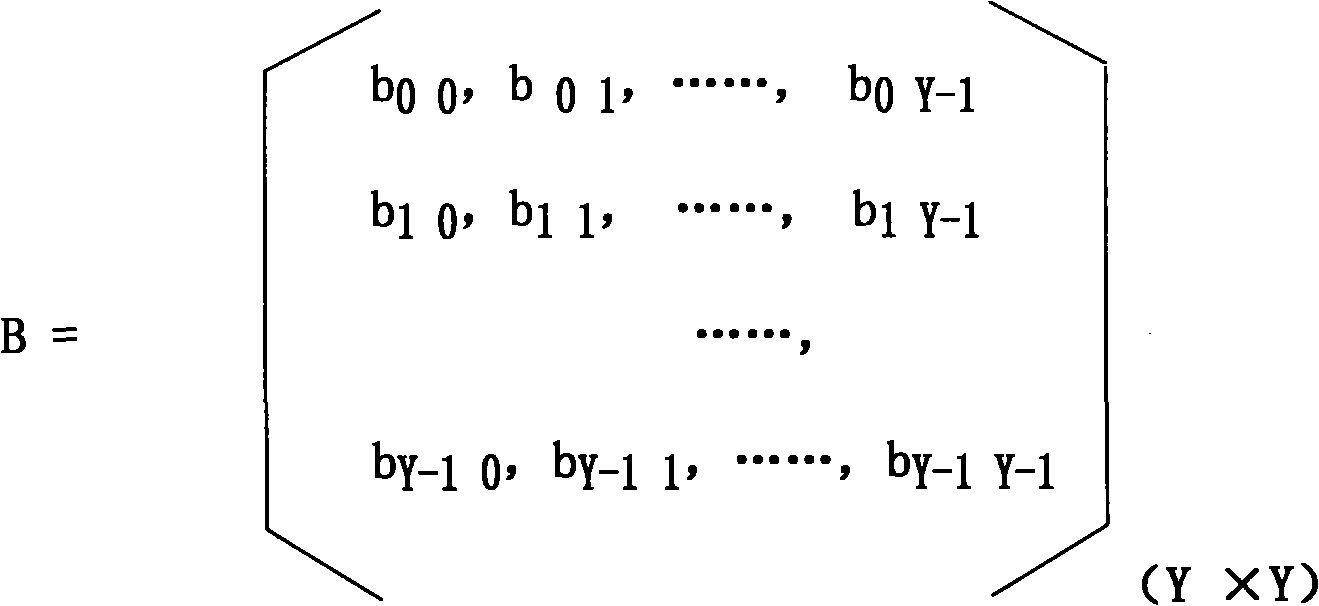Method for realizing equipment authentication, data integrity and secrecy transmission for Internet of Things
A data integrity and confidential transmission technology, applied in digital data protection, transmission system, digital data authentication, etc., can solve problems such as high establishment cost, insufficient number of managed users, slow PKI/CA authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The following describes the implementation steps of IoT for device authentication, data integrity and confidential transmission with reference to the accompanying drawings:
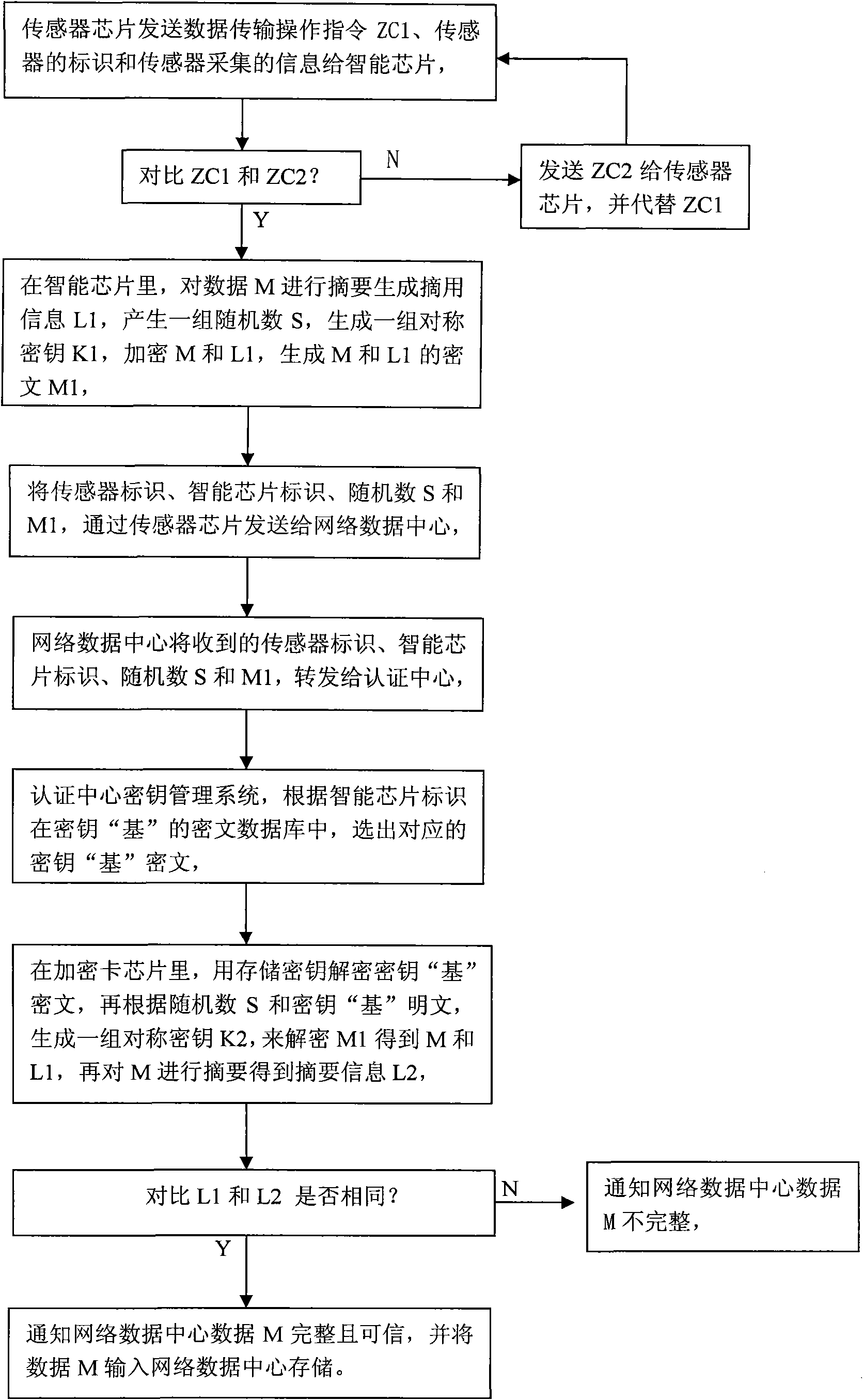
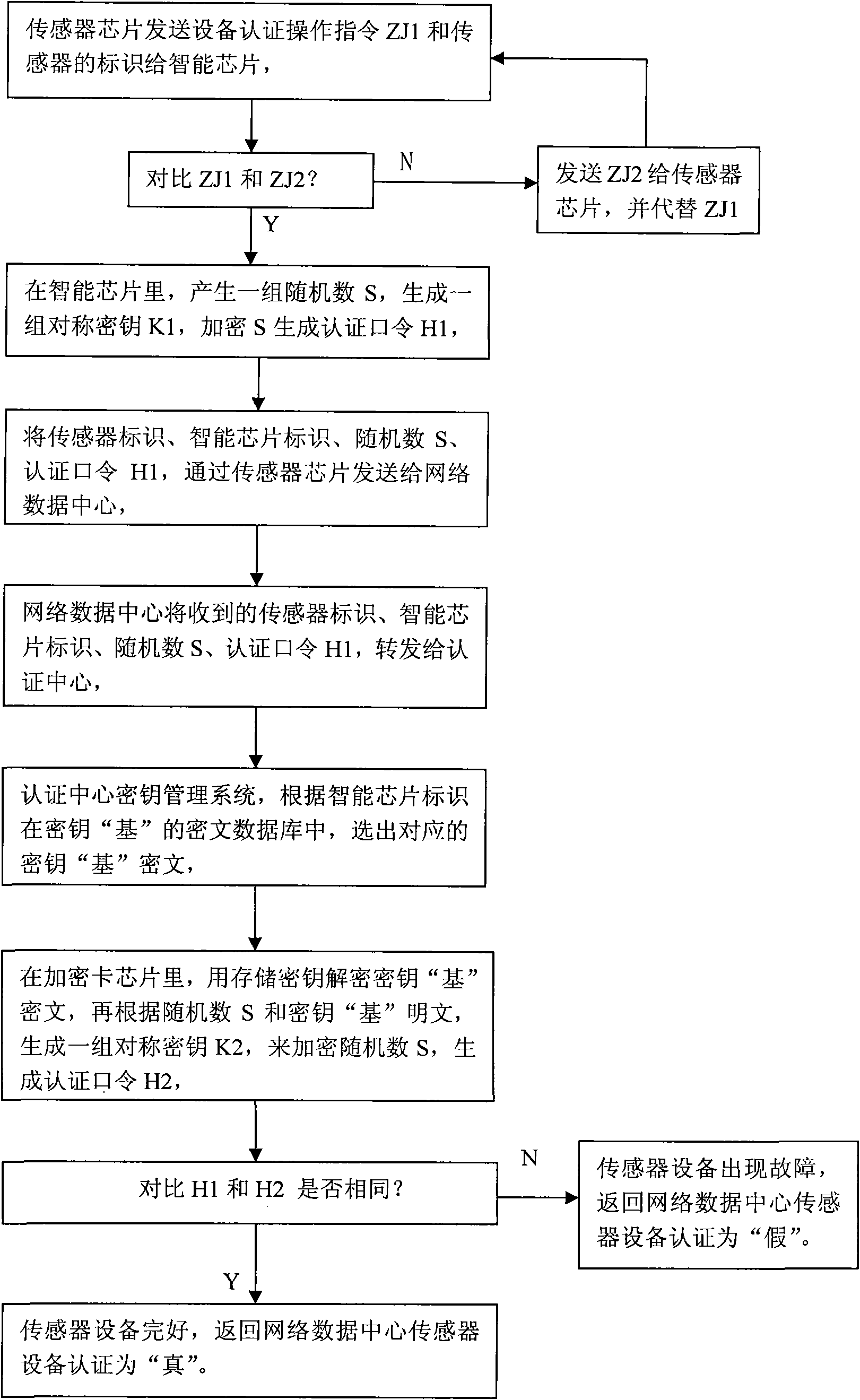
[0061] figure 1 : Indicates the process of the sensor transmitting data to the network data center in a complete and confidential manner. After the sensor collects information (set as: data M), it immediately sends a data encryption transmission request to the smart chip according to the data transmission operation command ZC1 in the sensor chip. : Send the data transmission operation instruction ZC1, the identification of the sensor and the information collected by the sensor to the smart chip together. In the smart chip, the operation instruction comparison protocol will store the data transmission operation instruction in the smart chip ciphertext file package (set as: ZC2 ), compared with the received data transmission operation command ZC1 sent by the sensor. If ZC1≠ZC2, it means that ZC1 has ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com