User identity authentication method, device and system
A technology for user identity authentication and user identity information, applied in the field of data communication, can solve the problems of high cost, difficult to crack, and cannot be spread, and achieve the effect of lowering the threshold, expanding market share, and reducing operating costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
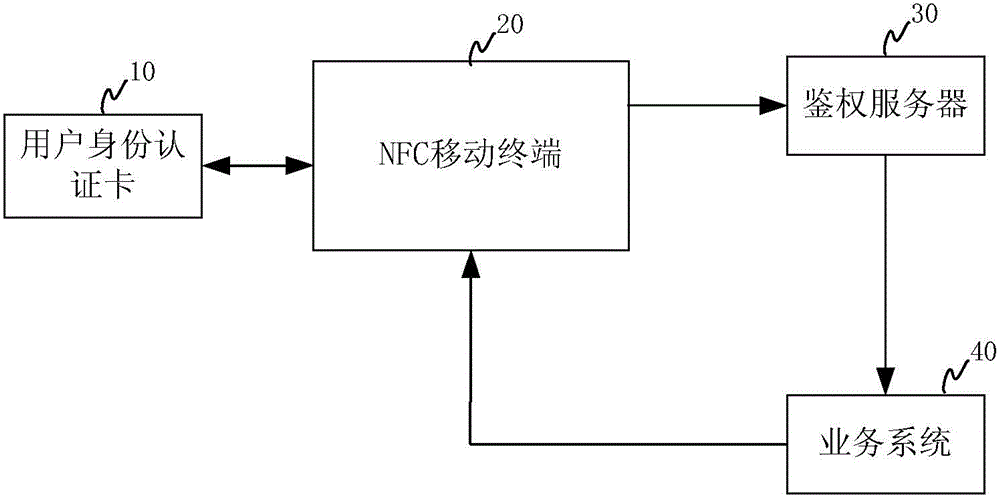
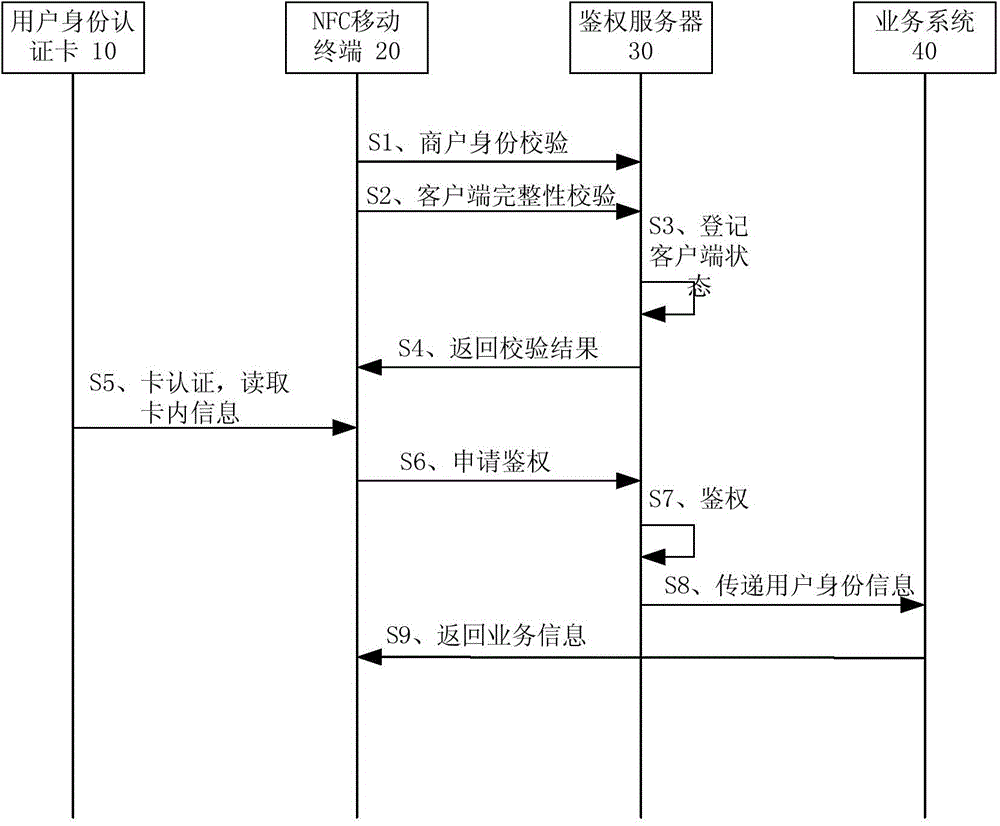
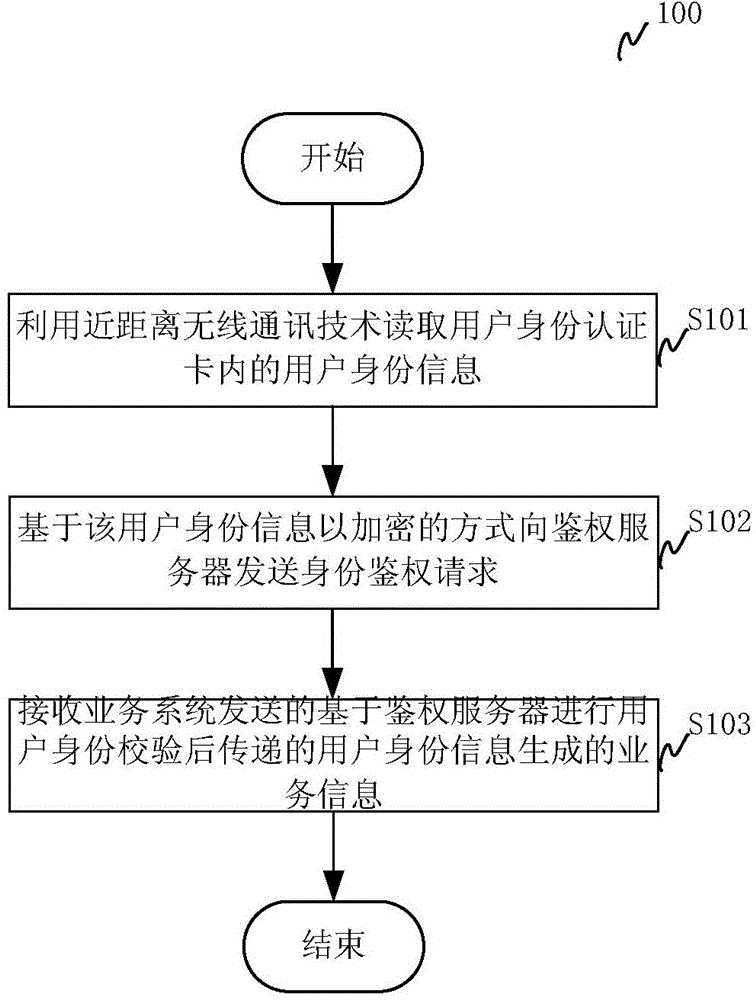
[0034] The present invention proposes a system that uses NFC mobile terminals to replace the dedicated POS machine used in the existing unified user identity authentication card solution to perform user identity authentication. figure 1 A schematic diagram of a logical structure of a user identity authentication system according to an embodiment of the present invention is shown. Such as figure 1 As shown, the user identity authentication system includes a user identity authentication card 10 , an NFC mobile terminal 20 , an authentication server 30 and a business system 40 . The user identity au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com