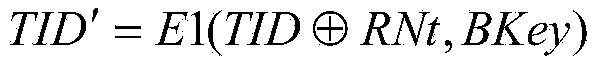Safety authentication method for hiding ultrahigh-frequency electronic tag identifier (TID)
An electronic label and security authentication technology, which is applied in the direction of security communication devices, electrical components, and cooperative operation devices, etc., can solve problems such as potential safety hazards, inability to read and protect TID information, and achieve the effect of preventing theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
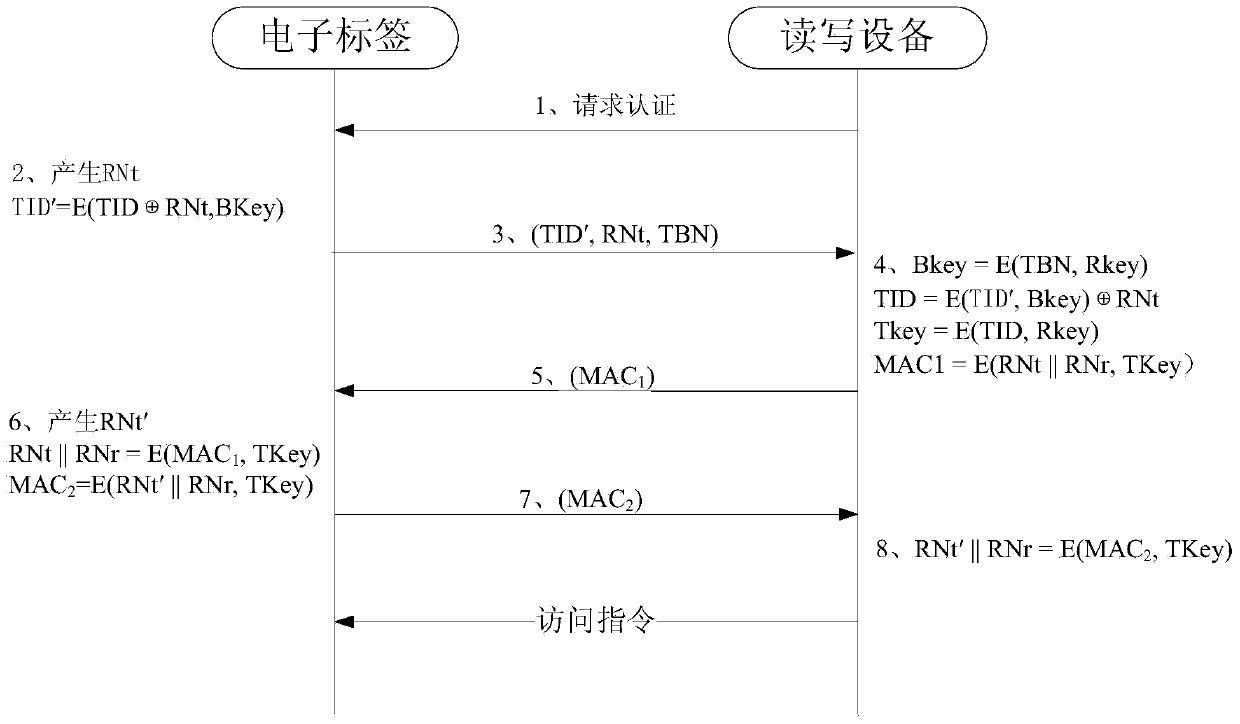
[0038] The present invention will be further described below in conjunction with specific drawings and embodiments.
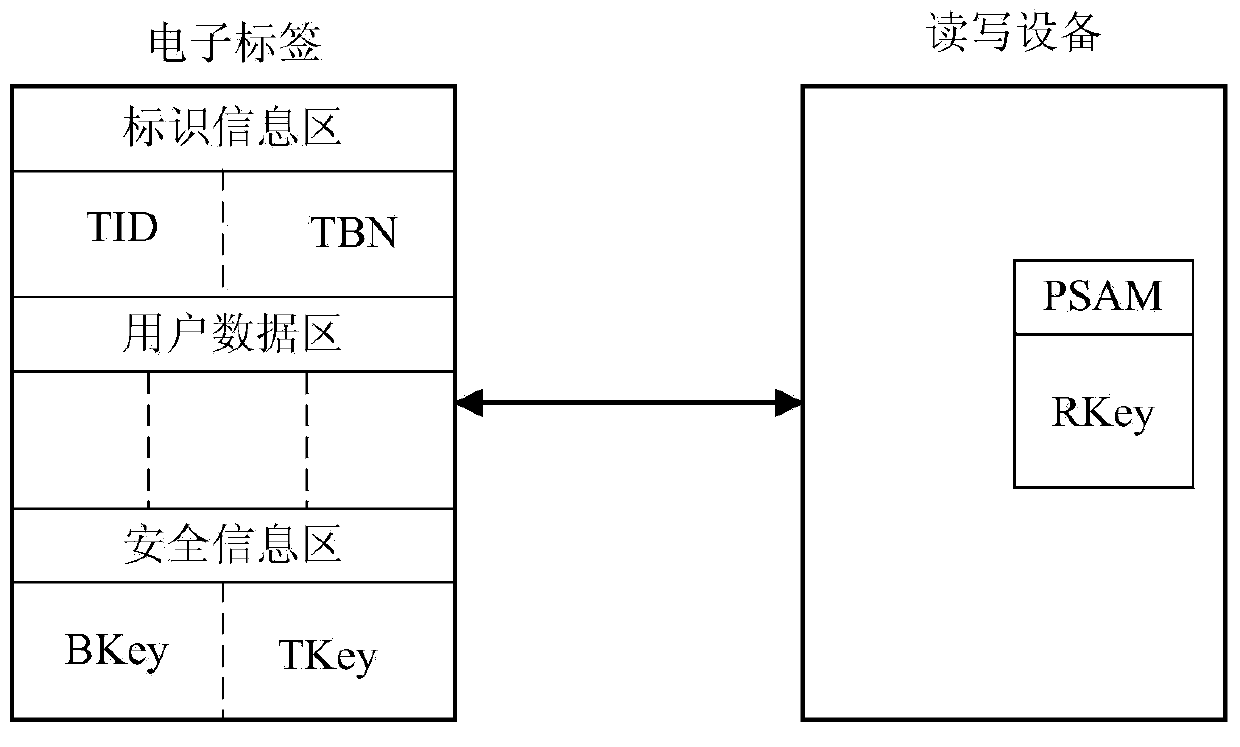
[0039] Such as figure 1 Shown: a schematic diagram of the structure of the passive UHF radio frequency identification system authentication system of the present invention, the system includes electronic tags and read-write equipment.
[0040] The electronic tag includes three storage partitions: an identification information area, a user data area, and a security information area. The identification information area stores electronic tag identification number TID (unique serial number) and electronic tag batch number TBN information. The electronic label identification number TID is initialized and written by the label chip manufacturer, and the electronic label batch number TBN is initialized and written by the key management center. The electronic label identification number TID and the electronic label batch number TBN cannot be changed after being written...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com