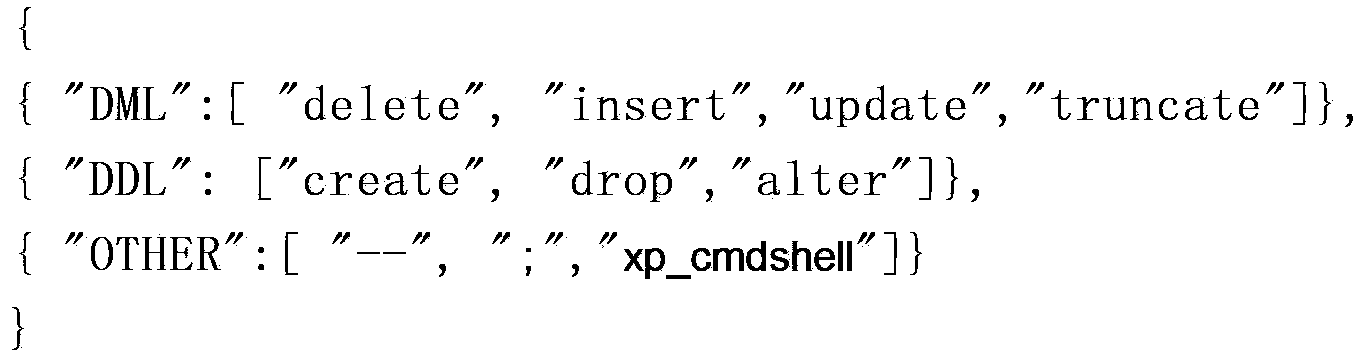Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
212 results about "Web application security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
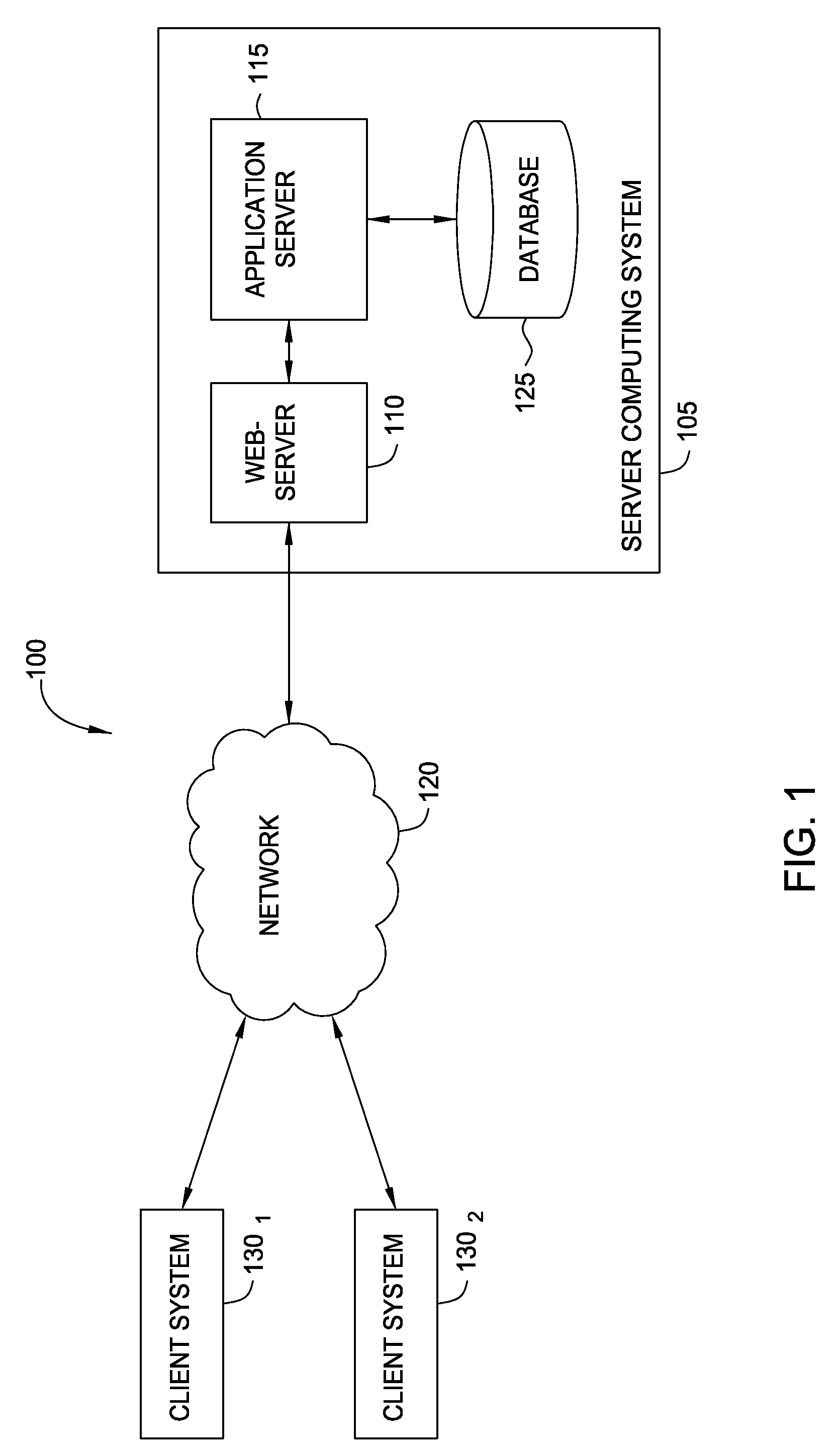
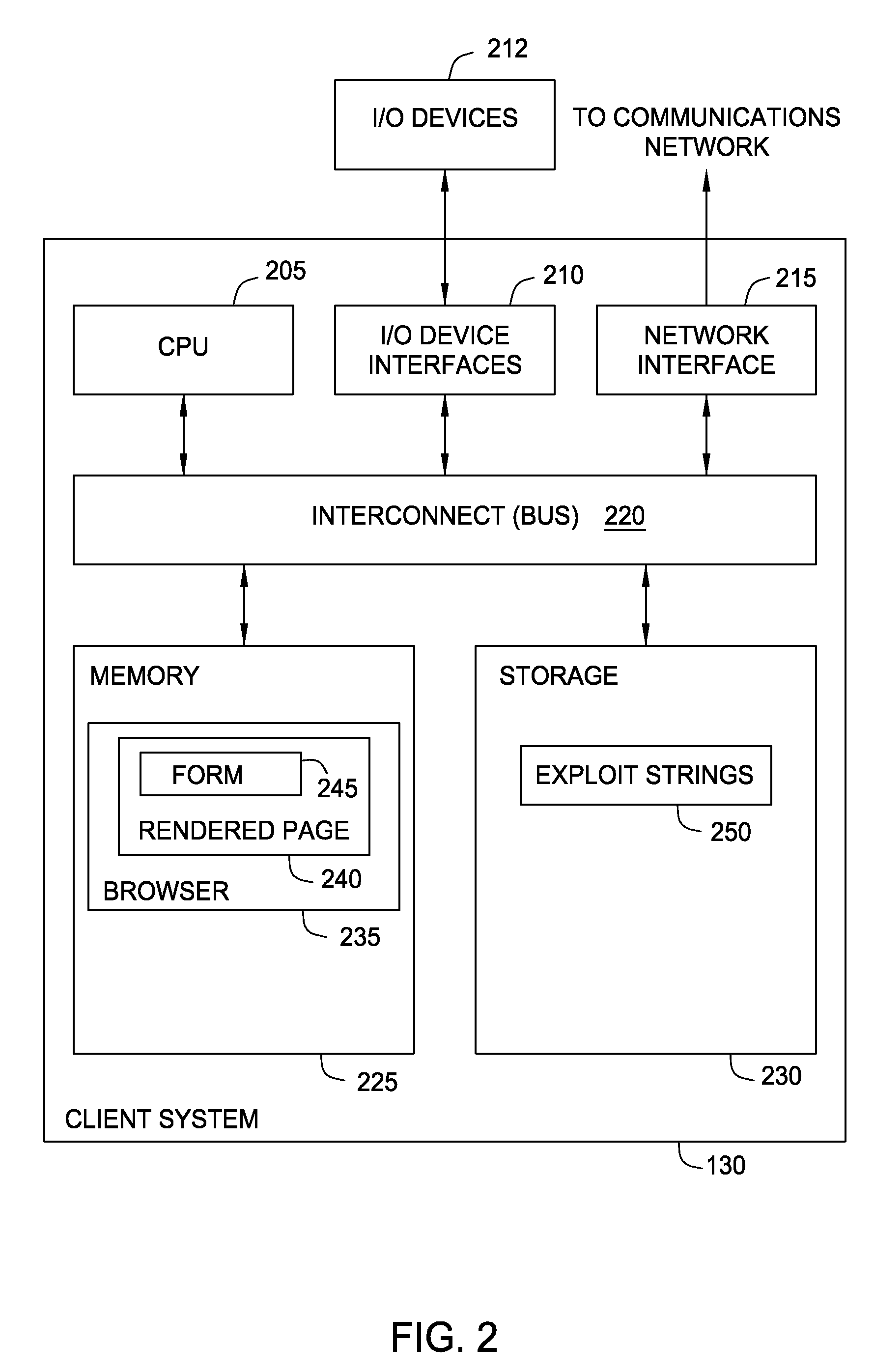
Web application security is a branch of information security that deals specifically with security of websites, web applications and web services. At a high level, web application security draws on the principles of application security but applies them specifically to internet and web systems.
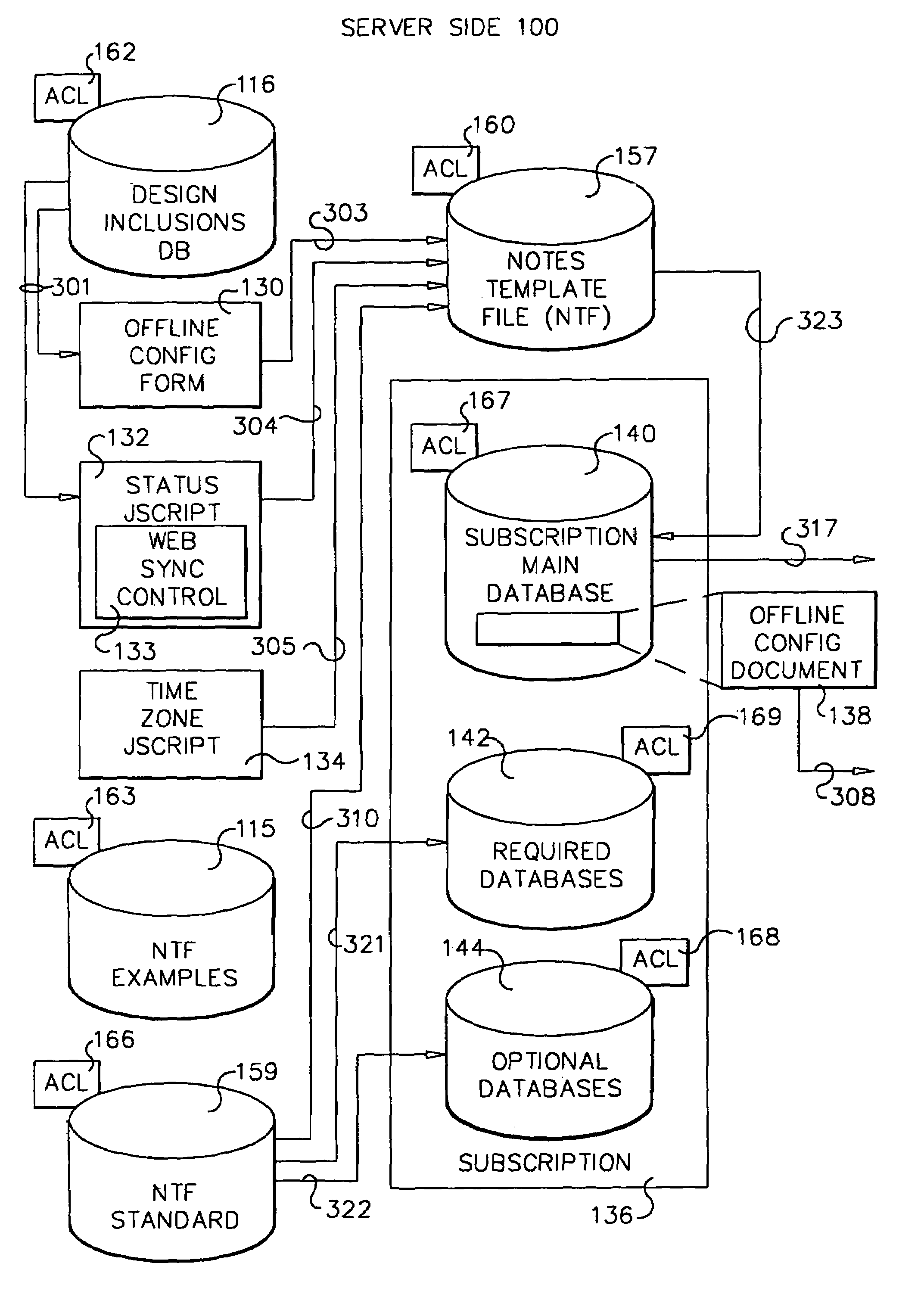
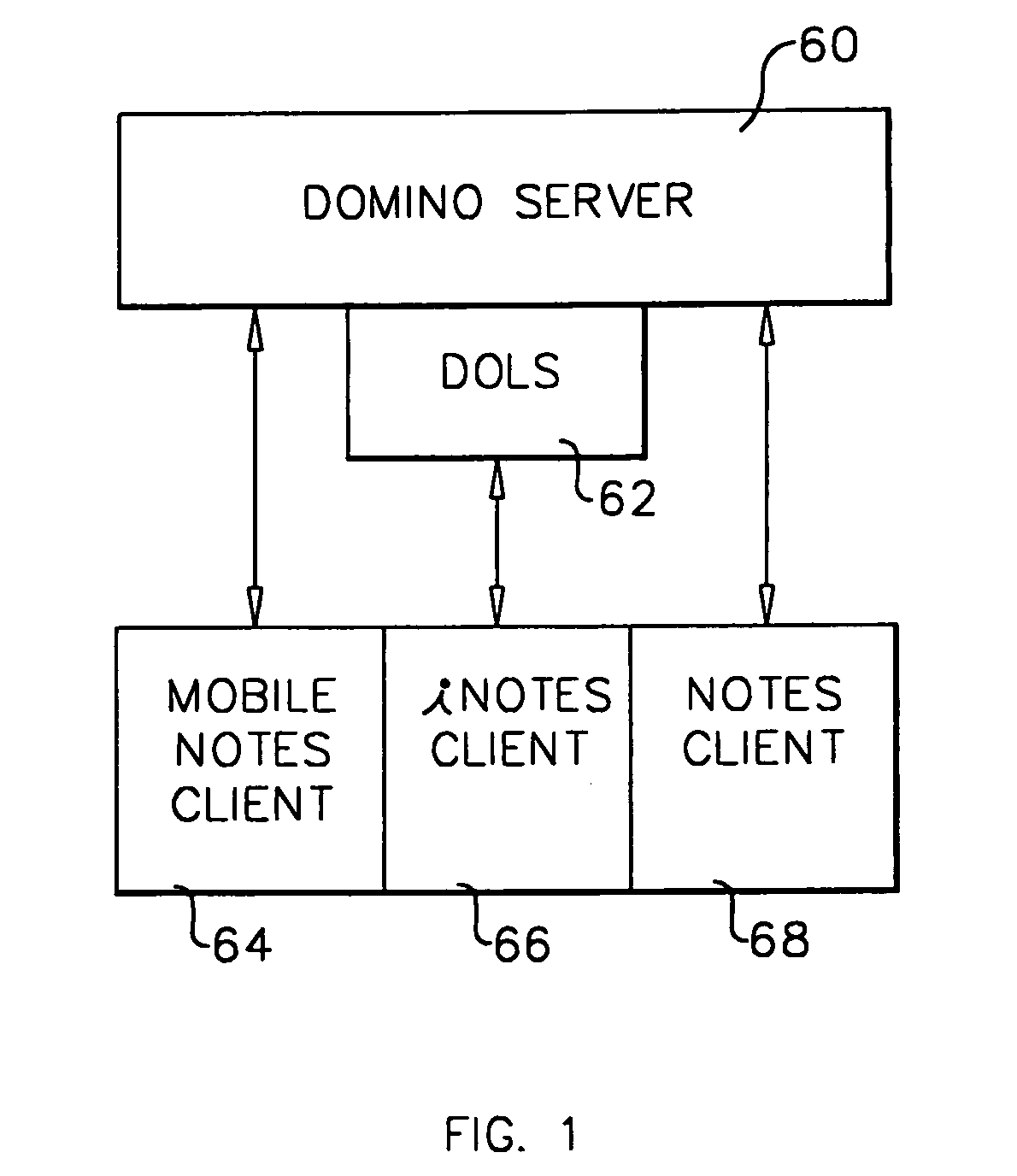
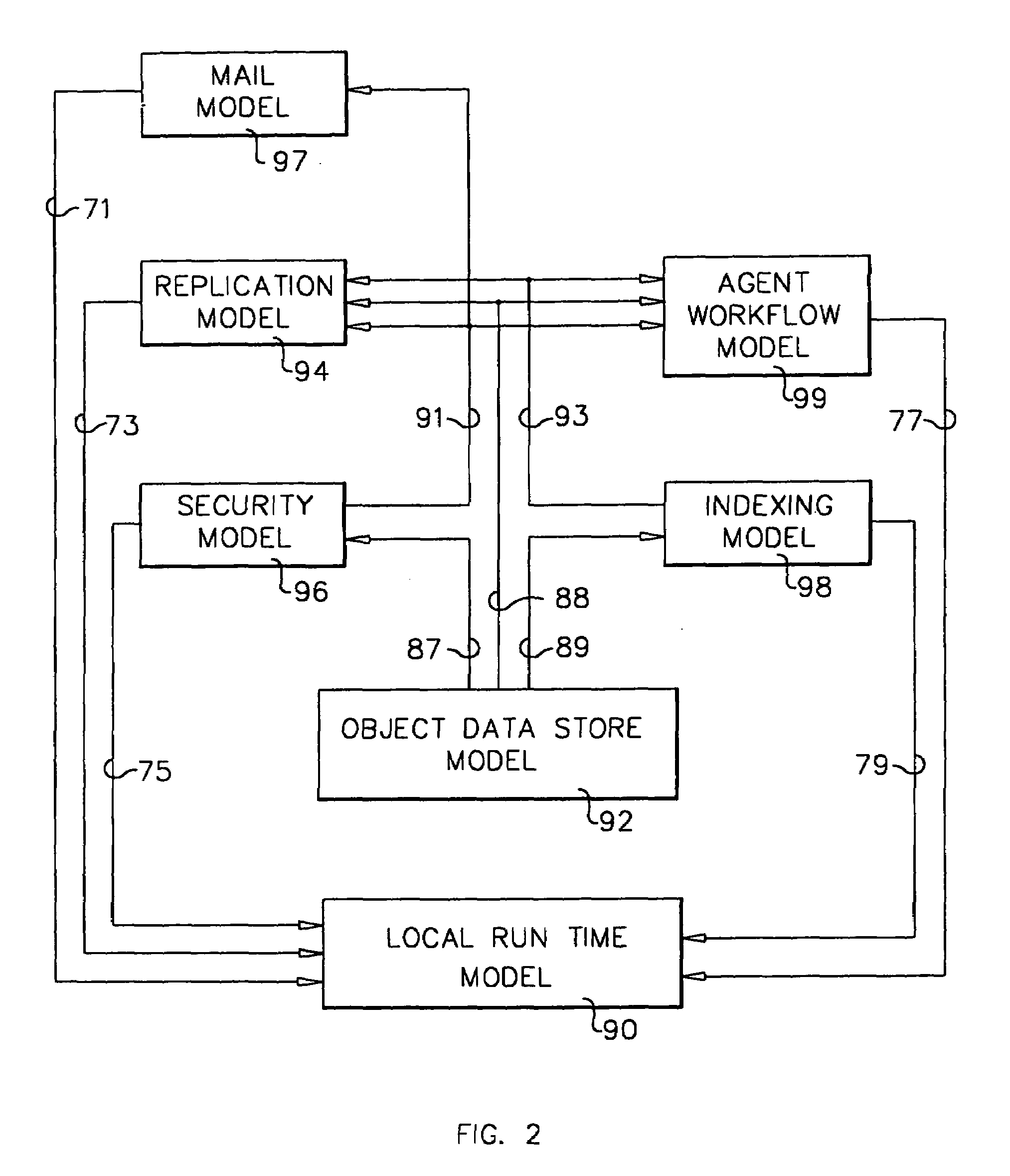
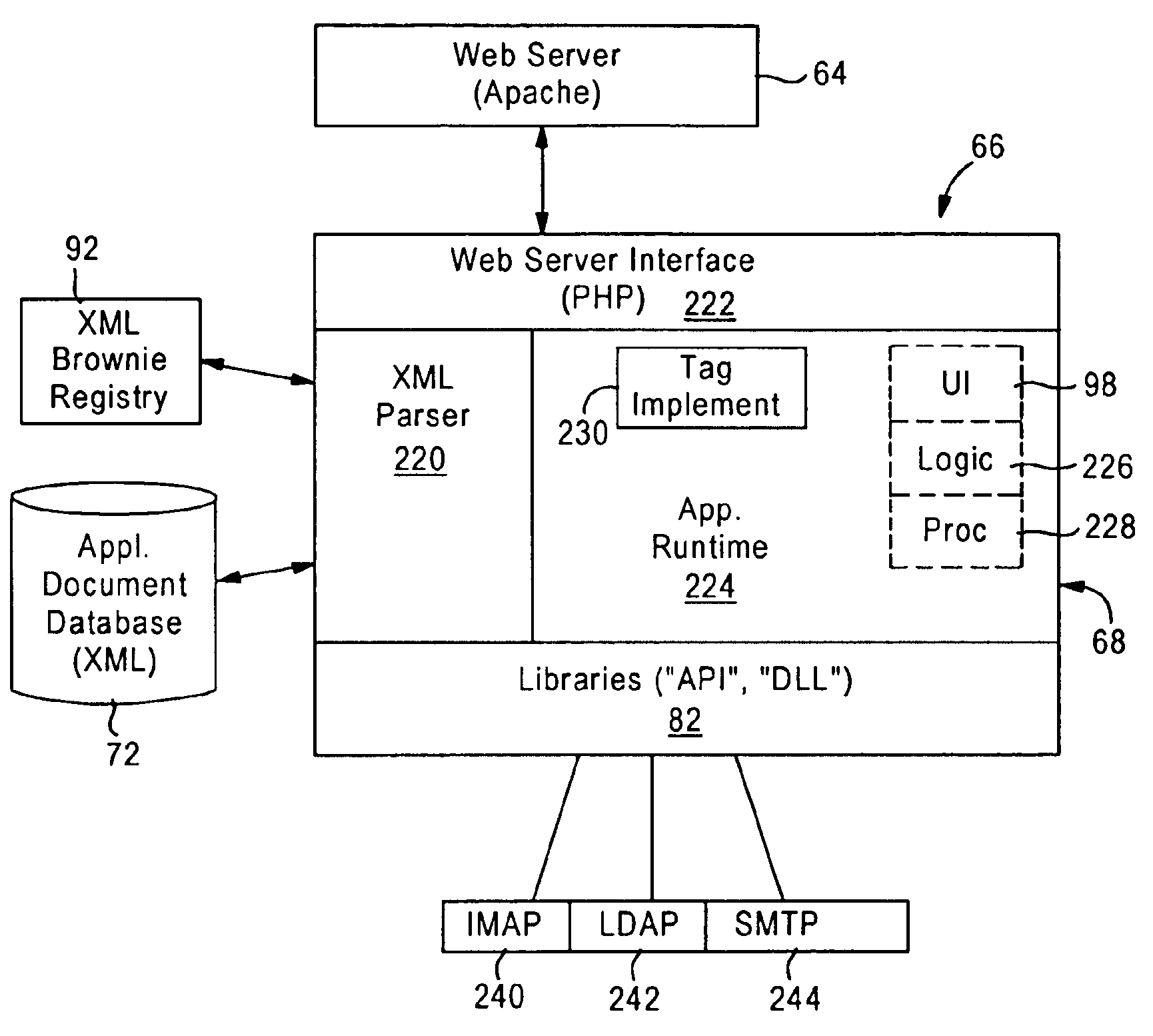
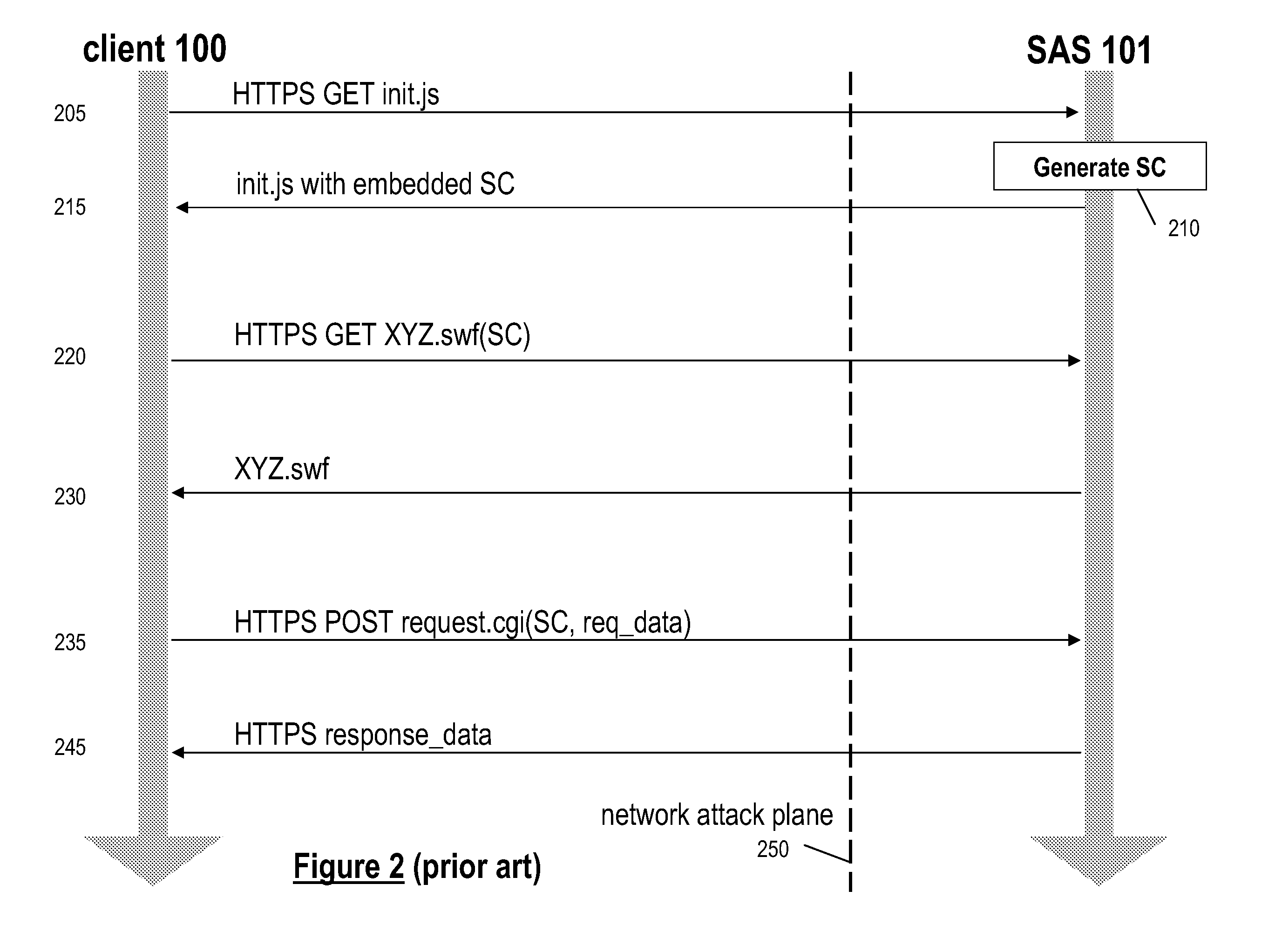
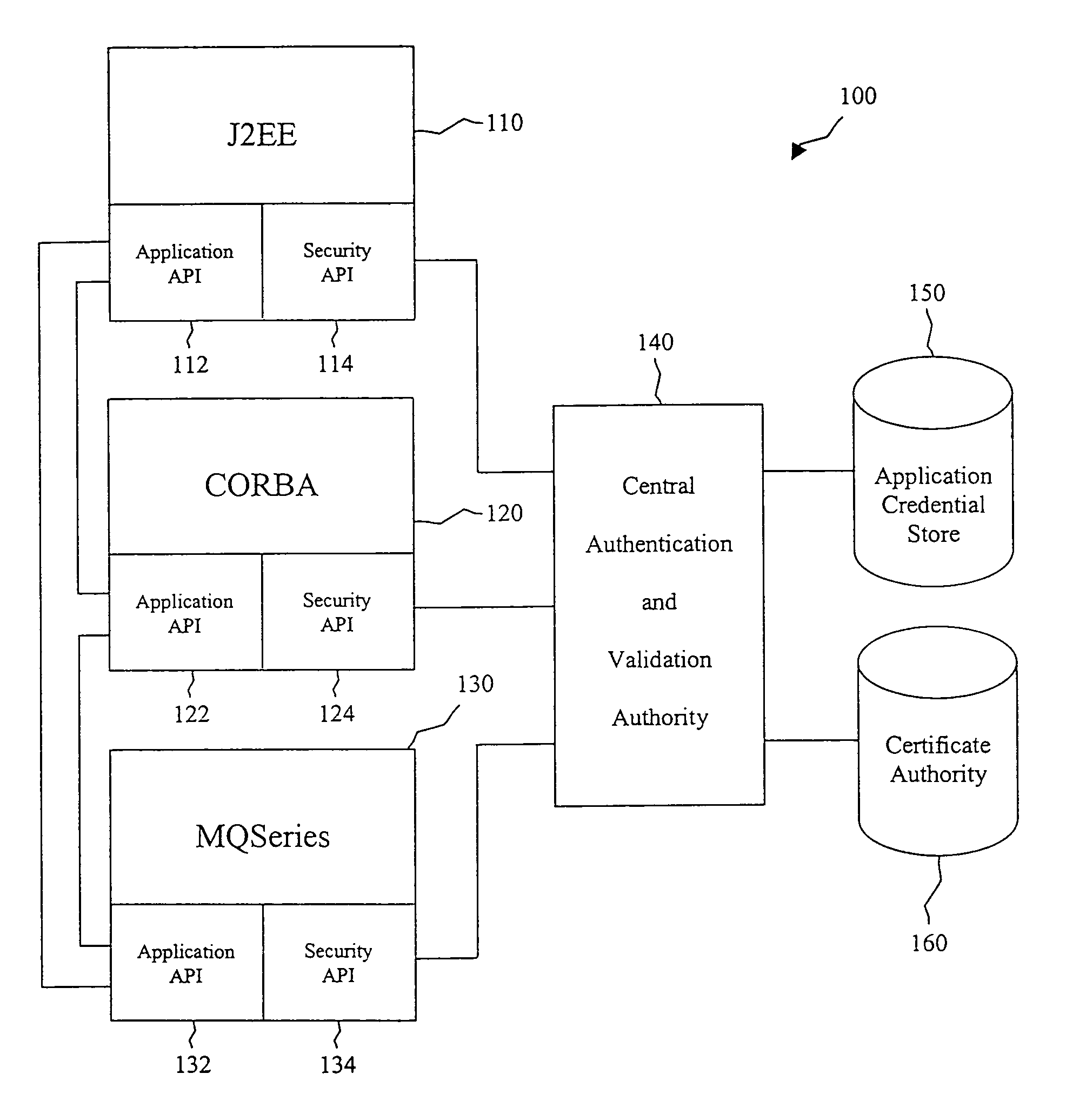
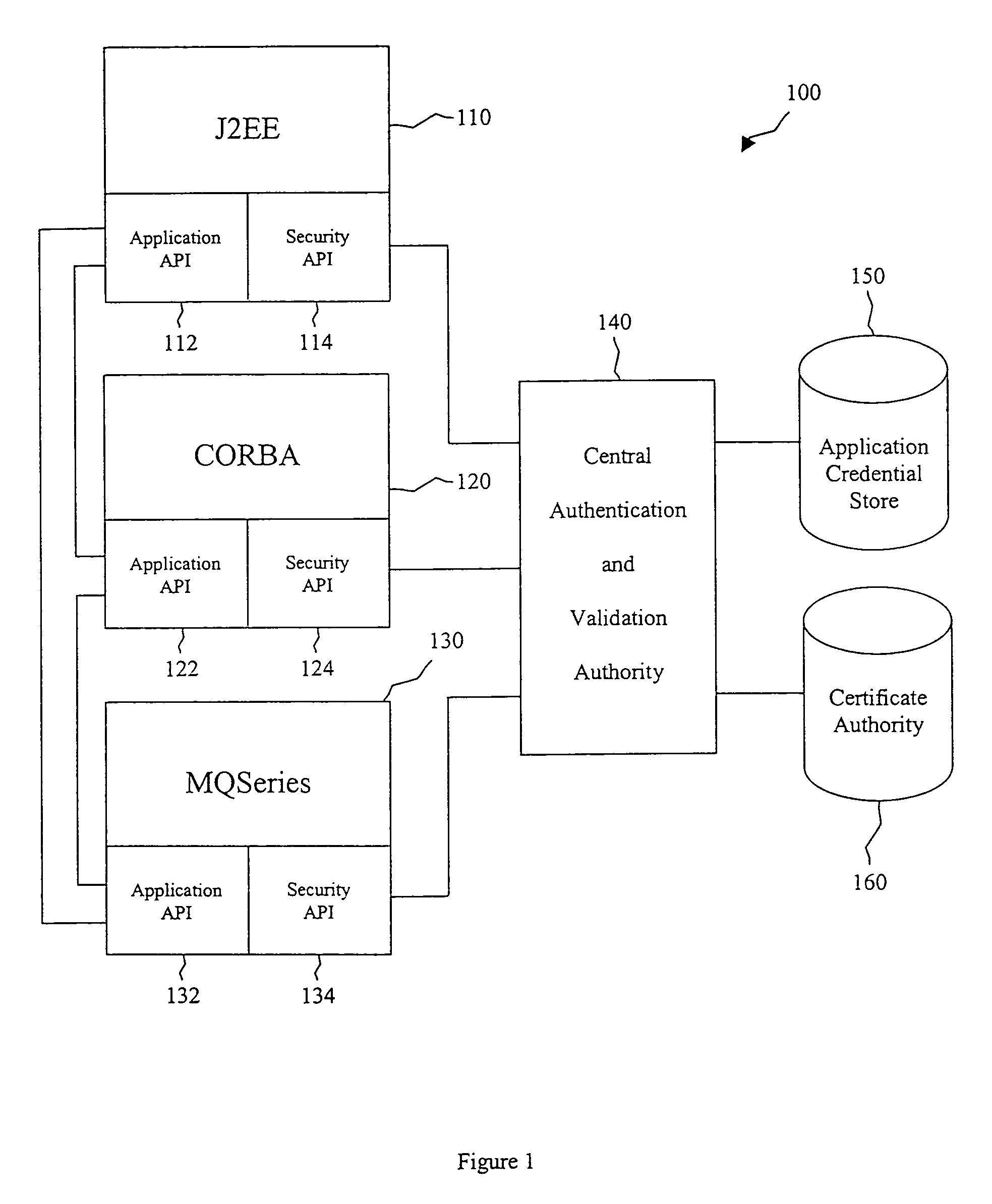
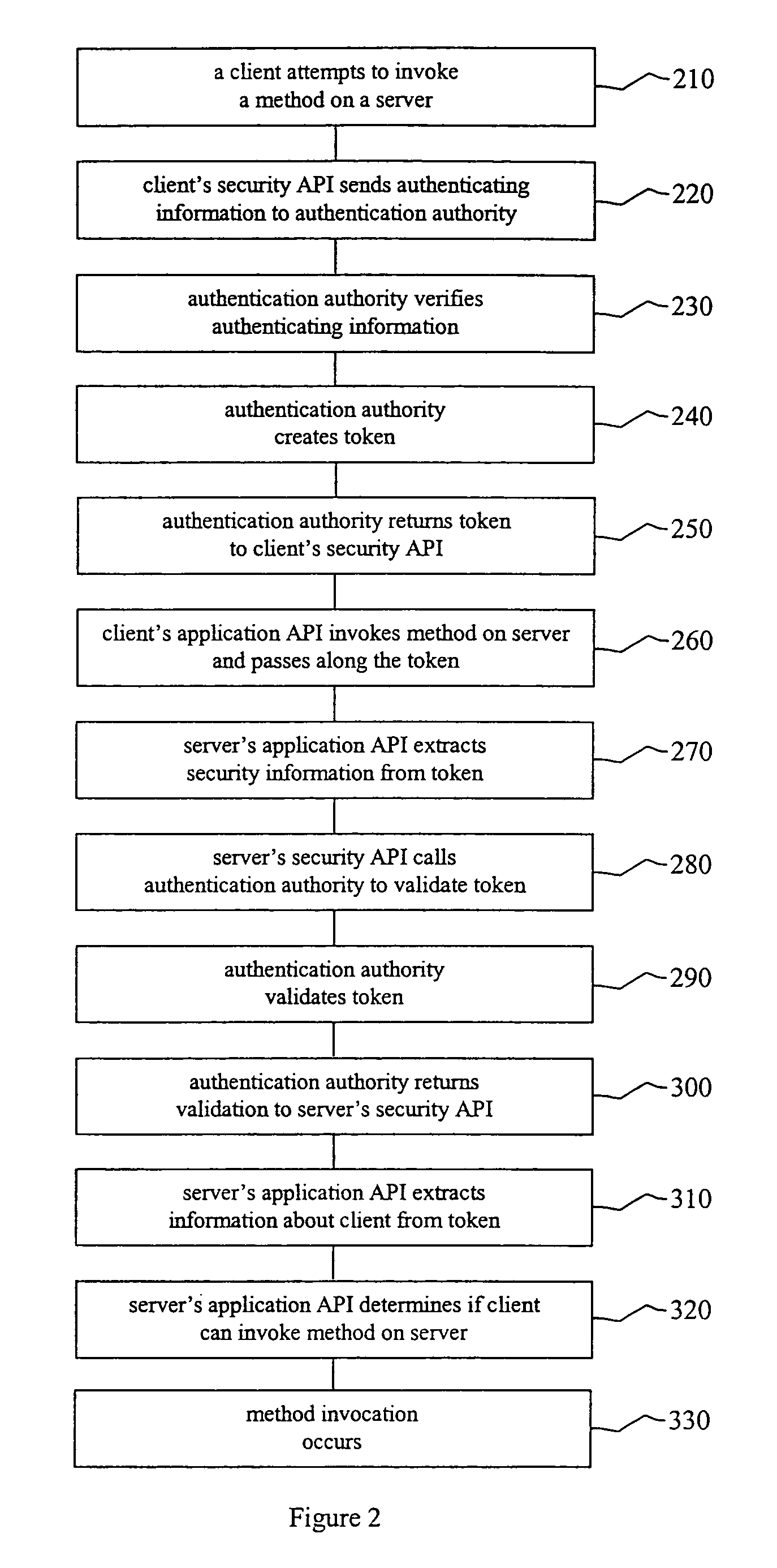
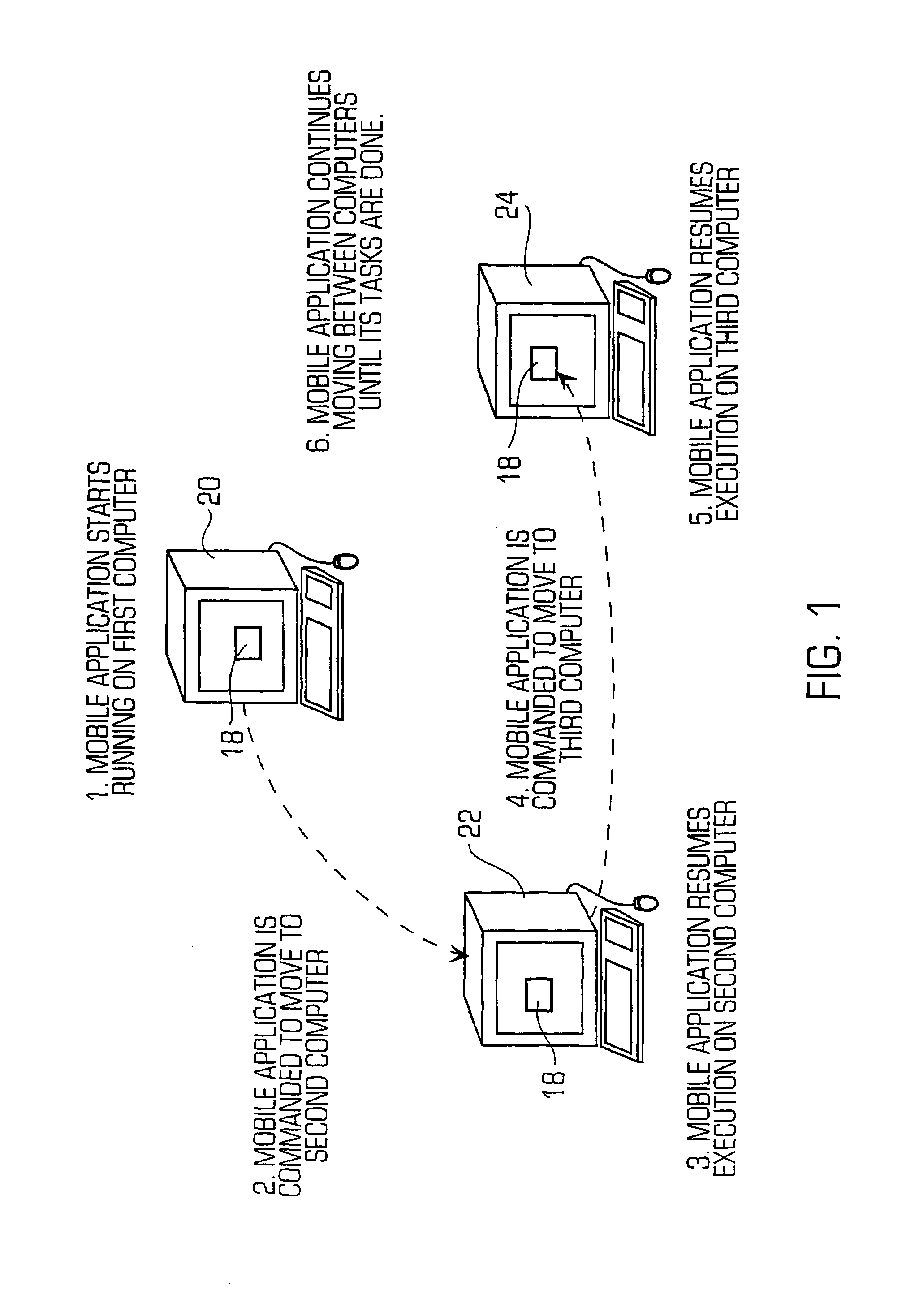
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
ActiveUS20040201604A1Digital computer detailsOffice automationDocumentation procedurePartial application
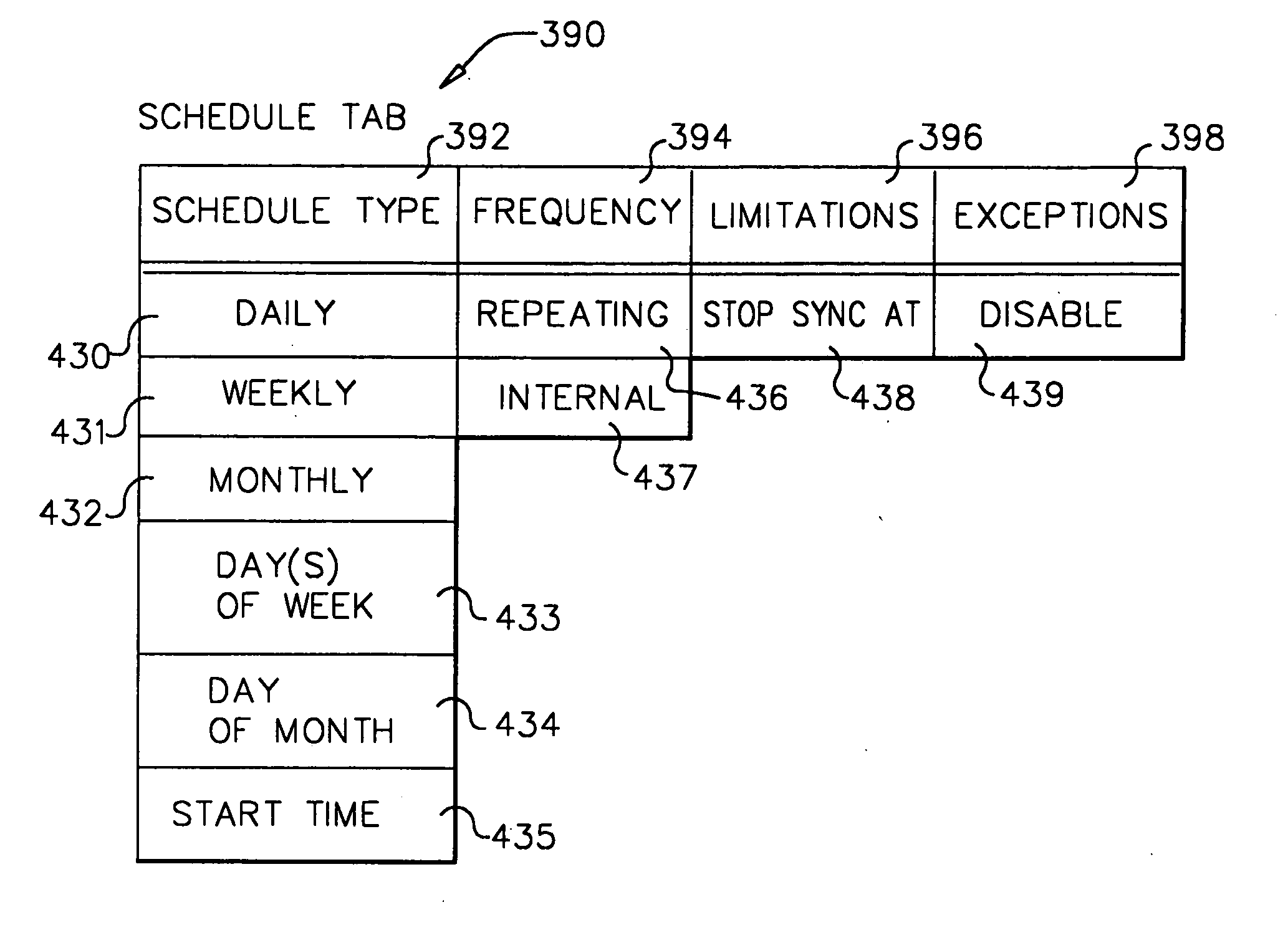
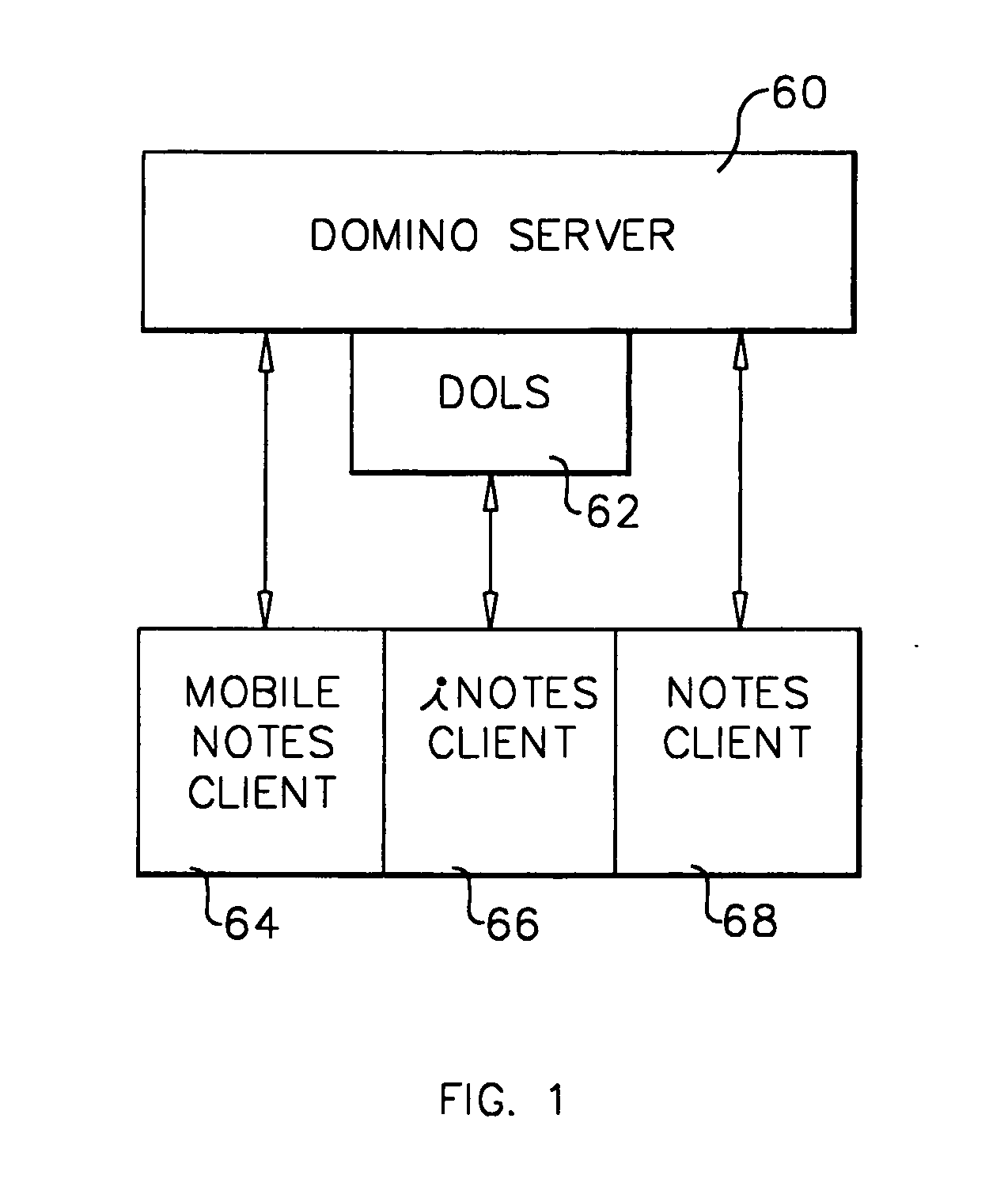
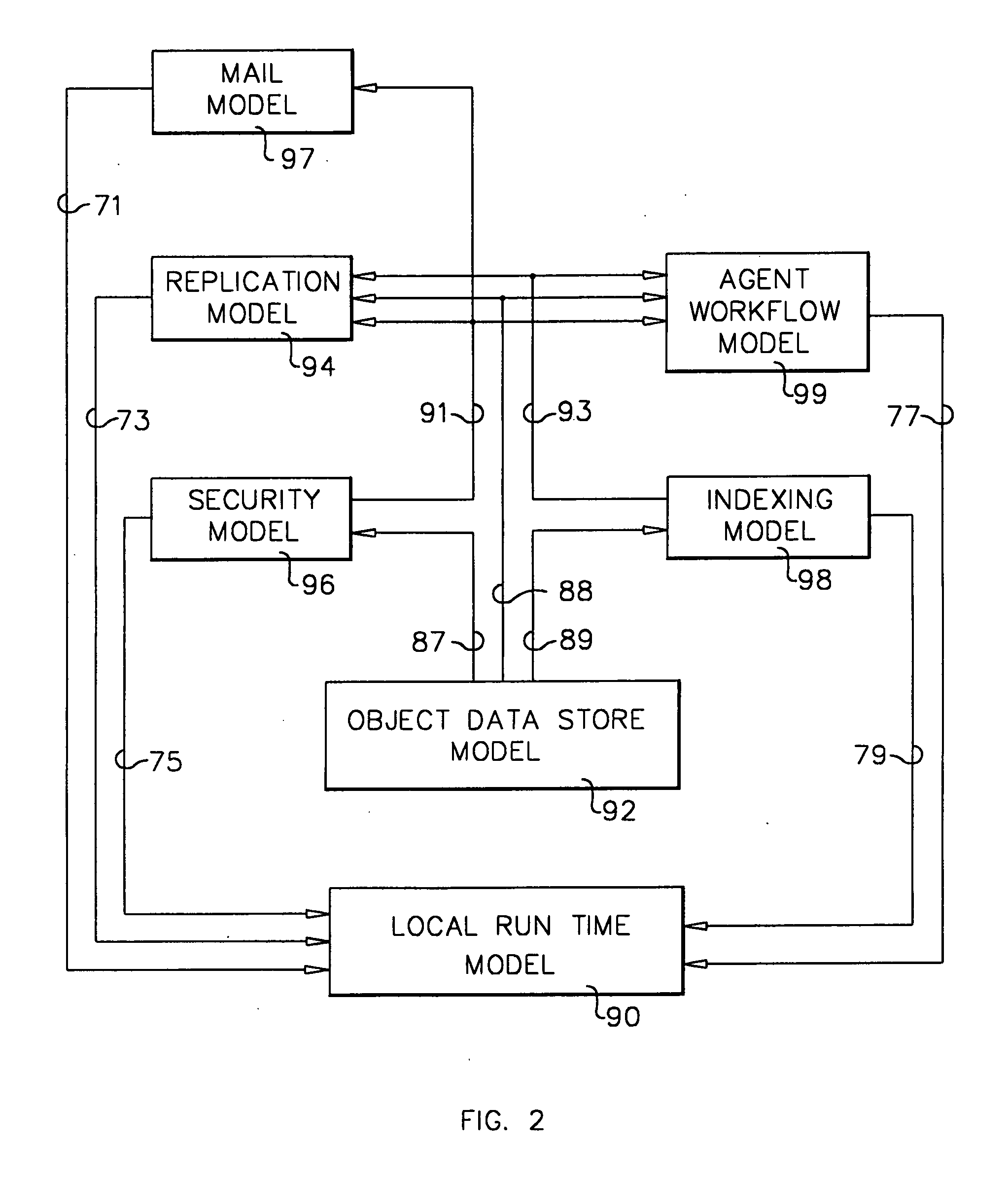
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and. remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
System and method of securing networks against applications threats
InactiveUS20080047009A1Easy to deployMinimal impactMemory loss protectionError detection/correctionWeb applicationInternet privacy
A system and method for protection of Web based applications are described. A Web application security system is included within a computer network to monitor traffic received from a wide area network, such as the Internet, and determine if there is a threat to the Web application. The Web application security system monitors web traffic in a non-inline configuration and identifies any anomalous traffic against a profile that identifies acceptable behavior of a user of the application. Any anomalous traffic is analyzed and appropriate protective action is taken to secure the Web application against an attack.
Owner:TRUSTWAVE HOLDINGS
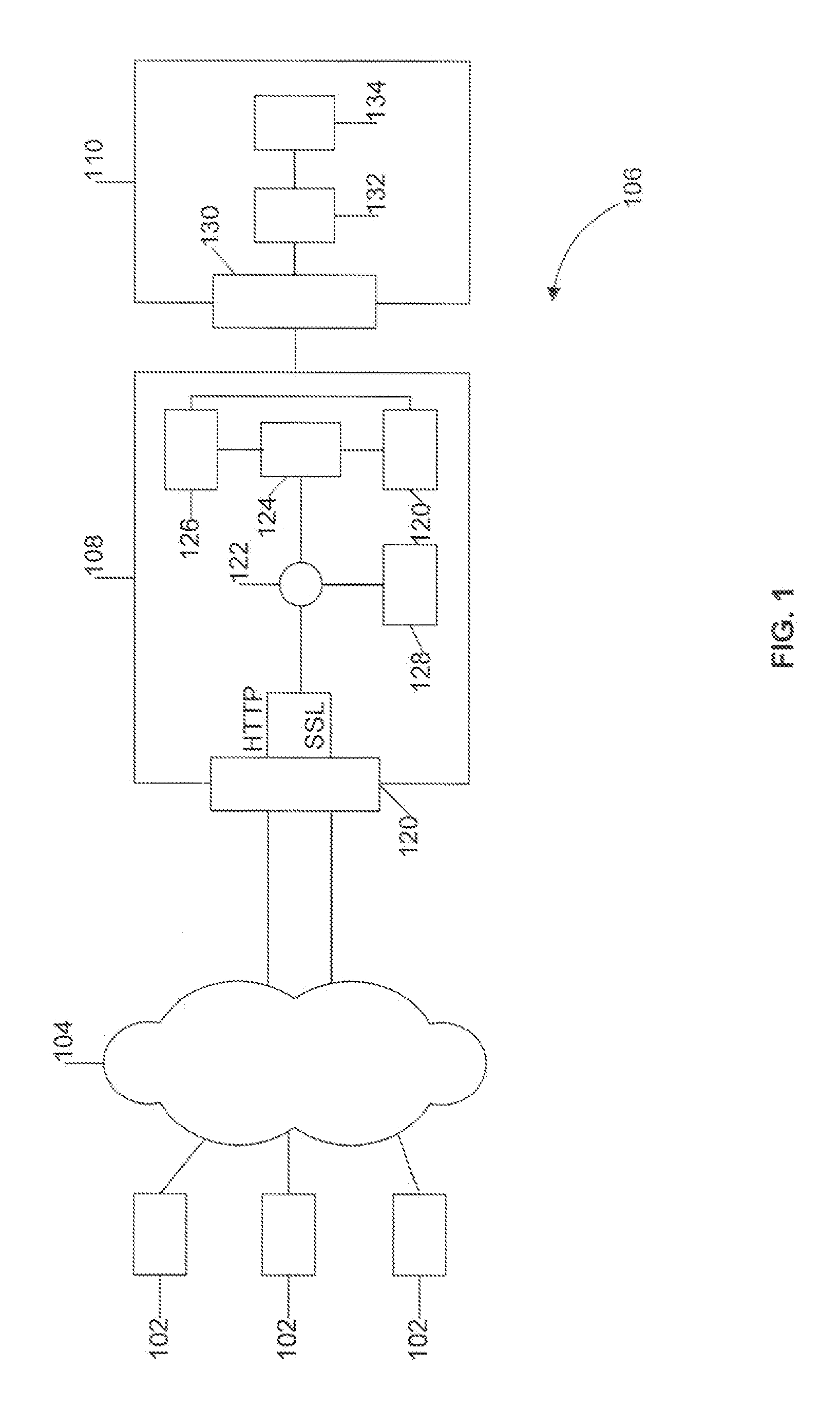
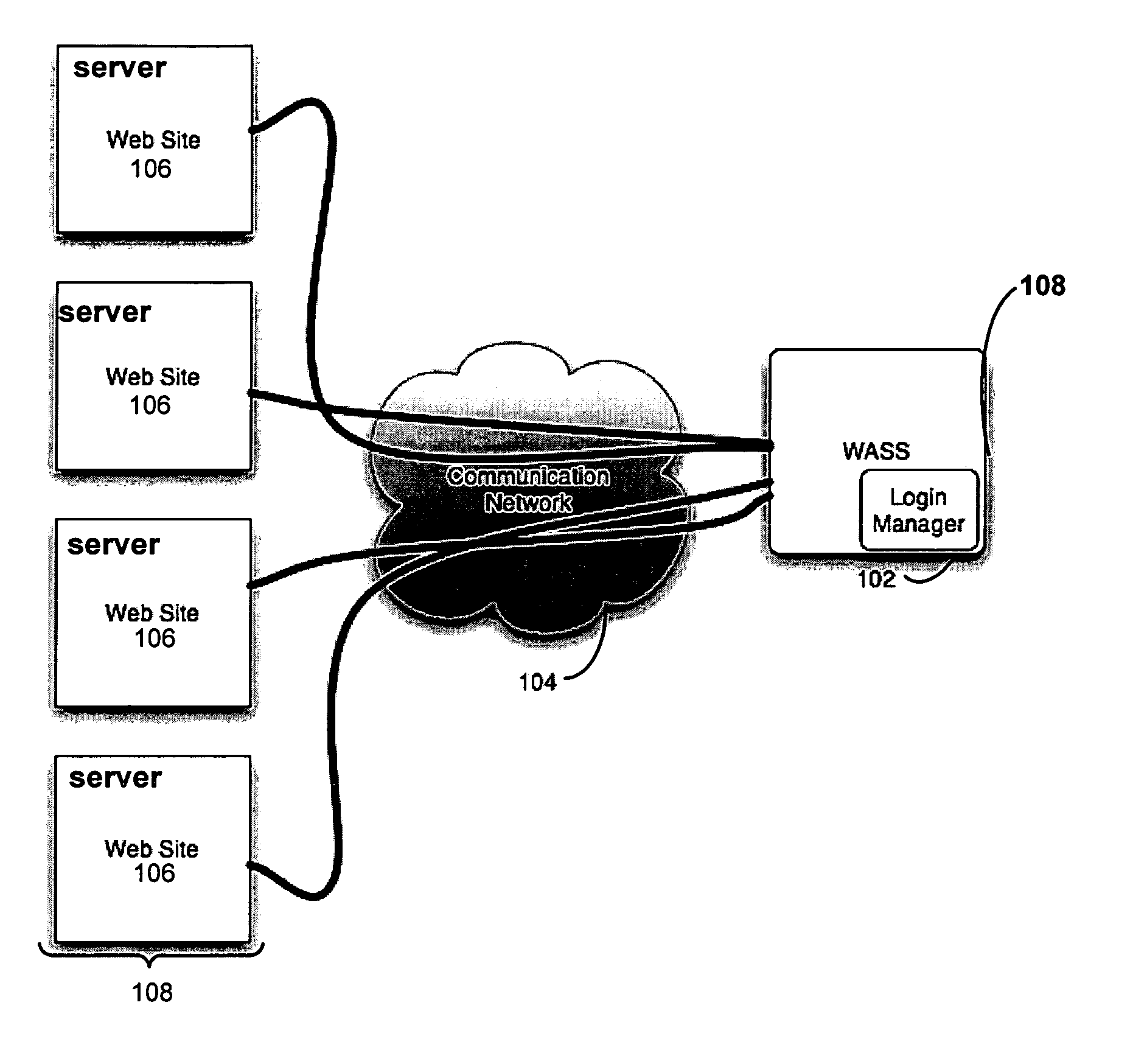
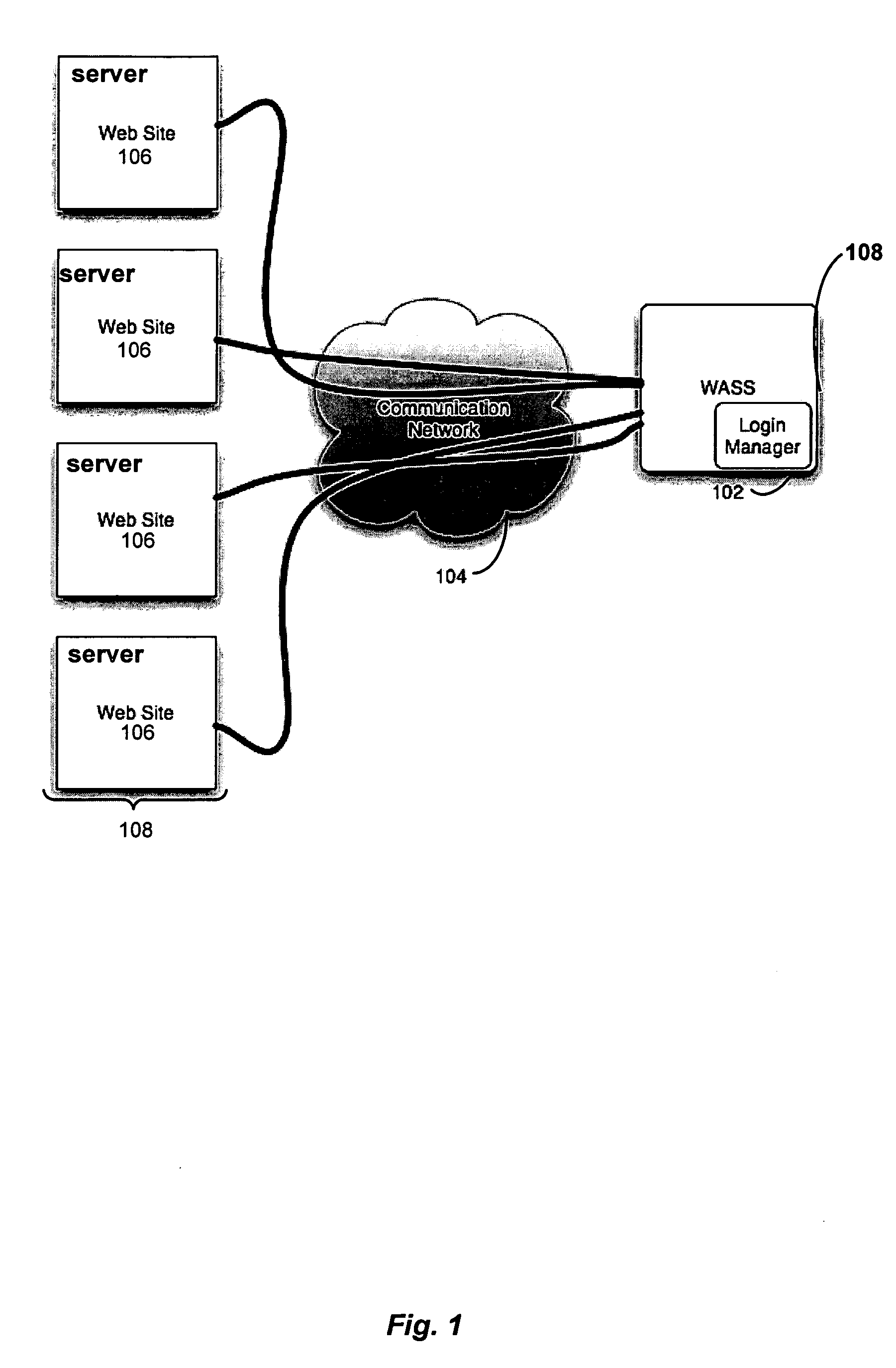
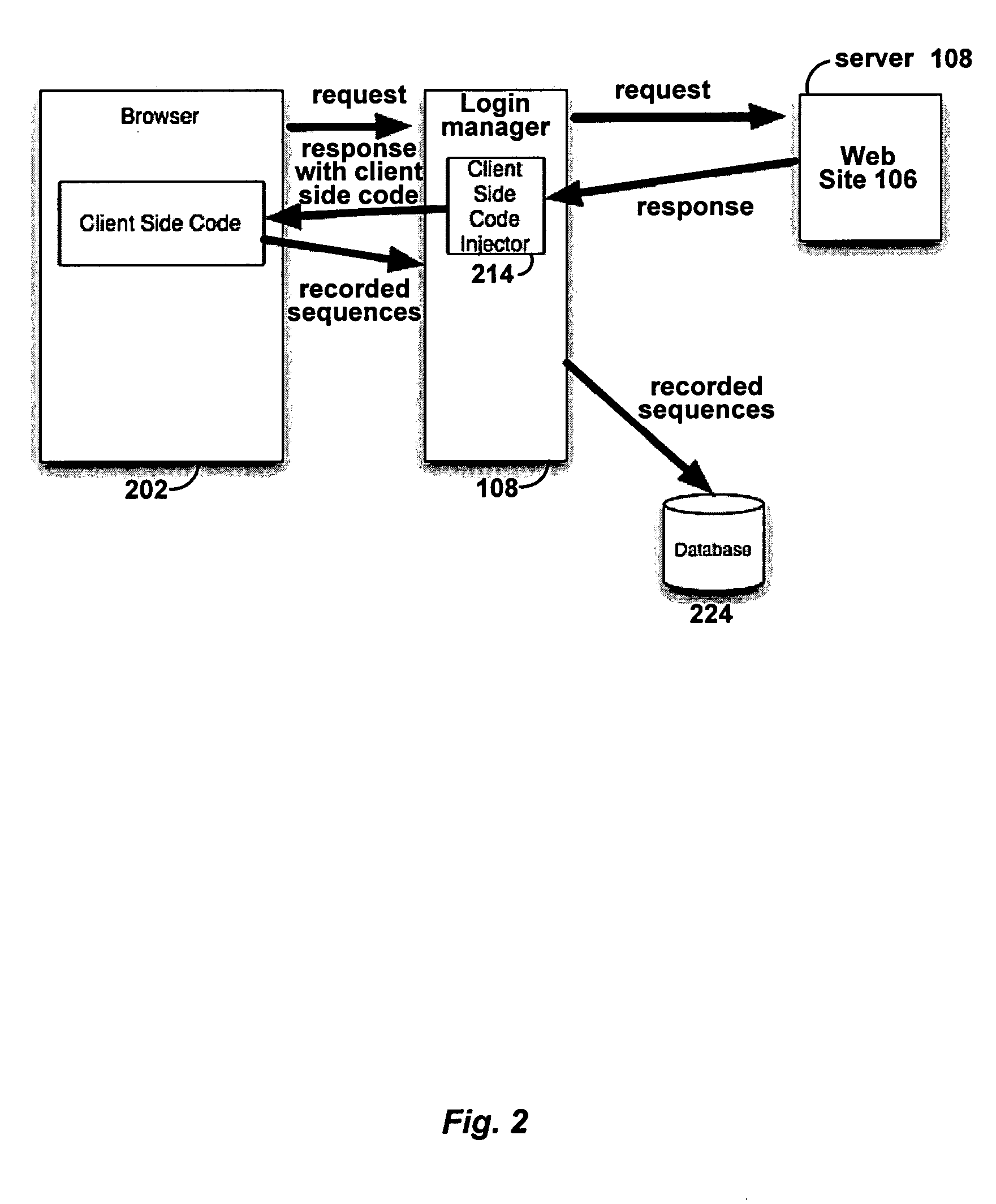
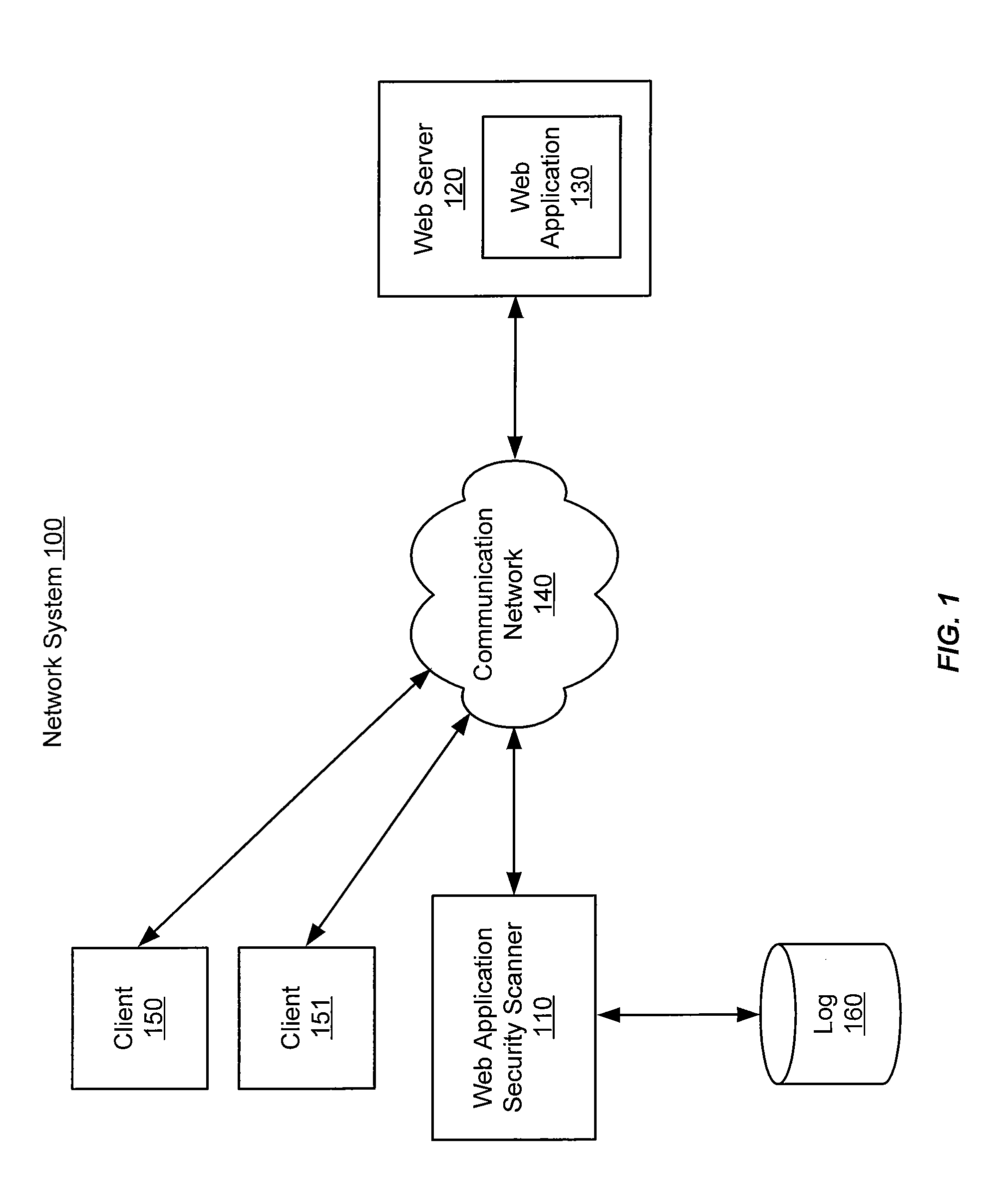
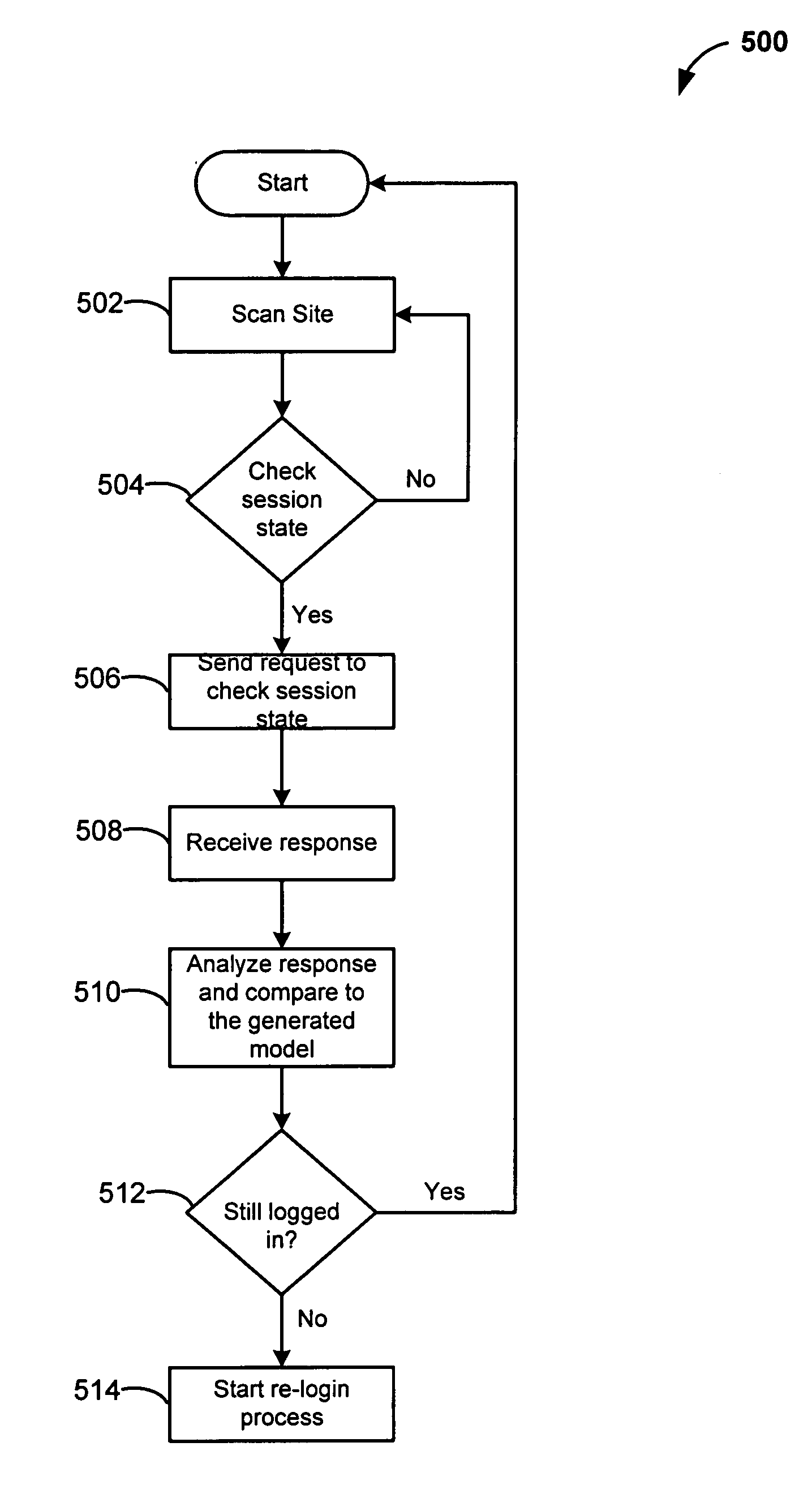
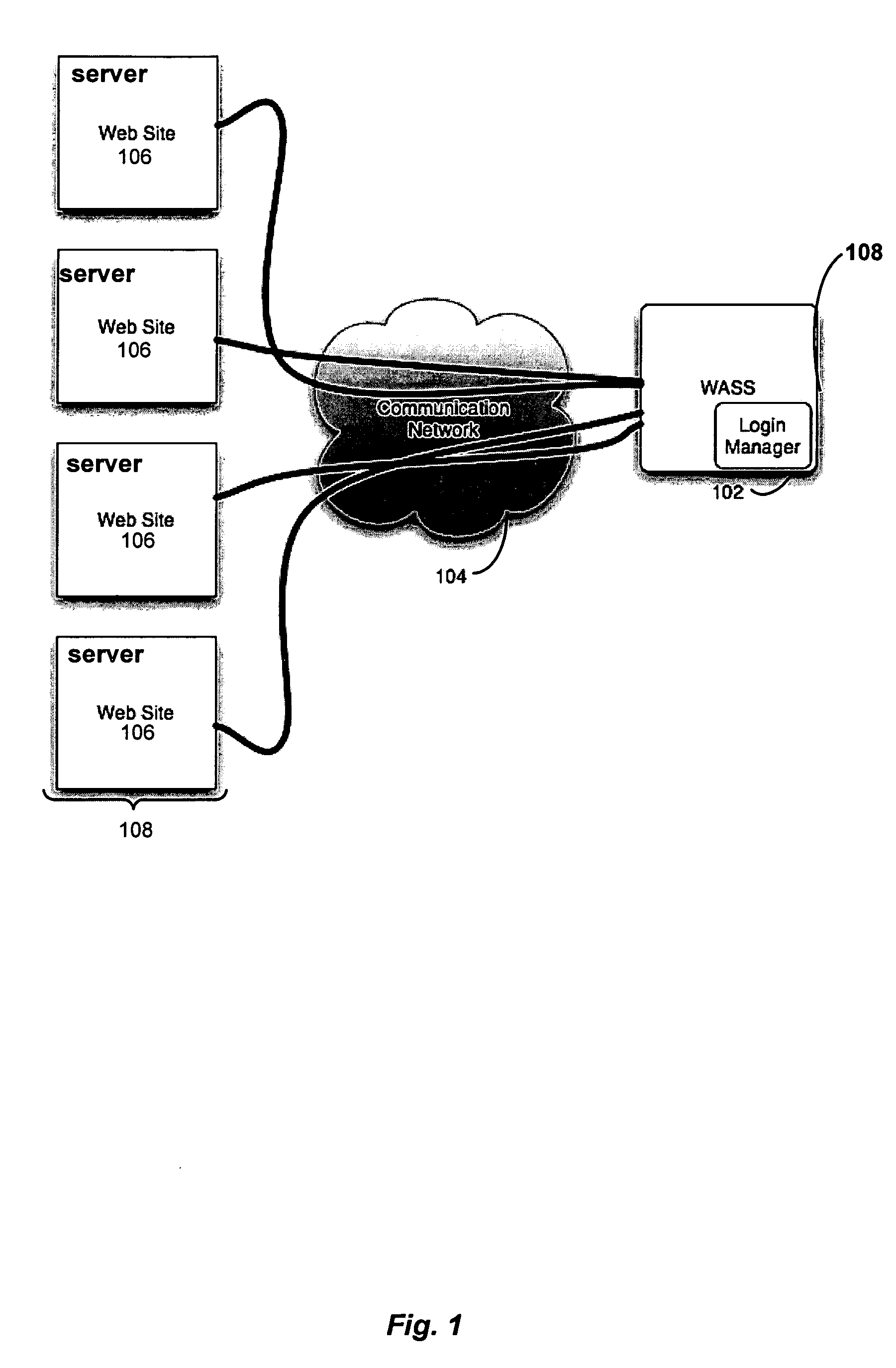
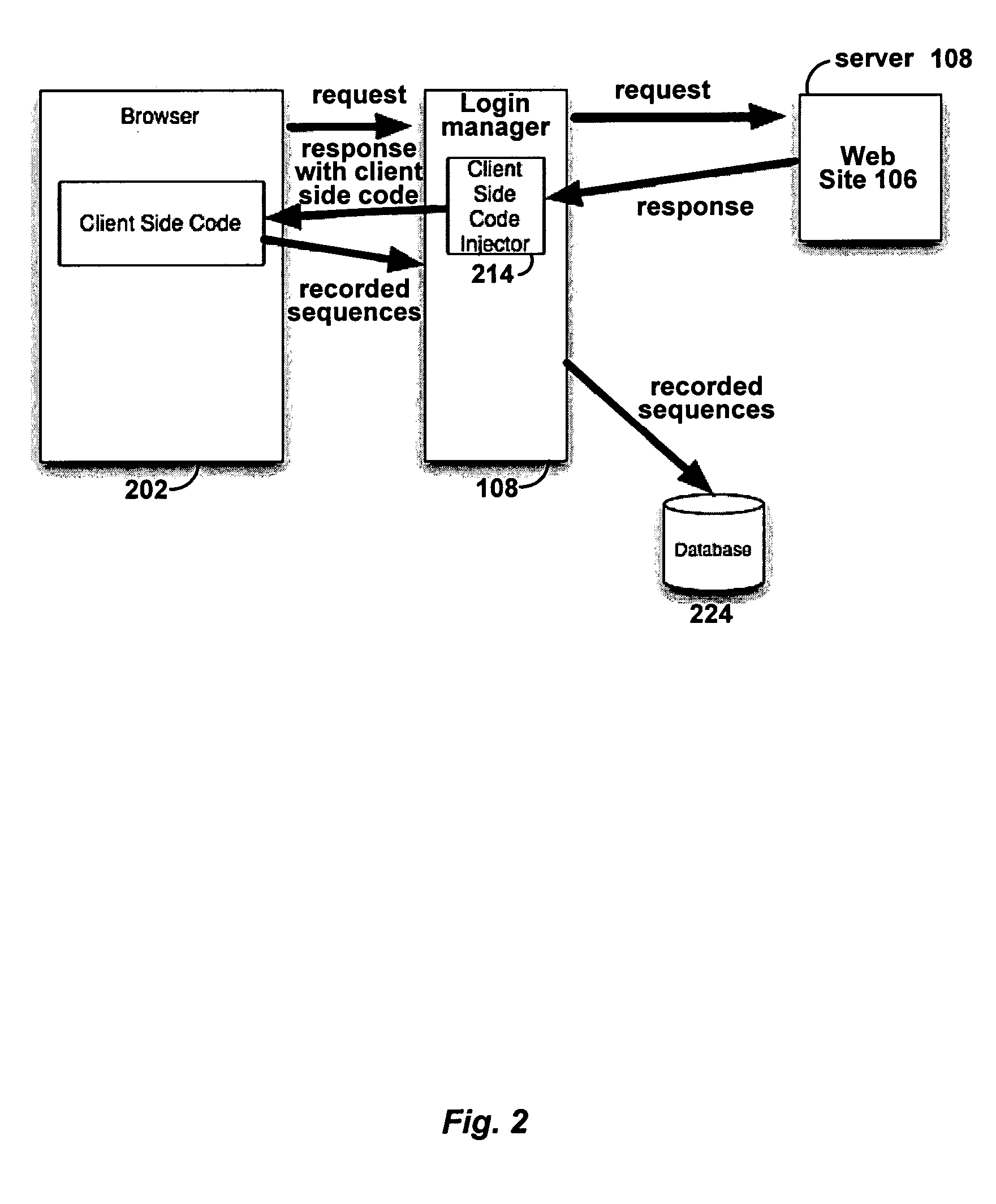
Automated login session extender for use in security analysis systems
ActiveUS20060048214A1Digital data processing detailsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
InactiveUS7219304B1Digital data processing detailsAnalogue secracy/subscription systemsDocumentation procedurePartial application
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
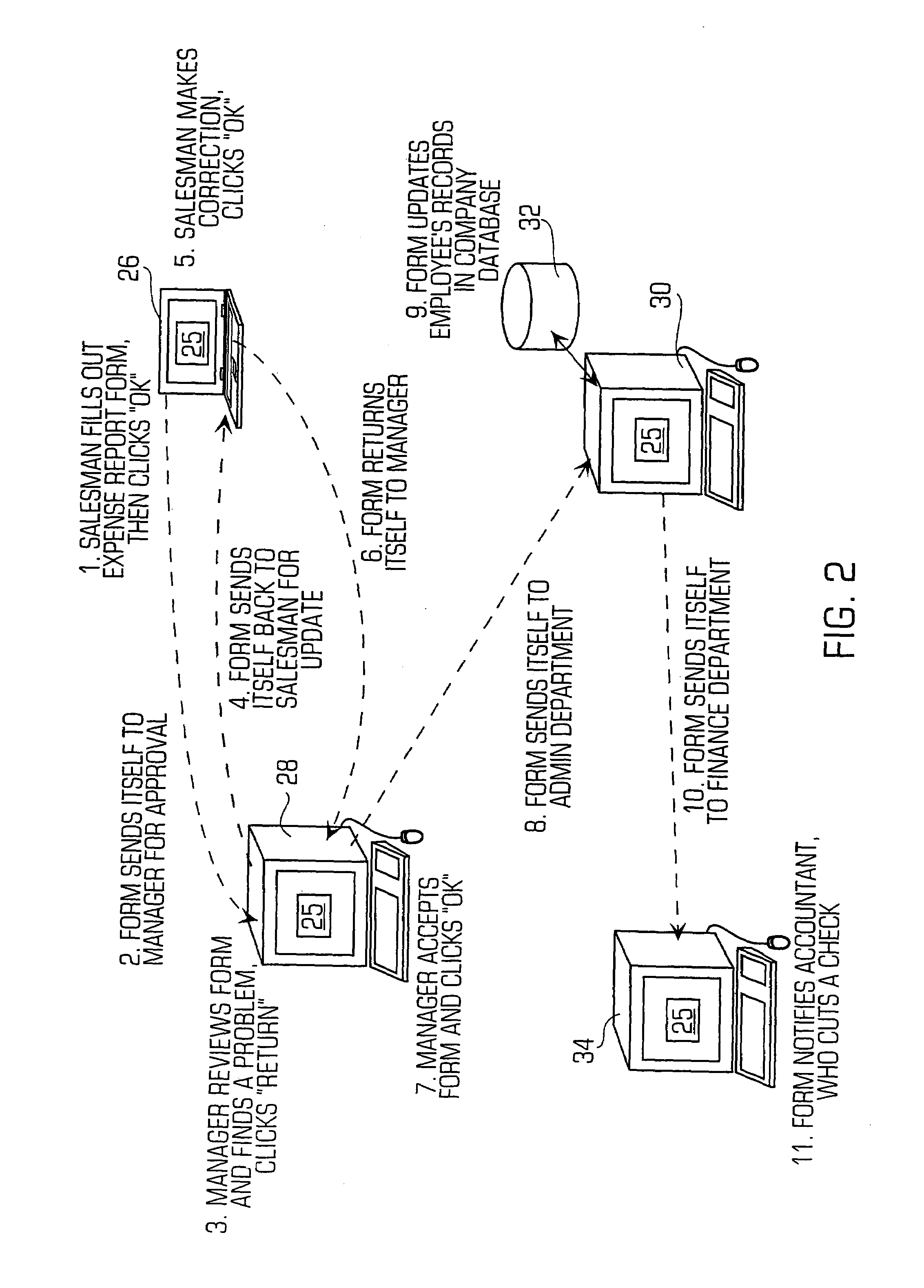
Application server providing personalized voice enabled web application services using extensible markup language documents
InactiveUS6901431B1Interconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingPersonalizationSpeech applications
A unified web-based voice messaging system provides voice application control between a web browser and an application server via an hypertext transport protocol (HTTP) connection on an Internet Protocol (IP) network. The application server, configured for executing a voice application defined by XML documents, selects an XML document for execution of a corresponding voice application operation based on a determined presence of a user-specific XML document that specifies the corresponding voice application operation. The application server, upon receiving a voice application operation request from a browser serving a user, determines whether a personalized, user specific XML document exists for the user and for the corresponding voice application operation. If the application server determines the presence of the personalized XML document for a user-specific execution of the corresponding voice application operation, the application server dynamically generates a personalized HTML page having media content and control tags for personalized execution of the voice application operation; however if the application server determines an absence of the personalized XML document for the user-specific execution of the corresponding voice application operation, the application server dynamically generates a generic HTML page for generic execution of the voice application operation. Hence, a user can personalize any number of voice application operations, enabling a web-based voice application to be completely customized or merely partially customized.
Owner:CISCO TECH INC
Method for enhancing network application security
InactiveUS8302170B2Improve securityDigital data processing detailsUser identity/authority verificationSecure communicationEmbedded security
Owner:RICHEMONT INT
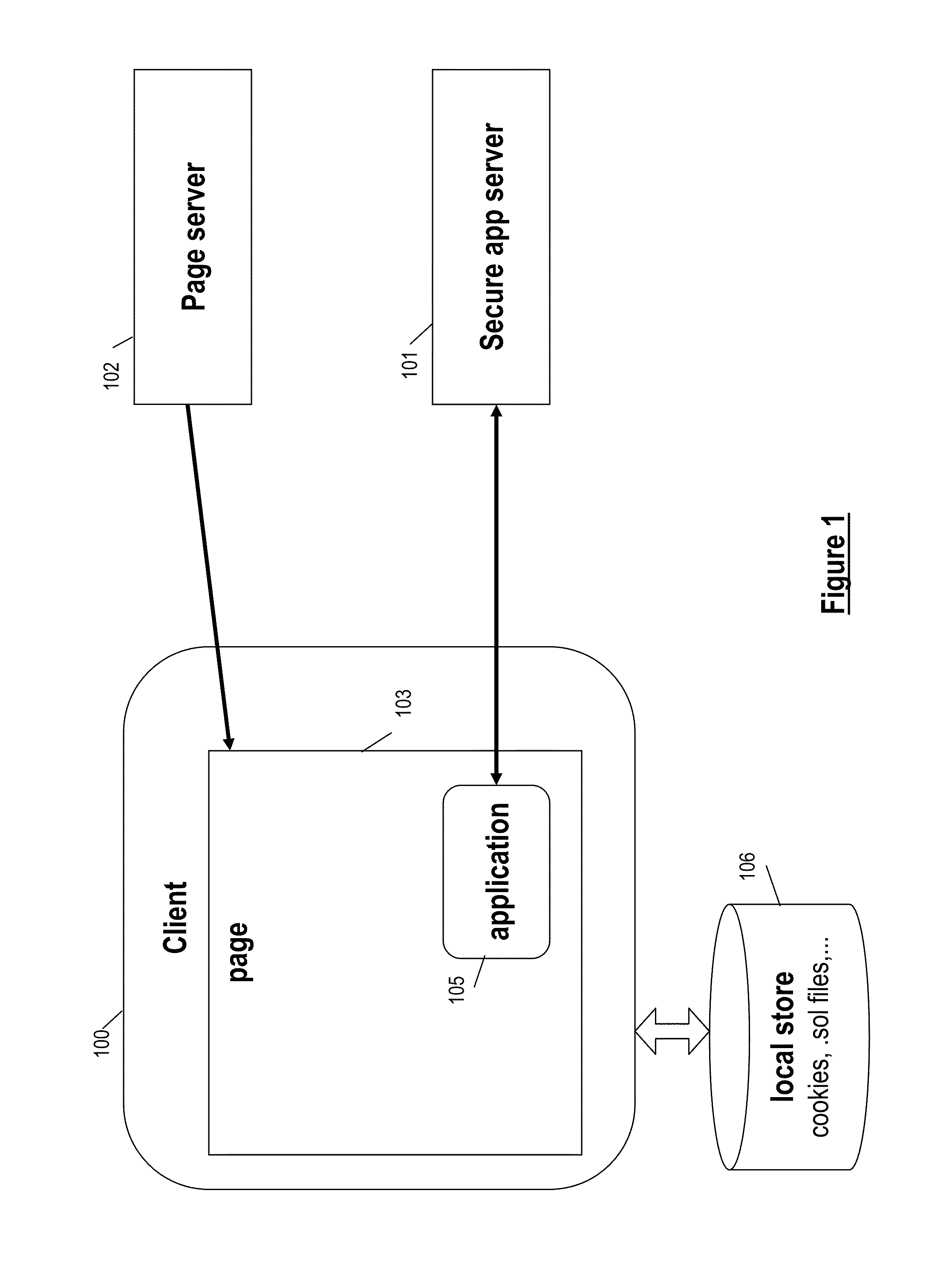
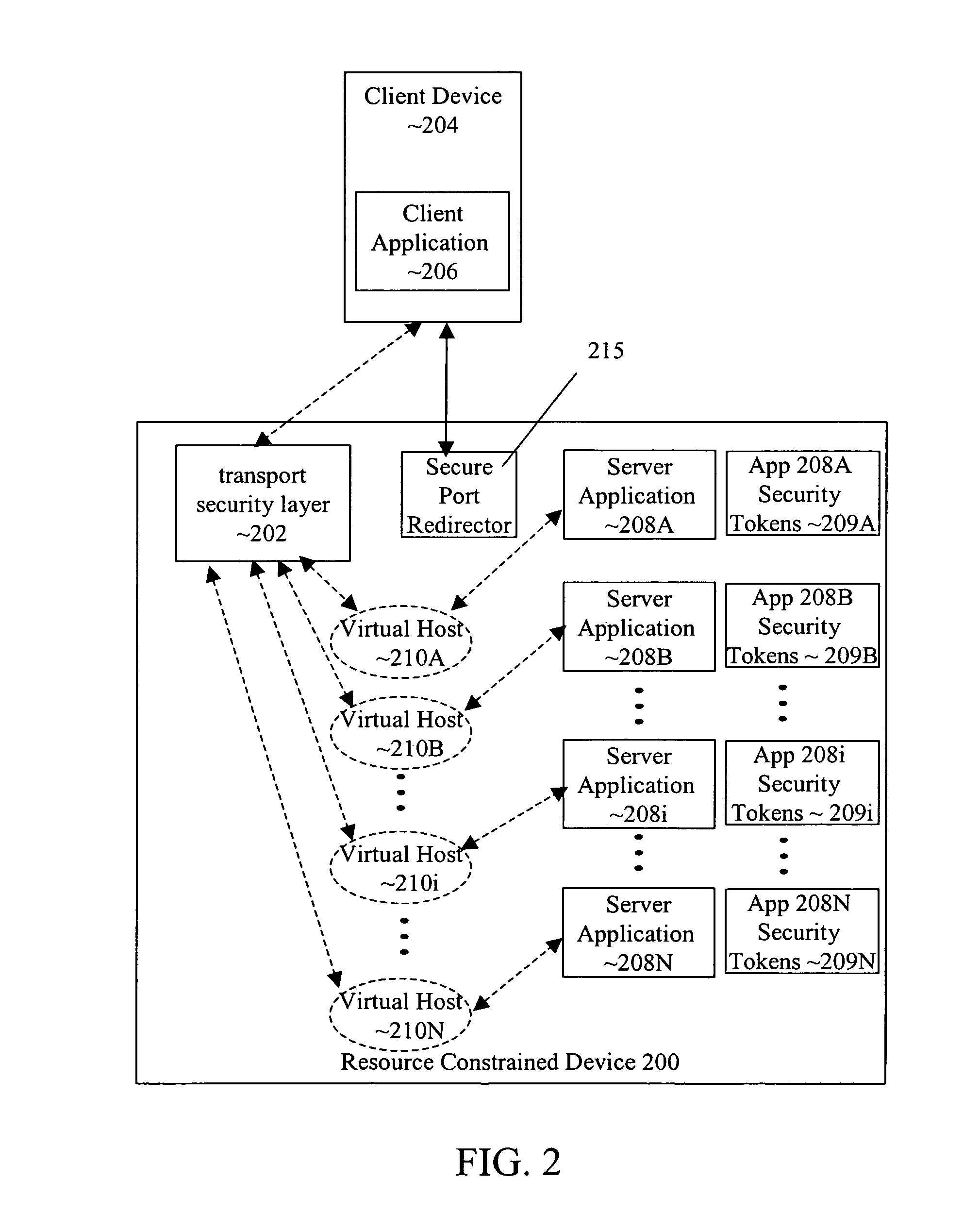
Transport-level web application security on a resource-constrained device
ActiveUS8245285B1Facilitates secure communicationFacilitate communicationDigital data processing detailsMultiple digital computer combinationsSecure communicationClient-side
A system and method is provided to facilitate secure communications for a server-application executing on a resource-constrained device. A request, from a client application executing on a client device to access a server application executing on the resource-constrained device is received on an application-specific secure port of a resource-constrained device. The request is authenticated using a security token stored in an application context of the server application. The authentication is performed by a transport security layer protocol executing within the application context of the server application. The security token is specific for the server application. A secure connection is established directly between the secure port and the client application upon the authentication being successful.
Owner:ORACLE INT CORP
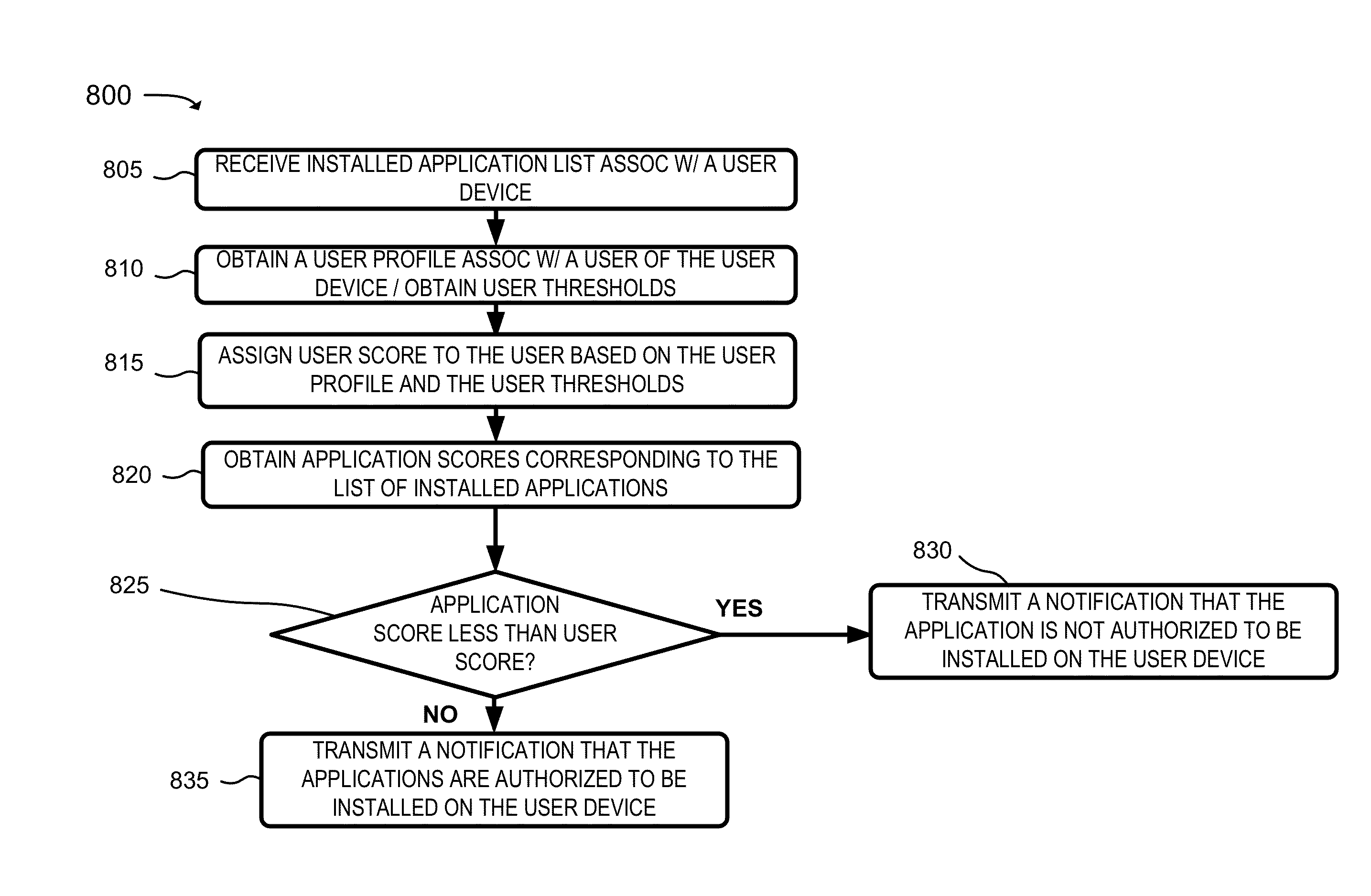
Mobile application security and management service
A system is configured to receive a list of applications installed on a user device; obtain application profiles that identify risk levels associated with the applications; obtain a user profile that identifies a job level, security risk level, or an access level to confidential information associated with the user of the user device; identify a highest risk level authorized for the user device based on whether the job level is greater than a first threshold, the security risk level is greater than a second threshold, or the access level is greater than a third threshold; determine whether any of the risk levels are greater than the highest risk level; and transmit a notification that one of the applications is to be removed from the user device when one of the risk levels, associated with the one of the applications, is greater than the highest risk level.
Owner:VERIZON PATENT & LICENSING INC
Security for WAP servers
ActiveUS7472413B1Digital data processing detailsMultiple digital computer combinationsApplication serverWeb application
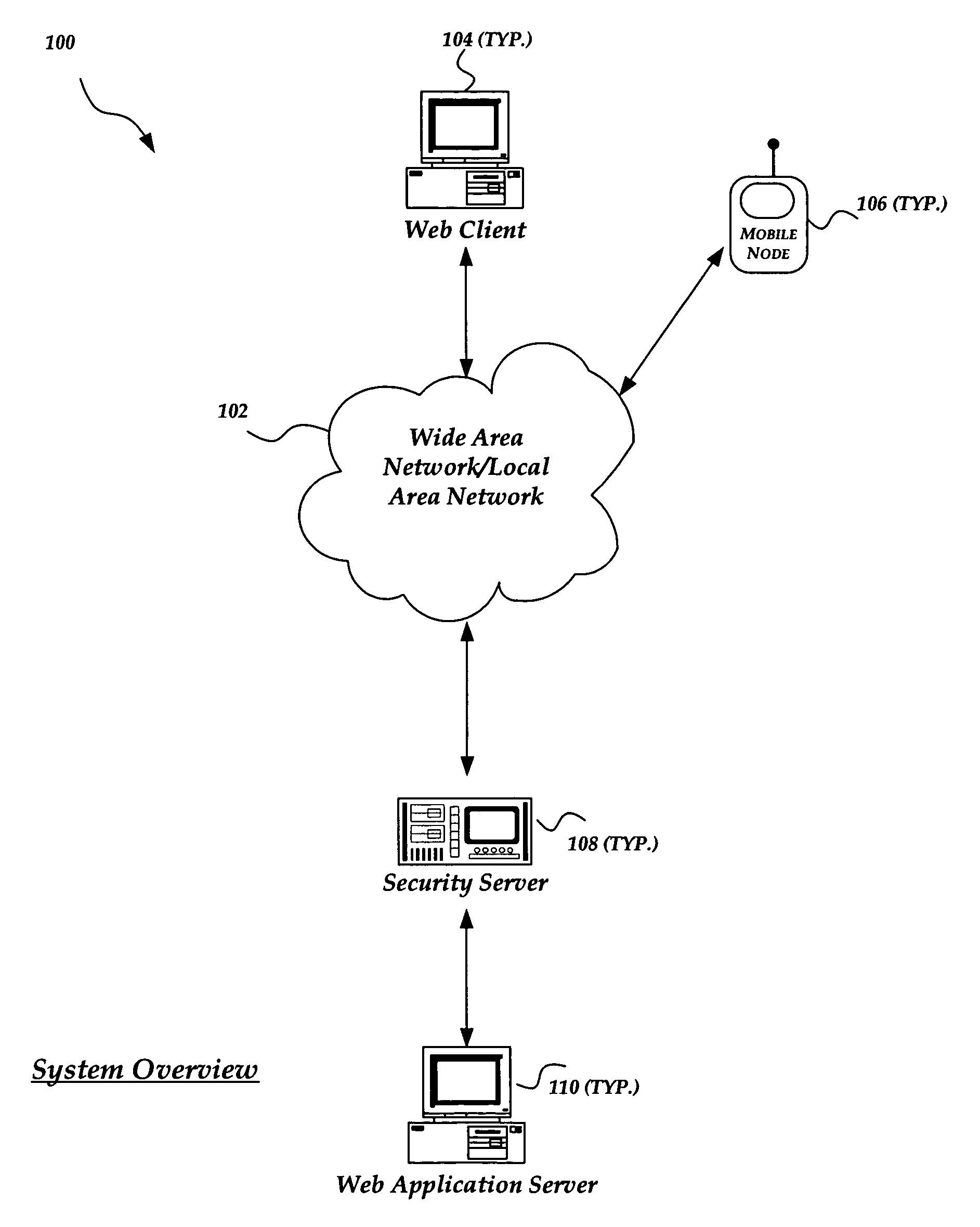
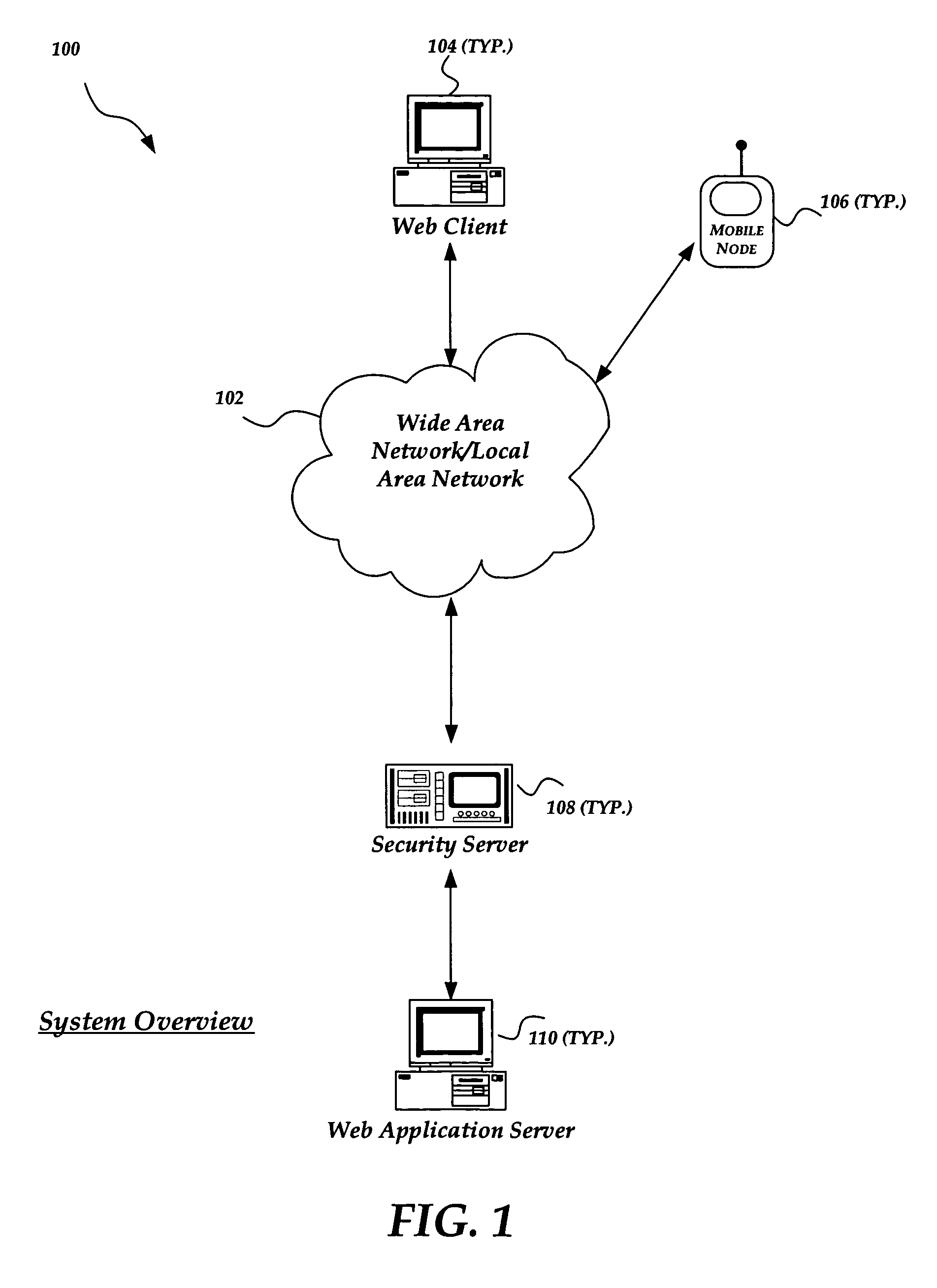
A method and system for improving the security and control of internet / network web application processes, such as web applications. The invention enables validation of requests from web clients before the request reaches a web application server. Incoming web client requests are compared to an application model that may include an allowed navigation path within an underlying web application. Requests inconsistent with the application model are blocked before reaching the application server. The invention may also verify that application state data sent to application servers has not been inappropriately modified. Furthermore, the invention enables application models to be automatically generated by employing, for example, a web crawler to probe target applications. Once a preliminary application model is generated it can be operated in a training mode. An administrator may tune the application model by adding a request that was incorrectly marked as non-compliant to the application model.
Owner:F5 NETWORKS INC
Mobile application security system and method
ActiveUS20130014248A1Digital data processing detailsUnauthorized memory use protectionInternet privacyApplication security
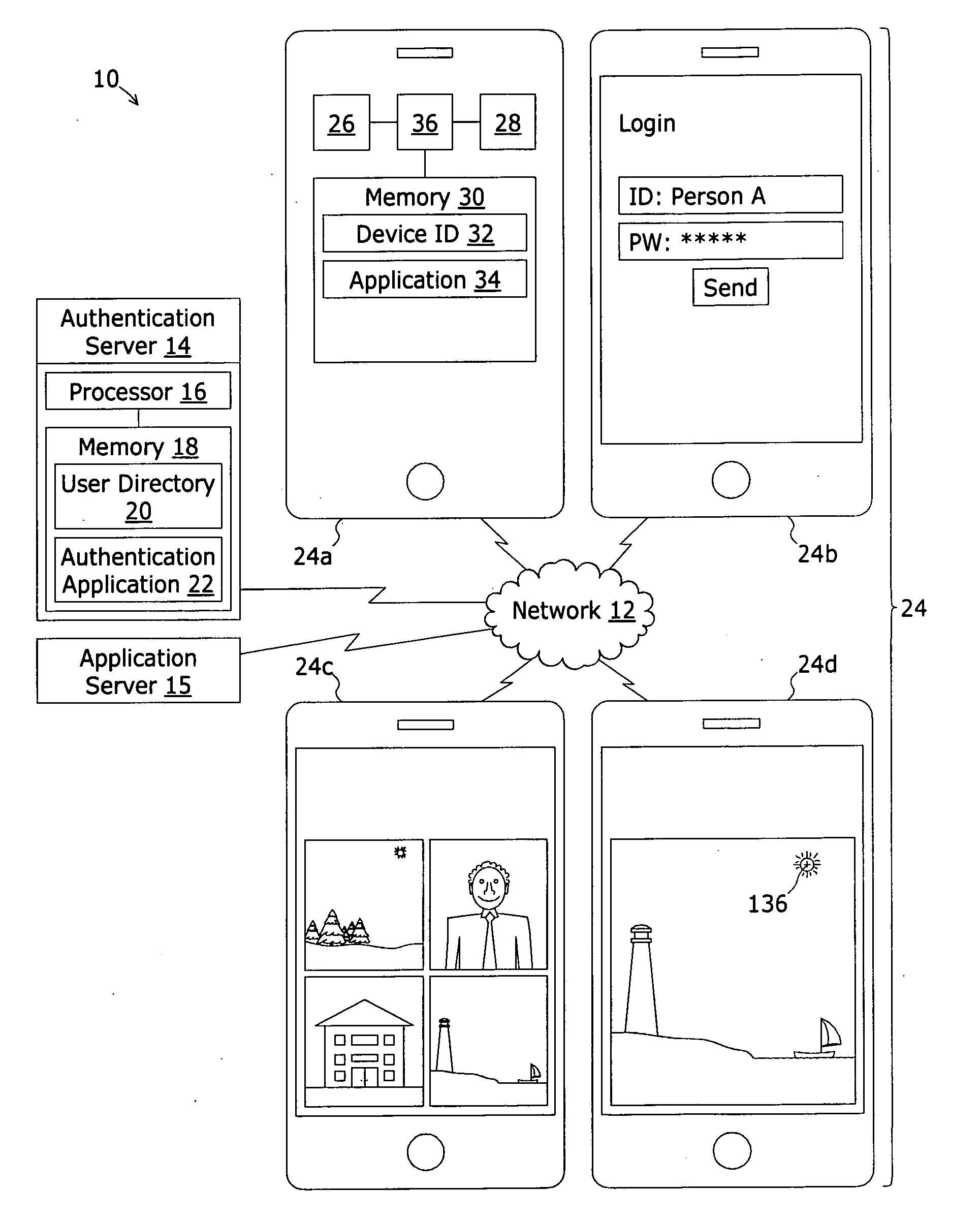
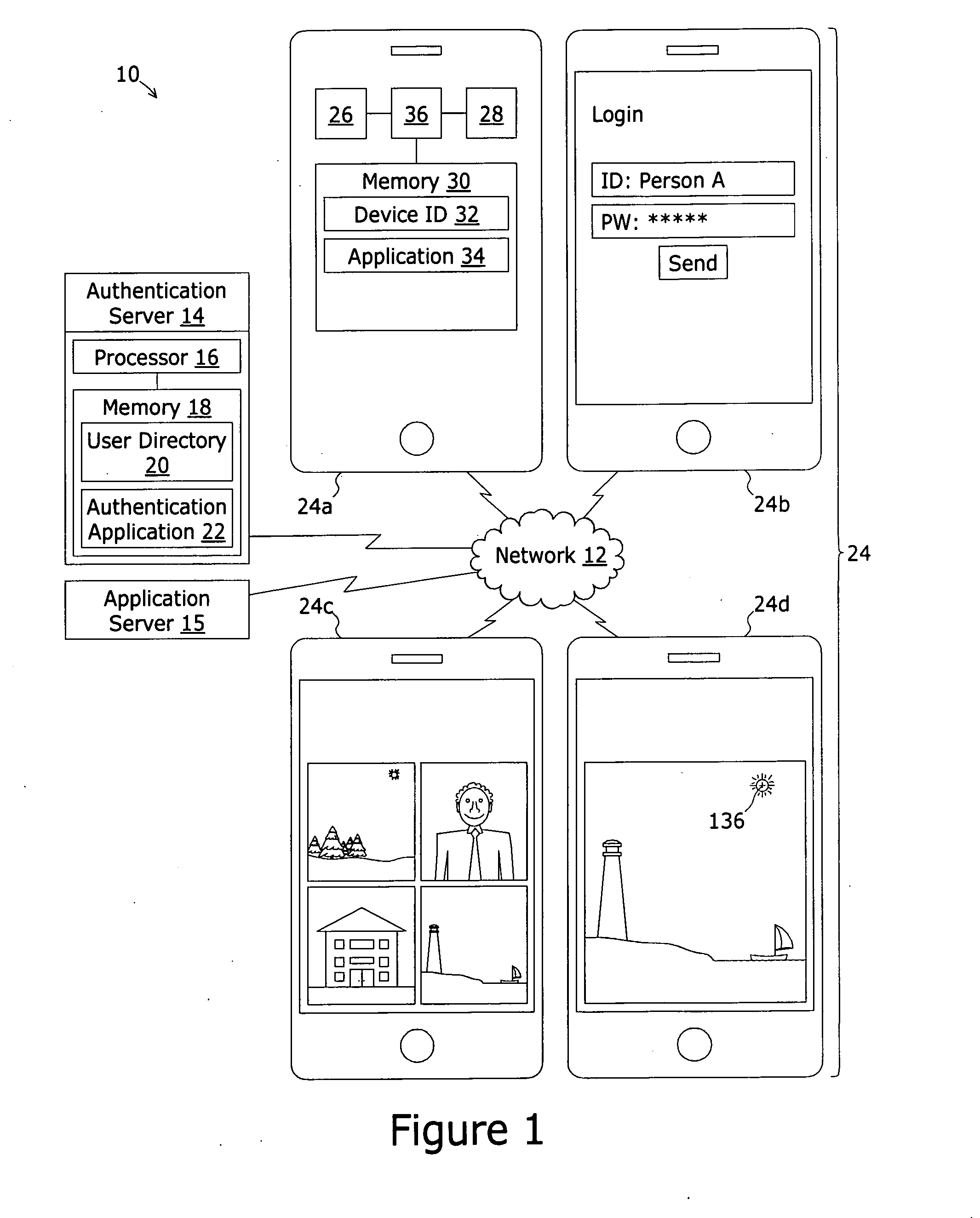
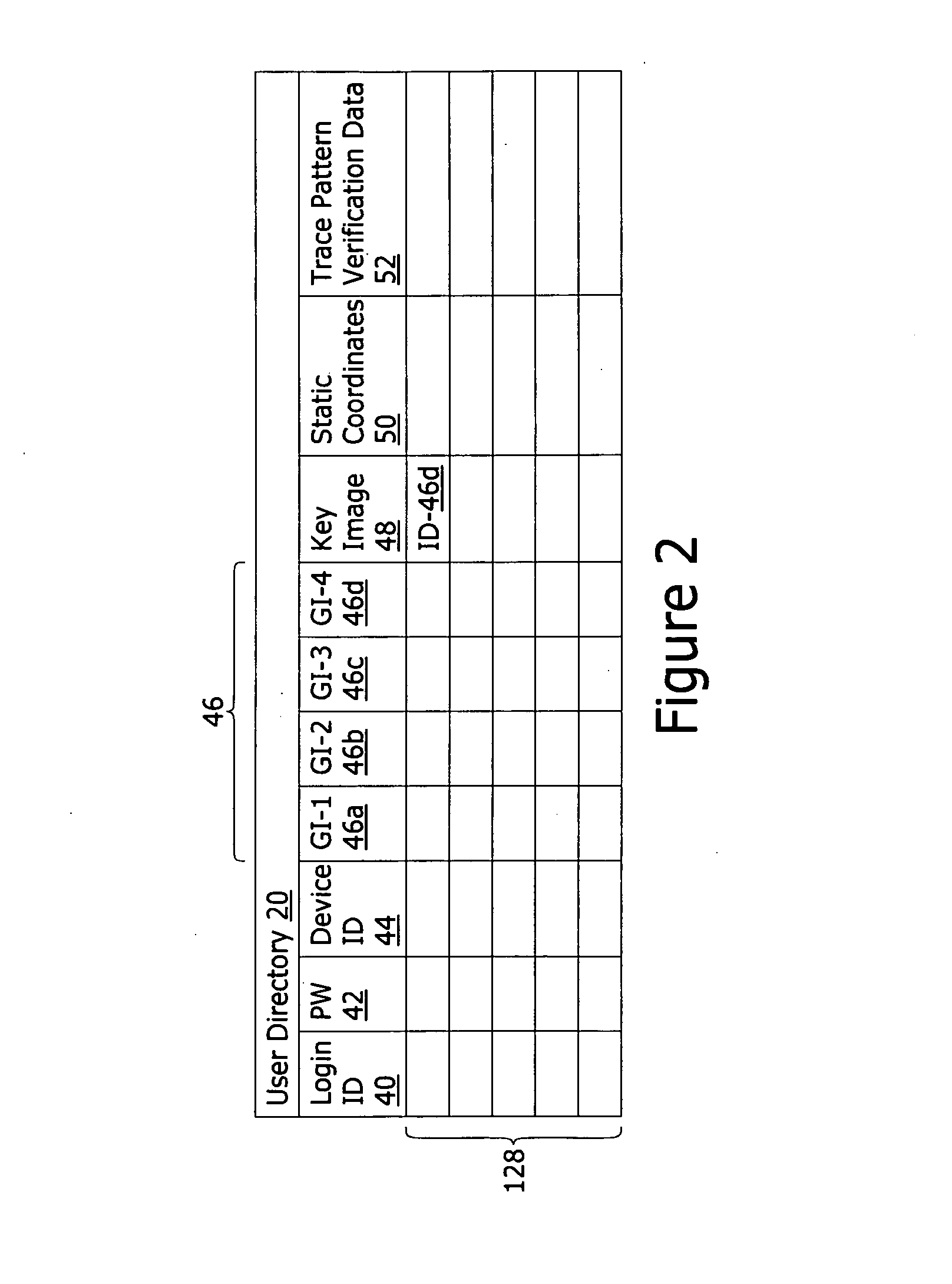
A system for authenticating the user of a computing device comprises an authorized user directory. Each record is uniquely associated with an authorized user and includes at least a computing device ID value that is a globally unique value assigned to the authorized user's computing device, a group of unique depictions such as photographs, an identification of a key depiction. Portions of each image form fiducials recognizable by the user. The record further includes trace pattern verification data representing continuous trace strokes between pairs of the fiducials within the key depiction. To authenticate, the group of images are displayed to the user. The user must first select the key image and secondly trace continuous trace strokes between the pairs of fiducials to match the trace pattern verification data.
Owner:BOTTOMLINE TECH
Method for enhancing network application security
InactiveUS20100077216A1Improve securityDetection valueDigital data processing detailsUser identity/authority verificationSecure communicationEmbedded security
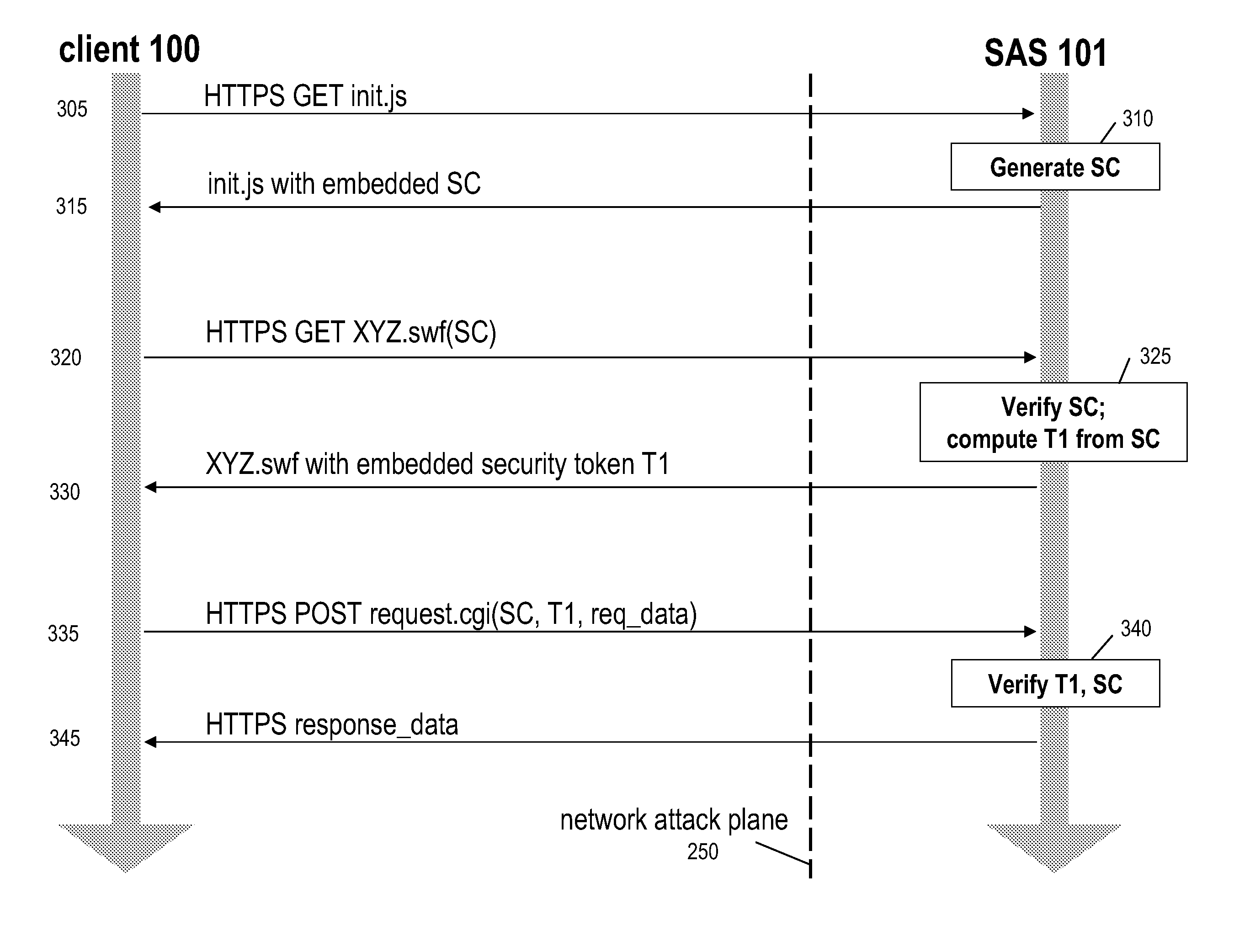
A method for securing communications between a server and an application downloaded over a network onto a client of the server is disclosed. A first request is received from the client, and in response a session credential security token is generated and sent to the client. A second request is received from the client to download the application and includes the value of the session credential security token. The server verifies that the value of the session credential security token is valid and, if so, generates a second security token that is tied to the session credential security token. The second token is embedded in application code and then the application code is sent to the client. A subsequent request for data from the application running on the client includes the value of the session credential security token and the value of the embedded security token. Verification of validity of the values of the session credential security token and the second security token received with the data request then occurs at least in part by determining that the values are cryptographically tied to one another. Upon verification, the requested data is sent to the client.
Owner:RICHEMONT INT
Application-to-application security in enterprise security services
ActiveUS7823192B1Provide securityDigital data processing detailsUser identity/authority verificationCharacter String Data TypeApplication software
The present system allows disparate secure applications to communicate directly with one another in a heterogeneous application environment by providing for the creation of tokens that can be passed between the applications without human intervention. Security information is passed between applications in the form of a token with a string data type. Since a string is a primitive data type, it can be recognized by a large number of applications and interfaces. The token has no header and therefore no application-specific header configuration, making it platform and technology independent. This eliminates the need for conversion of security information between different formats. The use of tokens also eliminates the need for an application to be authenticated and authorized every time it sends a message to another application. Instead of a permanent context or session, a context is created with every invocation from one application to another.
Owner:T MOBILE INNOVATIONS LLC
Using fuzzy classification models to perform matching operations in a web application security scanner
A system provides for fuzzy classification in comparisons of scanner responses. A web application test suite performs tests against a web application by sending client requests from a testing computer to the server running the web application and checking how the web application responds. A thorough web application security scan might involve thousands of checks and responses. As a result, some sort of programmatic analysis is needed. One such evaluation involves comparing one response against another. Response matching that compares two HTTP responses might use fuzzy classification processes.
Owner:SYNOPSYS INC
Automated login session extender for use in security analysis systems
ActiveUS7467402B2Random number generatorsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
Measuring Coverage of Application Inputs for Advanced Web Application Security Testing
ActiveUS20100169974A1Memory loss protectionError detection/correctionData processing systemWeb application
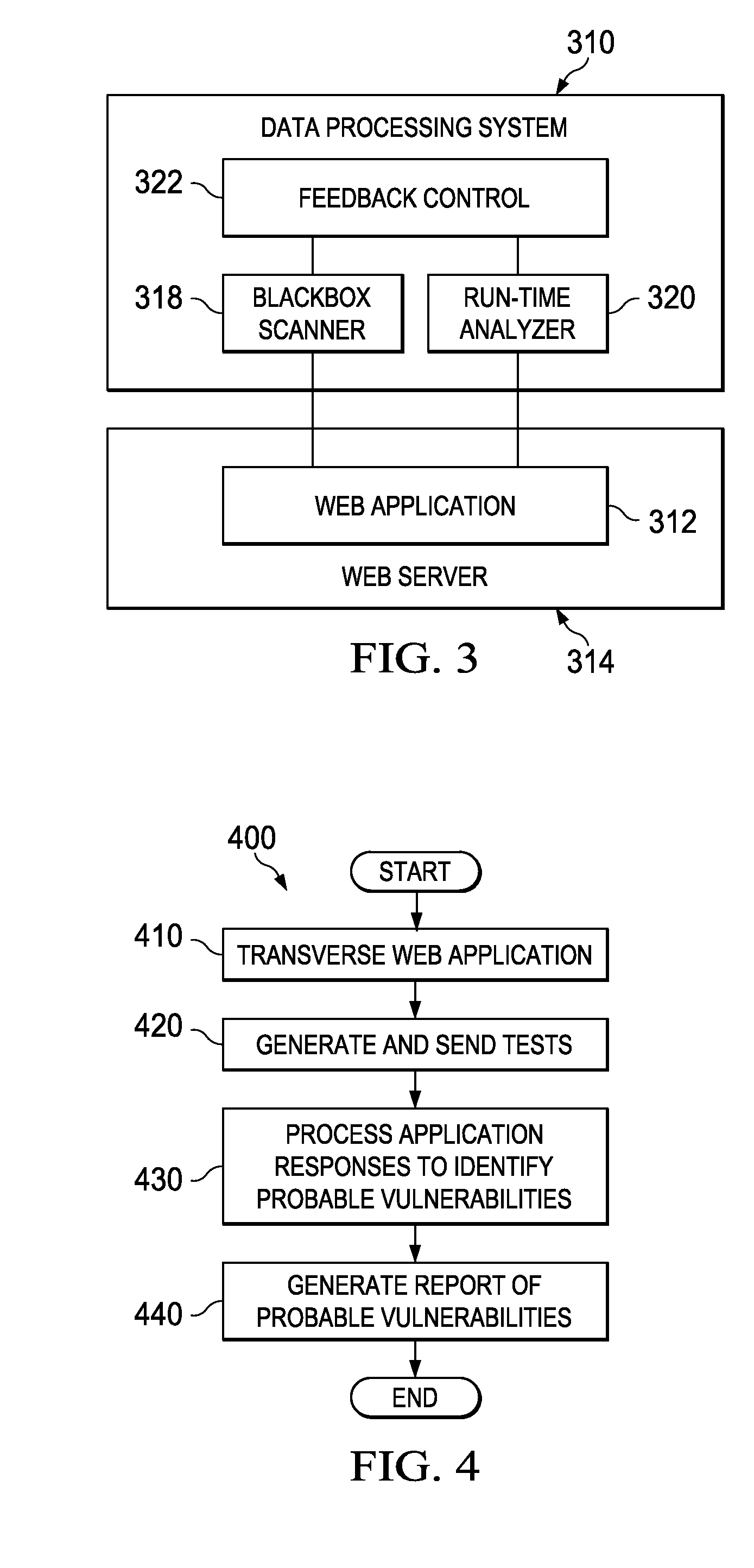
A computer implemented method, a data processing system, and a computer usable recordable-type medium having a computer usable program code monitor a black box web application security scan. A black box scan of a web application is initiated. The black box scan sends a test is sent to a plurality of web application inputs of the web application. A runtime analysis is performed on the black box scan of the web application. Based on the run time analysis of the black box scan, the black box scan is modified.
Owner:IBM CORP
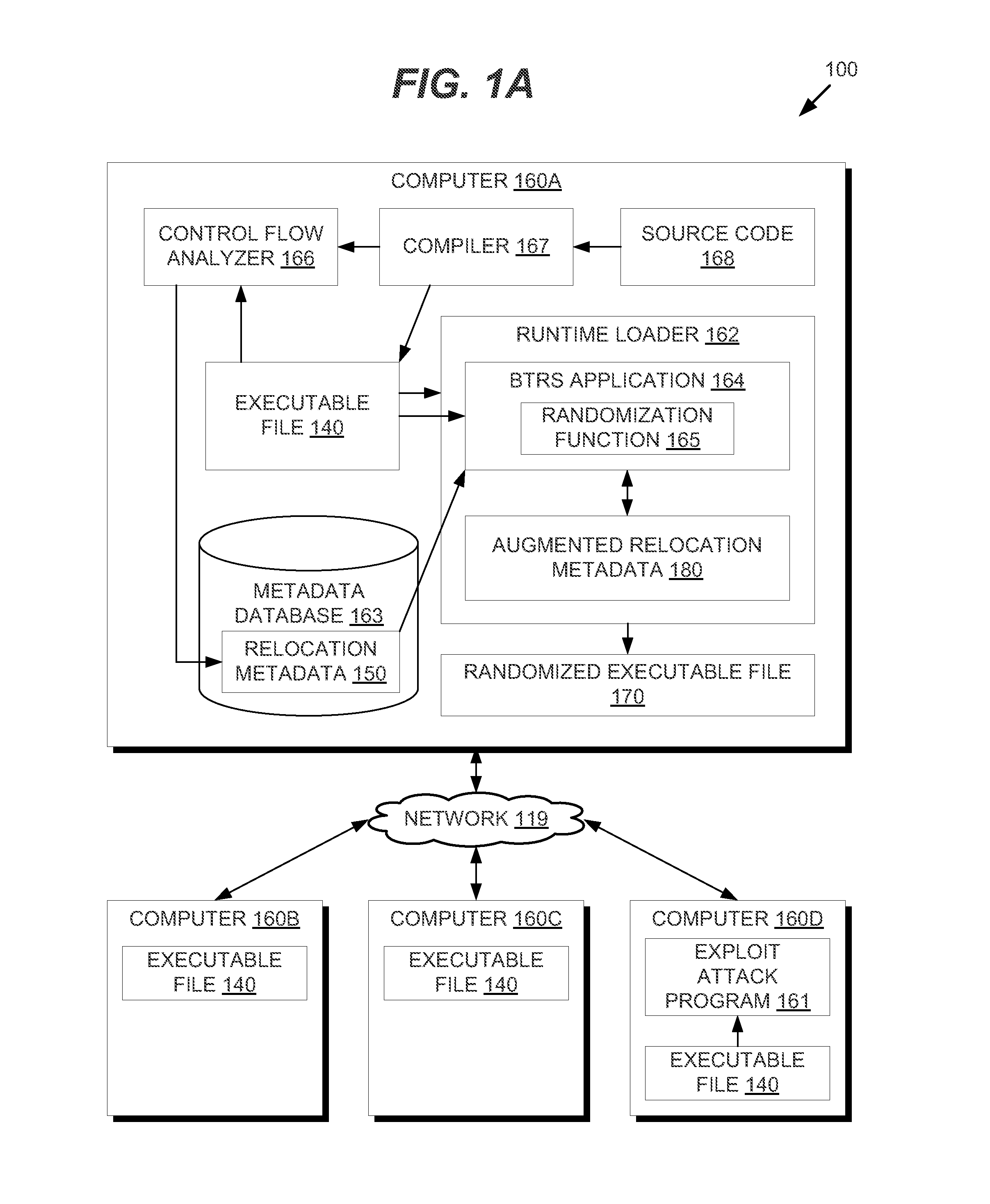
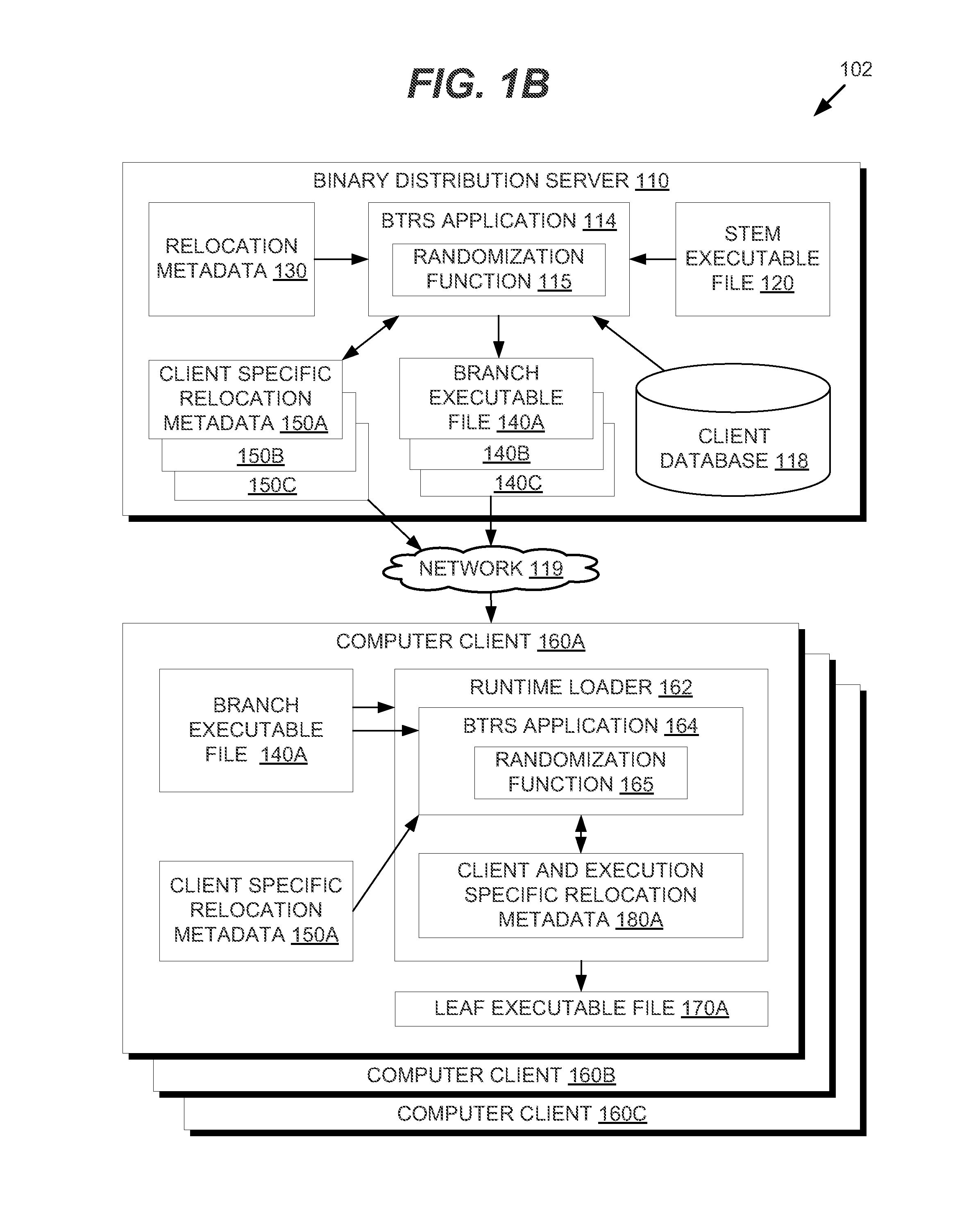
Binary Translation and Randomization System for Application Security
ActiveUS20150047049A1Digital data processing detailsAnalogue secracy/subscription systemsParallel computingExecution unit
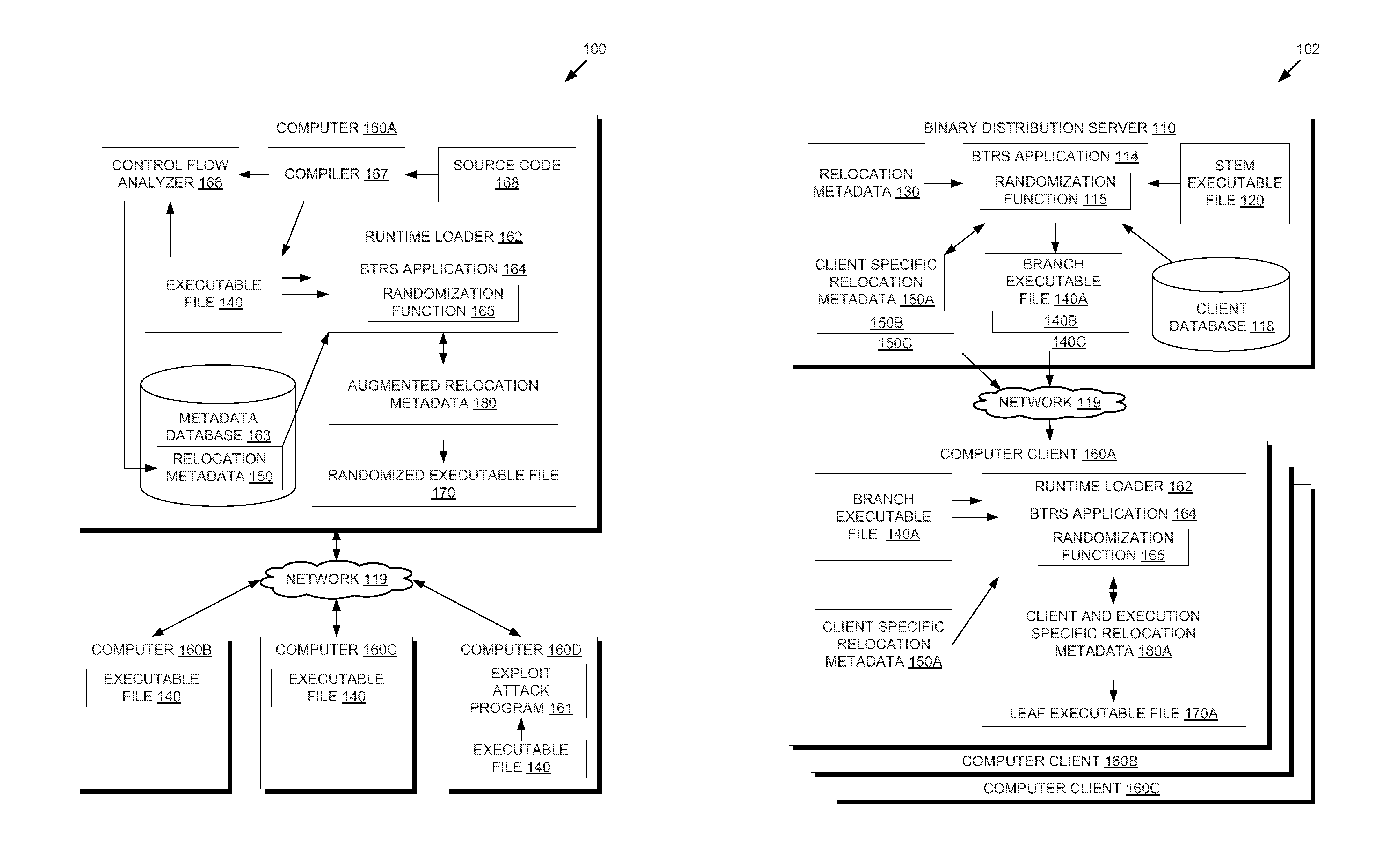
In one embodiment, methods are described to provide a binary translation and randomization system. Relocation metadata is received, which comprises, for each of a plurality of execution units in an executable file, a mapping from the executable file into an address space range. For at least one of the plurality of execution units, the mapping is modified to replace instructions within the address space range with a relocated copy of the instructions at a randomly located address space range. An order of the plurality of execution units may thus be modified. An image is generated from the executable file using the relocation metadata, and an execution of the image is caused. The randomization may be carried out in two passes to provide executable files that are uniquely randomized for each computer and for each execution.
Owner:CISCO TECH INC
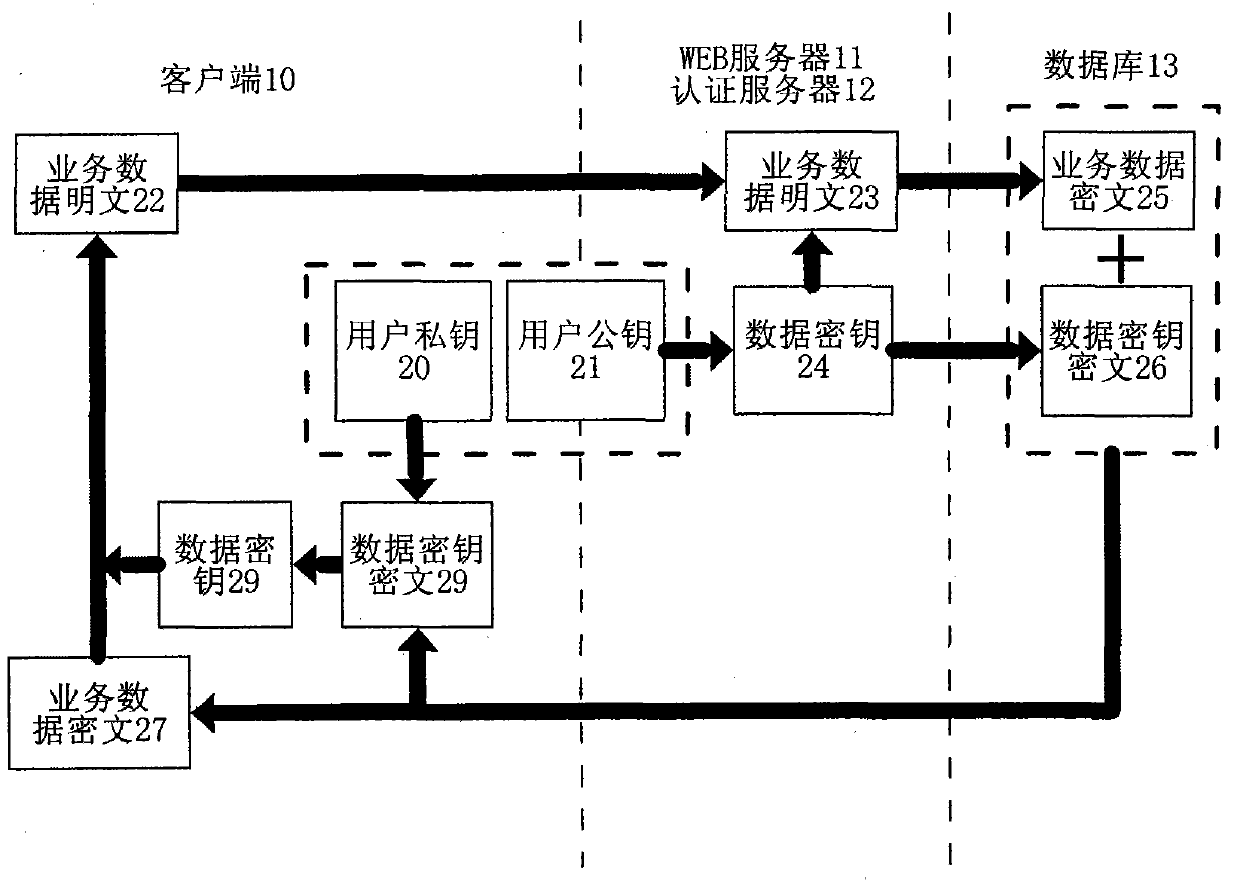
Method and system for improving SaaS application security
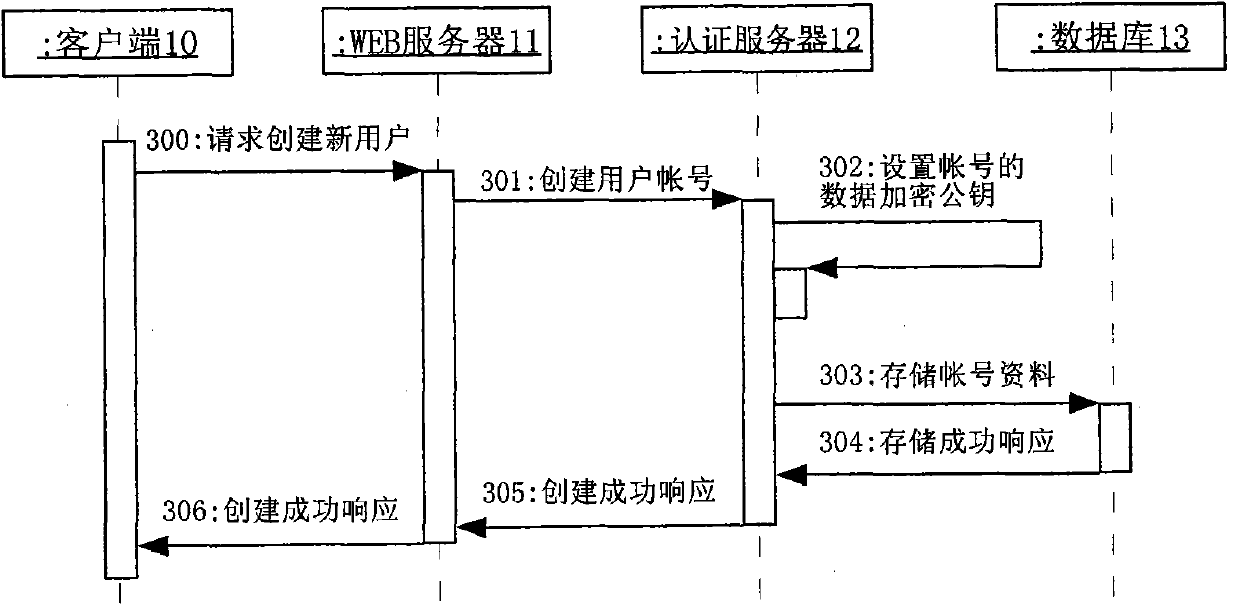
InactiveCN101771699AImprove securityPrevent leakageEncryption apparatus with shift registers/memoriesPublic key for secure communicationWeb serviceCiphertext
The invention provides a method and a system for improving SaaS application security. The encryption method includes that a public password belonging to the client is set up; a data password used for encrypting business data for the client is randomly generated when the business data of the client is saved; the data password is used as the password to encrypt the business data according to a symmetrical cryptographic algorithm; the business data are encrypted through the public password and according to an unsymmetrical cryptographic algorithm; the business data cryptograph and the data password cryptograph are saved in a server; the client gets the cryptograph saved in the server after successfully decrypting the challenge message of the server with the private password; the client decrypts the data password cryptograph with the private password and further decrypts the business data according to the symmetrical cryptographic algorithm. The system includes a WEB server, an authentication server and a database server which can transmit data each other. The invention effectively prevents the administrator from reveal and malicious use of the data password.
Owner:SOUTH CHINA UNIV OF TECH +1
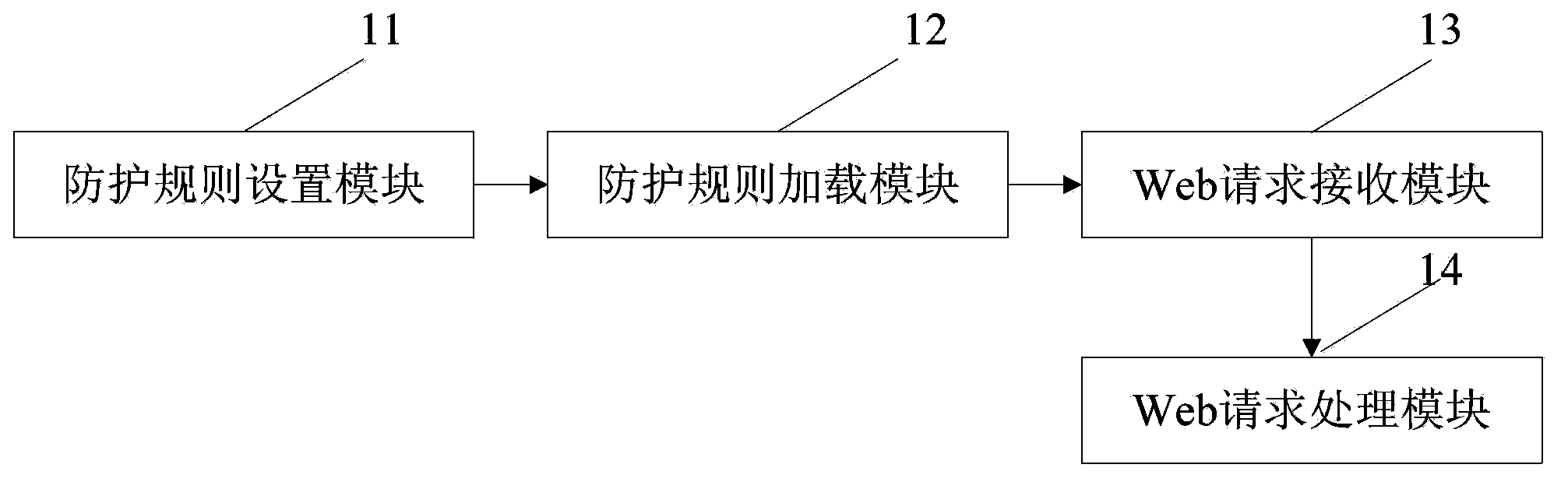
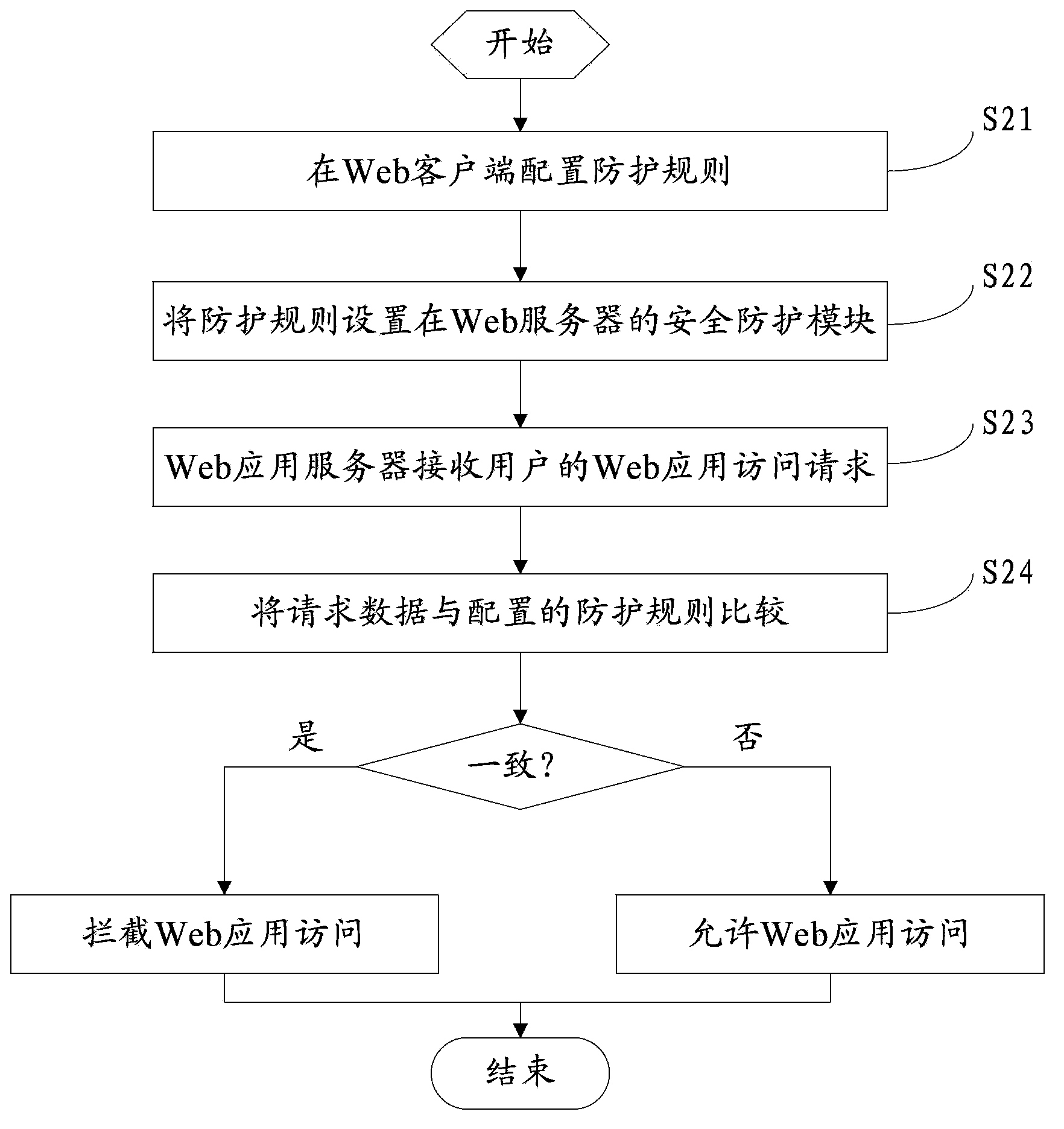
Method and system of safety protection of Web application
The invention discloses a method and a system of safety protection of a Web application. According to the method and the system, the method comprises the following steps that: an administrator configures a protection rule on a Web client according to the need, so that a protection rule file is formed, the protection rule file is arranged in a safety protection module of a server, and a global filter is provided; when a Web application server receives a Web application access request of a user, the safety protection module compares request data of the Web application access request and the configured protection rule file and checks whether the request data is matched with the protection rule file, if so, the Web application access is intercepted; and otherwise, the Web application access is allowed. According to the method and the system, which are disclosed by the invention, all Web applications can be protected according to the need, so that safety of the Web access is improved. The intercept action of the Web application access is transferred into a proxy service server from an application program, so that repeated development or missing intercept of the application program is avoided, and the cost is reduced.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Web application exploit mitigation in an information technology environment
ActiveUS20130086688A1Improve protectionMemory loss protectionUnauthorized memory use protectionEnd to end securityProgram management
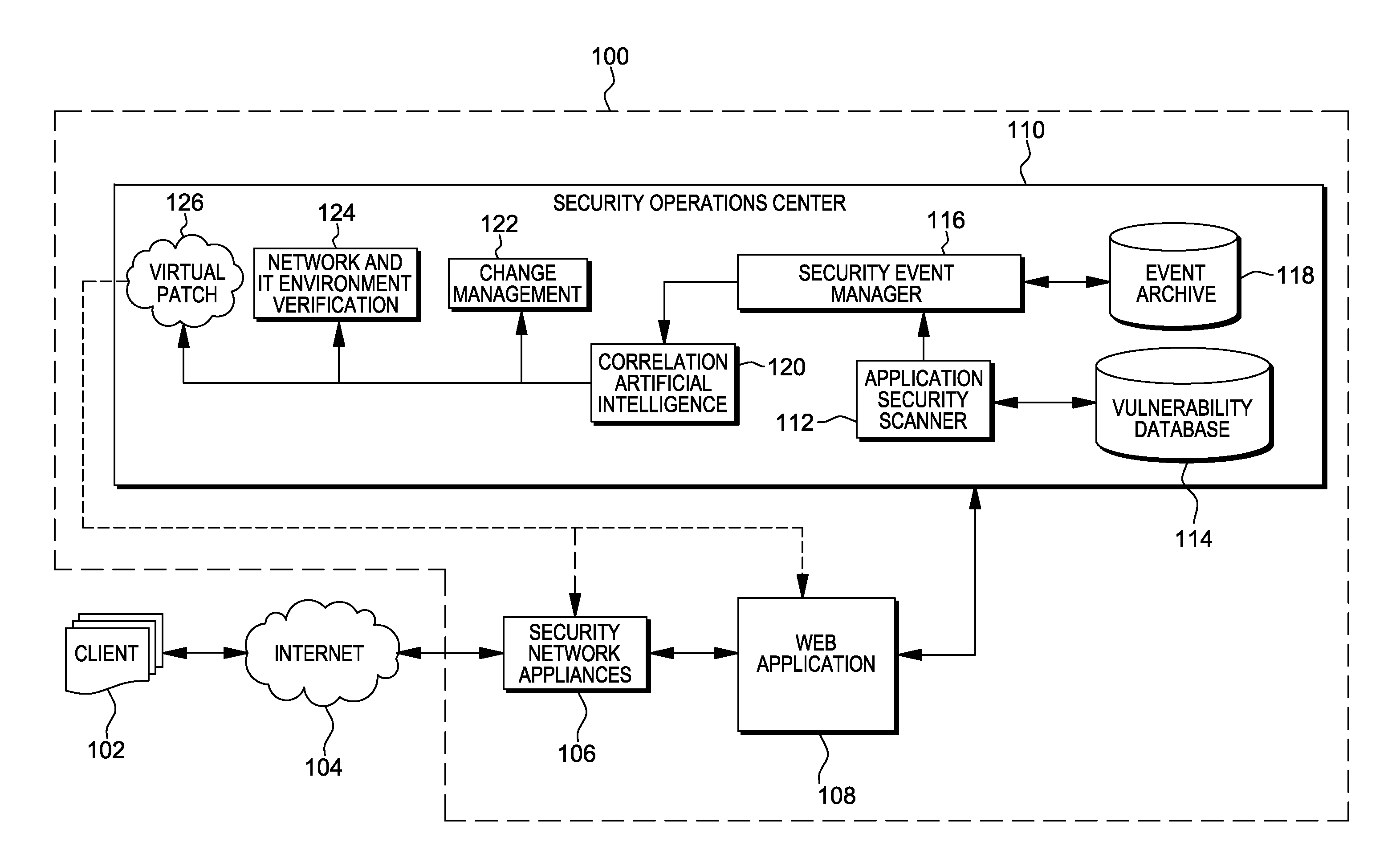
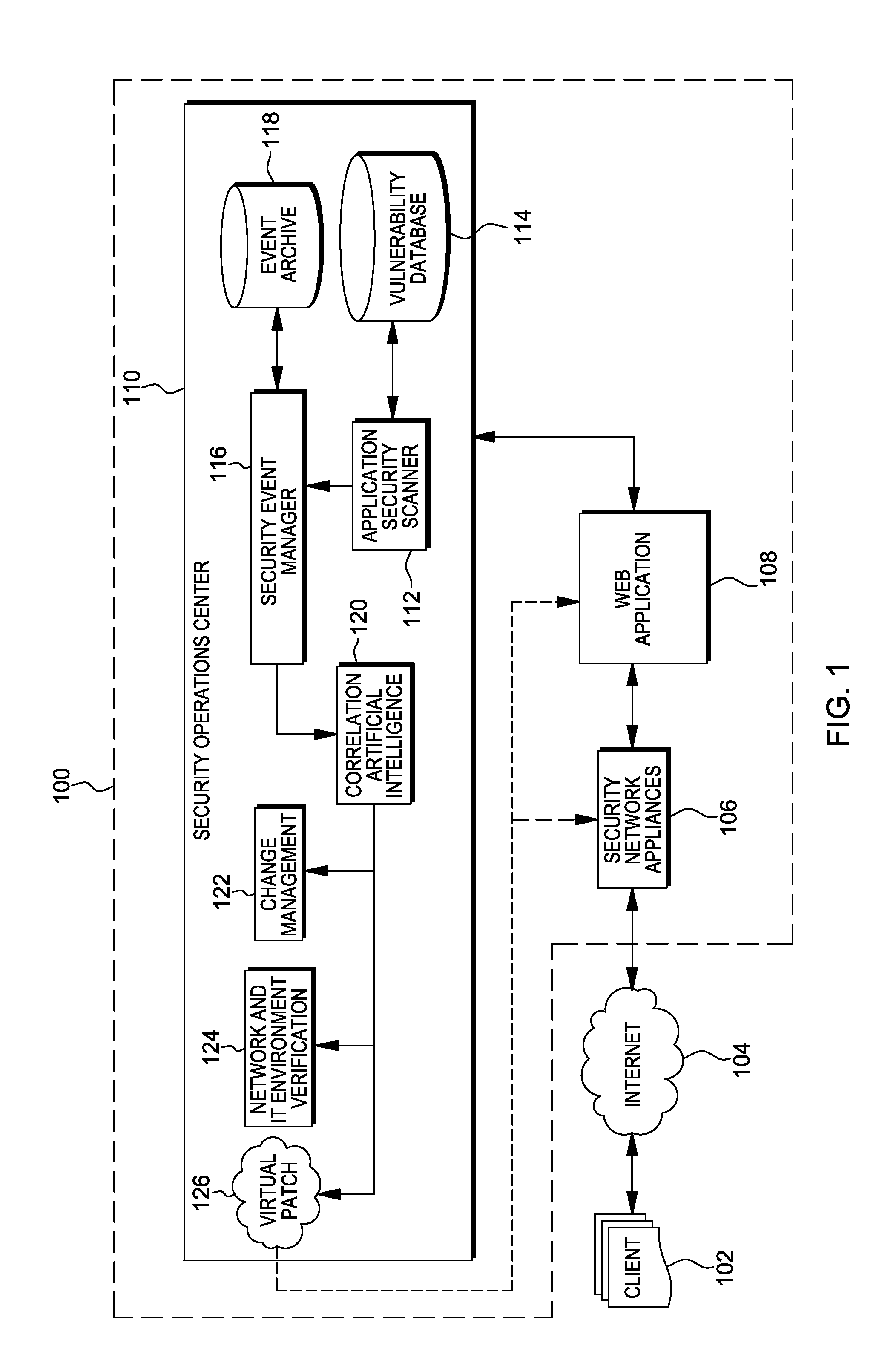
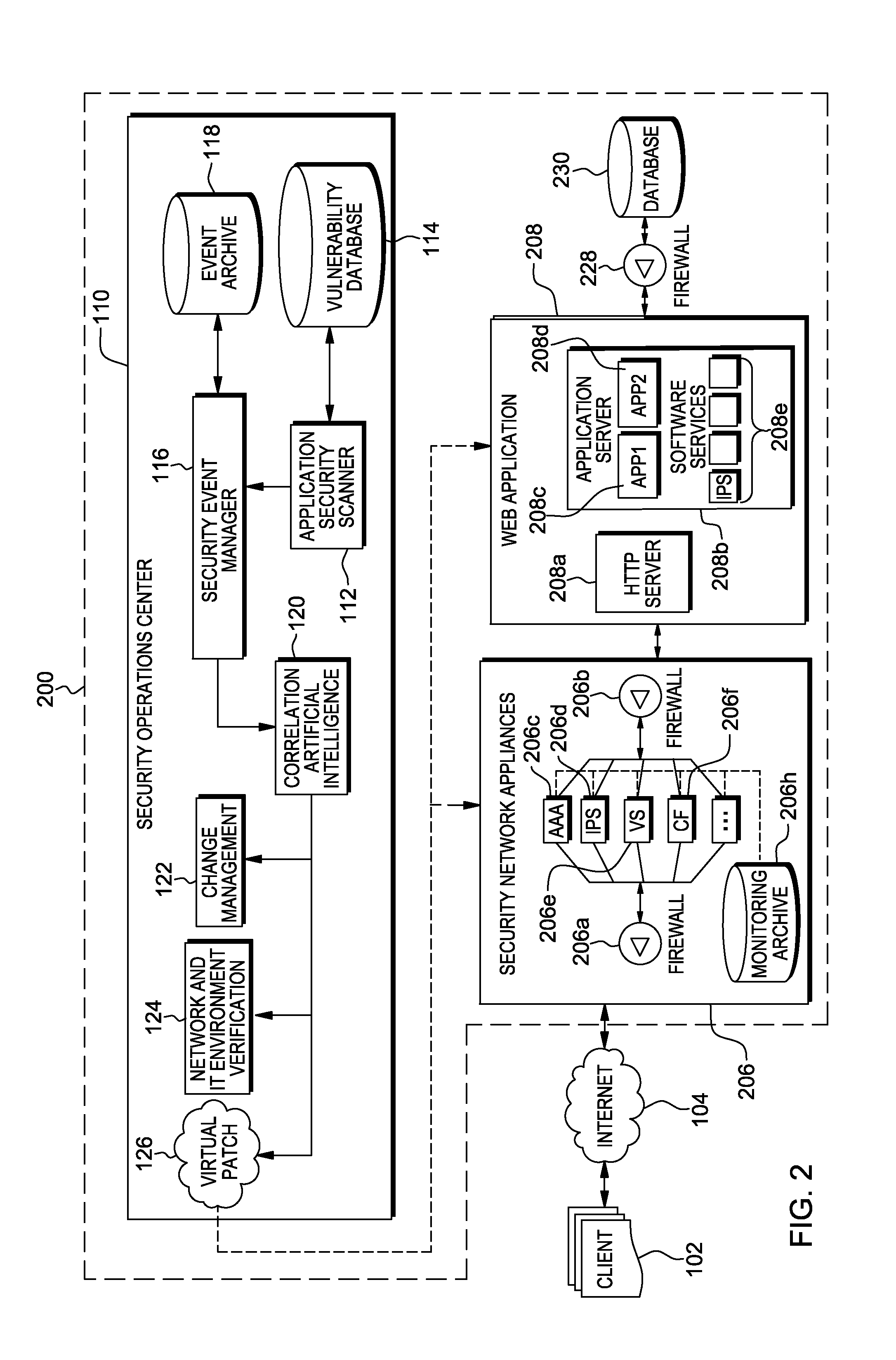
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
Mobile application access control list security system
InactiveUS7065783B2Ensure safetyDigital data processing detailsUnauthorized memory use protectionComputer compatibilityApplication security
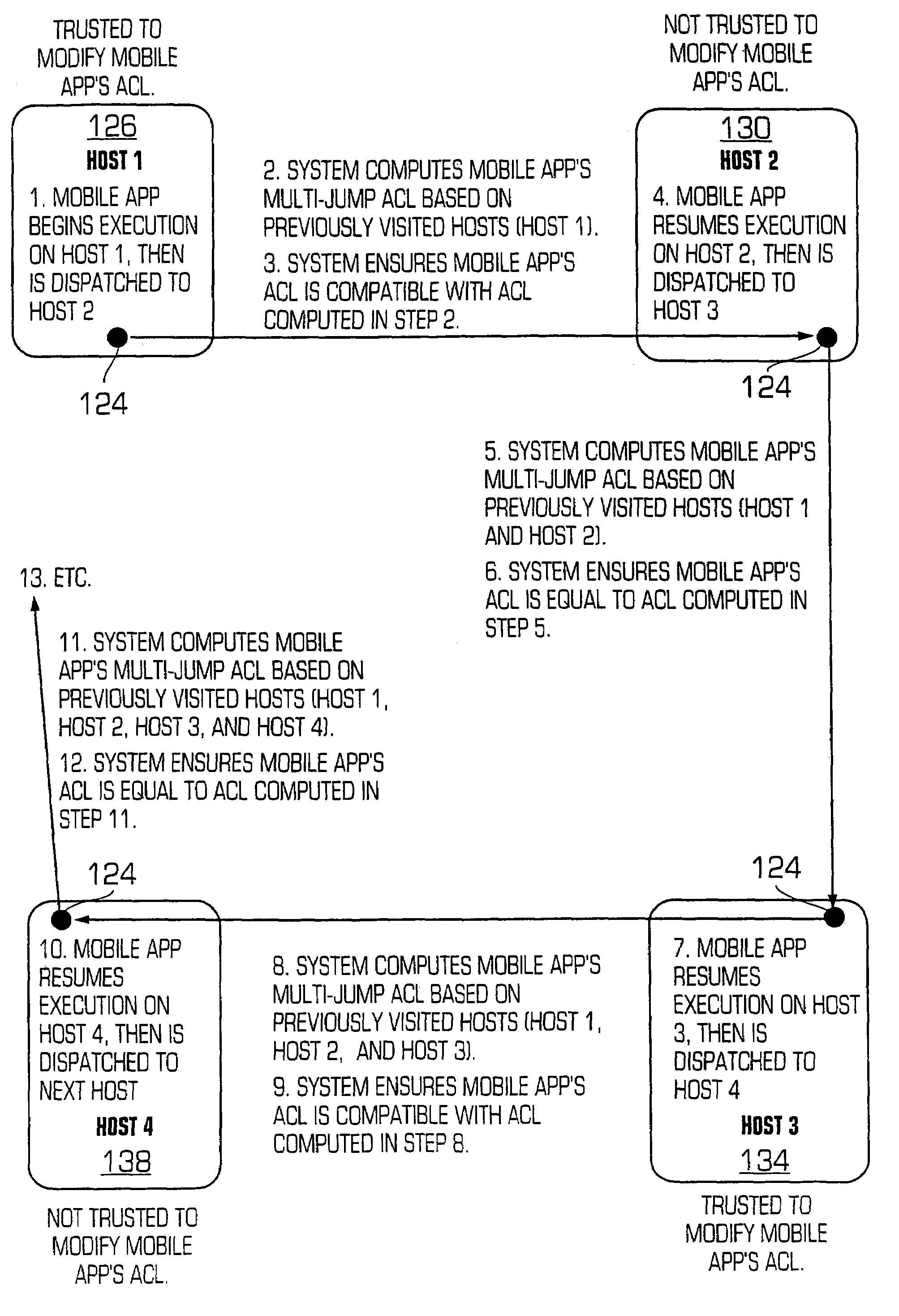
A mobile application security system and method, in the preferred embodiment, ensures the integrity of a mobile application's multi-jump access control list (ACL) by either (a) checking the compatibility of a mobile application's multi-jump ACL with a known accurate multi-jump ACL, or (b) overwriting a mobile application's multi-jump ACL with an ACL which is known to be accurate, depending on whether the host dispatching the mobile application is trusted or not trusted to modify a mobile application's multi-jump ACL, respectively.
Owner:ARAMIRA CORP
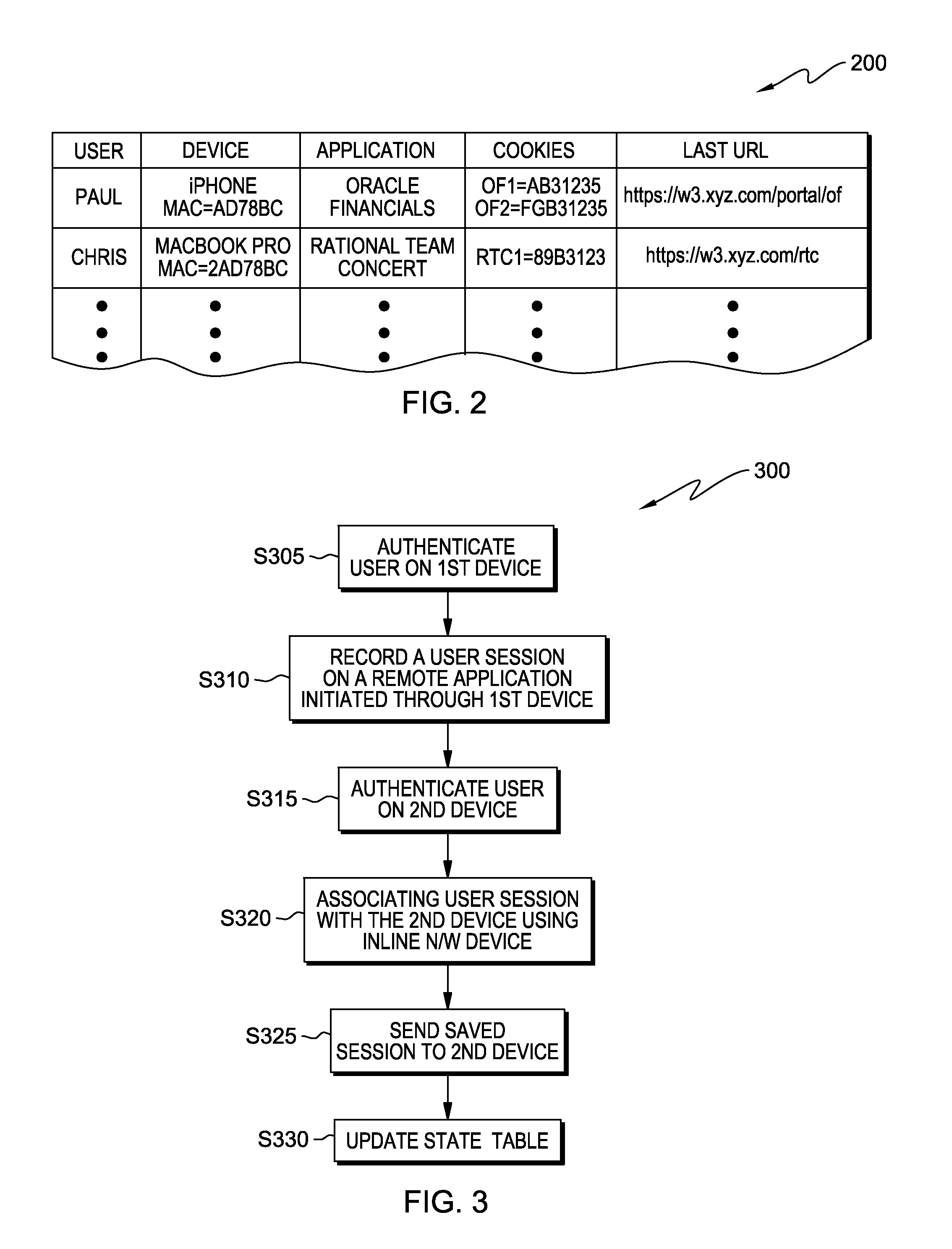
Sharing web application sessions across multiple devices
A technique to at least partial transfer an active network communication session associated with a server and an authenticated user communicating through a first device. The at least partial transfer includes the following actions (not necessarily in the following order): (i) recording the network communication session on an inline network device; (ii) associating the network communication session with the second device on the inline network device; and (iii) sending session continuation information from the inline network device to at least the second device and / or the server. The first device is in data communication with the inline network device during at least a portion of the recording step. The session continuation information sent at the sending step includes information enabling the user to continue the active network communication session through the second device. The inline network device performs at least the associating step and the sending step under control of computer software running on computer hardware.
Owner:IBM CORP
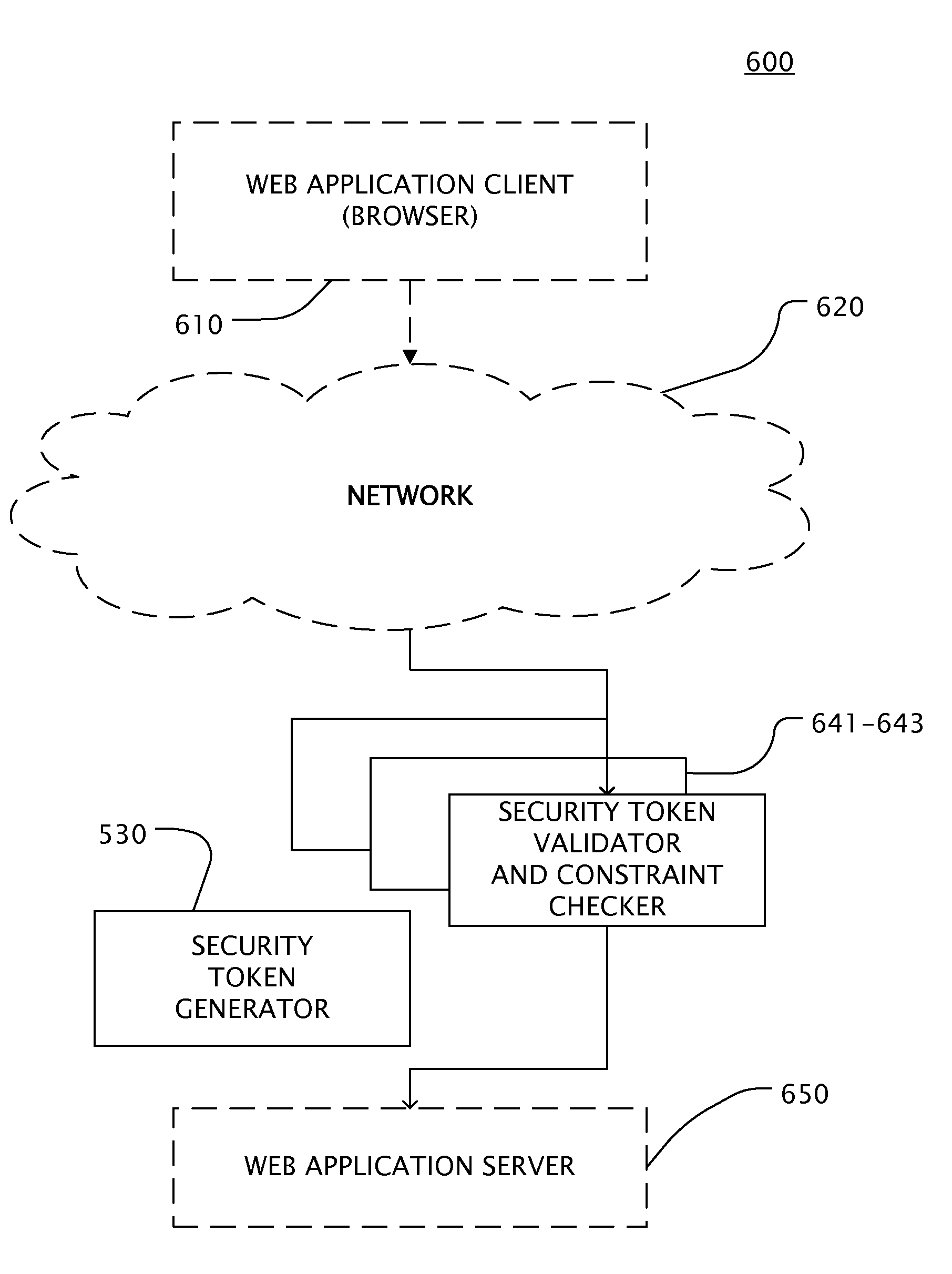
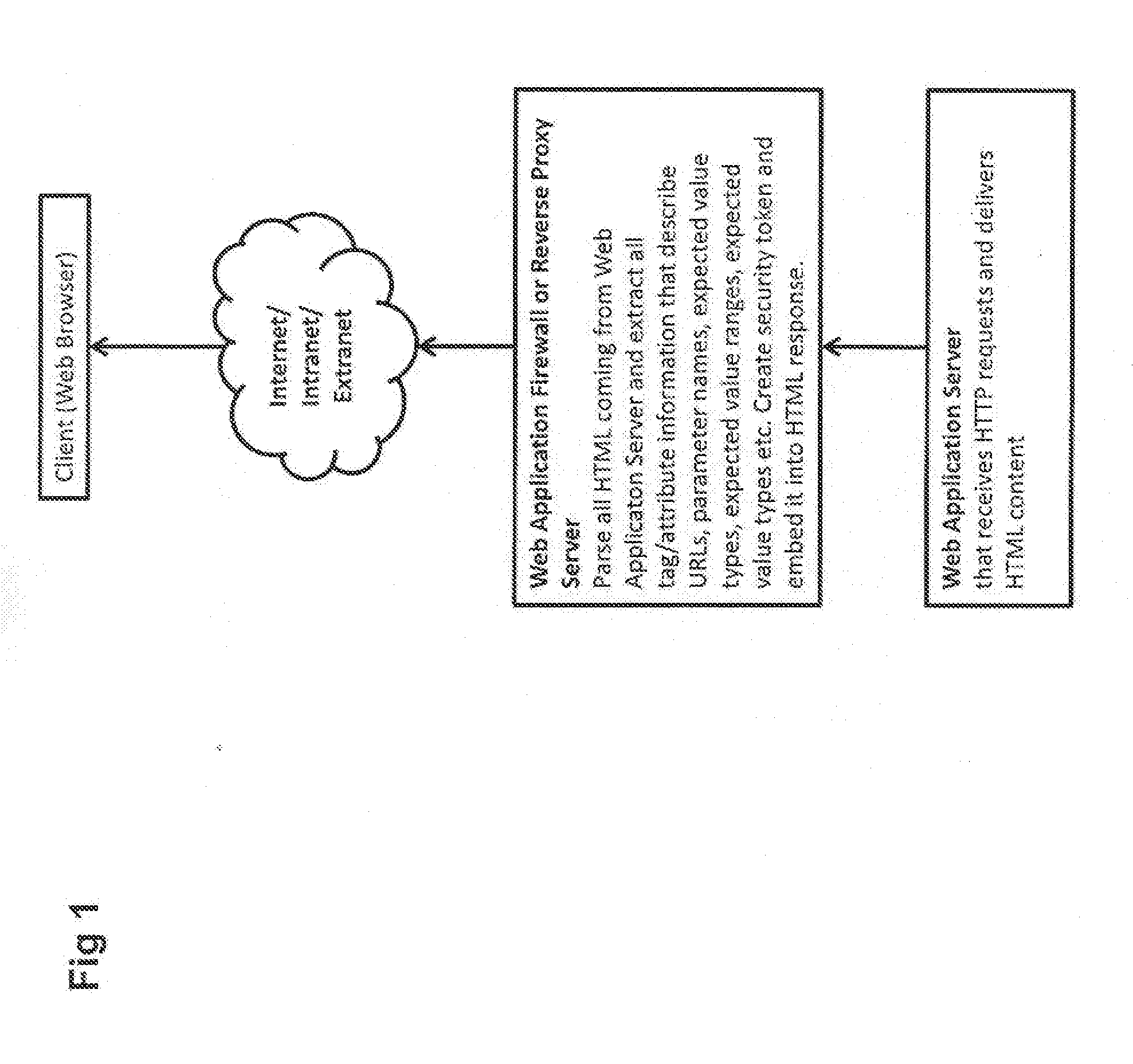
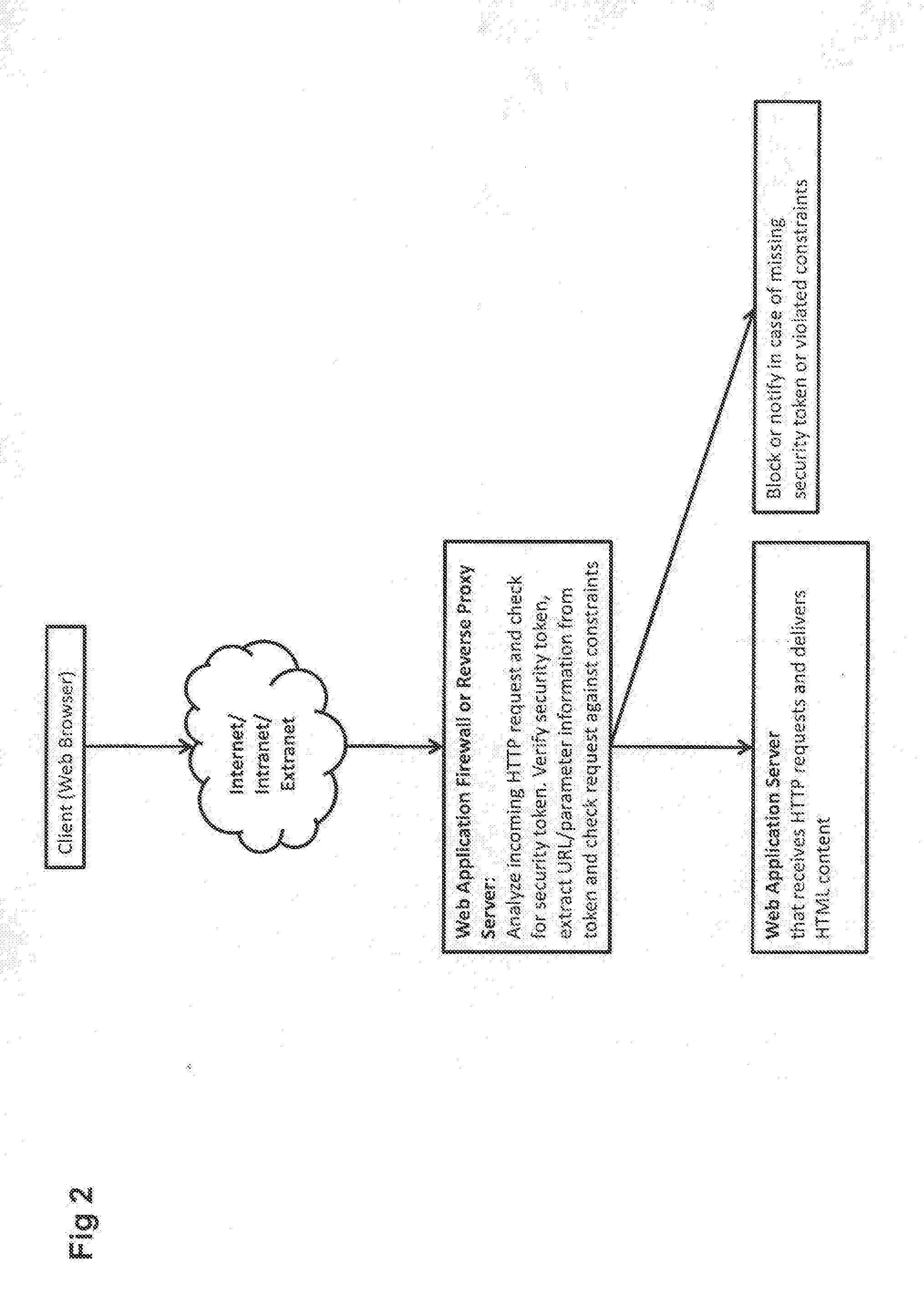
Web application security filtering
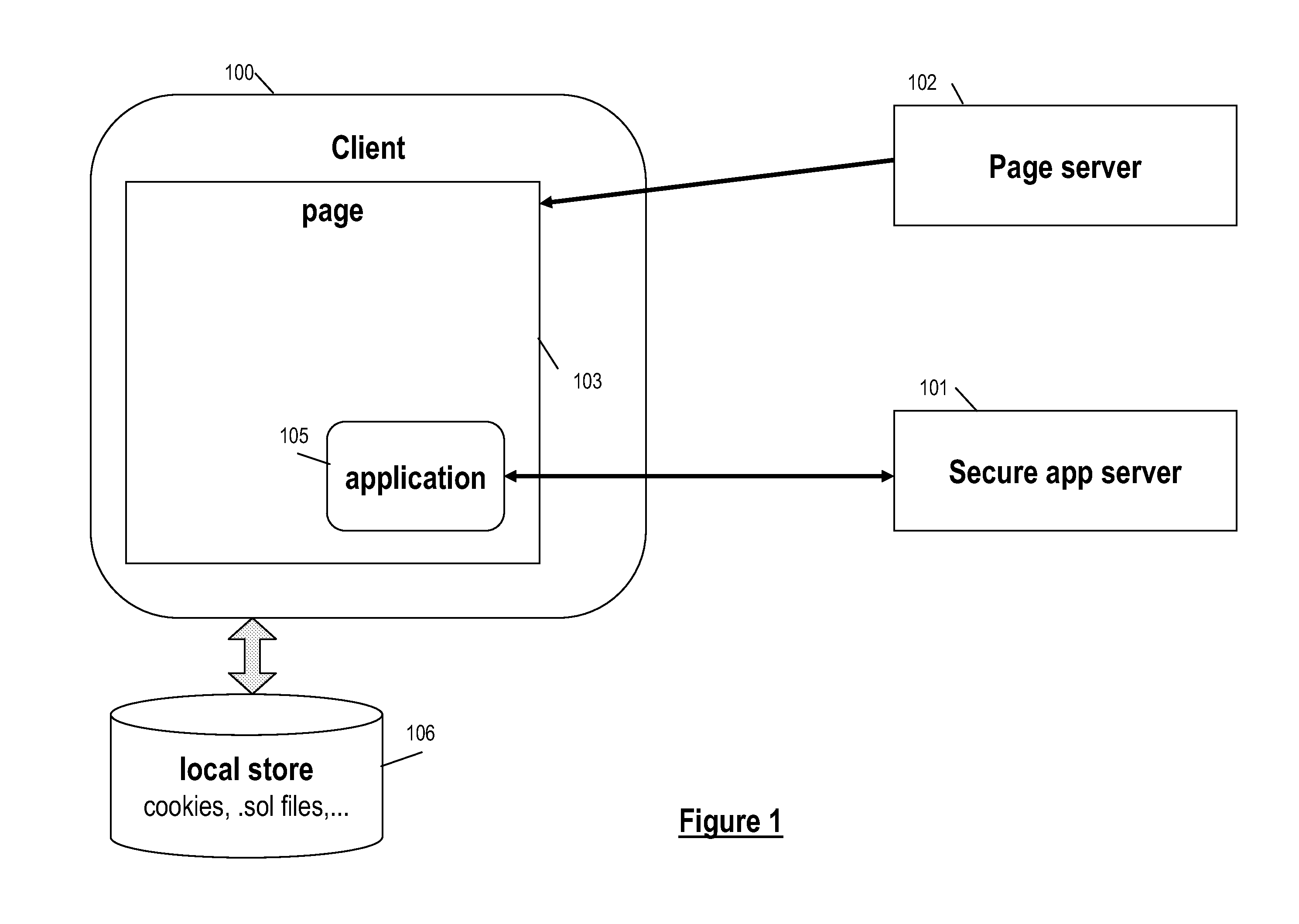
InactiveUS20100332837A1Simple and efficientLess sensitiveDigital data processing detailsUser identity/authority verificationWeb applicationApplication server
User inputs and / or Uniform Resource Identifier (URI), historically and popularly referred to as Universal Resource Locator (URL), requests in a content description language are passed through a security service (Web application firewall or a reverse Web proxy server) that is placed in front of Web application servers in order to protect the servers from hacking attempts. For validating Webform user inputs and / or URI requests and parameters the content description language is enriched by the security service with additional security tokens that are dynamically created based on the content being transferred. The user receives the information and returns input with the security tokens. The security service can then verify all provided user input data against the constraints described in the corresponding security token. As a result, the method may block the HTTP request or create log messages or notification events in reaction to violations of the user input data compared to the constraints in the security token.
Owner:PHION
Server apparatus, terminal apparatus, and printing system and data conversion method thereof
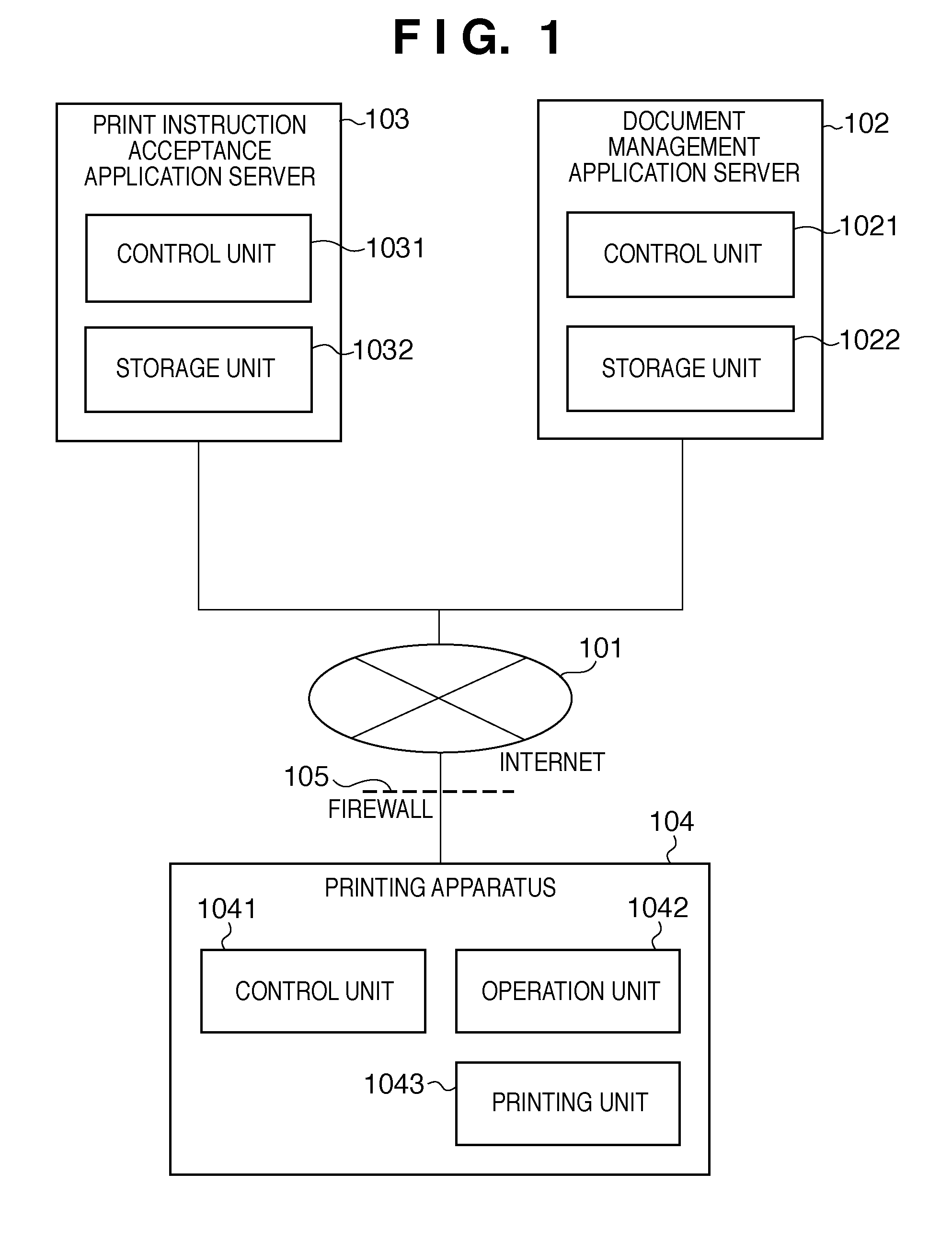
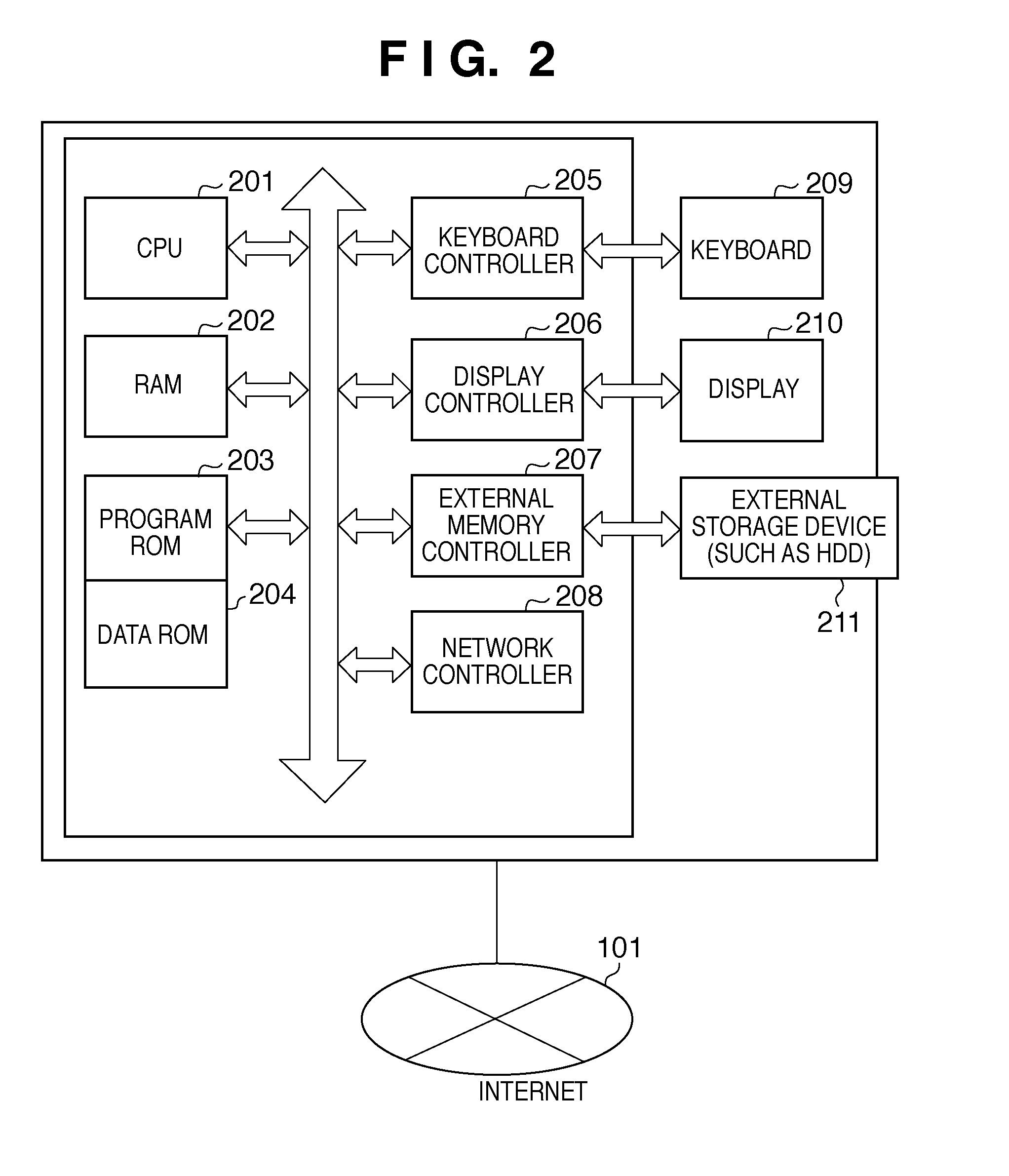
InactiveUS20110242594A1Easy to useVisual presentationDigital output to print unitsWeb applicationWeb browser
For a web application requiring a time to execute processing, it is necessary to maintain Internet connection between a web browser and the web application until the processing is completed. Conventionally, the connection is maintained by causing the web browser to inquire a web application server about the execution state of the processing at regular intervals. In this case, however, the web browser cannot execute another different web application until the processing in the web application server is completed. In this invention, a web application server provides processing of converting from document data into print data as a software process asynchronous to a web application and the web application only accepts an execution request for the conversion processing.
Owner:CANON KK
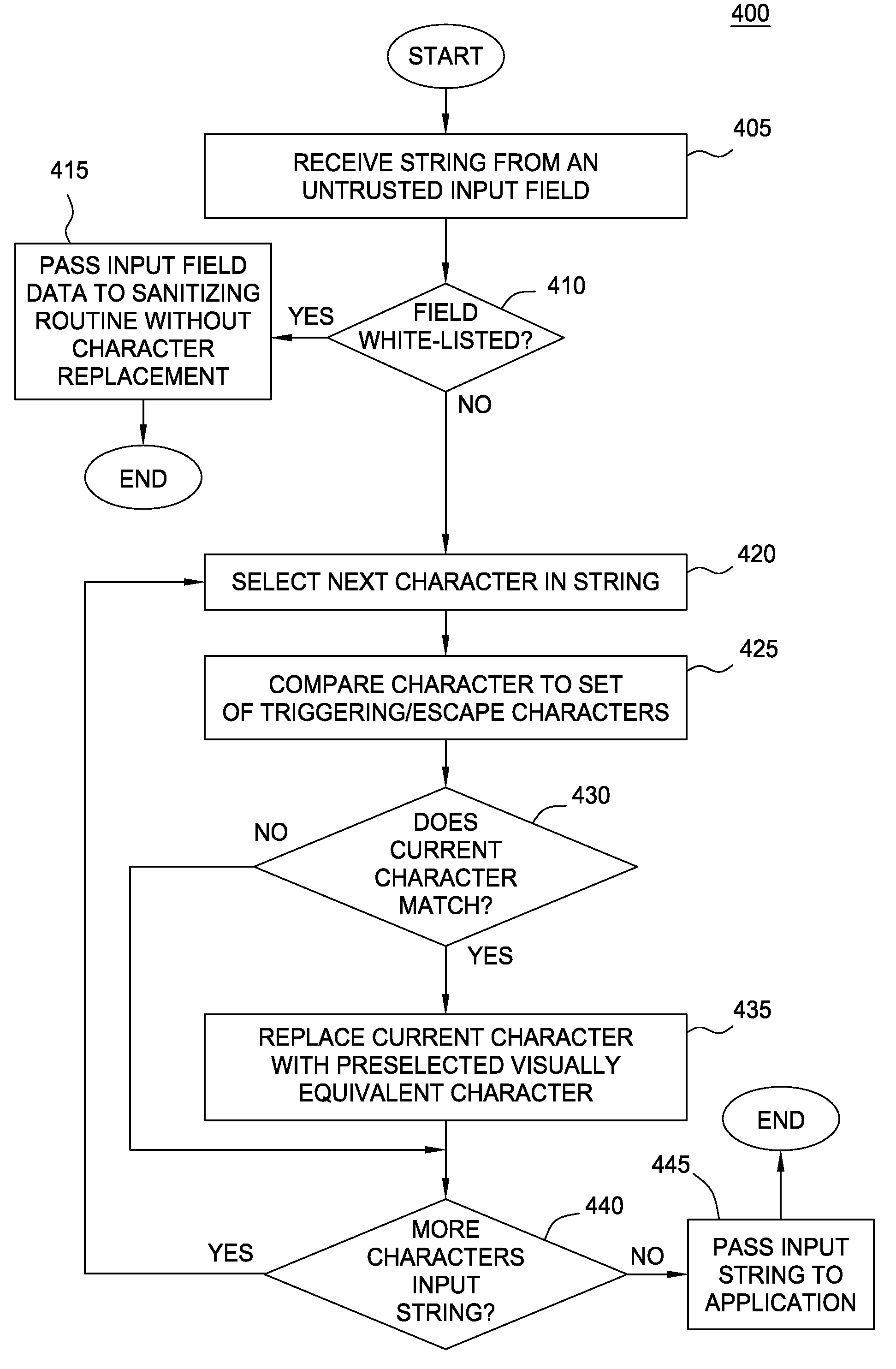
Input parameter filtering for web application security
InactiveUS20110219446A1Improve securityMemory loss protectionError detection/correctionPattern recognitionWeb application
Techniques are disclosed for enhancing the security of a web application by using input filtering. An input filter may be configured to process untrusted input data, character by character, and to replace certain characters in text-based input with visually similar characters. This approach may be used to block a specified list of “triggering” characters as they come in and replace them with characters similar in appearance but without the syntactic meaning that triggers an attack or otherwise exploits a vulnerability in a web-application.
Owner:SUCCESSFACTORS
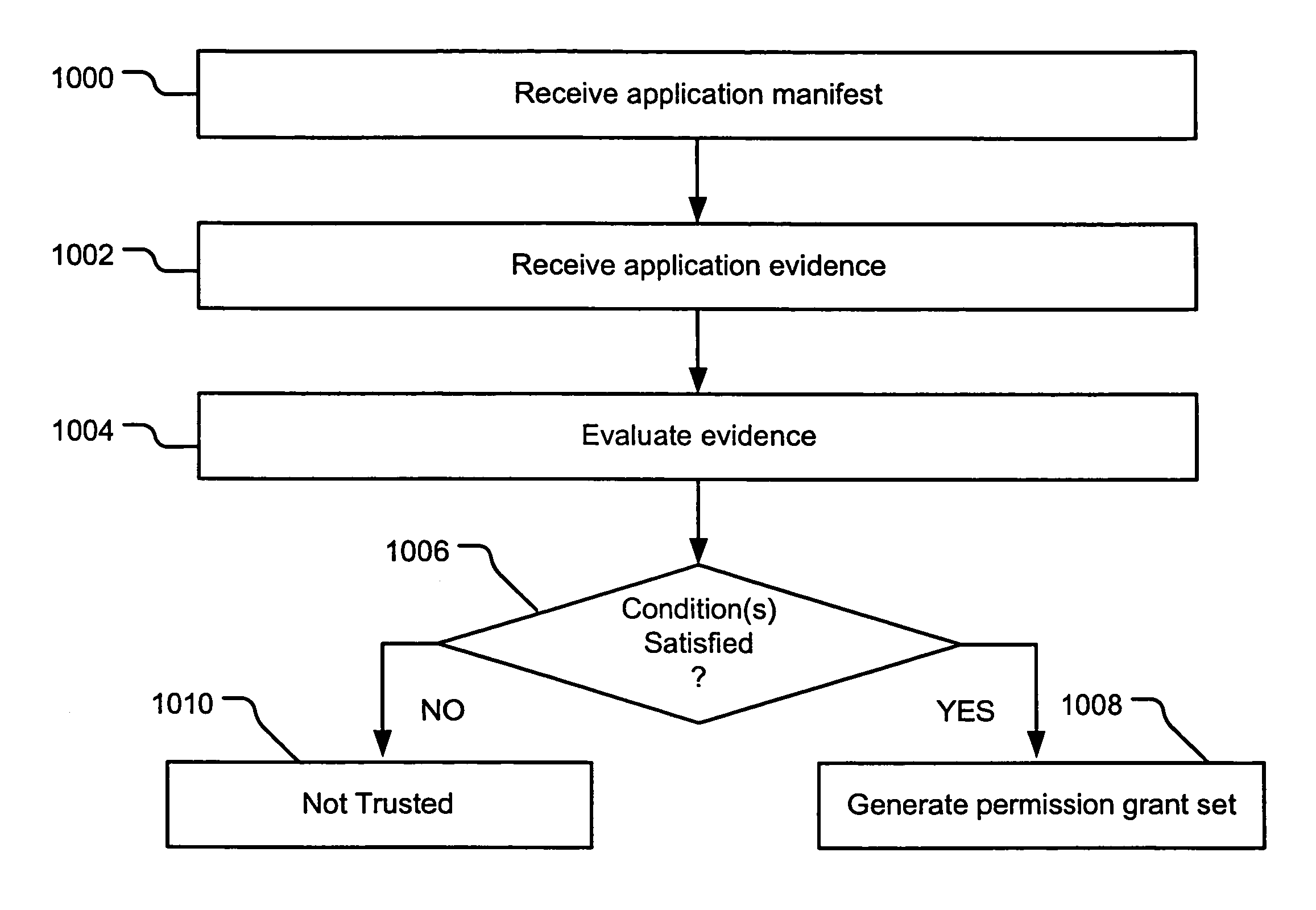
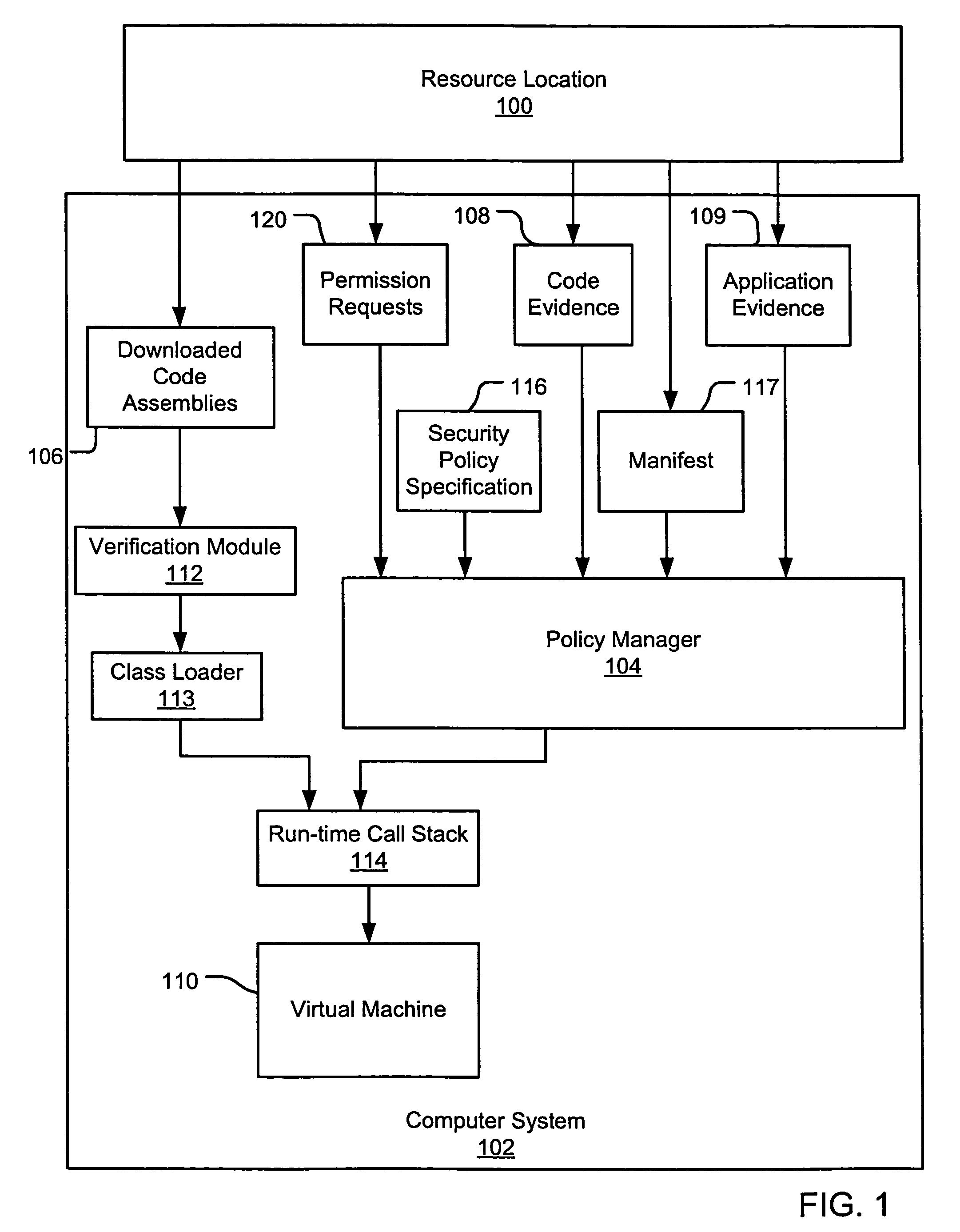
Evidence-based application security
InactiveUS7669238B2Memory loss protectionDigital data processing detailsComputerized systemApplication software
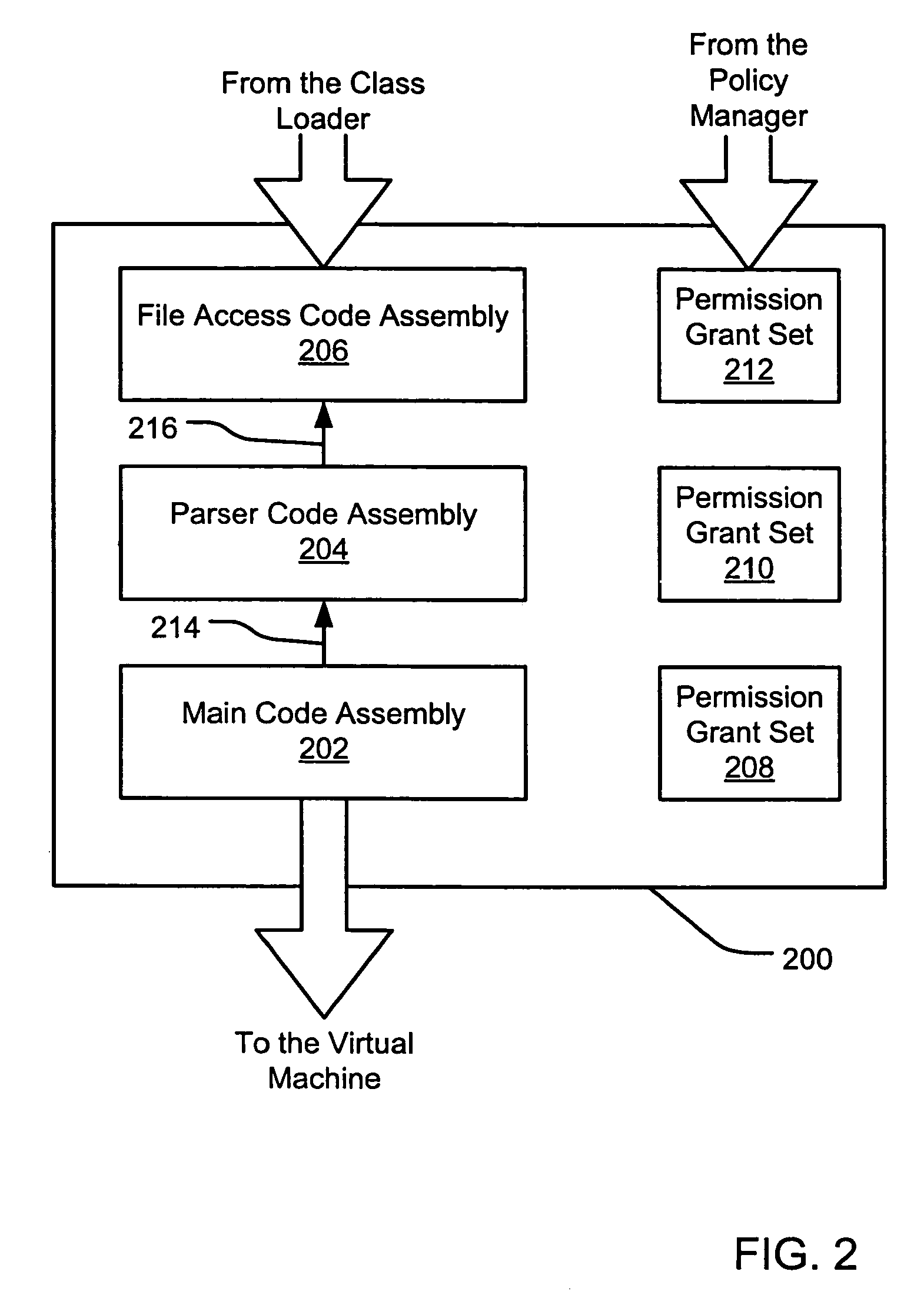
Evidence-based application security may be implemented at the application and / or application group levels. A manifest may be provided defining at least one trust condition for the application or application group. A policy manager evaluates application evidence (e.g., an XrML license) for an application or group of applications relative to the manifest. The application is only granted permissions on the computer system if the application evidence indicates that the application is trusted. Similarly, a group of applications are only granted permissions on the computer system if the evidence indicates that the group of applications is trusted. If the application evidence satisfies the at least one trust condition defined by the manifest, the policy manager generates a permission grant set for each code assembly that is a member of the at least one application. Evidence may be further evaluated for code assemblies that are members of the trusted application or application group.
Owner:MICROSOFT TECH LICENSING LLC
Secure bootstrapping for wireless communications
ActiveUS7966000B2Unauthorised/fraudulent call preventionMultiple keys/algorithms usageKey exchangeChallenge response
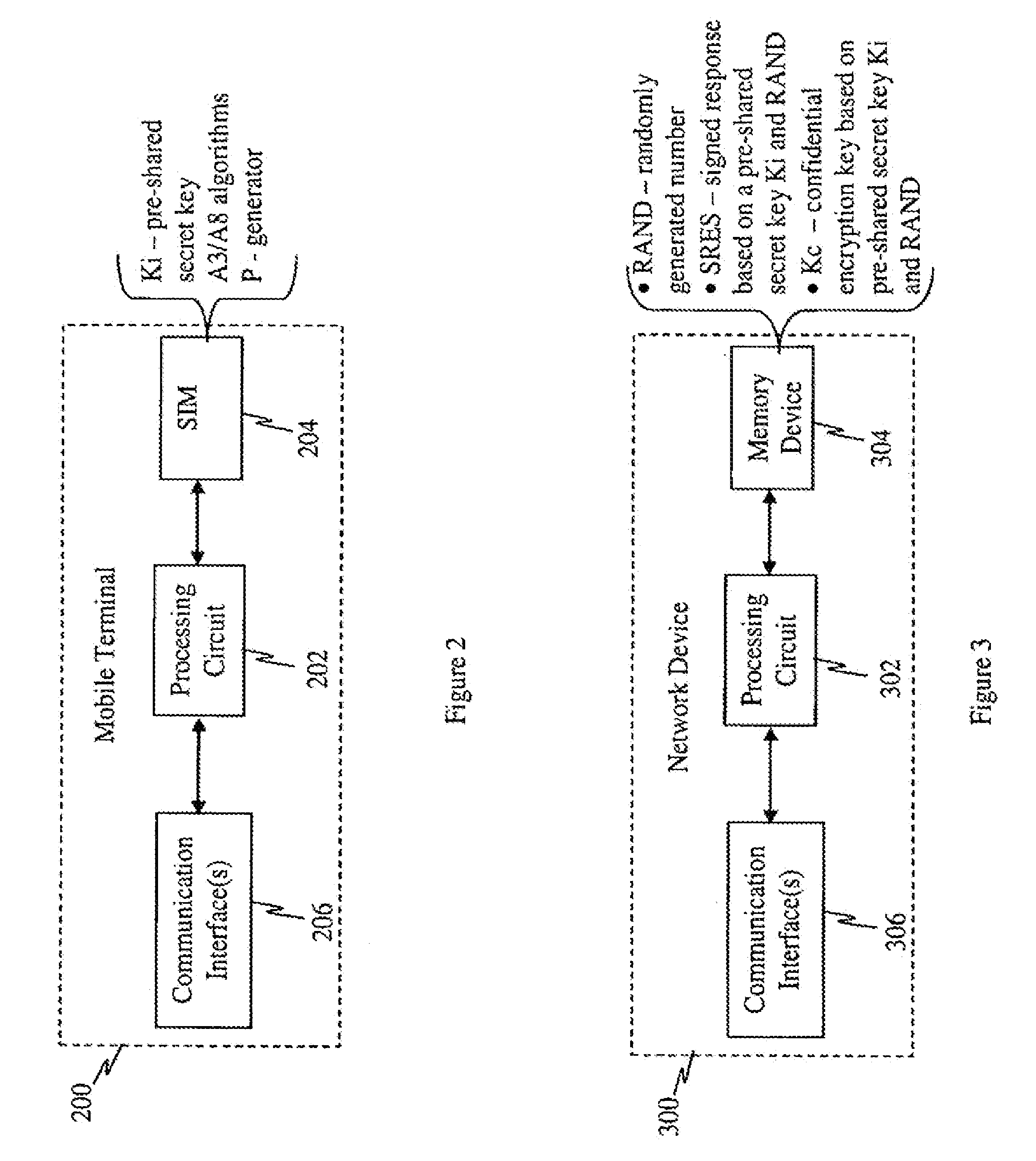
A mutual authentication method is provided for securely agreeing application-security keys with mobile terminals supporting legacy Subscriber Identity Modules (e.g., GSM SIM and CDMA2000 R-UIM, which do not support 3G AKA mechanisms). A challenge-response key exchange is implemented between a bootstrapping server function (BSF) and mobile terminal (MT). The BSF generates an authentication challenge and sends it to the MT under a server-authenticated public key mechanism. The MT receives the challenge and determines whether it originates from the BSF based on a bootstrapping server certificate. The MT formulates a response to the authentication challenge based on keys derived from the authentication challenge and a pre-shared secret key. The BSF receives the authentication response and verifies whether it originates from the MT. Once verified, the BSF and MT independently calculate an application security key that the BSF sends to a requesting network application function to establish secure communications with the MT.
Owner:QUALCOMM INC
Power savings through cooperative operation of multiradio devices
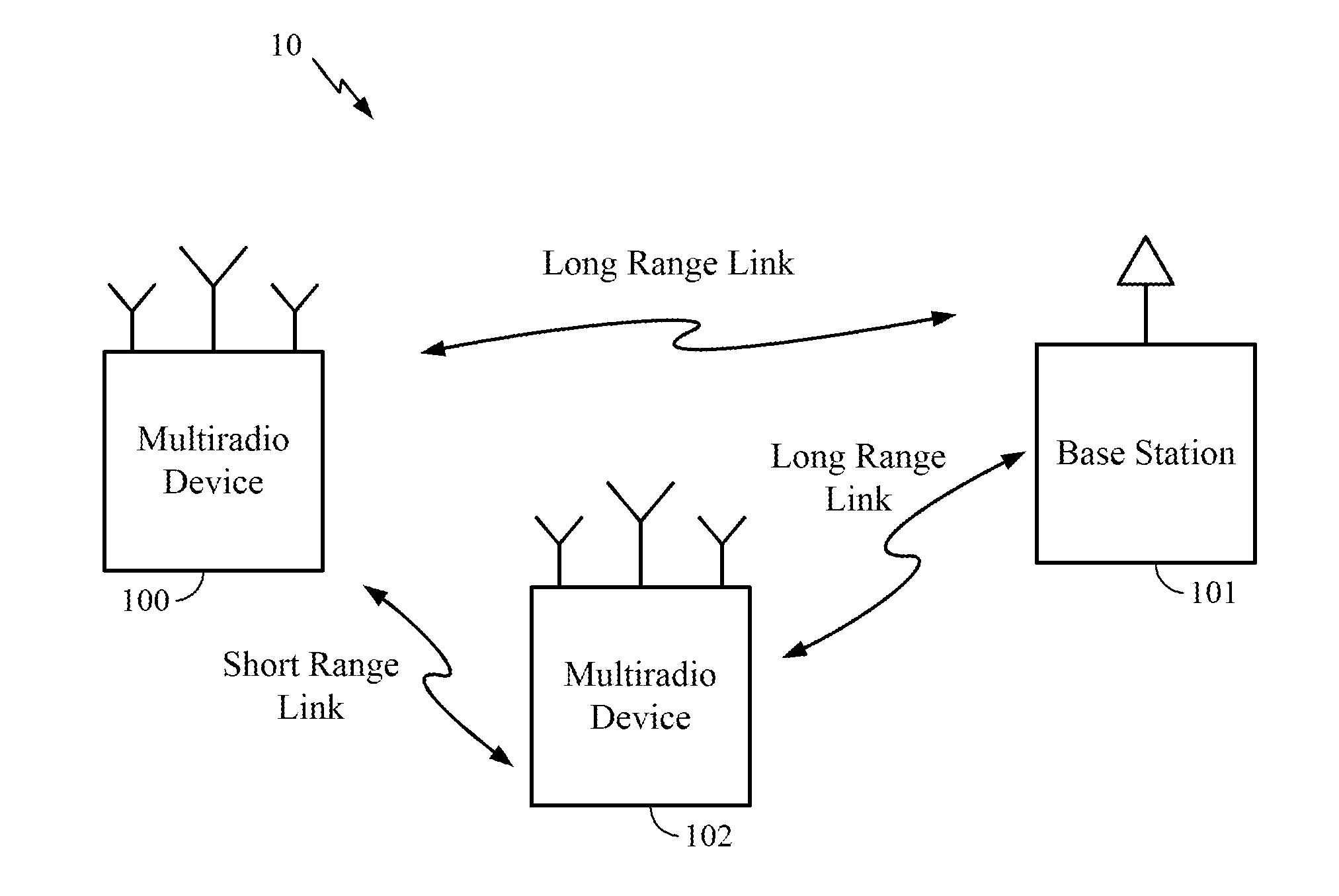
InactiveUS20110255692A1Energy efficient ICTKey distribution for secure communicationThird partyRadio equipment
Trust establishment in short range protocol pairing between client and proxy devices includes a first aspect in which application level security is used to encrypt all packets transmitted between the client and proxy. An application-based security derives a public key from the General Bootstrapping Architecture (GBA) and used that public key to generate an encryption key in an AES encryption algorithm. A second aspect provides for out of band security to be used to establish short range protocol pairing. In this second aspect, the client and proxy exchange identification information over a third party network that is out of band to the short range protocol. With this identification information exchanged out of band, the client and proxy may establish pairing in the short range protocol.
Owner:QUALCOMM INC
Secure digital signature system
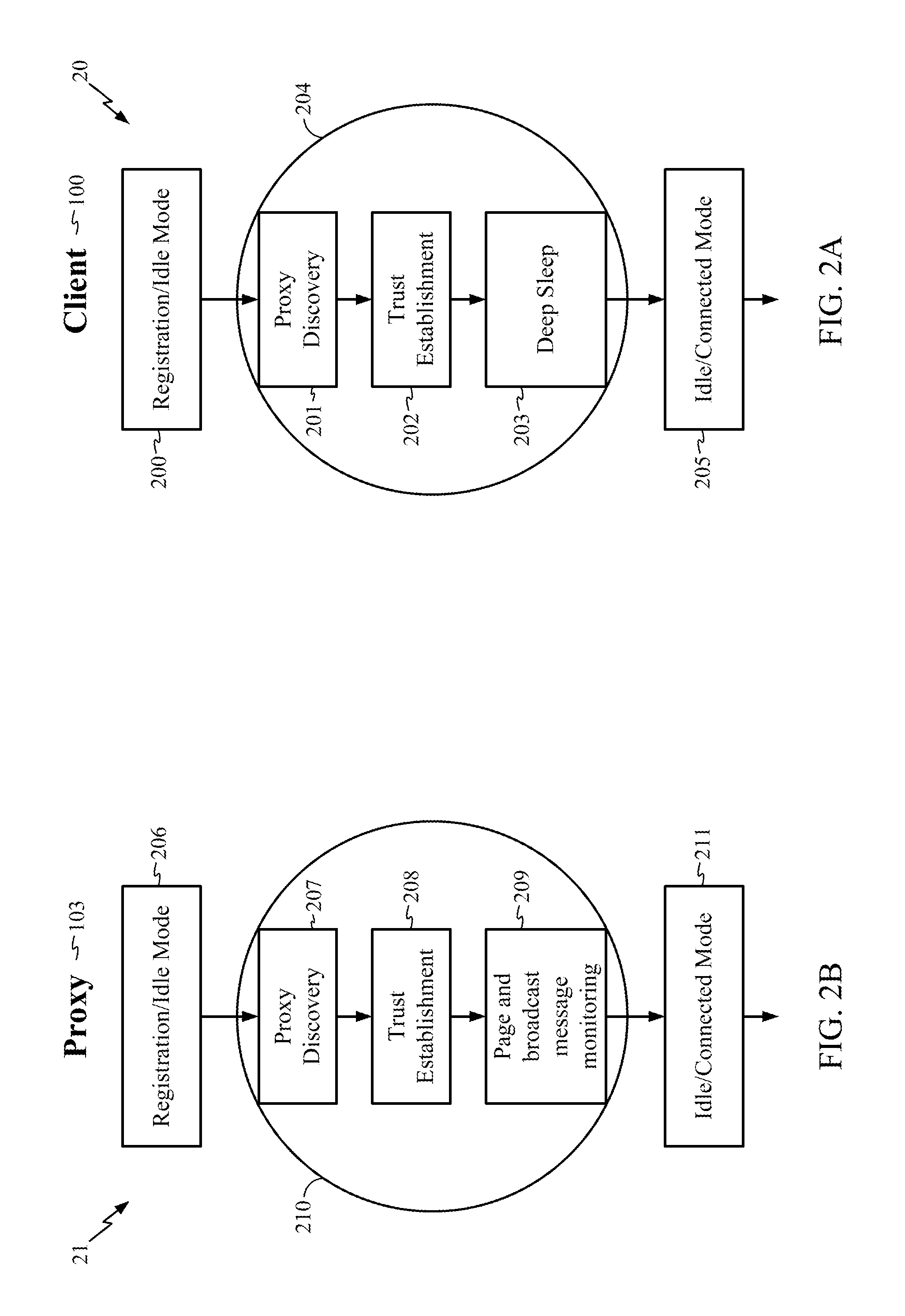
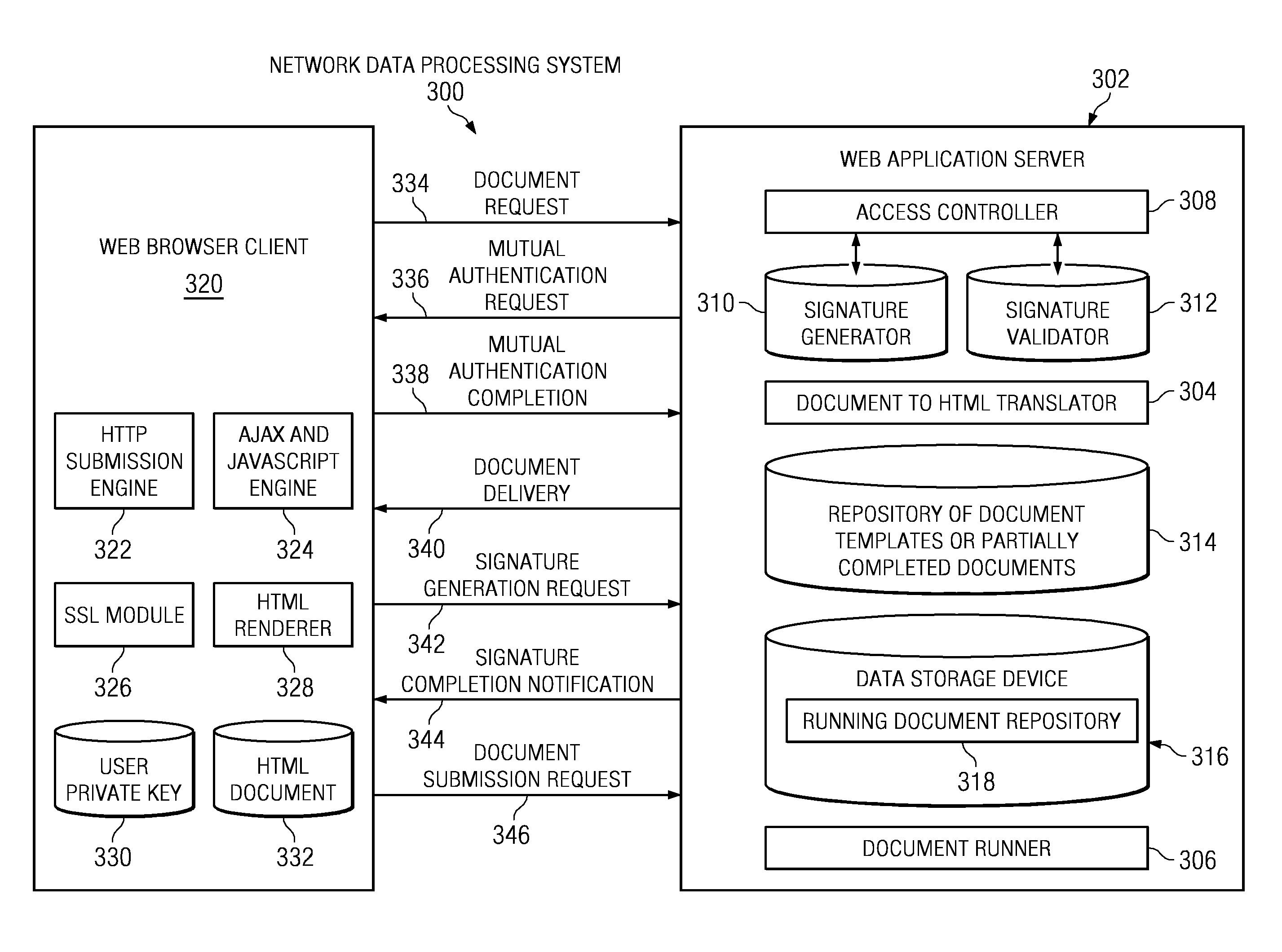
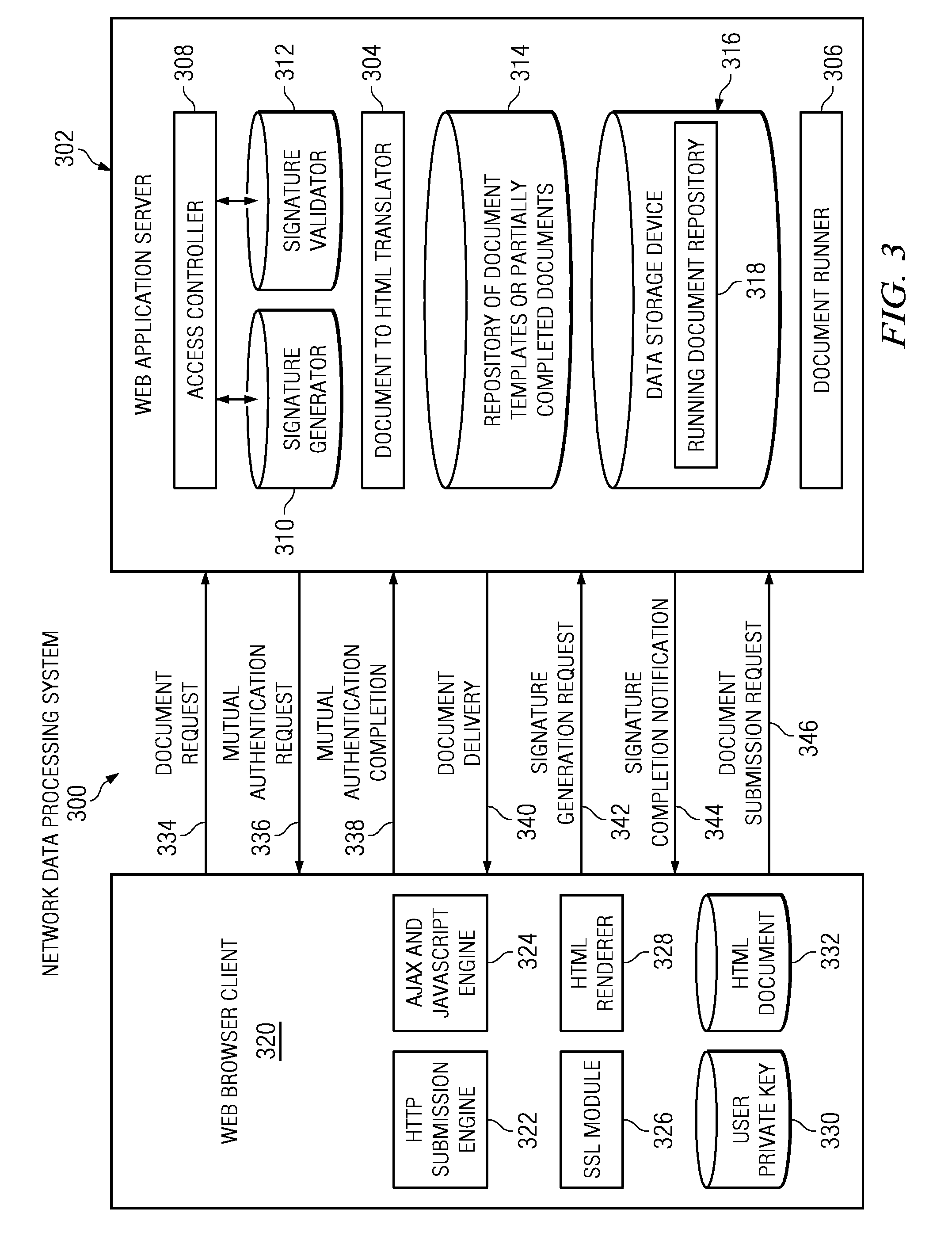
ActiveUS20090158043A1Speed up the processUser identity/authority verificationDigital data protectionApplication softwareWeb application security
The illustrative embodiments provide a computer implemented method, apparatus, and computer program product for receiving a request from a client to instantiate an electronic document. After successful completion of mutual authentication between a web application server and the client, the web application server provides the electronic document to the client. The web application server may then receive a set of changes associated with the electronic document to form a modified document. After receiving a request from the client for a digital signature to be generated for the modified document, the web application server generates a digital signature using a private key of the web application server and an identity of an end-user associated with the client. The web application server then signs the modified document with the digital signature.
Owner:IBM CORP
Method for improving network application security and system thereof
ActiveUS20110113251A1Improving network application securityDigital data processing detailsUser identity/authority verificationNetwork intelligenceComputer terminal
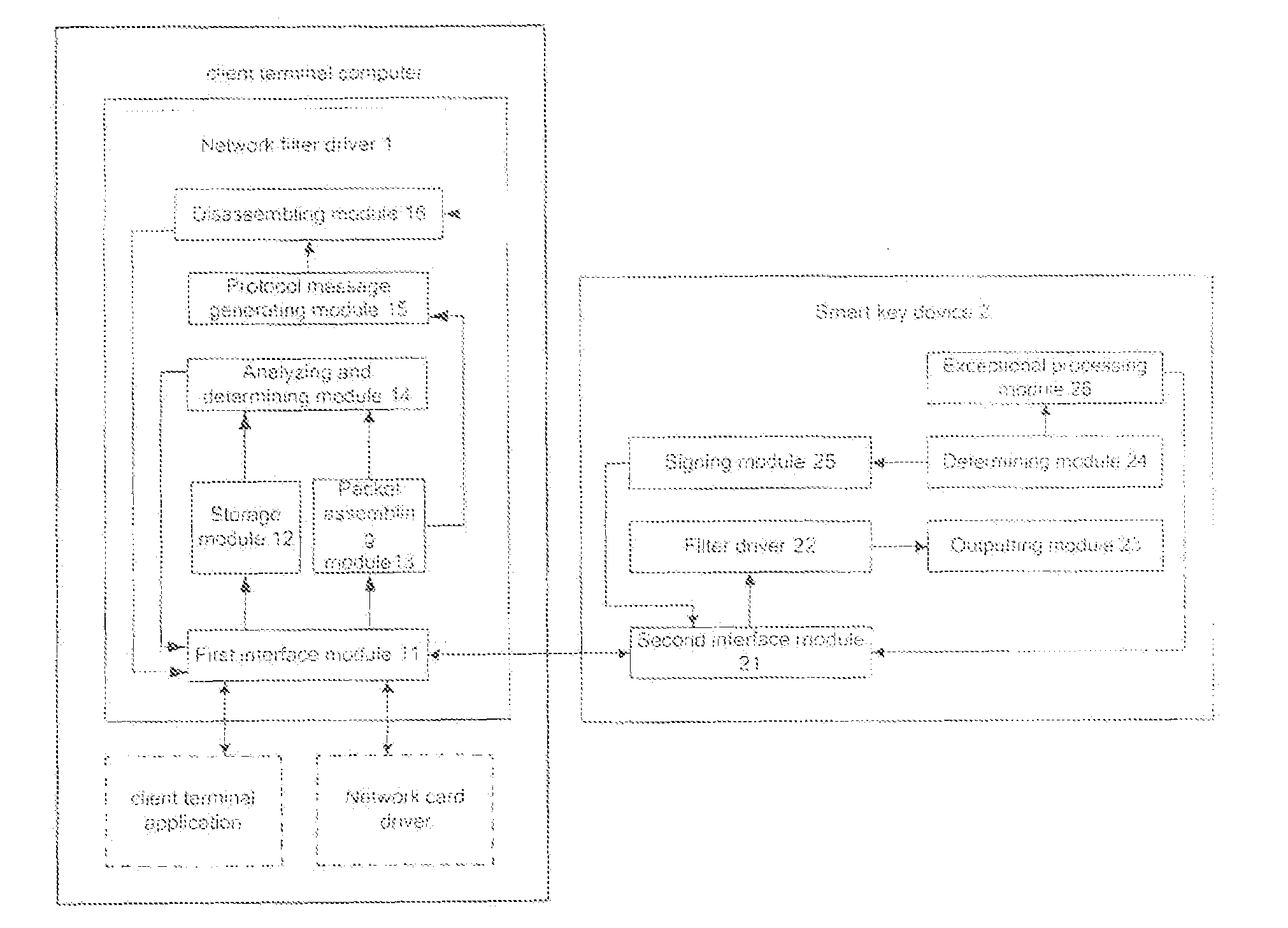
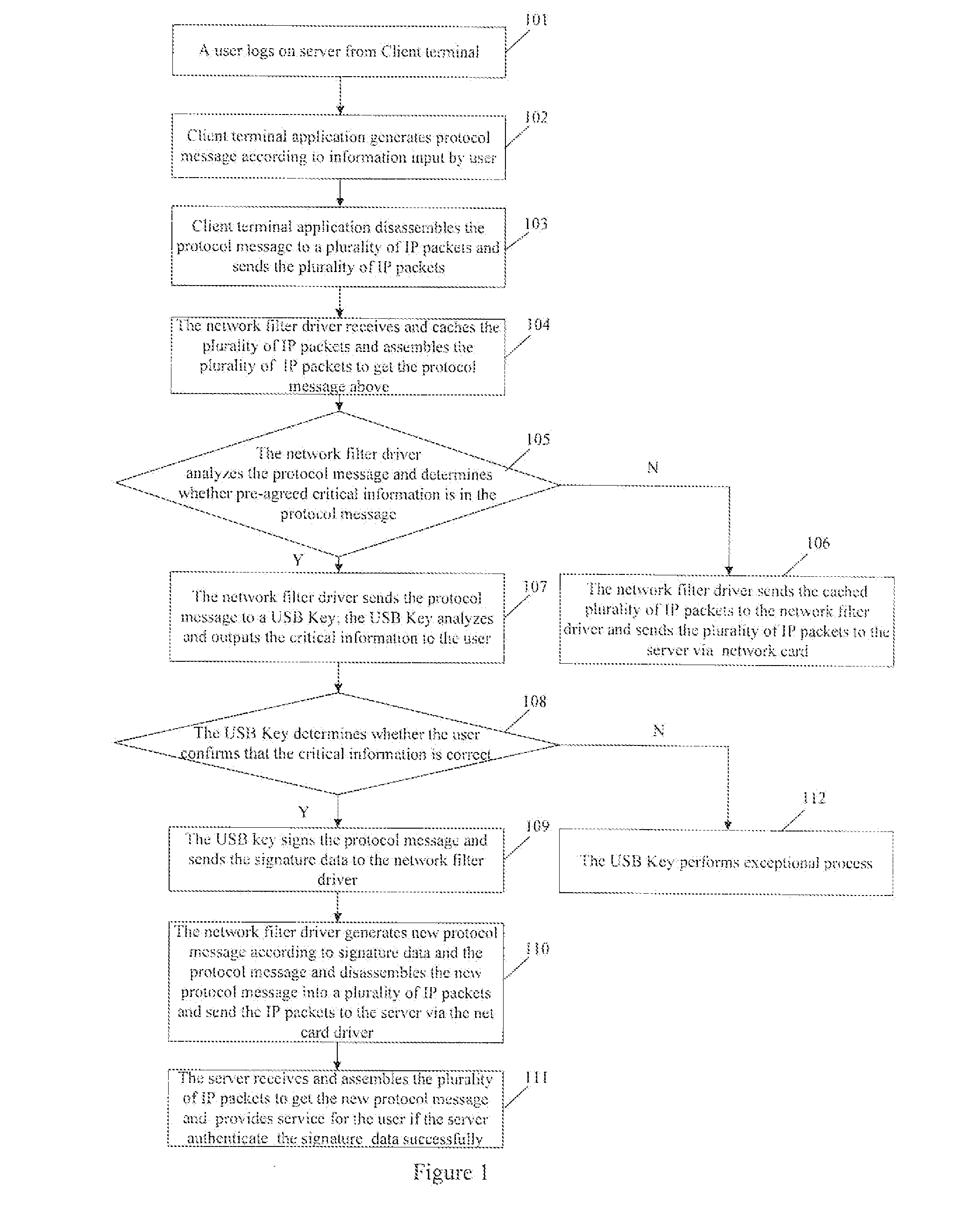
The invention, related to information security field, discloses a method for improving network application security and a system thereof. The method comprises that client terminal application generates protocol message and disassembles the protocol message to plural IP packets and sends the plural IP packets; network filter driver receives and caches the plural IP packets and assembles the plural IP packets to obtain the protocol message and determines whether critical information is in the protocol message; if so, the network filter driver sends the protocol message to a smart key device; the smart key device analyzes the protocol message to obtain the critical information and sends the critical information to the user for confirming, if the user confirms that the critical information is correct, the network smart key device signs the protocol message and returns the signature data, the network filter driver generates new protocol message according to the signature data and the protocol message and disassembles the new protocol message to plural IP packets and sends the plural IP packets to the server via network card driver; if the user confirms that the critical information is not correct or no confirmation is received from user in predetermined time period, the smart key device performs exceptional operation. The system comprises a smart key device and network filter driver of client terminal computer. With compatibility and usability, the invention enhances network application security without modifying the client terminal.
Owner:FEITIAN TECHNOLOGIES
User behavior mode digging system and user behavior mode digging method
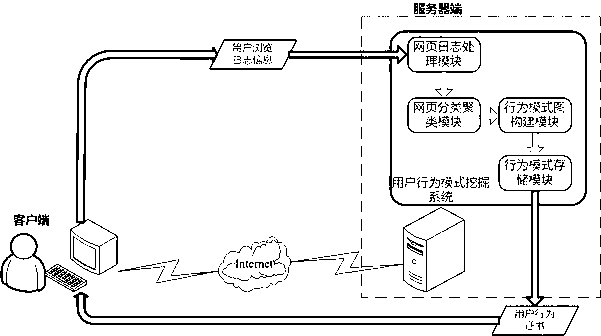
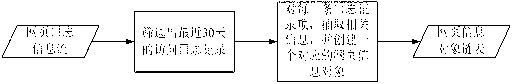
ActiveCN102999572APasswords are less reliableImprove recognition rateSpecial data processing applicationsIdentity recognitionNetizen
The invention relates to a user behavior mode digging system and a user behavior mode digging method. The whole user behavior mode digging system is deployed at a server and is used for receiving user log browsing information submitted by a client, recording access logs that a user browses web pages and accomplishing corresponding data preprocessing according to recent web page access log information of the user, extracting main access behaviors, establishing an initial behavior mode graph, storing the user behavior mode and issuing the user behavior mode as a user behavior certificate so as to be downloaded by the client. The method has transportability, is convenient to configure and needs no support of third-party software. By utilizing the system, the real user identity recognition rate is improved, and under the condition that the reliability of a user password is reduced and a user account password is stolen by lawbreakers, the personal property security and benefits of vast network users are enhanced, and the web application security is guaranteed.
Owner:TONGJI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com