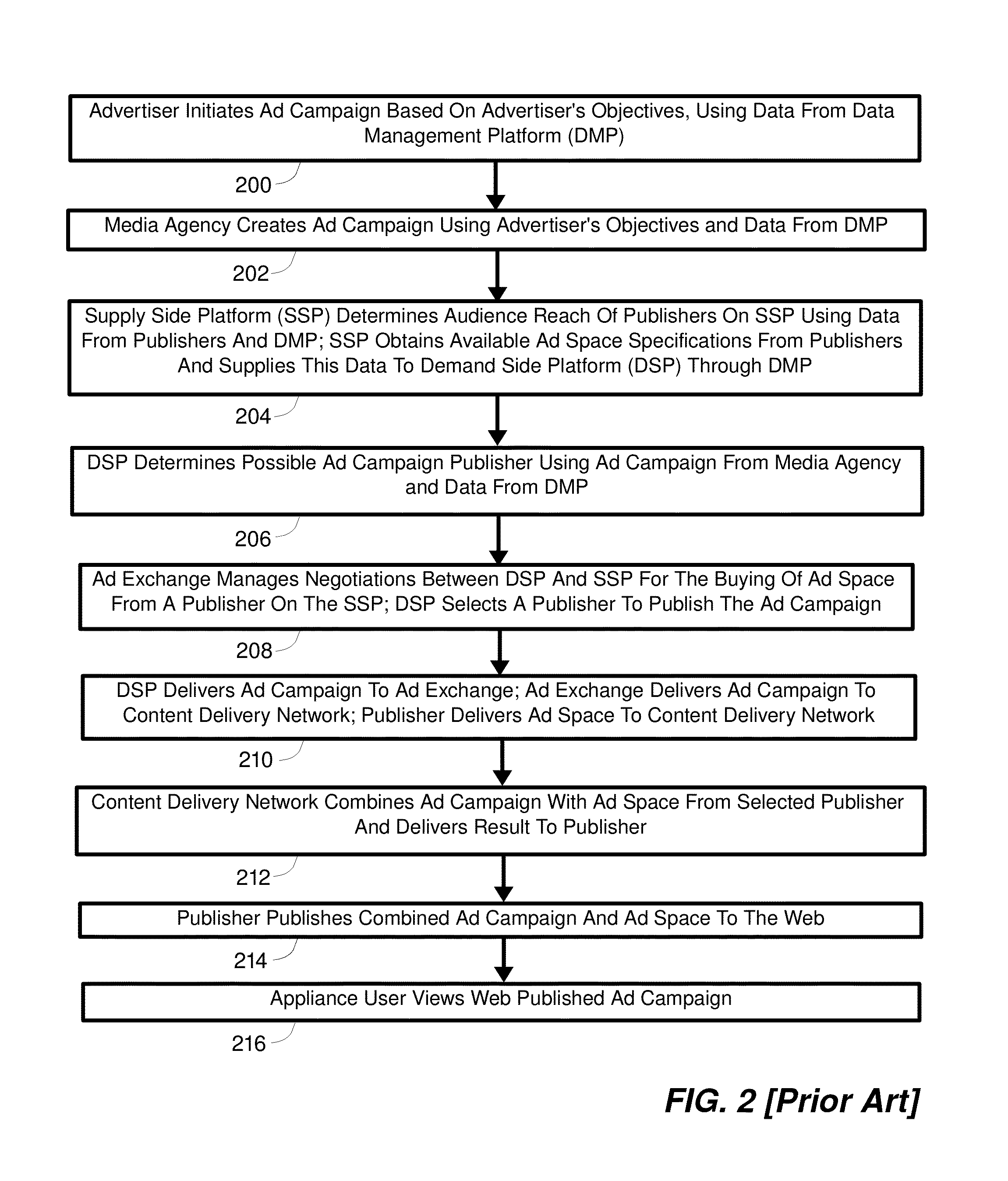
A method, system, and apparatus for effecting targeted access to anonymous users of a network is provided. A second entity delineates parameters of an audience with heightened interest in an offering, and a first entity provides the second entity with access to an audience accordant with these parameters. Consumer data collected by a network connected appliance used by an appliance user is linked with an appliance user anonymous identifier, and communicated to the first entity. Using the parameters, the first entity analyzes the collected consumer data and aggregates the appliance user's anonymous identifier with anonymous identifiers of other appliance users, thereby generating an aggregate set of anonymous identifiers that point to members of the audience. This set is marked with an identification code that is communicated to the second entity that can be used by the second entity to gain access to the audience through the first entity.
Owner:GOLDBERG PAUL R
Secure consumer data exchange method, apparatus, and system therfor
InactiveUS8799053B1Enhanced anonymityEasy to followDigital data protectionTransmissionNetwork connectionInternet privacy
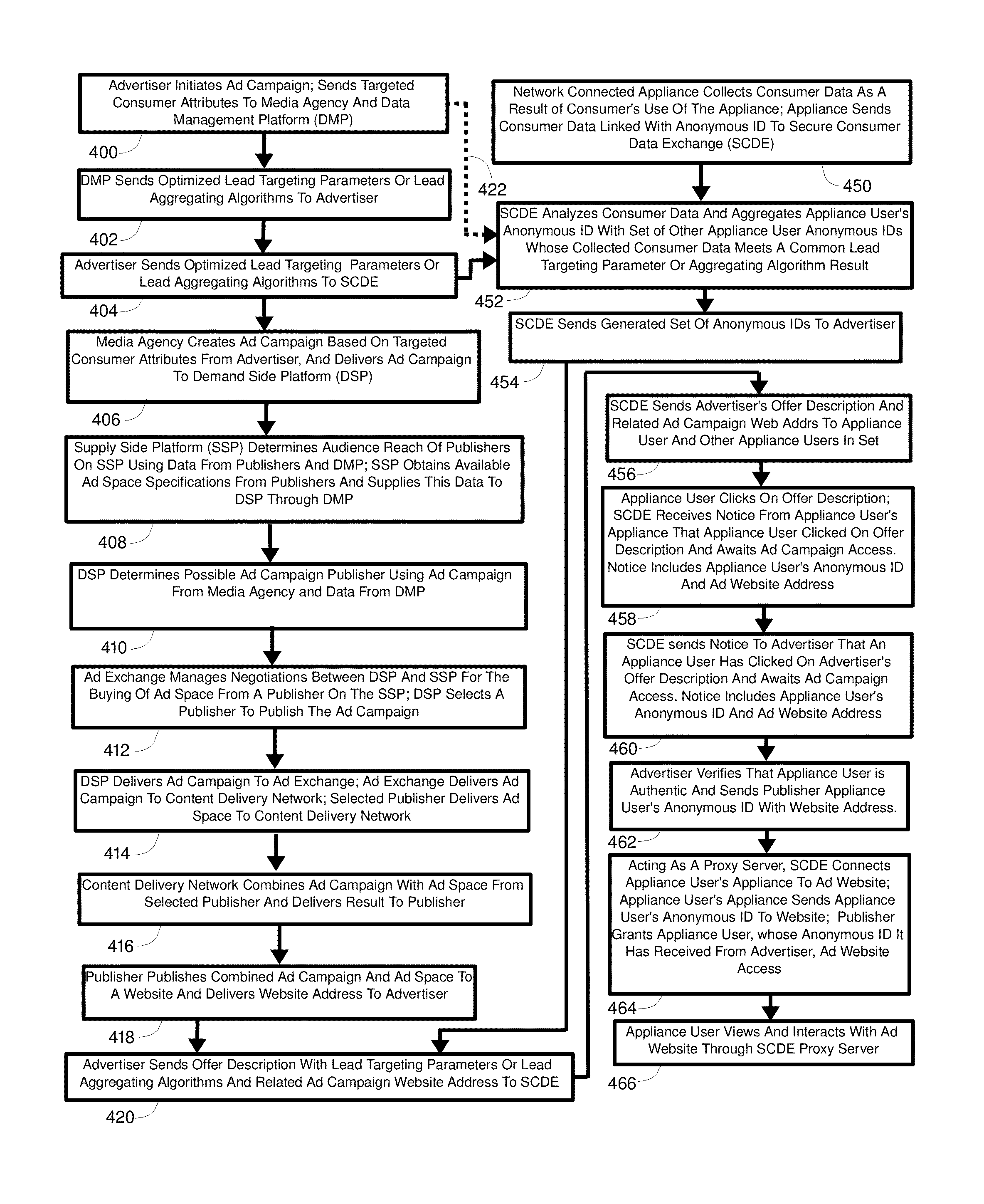
A method, system, and apparatus for consumer authorized collection and communication of consumer data, while facilitating compliance with government consumer privacy legislation and regulations, is provided. Authorization is obtained from a user of a network connected appliance to collect and communicate to other entities consumer data resulting from the user's use of the appliance. The data is encrypted, linked with an appliance user anonymous identifier and communicated to a first entity, where it is analyzed by the use of defined parameters. Based on this analysis, the anonymous identifier of the appliance user is aggregated with anonymous identifiers linked with the consumer data of other appliance users whose consumer data has at least one parameter in common with the consumer data of the appliance user. The aggregate set of anonymous identifiers is provisioned to a second entity by the first entity. Subsequent interaction with the first entity provides the second entity with access to the appliance user of the appliance without revealing the identity of the appliance user or providing access to the appliance user's consumer's data.
Owner:GOLDBERG PAUL R
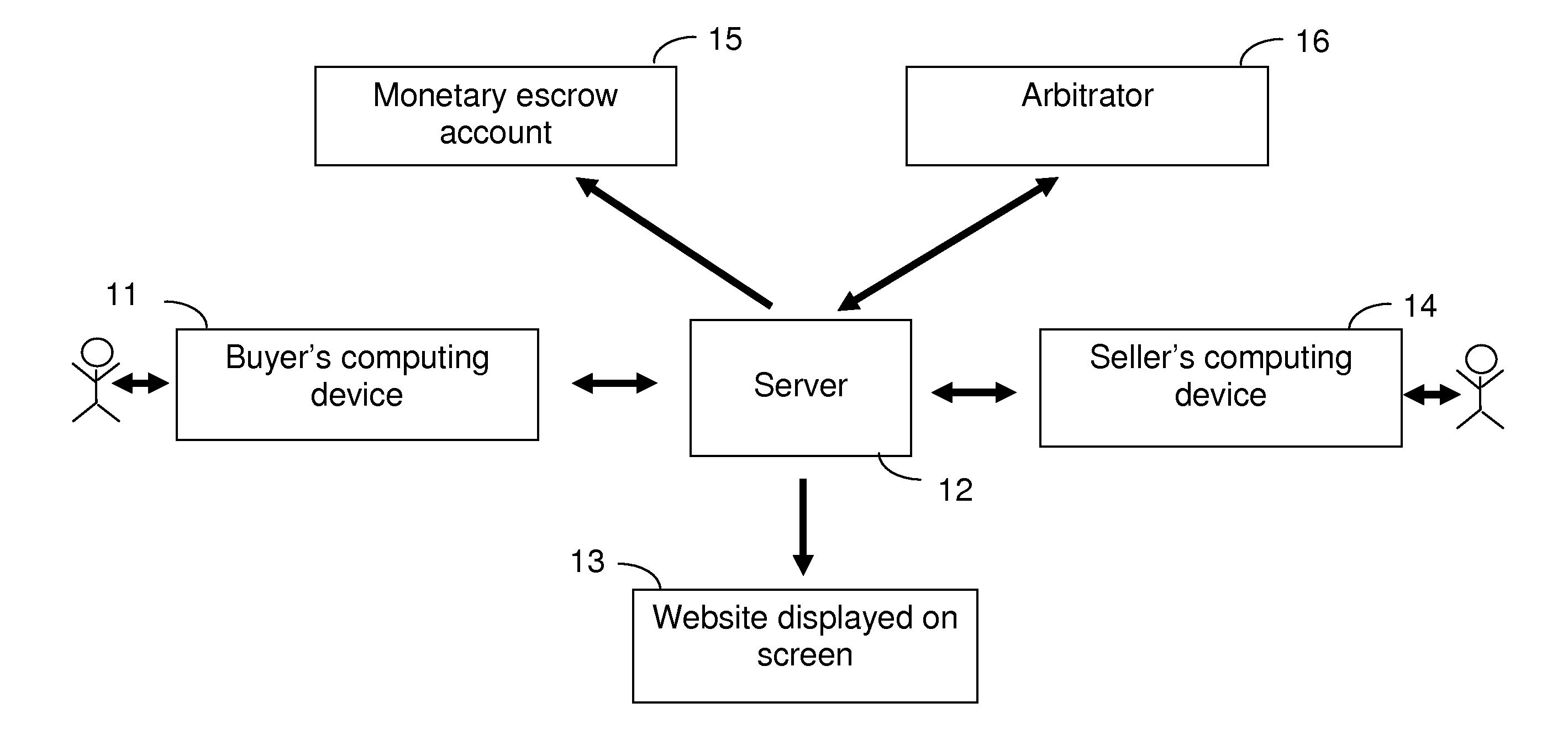
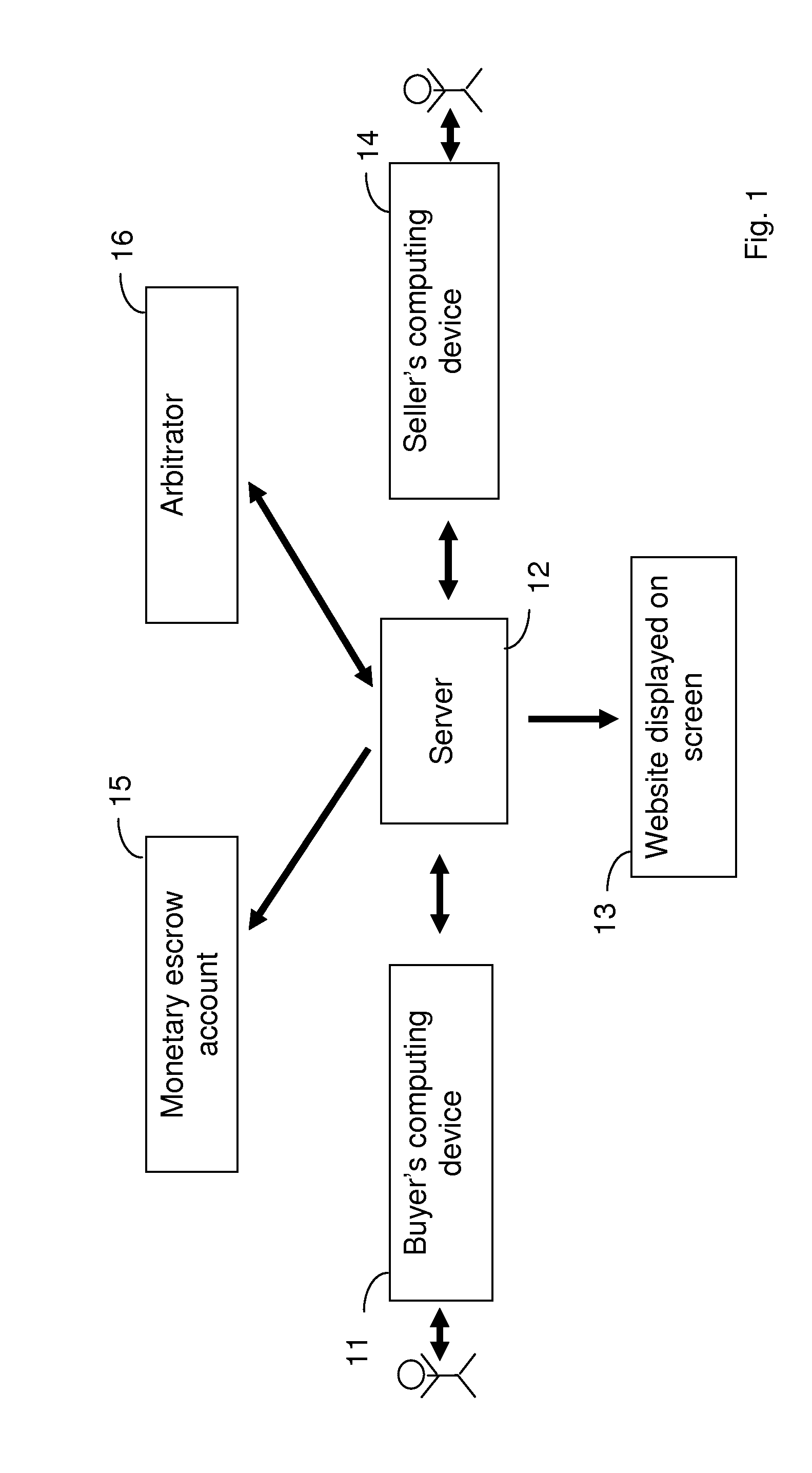
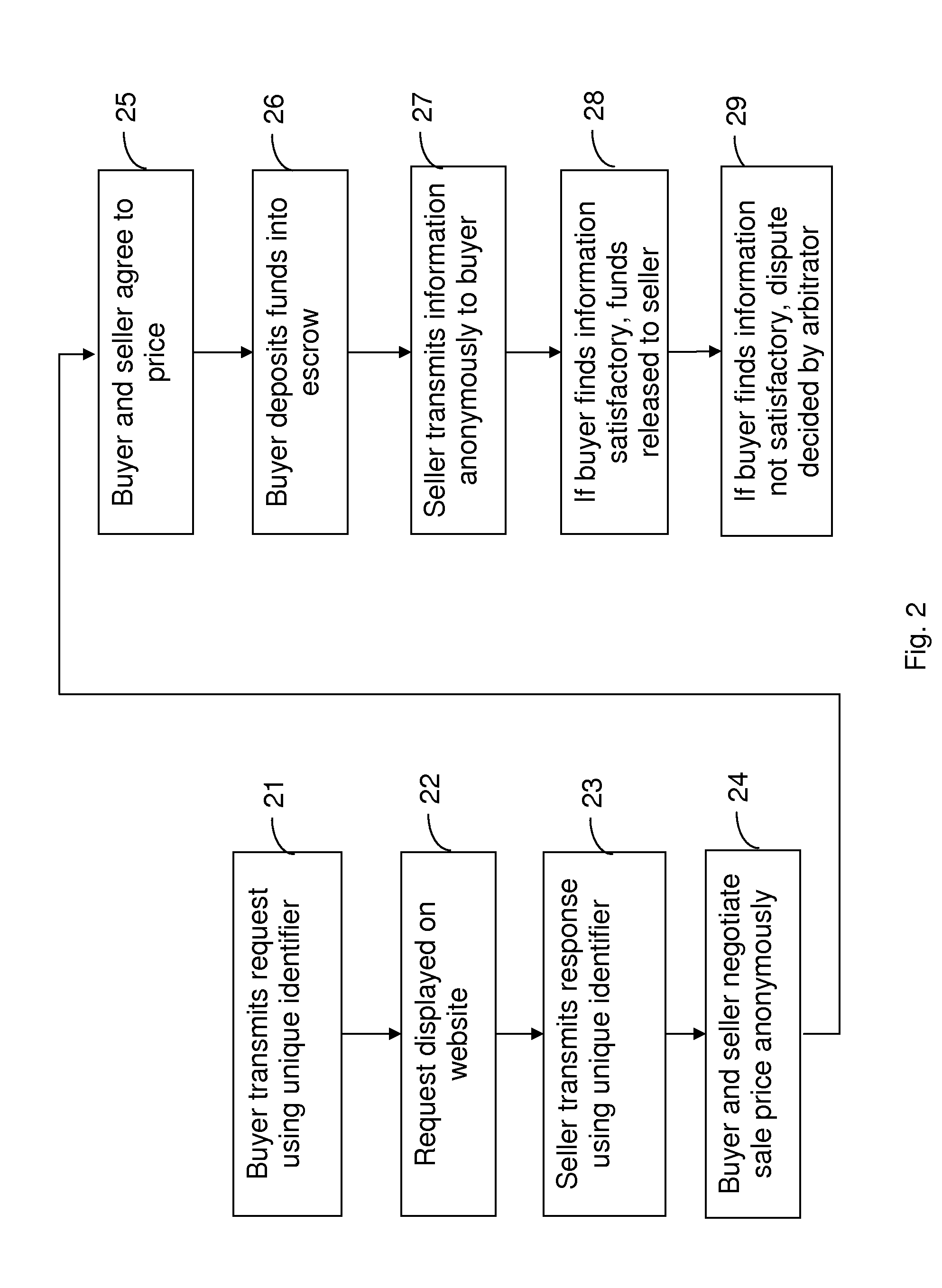
System for Anonymous Negotiated Sale of Information and Property
A system for executing a sale of information between a buyer and an anonymous seller. The buyer transmits a request for information to a website hosted by a server. A seller who has information transmits a response to the website indicating that the seller has relevant information to sell. The buyer and the seller negotiate anonymously through the server using unique, anonymous identifiers to agree to the price and content of the information.Upon agreement, the buyer deposits the payment in an escrow account. The seller is instructed to disclose information to the buyer through the anonymous relay system. The buyer reviews the information and, if satisfactory, transmits acceptance of it to the server. The server then instructs the escrow account to release the funds to the seller. If the information is not satisfactory, a third-party arbitrator decides whether the funds are released to the seller.
Owner:RAT OUT YOUR FRIENDS
Anonymous preservation of a relationship and its application in account system management
InactiveCN102509030AImprove protectionRestoration of ownershipUser identity/authority verificationDigital data authenticationHash functionInternet privacy
Disclosed is a system or method of using hash functions to preserve a relationship. A relationship is anonymously preserved by storing the hash result of a relationship token that comprises a finite set of values of a plurality of objects. Specifically, an account anonymous identifier of an account can be produced by hashing a relationship token that comprises identity information of an owner of said account. A party that has enough knowledge of an account owner can independently produces said account anonymous identifier and therefore, securely communicates with a specific account without prior communication or a password. An account owner can further prove his / her ownership of an account by submitting related documents and a relationship token that comprises his / her identity information to an account system.
Owner:郭敏 +1
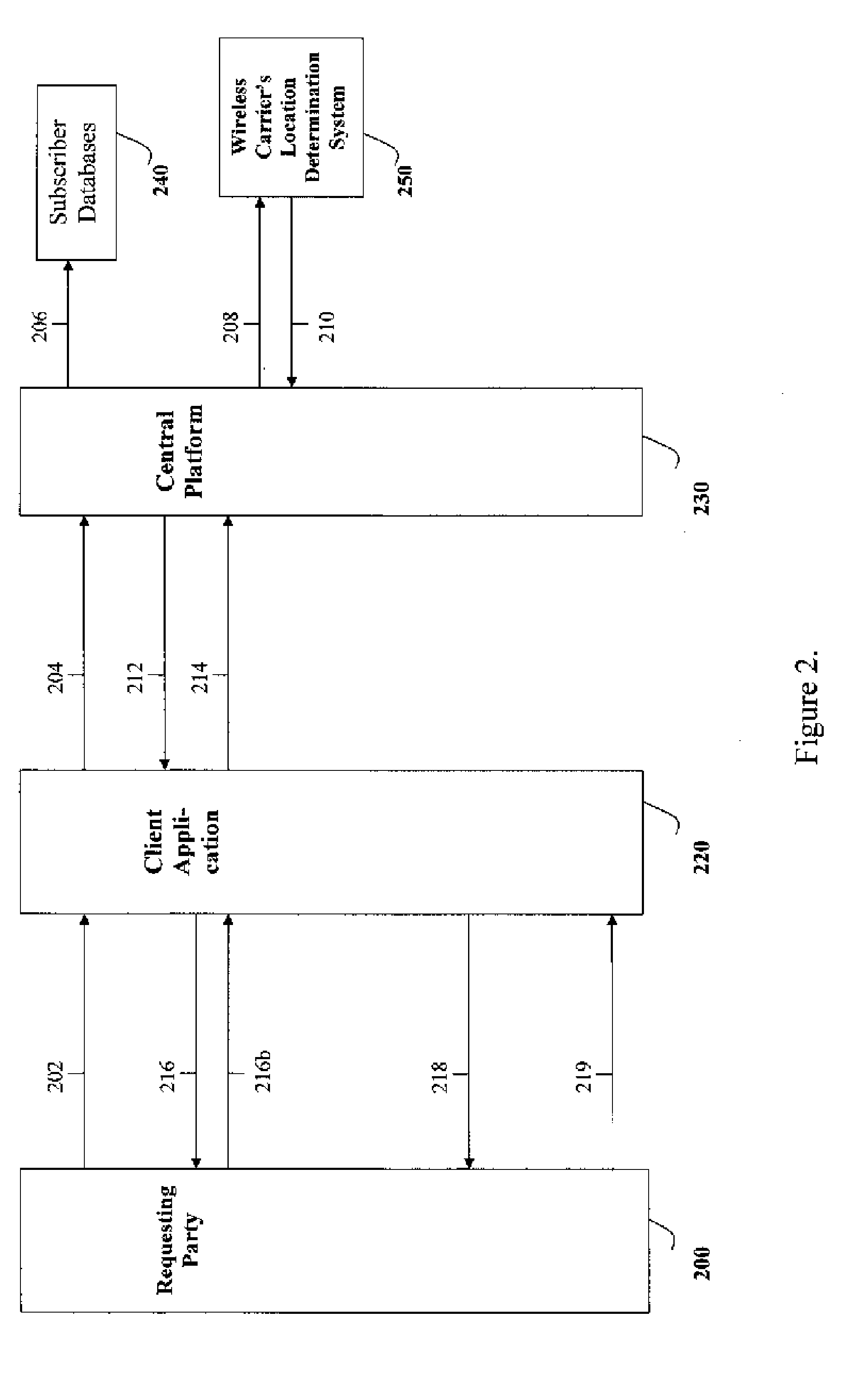
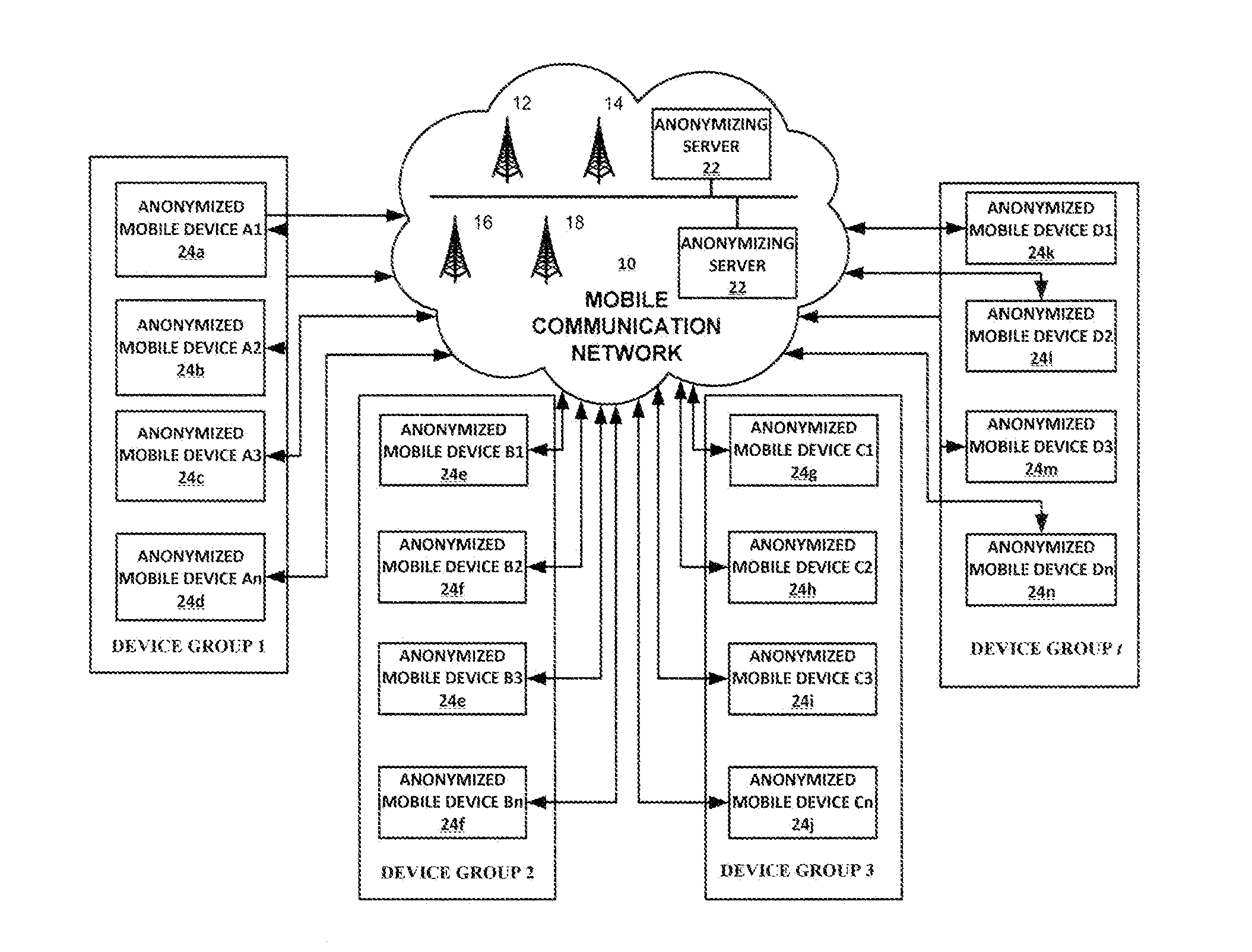
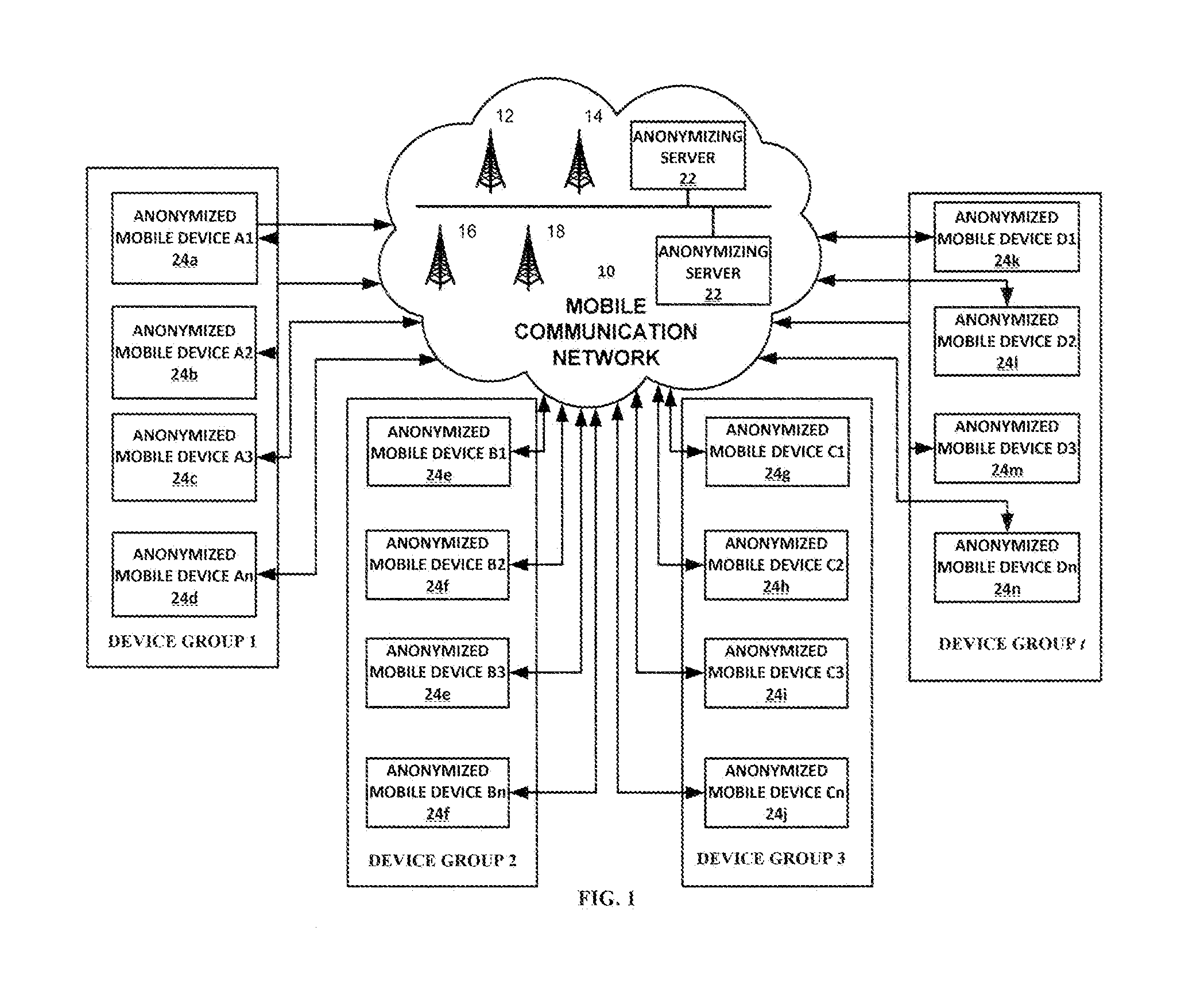
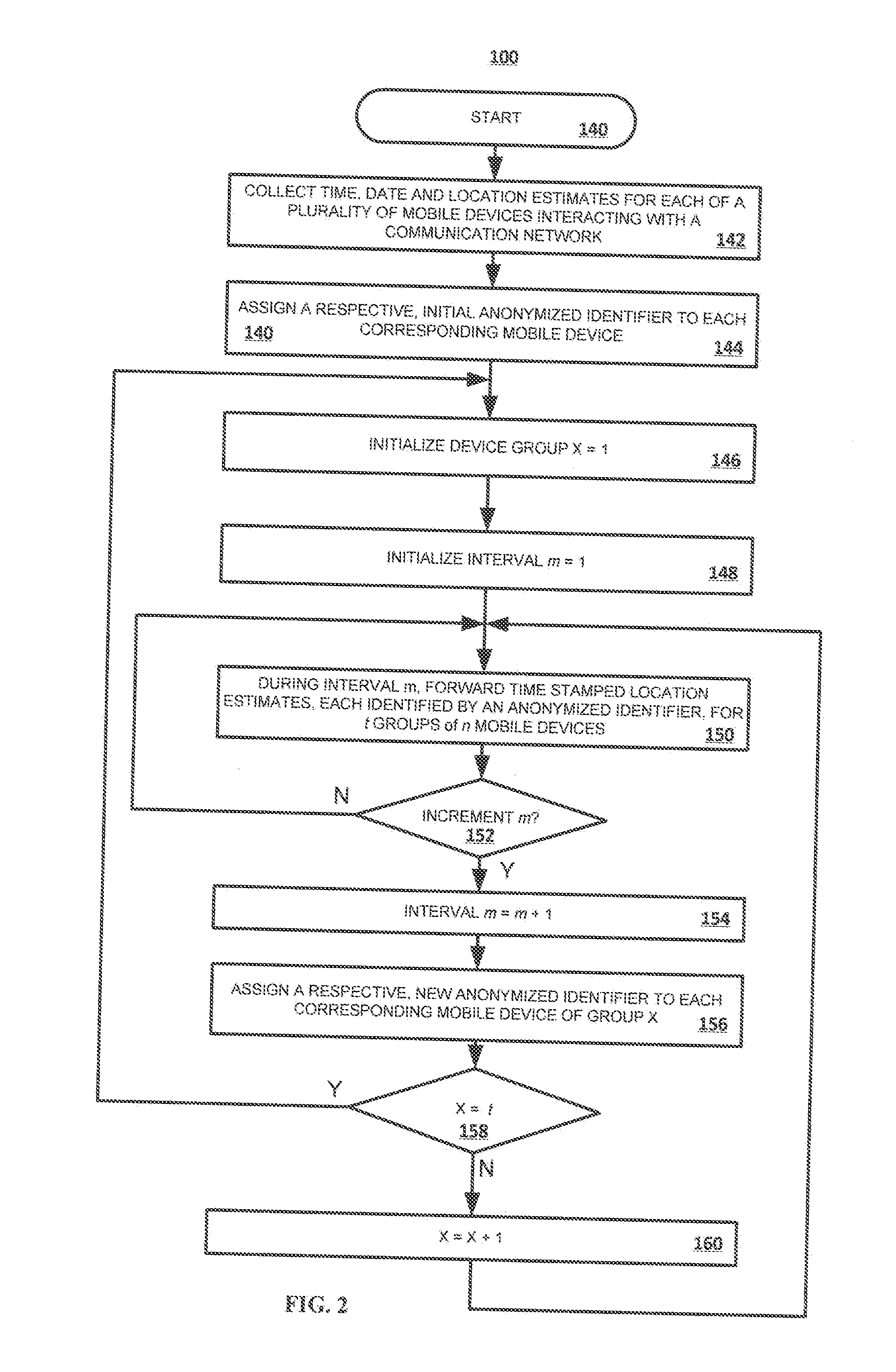
Methods, Systems and Apparatus for Estimating the Number and Profile of Persons in a Defined Area Over Time
A passive measuring technique and system processes and analyzes imprecisely reported location estimates collected from a plurality of mobile devices. The number and socio-demographic composition of persons within defined areas of interest are estimated over time. Each mobile device is assigned to a group and identified by an anonymized identifier, and the identifiers of devices within each group are refreshed on a rolling basis to further enhance privacy. A statistical weighting approach is applied so that each device represents a fraction of the population and socio-demographic profile of one or more segmentation districts. Users requesting a defined area of interest via a communication network receive an estimate—derived by modeling respectively anonymized mobile devices within an area of interest over a selectable time period as corresponding, statistically weighted devices—of the number and socio-demographic profile of all persons within the area of interest over the selectable time period.
Owner:WAGENSEIL HENDRIK +2
Patient community system with anonymized electronic medical data
ActiveUS10096075B2Enhance information sharingImprove the level ofMedical communicationMedical data miningMedical recordCommunity system
A computerized system allows intercommunication of patients with respect to the treatment of their diseases. This system includes an electronic medical record database providing electronic medical records of a given set of patients as developed by healthcare professionals and linked to an anonymous identifier for each patient and a set of terminal devices accessible to the patients allowing for the electronic exchange of information through a display and data input device. A server system connects the anonymous medical record database and the terminal devices and executes a stored program to: (1) allow an authenticated connection by a given patient to the server system through a terminal device and associate the connection with an anonymous identifier; (2) permit authoring by the given patient of a patient site viewable on a terminal device incorporating medical records from the anonymous medical record database associated with the anonymous identifier; and (3) identify to the given patient other patient sites for other patients having shared medical conditions according to a predetermined clustering of data of the anonymous medical record database.
Owner:EPIC SYST CORP (US)
Method and apparatus for providing exchange of profile information
An approach for providing an exchange of profile information by using anonymous identifiers is described. An information exchange platform may select one of a plurality of device identifiers specific to corresponding one or more devices. The information exchange platform may also cause, at least in part, a transmission of the selected device identifier to another device separate from the one or more devices. Further, the plurality of device identifiers may be associated with one or more user profiles.
Owner:SEREBOFF AARON
Method for managing anonymous communication between users according to short-distance wireless connection identifier
In network equipment (1) of a communication network (100), a method for managing anonymous communication between users according to a short-distance wireless connection identifier comprises the following steps of: a) receiving data which indicate that the short distance wireless connection between first mobile user equipment (120) and second mobile user equipment (120) is established from the first mobile user equipment (120) through a first network connection, wherein the data comprises a second unique short-distance wireless connection identifier associated with the second mobile user equipment (120) and a message for the second mobile user equipment (120); b) acquiring a network address associated with the second mobile user equipment (120) through using the second unique short-distance wireless connection identifier; and c) sending the data to the second mobile user equipment (120) through a second network connection through the network address acquired in the step b), wherein thedata comprises a message received from the first mobile user equipment (120) in the step a) and a first anonymous identifier singly associated with the first mobile user equipment (120).
Owner:TELECOM ITALIA SPA
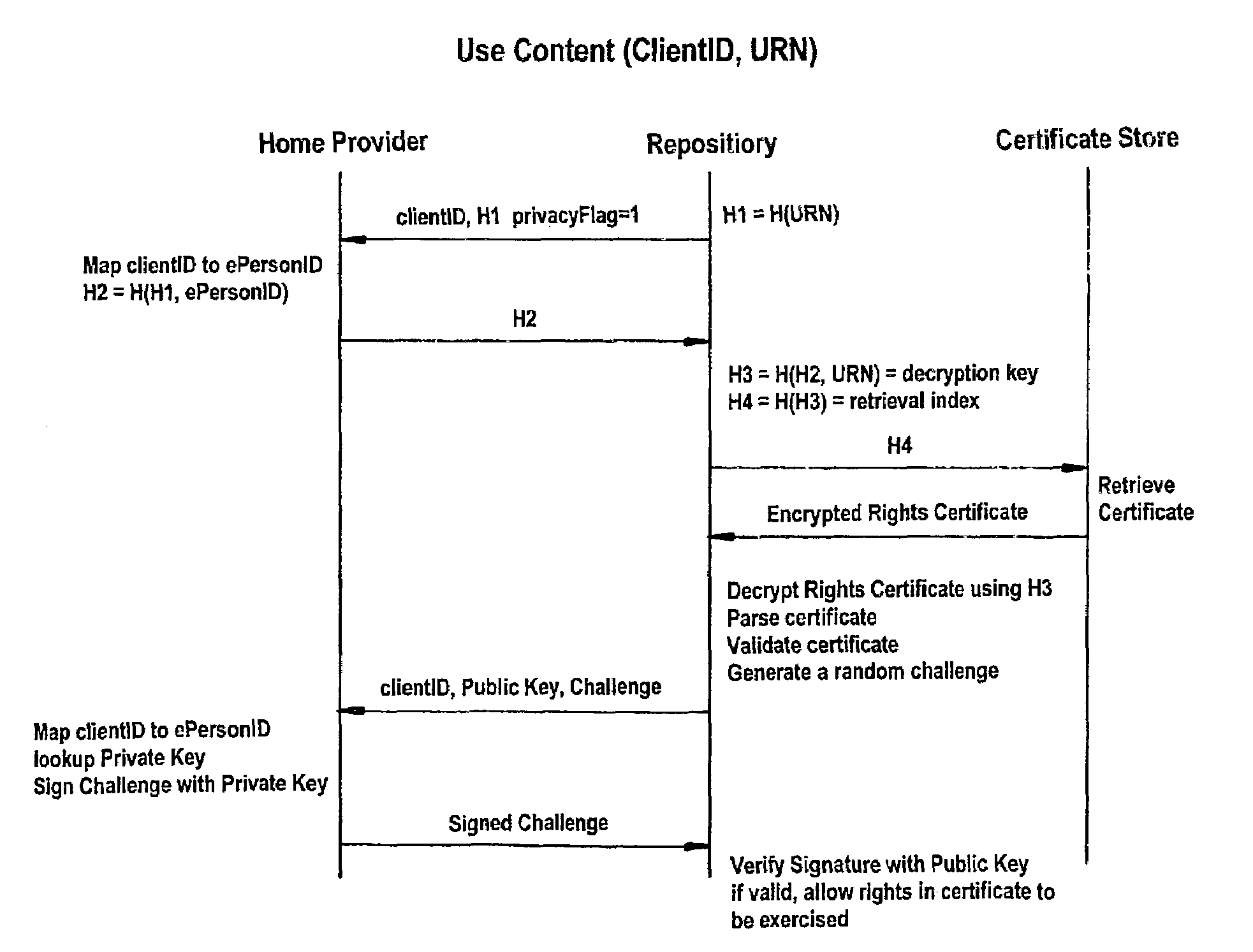
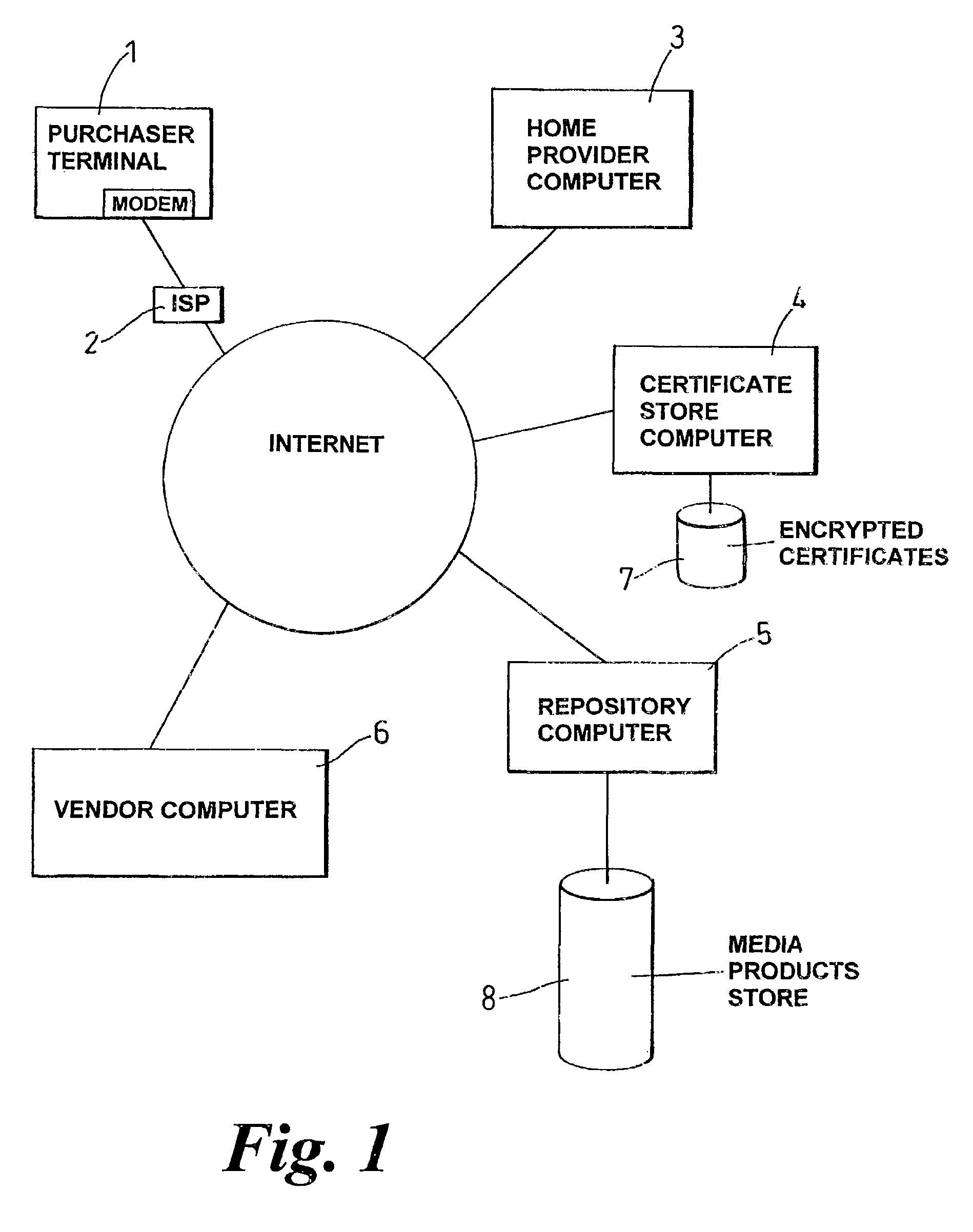
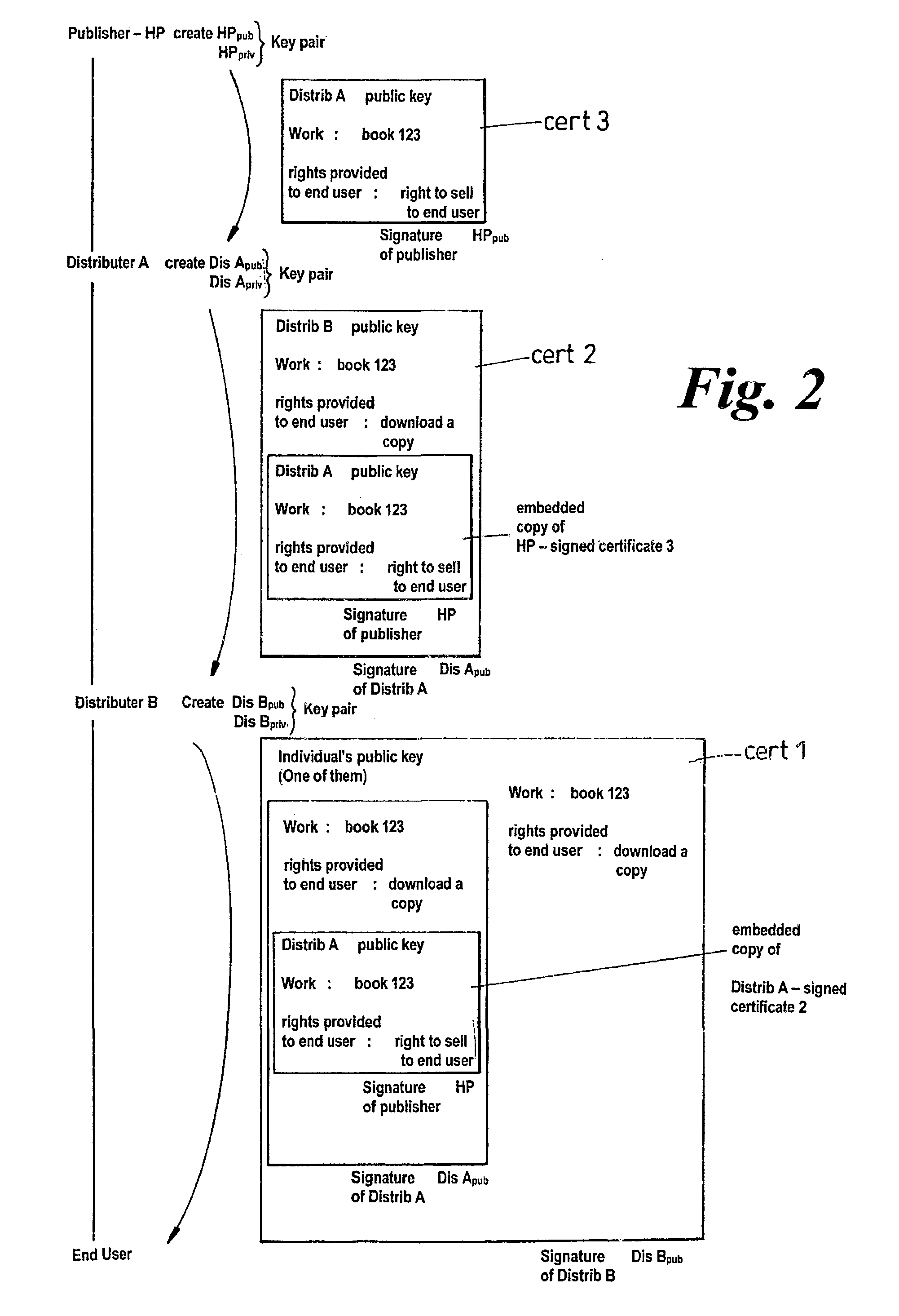
Method and system for controlling the on-line supply of digital products or the access to on-line services
The invention is concerned with enabling substantially anonymous purchases of media products or other products (or access to an on-line service) to be made on-line. In order to initiate a purchasing session, consisting of one or more purchasing transactions, the purchaser authenticates himself to a home provider computer (3) which ten allots an anonymous client identifier (clientID) to the client for the purposes of that session. The purchaser (1) contacts a vendor computer (6), using the anonymous identifier (clientID) and an anonymising HTTP proxy, in order to place an order for one or more products or services for which the vendor computer has the right to authorize delivery. In order to obtain delivery of the product or service from the repository computer (5), the purchaser (1) provides the clientID to the repository computer (3).
Owner:HEWLETT PACKARD DEV CO LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com