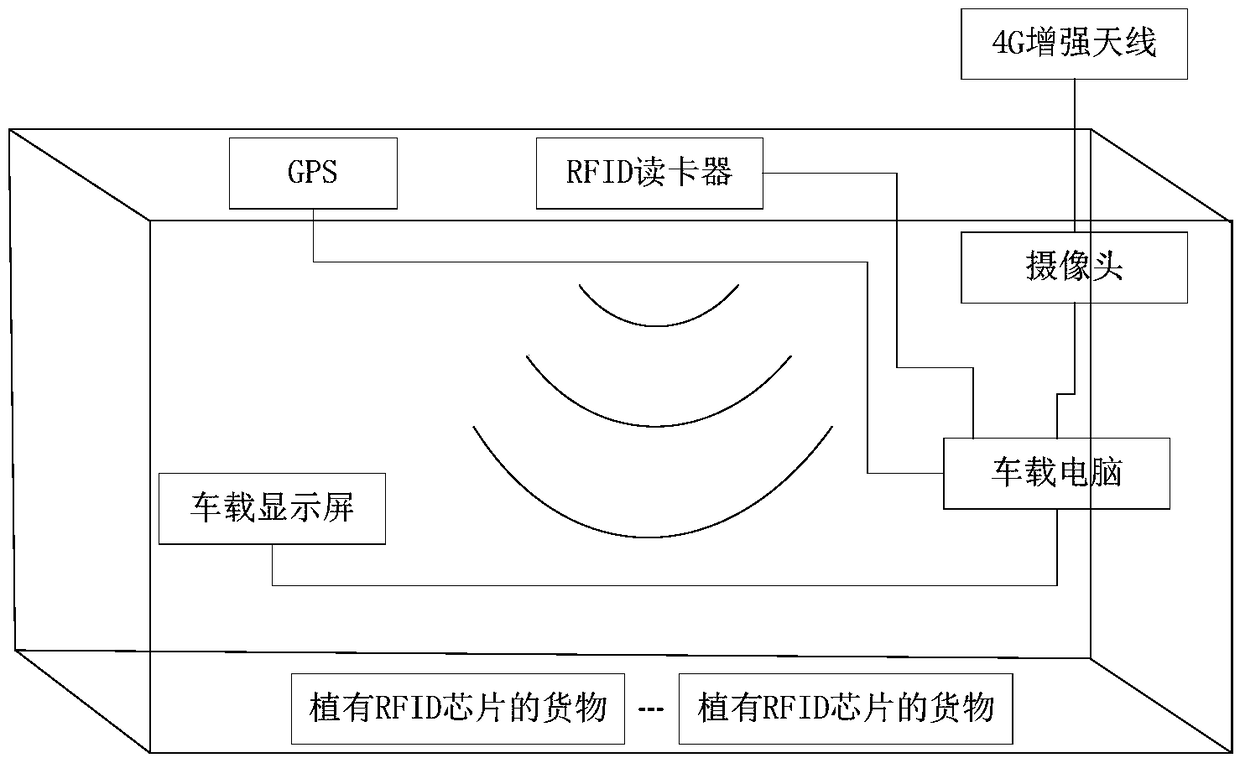
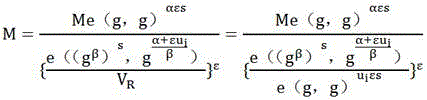
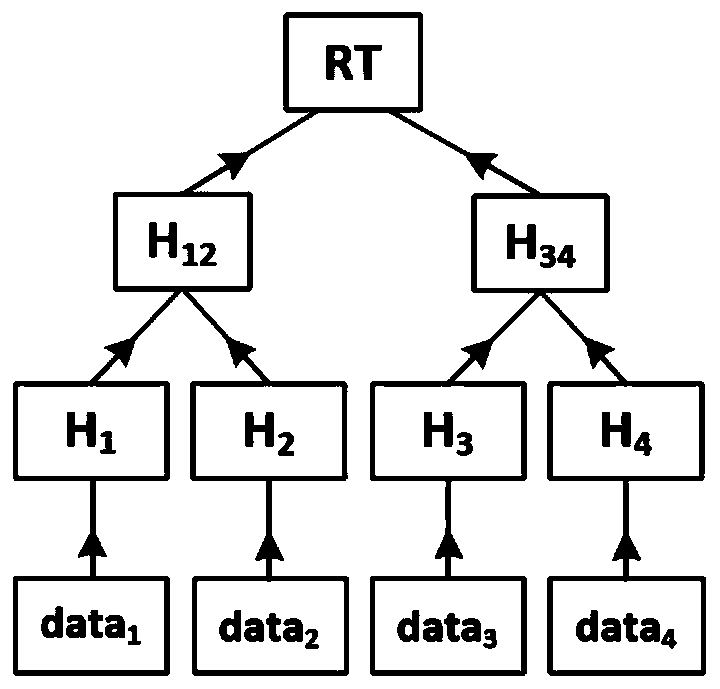
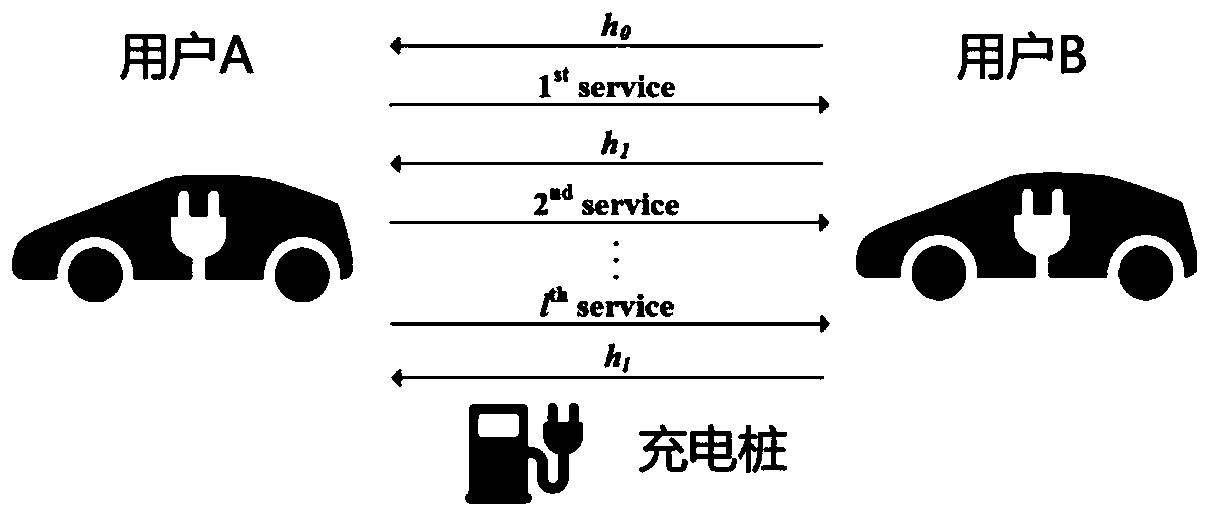
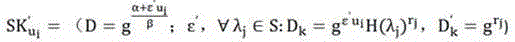Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
134results about How to "Resolve trust issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
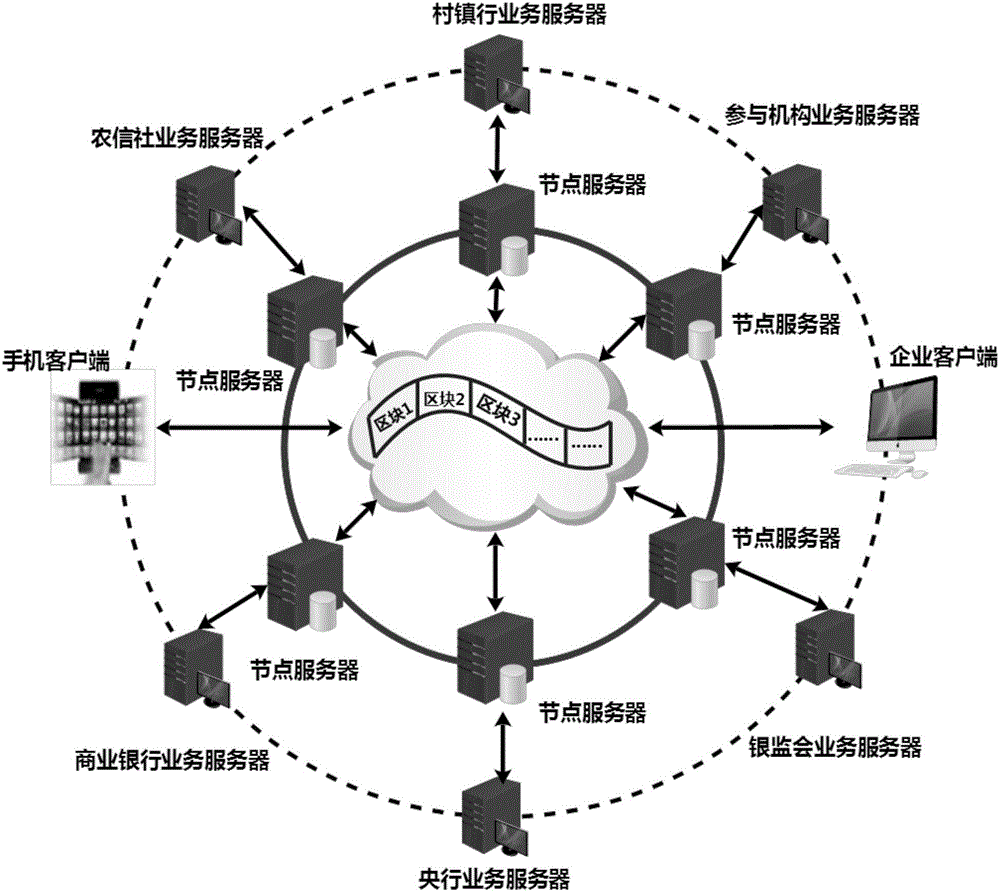
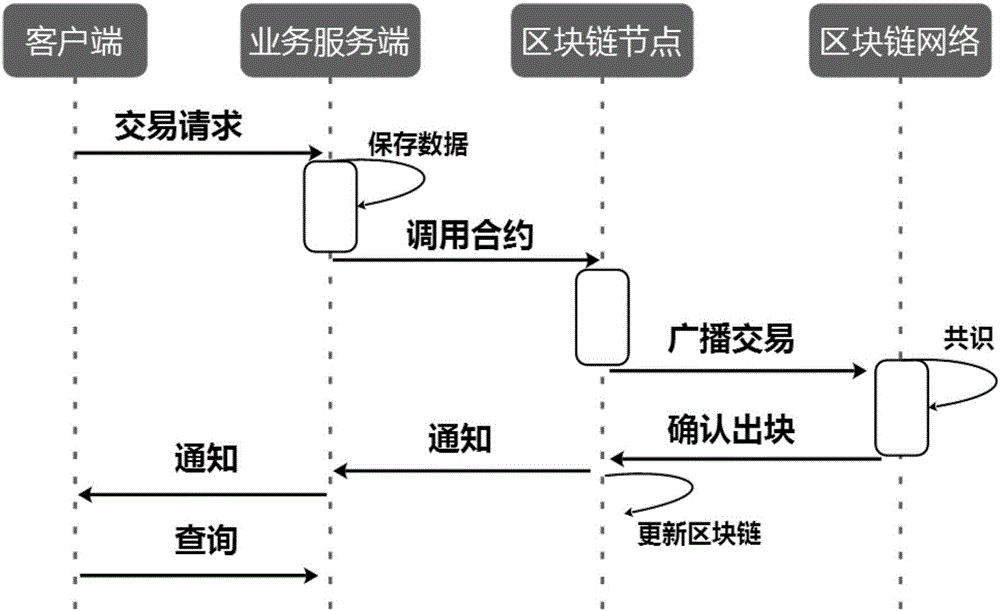
Consortium chain-based digital bill trading system construction method
InactiveCN106780033AImprove safety and reliabilityAvoid reconciliation workFinanceTechnical supportBlockchain
The invention discloses a consortium chain-based digital bill trading system construction method, which develops a brand-new bill display form, namely, a digital bill in combination with existing bill attributes, laws and regulations and market by taking a consortium chain as technical support. Compared with an existing electronic bill, the digital bill is totally different from the electronic bill in technical framework, not only has all functions and advantages of the electronic bill but also fuses the advantages of a block chain technology, and is a securer, more intelligent, more convenient and more promising bill form. In addition, the block chain technology is applied to the field of bill businesses for the first time; a unified standard bill trading platform is established; the problems of trade background forgery, bill authenticity authentication failure, paper bill multi-time selling, non-synchronous electronic bill discounting and bill endorsing, and the like are solved; and various risks are effectively managed, controlled and prevented.
Owner:HANGZHOU YUNXIANG NETWORK TECH
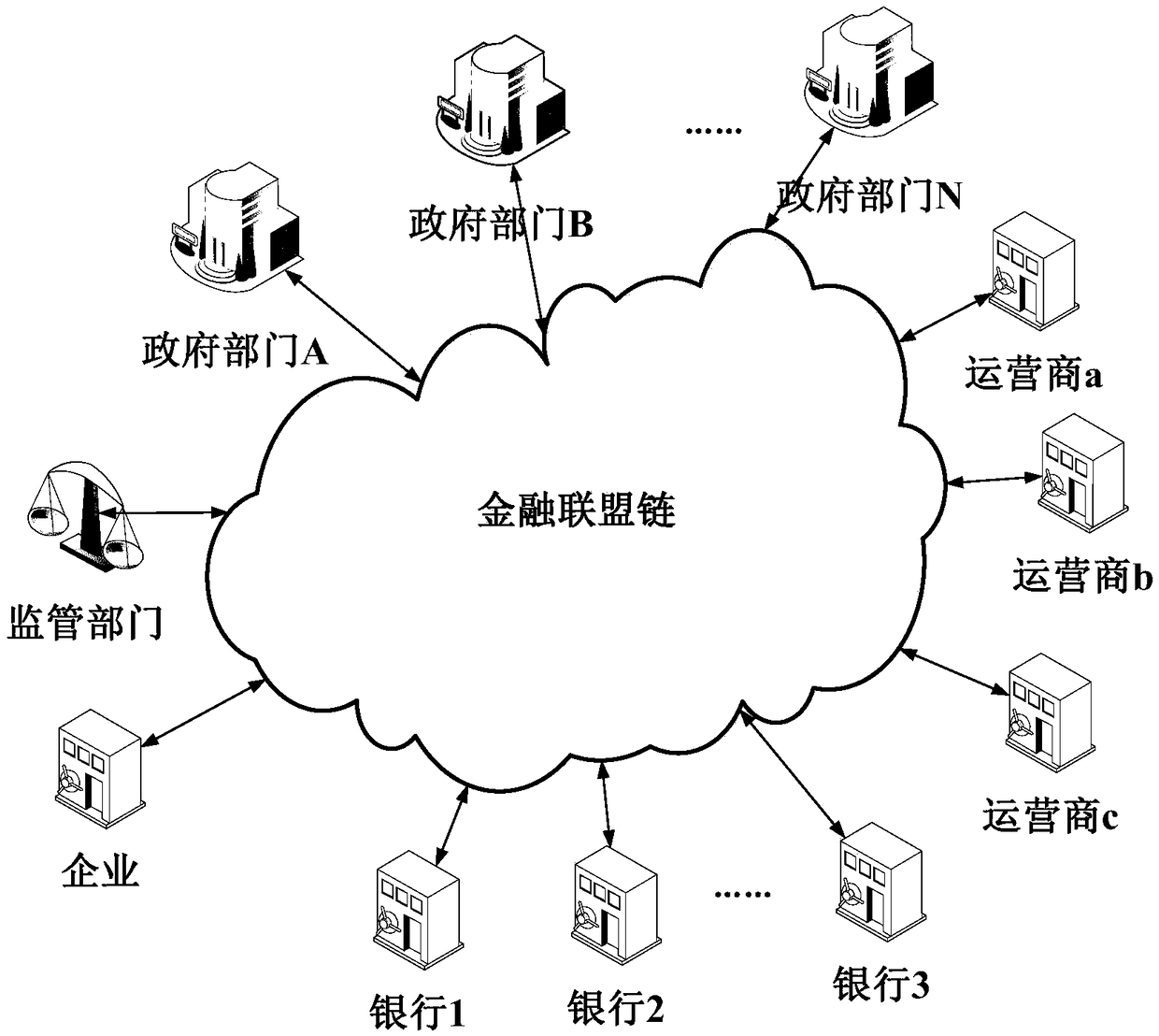
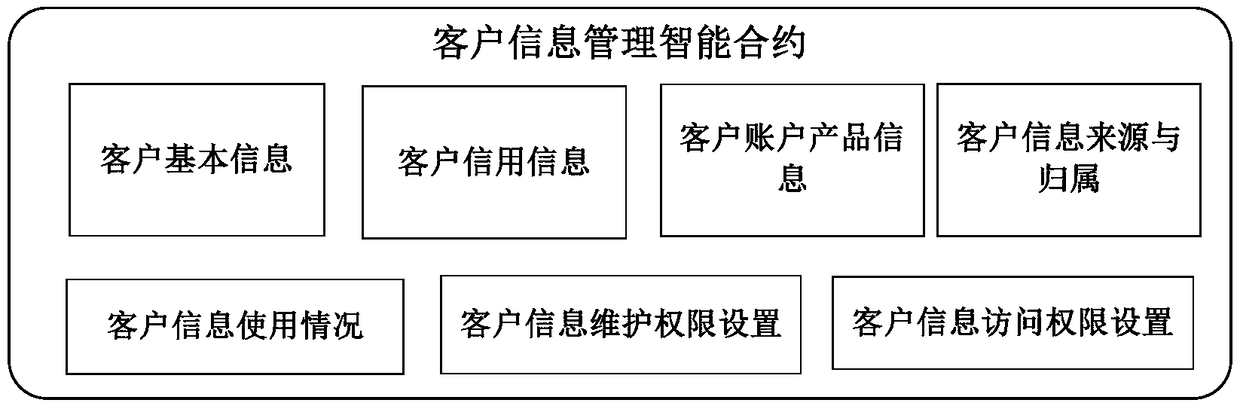
Customer data management system based on block chain
InactiveCN109063169AImprove timeliness and accuracyRelieve concurrent pressurePayment circuitsSpecial data processing applicationsCustomer intelligenceManagement system
The invention provides a customer data management system based on a block chain. Participants are connected to a financial union chain through a corresponding block link-in node, so as to realize theuplink of customer data, and realize the inquiry, addition, modification and synchronization of customer data according to the customer intelligent account book and the customer intelligent contract.The financial union chain designs a sectional protection lock for the customer data on the chain to realize the circulation of the customer data among the set participants; The client intelligent account book comprises a client information access authority, a newly added authority and a client information maintenance authority, wherein the client intelligent account book comprises a client information access authority, a client information access authority and a client information maintenance authority. Customer Intelligence Contract includes Customer Information Addition Service, Customer Information Maintenance Service and Customer Information Change Notification Service. The invention realizes the non-tampering, encrypted storage and privilege access of the uplink information, which canensure the privacy of the customer information and realize the cross-organization sharing of the public basic customer information on demand, such as the mobile phone number is shared between the operator and the government department, and between the operator and the bank.
Owner:FUJIAN RURAL CREDIT UNION
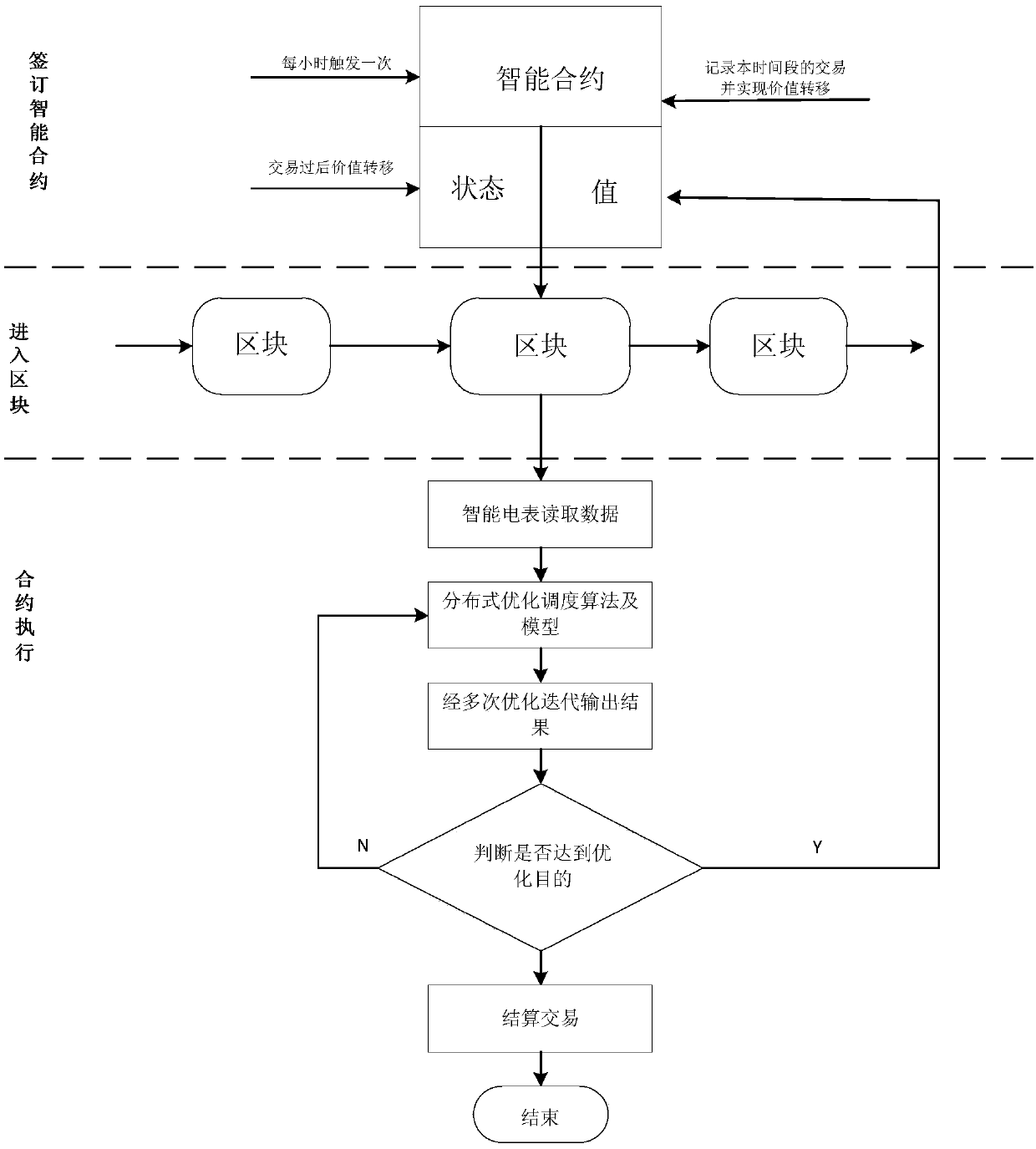
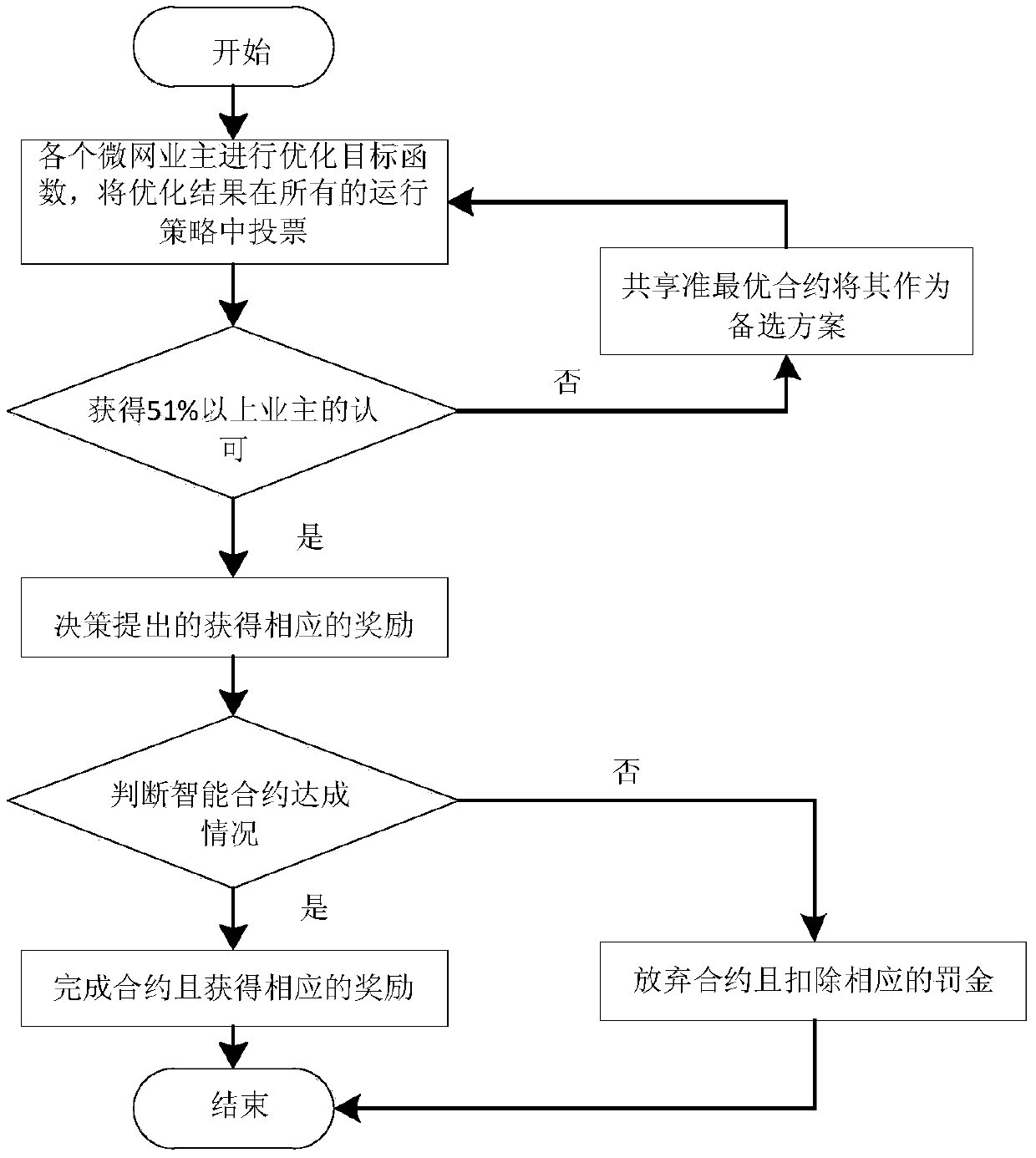
Distributed optimal scheduling method for interconnected micronetworks based on intelligent contract
ActiveCN109034480ALower default rateImprove rationalityForecastingElectric power transmissionElectricity
The invention discloses a distributed optimization dispatching method of an interconnected micro-network based on an intelligent contract, which comprises the following steps: establishing a block chain of electric power transaction; setting the dispatching cycle, recording the electricity quantity sent and received in the dispatching cycle; the optimal dispatching model of interconnected micro-grid system being established and solved, and the optimal dispatching scheme being obtained. According to the optimal dispatching scheme, the transaction contents of the micro-grid involved in the transaction are determined, and the smart contract is signed and sent to other micro-grids in the network. The microgrid to reach consensus; verify the transaction, judge whether the transaction is safe ornot, cancel the transaction if it is not safe, complete the transaction if it is safe, and transfer funds between microgrids. The invention provides a distributed optimal dispatching model and a distributed iterative algorithm of an interconnected micro-grid system, and applies a block chain to the recording and value transfer of the distributed transaction, and signs an intelligent contract between the micro-grids, thereby solving the trust problem between the transaction parties and achieving high automation degree.
Owner:XIANGTAN UNIV
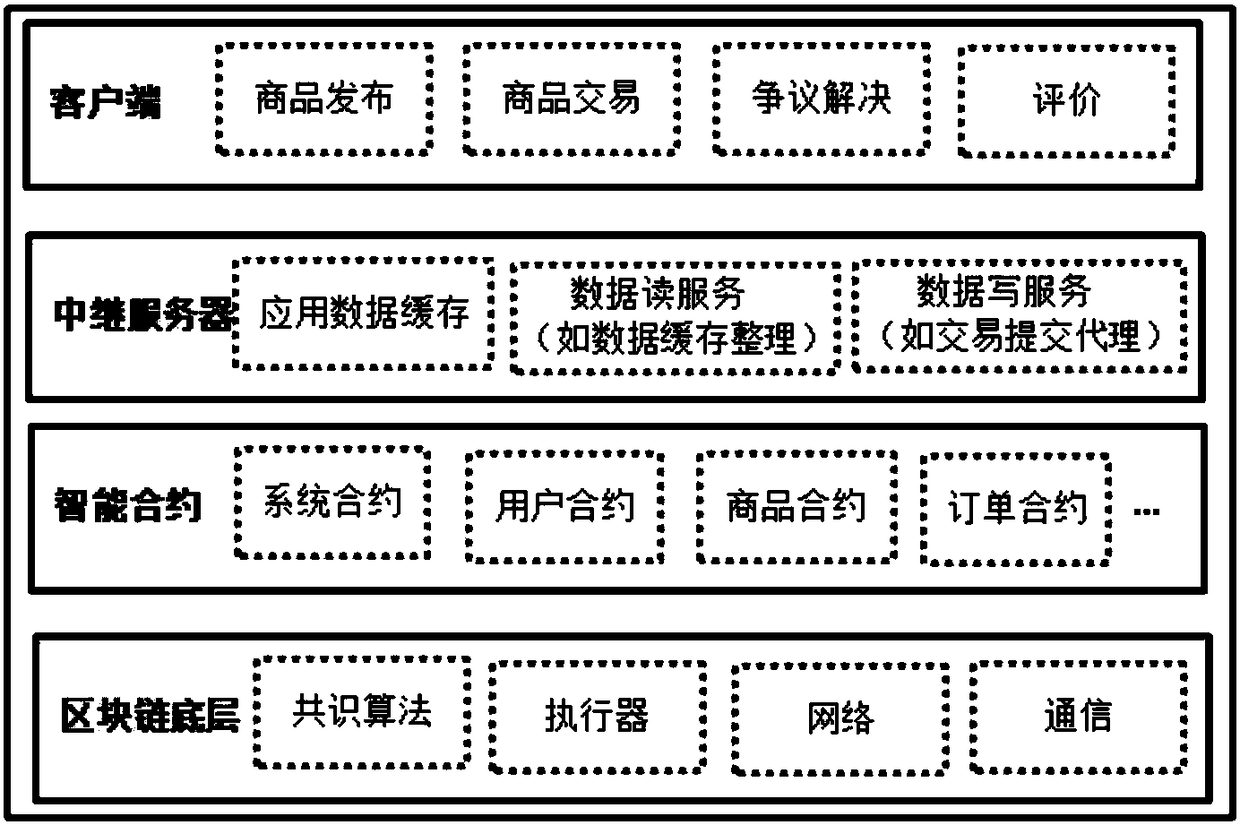
Distributed e-commerce platform system based on block chain
InactiveCN108256965ALow costReduce riskPayment protocolsBuying/selling/leasing transactionsE-commerceClient-side
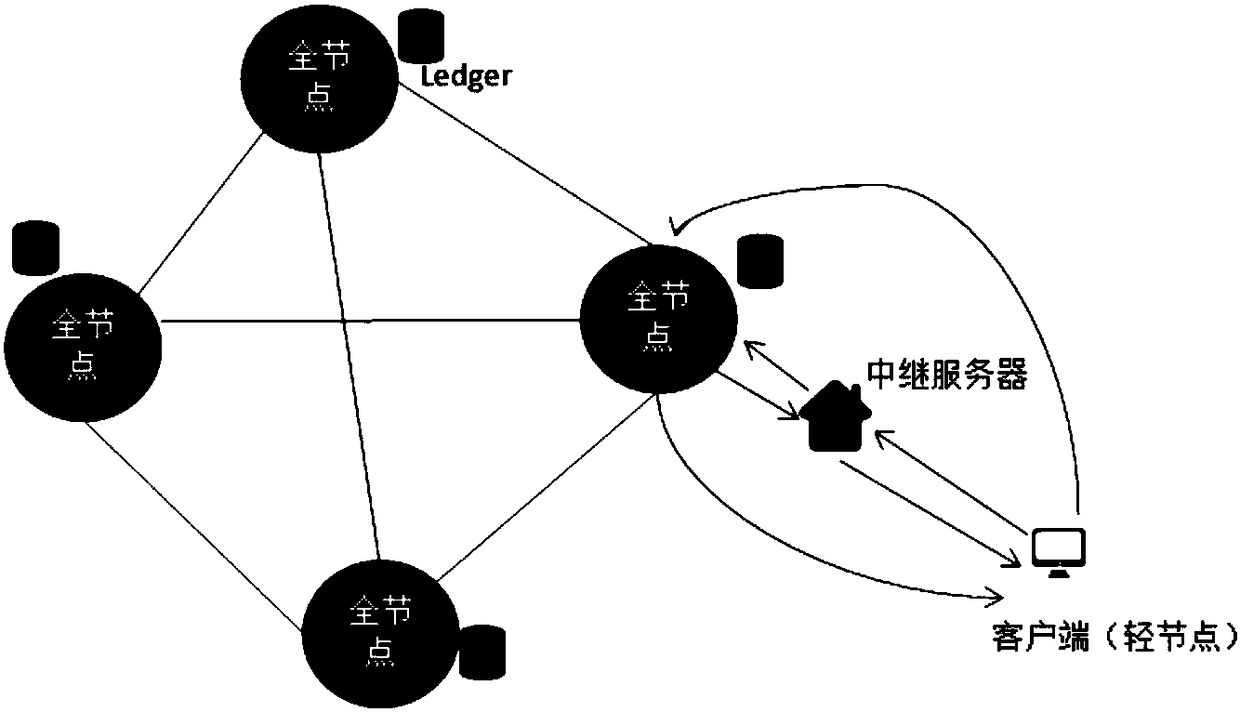
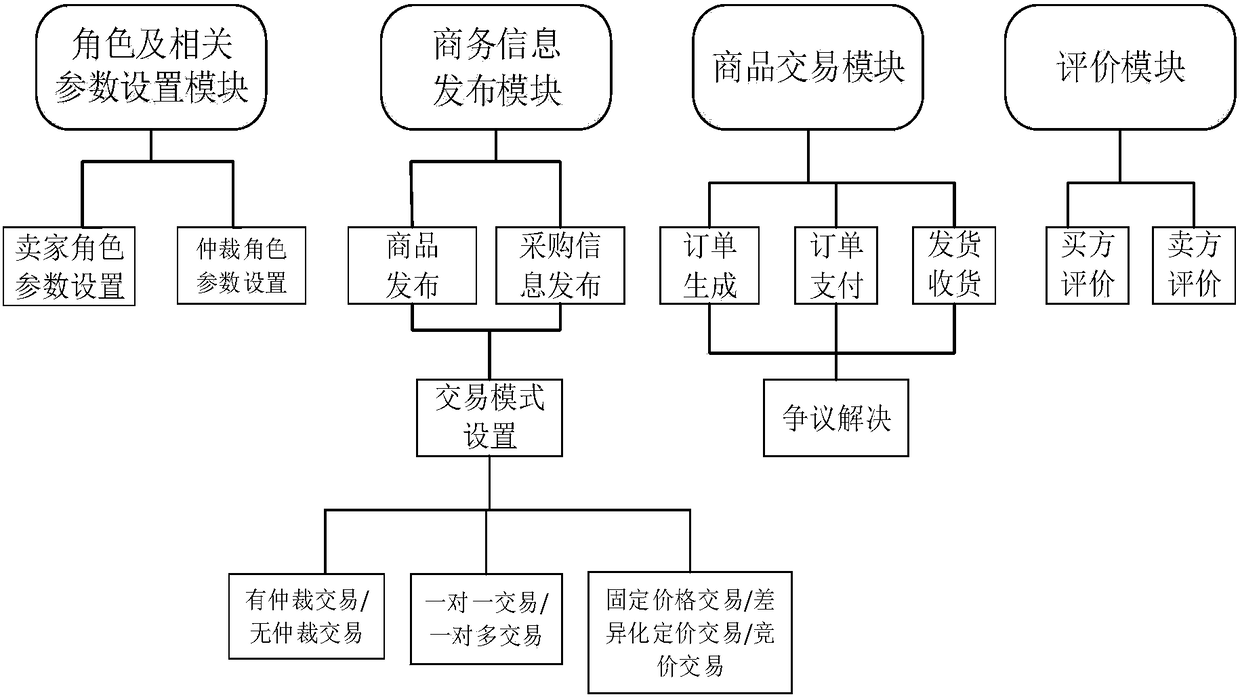
The invention discloses a distributed e-commerce platform system based on a block chain. The system comprises a client, a relay server and block chain network full nodes. The client is connected withthe relay server and the block chain network full nodes. The relay server node is connected with the block chain network full nodes. The system further comprises a role and related parameter setting module, a business information release module, a commodity transaction module and an evaluation module. Through the system, cost and risk can be reduced, data modification can be traced, flexible ordercustomization can be realized, the profit space can be increased for sellers through intelligent pricing, and functions such as closed auction and intelligent bidding can be achieved.
Owner:HANGZHOU RIVTOWER TECH CO LTD
Bulk commodity transaction data processing system and data processing method
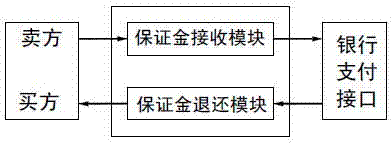
InactiveCN104766235AResolve trust issuesImprove reliabilityBuying/selling/leasing transactionsPayments involving neutral partyHandling systemReceipt
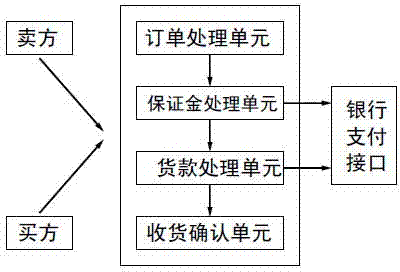
The invention relates to a bulk commodity transaction data processing system and data processing method, and belongs to the field of electronic commerce. The system comprises a transaction server which can be logged in by a buyer and a seller. The system is characterized in that the transaction server is at least provided with an order processing unit, a security deposit processing unit, a goods payment processing unit, a goods receipt confirmation unit, and a master control unit. The method comprises the steps that pending an order is conducted; ordering is conducted; paying the security deposit is conducted; earnest money is paid by the buyer; full payment is paid; the buyer confirms that the goods are received; the goods payment is transferred to the account of the seller; the security deposit is returned. According to the bulk commodity transaction data processing system and data processing method, the goods payment is not paid to a third-party transaction platform, but paid to a payment channel of a bank, the bulk commodity transaction data processing system and data processing method are especially suitable for online transactions between enterprises, and the phenomenon that taxes are paid for two times is avoided simultaneously.
Owner:SHANDONG ZHUOCHUANG INFORMATION GRP CO LTD
Credible advertisement data management system based on block chain
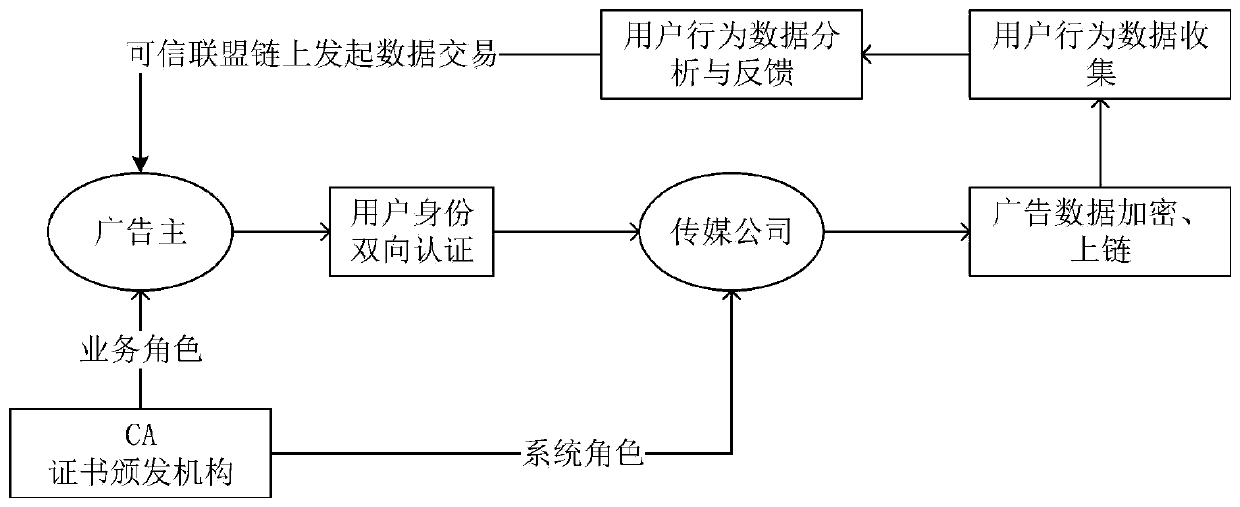
InactiveCN110309634AResolve trust issuesKey distribution for secure communicationPublic key for secure communicationData managementPrivacy preserving
The invention belongs to the technical field of data security, particularly relates to a credible advertisement data management system based on a block chain, and solves the problems that the data reliability is low, the data is not public and transparent enough, the data can be manually operated and is easily tampered, the privacy protection is difficult, and the data security is difficult to guarantee. According to the invention, the block chain technology is applied to the media industry, the big data technology is combined, identity management and authorization and user identity bidirectional authentication are carried out on an advertiser and a media company based on the credible alliance chain, advertisement data are linked, and user data are transacted and analyzed. A safe and reliable advertisement data management method is provided for media companies, advertisers and consumers.
Owner:深圳大通实业股份有限公司
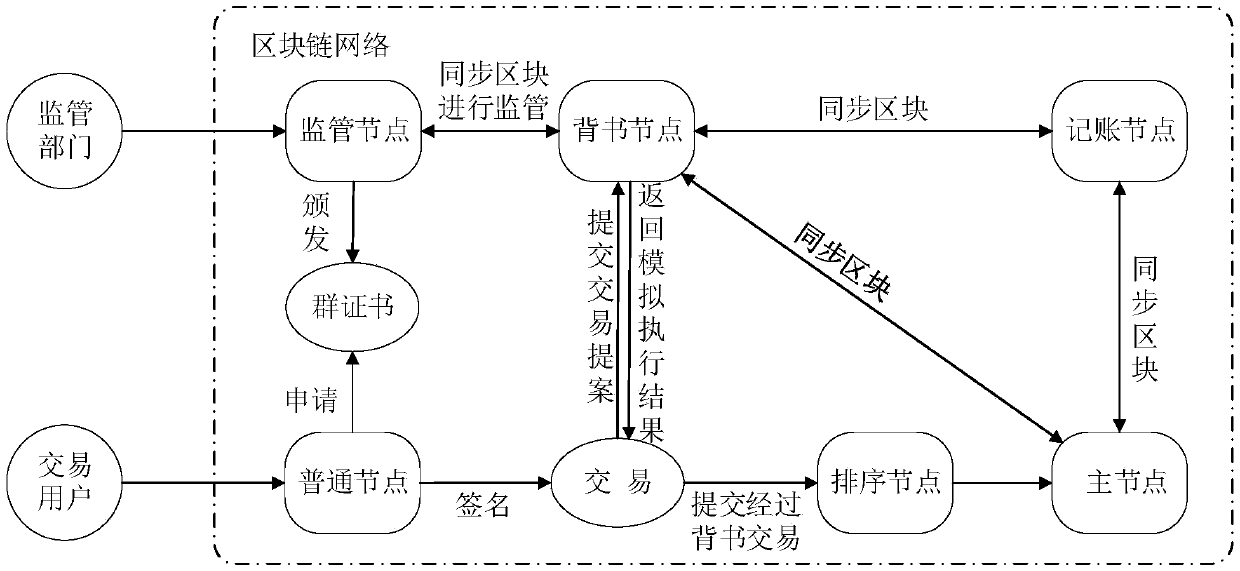
Permission block chain privacy protection and supervision method based on group signatures
InactiveCN109636599AProtect identity privacyGood anonymityFinanceDigital data protectionPrivacy protectionIdentity privacy
The invention discloses a permission block chain privacy protection and supervision method based on group signatures. In a transaction process, whether the endorsement verification of the endorsementnode, the sequencing service of the sequencing node and the consensus process of the main node and the accounting node can only verify the legality of the identities of the two parties of the transaction, and cannot correspond the signature to the real identity of the user, so that the identity privacy of the user is guaranteed. After the transaction is completed, the supervision department can synchronize the block with other nodes through the supervision node, then open the signature contained in the transaction, and enable the signature to correspond to the real identity of the transactionuser, so as to supervise the block chain.
Owner:GUANGXI NORMAL UNIV
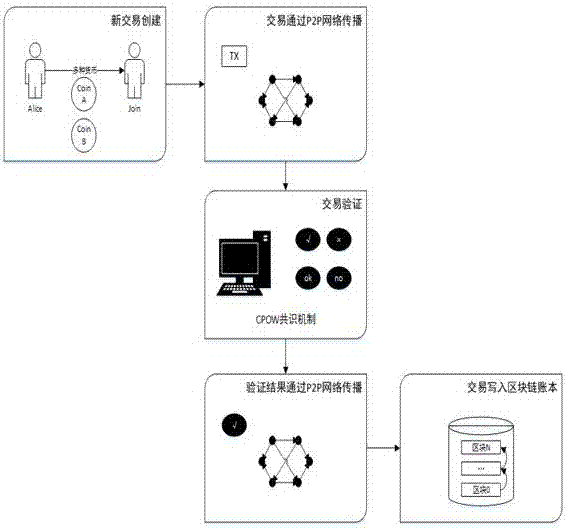
Establishing method of electronic wallet based on block chain
InactiveCN107369010ASolve the ceiling problemResolve trust issuesPayment protocolsPayment circuitsCredit systemValue passing
The invention discloses an establishing method of an electronic wallet based on a block chain. The method comprises steps of 1) establishing a new transaction and issuing various types of assets; 2) carrying out the transaction and broadcasting transaction lists to the whole network through a P2 network; 3) carrying out transaction verification; 4) verifying results and broadcasting transaction results to the whole network after the transaction is finished; and 5) writing the transaction results into a block of a block chain. According to the invention, by use of the distributed account book technology, the digital asset flows and real cash payment on the block chain are connected, so in the global Internet market, the function of high-efficiency and low cost value delivery that the traditional financial mechanism cannot replace can be developed; a block chain credit system from the information to the value network is formed; the cryptography packet of each person can be developed into a 'self-finance' platform; and payment, depositing, transferring, exchange, loans and the bookkeeping and clearing in the whole network of the P2P can be achieved.
Owner:兰考同心互联数据管理有限公司
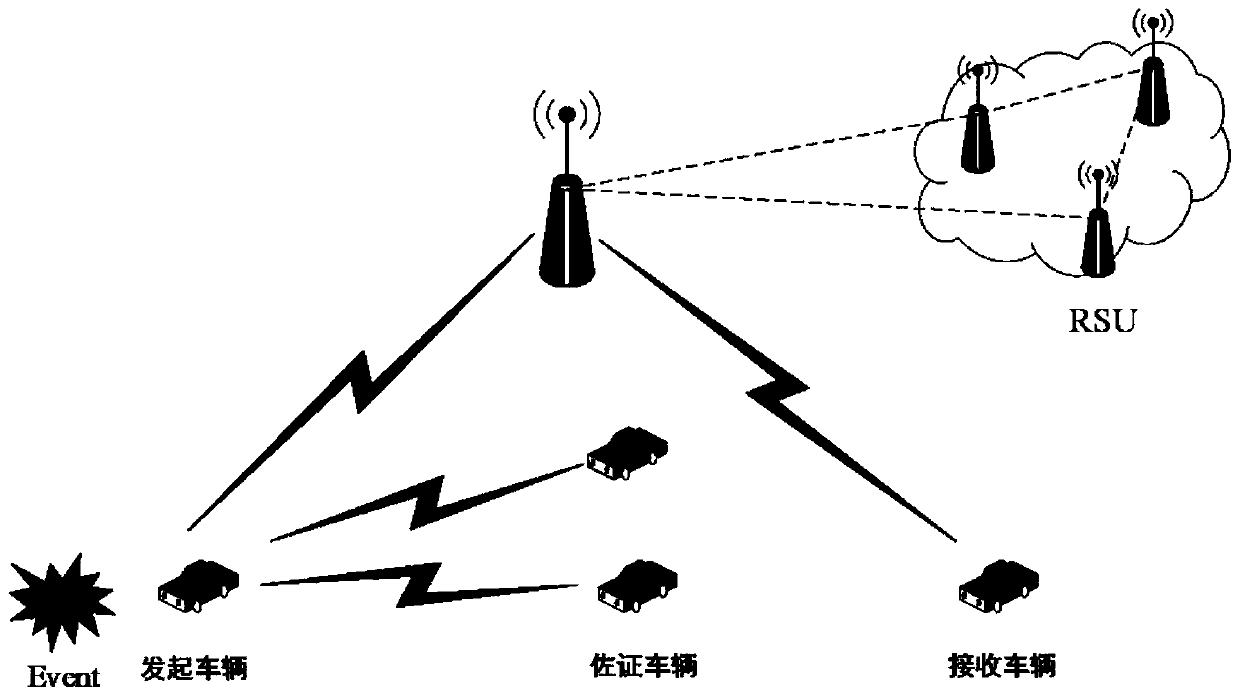
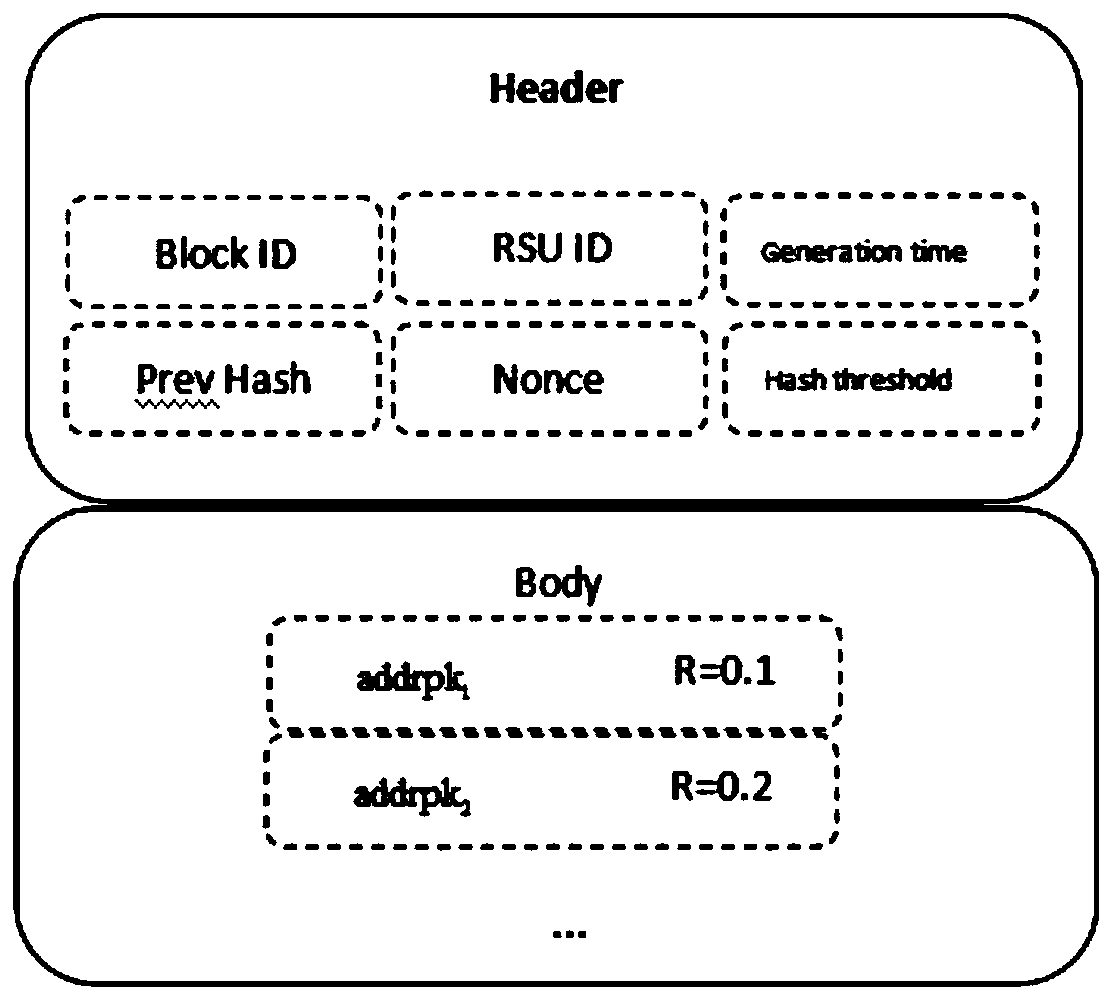
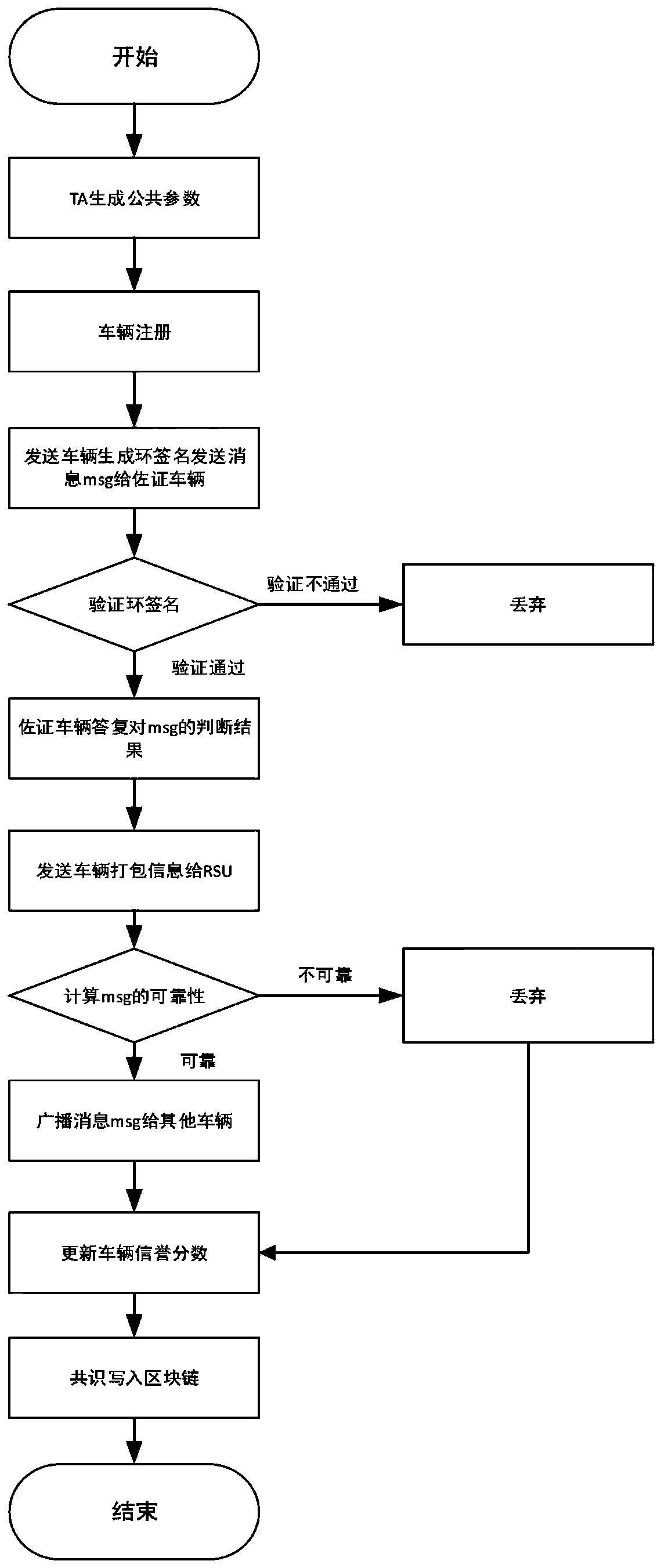
Internet of Vehicles privacy protection trust model based on block chain
ActiveCN110300107AAddress privacy concernsResolve trust issuesUser identity/authority verificationRing signaturePrivacy protection
The invention provides an Internet of Vehicles privacy protection trust model based on a block chain. Vehicles on the road generate and broadcast messages through the vehicle-mounted ad hoc network toshare surrounding traffic information so as to improve the traffic efficiency and safety. However, due to the untrusted network environment of the vehicle-mounted ad hoc network, the privacy of the vehicle is easy to expose, and whether the received message is reliable cannot be judged. The message is anonymously sent by the vehicle through the ring signature technology, so that the vehicle is prevented from being tracked by a malicious vehicle. Messages sent by the vehicle are evaluated and screened through a reputation evaluation mechanism based on the block chain technology, and forged information in the messages is filtered. Based on the characteristics of the block chain, it is guaranteed that the vehicle reputation is not maliciously tampered, real-time synchronous updating of the vehicle reputation is achieved, and the safety and usability of the vehicle-mounted ad hoc network are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
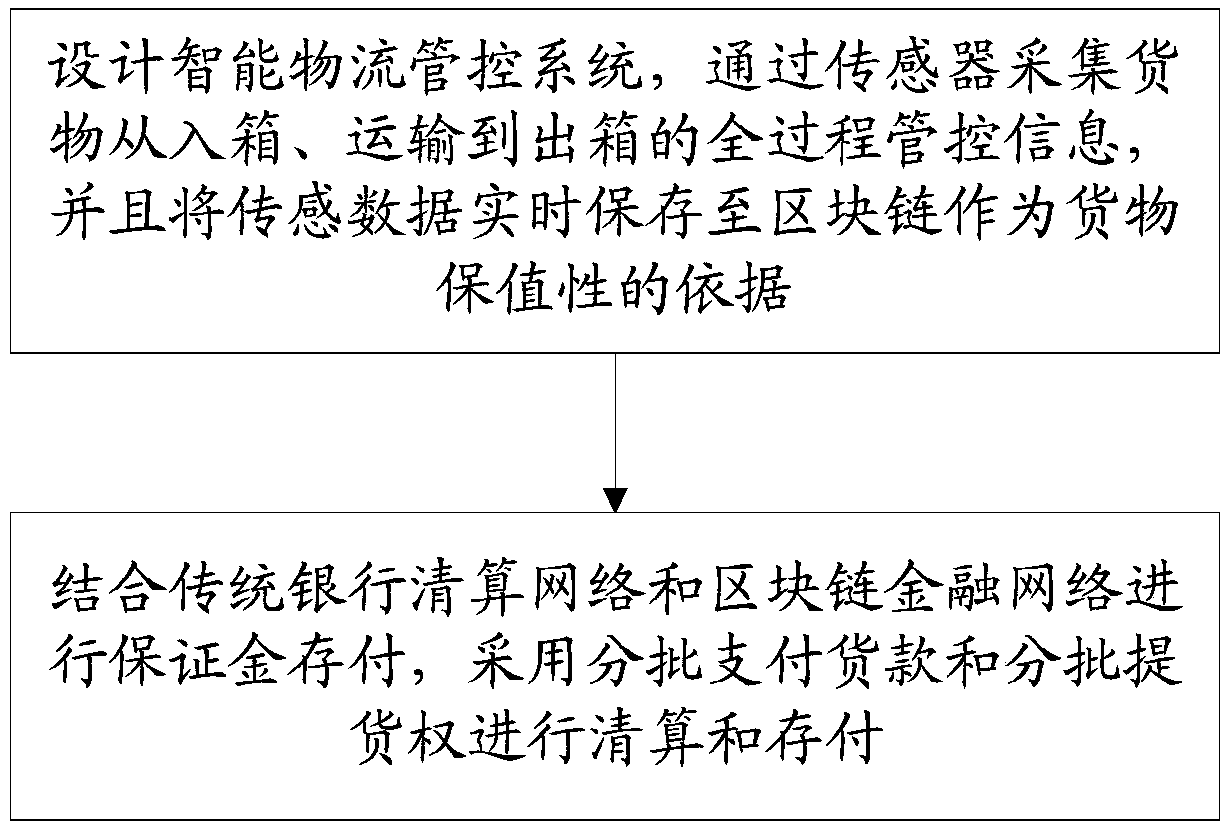
Supply chain prepayment financing method based on block chain of internet of things
PendingCN108694551AResolve trust issuesRealize the payment problemFinanceLogisticsPaymentSensing data
The invention provides a supply chain prepayment financing method based on a block chain of the internet of things. The method comprises the following steps: designing an intelligent logistics management and control system, acquiring the whole process management and control information of goods from container loading, transportation to container unloading by a sensor, and saving the sensing data to the block chain in real time as the basis of goods value preservation; and by combining with the traditional bank clearing network and block chain financial network to deposit and pay deposits, performing clearing and depositing and paying by using batch payment of the price for goods and batch right of taking delivery of goods. The invention designs a supply chain prepayment financing method based on the internet of things and the block chain technology, the issue of trust among multi-agency bodies has been effectively resolved, the invention realizes the payment problem of purchasing and selling goods and four-party silver under the heterogeneous network, the method is suitable for the safe transportation of goods of various enterprises, realizes the real-time collection and trustworthy saving of data in the transmission process, guarantees the value preservation of the goods transportation, reduces the risks of the bank, and effectively alleviates the short-term capital pressure brought by the full-amount purchase, and realizes the multi-win purpose.
Owner:FUJIAN RURAL CREDIT UNION
Method for safe data backup, client side and cloud server side based on alliance chain
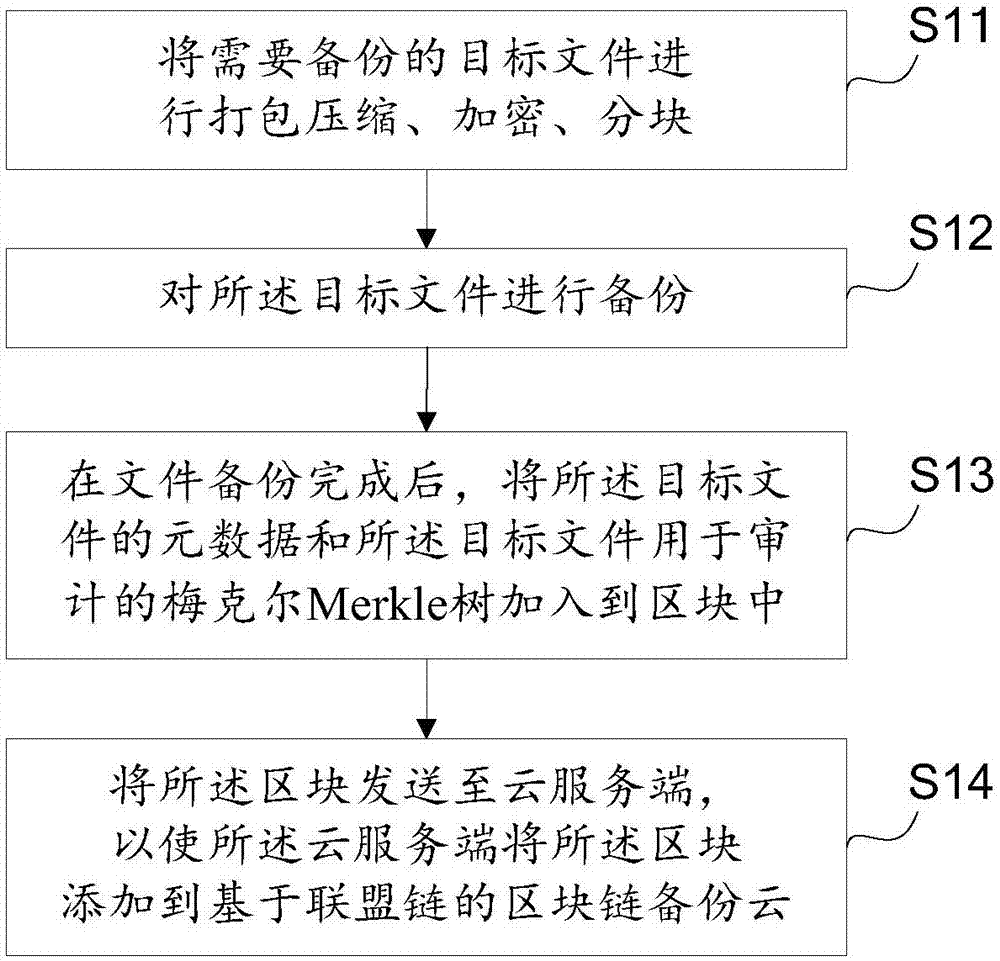
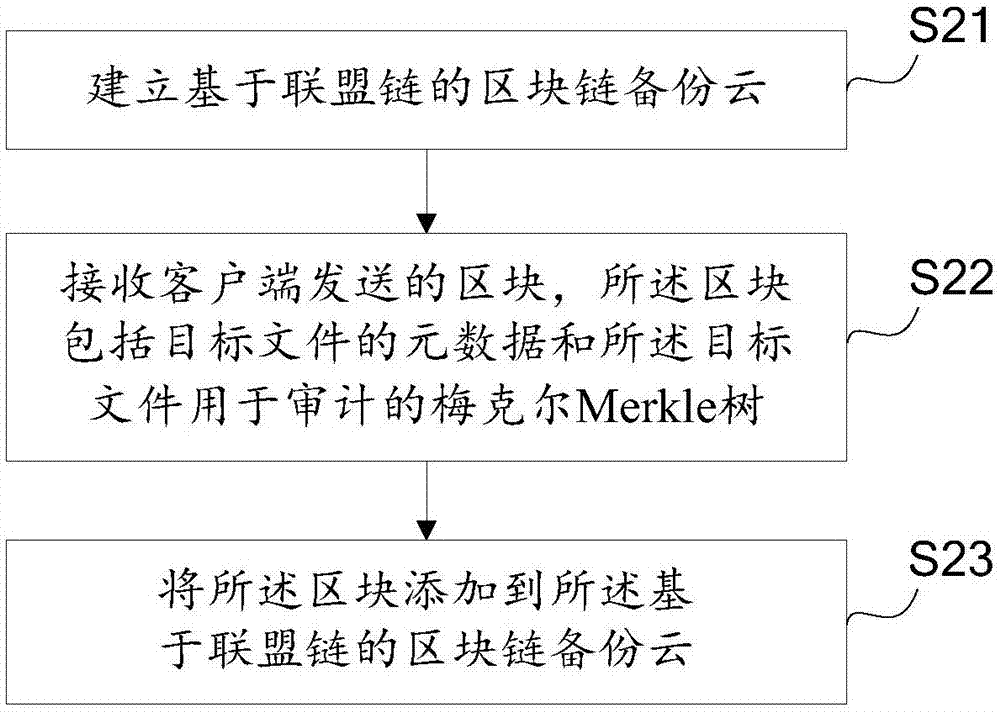
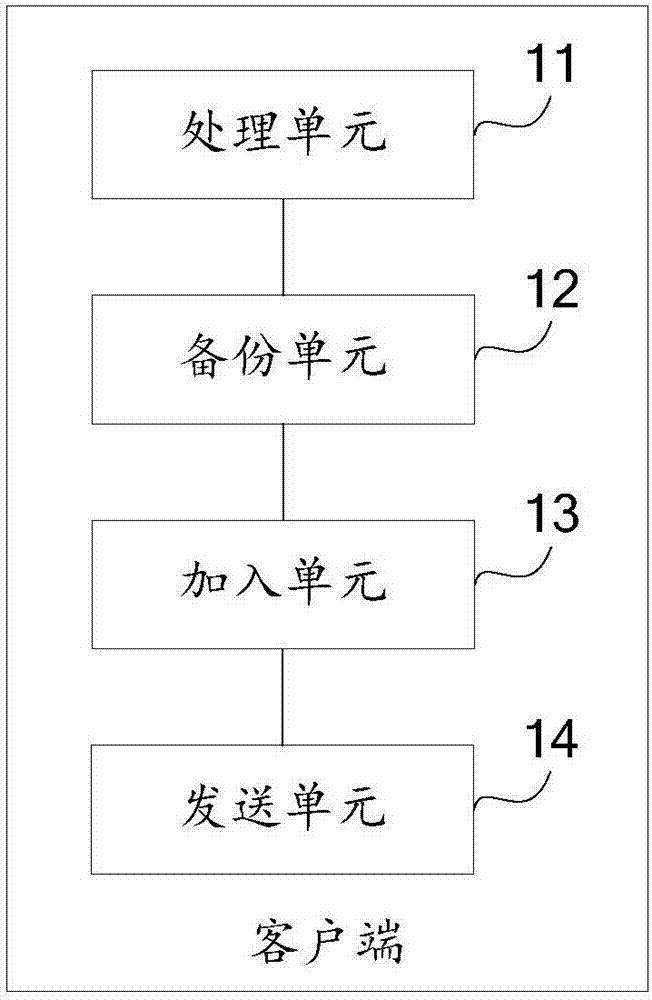
InactiveCN106919476AReduce overheadRealize remote backupTransmissionRedundant operation error correctionClient-sideMerkle tree
The invention discloses a safe data backup method, a client side and a cloud server side based on an alliance chain. On the client side, the method comprises the steps that a target document to be backed up is packaged, compressed, encrypted and partitioned; the target document is backed up; after backing up of the document, metadata of the target document and a Merkle tree of the target document used for auditing are added into a partition block; and the partition block is sent to the cloud server side, so the cloud server side can add the partition block to a partition block chain backup cloud based on the alliance chain. On the cloud server side, the method comprises the steps that the partition block chain backup cloud based on the alliance chain is established; the partition block sent by the client side is received, wherein the partition block comprises the metadata of the target document and the Merkle tree of the target document used for the auditing; and the partition block is added to the partition block chain backup cloud based on the alliance chain. According to the invention, resource sharing is achieved, and expenditures of conventional remote backup are saved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
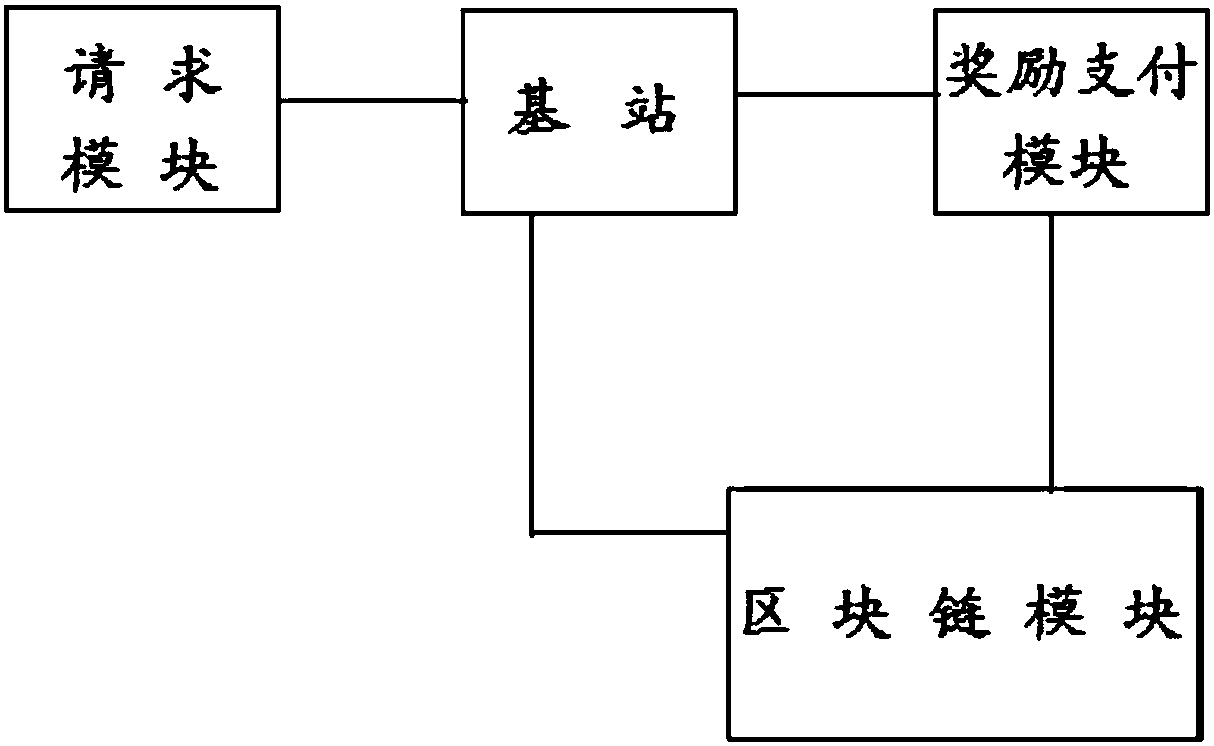
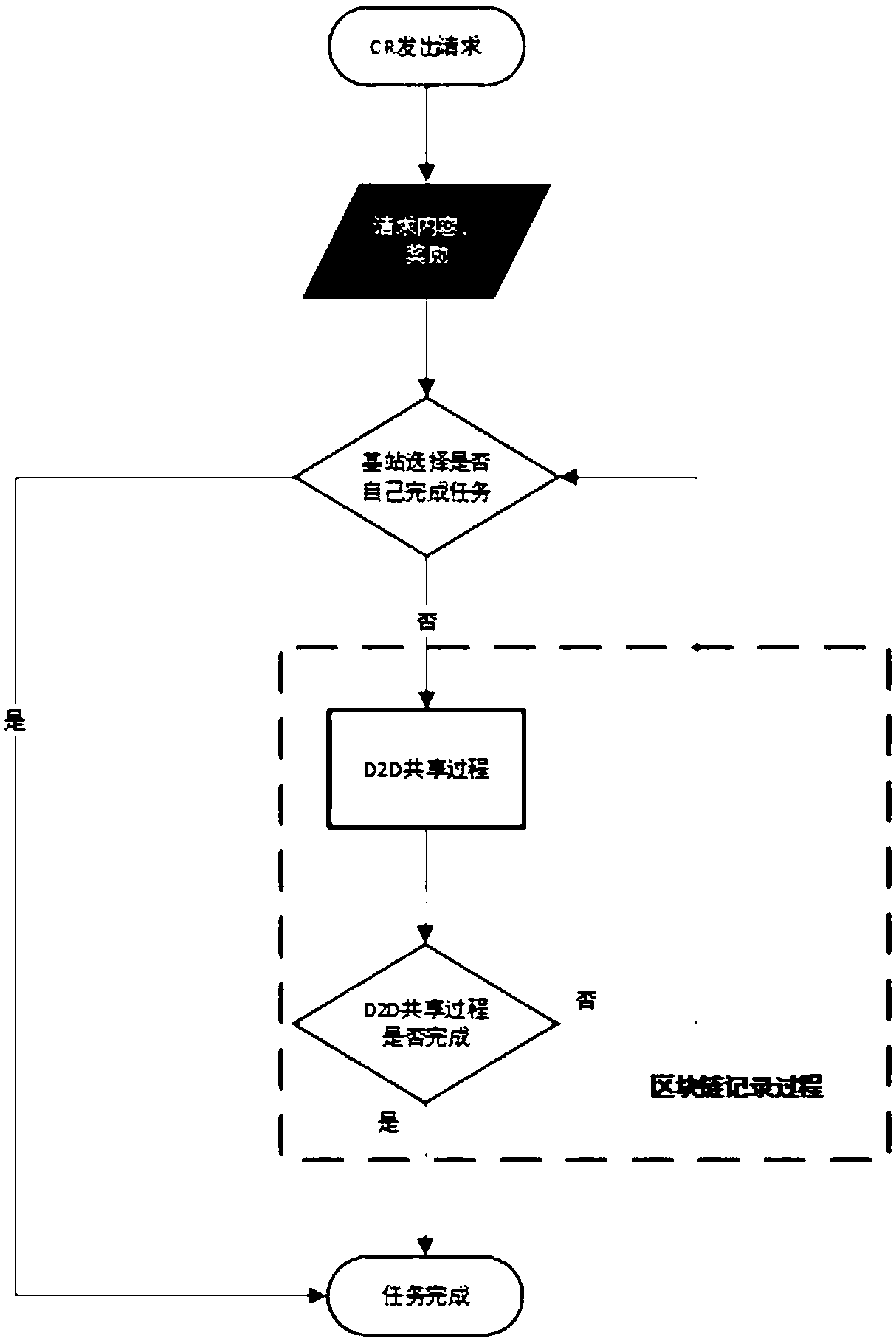
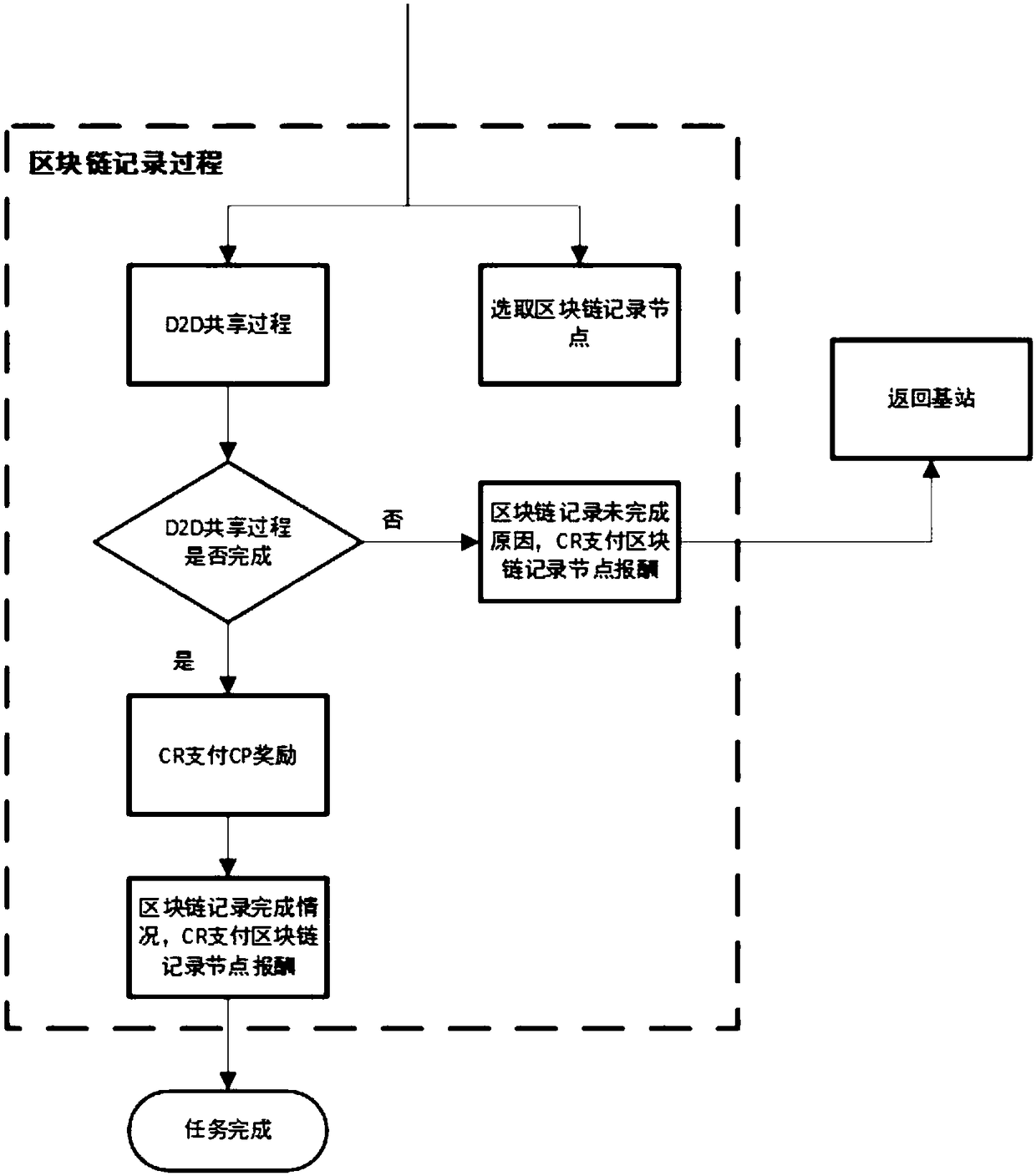
D2D reward sharing system based on blockchain and implementation method
InactiveCN108197969APromote practical implementationResolve trust issuesDiscounts/incentivesPayment architectureDigital currencyInternet privacy
The invention provides a D2D reward sharing system based on a blockchain. The system comprises a content request module, a base station, a reward payment module and a blockchain module. The content request module is used for requesting a specific content which needs to be acquired by a user. The base station searches a content provider according to the specific content requested by the content request module. The reward payment module uses a digital currency mode to carry out reward payment on the blockchain module and the content provider. The blockchain module is used to record the behaviorcondition of the content provider during a sharing process in the system. In the invention, through a reasonable excitation mechanism, the participation enthusiasm of a D2D user is increased; throughusing a blockchain technology, the historical behavior of the user can be guaranteed to be recorded and not to be tampered so that a trust problem among the users is solved; and through using a digital currency technology, transactions among the user can be realized.
Owner:BEIJING JIAOTONG UNIV
Safe data sharing method in cloud environment
InactiveCN106612169AResistant to Collusion AttacksImprove securityKey distribution for secure communicationMultiple keys/algorithms usageAttribute-based encryptionRevocation
The invention provides a safe data sharing method in a cloud environment. The safe data sharing method is provided in allusion to a problem of encrypted data access control in the cloud storage environment by combining CP-ABE (ciphertext-policy attribute-based encryption). According to the method, a problem of trusted third party dependency in a CP-ABE algorithm is solved through combining a symmetric key of a cloud storage center and a asymmetric private key of an authorized agency; secondly, user unique identification is added to an attribute private key of a user so as to enable a sharing mechanism to resist collusion attacks from illegal users; and finally, revocation of the user is completed through updating the symmetric key, the backward security of shared data is ensured, and the updating efficiency is improved.
Owner:SICHUAN YONGLIAN INFORMATION TECH CO LTD
Block chain-based V2G transaction privacy protection method, device and system
ActiveCN111428268AResolve trust issuesFair and reliable transaction settlementFinanceDigital data protectionPaymentComputer network
The invention discloses a V2G transaction privacy protection method, device and system based on a block chain. The method comprises the steps: enabling a block chain node to receive a transaction parameter anonymously transmitted by a buyer client, and recording the transaction parameter and a first zero-knowledge proof generated by the buyer client on the block chain in a form of an intelligent contract; the blockchain node verifies the correctness of the first zero-knowledge proof, and records the transaction parameters passing the verification on the blockchain; the block chain node receives guarantee expenses anonymously sent by the buyer client, and records the guarantee expenses passing the verification on the block chain; the blockchain node receives a payment voucher for settlementanonymously sent by the seller client, and records the payment voucher passing the verification on a blockchain; converting the payment voucher into a corresponding amount of funds based on the intelligent contract of the blockchain; the fund of the corresponding amount is sent to the seller client; and sending the guarantee fee to the buyer client.
Owner:SHANDONG UNIV
Data transaction system and method based on smart contract technology of blockchain
PendingCN111951106AResolve trust issuesNo cheatingDigital data information retrievalFinanceDigital assetData file
The invention discloses a data transaction system and method based on smart contract technology of a blockchain. The system comprises a data selling end, a data purchasing end and a service node, thedata purchasing end pays corresponding digital assets to a smart contract running in a blockchain, stores a digital assets in the intelligent contract, and sends a loaning request to the smart contract after receiving the data file; and the smart contract sends the digital assets to the data selling end. The data transaction system based on the smart contract technology of the blockchain and the method thereof provided by the invention are realized by the smart contract on the blockchain, all digital assets in the transaction process are hosted in the smart contract on the blockchain, the assets are public, transparent and viewable, the digital assets are hosted in the smart contract, the problem of centralized trust does not exist, and the security of the data transaction system is improved. The transfer-in and transfer-out records of the digital assets in the smart contract are all recorded on the blockchain, can be checked publicly and cannot be modified, so that the trust problem of two transaction parties is solved.
Owner:杭州增信信息技术有限公司
Seal management system and method
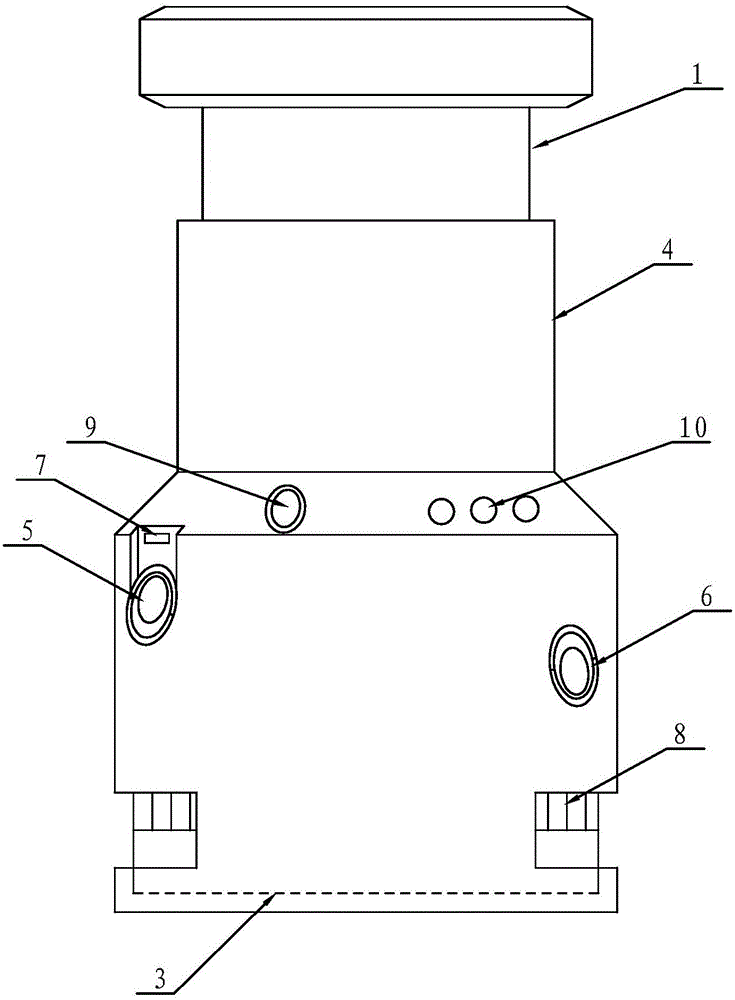
ActiveCN105072400AEnsure safetyClear positioningClosed circuit television systemsResourcesSoftware engineeringManagement efficiency
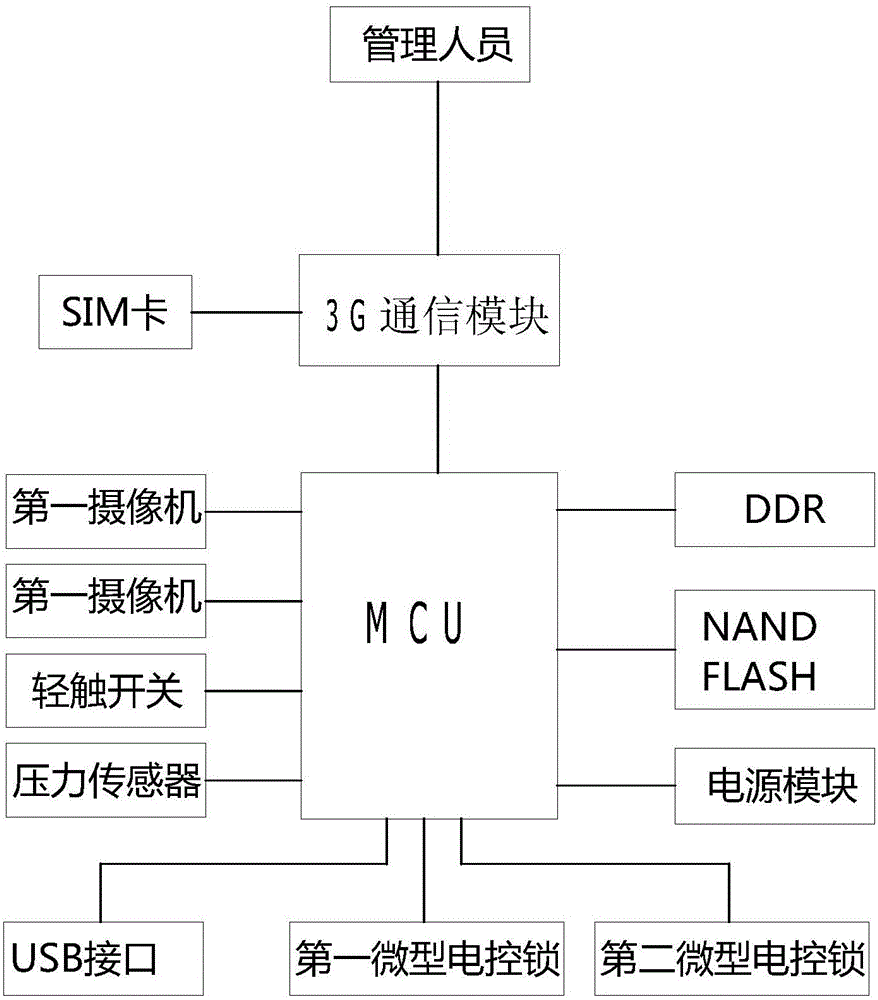
The invention discloses a seal management system and method. The system comprises a seal and a management device; the management device comprises a main controller, an image acquisition module, a communication module, an SIM card and a power module; the seal comprises a handle, a connector, a seal head and a shell. The method comprises an initial setting process, a seal application monitoring process and an illegal seal unpacking warning process. The seal management system effectively avoids the disadvantages of man-run management phenomena, and is integrated with techniques such as machinery, electronics and communications so that a manager and a user can be located more clearly; in the process when the user applies the seal, two photos of the user and the application action are sent to the cellphone of the manager so that the manager can get the actual seal application condition in time; as a result, the problem of trust between the user and the manager is avoided, the management efficiency is effectively improved and the safety of seal application is guaranteed.
Owner:日照爱国小男孩物联网科技有限公司
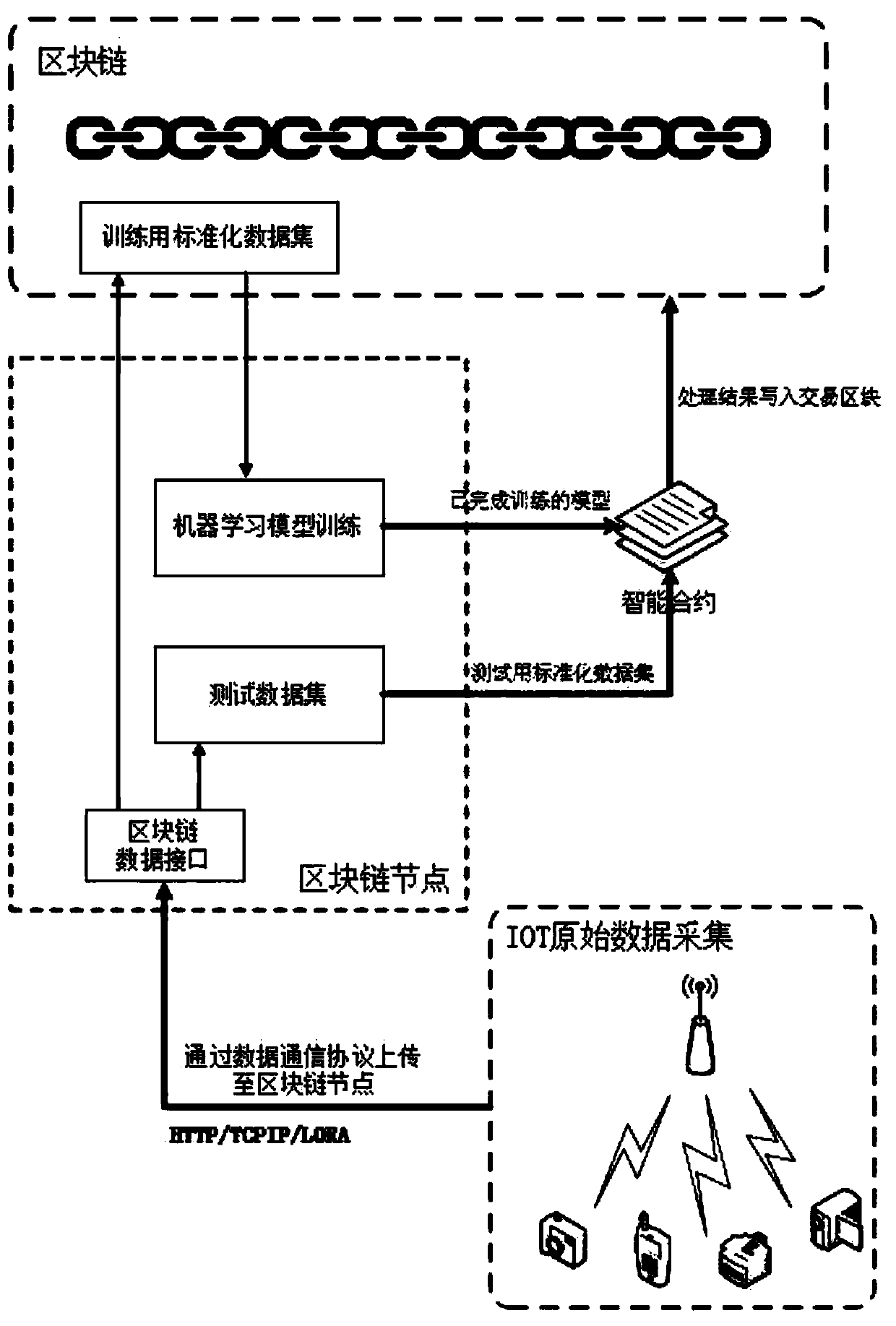
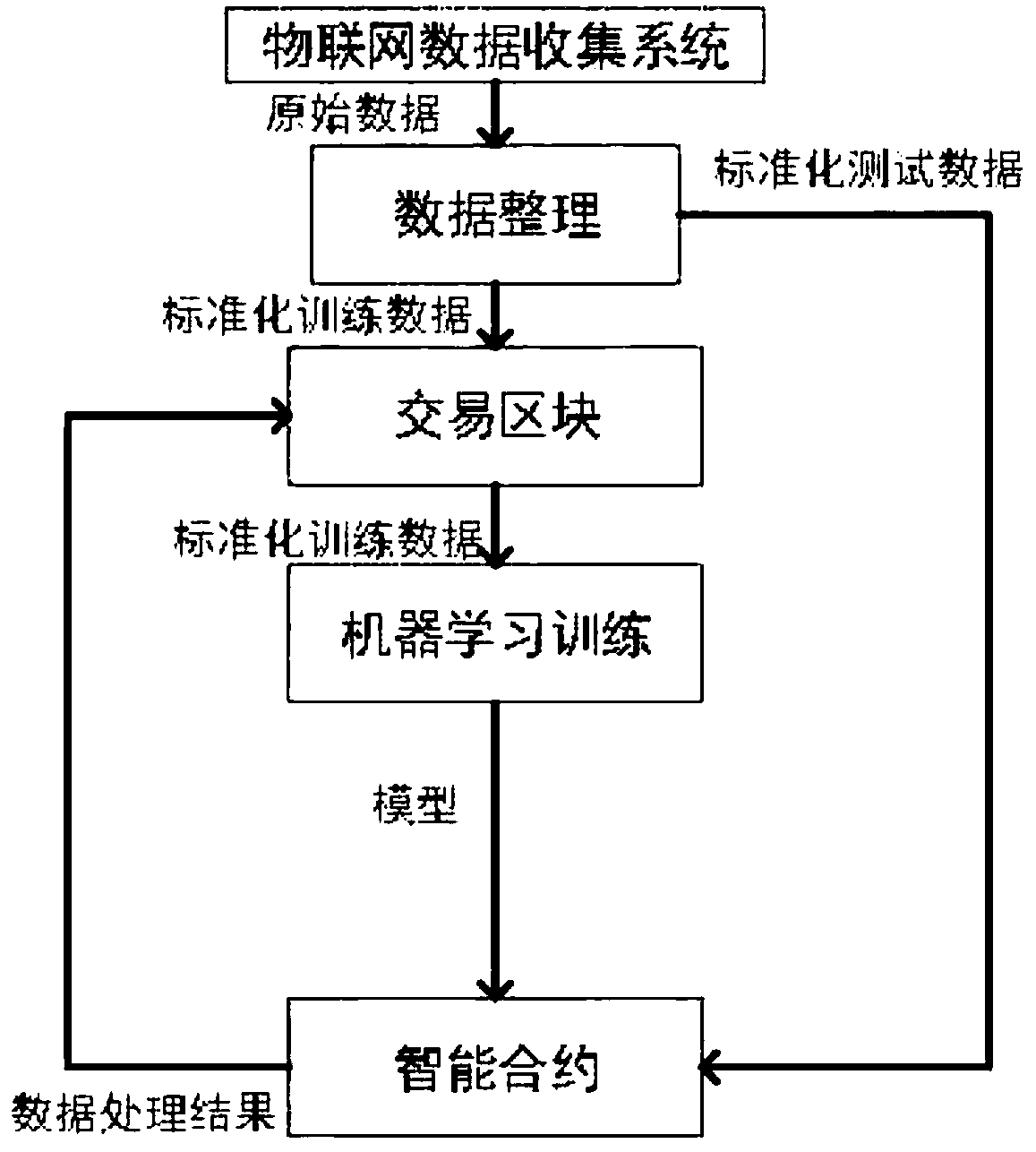
The invention discloses a dData preprocessing method based on a block chain intelligent contract and machine learning
InactiveCN109615015AResolve trust issuesImprove data mining capabilitiesCharacter and pattern recognitionTransmissionLink modelThe Internet
The invention discloses a data preprocessing method based on a block chain intelligent contract and machine learning. Data preprocessing on nodes is completed through cooperation of a block chain technology and a machine learning technology. The method specifically comprises the steps of collecting Internet of Things data, and standardizing the Internet of Things data after storing the Internet ofThings data to local nodes; C; creating a machine learning algorithm file on the local node, wherein the machine learning algorithm file is used for preprocessing the Internet of Things data; S; storing the data into a block chain; T; training a learning algorithm by using the linked data to obtain a model coefficient, and storing the model coefficient in a local node; Firstly, a machine learningalgorithm expression is written into an intelligent contract, and then an obtained model coefficient is stored into a block chain by calling the intelligent contract; P; processing the to-be-processed data by using the linked model; A; and storing the processed data into a block chain. According to the method, a machine learning algorithm is added into an intelligent contract of a block chain, and the data mining capability of the block chain is improved by utilizing machine learning.
Owner:BEIJING UNIV OF TECH
Multi-party privacy computing system based on trusted execution environment
InactiveCN111224986AStrong privacy effectResolve trust issuesUser identity/authority verificationComputing systemsData sharing
The invention discloses a secure and credible data multi-party computation implementation mode under the condition that a plurality of participants exist. By adopting the computing system provided bythe invention, a provider of the original data can clearly know which objects acquires the provided original data , in what way the provided original data is acquired, and whether unauthorized use orpropagation exists in an analysis process and an analysis result of the original data or not; and a data demander can also ensure the accuracy and authenticity of the original data and the data calculation result. According to the computing system, the original data needing to be protected and the computing program are placed in a specified trusted execution environment for data sharing, and underthe condition that multi-party data computing and privacy protection requirements exist, the technical scheme can well solve the safety problem concerned by all parties in the multi-party data computing problem.
Owner:杭州宇链科技有限公司
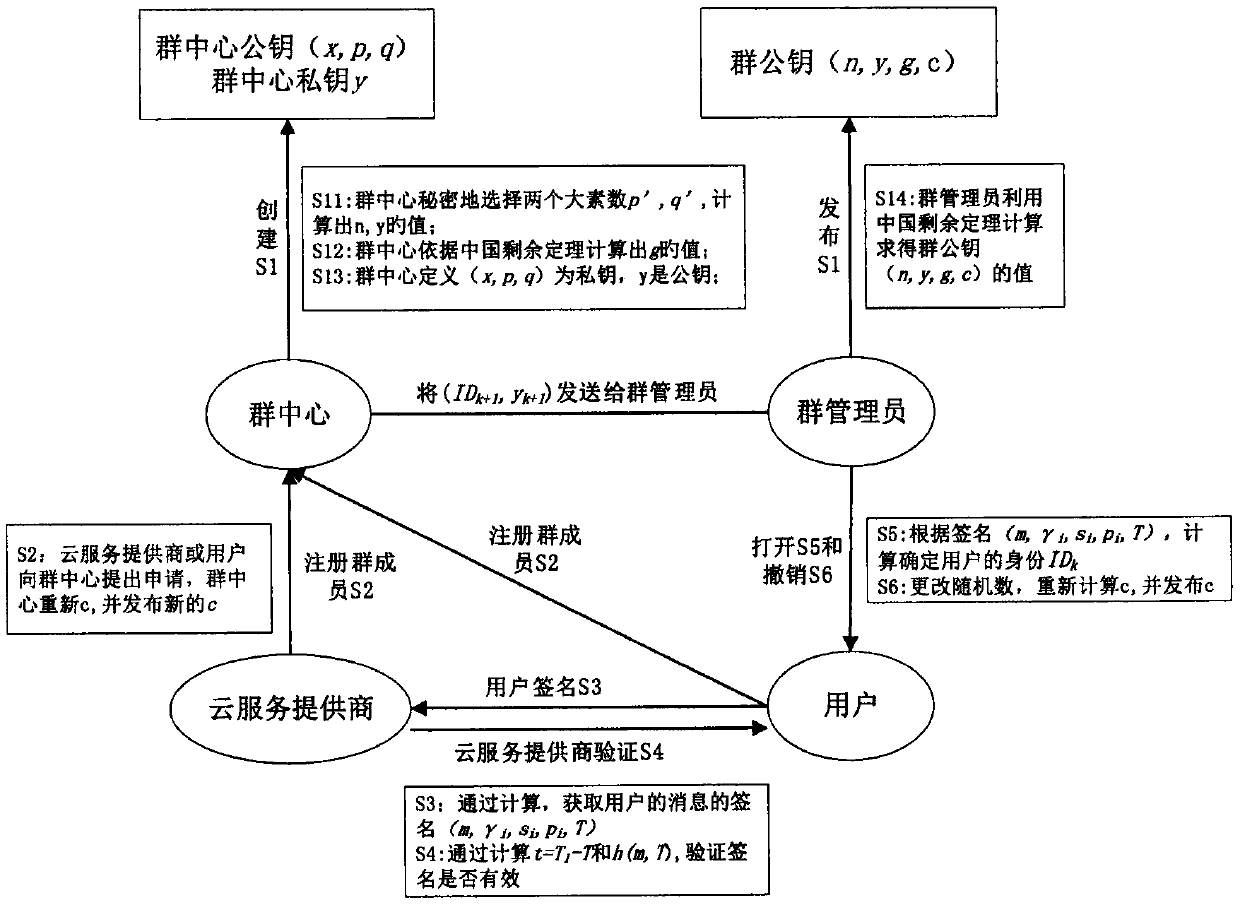
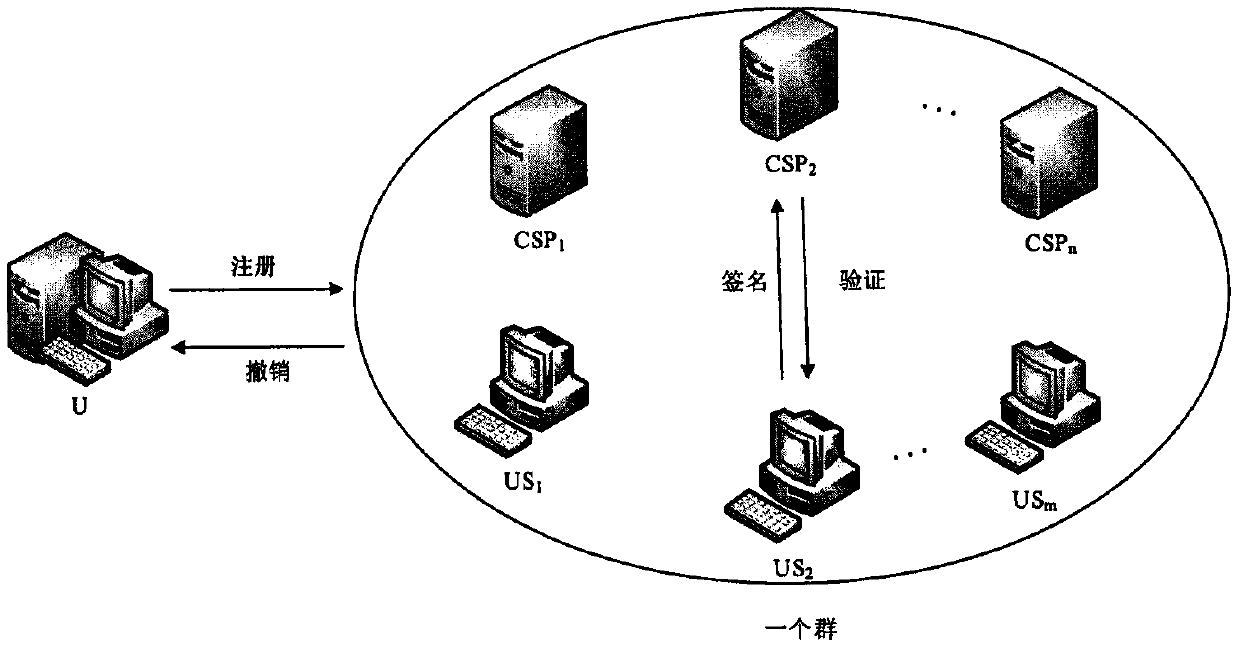
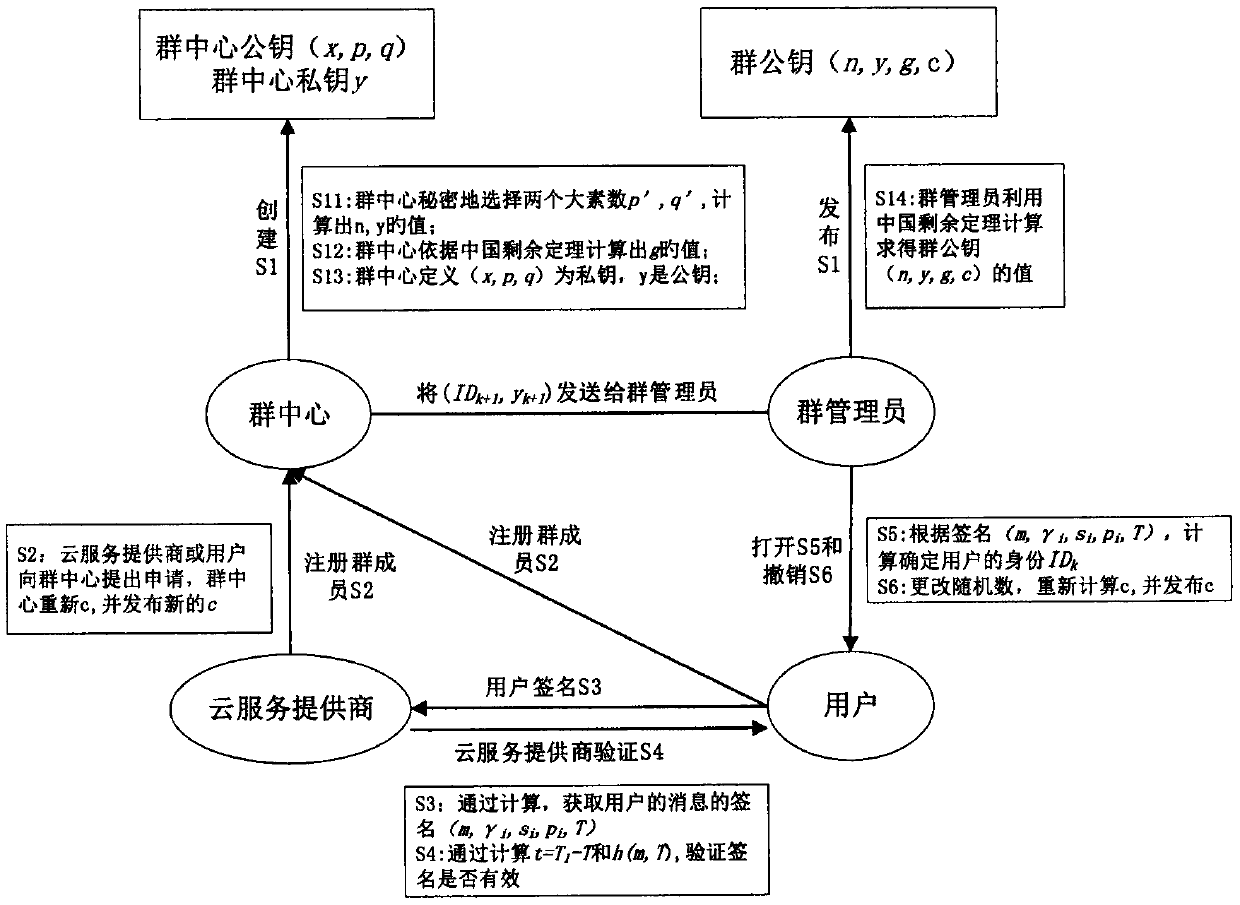
Cloud computing cross-domain identity authentication method
InactiveCN110034935AImplement identity authenticationGuaranteed identity anonymityKey distribution for secure communicationUser identity/authority verificationAnonymitySystem parameters
The invention belongs to the technical field of cloud computing, and particularly relates to a cloud computing cross-domain identity authentication method, which comprises the following participants:(1) a cloud service provider group member CSP provides various cloud services for a user in a cloud environment, and verifies the identity of the user; (2) the user group member US accesses the cloudservice to complete a cross-domain identity authentication process of a cloud service provider; (3) the group administrator GM is responsible for joining group members and opening signatures so as totrack group member information; and (4) the group center GC initializes system parameters and issues a group member certificate, and the group administrator also participates in the group member certificate issuing process and simultaneously exposes group member identity responsibility. According to the method, identity authentication between the user and the cloud service provider under differenttrust domains is realized by utilizing the security of the group signature and the validity verification of the message, so that the user identity anonymity is ensured, and meanwhile, the user identity traceability is realized, and the cloud computing has higher security.
Owner:ZHENGZHOU NORMAL UNIV
Data sharing method and device based on federal data and federal service
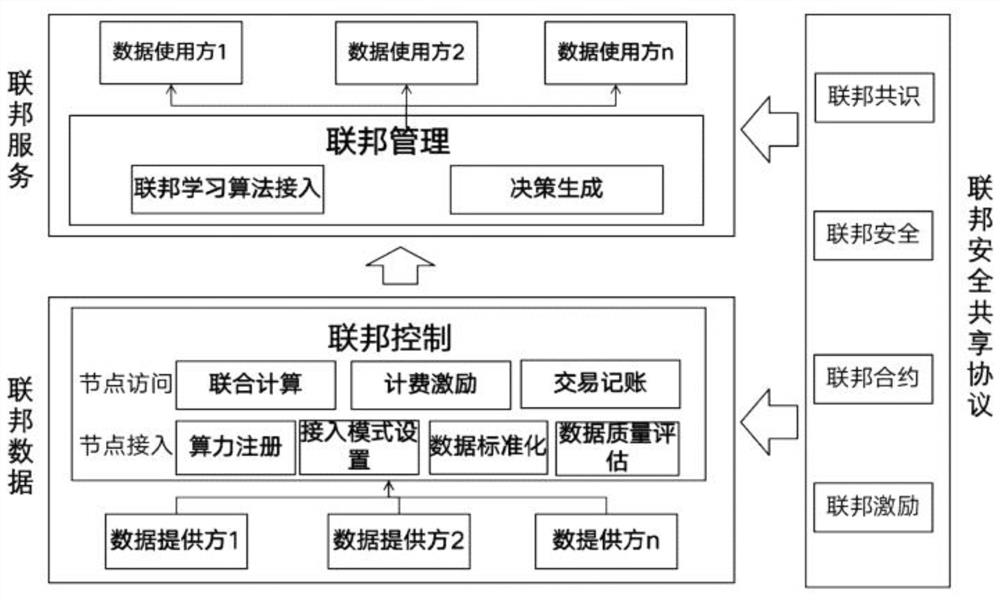
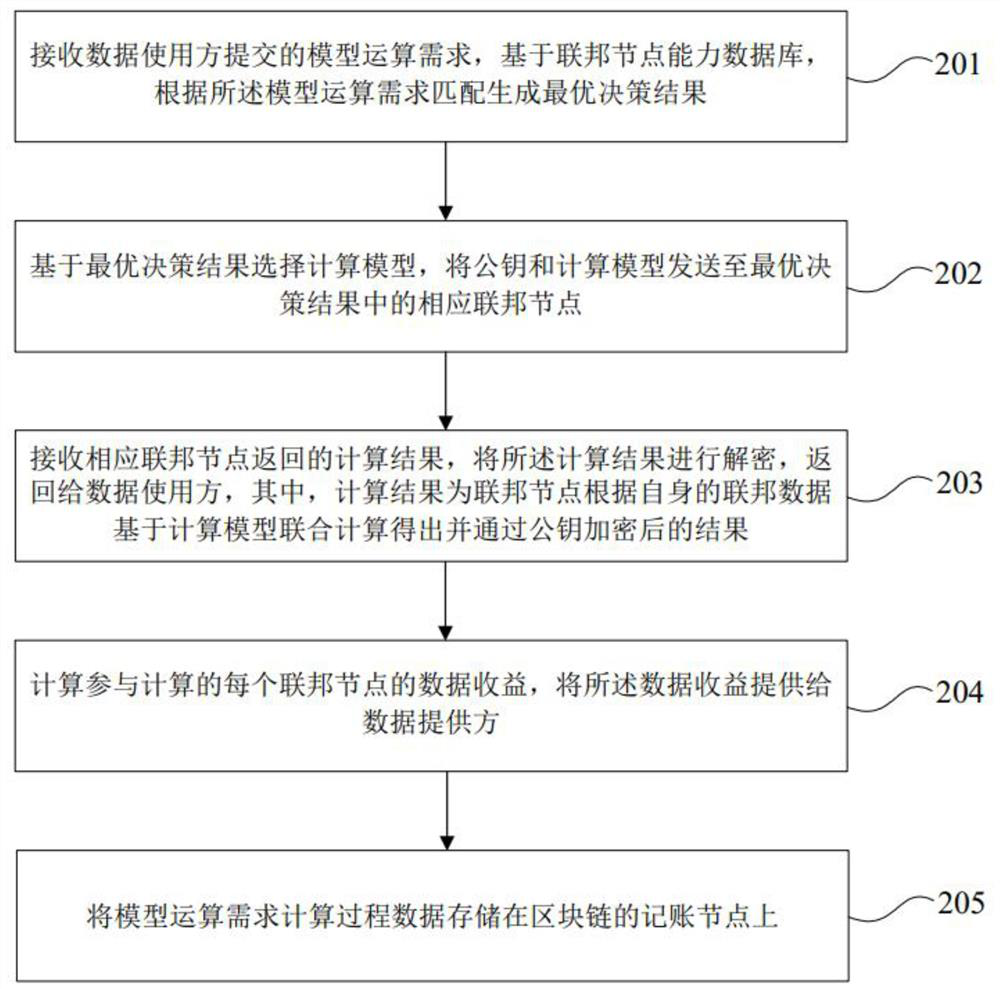
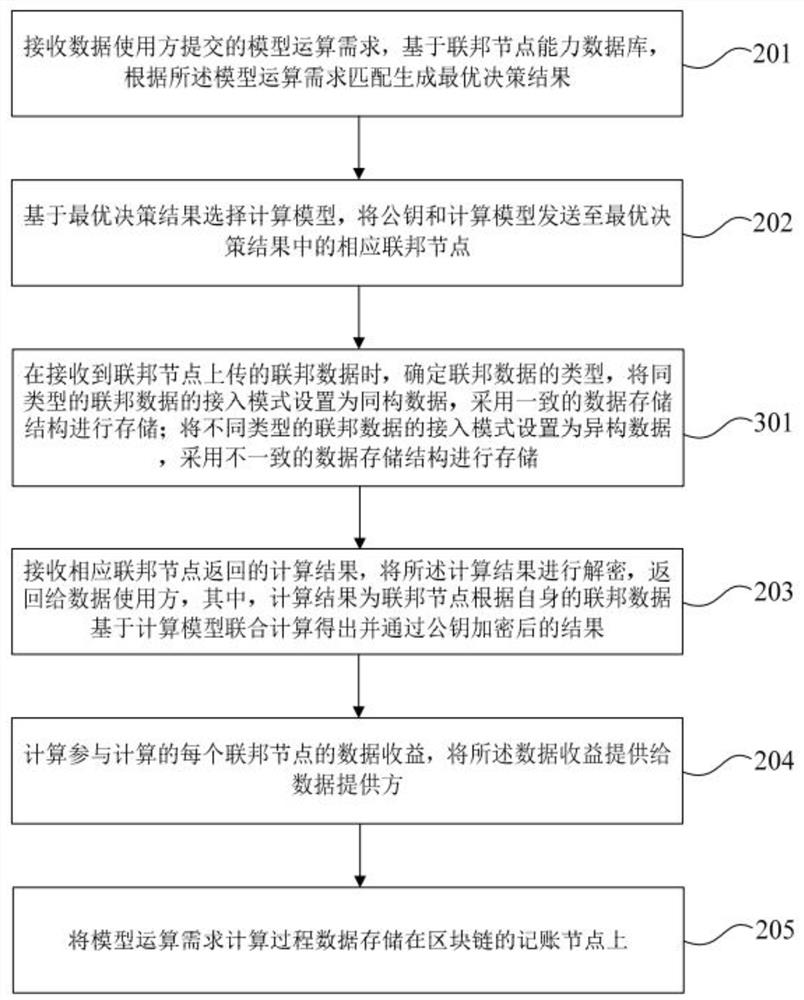
ActiveCN113204795AFederalizeResolve trust issuesDatabase distribution/replicationDigital data protectionOptimal decisionData provider
The invention discloses a data sharing method and device based on federal data and federal service. The method comprises the following steps: receiving a model operation demand submitted by a data user; on the basis of the federated node capability database, generating an optimal decision result through matching according to model operation requirements; selecting a calculation model based on the optimal decision result, and sending the public key and the calculation model to a corresponding federated node; receiving a calculation result returned by the corresponding federated node, wherein the calculation result is obtained by calculation, through the federated node, based on the calculation model according to the federated data of the federated node and encryption through the public key; decrypting the result and returning to the data user; calculating the data revenue of each federated node participating in calculation, and providing the data revenue to a data provider; storing the calculation process data on an accounting node of the block chain; the data provider serving as a federal node. According to the invention, decision generation of demands of each data user is realized through a federation service mechanism, so that federation of services is realized.
Owner:数据堂(北京)科技股份有限公司
H5 non-login user session tracking method
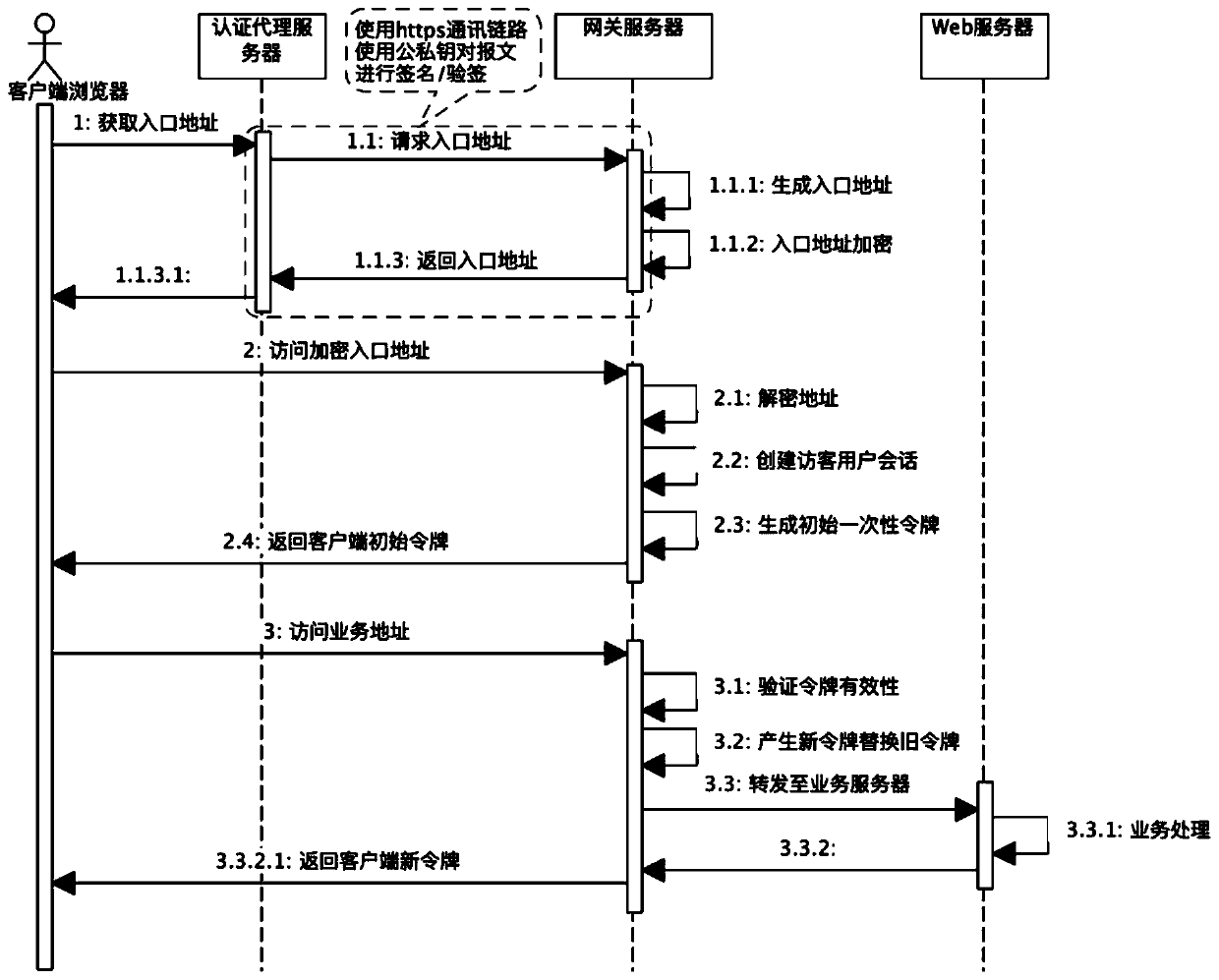
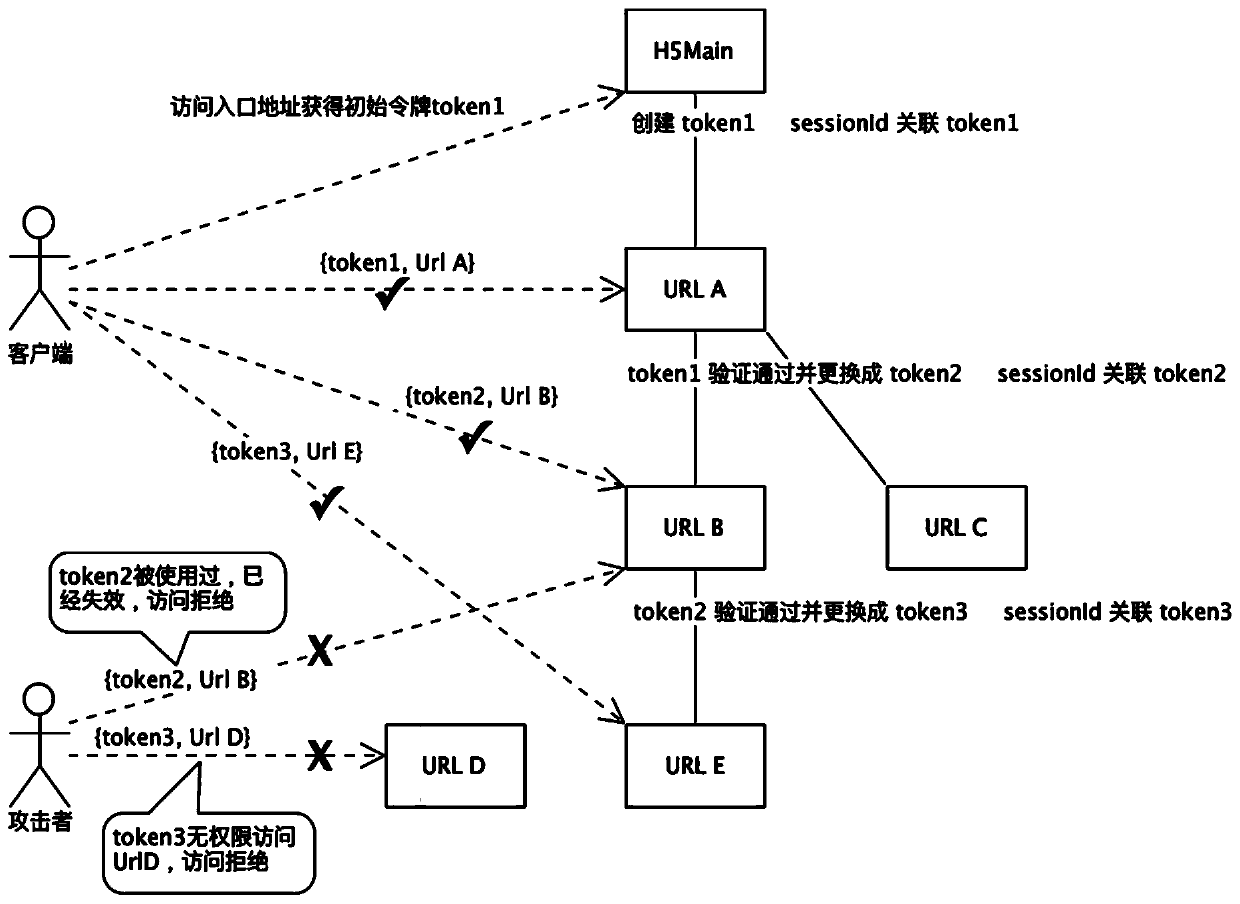
ActiveCN110933078AImprove interception rateProtect information security and operational securityTransmissionEngineeringServer-side
The invention relates to an H5 non-login user session tracking method. the method comprises: a server adopting a two-layer architecture design; the server generating an entry link address for creatinga user session; wherein the address is an entrance of all subsequent H5 services; a request for accessing the address needing to be authenticated by the server; after the user session is successfullycreated, the server issuing a one-time token to the client; wherein the token is used for user identity confirmation in the subsequent request process, sending the token to the server side along withthe user request, the token being immediately invalid after the server side passes the verification, and then the server side creating a new token and issuing the new token to the user for the next request to confirm the identity of the user. Compared with the prior art, effective user login can be realized in a scene that a client browser cannot provide user password input or other identity authentication capabilities, the illegal request interception rate of malicious attackers can be improved, and the development cost and the maintenance cost are reduced.
Owner:BANK OF COMMUNICATIONS
Blockchain consensus method and device
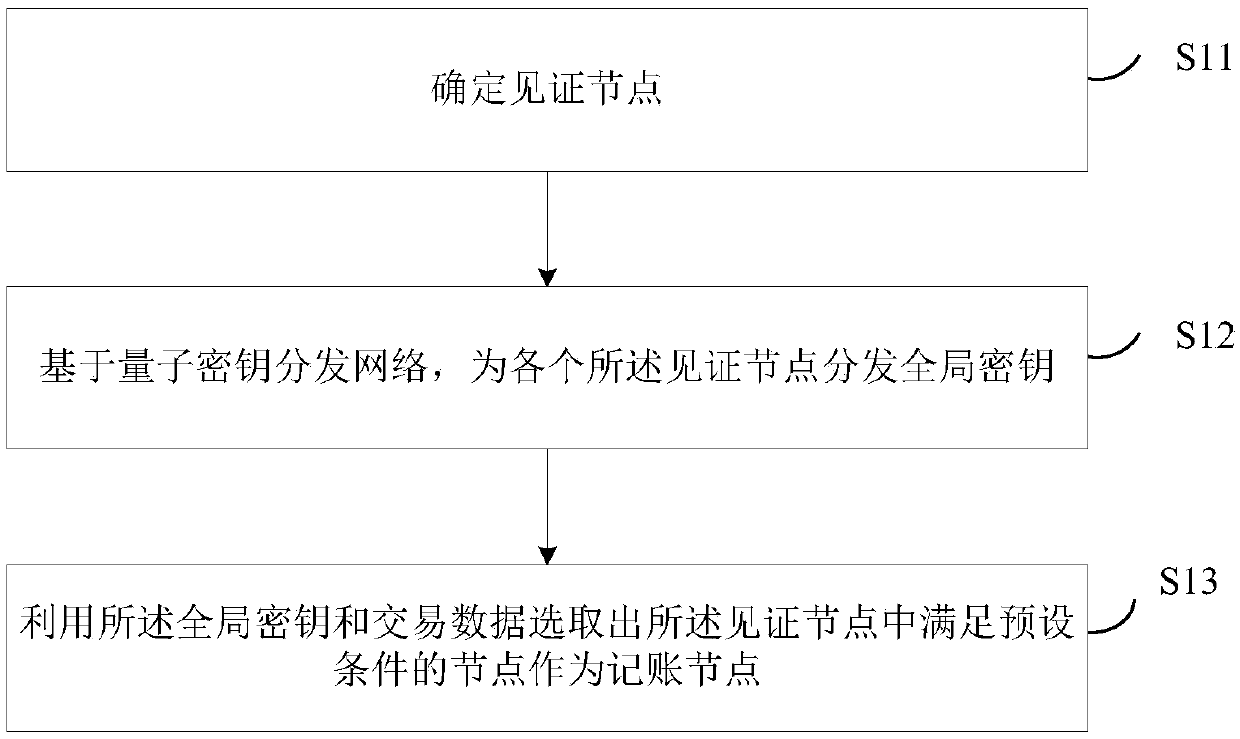
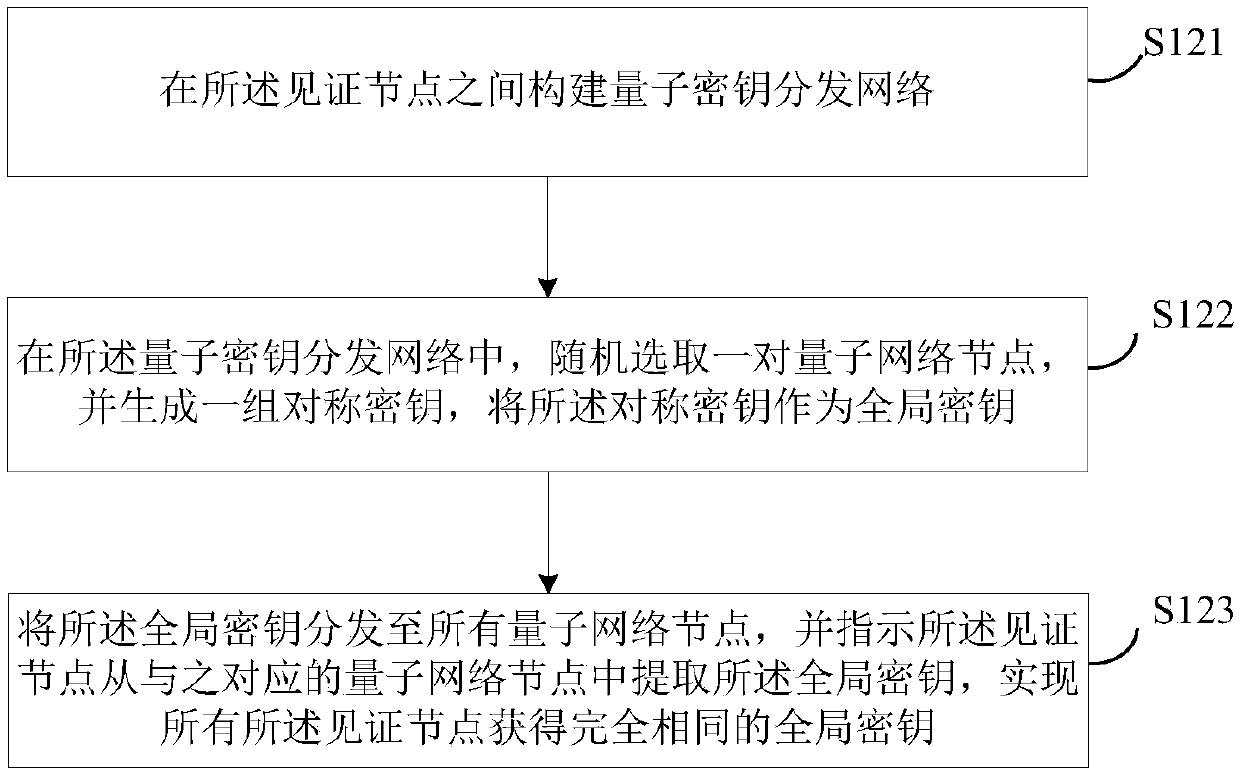
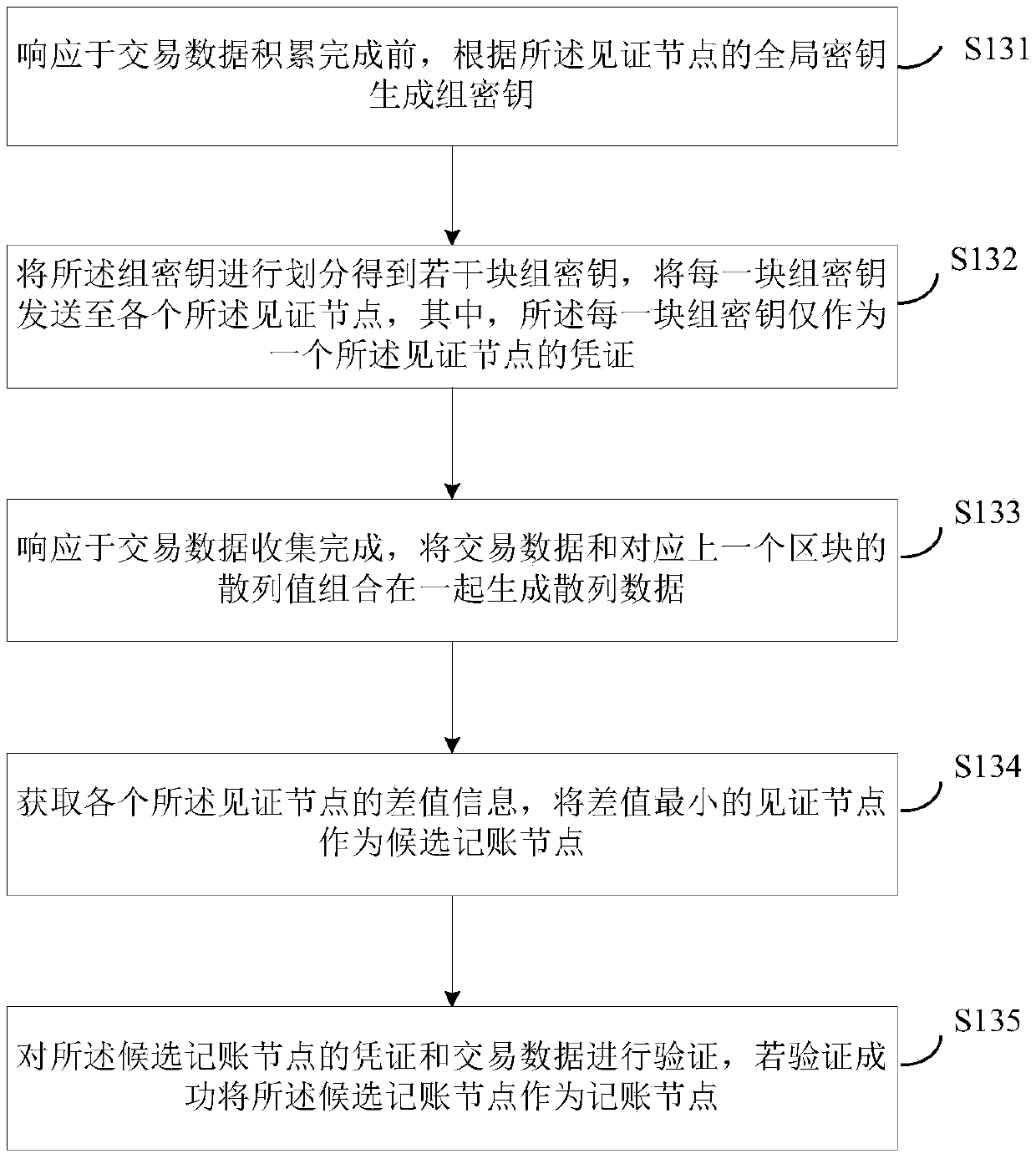
ActiveCN111104678AResolve trust issuesSolve the problem of fair selection of accounting nodesFinanceDigital data protectionBlockchainConsensus method
The invention discloses a blockchain consensus method and a device. The method comprises the steps of determining a witness node; distributing a global key to each witness node based on a quantum keydistribution network; and selecting a node satisfying a preset condition from the witness nodes as an accounting node by using the global key and the transaction data. Due to the fact that all witnessnodes share the global secret key, the nodes meeting the preset conditions are selected through the global secret key, namely the accounting nodes are obtained through selection of the quantum lottery ticket mechanism, the trust problem of the witness nodes and the problem of fair selection of the accounting nodes in the witness nodes are solved on the basis of use of the quantum secret key.
Owner:北京国盾量子信息技术有限公司 +1
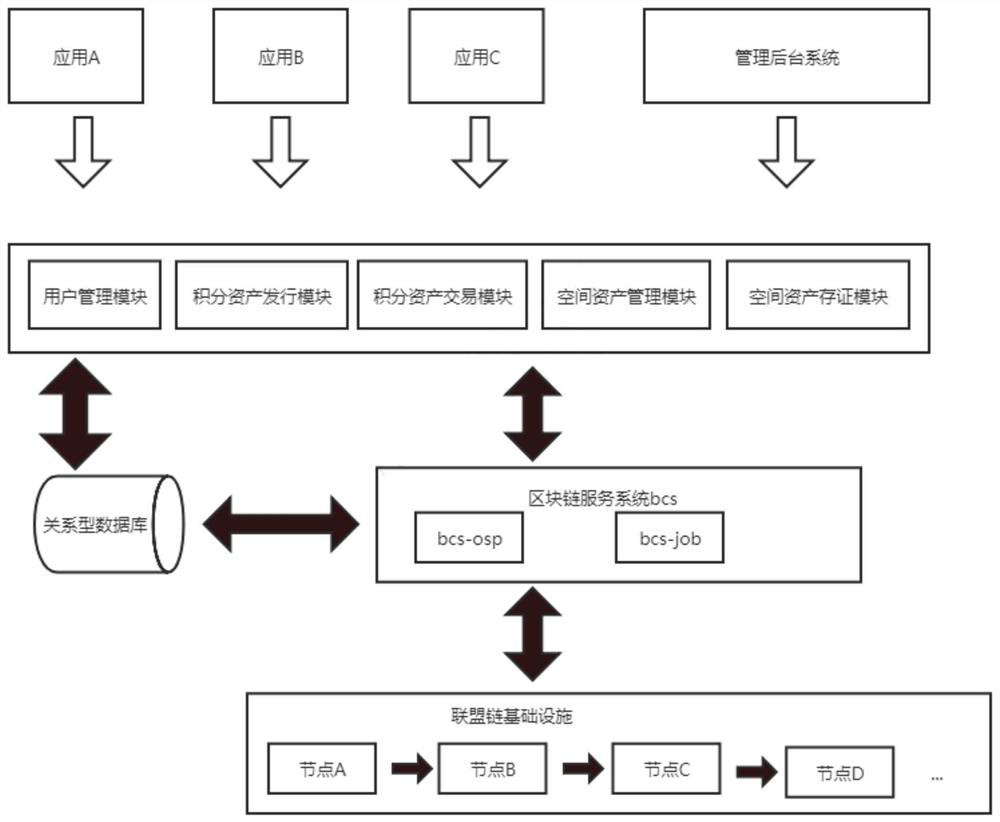
General asset commercial ecosystem based on blockchain
InactiveCN112328689AResolve trust issuesCooperate wellFinanceDatabase distribution/replicationRelational databaseFinancial transaction
The invention discloses a general asset business ecosystem based on a blockchain, which comprises an integral and space asset management function module, and further comprises more than one application, a management background system, a relational database and an alliance chain which are respectively connected with the integral and space asset management function module, wherein the alliance chaincomprises more than four nodes; and the integral and space asset management function module comprises a user management module, an integral asset issuing module, an integral asset transaction module,a space asset management module and a space asset evidence storage module. According to the method, the characteristic that the blockchain cannot be tampered is utilized, and a trustworthy commercialecosystem can be established. The credits generated by the user in each partner application can be used in other partner applications. The universal asset circulation problem of partner applicationsis solved, the cooperation between the applications is enhanced, and the trust problem between franchise nodes is solved.
Owner:广州点点办公科技有限公司
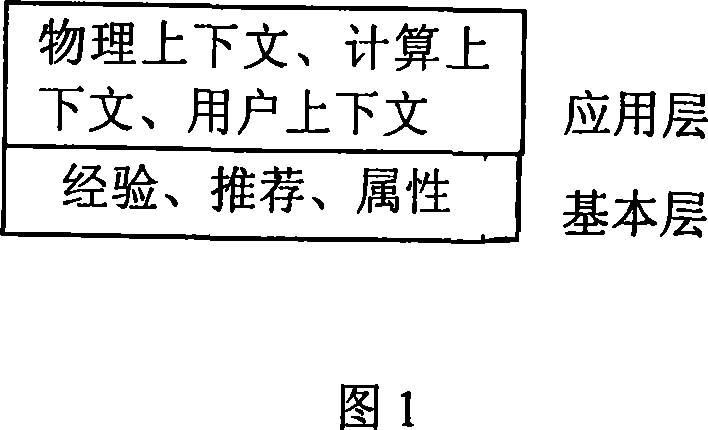
Method for building hierachical trust model in open system
InactiveCN101039178AResolve trust issuesEasy to operateData switching by path configurationSecuring communicationExtensibilityOperability
The invention discloses a method for establishing level trust model in an open system. According to the characteristic of trust and the characteristic of the open system, the method divides the element which effects trust into two layers, bottom layer and basic trust layer. The element comprises property, recommendation and experience. The method mainly solves the initial trust creation of a strange entity. The upper layer is a trust layer, determined by application context. The application trust layer is established on the base of the basic trust layer. The invention can be applied in open system for safety decision-making, has the advantages of extensibility and good maneuverability, etc.
Owner:HUAZHONG NORMAL UNIV
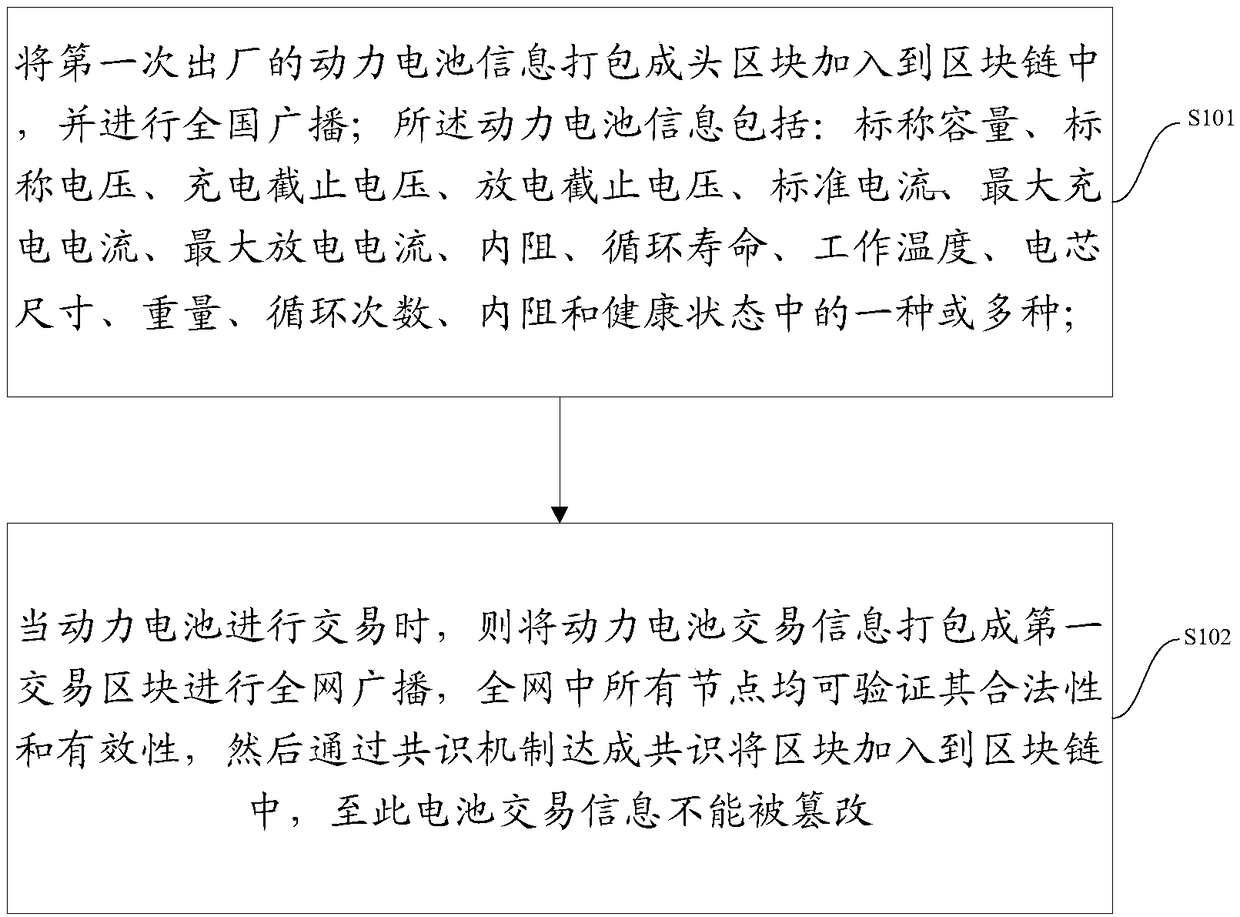
A traceability method of power battery cascade utilization based on block chain technology and a system thereof
InactiveCN109165530AResolve trust issuesRealize uploadDigital data protectionPayment protocolsOperating temperatureBlockchain
The invention relates to a traceability method of power battery cascade utilization based on block chain technology and a system thereof. The method comprises the following steps: packaging the powerbattery information of the first shipment into a head block and adding the head block into the block chain, and broadcasting nationwide, wherein the power battery information comprises one or more ofa factory number, an information ID, a cell material, a nominal capacity, a nominal voltage, a charging cut-off voltage, a discharging cut-off voltage, a standard current, a maximum charging current,a maximum discharging current, a DC internal resistance, an operating temperature, a cell size, a weight, a number of cycles and a healthy state of the battery; when the power battery is traded, packaging the trading information of the power battery into a first trading block for broadcasting throughout the network, wherein all nodes in the network can verify its legitimacy and effectiveness, andthen adding the block into the block chain by a consensus mechanism. The invention realizes the functions of uploading, storing, inquiring, encrypting and decrypting the data of the whole battery supply chain, and the data is open, transparent, traceable and non-alterable.
Owner:深圳汽航院科技有限公司
Trusted product transaction system realizing method and realizing system
InactiveCN105844484ASave the cost of counterfeitingResolve trust issuesCustomer relationshipRelational systemE-commerce
The present invention relates to the field of electronic commerce, and provides a reliable product transaction system realization method and realization system, and establishes a user-based user relationship system based on trusted acquaintances in the real society to control product transactions or product promotion levels, without restrictions Products with trustworthy qualifications continue to trade, restrict products that do not have trustworthy qualifications from continuing to recommend, prevent products from being traded or advertised at the level of untrustworthy users, and check products at all levels through trusted acquaintances in the real society, and trade products Or product promotion is always controlled within the trustworthy range, effectively solving the trust problem, so that users can shop online with confidence; and because users in the trusted user level are acquaintances in the real world, it is easy to form a community of interests, and the system can explore the community of interests. Allow users within the trusted hierarchy to benefit.
Owner:郭英
User privacy protection crowd sensing system based on block chain
ActiveCN110602694APrivacy protectionResolve trust issuesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesNetwork packetUser privacy
The invention discloses a user privacy protection crowd sensing system based on a block chain, and the system is characterized in that a first mobile terminal issues a task to a main block chain, andthe main block chain consists of a first mobile terminal and a second mobile terminal; according to a second mobile terminal participating in the task, a plurality of sub-block chains are created according to a preset creation rule; a second mobile terminal located in the sub-blockchain collects data according to the task and encrypts the data, and the second mobile terminal uploads the data to apreset data packet according to a preset random sequence list; and one of the second mobile terminals uploads the data packet to the main block chain. By adopting the method and the device, on the premise that the user can accurately upload the data, the data cannot be matched with the corresponding user, so that the privacy of the user is protected.
Owner:南方电网互联网服务有限公司
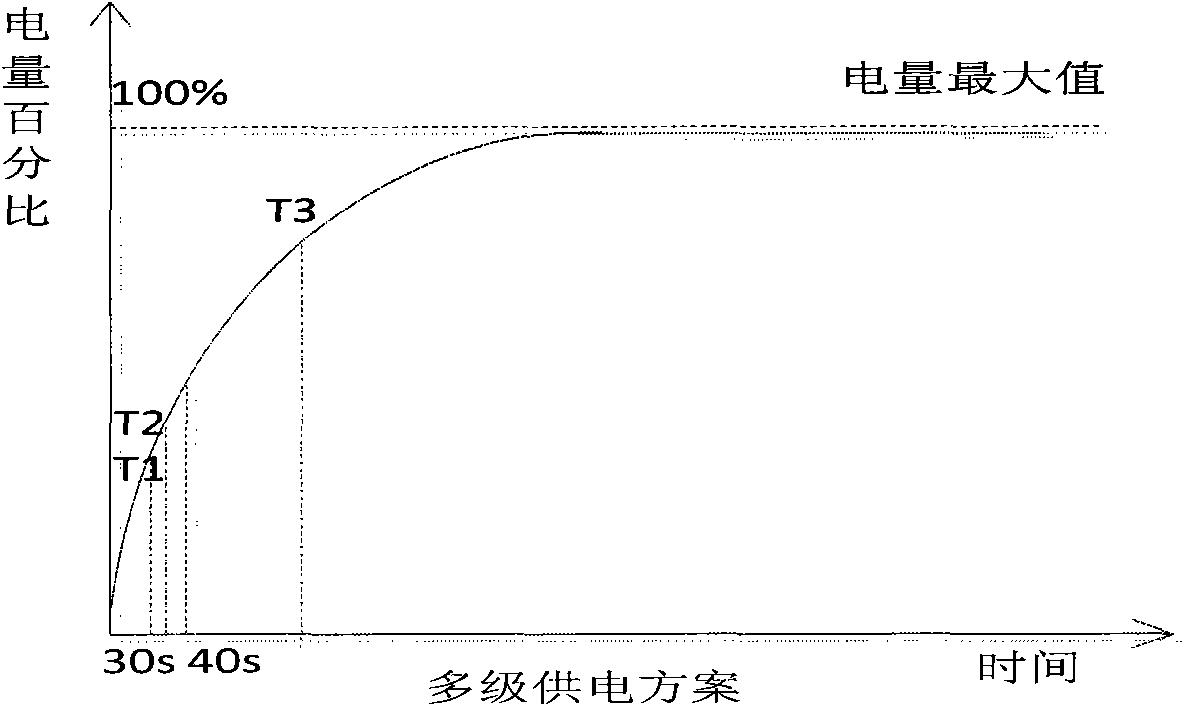
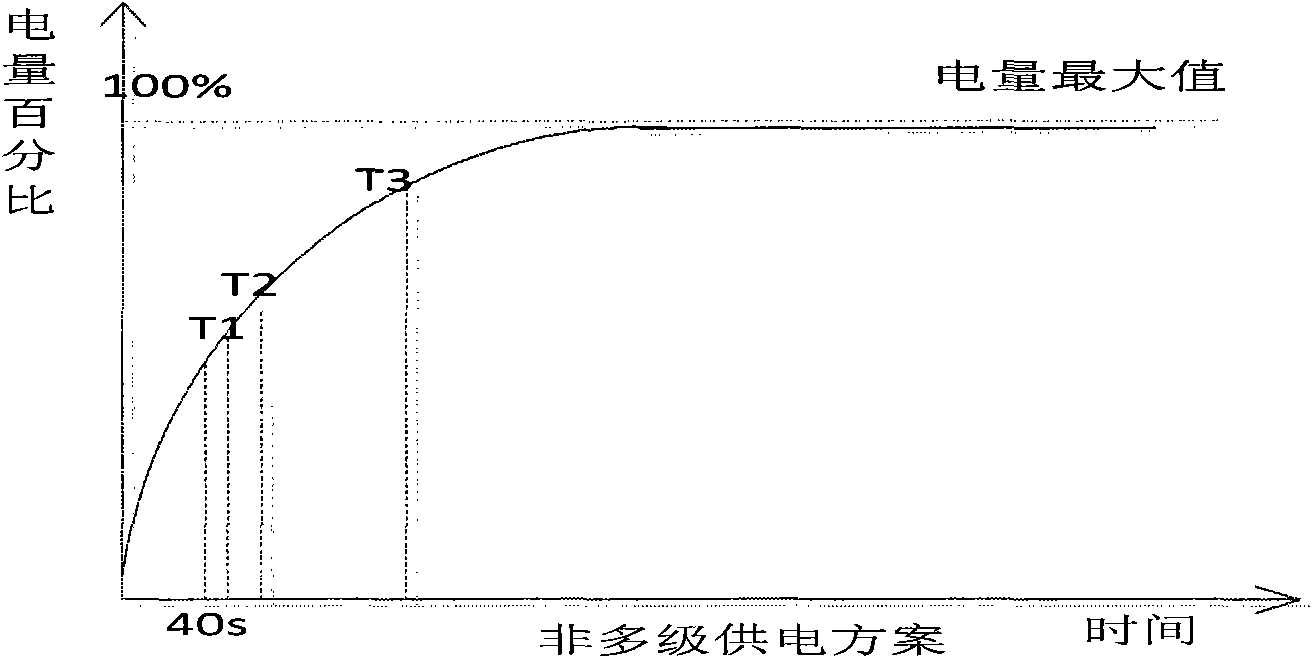
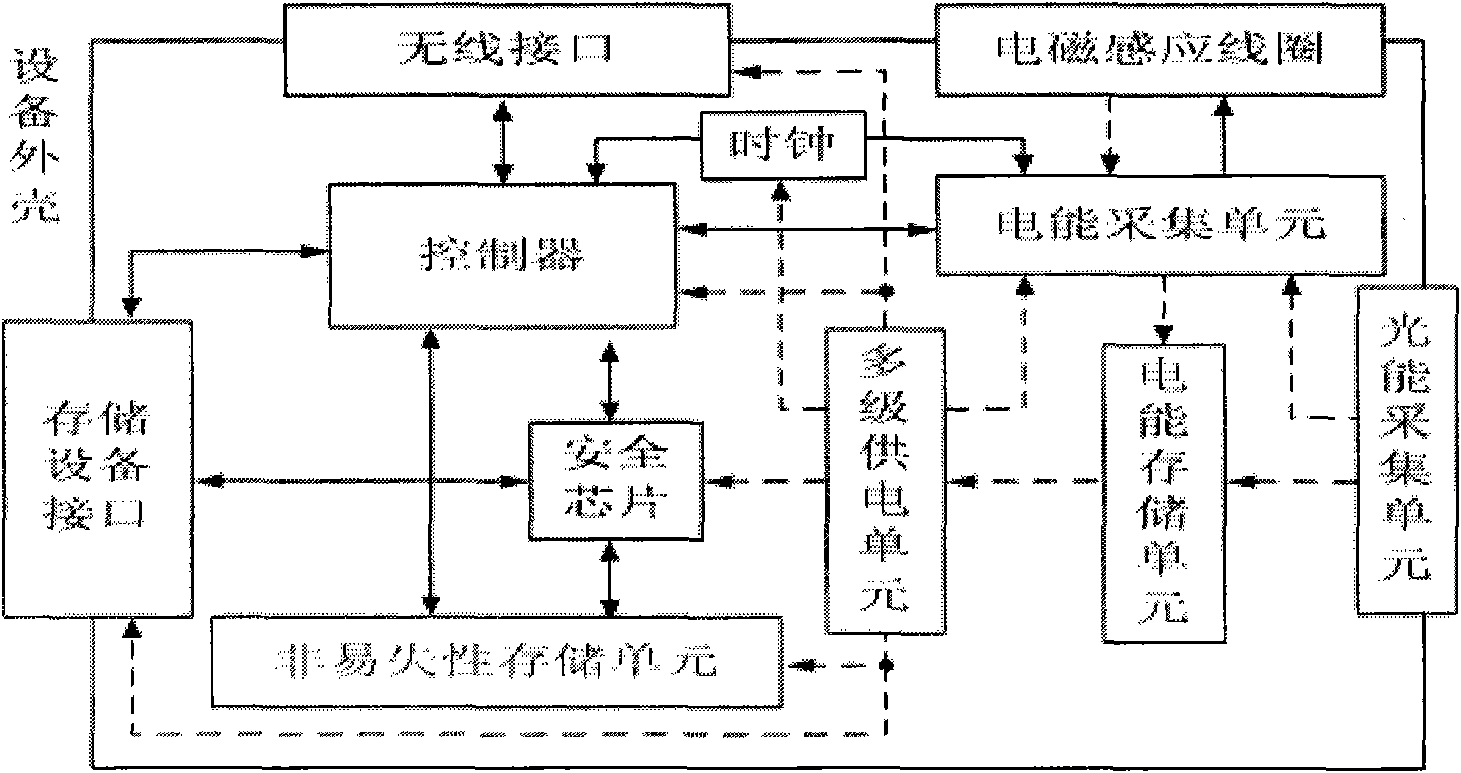
Trusted wireless storage equipment for wireless power supply and application method thereof
InactiveCN102063942AEnsure safetyRealize functionEnergy efficient ICTRead-only memoriesWireless transmissionComputer network
The invention discloses trusted wireless storage equipment for wireless power supply and an application method thereof, and relates to the field of secure information storage. A secure chip is a root of trust of the trusted wireless storage equipment and is a core module of the trusted wireless storage equipment. The invention points out information security problem in a wireless transmission process of the wireless storage equipment and provides a new trusted wireless storage solution for the wireless power supply. Each chip in the trusted wireless storage equipment for the wireless power supply is powered in turn according to a multi-stage power supply method, so that a system can quickly switch to a normal working state, and energy consumption is reduced to the greatest extent. Reliable power guarantee is provided for the trusted wireless storage equipment for the wireless power supply by various power supply methods. A trusted storage method guarantees confidentiality and completeness of data during interaction of the trusted wireless storage equipment for the wireless power supply and a computer and the confidentiality of the data during the interaction of the trusted wireless storage equipment and the storage equipment.
Owner:BEIJING UNIV OF TECH
Electronic case history folder information system based on block chain and IPFS
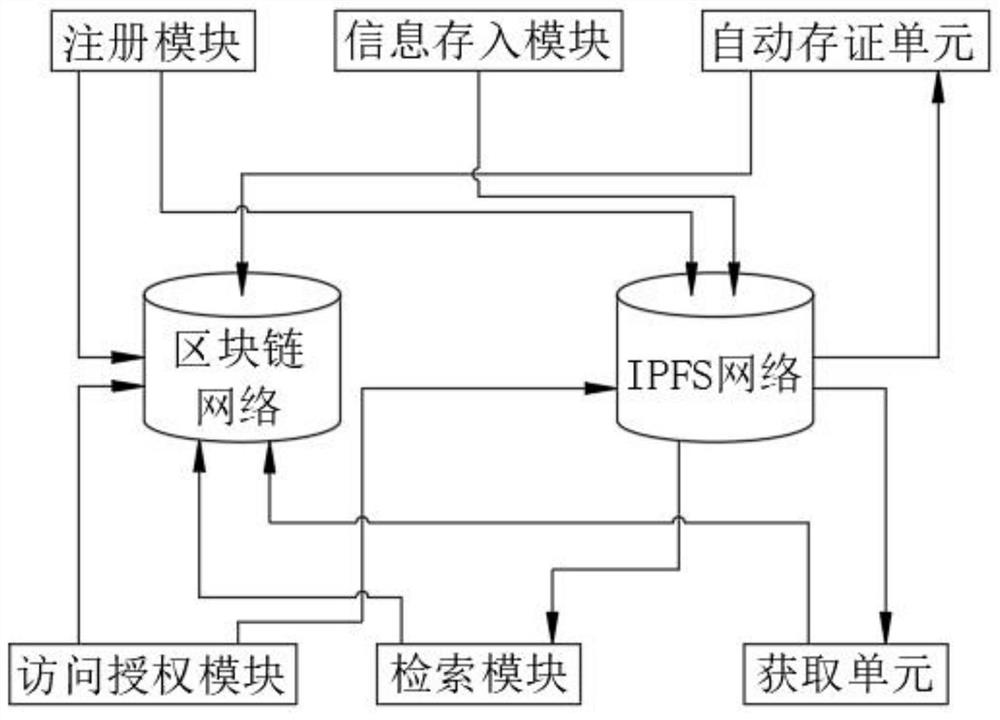
PendingCN112735552AAchieve self-managementAchieve sharingDatabase distribution/replicationDigital data protectionMedical recordEngineering
The invention provides an electronic case history folder information system based on a block chain and an IPFS, and belongs to the field of medical information management, and the system comprises a registration module, an information storage module, an automatic evidence storage unit, an authorized access module, a retrieval module and an acquisition unit. According to the invention, a patient can autonomously manage own electronic medical records, including authorized access by the patient and completely eradication of access to the electronic medical records without authorization of the patient; the trust problem of the electronic medical record sharing and developing process is solved, permanent storage of the electronic medical record is achieved, tampering cannot happen, and retrieval and modification are traceable. And safe sharing of electronic medical records is ensured. And meanwhile, the storage and transmission of the electronic medical record can be safely, efficiently and quickly processed.
Owner:上海信医科技有限公司
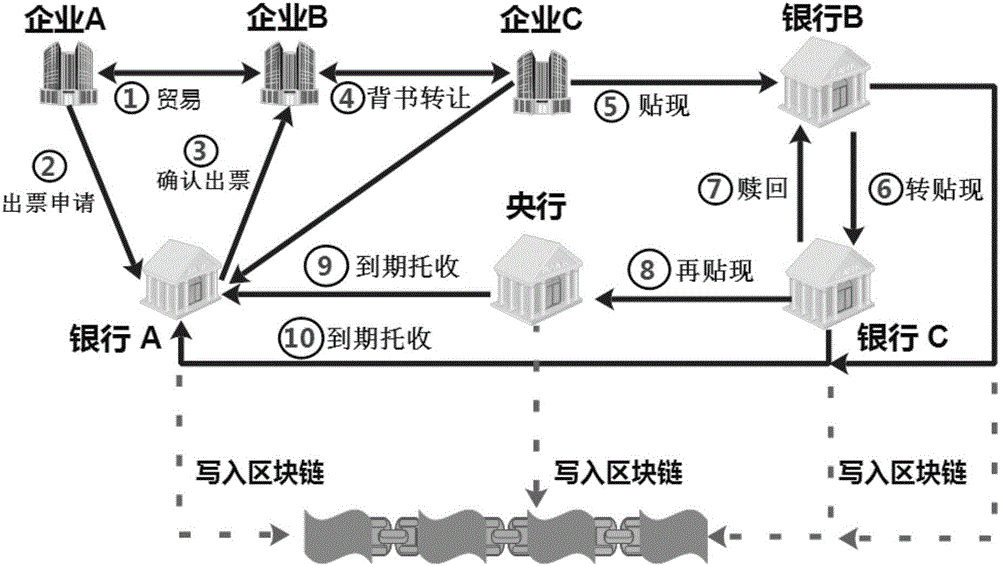
A bill discount transaction matching method based on a block chain
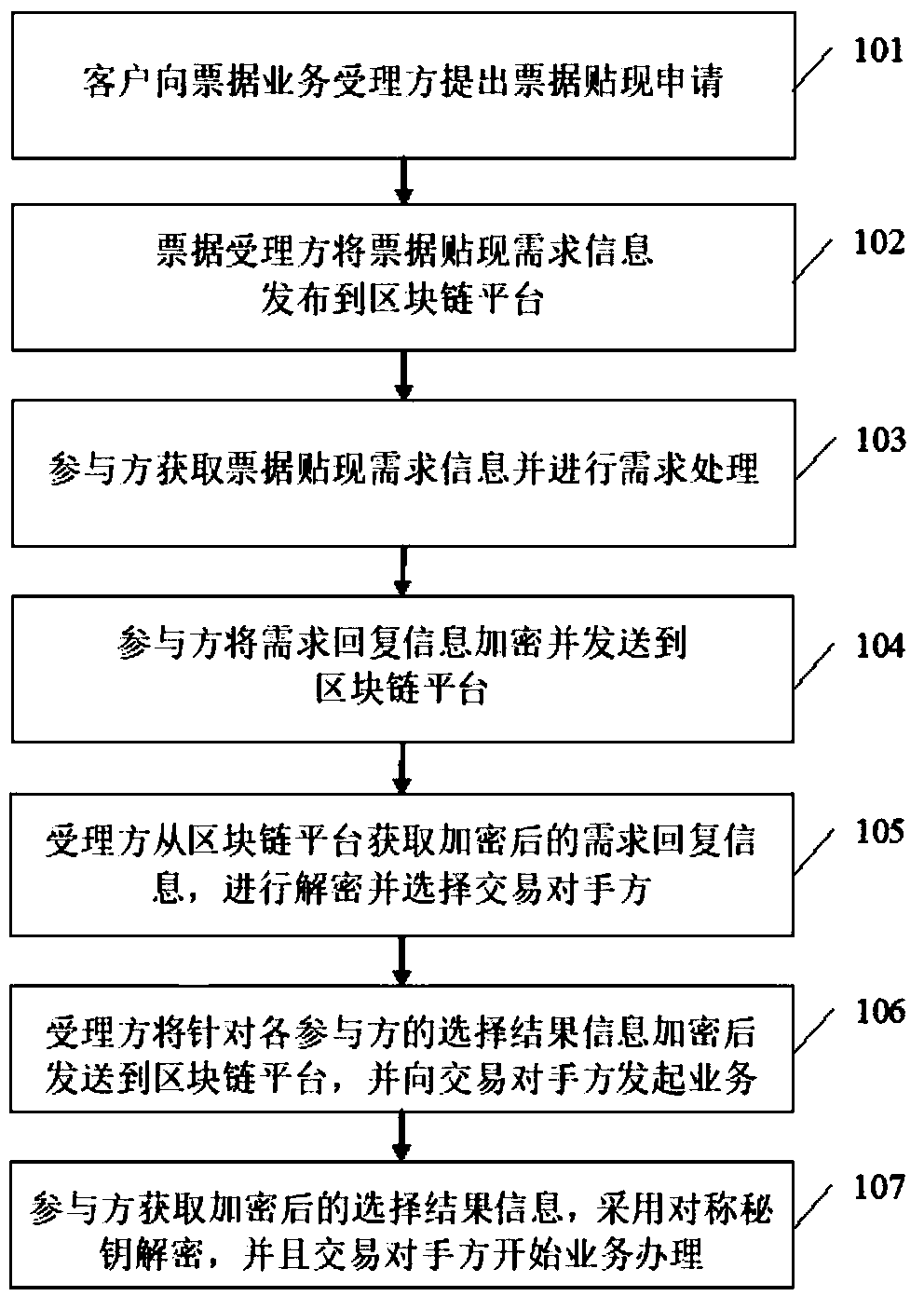
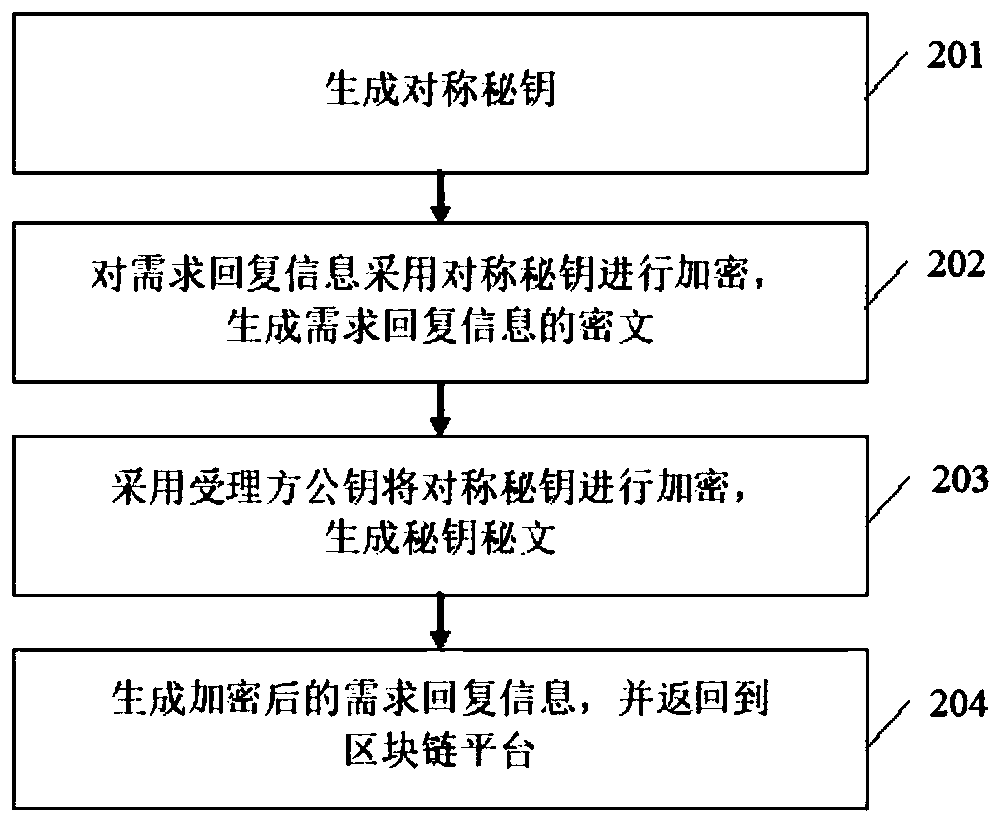
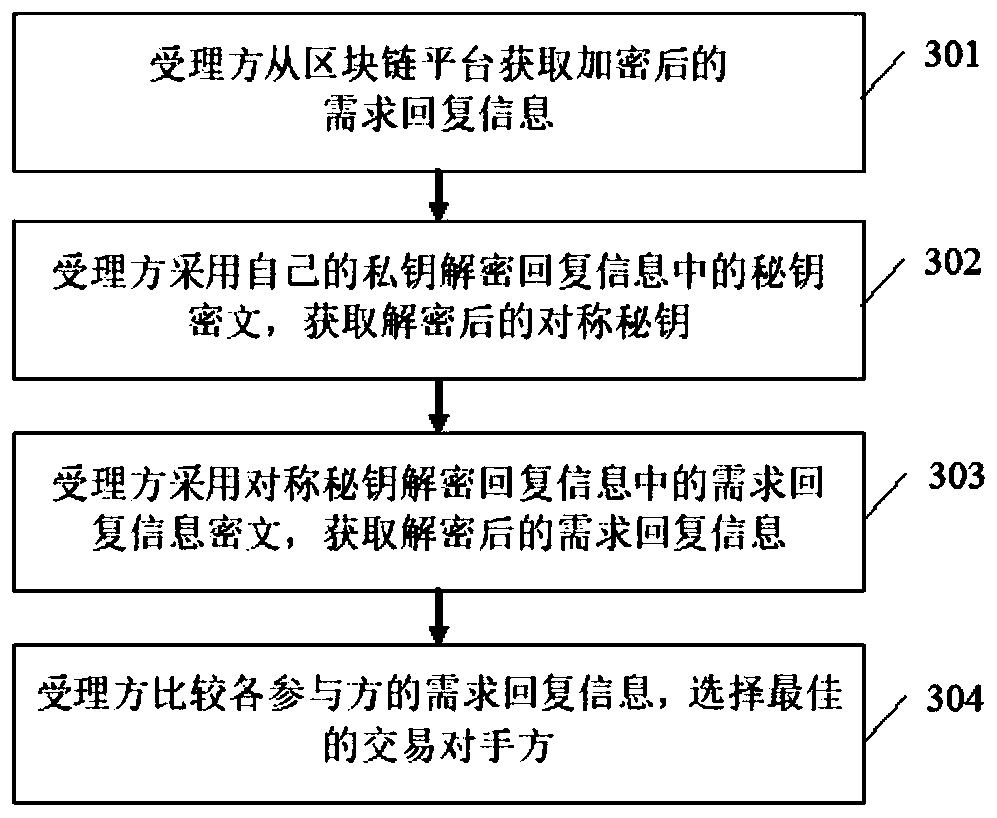
InactiveCN109377359AGuard against market risksResolve trust issuesFinanceTransmissionComputer scienceOperating system
The invention provides a bill discount transaction matching method based on a block chain. The bill business acceptor converts the bill discount application information into bill discount demand information and publishes it to the block chain platform. Participants obtain bill discount demand information from the block chain platform and form demand response information; The participant encrypts the demand response information and sends it to the block chain platform. The acceptor obtains the encrypted demand response information from the block chain platform, decrypts it and selects the counterparty among the participants; The acceptor encrypts the selection result information of each participant and sends it to the block chain platform, and initiates the bill discount service to the counterparty. After obtaining the encrypted selection result information, the participant is decrypted, and the participant selected as the counterparty starts the processing of bill discount business. The invention fully utilizes the characteristics of decentralization and non-tampering of the block chain technology, solves the trust problem in bill discount transaction, establishes a credible bill transaction shared account book, and effectively prevents bill market risks.
Owner:BANK OF JIANGSU CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com