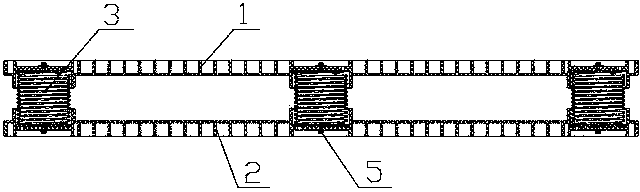
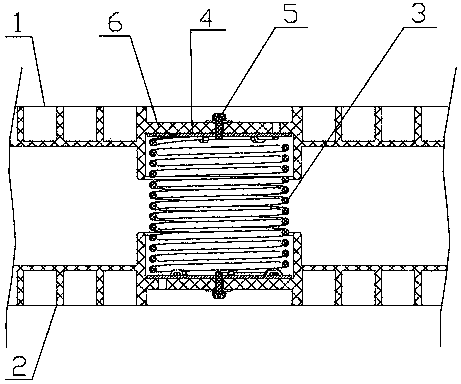
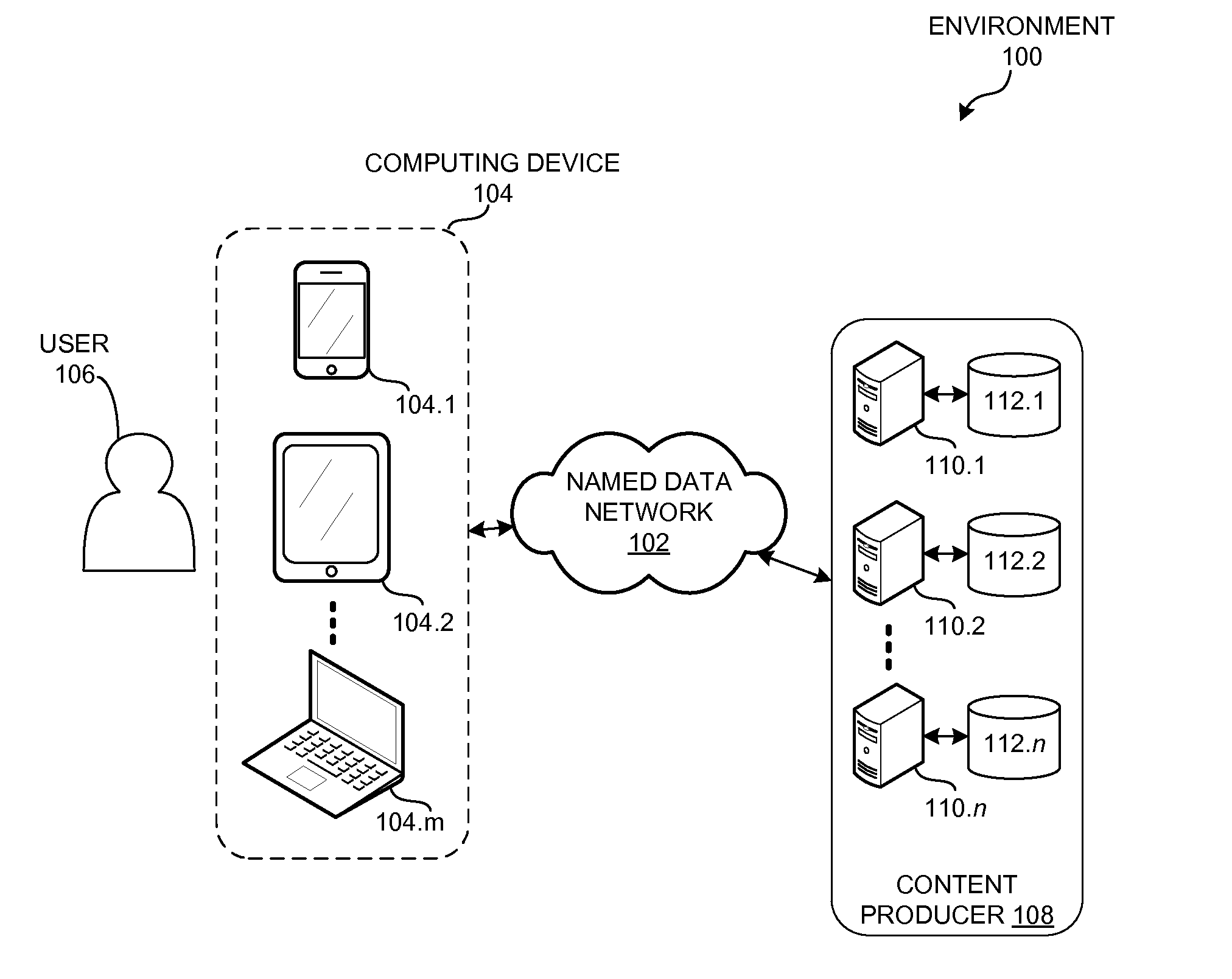
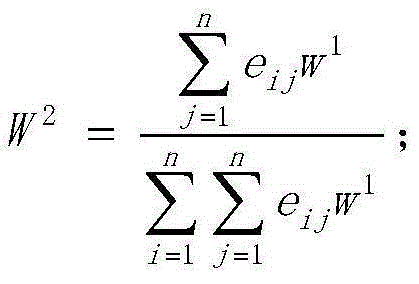Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
146 results about "Transport security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
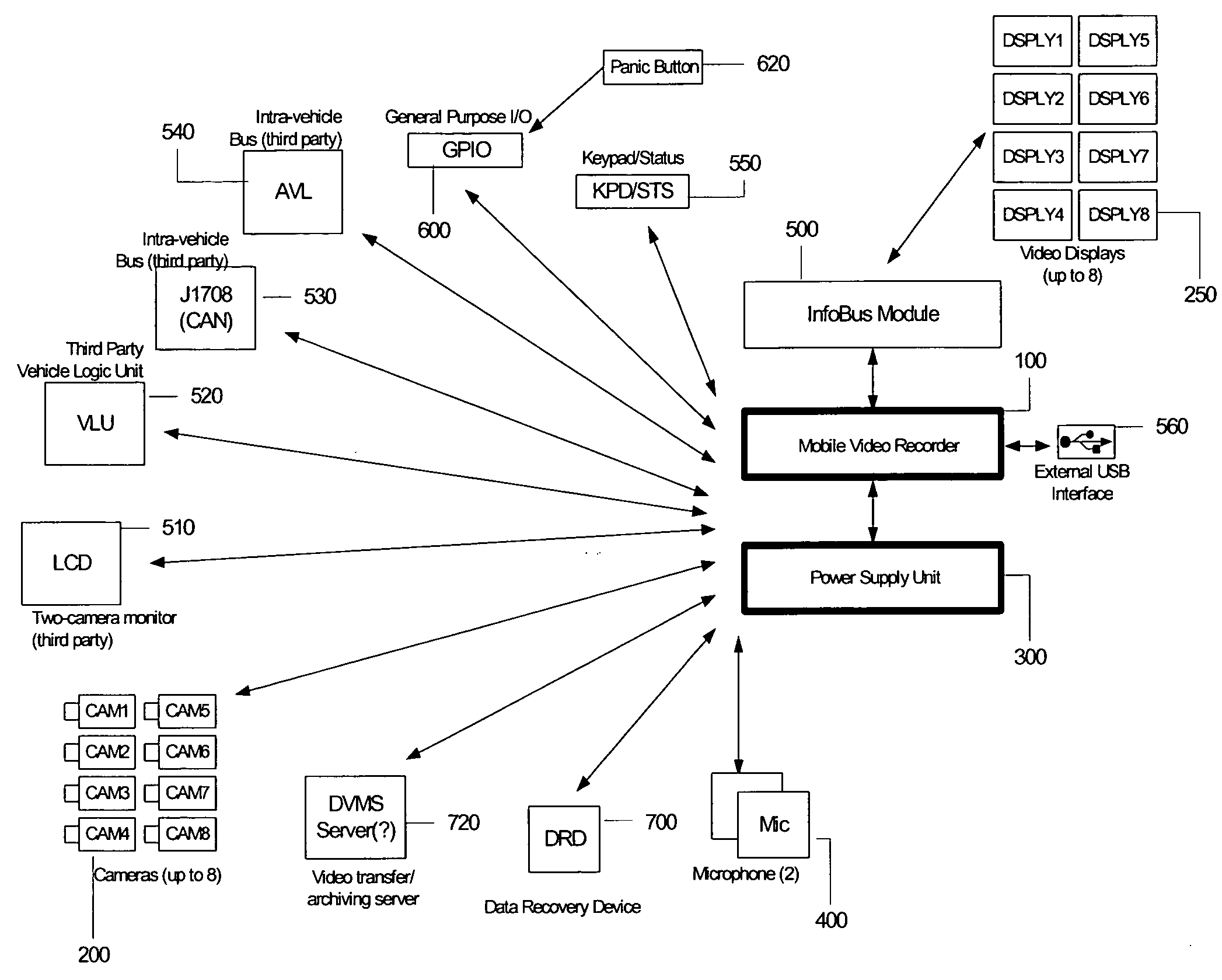
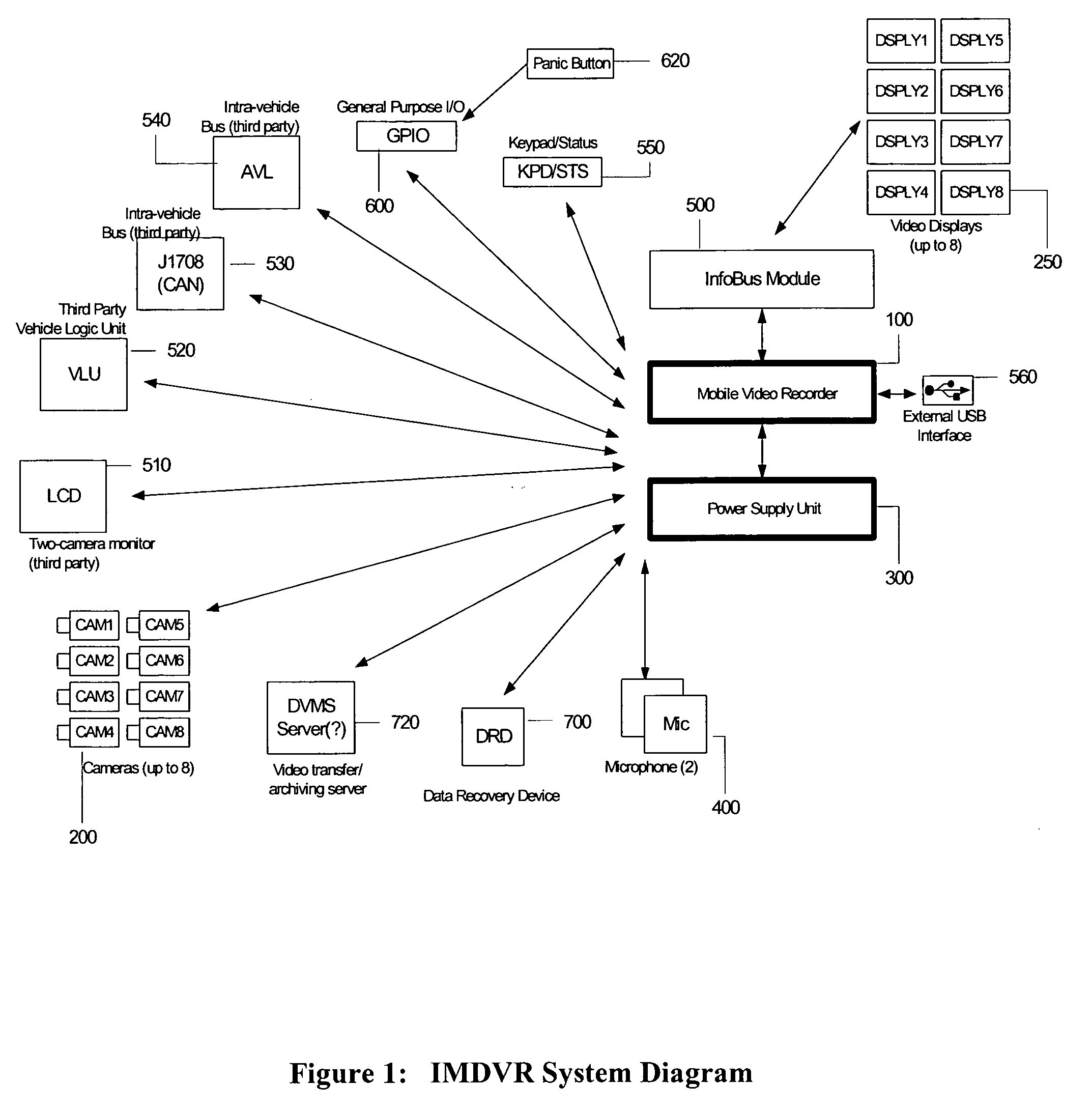
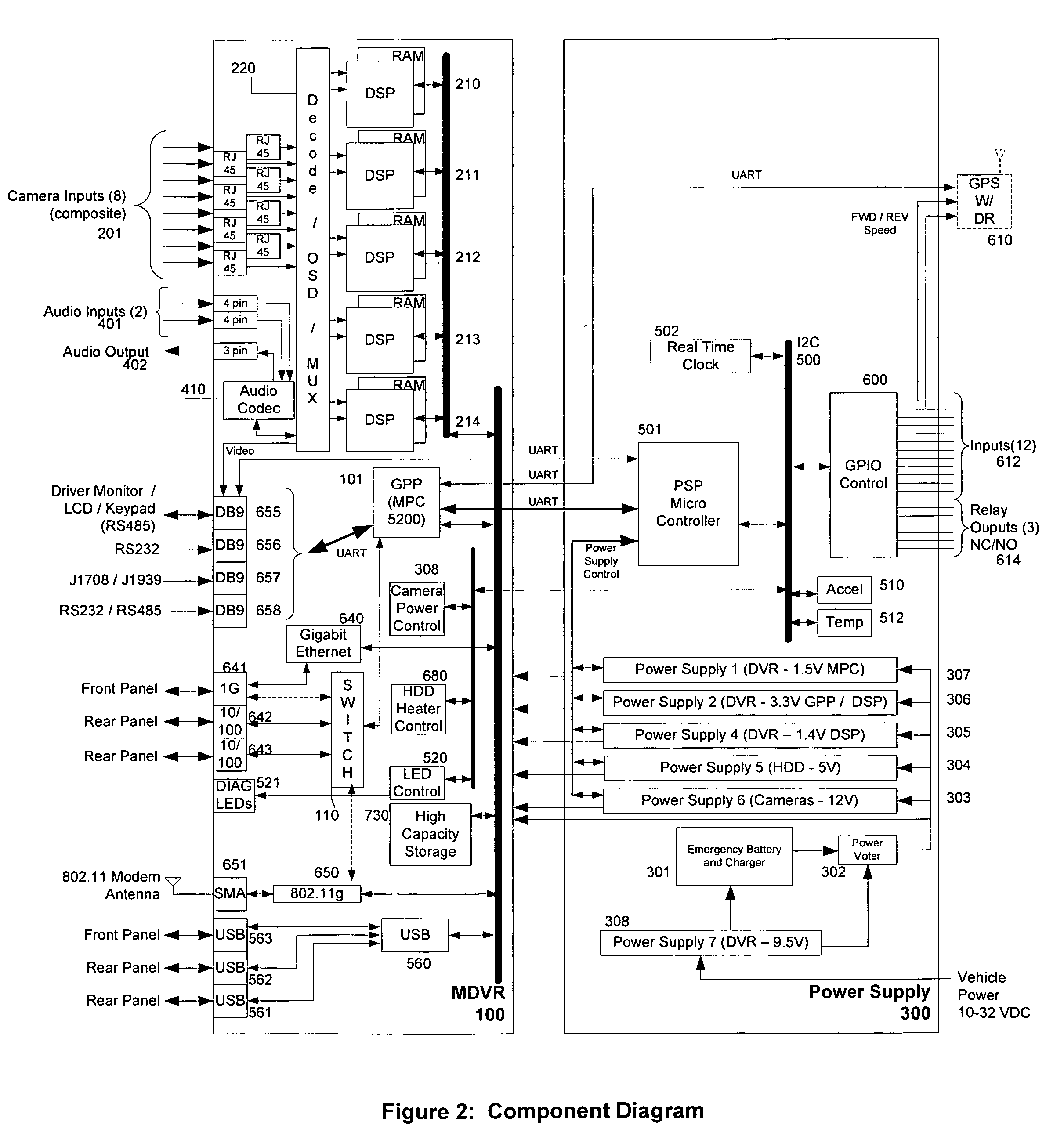
Mobile digital video recording system
ActiveUS20070035632A1Television system detailsCosmonautic condition simulationsDigital videoData stream
The Improved Mobile Digital Video Recorder (IMDVR) system is a ruggedized, multiple camera video and audio recording system that is installed within a public transit vehicle to record, store, and manage an integrated data stream of data captured within and exterior to the transit vehicle. The system is focused on multiple person vehicles and the capture of an integrated data stream for use in transit security, liability, and evidentiary processes.
Owner:UTILITY ASSOCS
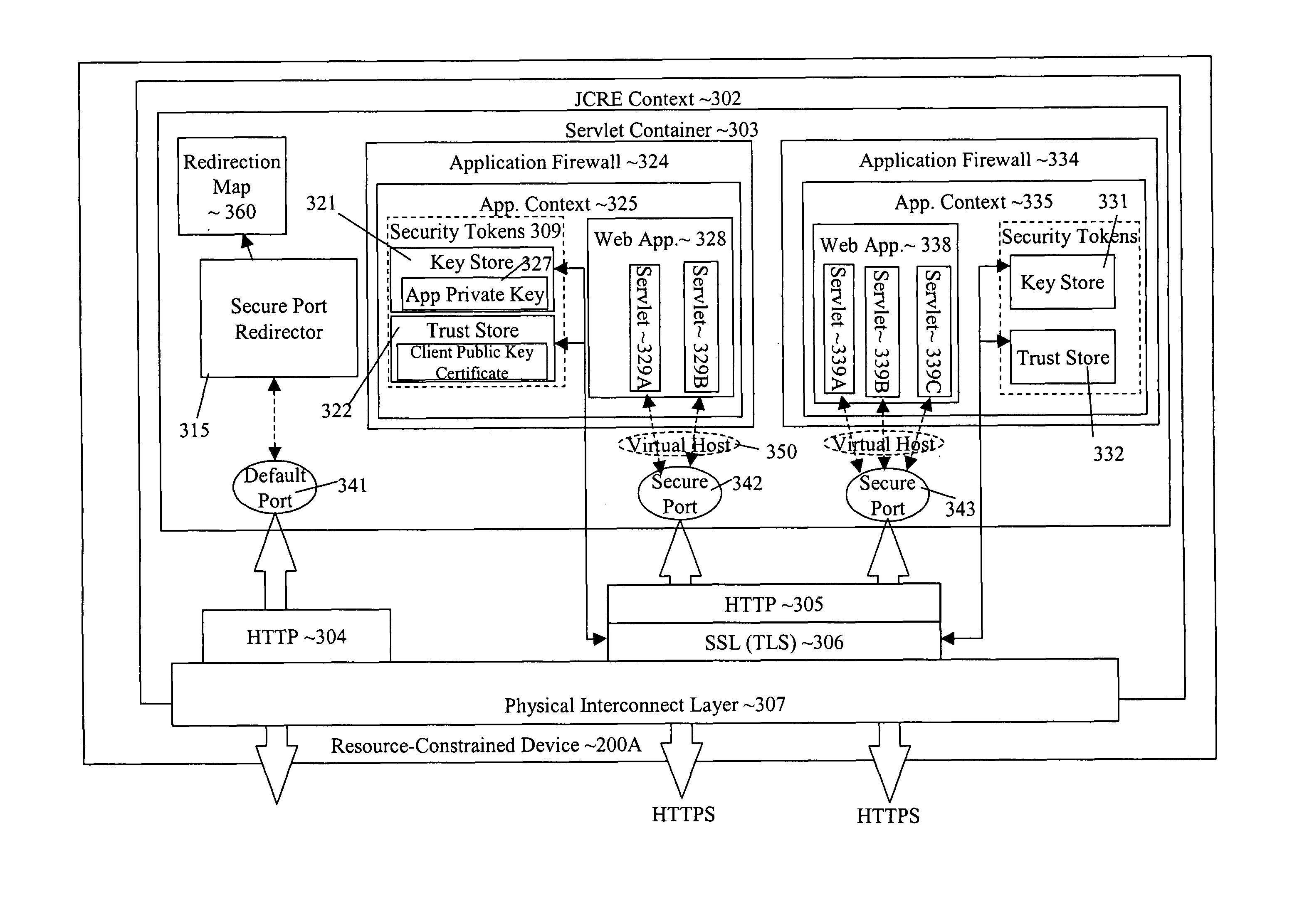
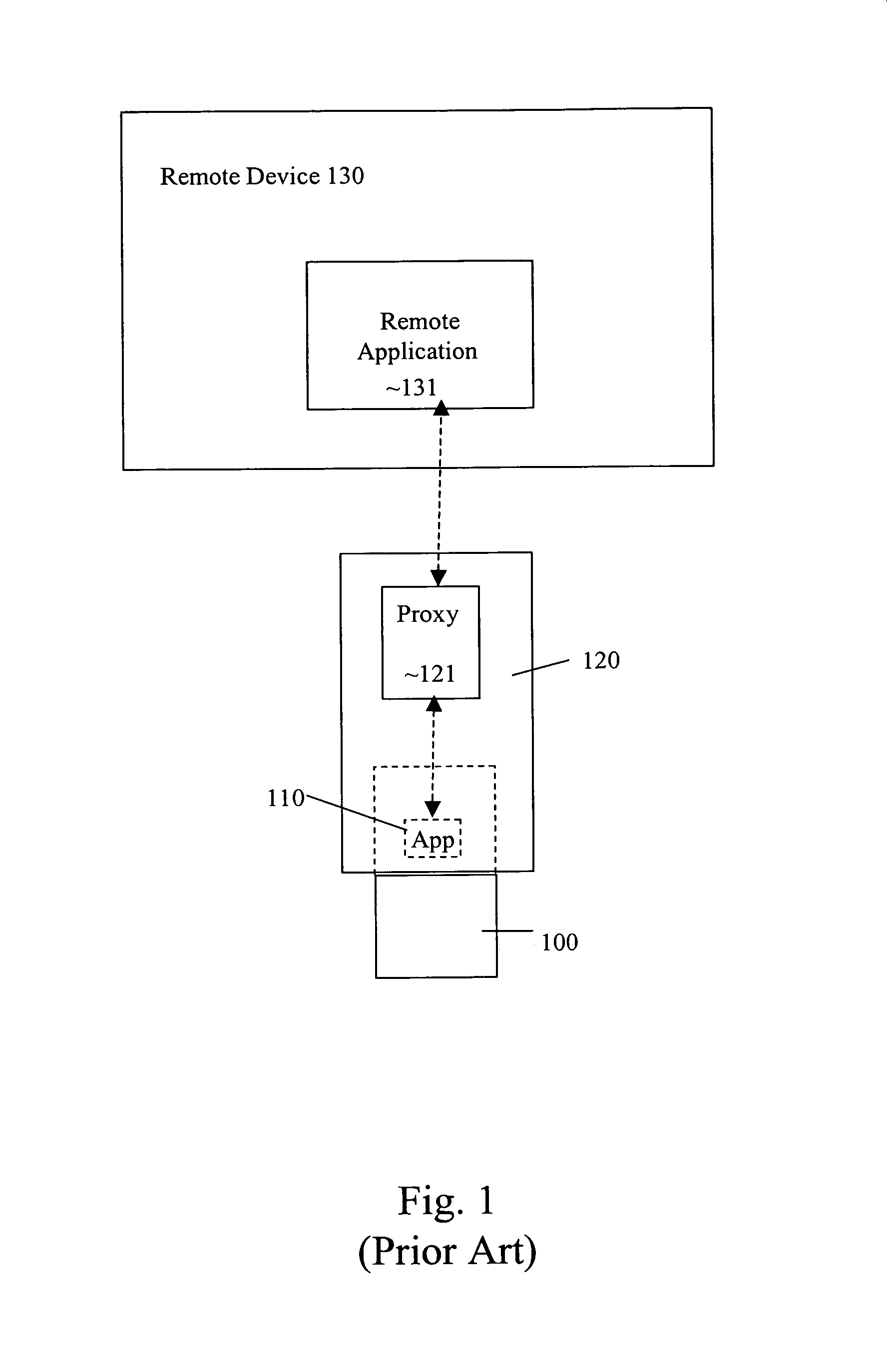
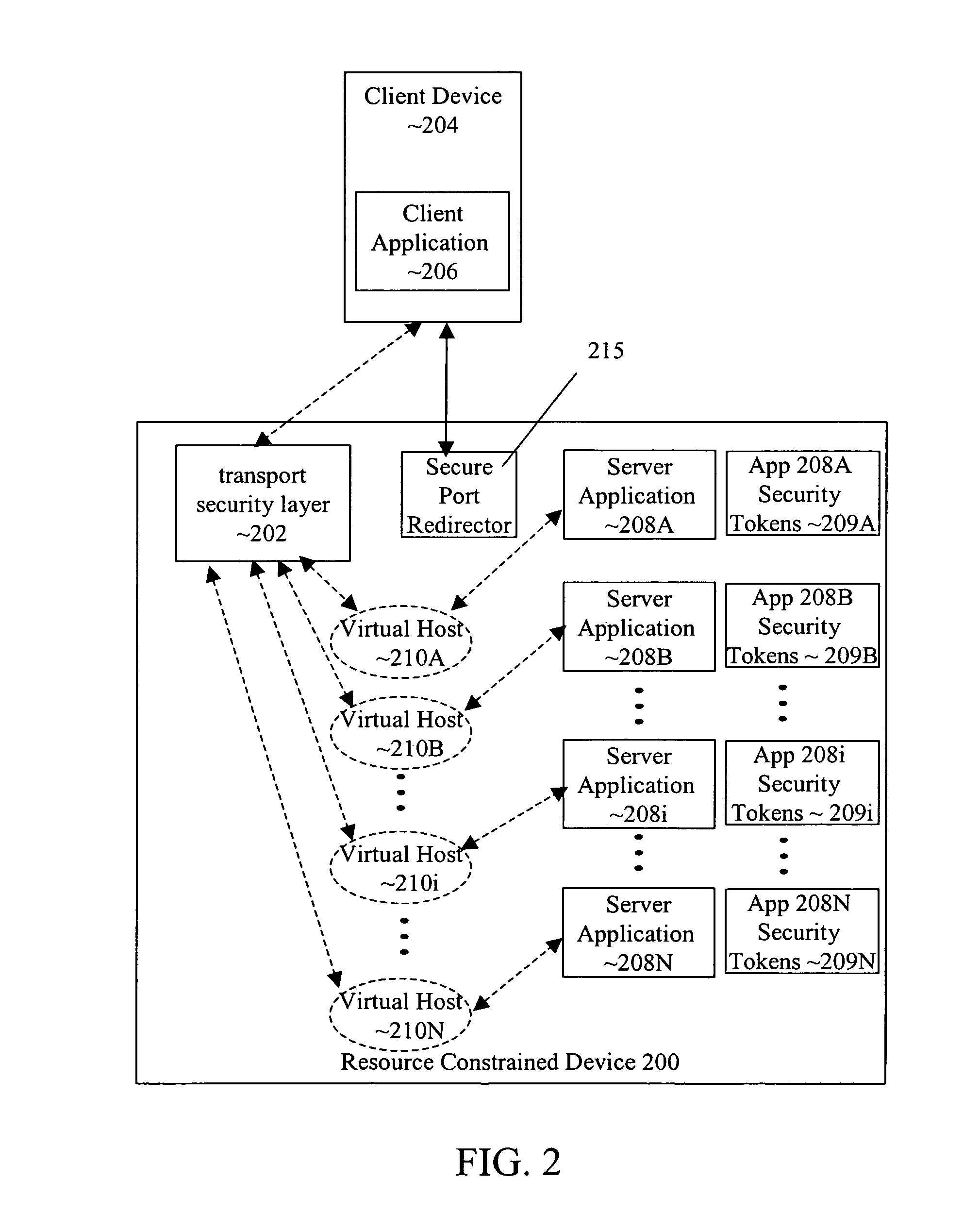
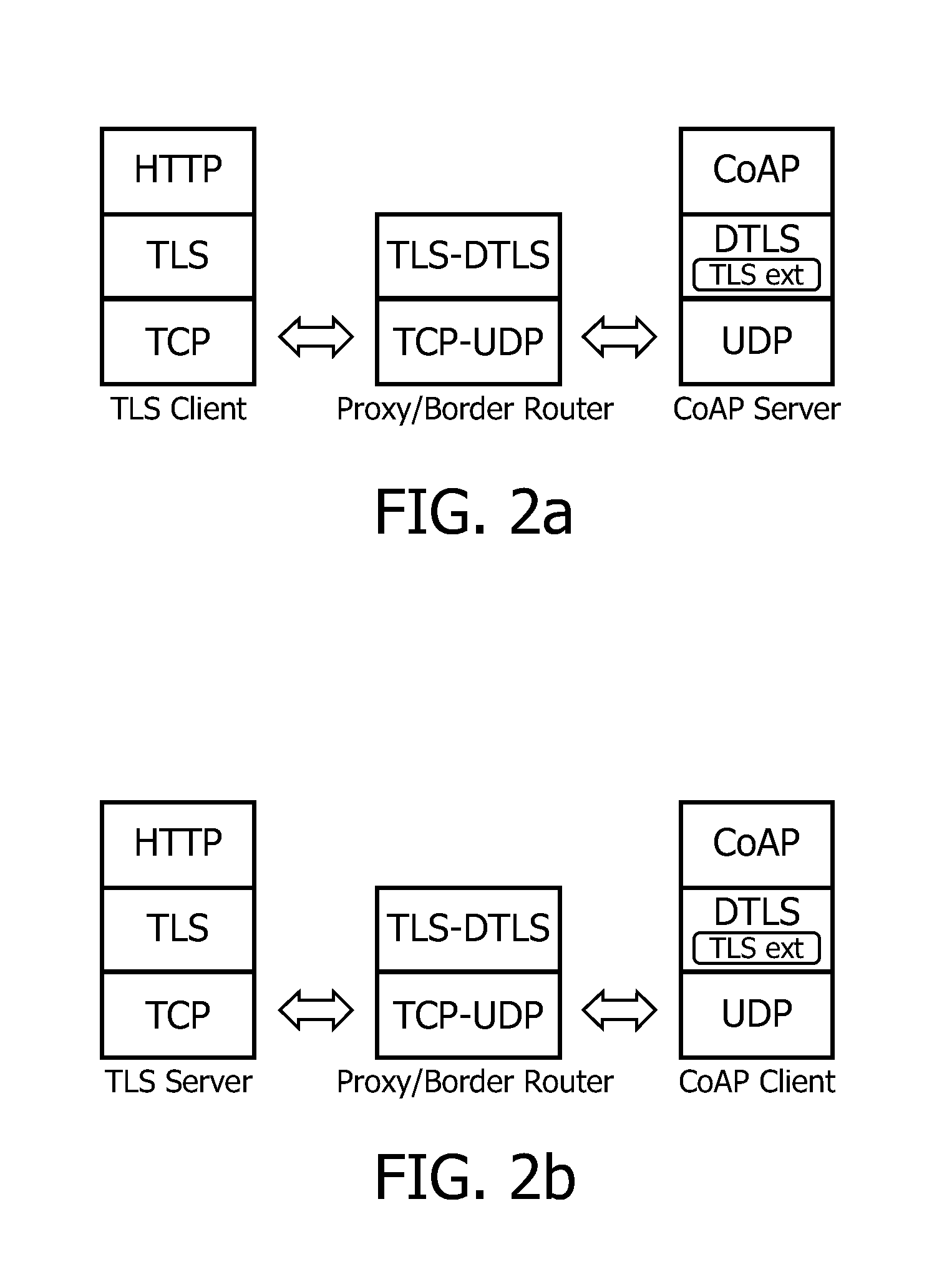
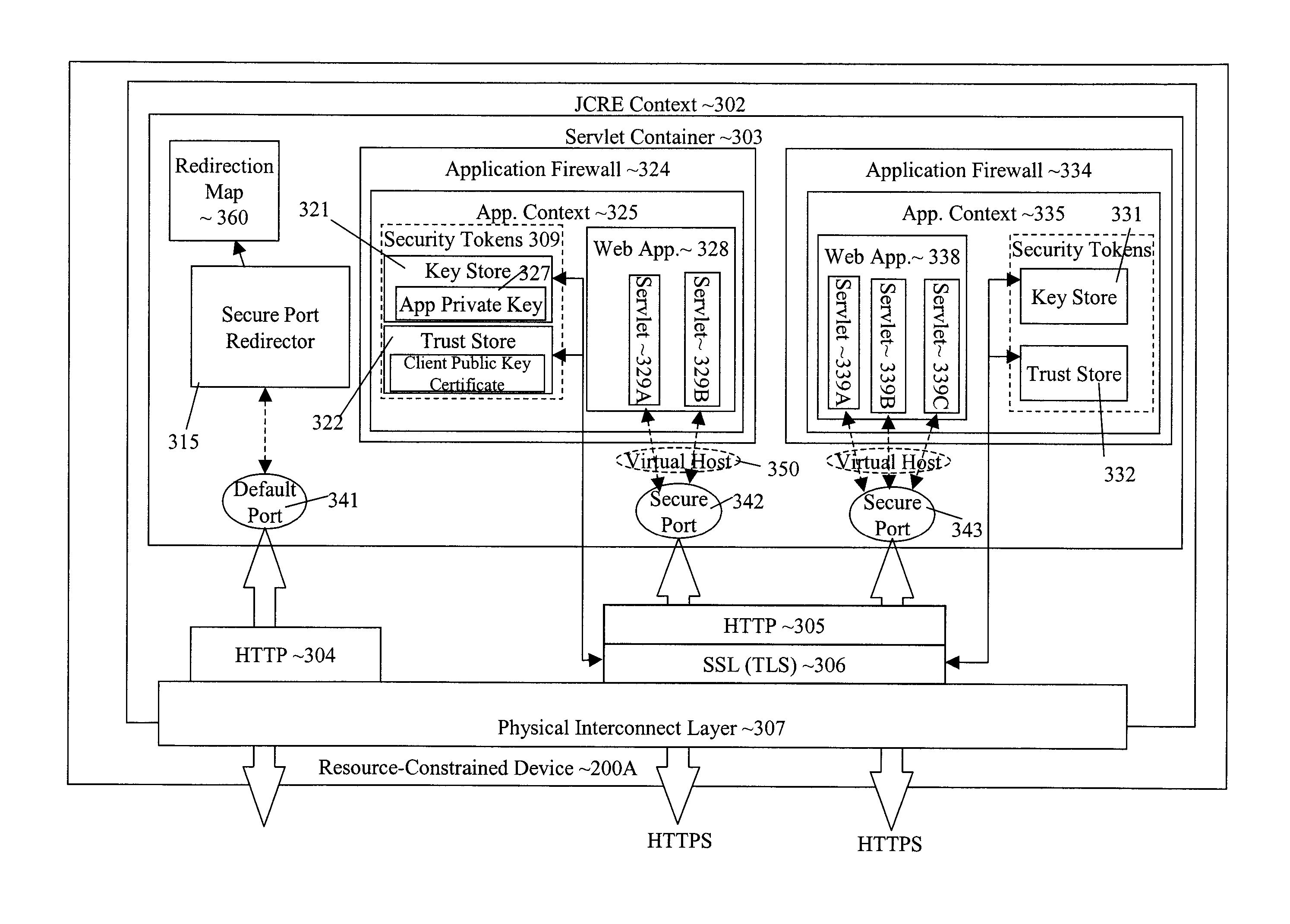
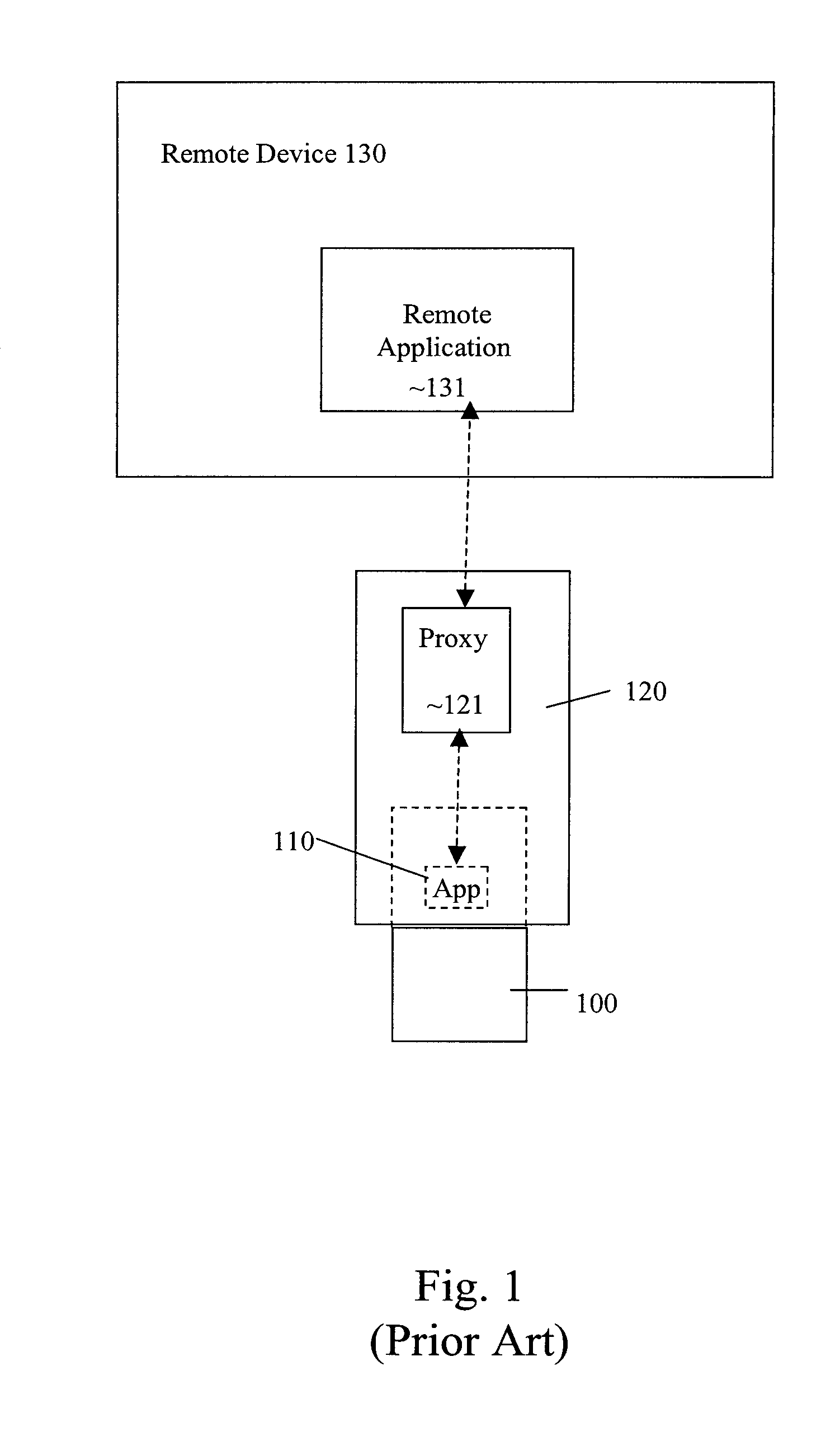
Transport-level web application security on a resource-constrained device
ActiveUS8245285B1Facilitates secure communicationFacilitate communicationDigital data processing detailsMultiple digital computer combinationsSecure communicationClient-side
A system and method is provided to facilitate secure communications for a server-application executing on a resource-constrained device. A request, from a client application executing on a client device to access a server application executing on the resource-constrained device is received on an application-specific secure port of a resource-constrained device. The request is authenticated using a security token stored in an application context of the server application. The authentication is performed by a transport security layer protocol executing within the application context of the server application. The security token is specific for the server application. A secure connection is established directly between the secure port and the client application upon the authentication being successful.
Owner:ORACLE INT CORP
Methods, devices and systems for establishing end-to-end secure connections and for securely communicating data packets
ActiveUS20140143855A1Guaranteed availabilityImprove efficiencyMultiple digital computer combinationsProgram controlEnd to end securityCommunications system
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
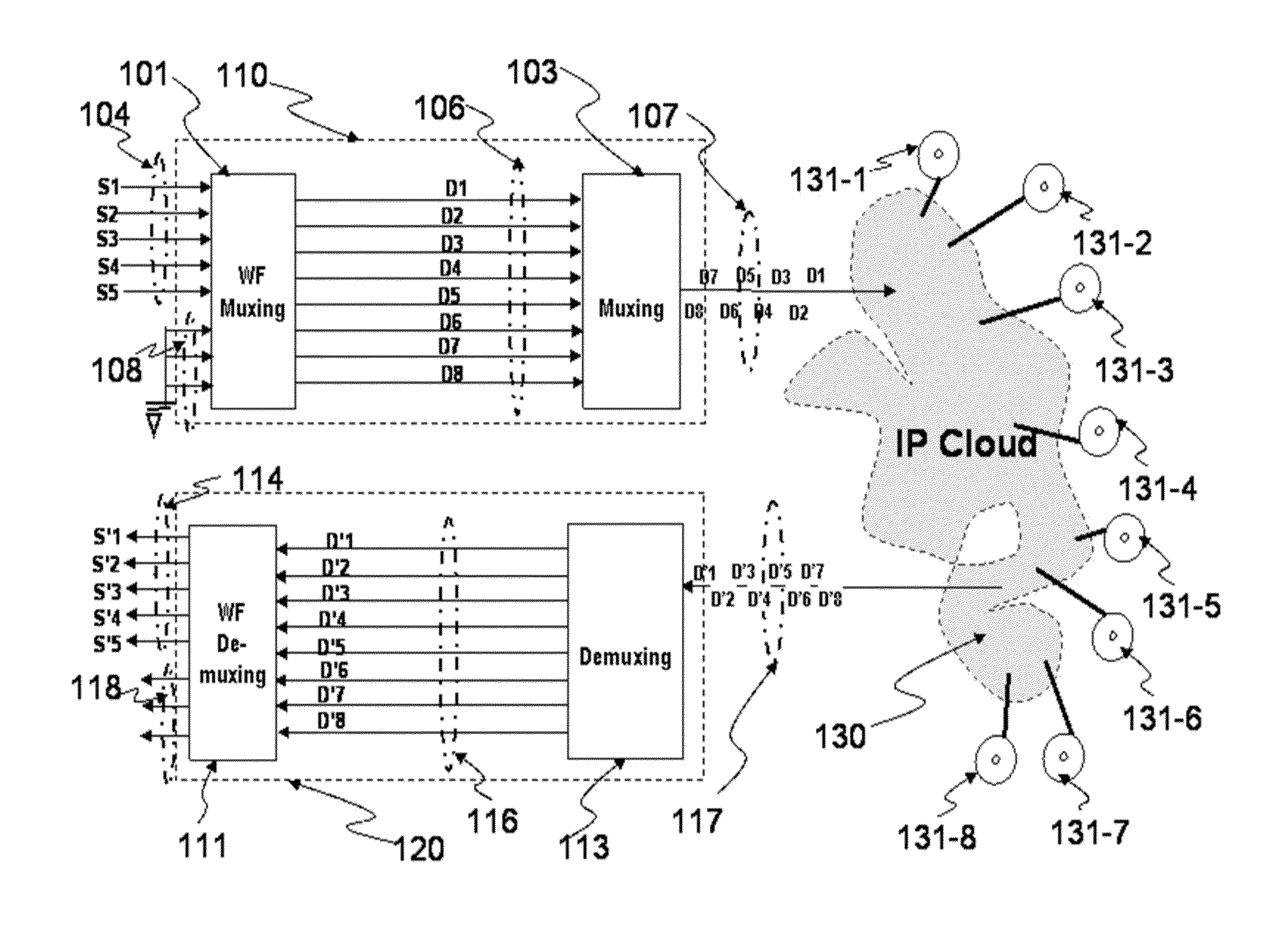
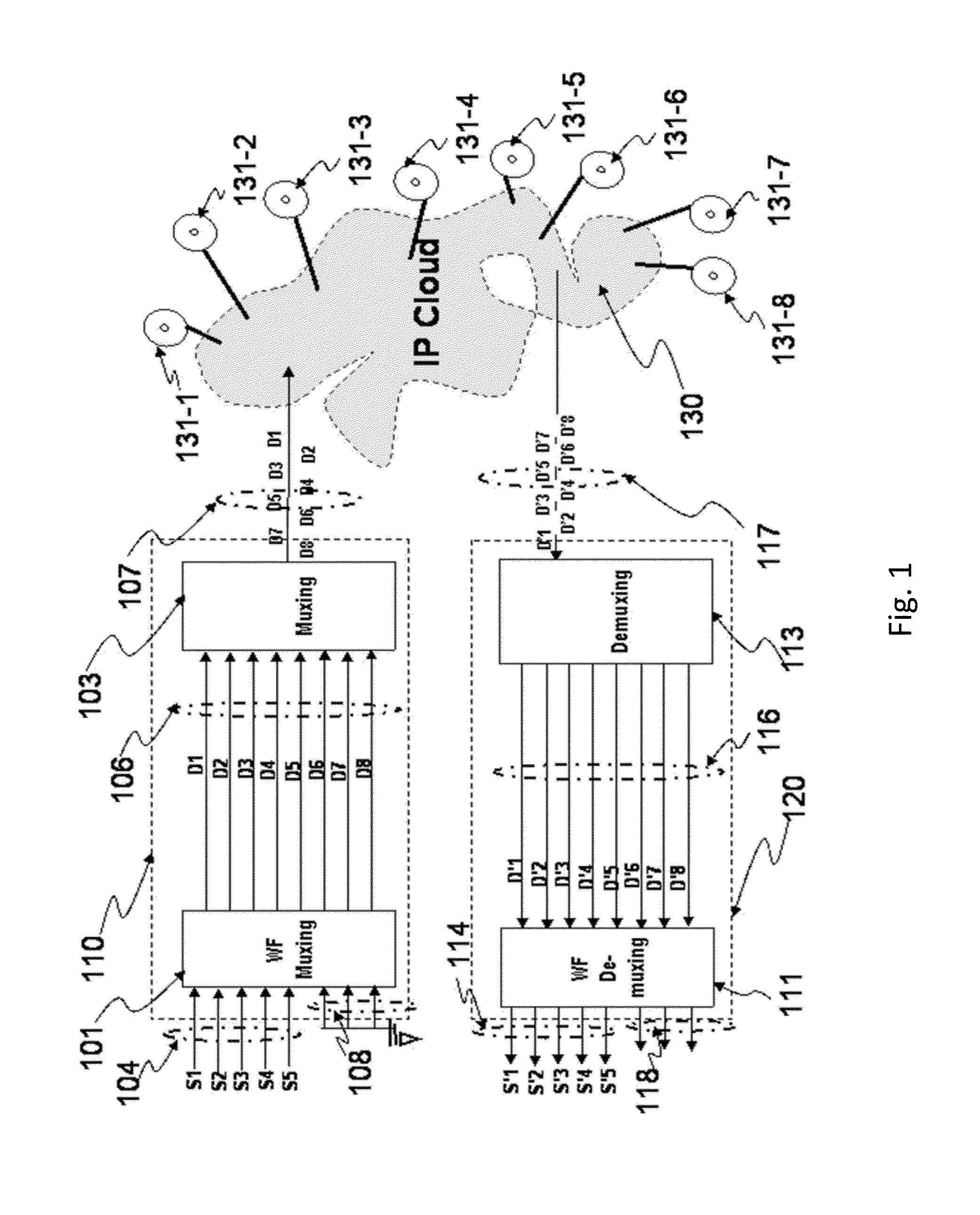
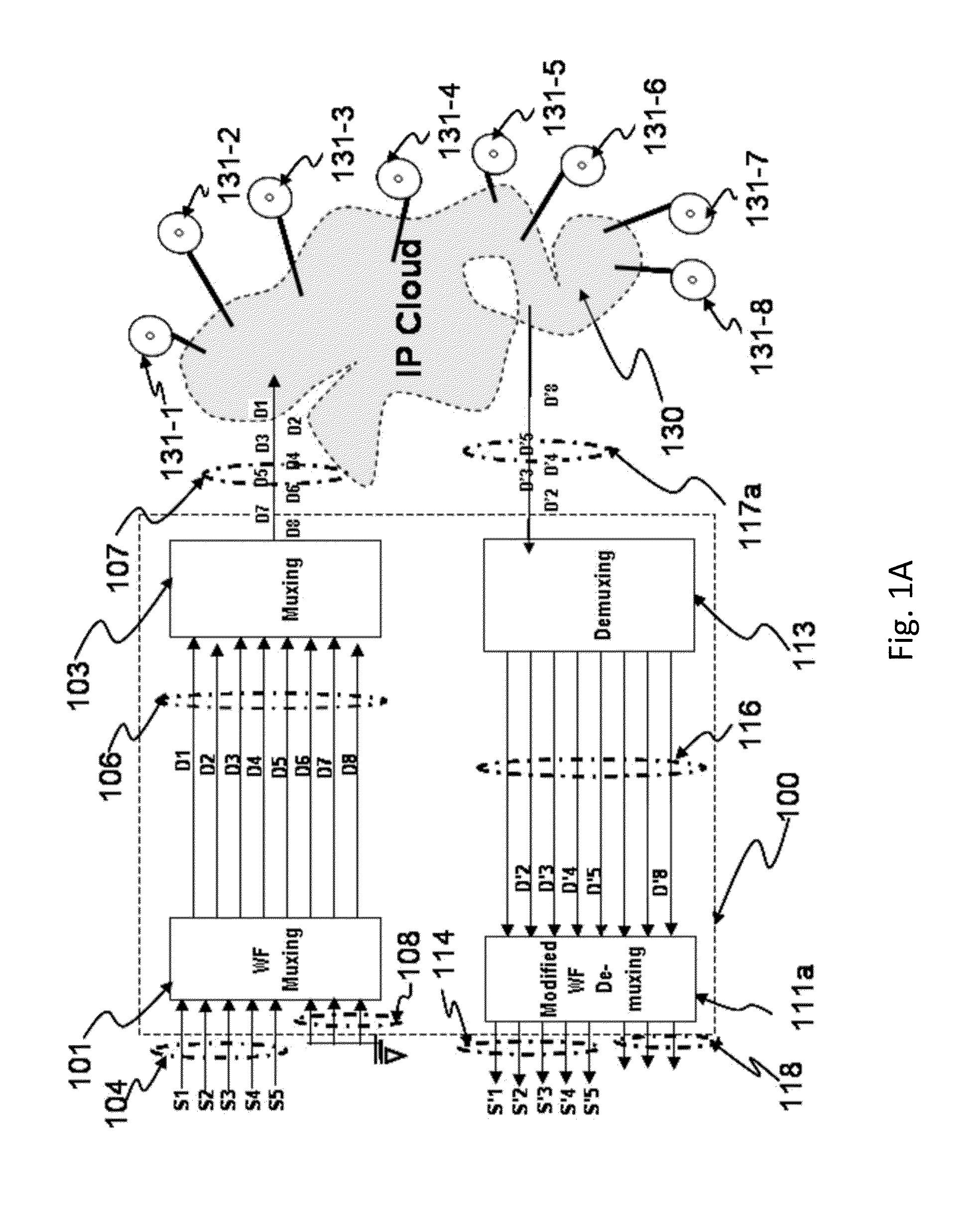
Wavefront muxing and demuxing for cloud data storage and transport
ActiveUS20140081989A1Improve privacyImprove reliabilityDigital data information retrievalDigital data processing detailsMultiplexingData set
Security on data storage and transport are important concerns on cloud computing. Wavefront multiplexing / demultiplexing process (WF muxing / demuxing) embodying an architecture that utilizes multi-dimensional waveforms has found applications in data storage and transport on cloud. Multiple data sets are preprocessed by WF muxing before stored / transported. WF muxed data is aggregated data from multiple data sets that have been “customized processed” and disassembled into any scalable number of sets of processed data, with each set being stored on a storage site. The original data is reassembled via WF demuxing after retrieving a lesser but scalable number of WF muxed data sets. In short, the WF muxed data storage solution enhances data security and data redundancy by, respectively, creating a new dimension to existing security / privacy methods and significantly reducing the storage space needed for data redundancy. In addition, WF muxing / demuxing methods enable a monitoring capability on the integrity of stored data.
Owner:SPATIAL DIGITAL SYST
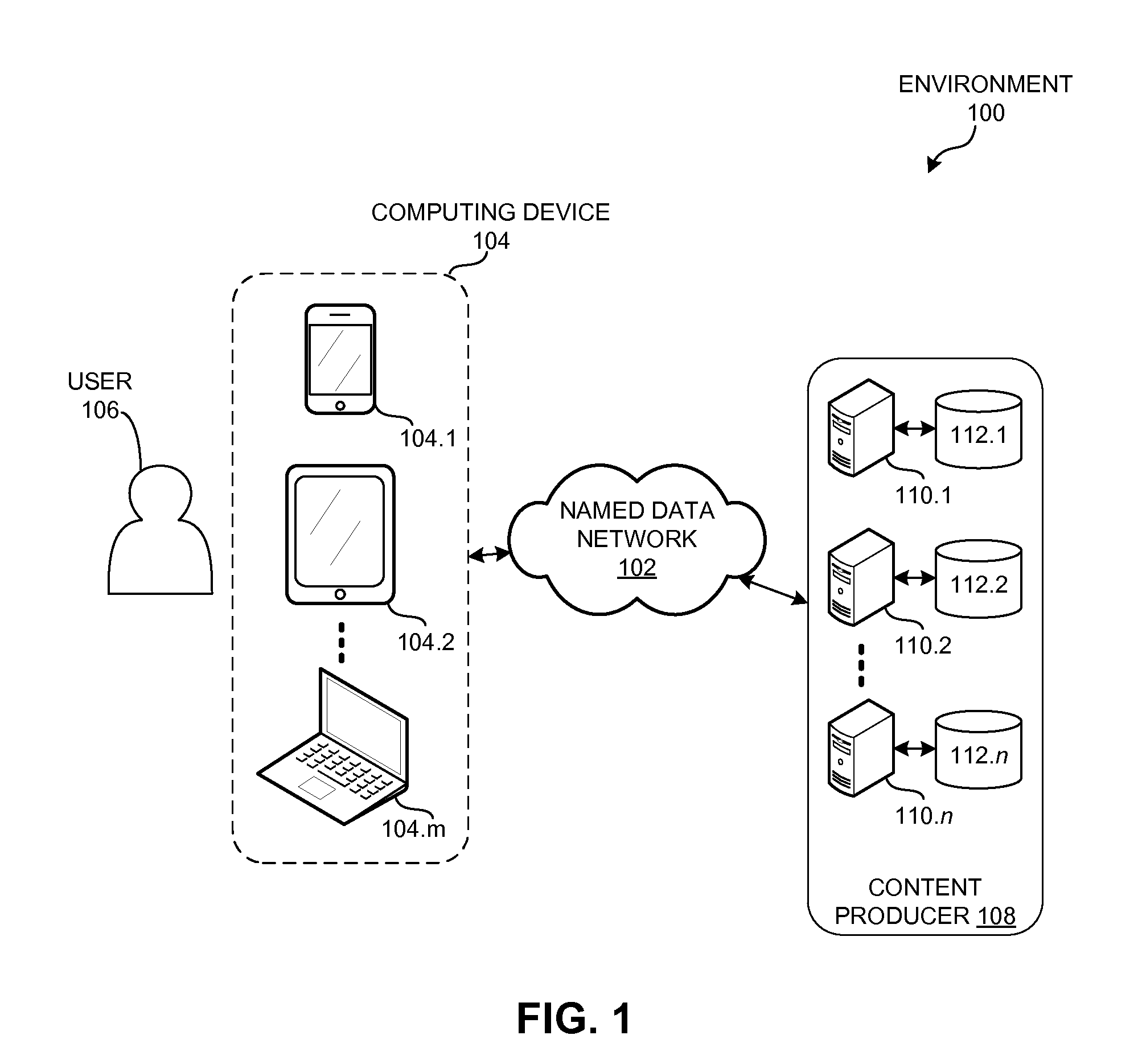
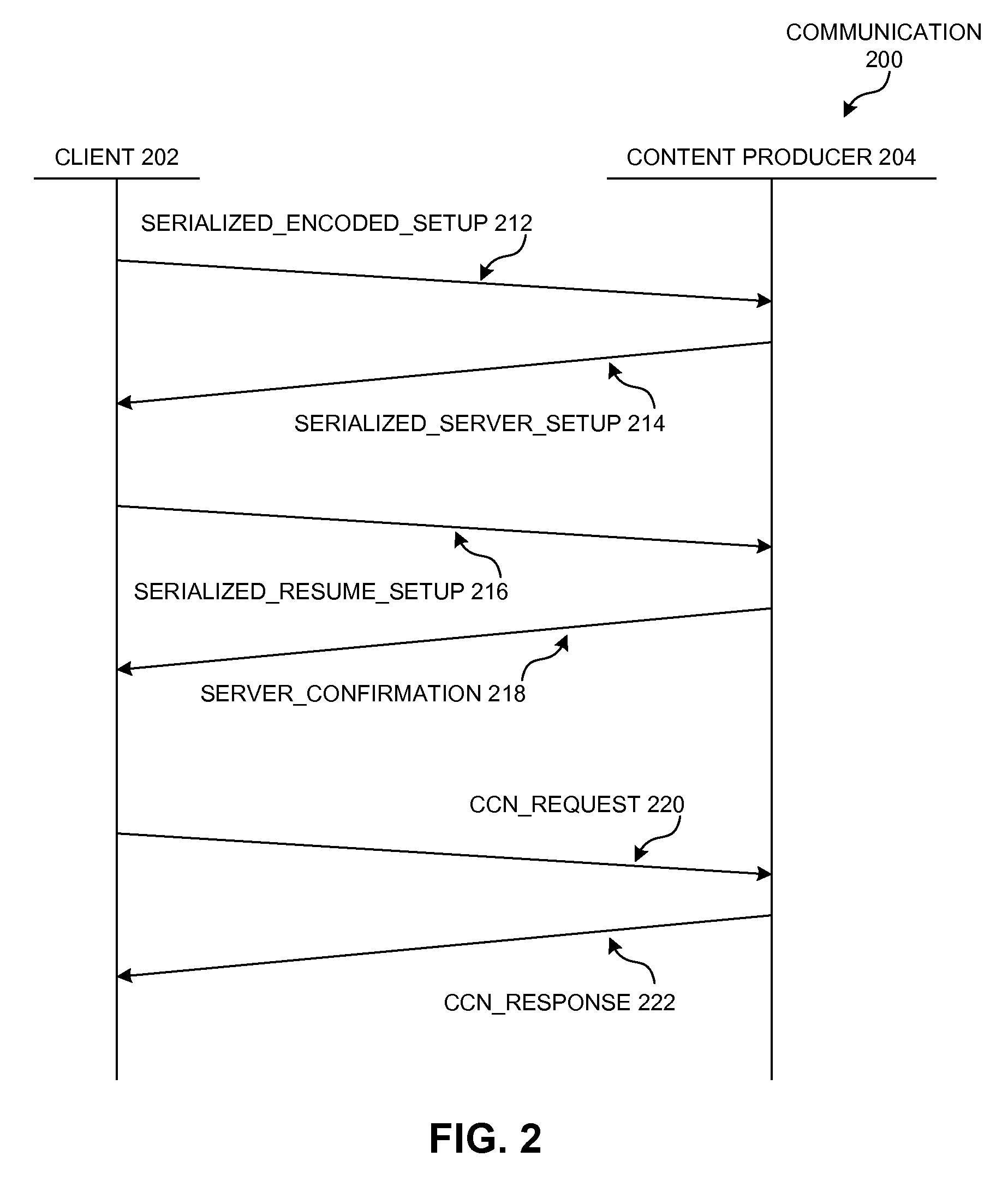
Content-based transport security
InactiveUS20150222424A1Key distribution for secure communicationPublic key for secure communicationComputerized systemRemote computer
A computer system can send a secure request over a named-data network to a remote device by generating an Interest with encrypted name components. During operation, the computer system can receive or obtain a request for data, such as from a local user or from a local application. If the system cannot satisfy the request locally, the system can determine at least a routable prefix and a name suffix associated with the request. The system can generate the secure Interest for the request by determining an encryption key that corresponds to a session with the remote computer system, and encrypts the name suffix using the session encryption key. The system then generates an Interest whose name includes the routable prefix and the encrypted name suffix, and disseminates the Interest over a named-data network to send the request to the remote computer system.
Owner:CISCO TECH INC
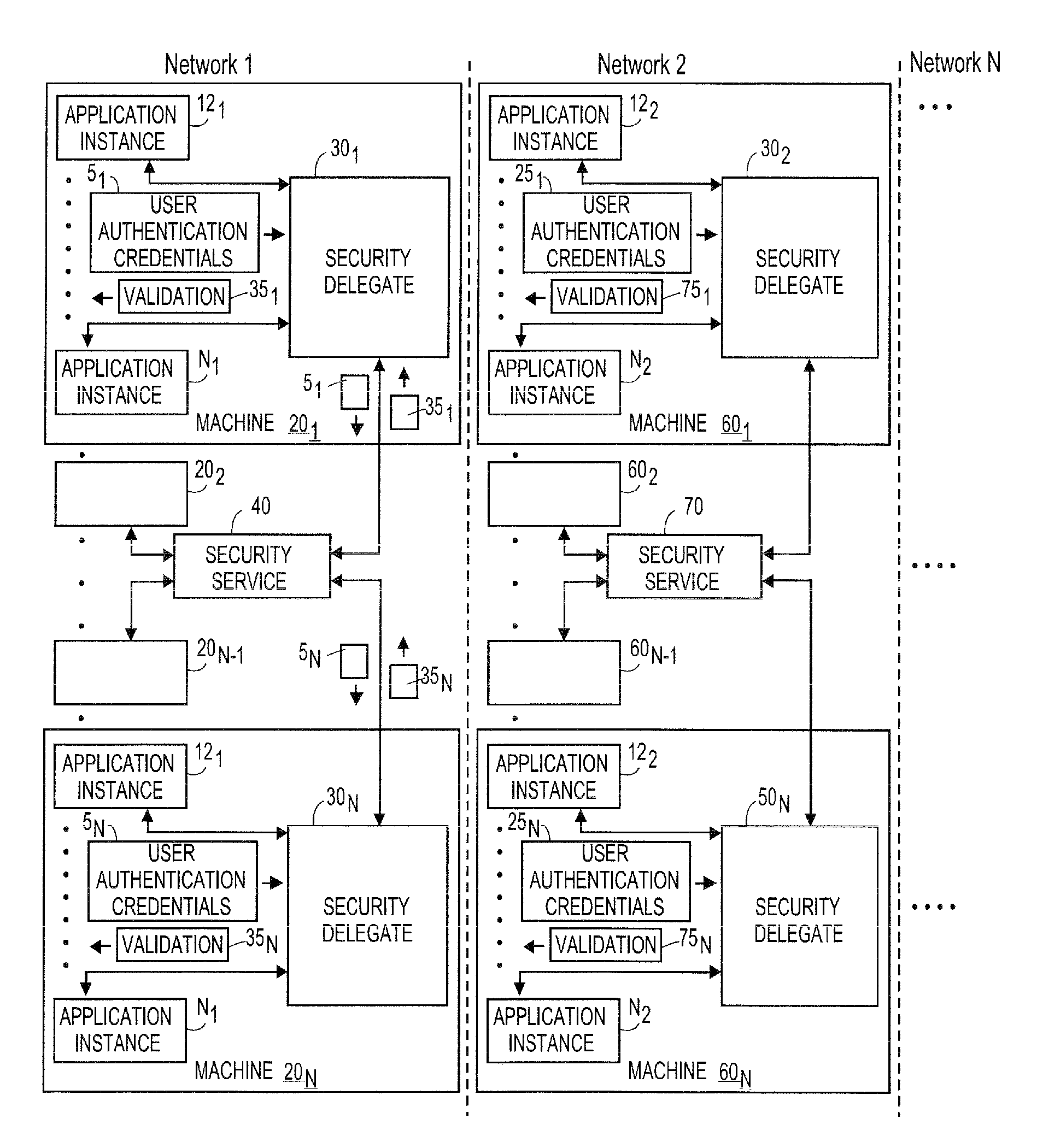
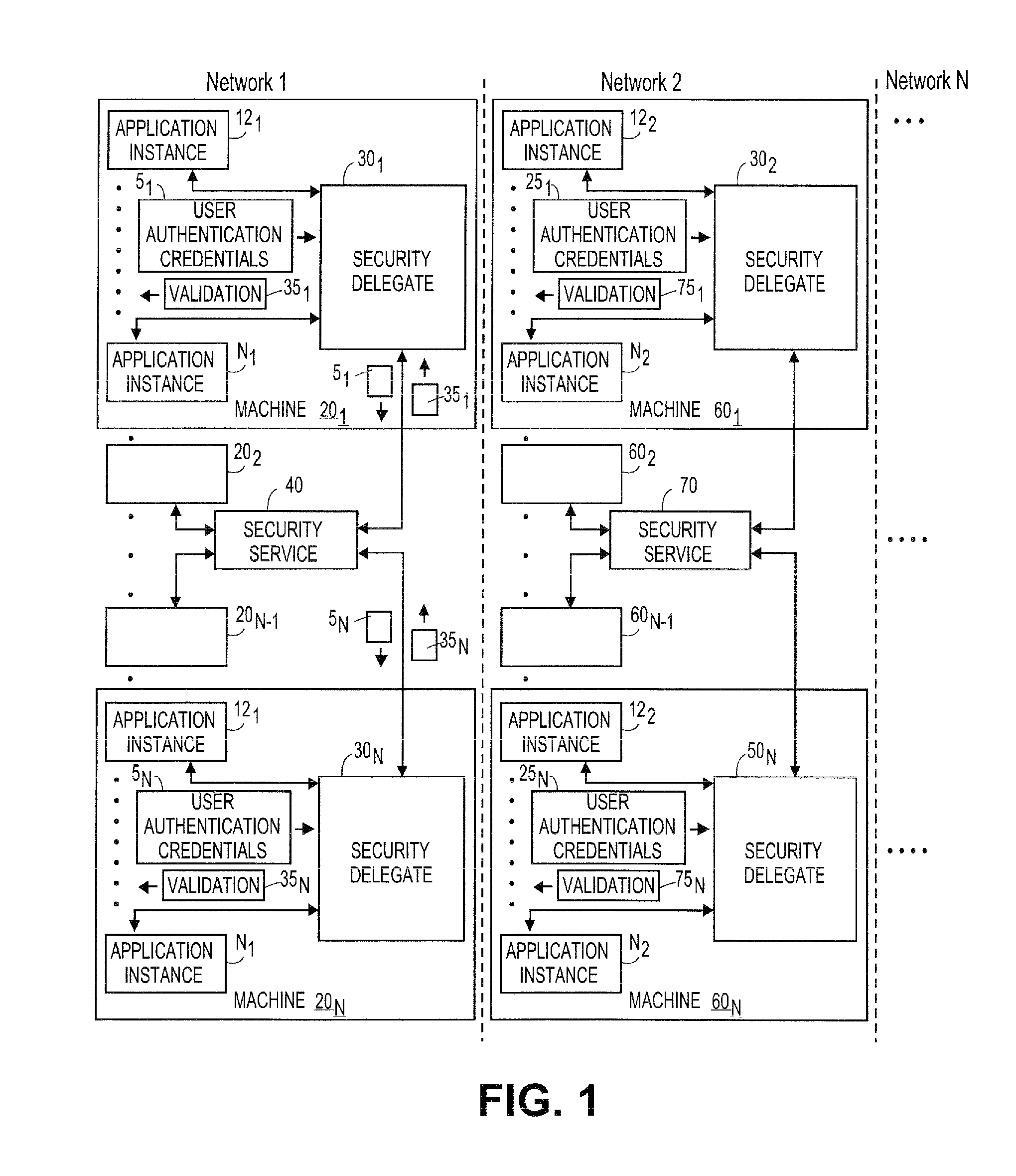
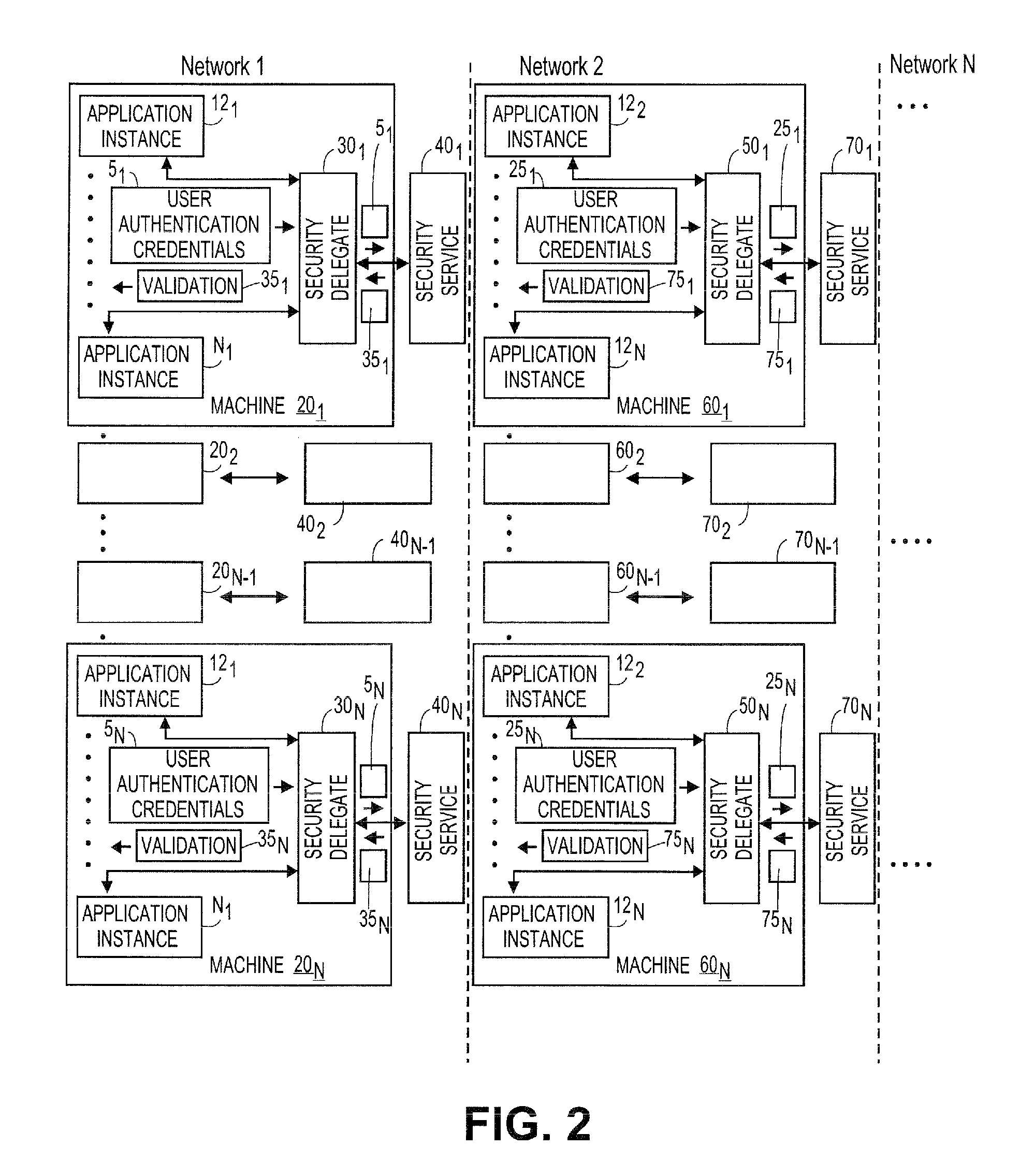
Systems and methods for generating modular security delegates for applications
ActiveUS20120240212A1Digital data processing detailsUser identity/authority verificationVirtualizationPrivate network
Embodiments of the present teachings relate to systems and methods for generating modular security delegates for application instances, including, for example, applications usable on physical machines, virtualized environments, in the cloud, etc. According to embodiments, in a multiple network environment, multiple machines (or clients) can be configured, each having a defined security level. Each machine can include a plurality of application instances and corresponding security delegates for various defined security levels. For example, the defined security levels can be based on various authentication mechanisms, including, Kerberos, NT Lan Manager (NTLM) authentication protocol, secure sockets layer / transport security layer (SSL / TSL), token authentication, virtual private network (VPN), remote access security (RAS), digest authentication, etc.
Owner:RED HAT
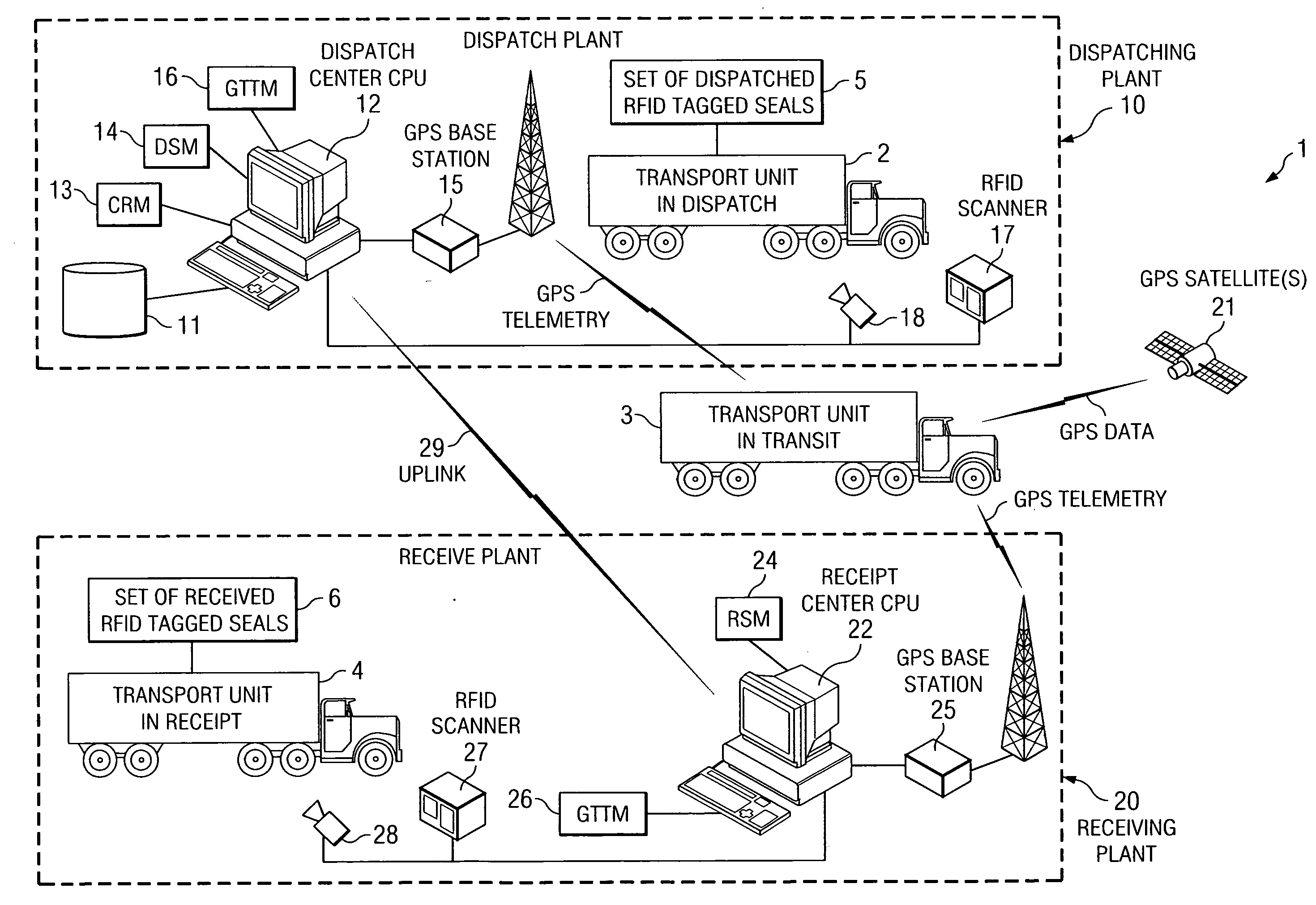
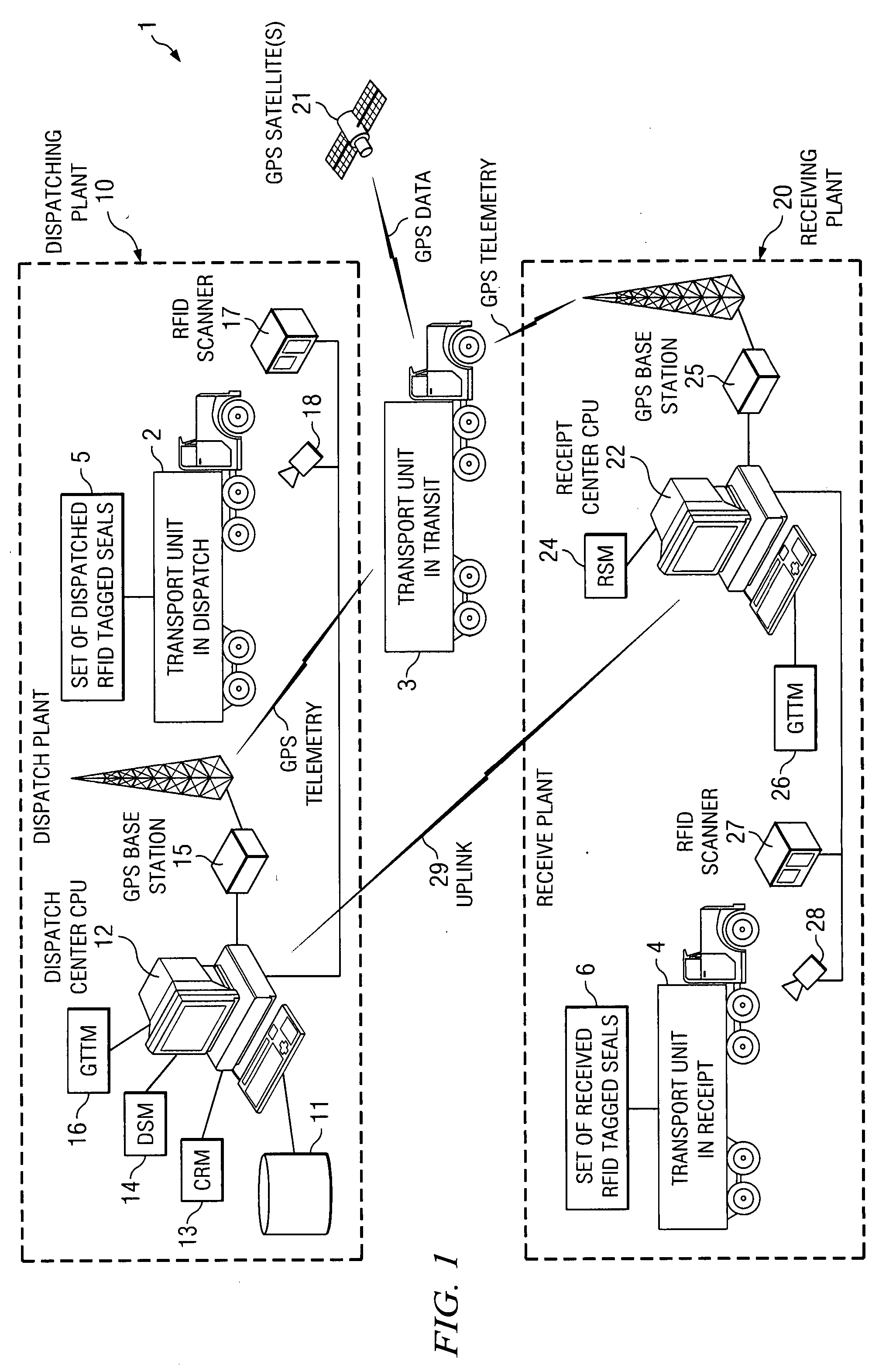
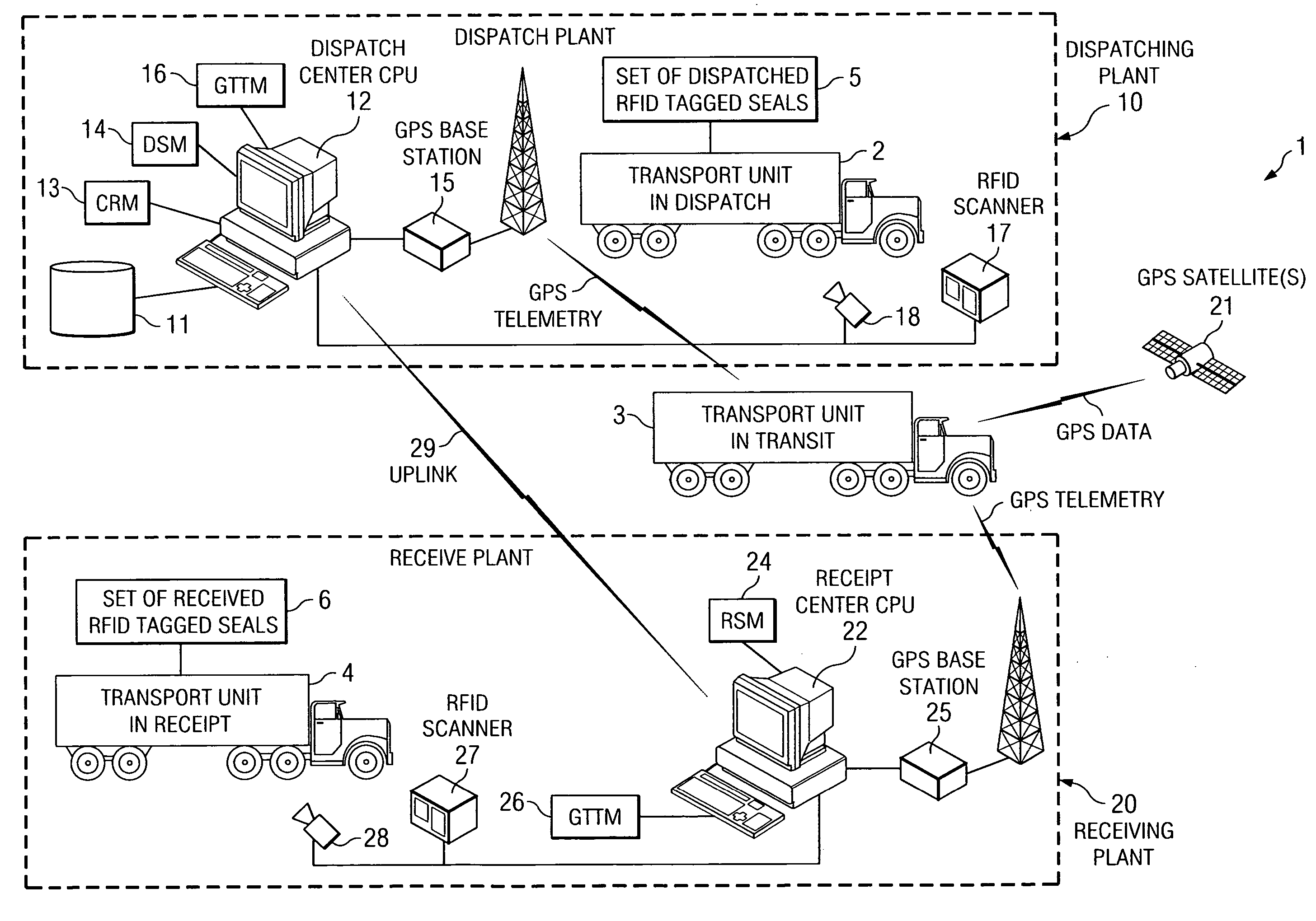
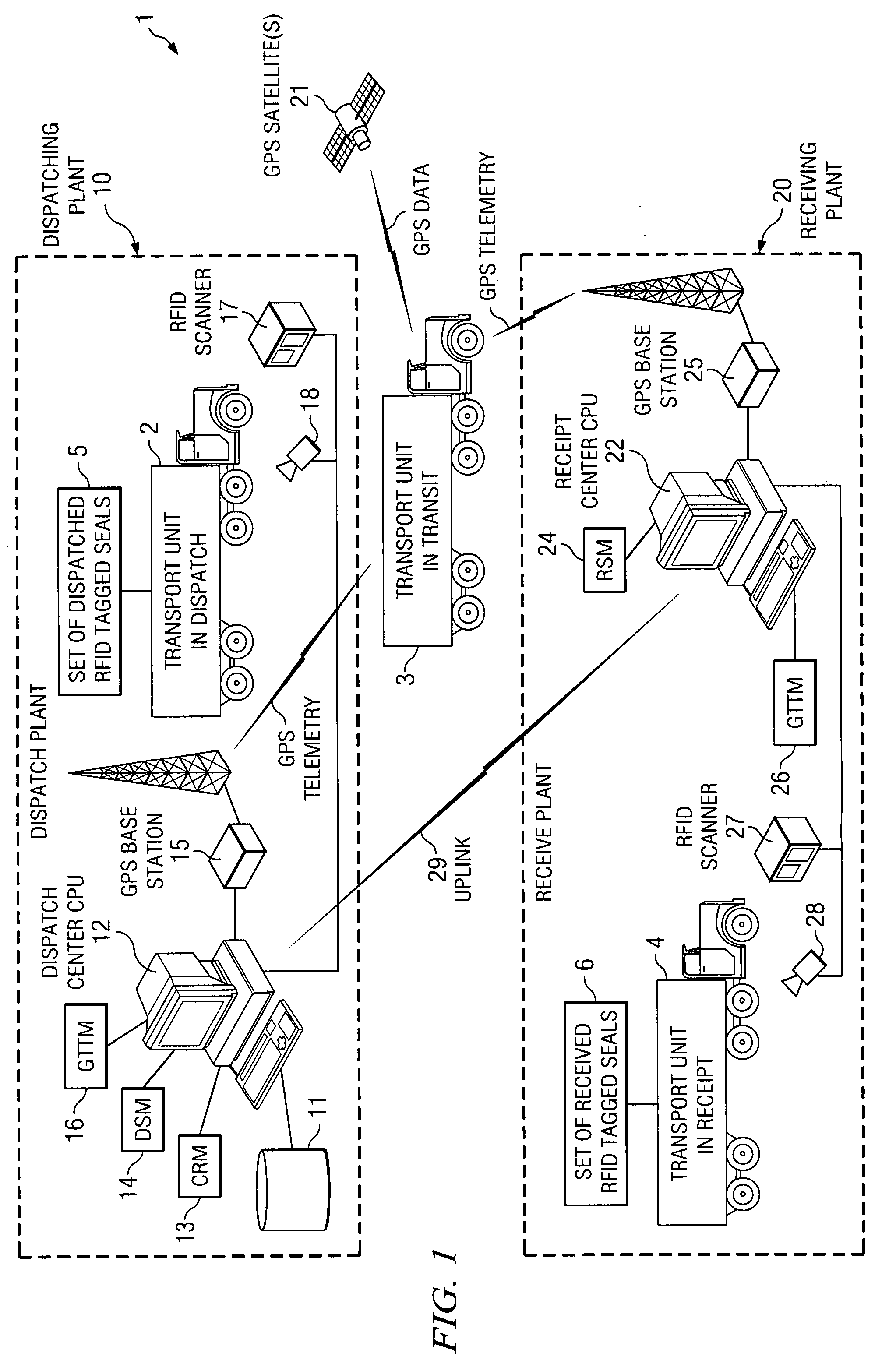
System and method for transport security control and tracking
ActiveUS20080042842A1Reduced cargo inspection timeReduce laborLogisticsBurglar alarm by hand-portable articles removalBulk cargoEngineering
The invention disclosed provides an apparatus and method to monitor and track the security of bulk cargo from a dispatch point to a receipt point. The apparatus includes a plurality of RFID antennas at a dispatch location and at a receipt location, networked software modules in communication with the RFID antennas, and disposable RFID tags used as security seals affixed to a carrier at multiple locations. The software modules include a Cargo Registration Module, a Dispatch Scanning Module, and a Receipt Scanning Module. The apparatus and method reduce cargo inspection time and labor at the points of departure and receipt. The automation of the dispatch and receipt process eliminates the human element thereby increasing the efficiency of the process. An additional embodiment includes a “single-use” disposable RFID tagged seal adapted to be attached to a transport portal unable to be removed without damaging an RFID transmitter contained within.
Owner:SURELOCK SEALS
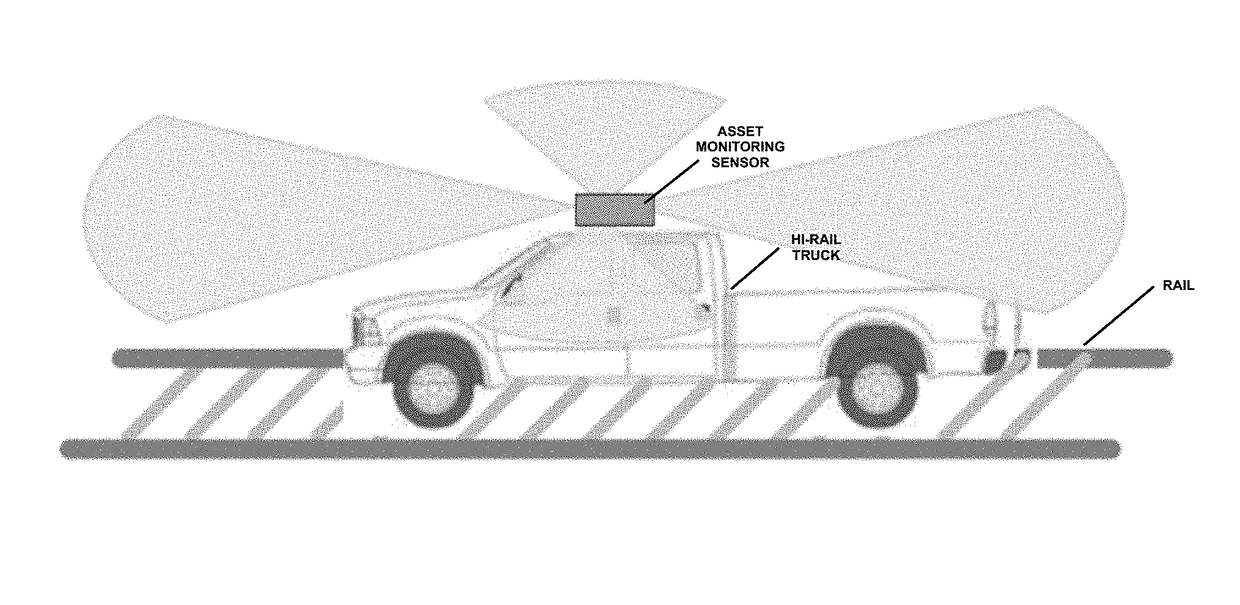
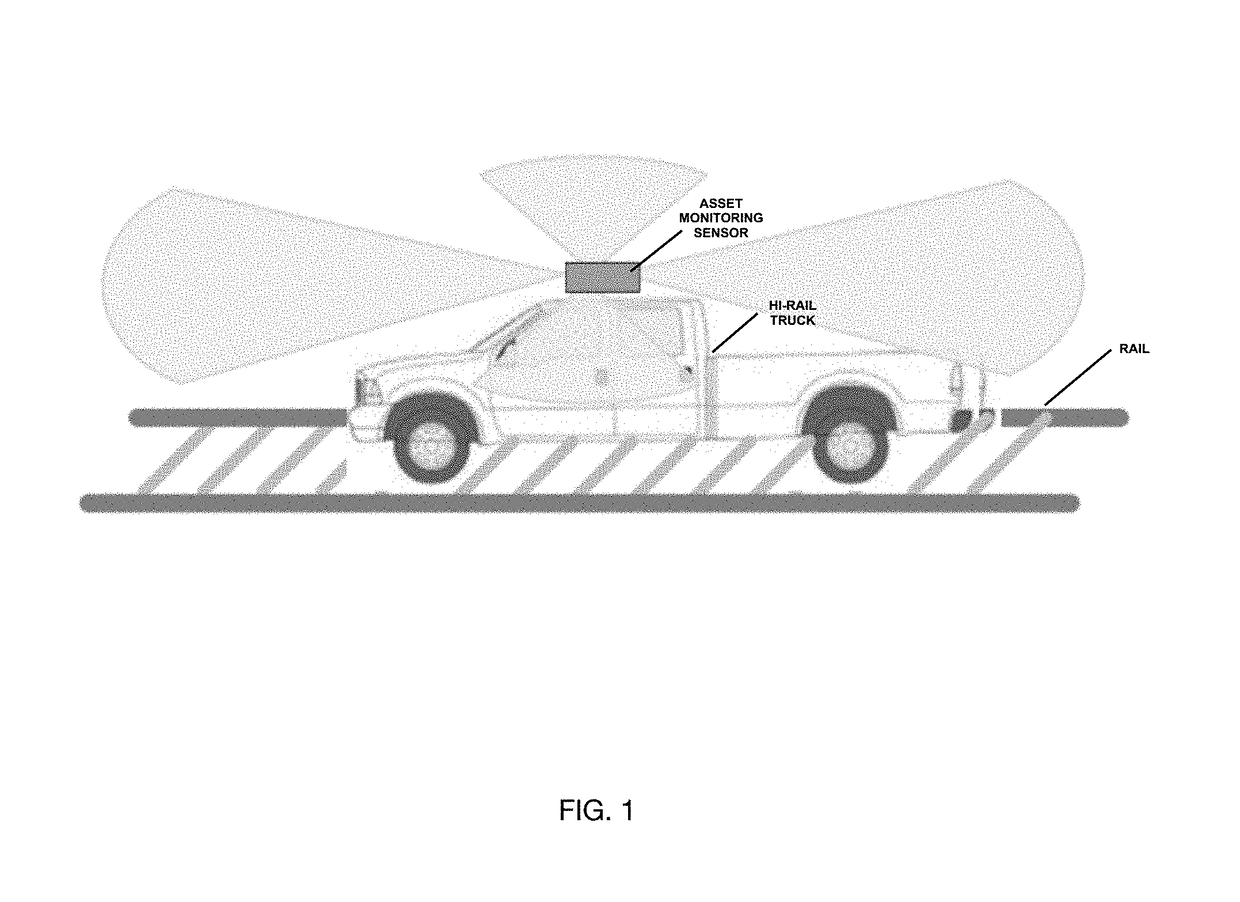
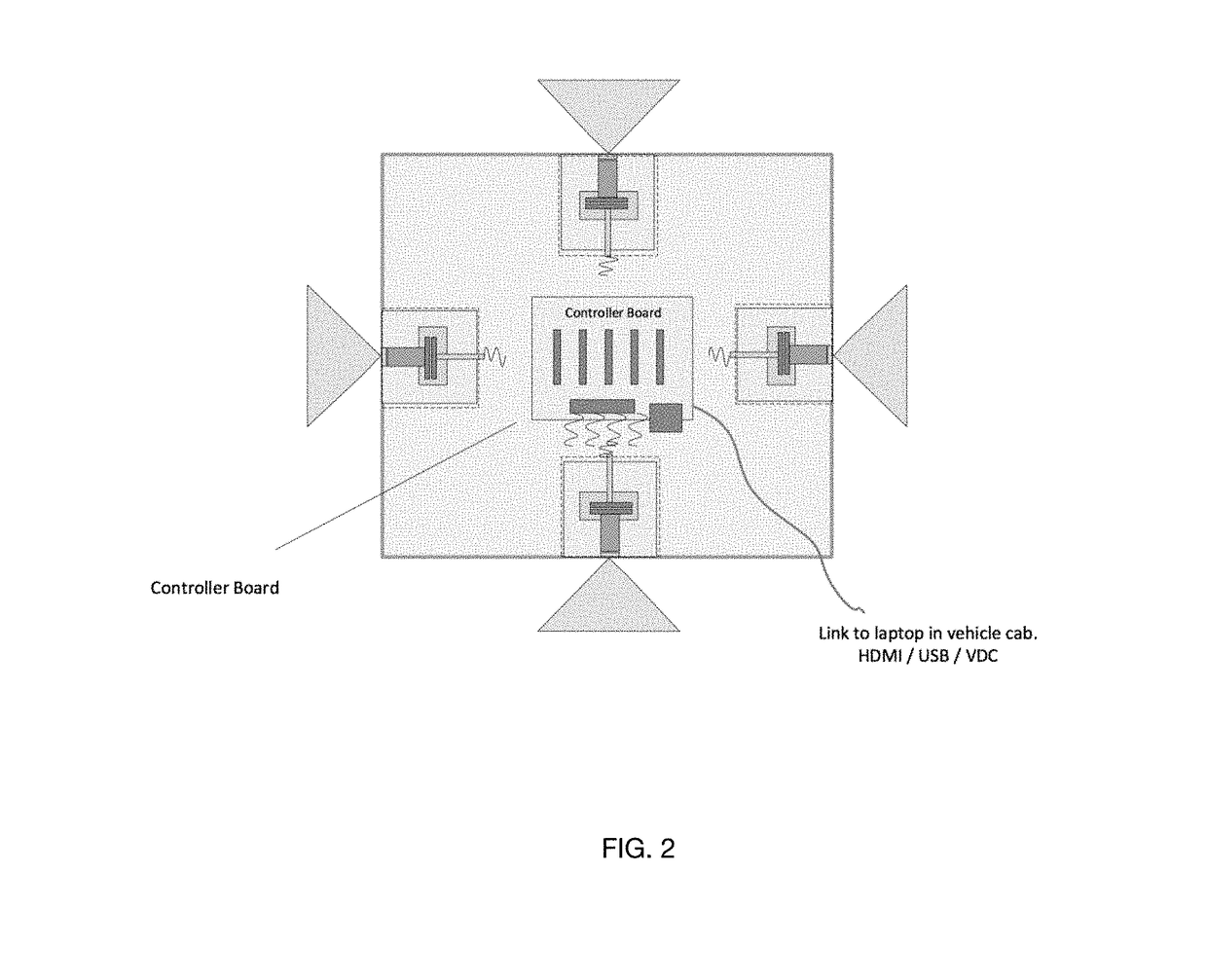
Automated wayside asset monitoring with optical imaging and visualization
ActiveUS20180127006A1Enhanced Situational AwarenessImprove eyesightTrack side maintainanceCharacter and pattern recognitionImage databaseTransport security
The Automated Wayside Asset Monitoring system utilizes a camera-based optical imaging device and an image database to provide intelligence, surveillance and reconnaissance of environmental geographical information pertaining to railway transportation. Various components of the Automated Wayside Asset Monitoring system can provide features and functions that can facilitate the operation and improve the safety of transportation via a railway vehicle.
Owner:WADE JACK
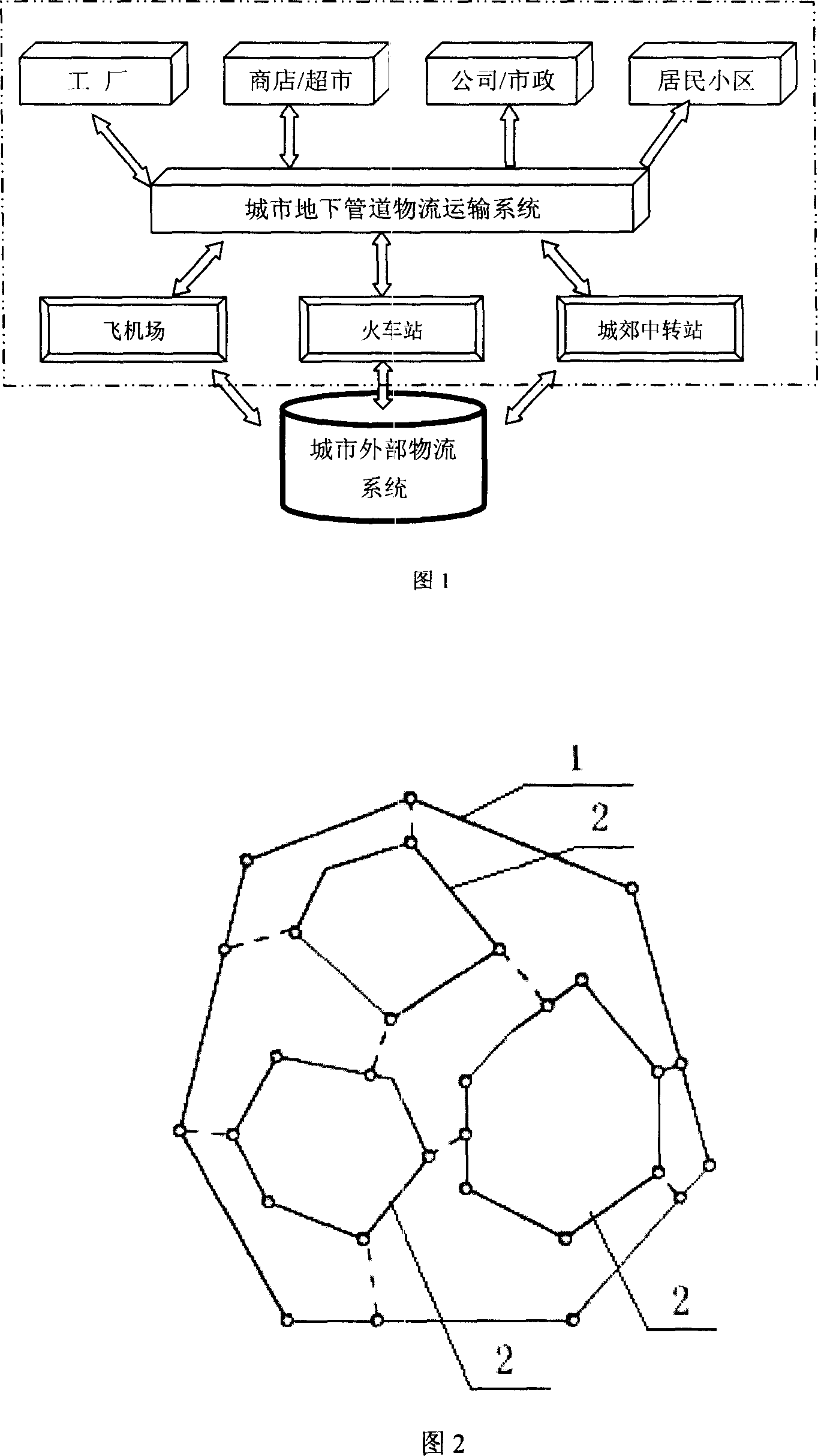
Urban underground looped pipeline network logistics transportation system
InactiveCN1978262AHarm reductionReduce pollutionRailway componentsRailway stationLogistics managementDistribution Volume
This invention relates to an underground ring-like pipeline network distribution transportation system in a city, which includes a transportation system with a safe and protection control mode including multiple ring-like networks connected by a transfer station, in which, the ring-like networks are divided into a first grade, a second grade or a third grade according to the distribution volume and sizes of the covering regions, multiple second grade ring-like networks in different covering regions and distribution volumes are connected with the first grade networks circling the whole city by the transfer station to make up of a basic network of the underground distribution system, and the transfer station is taken as the interface interacting with the ground and conveyances realize goods transportation among different loops.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
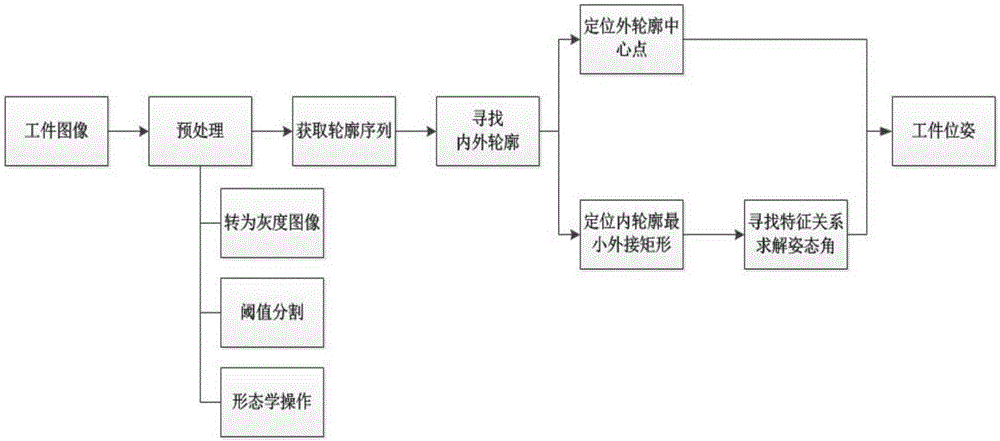
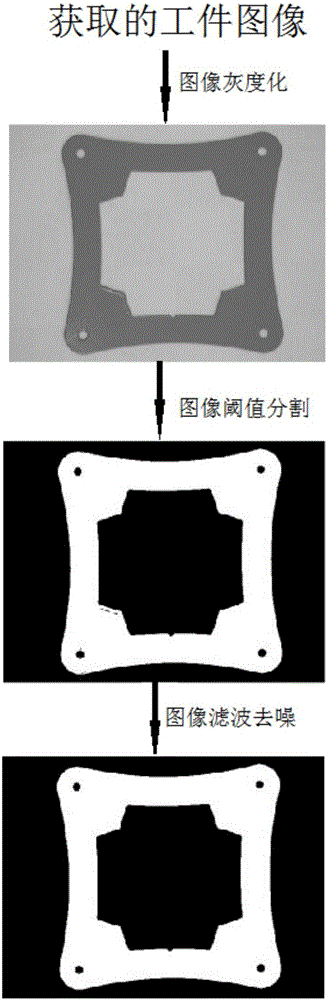
Quick pose detection method based on geometric features of inside and outside contours of workpiece
InactiveCN106846404AMeet real-time requirementsImprove detection accuracyImage enhancementImage analysisComputer scienceClosed state
The invention discloses a quick pose detection method based on geometric features of inside and outside contours of a workpiece. The method comprises the following steps of (1) obtaining a workpiece image; (2) performing preprocessing operation on the obtained workpiece image; (3) performing geometric feature acquisition on the preprocessed workpiece image; and (4) performing pose identification according to the obtained geometric features. According to the method, a compartment in a closed state during transport is transformed to be in a position state that drawers in a box body are all outward through rotation, so that cargos can be conveniently taken under the condition of ensuring cargo transport safety. Compared with the prior art, the method has the advantages that the detection precision is relatively high, relatively little time is consumed, timeliness requirements of automated production can be met, the detection speed and the detection precision are better considered, and very good robustness in a practical application environment is achieved.
Owner:HOHAI UNIV CHANGZHOU
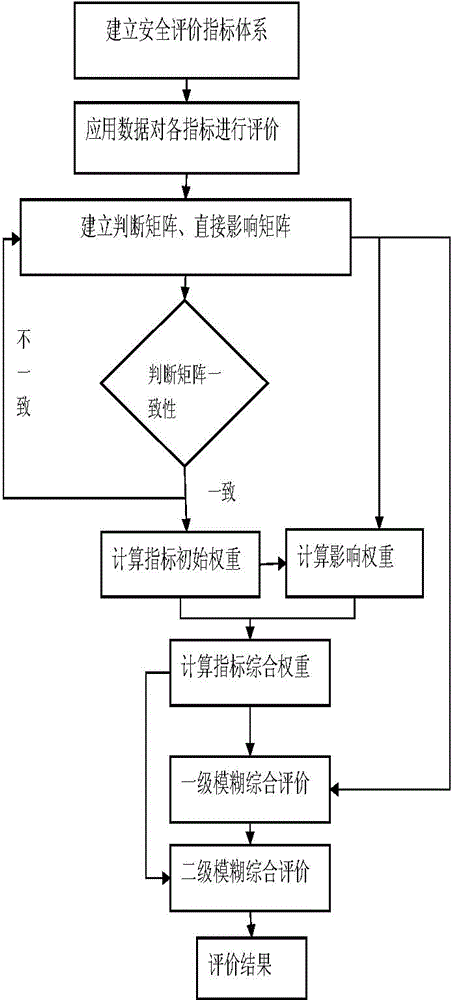
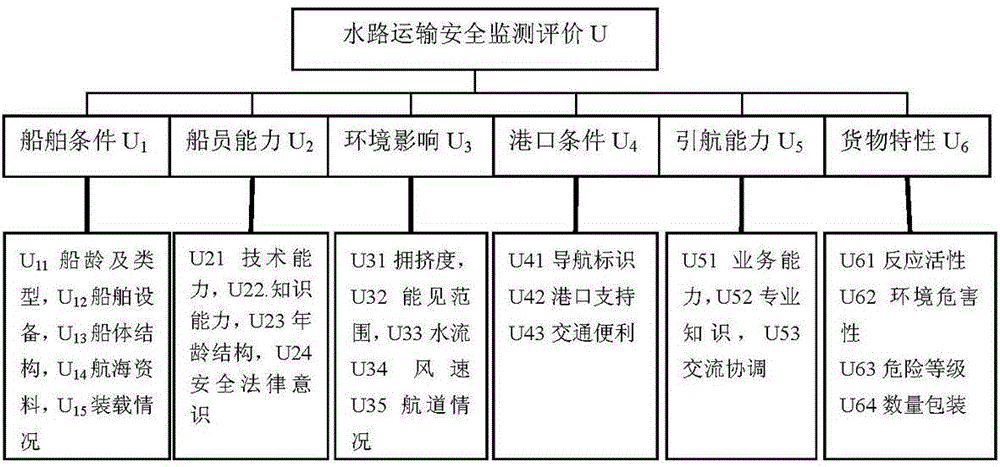
Method for monitoring and evaluating waterway transport security
InactiveCN104680037ARealize monitoring and evaluationEliminate risk factorsSpecial data processing applicationsSensing dataSocial benefits
The invention relates to a method for monitoring and evaluating waterway transport security, which is used for effectively solving the problem for monitoring and evaluating the waterway transport security. The method comprises the following steps: establishing a waterway transport security monitoring and evaluating index system; evaluating various evaluation indexes of waterway transport security in combination with ground port navigation monitoring data, remote sensing data of ship cargos and meteorological data; calculating the initial weights of the evaluation indexes by using an analytic hierarchy process; correcting the initial weights, calculating influence weights, correcting the initial weights by using a DEMATEL method, and establishing a direct influence matrix; obtaining the comprehensive weights of the indexes by using a weighted averaging summation method; and comprehensively evaluating the waterway transport security state and grade in combination with the fuzzy theory, establishing an early warning mechanism and an emergency mechanism according to the evaluation result, carrying out comprehensive evaluation based on the fuzzy theory, analyzing the transport security level, and determining the security sate and grade to monitor and evaluate the waterway transport security. The method provided by the invention is used for monitoring and evaluating the waterway transport security within a large range quickly, comprehensively and objectively, so that the economic and social benefits are huge.
Owner:NORTH CHINA UNIV OF WATER RESOURCES & ELECTRIC POWER
Engine material rest
ActiveCN101723149ALabor-saving operationGuaranteed reliabilityPackaging vehiclesContainers for machinesEngineeringBriquette
The invention discloses an engine material rest. The engine material rest comprises an material rest body, wherein at least one engine placing station is arranged on the material rest body; a place of the station, corresponding to the positioning part of the engine, is provided with three fixed positioning parts and plurality of adjustable positioning parts; the three fixed positioning parts comprises two fixed supporting frame and one fixed positioning support pin; the adjustable positioning parts contain at least one movable briquette positioning frame; and each movable briquette positioning frame is provided with a movable briquette. The invention can be used to hold multiple engines in different types and standards, completely fix the engine and ensure safe transportation; in addition, different numbers of material rests can be piled up according to the requirements of the site and the transport vehicle, thus increasing the efficiency of transportation. The operation is simple and flexible, thus reducing the labor intensity of the staff.
Owner:上海众德金属制品启东有限公司 +1
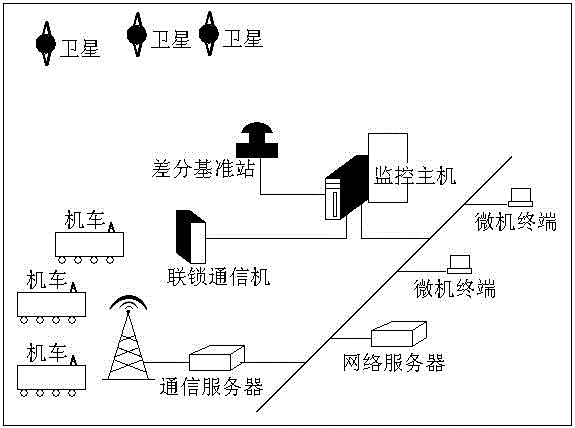
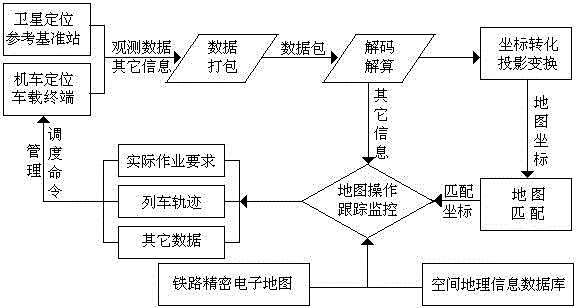
Railroad locomotive accurate positioning system
ActiveCN104880725AImproving transportation safety supervision capabilitiesEnsure transportation safetySatellite radio beaconingRailway signalling and safetyEngineeringPositioning system
The invention discloses a railroad locomotive accurate positioning system including a ground monitoring center host, a ground network system server, a ground communication server, a ground satellite difference reference station, a ground wired communication network, a vehicle-ground wireless communication network, a locomotive position positioning device, a ground microcomputer management terminal, a railway yard microcomputer interlocking data communication device, and an accurate railway track electronic map. The track electronic map is arranged in the ground network system server and the microcomputer management terminal to reproduce the track circuit state and the locomotive operation position in real time, and the ground monitoring center host acquires the satellite data, yard microcomputer interlocking data, and locomotive position data, and outputs the result obtained through the comprehensive solution of the data to the ground network microcomputer management terminals. Compared with the prior art, the railroad locomotive accurate positioning system realizes the locomotive remote management and accurate control, realizes the railway transportation safety supervision, optimizes the transportation efficiency, improves the travelling safety, and has the popularization and application values.
Owner:成都可益轨道技术有限公司
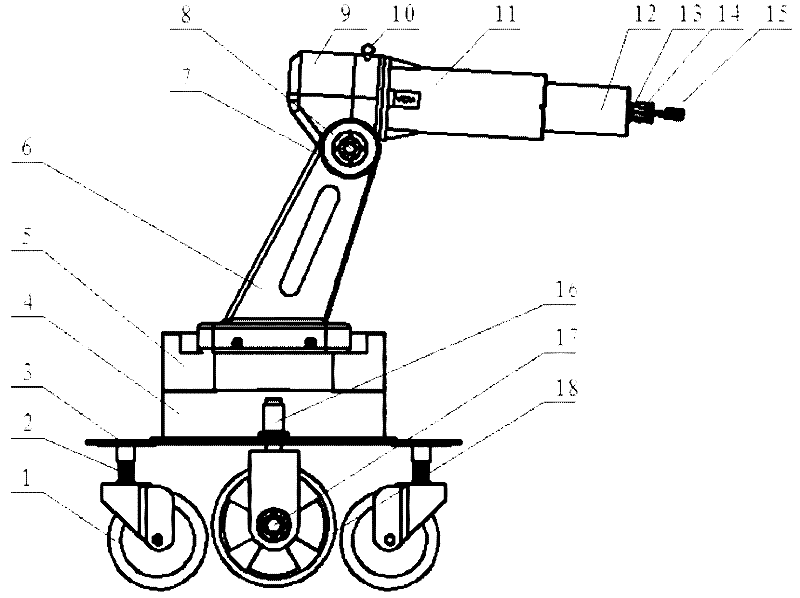
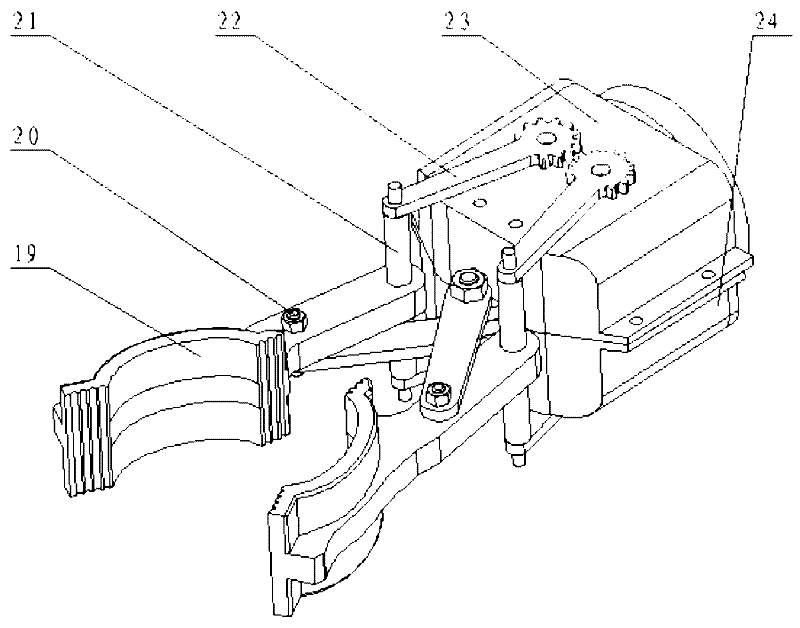
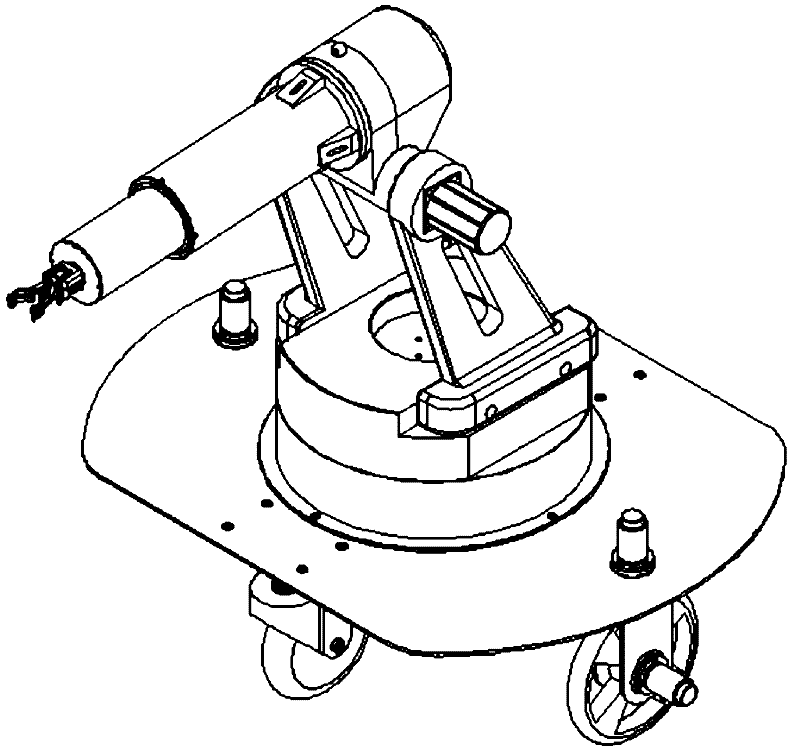
Transport security robot based on omnidirectional moving platform
InactiveCN102380866AFlexible storage and transportationFlexible monitoringManipulatorDrive wheelEngineering
The invention aims to provide a transport security robot based on an omnidirectional moving platform. Driving wheels and driven wheels are mounted below a base plate, a first drive motor is mounted on each driving wheel, a fixed base is mounted on the base plate, an arm base is mounted on the fixed base, a first speed reducing motor is mounted in the fixed base and connected with the arm base, a big arm plate is mounted on the arm base and connected with a forearm shell through a shoulder rotating shaft and a shoulder rear cover, a shoulder joint speed reducing motor is mounted at the position of the shoulder rotating shaft, a second speed reducing motor is mounted in the shoulder rear cover and connected with the forearm shell, a linear motor is mounted in the forearm shell and connected with a telescopic forearm, a paw is connected with the telescopic forearm through a paw base, and a miniature camera is mounted on the shoulder rear cover. The transport security robot provided with the moving platform capable of moving omnidirectionally adapts to complex situations of storage space, narrow working space, complex ground conditions and the like effectively, and can be used for cargo storage and transport flexibly.
Owner:HARBIN ENG UNIV
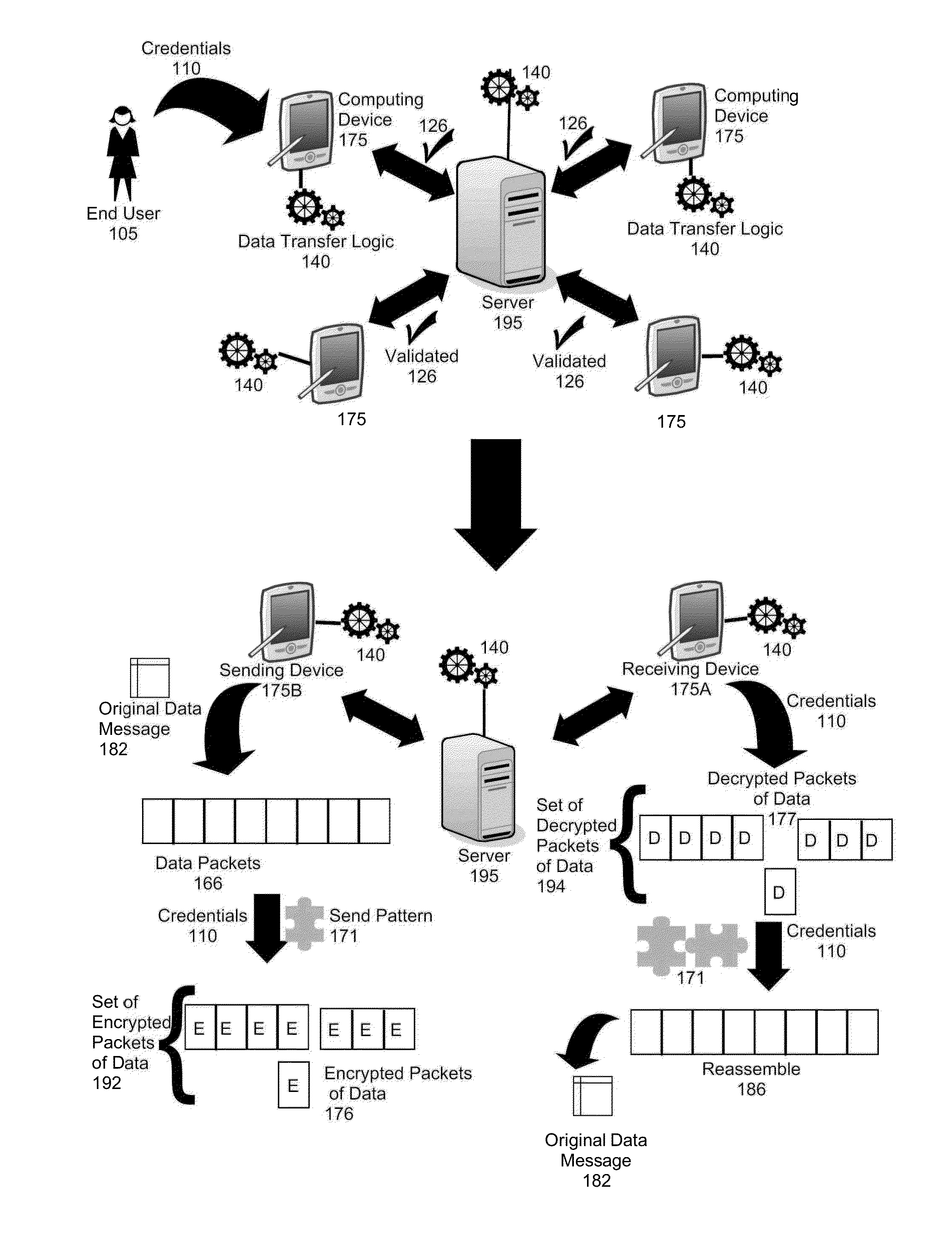
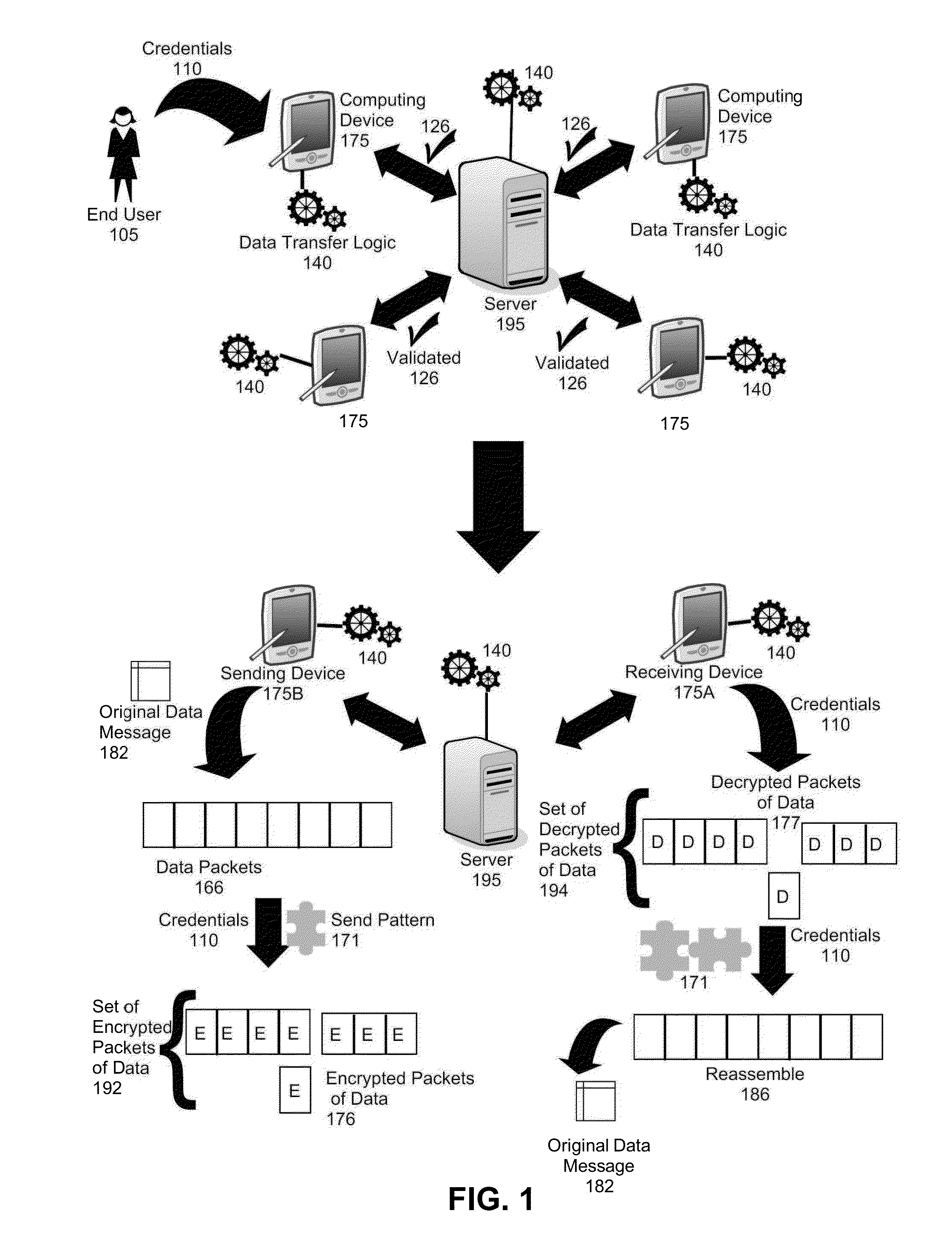
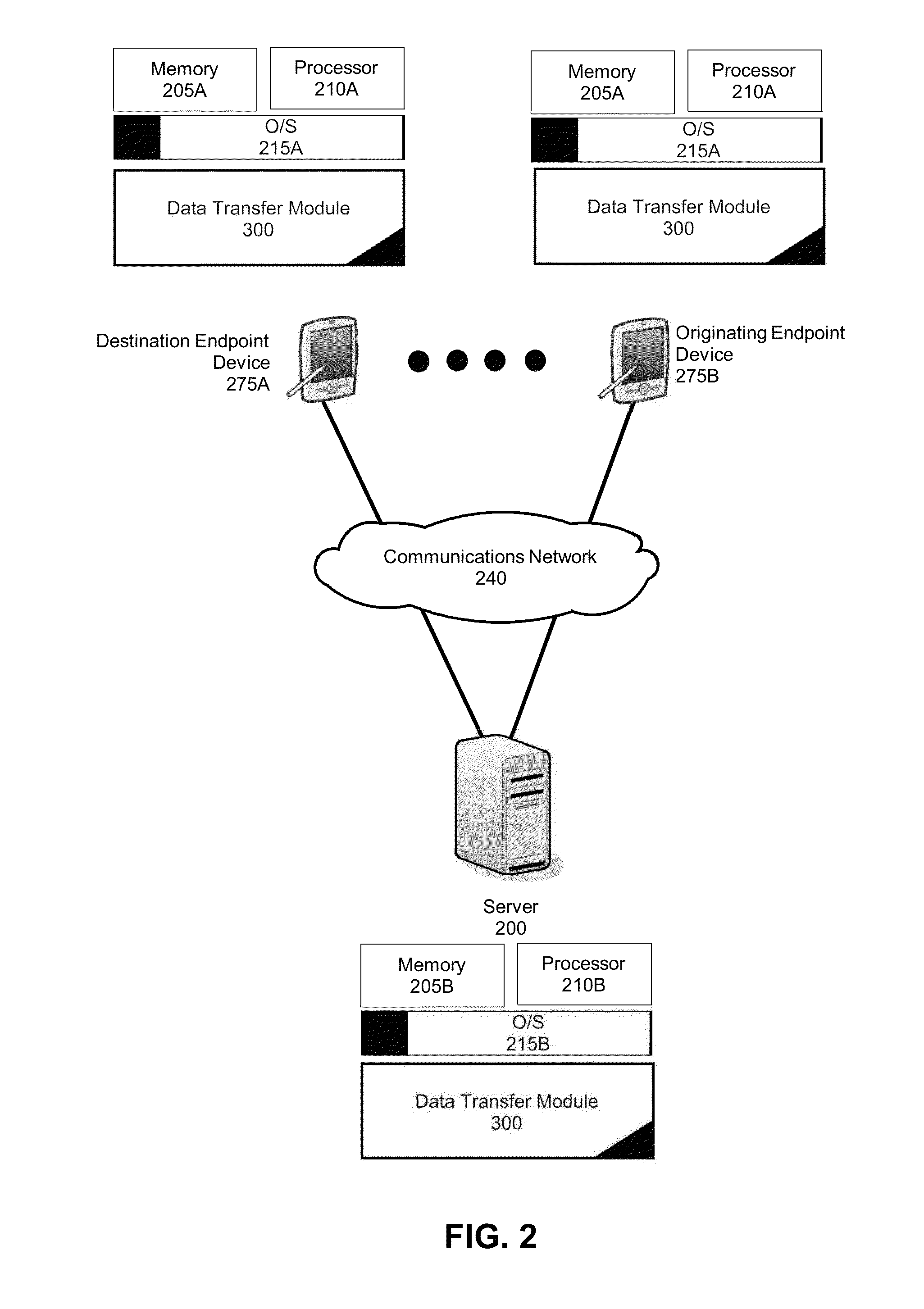
Secure data transfer over an arbitrary public or private transport
InactiveUS20130283363A1Digital data processing detailsMultiple digital computer combinationsNetwork packetComputer program
A method, system, and computer program product for transferring data between endpoint devices is provided. The method includes determining a send pattern utilizing account credentials of a user. The send pattern defines a plurality of offset and length pairs. The method further includes creating packets of data according to the send pattern. Each packet of data contains randomly assigned data of different sizes. The method also includes encrypting each packet of data to produce a set of encrypted packets of data and sending the set of encrypted packets of data to a destination endpoint device in an order determined according to the account credentials.
Owner:NXGEN SOFTWARE
Railway signal system electricity maintaining and monitoring method based on computer control
This invention relates to a railway signal system maintenance and monitor method based on computer control, which belongs to railway transmission signal system automatic monitoring and electric maintenance technique field and is characterized by the following: the indoor main control computer controls the outdoor spot device through railway communication circuit to realize the outdoor device monitor and alarm; it standardize the spot maintenance person operations and avoids the car accident caused by peccancy operations of the maintenance persons.
Owner:张守利
Vibration reducing tray with spring device
InactiveCN104029894AAddress transportation security issuesSimple structureContainers to prevent mechanical damageRigid containersEngineeringMechanical engineering
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
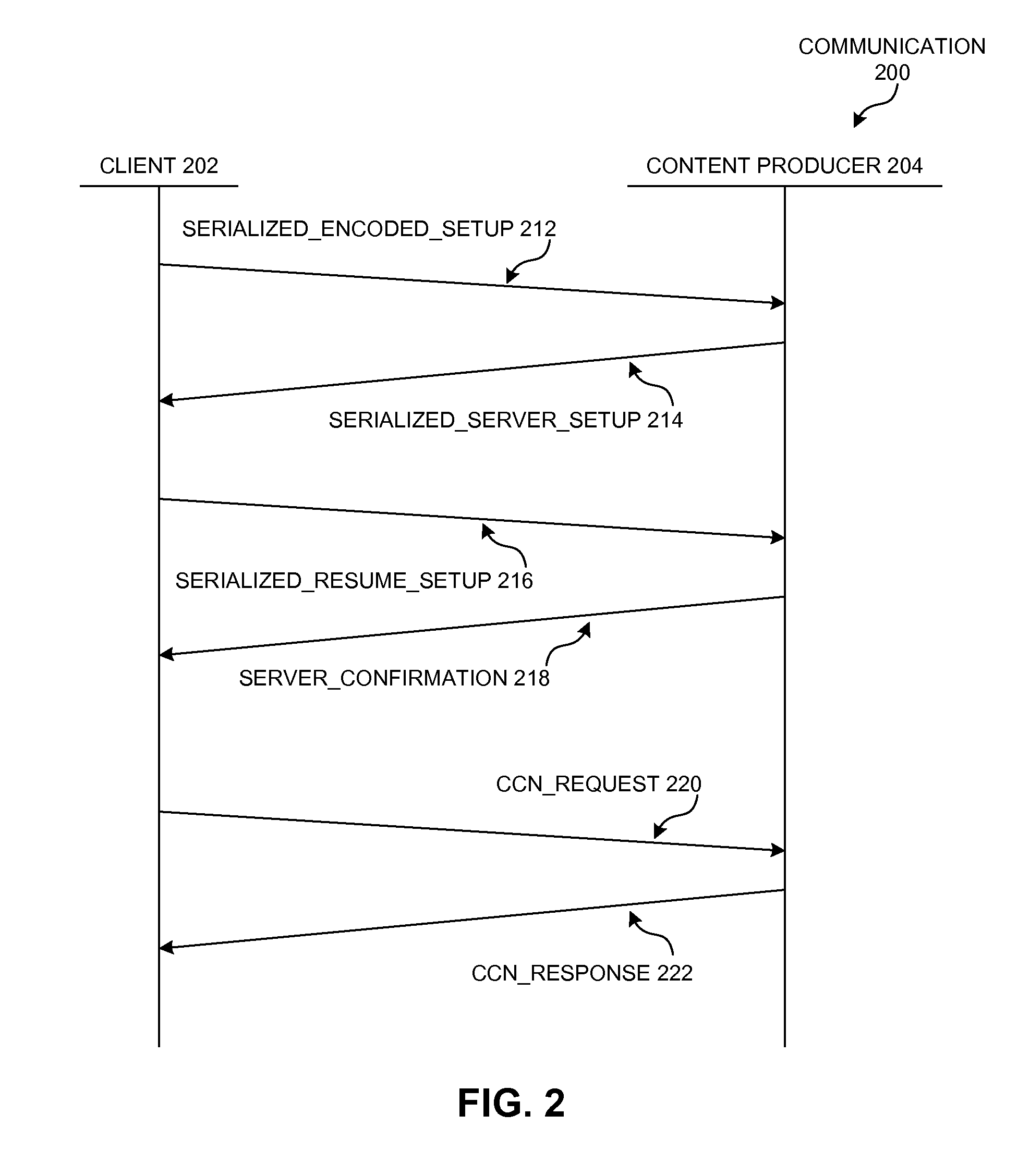
Content-based transport security for distributed producers
A content-producing computer system can use a locally generated key or a client-generated key to communicate with a client device during a session over a named-data network. During operation, the computer system can receive an Interest packet that includes a name for a piece of data or a service. The Interest's name can include a routable prefix, a session identifier, and an encrypted suffix. In some embodiments, the system can generating a session key based on the session identifier and a secret value, and decrypts the encrypted suffix using the session key to obtain a plaintext suffix. The system processes the plaintext suffix to obtain data requested by the Interest, and encrypts the data using the session key. In some other embodiments, the system can use a local private key to decrypt the encrypted suffix, and uses an encryption key obtained from the Interest to encrypt the Content Object.
Owner:CISCO TECH INC
Encapsulated sustained-release acid for oil-water well reconstruction and preparation method thereof
ActiveCN102533244AUniform particle sizeHigh true sphericityDrilling compositionAcrylic resinControl manner
The invention discloses an encapsulated sustained-release acid for oil-water well reconstruction and a preparation method thereof. The encapsulated sustained-release acid comprises a capsule core and a sustained-release supporting layer coated on the outer layer of the capsule core, wherein the capsule core is a soluble or meltable solid acid, the sustained-release supporting layer comprises a sustained-release wall material and a supporting wall material, the sustained-release wall material is an organic fatty acid or a derivative thereof, the supporting wall material is acrylic resin or a derivative thereof, and the solid acid is solid hydrochloric acid powder or citrate. The encapsulated sustained-release acid is a spherical granule with the particle size of 0.15-0.25 mm. The encapsulated sustained-release acid also comprises an adhesive spray-coated on the capsule core, wherein the adhesive is water-soluble vegetable gum or a derivative thereof, and is specifically guar gum, hydroxypropyl guar gum or carboxymethyl hydroxypropyl guar gum. According to the invention, the control mode of the acid radical ion consumption is simple and accurate; the preparation process is simple; and the encapsulated sustained-release acid is reliable in performance, safe for transportation and carrying, and convenient for use, and can be used for reducing the probability of underground tool acid corrosion and operation personnel damage in the application.
Owner:PETROCHINA CO LTD
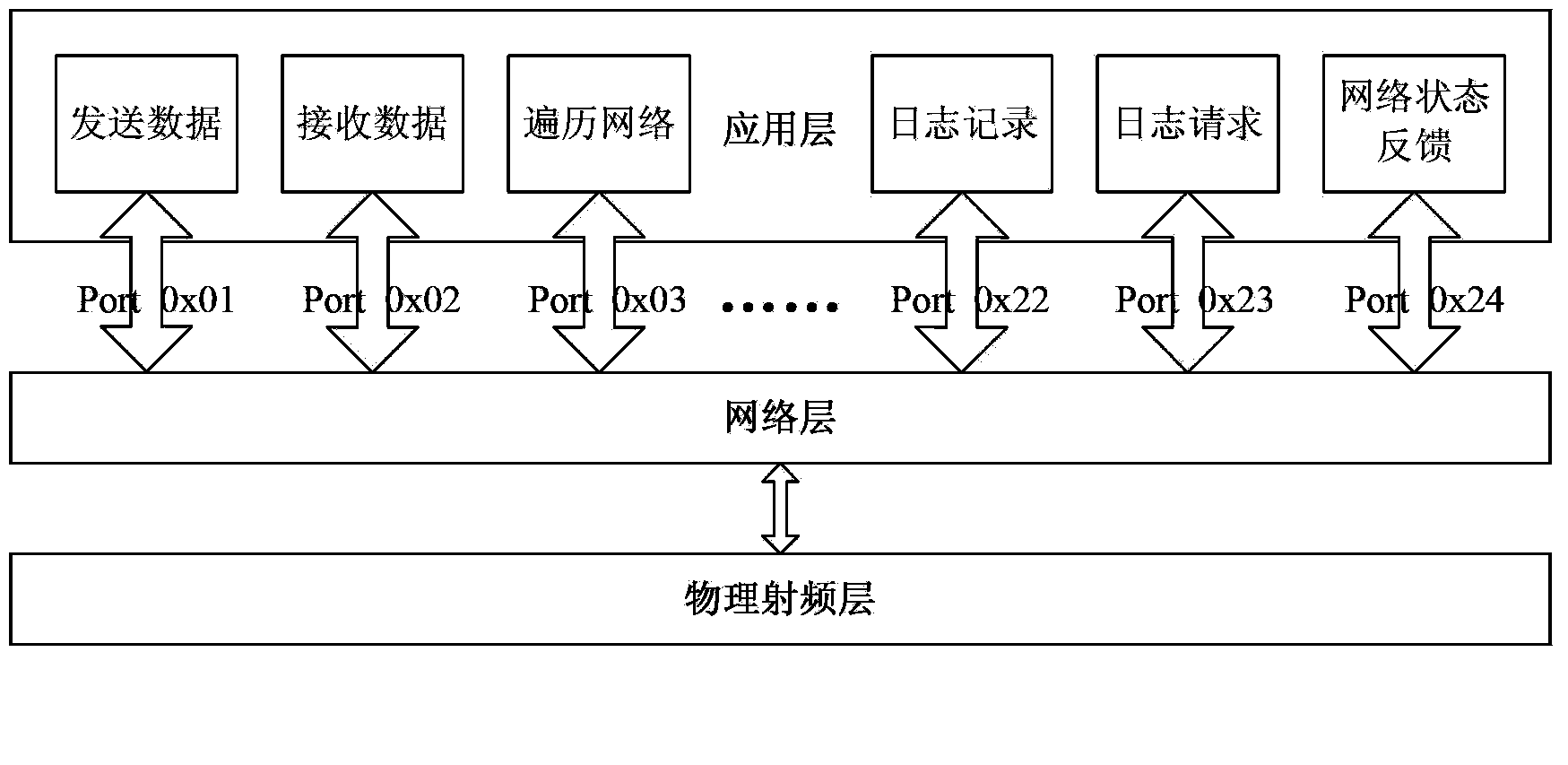
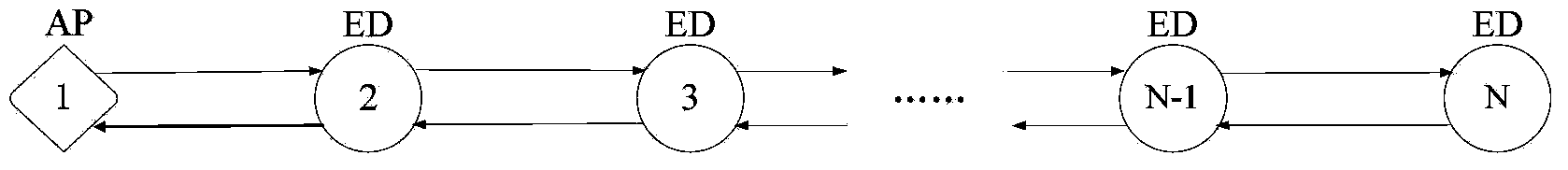
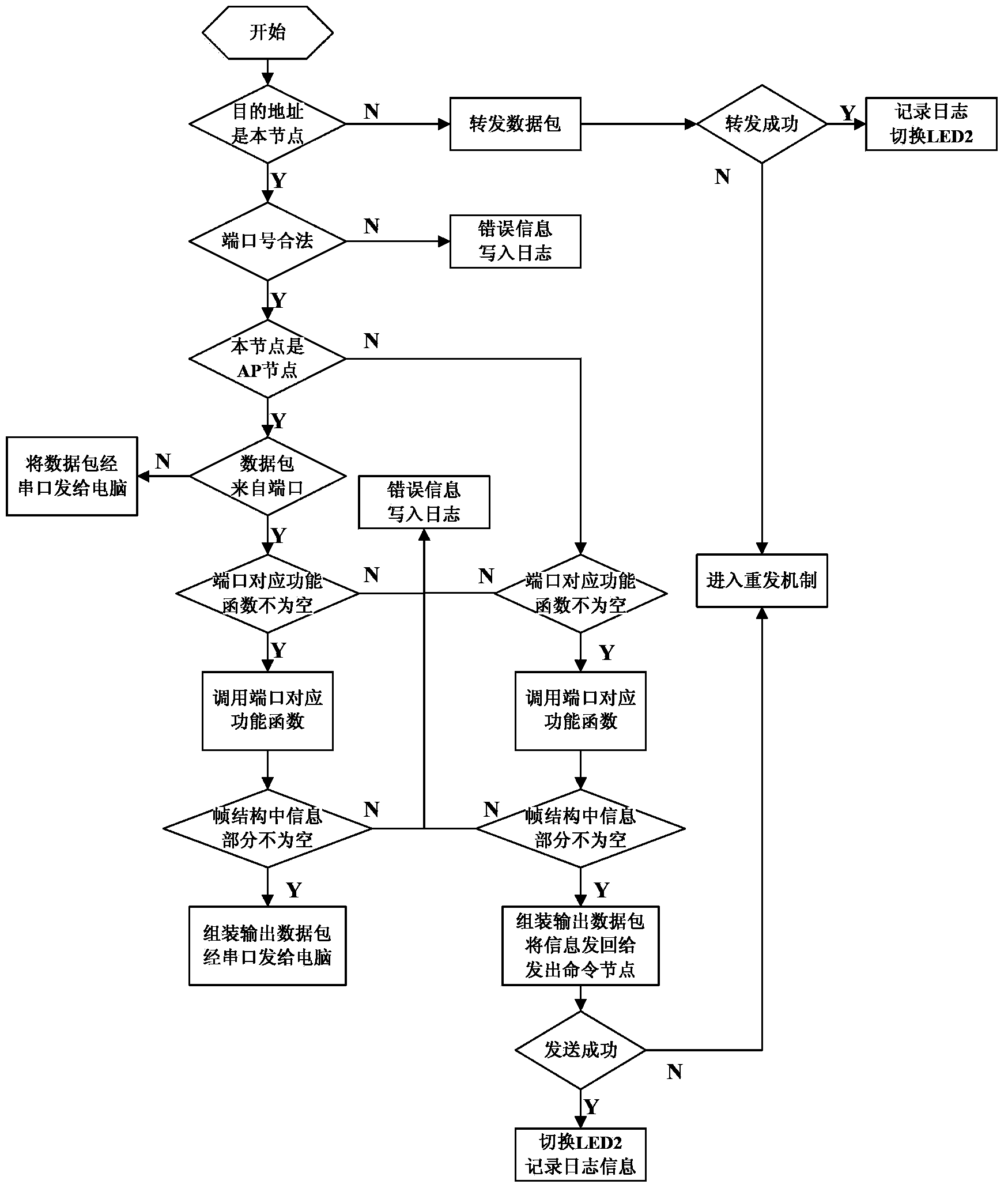
Wireless sensor network communication protocol method of automatic cathodic protection data collection system
ActiveCN103841620AImprove work efficiencyEasy maintenanceNetwork topologiesWireless network protocolsNetwork Communication ProtocolsRadio frequency
The invention discloses a wireless sensor network communication protocol method of an automatic cathodic protection data collection system and relates to the technical field of digital information transmission and pipe systems. The wireless sensor network communication protocol method adopts a three-layer protocol structure which comprises a physical radio frequency layer, a network layer and an application layer from bottom to top, wherein the physical radio frequency layer encapsulates data of the bottom layer into a frame structure, and a CSMA-CA carrier monitoring conflict avoidance algorithm is planted into the frame structure; the network layer achieves formation, retrieval and input and output control of data packets in the protocol and interface function transmission and reception by calling a software interface encapsulated by the physical radio frequency layer; the application layer establishes an application program interface function capable of achieving all functions of the application layer by calling a software interface provided by the network layer. By means of the wireless sensor network communication protocol method, communication can be guaranteed greatly, work efficiency of the automatic cathodic protection data collection system is greatly increased, management cost is reduced, and transport security of petroleum pipelines is guaranteed.
Owner:PIPECHINA SOUTH CHINA CO
Engine material frame
ActiveCN102514839AEasy to transportFast and labor-saving transportationPackaging vehiclesContainers for machinesTransport securityChassis
The invention discloses an engine material frame, which comprises at least one engine material frame assembly which comprises an underframe and a plurality of material frame trolleys. A plurality of material frame trolley stations are arranged on the underframe, the plurality of material frame trolleys are correspondingly arranged in the material frame trolley stations, and one engine setting station is respectively and correspondingly arranged on each material frame trolley. The engine material frame has the following advantages that: 1 the material frame trolleys and the corresponding underframe are arranged so that transportation of engines is convenient, fast and labor-saving, and labor intensity of operating personnel is reduced greatly; and 2 the engine material frame can transport a plurality of engines of different models and specifications simultaneously, thereby improving transporting efficiency and being capable of guaranteeing transporting security.
Owner:上海众德金属制品启东有限公司
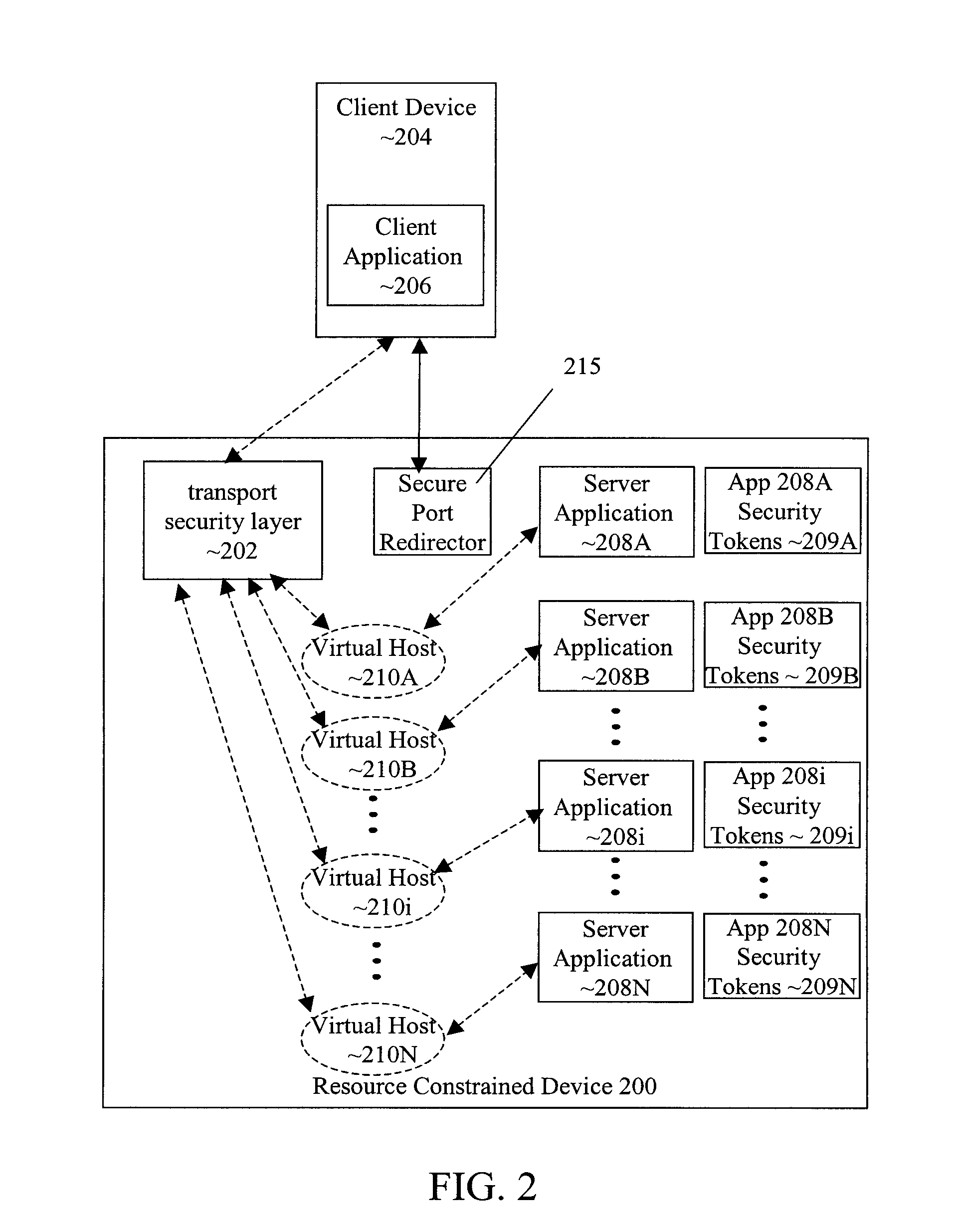
Transport-level web application security on a resource-constrained device
ActiveUS8484713B1Facilitate communicationEliminate requirementsDigital data processing detailsMultiple digital computer combinationsSecure communicationApplication specific
Owner:ORACLE INT CORP
Normally closed type inclined alley stopping device
InactiveCN101397018AReduce investmentEliminate the potential for injuryPositive railway stopsStops deviceEngineering
The invention discloses a car lug of a normally-closed inclined tunnel used for the safe transporting measure of the inclined tunnel of a coal mine, which comprises a normally-closed duplex car lug, a car lug bar of the normally-closed inclined tunnel, an interlocking pneumatic control box and a connection pipeline. The car lug has simple structure and is convenient to be maintained; interlocking control is adopted, therefore, devices are mutually closed and locked, thus being capable of preventing the running-way of the inclined tunnel reliably or stopping the running-way reliably and timely once the running-way happens; the original compressed air on the spot under a well is used as power, therefore, the car lug of the invention is safe and reliable, and the capital investment is reduced.
Owner:无锡市锡湖液压气动机械有限公司
System and method for transport security control and tracking
ActiveUS7602296B2Reduce laborShorten the timeLogisticsBurglar alarm by hand-portable articles removalBulk cargoInspection time
The invention disclosed provides an apparatus and method to monitor and track the security of bulk cargo from a dispatch point to a receipt point. The apparatus includes a plurality of RFID antennas at a dispatch location and at a receipt location, networked software modules in communication with the RFID antennas, and disposable RFID tags used as security seals affixed to a carrier at multiple locations. The software modules include a Cargo Registration Module, a Dispatch Scanning Module, and a Receipt Scanning Module. The apparatus and method reduce cargo inspection time and labor at the points of departure and receipt. The automation of the dispatch and receipt process eliminates the human element thereby increasing the efficiency of the process. An additional embodiment includes a “single-use” disposable RFID tagged seal adapted to be attached to a transport portal unable to be removed without damaging an RFID transmitter contained within.
Owner:SURELOCK SEALS
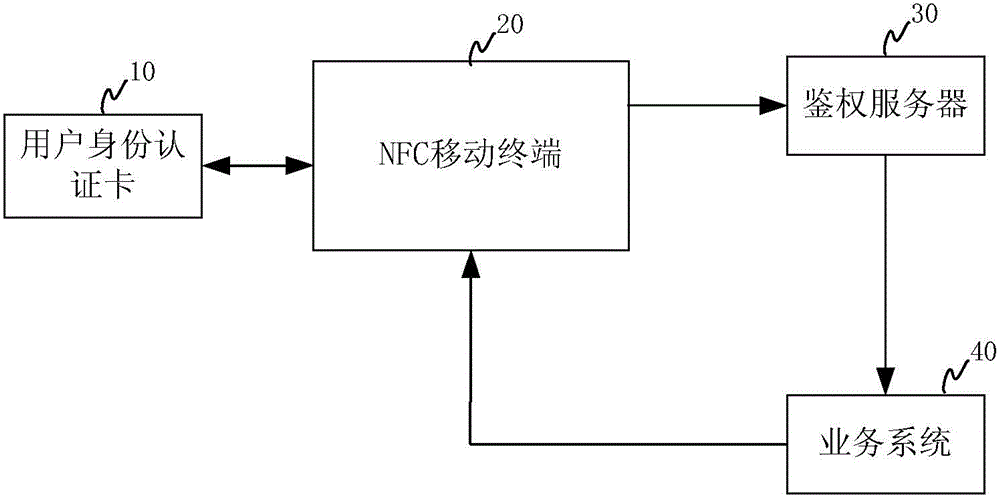
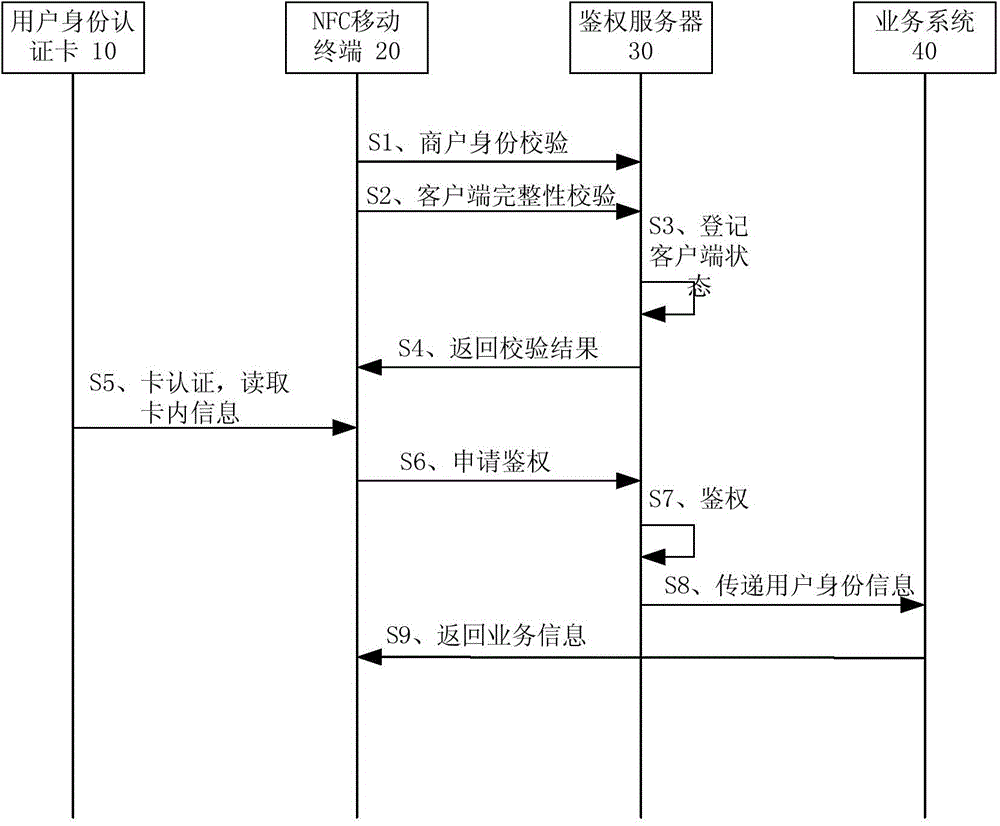
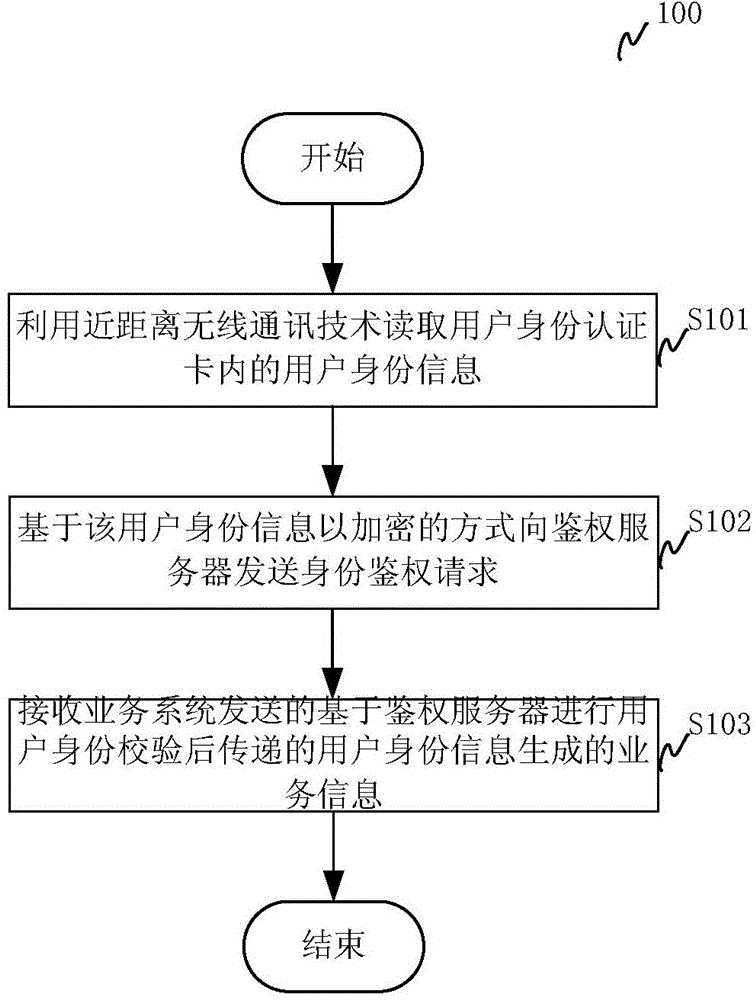
User identity authentication method, device and system
InactiveCN105704092AReduce operating costsLower the thresholdUser identity/authority verificationShortest distanceAuthentication server
The invention relates to a user identity authentication method, a user identity authentication device and a user identity authentication system. The system includes: a user identity authentication card for storing encrypted user identity information; a mobile terminal with short-range wireless communication function for reading the user identity information in the user identity authentication card by using short-range wireless communication technology, and Send an identity authentication request in an encrypted manner based on the user identity information; the authentication server is used to receive and verify the identity authentication request, and decrypt the user identity information; the business system is used to receive the user identity delivered by the authentication server information, generating service information based on the user identity information and returning it to the mobile terminal. The invention adopts the NFC mobile terminal which is easily configured by merchants as the reading device, which greatly reduces the operating cost, and at the same time fully considers factors such as process safety and transmission safety, achieves a balance in performance and safety, and is easy to promote and cover the market.
Owner:卓望数码技术(深圳)有限公司
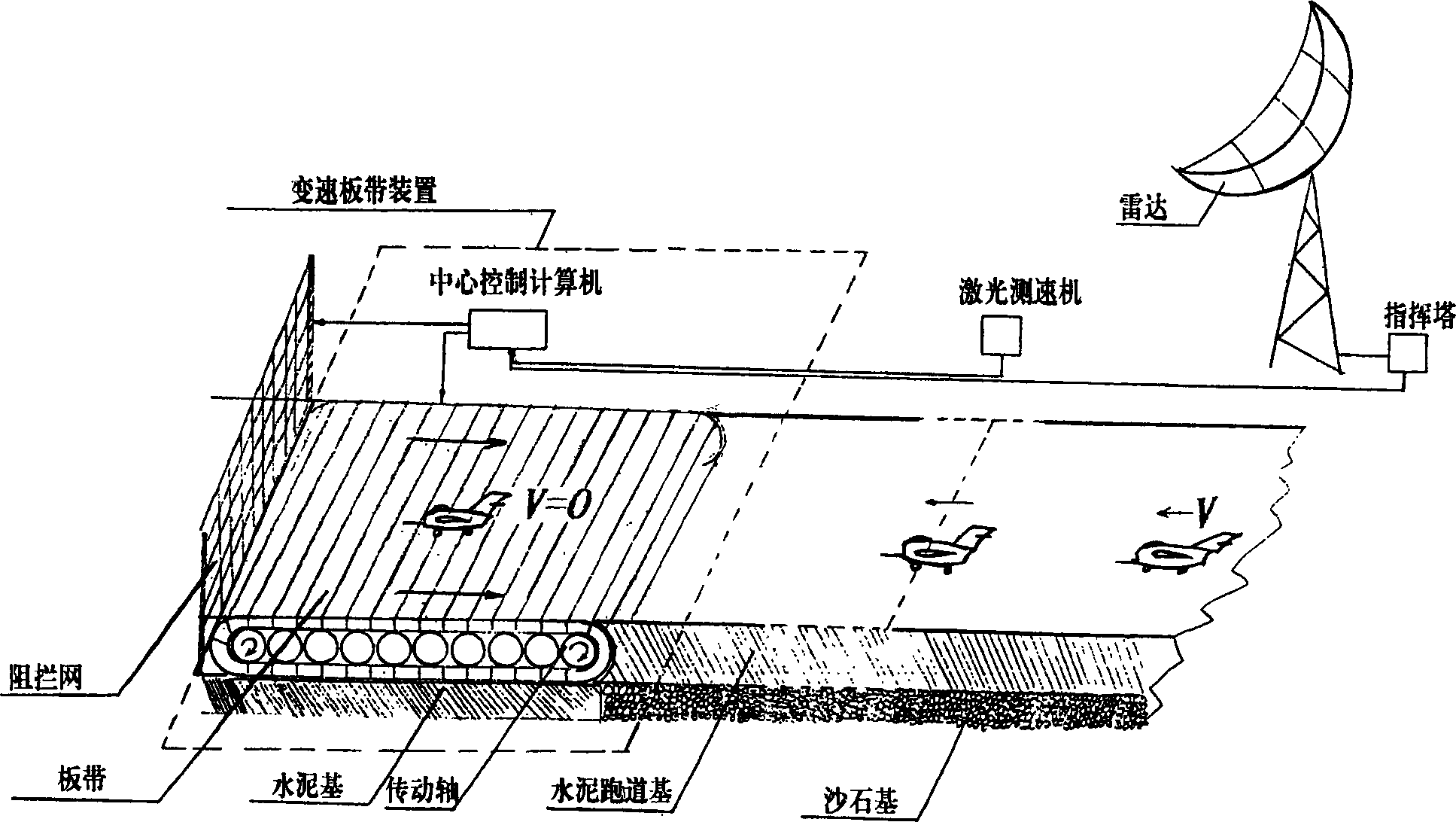
Automatic control speed-changing belt for airport runaway
The invention relates to an automatic speed-transmission band device of airdrome runway, which is purposed to prevent the plane outside the runway or the vehicle impacting building. The invention utilizes the micro-fine axial roller metallic hinge circle band to produce an optical mechanical electric automatic control system.
Owner:孟中
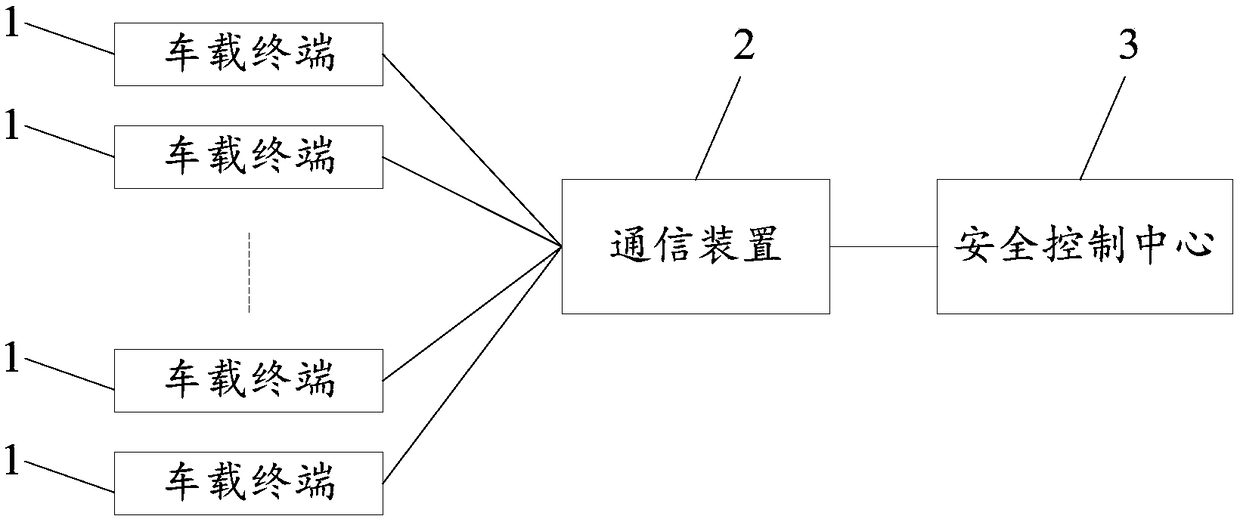
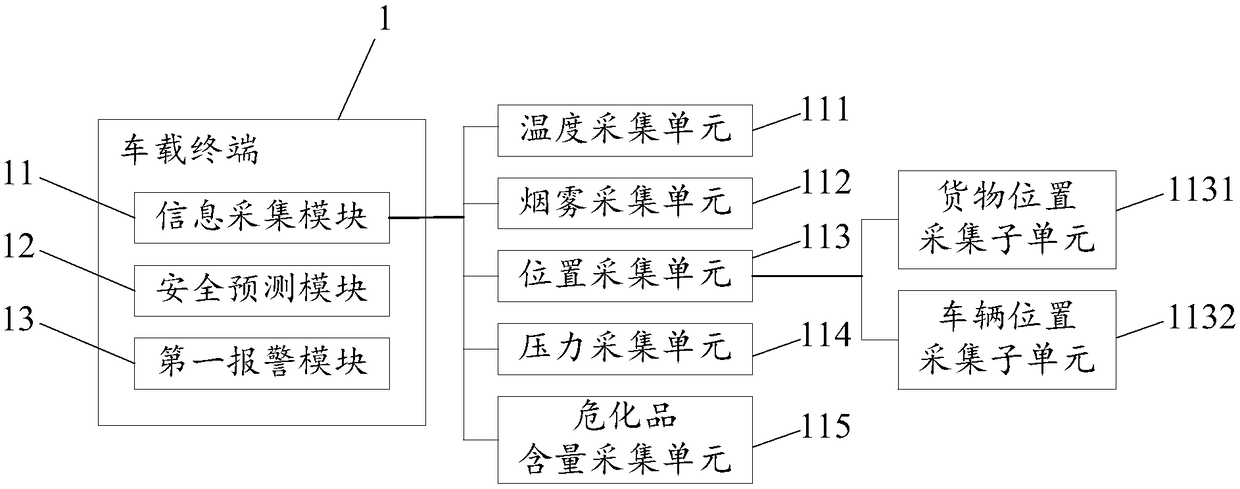
IoT based traffic transport safety control system
InactiveCN108629965AImprove securityBe vigilantRoad vehicles traffic controlAlarmsElectricityDriver/operator
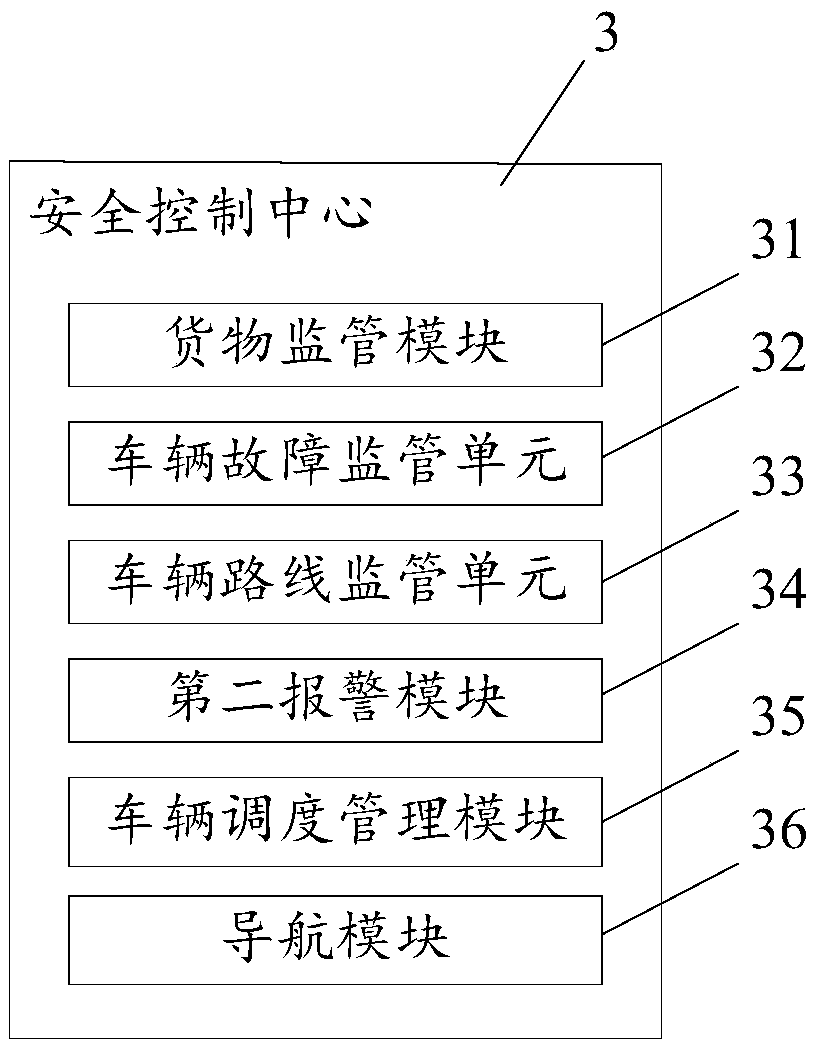
The invention discloses an IoT based traffic transport safety control system. The system includes multiple vehicle terminal, a communication device and a safety control center. The multiple vehicle terminals are connected to the safety control center electrically. Each vehicle terminal includes an information collection module, a safety prediction module and a first alarm module. The safety control center includes a cargo supervision module, a vehicle fault supervision unit, a vehicle route supervision unit and a second alarm module. In one aspect, the system can remind a driver to pay more attention on driving, at the same time, the safety control center can perform centralized supervision on transport vehicles, so that the safety performance of hazardous chemical substance transportationcan be improved. In the other aspect, through supervision of cargo labels, supervision of cargo and vehicle relative states, supervision of vehicle faults and supervision of vehicle routes, safety ofcargo in the transport process can be ensured effectively and cargo change with inferior cargo during the transport process can be prevented, so that the traffic transport safety supervision system is improved.
Owner:ANKANG UNIV
Can-type container having electronic monitoring device
ActiveCN1733568AMonitoring leak monitoringMonitor illegal openingLarge containersProcess moduleTank container
The invention relates to tank container with electric detection device in the valve piece protection box, wherein, the said detection device comprises a travel switch with contact head with a first and second place, a sensor used to detect the leakage of carried material in container and send corresponding data, and a data process module to communicate with the switch and sensor; wherein, on the first place, the contact head is propped by the box cap, the switch is working normally; on the second place, the contact head departs the box cap for a predetermined safe distance, and the switch is on abnormal state. This invention can detect the leakage and illegal open for the box cap globally and ensures the transposition security.
Owner:NANTONG CIMC TANK EQUIP CO LTD
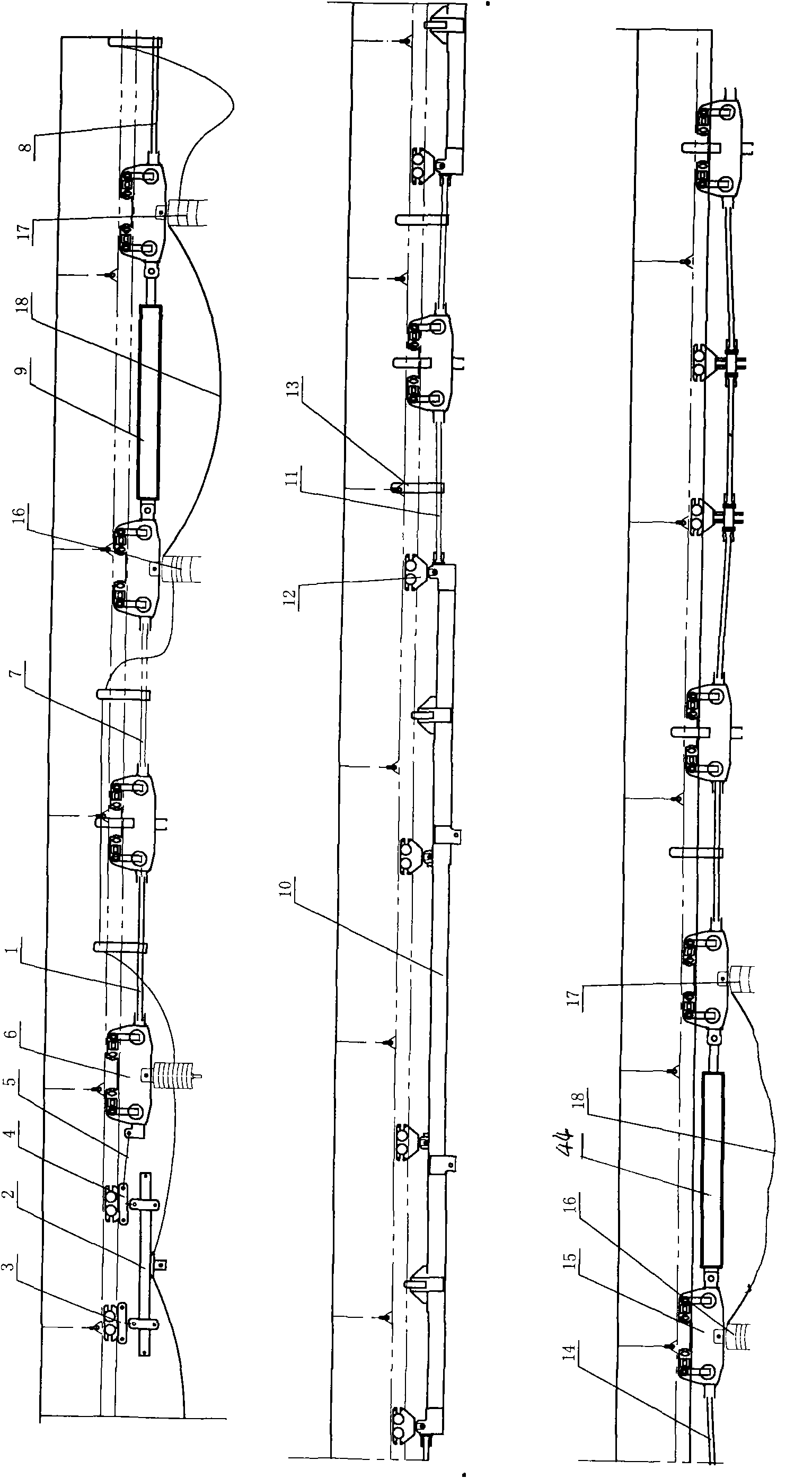
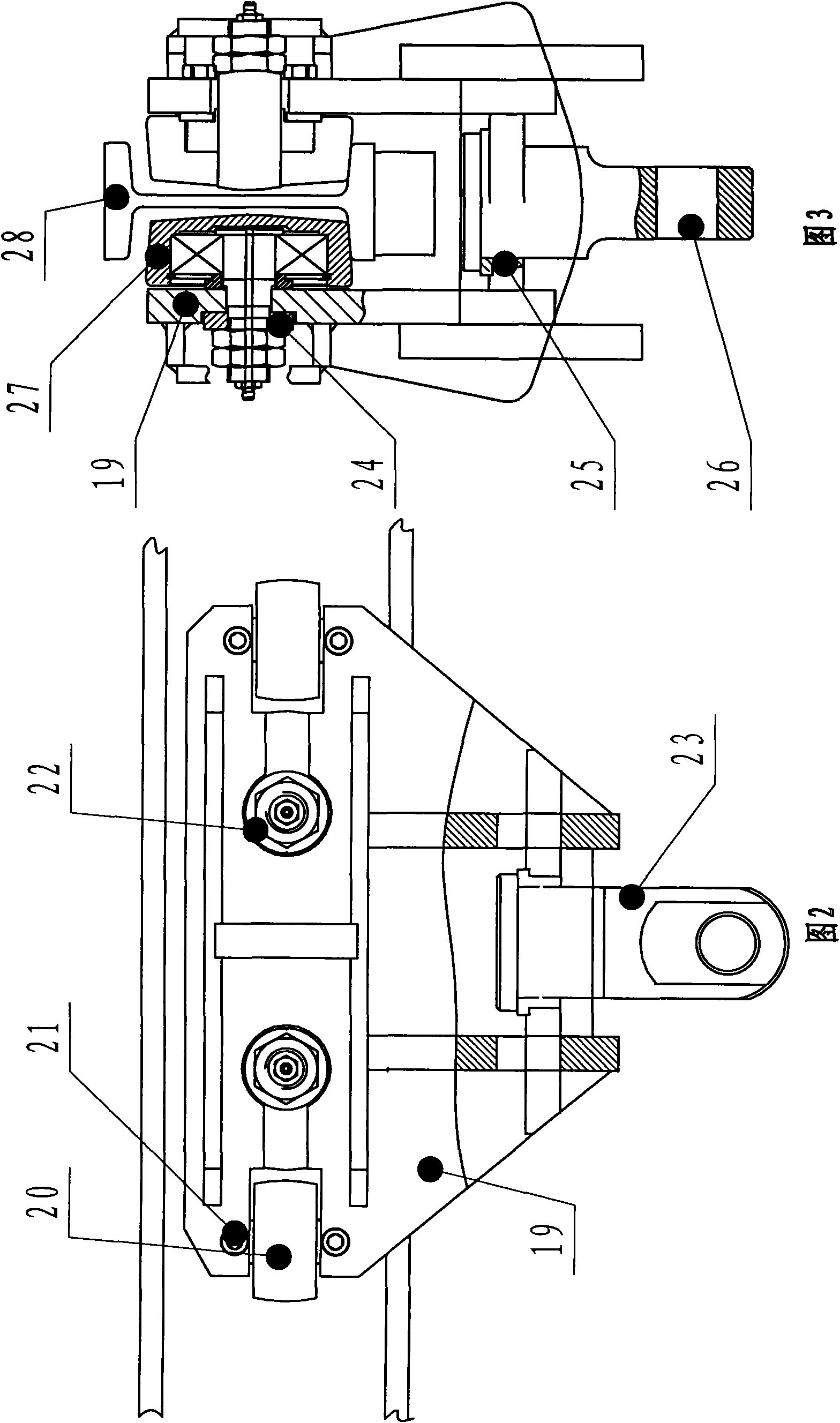
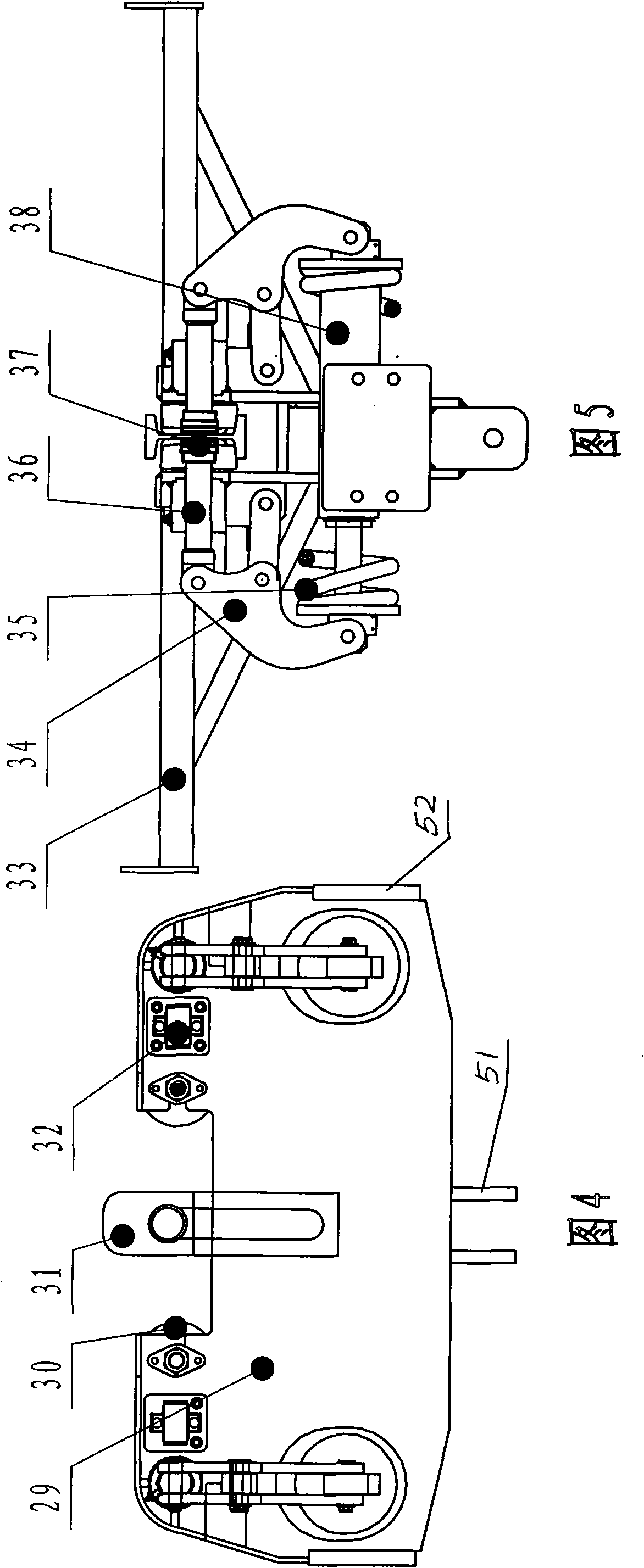
Curving-type monorail crane and traveling method thereof
InactiveCN101602469AImprove work efficiencyTransportation safetyTravelling gearTrolleysHydraulic cylinderCarrying capacity
The invention relates to a curving-type monorail crane and a traveling method thereof. The curving-type monorail crane belongs to undermine comprehensive coal mining conveying machinery, which comprises a track, wherein the track is suspended in an underworking through a hoisting ring and an anchor rod. The curving-type monorail crane is characterized in that a plurality of load bearing devices and braking devices are arranged on the track; and the load bearing devices are connected with the braking devices through a connecting piece or hydraulic cylinder or pull rod. The traveling method is three-segment type traveling; when the crane travels, a front segment and a back segment simultaneously move a step pitch first; and after the front segment and the back segment stop moving, a middle segment moves a step pitch. The curving-type monorail crane has the advantages of high working efficiency, safe conveying, simple installation, flexible and convenient operation and self-propelling traveling during operation. In addition, the curving-type monorail crane can carry crossheading-powered equipment, an atomizing pump, an emulsion box, a frequency converter and other heavy-load equipment and has a maximum carrying capacity of 150 tons.
Owner:TAIYUAN KUANGJI ELECTRIC
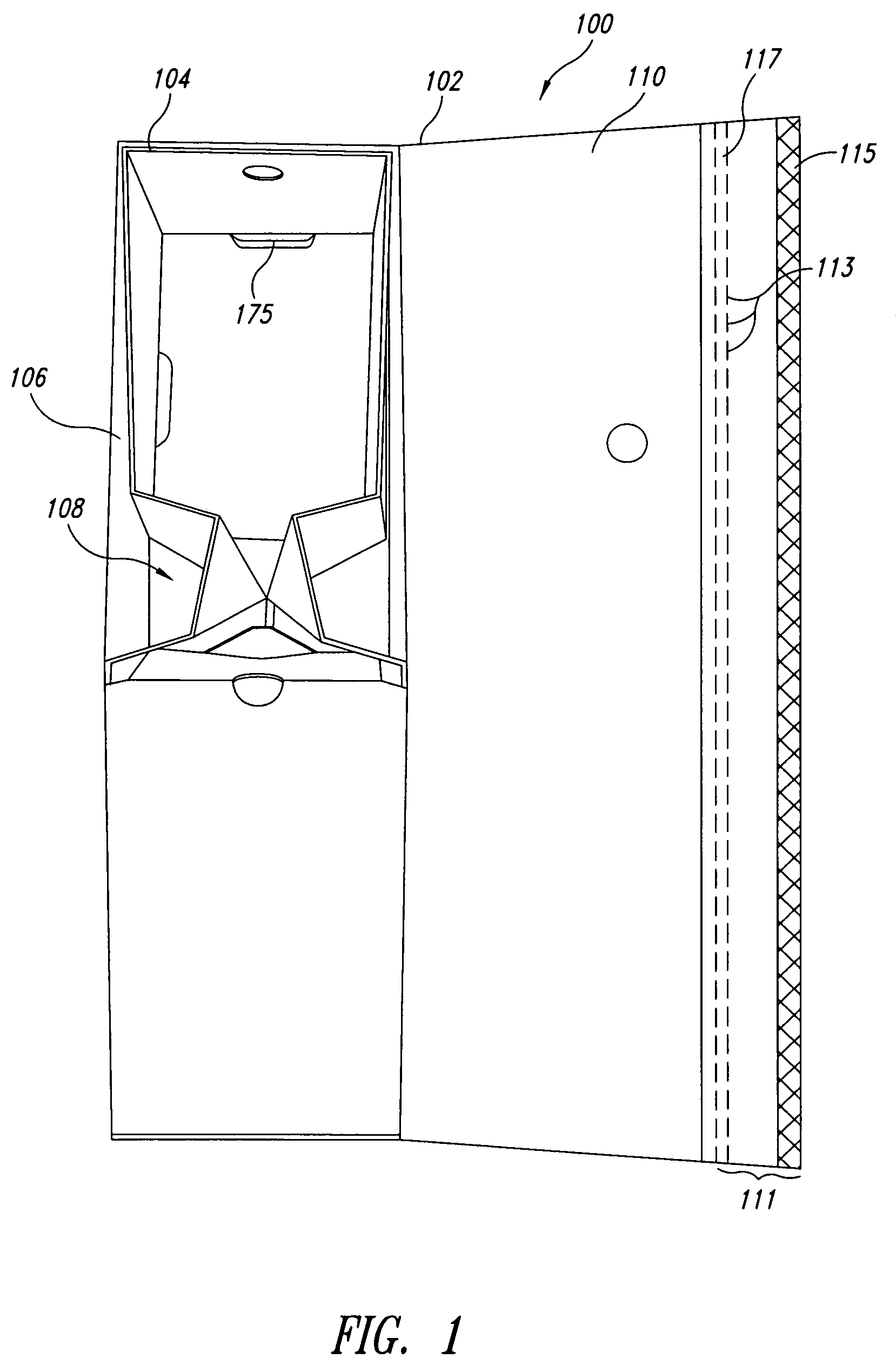
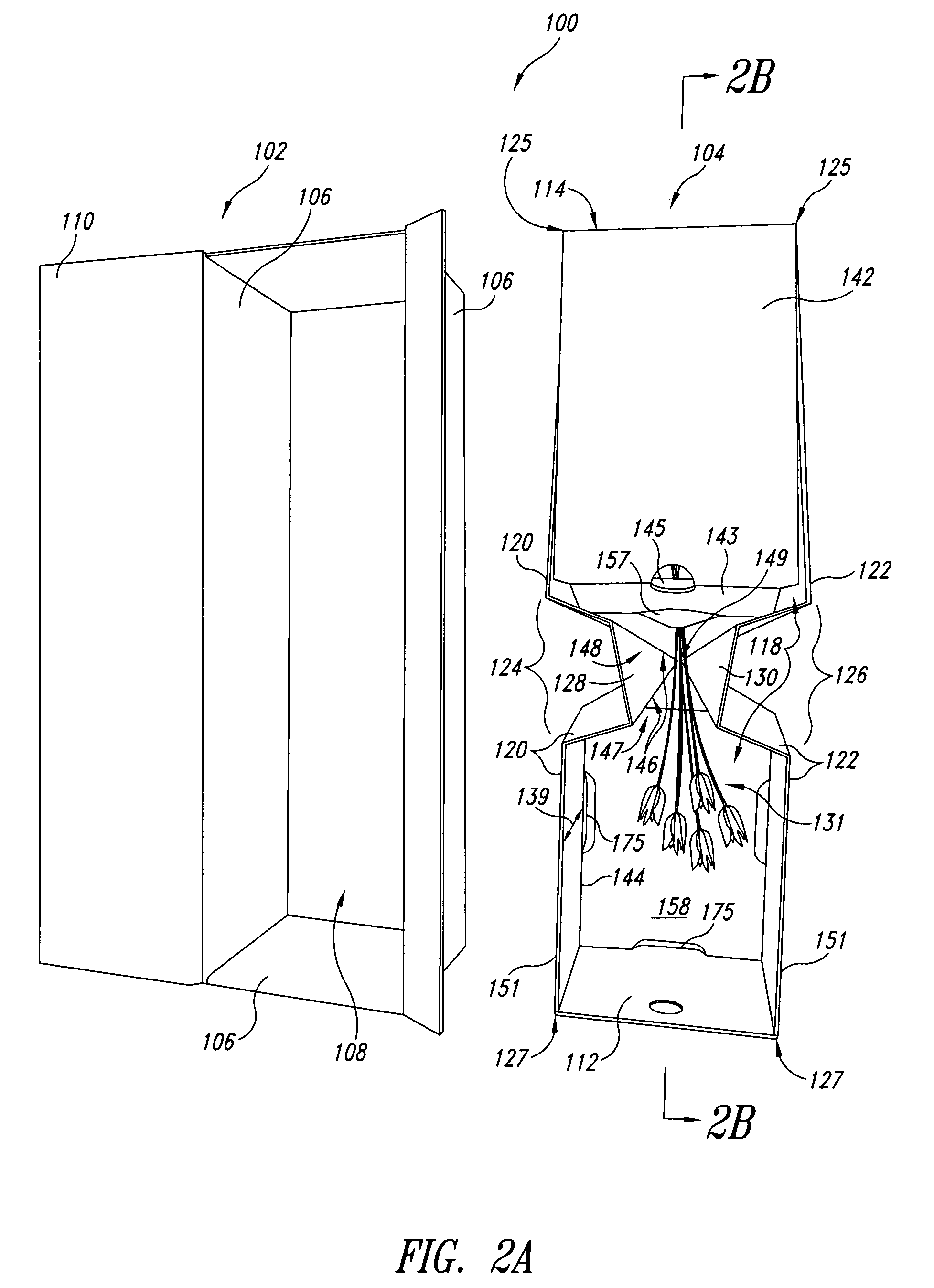
Container and method for tie-less storage and transport of secured contents
Owner:ALLIANCE PACKAGING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com