Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1549 results about "IEEE 802" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
IEEE 802 is a family of IEEE standards dealing with local area networks and metropolitan area networks. The IEEE 802 standards are restricted to networks carrying variable-size packets, unlike cell relay networks, for example, where data is transmitted in short, uniformly sized units called cells. Isochronous networks, where data is transmitted as a steady stream of octets, or groups of octets, at regular time intervals, are also beyond the scope of the IEEE 802 standards.
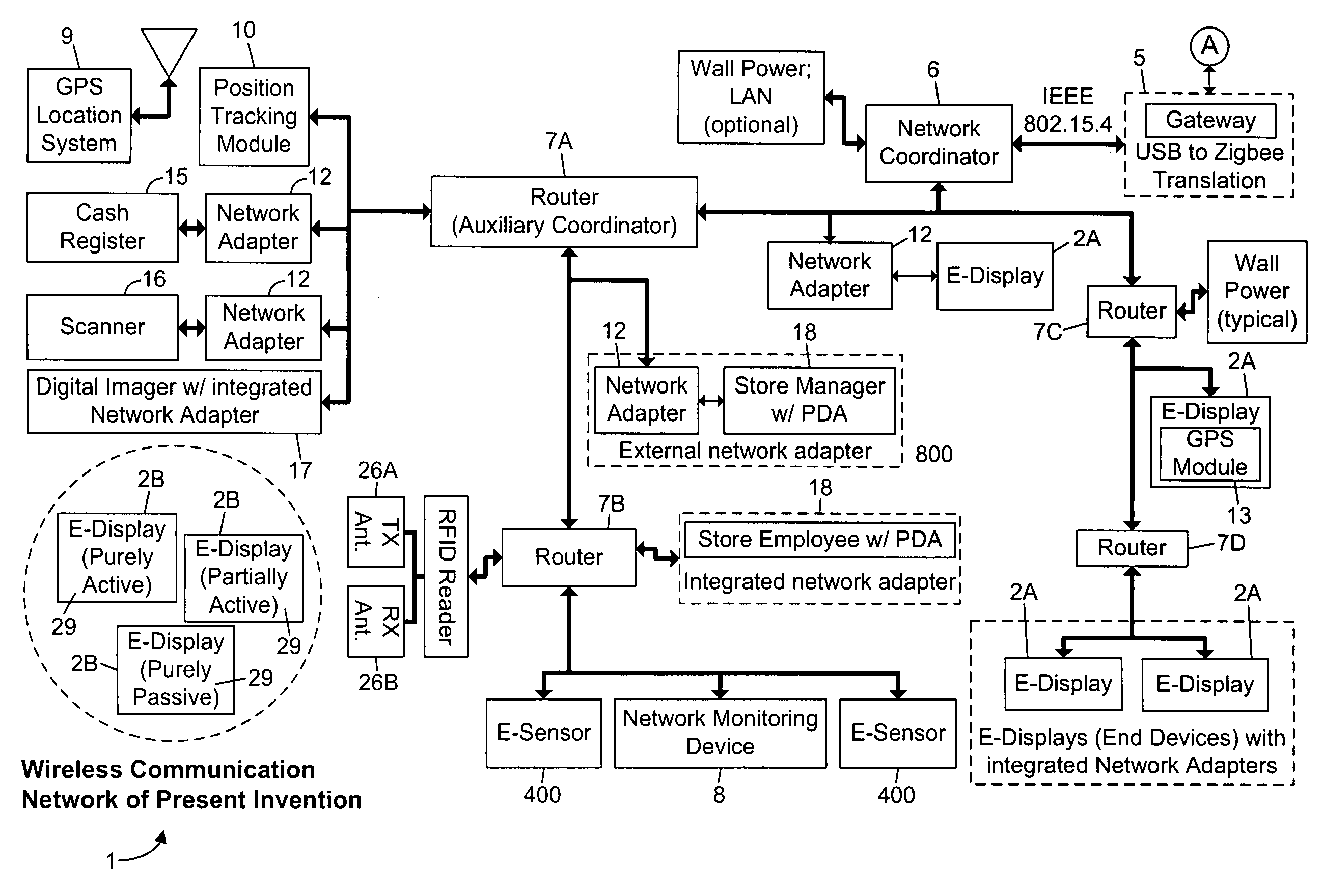
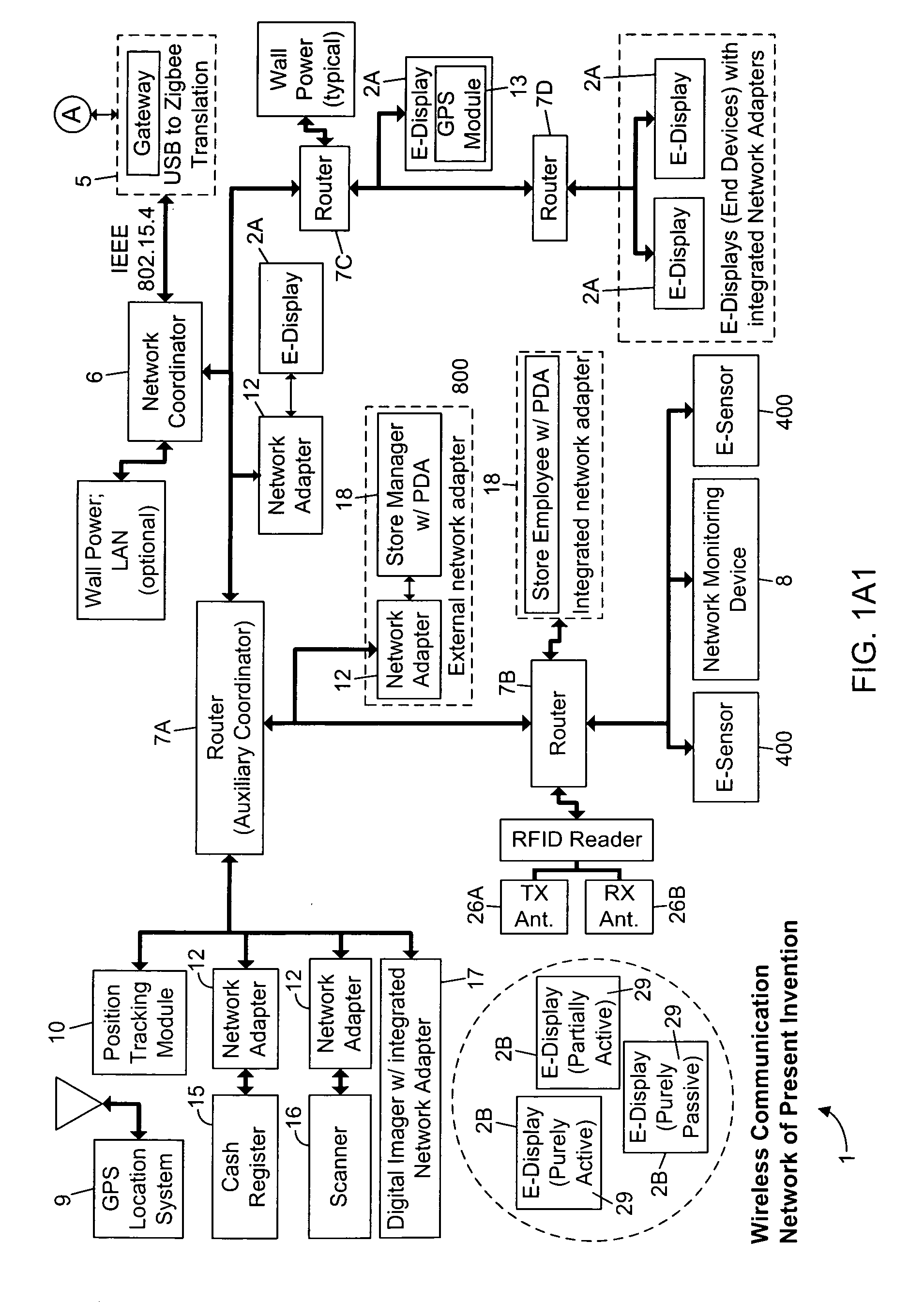
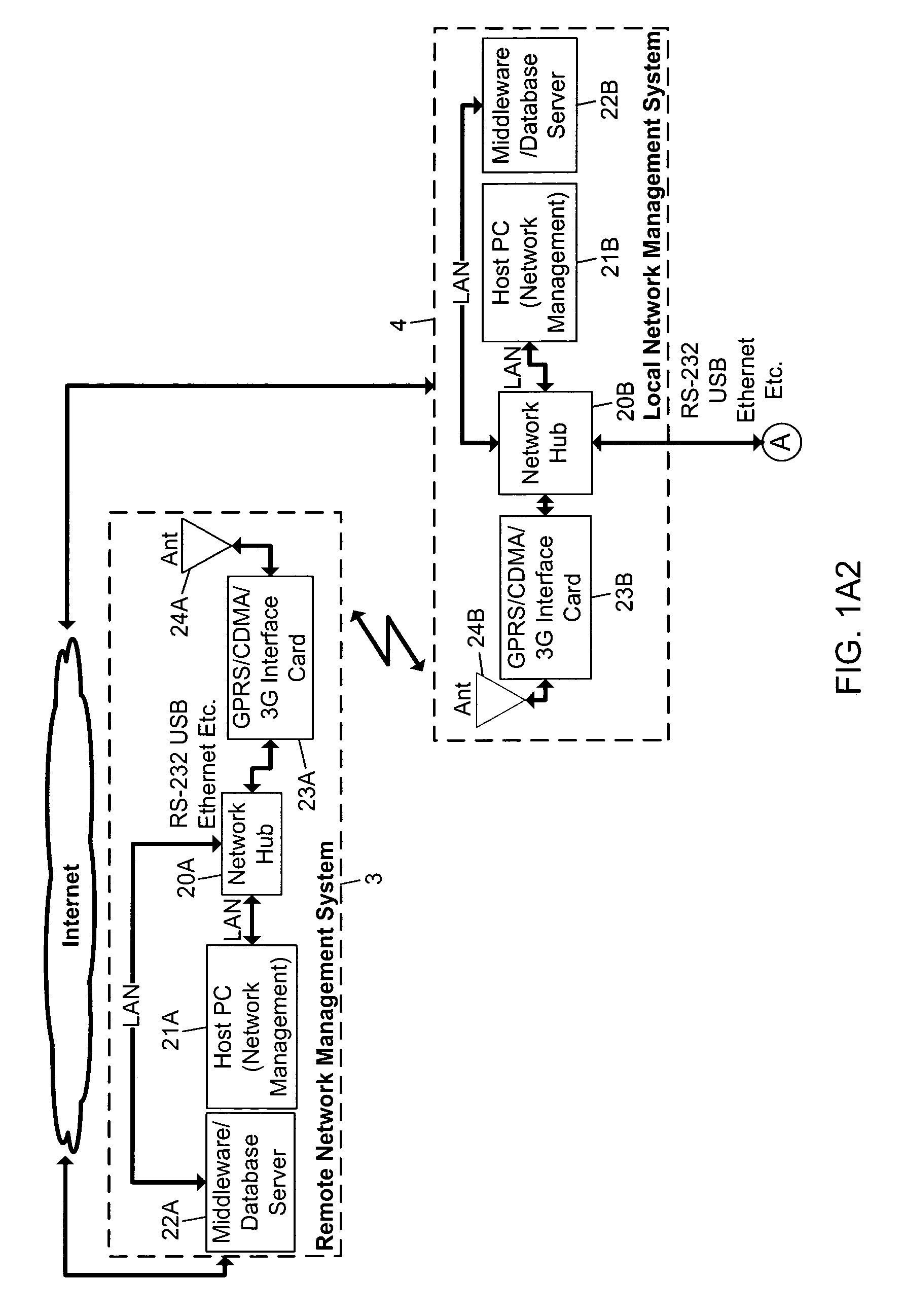
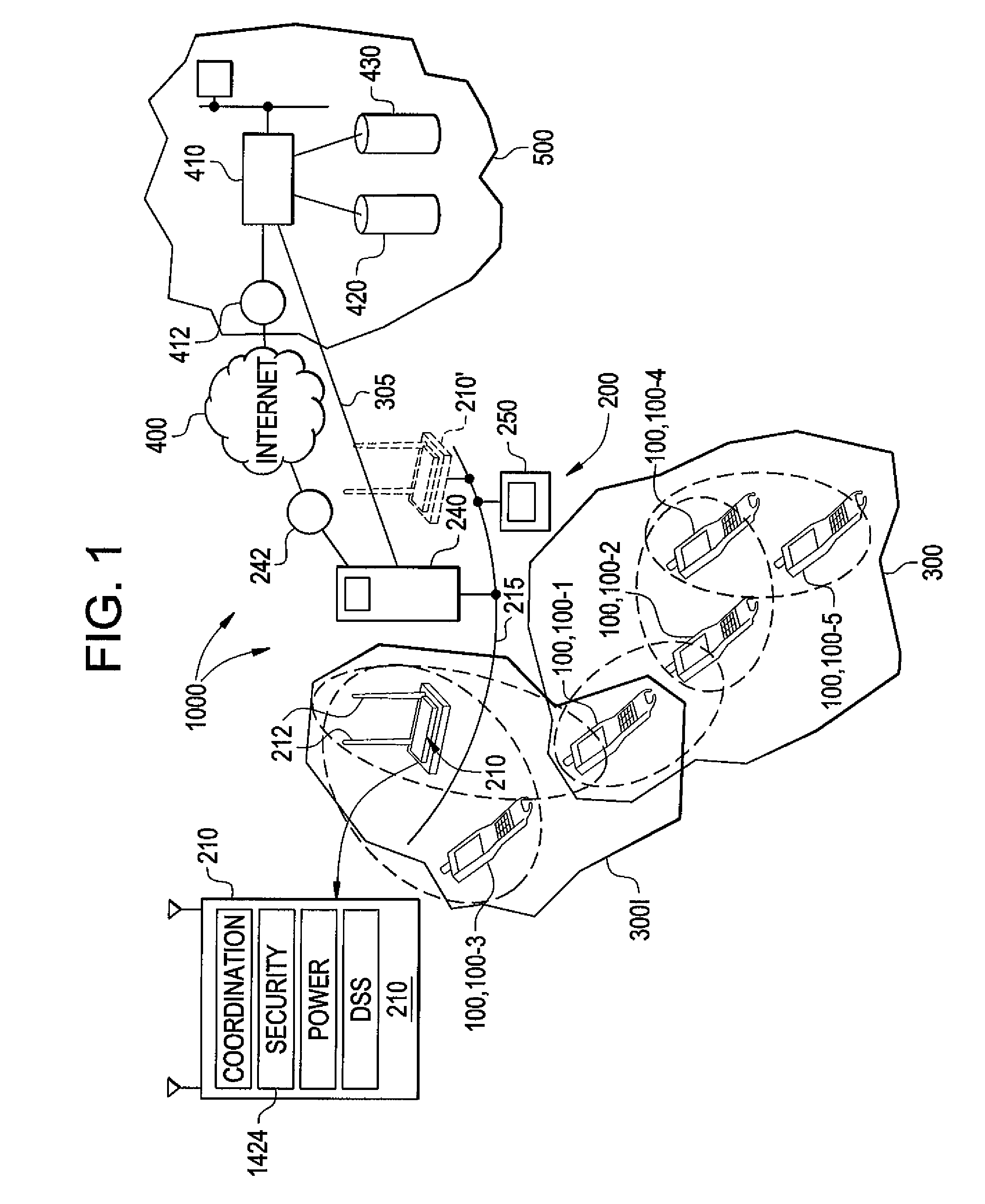
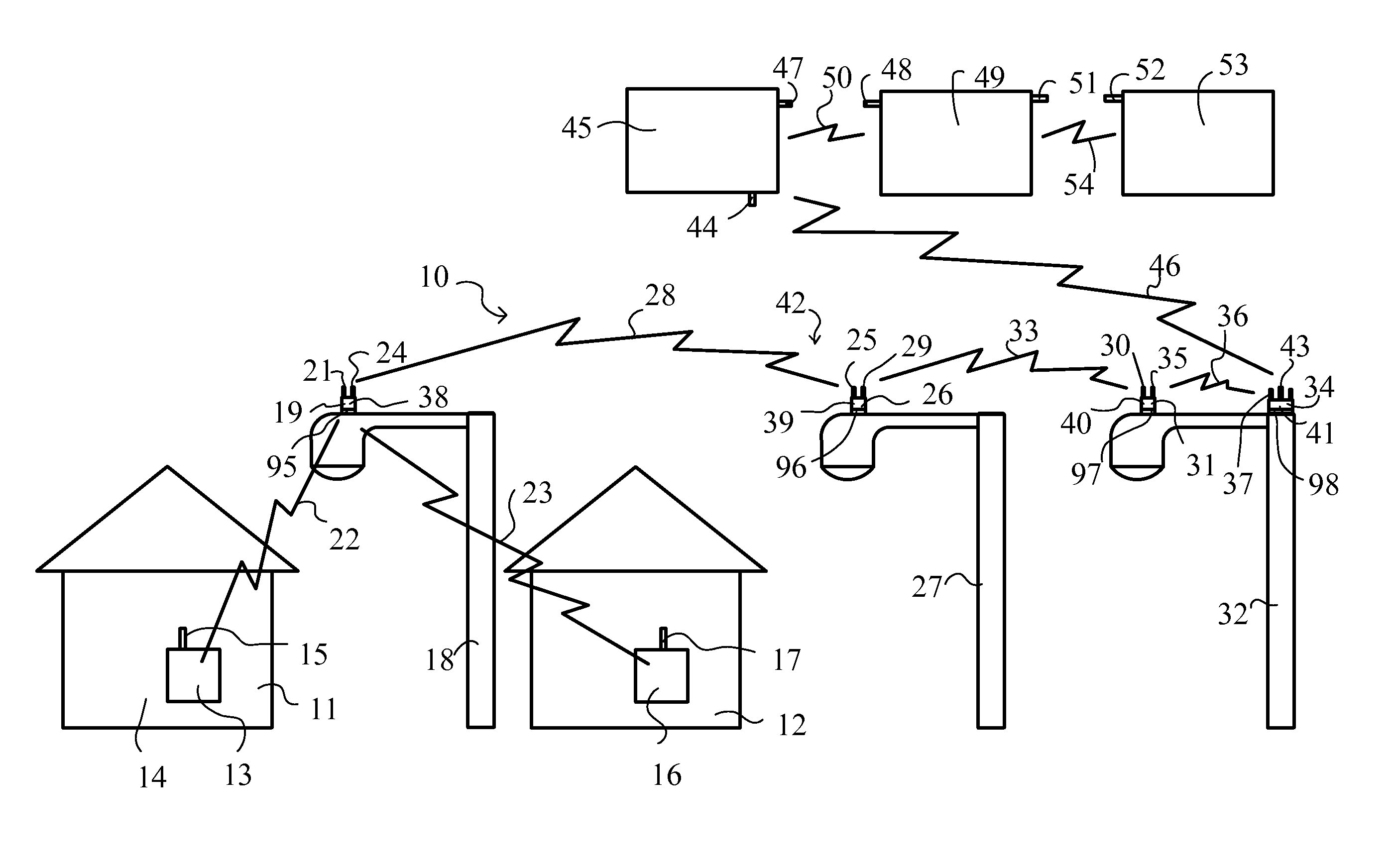
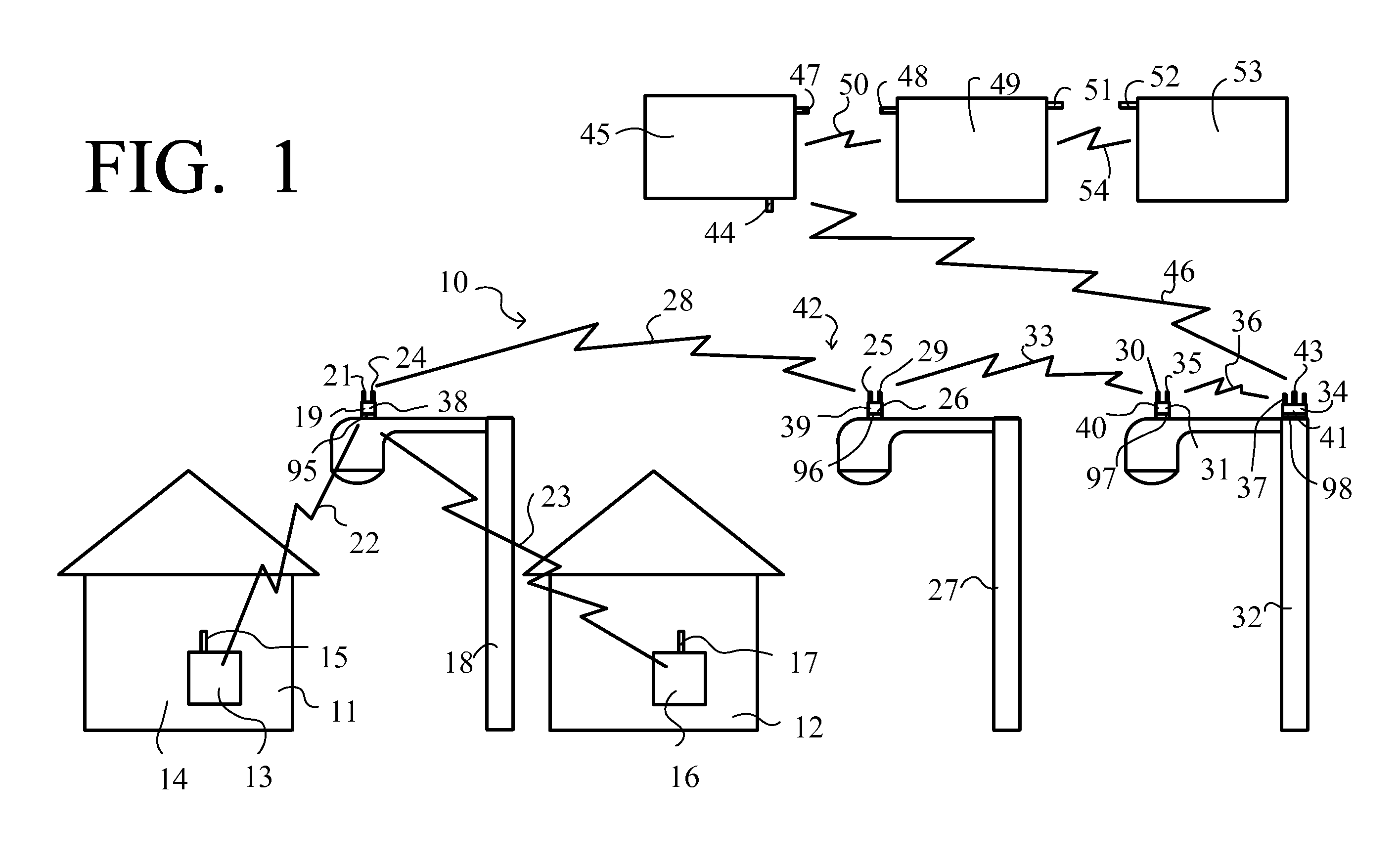
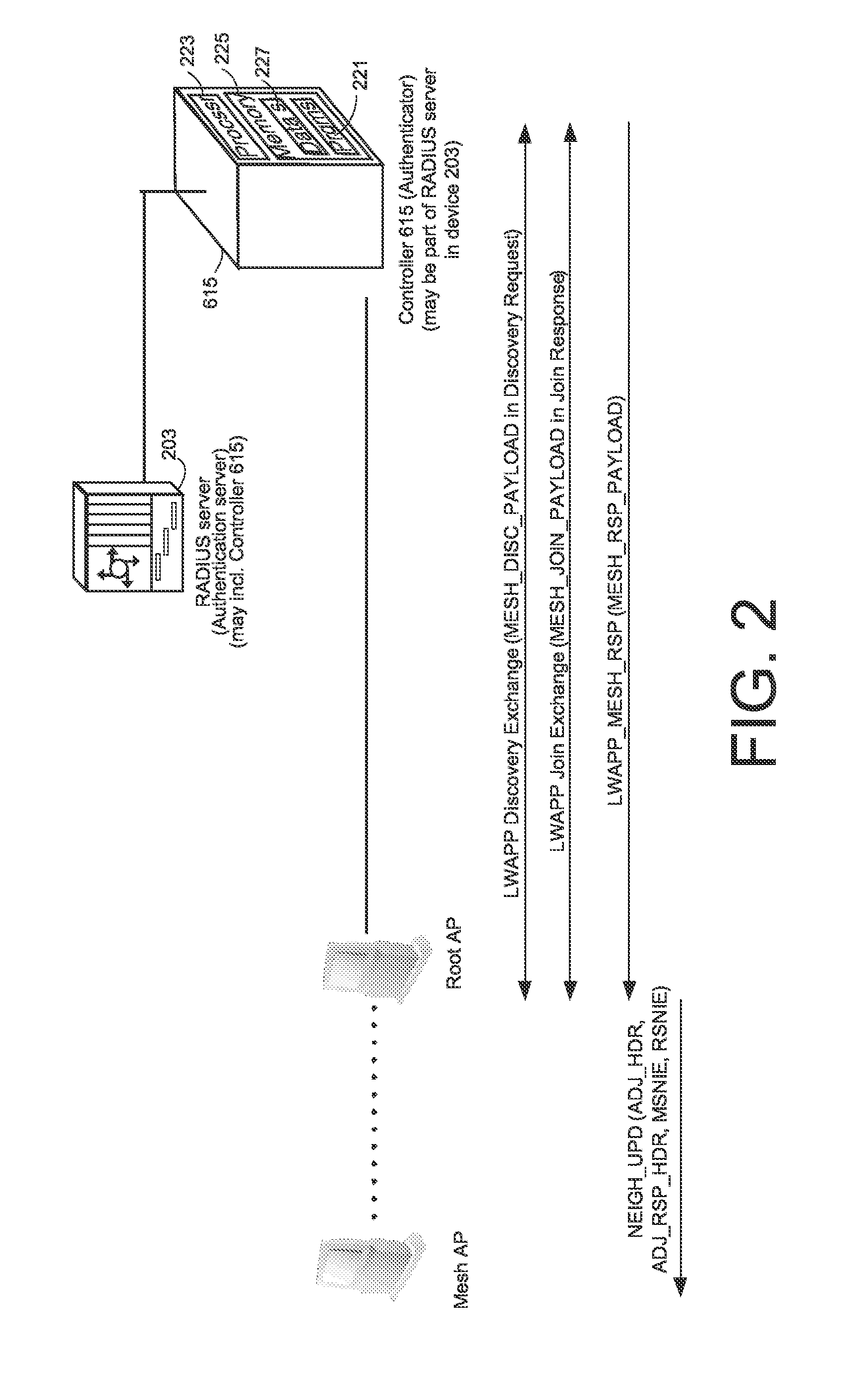
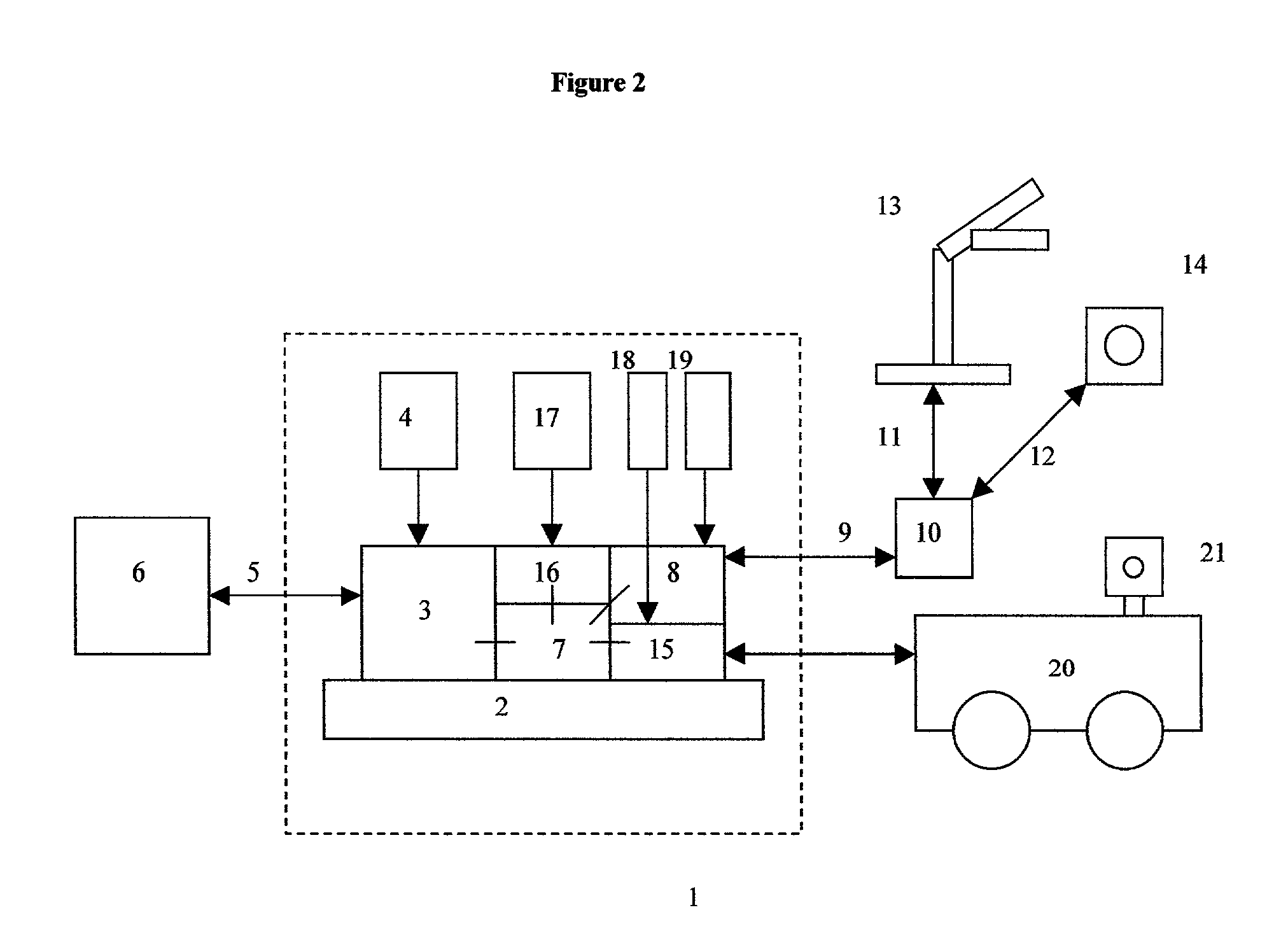
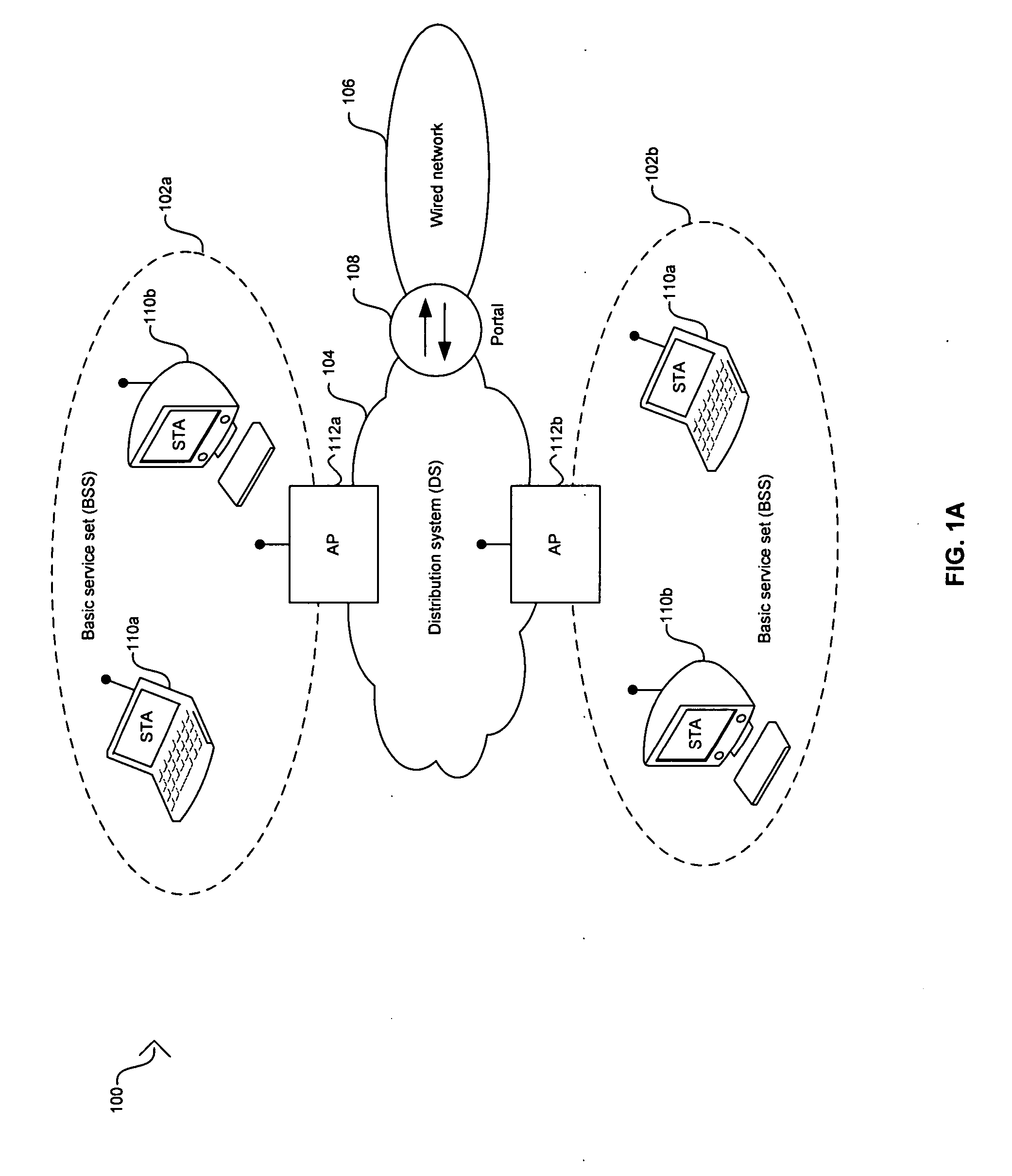
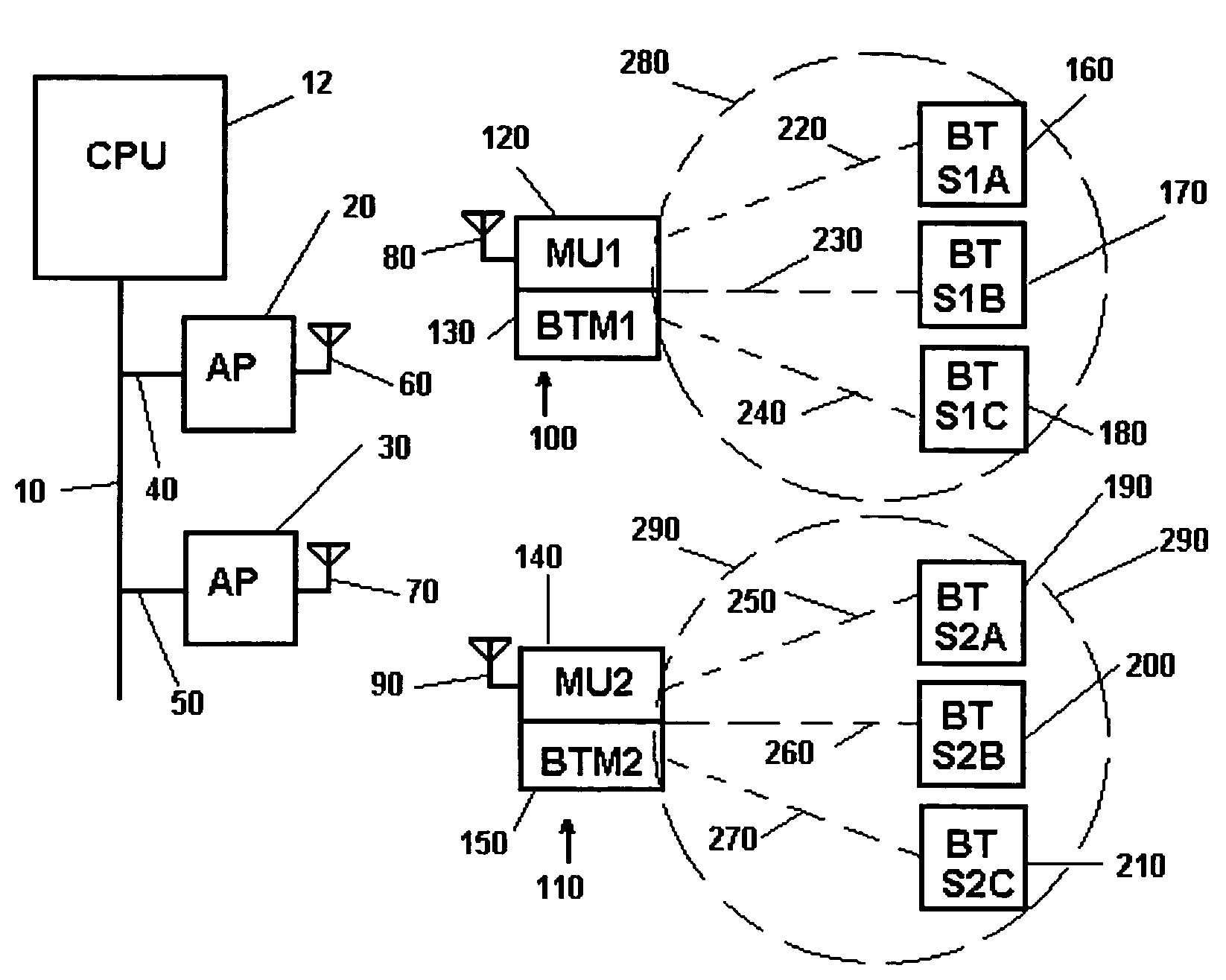
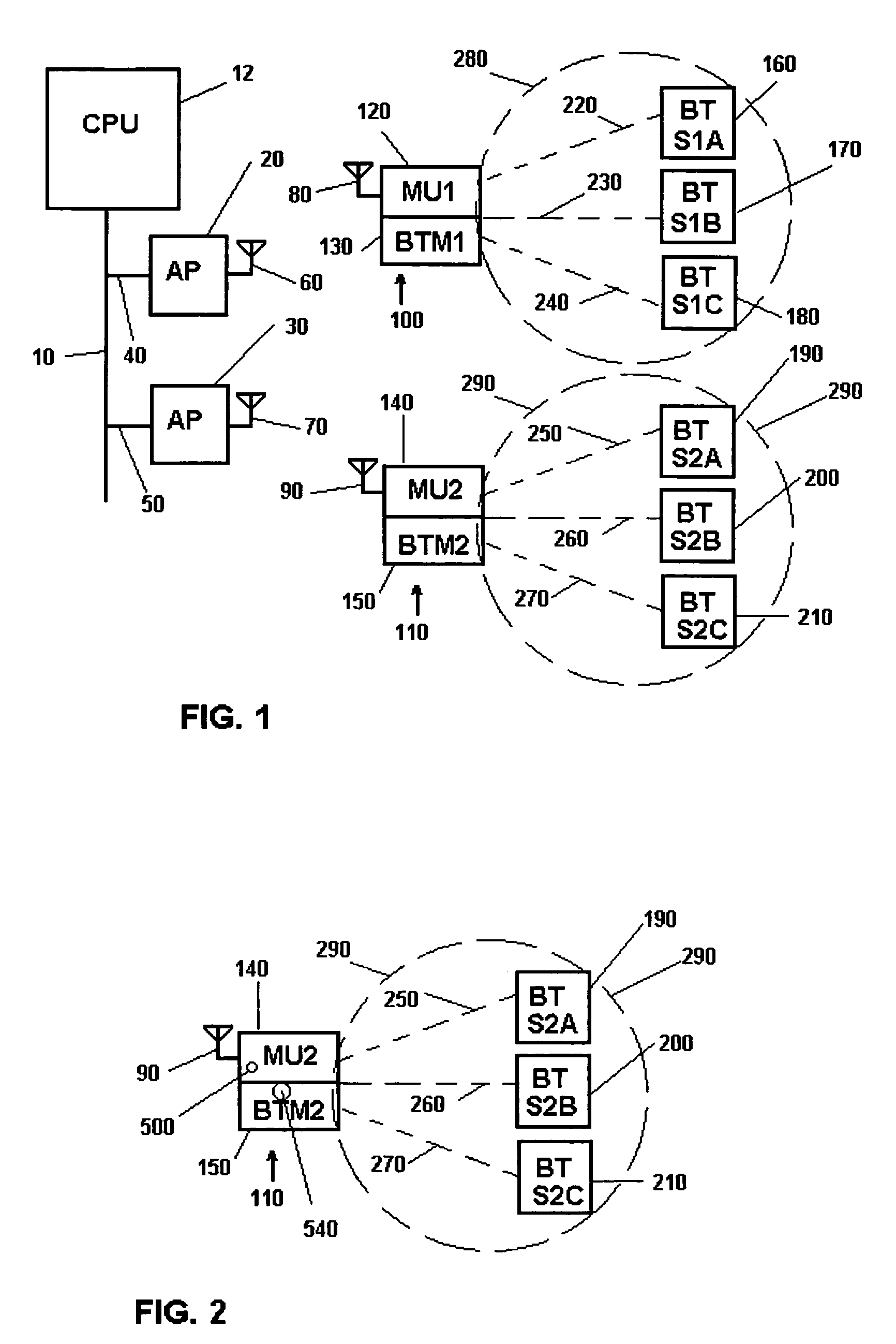
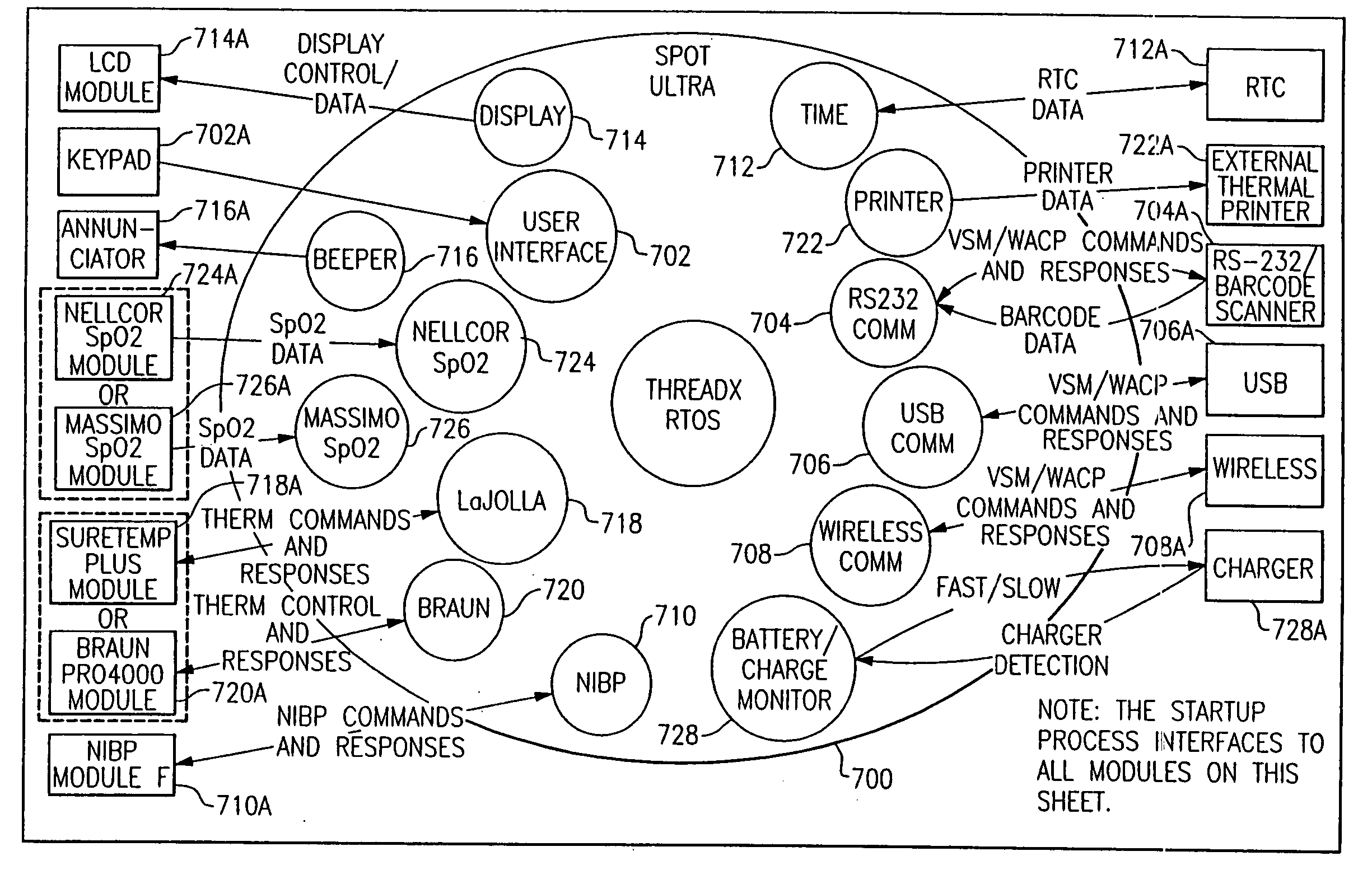
Methods of and apparatus for programming and managing diverse network components, including electronic-ink based display devices, in a mesh-type wireless communication network
InactiveUS20100177749A1Static indicating devicesDigital data processing detailsLogistics managementDisplay device
A wireless communication network for programming and monitoring a plurality of network-managed devices, including electronic-ink based display devices, comprising a network management computer system, a network gateway device, one or more wireless network routers, a plurality of network-managed devices, and a network coordinator. The wireless communication network of the present invention bridges the gap between wireless display networks, wireless sensor networks, and the worlds of passive, active and partially-active RFID and real-time locating systems. The wireless communication network of the present invention allows conventional communication network protocols to operate in more flexible ways in dynamic, diverse, and heterogeneous application environments, in fields including retail, healthcare, transport, logistics, manufacturing, education, etc. At the same time, the wireless communication network of the present invention is preferably based on the IEEE 802.15.4 network layer standard, which offers low-cost wireless network communication between a large number of wireless network end-devices.
Owner:METROLOGIC INSTR
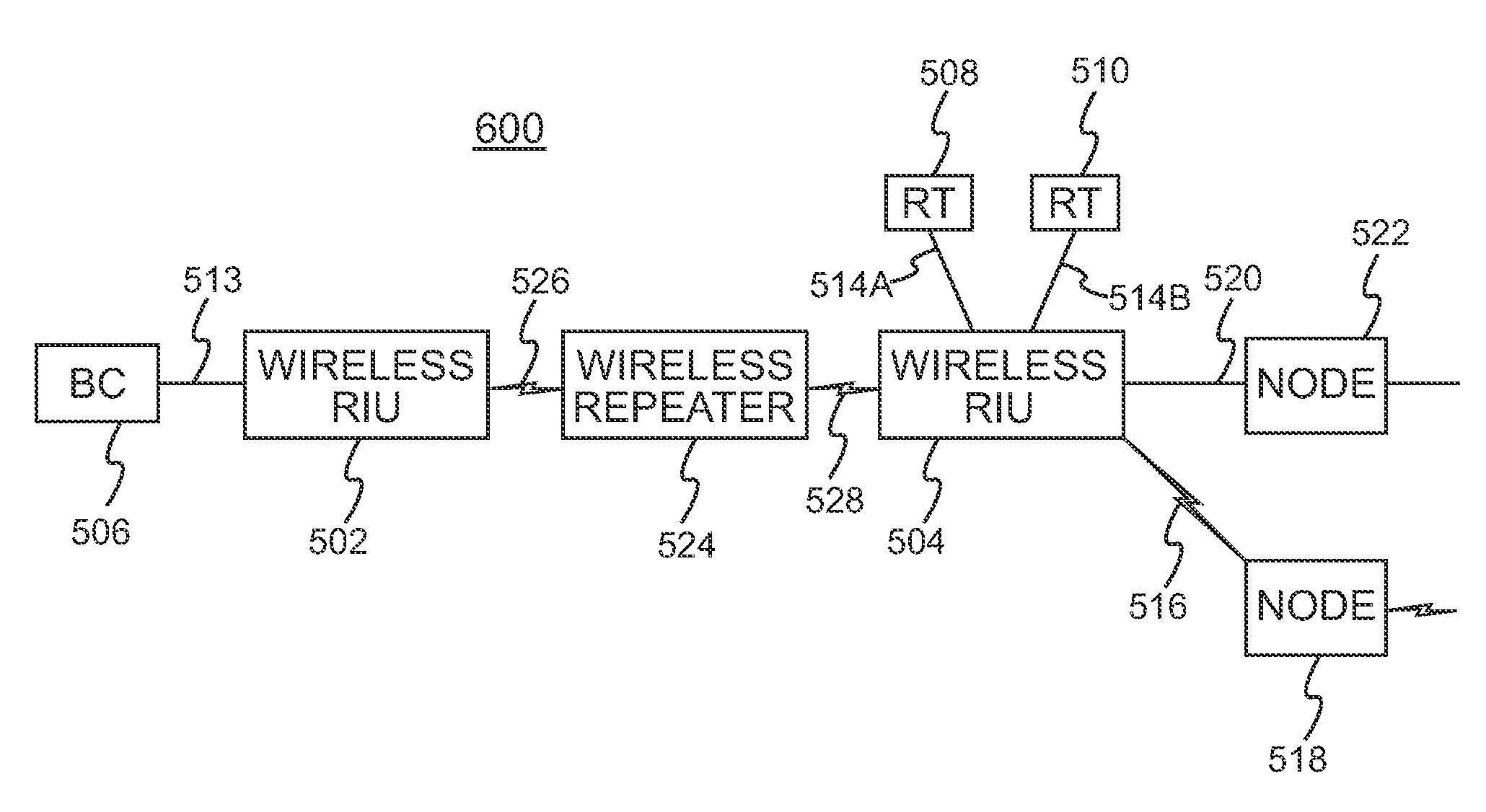
Wireless mesh point portable data terminal
ActiveUS8638806B2Power managementDigital data processing detailsMicrocontrollerWireless mesh network
A portable data terminal (PDT) adapted to participate in a wireless mesh network including a plurality of peer PDTs can comprise: a PDT module including an encoded information reading (EIR) device, and a mesh point (MP) module communicatively coupled to the PDT module. The MP module can include a microcontroller and at least one wireless communication interface and can be configured to perform IEEE 802.11-conformant wireless station services including authentication, de-authentication, privacy, and MAC service data unit delivery, and IEEE 802.11-conformant wireless distribution system services including association, disassociation, distribution, integration, and re-association. The MP module can be further configured, responsive to receiving a MAC frame addressed to a recipient inside the wireless mesh network, to deliver the MAC frame using the distribution service. The MP module can be further configured, responsive to receiving a MAC frame addressed to a recipient outside of the wireless mesh network, to deliver the MAC frame using the integration service. The MP module can be further configured to route an incoming MAC frame according to its destination address and the frame control field. The MP module can be further configured to cause the PDT module to exit said sleeping state responsive to receiving a mobile management software (MMS) wake-up command.
Owner:HAND HELD PRODS
Method of interference management for interference/collision avoidance and spatial reuse enhancement
InactiveUS20050058151A1Improve rendering capabilitiesImprove channel utilizationEnergy efficient ICTPower managementDifferentiated servicesDifferentiated service
A method called the evolvable interference management (EIM) method is disclosed in this patent for avoiding interference and collision and increasing network throughput and energy efficiency in wireless networks. EIM employs sensitive CSMA / CA, patching approaches, interference engineering, differentiated multichannel, detached dialogues, and / or spread spectrum techniques to solve the interference and QoS problems. EIM-based protocols can considerably increase network throughput and QoS differentiation capability as compared to IEEE 802.11e in multihop networking environments. Due to the improvements achievable by EIM, the techniques and mechanisms presented in this application may be applied to obtain an extension to IEEE 802.11 to better support differentiated service and power control in ad hoc networks and multihop wireless LANs. New protocols may also be designed based on EIM.
Owner:YEH CHIHSIANG
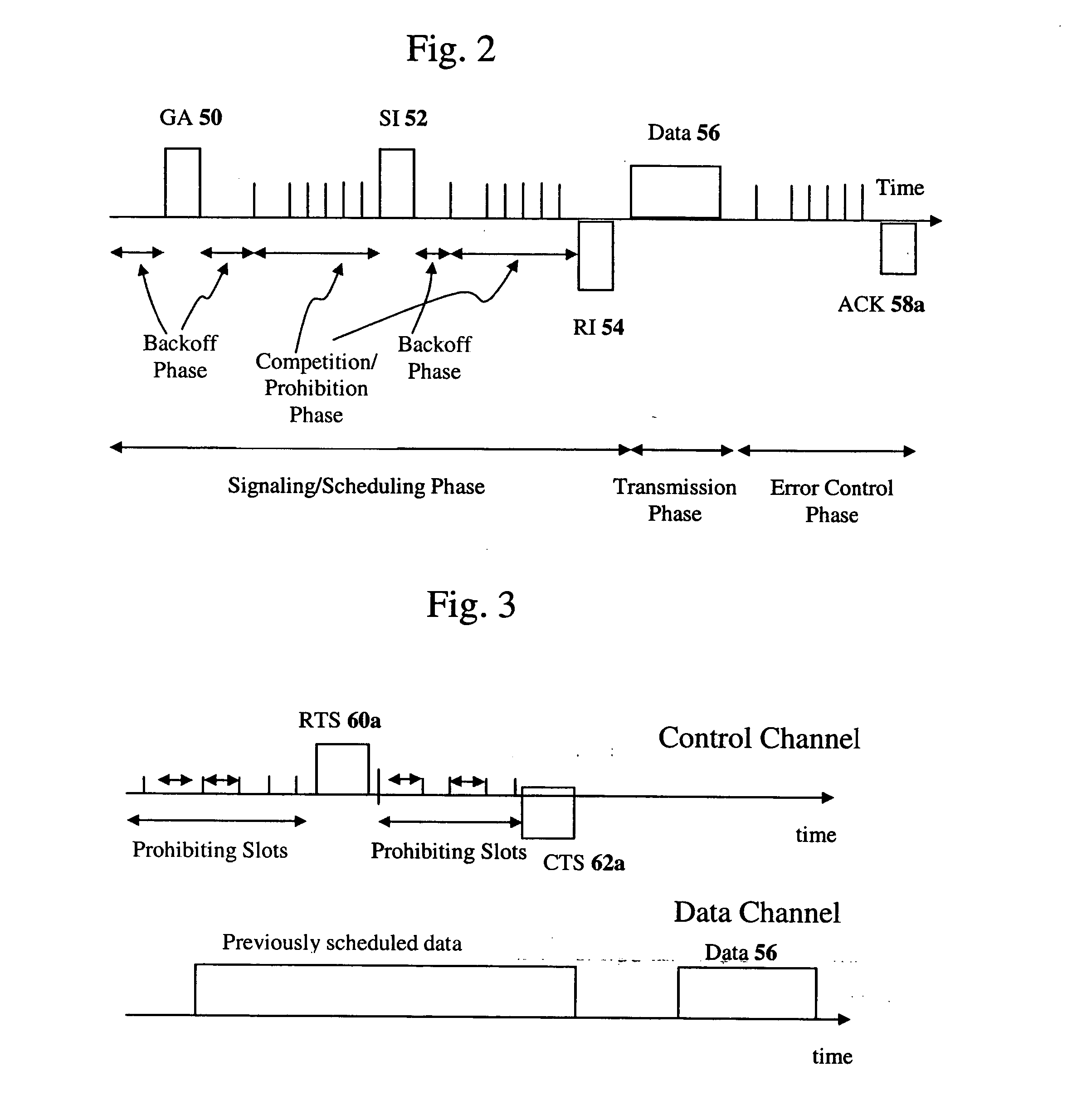
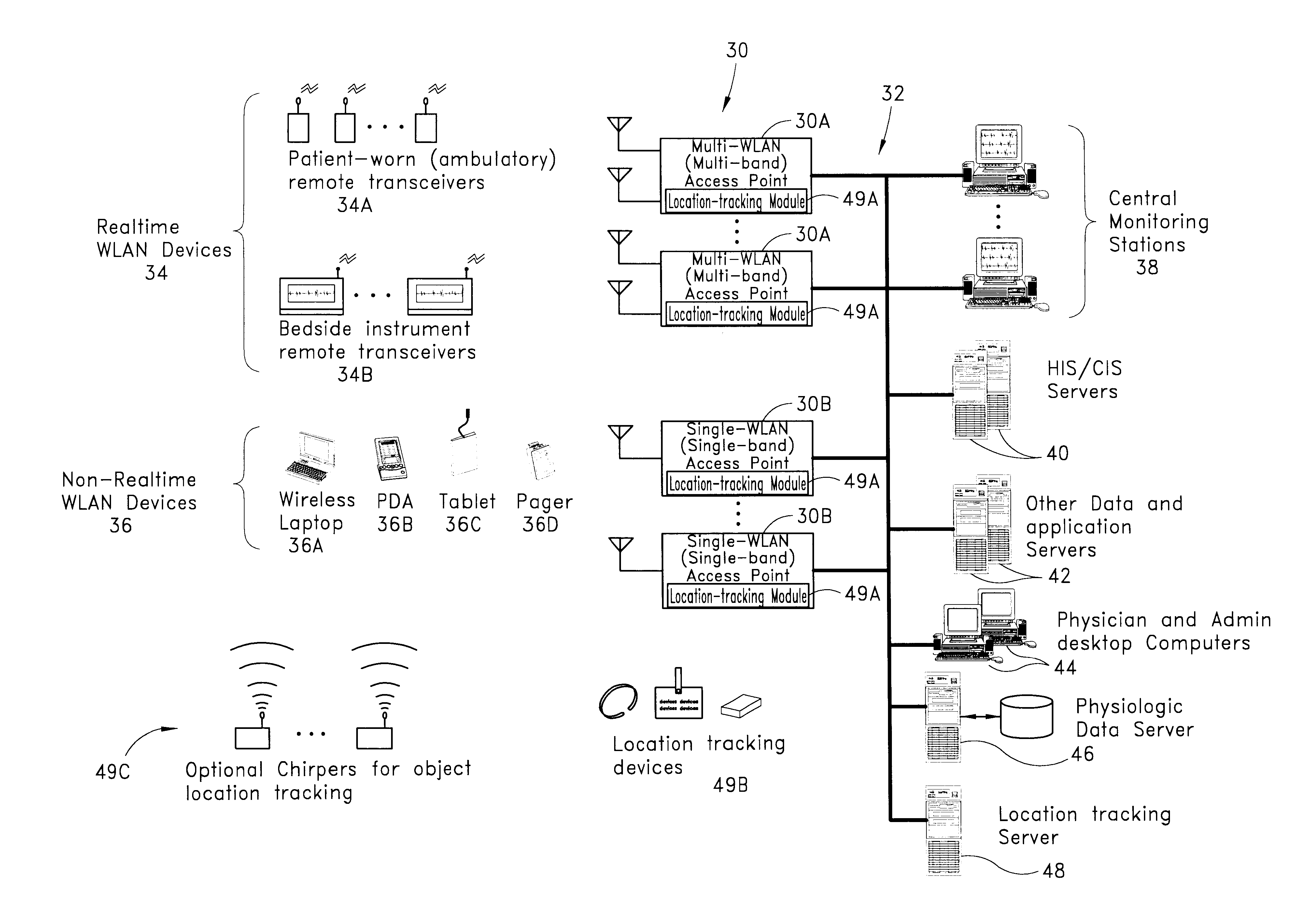
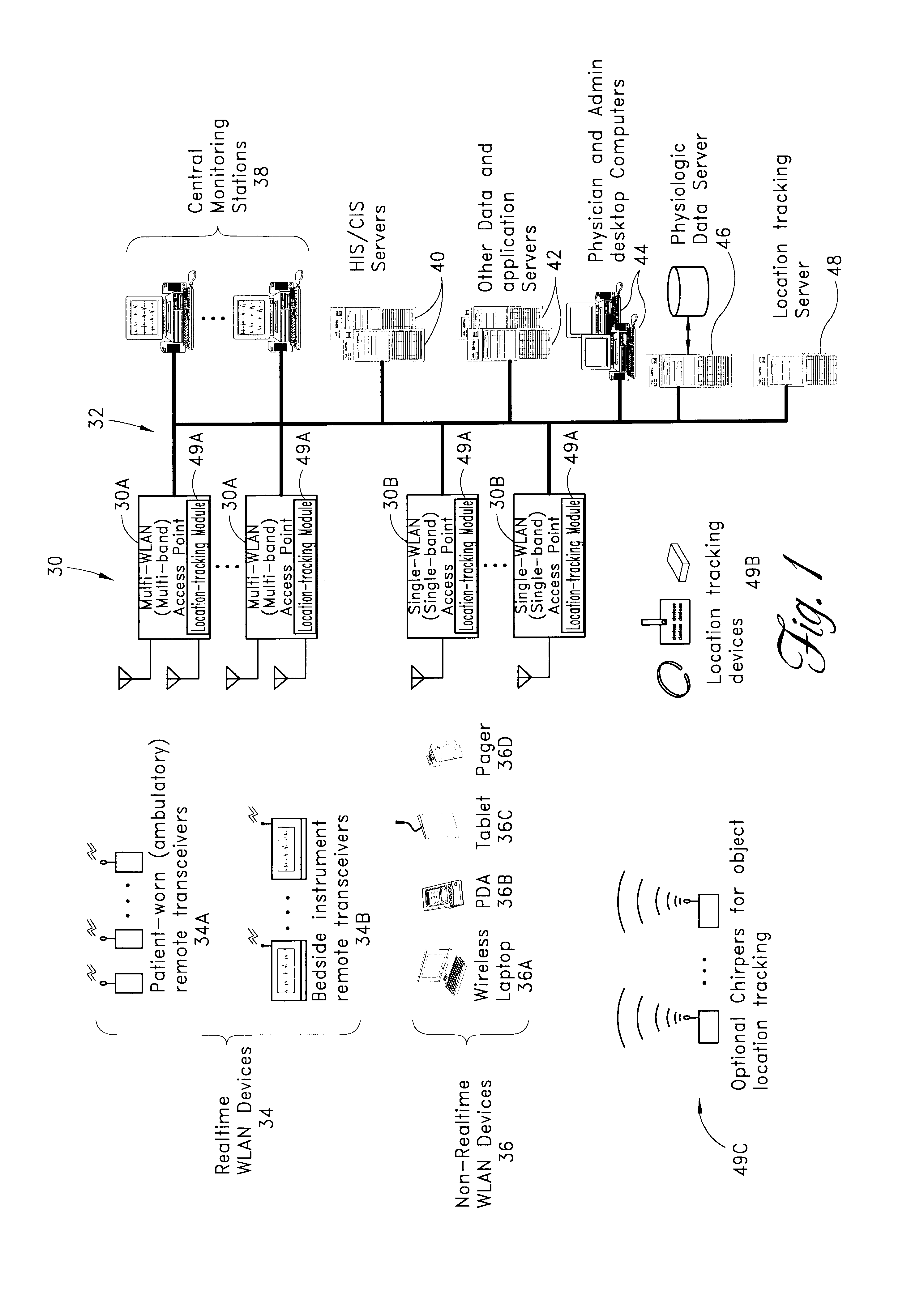
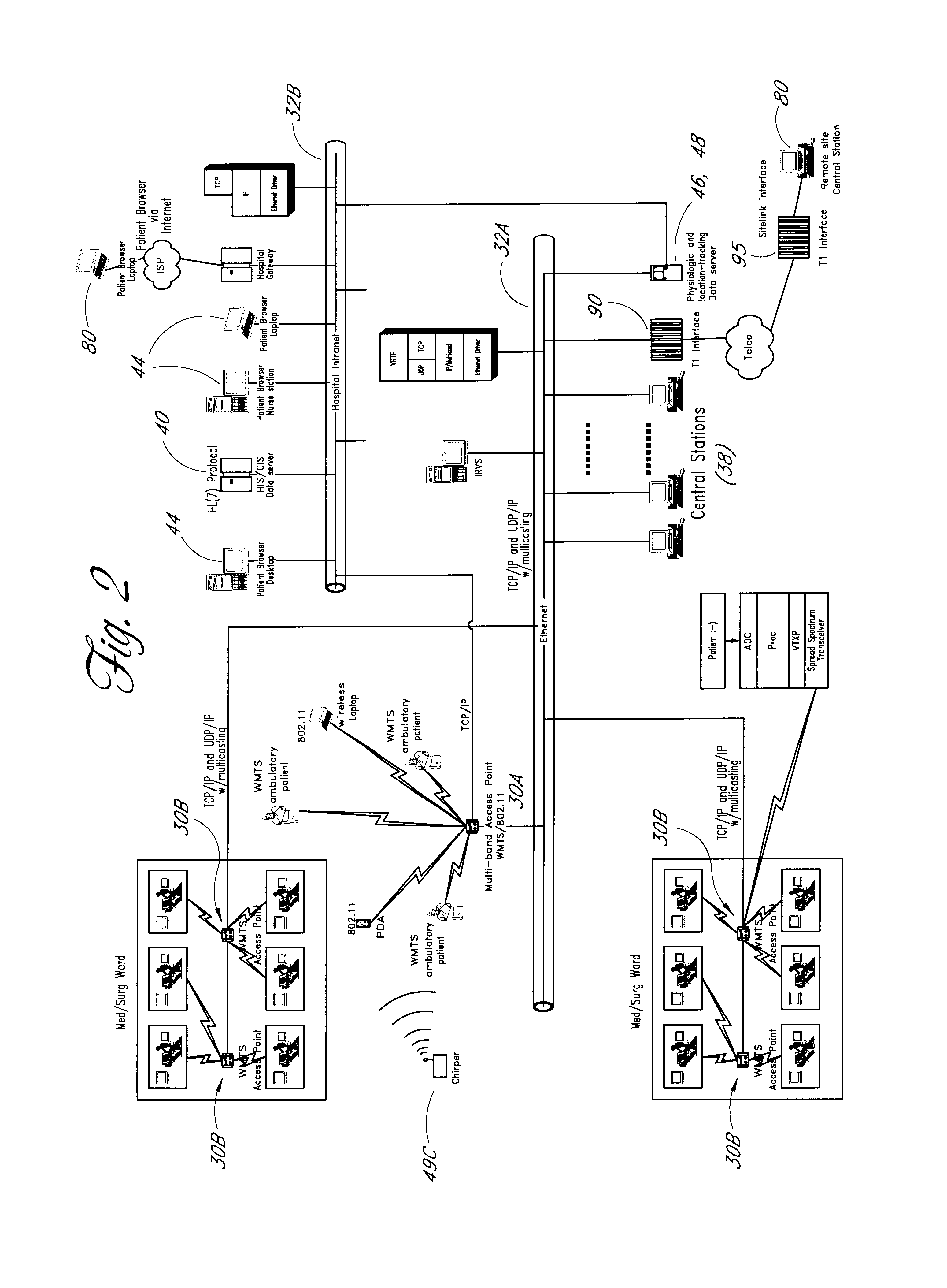
Wireless LAN architecture for integrated time-critical and non-time-critical services within medical facilities
InactiveUS6659947B1Avoiding lockstep interferenceEasy to receiveSurgeryData switching by path configurationAntenna designDevice type
A wireless local area network (WLAN) system comprises multiple access points that are distributed throughout a medical facility to provide wireless access to a hardwired network. The access points implement multiple WLAN protocols, including a realtime protocol for realtime patient monitoring (telemetry) and a standard WLAN protocol (such as IEEE 802.11 within an ISM band) for providing general-purpose wireless access. Some or all of the access points preferably implement both WLAN protocols such that the different WLANs and wireless device types share network access resources. Some or all of the access points may also include RF location-tracking modules which may be used to track locations of patients, hospital personnel, capital equipment, and / or disposable medical supplies. Also disclosed are an antenna design which may be used with the access points to improve reception (particularly for patient monitoring), and a TDMA timeslot rotation method for avoiding lockstep interference between access points that operate on the same channel.
Owner:GE MEDICAL SYST INFORMATION TECH
Remote monitoring and control system
ActiveUS7825793B1Substation equipmentTransmissionCommunications systemNetwork Communication Protocols
A communication system that provides communication of information between an end user device and a remote end user. The system includes a communication node mounted on the upper part of a utility pole, and drawing its power from the utility pole through a standard NEMA Locking 3 Pole Receptacle, and adapted to communicate with a nearby user device using the low-power communication protocol, such as the ZigBee protocol (ANSI IEEE 802.15.4) or Radio Frequency Identification Device (RFID) technology, and also adapted to communicate with a neighborhood mesh network of nodes mounted on utility poles. The neighborhood mesh network is capable of communicating, through a regional computer network, with the remote end user.
Owner:SUNRISE TECH
Apparatus for and method of coordinating transmission and reception opportunities in a communications device incorporating multiple radios
InactiveUS20090180451A1Avoid interferenceDelay transitionNetwork topologiesSubstation equipmentOperation modeMobile station
A novel and useful apparatus for and method of coordinating the allocation of transmission and reception availability and / or unavailability periods for use in a communications device incorporating collocated multiple radios. The mechanism provide both centralized and distributed coordination to enable the coordination (e.g., to achieve coexistence) of multiple radio access communication devices (RACDs) collocated in a single device such as a mobile station. A distributed activity coordinator modifies the activity pattern of multiple RACDs. The activity pattern comprises a set of radio access specific modes of operation, (e.g., IEEE 802.16 Normal, Sleep, Scan or Idle modes, 3GPP GSM / EDGE operation mode (PTM, IDLE, Connected, DTM modes), etc.) and a compatible set of wake-up events, such as reception and transmission availability periods. To prevent interference and possible loss of data, a radio access is prevented from transmitting or receiving data packets while another radio access is transmitting or receiving. In the event two or more RATs desire to be active at the same time, the mechanism negotiates an availability pattern between the MS and a corresponding BS to achieve coordination between the RATs.
Owner:COMSYS COMM & SIGNAL PROC
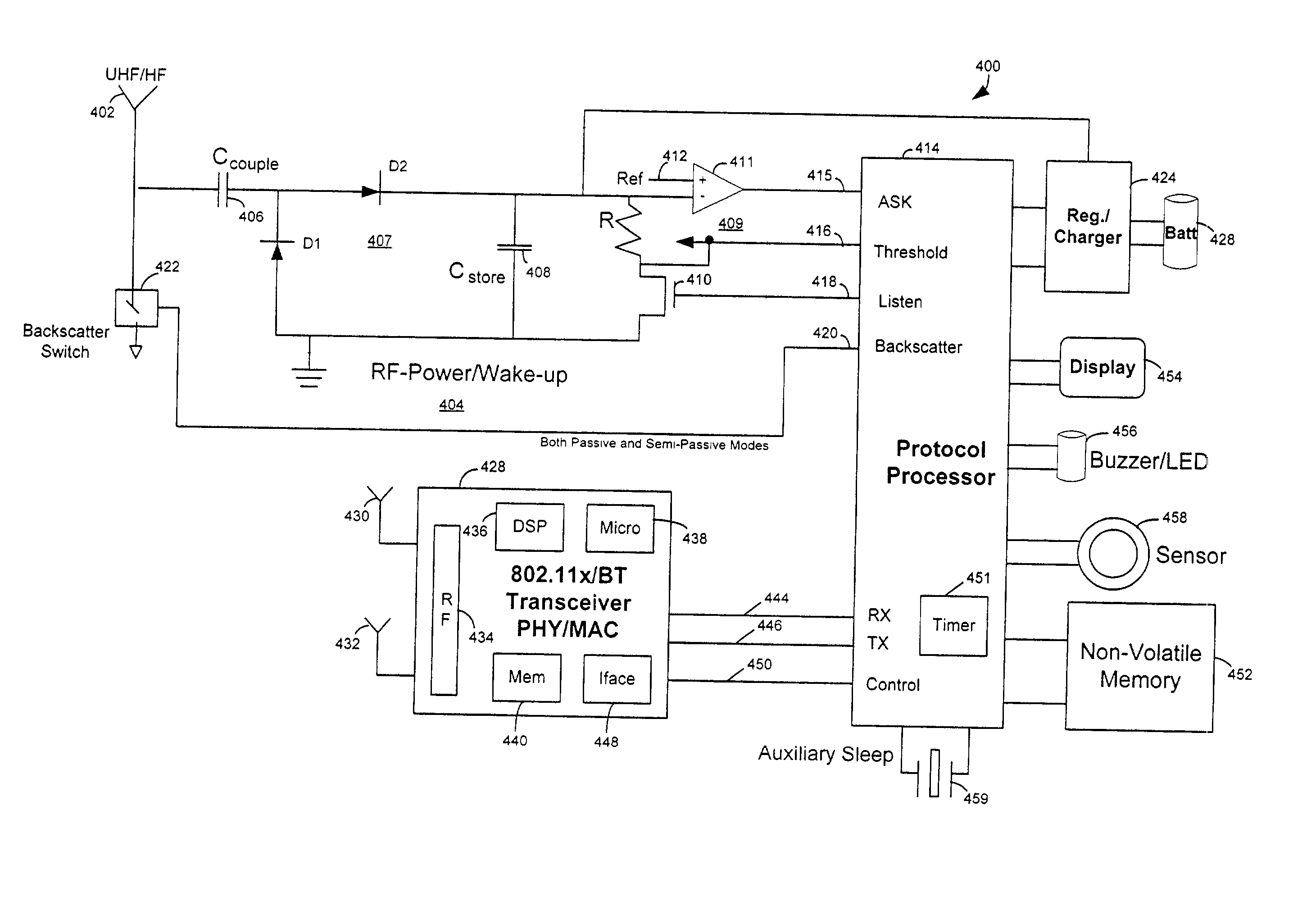
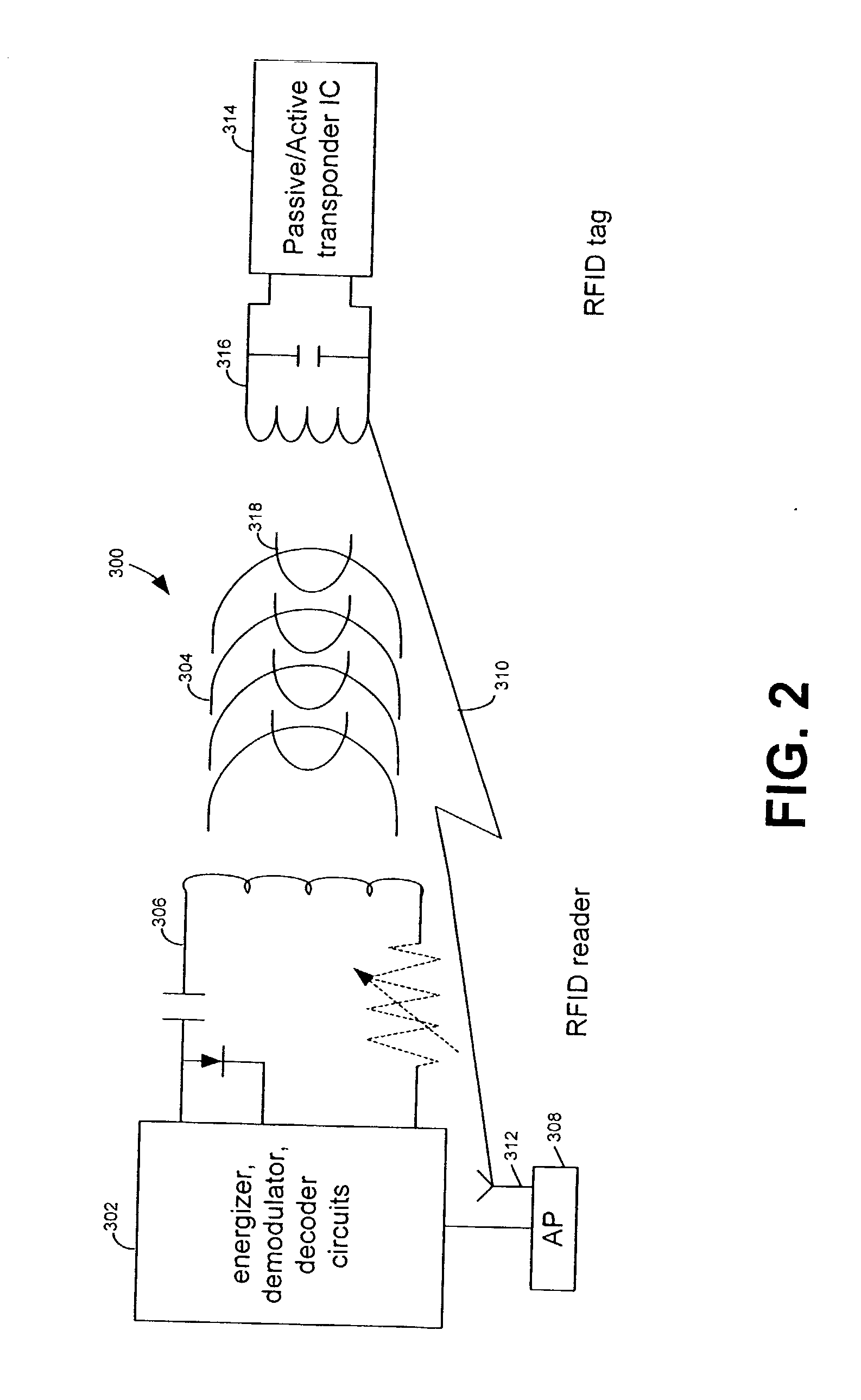
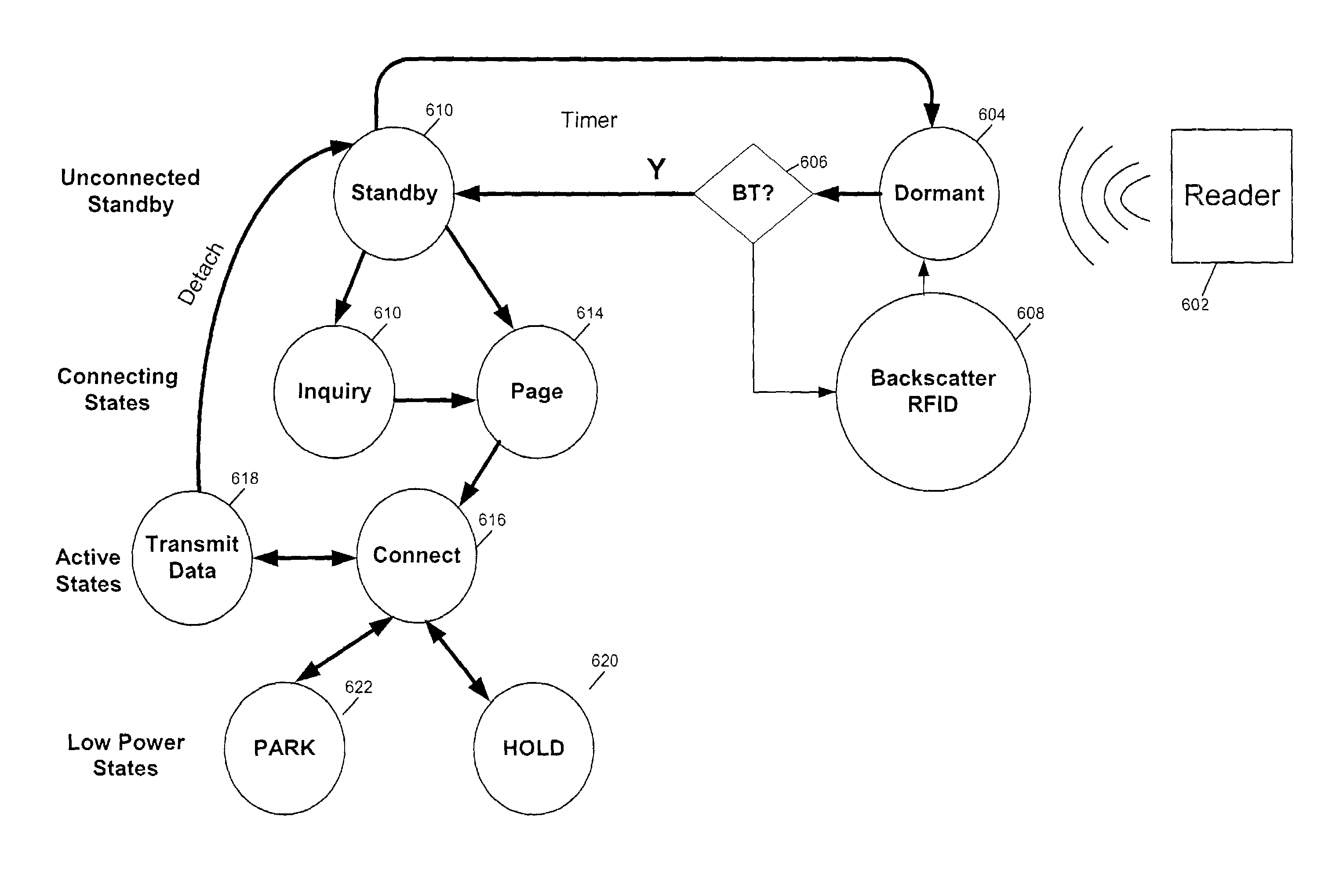
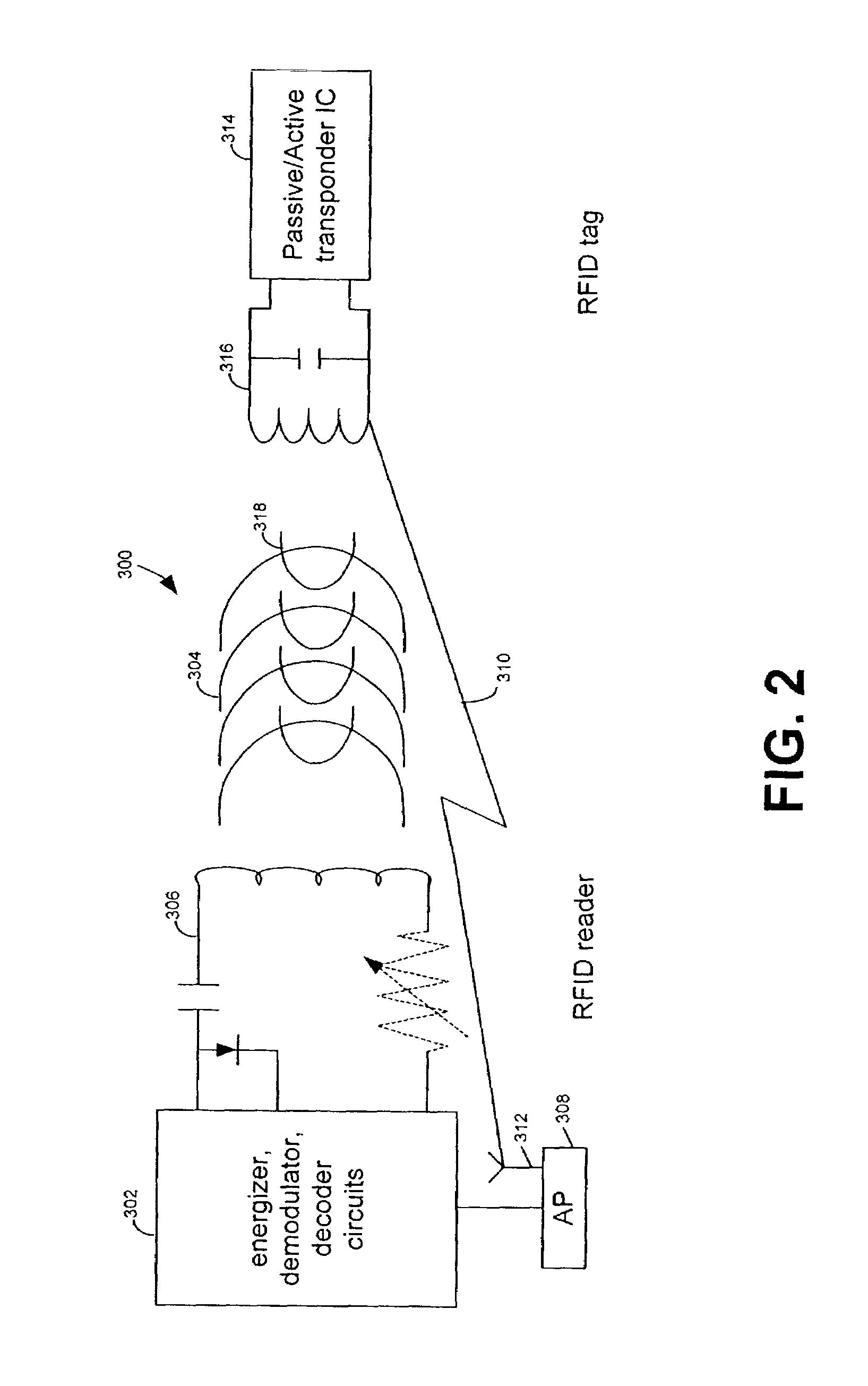
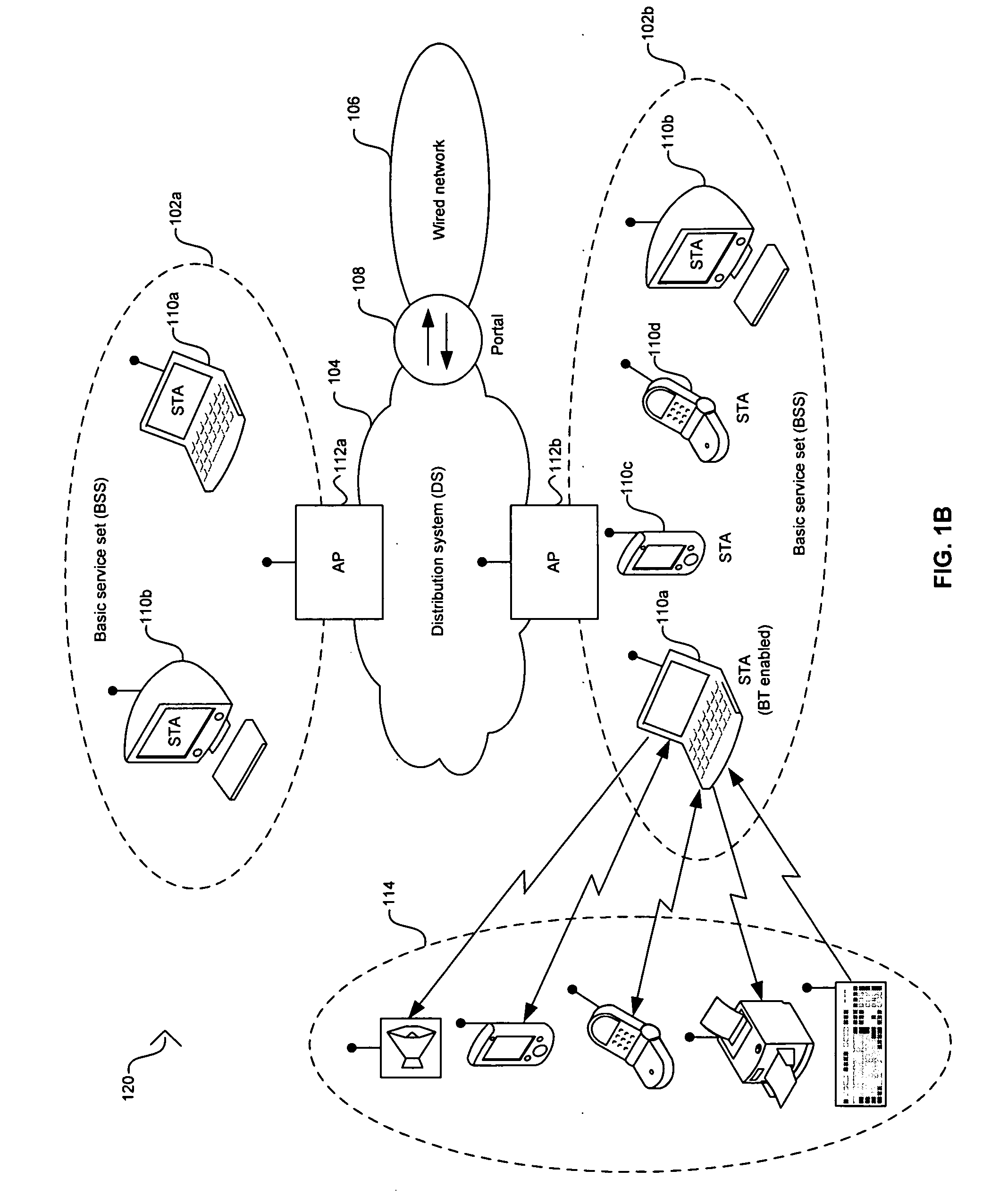
RFID device, system and method of operation including a hybrid backscatter-based RFID tag protocol compatible with RFID, bluetooth and/or IEEE 802.11x infrastructure
ActiveUS20030104848A1Near-field transmissionMemory record carrier reading problemsTransceiverAntenna impedance
An RFID system includes a hybrid backscatter-based RFID tag protocol-compatible with existing 802.11x / Bluetooth Standards as well as RFID standards. The tag is linked to a multi-protocol Interrogator via a generated RF Continuous Wave (CW) field. The tag includes an antenna coupled to an RFID and a Bluetooth / 802.11x transceiver section. A Protocol Processor services RFID and transceiver sections and is coupled to the antenna via a backscatter switch. The Interrogator can switch the tag to an RFID backscatter radiation mode where the processor switches the antenna impedance to reflect the CW signal. For transceiver operation the processor switches antenna impedance in synchronization with a frame organized bit stream. For reception, the RFID section utilizes demodulation techniques, typically Amplitude Shift Keying (ASK), and provides a wake up mode within a predetermined distance of the Interrogator. The transceiver may operate in a backscatter or regular mode as directed by an Access Point.
Owner:GOOGLE TECH HLDG LLC
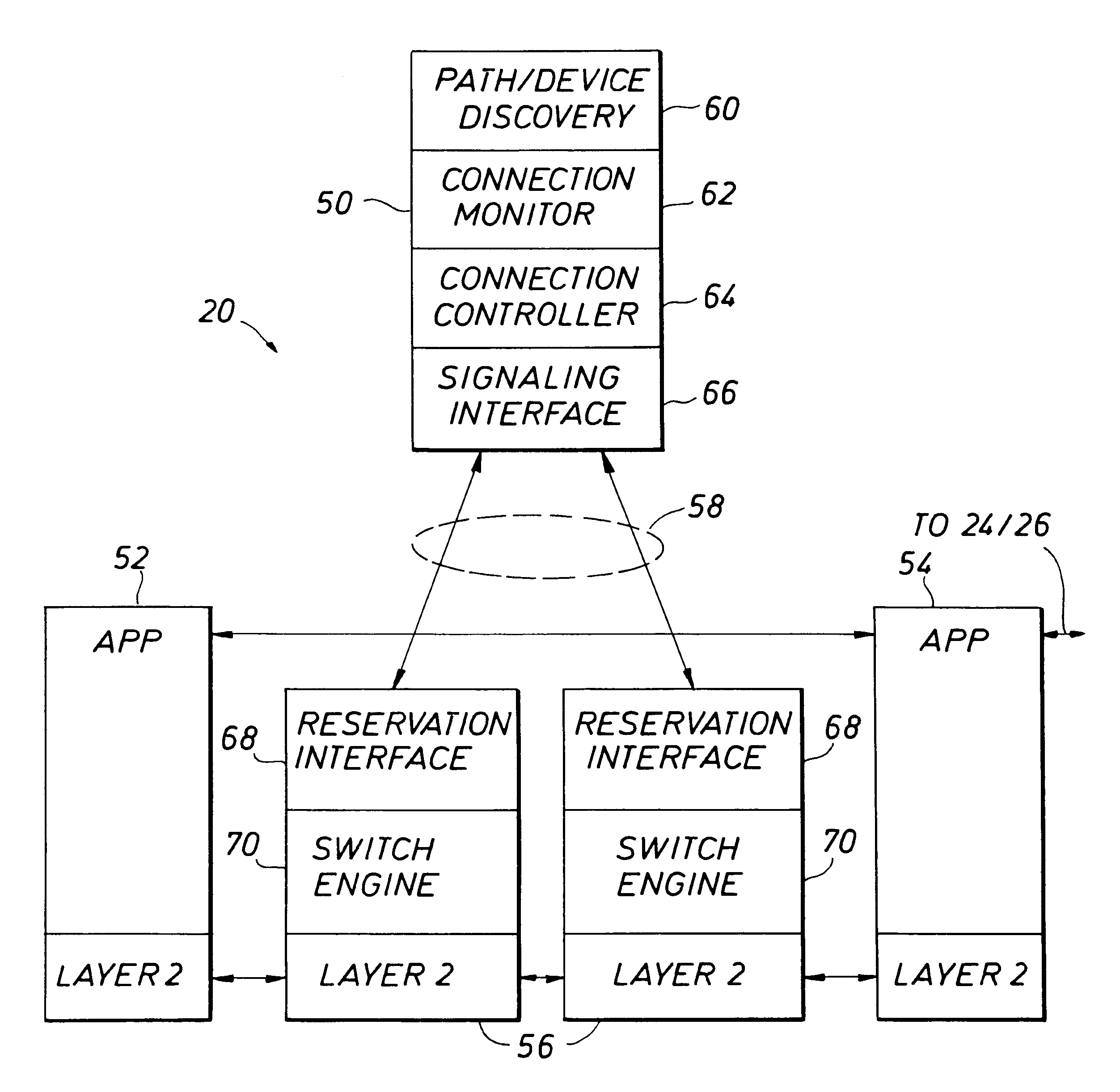
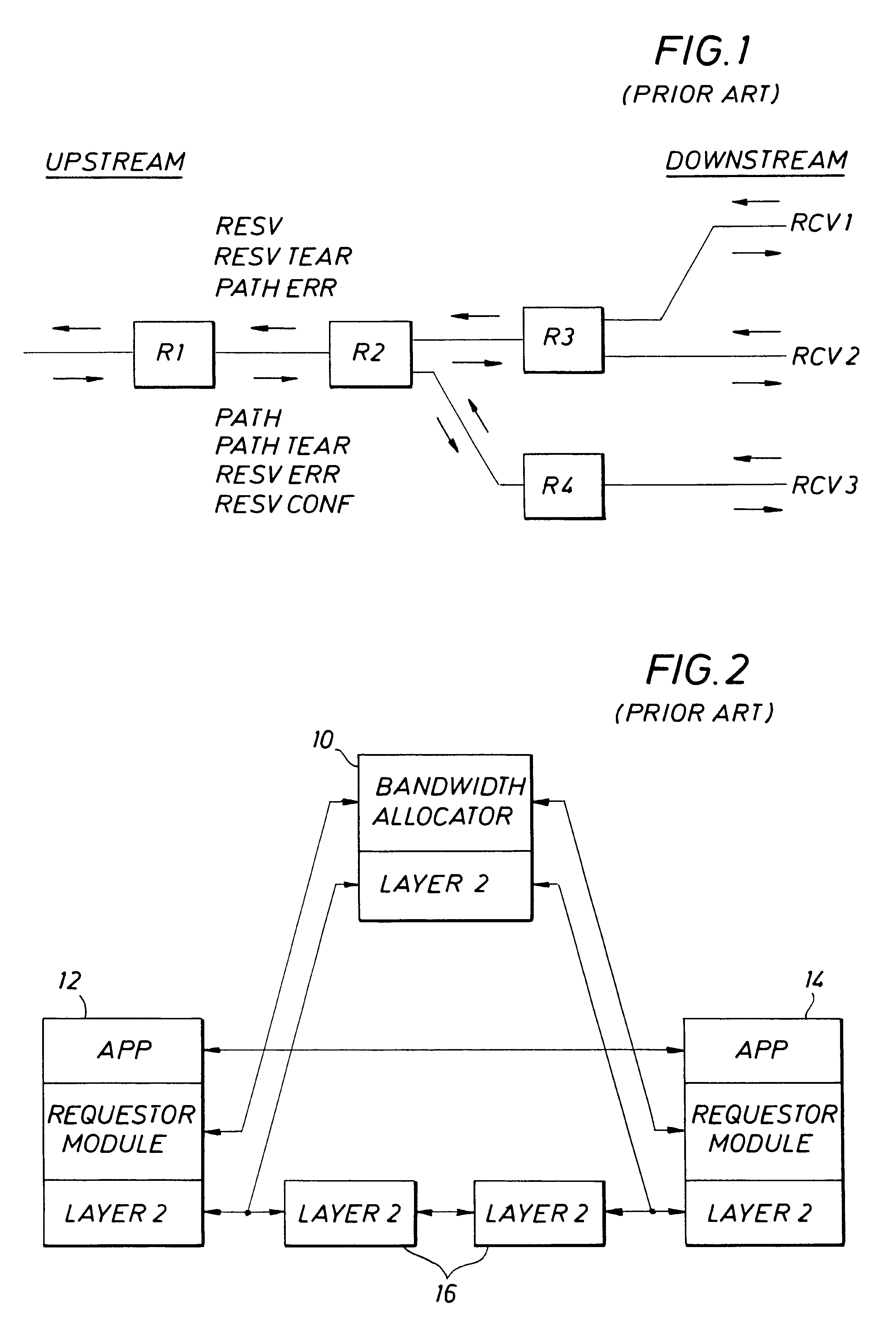
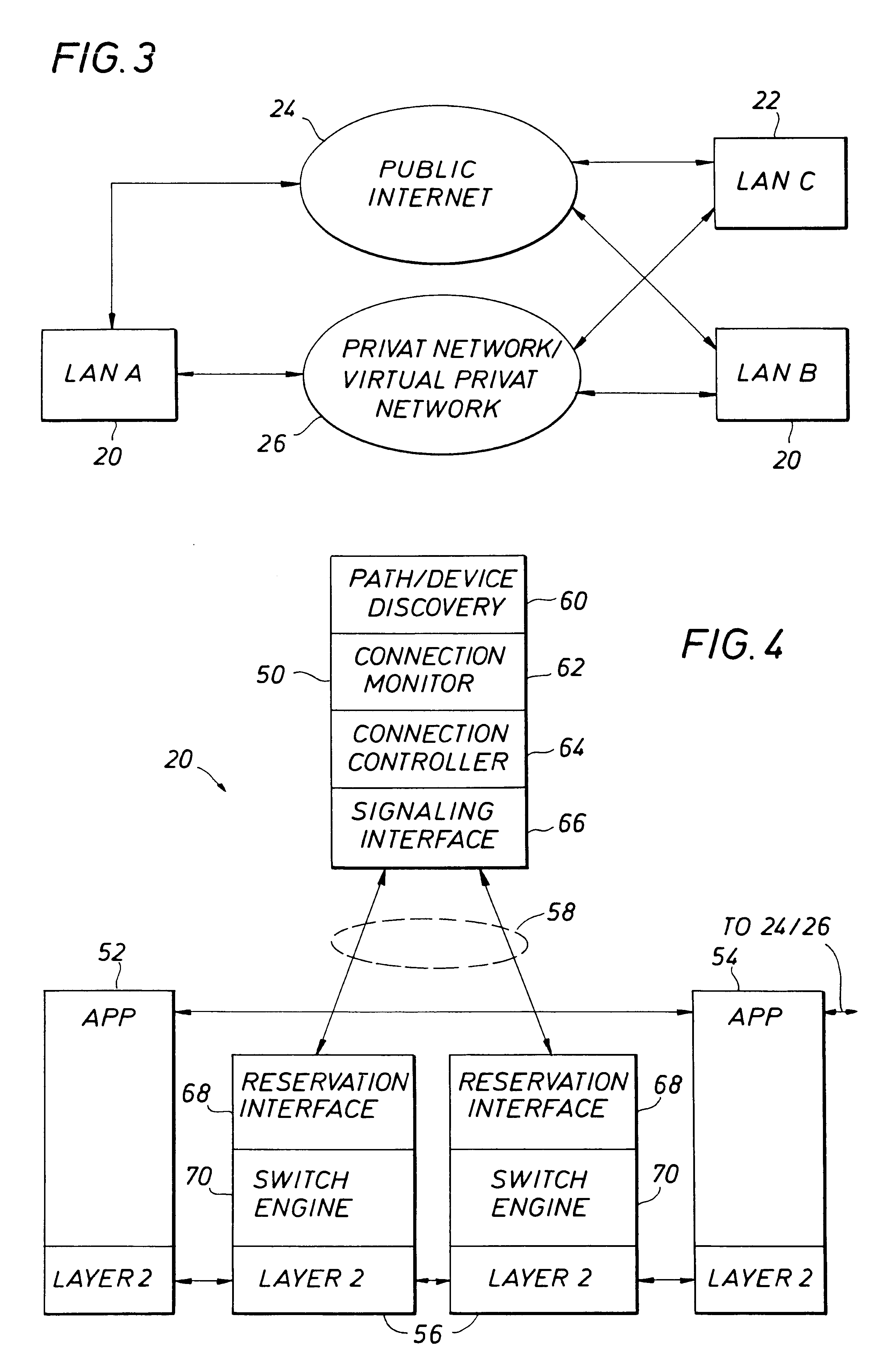
Method and apparatus for providing guaranteed quality/class of service within and across networks using existing reservation protocols and frame formats
InactiveUS6563793B1Error preventionFrequency-division multiplex detailsAssurance qualityClass of service
A method and apparatus provide reserved bandwidth and QOS / COS virtual circuit connections in a network using both conventional and novel reservation protocols and frame formats. An apparatus according to the invention includes an enterprise control point that communicates with switches via a reserved signaling channel. The switches have been upgraded or replaced to include enhanced functionality. The enhanced switches detect packets that include requests for reserved connections according to existing reservation protocols such as RSVP and IEEE 802.1P / Q. Such detected packets are forwarded to the enterprise control point for processing via a reserved signaling channel. The enterprise control point identifies a path within the network that can satisfy the requested QOS / COS and reserves the requested resources all along the path from beginning to end. A method according to the invention includes detecting packets that include requests for reserved connections according to existing reservation protocols such as RSVP and IEEE 802.1P / Q, forwarding detected packets to an enterprise control point for processing via a reserved signaling channel, identifying a path within the network that can satisfy the requested QOS / COS and reserving the requested resources all along the path from beginning to end.
Owner:WARPSPEED COMM
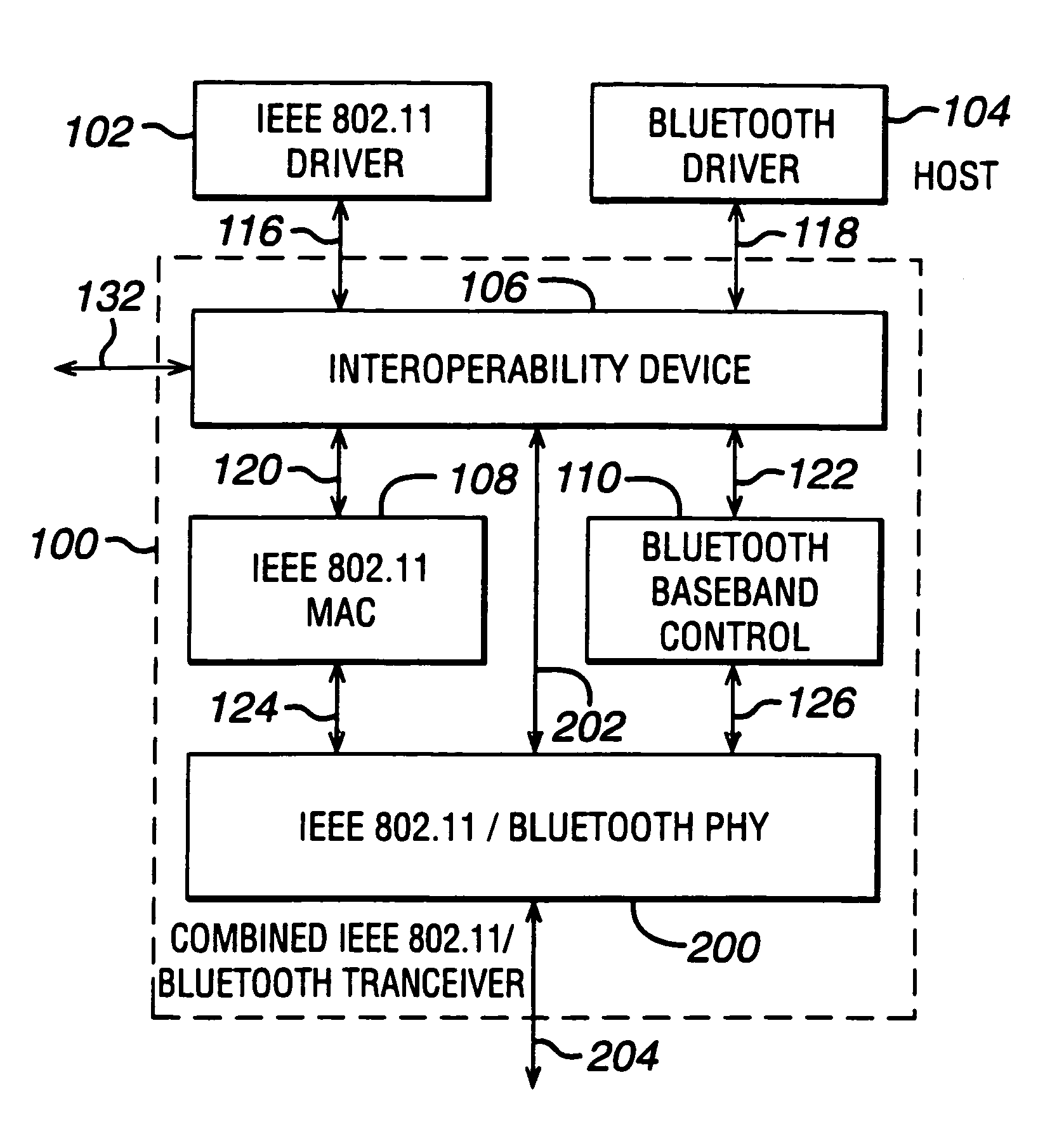
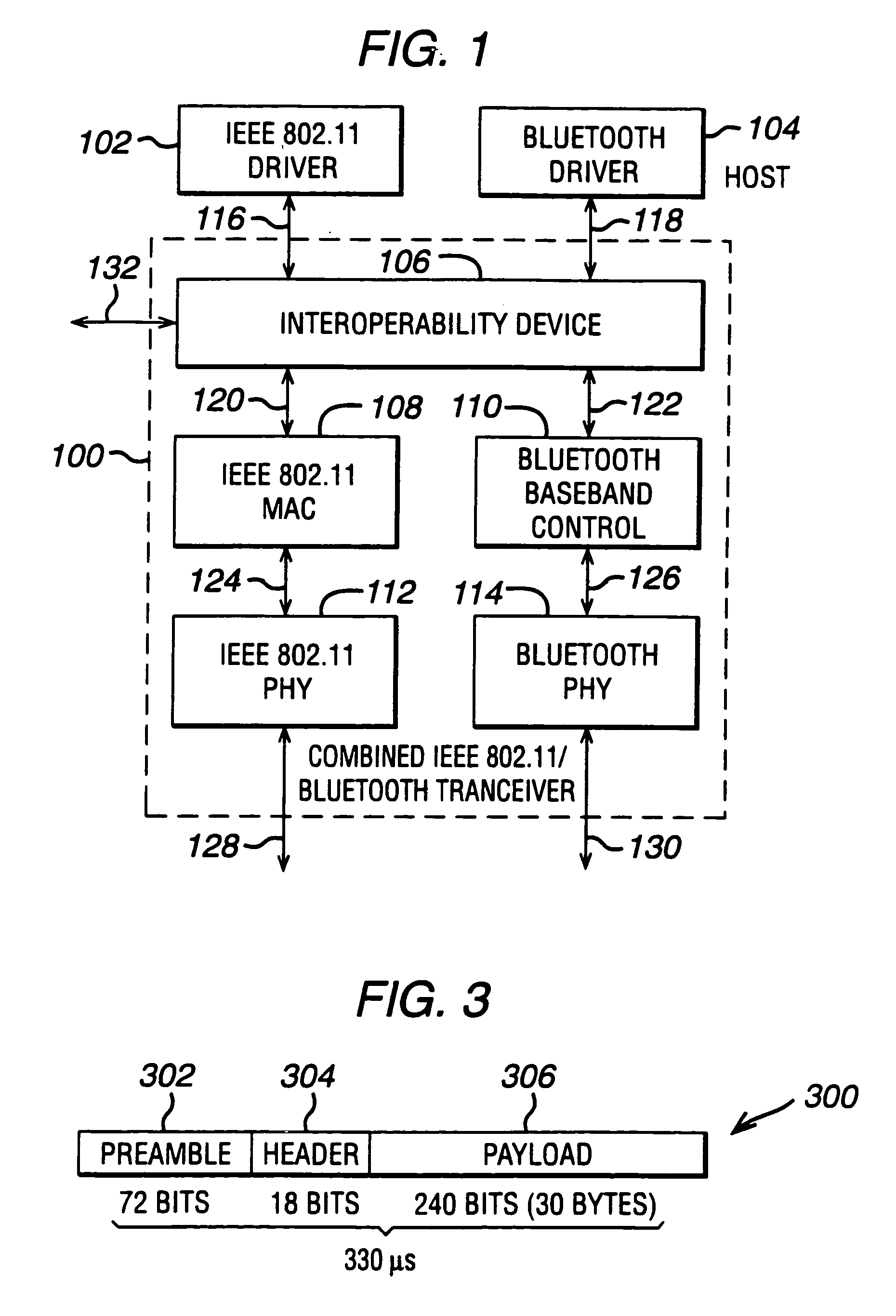
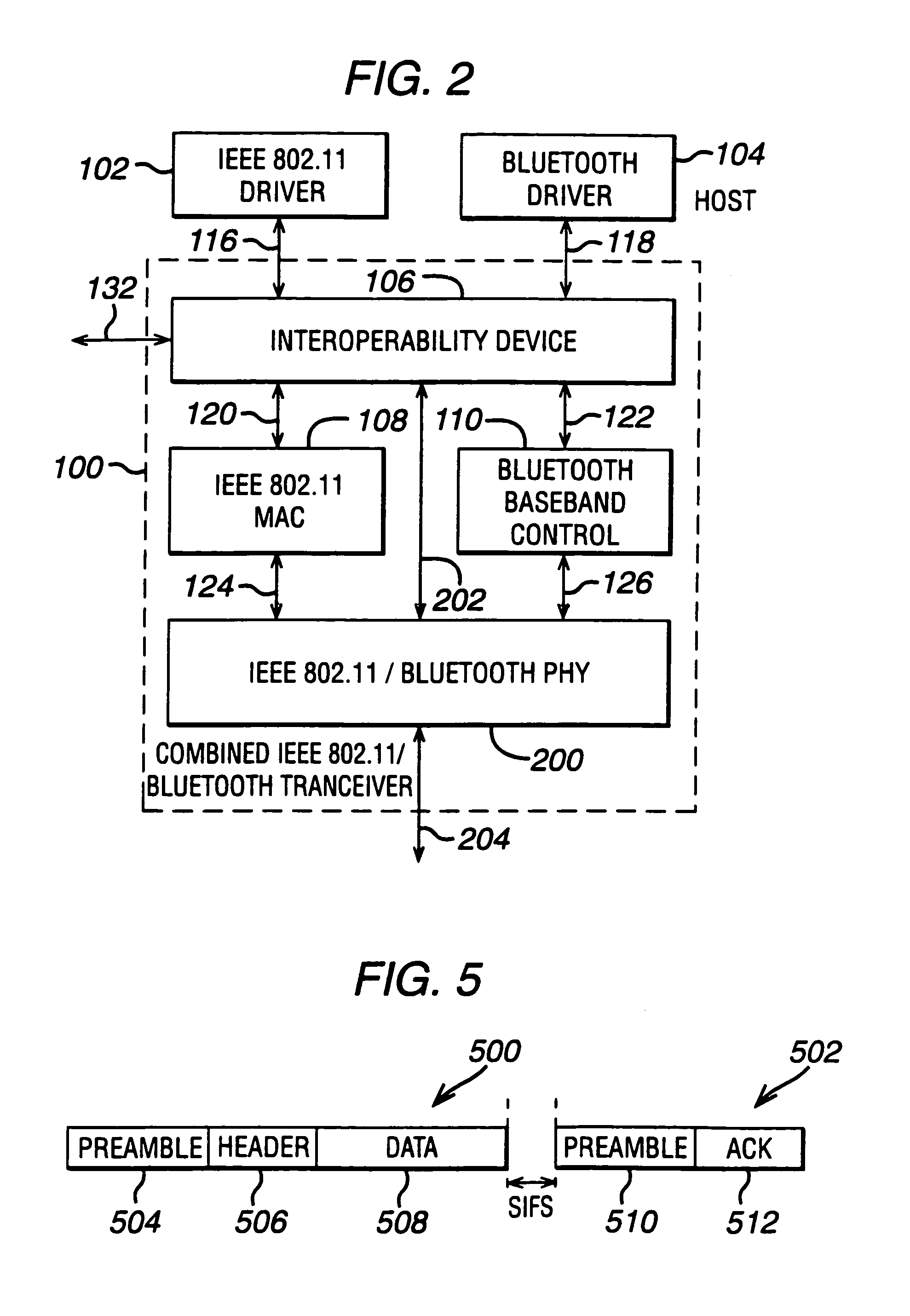
Interoperability for bluetooth/IEEE 802.11
InactiveUS7046649B2Cheap and small hardware designAvoid spreadingMultiplex communicationNetwork topologiesCommunications systemTransceiver
The key of the invention is to introduce an interoperability device in a communication system which integrates an IEEE 802.11 transceiver and a Bluetooth transceiver. The device prevents that one transceiver is transmitting while the other is receiving, which would cause interference at the receiving transceiver. In addition, the device preferably prevents that both systems are transmitting at the same time to avoid interference at the receiving device(s). Optionally the device prohibits simultaneous reception of both transceivers. In that way the radio receiver can be shared between the devices, allowing a cheaper and smaller hardware design.
Owner:AVAGO TECH INT SALES PTE LTD
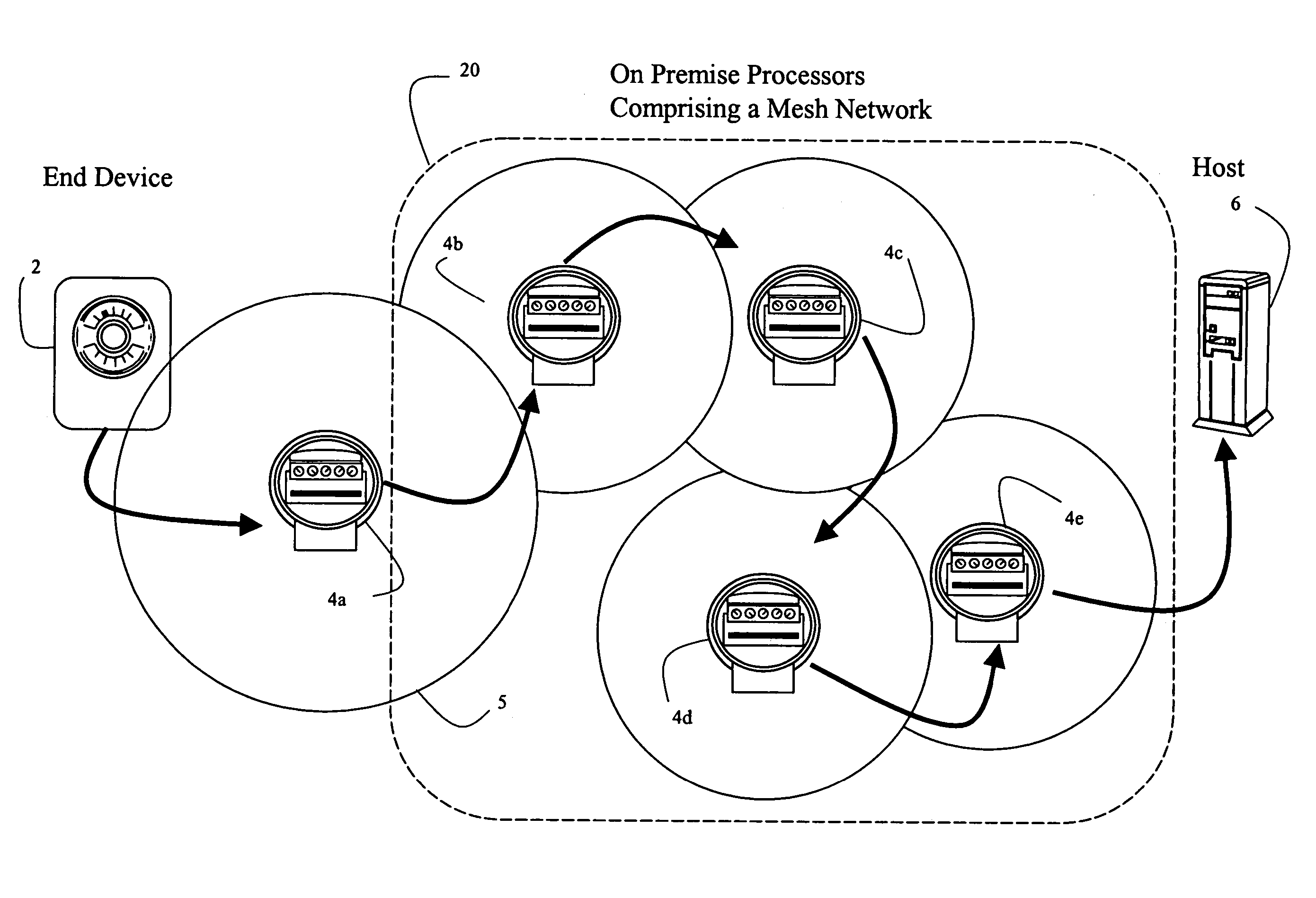
Systems and methods for remote power management using IEEE 802 based wireless communication links
InactiveUS7289887B2Reduce power consumptionLow costLevel controlData switching by path configurationTelecommunications linkTerminal equipment
Systems and methods are disclosed for using 802.11 based wireless protocols in various energy management applications wherein a host controller uses various types of communication networks to distribute information to an on-premise processor that in turn uses 802.11 based wireless protocols to communicate with various types of end devices, such as utility meters. Various forms of communication are defined between the end device, the on-premise processor, and the energy management host for accomplishing power load control, including determining when to activate or deactivate a load, requesting permission to activate a load, reading usage data, activating or deactivating a meter, and determining rate schedules. A flexible scheme allows control to be shifted to be resident in various entities. The architecture is applicable not only for power load control, but other control type and metering devices.
Owner:ITRON +1
System and method for securing mesh access points in a wireless mesh network, including rapid roaming
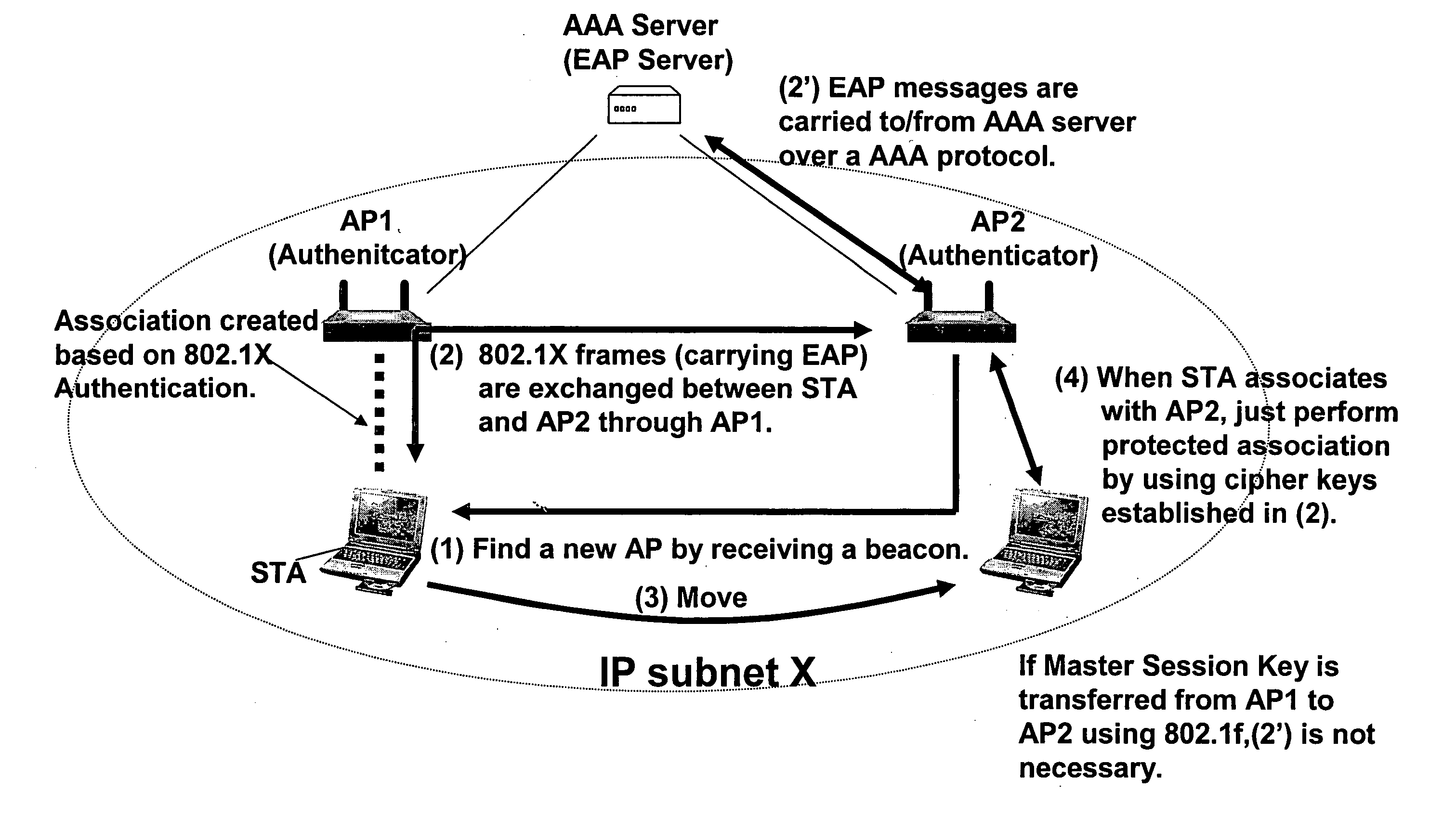
ActiveUS20070206537A1Fast rebuildFast roamingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRoamingWireless mesh network
An authentication method in a mesh AP including using standard IEEE 802.11i mechanisms between the mesh AP and an authenticator for authenticating the mesh AP to become a child mesh AP with a secure layer-2 link to a first parent mesh AP that has a secure tunnel to a Controller, including, after a layer-2 link between the child mesh AP and the first parent mesh AP is secured, undergoing a join exchange for form a secure tunnel between the child mesh AP and the Controller. Further, a fast roaming method for re-establishing a secure layer-2 link with a new parent mesh AP including, while the mesh AP is a child mesh AP to the first parent mesh AP and has a secure layer-2 link to the first parent mesh AP, caching key information and wireless mesh network identity information, and using the cached information to establish a secure layer-2 link with a new parent mesh AP without having to undergo a 4-way authentication. Further, while the mesh AP is a child mesh AP to the first parent mesh AP, has a secure layer-2 link to the first parent mesh AP, and has a secure tunnel to the Controller, caching session information on the secure tunnel, and using the cached information to re-establish the secure tunnel with the Controller, the secure tunnel now via the new mesh AP.
Owner:CISCO TECH INC
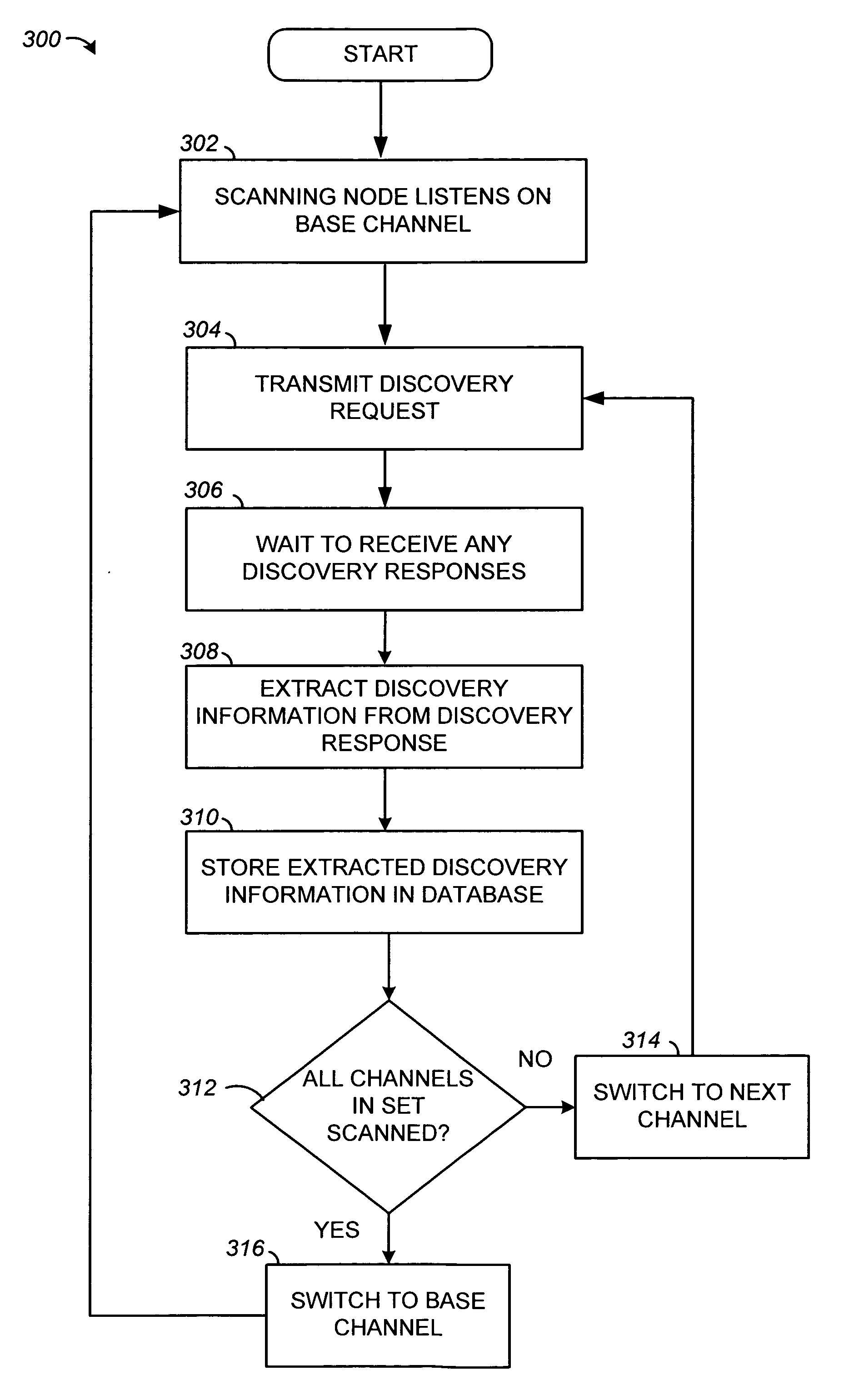
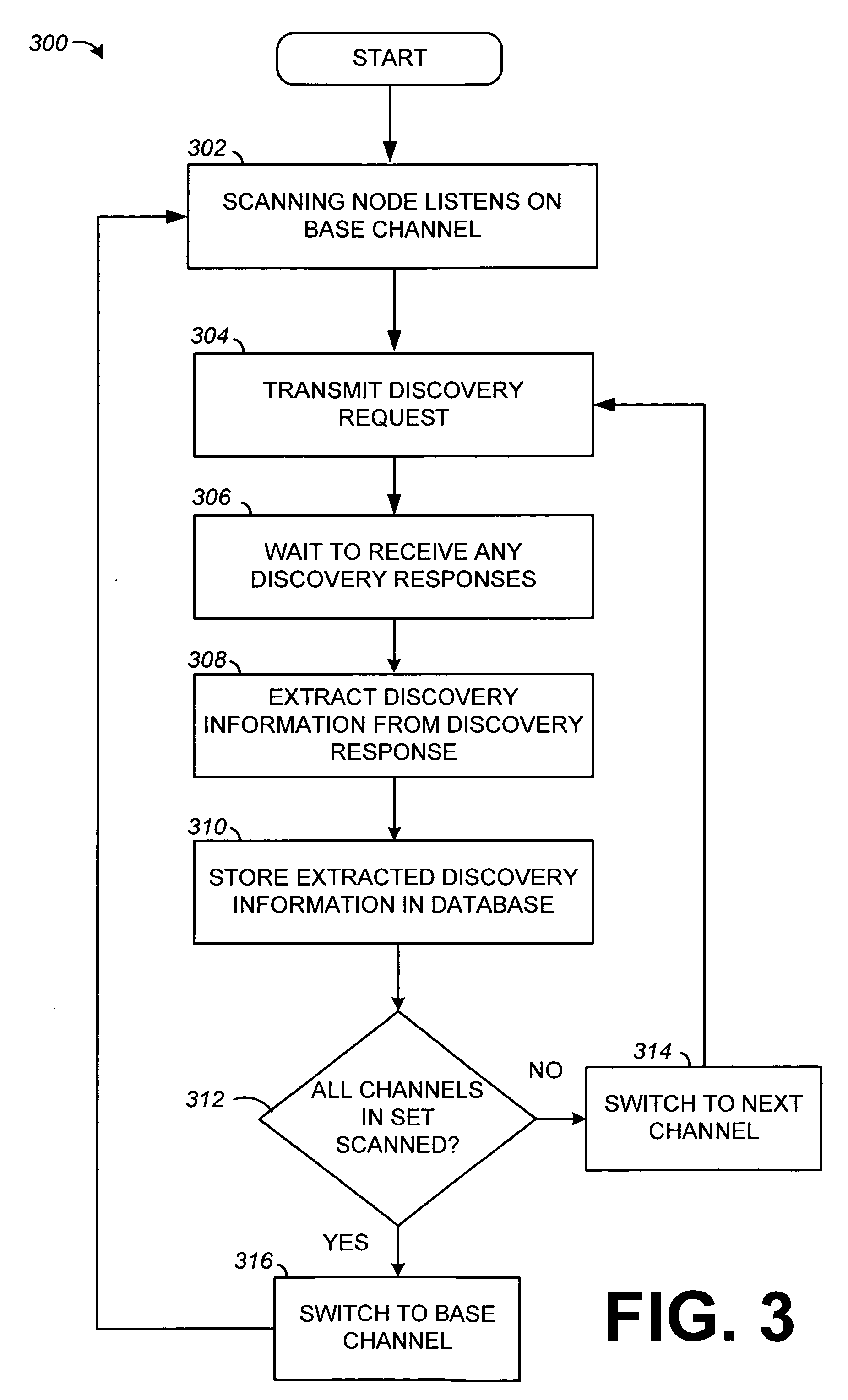
Systems and methods for device discovery
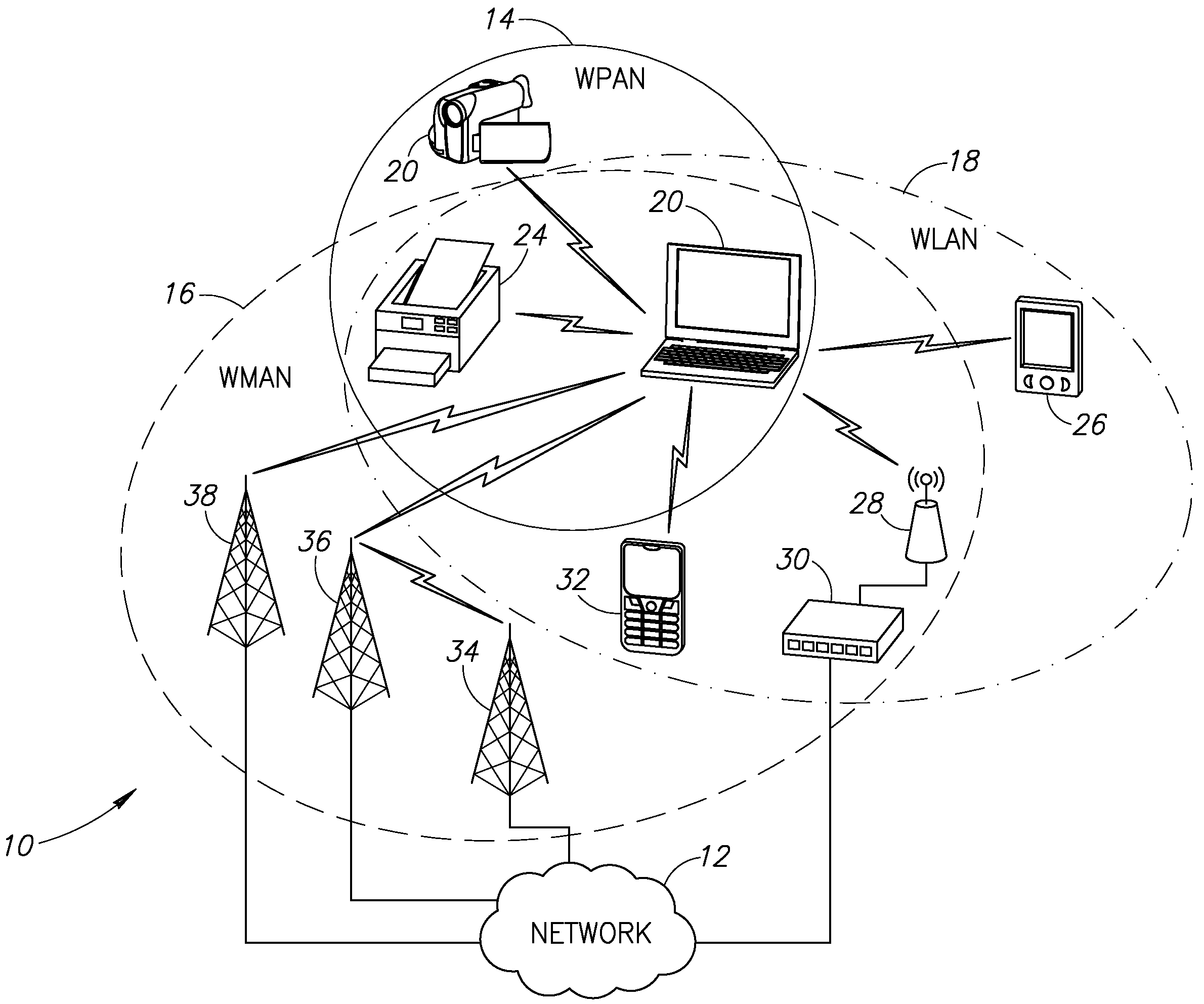
Systems and methods for enabling wireless devices to discover a number of other proximate wireless devices are disclosed. The discovery may include the discovery of network configuration parameters useful for establishing a connection between the wireless devices. The disclosed systems and methods for device discovery may operate in a number of different modes to timely discover wireless devices that receive communications continuously, as well as wireless devices that turn off their wireless receivers for intermittent periods of time. The wireless devices may, for example, communicate using the IEEE 802.11 protocol.
Owner:INTELLECTUAL VENTURES I LLC
Mobile robotic with web server and digital radio links
InactiveUS6658325B2Programme-controlled manipulatorDigital data processing detailsWeb serviceNetwork Communication Protocols
The invention is a computerized mobile robot with an onboard internet web server, and a capability of establishing a first connection to a remote web browser on the internet for robotic control purposes, and a capability of establishing a second short range bi-directional digital radio connection to one or more nearby computerized digital radio equipped devices external to the robot. The short-range bi-directional digital radio connection will typically have a maximum range of about 300 feet. In a preferred embodiment, this short-range wireless digital connection will use the 2.4 gHz band and digital protocols following the IEEE 802.11, 802.15, or other digital communications protocol. By employing the proper set of external short-range digital radio devices capable of interfacing with the robot (such as sensors, mechanical actuators, appliances, and the like), a remote user on the internet may direct the robot to move within range of the external devices, discover their functionality, and send and receive commands and data to the external devices through the CGI interface on the robot's onboard web server.
Owner:ZWEIG STEPHEN ELIOT
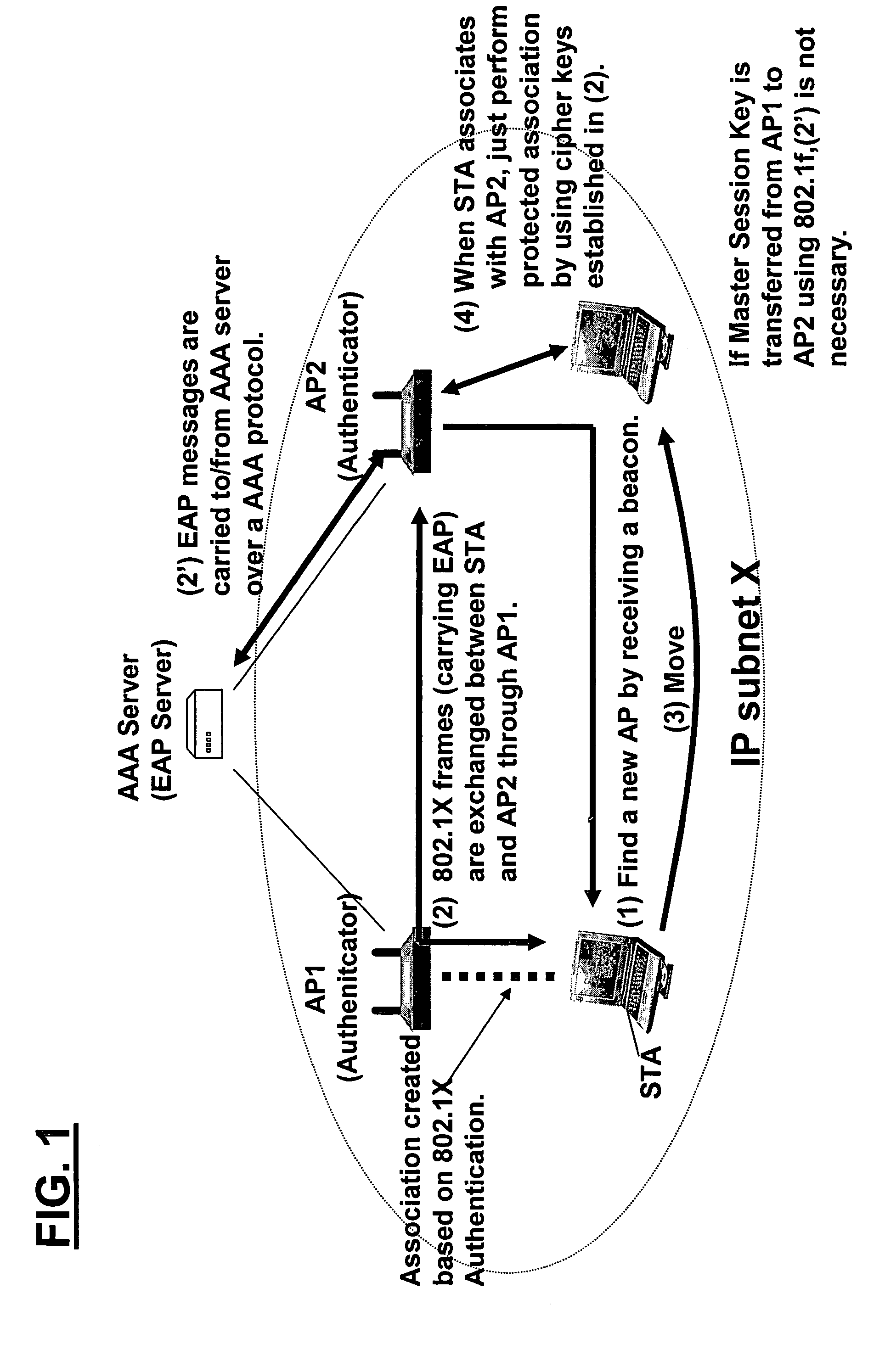
Mobility architecture using pre-authentication, pre-configuration and/or virtual soft-handoff
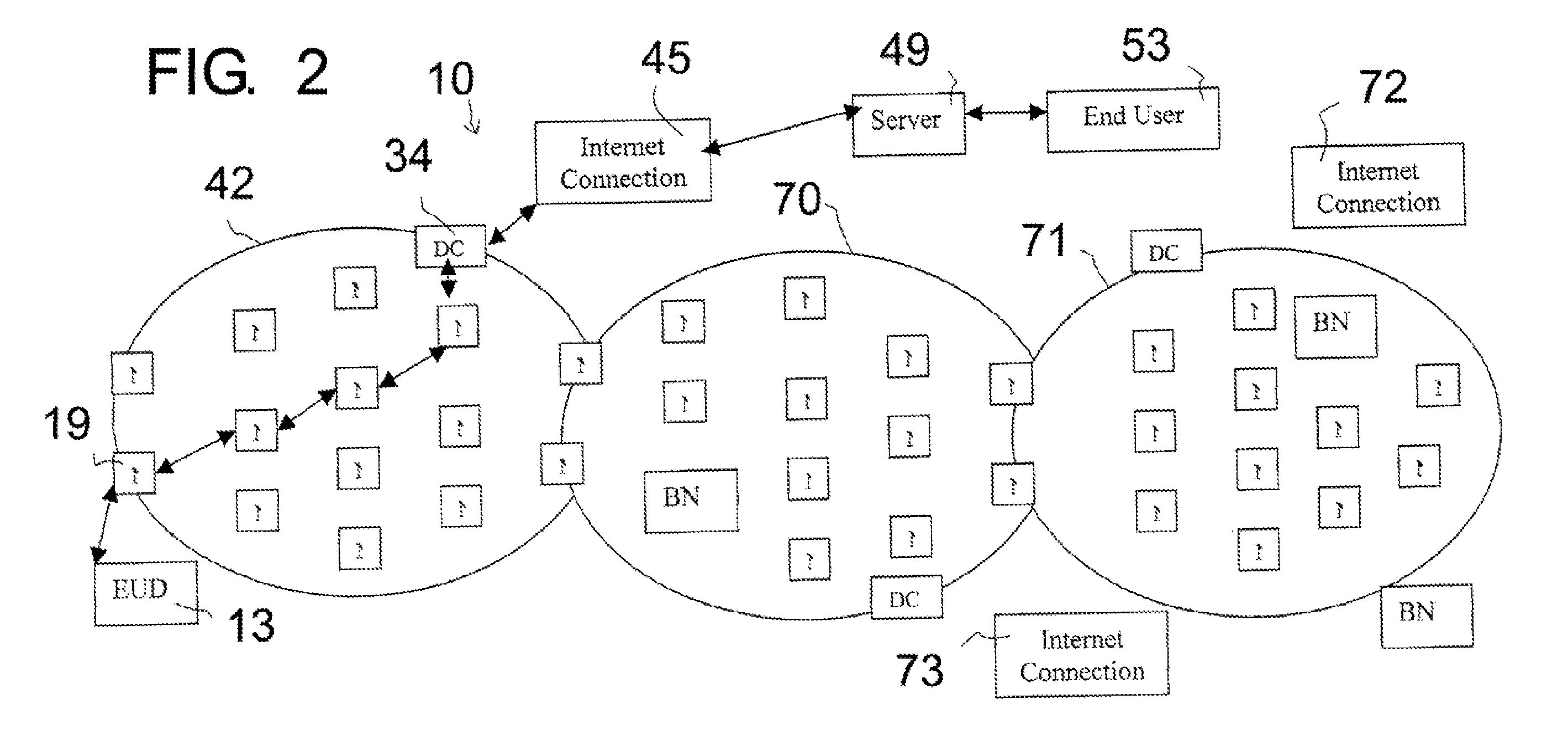
ActiveUS20050163078A1Higher-layer handoffMinimizing interruptionData switching by path configurationWireless network protocolsMobile architectureDistributed computing
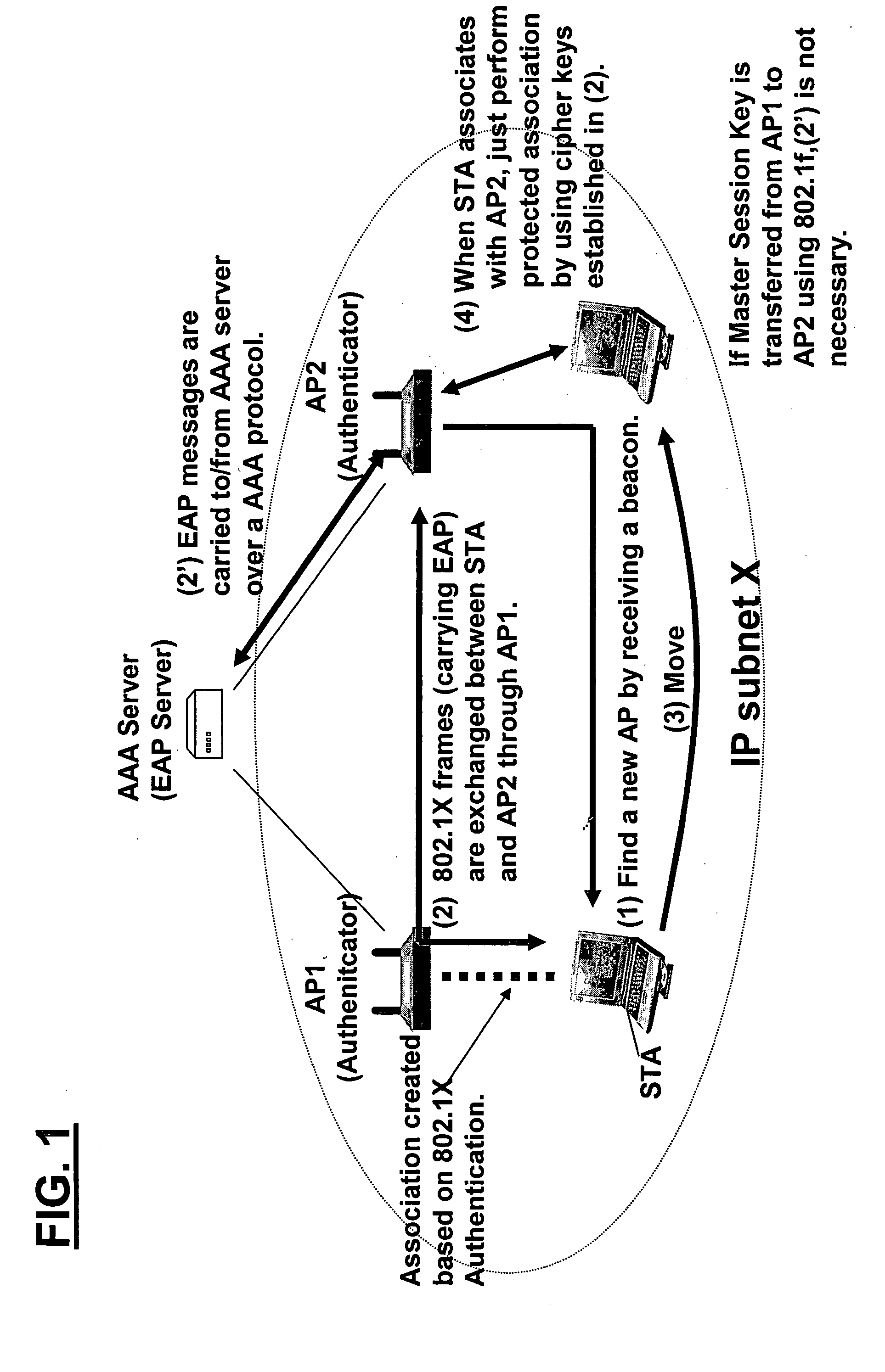
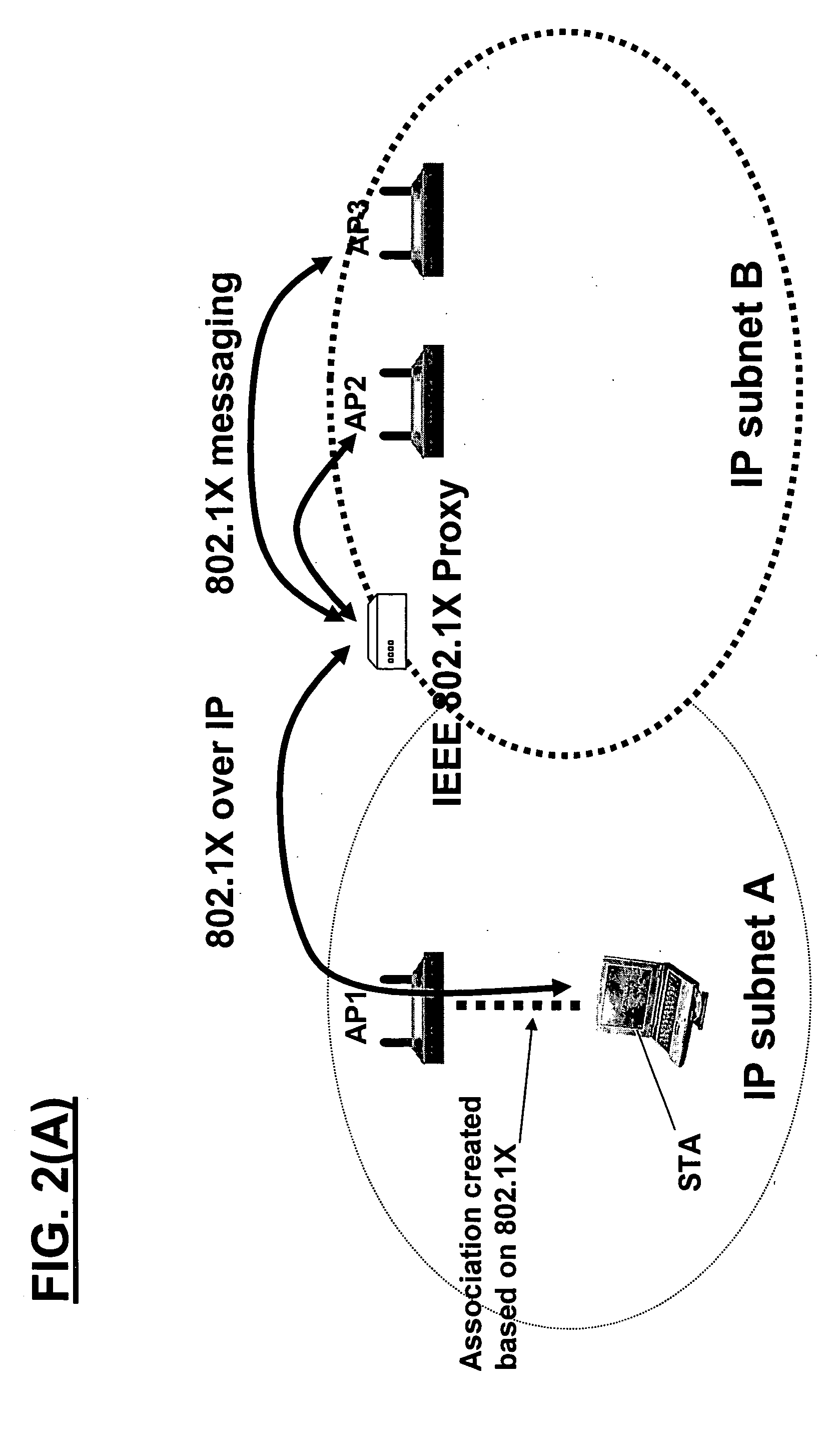
In some illustrative embodiments, a novel system and method is provided that can, for example, extend concepts of pre-authentication (such as, e.g., IEEE 802.11i pre-authentication) so as to operate across networks or subnetworks (such as, e.g., IP subnets). In preferred embodiments, a novel architecture includes one or both of two new mechanisms that substantially improve, e.g., higher-layer handoff performance. A first mechanism is referred to as “pre-configuration,” which allows a mobile to pre-configure higher-layer information effective in candidate IP subnets to handoff. A second mechanism is referred to as “virtual soft-handoff,” which allows a mobile to send or receive packets through the candidate IP subnets even before it is actually perform a handoff to any of the candidate IP subnets.
Owner:TELCORDIA TECHNOLOGIES INC +1
RFID device, system and method of operation including a hybrid backscatter-based RFID tag protocol compatible with RFID, bluetooth and/or IEEE 802.11x infrastructure
ActiveUS7215976B2Near-field transmissionMemory record carrier reading problemsTransceiverAntenna impedance
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
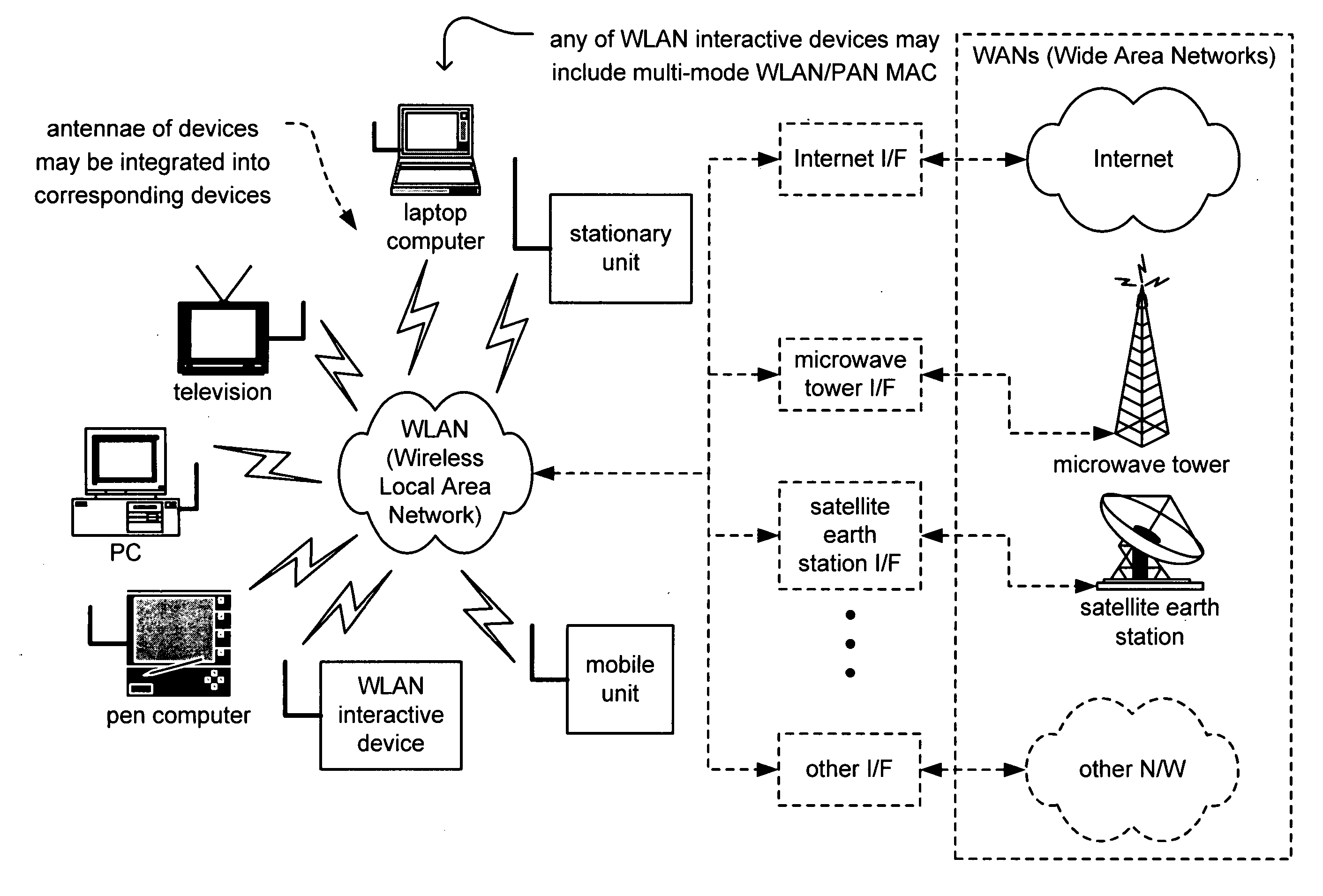
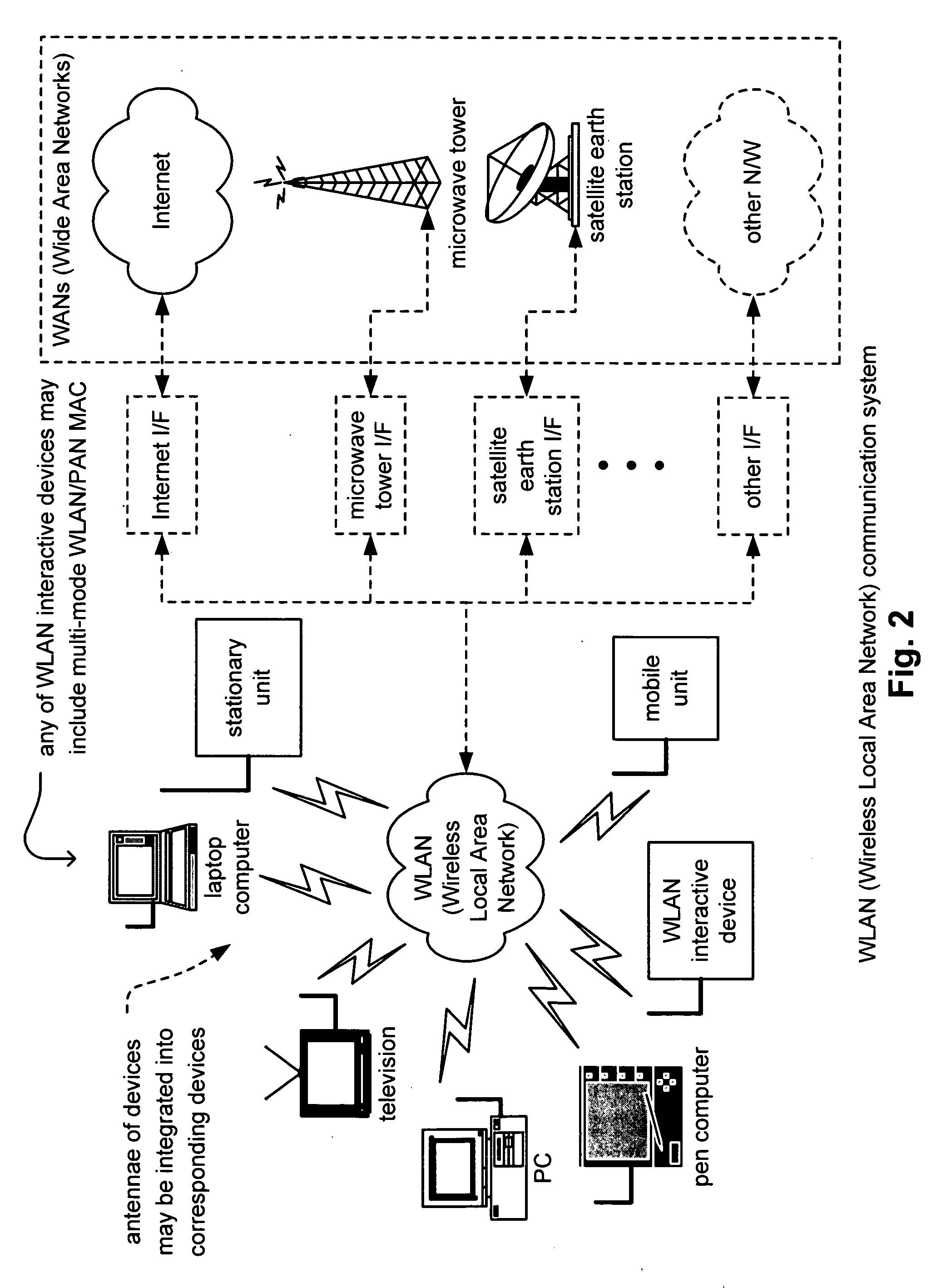
Multi-mode WLAN/PAN MAC
ActiveUS20050147071A1Network topologiesData switching by path configurationCommunications systemWireless lan
Multi-mode WLAN / PAN MAC. A novel solution is presented in which a MAC (Medium Access Controller) is implemented that includes multiple functionality types. This MAC may include functionality supporting communication according to one or more of the IEEE 802.11 WLAN (Wireless Local Area Network) related standards and also to one or more of the standards generated by the IEEE 802.15.3 PAN (Personal Area Network) working group. By providing this dual functionality of a multi-mode WLAN / PAN MAC, a communication device may adaptively change the manner in which it communicates with other communication devices. For example, in an effort to maximize throughput and overall efficiency of communication within a communication system, certain of the various devices may change from using the WLAN related standards to using the PAN related standards, and vice versa, based on any one or more of a variety of operational parameters including system configuration.
Owner:AVAGO TECH INT SALES PTE LTD
Methods and systems for a wireless routing architecture and protocol
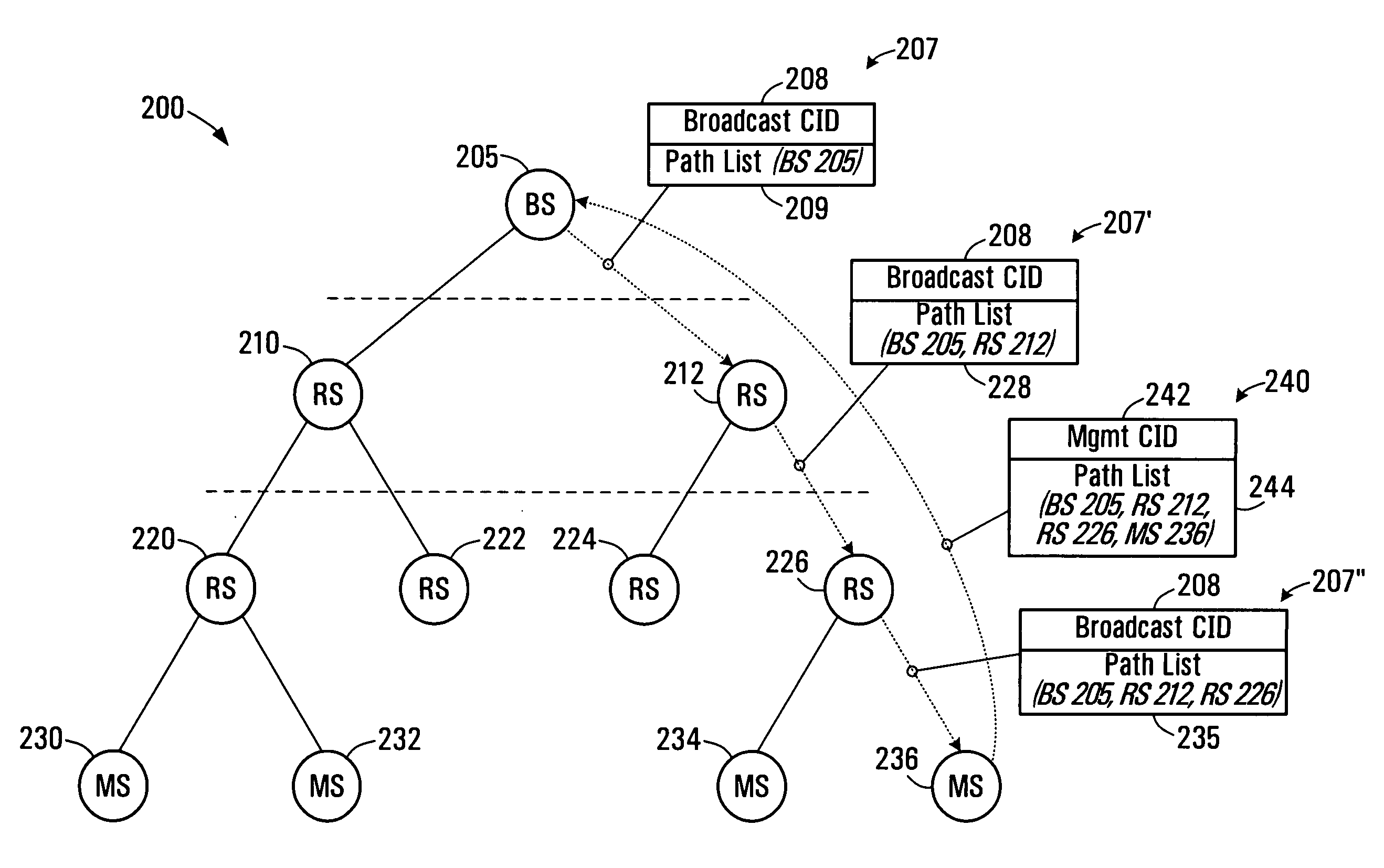
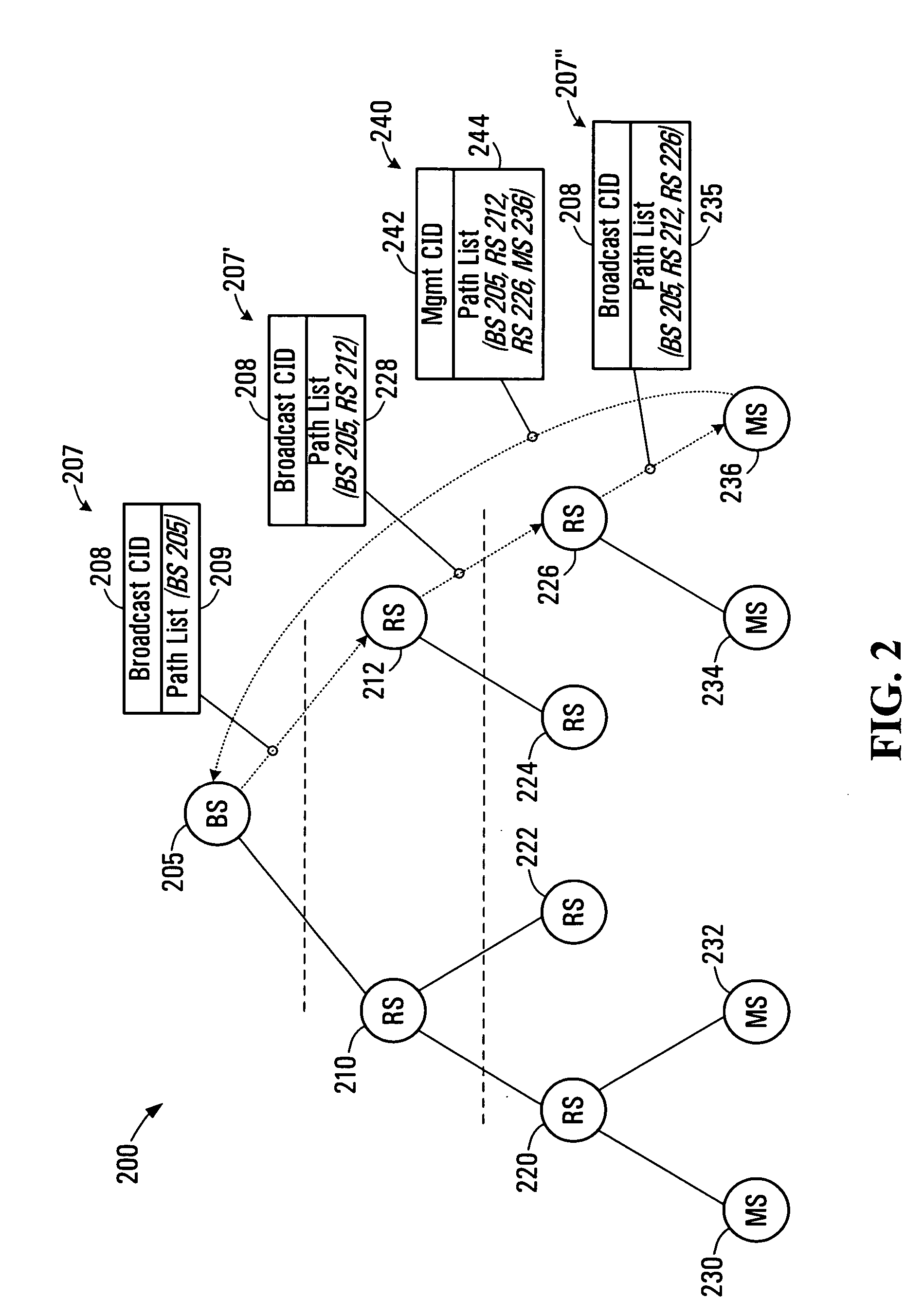
ActiveUS20070097945A1Short pathTime-division multiplexData switching by path configurationMobile stationIEEE 802
The present invention provides a method for generating routing paths in a multi-hop network. The multi-hop network includes a base station, at least one relay station, and at least one non-relay mobile station. The routing paths are paths between the base station and the at least one non-relay mobile station via the at least one relay station. The base station broadcasts a path discovery message (PDM) including a path list with a starting point of the path list being the base station. Each of the relay stations receives the PDM and updates the PDM by adding their own respective node identifier to the path list and broadcasting the updated PDM. The PDMs eventually reach the non-relay mobile station. The non-relay mobile stations reply to the base station by sending the base station the updated path list between the base station and the non-relay mobile station. In some embodiments the base station or the at least one non-relay mobile station acting as a source node sends a dynamic service (DSx) message including an end-to-end path list to an end of path destination. The relay stations use the path list to forward the message between the source node and the end of path destination. In some implementations the multi-hop network operates in a manner that is consistent with any one of: IEEE 802.16, IEEE 802.16d, and IEEE 802.16e.
Owner:APPLE INC
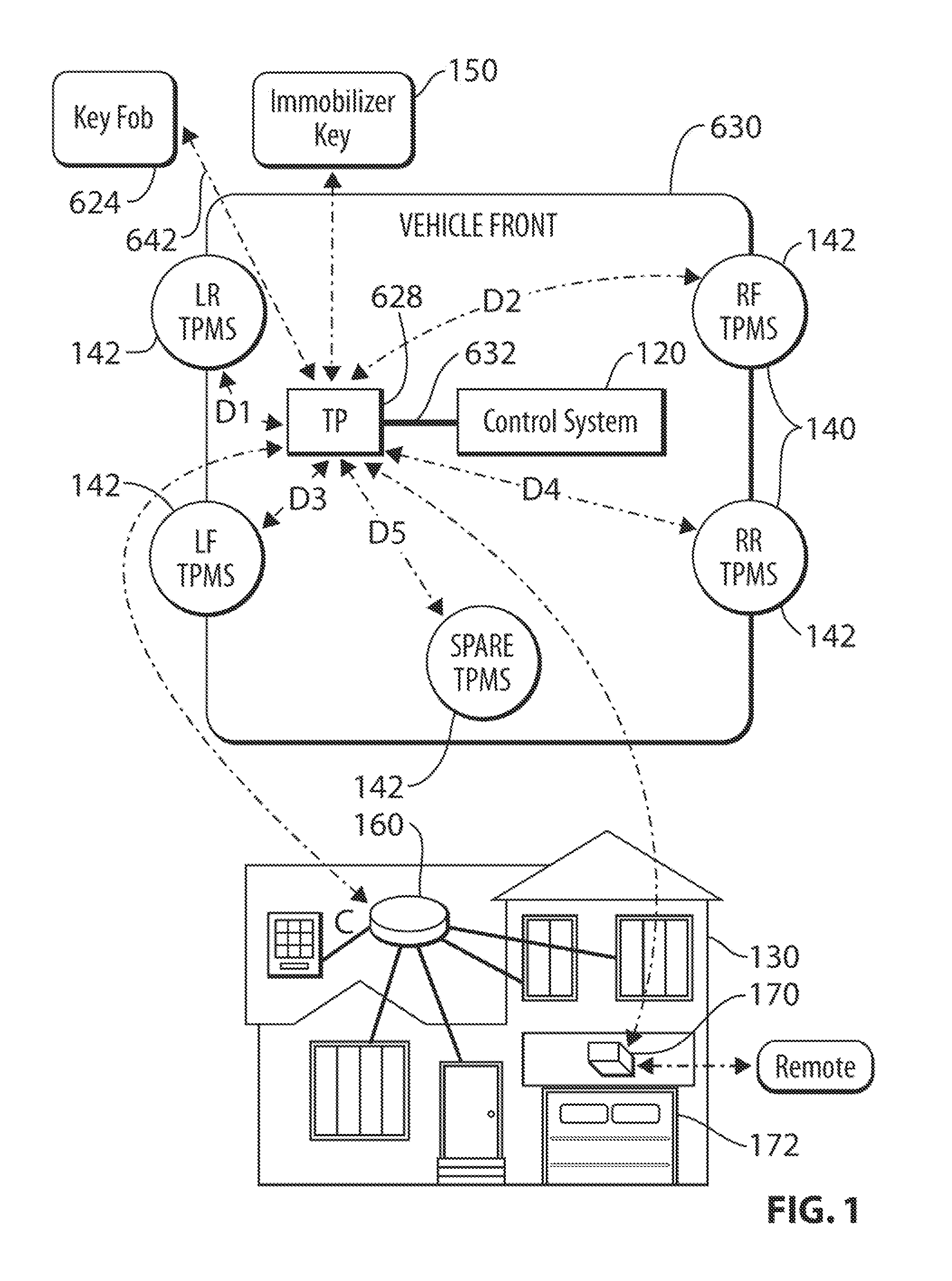
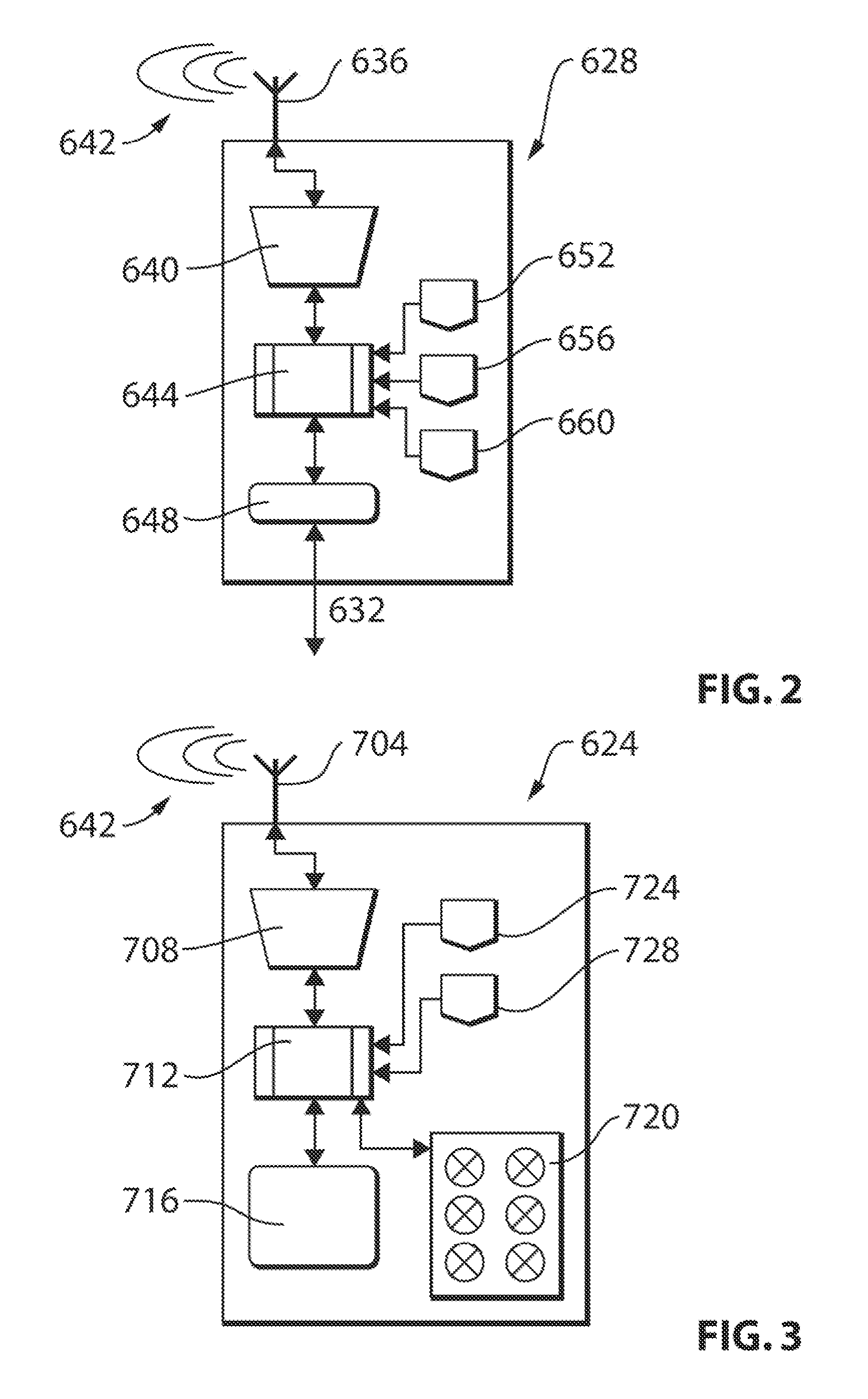
Remote vehicle control system utilizing multiple antennas
ActiveUS20100305779A1Low costDigital data processing detailsAnti-theft devicesTransceiverDriver/operator
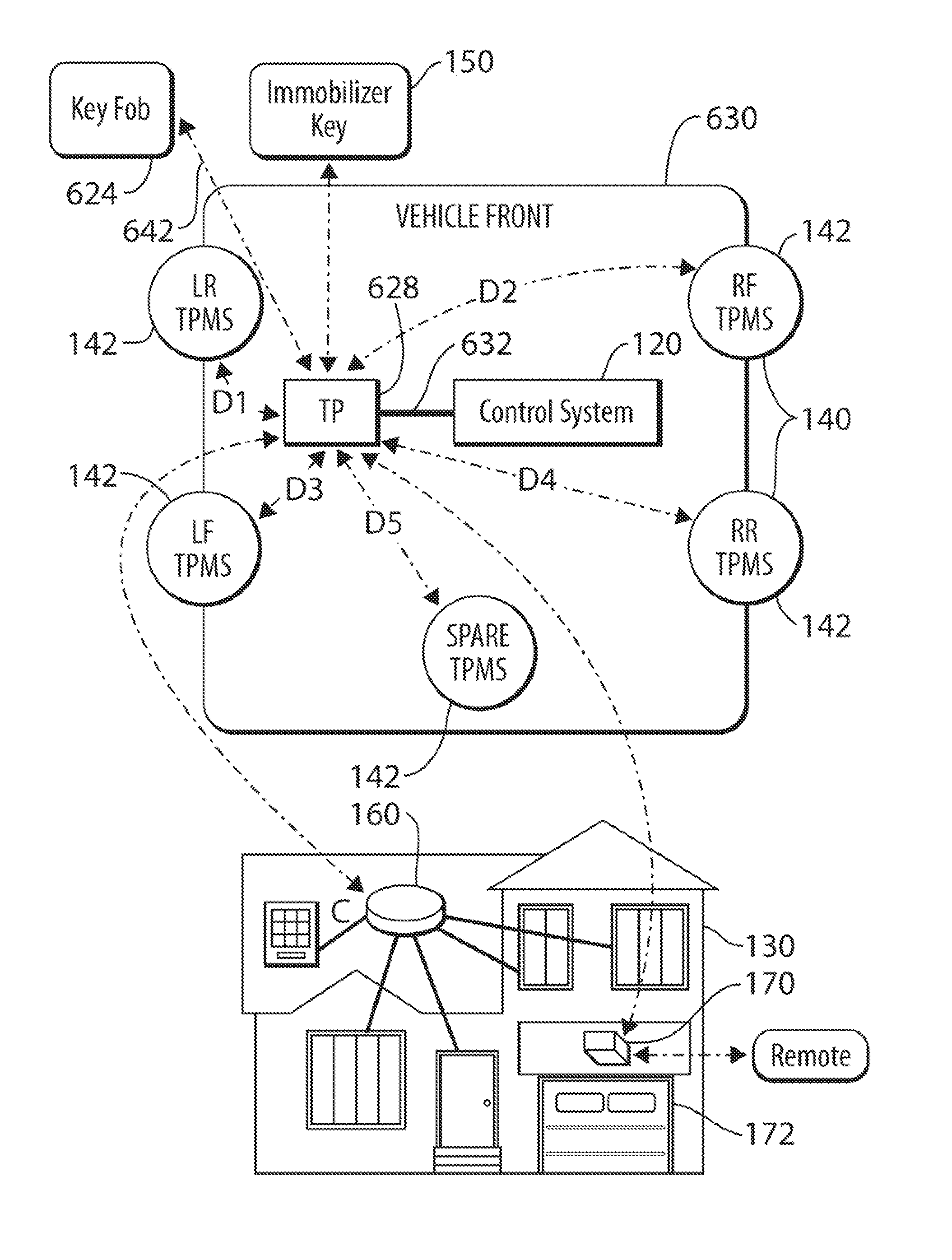
A remote vehicle control system having a base transceiver mounted in a vehicle and a mobile key fob. The base transceiver utilizes an omni-directional antenna to communicate wirelessly with the key fob via the IEEE 802.15.4 communication protocol. Additional antennas are mounted to the vehicle and are also tuned to communicate over the IEEE 802.15.4 bandwidth. The additional antennas have radiation patterns extending outwardly to various sides of the vehicle (e.g., driver, passenger and rear sides). The system provides remote control functions and enables passive keyless entry functions such as unlocking doors or trunk latches by detecting the presence of the key fob proximate to one or more sides of the vehicle based on the ability of the key fob to communicate over IEEE 802.15.4 via the additional antennas.
Owner:MAGNA ELECTRONICS
Mobile robotic with web server and digital radio links
InactiveUS20020173877A1Programme controlProgramme-controlled manipulatorWeb serviceNetwork Communication Protocols
The invention is a computerized mobile robot with an onboard internet web server, and a capability of establishing a first connection to a remote web browser on the internet for robotic control purposes, and a capability of establishing a second short range bi-directional digital radio connection to one or more nearby computerized digital radio equipped devices external to the robot. The short-range bi-directional digital radio connection will typically have a maximum range of about 300 feet. In a preferred embodiment, this short-range wireless digital connection will use the 2.4 gHz band and digital protocols following the IEEE 802.11, 802.15, or other digital communications protocol. By employing the proper set of external short-range digital radio devices capable of interfacing with the robot (such as sensors, mechanical actuators, appliances, and the like), a remote user on the internet may direct the robot to move within range of the external devices, discover their functionality, and send and receive commands and data to the external devices through the CGI interface on the robot's onboard web server.
Owner:ZWEIG STEPHEN ELIOT
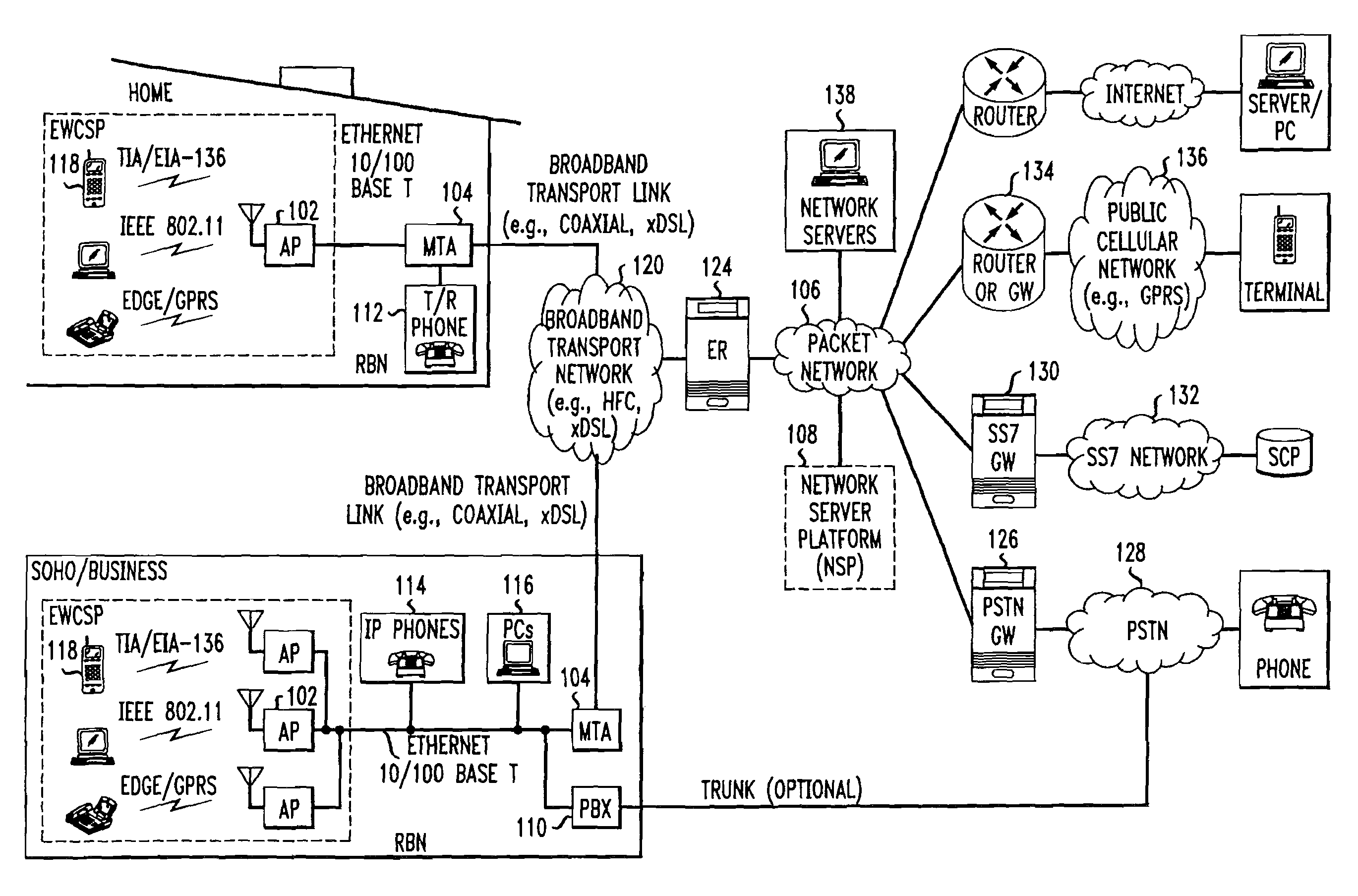
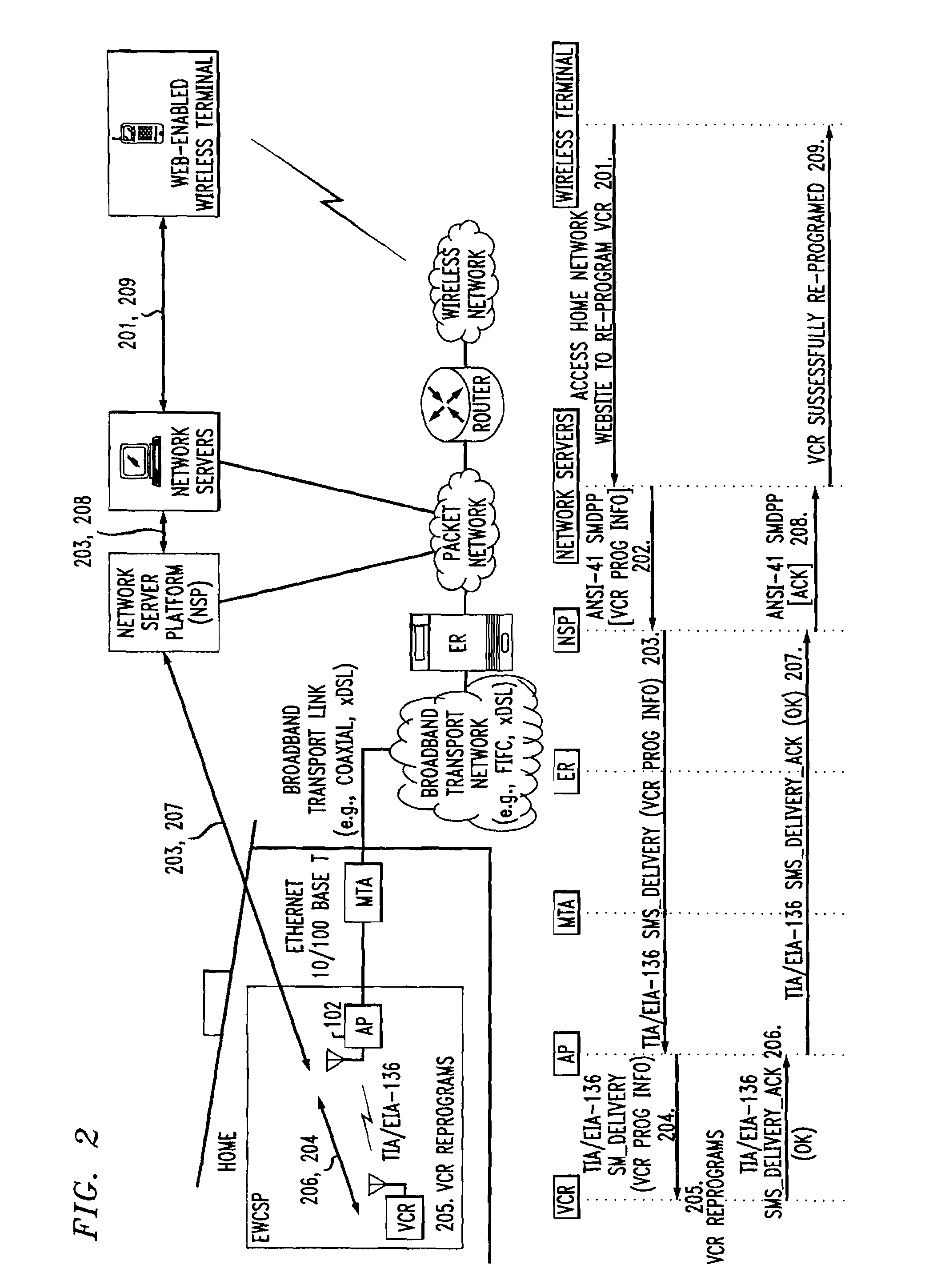
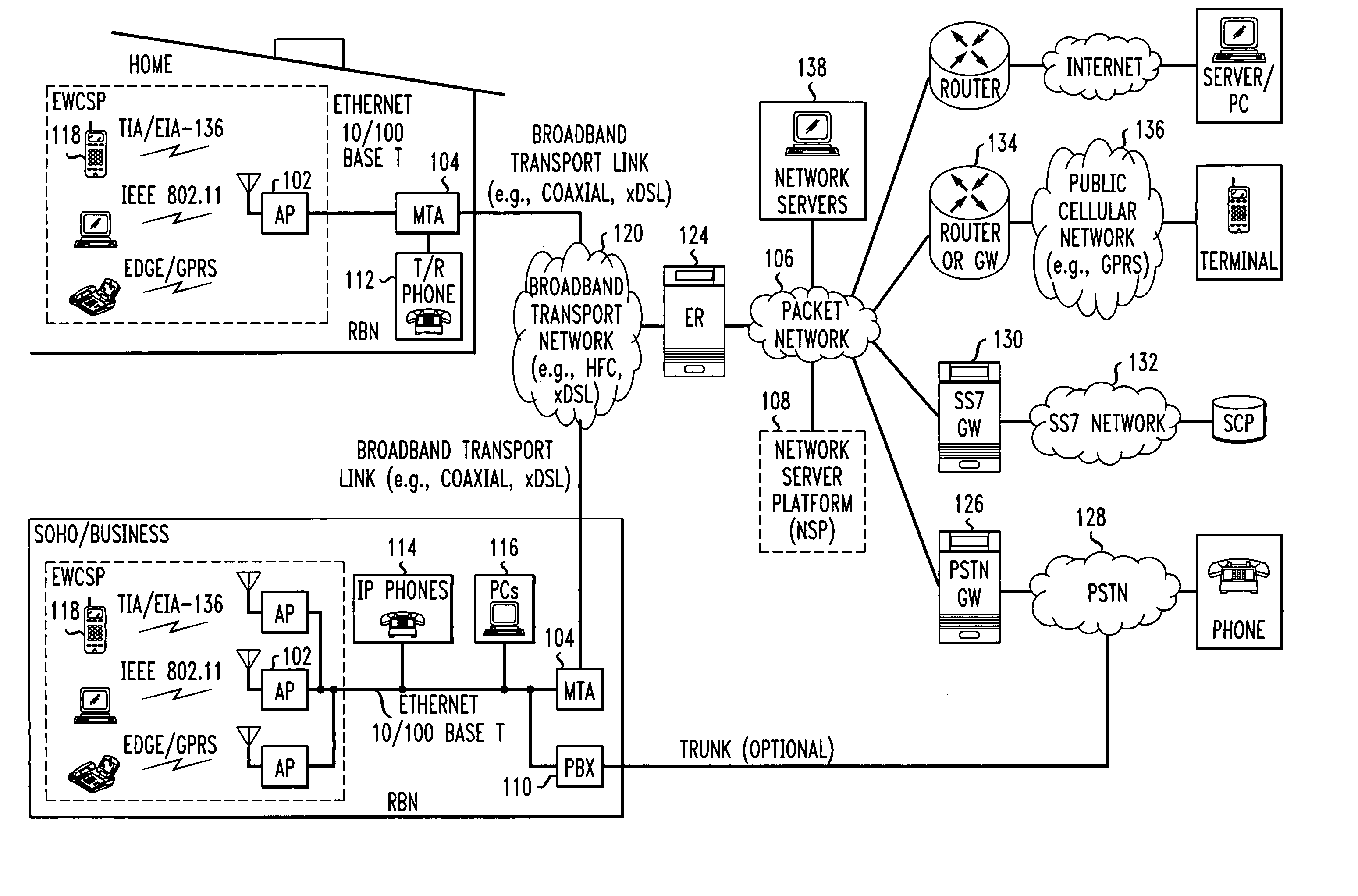
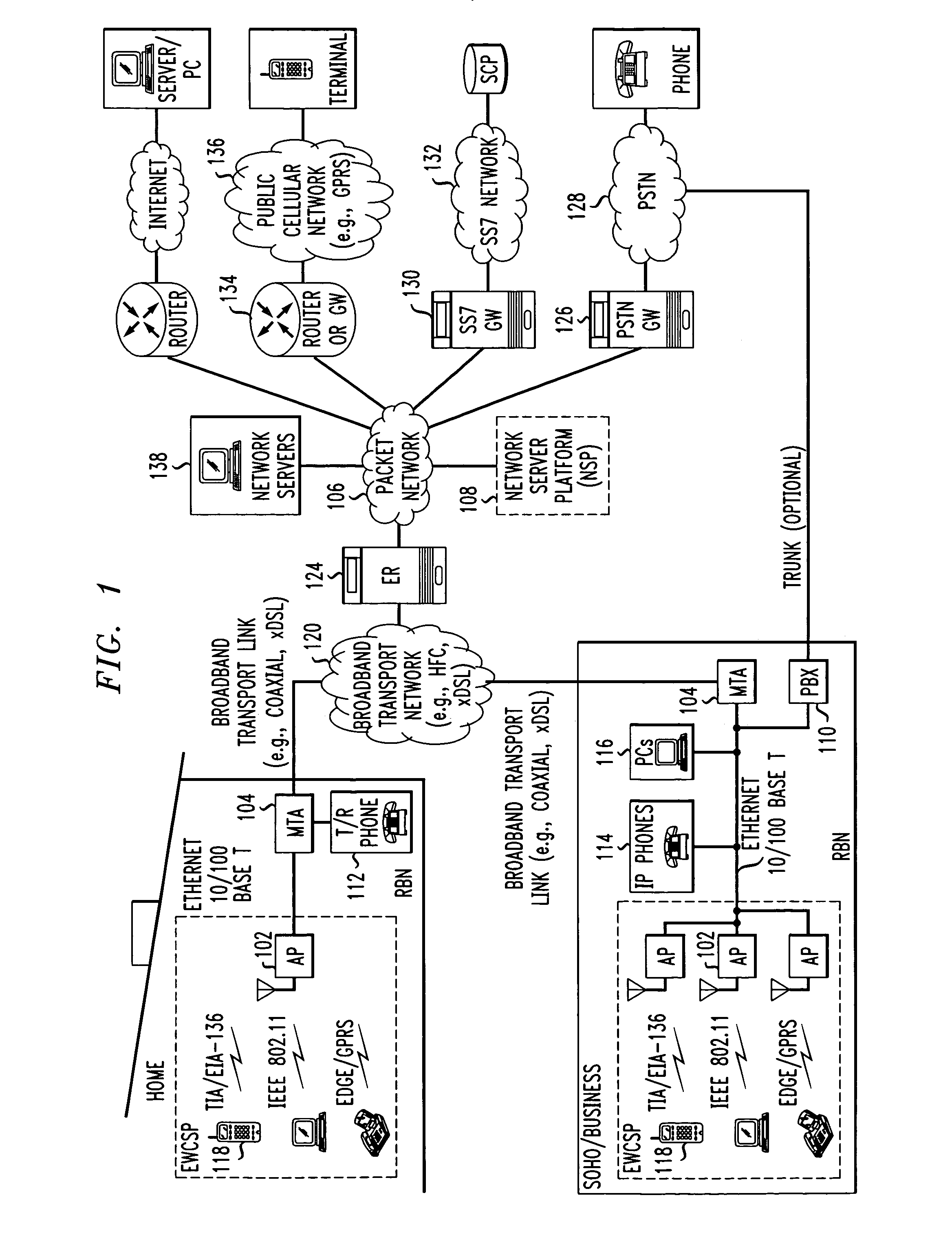
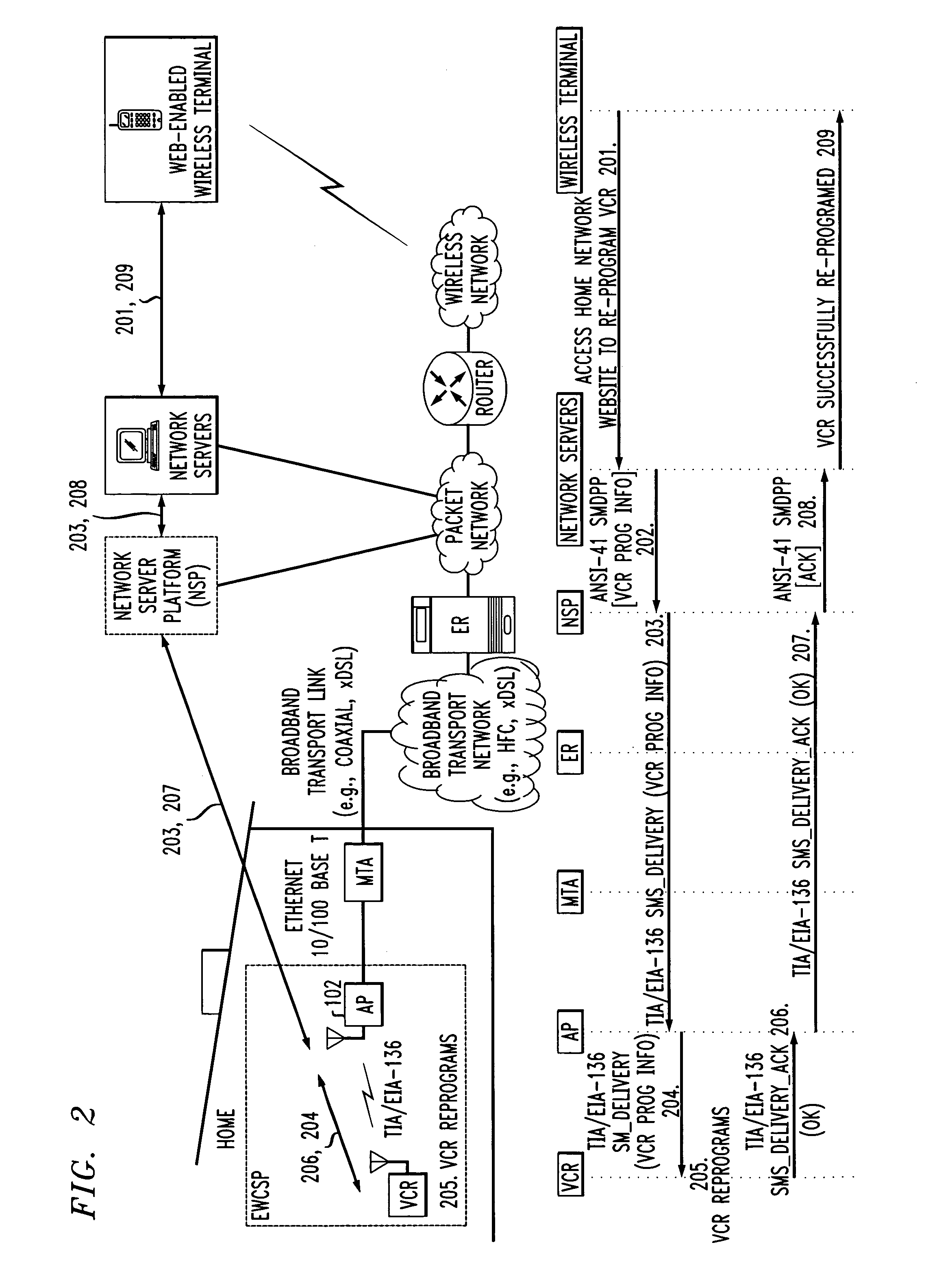
Computer readable medium with embedded instructions for providing communication services between a broadband network and an enterprise wireless communication platform within a residential or business environment
InactiveUS8155155B1Easy maintenanceCost-effectivelyError preventionFrequency-division multiplex detailsModem deviceBroadband transmission
The present invention sets forth computer-readable non-transitory medium having computer-executable instructions for providing network-centric service distribution method that integrates a wireless access system / service with conventional telecommunications services in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN). The RBN communicates with the service provider's broadband transport network and broadband packet network to facilitate end-to-end packet telecommunication services. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data.
Owner:AT & T INTPROP II LP
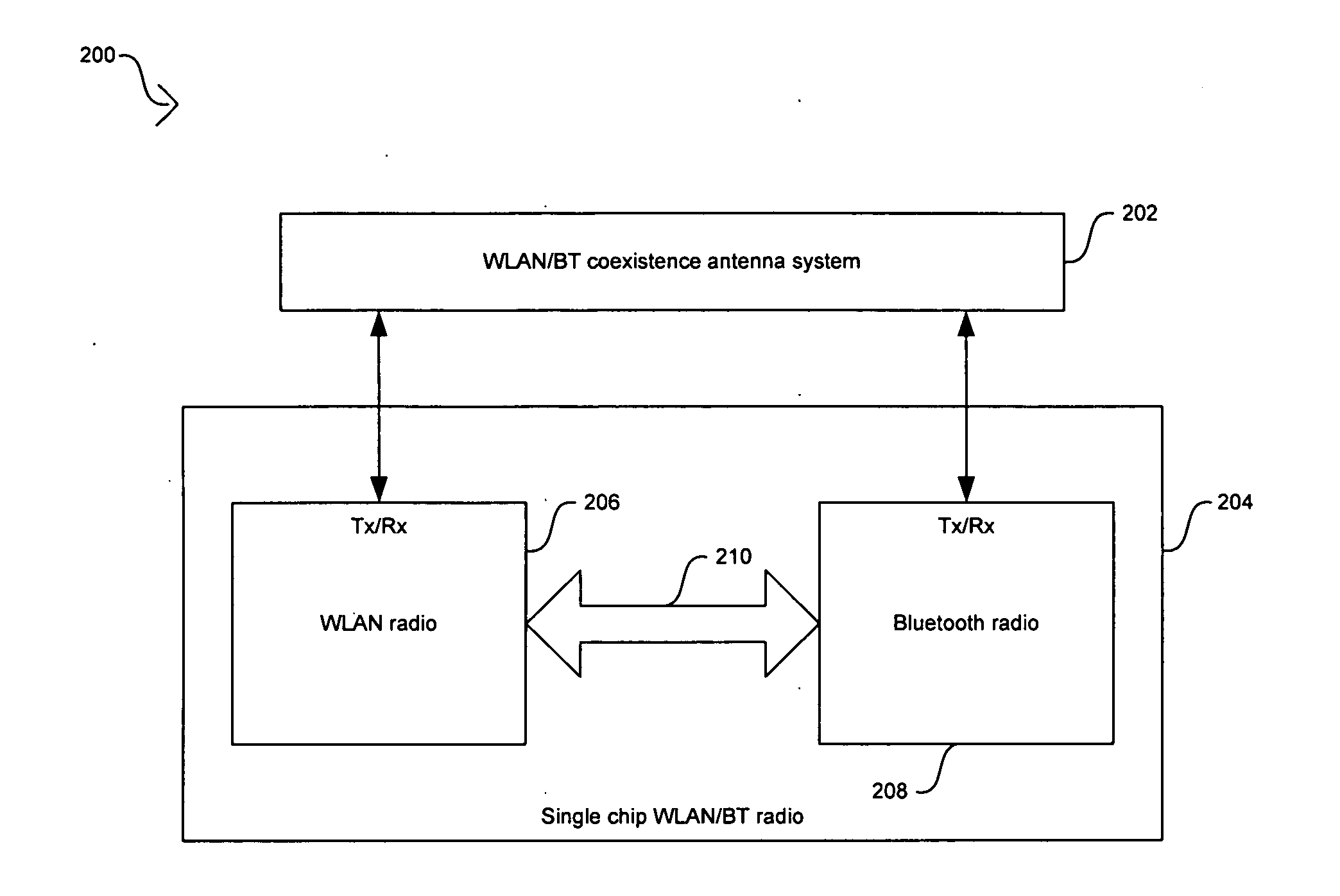
Method and system for antenna and radio front-end topologies for a system-on-a-chip (SOC) device that combines bluetooth and IEEE 802.11 b/g WLAN technologies
Certain embodiments of the invention may be found in a method and system for antenna and radio front-end topologies for a system-on-a-chip (SOC) device that combines Bluetooth and IEEE 802.11 b / g WLAN technologies. A single chip radio device that supports WLAN and Bluetooth technologies receives a WLAN signal in a WLAN processing circuitry of the radio front-end and in a Bluetooth processing circuitry of the radio front-end. Signals generated by the WLAN processing circuitry and the Bluetooth processing circuitry from the received WLAN signal may be combined in a diversity combiner that utilizes selection diversity gain combining or maximal ratio combining (MRC). When a generated signal is below a threshold value, the signal may be dropped from the combining operation. A single antenna usage model may be utilized with the single chip radio device front-end topology to support WLAN and Bluetooth communications.
Owner:AVAGO TECH INT SALES PTE LTD
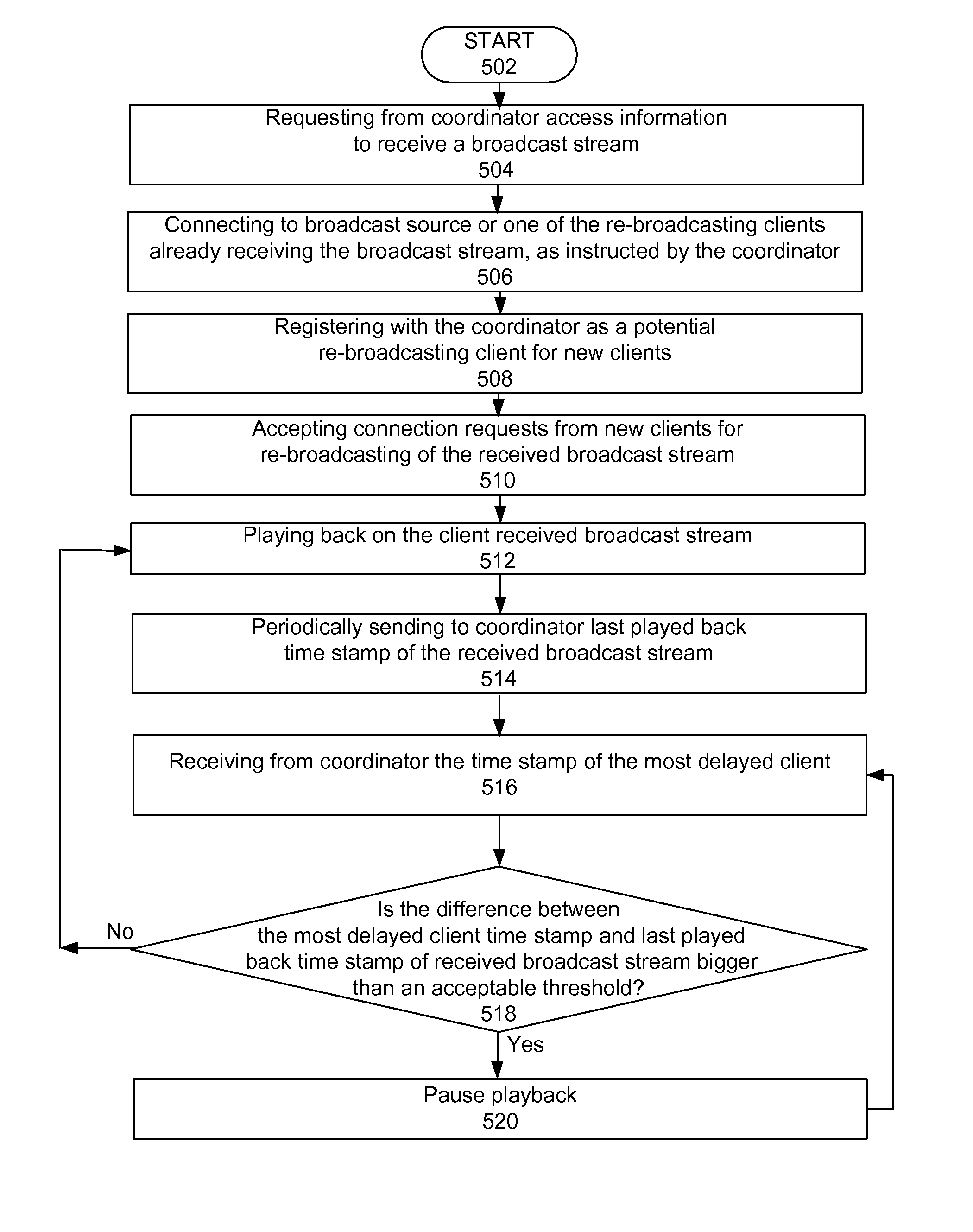
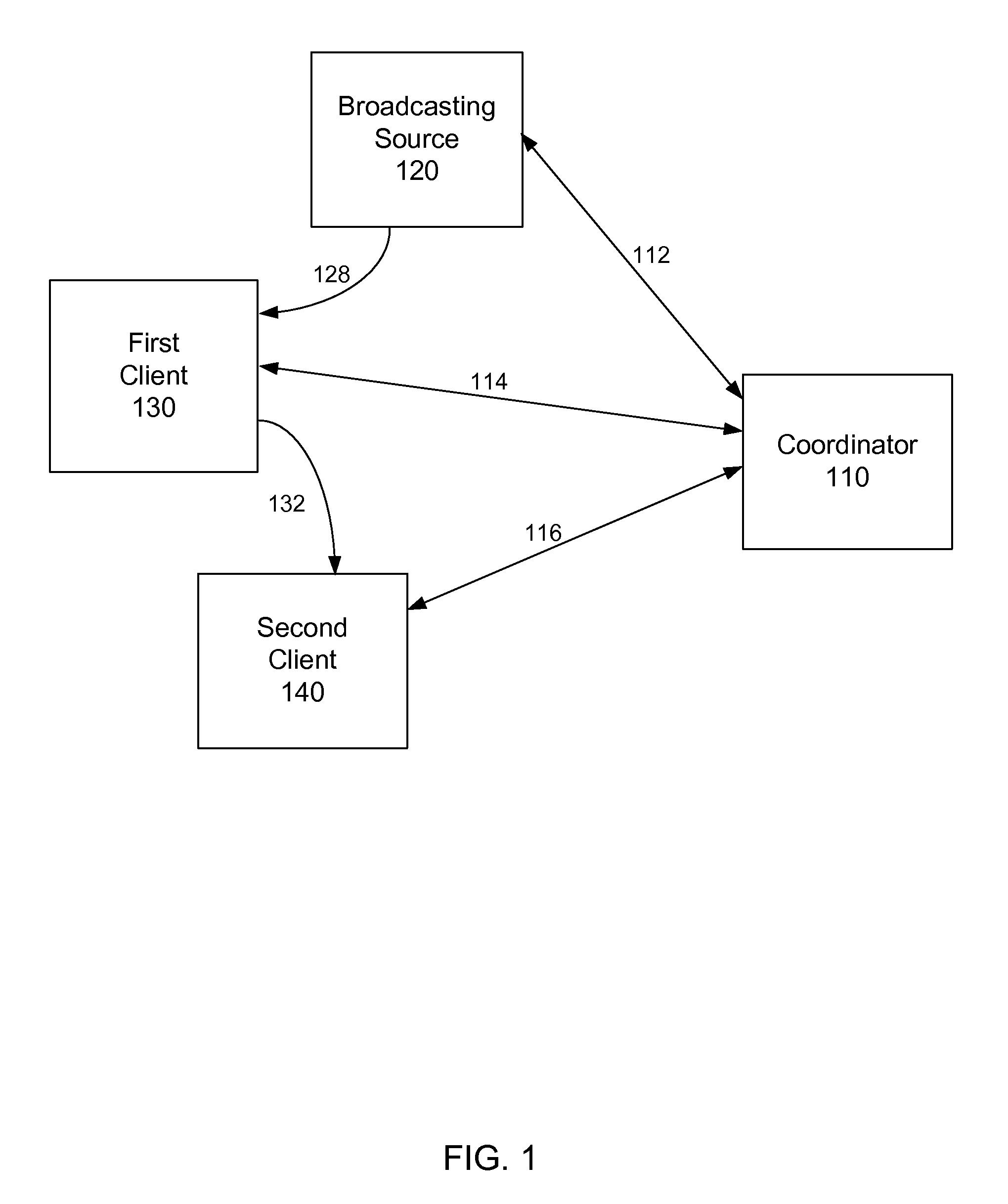
Method and system to daisy-chain access to video resources
InactiveUS7934239B1Two-way working systemsSelective content distributionTelecommunications linkTelecommunications
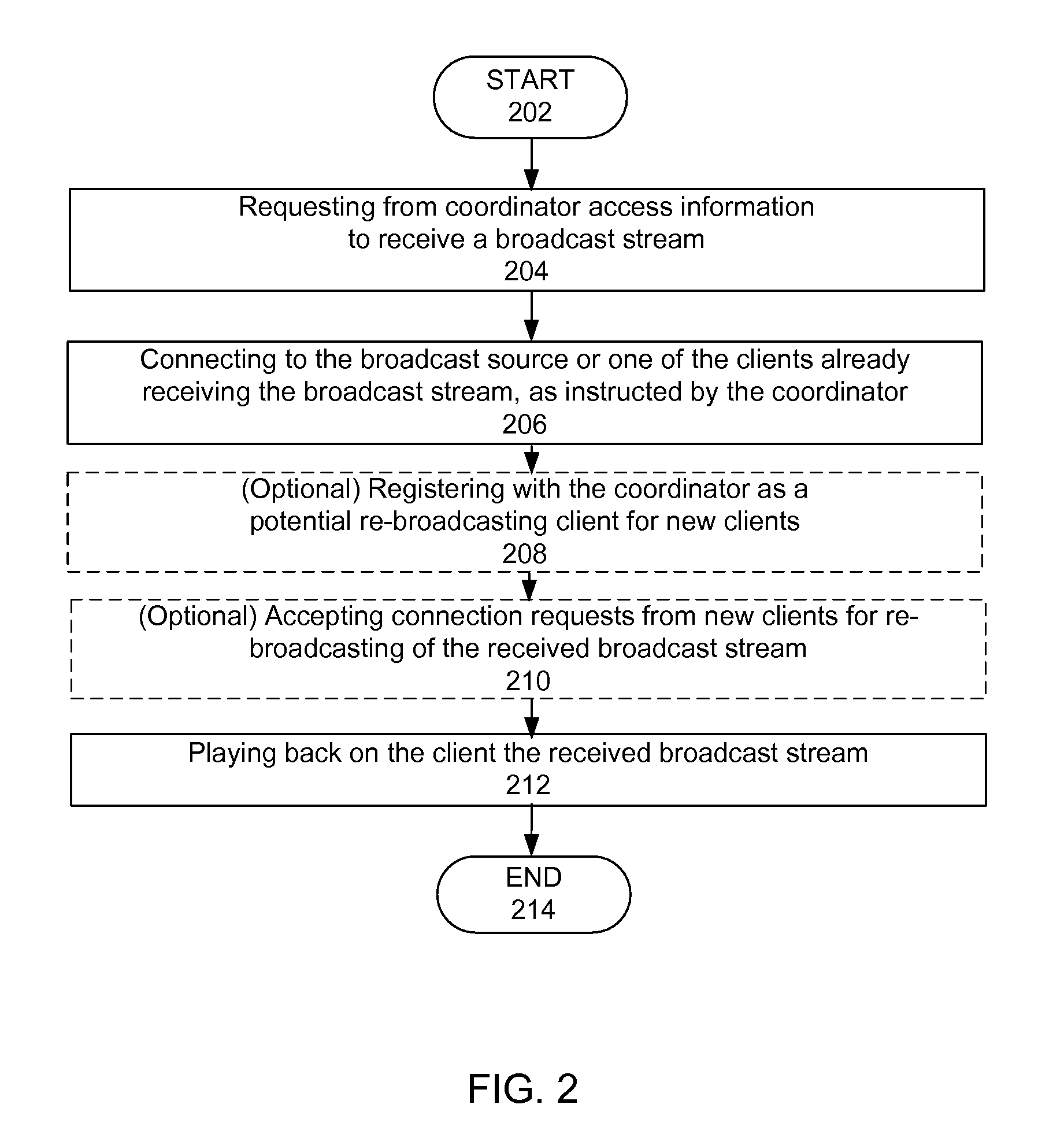
A method and system to control at least one video resource daisy-chain access system. A first embodiment is a method to operate a video resource daisy-chain access system. The method includes requesting from a coordinator access instructions to receive a broadcast stream from a broadcast source; connecting to the broadcast source, or one of the re-broadcasting clients already receiving the broadcast stream, as instructed by the coordinator; optionally registering with the coordinator as a potential re-broadcasting source for new clients; optionally accepting connection requests from new clients for re-broadcasting of the received broadcast stream; and playing back on the client the received broadcast stream. A second embodiment is a video resource daisy-chain access system. The system includes a coordinator; a broadcasting source having a communication link with the coordinator; a first client having a communication link with the coordinator and a communication link with the broadcasting source; and a second client having a communication link with the coordinator and a communication link with the first client. These embodiments can be applied in several wired and wireless communication applications, even combinations of wired and wireless technologies including, but not limited to, IEEE 802.16 wireless applications, and equivalent technologies.
Owner:CLYP ENGINES PTE LTD
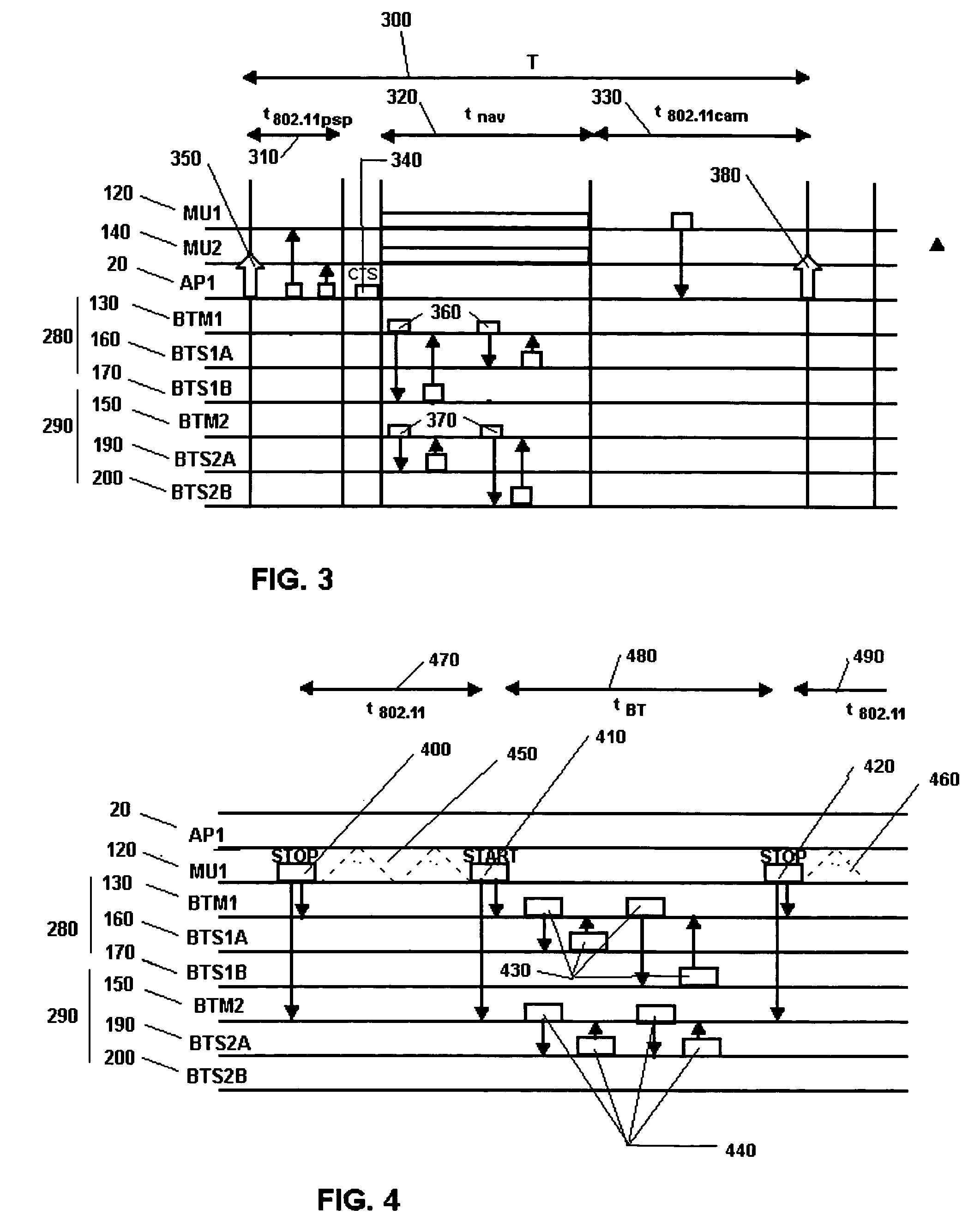
Coexistence techniques in wireless networks
InactiveUS7039358B1Communication be discontinueInterference minimizationRadio transmissionWireless commuication servicesTransceiverNetwork Communication Protocols
Techniques are provided for frequency coordination among two different wireless network protocols, such as the IEEE 802.11 and Bluetooth protocols, operating in proximity with one another. Coordination is accomplished by the use of a first radio transceiver operating in accordance with a first communication protocol (which may be the 802.11 protocol) and using a frequency band (which may be the 2.4 GHz band), a base station connected to a wired network and operating in accordance with the first communication protocol, a second radio transceiver operating in accordance with a second communication protocol (which may be the Bluetooth protocol) and using the frequency band, and a coordinator associated with the base station for, in turn, activating the first radio transceiver, deactivating the first radio transceiver, activating the second radio transceiver, and deactivating the second radio transceiver.
Owner:SYMBOL TECH LLC
Broadband network with enterprise wireless communication method for residential and business environment
InactiveUS7010002B2Easy to optimizeCost-effective deploymentMultiplex system selection arrangementsTelephone data network interconnectionsModem deviceBroadband transmission
The present invention sets forth a network-centric service distribution architecture and method that integrates a wireless access system / service in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN), to the service provider's broadband transport network and to a service provider's broadband packet network that facilitates end-to-end packet telecommunication services. Access functions for connecting said service provider's broadband packet network to the RBN via said service provider's broadband transport network are provided. Call and service termination functions to a plurality of local RBN devices are also provided. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data. Voice signals are also accepted from a plurality of tip / ring interfaces and forwarded to a broadband transport interface for back haul of data and voice packets. A service provider can deploy services in an integrated voice, data and multimedia environment cost-effectively based on one broadband packet network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Mobility architecture using pre-authentication, pre-configuration and/or virtual soft-handoff
ActiveUS7046647B2Higher-layer handoffMinimizing interruptionData switching by path configurationWireless network protocolsMobile architectureDistributed computing
In some illustrative embodiments, a novel system and method is provided that can, for example, extend concepts of pre-authentication (such as, e.g., IEEE 802.11i pre-authentication) so as to operate across networks or subnetworks (such as, e.g., IP subnets). In preferred embodiments, a novel architecture includes one or both of two new mechanisms that substantially improve, e.g., higher-layer handoff performance. A first mechanism is referred to as “pre-configuration,” which allows a mobile to pre-configure higher-layer information effective in candidate IP subnets to handoff. A second mechanism is referred to as “virtual soft-handoff,” which allows a mobile to send or receive packets through the candidate IP subnets even before it is actually perform a handoff to any of the candidate IP subnets.
Owner:TELCORDIA TECHNOLOGIES INC +1
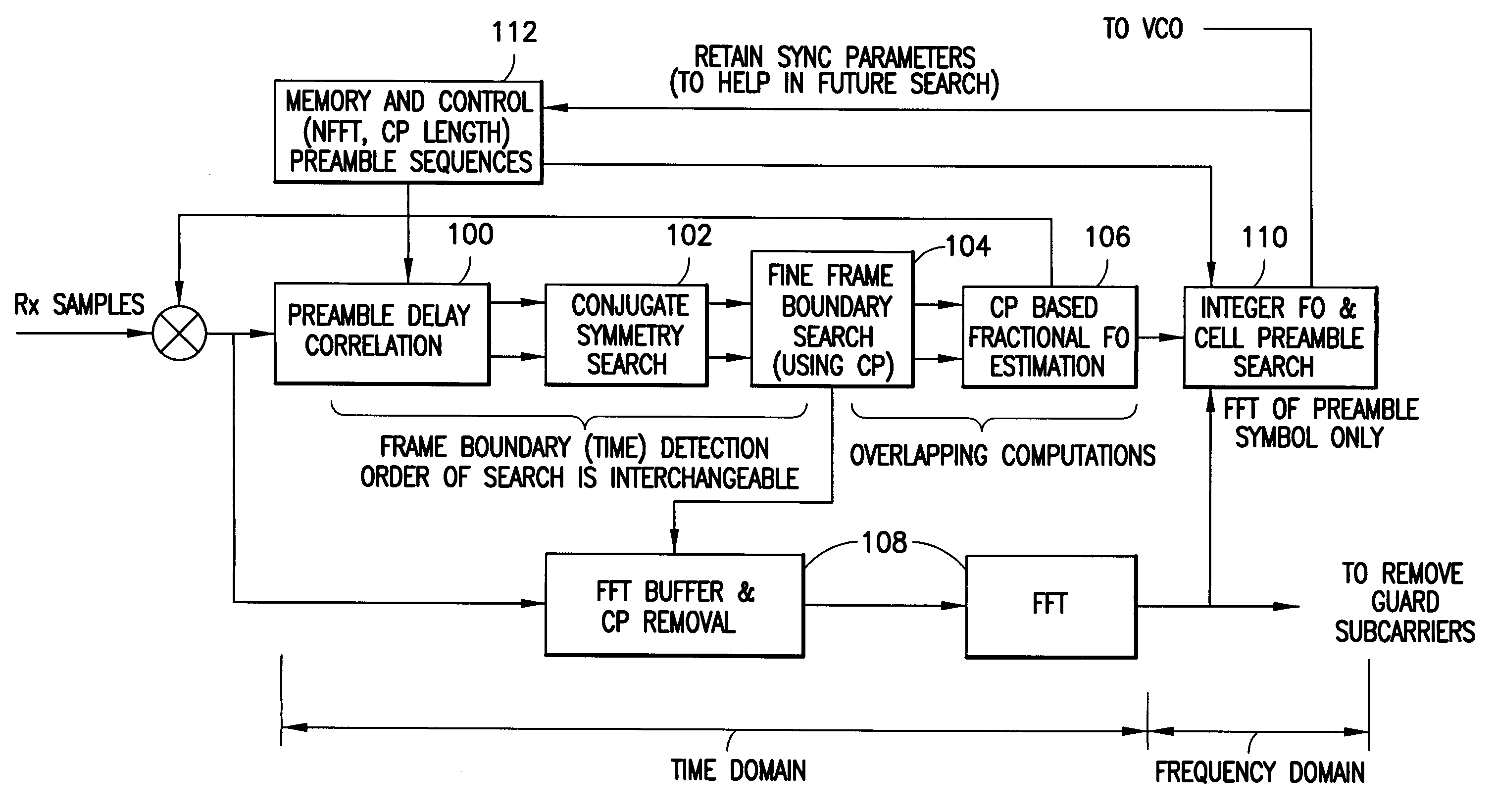
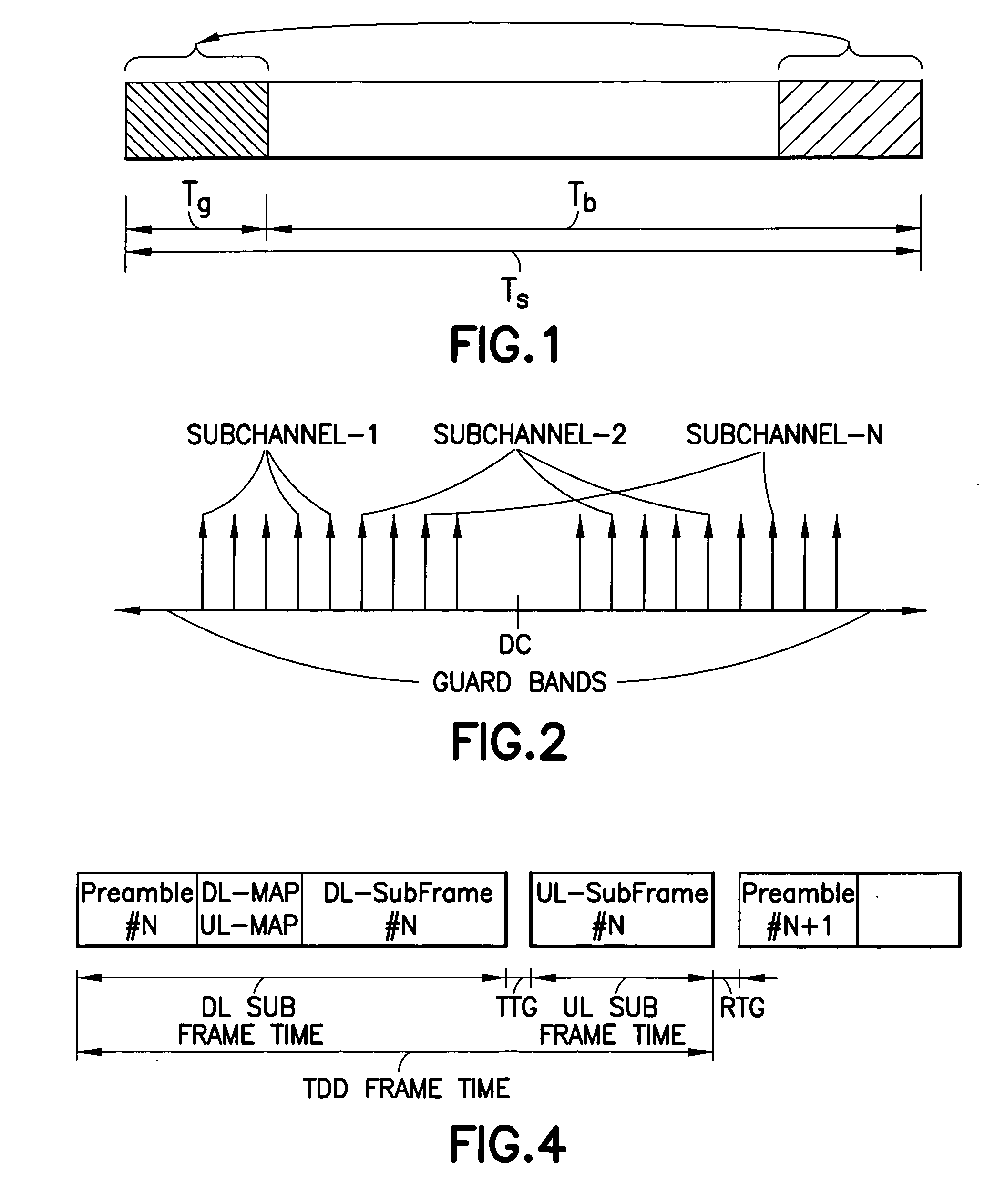
Method, apparatus and computer program product providing synchronization for OFDMA downlink signal
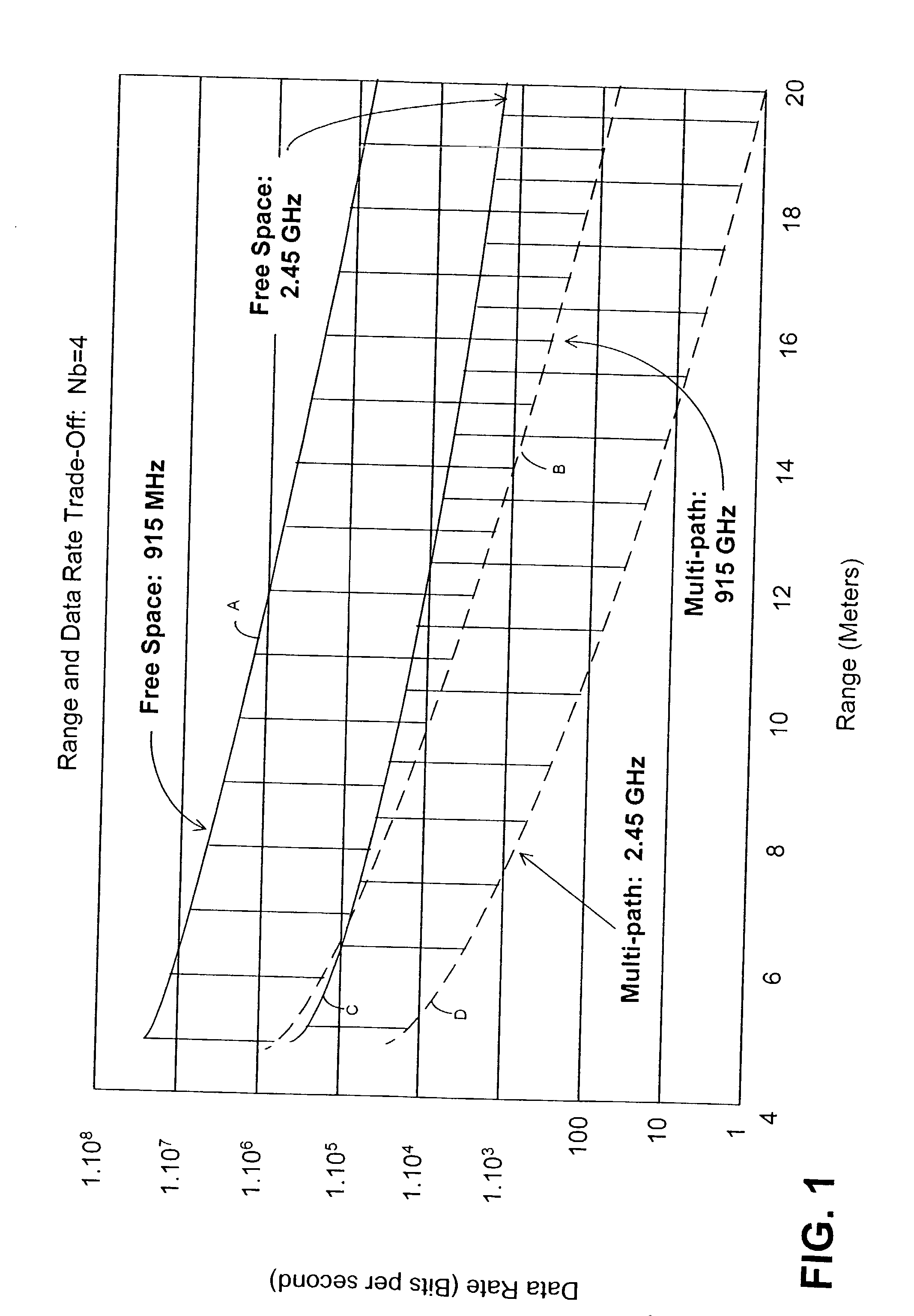
InactiveUS20070280098A1Good precisionModulated-carrier systemsTime-division multiplexCell specificCarrier frequency offset
Disclosed is a method, a computer program product and a device that includes a receiver for receiving a downlink signal transmitted into a cell. The receiver is operable to obtain time, carrier frequency and cell-specific preamble synchronization to the received signal and includes a plurality of synchronization units that include a first detector to detect a frame boundary using preamble delay correlation; a second detector to detect the frame boundary with greater precision using a conjugate symmetry property over a region identified by the first detector; a cyclic prefix correlator to resolve symbol boundary repetition; an estimator, using the cyclic prefix, to estimate and correct a fractional carrier frequency offset; an operator to perform a Fast Fourier Transform of an identified preamble symbol and a frequency domain cross-correlator to identify cell-specific preamble sequences and an integer frequency offset in sub-carrier spacing. The transmitted signal may be a downlink signal transmitted into the cell from a base station that is compatible with IEEE 802.16e (WiMAX).
Owner:NOKIA TECHNOLOGLES OY
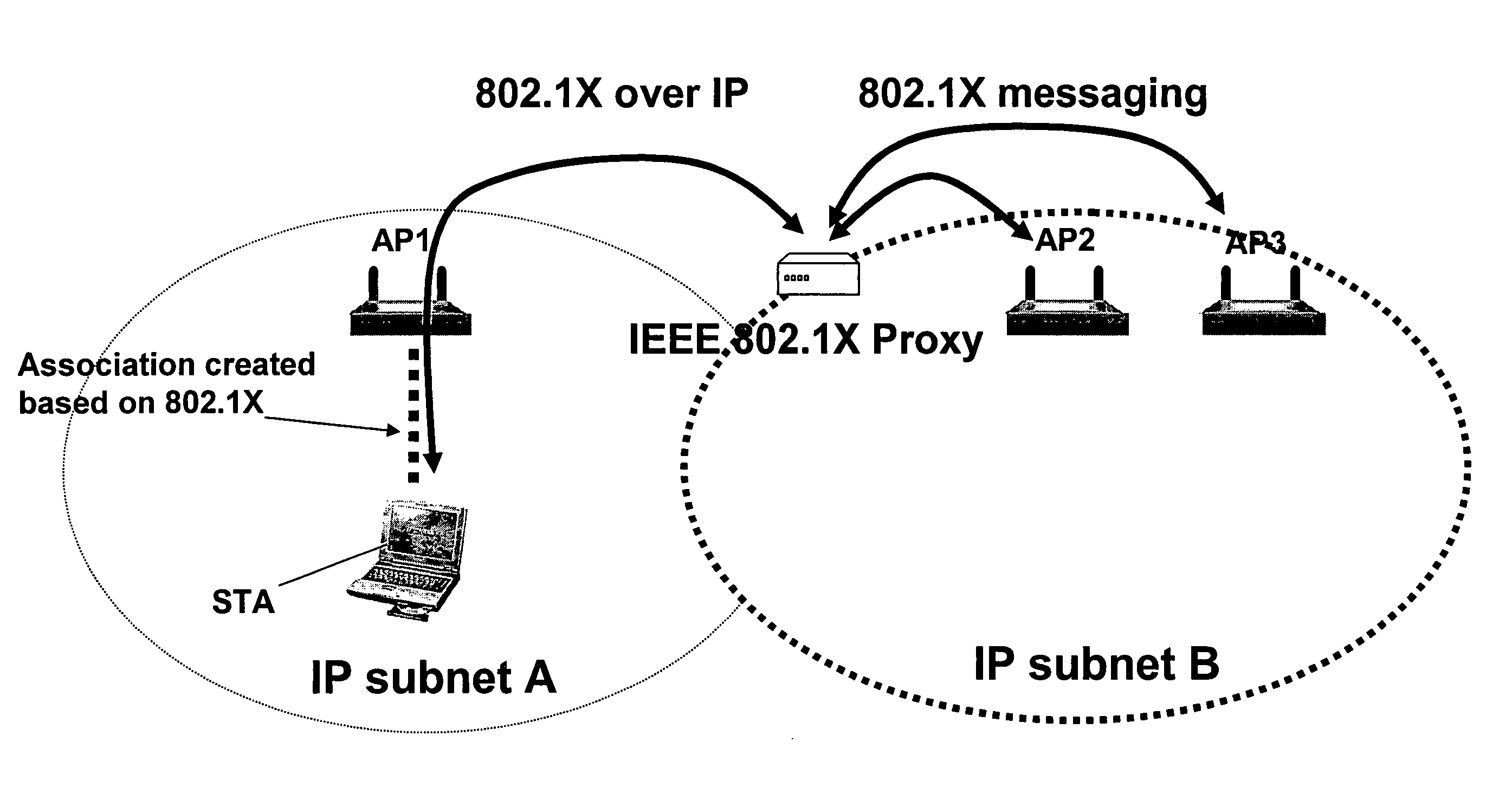
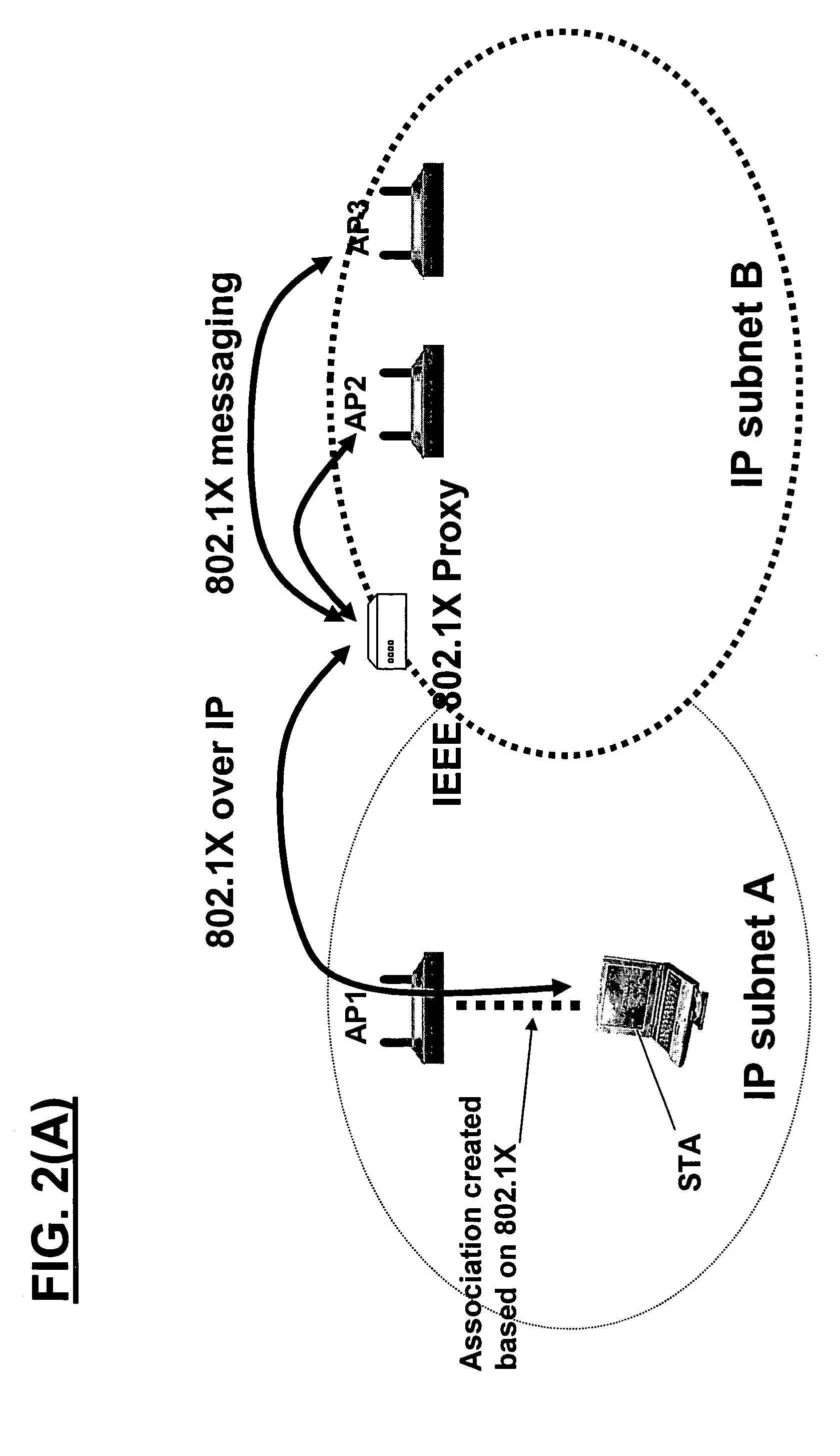
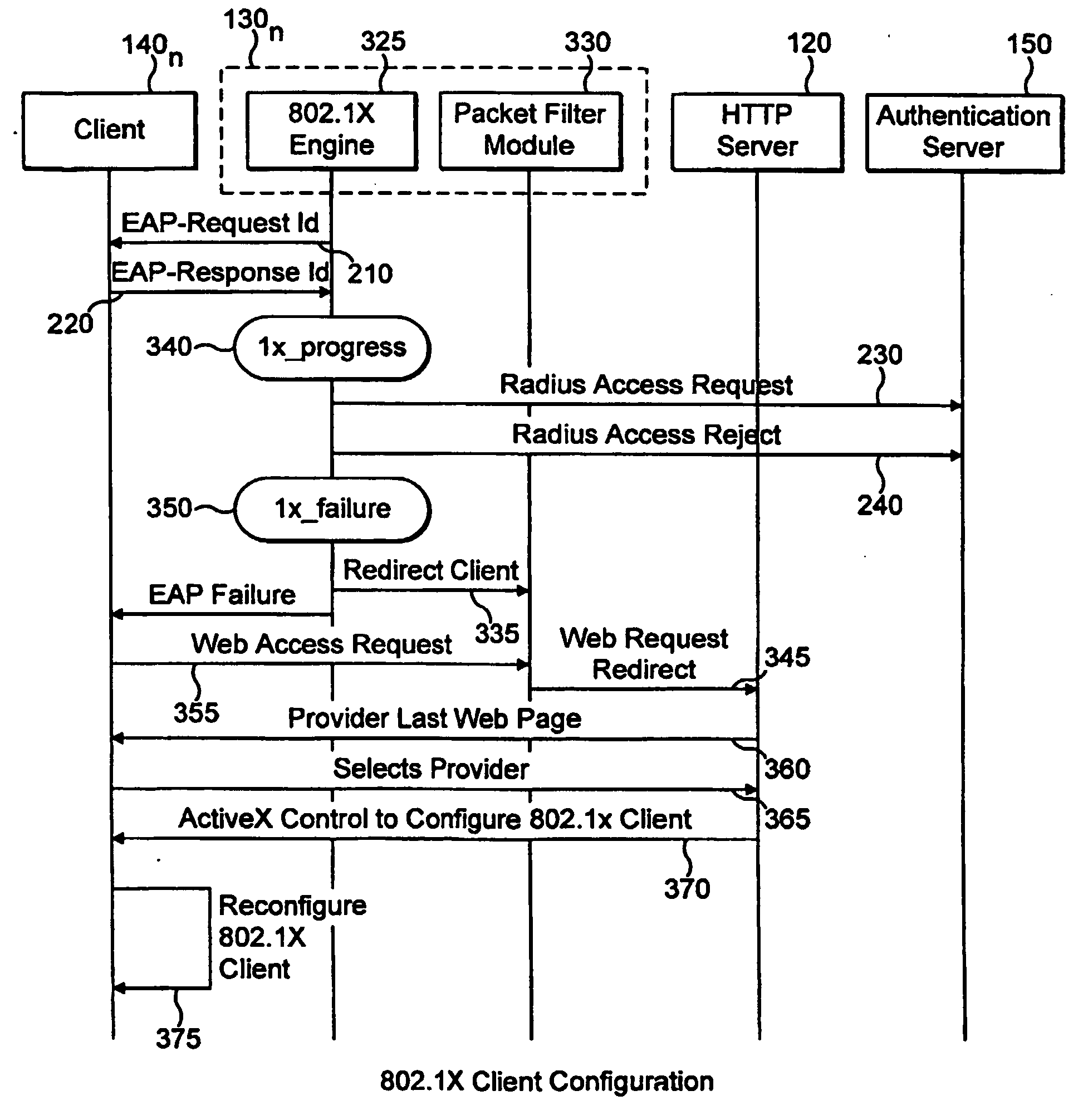
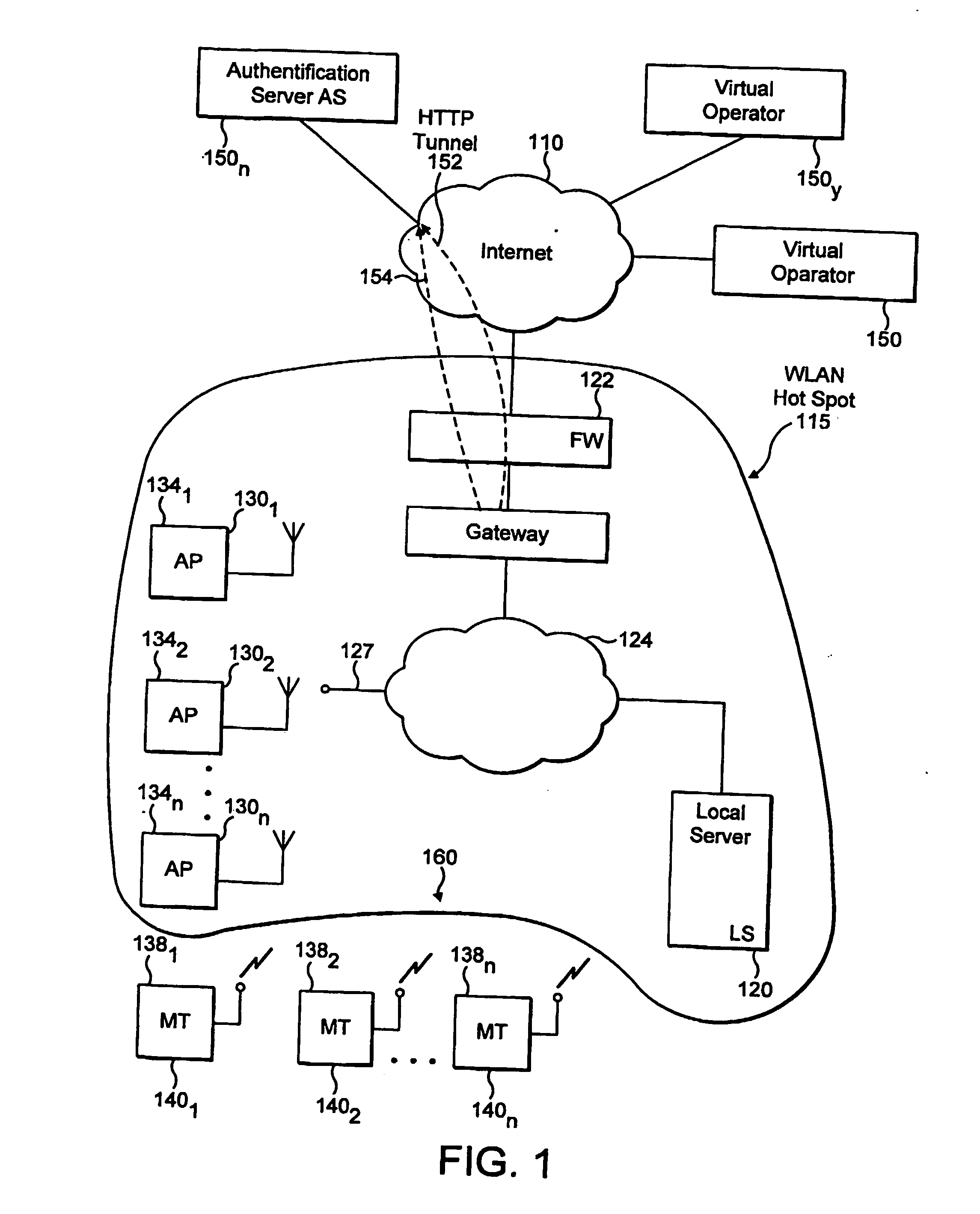
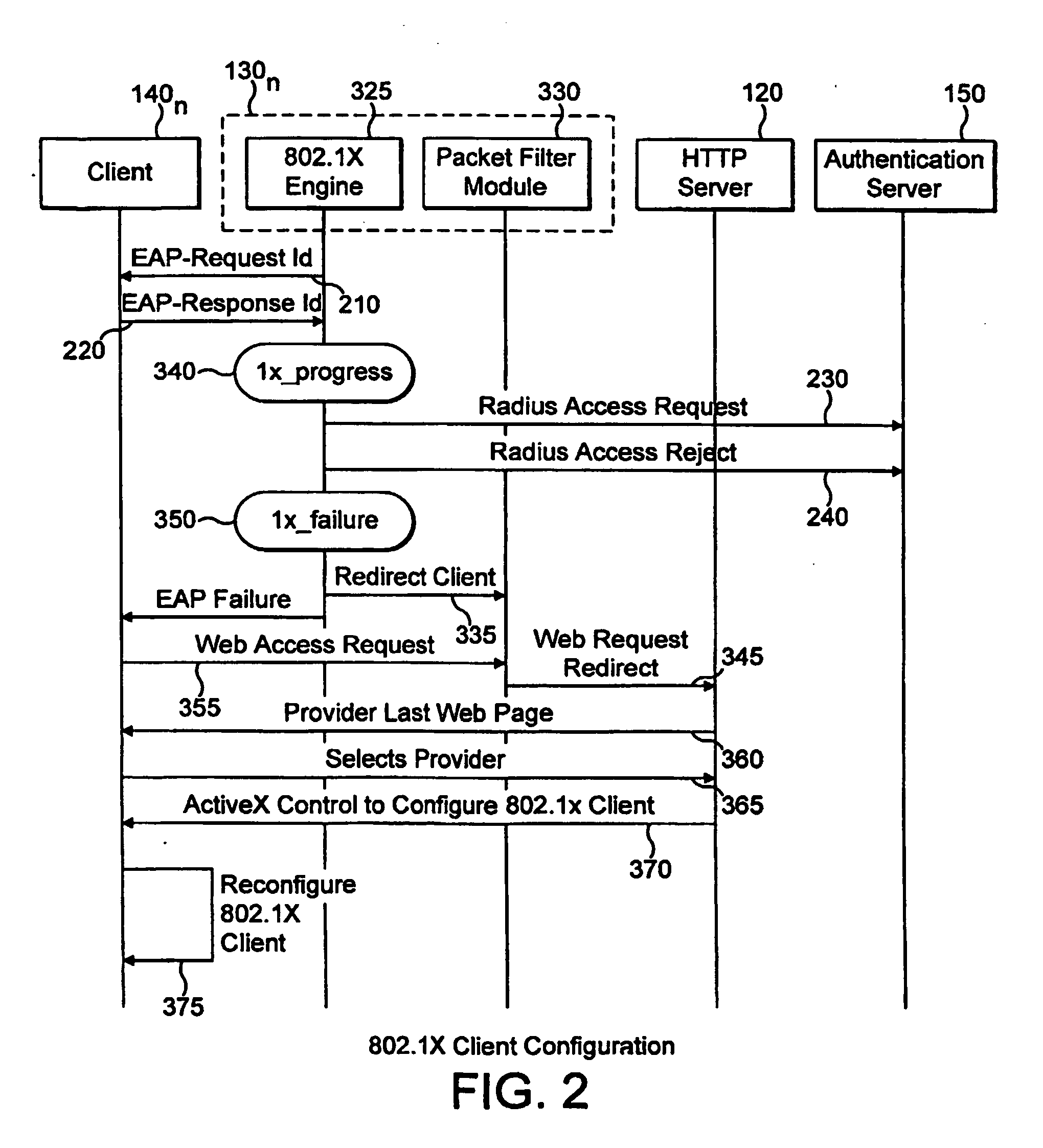
Automatic configuration of client terminal in public hot spot
ActiveUS20060173844A1Easy accessDigital data processing detailsUser identity/authority verificationLimited accessAuto-configuration
The invention herein provides an apparatus and a method for automatically configuring an IEEE 802.1x client terminal to provide limited access in a WLAN environment, specifically utilizing the access point to filter traffic associated with the limited access so as to redirect the client terminal's HTTP request to a designated local web server. The web server responds to the client terminal by requesting information required to establish an authorized communication. Thereafter the client terminal provides information required to establish an authorized communication. In the course of the communication the web server sends information such as transmission rates, new user account creation information, authentication method selection, and access user terms and conditions of acceptance, all typically required to establish an authorized access. The client responds with information, required to establish an authorized communication.
Owner:BOSTON MEDICAL CENTER INC +1
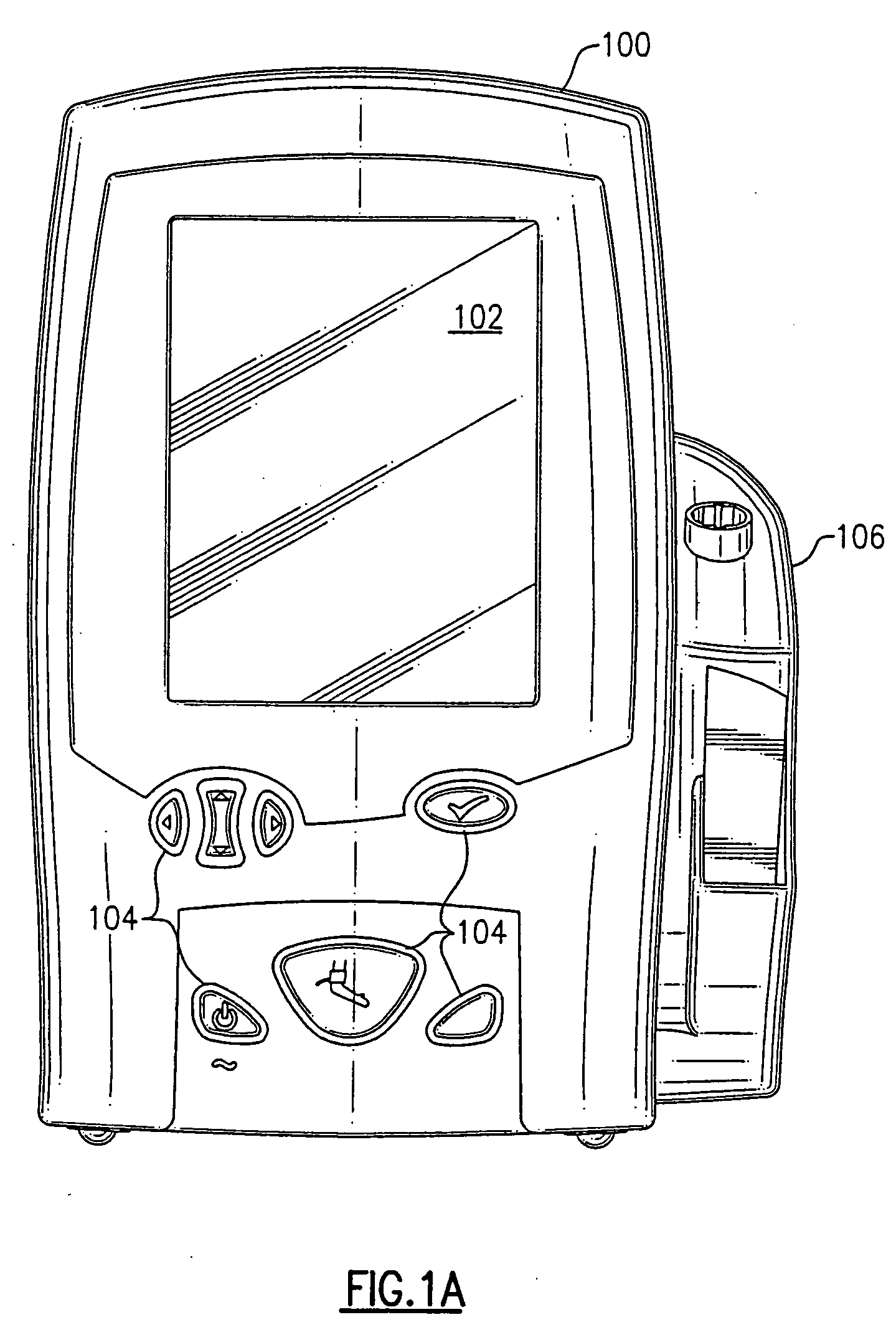
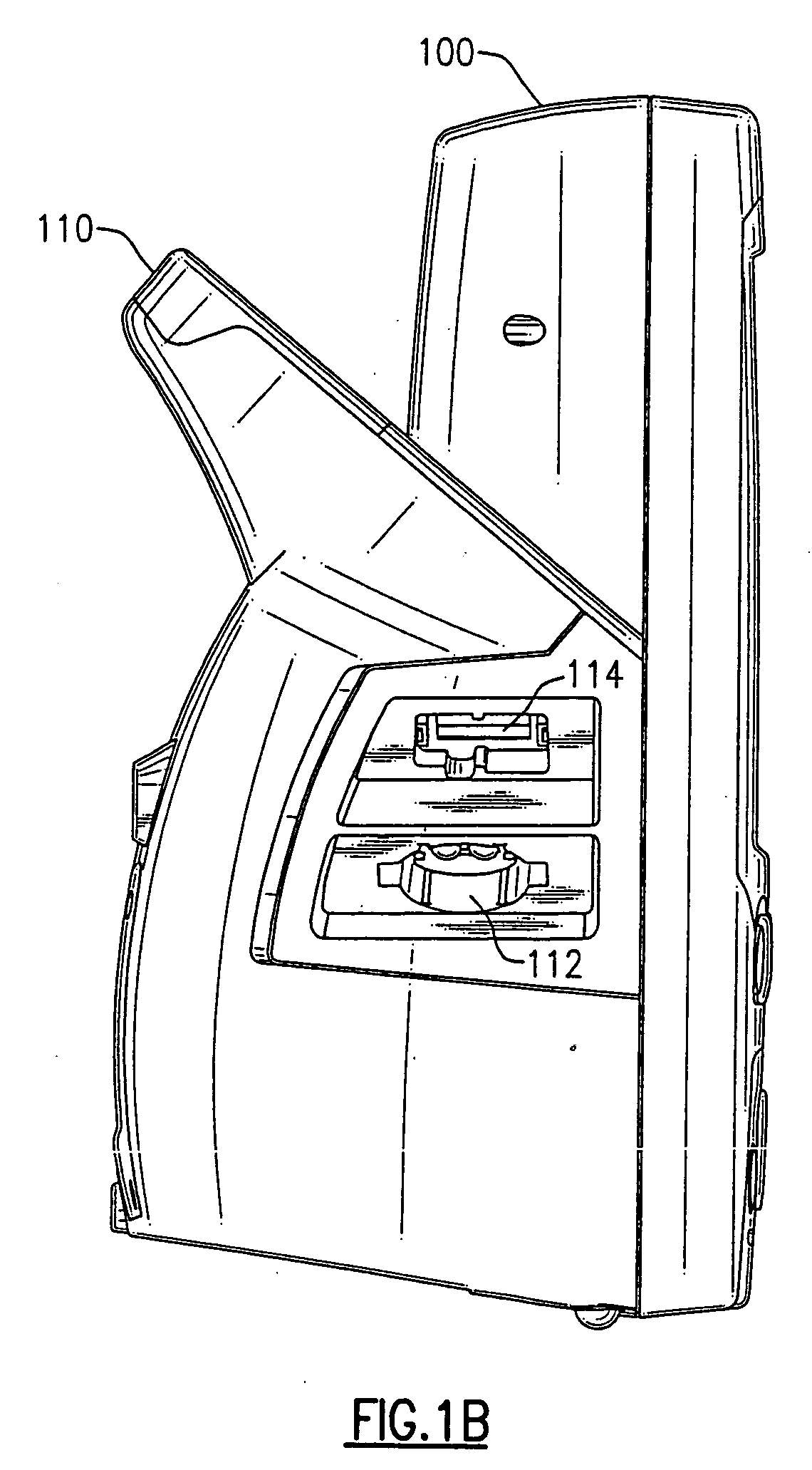
Portable vital signs measurement instrument and method of use thereof
The invention is a portable vital signs measurement instrument, systems and methods that provide a variety of measurement capabilities, including blood pressure, temperature, pulse oximetry, and other indications of patient status. The instrument, systems and methods include the ability to communicate wirelessly, for example using Wi-Fi (IEEE 802.11B), with a server, so that information can be entered easily, securely and reliably into a medical database system accessible by way of the server. The systems and methods provide for the instrument to initiate a communication session by attempting to discover a server access point in its vicinity.
Owner:WELCH ALLYN INC
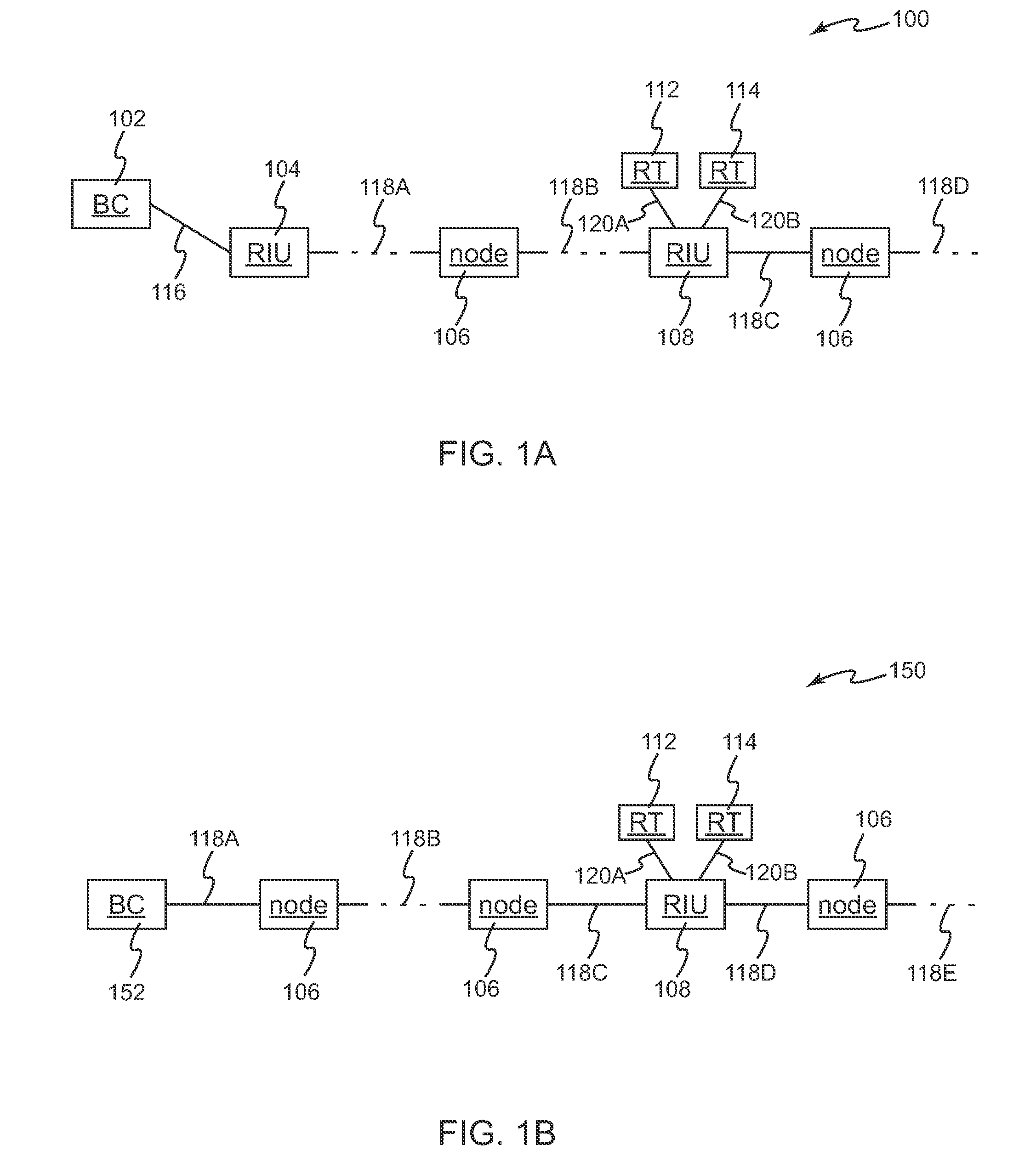
Interfacing a legacy data bus with a wideband wireless data resource utilizing an embedded bus controller
InactiveUS7558903B2Digital computer detailsElectric digital data processingMIL-STD-1553Wireless Application Protocol
Various methods and systems provide interfaces between legacy data buses such as MIL-STD 1553 buses and wideband wireless data links such as links compatible with IEEE 802.11 or IEEE 802.16e. One technique for interfacing a legacy bus to a wideband wireless data communication link involves providing a hybrid bus controller / remote interface unit as an interface between the two data communication architectures. In operation, the legacy interface suitably receives data intended for a legacy node from a wireless radio module that is compatible with a designated broadband wireless data communication protocol. The legacy data is converted in the legacy interface / remote interface unit to at least one legacy word having a legacy format for transmission on the legacy data bus. The legacy interface may be further configured to receive a reply message from the legacy component on the legacy data bus, and to forward a reply to the wireless radio module in a format that is compatible with the designated wireless data communication protocol.
Owner:THE BOEING CO
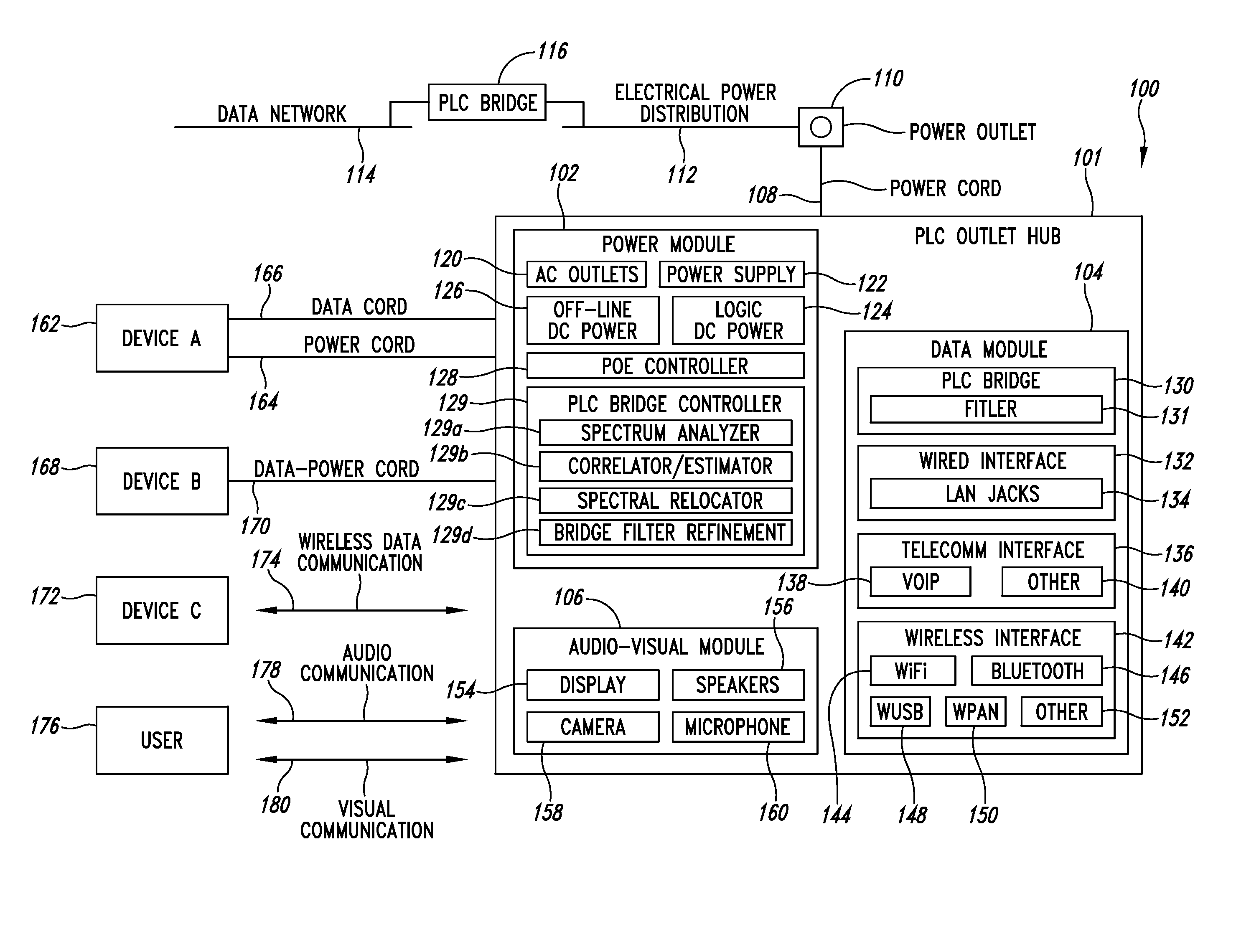
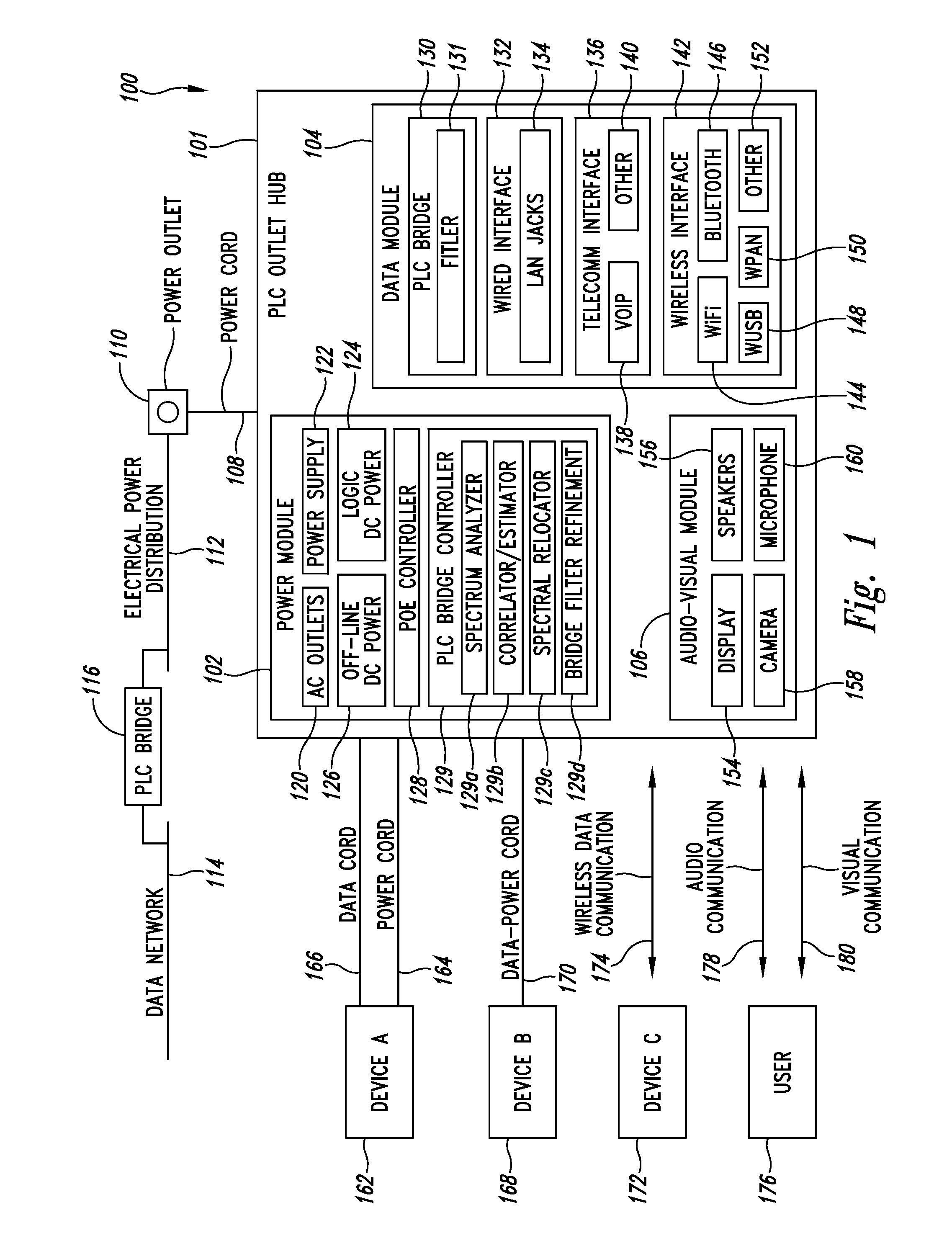
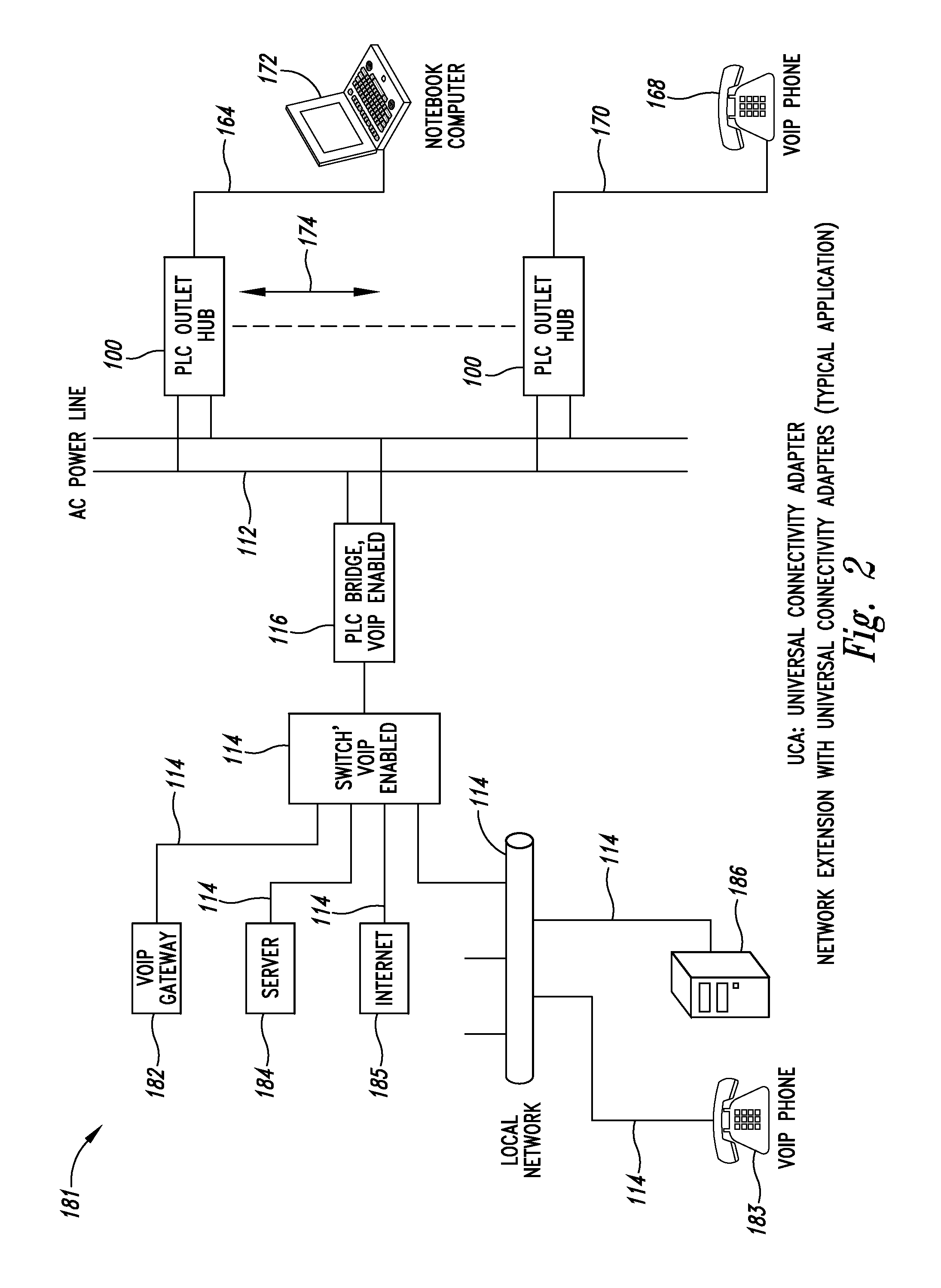
Power line communication hub system and method
InactiveUS20070198748A1Frequency-division multiplex detailsTelephonic communicationDistribution power systemNetwork communication
A power line communication (PLC) hub incorporates multiple network communication media and services for devices. Implementations can be plugged into an electrical outlet to furnish a single point for both electrical power and network connectivity. Each of the electrical outlets is tied through an electrical distribution system to a network through a conventional PLC bridge to provide network connectivity through the electrical distribution system using PLC technology. The PLC outlet hub can include various combinations of applications and / or services including Voice Over Internet Protocol (“VoIP”) gateway, media server, Internet router / gateway, Local Area Network (“LAN”), both wired and wireless voice and video conferencing capability, including a VoIP, Voice over WiFi (“VoWiFi”), Power Over Ethernet (“PoE”), Wireless 802.11a / b / g / n capability and (Wireless Universal Serial Bus “WUSB” / Ultra Wide Band “UWB”) wireless connectivity, and Blue Tooth. Versions of the PLC outlet hub can have an Ethernet IEEE 802.3 family (such as IEEE 802.3af) compliant power supply to furnish power to PoE enabled devices.
Owner:LEVITON MFG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com