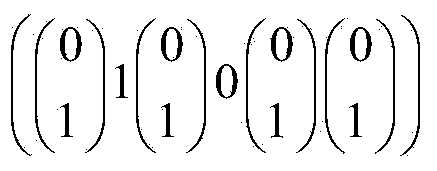Attribute-based hybrid encryption method capable of tracing leaked secret key
A hybrid encryption and traceable technology, applied in the field of cryptography in information security, can solve problems such as data insecurity, achieve the effects of improving system efficiency, saving storage space, and ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
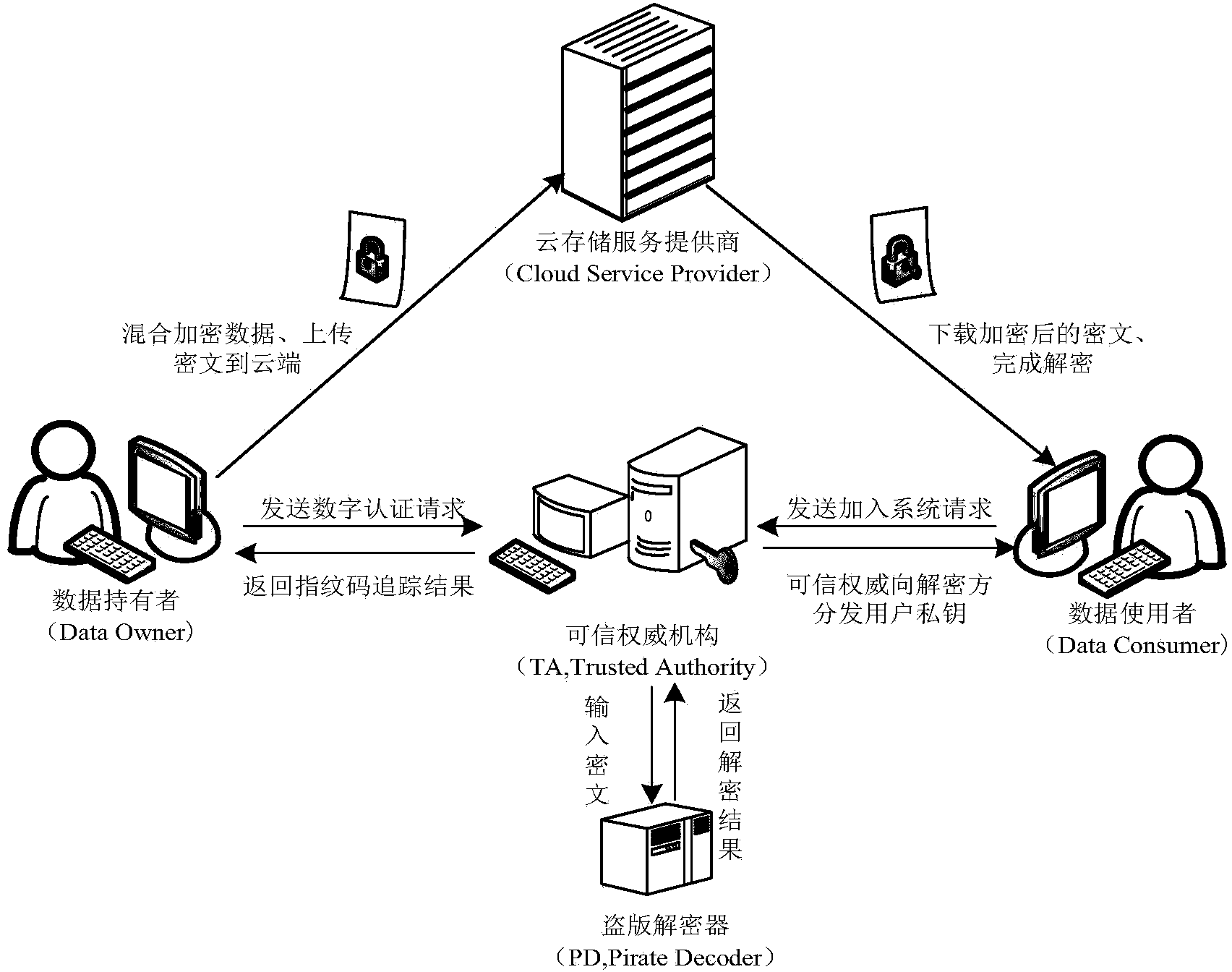
[0119] The invention is an attribute-based hybrid encryption method with traceable leaked key, which is realized by five modules: a system initialization module, a user input module, a document creation module, a document access module and a digital evidence acquisition module. The system architecture diagram of the operation of the attribute-based hybrid encryption method with traceable leaked keys is shown in figure 1 Shown, the flowchart block diagram of the method of the present invention sees figure 2 As shown, combined with the flow chart, the specific implementation steps of the method are introduced as follows:
[0120] The invention discloses an attribute-based hybrid encryption method with traceable leaked keys. The method is as follows:
[0121] Module 1: System initialization module:
[0122] Step 1: The trusted authority (TA, Trusted Authority) inputs the system security parameter λ, and runs the algorithm Output two groups whose order is a prime number p a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com