Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
154 results about "String Data." patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
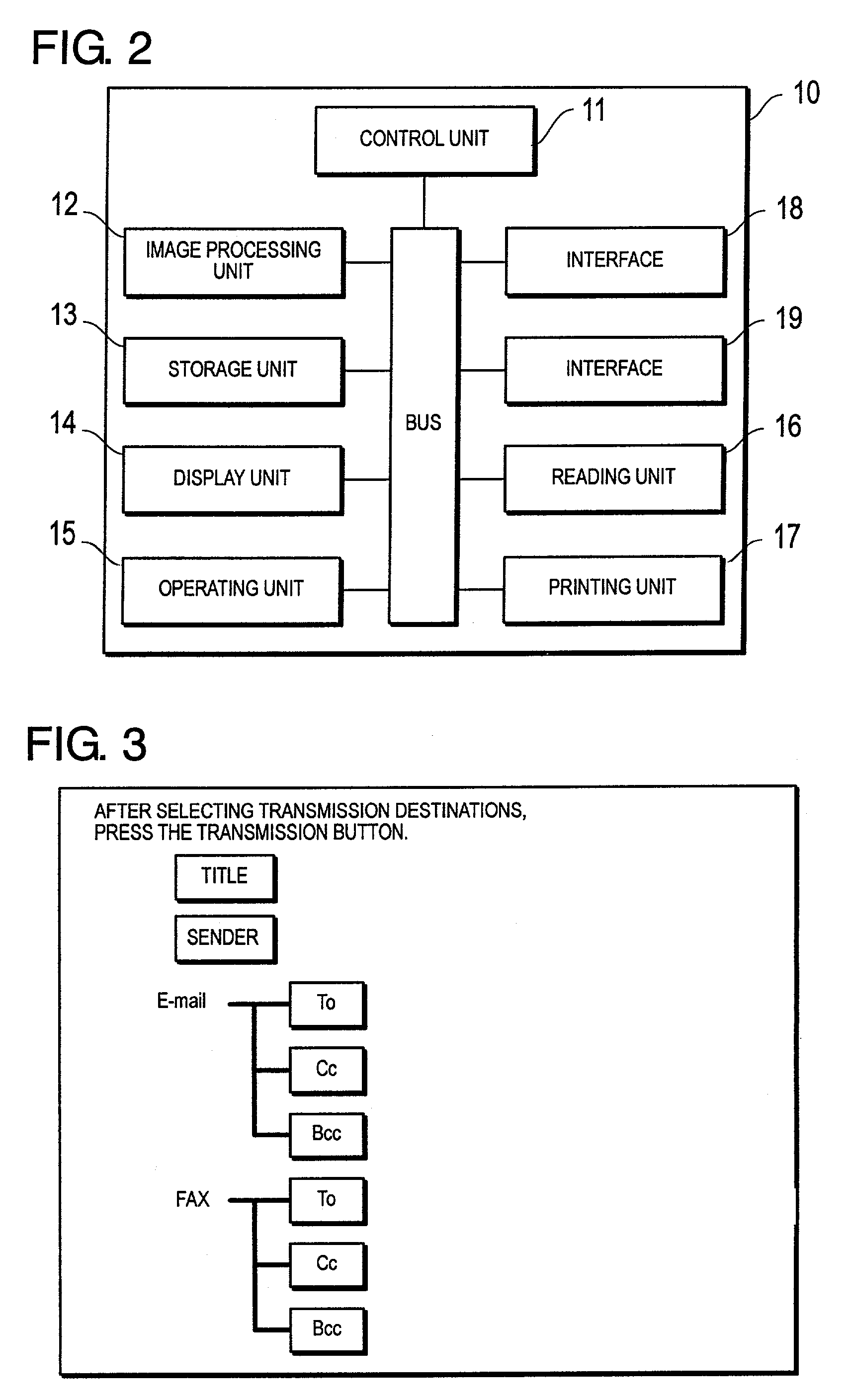
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A string is generally considered a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. String may also denote more general arrays or other sequence (or list) data types and structures.
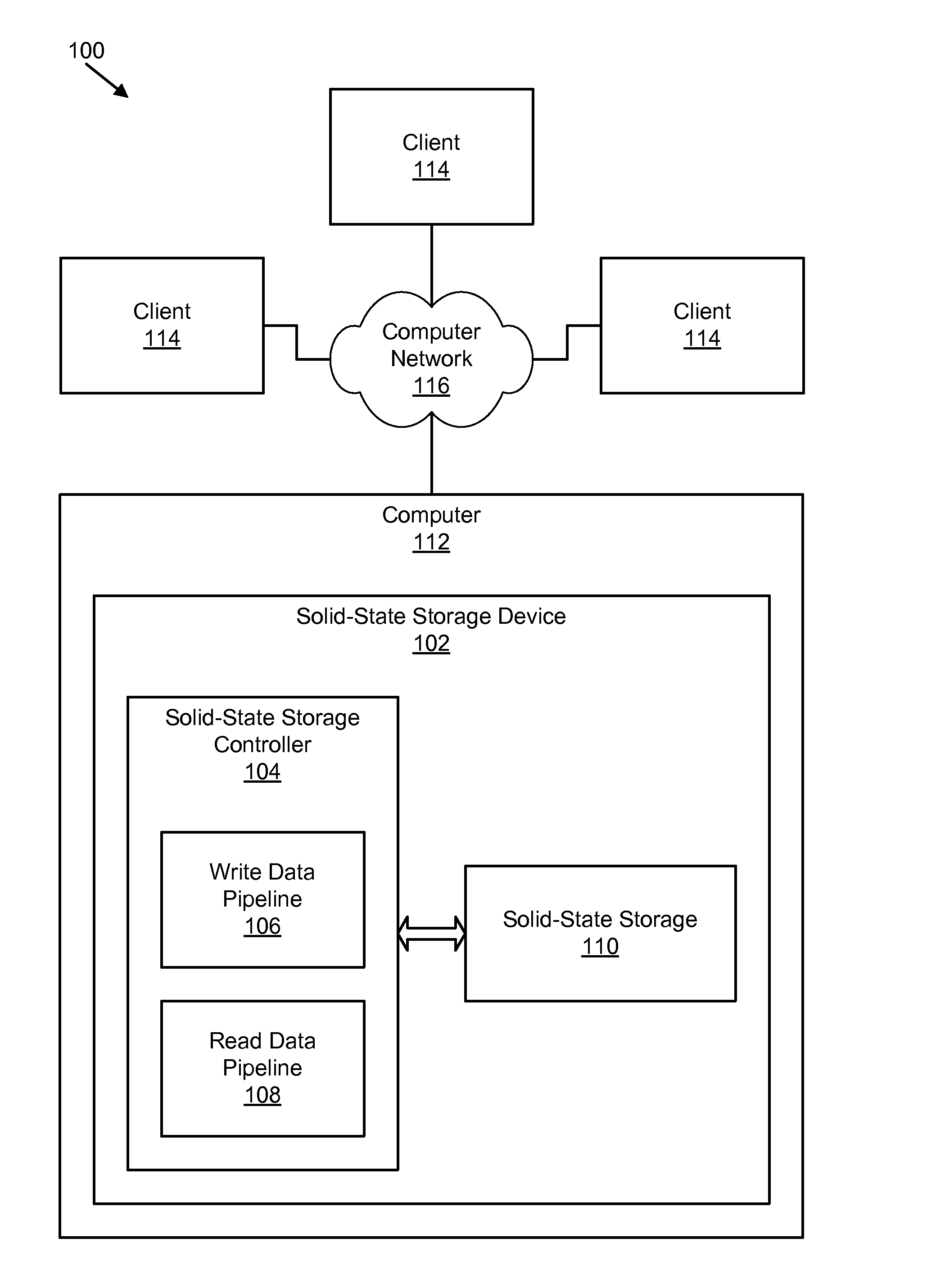
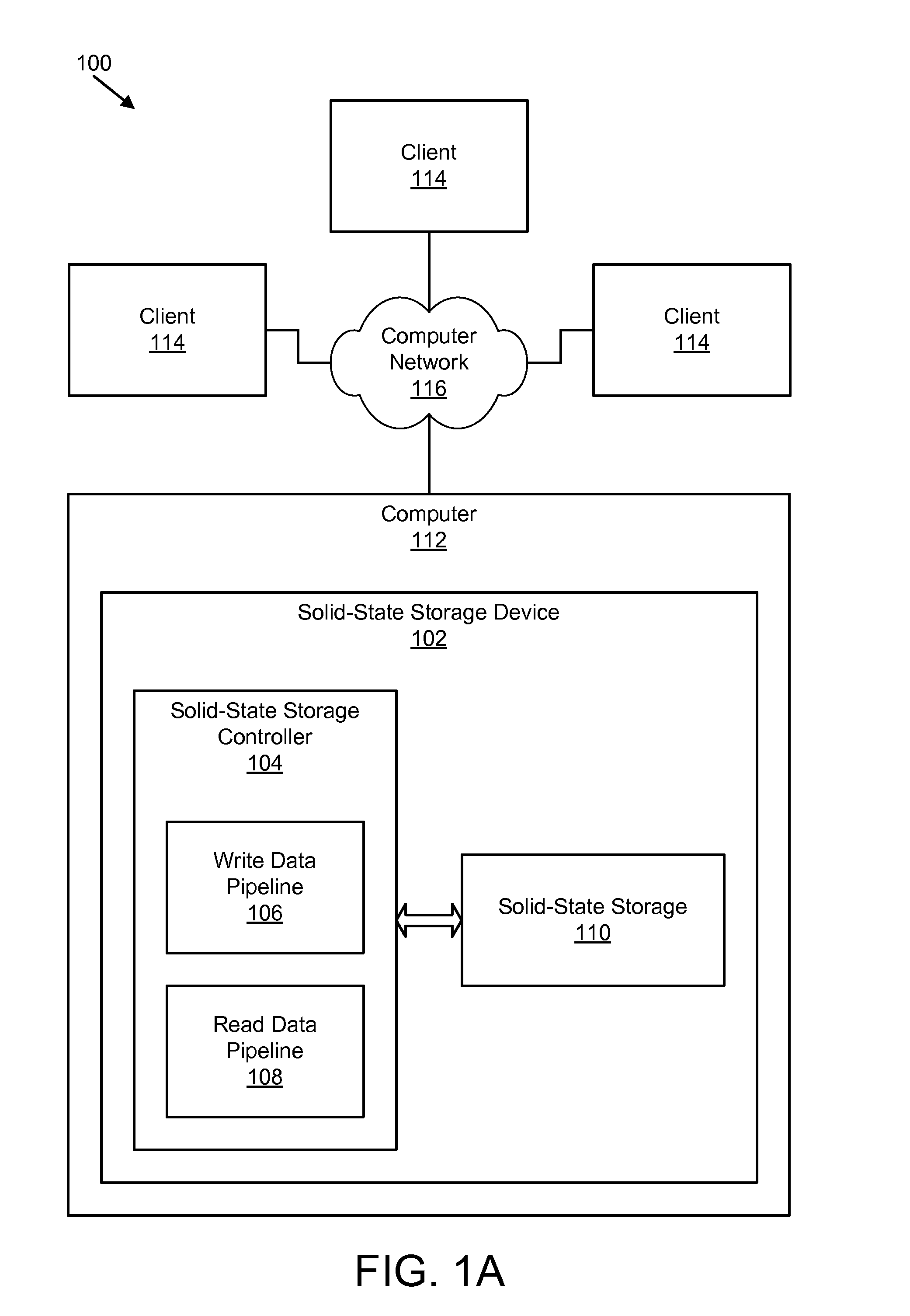
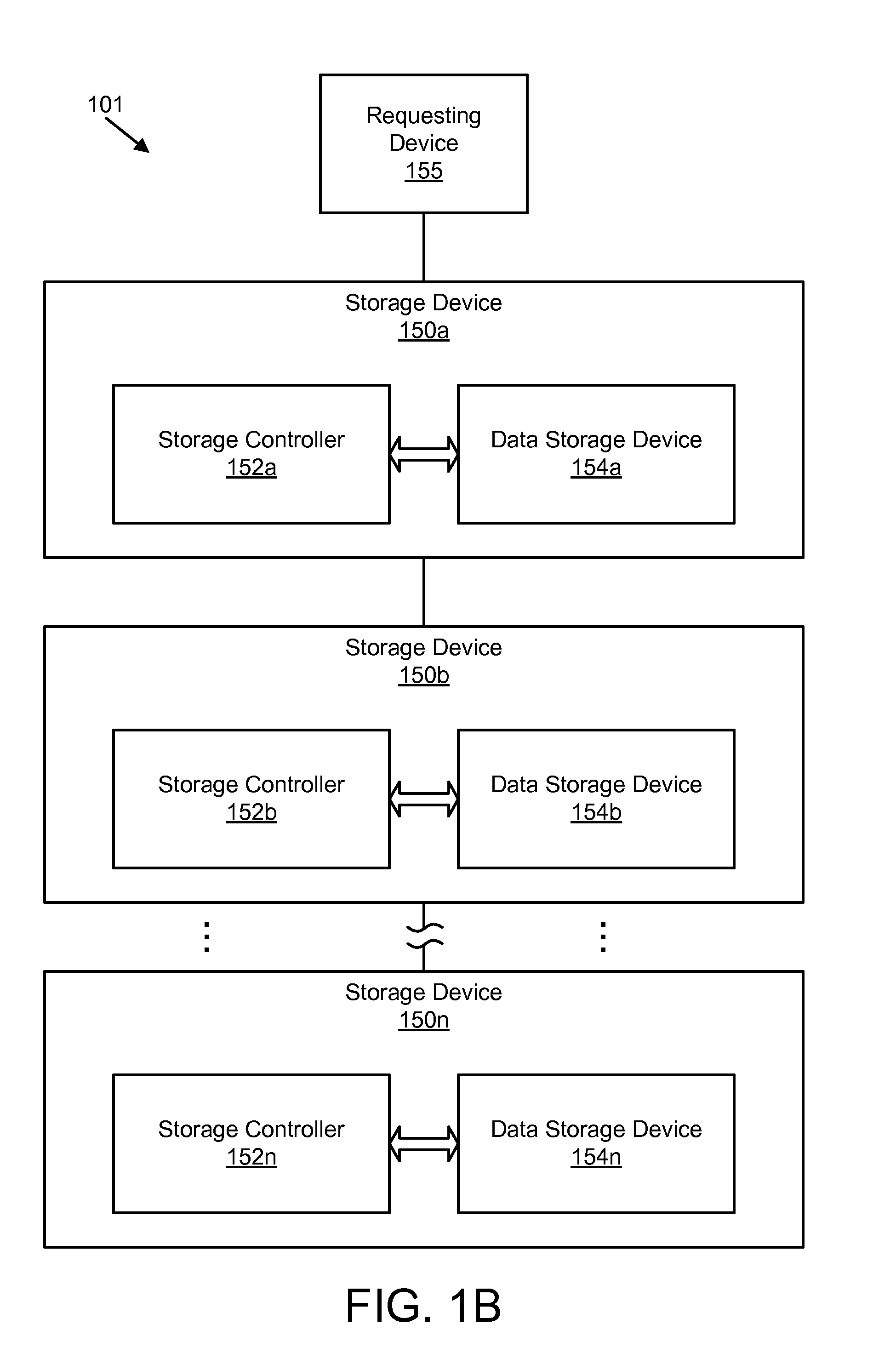
Apparatus, system, and method for managing data in a storage device with an empty data token directive
An apparatus, system, and method are disclosed for managing data with an empty data segment directive at the storage device. The apparatus, system, and method for managing data include a write request receiver module and a data segment token storage module. The write request receiver module receives a storage request from a requesting device. The storage request includes a request to store a data segment in a storage device. The data segment includes a series of repeated, identical characters or a series of repeated, identical character strings. The data segment token storage module stores a data segment token in the storage device. The data segment token includes at least a data segment identifier and a data segment length. The data segment token is substantially free of data from the data segment.
Owner:UNIFICATION TECH LLC
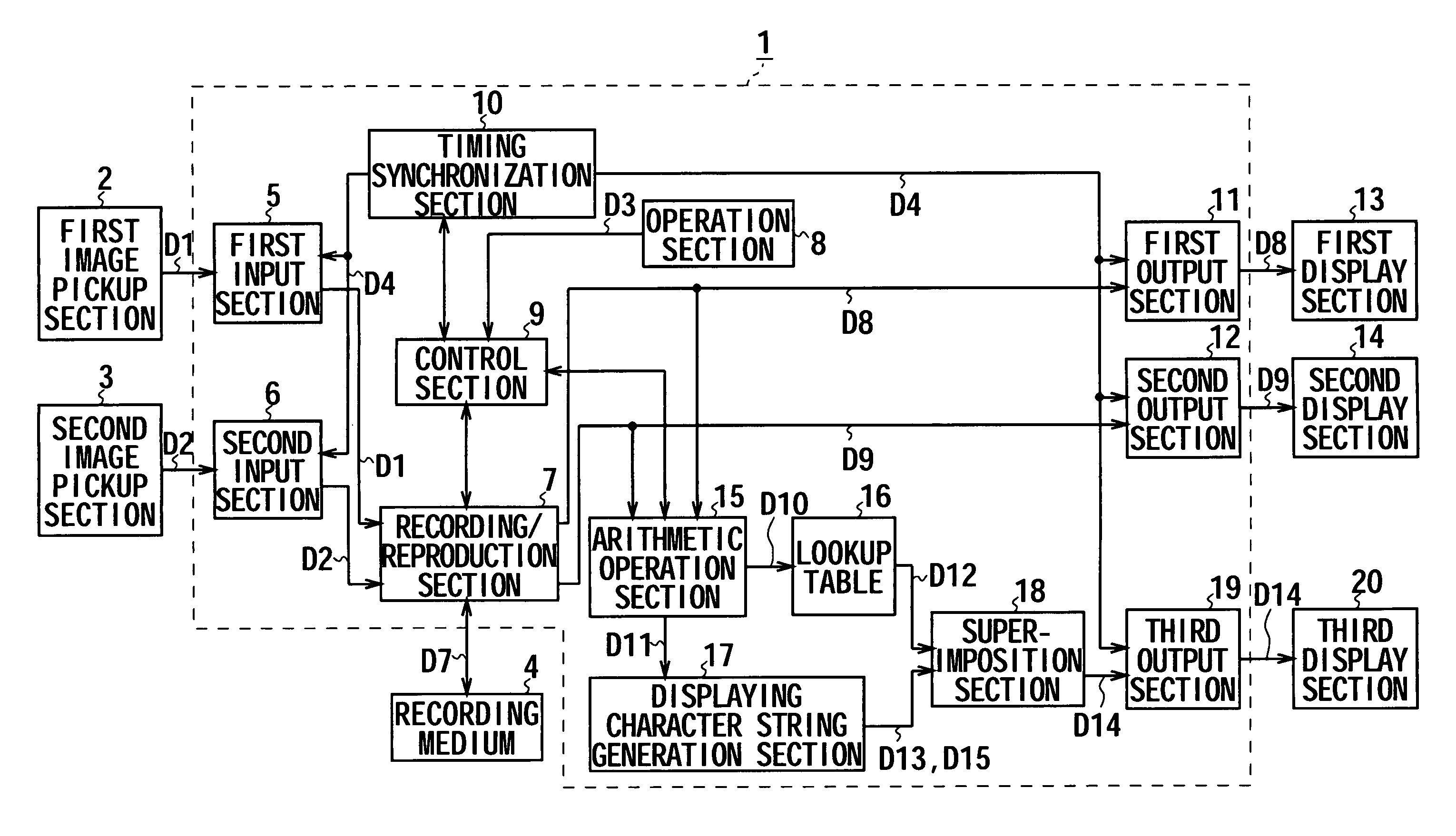
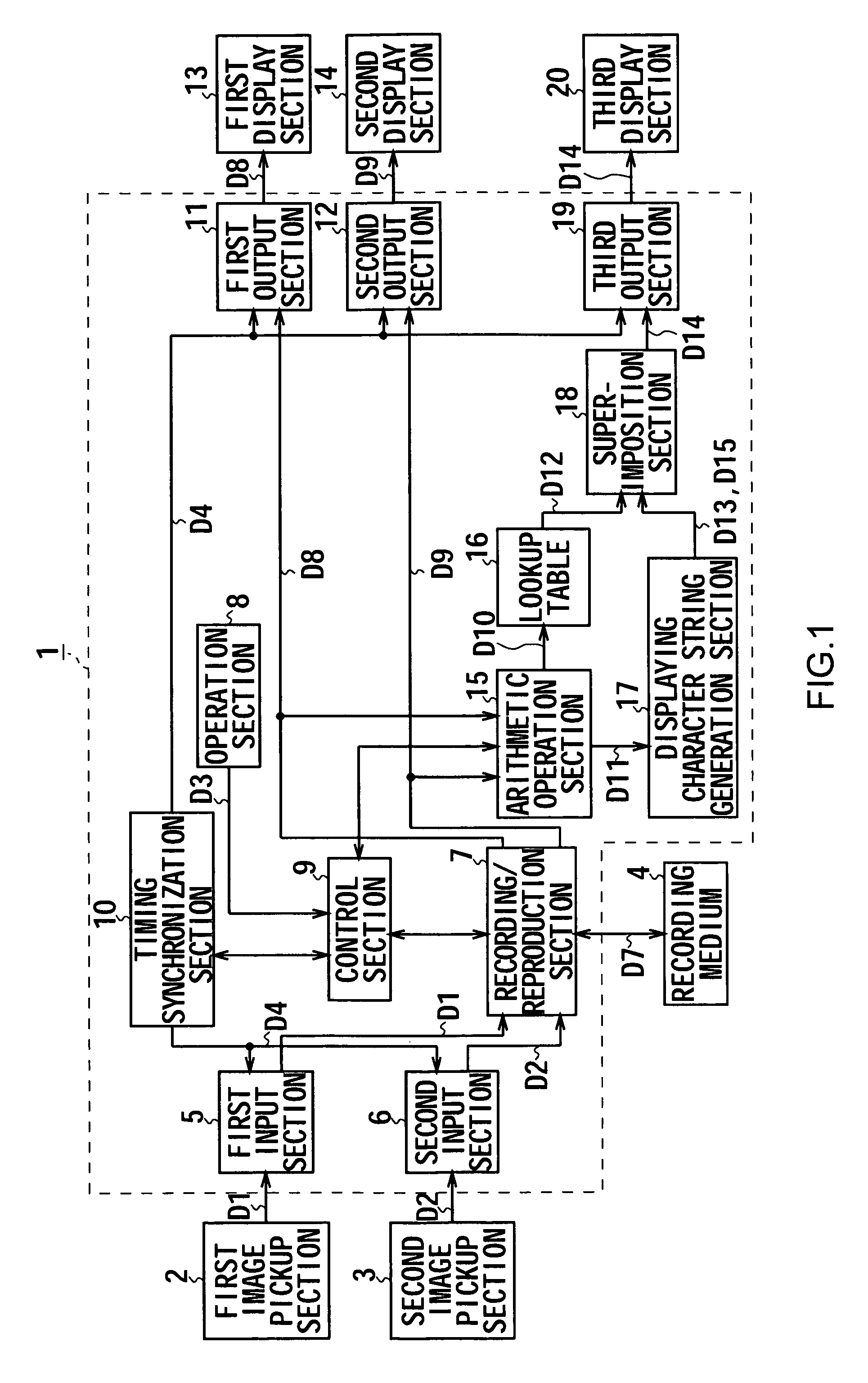
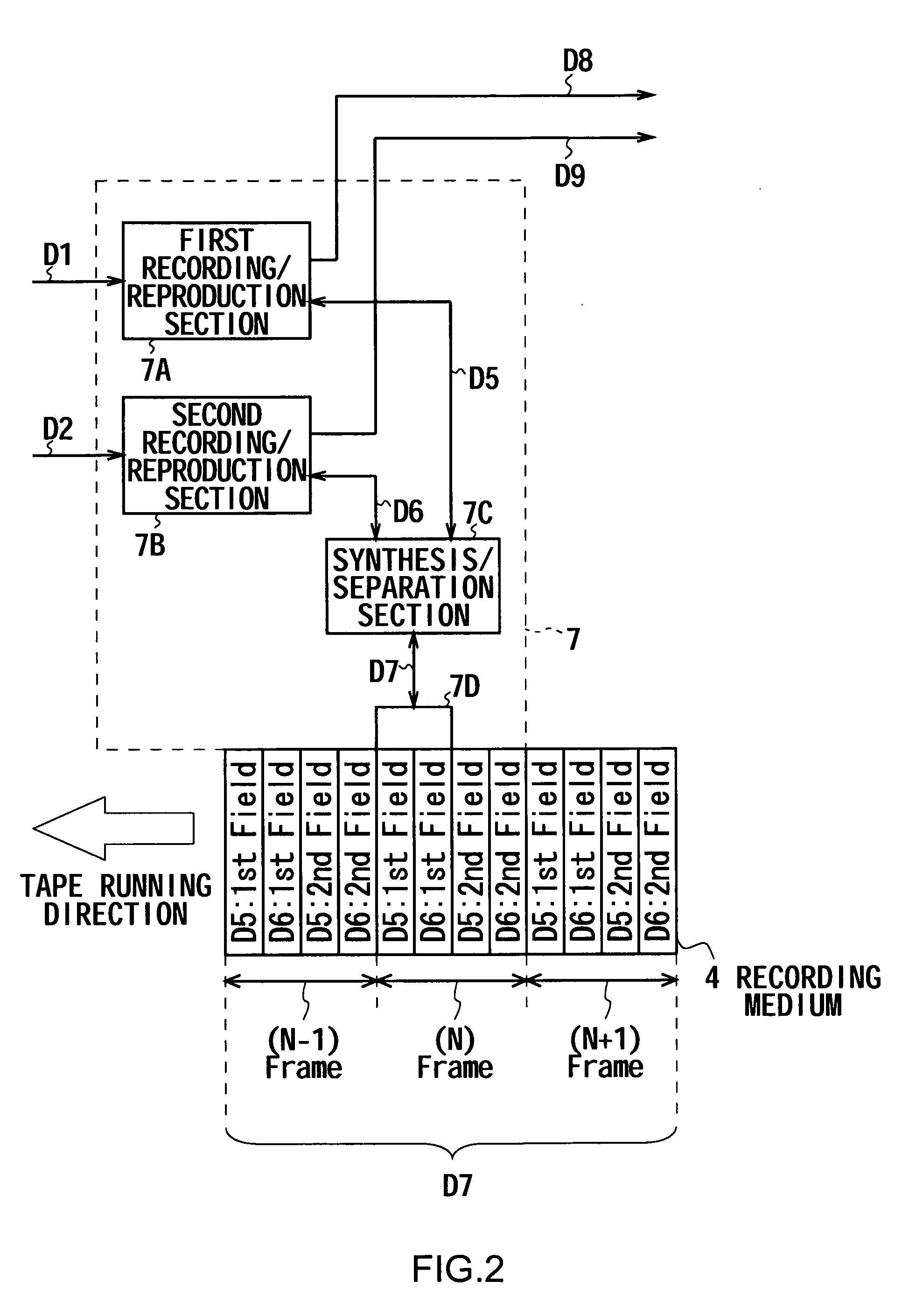
Recording/reproduction apparatus, and recording/reproduction method as well as stereoscopic image visual effects confirmation apparatus and stereoscopic image visual effects confirmation method
InactiveUS20060210249A1Television systemsDigital recording/reproducingComputer graphics (images)Superimposition
The present invention relates to an apparatus and a method for recording / reproduction of images with which the visual effects of a plurality of images can be visually confirmed with ease. The apparatus includes a recording / reproduction section that records a plurality of input sets of video data and reads them from the recording mediums for reproduction; an arithmetic operation section that performs arithmetic operations by a method corresponding to an external instruction on the plurality of sets of video data reproduced by the recording / reproduction section; and a superimposition section that generates character-string data indicating the arithmetic operation method of the arithmetic operation section, superimposes the arithmetic video data produced by arithmetic operations of the arithmetic operation section and the character-string data and outputs the superimposed video data produced by the superimposition as outcome of arithmetic operations.
Owner:SONY CORP
Data communication apparatus, data communication system, data communication method, control program, and computer readable storage medium stored with control program
InactiveUS7224491B2Special service provision for substationTelephonic communicationCommunications systemFacsimile
A data transmission apparatus including a multicasting means for executing multicasting transmission for a mixture of e-mails and facsimiles, a destination setting means for setting destinations of the multicasting transmission, a first adding means for, based on e-mail destinations set by the destination setting means, generating image data representing the e-mail destinations, and adding the image data to an image data to be transmitted as a facsimile by the multicasting transmission, and a second adding means for, based on facsimile destinations set by the destination setting means, generating character string data representing the facsimile destinations and adding the character string data to an e-mail to be transmitted by the multicasting transmission.
Owner:MINOLTA CO LTD
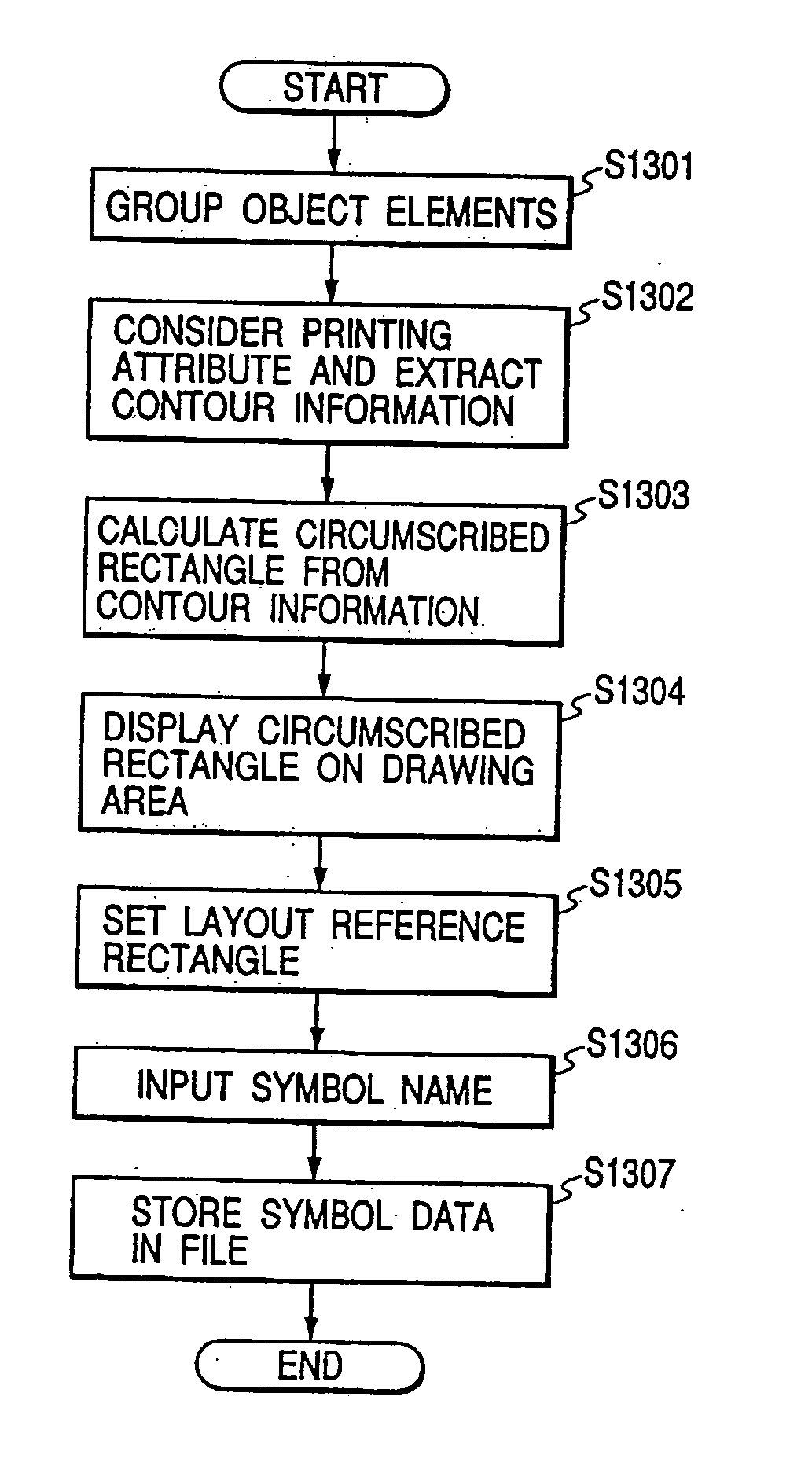
Information processing apparatus and information processing method
InactiveUS20050168778A1Easy to prepareWork can be droppedDigitally marking record carriersDrawing from basic elementsInformation processingArtificial intelligence
Information that is required for laying out character string data is entered, as are character string data. The printing attributes for the data are then edited, and are employed to extract contour information. Thereafter, the extracted contour information is employed to determine the information that is to be used as a reference when laying out the character string data, and a layout position is specified. Then, the various data that are obtained are stored as printing data, and the character string data are laid out in a drawing area. Therefore, the printing data can be precisely and easily prepared, without the work efficiency of a user being deteriorated.
Owner:CANON KK
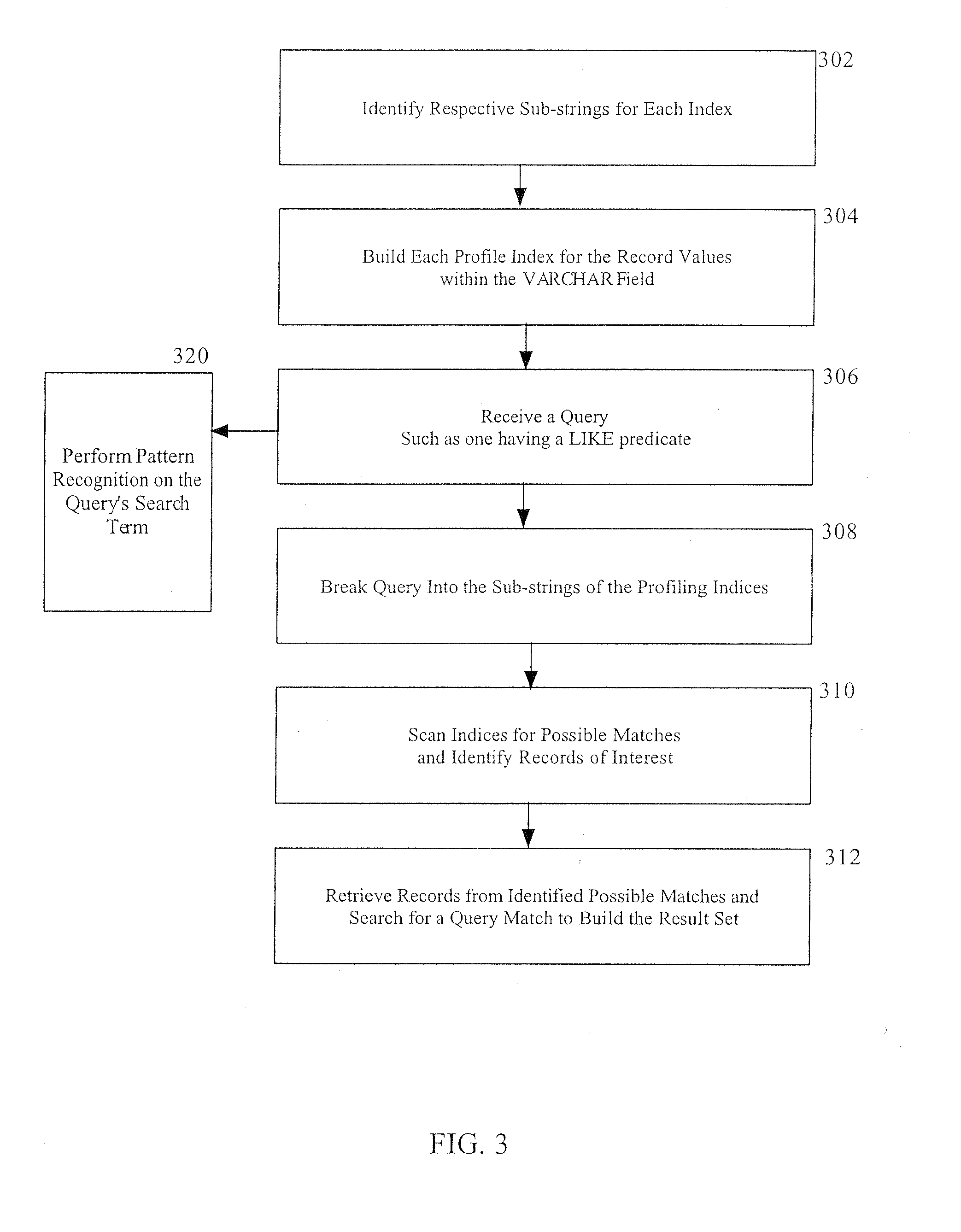
Method and system for creating profiling indices
InactiveUS20050154757A1Reduce in quantityData processing applicationsDigital data information retrievalDatabase engineData type
A database engine and optimizer framework support creation of a series of profiling indices over a column having character string data, such as a traditional “varchar” data type. The profiling indices result in a reduction of the number of records that are searched when searching for a sub-string match within that column. In some embodiments, the series of indices are created over a column that is typically searched using the LIKE predicate or some similar technique; these indices indicate for each record whether certain sub-strings may exist in that record's value in the column. Thus, the indices are used to find the rows that may match one or more portions of the particular term being queried or, in other words, eliminate those records that do not have at least a portion of the term to be matched. The number of records actually retrieved and searched for the query sub-string is thereby reduced.
Owner:IBM CORP
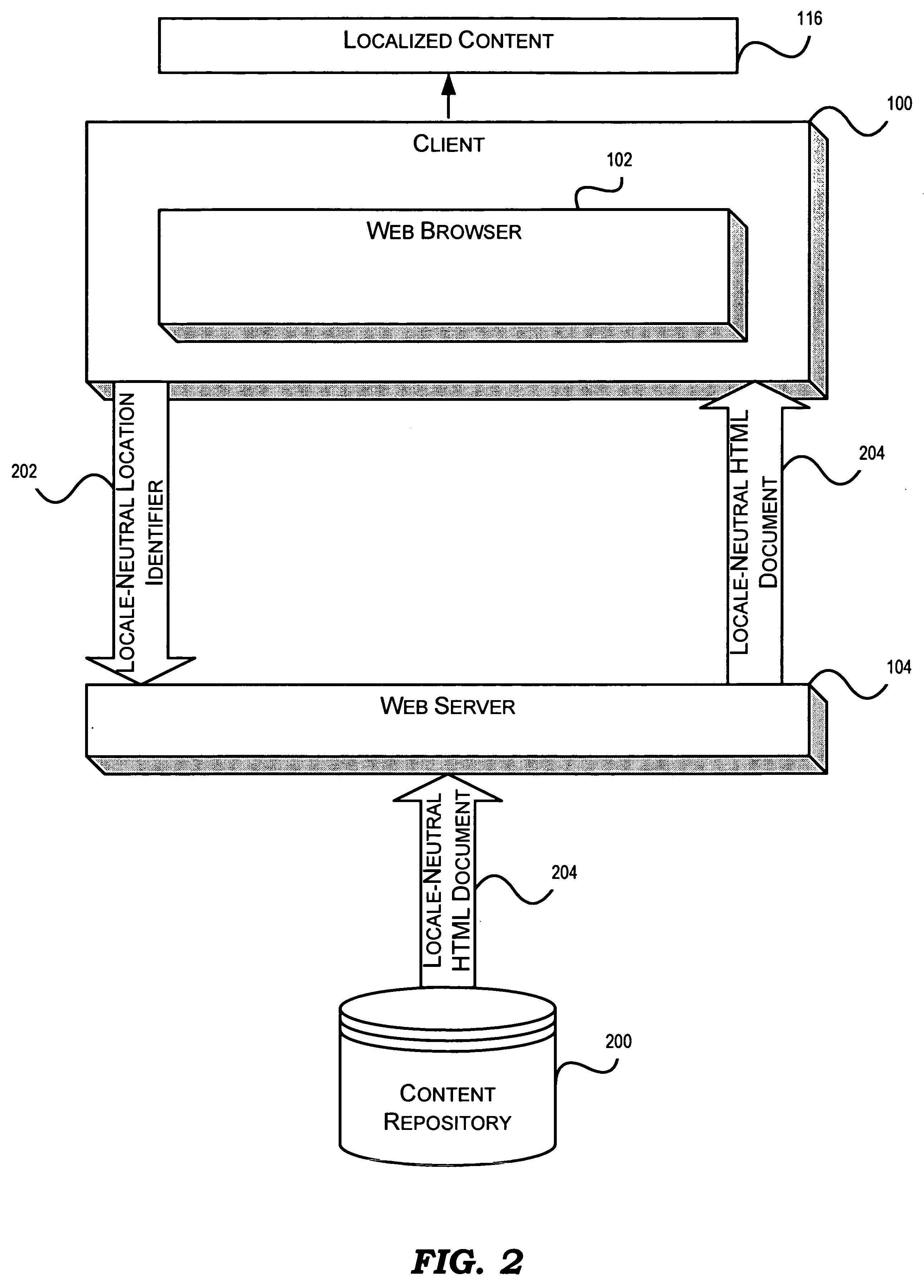
Dynamic localization for documents using language setting
InactiveUS20050102616A1Natural language translationSpeech analysisNatural language processingPaper document
A method, for dynamic document localization, includes issuing a request for locale-neutral content, the request having a locale-neutral identifier. The locale-neutral content is received responsive to the request. Localized language content is built by applying a language setting for a current language selection to the locale-neutral content. The language setting includes a language-specific string in a strings data structure corresponding to the current language selection.
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT
Method and system for creating profiling indices
InactiveUS20080059418A1Reduce in quantityData processing applicationsDigital data information retrievalDatabase engineData type
A database engine and optimizer framework support creation of a series of profiling indices over a column having character string data, such as a traditional “varchar” data type. The profiling indices result in a reduction of the number of records that are searched when searching for a sub-string match within that column. In some embodiments, the series of indices are created over a column that is typically searched using the LIKE predicate or some similar technique; these indices indicate for each record whether certain sub-strings may exist in that record's value in the column. Thus, the indices are used to find the rows that may match one or more portions of the particular term being queried or, in other words, eliminate those records that do not have at least a portion of the term to be matched. The number of records actually retrieved and searched for the query sub-string is thereby reduced.
Owner:IBM CORP
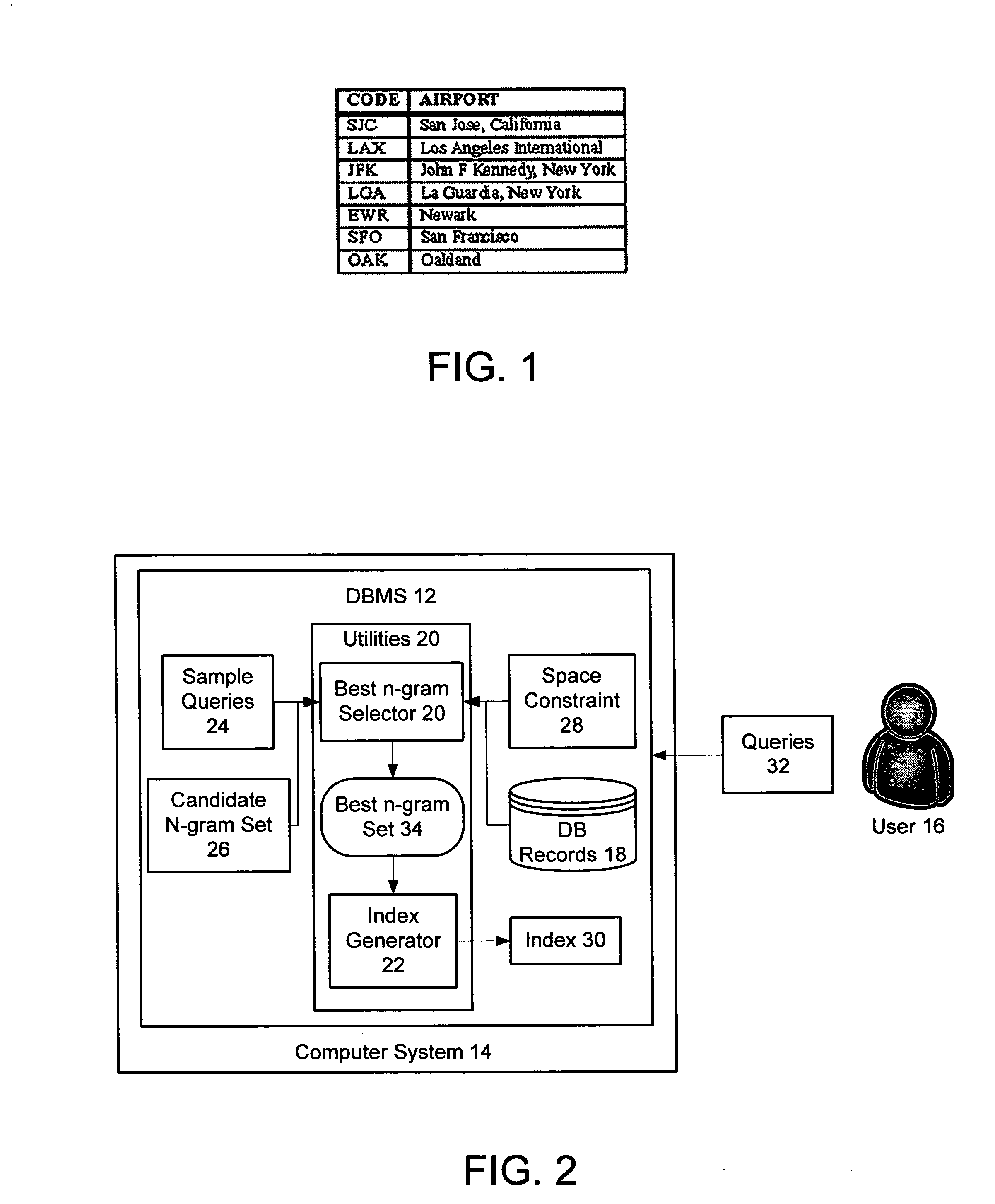
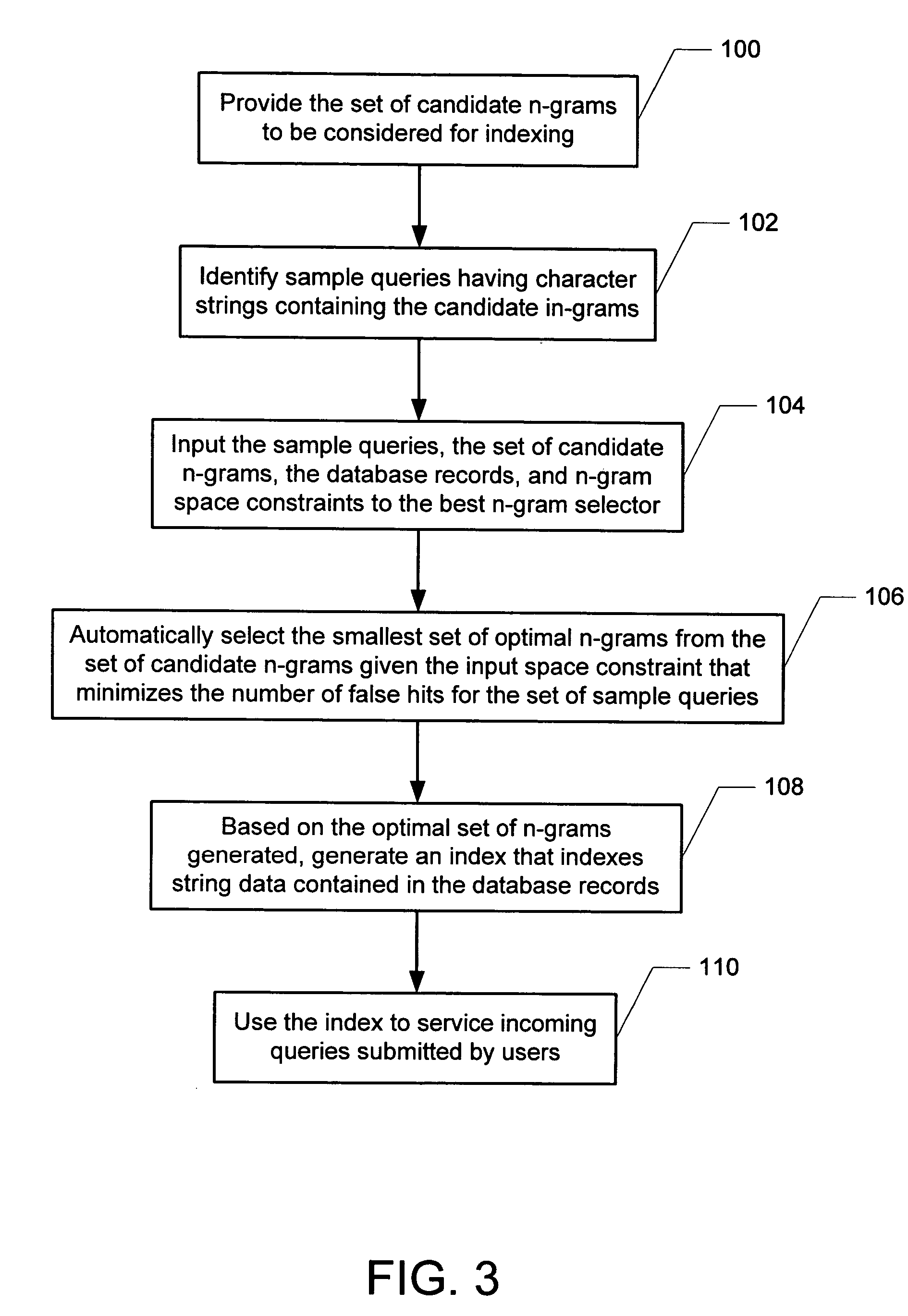
Selection of a set of optimal n-grams for indexing string data in a DBMS system under space constraints introduced by the system
InactiveUS20060101000A1Minimize the numberData processing applicationsDigital data information retrievalTheoretical computer scienceString Data.
The present invention provides a computer-readable medium and system for selecting a set of n-grams for indexing string data in a DBMS system. Aspects of the invention include providing a set of candidate in grams, each n-gram comprising a sequence of characters; identifying sample queries having character strings containing the candidate n-grams; and based on the set of candidate n-grams, the sample queries, database records, and an n-gram space constraint, automatically selecting, given the space constraint, a minimal set of an n-grams from the set of candidate n-grams that minimizes the number of false hits for the set of sample queries had the sample queries been executed against the database records.
Owner:IBM CORP
Order-preserving encryption method based on random interval partition
ActiveCN102843372ASolve the problem of order-preserving encryptionSolve matching problemsTransmissionCiphertextRelational calculus
The invention relates to an order-preserving encryption method based on random interval partition. The method provides a weighted random interval partition algorithm and an order-preserving random interval tree according to the fact that an existing algorithm is generated by random numbers based on interval partition, and the safe problem existing in the fact that intervals are divided in fixed mode is resolved. The order-preserving encryption method can effectively resolves the problem of order-preserving and encryption of character string data, analysis and testament show that the order-preserving encryption method has linear encryption time and decryption time and constant level ciphertext expansion rate, and can effectively resist exhaustive attack and attack based on statistic analysis. The order-preserving encryption method is specially suitable for outsourcing storage of confidential data, can effectively resolve the problem of matching, scope inquiring, relational calculus and other operations of ciphertext data.
Owner:XI AN JIAOTONG UNIV
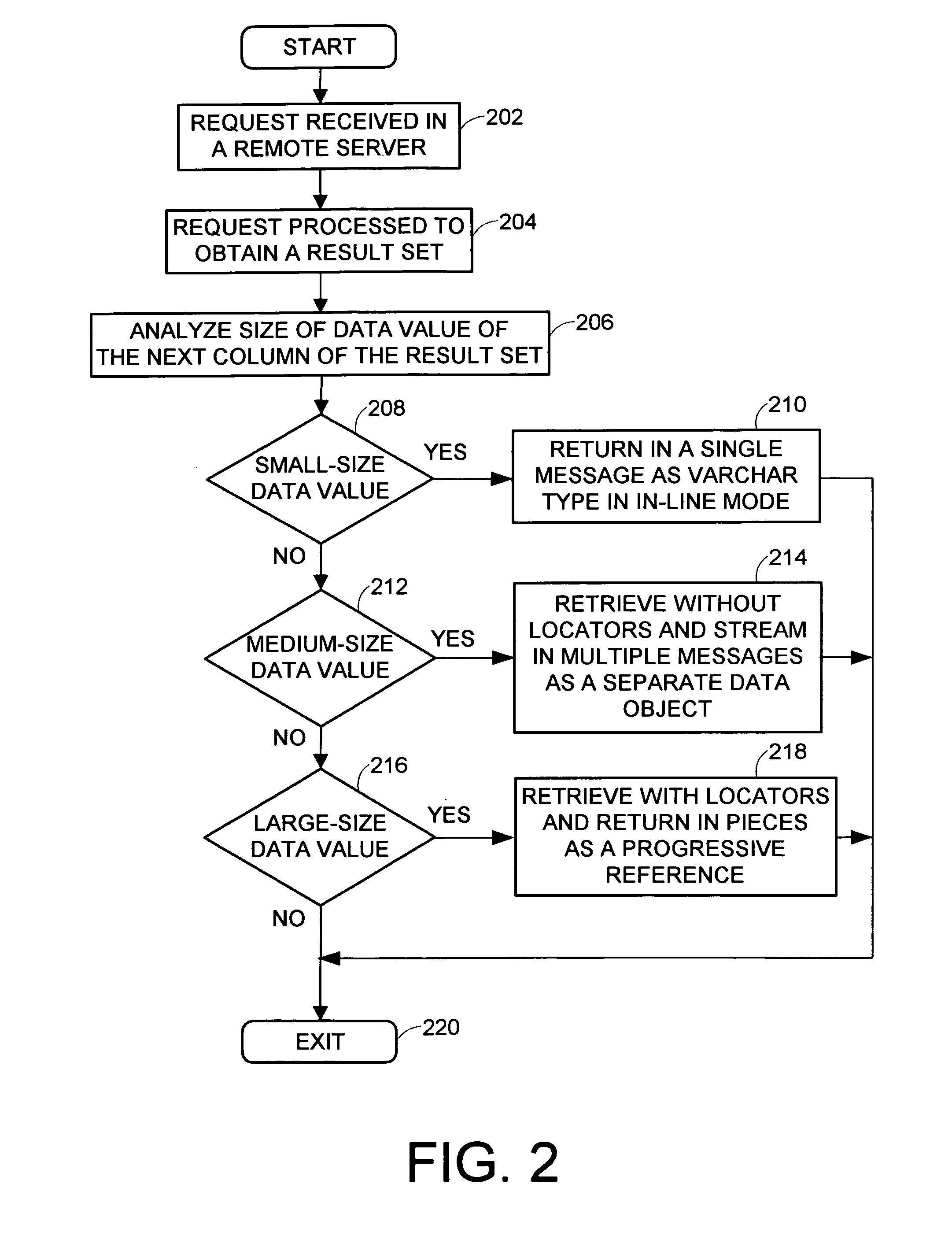
Dynamic data formatting during transmittal of generalized byte strings, such as XML or large objects, across a network
InactiveUS20070198482A1Eliminate needDigital data information retrievalSpecial data processing applicationsClient-sideResult set
A method, apparatus and program storage device is provided for dynamic data formatting during transmittal of generalized byte string data across a computer network. Remote server dynamically changes format of each column string data value from the result set separately, according to actual size of the string data value, and returns it to a client. Small-size data value is returned in a single network return message as varchar type, in-line with the rest of the query data. Medium-sized data value is retrieved without locators and streamed in multiple return network messages in a separate data object following the query data and in the same response. Large-size data value is retrieved using locators and returned as a progressive reference in pieces of specified size, where each piece of data value is separately transferred under client's control when needed, thus eliminating the need to buffer large amount of data.
Owner:IBM CORP
System and method for processing of markup language information
ActiveUS20050114762A1Natural language data processingSpecial data processing applicationsExtensible markupData mining
A system and method for processing of markup language information, such as extensible markup language (XML) based control information is disclosed. The system comprises a compression sender entity and a decompression receiver entity. The sender entity uses its internal, binary representation derived from textual XML-based protocol header and encodes the binary representation as a tag-length-value (TLV) binary value. The TLV binary value is embedded as encoded data in a specifically marked comment, which may be detected by the receiver entity. The receiver entity builds up an internal, binary data structure based on the encoded data representing the original XML data. The system avoids the usage of string data to represent a small set of well known strings and uses a more compact binary encoding which reduces space and time to process the data.
Owner:TWITTER INC
Computer-readable recording medium recorded with printing program
InactiveUS20080170264A1Inhibition lossSmall sizeDigital computer detailsCharacter and pattern recognitionData storingData store
A computer-readable recording medium recorded with a printing program causes a processor of a computer to calculate a rendering area of print data stored in a storing section of the computer as a primary area based on the print data, and to calculate a rendering area of commentary string data to be attached to the print data as a sub-area. The program then judges whether the primary area and the sub-area overlap, and whether the sub-area deviates from an effective printing area. The commentary string data can be changed so that the primary area and the sub-area do not overlap, and so that the entire sub-area is within the effective printing area, if at least one of the judgment results in the judging step is affirmative. The changed commentary string data then is attached to the print data.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
A method of identifying the brand and model of a projector
ActiveCN109190623AImprove recognition accuracy and speedAccurate automatic identificationCharacter recognitionData miningAlgorithm
The invention relates to a method for identifying the brand and model of a projector, comprising the steps of: S1, acquiring an image of an area where the brand and the model of the projector are located; S2: preprocessing the collected image to extract candidate target area; S3, screening the candidate target area by adopting a target area screen strategy to obtain a target area; S4: according tothe obtained target area, recognizing the character in the target area by using the OCR technology, and obtaining the character string of the target area; S5, matching the recognized target area string with the string data in the brand and model database to obtain a matching result of the brand and model. The invention can accurately and automatically identify the brand and model text informationon the surface of the projector fuselage shell.
Owner:MINJIANG UNIV
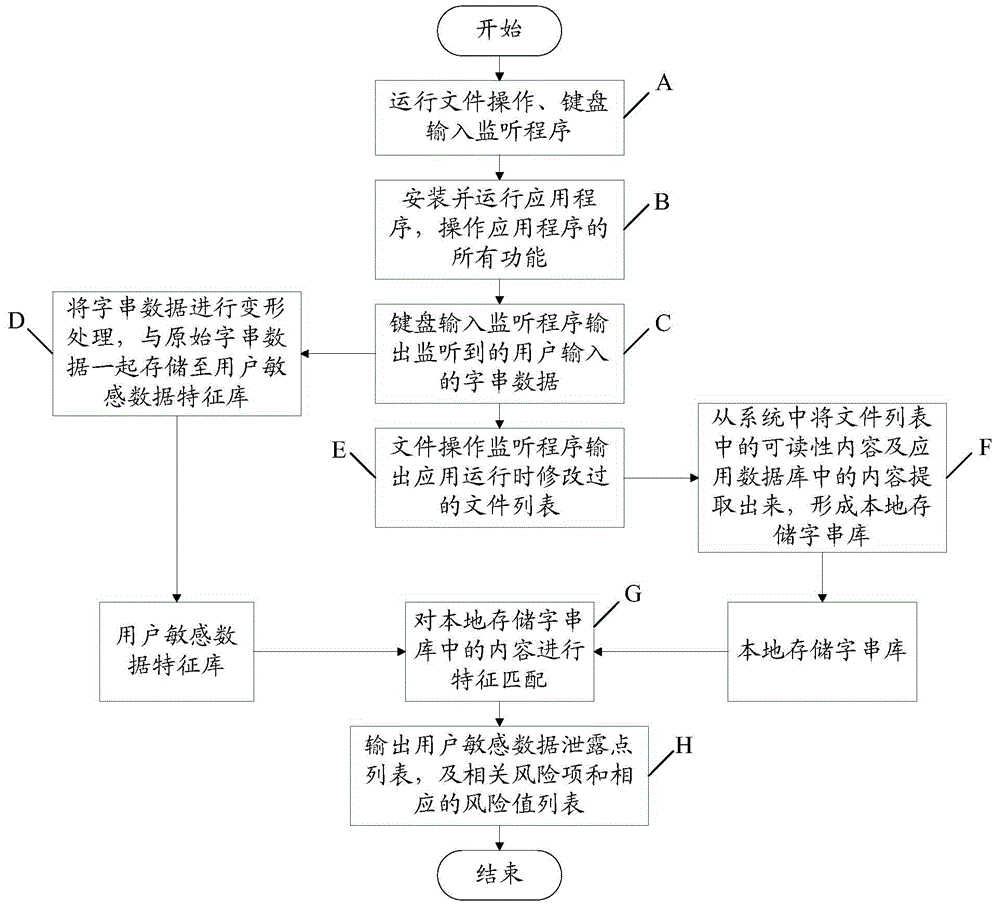
Method and device for assessing application data security risk
ActiveCN105653947AShorten assessment timeLow costPlatform integrity maintainanceData securityData mining
The invention provides a method and device for assessing the application data security risk. The method includes the following steps: acquiring first word string data in an input application; generating a sensitive data feature library according to the first word string data; acquiring first file list information generating file modification during operation of an application; generating a local storage word string library according to the first file list information; and matching the sensitive data feature library and the local storage word string library to obtain risk items of input data and risk values corresponding to the risk items. Through the method and the device, generation of the sensitive data feature library, collection of storage contents, and matching can be automatically performed, a mass of repeated manual works can be replaced, and the cost of application data security assessment can be reduced.
Owner:CHINA MOBILE COMM GRP CO LTD
Electronic document generation apparatus, recording medium, and electronic document generation system
ActiveUS20160072968A1Character recognitionPictoral communicationElectronic documentImaging processing
An electronic document generation apparatus generates a recognition object image by performing an image processing on a scan image so that each of a plurality of line areas extracted from a character area of the scan image should be determined as a unit recognition area and transmits the recognition object image to the cloud server. The apparatus further receives text data which is a processing result of an optical character recognition processing on the recognition object image, in which a delimiter code is added at the end of a character recognition result for each of a plurality of unit recognition areas, from the cloud server, separates the text data into a plurality of character string data on the basis of the delimiter code, and generates an electronic document by arranging each of the plurality of character string data in the line area corresponding to each character string data.
Owner:KONICA MINOLTA INC
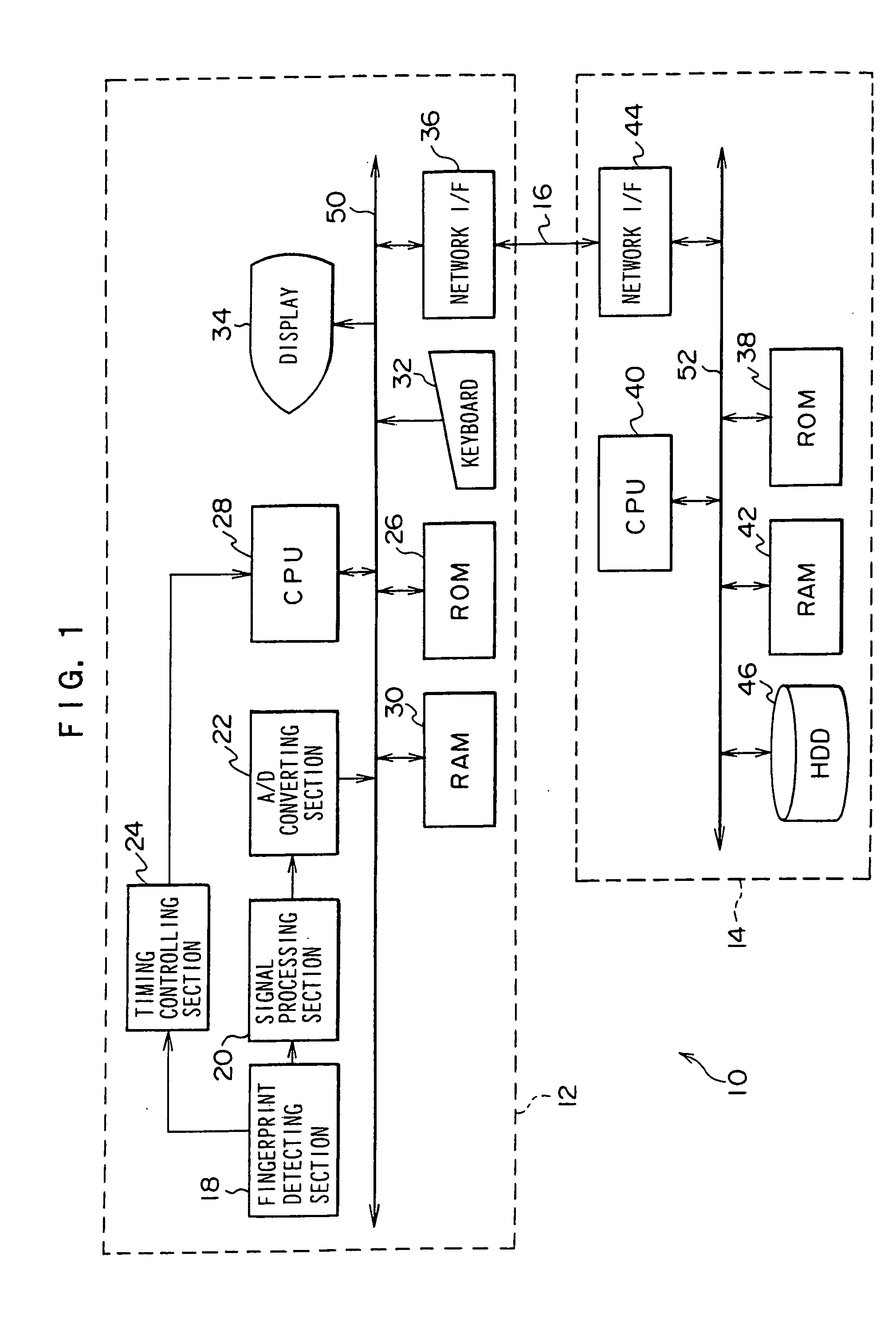
Device for verifying individual, and method for verifying individual
InactiveUS20060153428A1Reduce usageRealize verificationDigital data authenticationMatching and classificationPasswordOne-way function
For received fingerprint data, there are generated a large number of fingerprint data which are varied by estimating a frequency of appearance of errors due to offset of a finger and inverting predetermined bits. A one-way function is applied to data, which combines a received password and each of the large number of fingerprint data, so as to convert into data of 128 bits for example. Each of the large number of 128-bit data is converted into a character string of 32 characters for example. The large number of character string data are classified by using first two characters thereof, and are registered in an HDD as verification templates corresponding to a user name. By using these verification templates, it is possible to prevent surreptitious use of biological information in a device for verifying an individual by biological information.
Owner:GUNMA UNIVERSITY
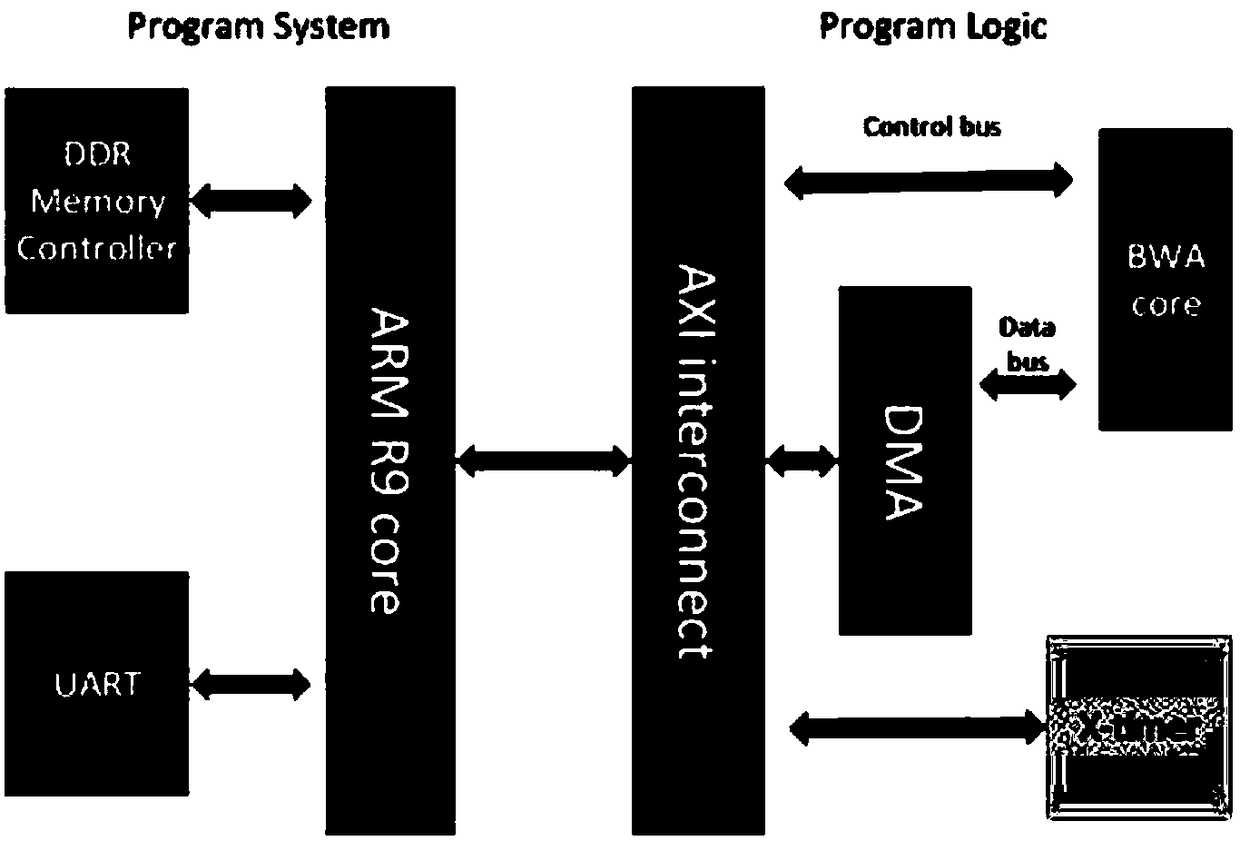
FPGA-based acceleration platform and design method for gene sequencing string matching algorithm
PendingCN108595917AImprove performanceHybridisationSpecial data processing applicationsGeneral purposeProgram logic
The invention discloses an FPGA-based acceleration platform and a design method for a gene sequencing string matching algorithm. The acceleration platform includes a PS (Program System) end and a PL (Program Logic) end, and the PS end includes a general-purpose processor and a DRAM to complete the software-side code operation and control of a hardware part, the PL end contains a plurality of IP cores that can be solidified according to requirements to achieve corresponding tasks. First, the general-purpose processor writes string data into the DRAM, and then the FPGA reads the string data fromthe DRAM and starts calculation, and the calculation result is written into the DRAM, and finally the general-purpose processor reads the matching result from the DRAM. The accelerator of the invention deploys multiple independent IP cores for calculation on the FPGA and the IP cores run in a pipeline mode, so that programmers without hardware knowledge can easily obtain good performance by usingexisting FPGA resources.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
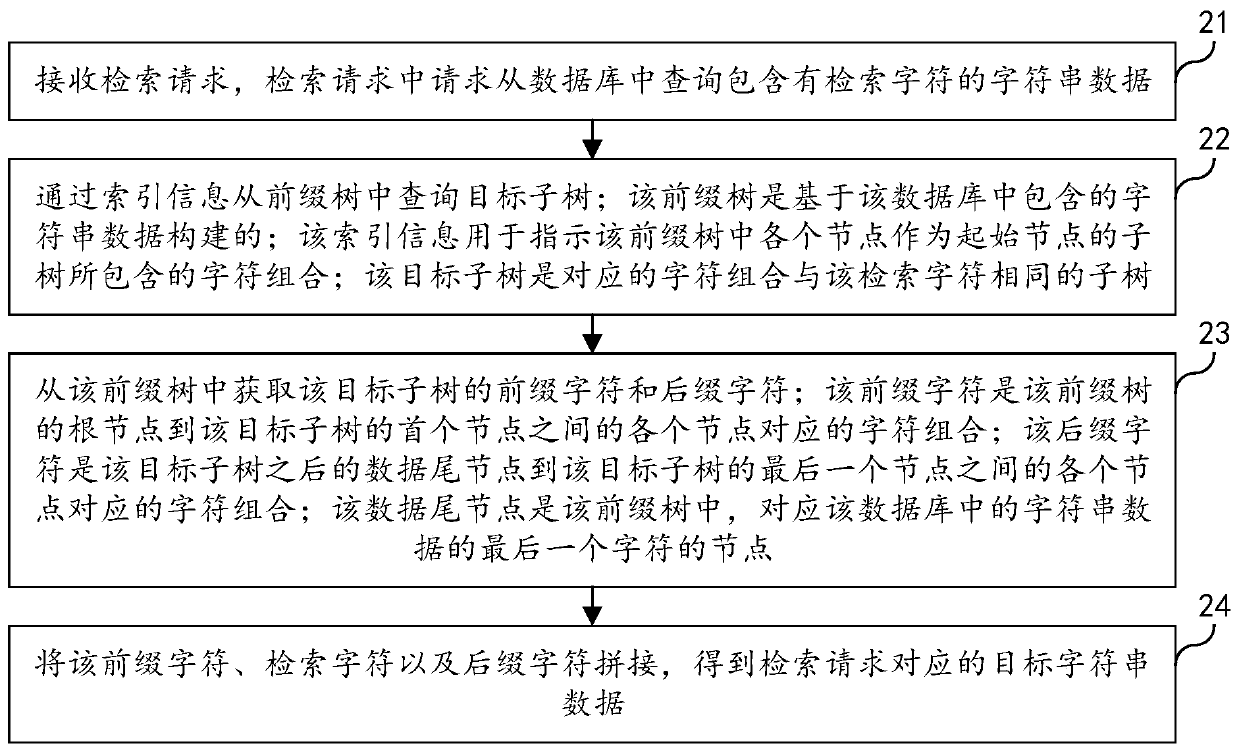
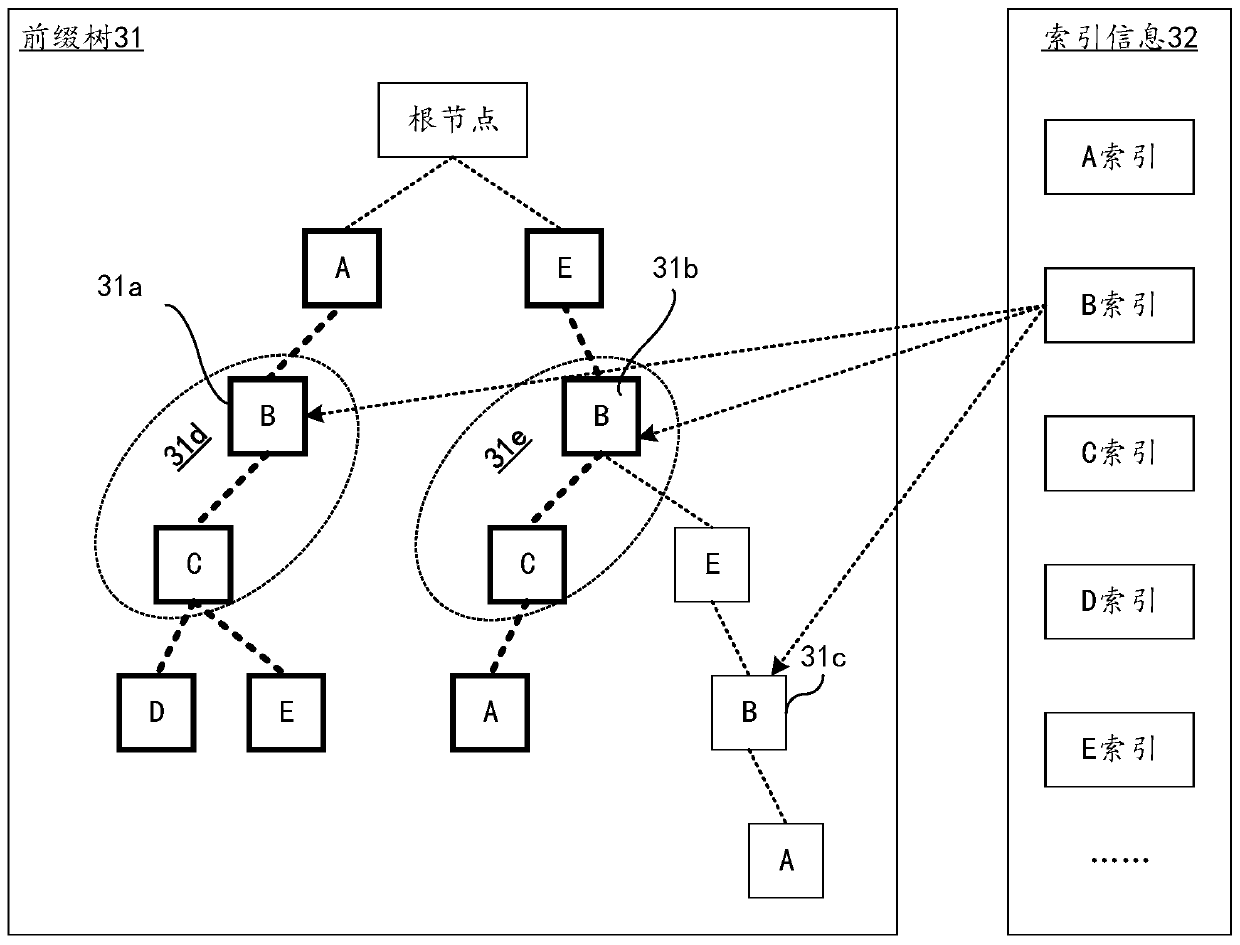
Character string data retrieval method and device, computer equipment and storage medium
PendingCN111339382AImprove retrieval efficiencyUses less memoryOther databases indexingOther databases queryingAlgorithmData retrieval
The invention relates to a character string data retrieval method and device, computer equipment and a storage medium. The method comprises the following steps: receiving a retrieval request, whereinthe retrieval request requests to inquire character string data containing retrieval characters from a database; querying a target sub-tree from the prefix tree through the index information; obtaining a prefix character and a suffix character of the target subtree from the prefix tree; and splicing the prefix character, the retrieval character and the suffix character to obtain target character string data corresponding to the retrieval request. According to the scheme, on one hand, all character string data in the database does not need to be traversed; high retrieval efficiency can be guaranteed, on the other hand, the index information is the index corresponding to the node in the prefix tree, the occupied memory amount is small compared with a full index, and therefore the retrieval efficiency and the memory occupation amount for fuzzy retrieval of the character string can be considered at the same time.
Owner:TENCENT TECH (SHENZHEN) CO LTD
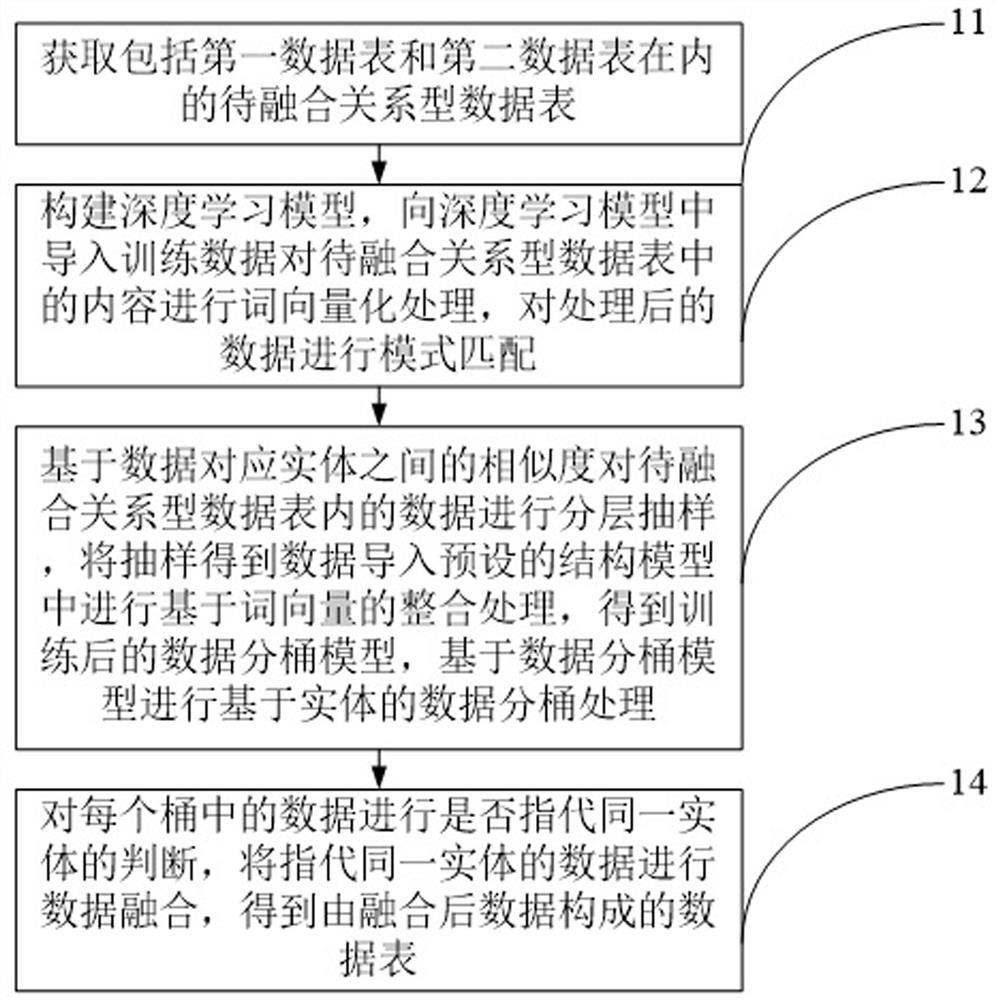
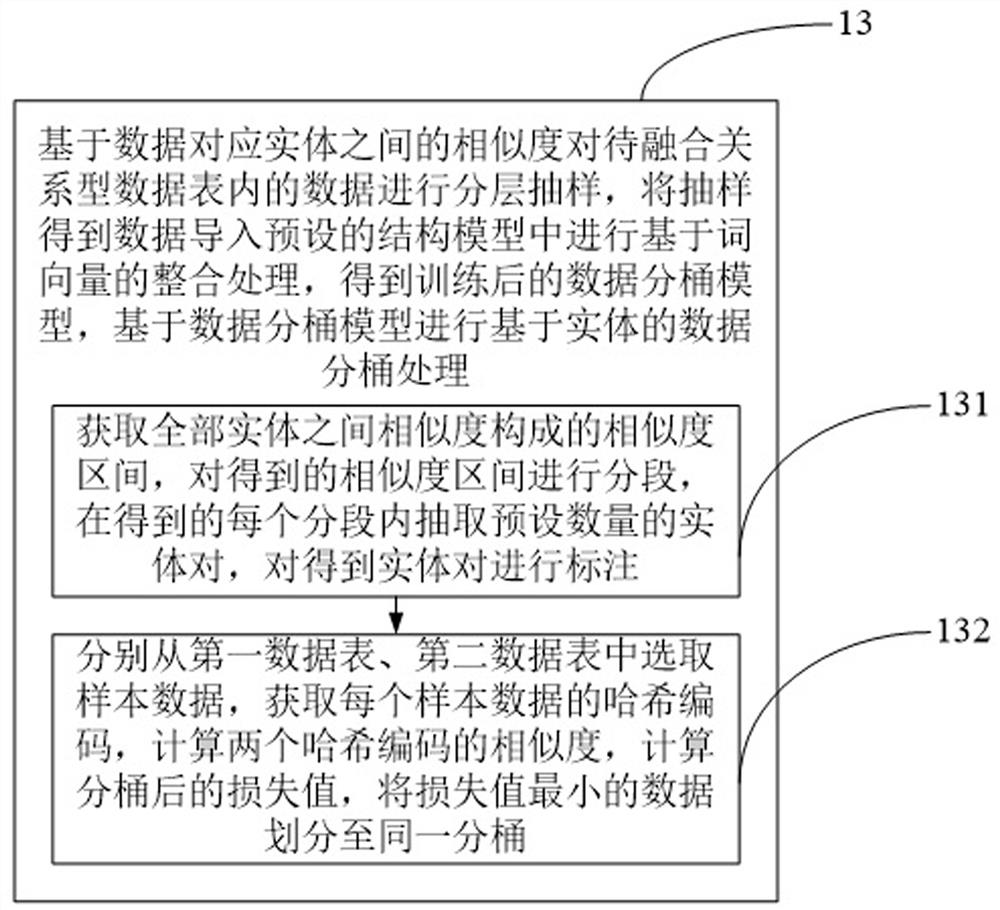
Multi-source data deep fusion method based on deep learning
ActiveCN111767325AImprove toleranceRelational databasesCharacter and pattern recognitionDatasheetDirty data
The embodiment of the invention provides a multi-source data deep fusion method based on deep learning. The method comprises the steps of obtaining a to-be-fused relational data table; constructing adeep learning model, importing training data to carry out word vectorization processing on contents in the to-be-fused relational data table, and carrying out mode matching on the processed data; performing stratified sampling on the data in the to-be-fused relational data table based on the similarity between entities corresponding to the data, importing the sampled data into a preset structure model to perform integration processing based on word vectors to obtain a trained data bucket model, and performing entity-based data bucket processing based on the data bucket model; and judging whether the data in each bucket refers to the same entity, and performing data fusion on the data referring to the same entity to obtain a data table formed by the fused data. According to the invention, character string data is modeled in a word vector mode, and the method can be used for modeling texts and semantics of the character string at the same time, so that the tolerance to dirty data is improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO MARKETING SERVICE CENT +2
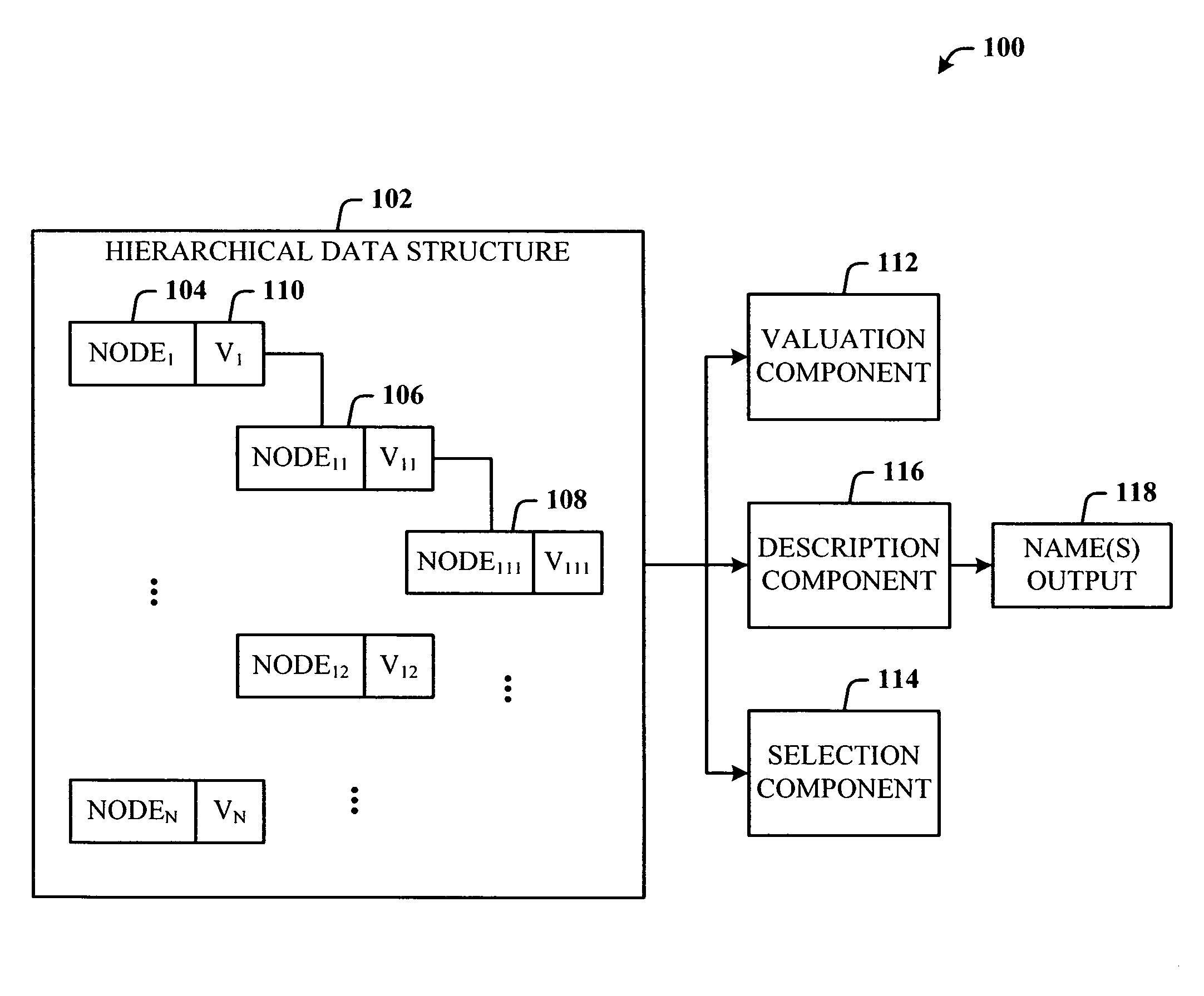
Generation of meaningful names in flattened hierarchical structures
InactiveUS20050216430A1Broaden applicationQuick reviewData processing applicationsDigital data processing detailsArtificial intelligenceData structure
Architecture for generating meaningful names for a flattened data structure. The architecture comprises a system that observes user activity associated with a hierarchical data structure, and then generates meaningful names derived from file and folder names or other character string data that are easier to navigate and understand by the user. The system includes a valuation component that facilitates applying the valuation metrics to each node of the data structure. A selection component selects the one or more nodes for the naming process. A naming component receives and processes the selected node information from the selection component and generates the name(s) for the one or more nodes for the given user. An output of the naming component is the flattened representation in the form of a meaningful name(s) for the data structure.
Owner:MICROSOFT TECH LICENSING LLC
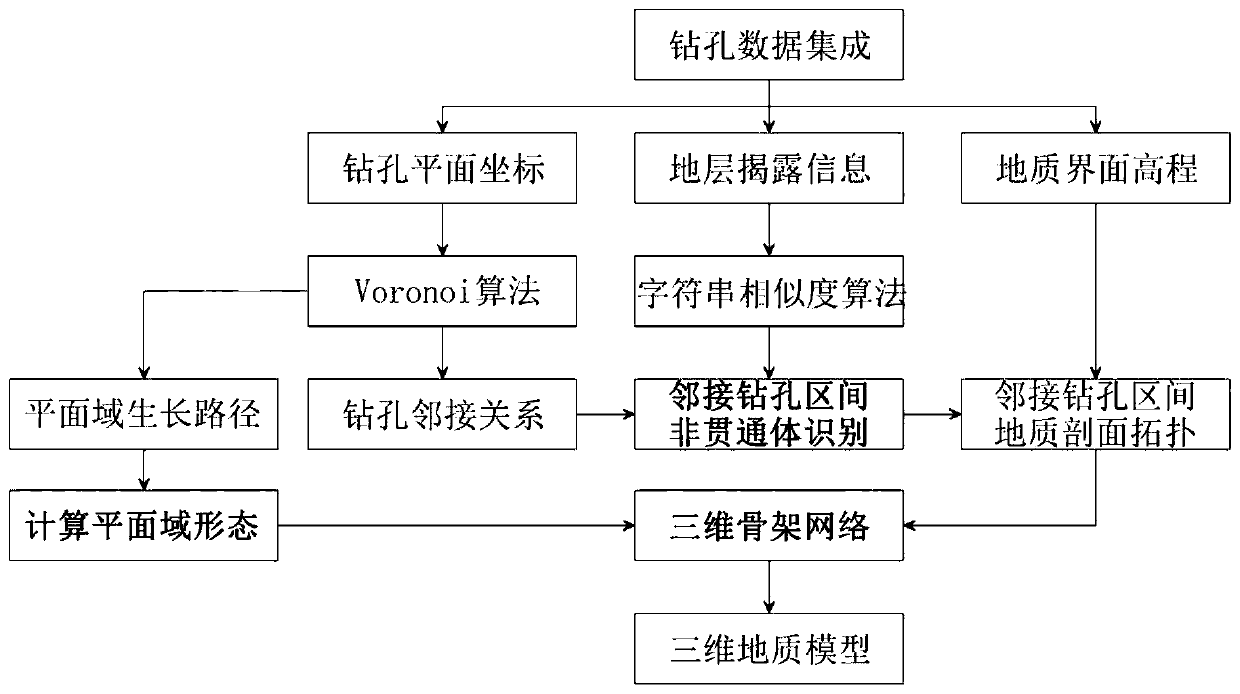
Intelligent three-dimensional geological modeling method based on drilling data
PendingCN111311746AIncrease the level of automationImprove data utilization efficiency3D modellingComputational scienceThree-dimensional space
The invention discloses an intelligent three-dimensional geological modeling method based on drilling data. Firstly, drilling group data are integrated, an adjacency relation matrix of a drilling group is determined according to a Voronoi algorithm, drilling geological disclosure information is converted into character string data, and a character string similarity algorithm is applied to identifya common subsequence of adjacent drilling character strings. And determining the growth path of the plane domain of the borehole group according to the Voronoi diagram, and solving the distribution form of each geosome in the projection area of the geodetic plane; introducing a new control point to the non-continuous through body in the adjacent drilling interval, connecting the continuous through geologic body and the control point, creating geological sections of the adjacent drilling interval, converting all the geological sections into a three-dimensional space to generate a three-dimensional geological skeleton network, and finally assembling to form a three-dimensional geological model. According to the method, automatic three-dimensional geological modeling can be directly carriedout on the complex geologic body based on the drilling data, the three-dimensional topological relation of the drilling group is comprehensively considered, the data utilization rate and the model precision are improved, and the method can be applied to BIM development and smart city construction.
Owner:CCCC GUANGZHOU DREDGING
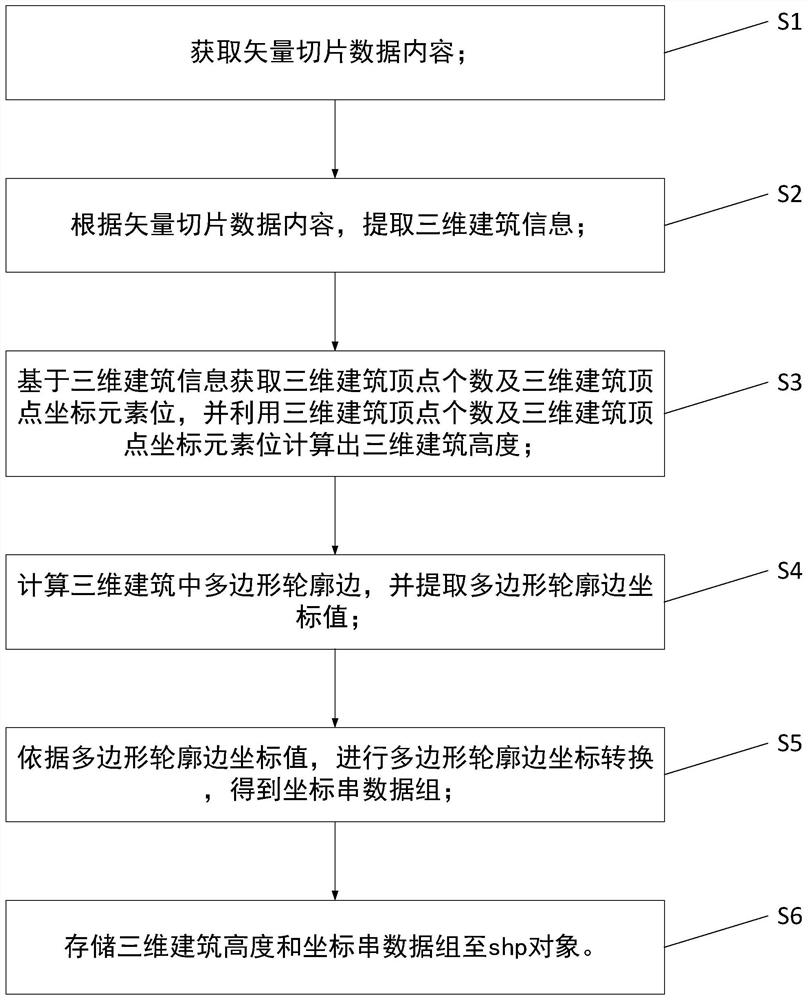
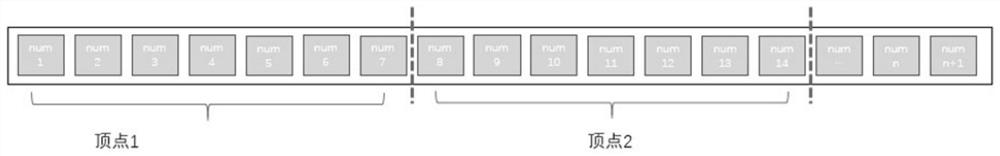
Method for converting three-dimensional house model into two-dimensional vector plane with height attributes
InactiveCN112115534AConsistent aging performanceGeometric CADGeographical information databasesData setComputer graphics (images)
The invention discloses a method for converting a three-dimensional house model into a two-dimensional vector surface with a height attribute. The method comprises the steps of obtaining vector slicedata content; extracting three-dimensional building information according to the vector slice data content; obtaining the number of three-dimensional building vertexes and coordinate element positionsof the three-dimensional building vertexes based on the three-dimensional building information, and calculating the height of the three-dimensional building by utilizing the number of the three-dimensional building vertexes and the coordinate element positions of the three-dimensional building vertexes; calculating polygonal contour edges in the three-dimensional building, and extracting coordinate values of the polygonal contour edges; performing polygon contour edge coordinate conversion according to the polygon contour edge coordinate values to obtain a coordinate string data set; and storing the three-dimensional building height and coordinate string data set to the shp object. In this way, the two-dimensional vector surface data corresponding to the three-dimensional building of theinternet map can be obtained, the building height can be extracted, and the timeliness of the data is consistent with the latest data updated by the internet map.
Owner:北京臻观尚璞文化产业有限公司
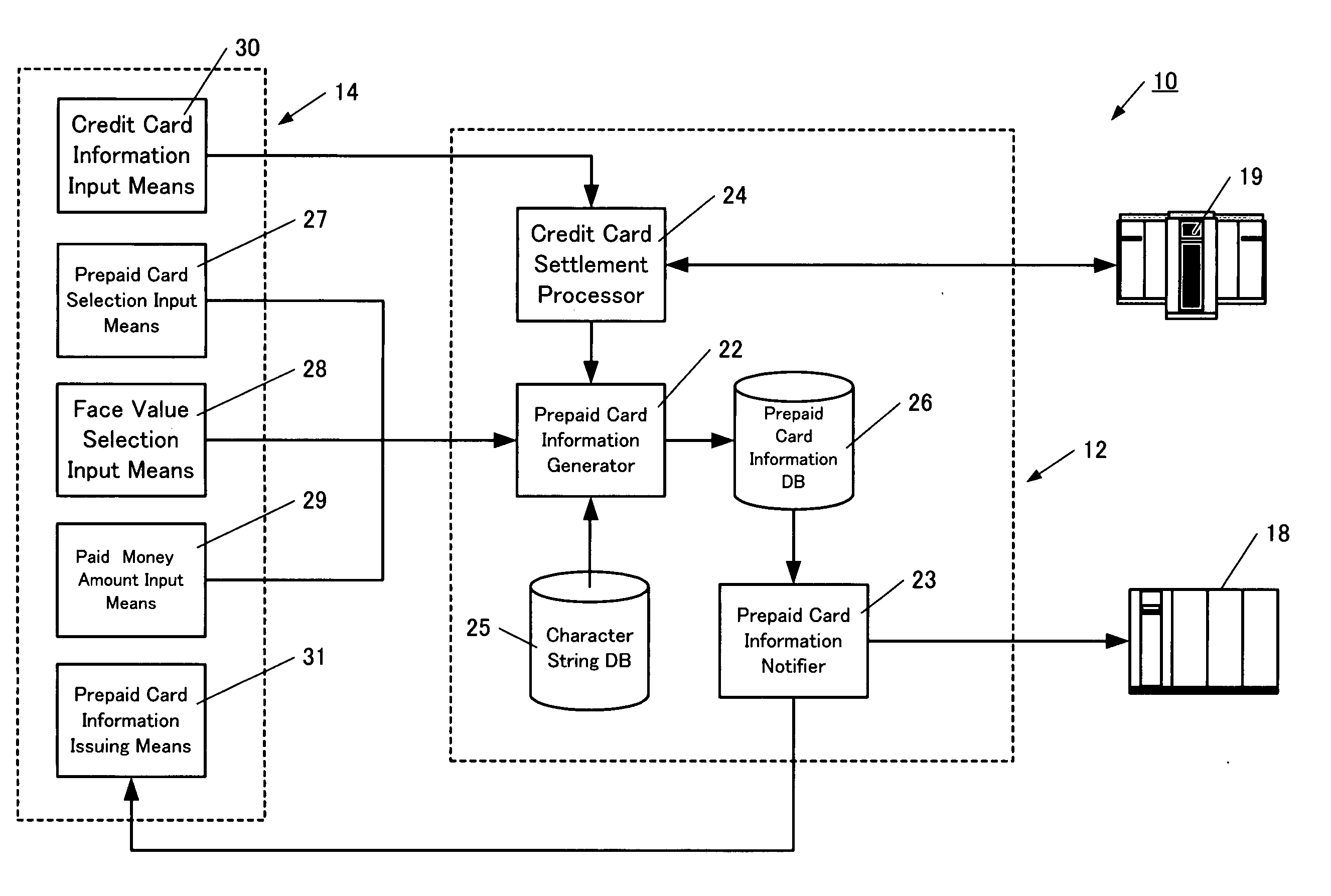
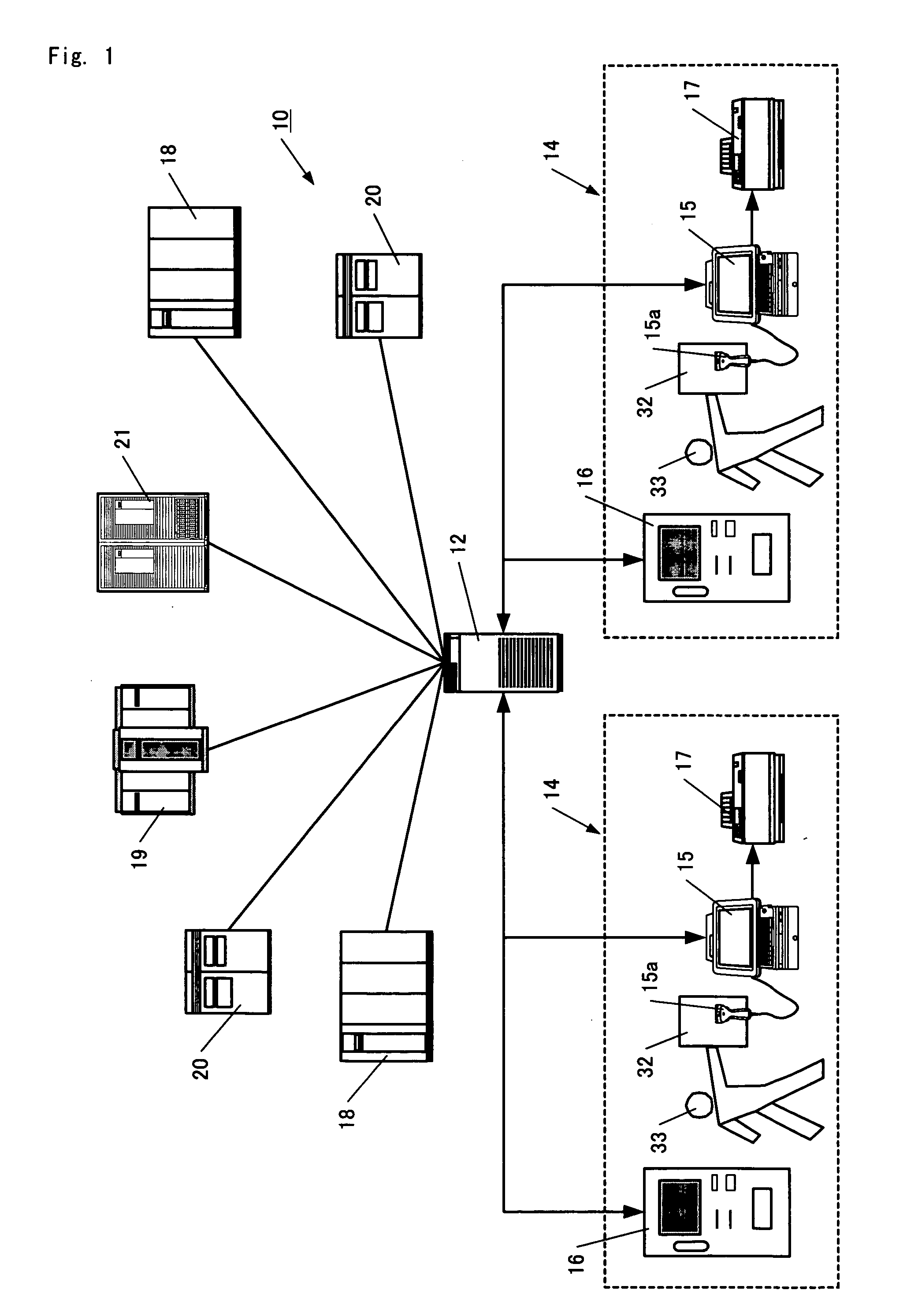
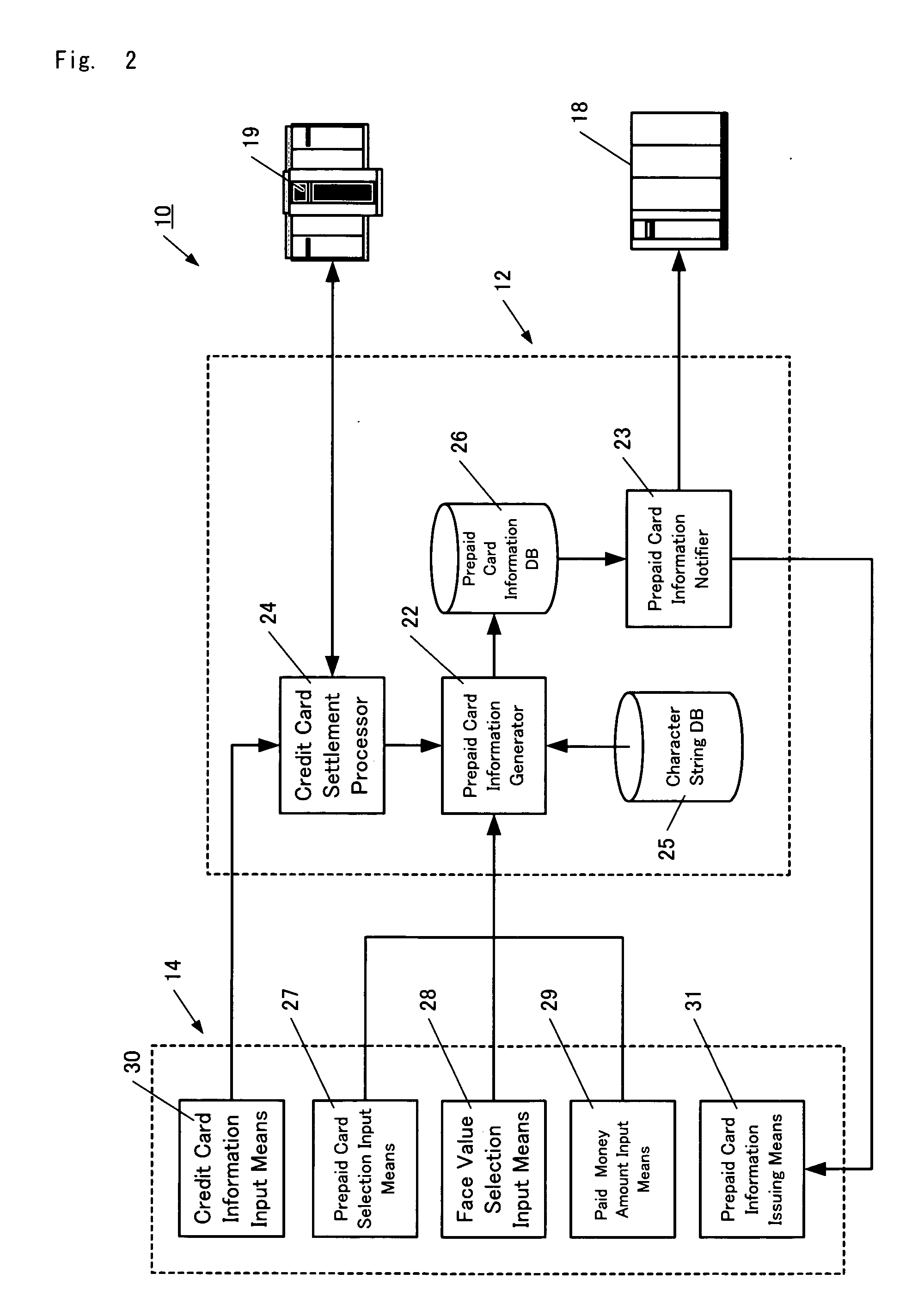
Prepaid card information issuing system, call rate settlement system, communication rate settlement system, and expense settlement system
InactiveUS20050015331A1Decreases communication rateEliminate riskFinanceCredit schemesComputer hardwareBarcode reader
A prepaid card information issuing system 10 comprising a character string data base 25 for storing a plurality of character strings each consisting of a predetermined number of digits, a selection sheet 32 on which barcodes 35, 36 for identifying the type and face value of a prepaid card are displayed, a barcode reader 15a for reading out the barcodes 35, 36 to input the type and face value of the prepaid card, paid amount of money input means for inputting the amount of cash paid, prepaid card information generator 22 for generating prepaid card information by associating some character string in the character string data base 25 with the face value concerned when the face value of the prepaid card thus selected is coincident with the paid money amount, a prepaid card information data base 26 for storing prepaid card information, and prepaid card information issuing means 31.
Owner:GREAT INFORMATION
Method and device for converting Json data into dictionary data and electronic equipment
PendingCN111680079AEasy to readDatabase management systemsNatural language data processingAlgorithmTheoretical computer science
The embodiment of the invention discloses a method and device for converting Json data into dictionary data and electronic equipment, relates to the technical field of computers, and can improve the speed of converting the Json data into the dictionary data. The method comprises the steps: converting data stored in a Json file into character string data, wherein the character string data are arraytype data; calling Unity Json to convert the character string data into a transition array, each array element in the transition array being in one-to-one correspondence with each object in the arraytype data; and converting the transition array into dictionary data, the dictionary data taking a field value corresponding to any field of the array element as an index value and taking a field value corresponding to at least one field of the array element as an attribute value corresponding to the index value. The method and the device are suitable for converting the Json data into the dictionary data in the game program.
Owner:北京金山猎豹科技有限公司
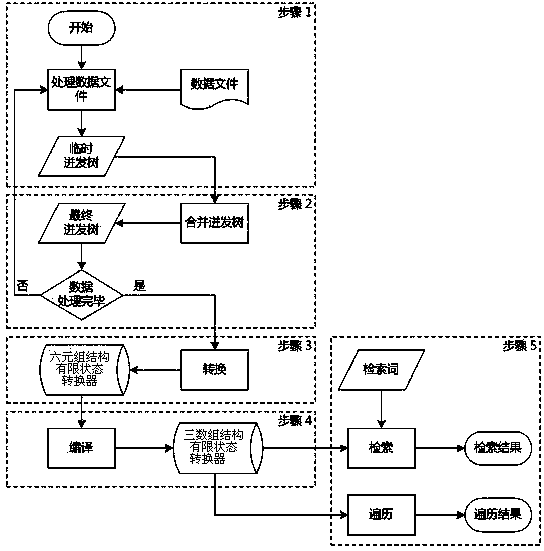
Method for orderly constructing and retrieving string data dictionary
ActiveCN103761270AGuaranteed ordered formReduce memory usageText database queryingSpecial data processing applicationsConvertersAlgorithm
The invention discloses a method for orderly constructing and retrieving a string data dictionary. The method includes S1, inputting string data into a temporary bursting tree one by one; S2, when data quantity in the temporary bursting tree reaches a threshold value condition, combing the data into a final bursting tree; S3, converting the final bursting tree into a six-tuple structure finite state converter; S4, compiling the six-tuple structure finite state converter to be in a three-array structure form; S5, according to application needs, utilizing the three-array structure finite state converter after being compiled to realize retrieving or order transversing of the data dictionary. By the method, high-efficiency dictionary construction can be performed on millions of data items, and retrieval needs in different environments and application can be met.
Owner:DALIAN UNIV OF TECH
Tourist information guiding apparatus
InactiveUS20060058956A1Information obtainedInstruments for road network navigationData processing applicationsImaging dataHuman language
A tourist information guiding apparatus is provided with a tourist spot information storage storing image data relating to tourist spots in correspondence with character string data for sightseeing guide written in a plurality of languages, a monitor for displaying operation screens used to input various instructions such as the display of tourist information, a language receiving section for receiving the selection of a language via the operation screen on the monitor, a tourist spot receiving section for receiving the selection of a tourist spot, and a display controlling section for causing the monitor to display an image of the tourist spot selected by the tourist spot receiving section together with a character string for sightseeing guide written in the language designated by the language receiving section. A traveler can obtain tourist information in his native language at a travel destination by means of a tourist information guiding apparatus.
Owner:NORITZ CORP
Character string encryption and decryption method and device, storage medium and processor
The invention discloses a character string encryption and decryption method and device, a storage medium and a processor. The method comprises the following steps: acquiring original character stringdata and actual encryption environment information; performing length extension on the original character string data to obtain first character string data; grouping and recombining each character ofthe first character string data to obtain second character string data; and performing operation on each character in the second character string data by taking the actual encryption environment information as a scrambling code to obtain an encrypted character string. According to the invention, the security problem that the ciphertext password is easy to crack under the condition that the plaintext password is encrypted through the ciphertext password without using an encryption function library or encryption hardware is solved.
Owner:国铁吉讯科技有限公司
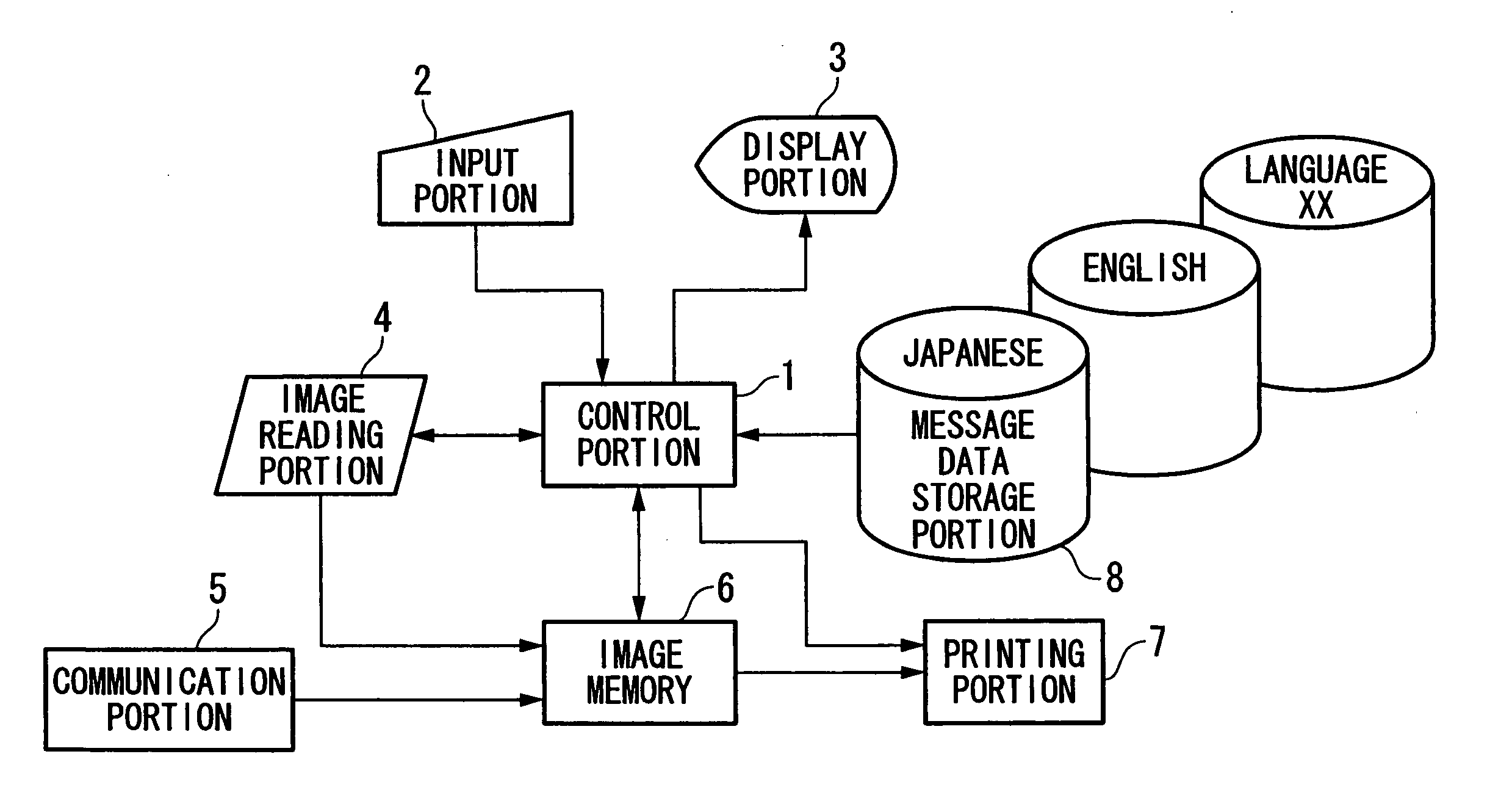
Message display device and storage medium
InactiveUS20060114257A1Easily conveyedEasy to operate2D-image generationPictoral communicationDisplay deviceArtificial intelligence
A message display device includes: a display unit; a message data storage unit; a language selection unit; a readout unit; a character counting unit; a calculation unit calculating a display time for the character string data by multiplying the number of characters included in the character string data by one of coefficients corresponding to the designated language, the coefficients having been assigned to the group of languages; and a display control unit displaying the character string data using the display unit, and erasing the character string data having been displayed when the display time has elapsed.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
Secure hidden three-element query method
ActiveCN113255007APrevent leakagePrivacy protectionDigital data protectionQuery stringTheoretical computer science
The invention discloses a secure hidden three-element query method. The method comprises the following steps: a preprocessing stage: a queried party reads stored three-element data, splits the three-element data into three sub-data, performs hash processing to obtain three character string data, allocates a corresponding secret key to each character string data, calculates a first-level encryption string corresponding to each character string data, the query party encrypts the first-level encrypted string under the cooperation of the queried party to obtain a second-level encrypted string; the online processing stage comprises the following steps of: the query party reads input three-element data, generates three pieces of query data, rperforms hash processing to obtain three pieces of corresponding query character string data, calculating a decryption key corresponding to each piece of query character string data, sends the decryption key to a queried party, and sends a query result to the query party after the queried party queries. When three-element query is carried out, query conditions are hidden, data leakage is avoided, a queried party cannot record query information which is not in a database of the queried party, and user privacy is protected.
Owner:蓝象智联(杭州)科技有限公司
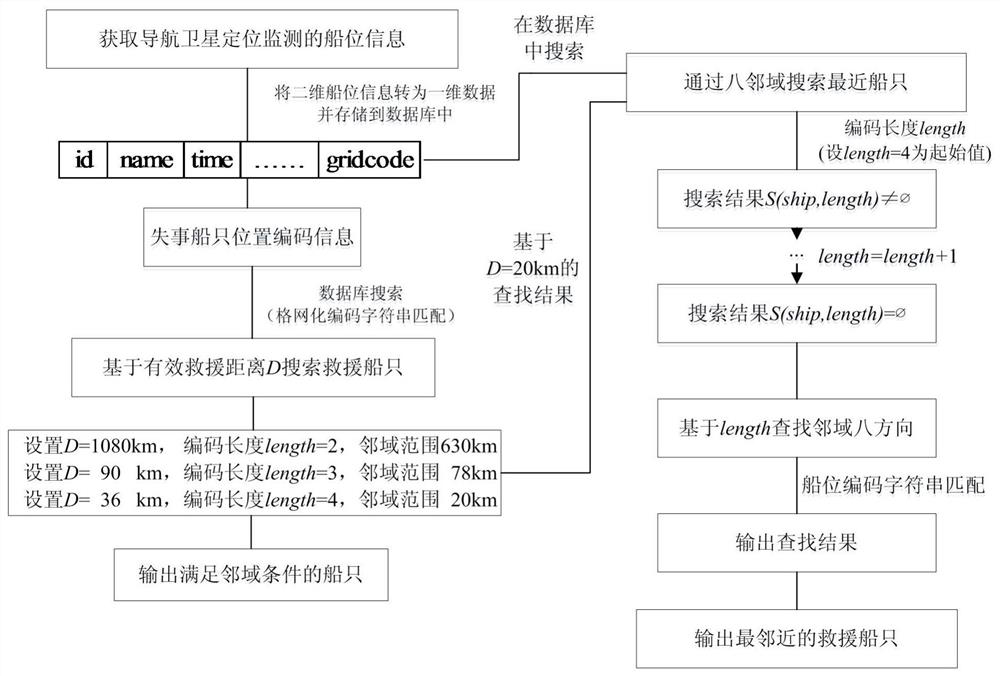
Gridding neighborhood-based marine ship effective rescue search method
ActiveCN112069371ASolve the problem of relatively low time efficiencyGeographical information databasesOther databases queryingMarine engineeringClassical mechanics
The invention relates to a gridding neighborhood-based marine ship effective rescue search method, which comprises the following steps of: performing gridding encoding on ship position data, storing agridding encoding result, and representing two-dimensional longitude and latitude space information of a ship by using encoded one-dimensional character string data; receiving position information ofthe wrecked ship, and determining a grid code corresponding to the wrecked ship based on the position information; searching ships meeting effective rescue distance conditions in neighborhoods of thewrecked ships according to the grid codes, and finding out to-be-selected rescue ships; and searching the nearest ship from the to-be-selected rescue ships as a priority rescue ship. A nearest ship and a closer ship of the wrecked ship can be quickly found.
Owner:EAST CHINA SEA FISHERIES RES INST CHINESE ACAD OF FISHERY SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com