Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
524results about How to "Examples cannot be limited" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Neural network model training method and device, and computer device
InactiveCN108898218AExamples cannot be limitedImplement transfer learningNeural learning methodsNerve networkNetwork model
A neural network model training method and device, and a computer device are disclosed. The neural network model training method includes: performing training by using a source domain sample set to obtain a neural network model; performing iterative processing by using the following steps until an iterative stop condition is satisfied: inputting an uncertain label sample in a target domain sampleset into the current neural network model, and using the output prediction result as a current learning label of the uncertain label sample; inputting a source domain sample set and the current targetdomain sample set in to the current neural network model, constructing a neural network loss function on the basis of the output prediction result, wherein independent variables of the neural networkloss function include at least: a difference between a mapping feature of the source domain sample set and a mapping feature of the current target domain sample set; using the current neural networkloss function to perform back propagation so as to update model parameters of the current neural network model; and determining the current neural network model as the final trained neural network model after iteration is ended.
Owner:ALIBABA GRP HLDG LTD
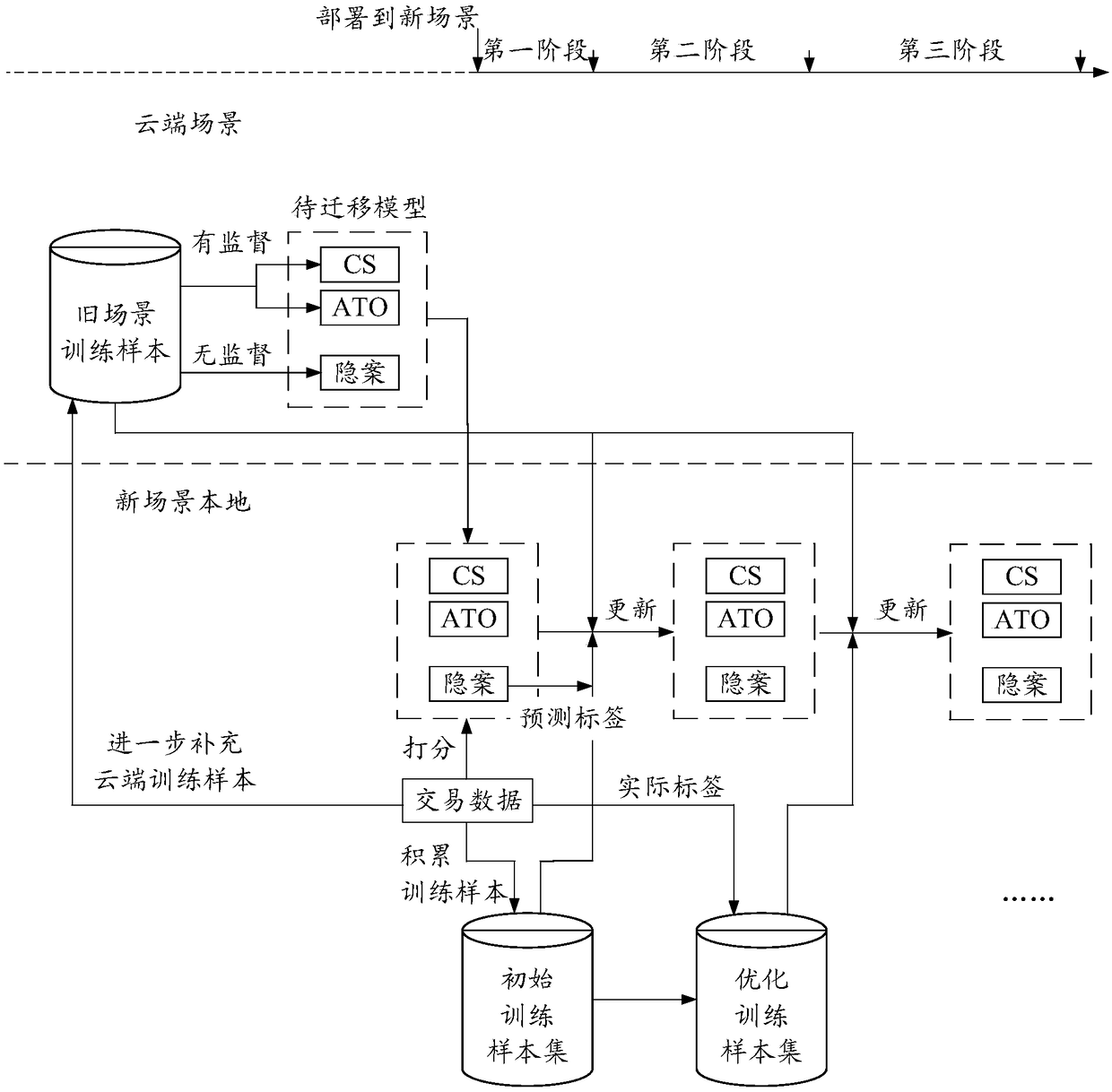
Prediction model training method and apparatus for a new scene
ActiveCN109359793AAccumulation time is shortSuitable for useComputing modelsResourcesSupervised learningTraining methods
A prediction model training method and apparatus for a new scene are disclosed. A prediction model training method for a new scene, the method comprising: obtaining a set of models to be migrated; Selecting at least one model from the set of models to be migrated for predictive labeling of unlabeled samples in a new scene; Obtaining an initial training sample set in the new scene; Using the selected model,adding the prediction tags to the untagged samples in the initial training sample set. Based on the supervised learning algorithm, the model to be migrated is updated by using the initial training sample set to which the prediction label has been added, and the model suitable for the new scene is obtained.
Owner:ADVANCED NEW TECH CO LTD
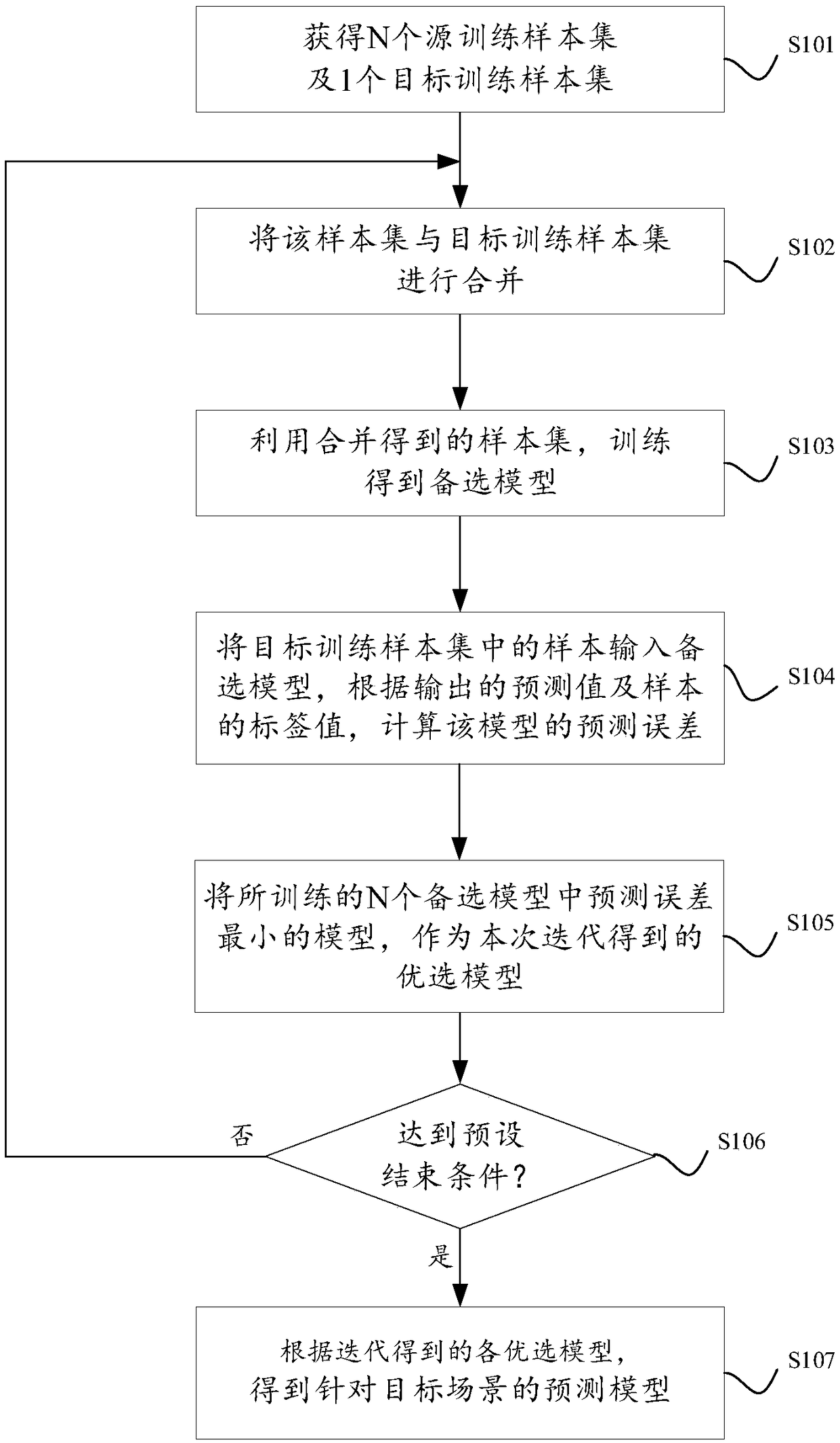
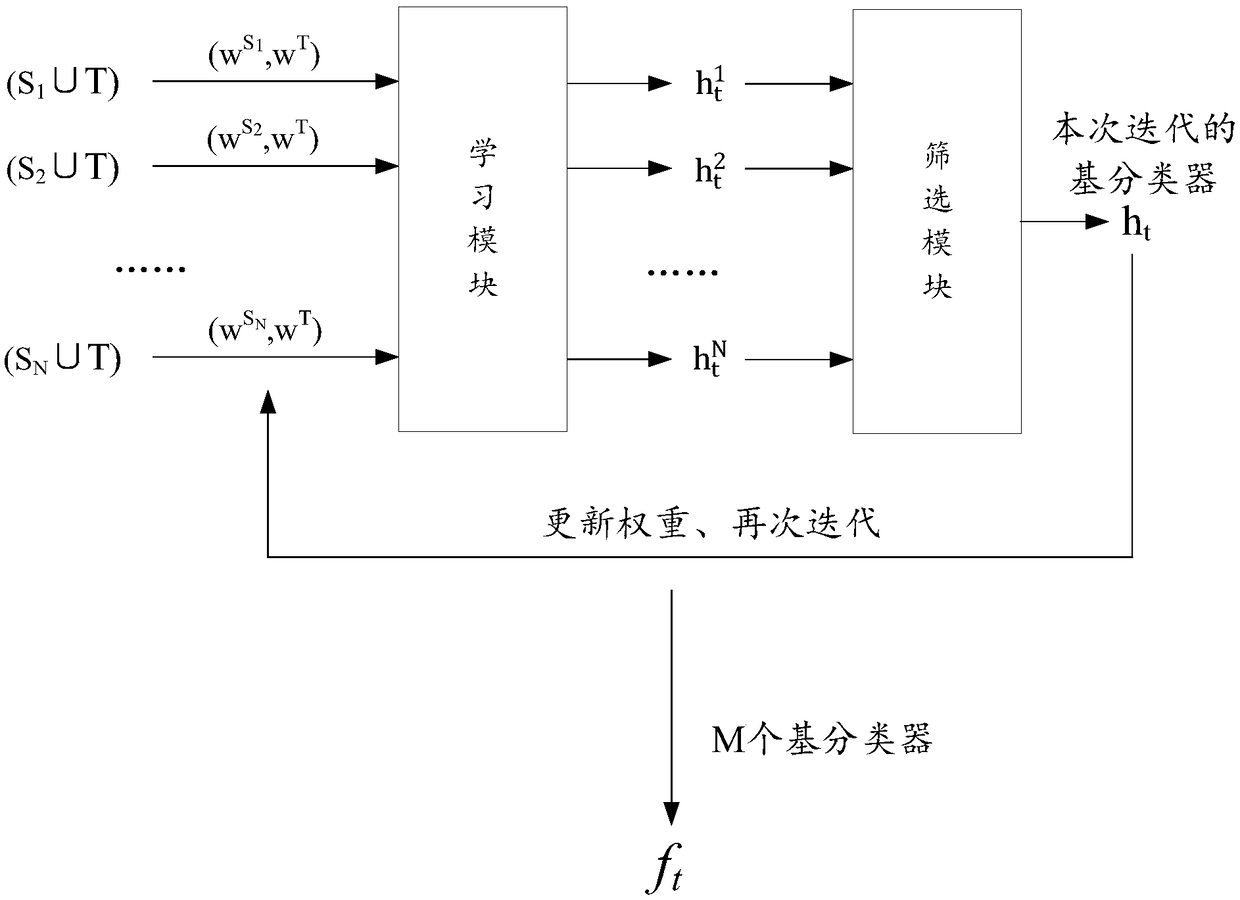
A method and apparatus for training a prediction model for a target scene
PendingCN109214436AExamples cannot be limitedCharacter and pattern recognitionPrediction methodsAlgorithm
Disclosed are a prediction model training method and device for a target scene. A prediction model training method for target scene includes obtaining N source training sample sets and one target training sample set; an iterative process is performed using the following steps until a preset end condition is reached: for each sample set of N source training sample sets, the sample set is merged with a target training sample set; using the merged sample set, the candidate model is trained. Each sample in the target training sample set is inputted into an alternative model, and the prediction error of the model is calculated according to the prediction value outputted from the model and the label value of each sample. The model with the smallest prediction error among the N candidate models is selected as the optimal model obtained by this iteration. After the iteration, according to the preset screening rules, all or part of the selected models are selected to be weighted from each iteration to obtain the prediction model for the target scenario.
Owner:ADVANCED NEW TECH CO LTD
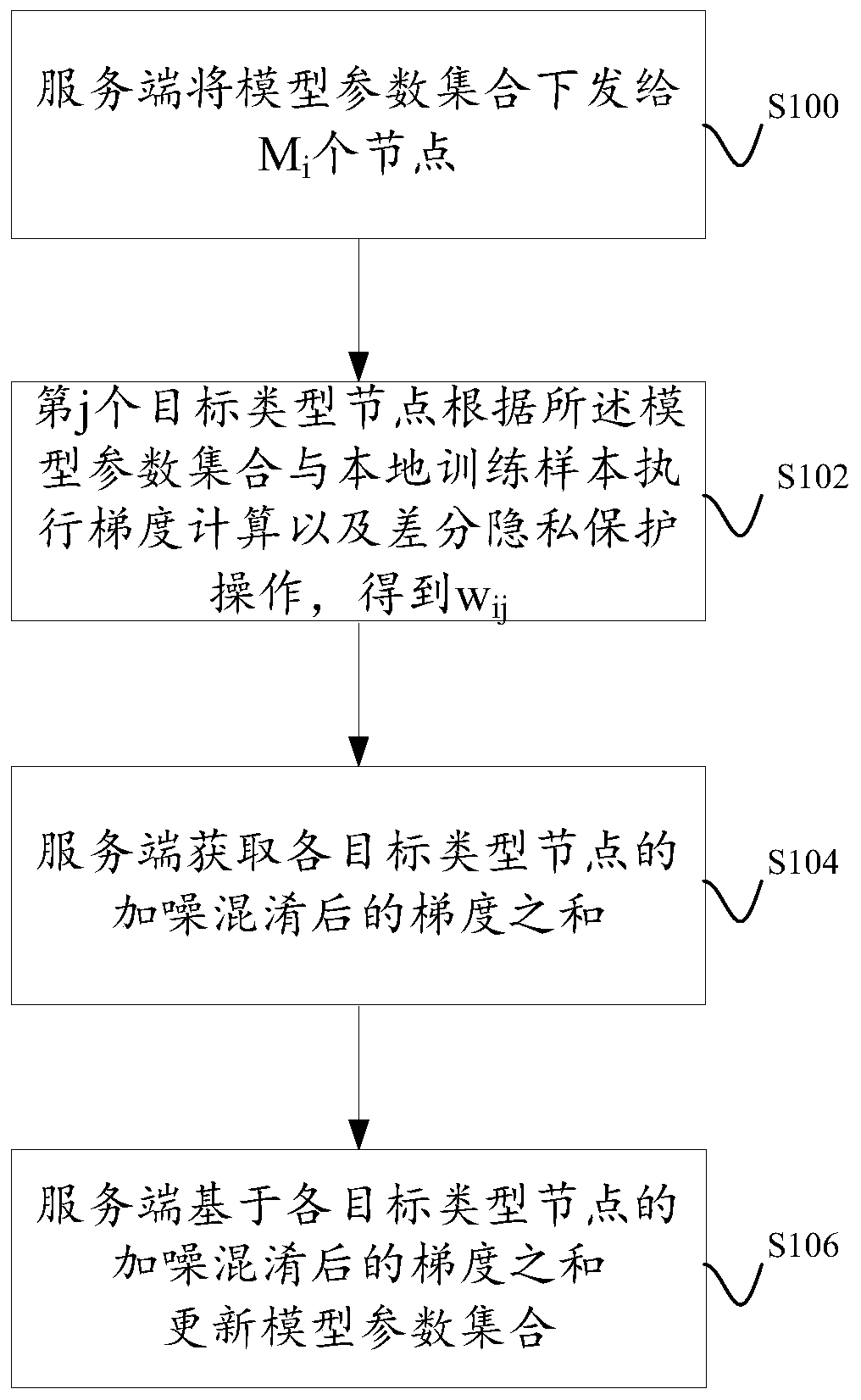
Model training method based on federated learning
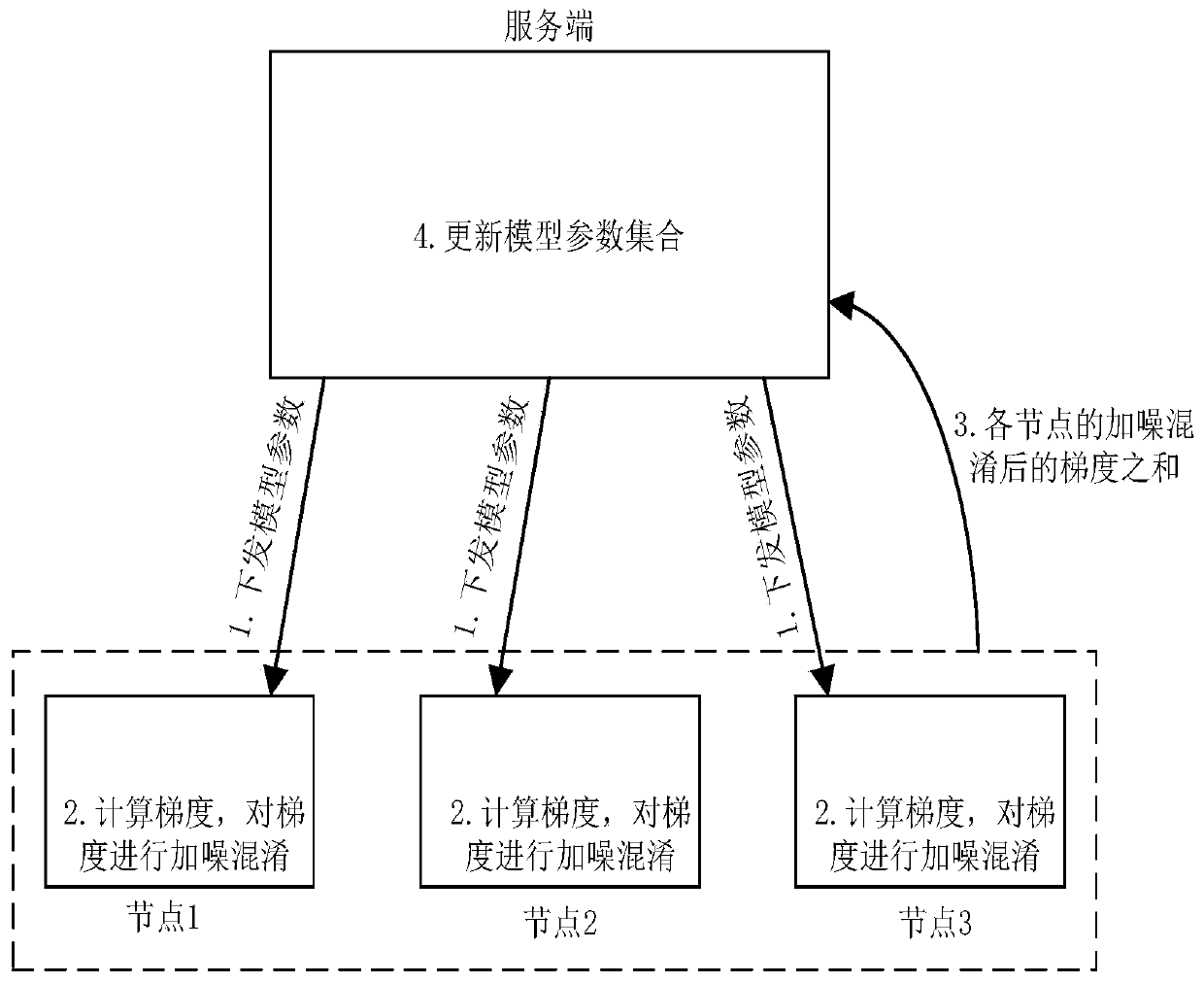
ActiveCN111046433AAchieving Noise and ObfuscationExamples cannot be limitedDigital data protectionMachine learningDifferential privacyEngineering
The invention discloses a model training method based on federated learning. In one training iteration, the nodes can achieve noise adding and confusion of the gradient through differential privacy protection operation, and the server can obtain the sum of the gradients after noise adding and confusion to update model parameters.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
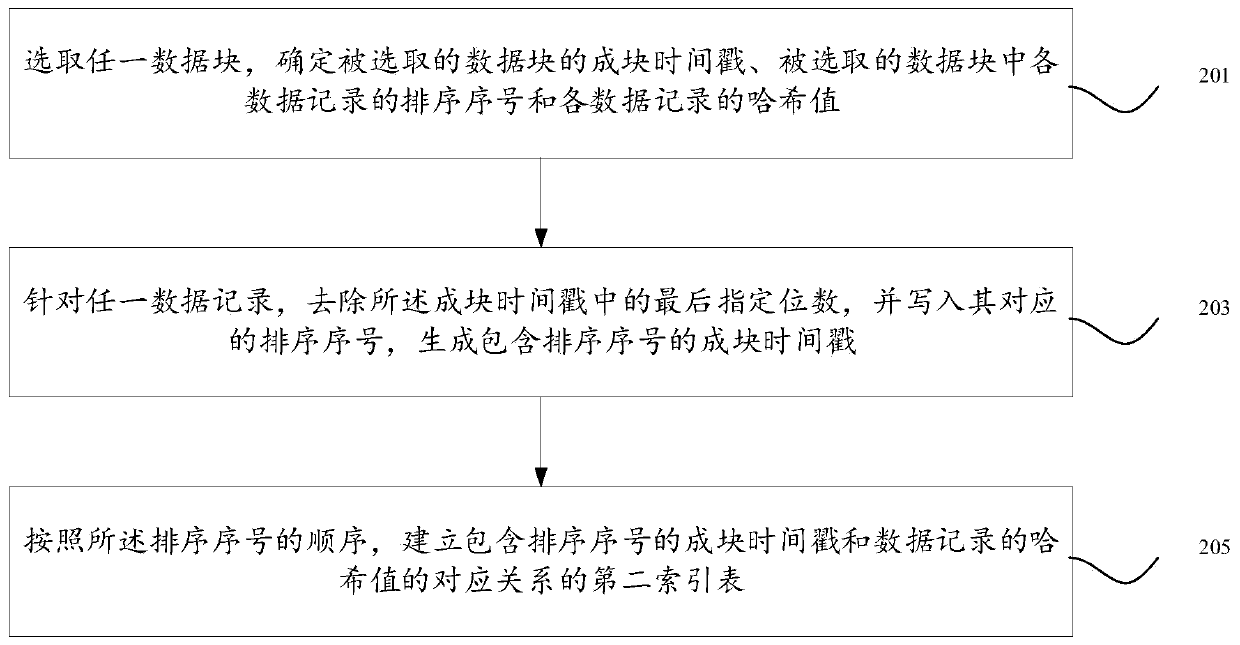
Index creating method, device and equipment
The invention discloses an index creation method, device and equipment. In a scene that a server centrally stores data records in a data block chain manner, each data block comprises a hash value of adata block itself determined by a hash value of a previous data block and the data records contained in the data block itself, and a provider of the data service cannot easily change the stored data.At the moment, the index table about the acceptance time sequence of the data records in the data block is created, so that the data records can be conveniently queried and traced, and the user experience is improved.
Owner:ADVANCED NEW TECH CO LTD
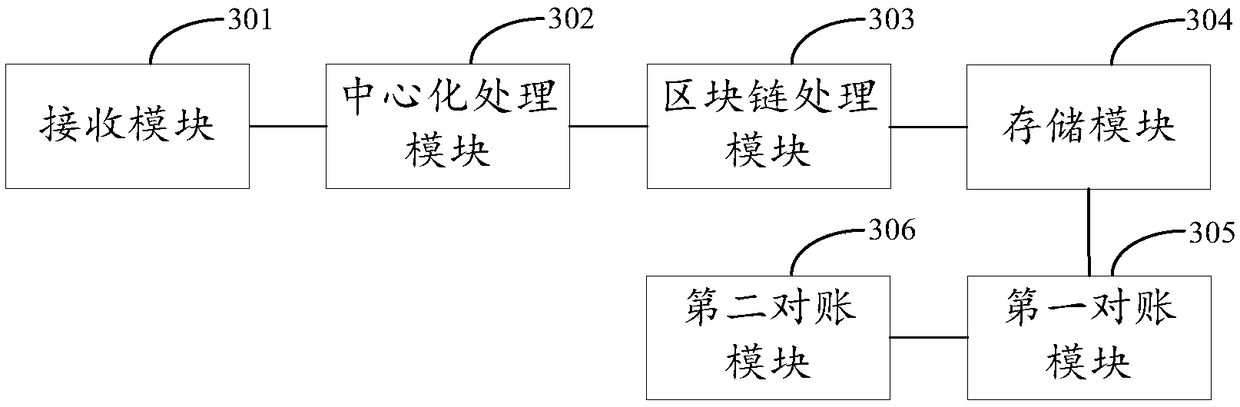
Transaction method and system based on centralized settlement and block chain deposit certification
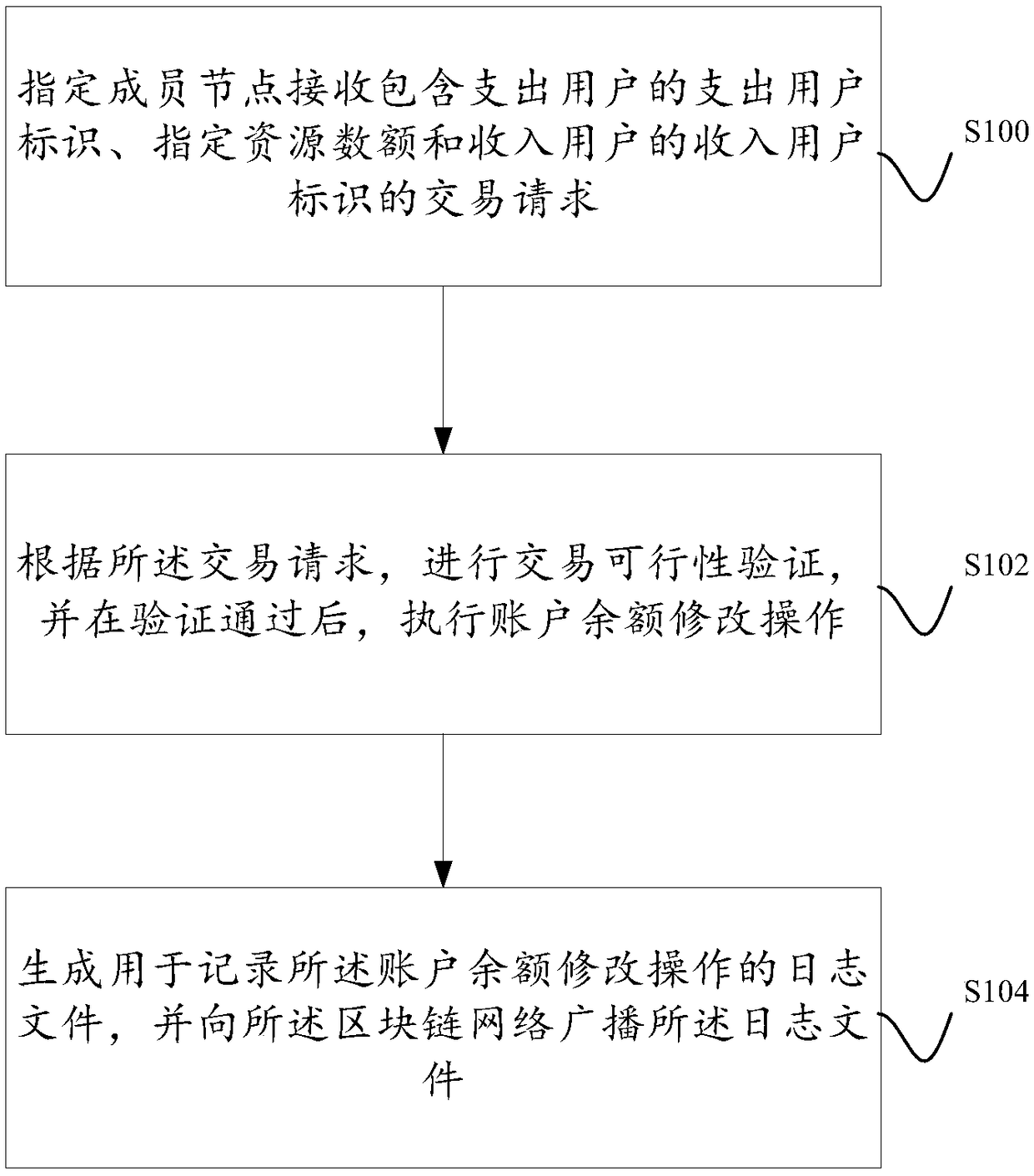
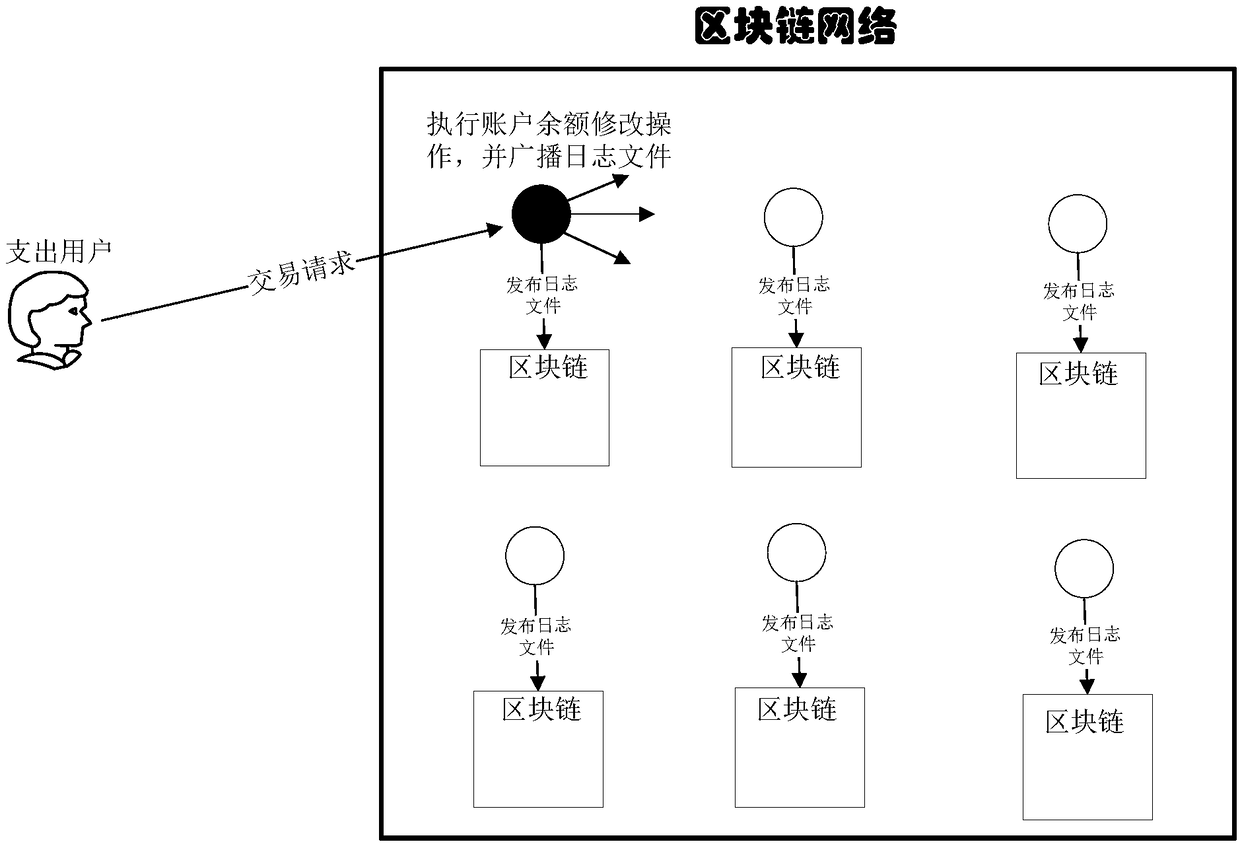
ActiveCN108876380AExamples cannot be limitedCryptography processingPayment protocolsChain networkOperating system
The invention discloses a transaction method and system based on centralized settlement and block chain deposit certification. A block chain network comprises a plurality of member nodes, a user registers a virtual resource account on a designated member node, and the designated member node comprises a business logic execution module, a database management module and a block chain function module.The business logic execution module verifies the feasibility of the transaction according to a transaction request, after passing the verification, the database management module is instructed to perform an account balance modification operation, that is, a designated resource amount is deducted from a virtual resource account corresponding to an expenditure user identity, and the designated resource amount is added to a virtual resource account corresponding to an income user identity. Besides, the business logic execution module also generates a log file for recording the account balance modification operation, the log file is sent to the block chain function module, and the block chain function module broadcasts the log file to the block chain network.
Owner:ADVANCED NEW TECH CO LTD
Model training method based on federated learning
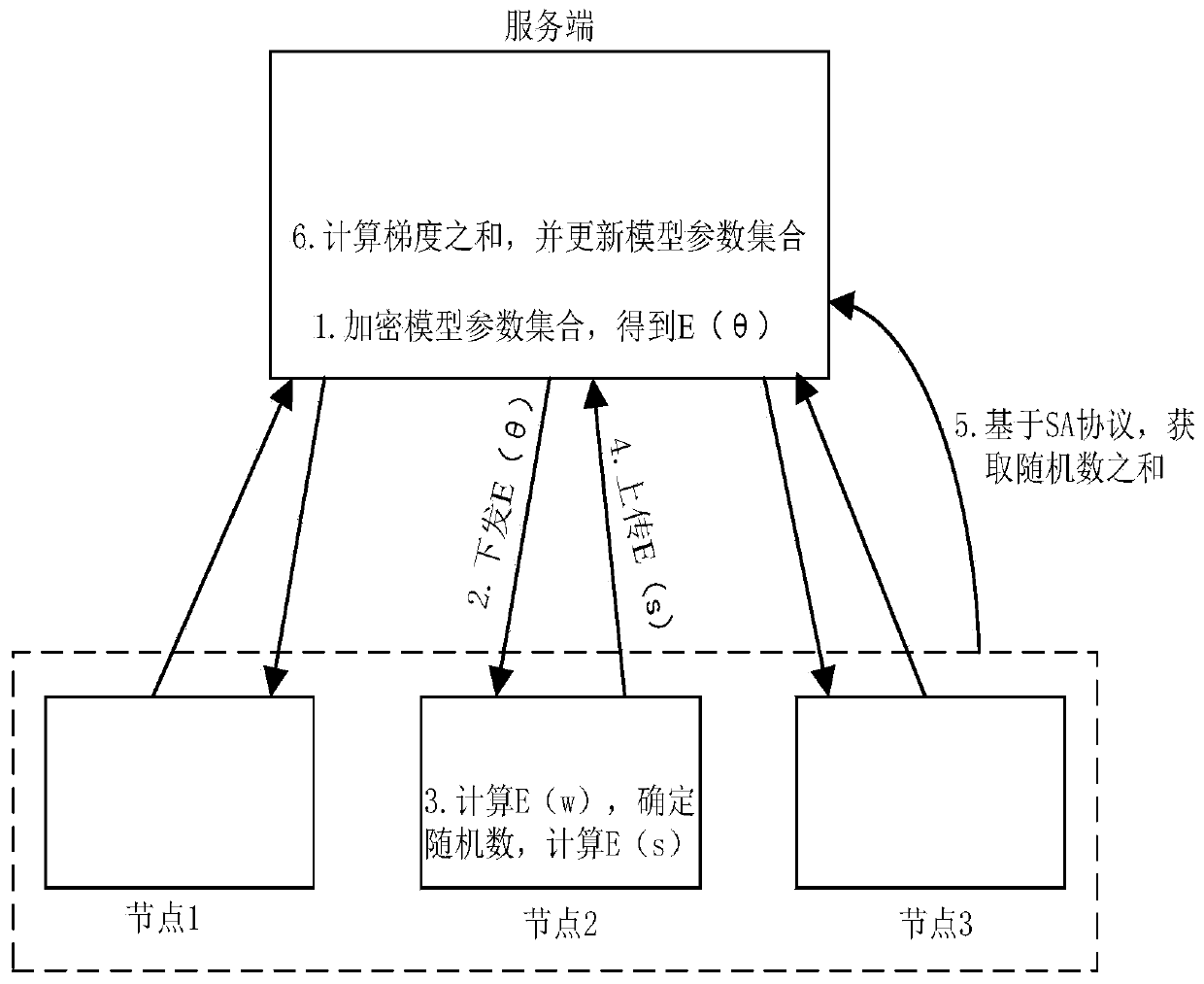
ActiveCN110955907AAvoid crackingExamples cannot be limitedDigital data protectionMachine learningPrivacy modelFederated learning
The invention discloses a model training method based on federated learning. In order to protect privacy (model parameters) of a server from being leaked, a server adopts a homomorphic encryption algorithm to encrypt a model parameter set and then issues the encrypted model parameter set to a node, and the node performs model calculation in an encrypted state by using the encrypted model parameters and a local training sample based on a homomorphic encryption principle to obtain an encryption gradient. Subsequently, the node calculates a difference between the encryption gradient and the encryption random number based on the homomorphic encryption principle, this difference being substantially a meaningless value of the encryption. And then, the node uploads the encrypted value to a server. Furthermore, the server can acquire the sum of the random numbers on each node by utilizing an SA protocol on the premise of not acquiring the random number on each node. Thus, the server can restore the sum of gradients generated by each node according to the sum of the encrypted value uploaded by each node and each random number, so that model parameters can be updated.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Merchant classification model construction and merchant classification method, device and equipment
ActiveCN109101989AComprehensive forecastExamples cannot be limitedCharacter and pattern recognitionMarketingFeature vectorClassification methods
A method, device and equipment for constructing a merchant classification model and merchant classification are disclosed. A method for constructing a merchant classification model includes obtaininga plurality of merchant samples, wherein each merchant sample includes historical transaction information and business model type of that merchant; extracting eigenvectors of each merchant sample; themerchant classification model being trained by a machine learning algorithm according to the business model types of several merchant samples and the extracted eigenvectors. A merchant classificationmethod based on the merchant classification model comprises the following steps: acquiring historical transaction information of the merchant to be classified; extracting a feature vector of the merchant to be classified; the extracted feature vector of the merchant to be classified being input to the merchant classification model to predict the business mode type of the merchant to be classified.
Owner:ADVANCED NEW TECH CO LTD
A method and a device for distributing copyright benefits based on a block chain
PendingCN109191289ANon-tamperableExamples cannot be limitedFinanceCryptography processingFinancial transactionChain network
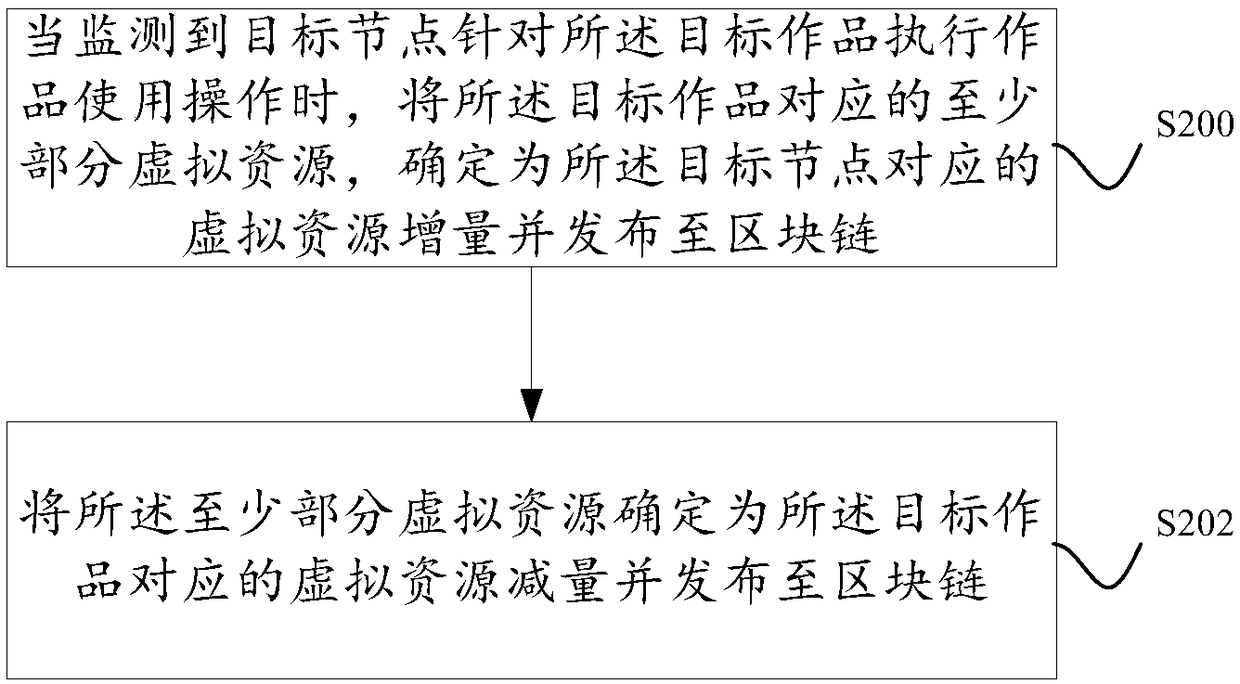
Disclosed are a method and a device for distributing copyright benefits based on a block chain. The block chain network comprises a plurality of service nodes, wherein copyright-related transactions are carried out between the plurality of service nodes through a virtual resource as a transaction medium. When any copyright-related transaction of the target work occurs, a part of the copyright proceeds generated by the copyright-related transaction is taken as the revenue of the publisher of the target work, and the remaining copyright proceeds are reserved as the virtual resources corresponding to the target work for distributing the copyright proceeds to the service nodes using the target work. For a service node using a target work, at least a part of virtual resources corresponding to the target work in the block chain are allocated to the service node through a consensus mechanism in the block chain network, so that the virtual resources corresponding to the service node are increased.
Owner:ADVANCED NEW TECH CO LTD
Method and device for credit evaluation of work publisher based on blockchain
ActiveCN108876560AExamples cannot be limitedCryptography processingOffice automationSoftware engineeringBlockchain
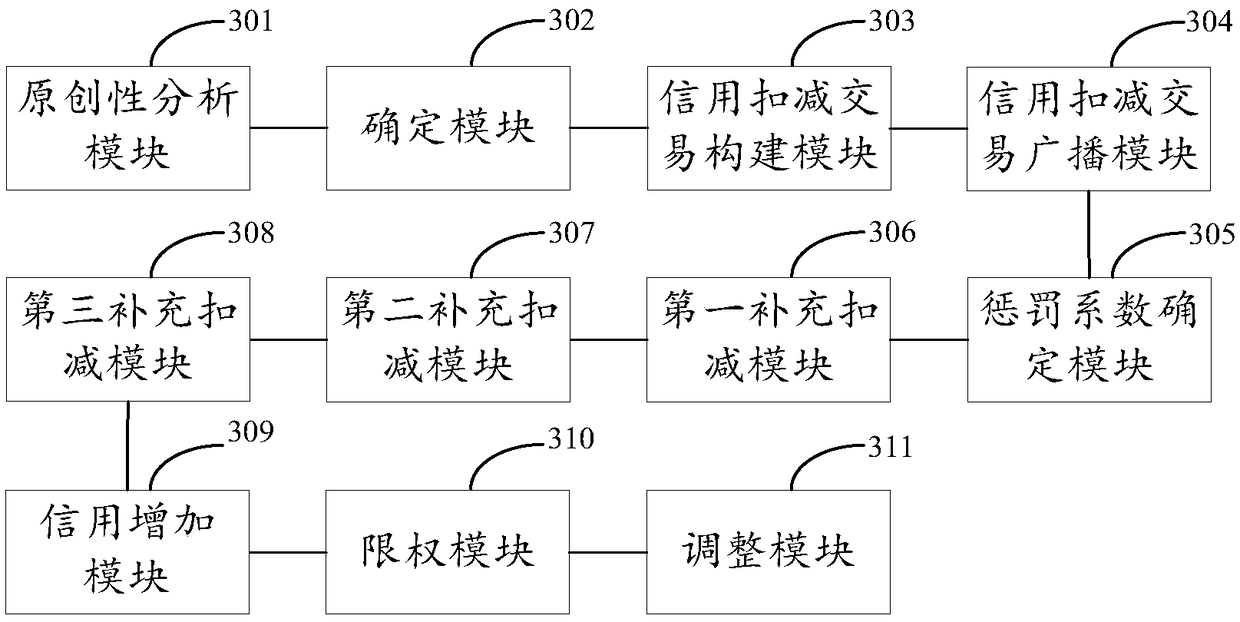
The invention discloses a method and device for the credit evaluation of a work publisher based on blockchain. The method and device can perform the originality analysis of target work published by atarget business node (any one business node) to the blockchain to obtain an originality representation value of the target work. If the originality representation value is lower (indicating that the target work is suspected of plagiarism), the copyright credit score corresponding to the target business node will be reduced, and after the reduced copyright credit score (copyright credit score reduction quantity) of the target business node needs to pass through the common verification of a plurality of business nodes, the reduced copyright credit score (copyright credit score reduction quantity) of the target business node can be publically displayed on the blockchain. The blockchain can publically display the copyright credit score reduction record of the target business node so as to determine the copyright credit score of the target business node according to the copyright credit score reduction record. The lower the copyright credit score of the target business node is, the poorer the credit level of the target business node is.
Owner:ADVANCED NEW TECH CO LTD
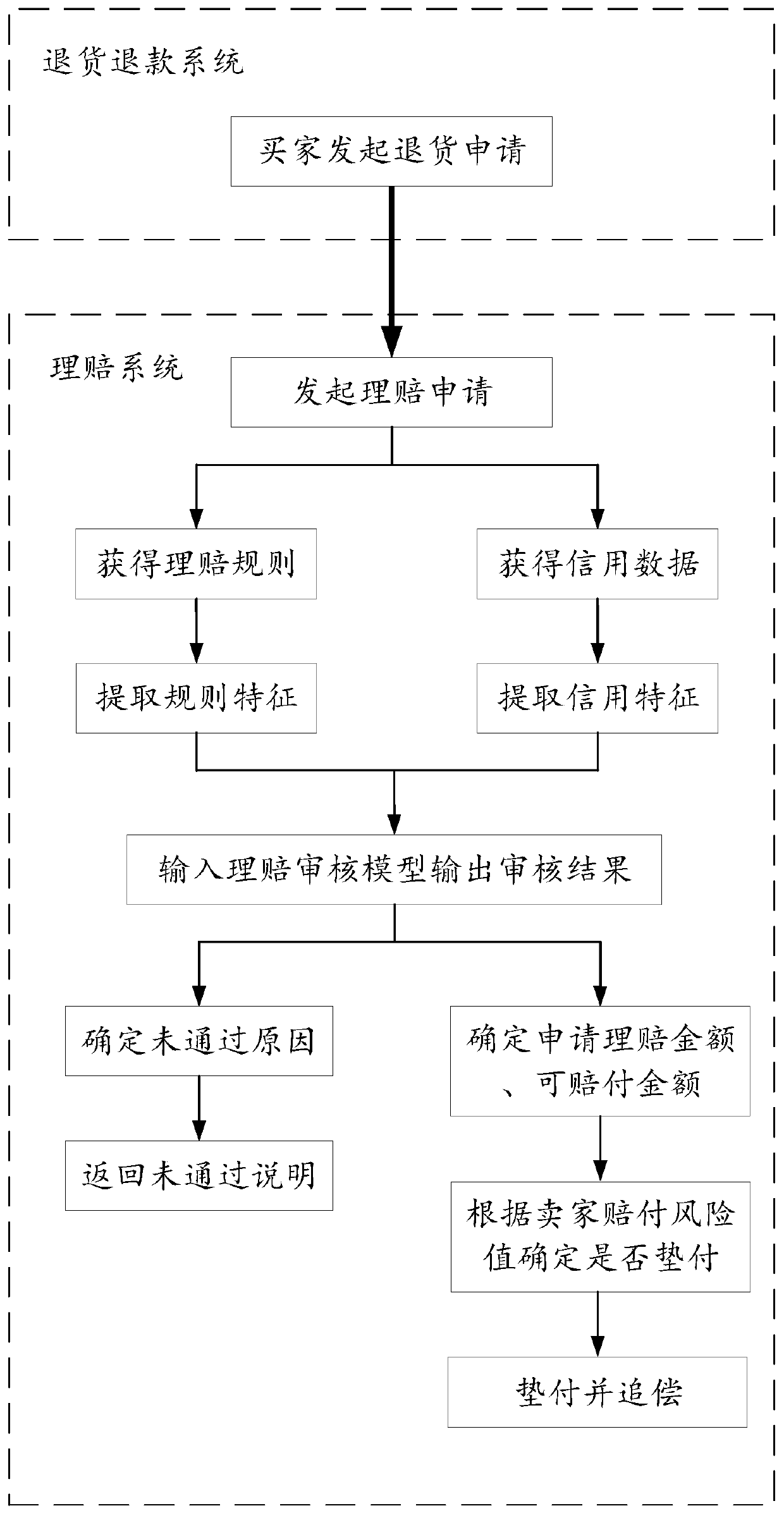
Claim settlement service processing method and device
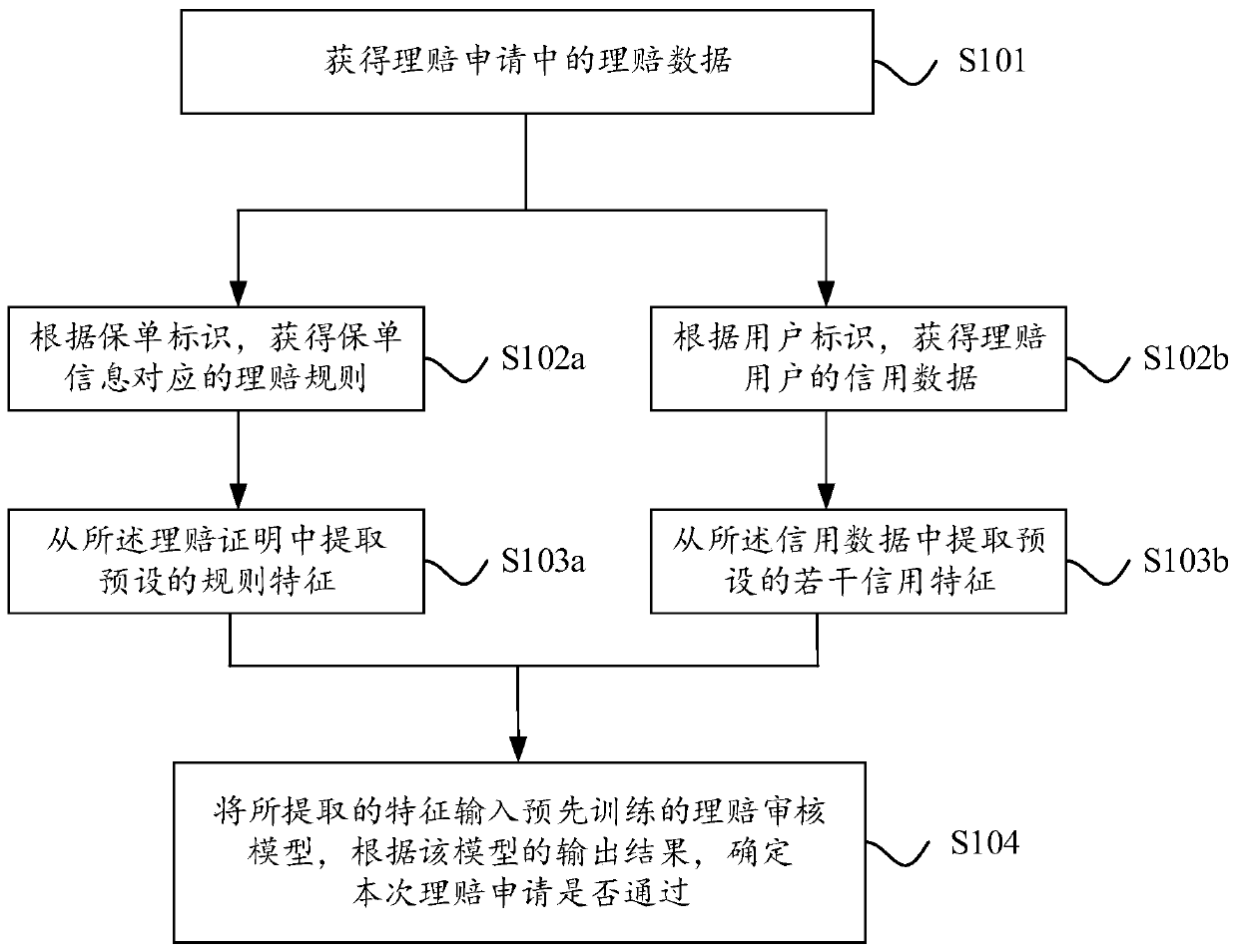
InactiveCN110047007AImprove processing efficiencySave human effortFinanceUser identifierData science
The invention discloses a claim settlement service processing method and device. The claim settlement service processing method comprises the steps of obtaining claim settlement data in a claim settlement application; obtaining a claim settlement rule corresponding to the insurance policy information of the insurance policy needing to be claimed according to the insurance policy identifier; obtaining credit data of a claim settlement user according to the user identifier; determining a plurality of rule features needing to be extracted according to a preset corresponding relation between the claim settlement rule and the rule features, and extracting the rule features from the claim settlement proof; extracting a plurality of preset credit characteristics from the credit data; and inputting the extracted features into a pre-trained claim audit model, and determining whether the claim application is passed or not according to an output result of the model.
Owner:ALIBABA GRP HLDG LTD
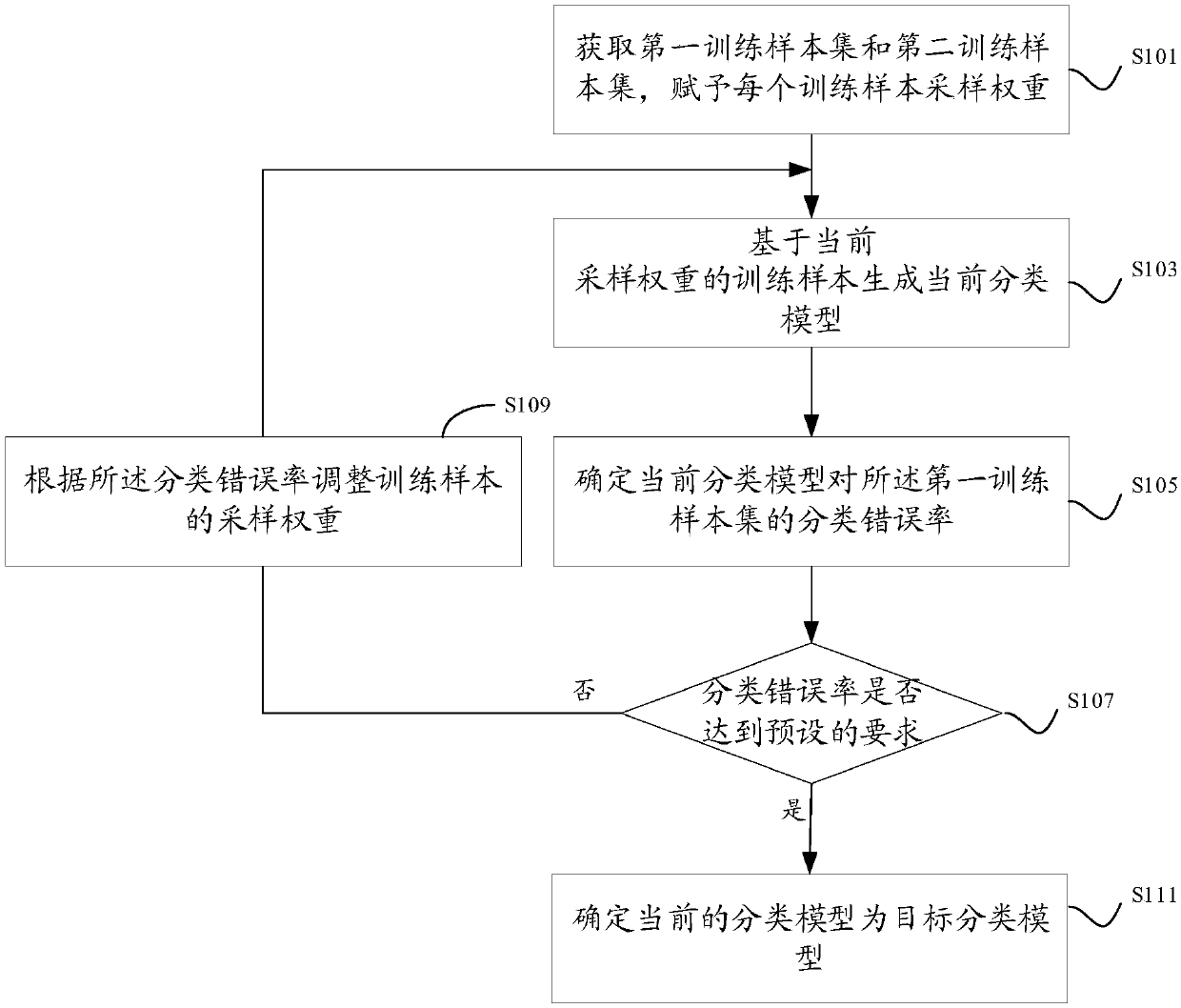
Business risk prevention and control method, device and equipment
ActiveCN109598281AExamples cannot be limitedImprove accuracyCharacter and pattern recognitionResourcesRisk ControlEngineering
The invention discloses a business risk prevention and control method, device and equipment. A first training sample set and a second training sample set are summarized to form a mixed training sampleset, and each training sample is endowed with a corresponding sampling weight. And then corresponding model training is carried on the training sample set to obtain a classification model, and an error recognition rate of the classification to the first training sample is calculated. And then the sampling weights of the first training sample and the second training sample in the training sample set are continuously adjusted based on the error recognition rate, so that a target classification model with certain accuracy on the first training sample can be finally obtained, and accurate risk control defense can be carried out on the first service according to the target classification model.
Owner:ADVANCED NEW TECH CO LTD
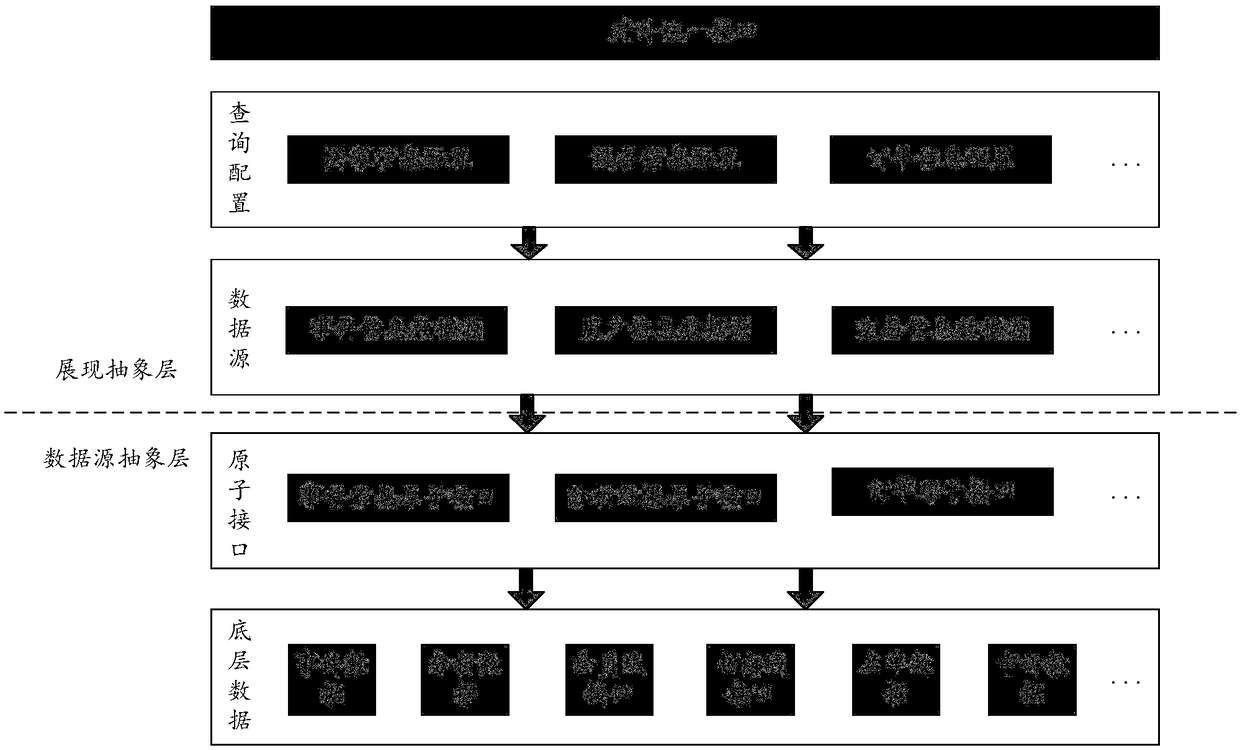
Page display method and system
PendingCN110020388AFlexible layoutExamples cannot be limitedWebsite content managementSpecial data processing applicationsClient-sideDatabase
The invention discloses a page display method and device. The page display method comprises the following steps that: after receiving a page display operation trigger, a client determines a page display demand corresponding to the operation; the client generates a page request including the page display requirement and sends the page request to the server; after receiving the page request sent bythe client, the server side obtains a page display demand in the page request; the server determines page layout information corresponding to the page display requirement according to a preset corresponding relation, and returns the page layout information to the client; and after receiving the page layout information returned by the server, the client performs layout on the page components included in the information according to the layout relation included in the information to obtain a page, and displays the obtained page.
Owner:ADVANCED NEW TECH CO LTD
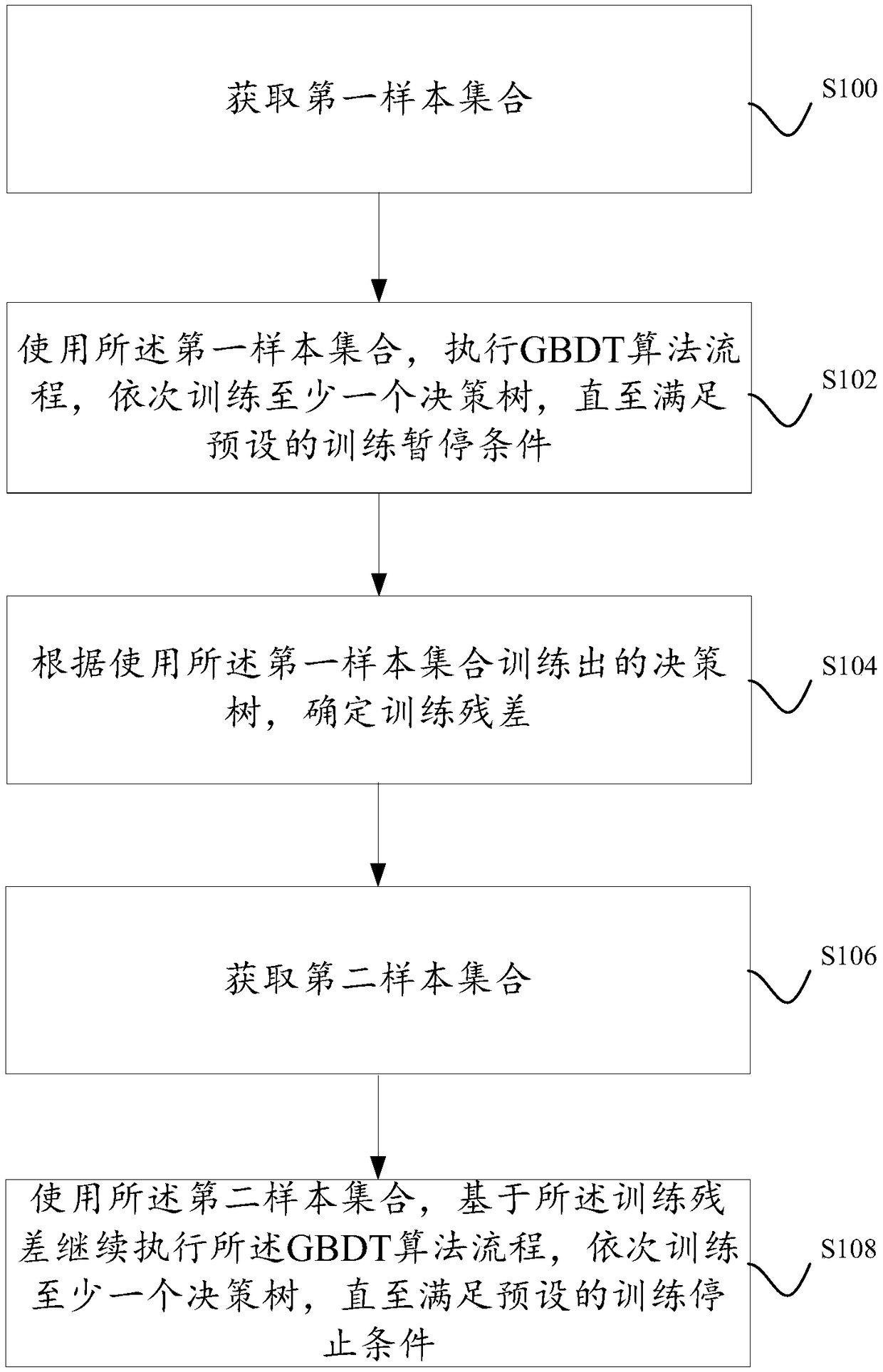
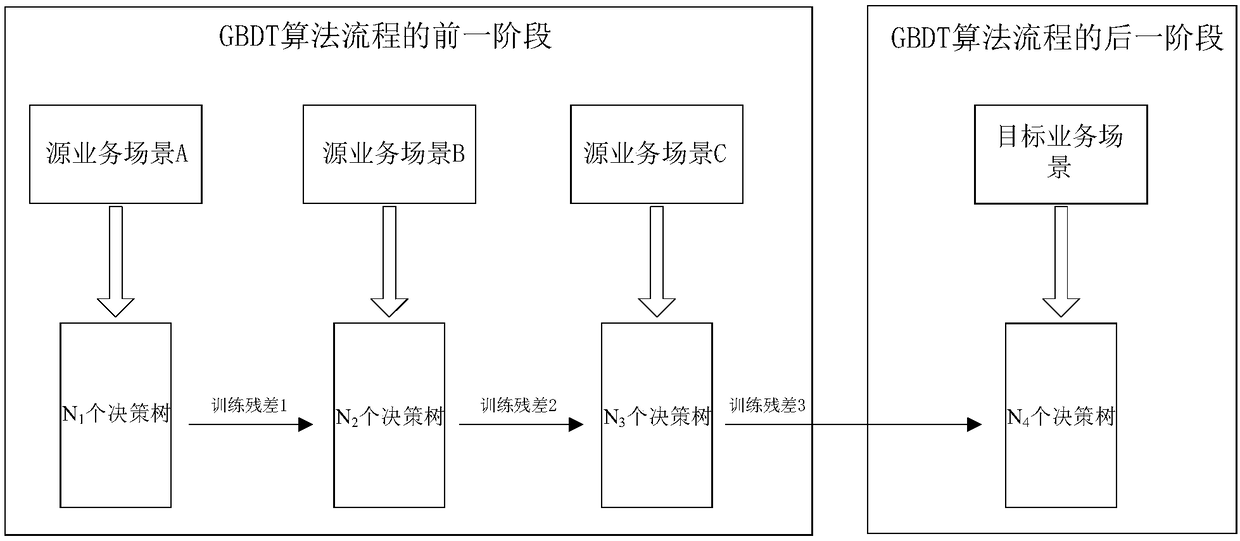
A method and apparatus for training a model based on a gradient lifting decision tree
InactiveCN109472296AThe effect is qualifiedExamples cannot be limitedEnsemble learningKernel methodsAlgorithmData domain
The invention discloses a model training method and a device based on a gradient lifting decision tree. A GBDT algorithm is divided into two phases. In the former phase, several decision trees are trained by obtaining labeled samples from the data domain of the business scenarios similar to the target business scenarios, and the training residuals generated after the training in the previous phaseare determined. At a later stage, that annotated sample are obtained from the data domain of the target business scenario, and a number of decision trees are continue to be trained based on the training residuals. Finally, the model applied to the target business scenario is actually integrated from the decision tree trained in the previous stage and the decision tree trained in the next stage.
Owner:ADVANCED NEW TECH CO LTD
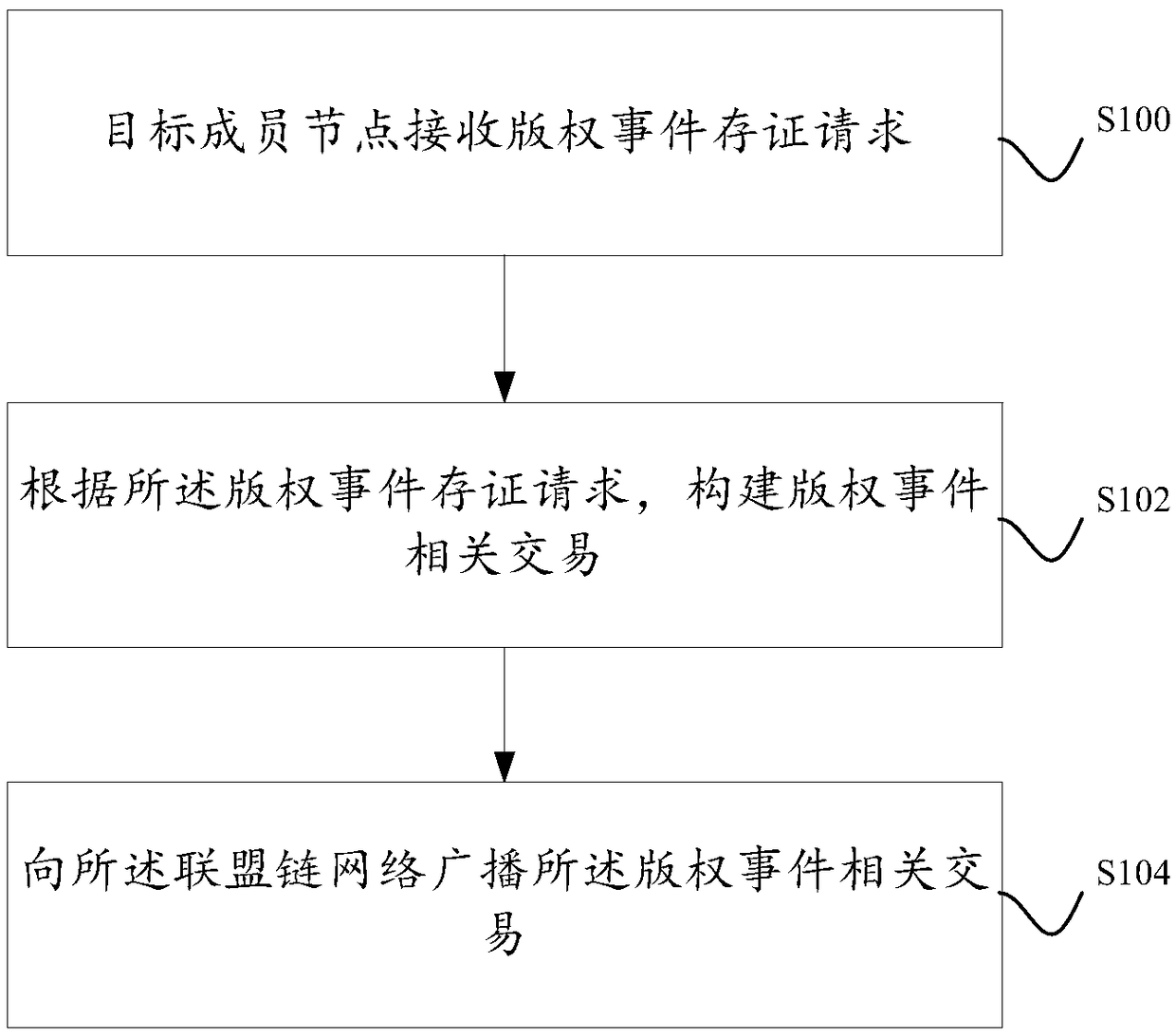
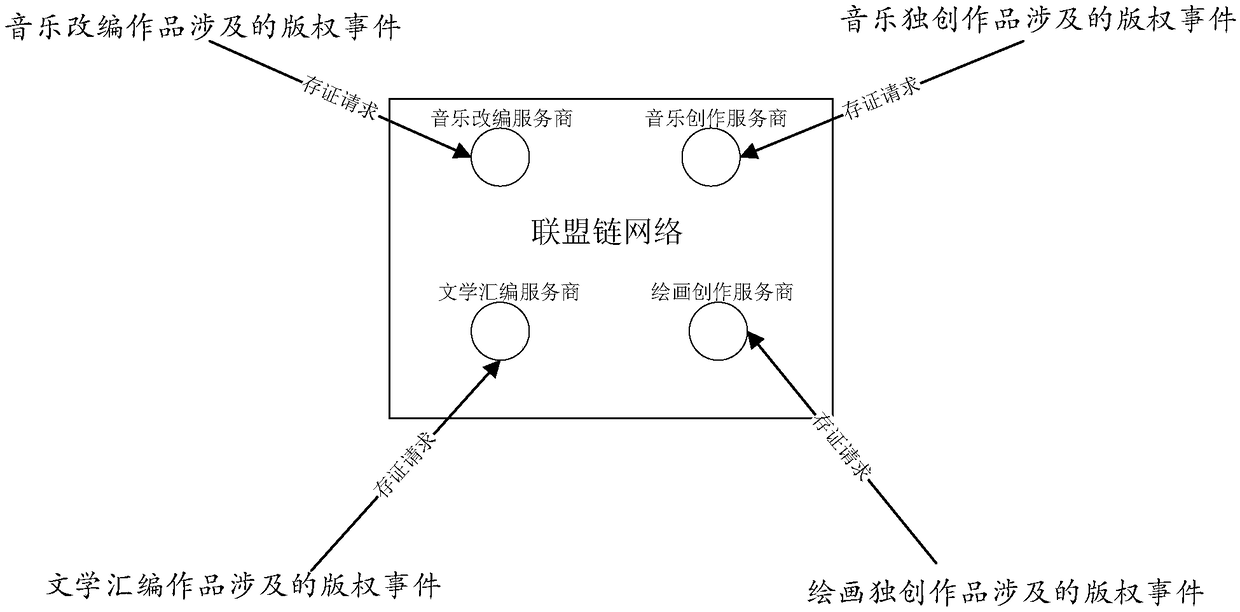
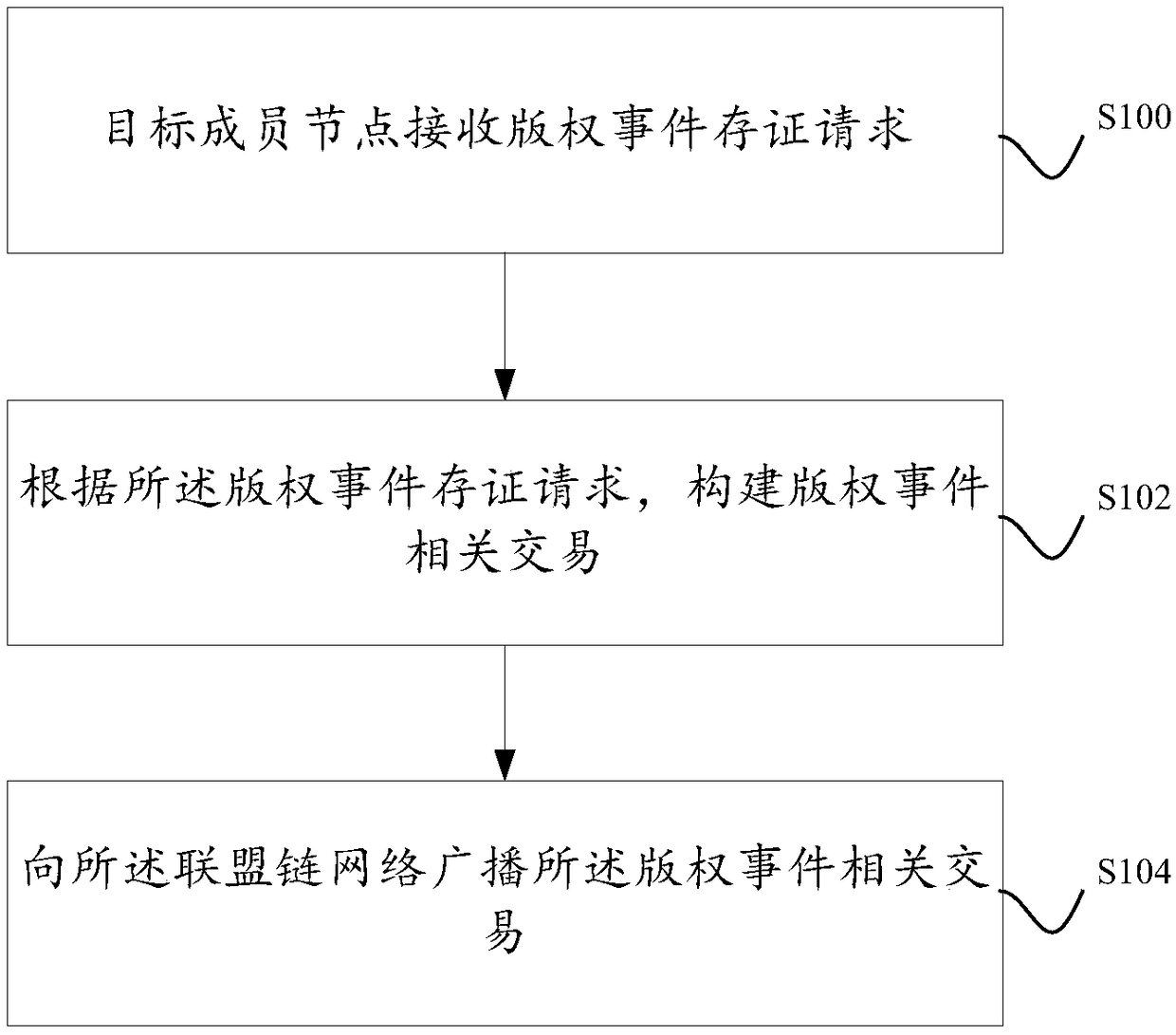
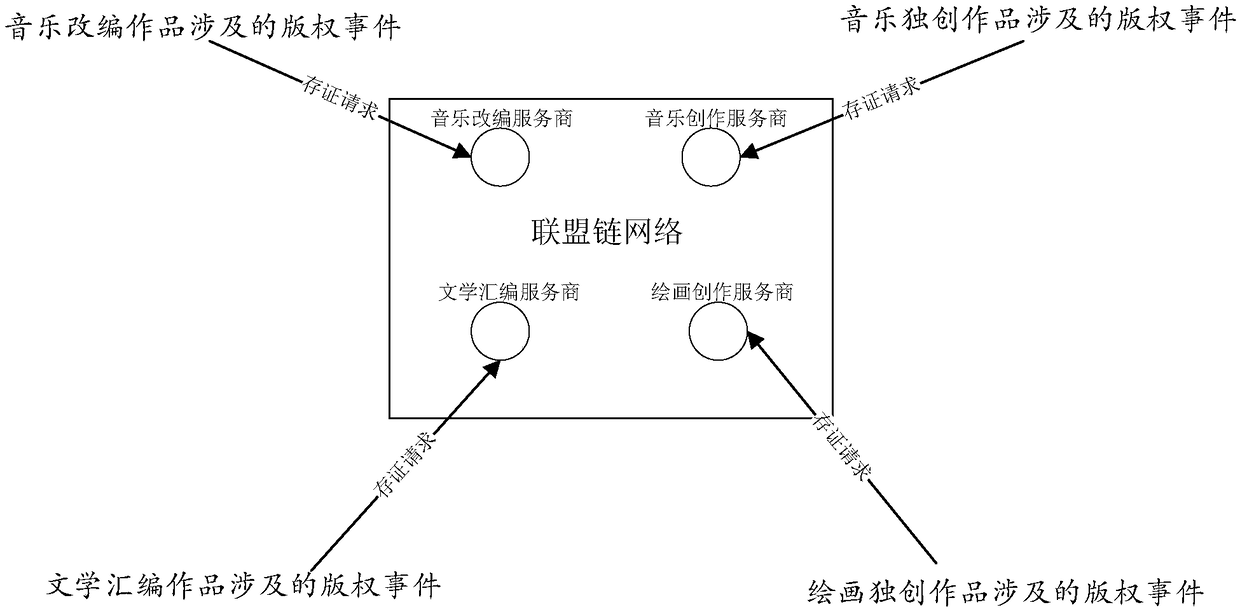
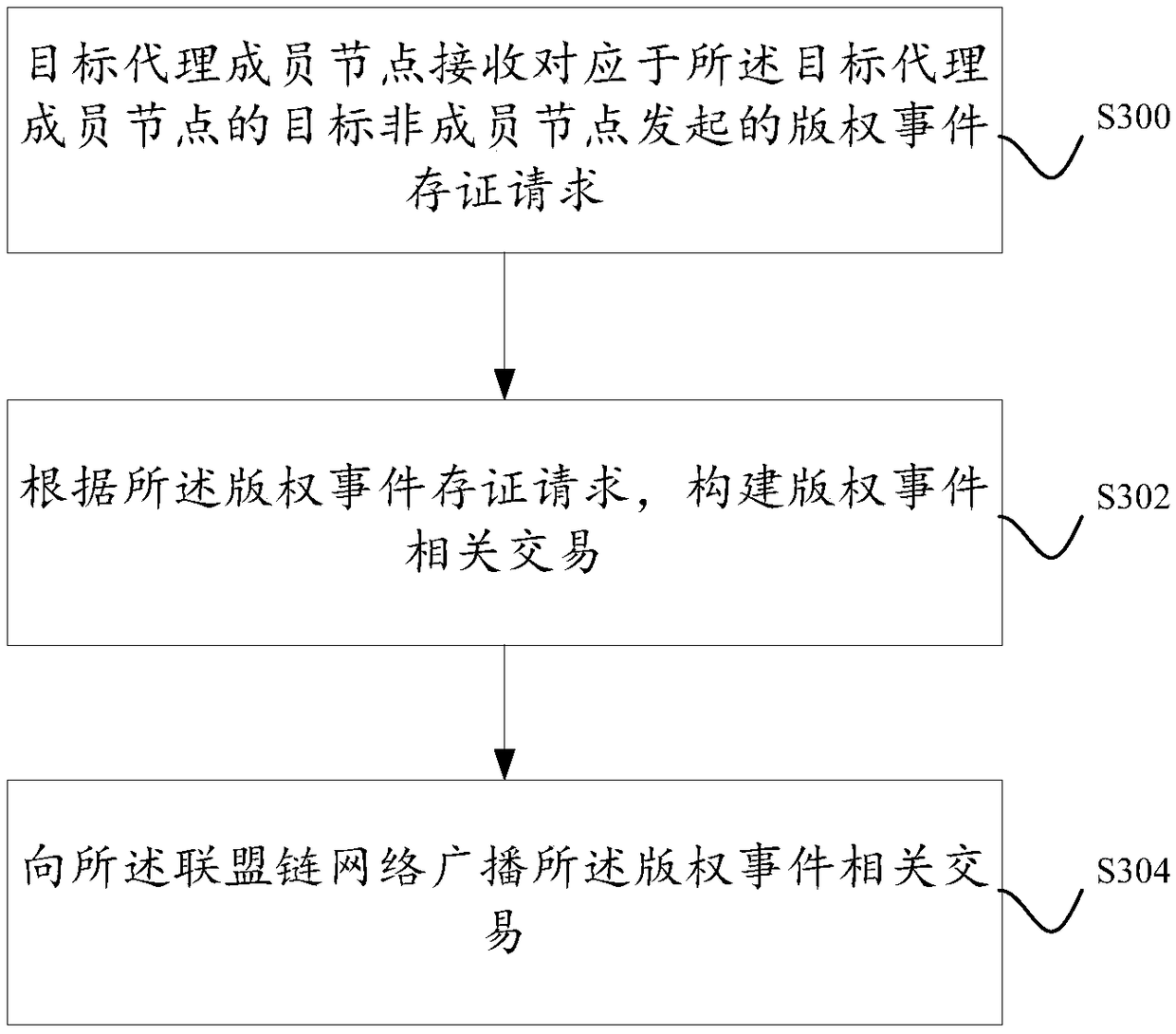
A method and system for storing copyright event authentication based on block chain
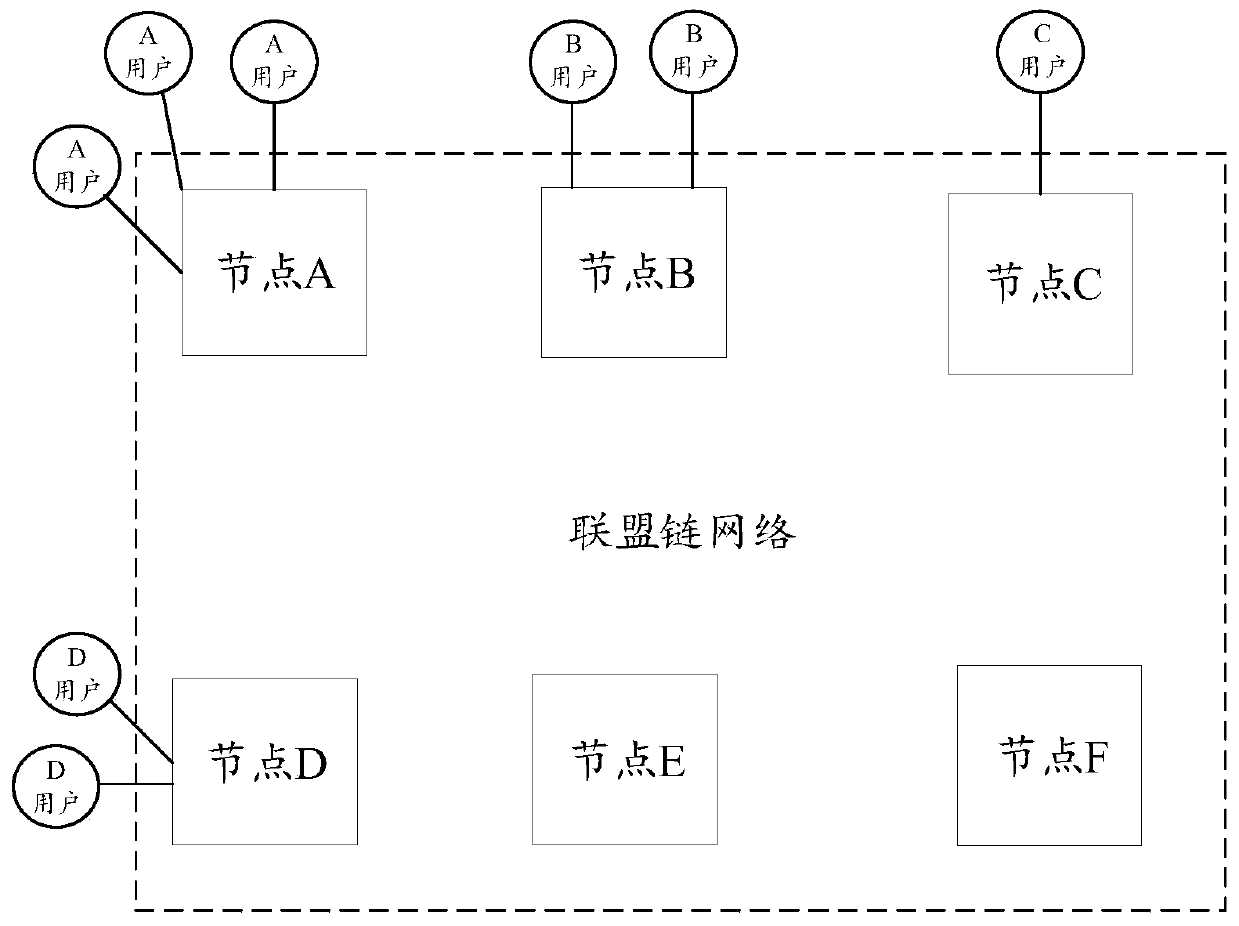
ActiveCN109274667AGuaranteed safe and reliableExamples cannot be limitedFinanceDatabase distribution/replicationChain networkAuthentication
The invention discloses a method and a system for storing copyright event based on a block chain. The devices of some works service providers that operate works-related services can be used as membernodes to form a federation chain network, and each works service provider broadcasts copyright events generated based on its own works-related services to the federation chain network, and each worksservice provider performs distributed certification based on the block chain.
Owner:ADVANCED NEW TECH CO LTD
Blockchain transaction query method and system
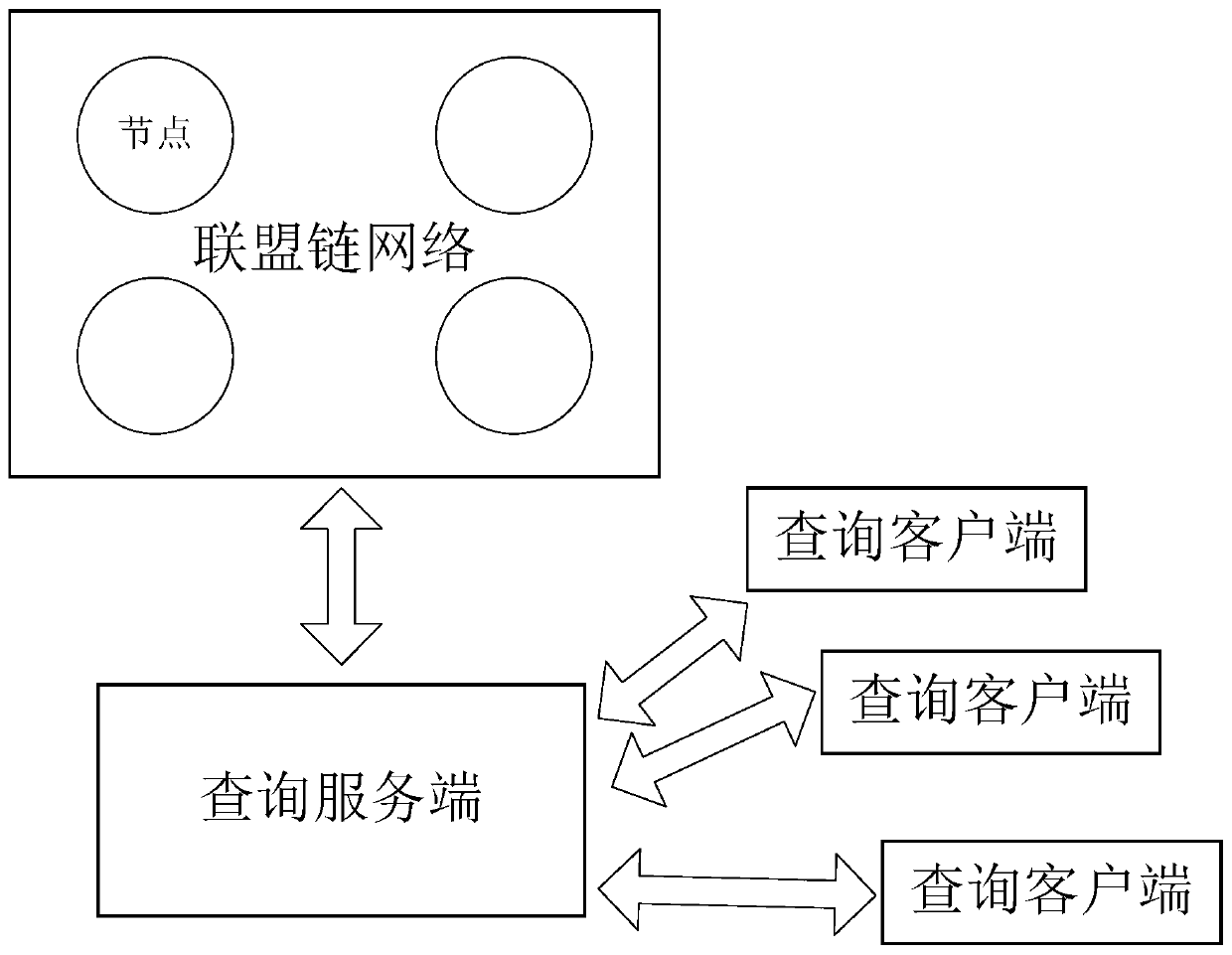
InactiveCN110569281AExamples cannot be limitedDatabase distribution/replicationPayment protocolsClient-sideChain network
The invention discloses a blockchain transaction query method and system. A centralized query server-query client architecture is introduced. A query server is in butt joint with an alliance chain network. A corresponding query service interface is created for each block chain transaction stored in an alliance chain network, and the query service interface corresponding to each block chain transaction is exposed to a query client. A user inquires the blockchain transaction in a mode of calling the inquiry service interface through the inquiry client.
Owner:ADVANCED NEW TECH CO LTD
Method, system, device and equipment for verifying credibility of alliance chain
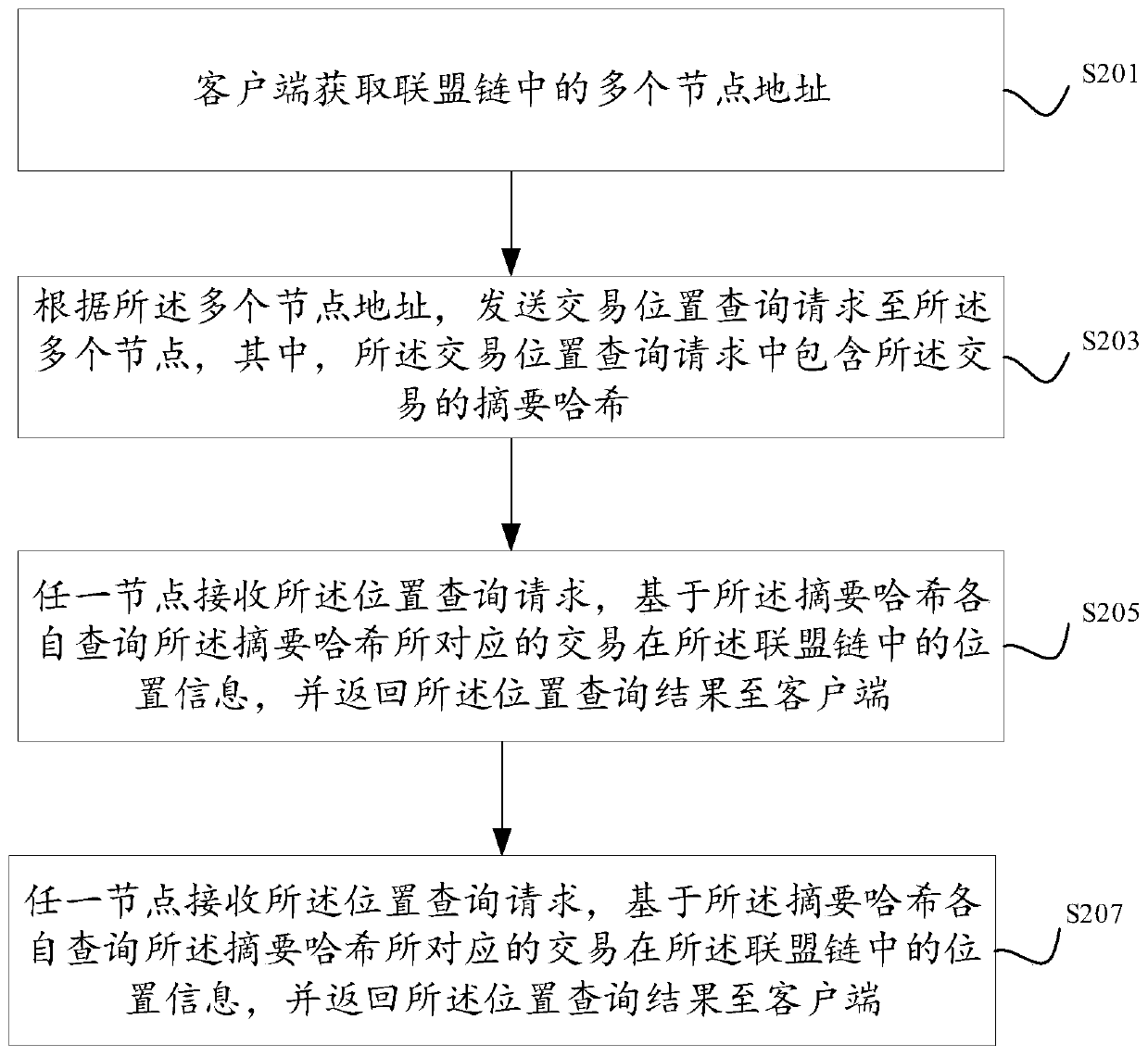
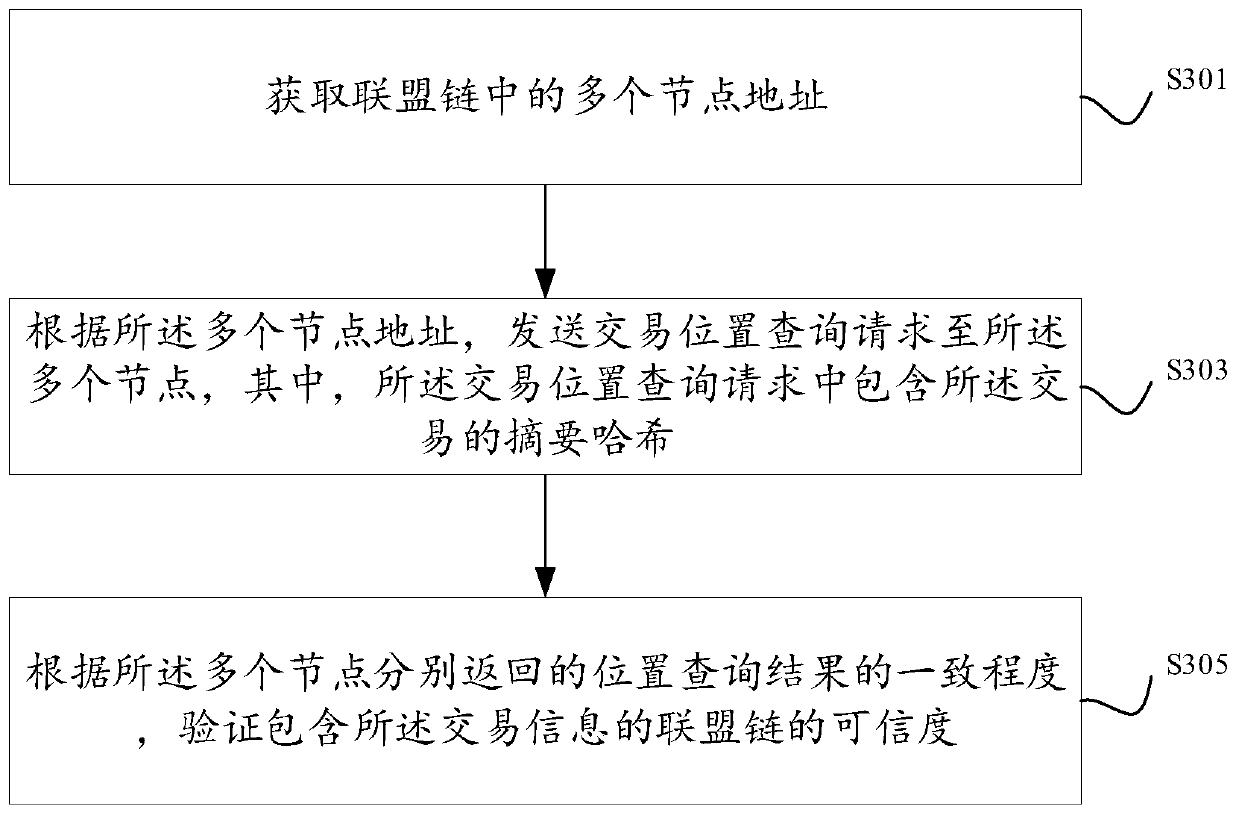
ActiveCN110049087AImprove experienceExamples cannot be limitedFinanceTransmissionProgramming languageButt joint
The invention discloses a method, system, device and equipment for verifying the credibility of an alliance chain. After a client completes transaction on-chain storage through a butt joint node, forthe transaction, the client initiates a transaction position query request to a plurality of nodes in an alliance chain for the transaction, so that respective query results of the plurality of nodesfor the transaction can be obtained. Furthermore, the credibility of the alliance chain can be verified based on the consistency degree of the position query results of the multiple nodes, and the user experience is improved.
Owner:ADVANCED NEW TECH CO LTD
Car-hailing information display method, device, system and equipment
InactiveCN109993329AGood choiceImprove ride-hailing experienceReservationsBuying/selling/leasing transactionsClient-sideServer-side
The invention discloses a car-hailing information display method, device, system and equipment. In the scheme provided by the embodiment of the invention, a first type of user route information is transmitted to a server side, and the server side matches the first type of user route information with a second type of user route information, screens out a batch of second type of user route information containing the matching degree and sends the second type of user route information to a client side. And the client sorts the second type of user schedules according to the matching degrees, performs descending order arrangement when the second type of user schedules are displayed, and displays the matching degrees.
Owner:ALIBABA GRP HLDG LTD
A method and a system for collecting evidence based on block chain storage
InactiveCN109376552ARealize multi-party depositHave the force of lawMathematical modelsDatabase updatingChain networkUser equipment
The invention discloses a method and a system for collecting evidence based on block chain storage. The user (party) may operate the user equipment, records his behavior and / or voice as a multimedia file, Then, the user equipment sends the multimedia file to the service equipment, and the service equipment builds the target transaction based on the multimedia file, broadcasts the target transaction to the block chain network, and each node in the block chain network publishes the target transaction to the block chain based on the consensus mechanism. Thus, the multi-party storage of the multimedia file is realized.
Owner:ADVANCED NEW TECH CO LTD
Replacing operation method and device after model update and business server
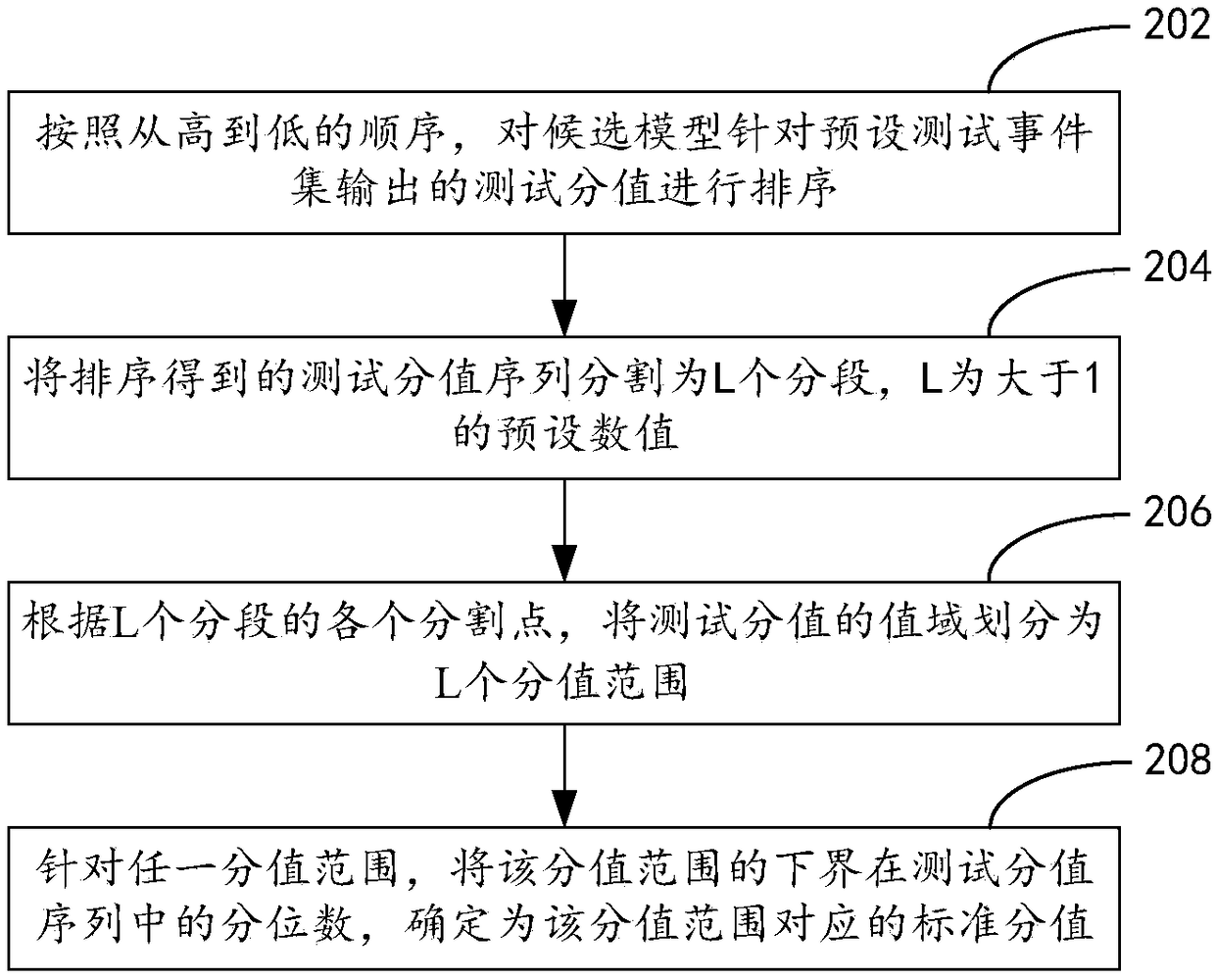
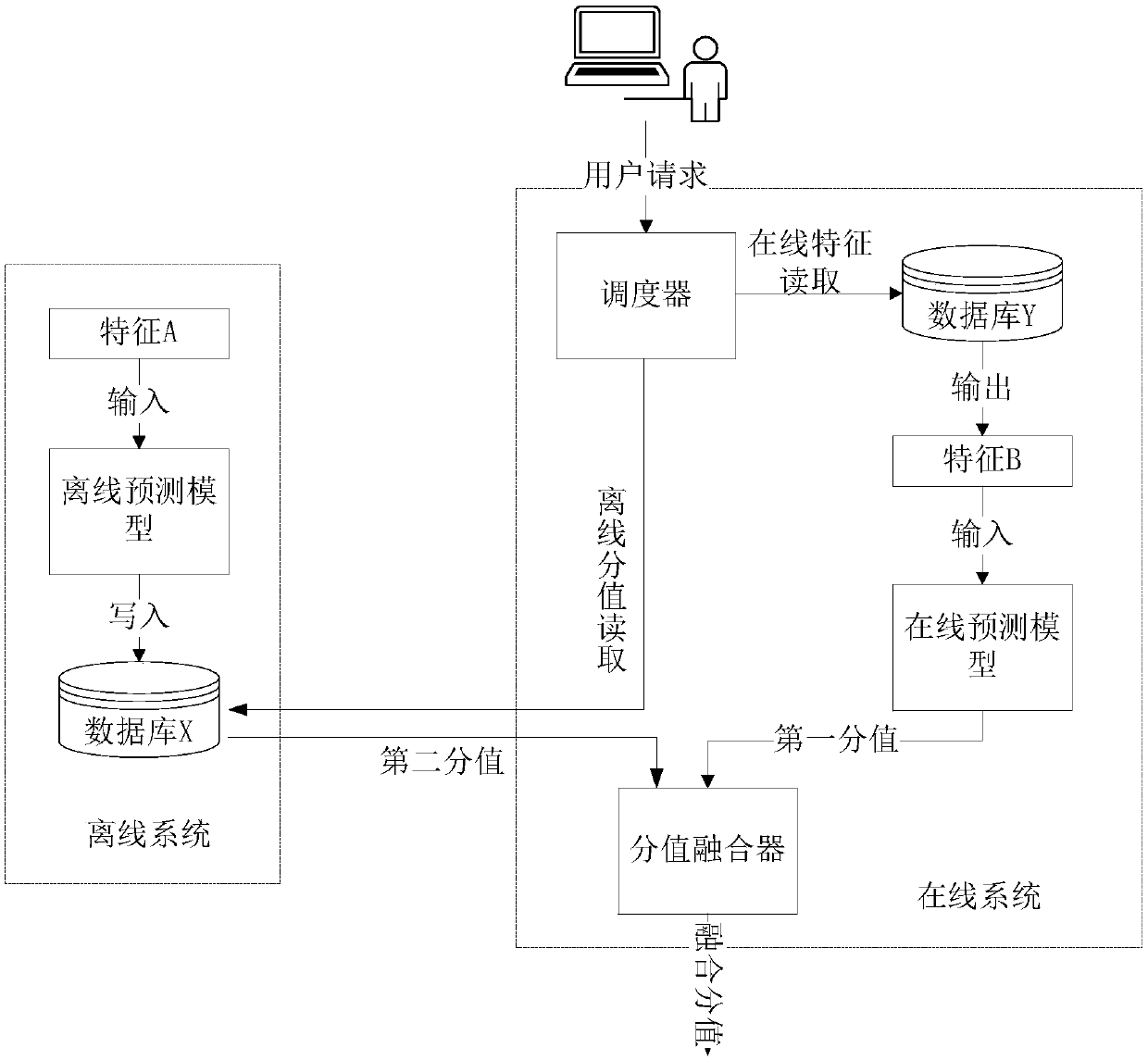
The invention discloses a replacing operation method and device after model update and a business server. The method comprise that comprehensive properties of different updated models are compared; the updated model with the optimal comprehensive property is determined to be a candidate model; performance of the candidate model is compared with that of a present online operation model in a specific risk threshold, the performance of the candidate model or the present online operation model in the specific risk threshold is determined according to a standard score corresponding the a score output by a specific online event set as well as an auditing result for the specific online event set obtained according to the standard score and the specific risk threshold, and the specific risk threshold is determined according to a preset model strategy; if the comparison result shows that the performance of the candidate model is higher than that of the present online operation model, the candidate model is disposed as the online operation model.
Owner:ADVANCED NEW TECH CO LTD
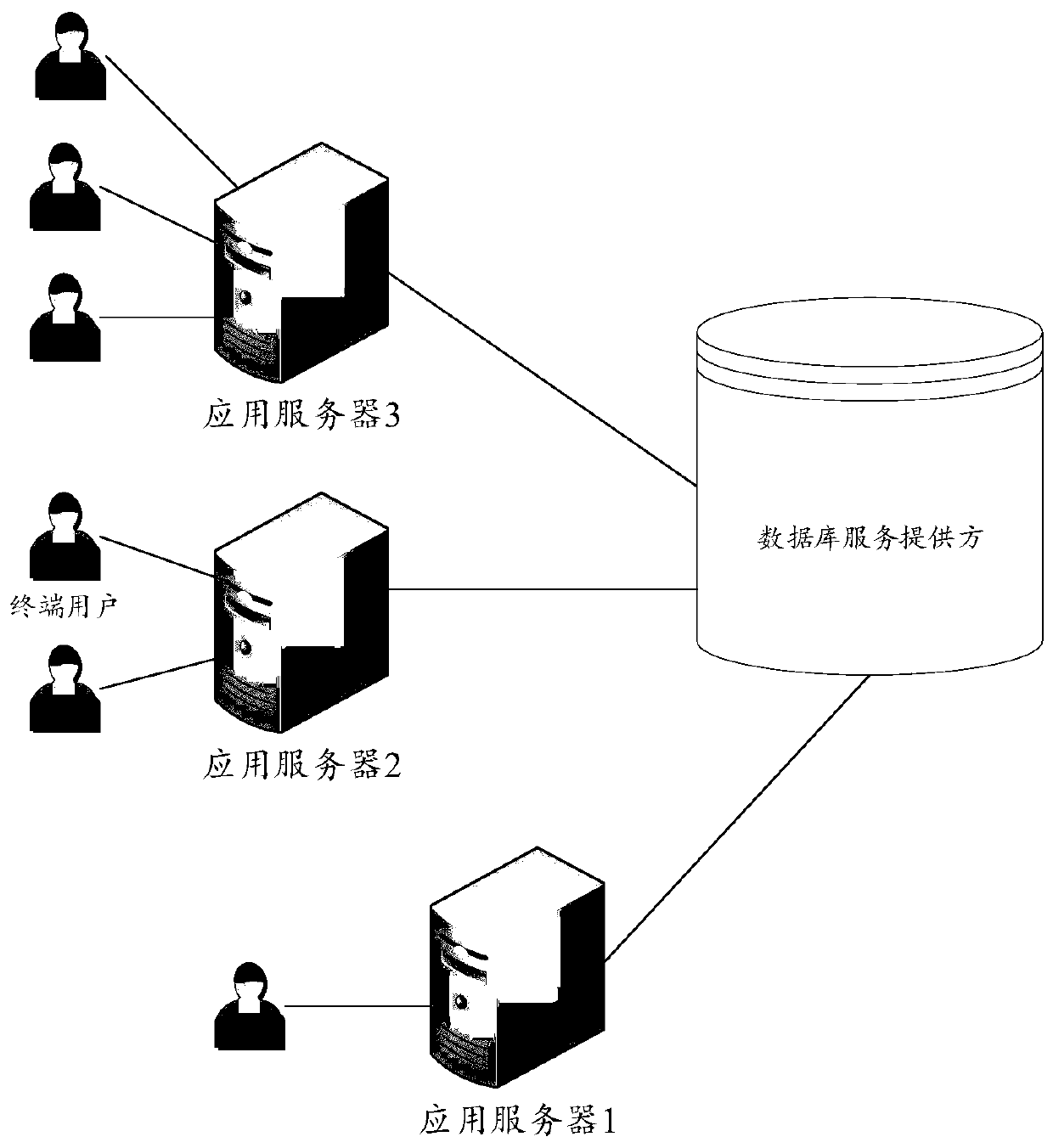
Data inquiry method, device and service server for integrating multiple data sources
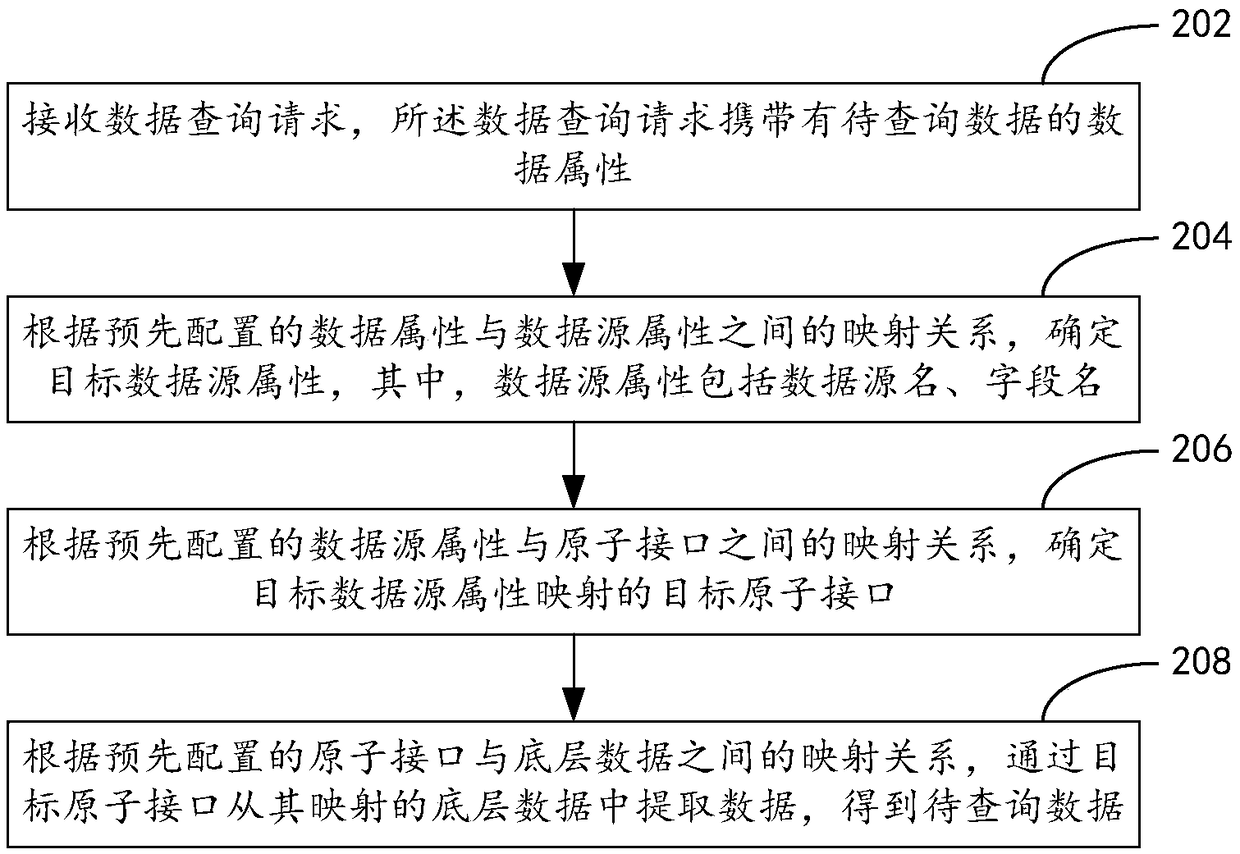
ActiveCN109145025AImprove query efficiencyImprove work efficiencyDatabase management systemsSpecial data processing applicationsData sourceData mining
The invention discloses a data inquiry method, a device and a service server integrated with multiple data sources. The method comprises the following steps: receiving a data inquiry request, whereinthe data inquiry request carries data attributes of data to be inquired; determining a target data source attribute according to a mapping relationship between a pre-configured data attribute and a data source attribute, wherein the data source attribute comprises a data source name and a field name; determining a target atomic interface of the target data source attribute mapping according to a pre-configured mapping relationship between the data source attribute and the atomic interface; according to the mapping relationship between the pre-configured atomic interface and the underlying data, the data being extracted from the underlying data mapped by the target atomic interface to obtain the data to be queried.
Owner:ADVANCED NEW TECH CO LTD
Third party authorized login method and system
InactiveCN108632291AImprove experienceEasy to operateTransmissionSensing by electromagnetic radiationThird partyInternet privacy
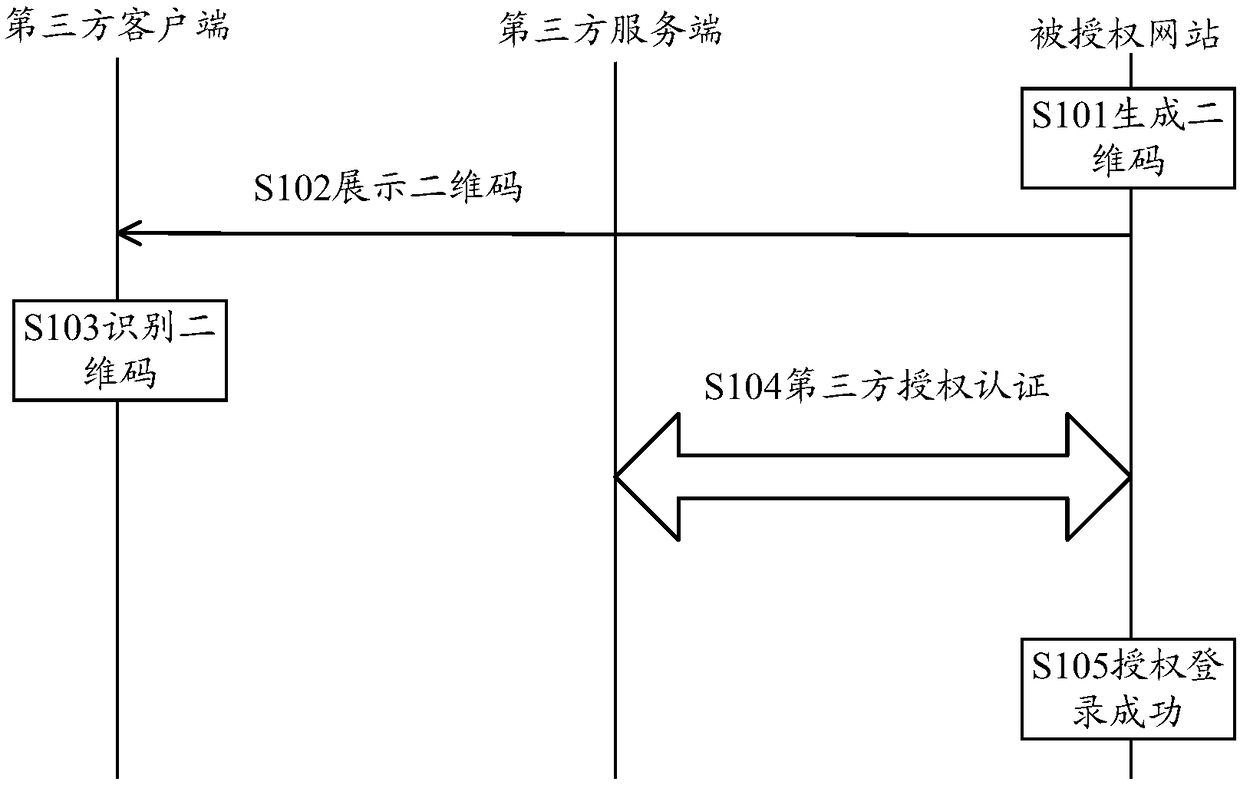
The invention discloses a third party authorized login method. The method comprises the following steps: when an authorized website detects that a login operation of a third party account of a user istriggered, the authorized website generates a two-dimensional code corresponding to the third party account; the authorized website displays the two-dimensional code to the user; when a third party client monitors that a two-dimensional code scanning operation of the user is triggered, the third party client identifies the two-dimensional code and prompts the user for authorization or not; when the third party client monitors that an authorization confirmation operation of the user is triggered, a third party server performs third party authorization authentication with the authorized website; and after the third party authorization authentication between the third party server and the authorized website is passed, the third party authorized login of the authorized website is successful.
Owner:ADVANCED NEW TECH CO LTD
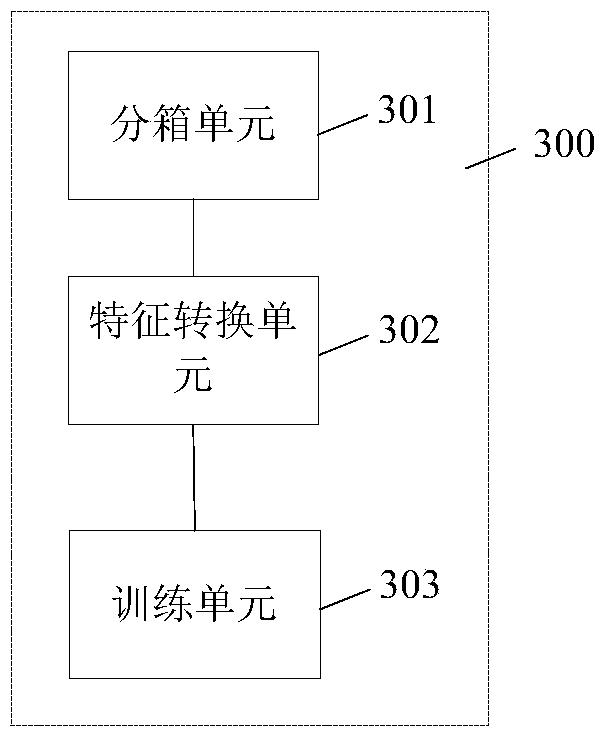
Method, apparatus and device for merging model prediction values
InactiveCN108052979AImprove accuracyReduce latencyCharacter and pattern recognitionData miningAlgorithm
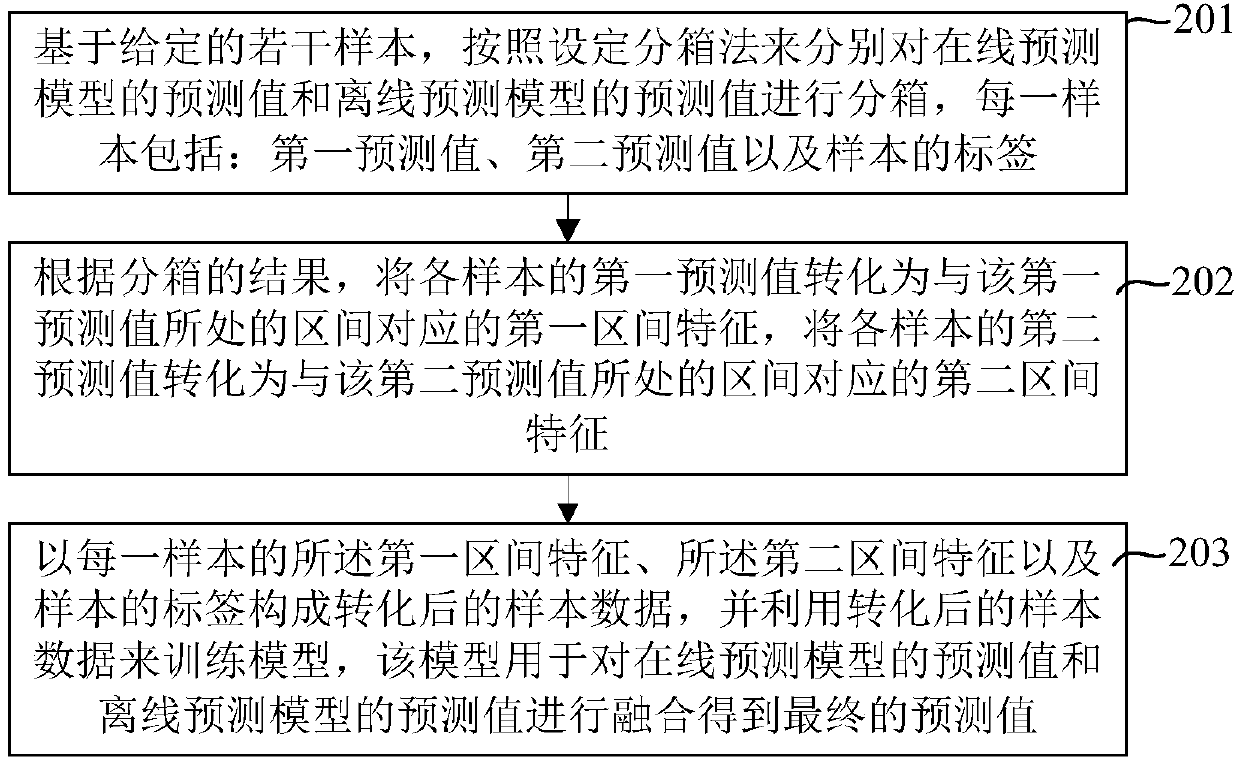
A method, an apparatus, and a device for merging model prediction values are disclosed. The method for merging model prediction values comprises: based on a given number of samples, binning a prediction value of an online prediction model and a prediction value of an off-line prediction model respectively according to a set binning method; according to a binning result, converting the first prediction value of each sample into a first interval feature corresponding to the interval in which the first prediction value is located, and converting the second prediction value of each sample into a second interval feature corresponding to the interval in which the second prediction value is located; and taking the first interval feature, the second interval feature and a sample tag correspondingto each sample to form converted sample data, and using the converted sample data to train the model, wherein the trained model is used to merge the prediction value of the online prediction model andthe prediction value of the off-line prediction model to obtain a final prediction value.
Owner:ADVANCED NEW TECH CO LTD
Method and device for map construction of robot based on semantics
ActiveCN108897836AAccurate observationReduce in quantityInstruments for road network navigationSpecial data processing applicationsAlgorithmSemantics
The embodiment of the invention provides a method for map construction of a robot based on semantics. Firstly, N particle samples are obtained after last resampling, according to pose information of the robot at the t-1 moment and a probabilistic motion model of the robot, pose information of N particles at the t moment is estimated, wherein each particle corresponds to a possible trajectory of the robot; in semantic scanning data at the t moment, K semantic points corresponding to each particle in the N particles in different poses are acquired, a weight of each semantic point at the t momentis calculated, according to the weights of the K semantic points, a weight of each particle at the t moment is calculated, and the semantic scanning data at least comprises data with object probability labels; the particle with the largest weight in the N particles is acquired, and according to the semantic scanning data corresponding to the particle with the largest weight, a semantic map is constructed.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
A slow attack detection method and apparatus
ActiveCN109040140AReduce false alarm rateLow attack valueTransmissionComputer securityEigenvalue computation
A slow attack detection method and apparatus are disclosed. The slow attack detection method is characterized in that the method comprises: determining a preset attack characteristic for calculating an attack value according to a preset attack value calculation rule; Determining values of each preset attack characteristic in the received message, and calculating an attack value of the message according to the characteristic value; Comparing whether the calculated attack value is greater than the preset attack threshold; Determining the the message is a slow attack message when the calculated attack value is greater than a preset attack threshold value, and calculating a new attack threshold value; wherein the new attack threshold is used for subsequent slow attack detection, and the new attack threshold is not greater than the old attack threshold.
Owner:杭州迪普信息技术有限公司
Model operation method, device, and service server
ActiveCN109242135AAutomate operationsImprove operational efficiencyForecastingResourcesPerformance indexOperating model
The invention discloses a model operation method, a device and a service server. The method comprises the following steps: in any preset model operation cycle, the following steps are executed: obtaining a prediction result output by the current running model for the preset test event set, and carrying out statistics on the prediction result to obtain at least one performance index value; obtaining at least one quantitative index value of a model independent variable of the current operating model; determining whether the current operating model is abnormal according to the at least one performance index value and the at least one quantitative index value; when it is determined that the current running model is abnormal, updating the current running model according to a preset set of optimization training events; comparing the performance of the updated model with that of the current running model, and if the performance of the updated model is superior to that of the current running model, deploying the updated model as an on-line running model.
Owner:ADVANCED NEW TECH CO LTD
A dual trading method and system based on centralization and decentralization
PendingCN109242483AQuick confirmationCause inconvenienceProtocol authorisationChain networkOperating system
The invention discloses a dual trading method and system based on centralization and decentralization. In embodiment of that present specification, when the designated member node receives the transaction request, on the one hand, the transaction feasibility verification is carried out for the transaction request, and after the verification is passed, the designated resource amount is subtracted from the virtual resource account corresponding to the expense user identification, and the designated resource amount is increased to the virtual resource account corresponding to the revenue user identification; on the other hand, according to the transaction request, the target transaction information is broadcast to the block chain network, so that after the block chain network performs transaction feasibility verification on the target transaction information, each member node publishes the target transaction information to the block chain based on a consensus mechanism.
Owner:ADVANCED NEW TECH CO LTD
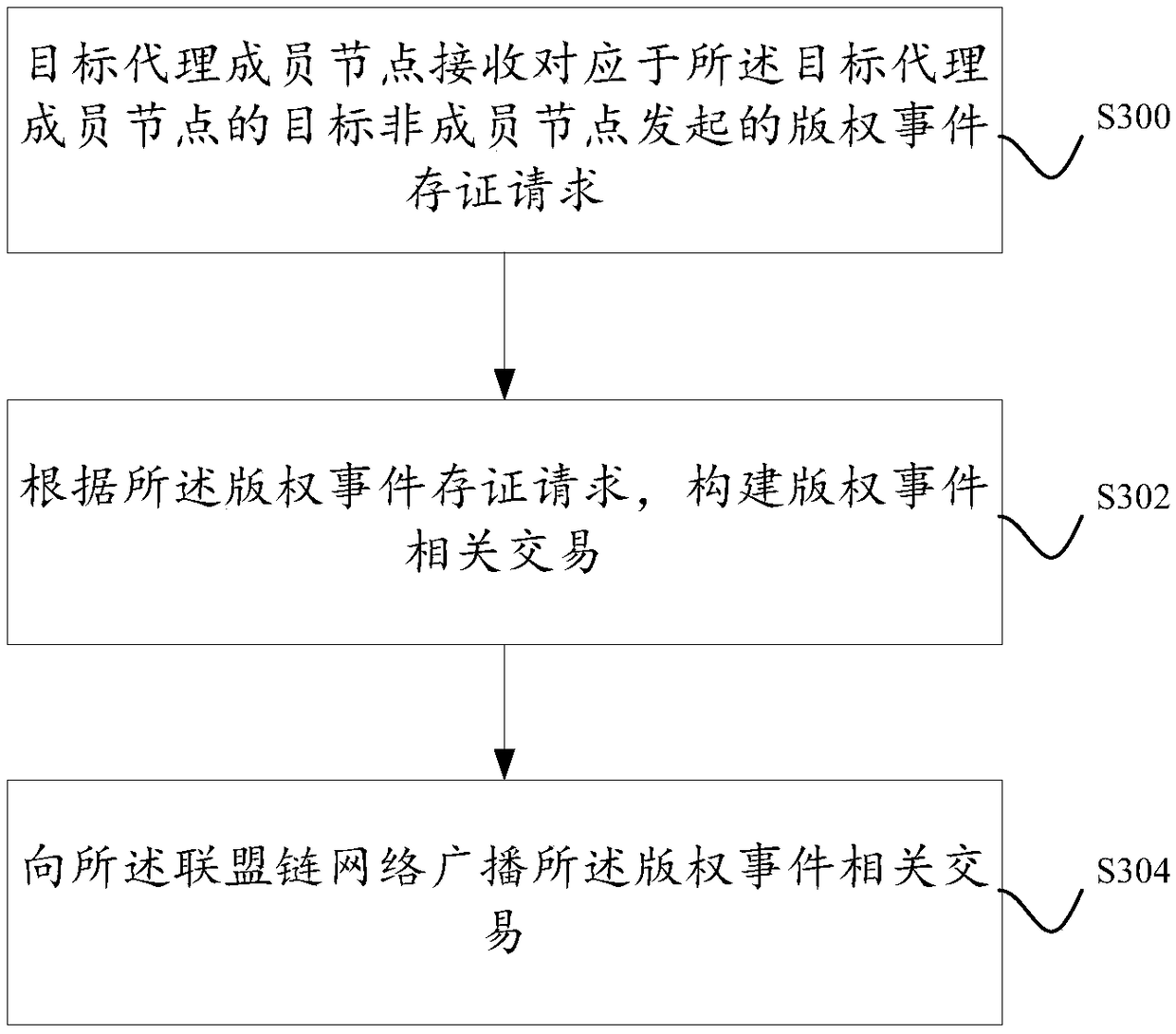
A block chain-based copyright event broker authentication method and system
ActiveCN109272385AGuaranteed safe and reliableExamples cannot be limitedOffice automationBuying/selling/leasing transactionsChain networkAuthentication
Disclosed are a block chain-based copyright event broker authentication method and system. The equipments of some works service providers that operate works-related services can be used as member nodes to form a federation chain network, and each works service provider broadcasts copyright events generated based on its own works-related services to the federation chain network, and each works service provider performs distributed certification based on the block chain. In addition, at least one proxy member node exists in each member node, and for each proxy member node, the proxy member nodehas the right to proxy non-member nodes corresponding to the proxy member node for copyright event certification.
Owner:ADVANCED NEW TECH CO LTD
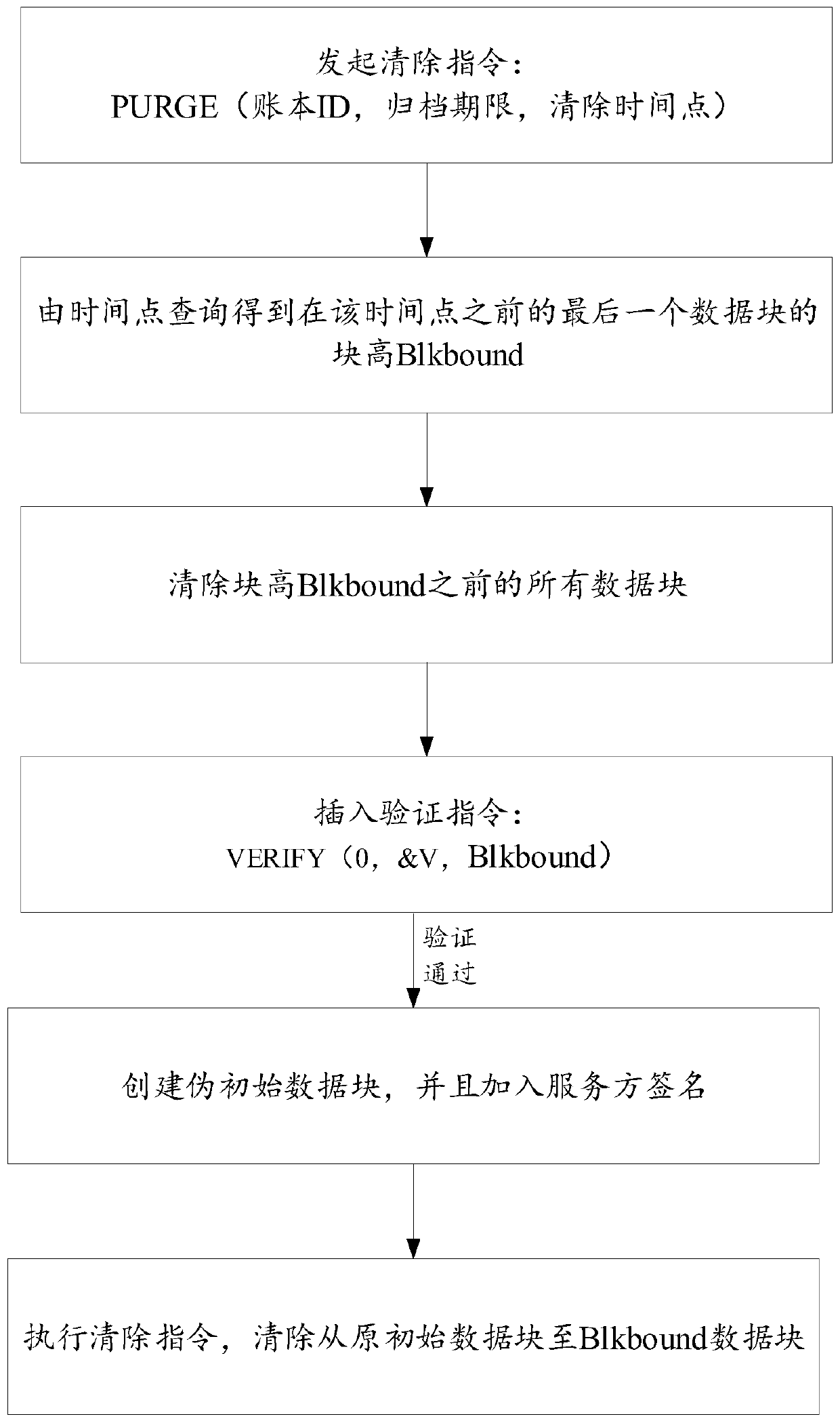
Method, device and equipment for creating block height in chain account book
ActiveCN110061843AEasy to createExamples cannot be limitedUser identity/authority verificationTimestampComputer science
The invention discloses a method, a device and equipment for creating block height in a chain account book. Through converting a block timestamp of a data block into large integer data, the large integer data monotonically increases, and the large integer is used as the block height of the data block. Therefore, the block height not only reflects the sequence of the data blocks in the chain account book, but also contains the generation time of the data blocks.
Owner:ADVANCED NEW TECH CO LTD
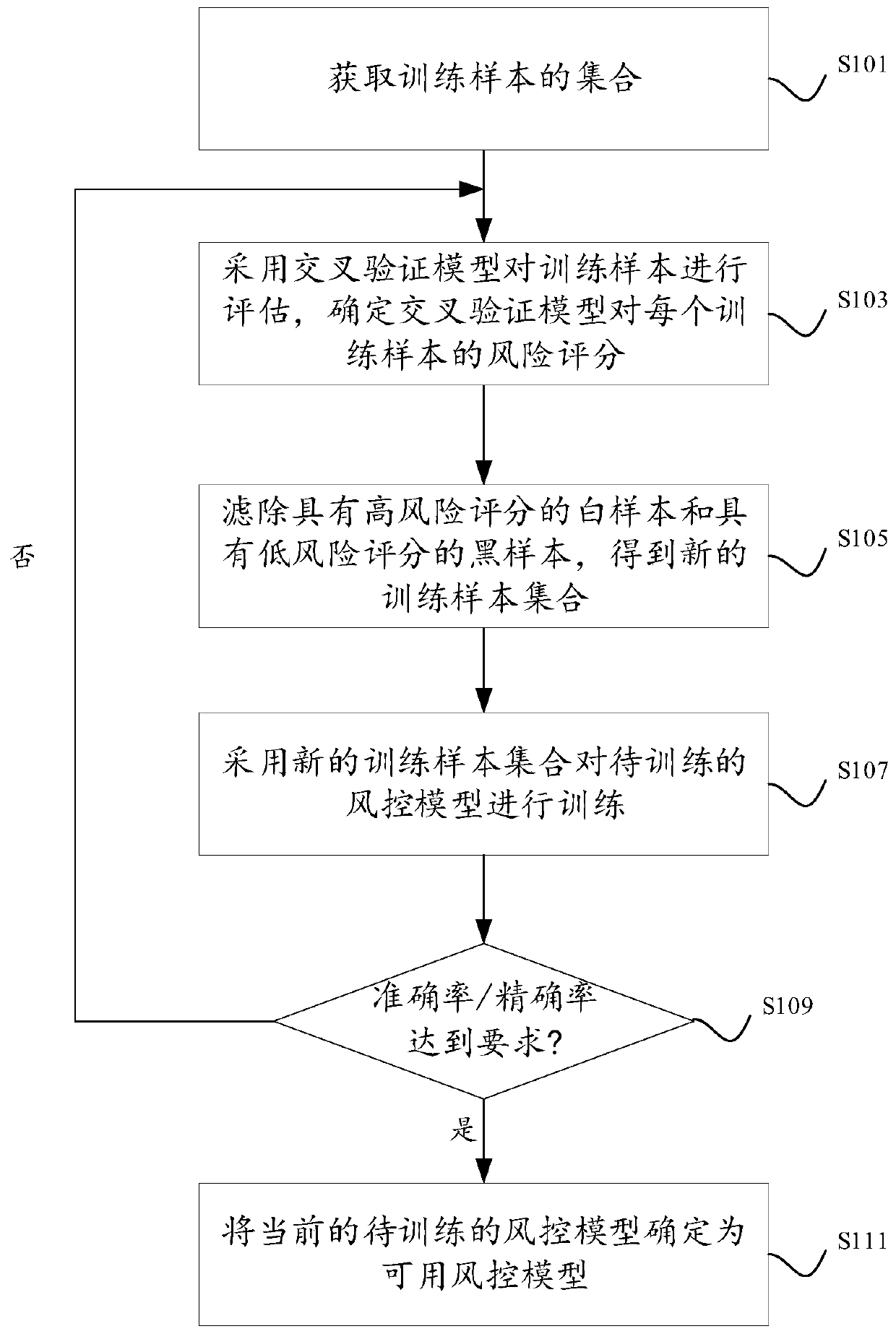
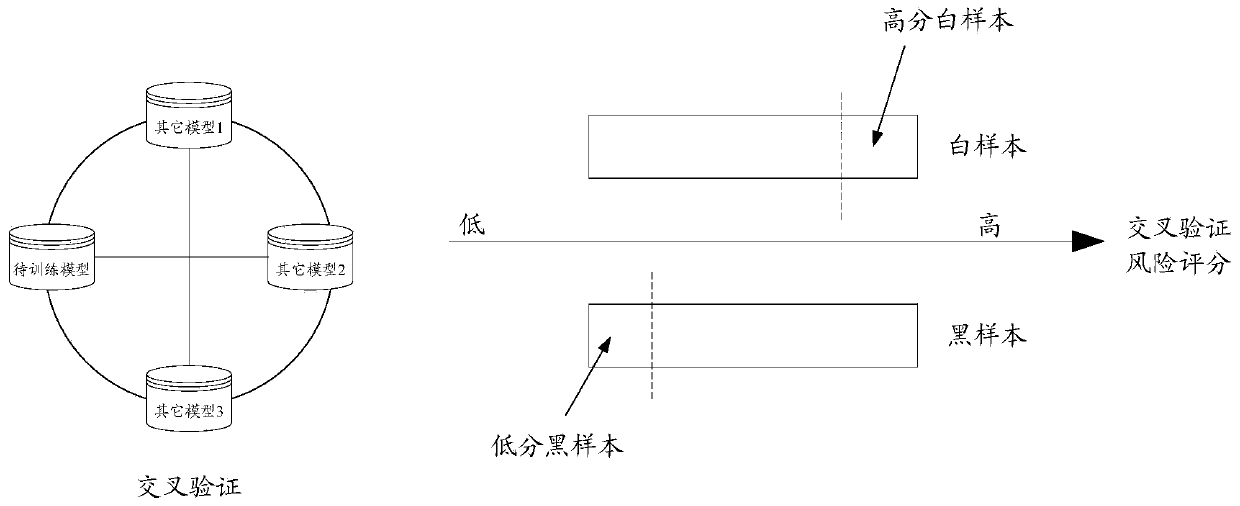
Risk control model training method and device, and equipment
ActiveCN110147823AExamples cannot be limitedCharacter and pattern recognitionResourcesRisk ControlLower score
The invention discloses a risk control model training method and device, and equipment. When the black samples in the training samples are impure and the risk control model is trained, cross validation is carried out on the training samples through other related trained risk identification models, so that the black samples with low scores and the white samples with high scores are filtered out, and the model is retrained by utilizing the screened samples.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com