Multifunctional fine-grained access control method for cloud storage
An access control and fine-grained technology, applied in the field of information security, to achieve good scalability and comprehensive functionality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
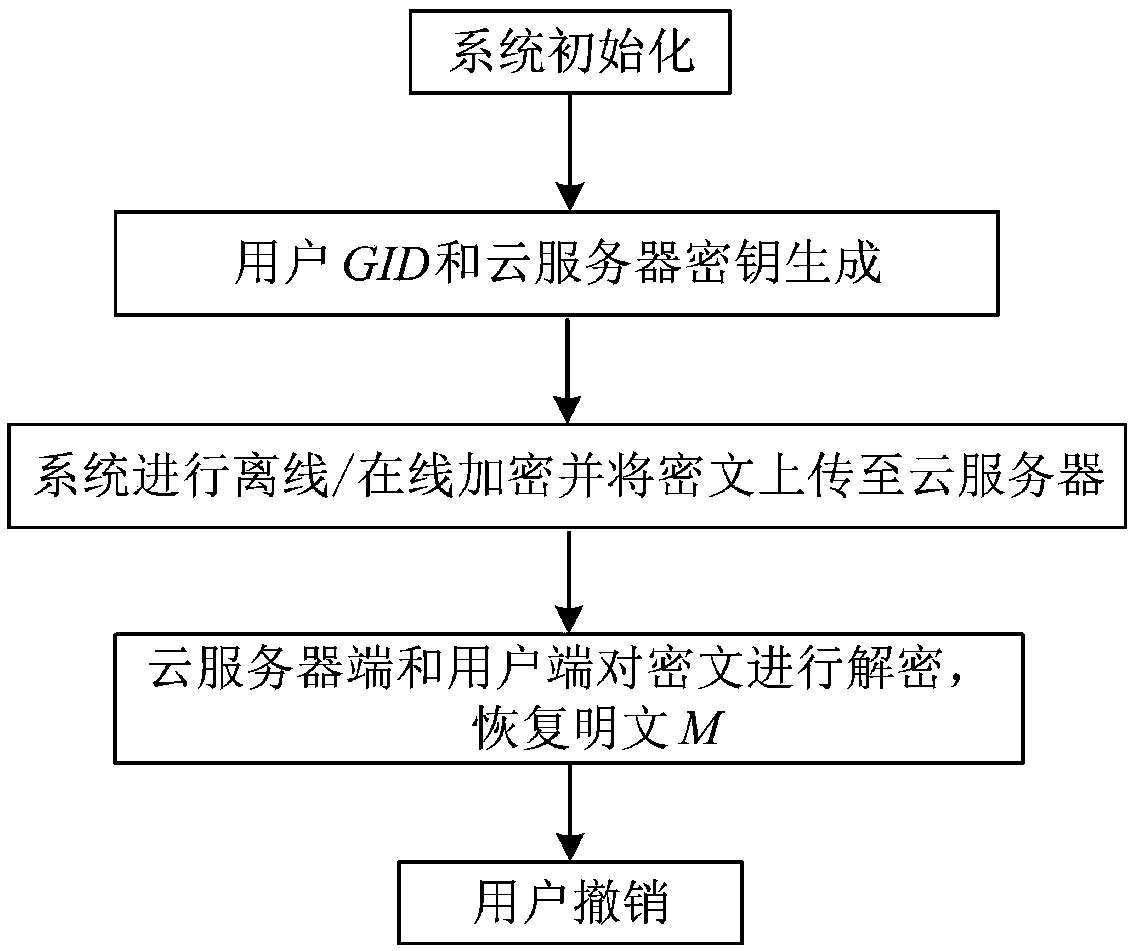
[0039] In recent years, cloud storage technology has been widely used in business, education, medical and other fields due to its convenience and low cost. With the in-depth application of cloud storage technology, data access control has become more and more important in the cloud environment. Based on Ciphertext attribute encryption technology is very suitable for data access control. Since the first CP-ABE scheme was proposed by Bethencourt et al. in 2007, according to different functional extensions, the CP-ABE scheme has been used in hidden access structures, computing outsourcing, searchable encryption, attribute revocation, traitor tracking, multi-attribute institutions, etc. There has been a lot of research on this aspect, but the latest multi-institutional CP-ABE schemes have different functional focuses, such as privacy protection and verifiability schemes. Based on this, the present invention proposes a multifunctional fine-grained access control method suitable for...
Embodiment 2
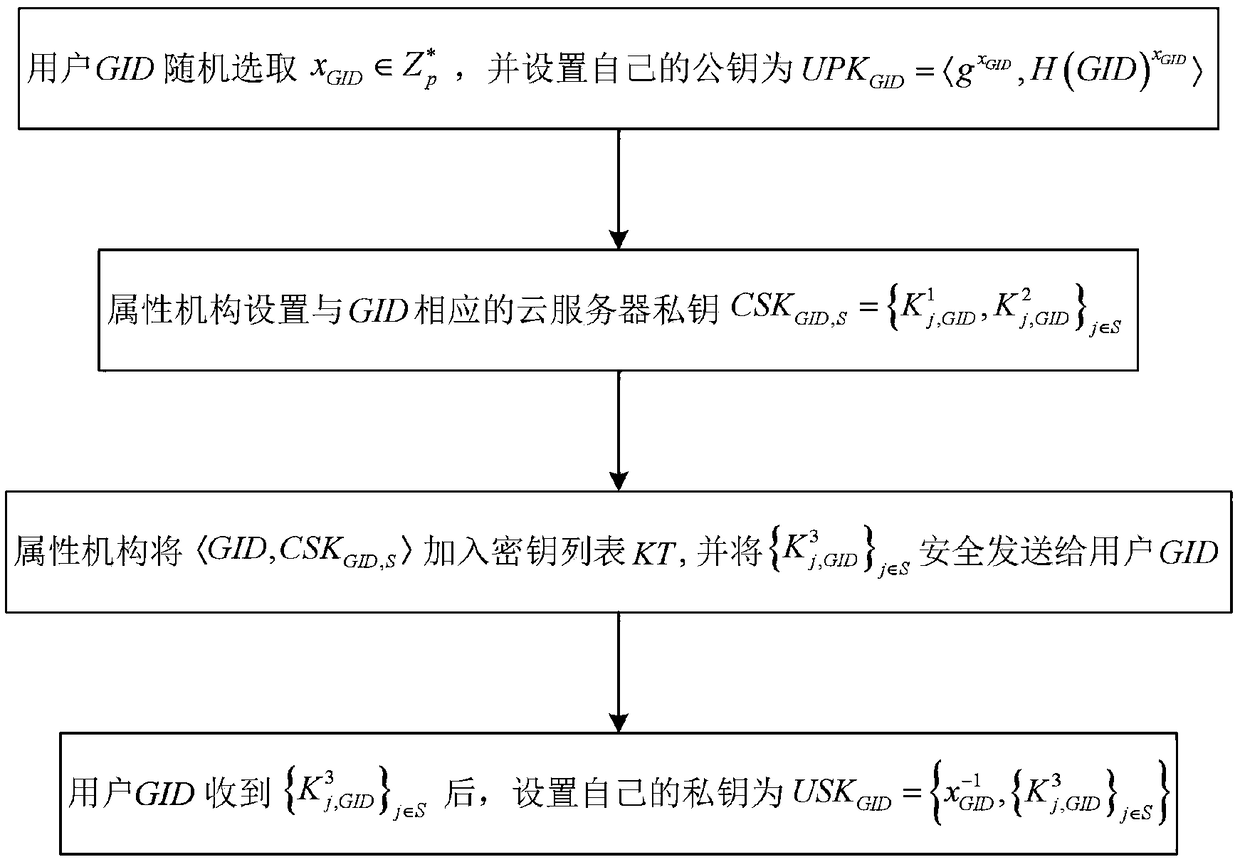
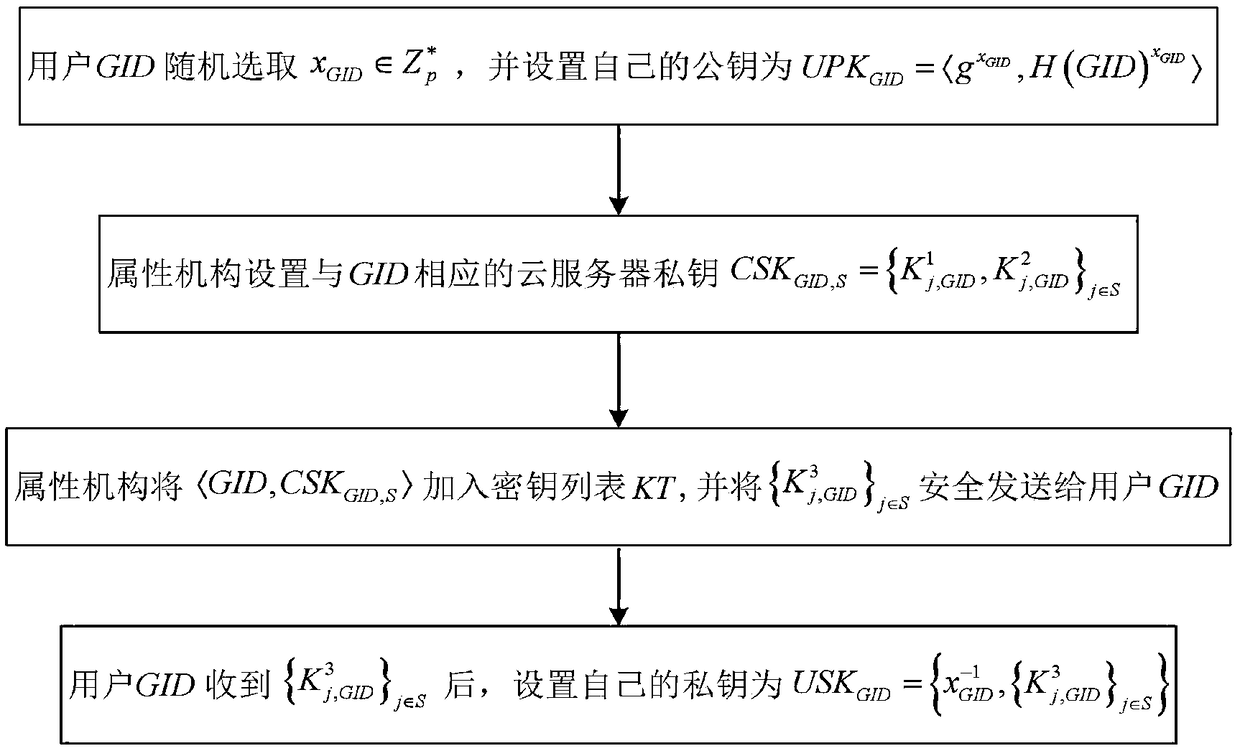
[0065] The multifunctional fine-grained access control method applicable to cloud storage is the same as that in Embodiment 1, refer to figure 2 , in the key generation described in step (2), the public-private key of the user and the private key of the cloud server are generated, including the following steps:
[0066] (2a) The user GID is in the multiplicative cyclic group Randomly choose an integer x from GID , and set the public key of the user GID according to the integer as Among them, g is the generator of the group G, is from the multiplicative cyclic group Map to the hash function of group G to complete the setting of the user's public key.
[0067] (2b) For each attribute j in the user attribute set S, if j is managed by attribute organization i, then the attribute organization is in the multiplicative cyclic group Select a private key random number t from j , use the random number to calculate and obtain the private key component of the cloud server. Th...
Embodiment 3
[0072] The multifunctional fine-grained access control method applicable to cloud storage is the same as that in Embodiment 1-2, refer to image 3 , the offline encryption stage described in step (3a) encrypts the data of the data owner locally, which reduces the computing overhead of the client, including the following steps:
[0073] (3a1) For any attribute j ∈ [1, U], U represents the attribute space, and the data owner selects the ciphertext random number Precomputing intermediate ciphertext components Among them, α δ(j) 、y δ(j) Indicates the property authority private key that manages property j.
[0074] (3a2) output intermediate ciphertext IC={λ' j ,w' j ,C 1,j ,C 2,j ,C 3,j ,C 4,j} j∈[1,U] , to complete offline data encryption.
[0075] The offline encryption mechanism used in the present invention solves the problem of encryption efficiency, and divides the encryption process into an offline encryption stage and an online encryption stage. The data is en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com