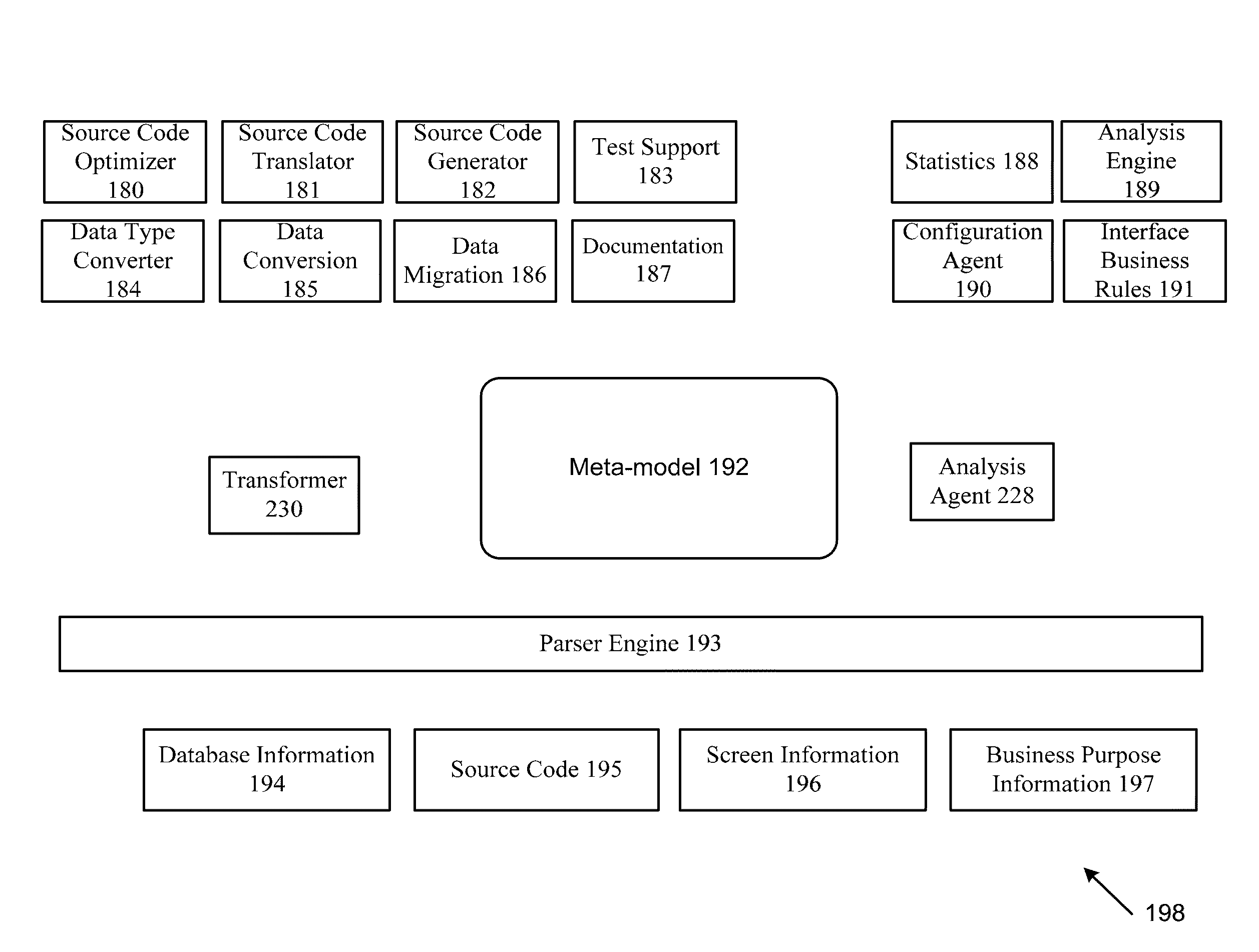
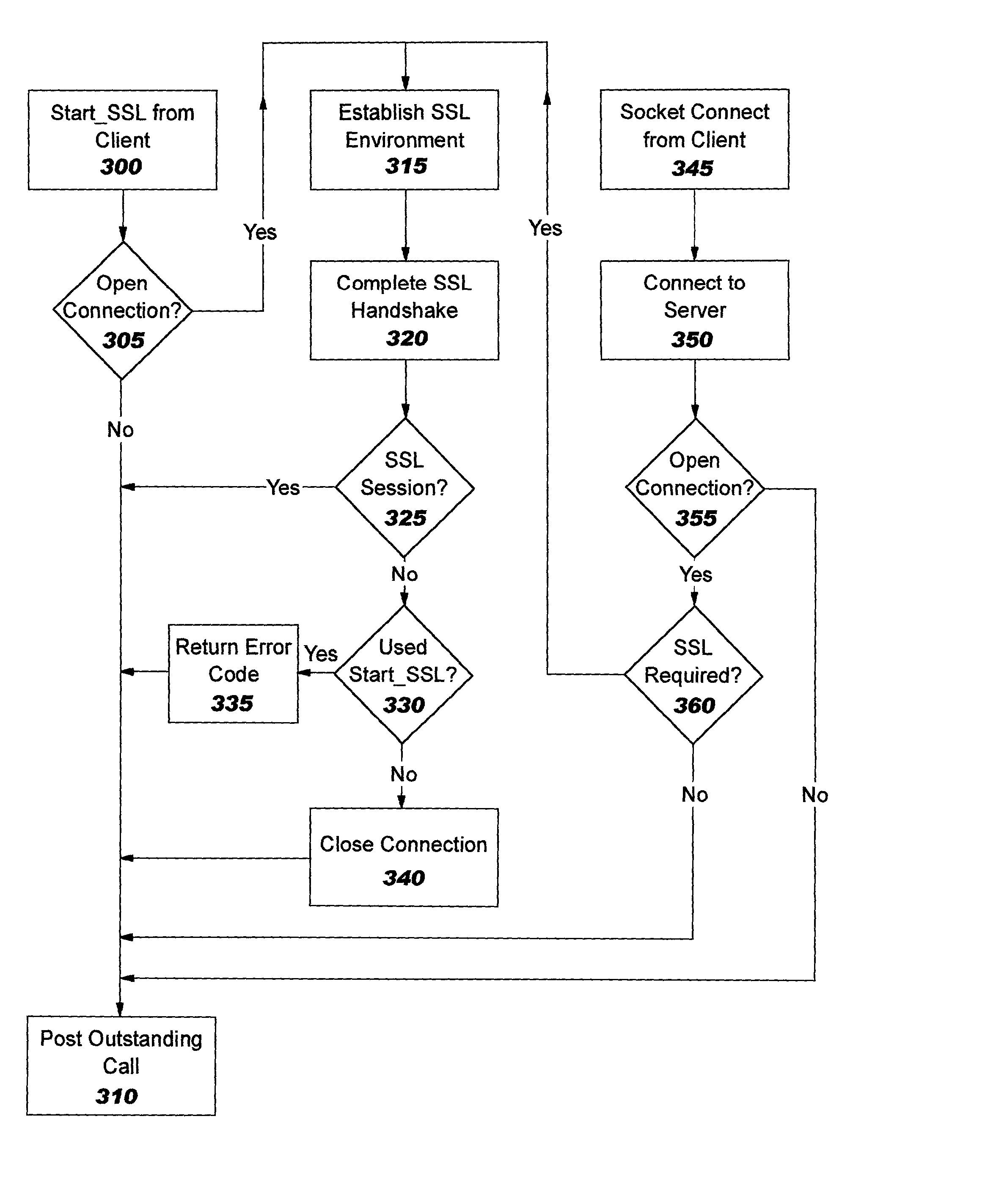
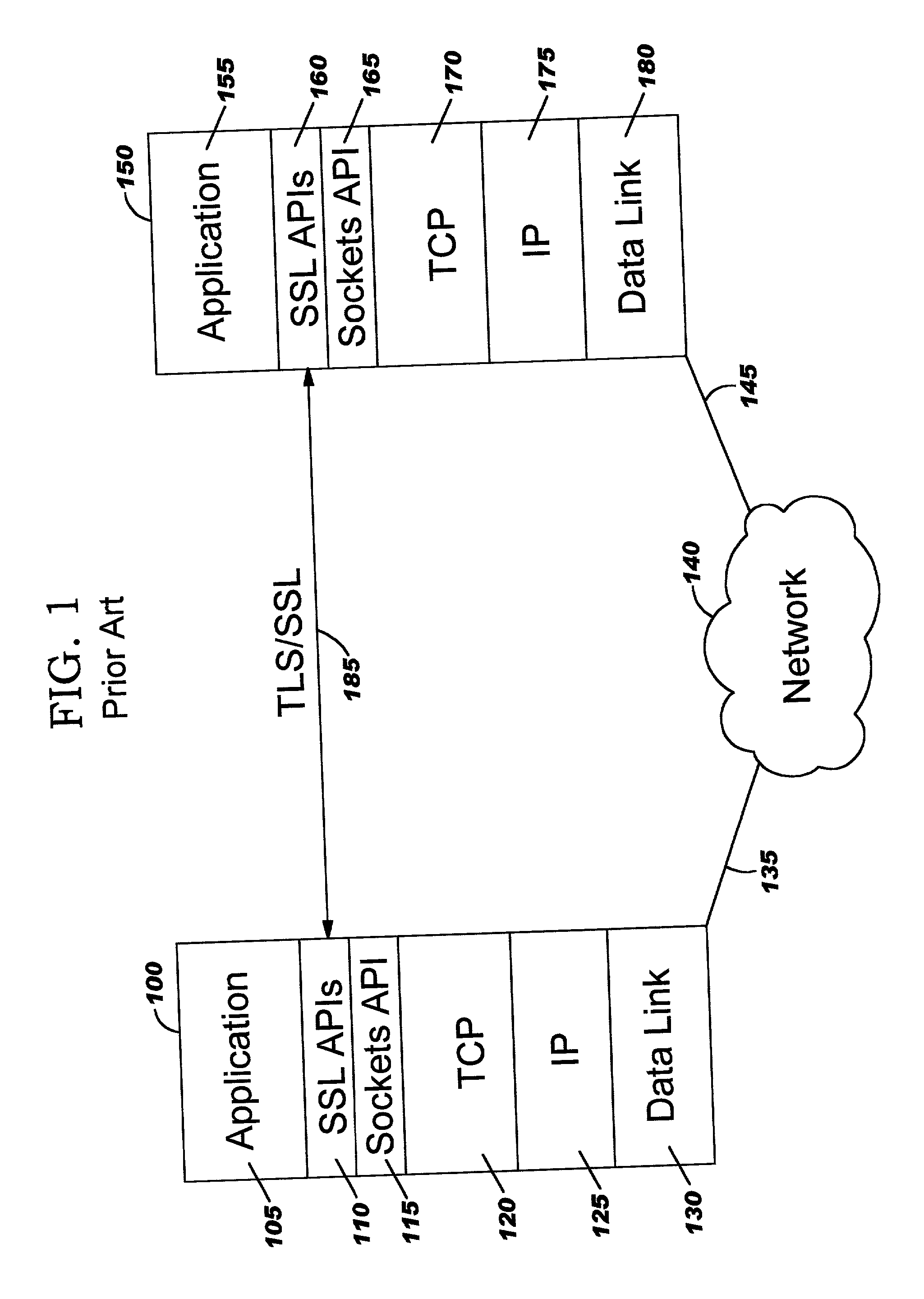
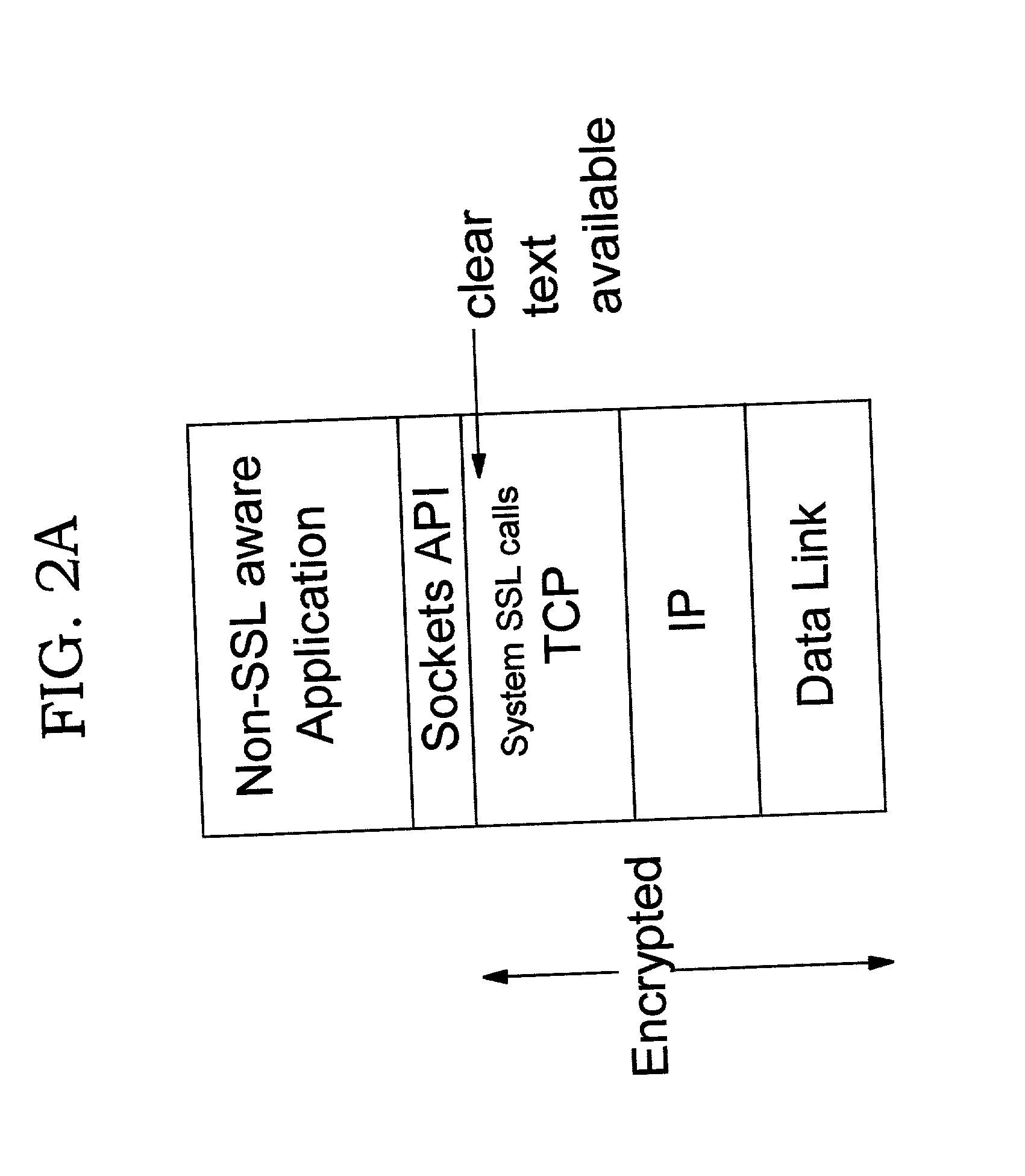
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1098 results about "Application Context" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Context is context of current state of the application/object.It’s an entity that represents various environment data . Context helps the current activity to interact with out side android environment like local files, databases, class loaders associated to the environment, services including system-level services, and more.
Method and system for providing context awareness
InactiveUS20030182394A1Easy accessInstruments for road network navigationMultiple digital computer combinationsContext awarenessData mining
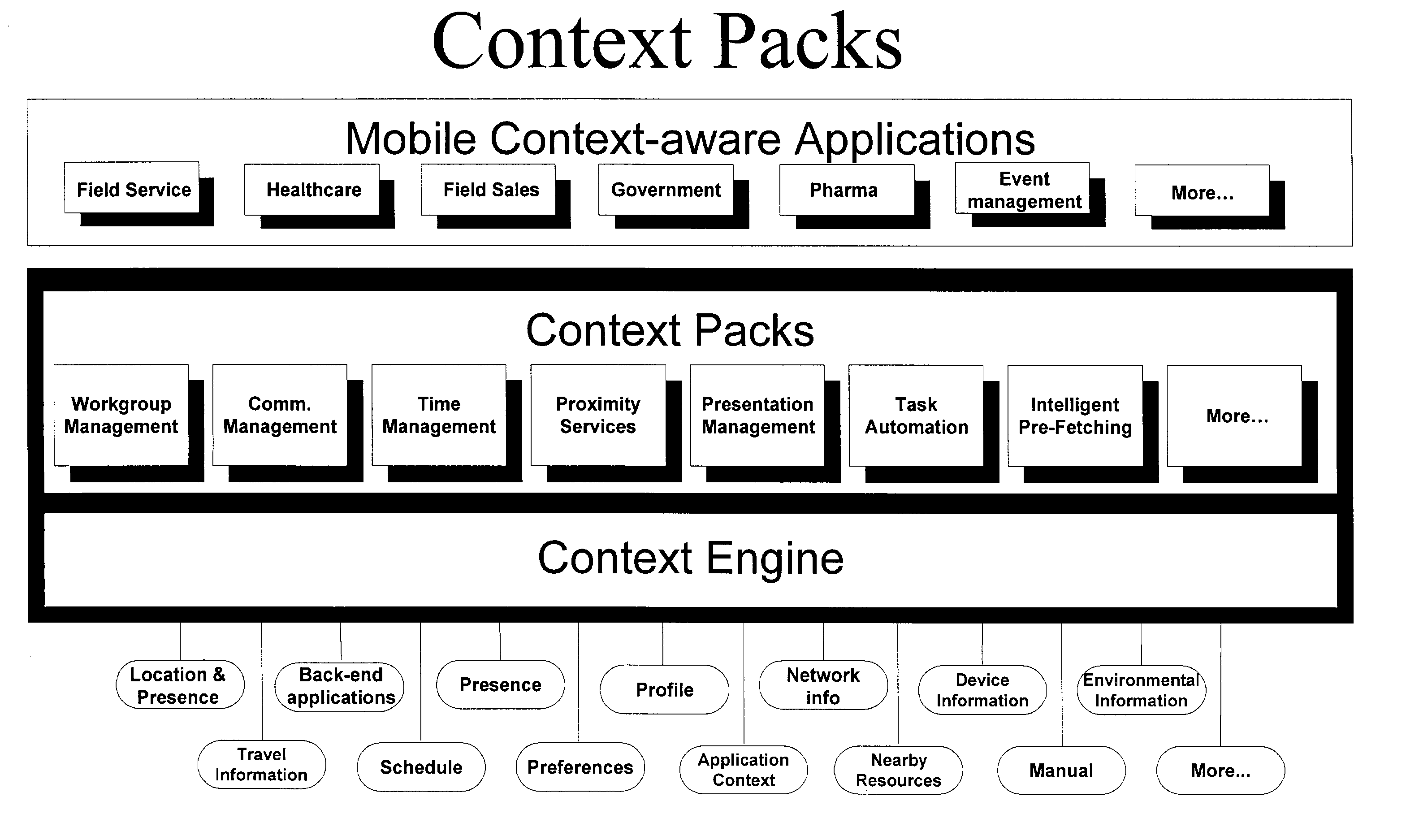
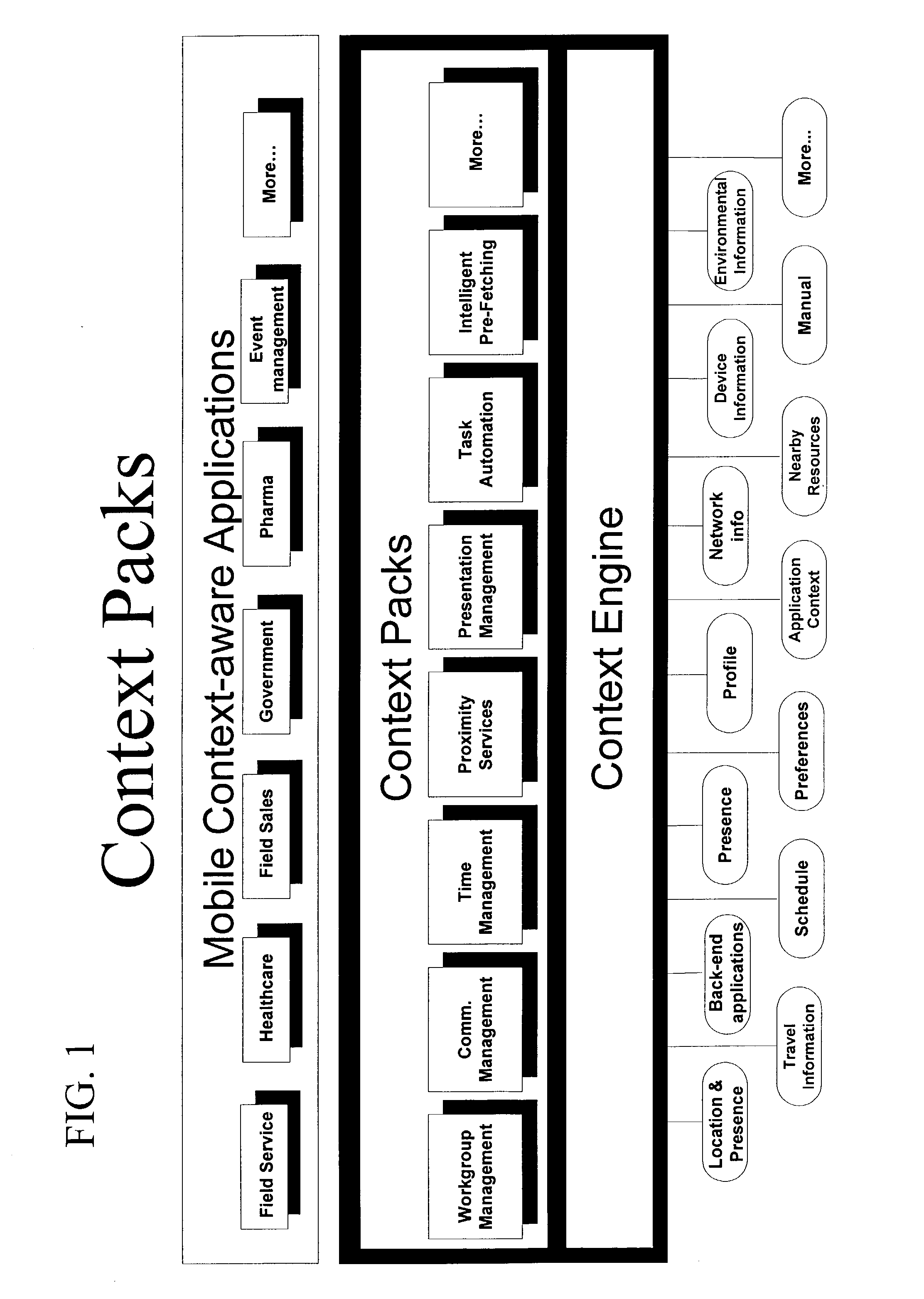
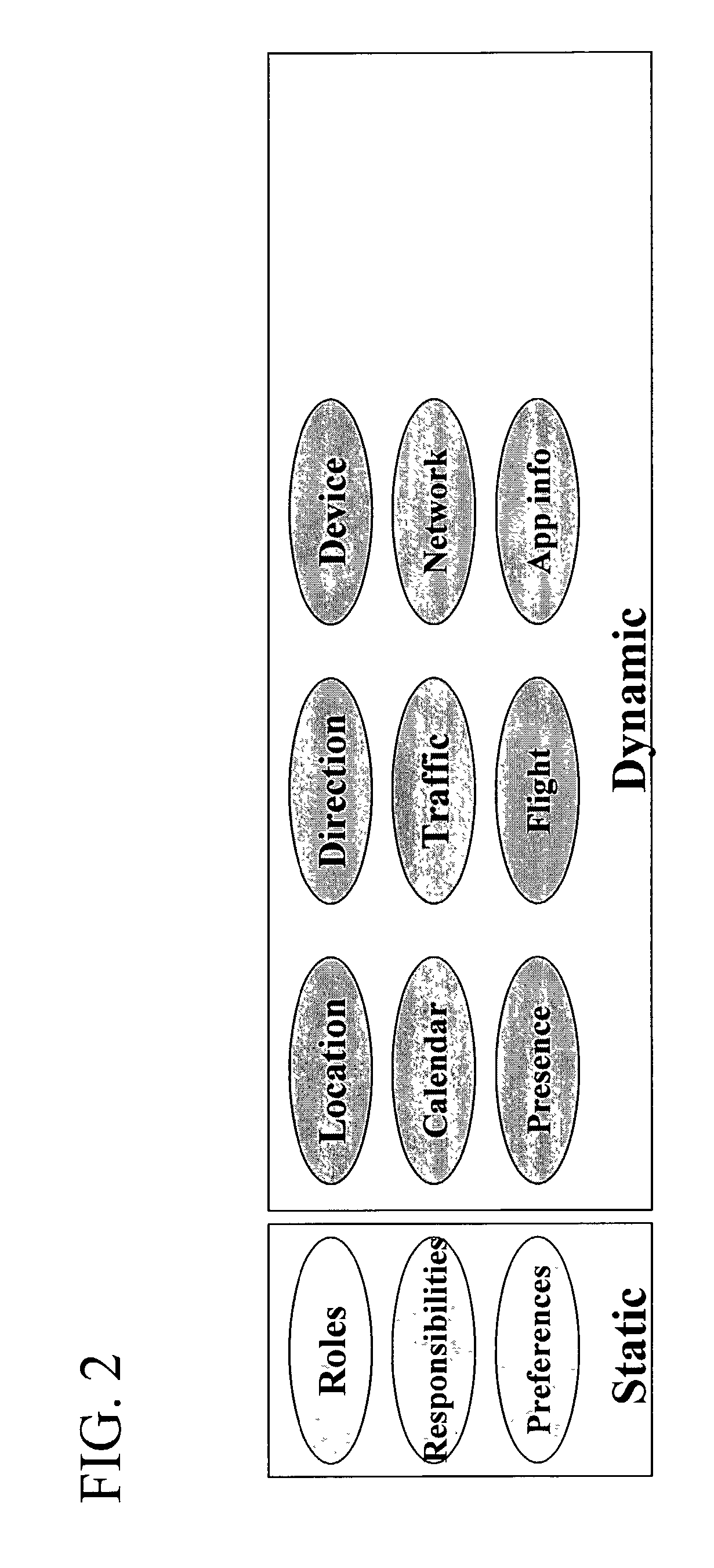
A method and system for providing context information, systems, and actions for a range of information technology platforms and interfaces. Context includes the aggregate knowledge about a user's situation and intent. Included in the system are tiers of features for enabling context awareness, including a collection tier, analysis tier, and action / effect tier. Information relating to entities, which are the elements that are included in the system, such as users and communication devices, along with states and relationships, is identified and accessed by a context engine, which obtains the information from sensors and interpreters for the information. In one application tier, the context engine is used with any set of entities, states, and relationships. Another application tier, referred to as "context packs," includes preset sets of entities, states, and relationships identified for predetermined applications.
Owner:RYNGLER OREN +5
Method and apparatus for the creation of personalized supervisory and control data acquisition systems for the management and integration of real-time enterprise-wide applications and systems
A system and method provide for the creation and operation of real-time enterprise-wide, personalize supervisory and control data acquisition systems. Personalized SCADA applications are constructed from a virtual application service and a personal agent framework using simple drag and drop operations or other high level action. The virtual application service includes a communications gateway that communicates with disparate and non-interoperable systems and external field devices to communicate low level time data collected from such systems into the application environment transforming the collected data in a single common data format. The virtual application service includes application cells that receive the reformatted data and process it to provide high level analysis and context, storing the processed data in an object server. The object server provides a unified, hierarchical object model for all of the data received from the underlying devices and systems. The virtual application service communicates with personal agent frameworks containing presentation cells and service agents. The service agents are representative of the virtual application service, and provide the personal agent framework with access to the object server to receive and send data from the object server to the presentation cells. The presentation cells subscribe to the object server's data objects via the service agent. Presentation cell provide a graphical representation and mapping of data objects and hence underlying devices and systems, to allow a user to manage and control such systems.
Owner:EUTECH CYBERNETICS PTE
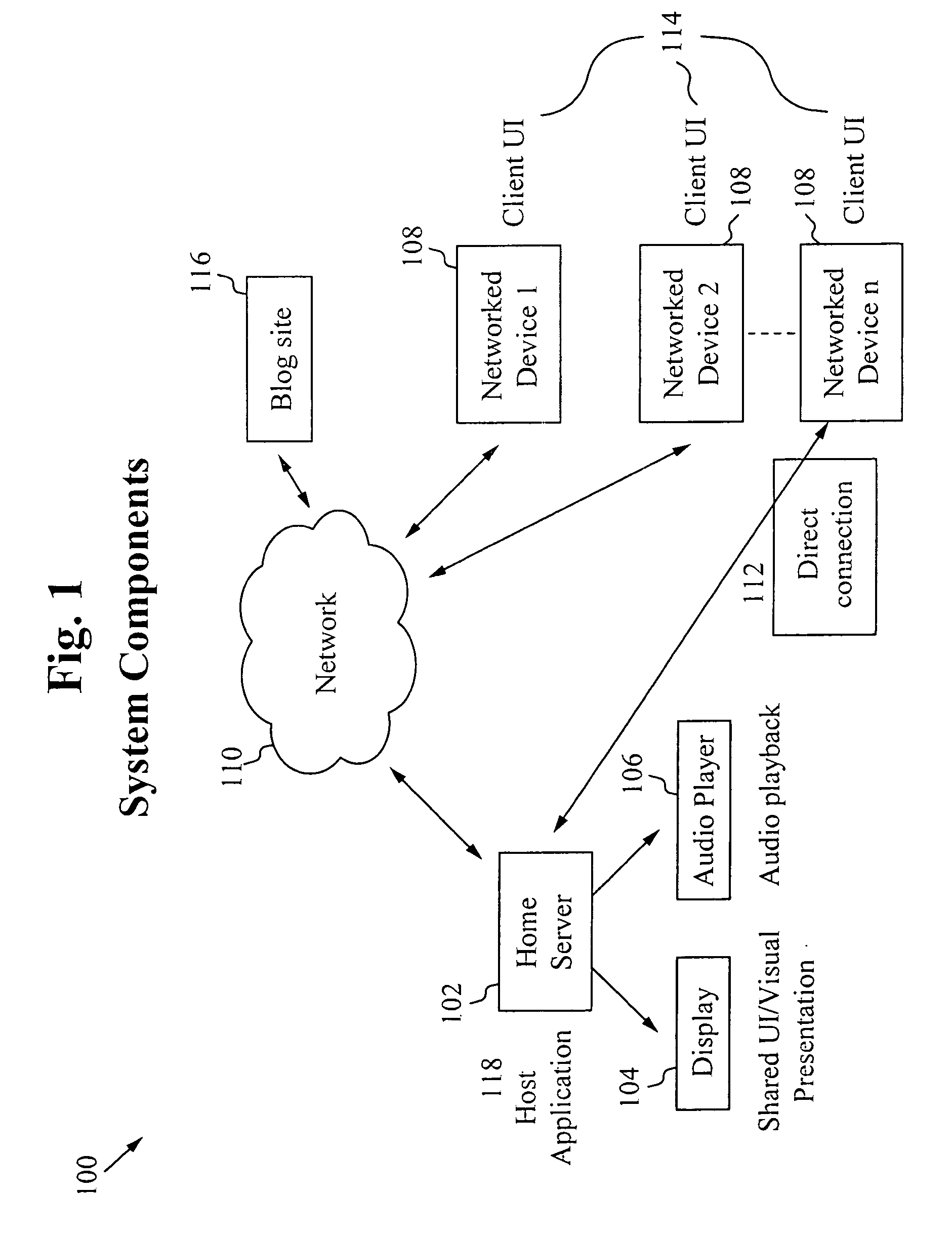
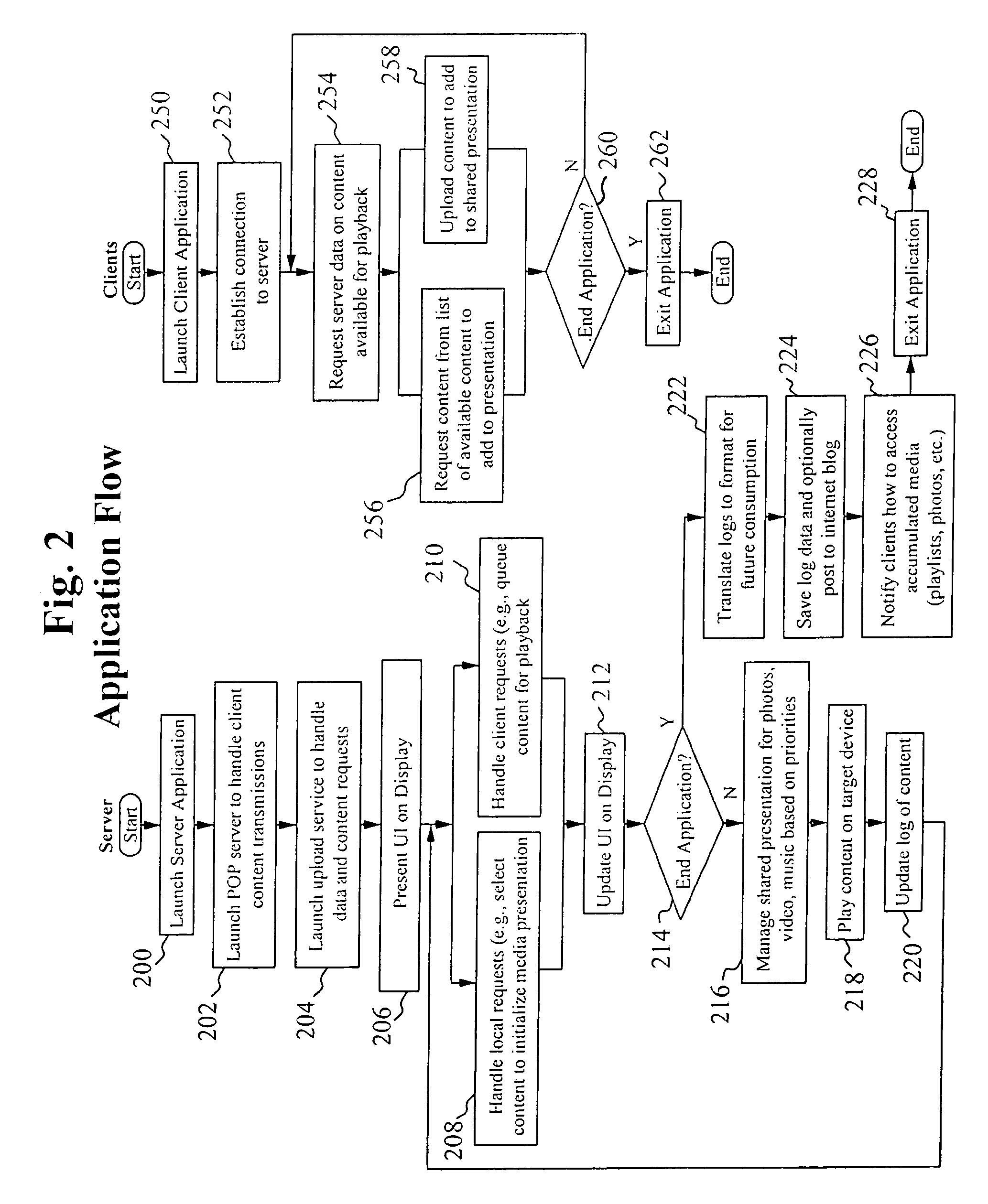
Shared home media platform to support multi-user control
InactiveUS20080184127A1Improve distributionDigital data information retrievalMultiple digital computer combinationsMedia typeApplication software
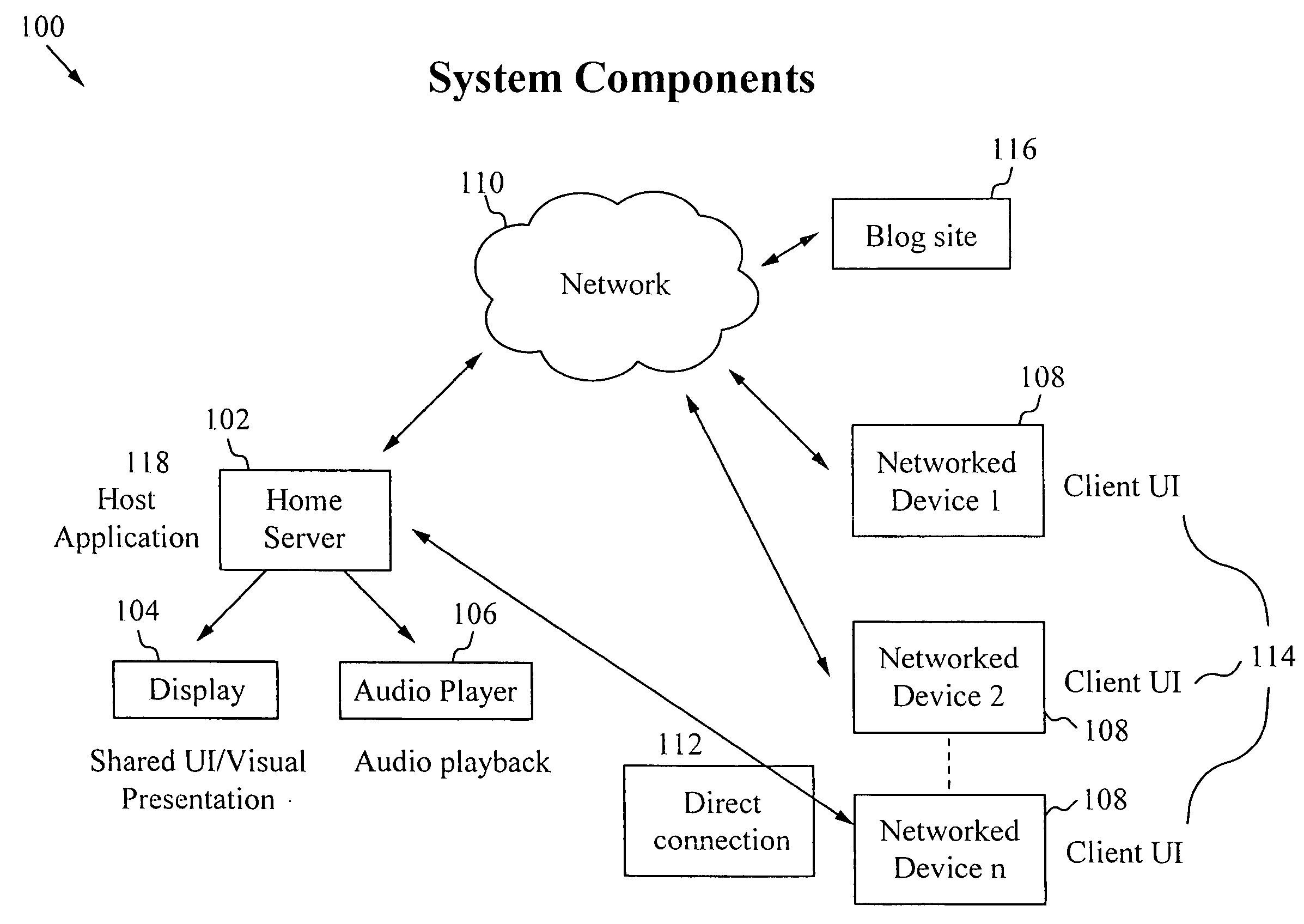
A system for and method of enabling people to share a common application context for media presentation and playback is described herein. The presentation results from input from a set of active participants where the input includes a set of media types such as music, artwork, visualizations, photographs and text messages. The participants use personal devices to couple to the system and utilize the application.
Owner:SONY CORP +1
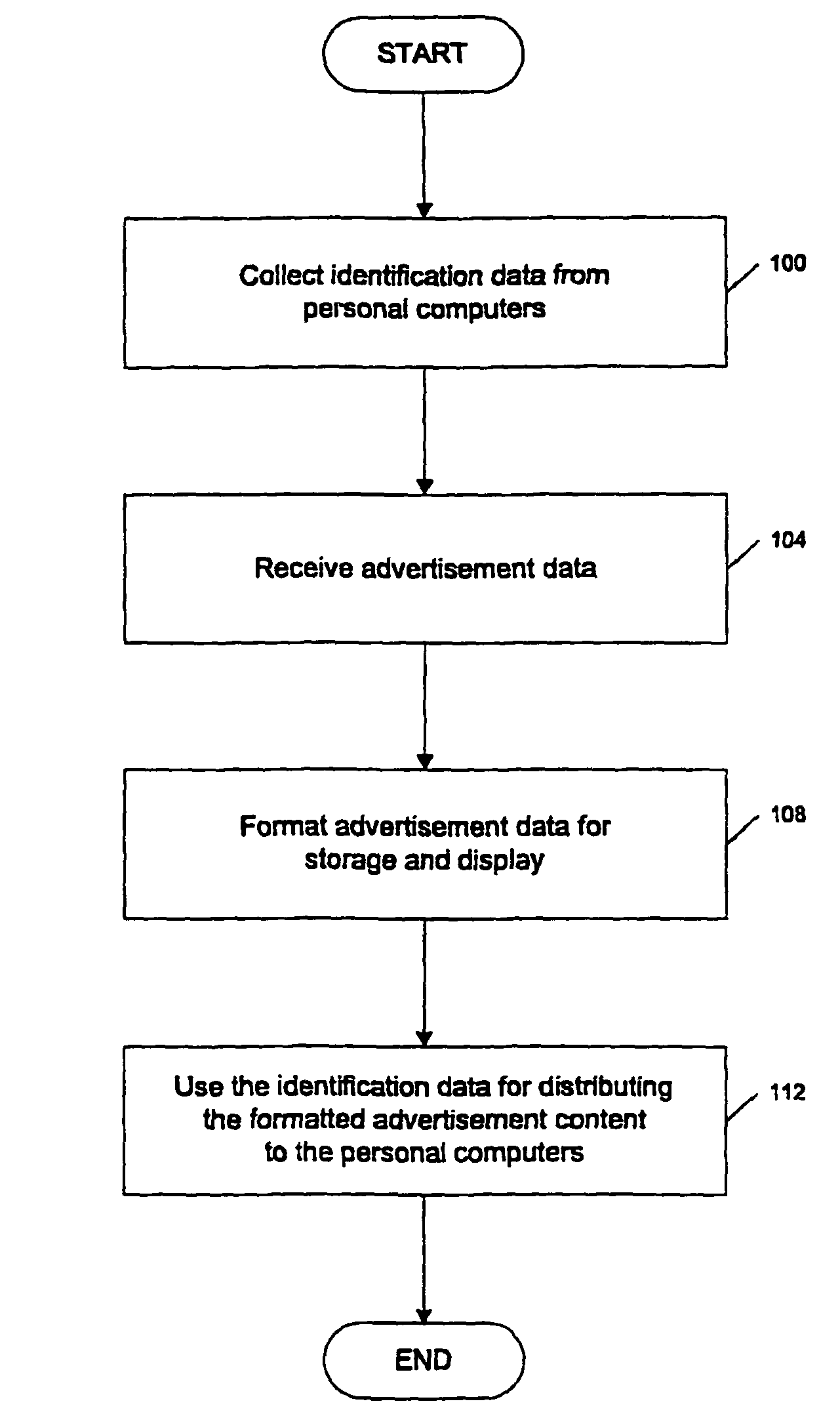
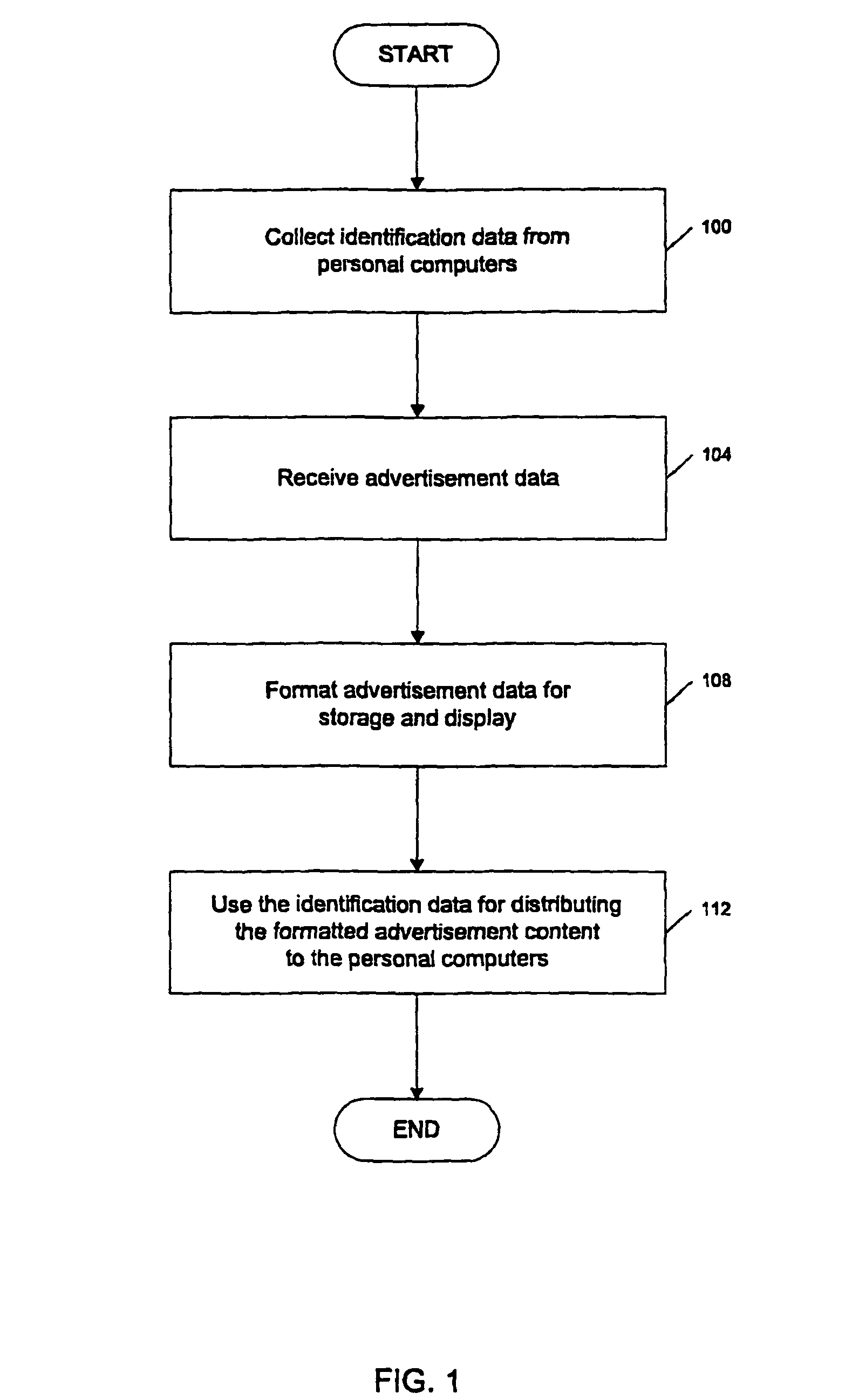
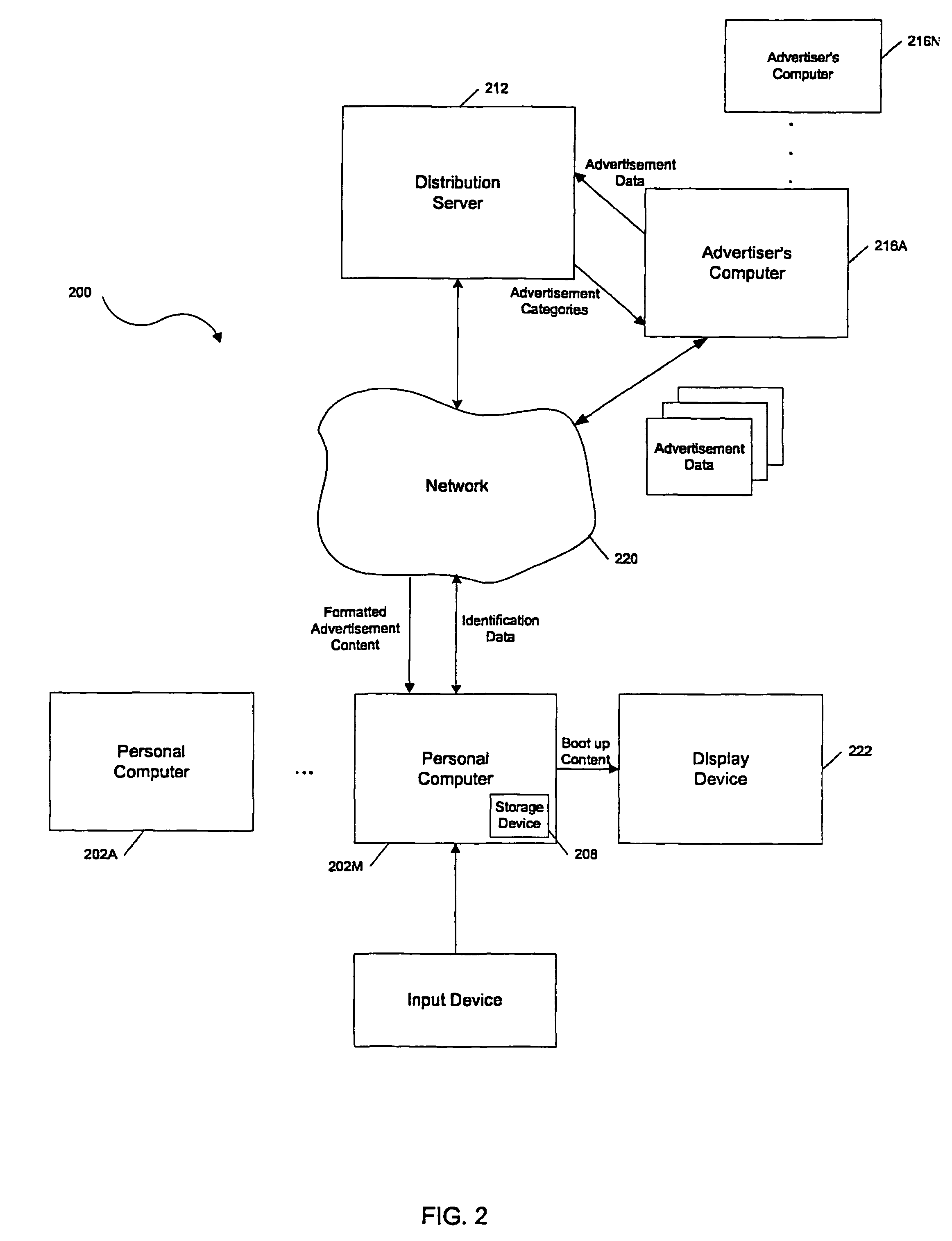
System and method of receiving advertisement content from advertisers and distributing the advertising content to a network of personal computers
A method of distributing advertisement content. One embodiment of the invention comprises a distribution server that is connected to a network of personal computers via a network. The distribution server receives advertising data from advertisers and formats the advertisement data for storage and display on the personal computers during or before bootloading a user selected application environment. Upon the occurrence of one or more events, the distribution server distributes the advertisement data to the network of personal computers. The personal computers receive the distributed advertisement content and store the advertisement data on a storage device. Upon the bootloading of the user selected application environment, the advertising data is displayed to the user.
Owner:WESTERN DIGITAL TECH INC
Software component execution management using context objects for tracking externally-defined intrinsic properties of executing software components within an execution environment
InactiveUS7076784B1Insufficient flexibilityData processing applicationsSpecific program execution arrangementsManagement objectApplication software
A run-time executive of an object management system for managing execution of software components in an object execution environment uses a component context object to store intrinsic context properties related to an associated component. The run-time executive maintains an implicit association of the component context object with the application component. For example, the context properties can include a client id, an activity id, and a transaction reference. The component context object also provides an interface accessible to the associated component, with member functions for use in transaction processing, in creating additional other application components inheriting component's context properties, and in access control based on abstract user classes (roles).
Owner:MICROSOFT TECH LICENSING LLC
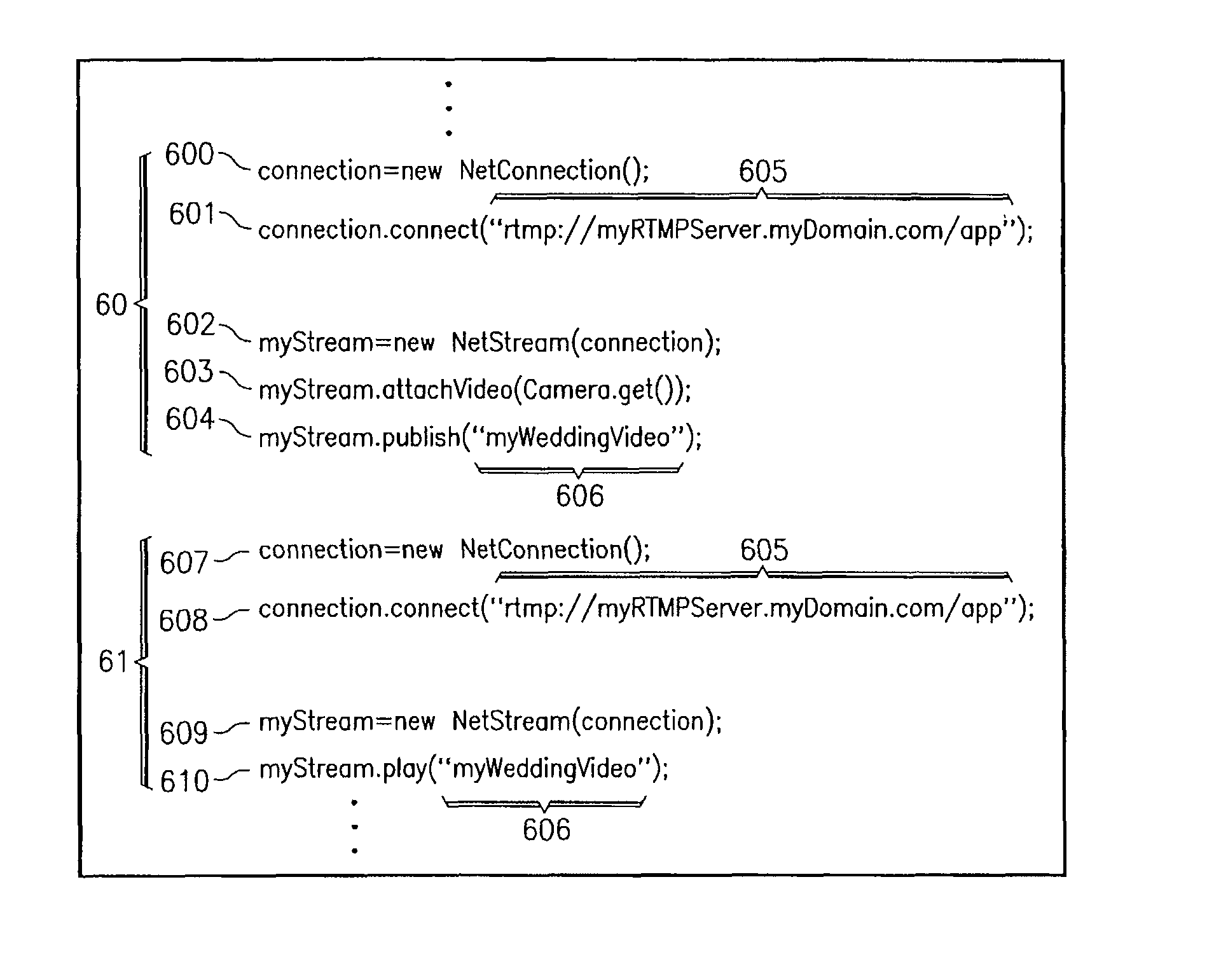
Client controllable server-side playlists
InactiveUS8150918B1Multiple digital computer combinationsTransmissionData streamApplication software
Owner:ADOBE SYST INC
Systems and methods for integration of an application runtime environment into a user computing environment
ActiveUS20110314389A1Simplify the development processFacilitates taskMultiple digital computer combinationsProgram controlOperational systemApplication software
Systems and methods for creating application runtime environments or application environments that can be downloaded and integrated into the computing environment of a computing device are disclosed. One embodiment of the invention includes a computing device on which an operating system is installed that creates a computing environment, an Application Platform application, where the Application Platform application is at least partially natively implemented and creates an application runtime environment when executed by the computing device, and a cross-platform application, where the cross-platform application is configured to be executed within the application runtime environment and is not natively executable by the computing device. In addition, the Application Platform application is configured to integrate the cross-platform application into the computing environment of the computing device by providing at least one launch point for the cross-platform application within the computing environment.
Owner:SWEETLABS
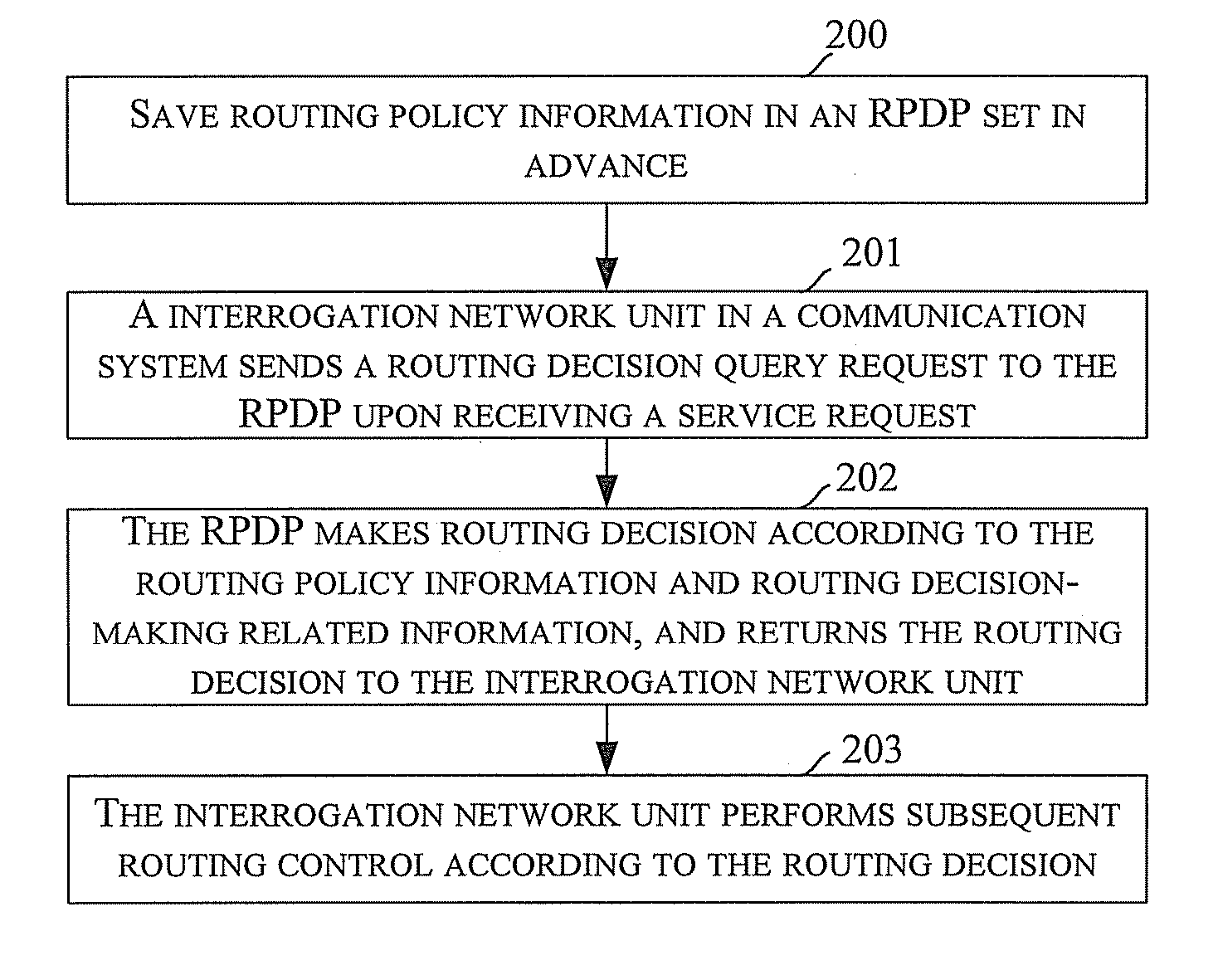
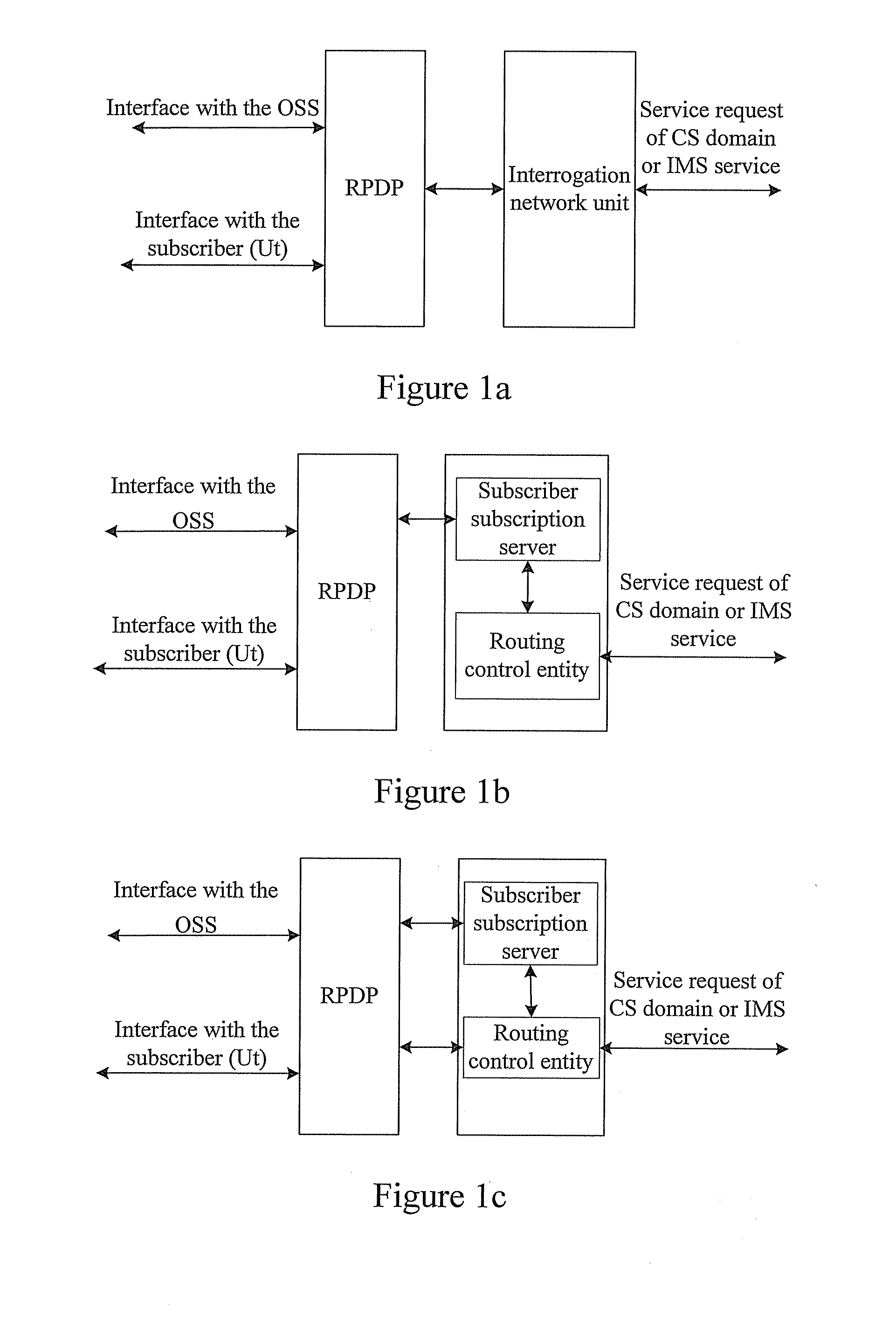
Method and system for routing control
InactiveUS20080039104A1Routing decisionImprove user experienceWireless network protocolsRadio/inductive link selection arrangementsRouting decisionPolicy decision
Embodiments of the present invention disclose a method for routing control applied to a communication system including a CS domain and an IMS and in which a Routing Policy Decision-making Point (RPDP) is set; and the method includes: initiating a routing query to the RPDP by an interrogation network unit in the communication system upon receiving a service request; making a routing decision by the RPDP according to routing decision-making related information and the routing policy information, returning the routing decision to the interrogation networking unit by the RPDP; and performing subsequent routing control by the interrogation network unit according to the routing decision. Embodiments of the present invention also disclose a system for routing control. In accordance with the embodiments of the present invention, across-domain routing control is thus realized in different network application environments according to different demands.
Owner:HUAWEI TECH CO LTD
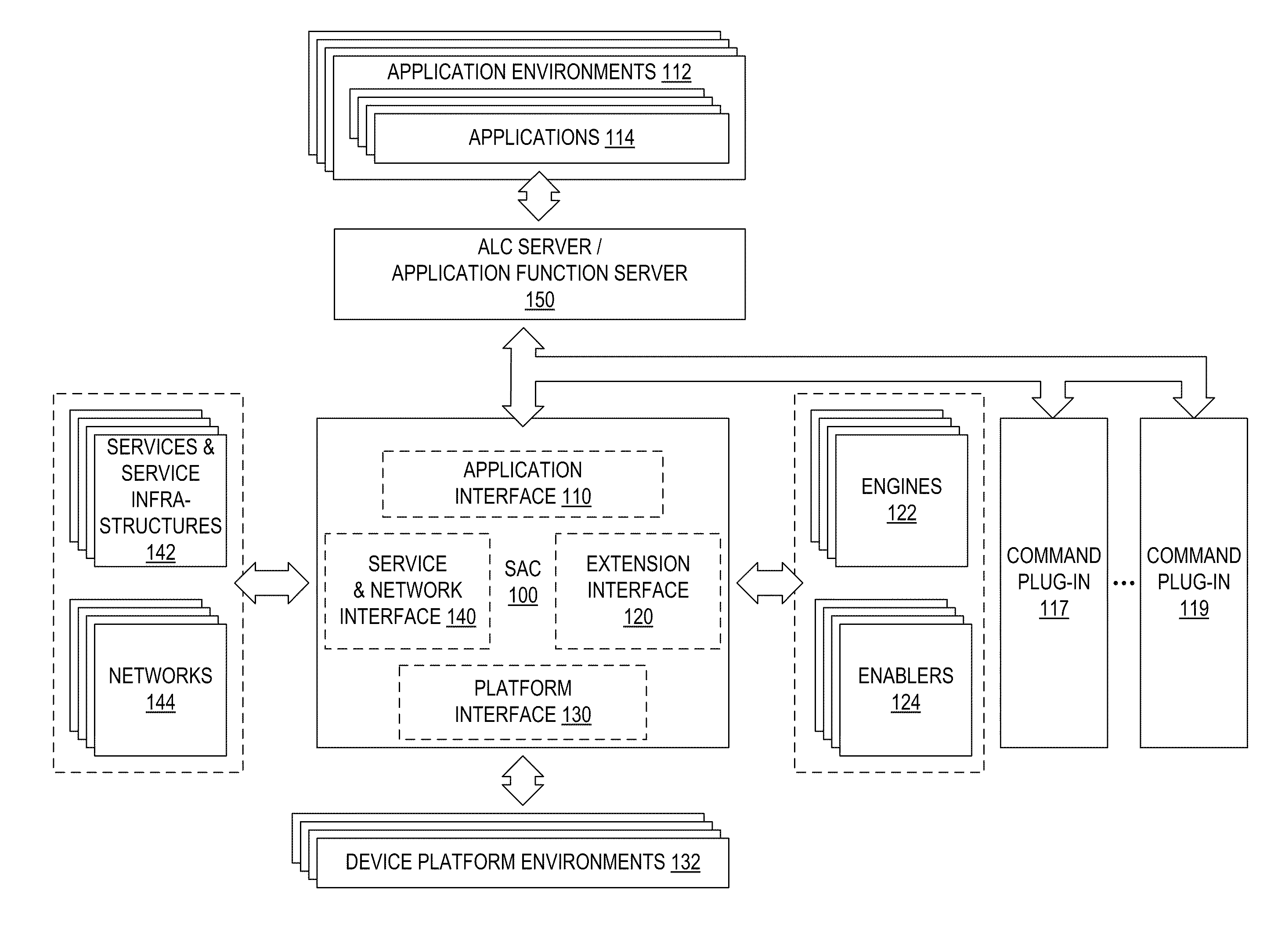
System, method and apparatus for providing functions to applications on a digital electronic device
InactiveUS20100257539A1Enabling and simplifying application developmentShorten development timeService provisioningInterprogram communicationDiscrete functionsApplication software
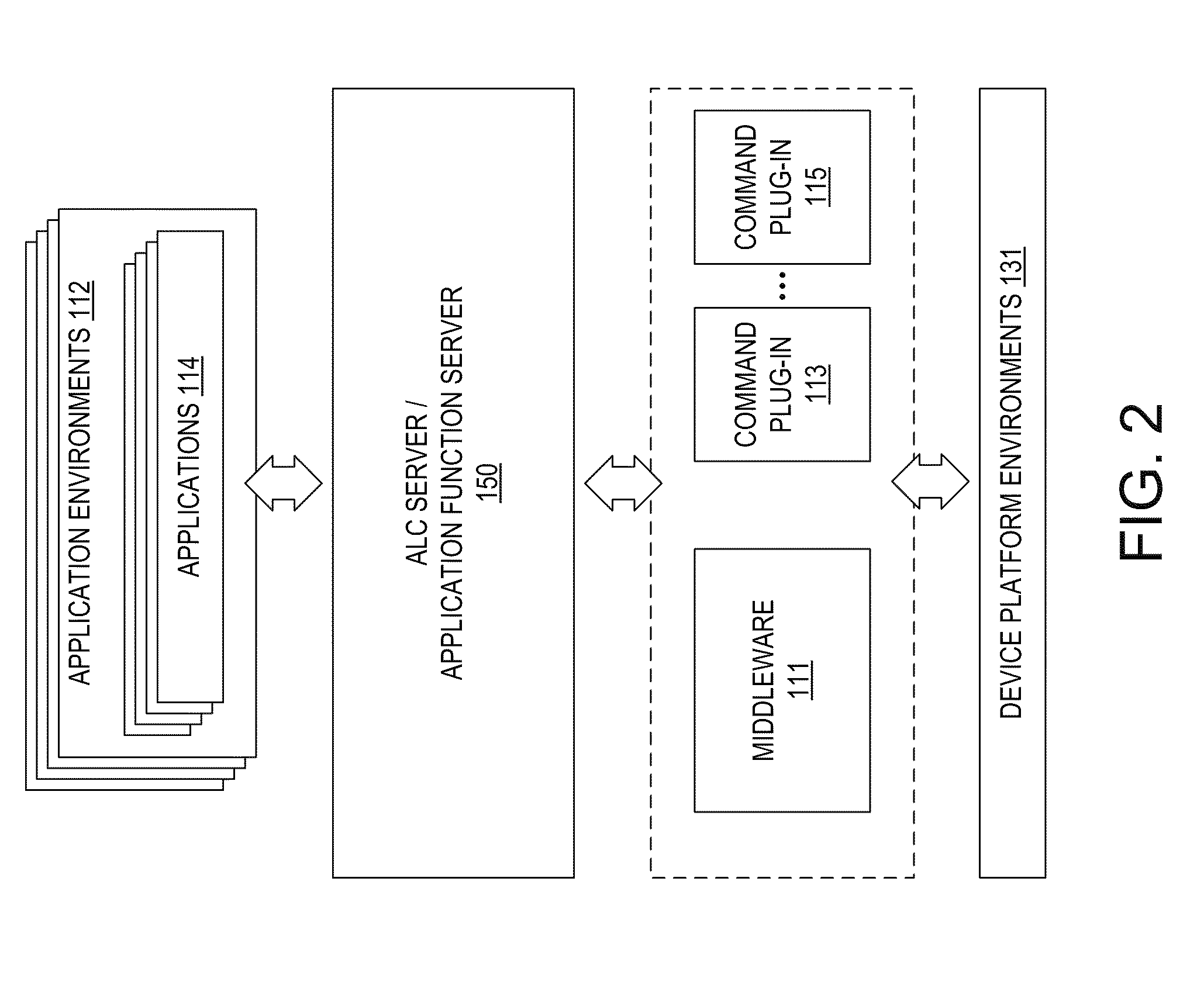
To greatly simplify the developer's task, an application function server or application logic controller (“ALC”) server runs on a digital electronic device with a common set of tools and methods to deliver high-value capabilities to applications developed in different application languages and running in various different application environments. The applications and the application function server have a local client-server relationship. The functions themselves are provided by various plug-ins. The interface of a plug-in illustratively is a discrete set of functions, common to the command plug-ins. The ALC Server accepts simplified commands directly from the applications, applies the appropriate policy, and interacts with the plug-ins to perform the requested functions on behalf of the applications. The result is that applications can use various capabilities without dealing with the complex methods, standards, and system interoperability required to make the technologies work, and technology additions and upgrades can be performed independently from the applications that use them.
Owner:ECRIO
Systems and methods for home automation scene control
ActiveUS20150082225A1Simplify creationRobust and flexibleAlarmsHome automation networksGraphicsGraphical user interface
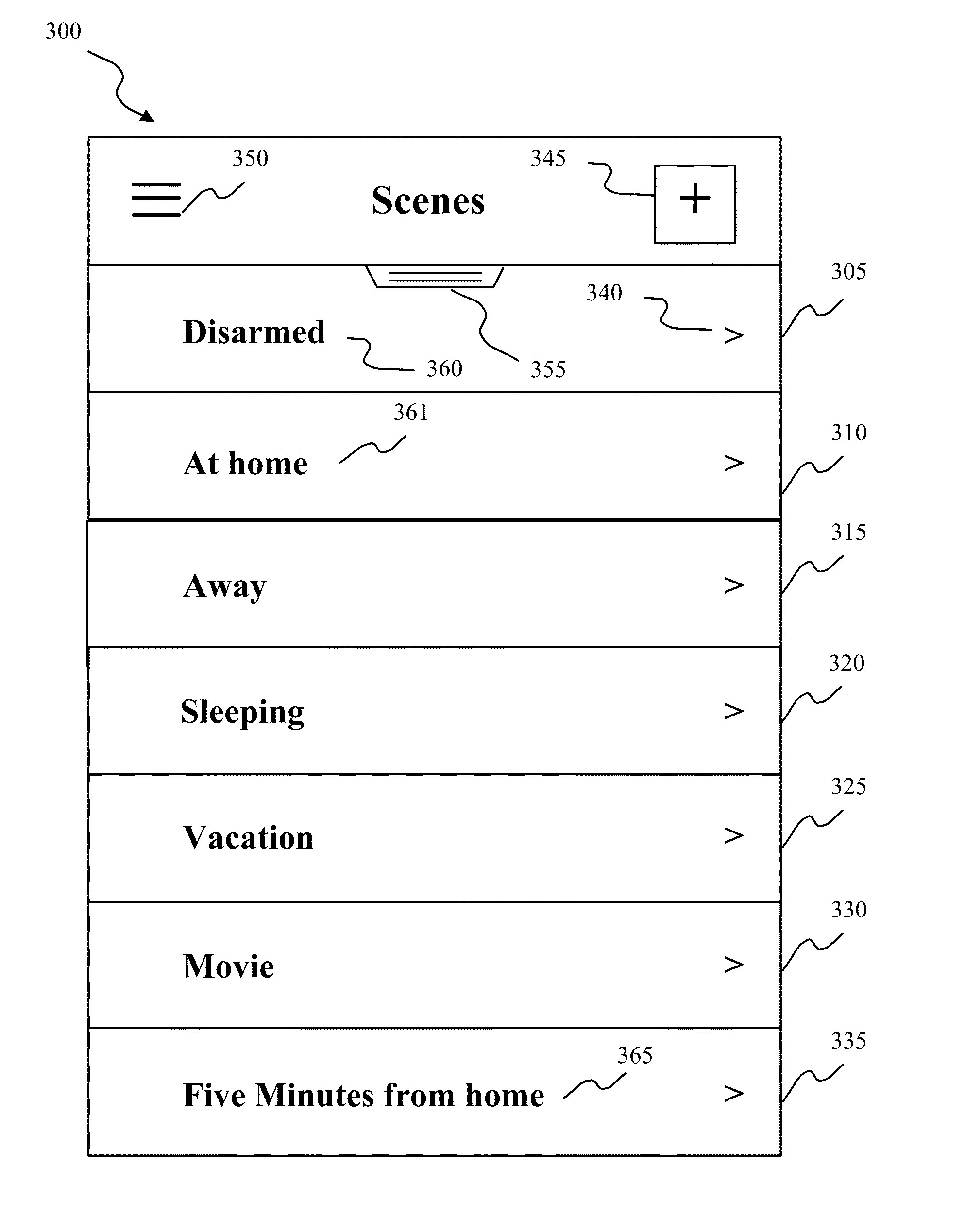
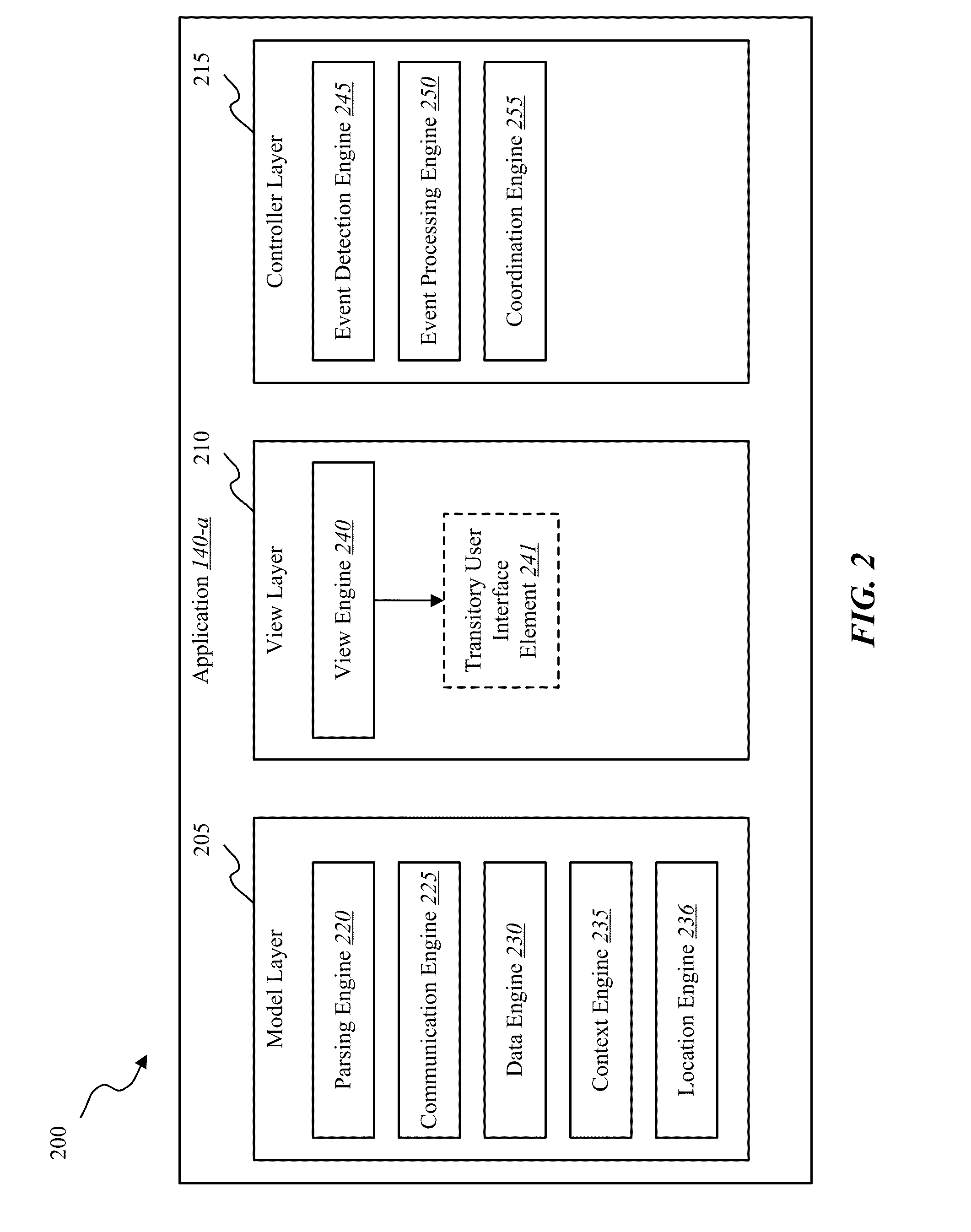
Methods and systems are described for providing a graphical user interface suitable for viewing and modifying home automation, home security, and / or energy management devices. In some embodiments, the graphical user interface may include a scene selection list displaying multiple selectable items representing various scenes. In certain instances, control and monitoring of one or more devices may at least be accessed through a transitory user interface element such as, for example, a drawer control, a pullable view, or the like. Multiple device states may be set in accordance with a scene definition associated with a selectable list item in a scene selection list displayed in the transitory user interface element. The contents of the scene selection, in certain embodiments, may be determined in part based on a detected application context, user context, or both.
Owner:VIVINT INC
Integrating traffic monitoring data and application runtime data
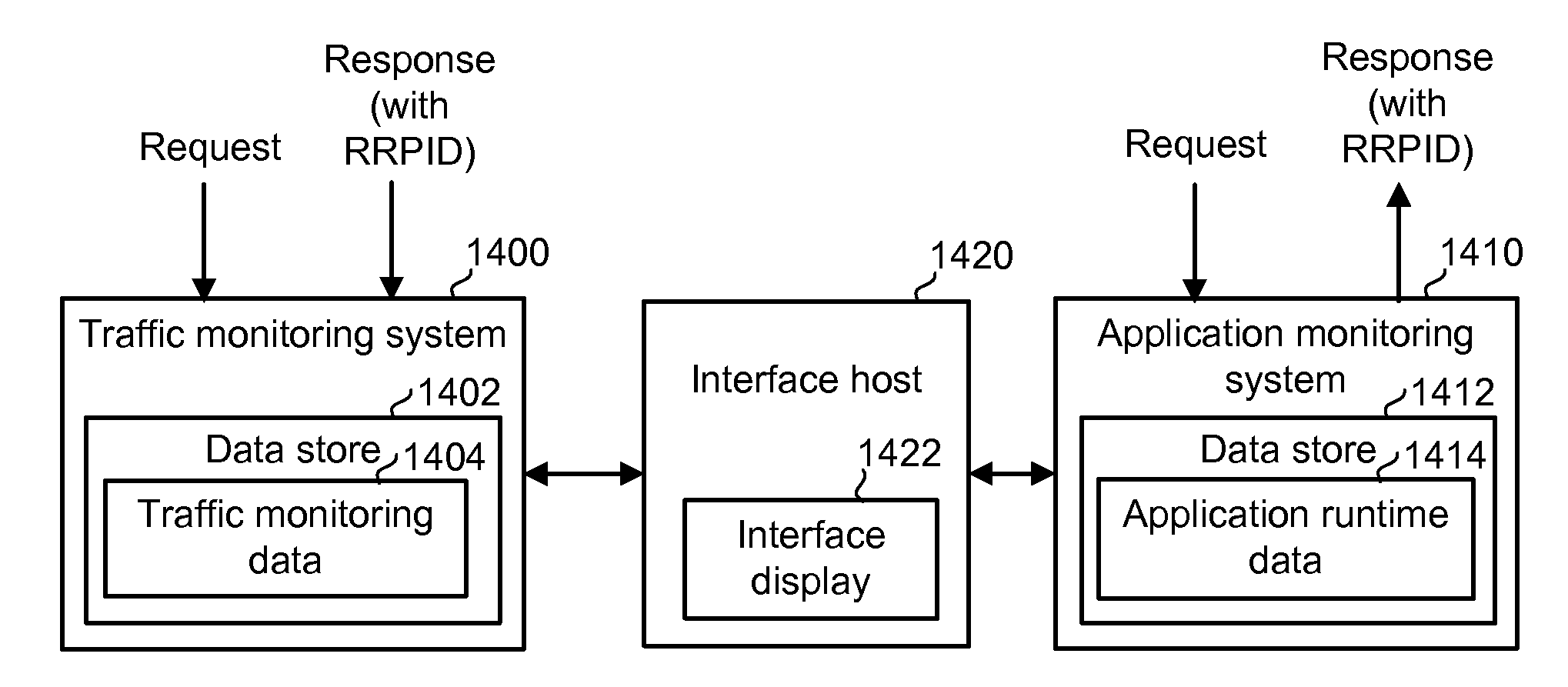
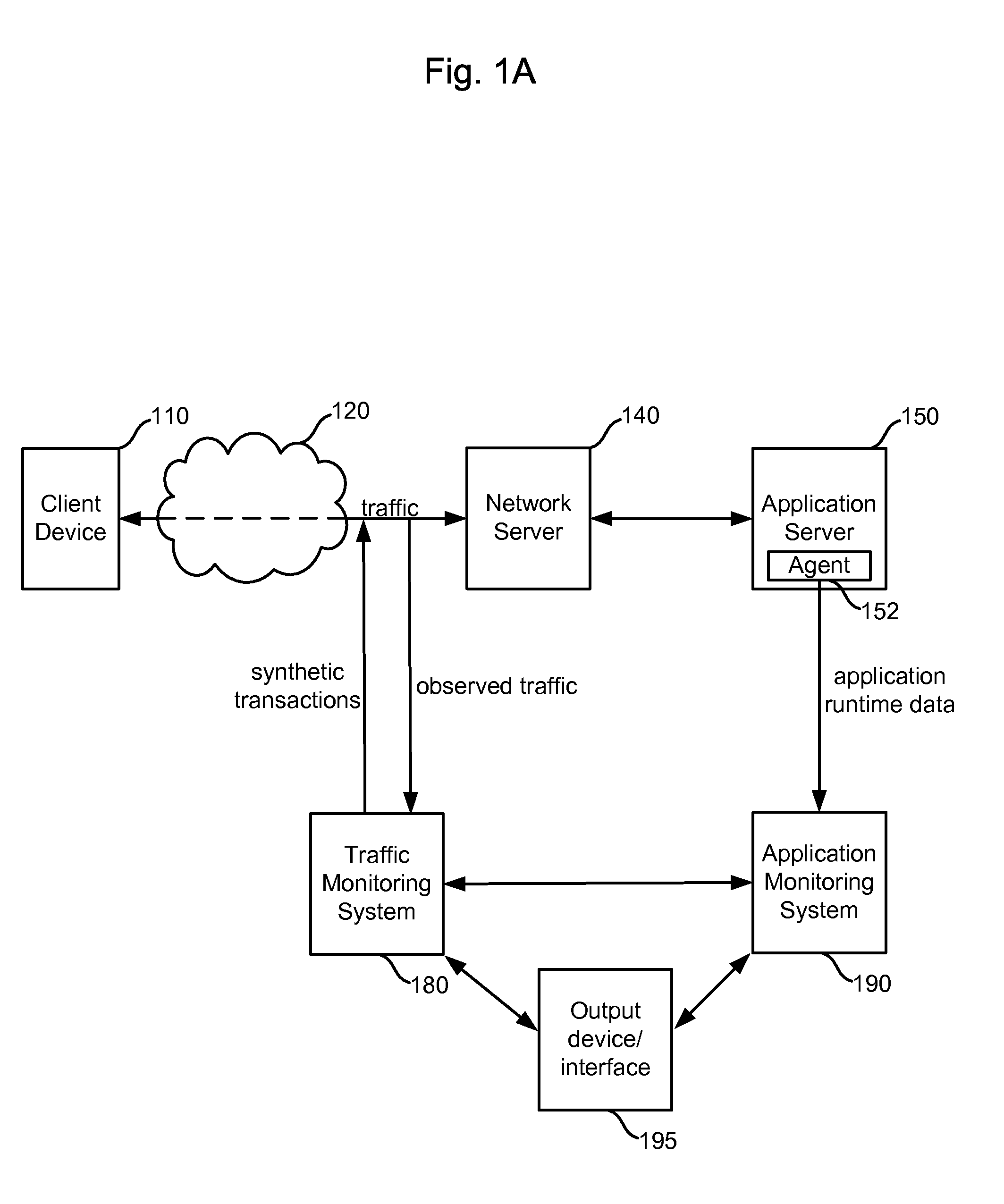
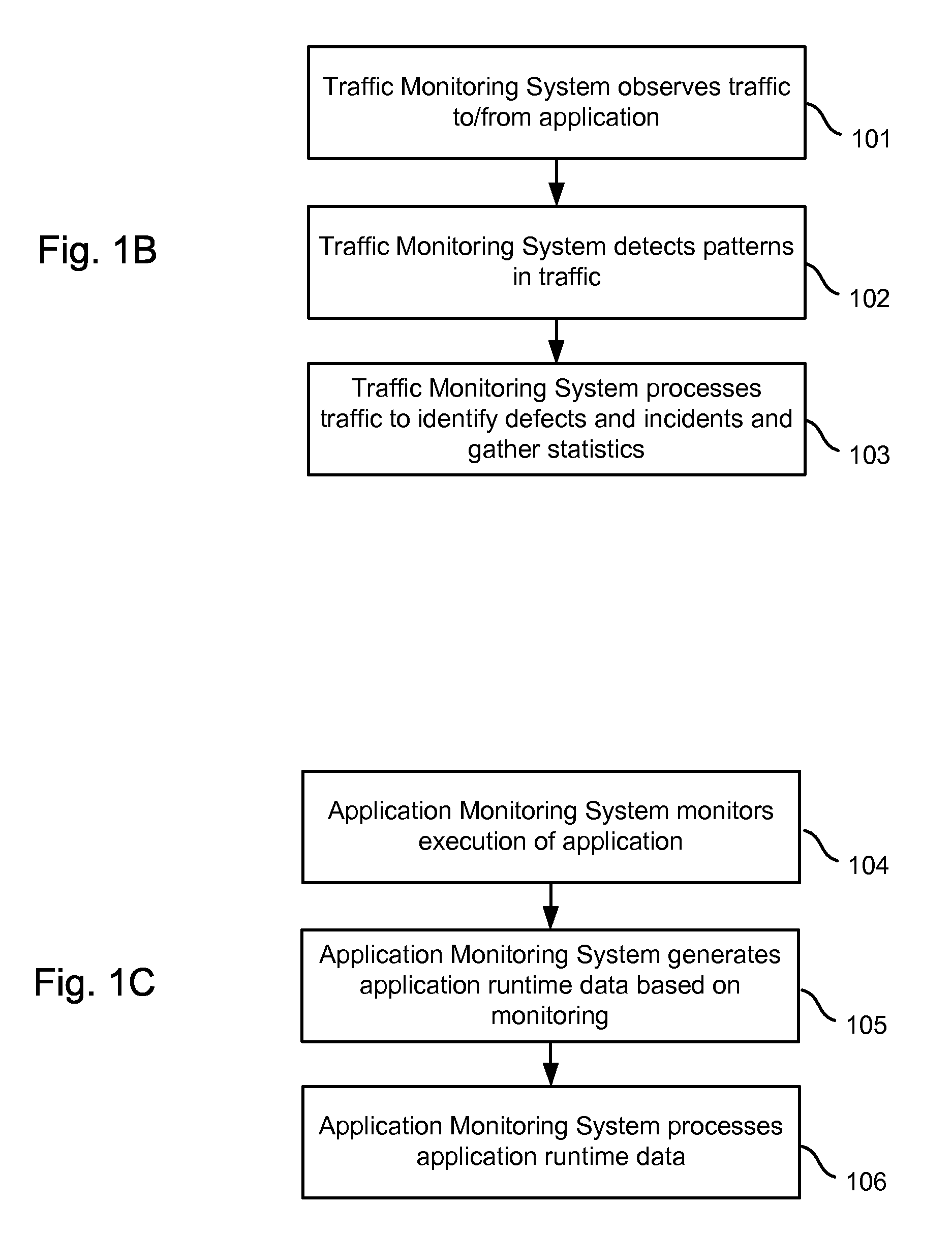
ActiveUS20070266149A1Enhance capacity planningImprove rendering capabilitiesDigital computer detailsTransmissionTraffic capacityData information
Information is obtained from an application monitoring system which monitors the execution of an application and a traffic monitoring system which monitors traffic between clients and the application. The clients interact with the application to perform transactions or other tasks. Traffic monitoring data, such as information regarding defects and incidents, and application runtime data, such as traces of invoked application components, can be integrated in an output such as an interface to provide an enhanced understanding of system performance. Related traffic monitoring data and application runtime data can be linked by a request-response pair identifier associated with a request provided to the application and a response provided by the application.
Owner:CA TECH INC
Exchanging Application Metadata for Application Context Aware Service Insertion in Service Function Chain
A method implemented by a network element (NE), comprising receiving a classification message comprising a classification rule for identifying a service function chain (SFC) in a network, wherein the SFC comprises an ordered set of service functions (SFs) that provides services to an application, and a dynamic application-specific contextual data associated with an operation of the application, receiving a first of a plurality of application data packets, determining that the first of the application data packets matches the classification rule, generating a first SFC packet by adding the dynamic application-specific contextual data to the first of the application data packets according to the classification rule to enable communication of the dynamic application-specific contextual data to at least one of the SFs in the SFC, and sending the first SFC packet towards a next NE according to an SF path in the network associated with the SFC.
Owner:FUTUREWEI TECH INC
Systems and methods for analyzing changes in application code from a previous instance of the application code
ActiveUS20110283270A1Version controlSpecific program execution arrangementsProgramming languageEnterprise resource planning
The present application is directed towards systems and methods for analyzing and transforming changes in customized code of an enterprise resource planning (ERP) application from a previous instance of transformation of the customized code of the ERP application. Customized functions, objects, databases, and code of the application may be analyzed to identify changes in application code from a previous instance of the application code. Changed code may be further analyzed to determine which portions violate a predetermined set of coding rules of the application. Portions that violate the predetermined set of coding rules may be enumerated by one of developer, time, or type of object. Transformation rules may be applied to the code that violates the predetermined coding rules to generate a transformed instance of the application that is in conformance with the coding rules.
Owner:SMARTSHIFT
Offload processing for secure data transfer
InactiveUS20030105977A1Safe handlingMultiple digital computer combinationsProgram controlPlaintextSafe handling
Improvements in security processing are disclosed which enable security processing to be transparent to the application. Security processing (such as Secure Sockets Layer, or "SSL", or Transport Layer Security, or "TLS") is performed in (or controlled by) the stack. A decision to enable security processing on a connection can be based on configuration data or security policy, and can also be controlled using explicit enablement directives. Directives may also be provided for allowing applications to communicate with the security processing in the stack for other purposes. Functions within the protocol stack that need access to clear text can now be supported without loss of security processing capability. No modifications to application code, or in some cases only minor modifications (such as inclusion of code to invoke directives), are required to provide this security processing. Improved offloading of security processing is also disclosed, which provides processing efficiencies over prior art offloading techniques.
Owner:IBM CORP
Wavefront sensing system employing active updating of reference positions and subaperture locations on wavefront sensor
ActiveUS20060024061A1Improve the situationSmall sizePhotometry using reference valueMaterial analysis by optical meansWavefront sensorCommunications system
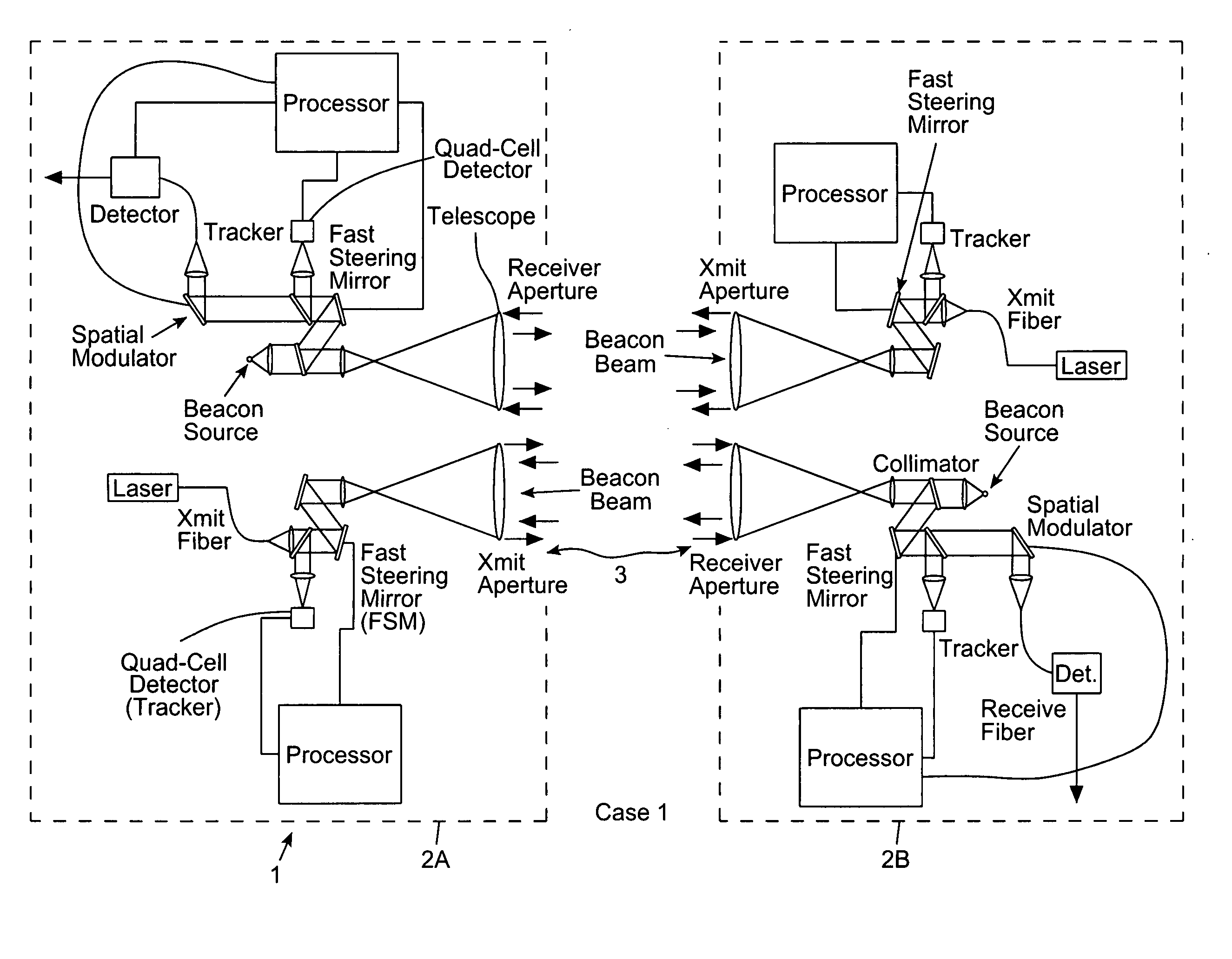
A free-space adaptive optical laser communication system having signal transmission and reception channels at all terminals in the communication system, wherein wavefront sensing (WFS) and wavefront correction mechanisms are employed along signal transmission and reception channels of all terminals in the communication system (i.e. adaptive optics) to improve the condition of the laser beam at the receiver (i.e. reduce the size of the spot a the detector plane). in the illustrative embodiment, the WFS mechanisms employ a novel WFS control process, in which active updating of reference positions and subaperture locations on the wavefront sensor. These WFS mechanism can be used in diverse application environments, including but not limited to FSO laser communication systems.
Owner:NORTHROP GRUMAN CORP
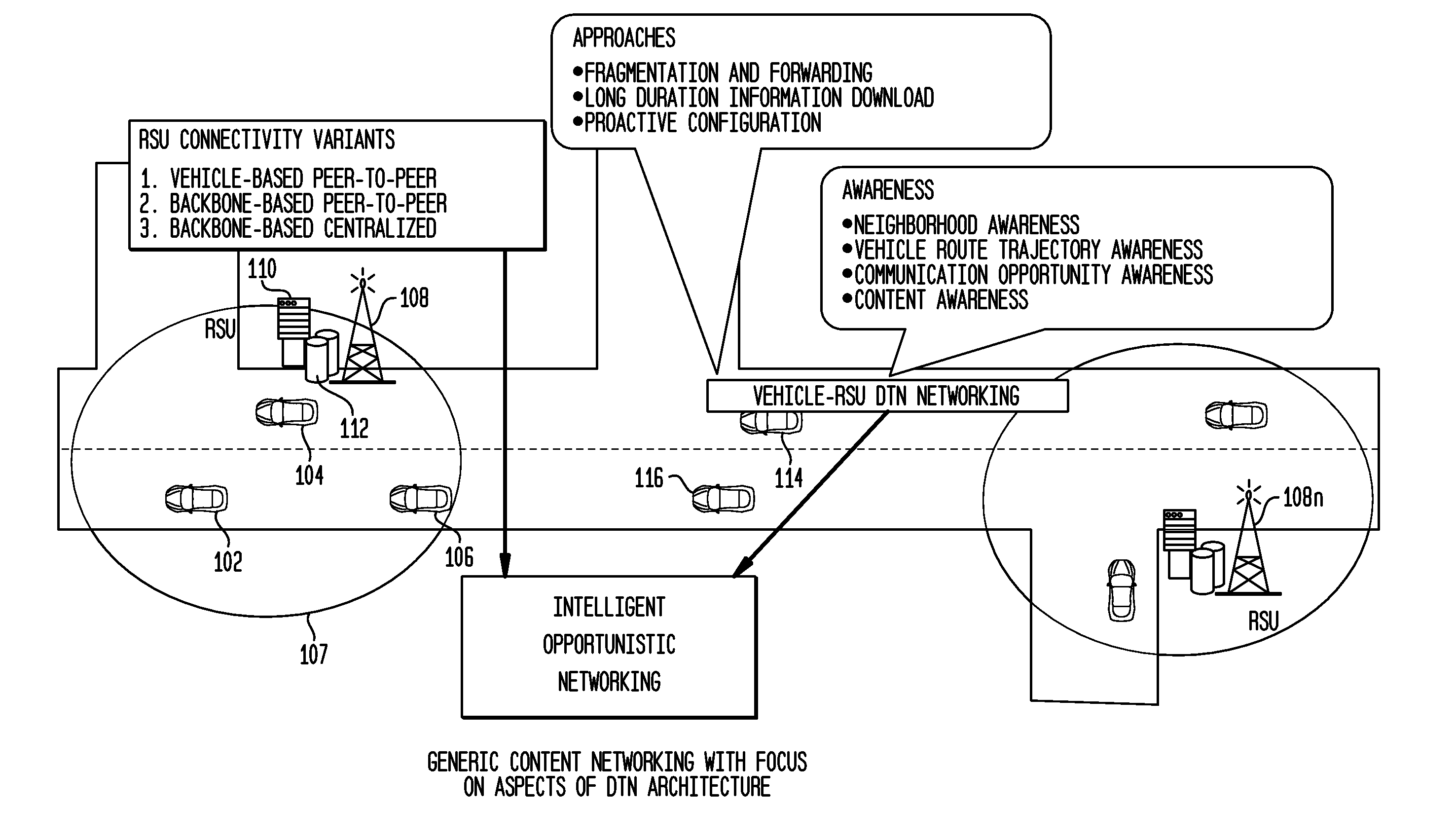
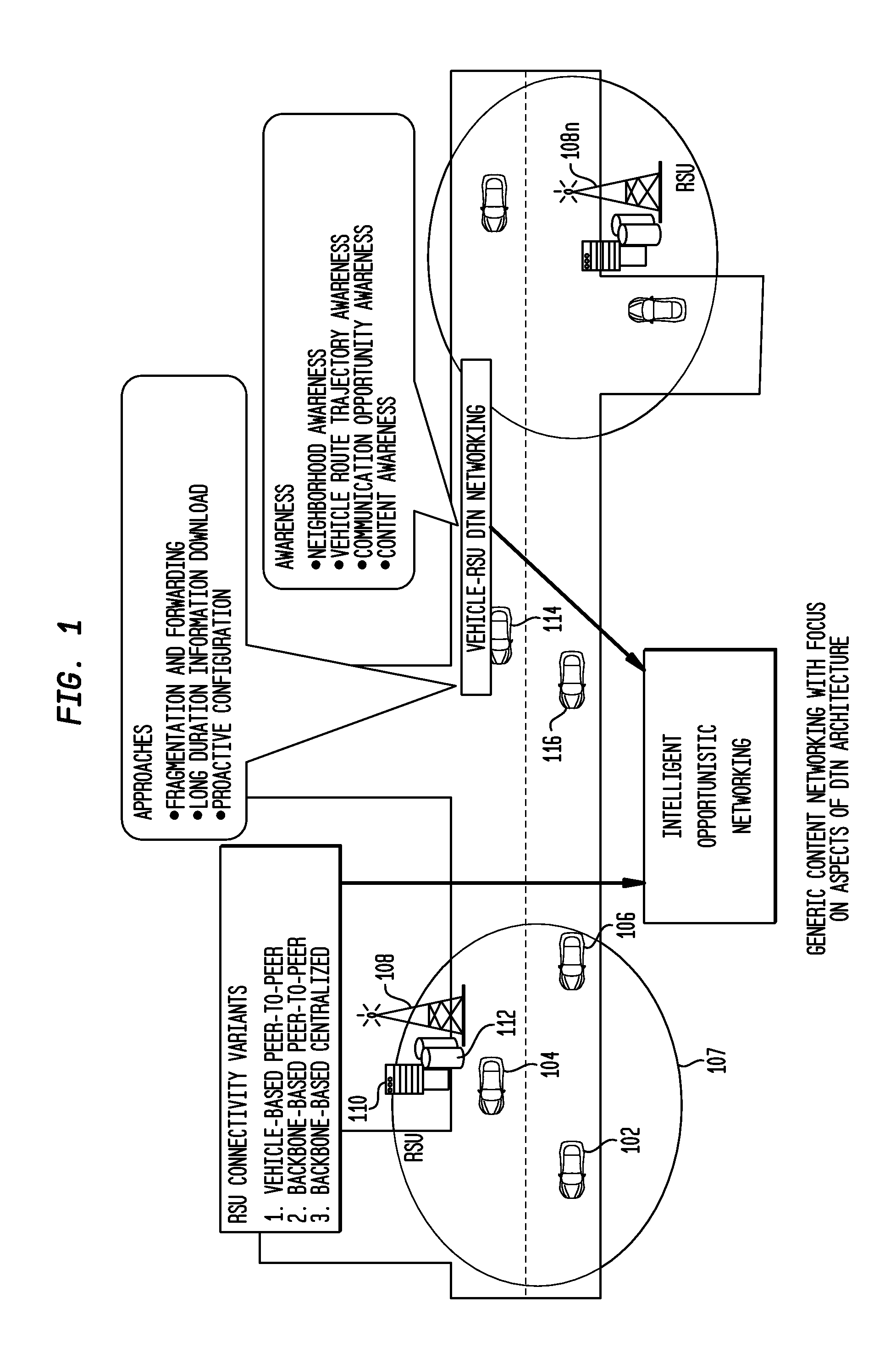
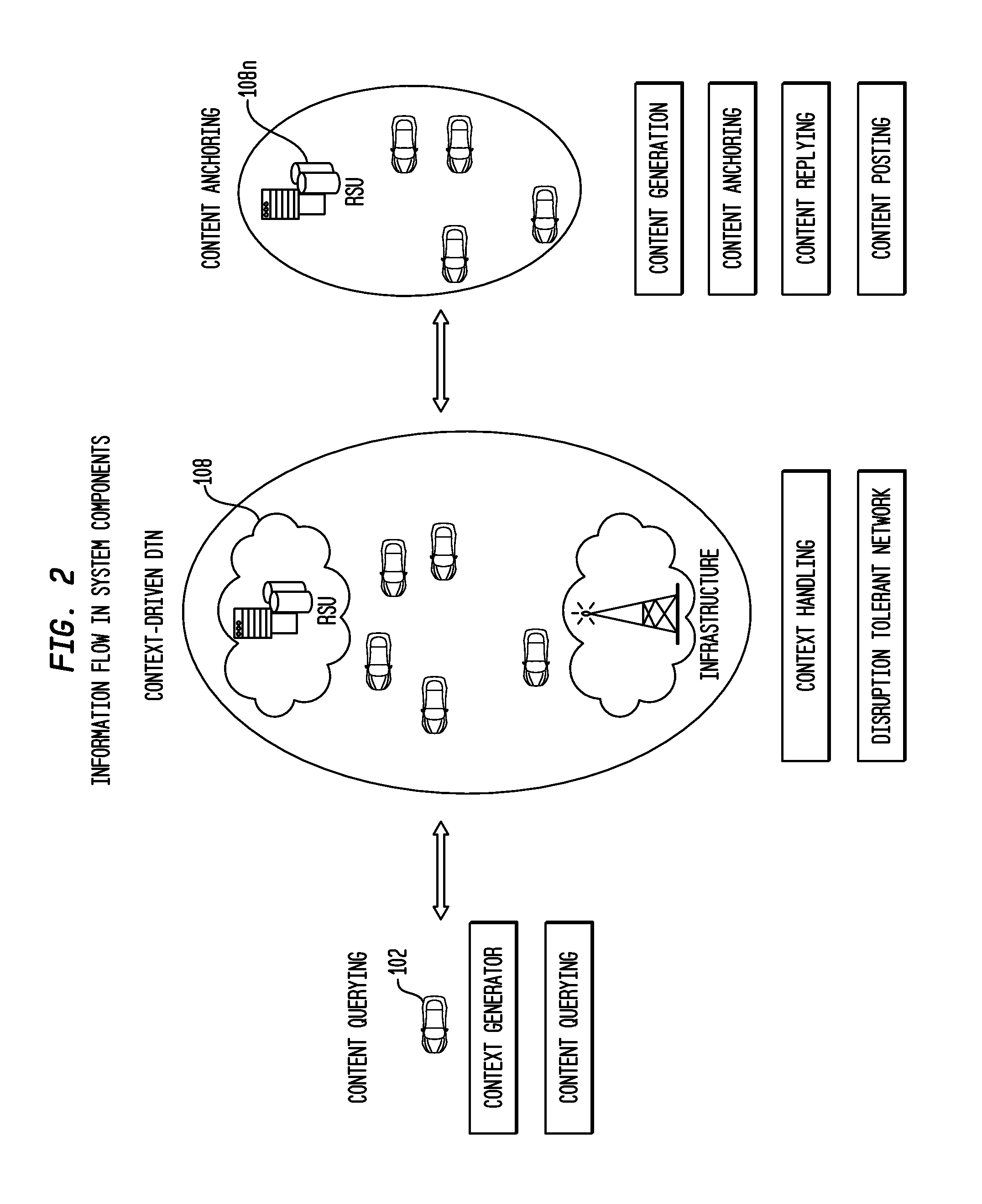
Methods for context driven disruption tolerant vehicular networking in dynamic roadway environments
A method and apparatus for optimizing communication of data within a disruption tolerant network. The method comprises of receiving a data packet, said data packet including a context and a state related to said context, storing the data packet to a buffer and disseminating the data packet to neighboring vehicles and RSU, and passing said state to an application, said application associated with said application context. In one embodiment, the method functions as a software protocol within a dashboard computer. The apparatus comprises a processor and a memory operable to receive a data packet, said data packet including a context and a state related to said context, store the data packet to a buffer when the context matches an application context, disseminating the data packet to neighboring vehicles and RSU, and pass said state to an application when the context matches an application context, said application associated with said application context. In one embodiment, the apparatus is presented as a dashboard computer within a vehicle.
Owner:TELCORDIA TECHNOLOGIES INC +1
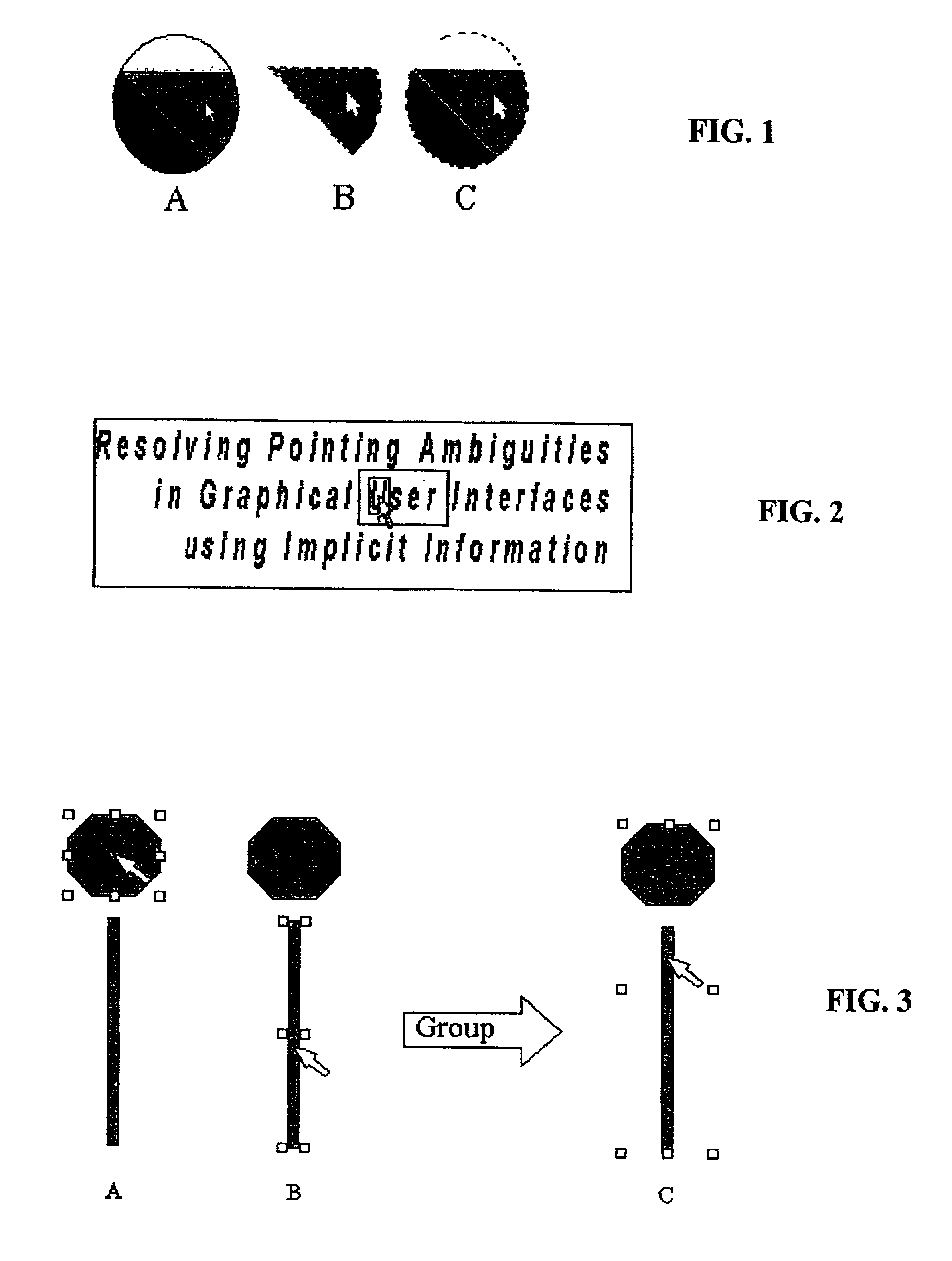
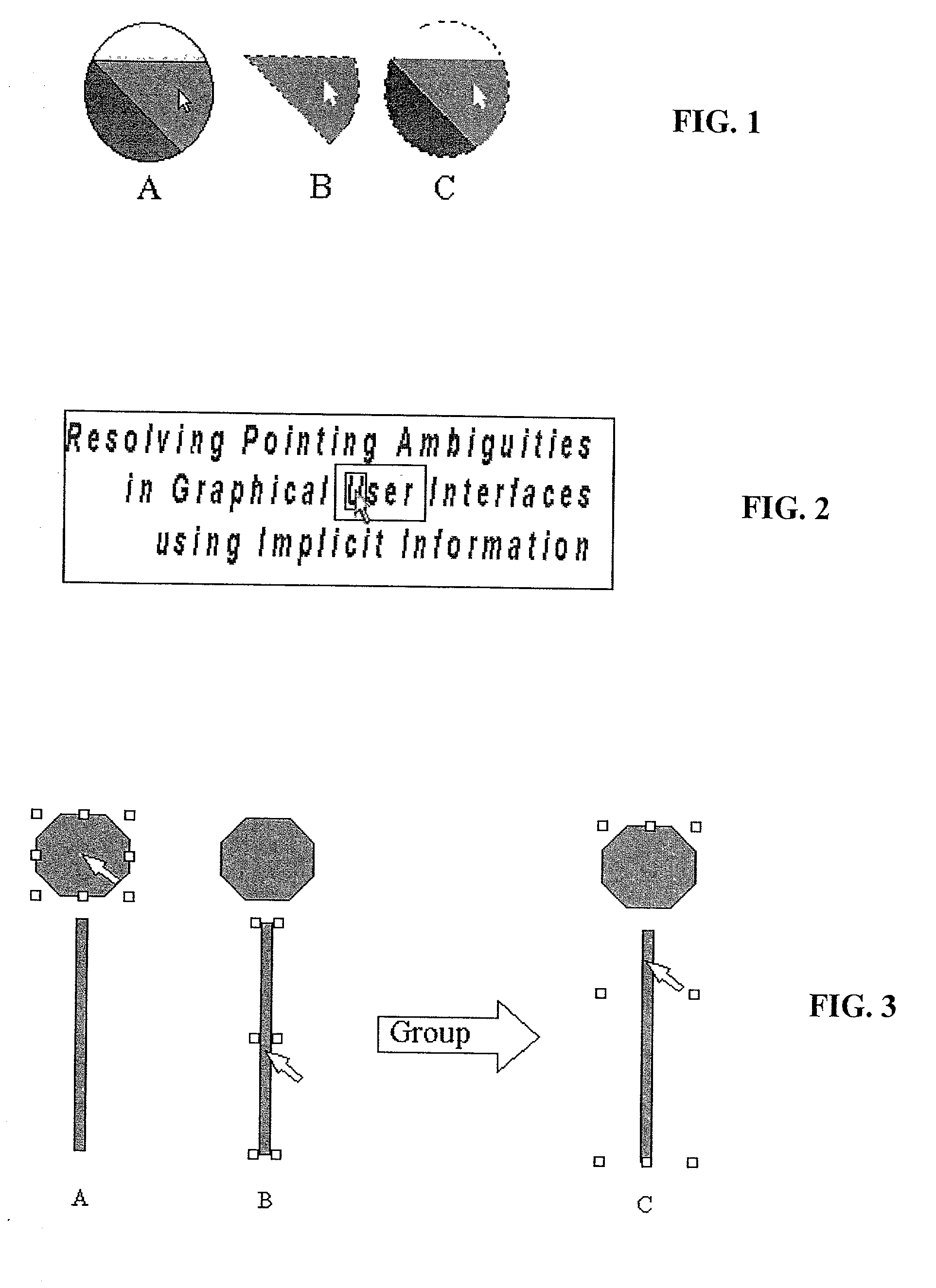
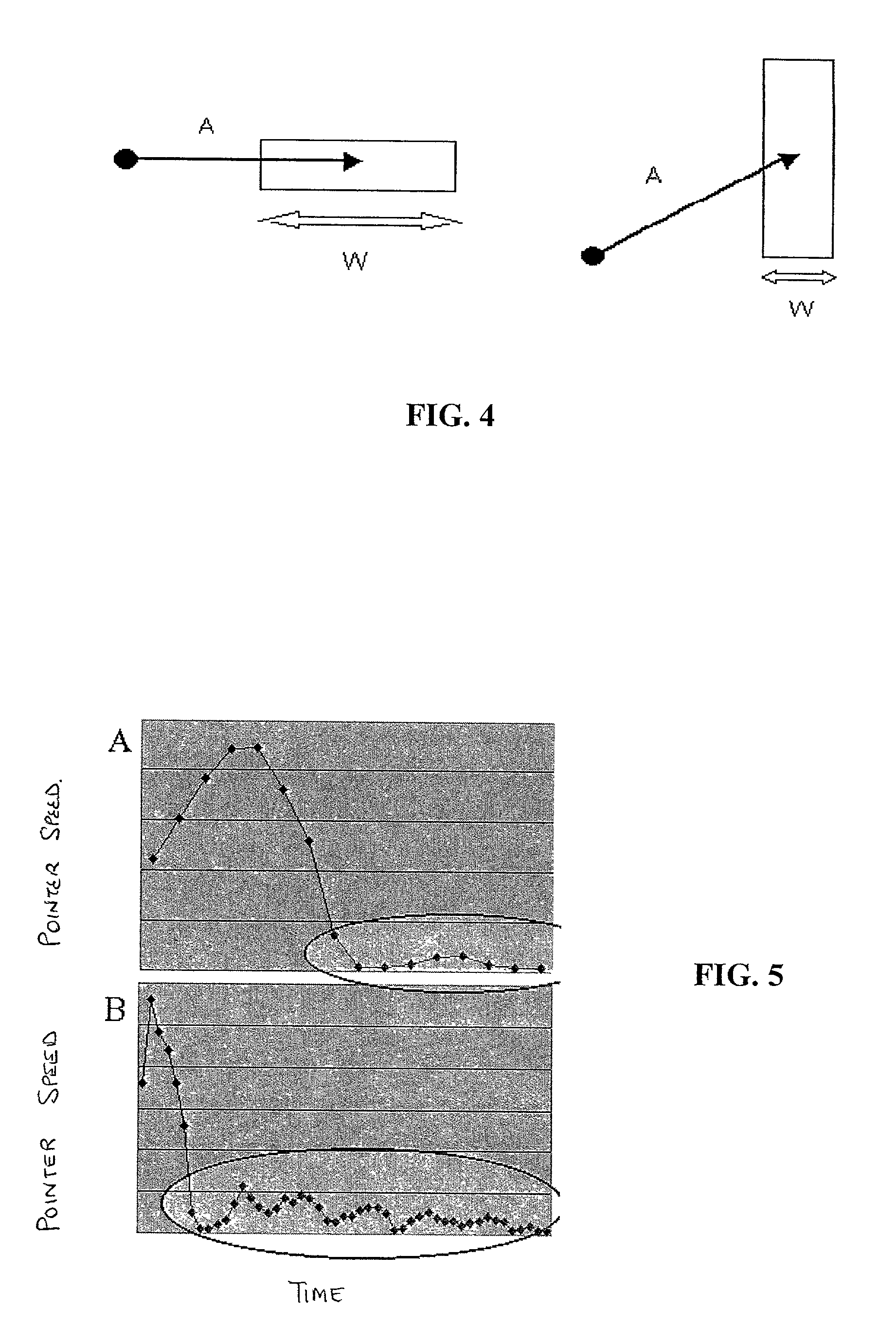
Method and system for implicitly resolving pointing ambiguities in human-computer interaction (HCI)
InactiveUS6907581B2Simple design and implementationEasy accessInput/output processes for data processingObject basedAmbiguity
Owner:RAMOT AT TEL AVIV UNIV LTD
Graphical user interface for large-scale, multi-user, multi-touch systems
ActiveUS20090193366A1Readily apparentInput/output for user-computer interactionGraph readingGraphicsOperational system
A method implemented on the graphical user interface device to invoke an independent, user-localized menu in an application environment, by making a predetermined gesture with a pointing device on an arbitrary part of a display screen or surface, especially when applied in a multi-touch, multi-user environment, and in environments where multiple concurrent pointing devices are present. As an example, the user may trace out a closed loop of a specific size that invokes a default system menu at any location on the surface, even when a second user may be operating a different portion of the system elsewhere on the same surface. As an additional aspect of the invention, the method allows the user to smoothly transition between the menu-invocation and menu control.
Owner:MICROSOFT TECH LICENSING LLC
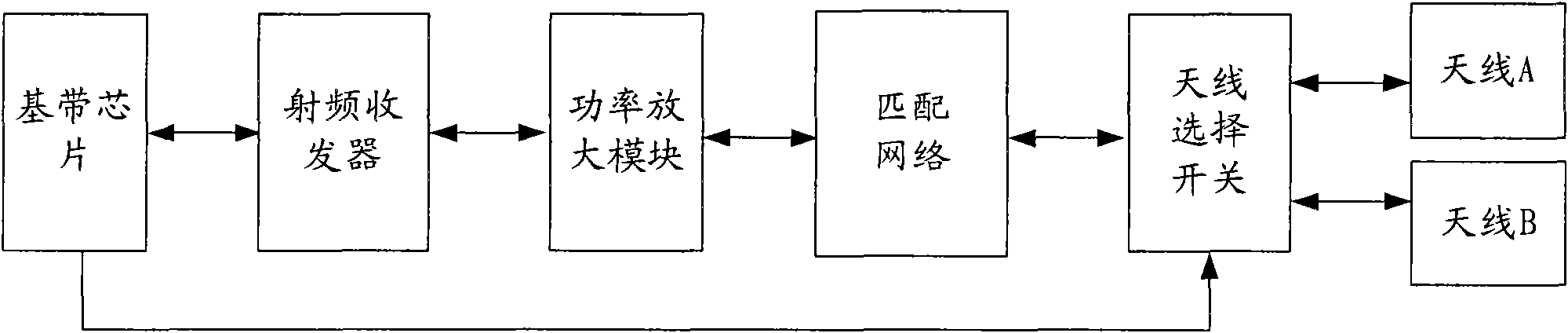
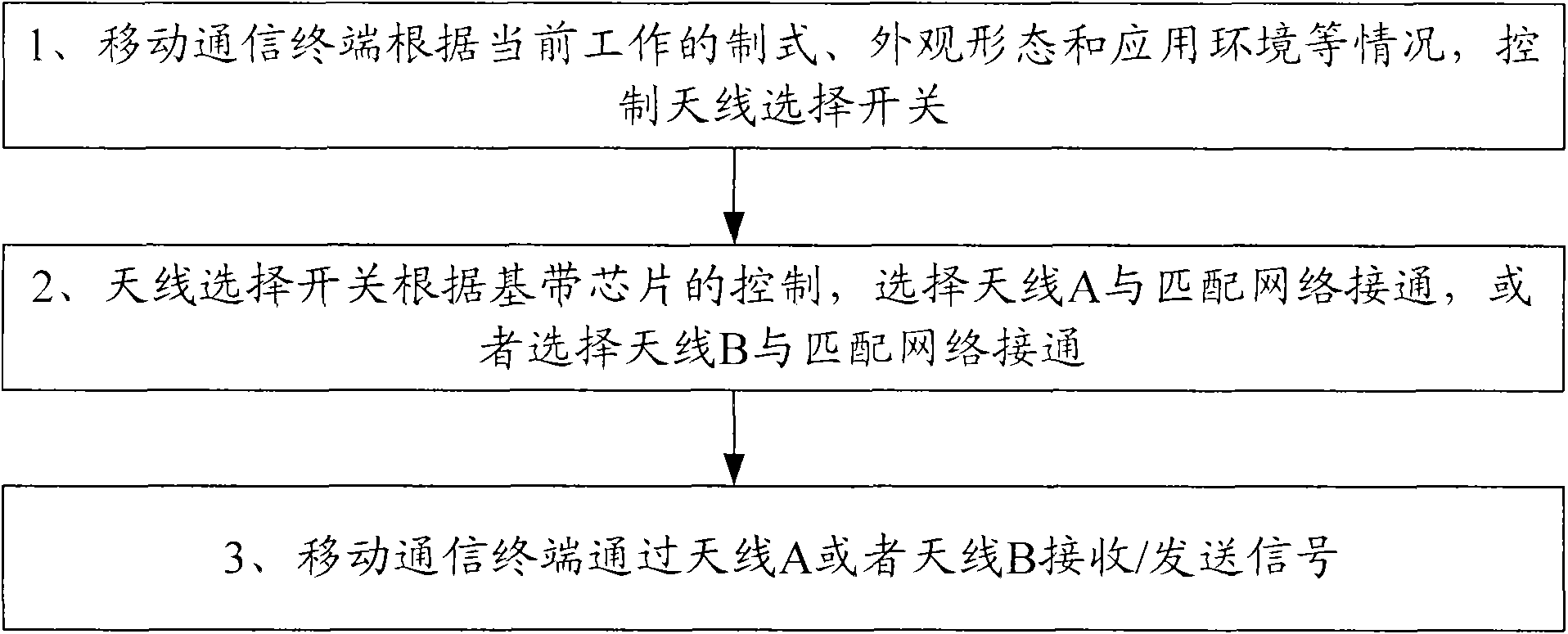
Multi-antenna wireless transceiving device
ActiveCN101640949AWireless Transceiver Performance OptimizationImprove wireless performanceRadio transmissionWireless communicationTransceiverPerformance index
The invention provides a multi-antenna wireless transceiving device which belongs to the technical field of communications and is suitable for a mobile communication terminal. The multi-antenna wireless transceiving device comprises a baseband chip, a radio frequency transceiver, a power amplification module, a matching network, an antenna selection switch and two or more antennae, wherein wireless transceiving performance indexes of the two or more antennae respectively correspond to different application modules of the mobile communication terminal; and the antenna selection switch is used for selecting one antenna from the two or antennae and controlling the selected antenna to be communicated with the matching network. By adopting the technical schemes, the invention enables that wireless performances of the mobile communication terminal are all optimized under various application environments, improves the customer satisfaction degree and is good for optimizing the mobile networkand improving the network capacity.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
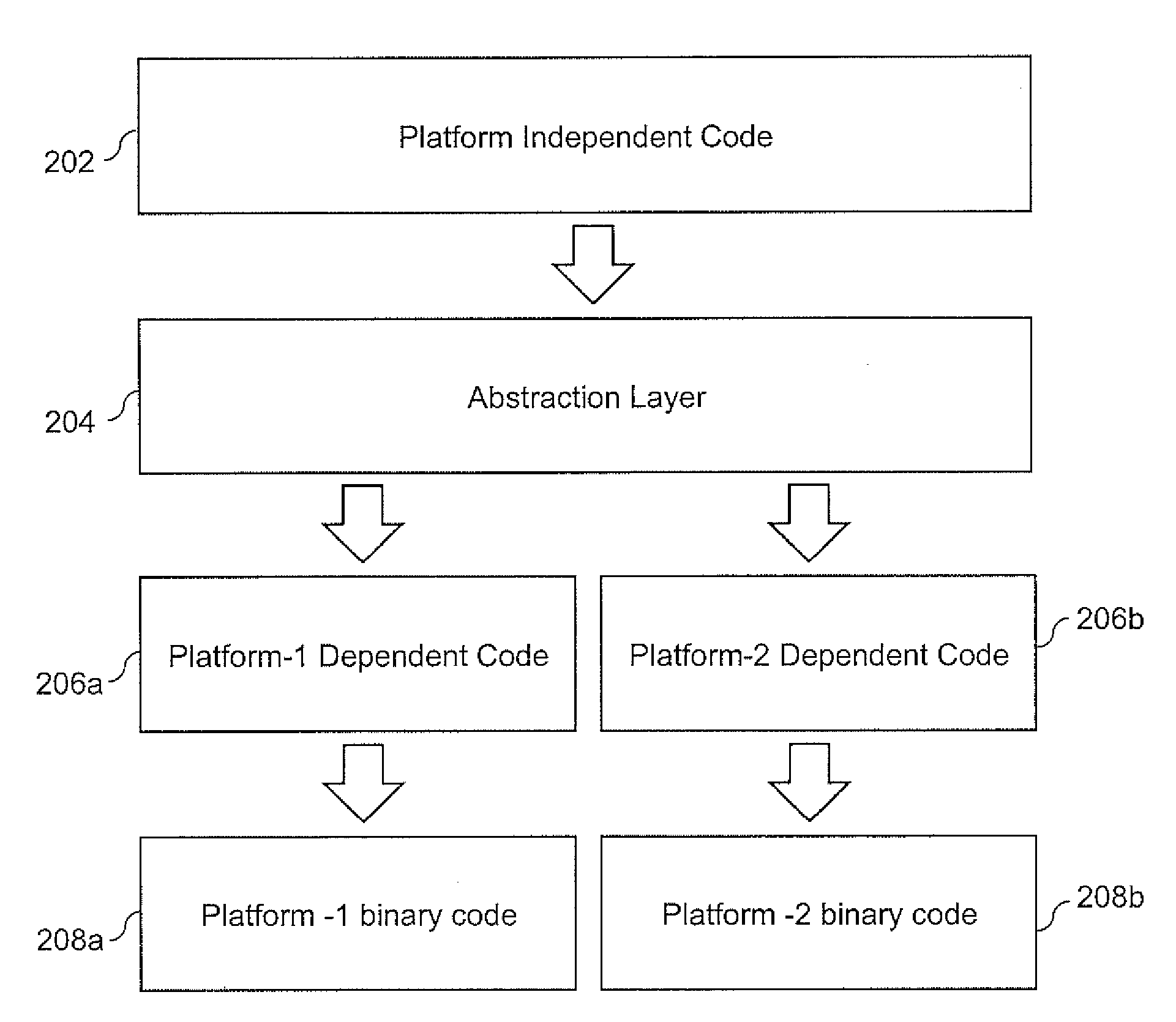
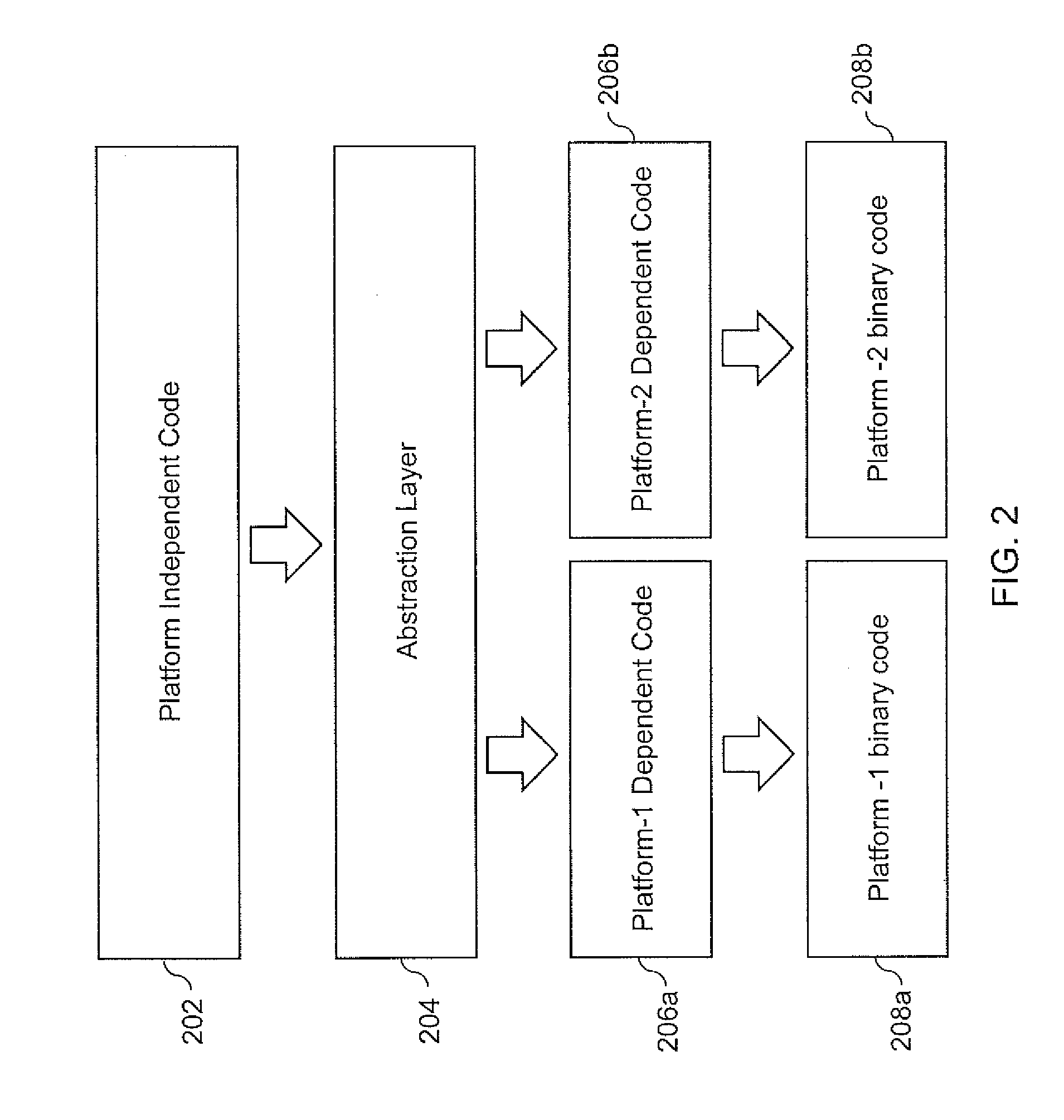
Platform-Independent Application Development Framework
ActiveUS20090313004A1Software reuseSoftware simulation/interpretation/emulationApplication programming interfaceMultiple platform
Embodiments of the invention provide a platform-independent application development framework for programming an application. The framework comprises a content interface configured to provide an Application Programming Interface (API) to program the application comprising a programming code to be executed on one or more platforms. The API provided by the framework is independent of the one or more platforms. The framework further comprises an application environment configured to provide an infrastructure that is independent of the one or more platforms and one or more plug-in interfaces configured to provide an interface between the application environment and the one or more platforms.
Owner:XENOGENIC DEV LLC
Application control in peer-to-peer ad-hoc communication networks
A computer system, method, and computer program product for controlling access to an application program in a wireless device connected to an ad-hoc communications network. The method comprises sending an inquiry message to the network, receiving a response, choosing a selected application, and examining control parameters associated with the selected application. The control parameters dictate a behavior of the selected application such as allowing or refusing communication with the selected application. When a nearby wireless device includes a matching application, connecting the selected application and the matching application further comprises sending a connection request, receiving connection response, launching the selected application, and sending a service request. When the selected application closes, the method further comprises erasing the selected application. To choose the selected application, the method further comprises retrieving an entry from a distributed application directory or selecting the application based on a priority assigned to the entry.
Owner:NOKIA CORP
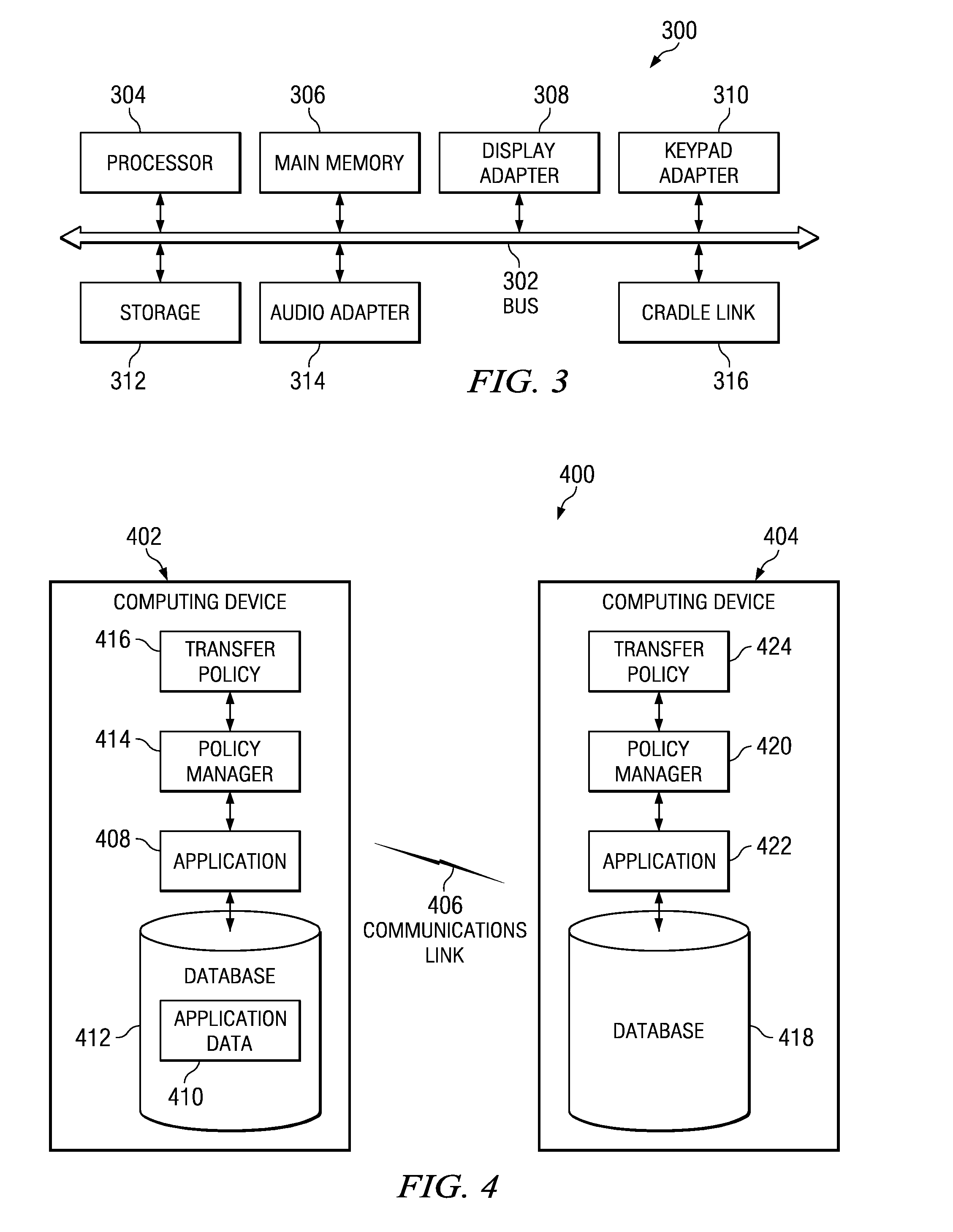
Method and Apparatus for Policy-Based Transfer of an Application Environment
InactiveUS20080313257A1Multiple digital computer combinationsProgram controlComputer networkData shipping
A computer implemented method, apparatus, and computer program product for transferring an application environment between a plurality of computing devices. The process retrieves a set of transfer policies in response to detecting a presence of a second computing device in the plurality of computing devices. The set of transfer policies govern the transfer of the application environment from a first computing device. The process then determines whether conditions for the transfer have been satisfied. Conditions for transfer are specified by the set of transfer policies. The process subsequently transfers application data to the second computing device if the conditions for the transfer have been satisfied. The application data is used to create the application environment on the second computing device.
Owner:IBM CORP
Systems and methods of risk based rules for application control
In various embodiments, an agent on a digital device may comprise a monitor module, an application identification module, a vulnerability module, a rules database, and a rule module. The monitor module may be configured to monitor a device for an instruction to execute a legitimate application. The application identification module may be configured to identify one or more attributes of the legitimate application. The vulnerability module may be configured to retrieve risk information based on the one or more attributes of the legitimate application. The risk information may be determined from known vulnerabilities of the legitimate application. The rules database may be for storing a rule associated with the risk information. The rule module may be configured to retrieve the rule from the rule database based on the risk information and to control the legitimate application based on the rule.
Owner:BEYONDTRUST SOFTWARE
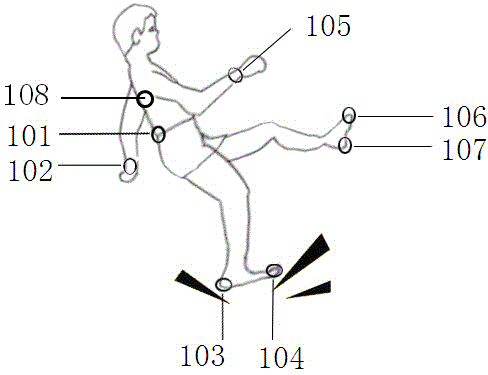
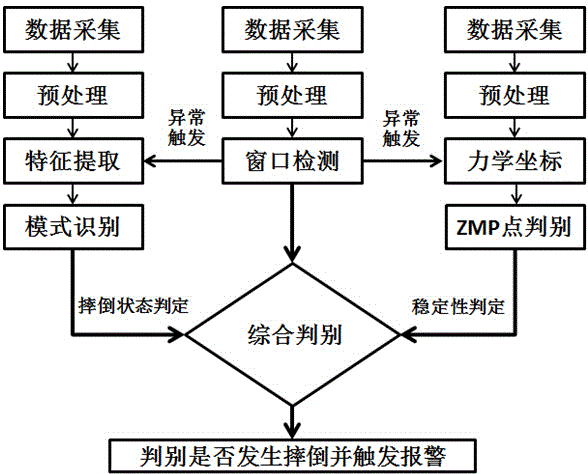
Wearing type dynamic real-time fall detection method and device
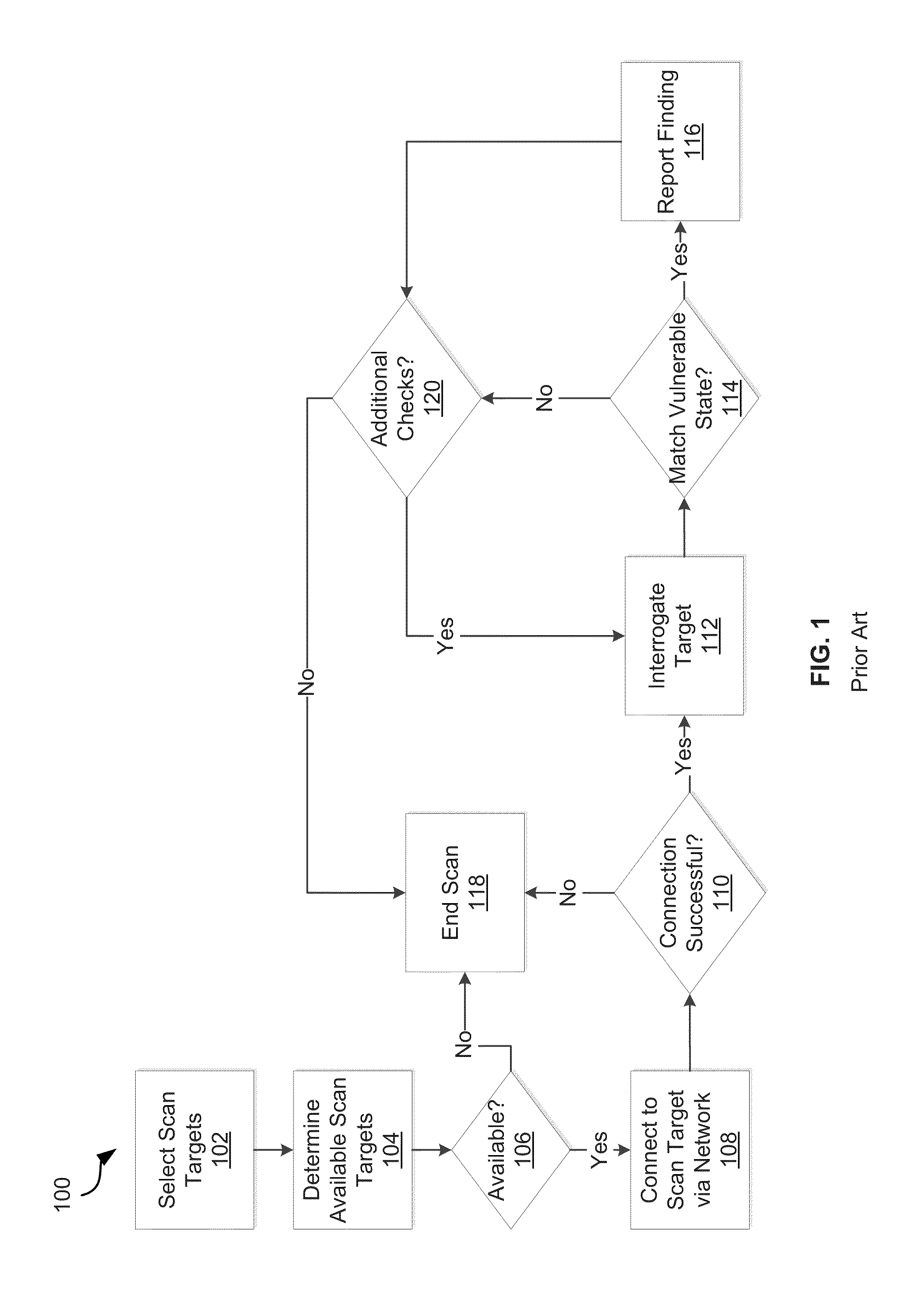
ActiveCN103976739AAchieve protectionHigh precisionCharacter and pattern recognitionDiagnostic recording/measuringHuman bodyHardware structure
The invention discloses a wearing type dynamic real-time fall detection method and device. The wearing type detection device comprises a specific hardware structure consisting of a foot part, a waist part, a wrist part and a back part. According to the dynamic real-time fall detection method, real-time judgment of the fall of human body in any state can be finished. The core algorithm of the detection device comprises a threshold opening logic structure caused by sudden change of gait acceleration, a human body posture dynamic stability judgment algorithm based on zero moment point (ZMP), and a fall mode identification algorithm based on a human body motion database. A complete dynamic real-time detection system is constructed, and the aims of wide application field, low dependence on the application environment and real-time detection are fulfilled. Moreover, the detection method and the detection device are high in accuracy, and have the advantages of low system cost, small system size and good convenience in wearing.
Owner:BEWIS TECH
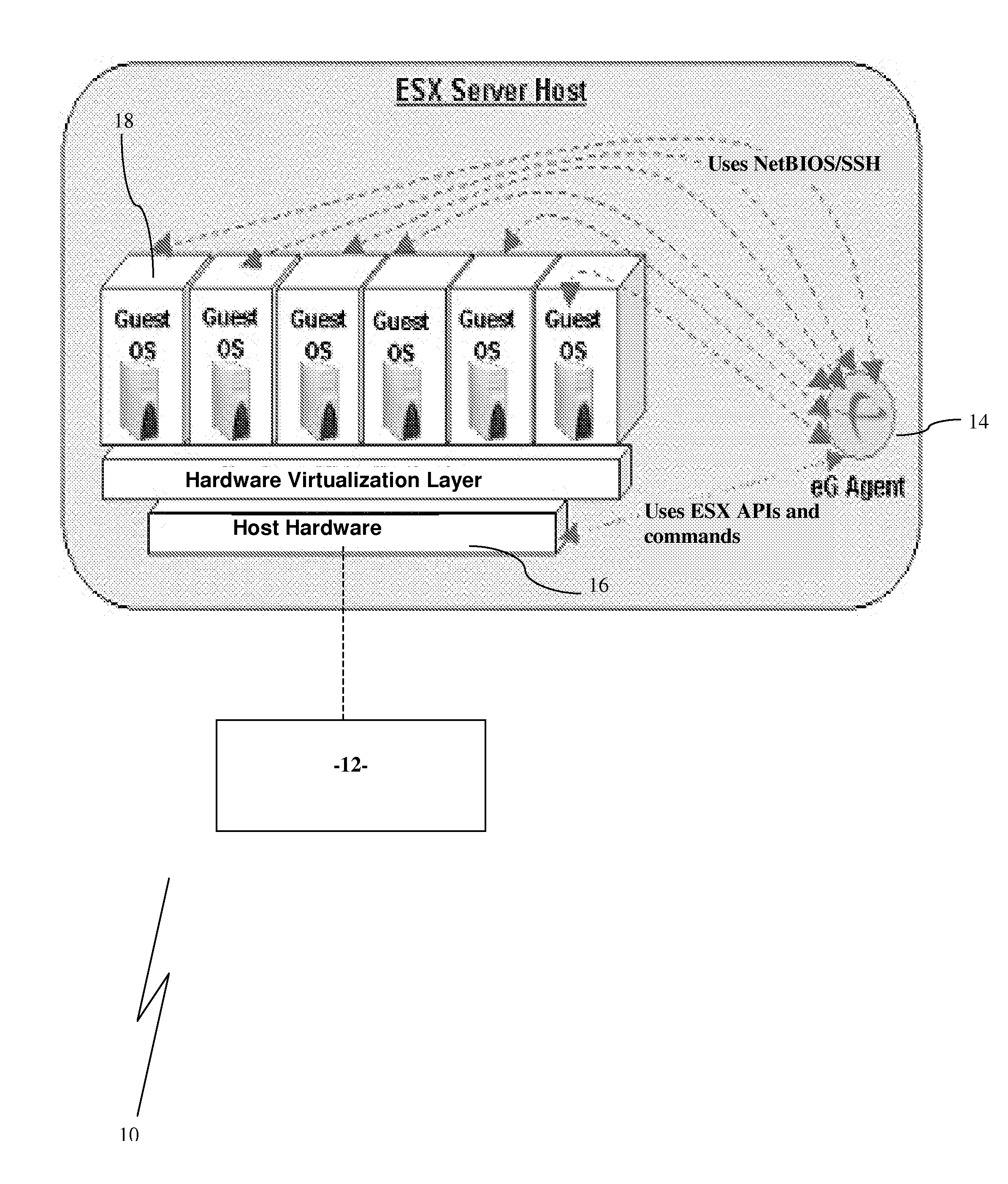
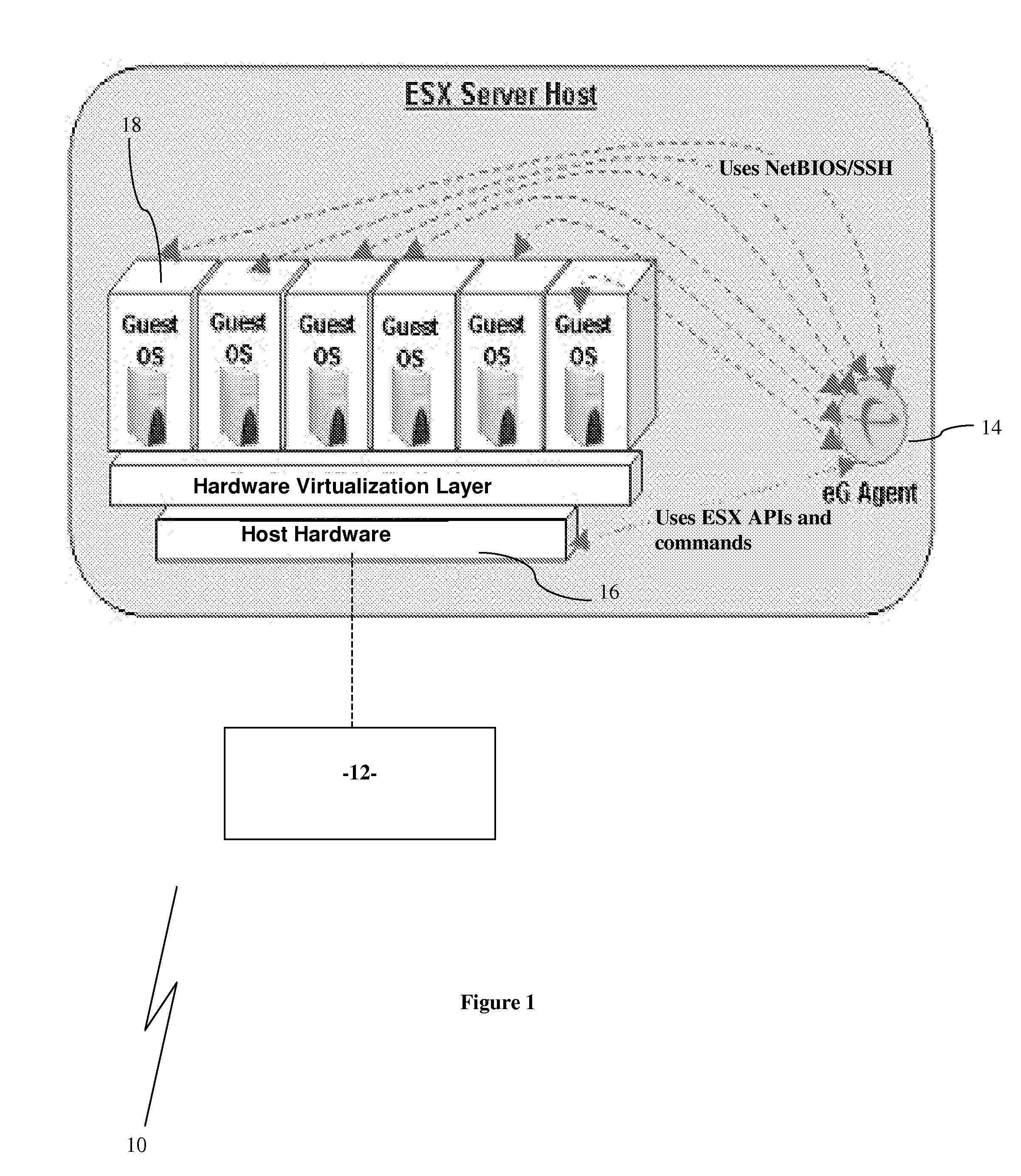
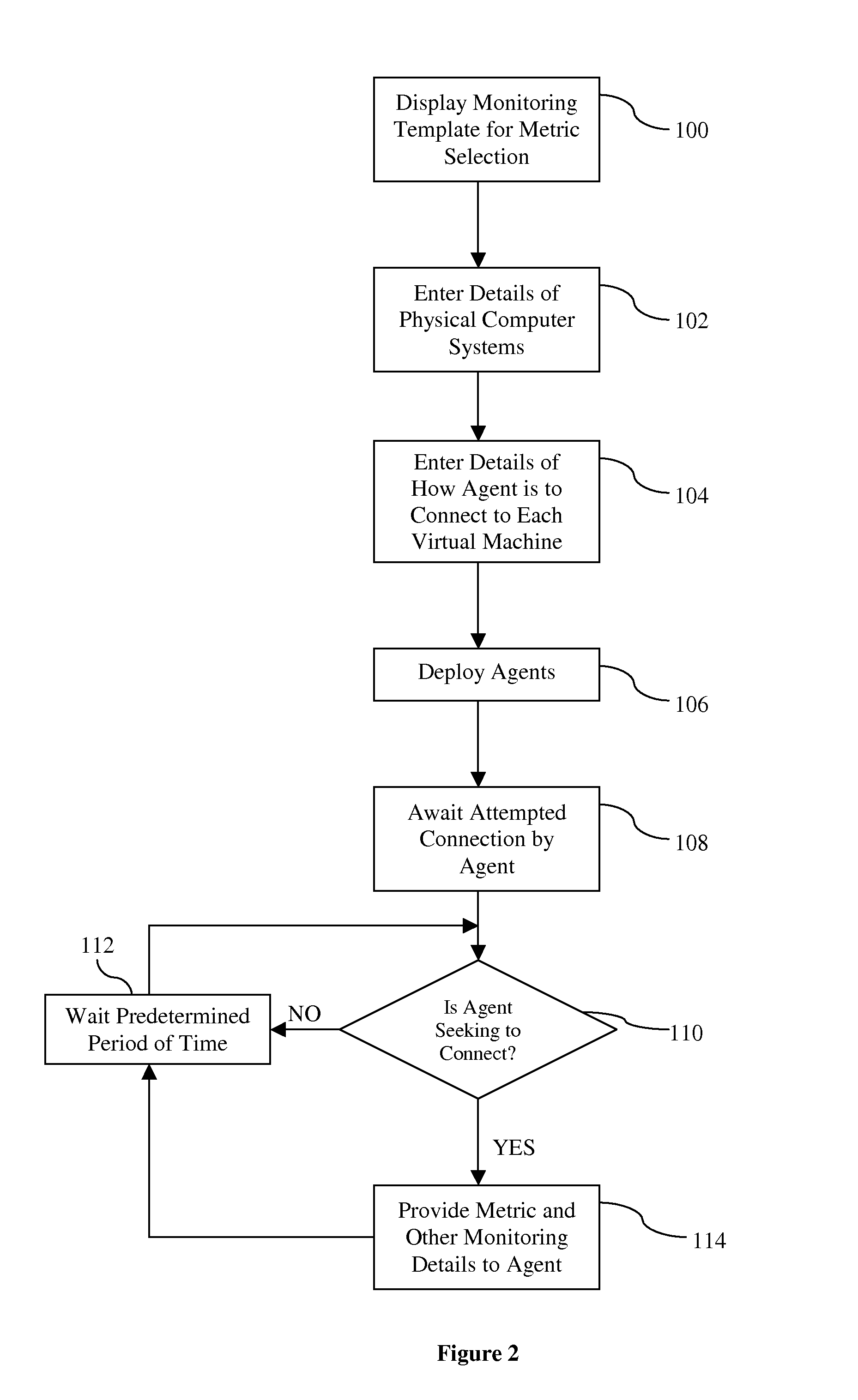
Monitoring System for Virtual Application Environments
ActiveUS20090024994A1Reduce resource consumptionEasy maintenanceError detection/correctionSoftware simulation/interpretation/emulationOperational systemMonitoring system
A monitoring system for virtual application environments comprising: at least one physical machine executing a first operating system; at least one virtual machine operating on at least one of the at least one physical machines, each such virtual machine operating a second operating system; and an agent program operating on each of the at least one physical machines, where, each agent program is operable to obtain a first set of metrics from the first operating system, such first set of metrics including metrics in respect of each virtual machine as viewed by the first operating system, and operable to connect to the second operating system of each virtual machine hosted on the physical machine the agent program operates on and obtain a second set of metrics in respect of the virtual machine from the second operating system, the agent program further operable to communicate the first and second sets of metrics to a manager program.
Owner:EG INNOVATIONS PTE
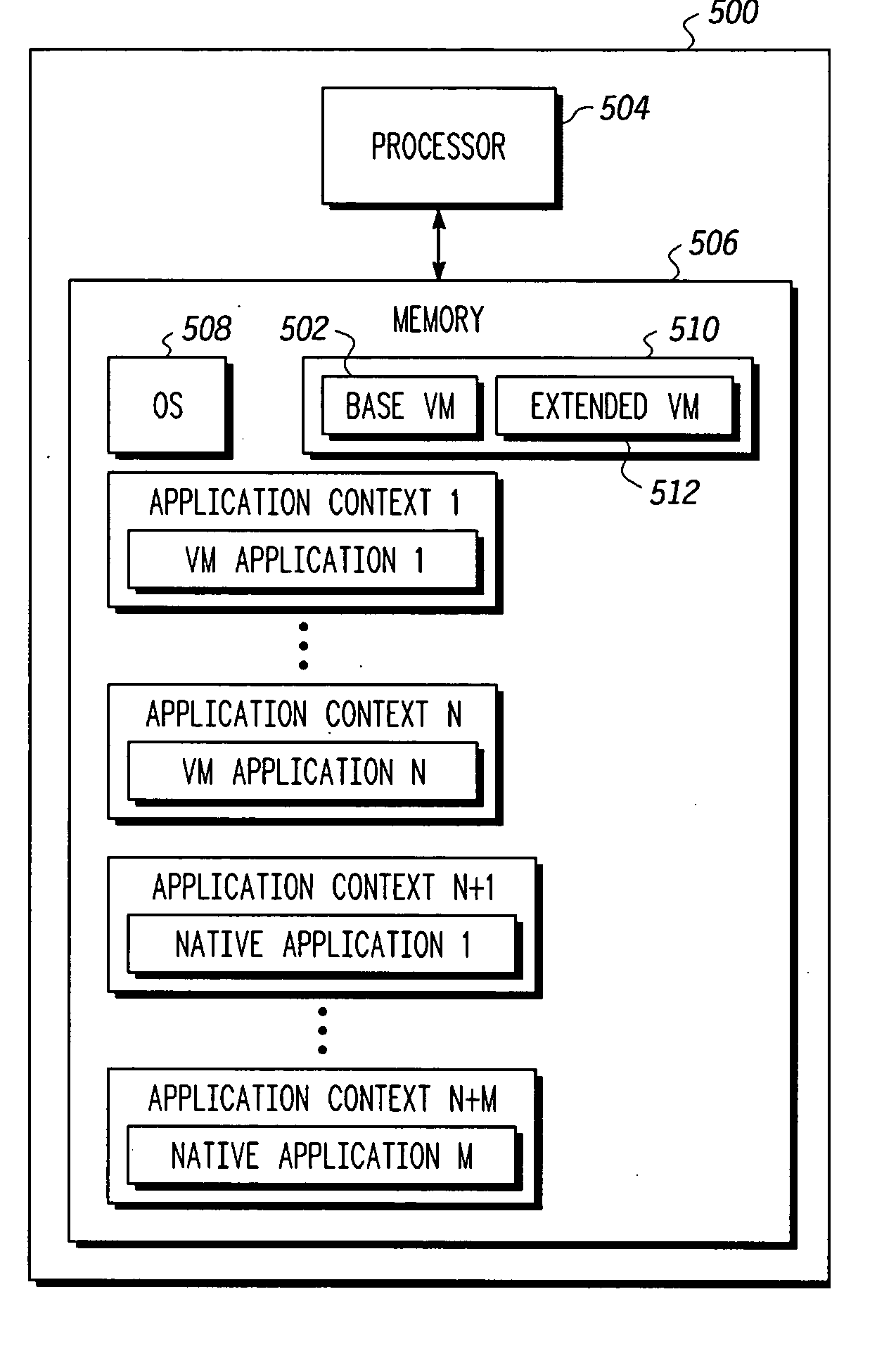
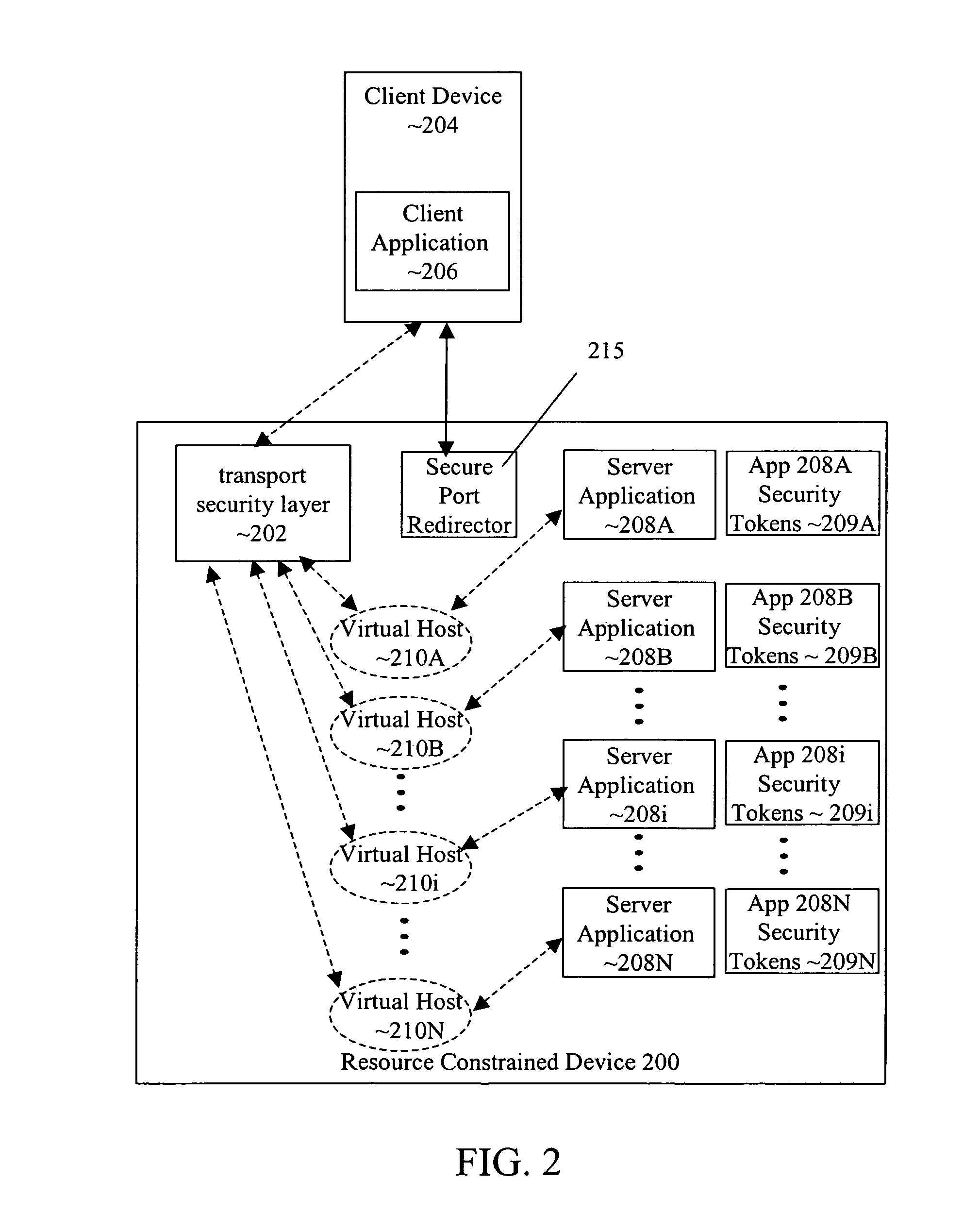
Virtual machine extended capabilities using application contexts in a resource-constrained device
ActiveUS20060218536A1Improve abilitiesMultiprogramming arrangementsSoftware simulation/interpretation/emulationFunction representationData structure
Embodiments of the systems and methods utilize application contexts for extending virtual machines in a resource-constrained device to allow virtual machines to at least exercise scheduling control over platform independent applications and platform dependent native applications. Application contexts can be assigned to each application in the system. An application is represented by one or more data structures and functions. In one embodiment, an “application context” includes an interface to a virtual machine and a container for an execution environment of the application. The interface represents a mapping of services to an execution environment. The application context can isolate control over the execution of the application from the execution environment, thus, allowing the virtual machine to control execution of the application and allowing the application to be executed in a native environment, a virtual machine environment, or any other execution environment.
Owner:GOOGLE TECH HLDG LLC +1
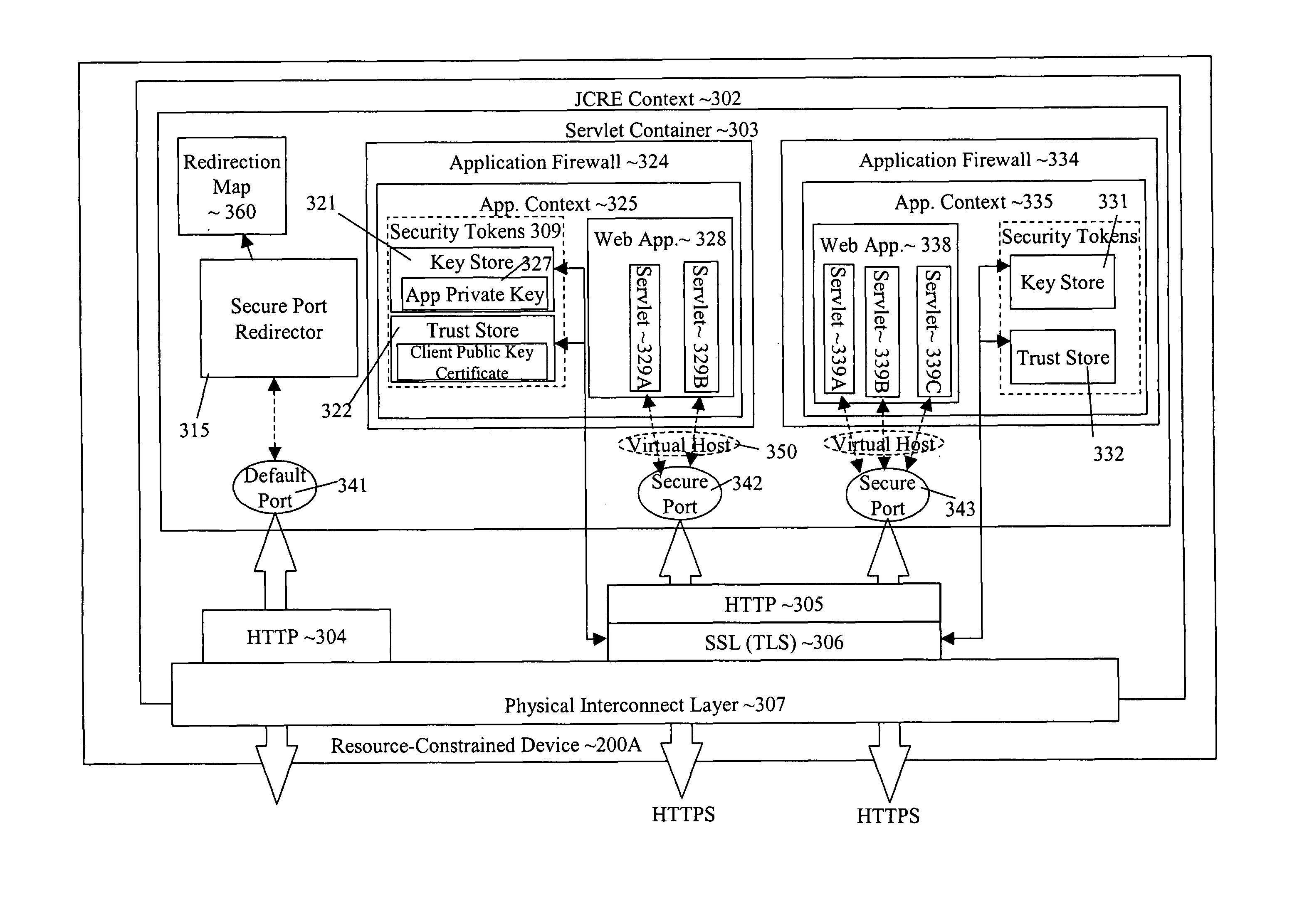
Transport-level web application security on a resource-constrained device
ActiveUS8245285B1Facilitates secure communicationFacilitate communicationDigital data processing detailsMultiple digital computer combinationsSecure communicationClient-side
A system and method is provided to facilitate secure communications for a server-application executing on a resource-constrained device. A request, from a client application executing on a client device to access a server application executing on the resource-constrained device is received on an application-specific secure port of a resource-constrained device. The request is authenticated using a security token stored in an application context of the server application. The authentication is performed by a transport security layer protocol executing within the application context of the server application. The security token is specific for the server application. A secure connection is established directly between the secure port and the client application upon the authentication being successful.
Owner:ORACLE INT CORP
Method and system for implicitly resolving pointing ambiguities in human-computer interaction (HCI)
InactiveUS20030016252A1Accurate understandingStatic indicating devicesInput/output processes for data processingObject basedAmbiguity
A method and system for implicitly resolving pointing ambiguities in human-computer interaction by implicitly analyzing user movements of a pointer toward a user targeted object located in an ambiguous multiple object domain and predicting the user targeted object, using different categories of heuristic (statically and / or dynamically learned) measures, such as (i) implicit user pointing gesture measures, (ii) application context, and (iii) number of computer suggestions of each predicted user targeted object. Featured are user pointing gesture measures of (1) speed-accuracy tradeoff, referred to as total movement time (TMT), and, amount of fine tuning (AFT) or tail-length (TL), and, (2) exact pointer position. A particular application context heuristic measure used is referred to as containment hierarchy. The invention is widely applicable to resolving a variety of different types of pointing ambiguities such as composite object types of pointing ambiguities, involving different types of pointing devices, and which are widely applicable to essentially any type of software and / or hardware methodology involving using a pointer, such as in computer aided design (CAD), object based graphical editing, and text editing.
Owner:RAMOT AT TEL AVIV UNIV LTD
Adaptive gateway for switching transactions and data on unreliable networks using context-based rules
ActiveUS20110047294A1Data switching by path configurationMultiple digital computer combinationsModularityService selection
Application level switching of transactions at a gateway is provided. The gateway is configured to switch the transaction based on the application level content, a current state of a transport environment, and / or dynamic rules for switching transactions. For example, several possible service providers can be selected for the type of transaction, and the gateway can monitor not only the round-trip time through the network(s) to different possible service providers, but also the time required to complete the transaction at the application level and return a response. The application is chosen on the sending side of the network, and application level formatting is done on the sending side as well. The gateway uses modular code and data, and separate instances of processing code to allow dynamic updating. Rules for application service selection can be selectively uploaded to the gateway from a client. The rules for different available application services can be distributed across different gateways.
Owner:VISA USA INC (US)
Network flux cleaning system
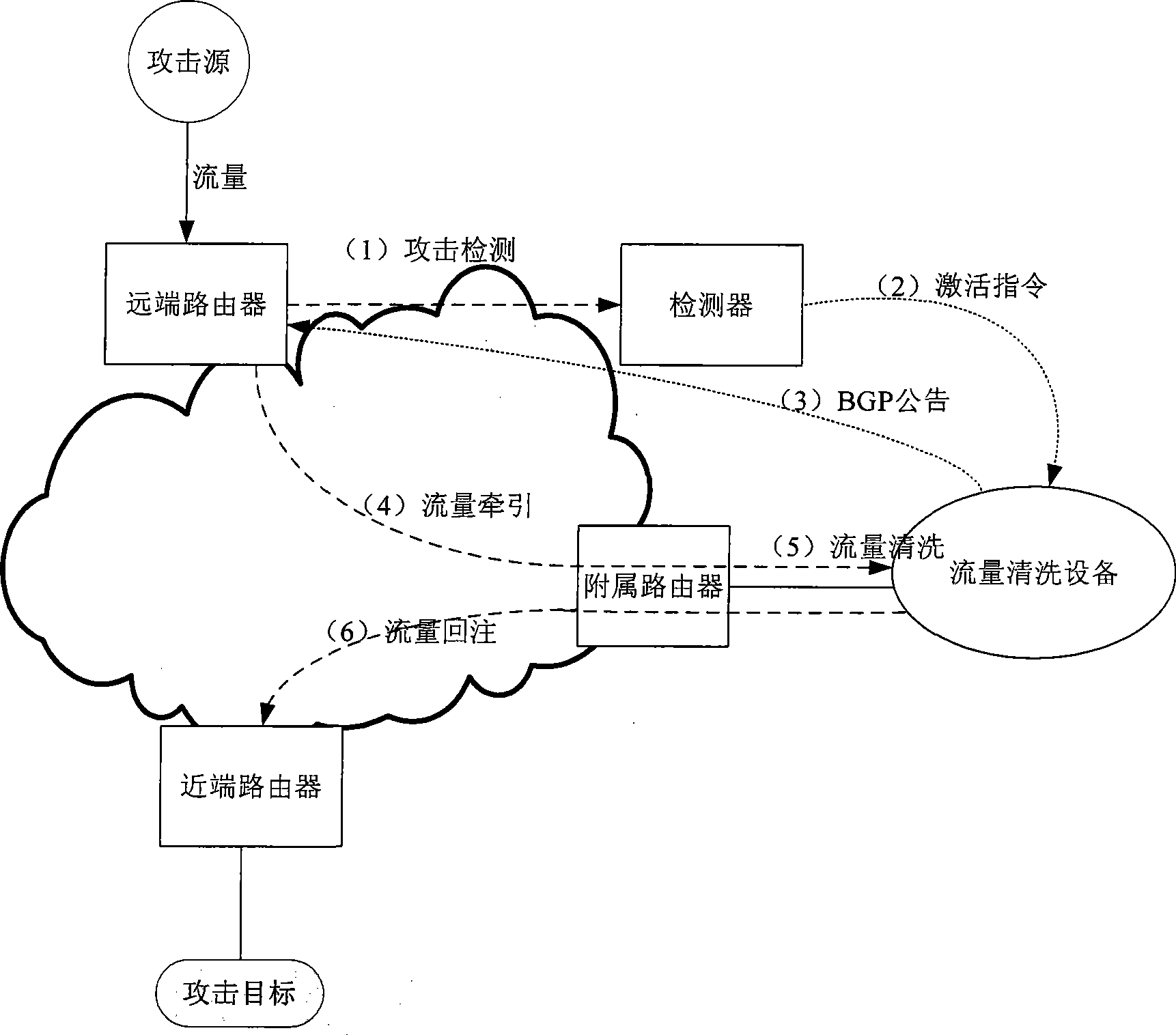
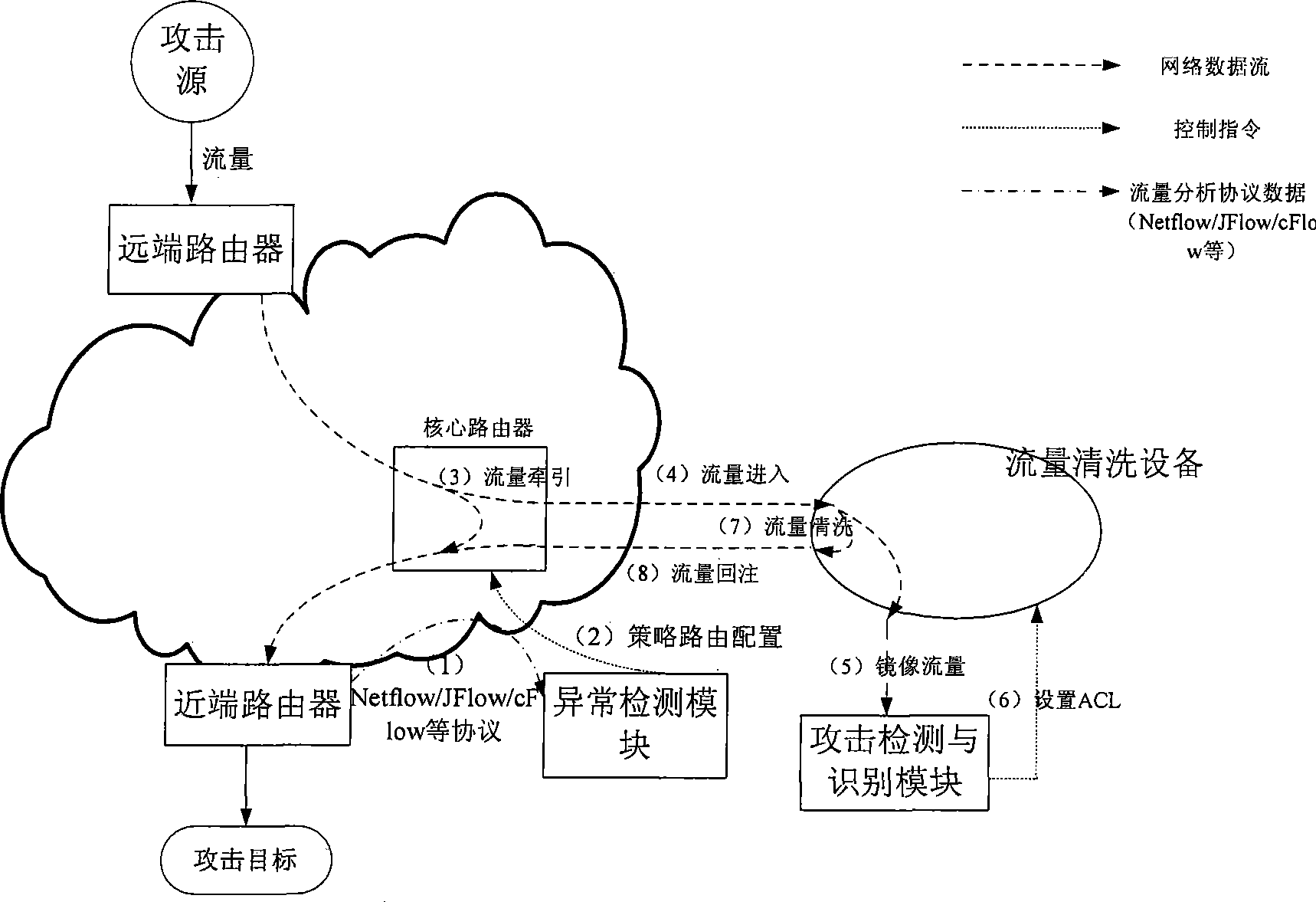
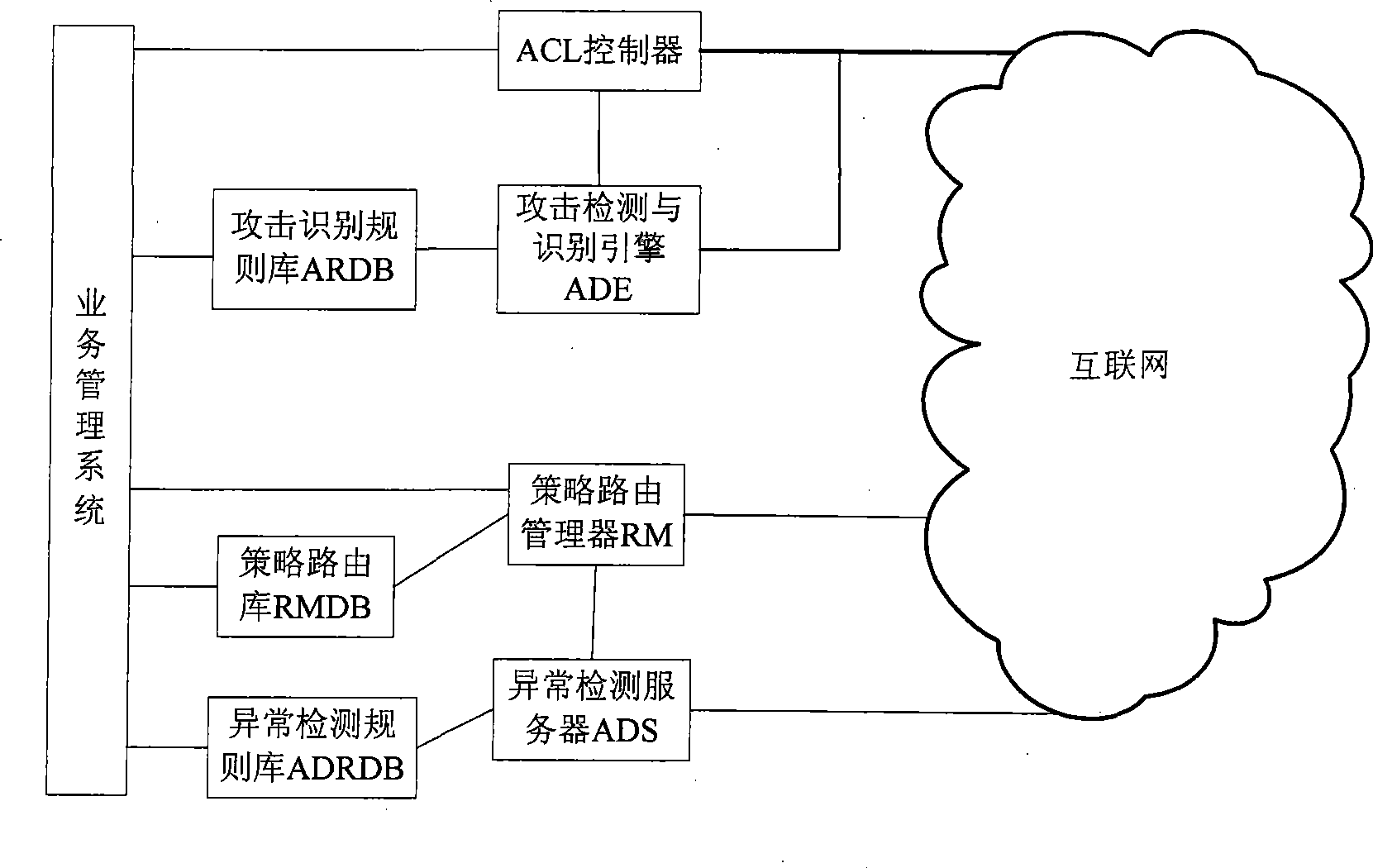
ActiveCN101431449AEasy to handleIncrease flexibilityData switching networksTraffic capacityRelevant information
The invention provides traffic rinsing system for monitoring and managing network traffic in network application environment comprising abnormal detection module, attack module and identifying module and traffic rinsing equipment. The abnormal detection module monitors the network traffic, creates strategy routing and transmits to designated router of network application environment once finding suspect network traffic; the designated router tows the suspect network traffic to traffic rinsing equipment; the traffic rinsing equipment mirrors the received suspect network traffic to attack detection and identifying module for identifying the attack traffic, and create ACL rule according to the related information of attack traffic, then transmits to traffic rinsing equipment; the rinsing equipment separates suspect traffic and normal traffic in the suspect network according to ACL rule. The invention adopts mechanism of separate decision-making and control so that the attack detection and identifying course as decision have huge agility.
Owner:北京智维盈讯网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com