A cloud data security sharing method based on a block chain
A blockchain and cloud data technology, applied in the field of cloud data security, can solve the problems of huge computing and communication overhead and security risks for data owners, and achieve the effect of improving key distribution efficiency, avoiding frequent communication, and reducing computing overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
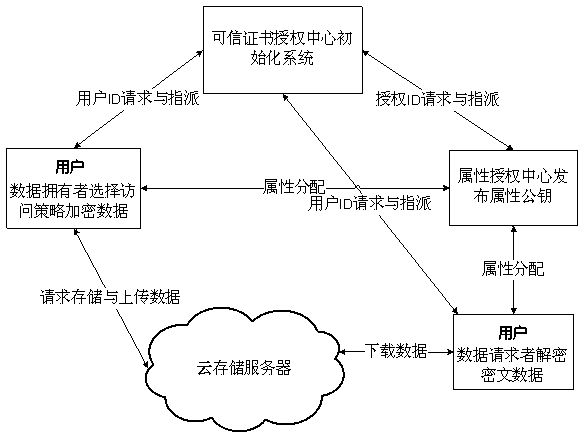
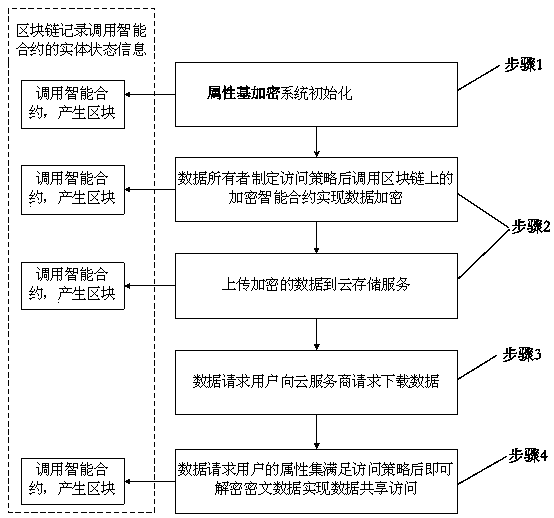
[0029] Such as figure 1 As shown, the ciphertext policy attribute-based encryption system model (referred to as "attribute-based encryption system") consists of entities such as trusted certificate authority, attribute authority, users including data owners and data requesters, and cloud storage servers. Each entity forms a blockchain network entity through the underlying blockchain platform, such as Ethereum or Hyperledger.
[0030] The trusted certificate authority selects security parameters to initialize the attribute-based encryption system, generates public parameters, and calls the parameter distribution smart contract to pass to For each entity in the attribute-based encryption system, users are divided into data owner users and data requester users. At the same time, the trusted certificate authority authenticates the legitimacy and authenticity of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com