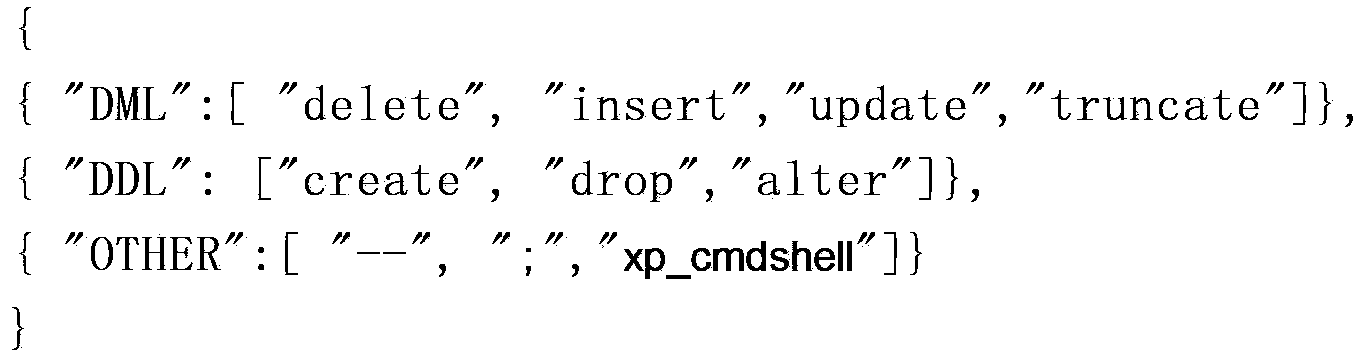Method and system of safety protection of Web application
A security protection and web application technology, applied in the field of information security, can solve problems such as insufficient security assessment of applications, large maintenance costs, inability to detect and prevent attacks by firewall intrusion prevention systems, avoid repeated development or omission of interception, improve Safety, cost reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
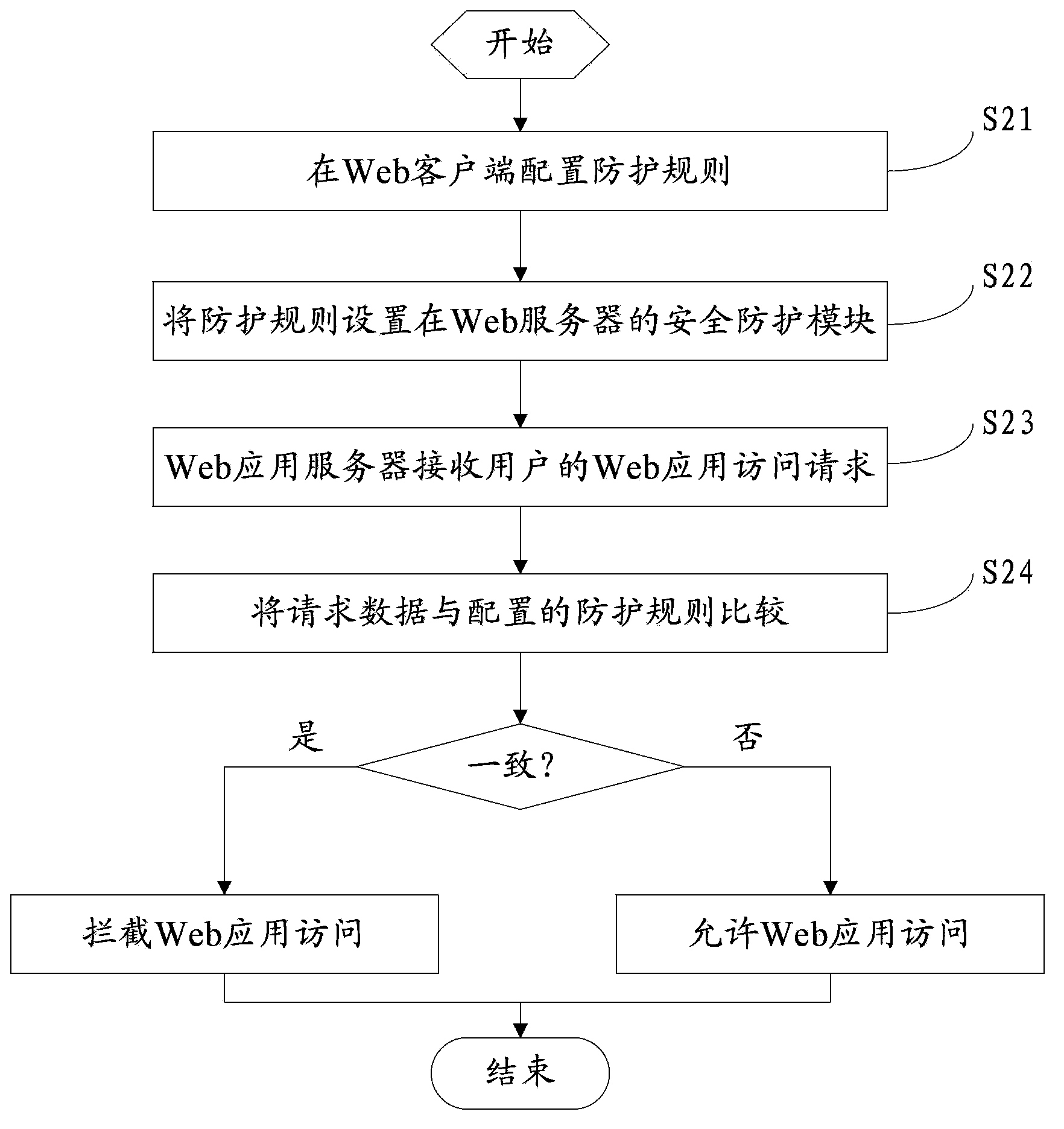
[0060] This embodiment takes the url protection that includes user input parameters as an example, and its main steps include:
[0061] Step 1: Configure protection rules;
[0062] For example, to prevent possible harmful SQL commands from being included in input parameters, you can create the following protection rule file QuerystringRule.json:
[0063]
[0064] Among them, the protection rule file in json format is a lightweight data exchange format file, which is easy to read and write. Of course, when creating the protection rule file, it can also be stored in other forms such as xml or database table.
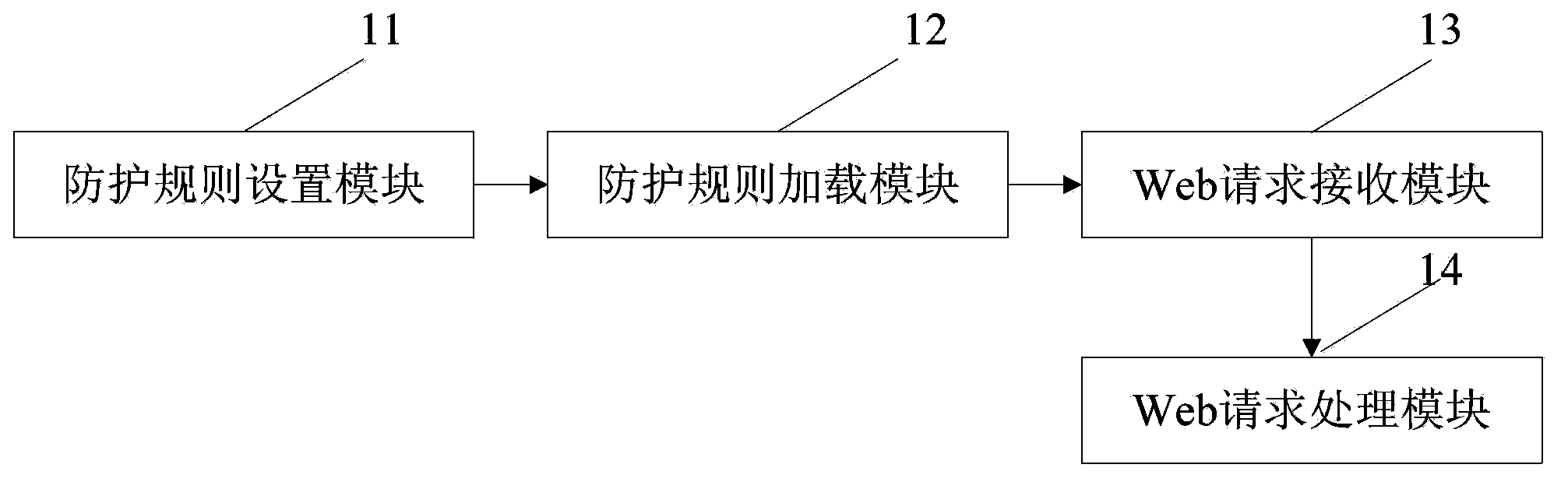
[0065] Step 2: Deploy the protection rule file in the security protection module.
[0066] Deploy the protection rule file set in the previous step in the security protection module, and set the security protection module as a global filter. Web application access requests will first be sent to the security protection module for security checks.
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com