A mapping method of a file system access control list
An access control list, file system technology, applied in the storage field, can solve problems such as normal access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
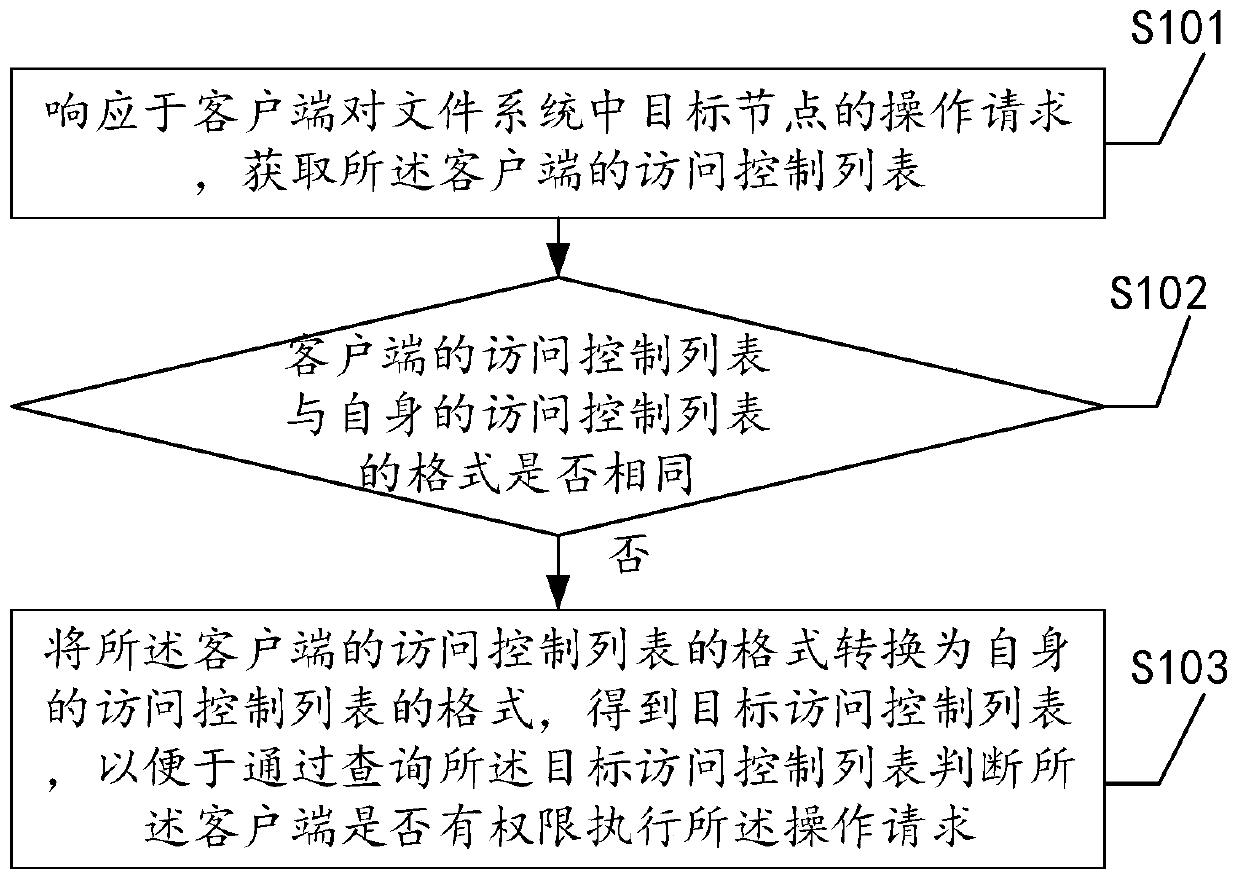
[0039] The following introduces Embodiment 1 of a mapping method for a file system access control list provided by the present invention. Embodiment 1 is applied to a file server, see figure 1 , embodiment one includes:
[0040] Step S101: Obtain an access control list of the client in response to the client's operation request on the target node in the file system.
[0041] The file system is the method and data structure used by the operating system to identify files on the disk or partition. Generally, the organizational structure of the file system is a tree structure, in which each node is a file or a directory. In the file system The file or directory of the may be the object to be accessed, therefore, the above target node is a certain file or a certain directory.
[0042] The access control list (Access Control List, referred to as ACL) contains the permission information of a certain node. The access control list is a list of fine-grained access permissions for speci...
Embodiment approach
[0095] As an optional implementation, the device also includes:
[0096] Storage module 504: configured to store the target ACL, and store the correspondence between the target ACL and the client.
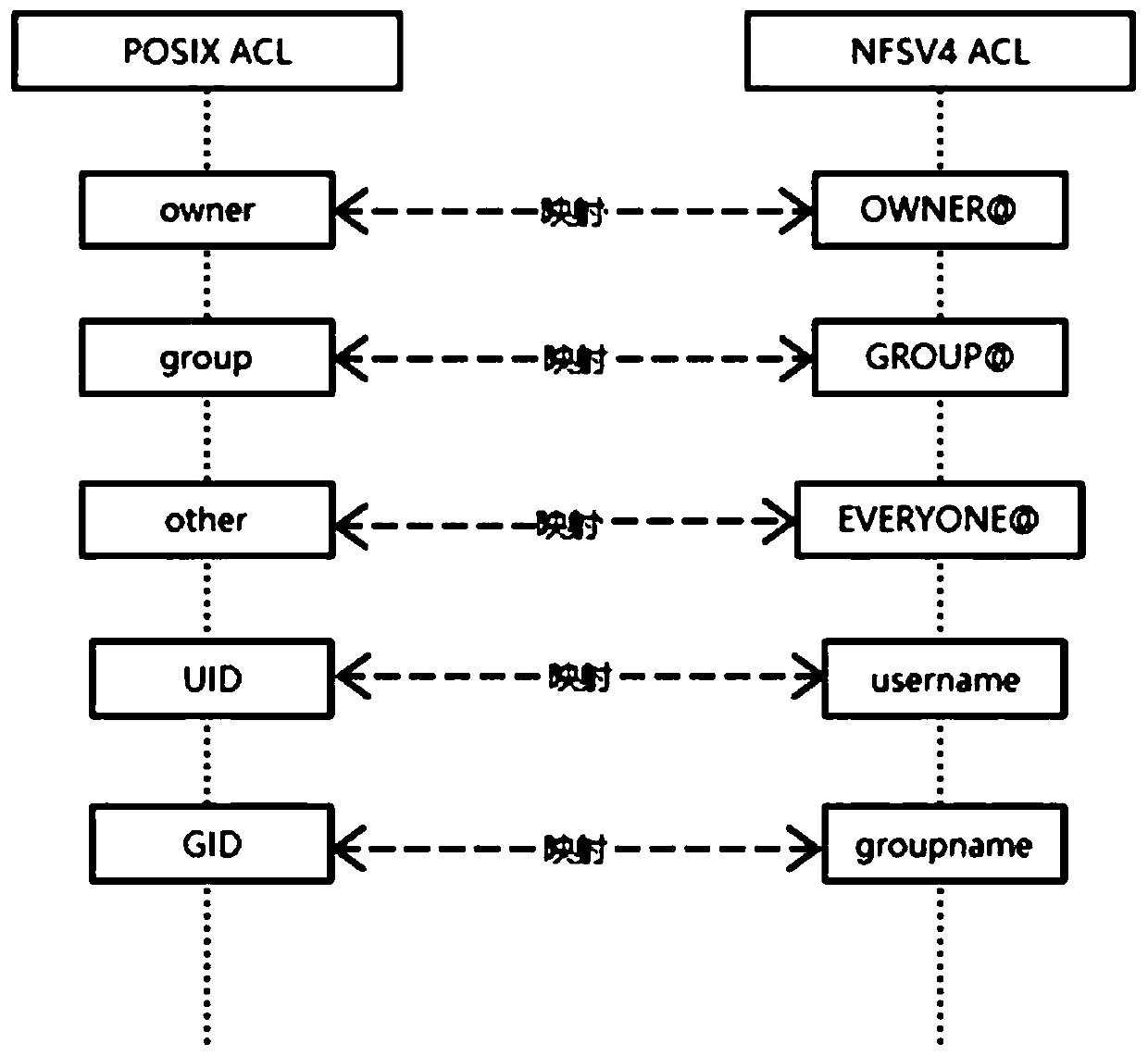
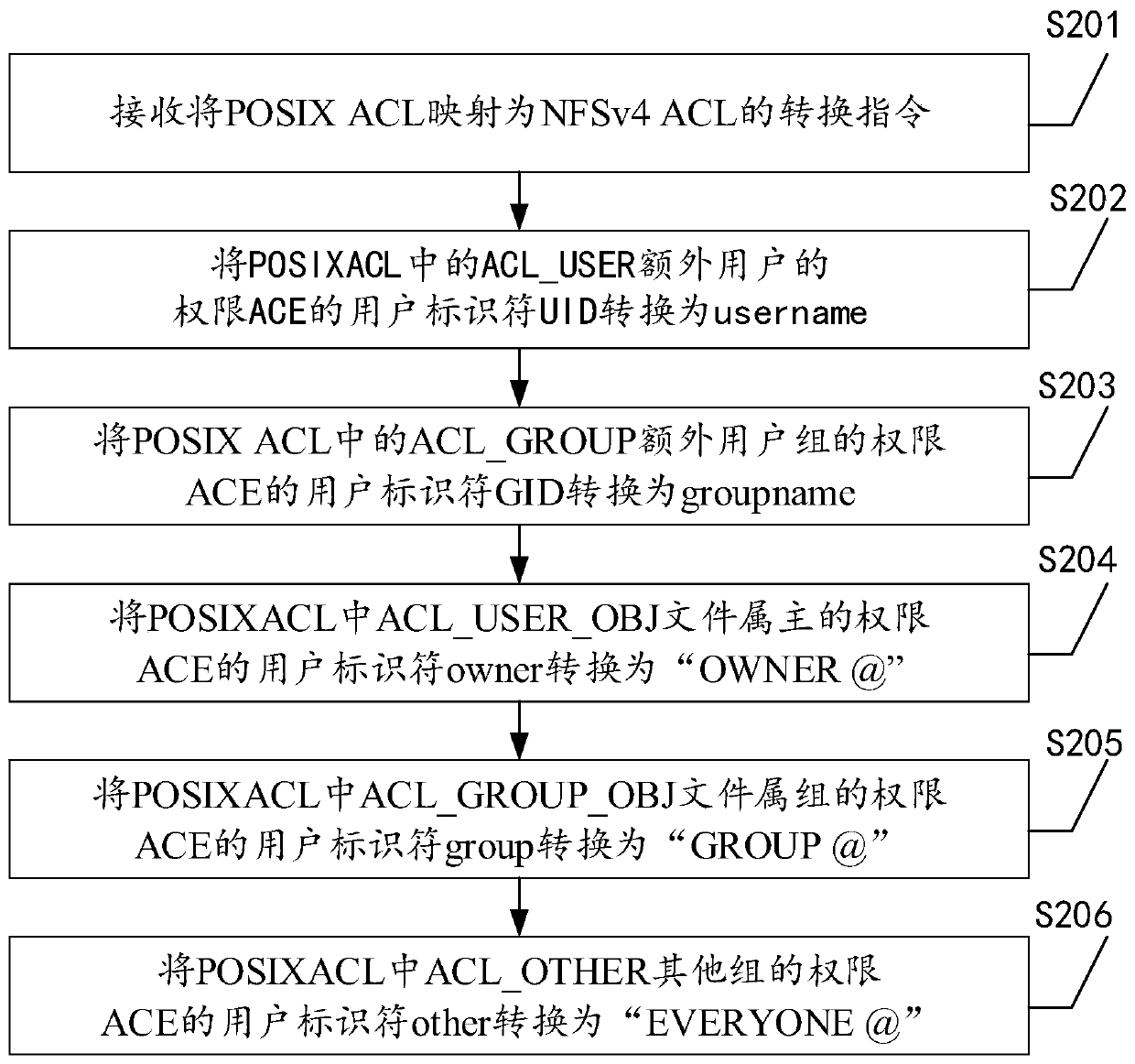
[0097] As an optional implementation manner, the format of the access control list includes: POSIX ACL and / or NFSv4ACL.
[0098] The device for mapping a file system access control list in this embodiment is used to implement the above-mentioned method for mapping a file system access control list, so the specific implementation of the device can be seen in the preceding file system access control list The embodiment part of the mapping method, for example, the obtaining module 501, the judging module 502, and the converting module 503 are respectively used to implement steps S101, S102, and S103 in the above-mentioned method for mapping a file system access control list. Therefore, for the specific implementation manners thereof, reference may be made to the descriptions of the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com