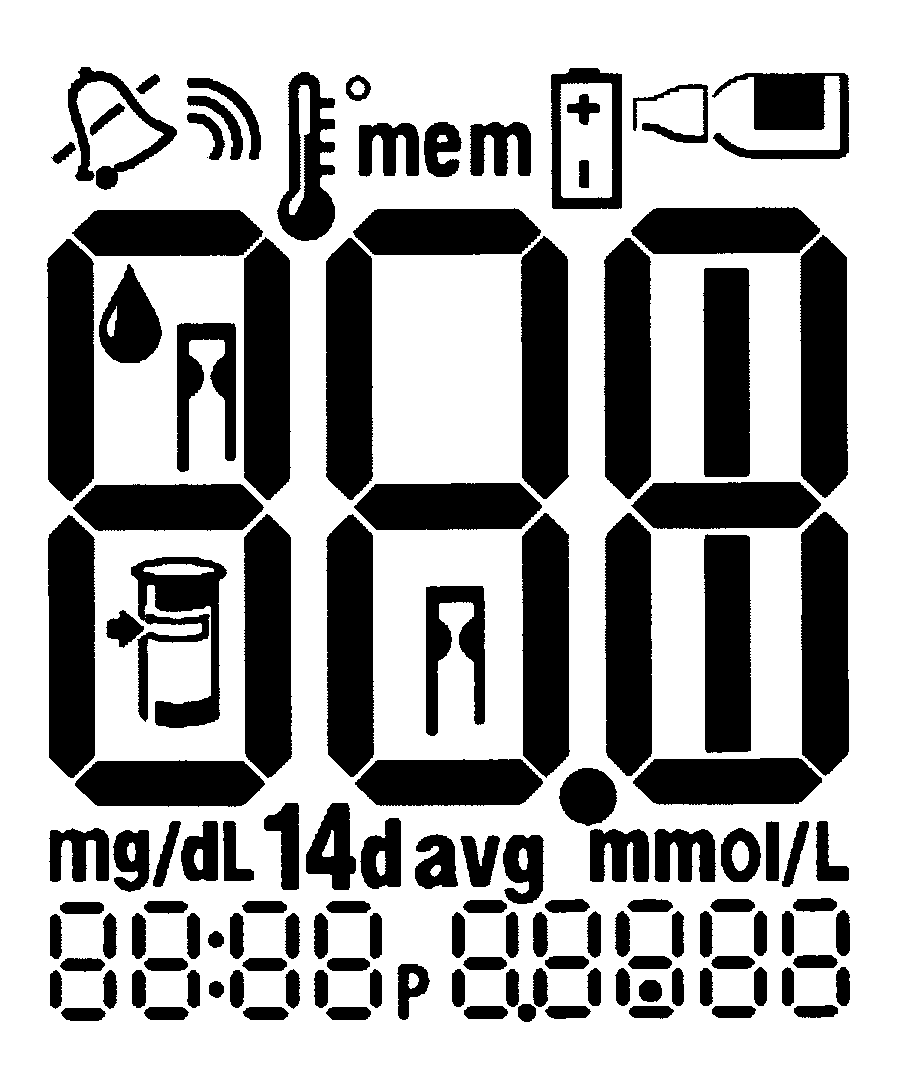Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
277results about How to "Minimizes probability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
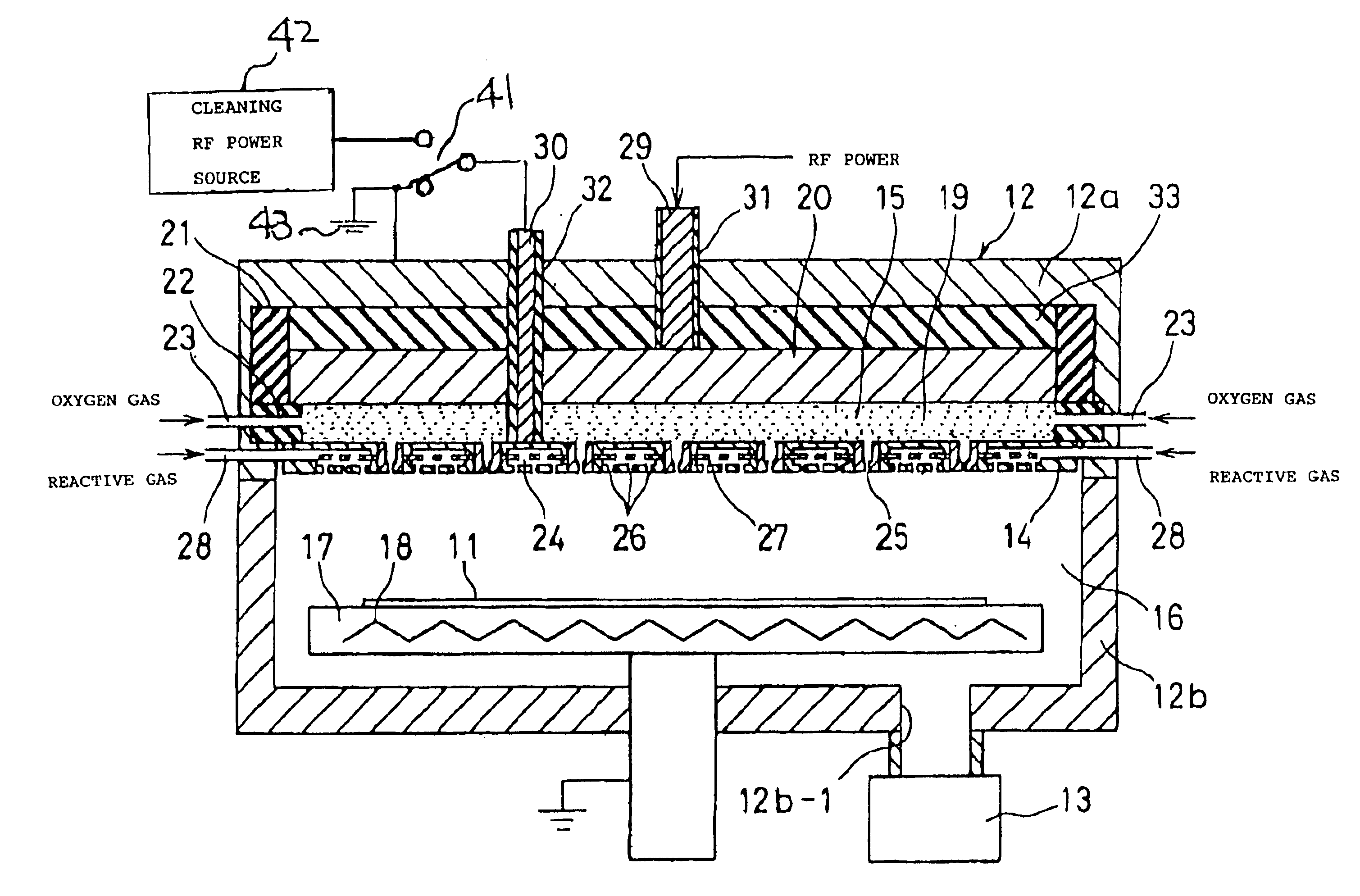
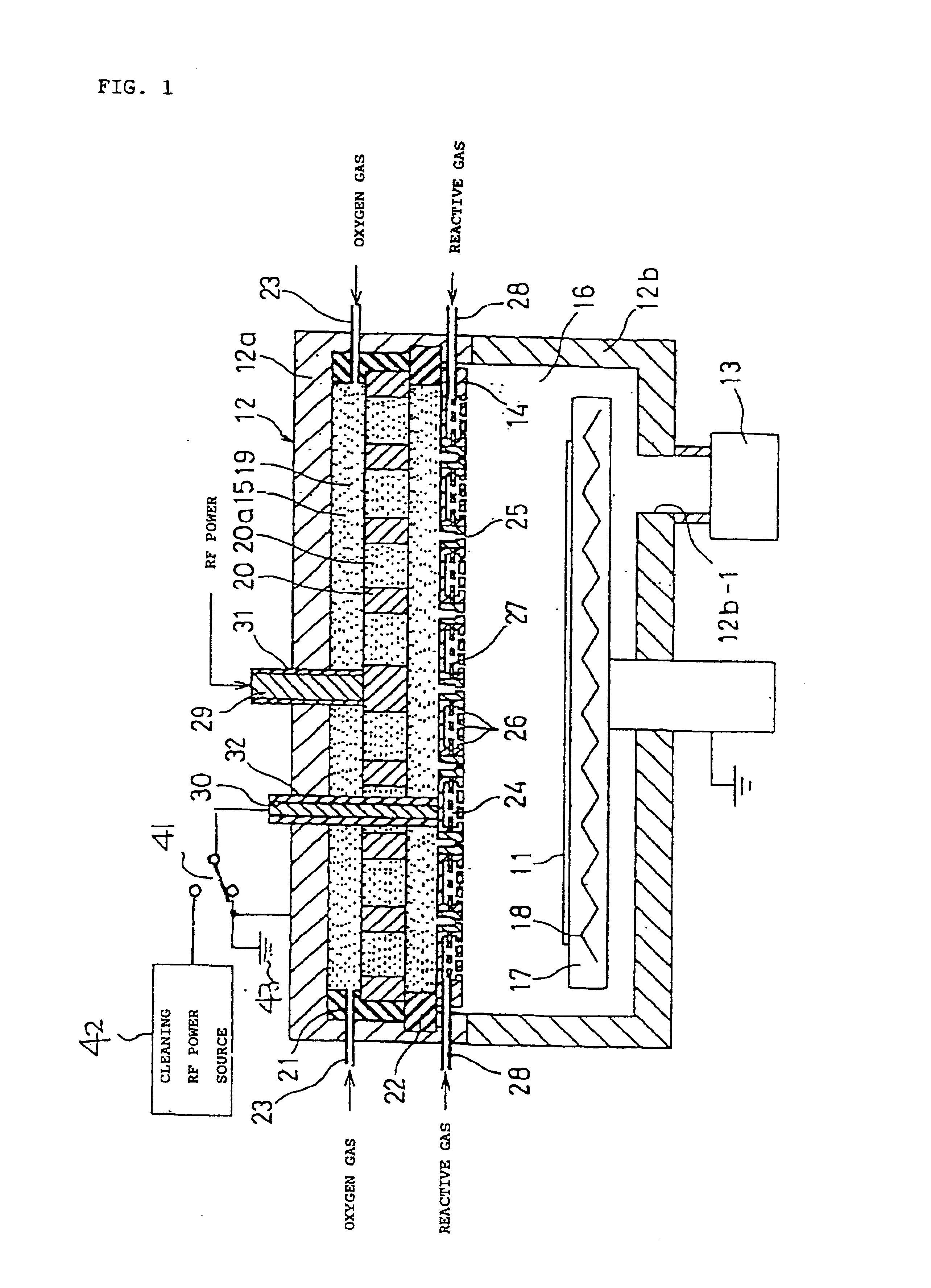
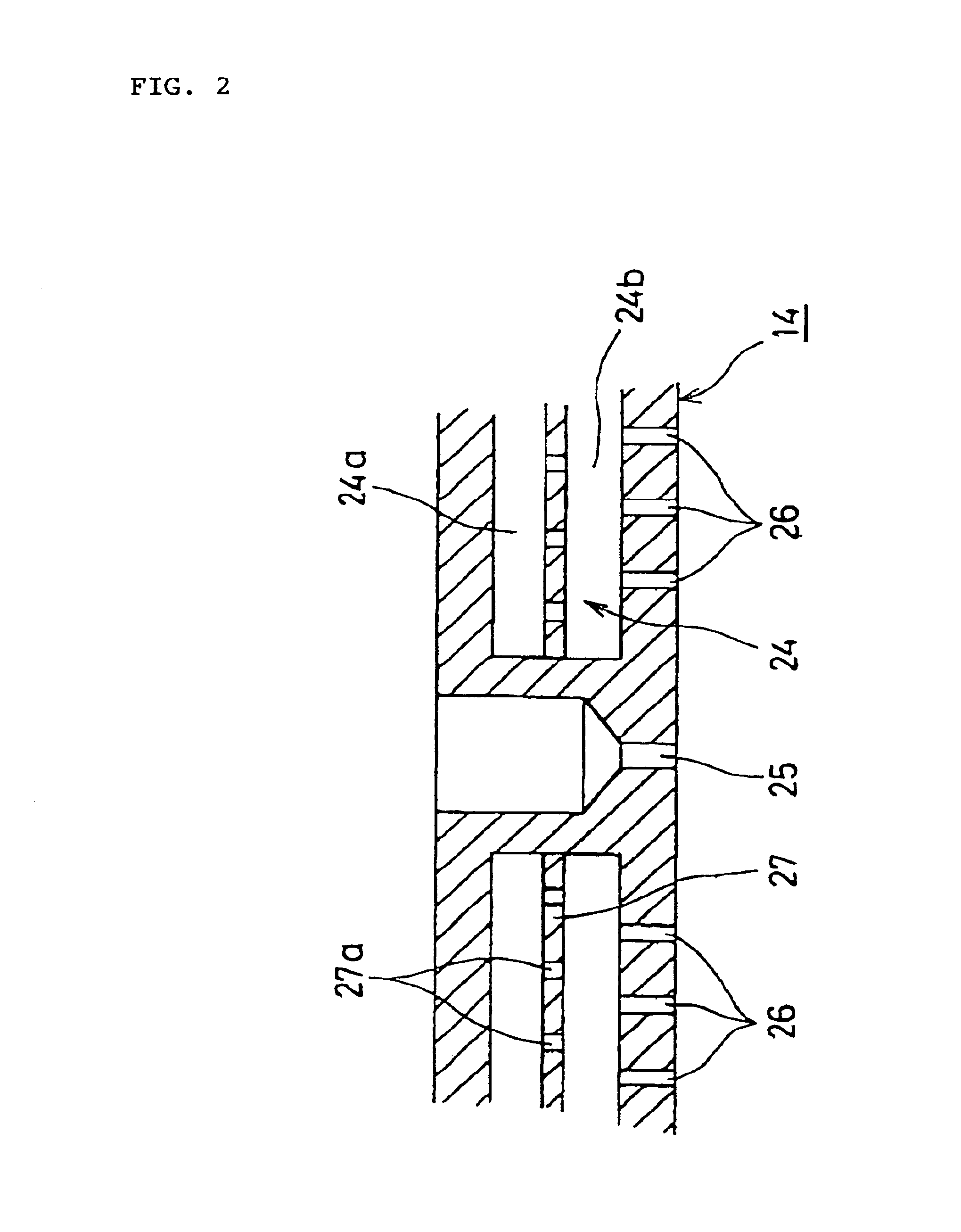
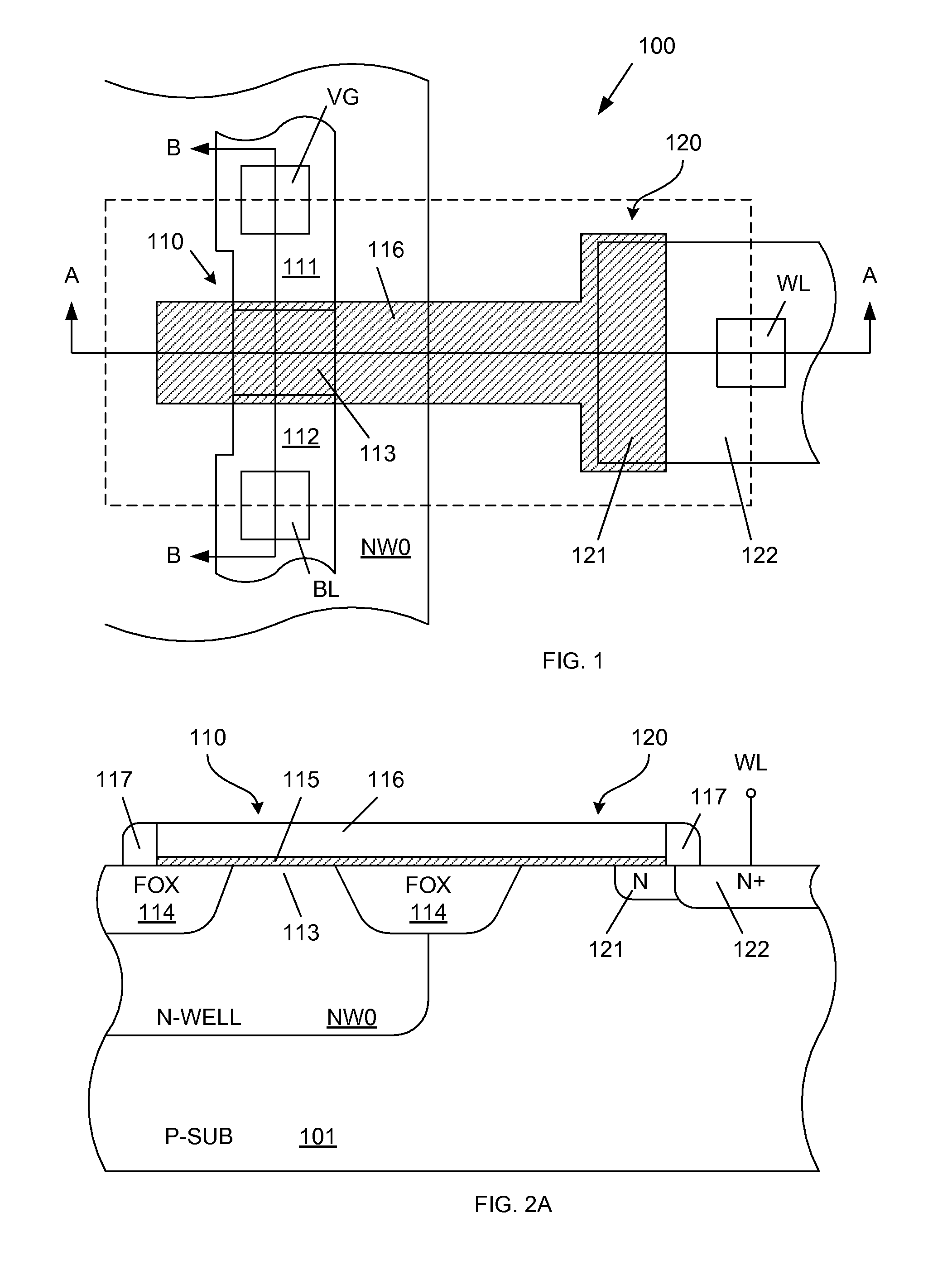
CVD apparatus
InactiveUS6892669B2Minimizes probabilityInhibition formationSemiconductor/solid-state device manufacturingChemical vapor deposition coatingInterior spacePolymer science
A CVD apparatus produces plasma to generate radicals and uses the radicals, silane, and the like so as to deposit films on substrates in a vacuum vessel 12. The vacuum vessel has a partitioning wall section 14 for separating the inside thereof into a plasma-generating space 15 and a film deposition process space 16. The partitioning wall section has a plurality of through-holes 25 and diffusion holes 26. An interior space 24 receives the silane or the like fed into the film deposition process space through diffusion holes 16. The radicals produced in the plasma-generating space are fed into the plasma-generating space through the through-holes. The through-holes satisfy the condition of uL / D>1, where u represents the gas flow velocity in the through-holes, L represents the effective length of the through-holes, and D represents the inter-diffusion coefficient.
Owner:ANELVA CORP
Means and method for the treatment of cerebral aneurysms
Disclosed is a system for the treatment of cerebral aneurysms using a stent and a aneurysm pocket fill structure delivery system. One embodiment of the present invention uses a highly radiopaque, drug eluting stent that is deployed with its sidewall over the ostium of the aneurysm pocket. A fill structure delivery catheter is then advanced through the patient's vascular system until the catheter's distal end is situated within the aneurysm pocket. Compressed aneurysm pocket filling structures are then pushed through the fill structure delivery catheter. As the aneurysm pocket filling structures emerge from an opening in the catheter's distal end, they promptly expand so that their minimum dimension is sufficiently large so that they cannot pass through the spaces between the struts of the stent that cover the ostium of the aneurysm pocket.
Owner:FISCHELL ROBERT E +1
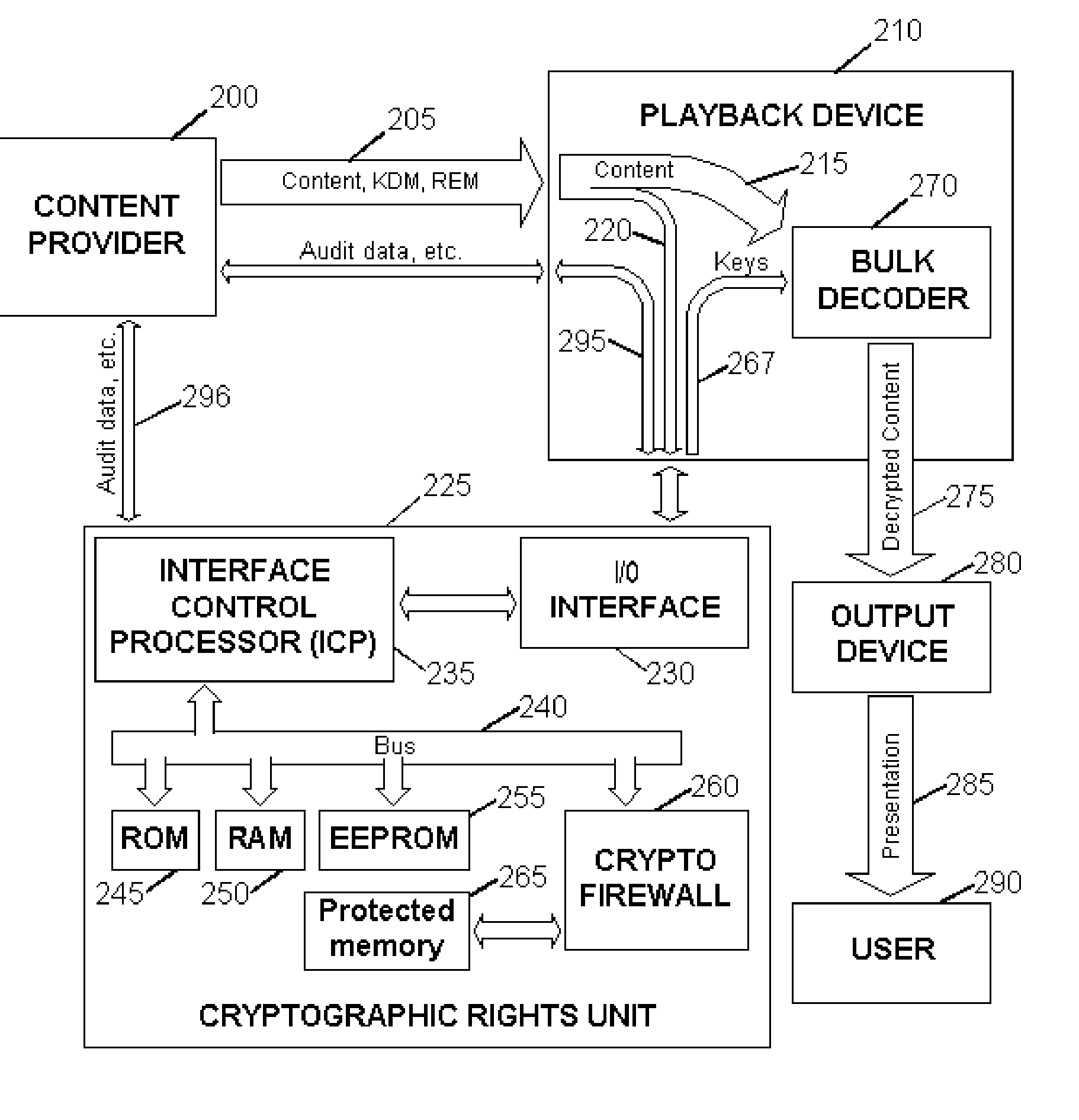
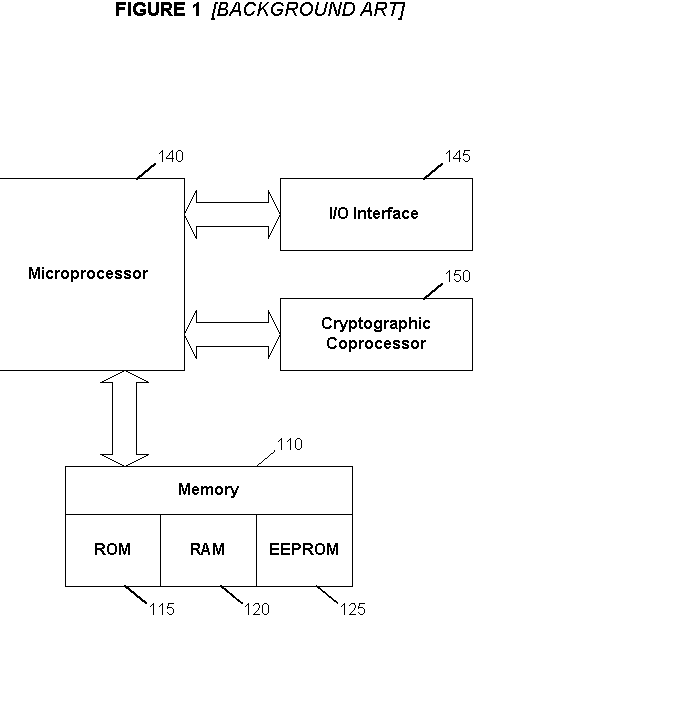
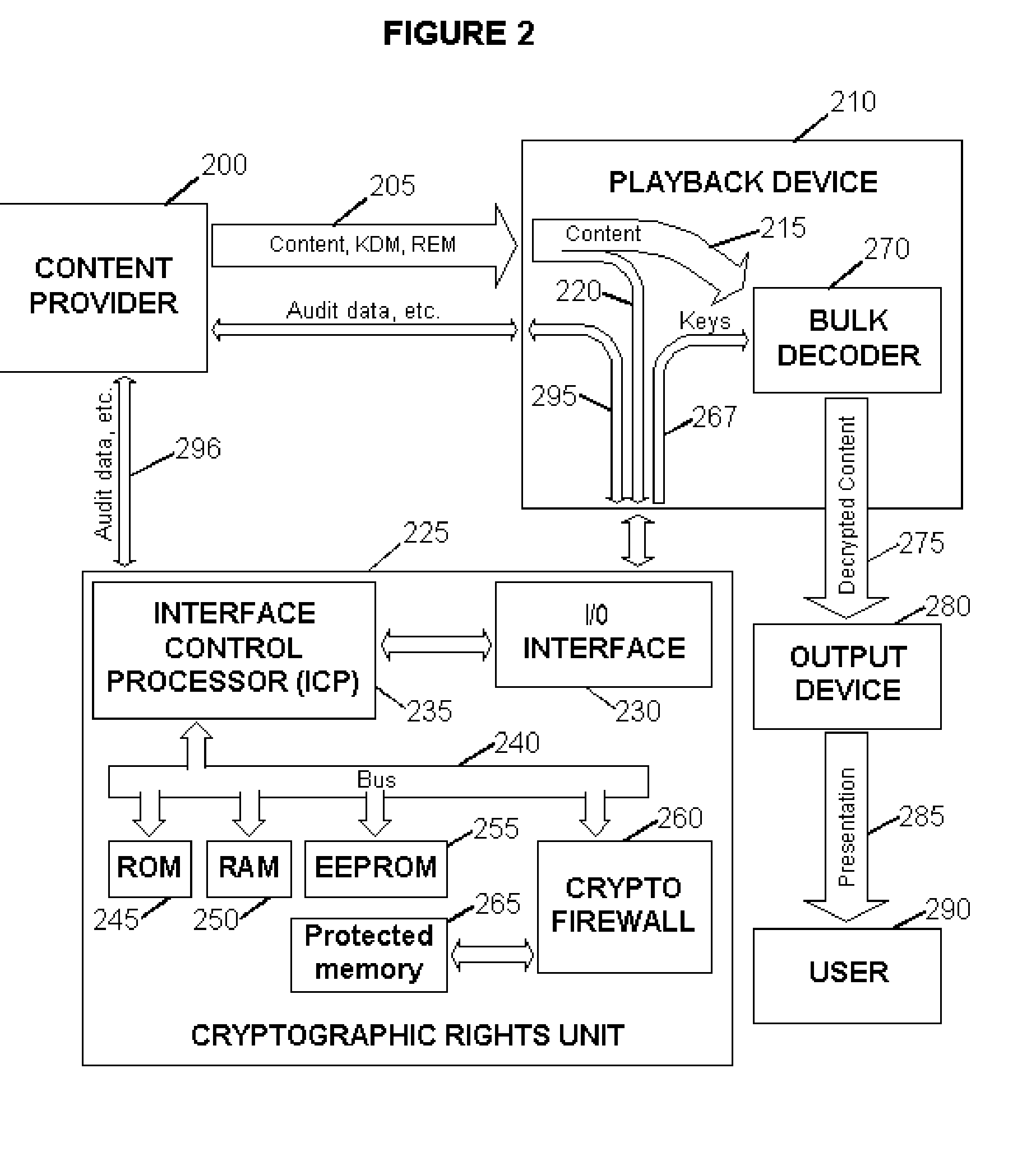
Digital Content Protection Method and Apparatus
InactiveUS20020099948A1Improve securityMinimizes probabilityKey distribution for secure communicationDigital data processing detailsDigital signatureDigital content
<heading lvl="0">Abstract of Disclosure< / heading> Before use, a population of tamper-resistant cryptographic enforcement devices is partitioned into groups and issued one or more group keys. Each tamper-resistant device contains multiple computational units to control access to digital content. One of the computational units within each tamper-resistant device communicates with another of the computational units acting as an interface control processor, and serves to protect the contents of a nonvolatile memory from unauthorized access or modification by other portions of the tamper-resistant device, while performing cryptographic computations using the memory contents. Content providers enforce viewing privileges by transmitting encrypted rights keys to a large number of recipient devices. These recipient devices process received messages using the protected processing environment and memory space of the secure unit. The processing result depends on whether the recipient device was specified by the content provider as authorized to view some encrypted digital content. Authorized recipient devices can use the processing result in decrypting the content, while unauthorized devices cannot decrypt the content. A related aspect of the invention provides for securing computational units and controlling attacks. For example, updates to the nonvolatile memory, including program updates, are supported and protected via a cryptographic unlocking and validation process in the secure unit, which can include digital signature verification.
Owner:CRYPTOGRAPHY RESEARCH
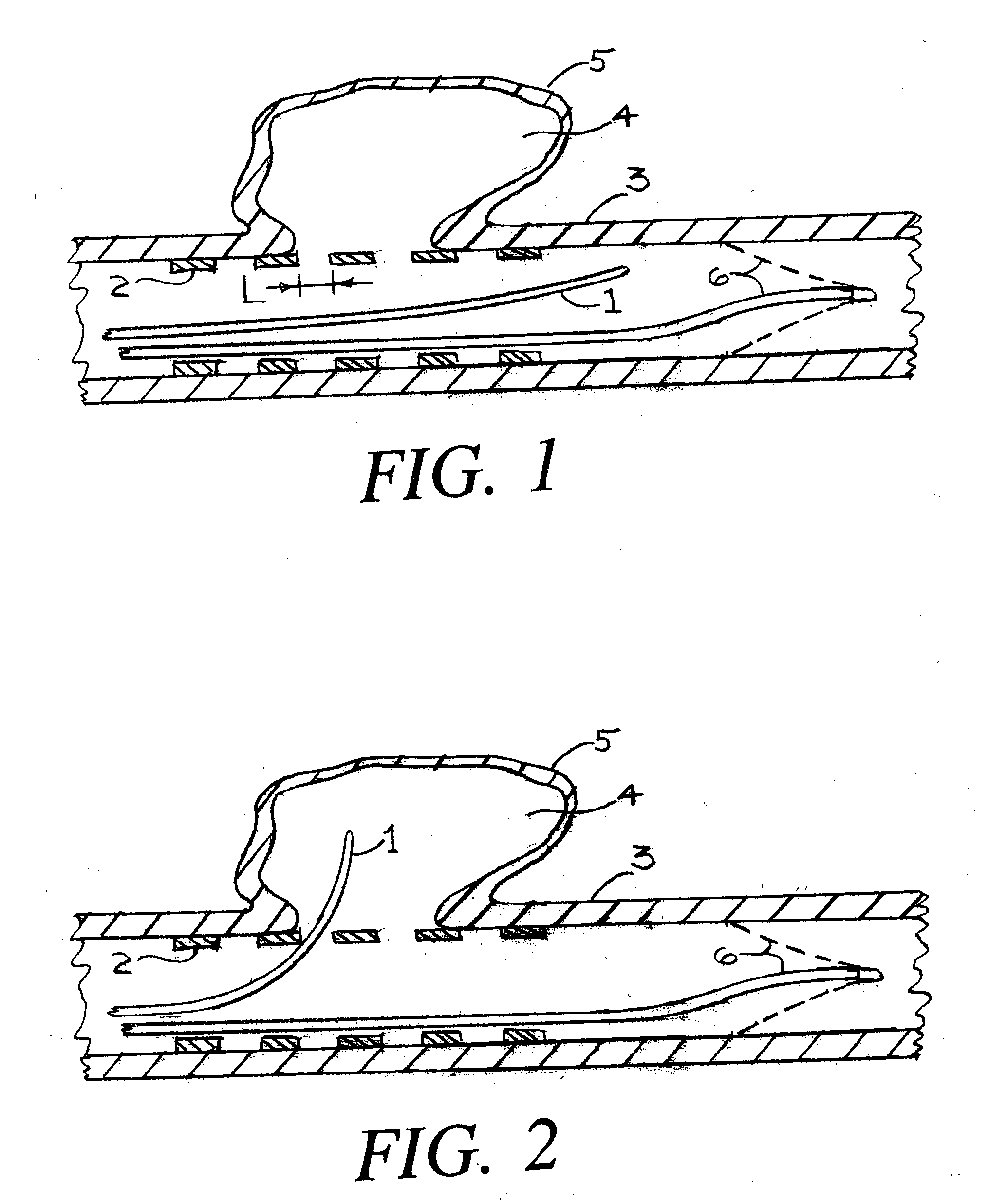
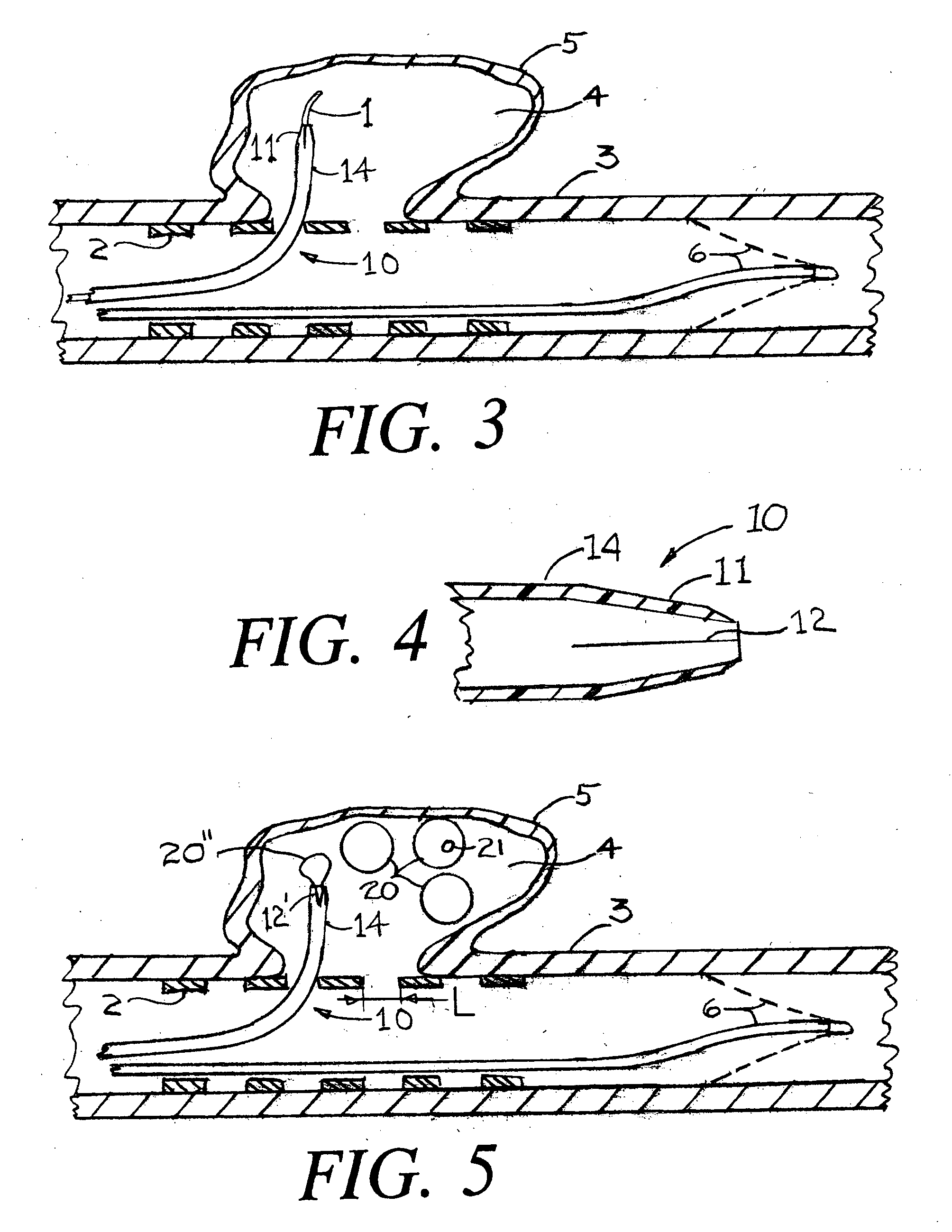
Suture management and tensioning devices and methods for soft tissue reconstruction or bone-to-bone fixation
ActiveUS20080154260A1Convenient introductionSimplifying retention of sutureSuture equipmentsDiagnosticsBone fixationSoft tissue reconstruction
Owner:CAYENNE MEDICAL INC
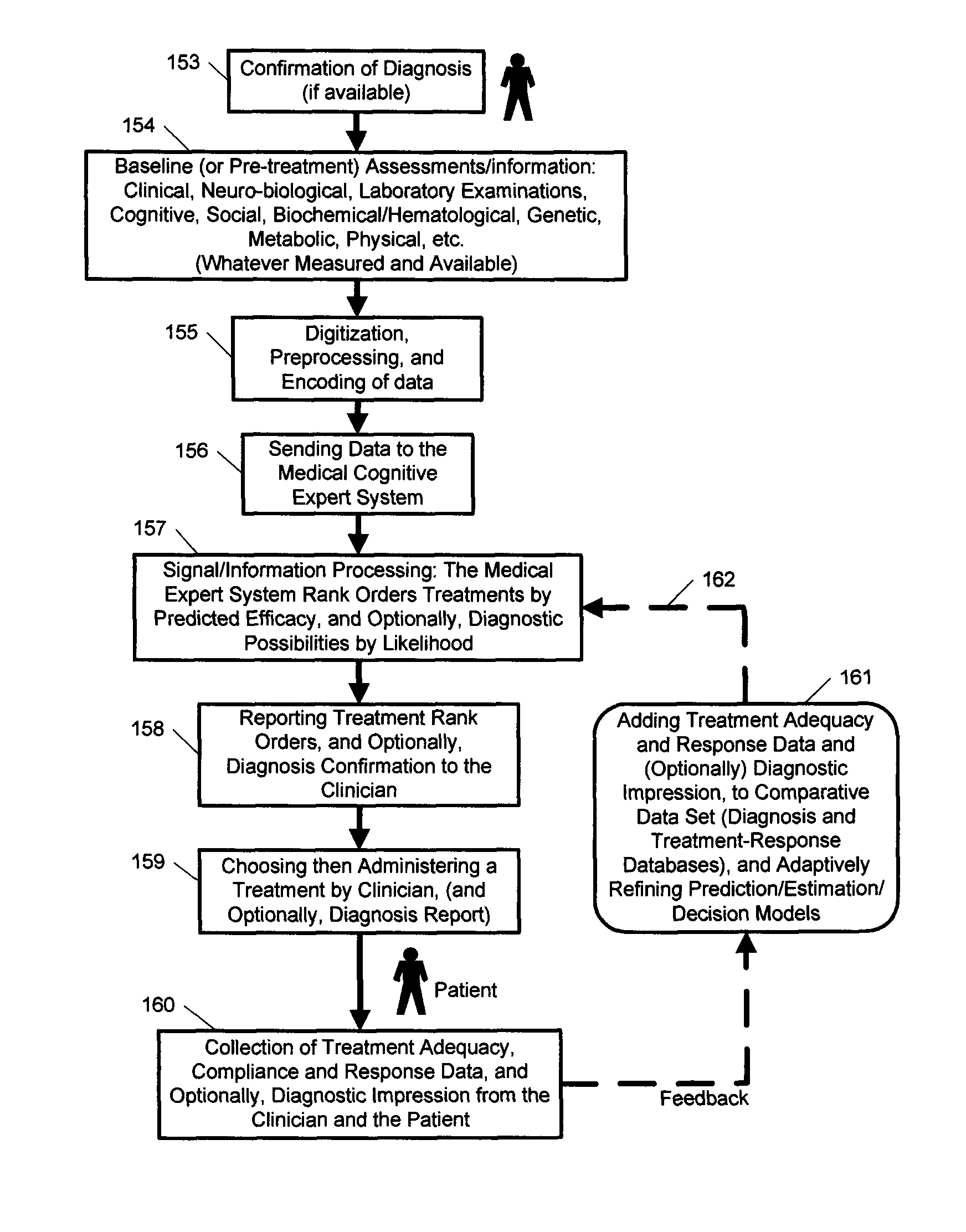
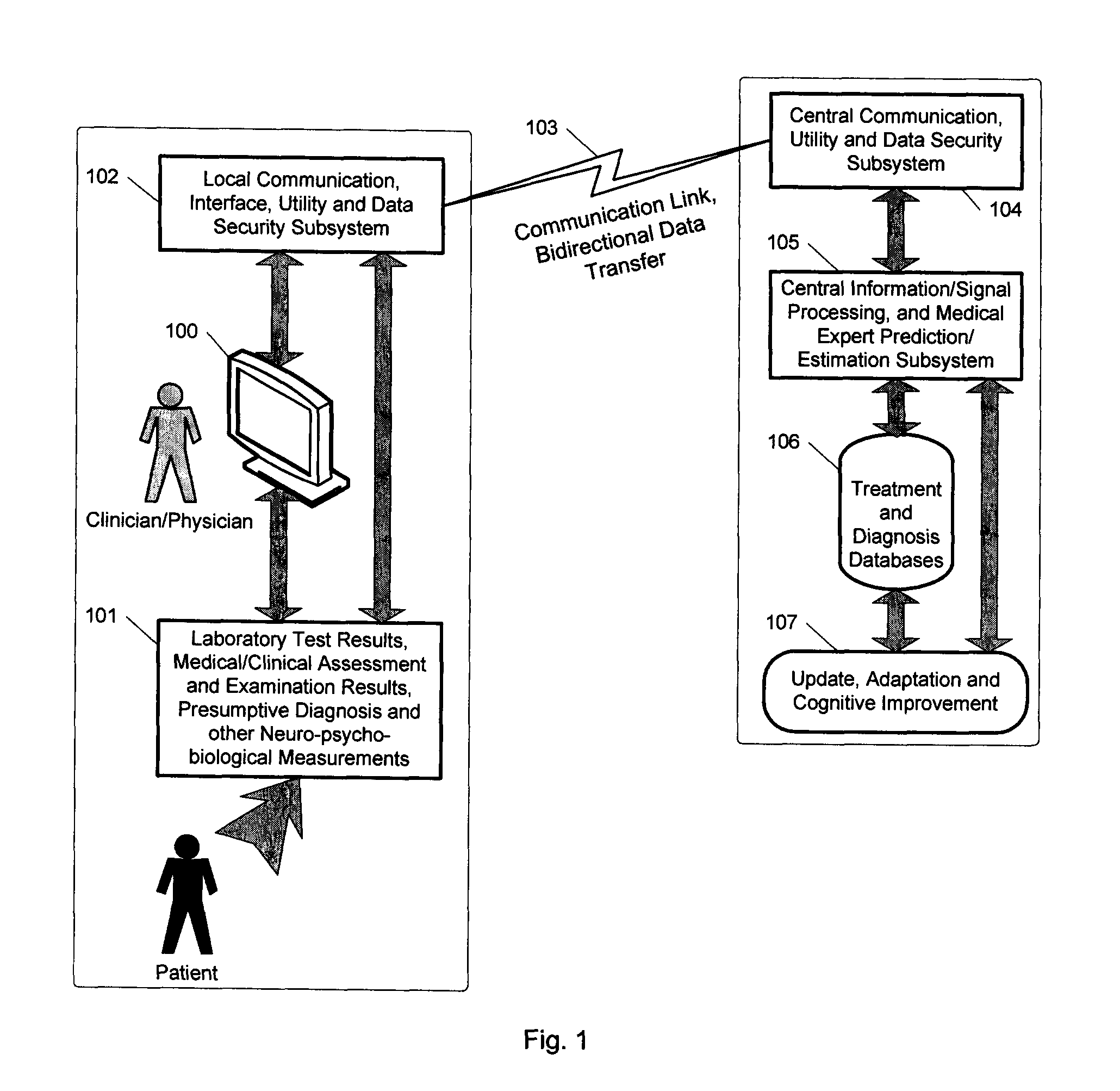
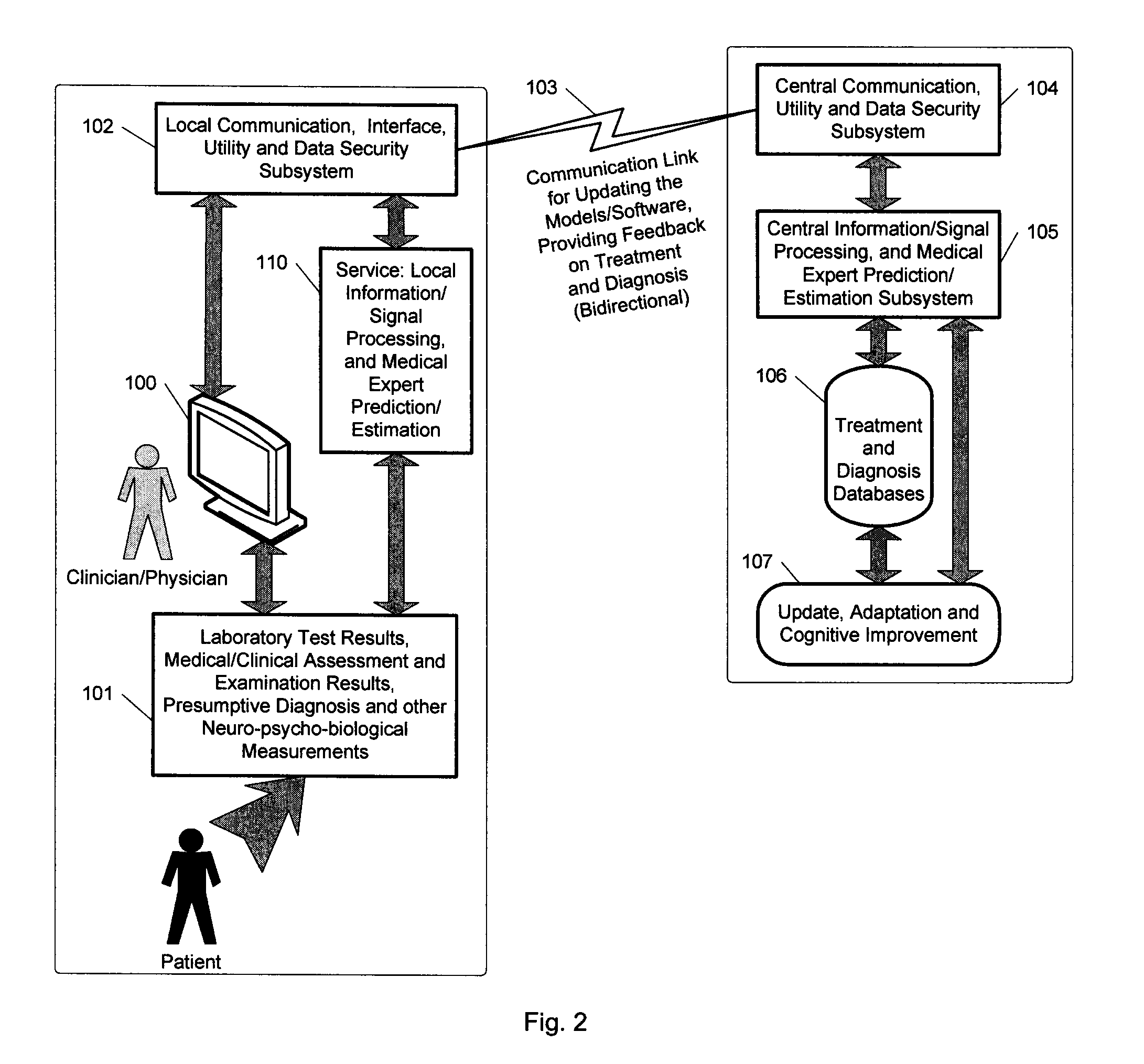
Expert system for determining patient treatment response
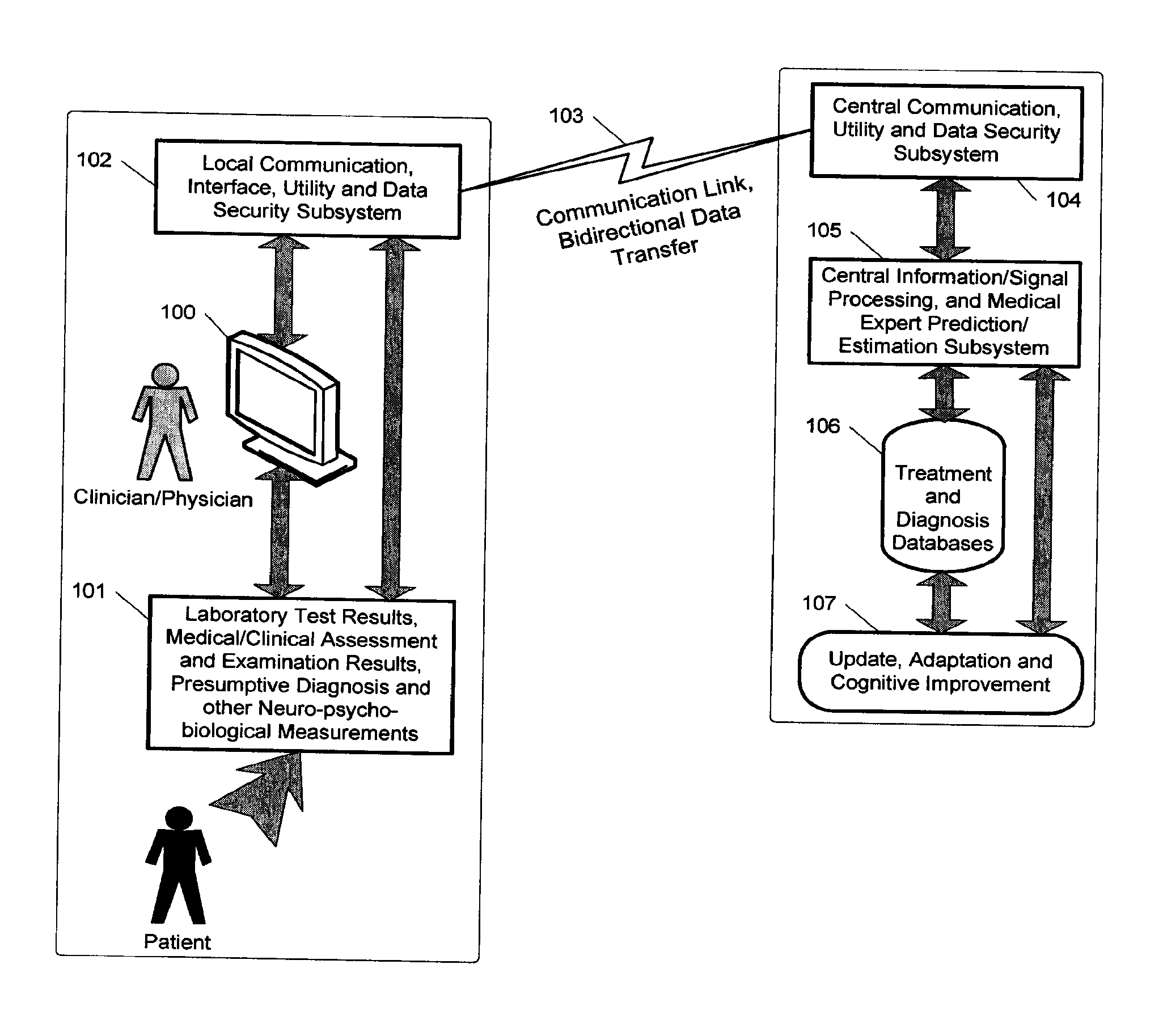
ActiveUS20140279746A1Improve performanceMinimize complexityMedical data miningHealth-index calculationDiseaseInformation processing
A medical digital expert system to predict a patient's response to a variety of treatments (using pre-treatment information) is described. The system utilizes data fusion, advanced signal / information processing and machine learning / inference methodologies and technologies to integrate and explore diverse sets of attributes, parameters and information that are available to select the optimal treatment choice for an individual or for a subset of individuals suffering from any illness or disease including psychiatric, mental or neurological disorders and illnesses. The methodology and system can also be used to determine or confirm medical diagnosis, estimate the level, index, severity or critical medical parameters of the illness or condition, or provide a list of likely diagnoses for an individual suffering / experiencing any illness, disorder or condition.
Owner:DIGITAL MEDICAL EXPERTS
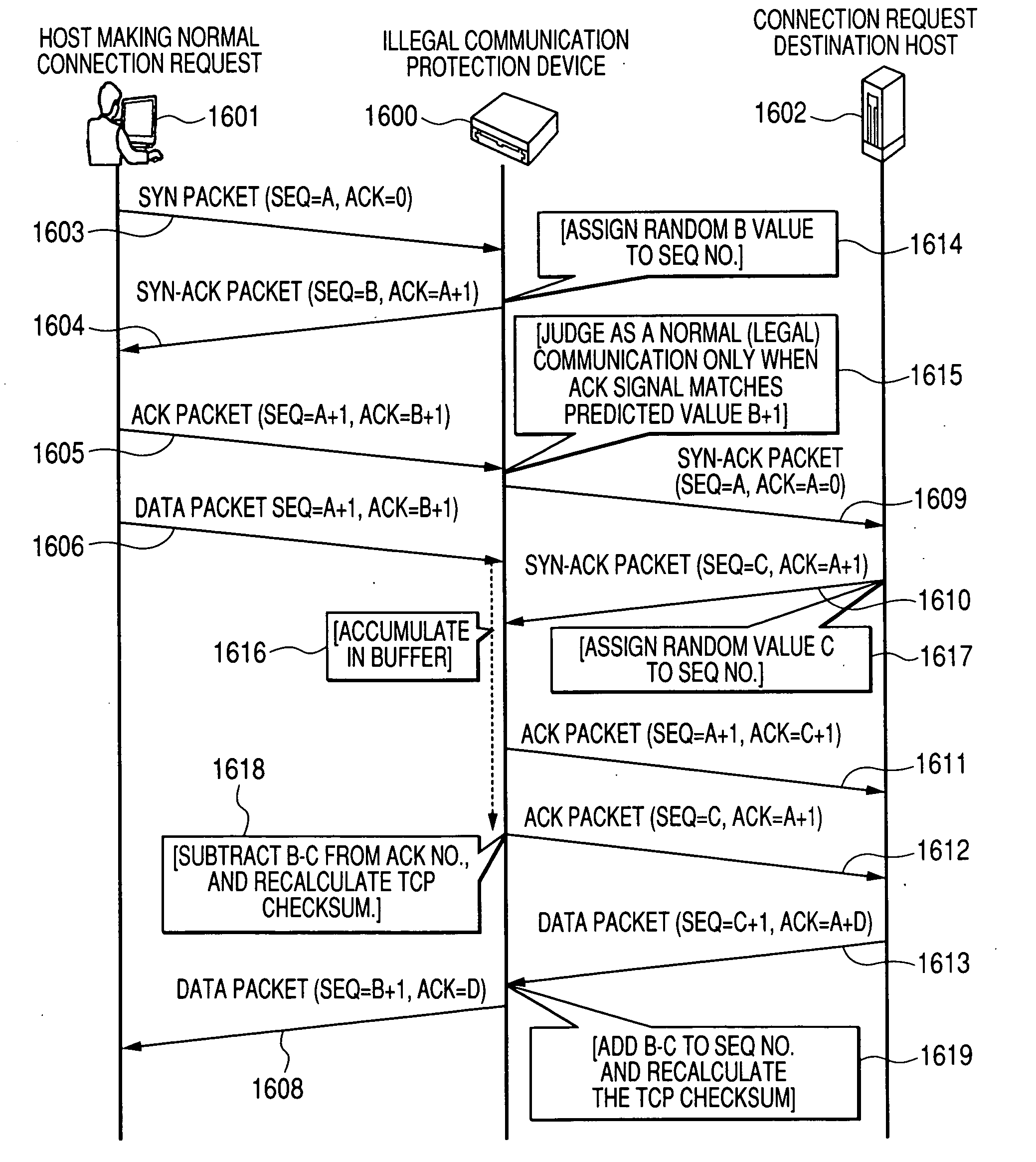
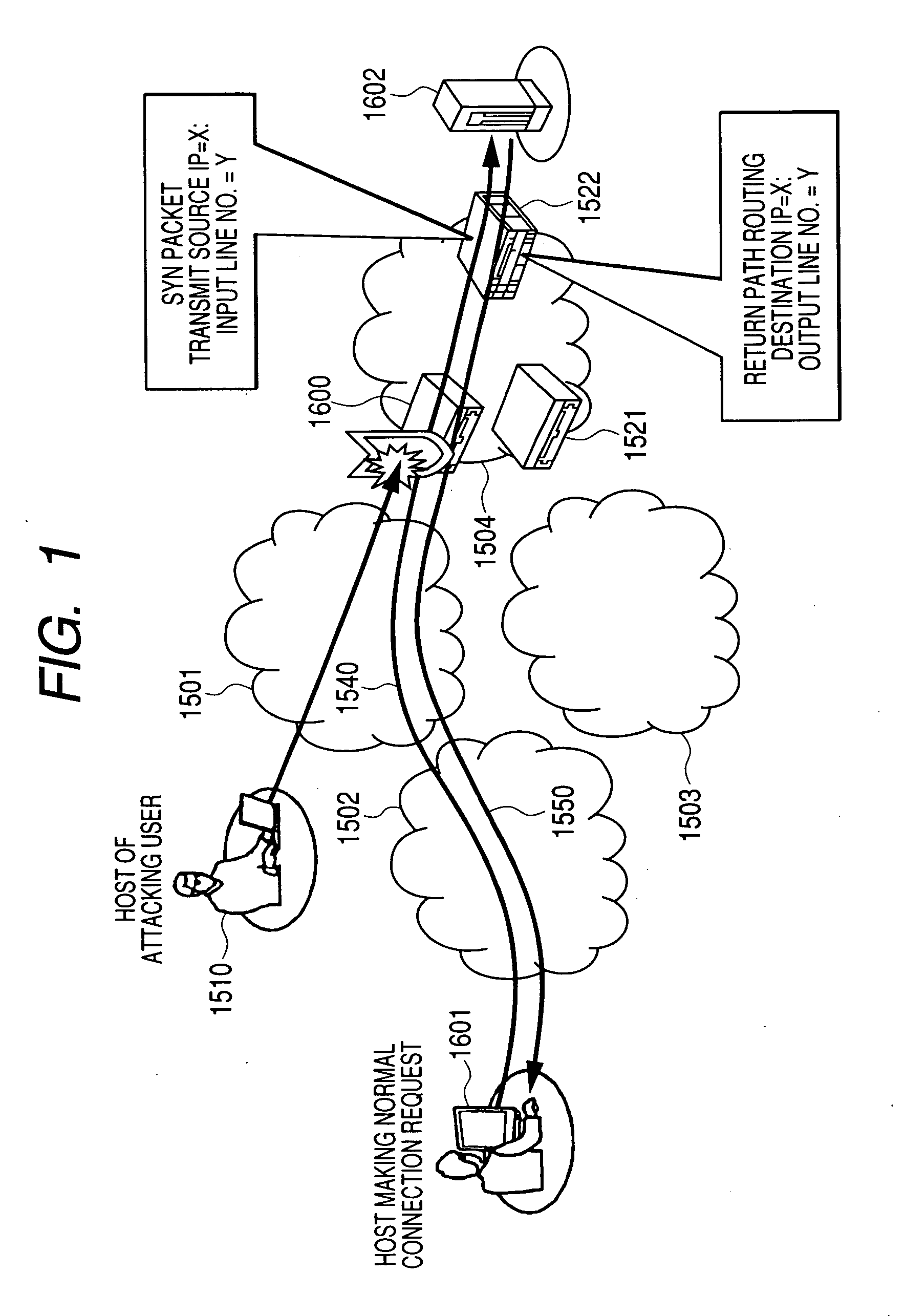
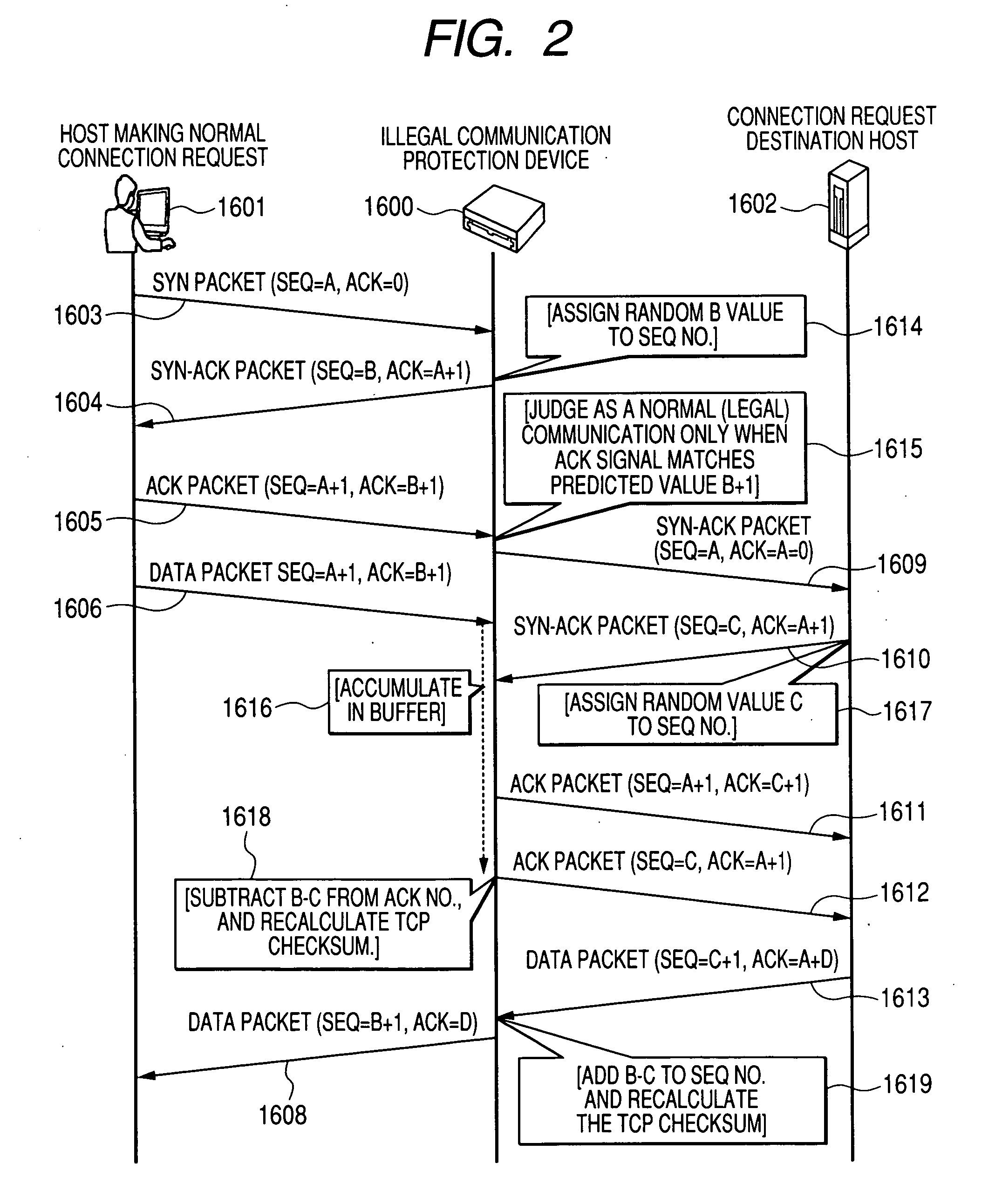
Device for protection against illegal communications and network system thereof
InactiveUS20070201474A1Minimize fail rateMinimizes probabilityTime-division multiplexData switching by path configurationRouting tableNetworked system
A communication device, an illegal communication protection device, and network system for providing protection from illegal communications. A communication device is connected to a network, for receiving packets sent and received over networks, and transmitting packets based on the packet destination, includes a control unit, and a storage unit for storing a routing table that stores the destination information. When there is a connection request from a packet that was received, the control unit stores the transmit source address of that packet and the line number where that packet was received, into a routing table, and where there is no connection request from the received packet, the control unit refers to the routing table, acquires the line number linked to an address matching the destination address of that packet, and sends the applicable packet via the acquired line number.
Owner:HITACHI LTD
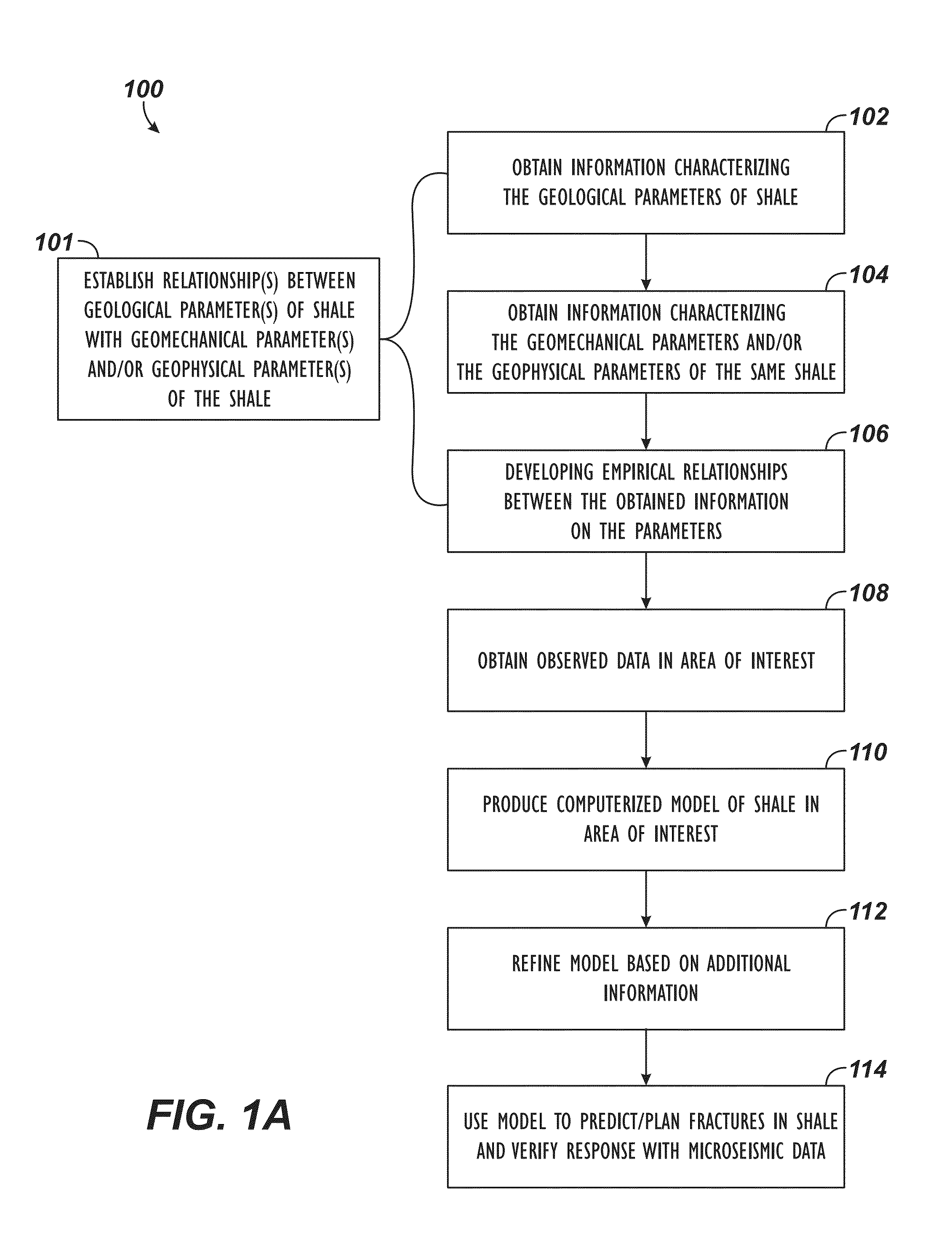
Model Predicting Fracturing of Shale
ActiveUS20130238304A1Promote recoveryMinimizes probabilityGeomodellingDesign optimisation/simulationWell loggingHydraulic fracturing
A model for predicting fracturing in shale can minimize surface disruption, protect groundwater, maximize efficiency of hydraulic fracturing, and manage fluids used in unconventional gas development. The model provides a more comprehensive understanding of the geological, geophysical, and geomechanical properties of shales and imbeds these properties in geomechanical computer simulations to predict both the reservoir performance from the fracturing, and the associated microseismic events generated by fracturing. Since the geological and geophysical properties can be estimated from surface seismic, well logs, and geologic concepts with regional context; the performance of the fracturing can be predicted and optimized. Since the microseismic events can be predicted with the model, the simulations can be verified and the model can be updated to be consistent with the observed microseismic.
Owner:ION GEOPHYSICAL CORP
System and Method of Extending the Communication Range in a Visible Light Communication System
ActiveUS20130183042A1Unlimited communication rangeMinimizes probabilityNon-electrical signal transmission systemsElectric light circuit arrangementComputer hardwareRemote control
A system, remote control device and method are provided herein for communicating with and controlling various devices using visible light communication (VLC). According to one embodiment, a method is provided for extending a communication range of a visible light communication system comprising a remote control device and a plurality of controlled devices. Such a method may include, for example, transmitting a communication message from a remote control device to a first controlled device located within range of the remote control device, wherein the communication message is transmitted through free space using visible light, and extending the communication range of the visible light communication system to a second controlled device, which is located outside of the range of the remote control device, by using the first controlled device to retransmit the communication message through free space using visible light to the second controlled device.
Owner:LUTRON TECH CO LLC
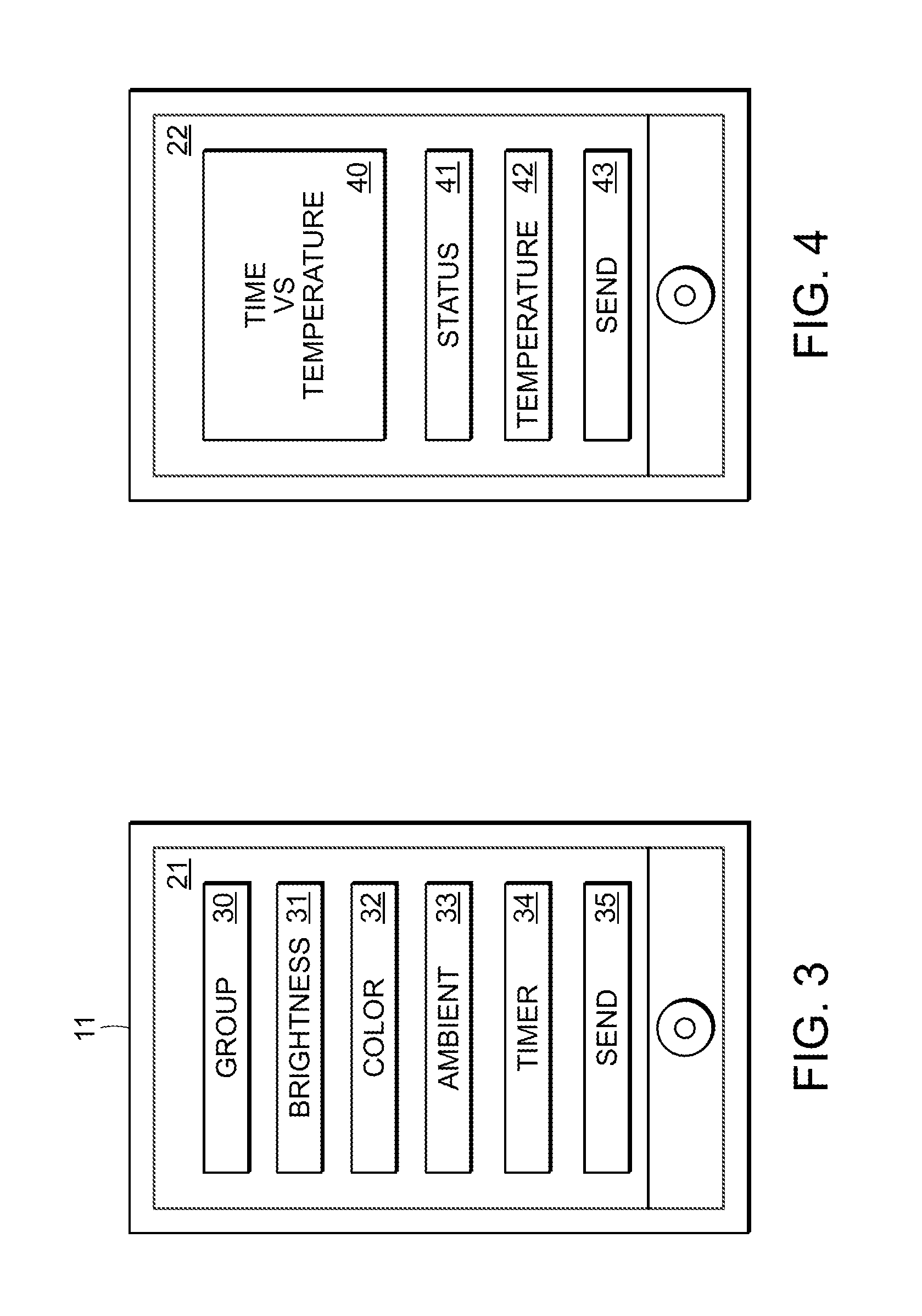
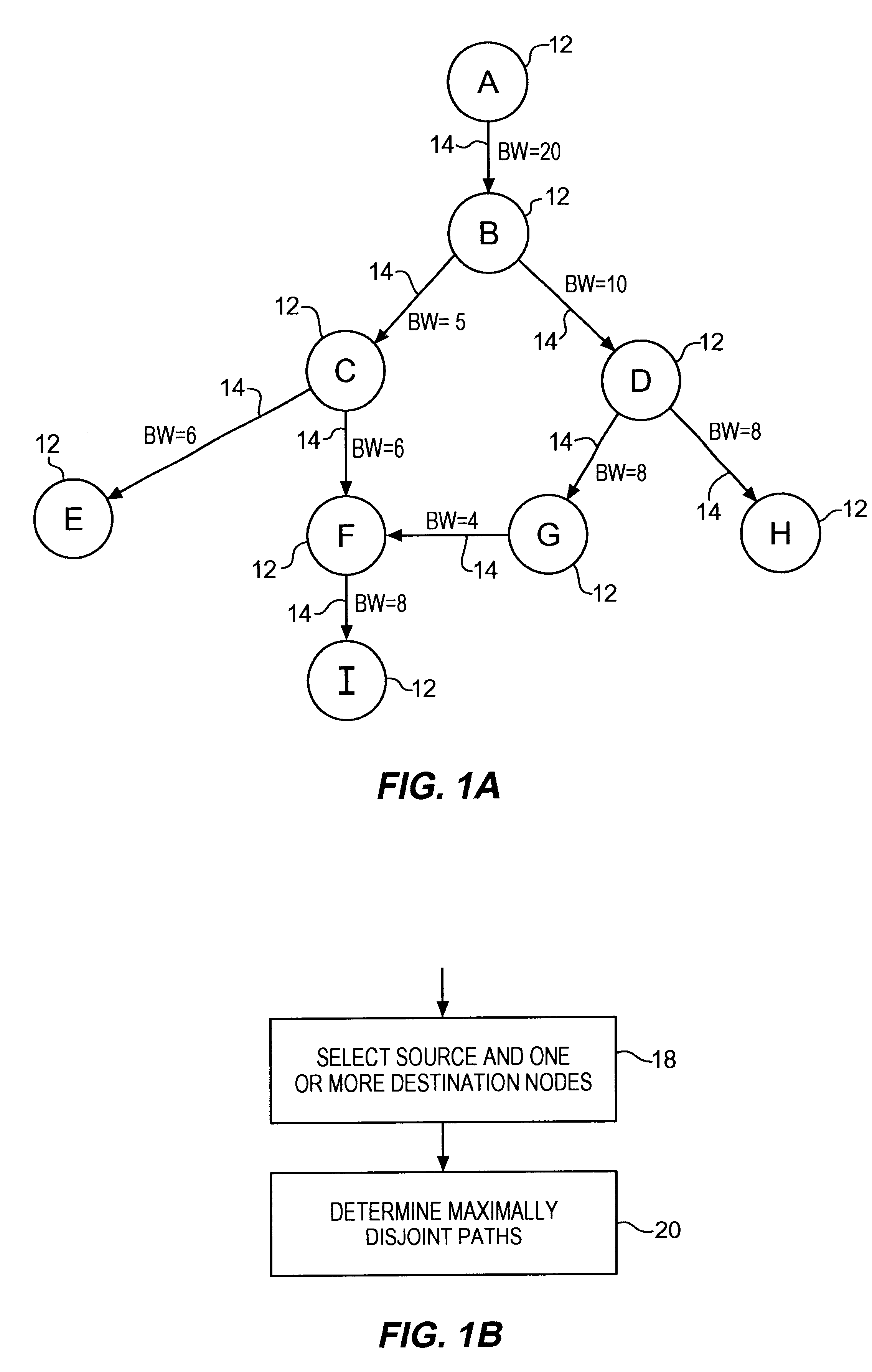
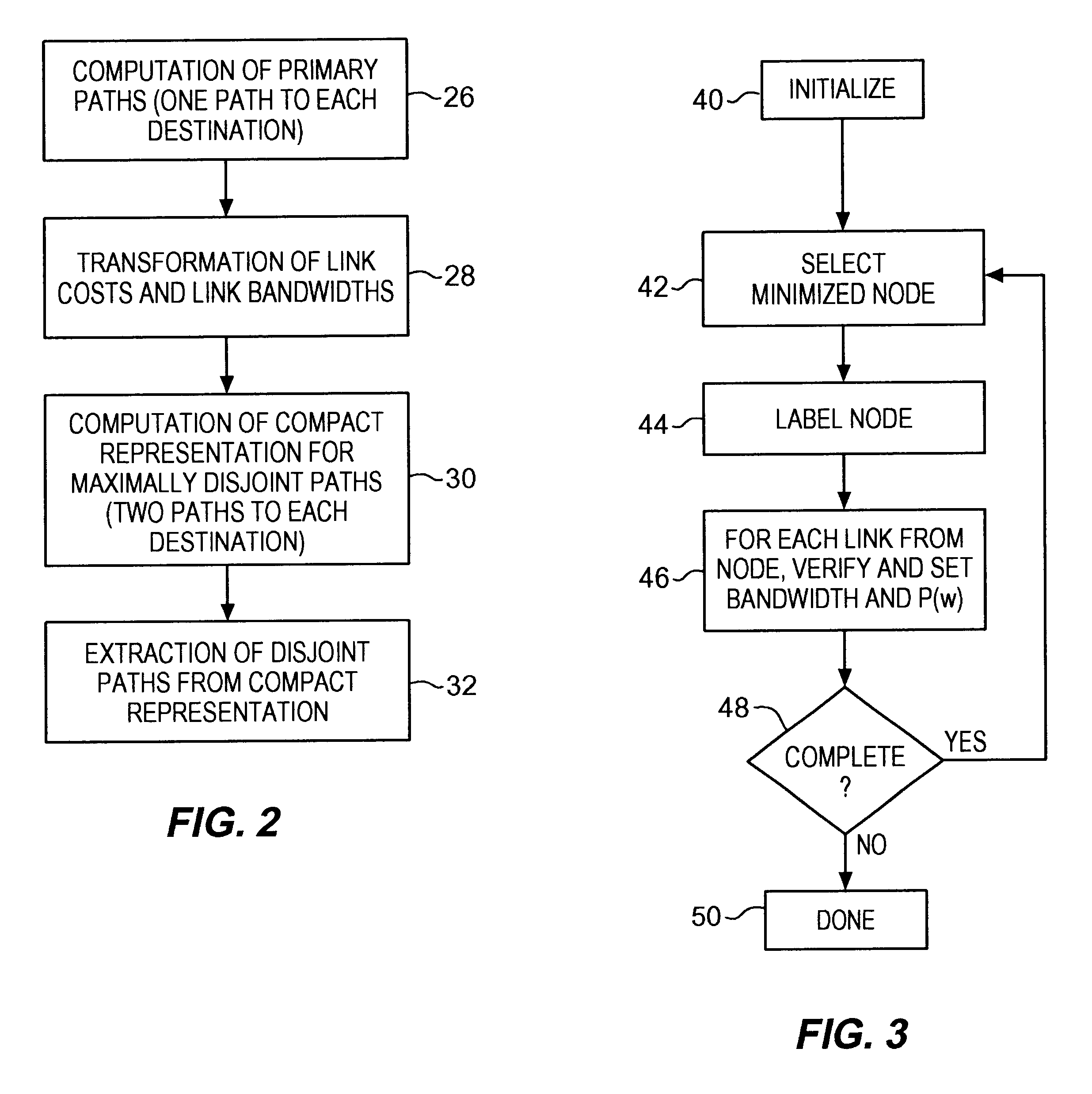
Communications network system and method for routing based on disjoint pairs of path
InactiveUS6542469B1Raise the possibilityMinimizes probabilityError preventionFrequency-division multiplex detailsPathPingHigh bandwidth
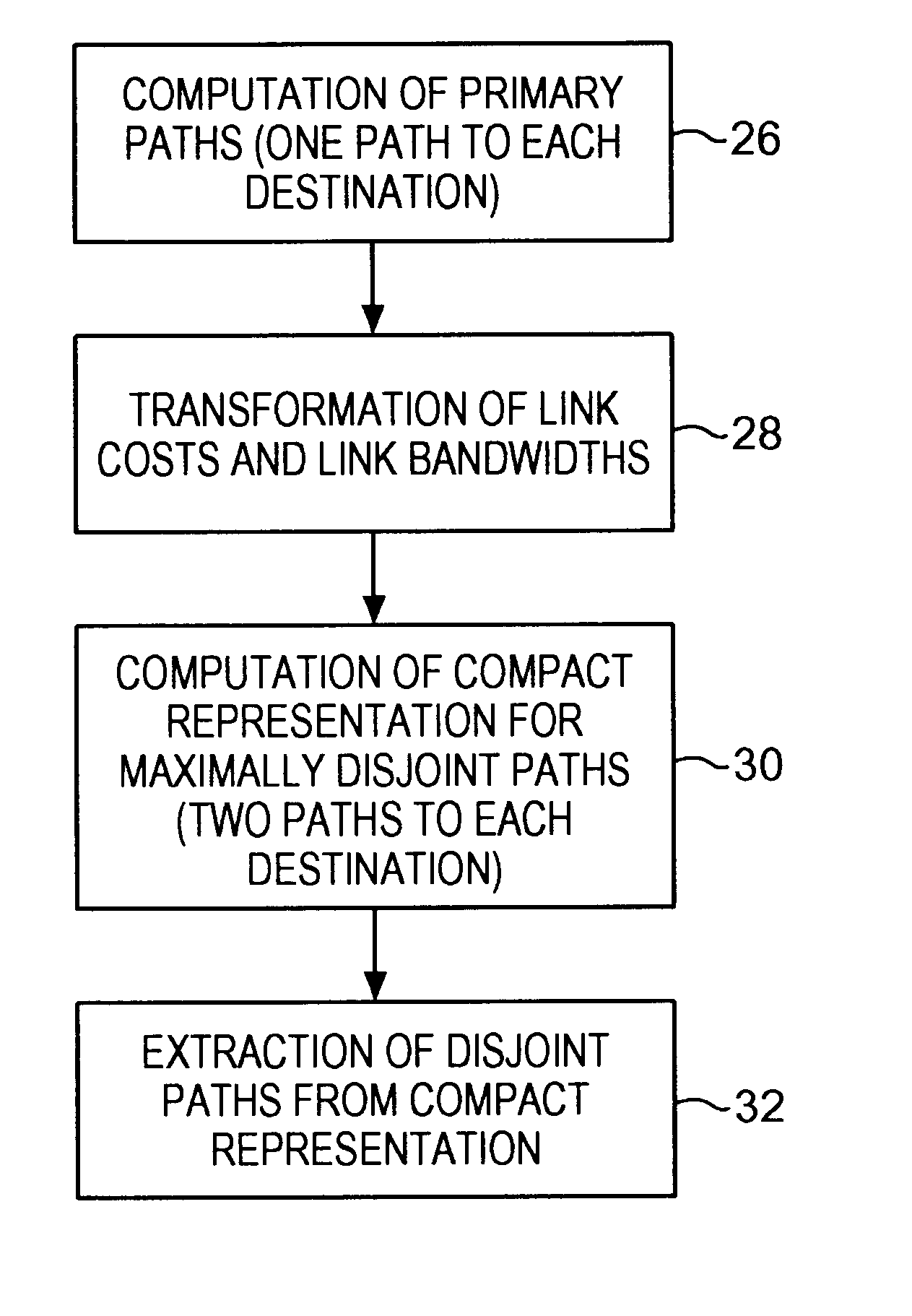
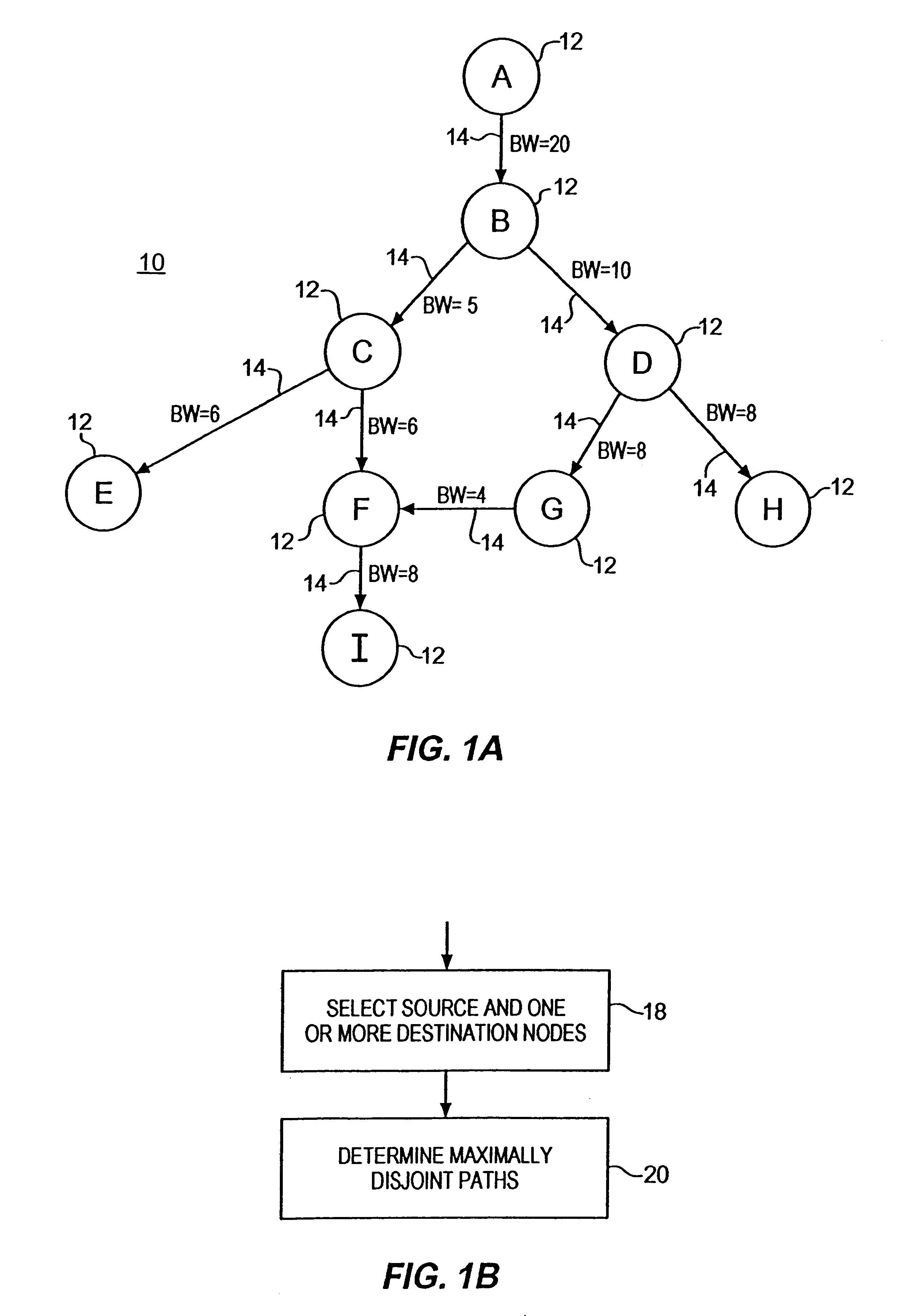
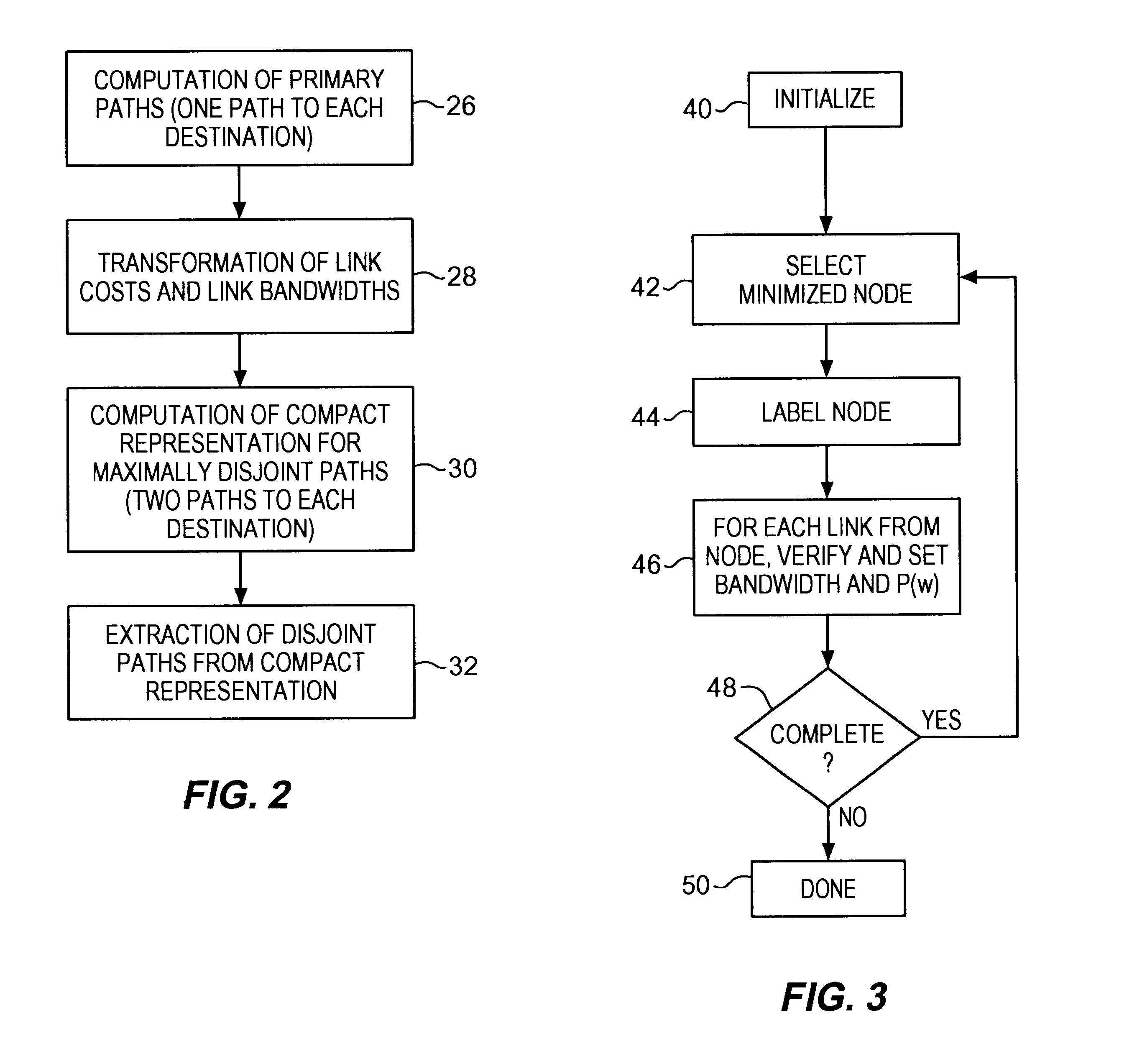
Methods for determining at least two pre-computed paths to a destination in a communications network are provided. The two paths are maximally disjoint. Maximally disjoint paths are paths where the number of links or nodes common to the two paths is minimized. This minimization is given a priority over other path considerations, such as bandwidth or cost metrics. By pre-computing a maximally disjoint pair of paths, the probability that an inoperable link or node is in both paths is minimized. The probability that the inoperable link or node blocks a transfer of data is minimized. Additionally, a pair of maximally disjoint paths is determined even if absolutely disjoint paths are not possible. The communications network may include at least four nodes, and maximally disjoint pairs of paths are pre-computed from each node to each other node. A third path from each node to each other node may also be computed as a function of bandwidth or a cost metric. Therefore, the advantages of the maximally disjoint pair of paths are provided as discussed above and a path associated with a higher bandwidth or lower cost is provided to more likely satisfy the user requirements of a data transfer.
Owner:SPRINT CORPORATION
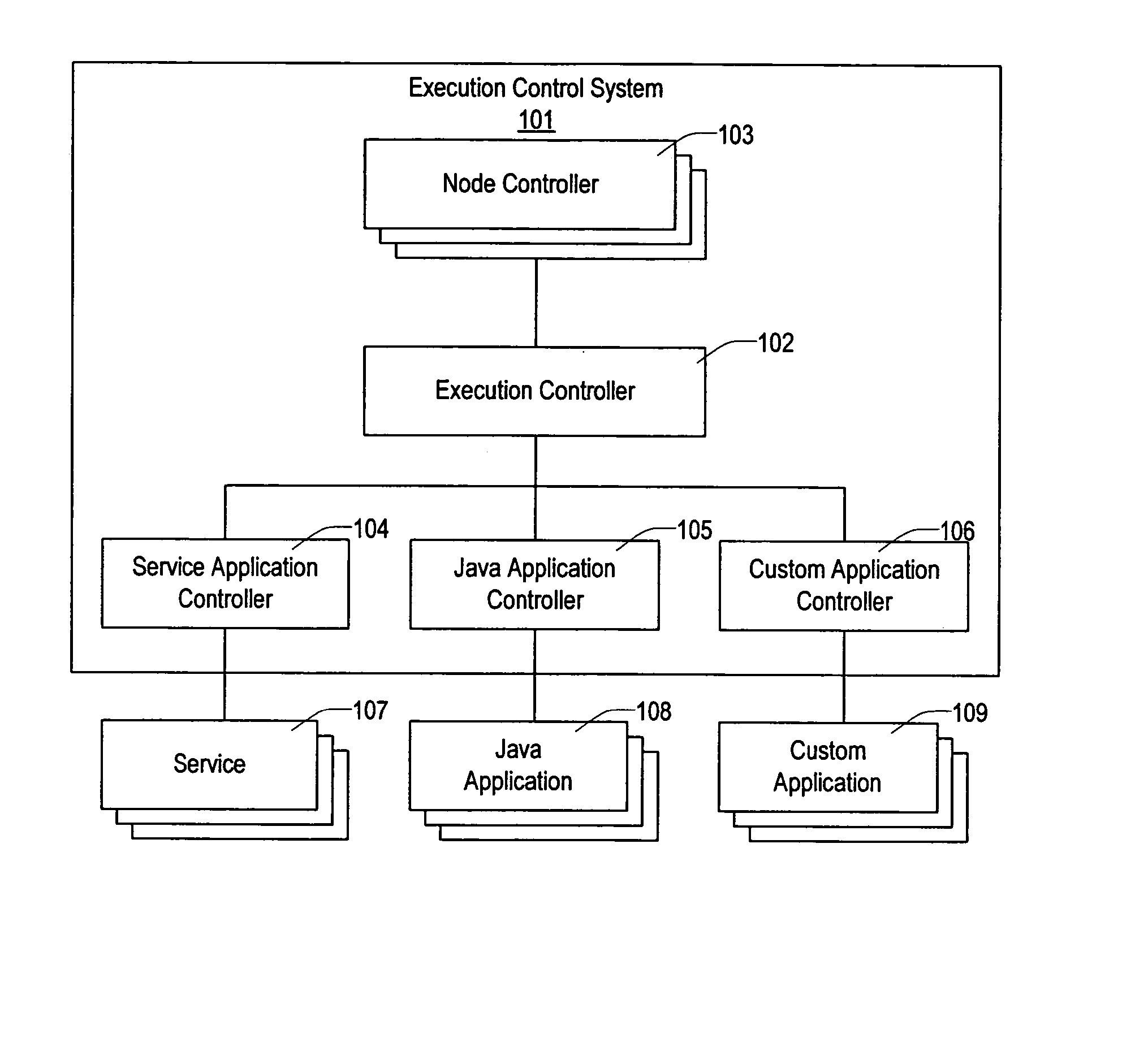
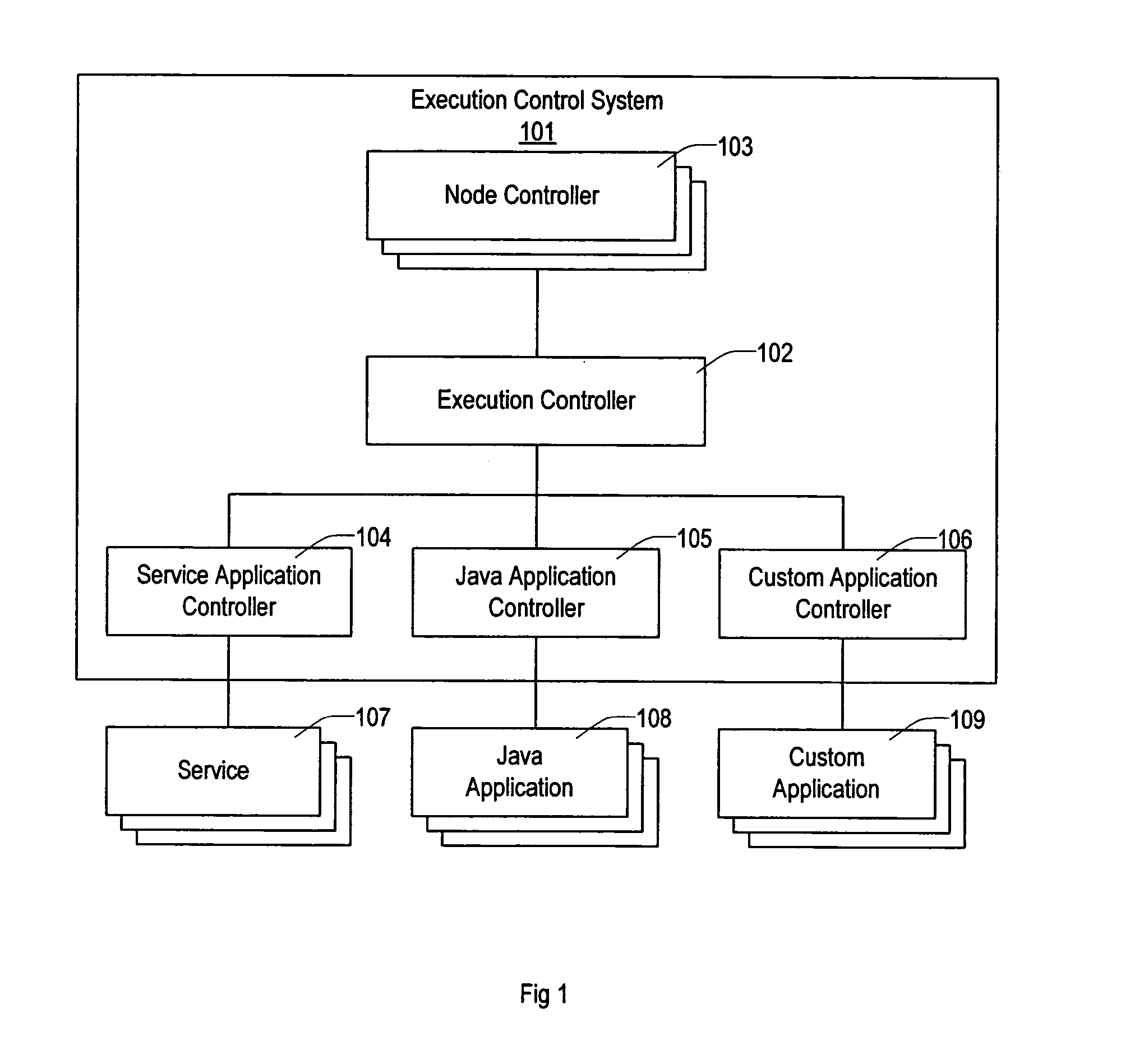
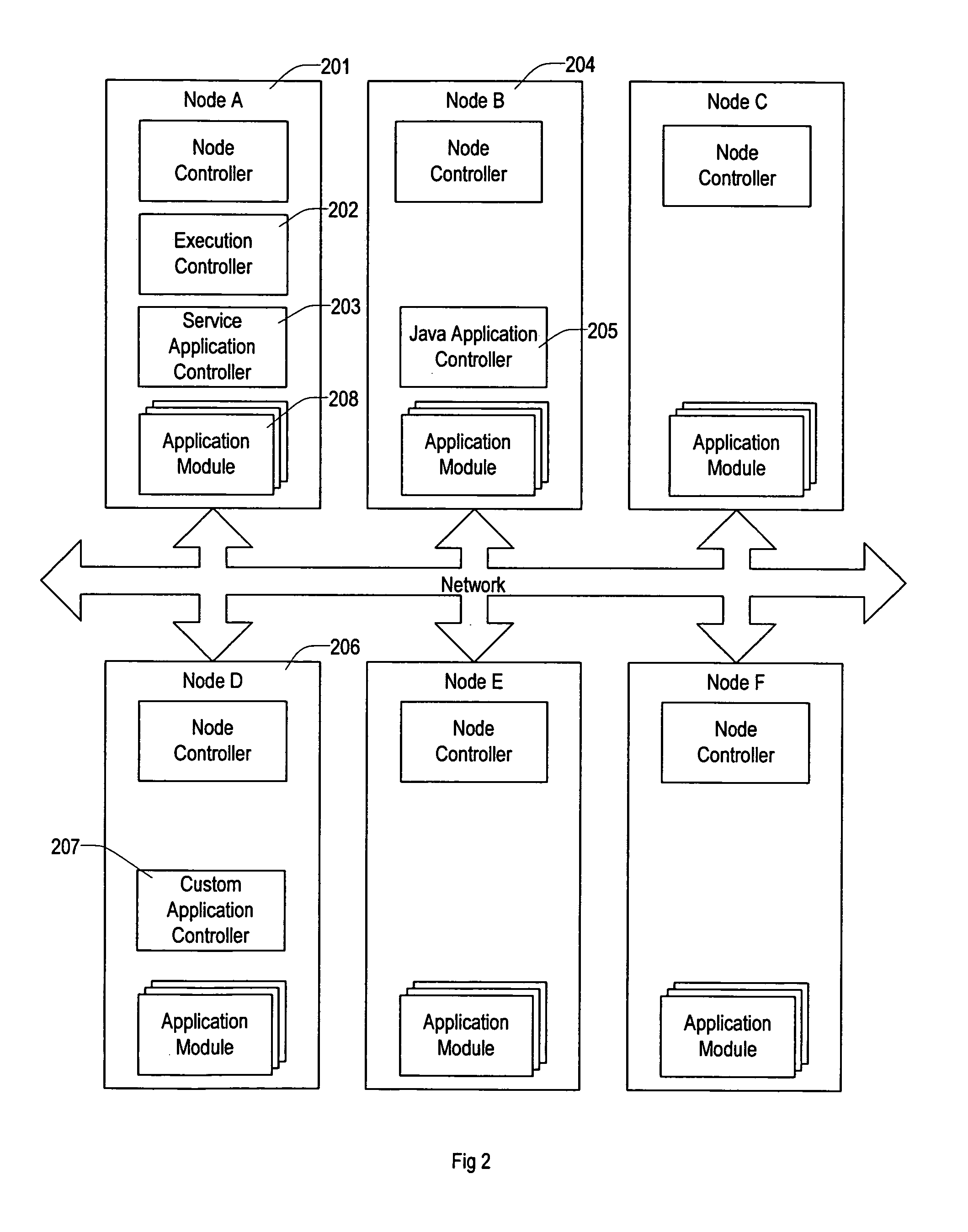
Method and apparatus for executing applications on a distributed computer system
ActiveUS7302609B2Simplify the management processEasy to manageDigital data processing detailsError detection/correctionControl systemComputerized system
Owner:VLADIMIR MATENA +1
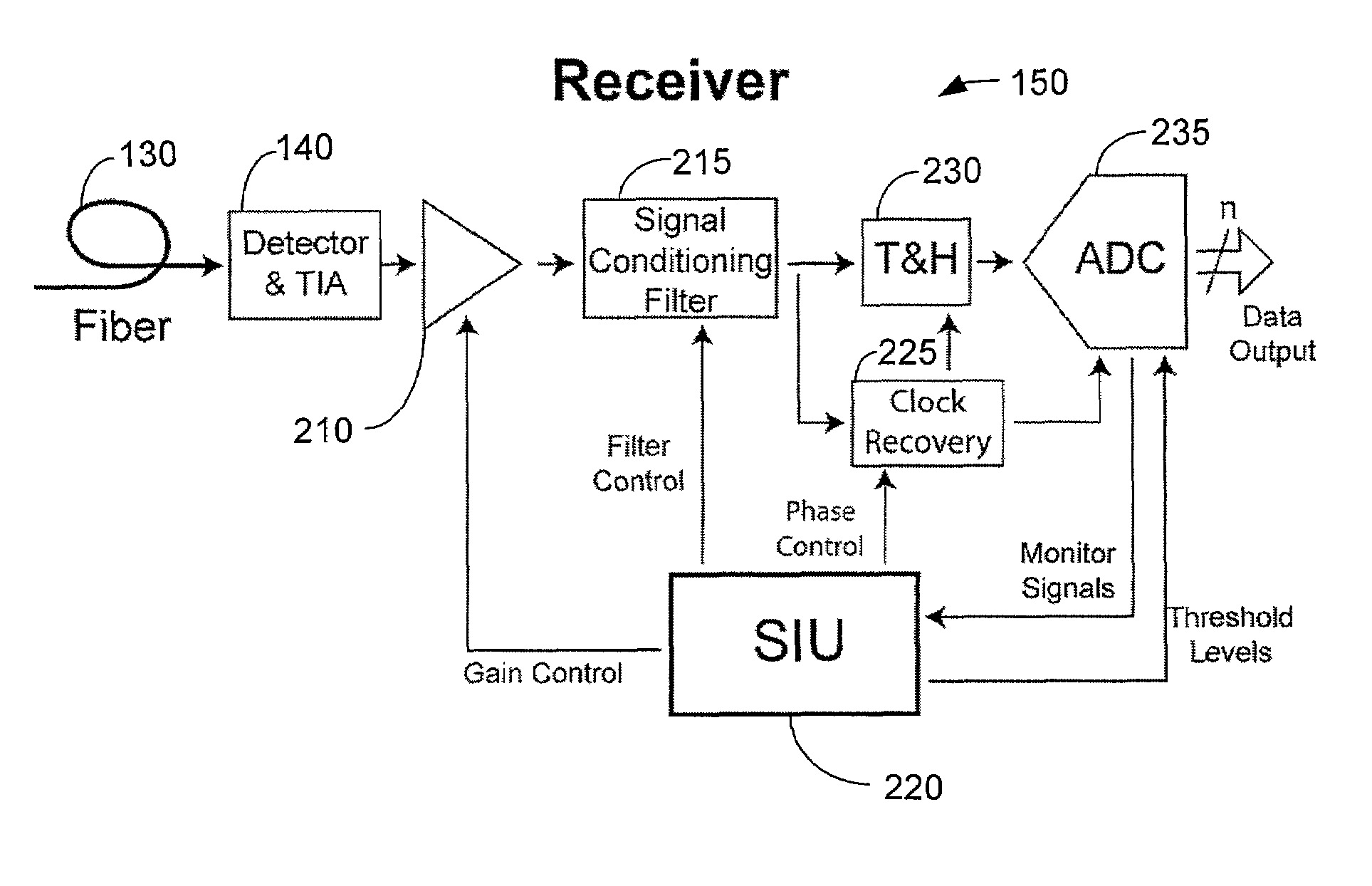
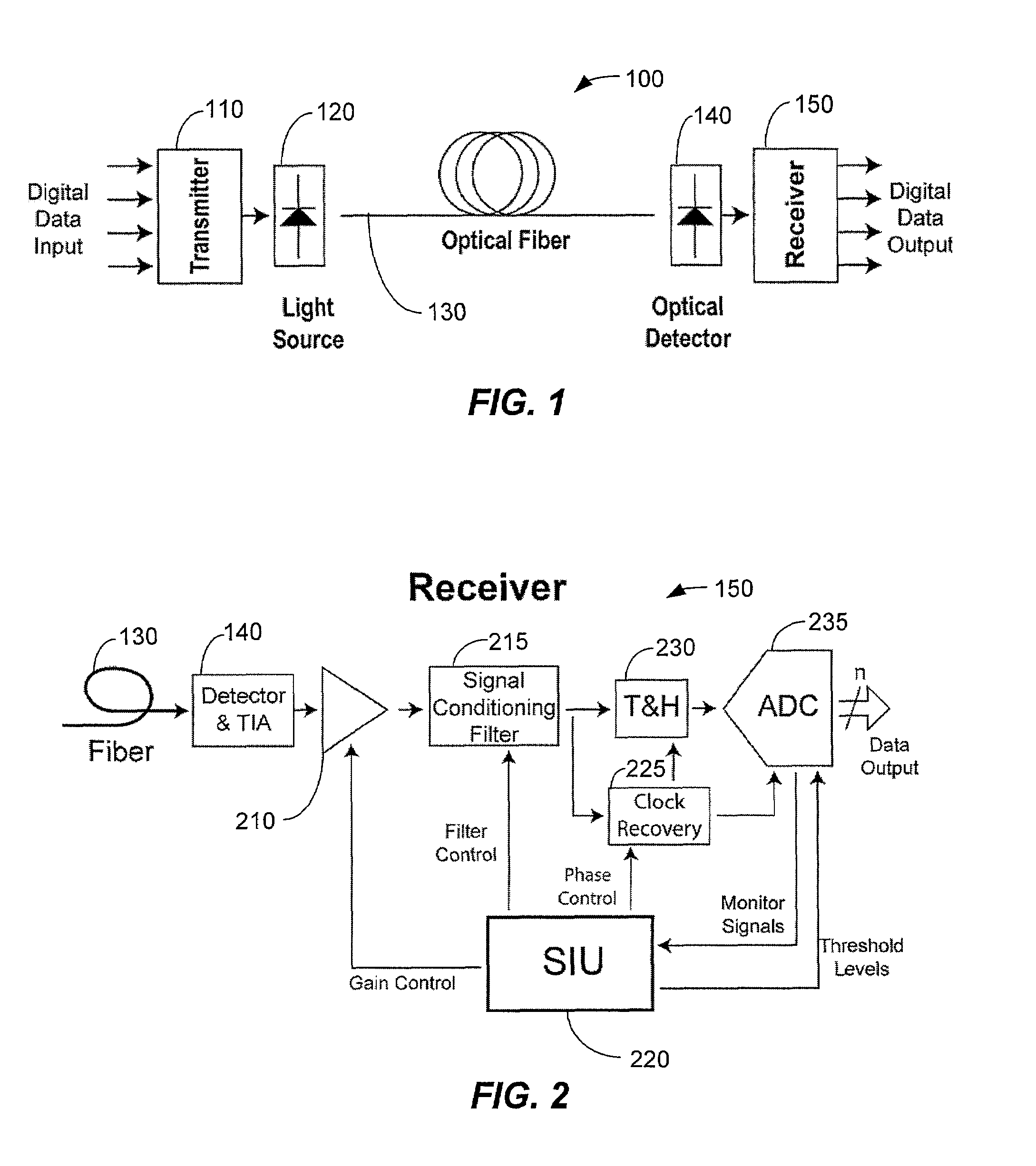
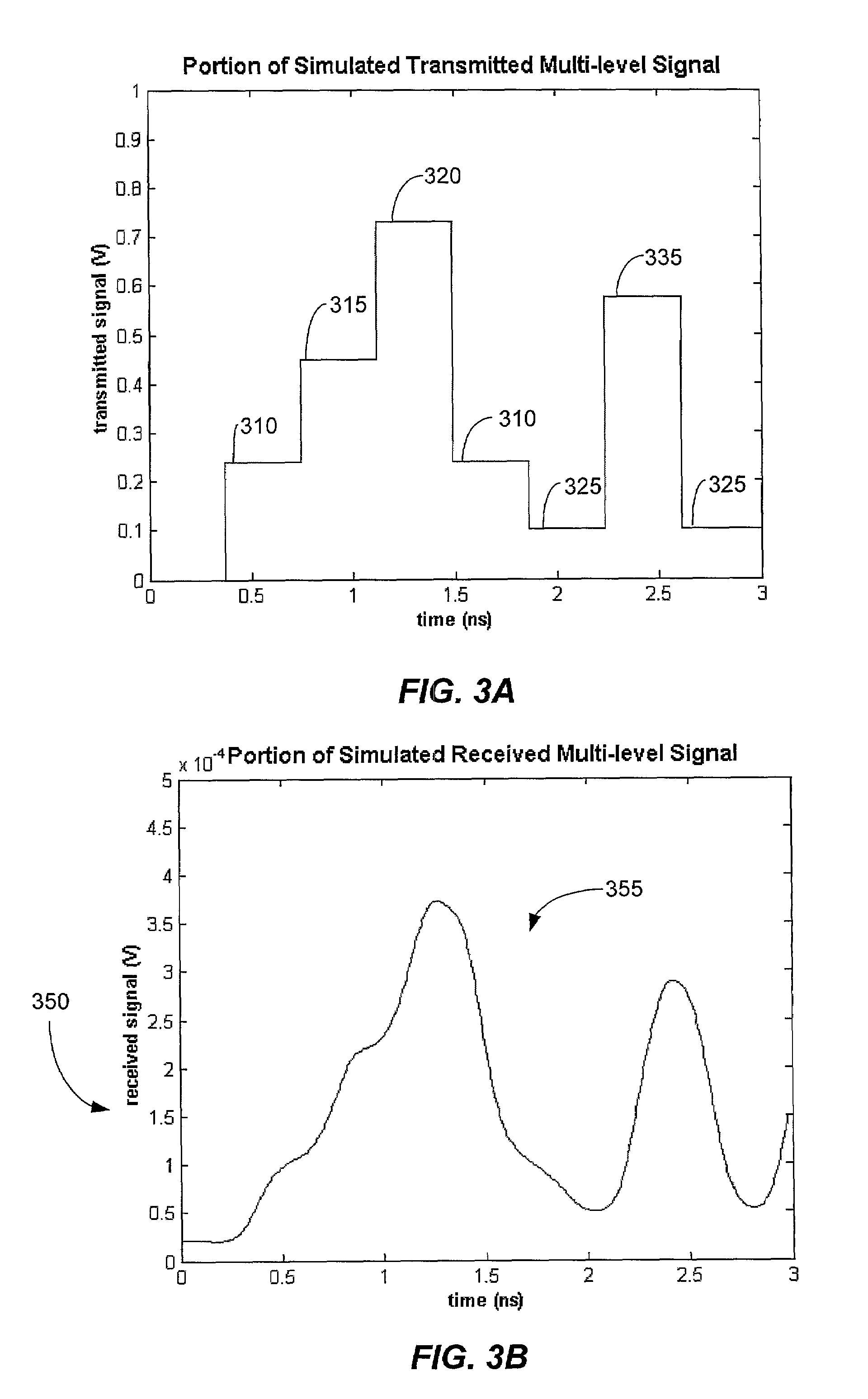
Method and system for decoding multilevel signals
ActiveUS7215721B2Efficient processingMinimizes average error probabilityRepeater/relay circuitsDc level restoring means or bias distort correctionNormal densityAutomatic control
A multilevel optical receiver can comprise a plurality of comparators that generally correspond with the number of levels in a multilevel data stream. Each comparator can be individually controlled and fed a decision threshold in order to decode a multilevel signal. The multilevel optical receiver can generate a statistical characterization of the received symbols in the form of a marginal cumulative distribution function (CDF) or probability density function (pdf). This characterization can be used to produce a set of ε-support estimates from which conditional pdfs are derived for each of the transmission symbols. These conditional pdfs may then be used to determine decision thresholds for decoding the received signal. The conditional pdfs may further be used to continuously estimate the fidelity or error rate of the received signal without the transmission of a testing sequence. The ε-supports may further be used to automatically control the gain on the receiver.
Owner:INTERSIL INC
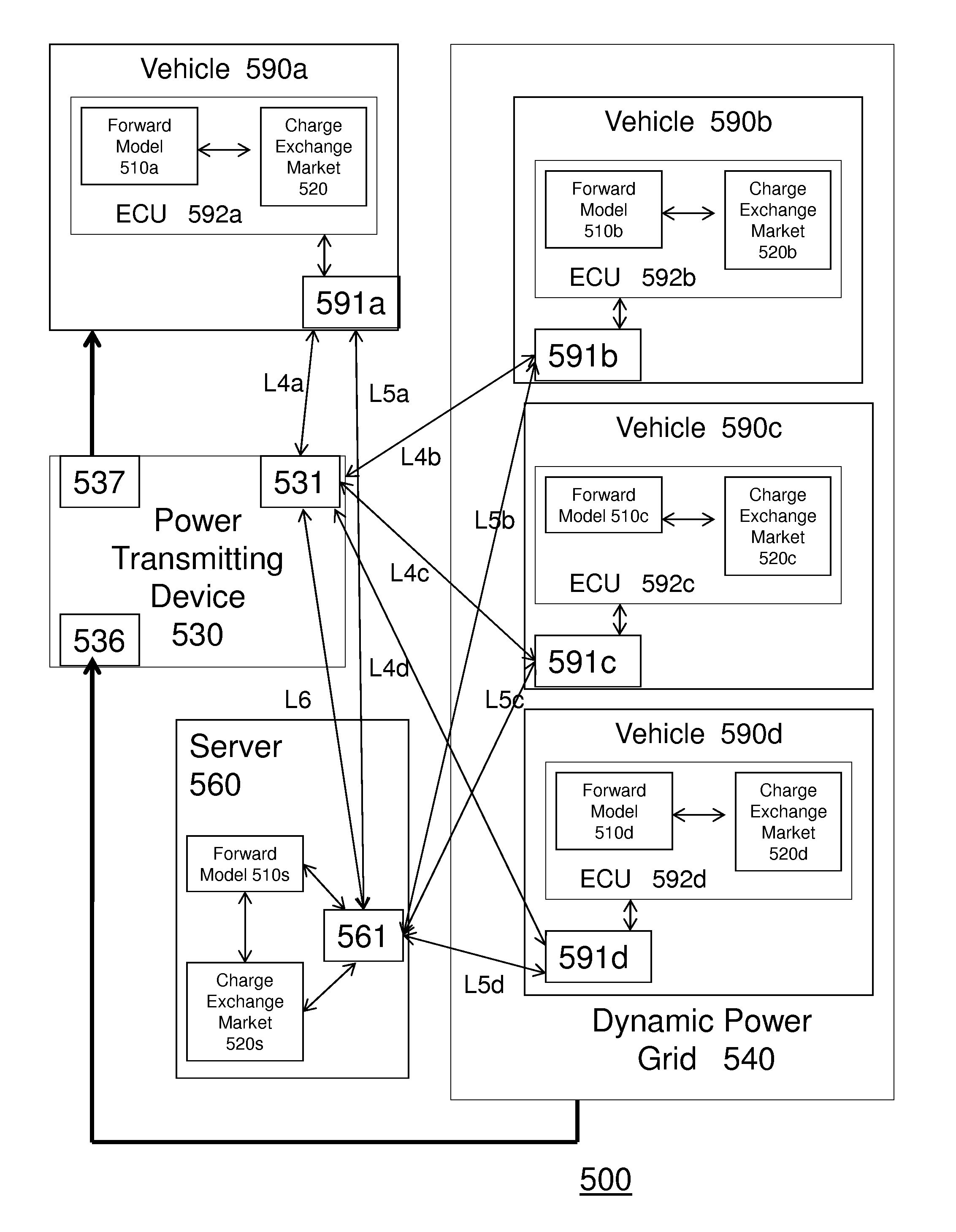
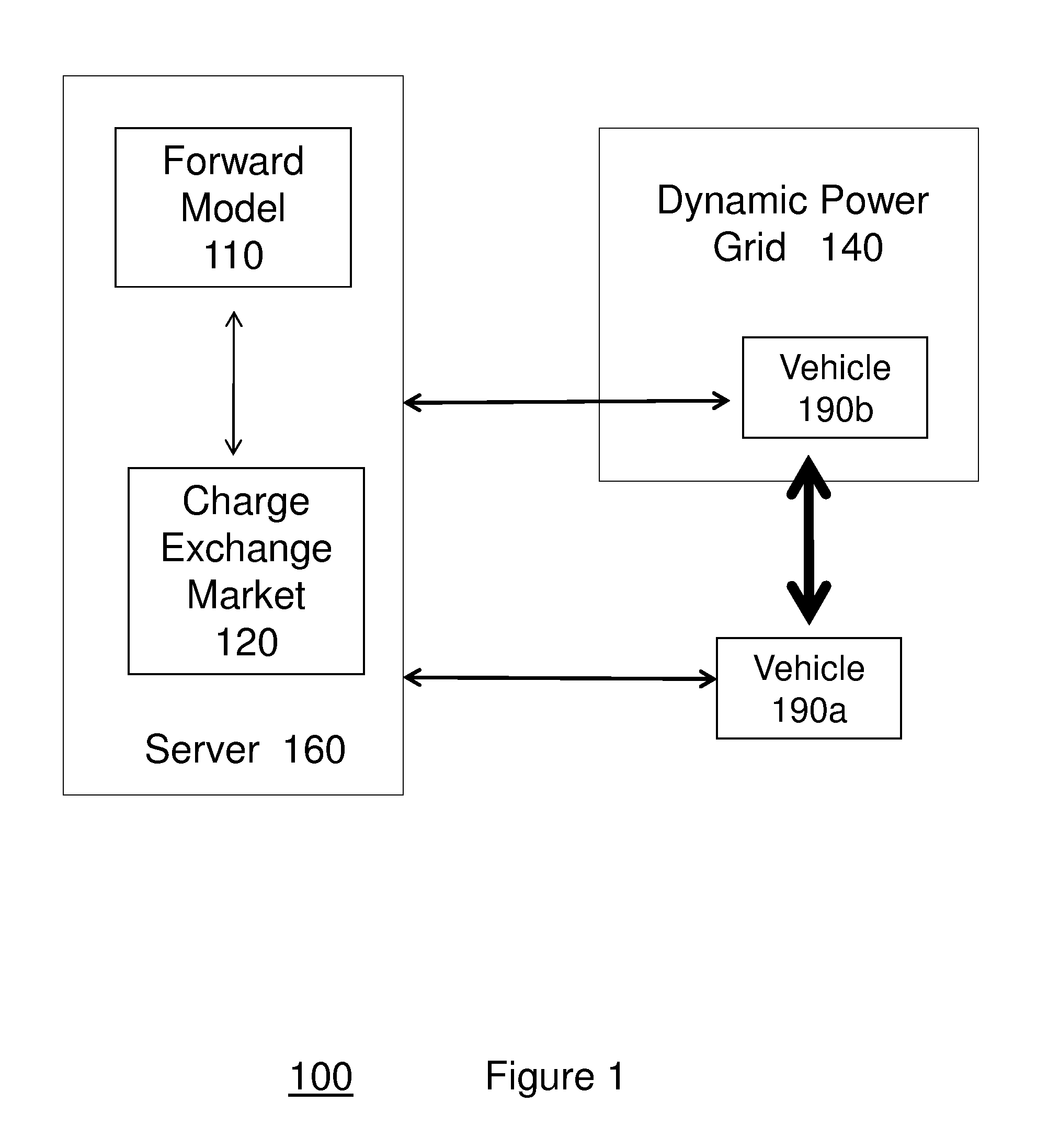
System and method of charging a vehicle using a dynamic power grid, and system and method of managing power consumption in the vehicle
ActiveUS20130204471A1The process is convenient and fastFacilitates agreementDigital data processing detailsNavigation instrumentsTransmitted powerCharge exchange
A system for charging a vehicle includes a forward model for modeling vehicle charging data for a plurality of vehicles, and a charge exchange market which, based on the forward model, facilitates an agreement for transmitting power to a first vehicle of the plurality of vehicles via a dynamic power grid including a second vehicle of the plurality of vehicles. A system of managing power consumption in the vehicle includes, an optimizing unit for optimizing a plurality of parameters to determine a power to be consumed by the vehicle based on a plurality of power source signatures for a plurality of power sources, and an operating mode setting unit for setting an operating mode for powering the vehicle based on the determined power.
Owner:IBM CORP
Sterilized safety syringe
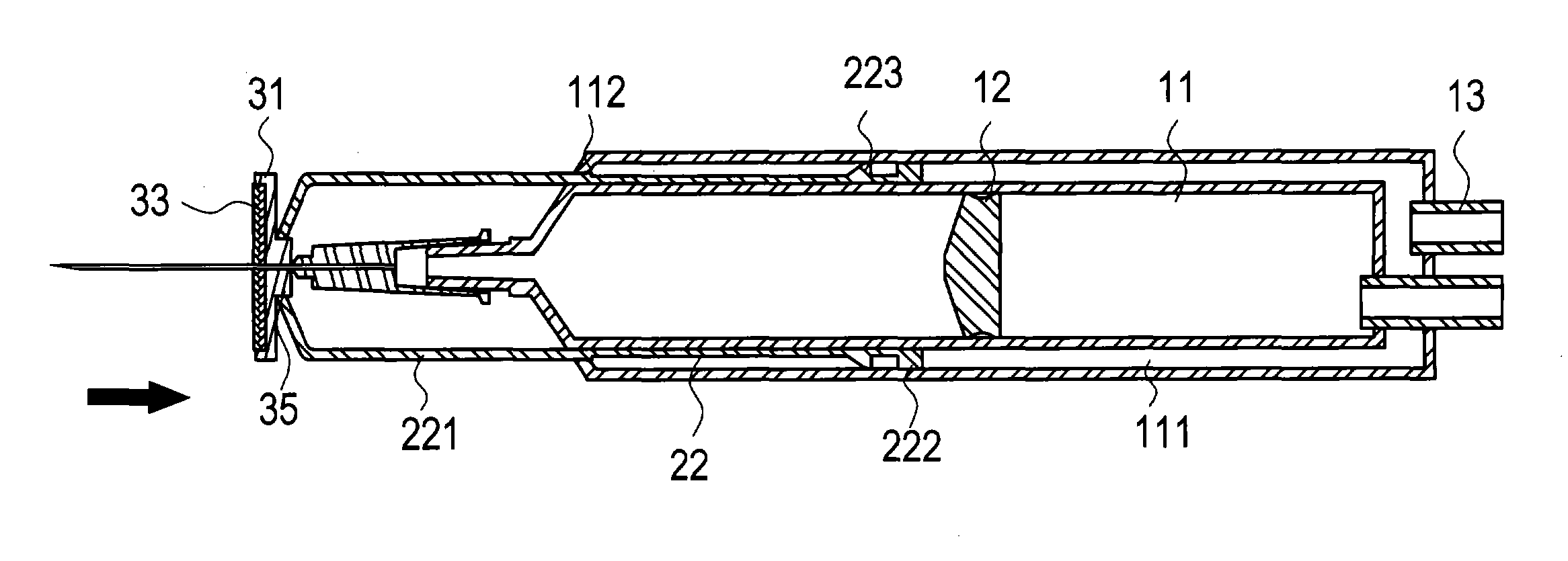
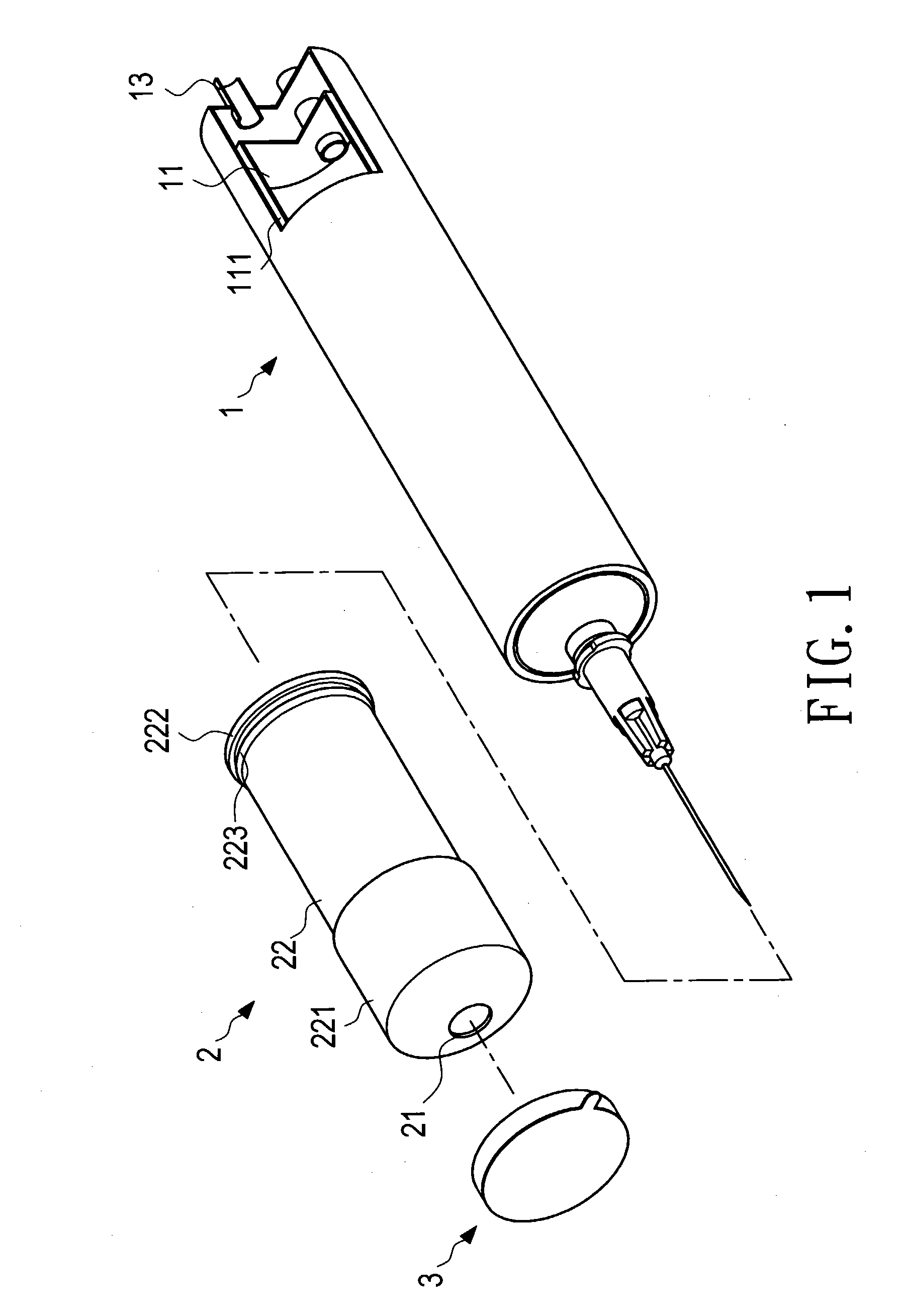
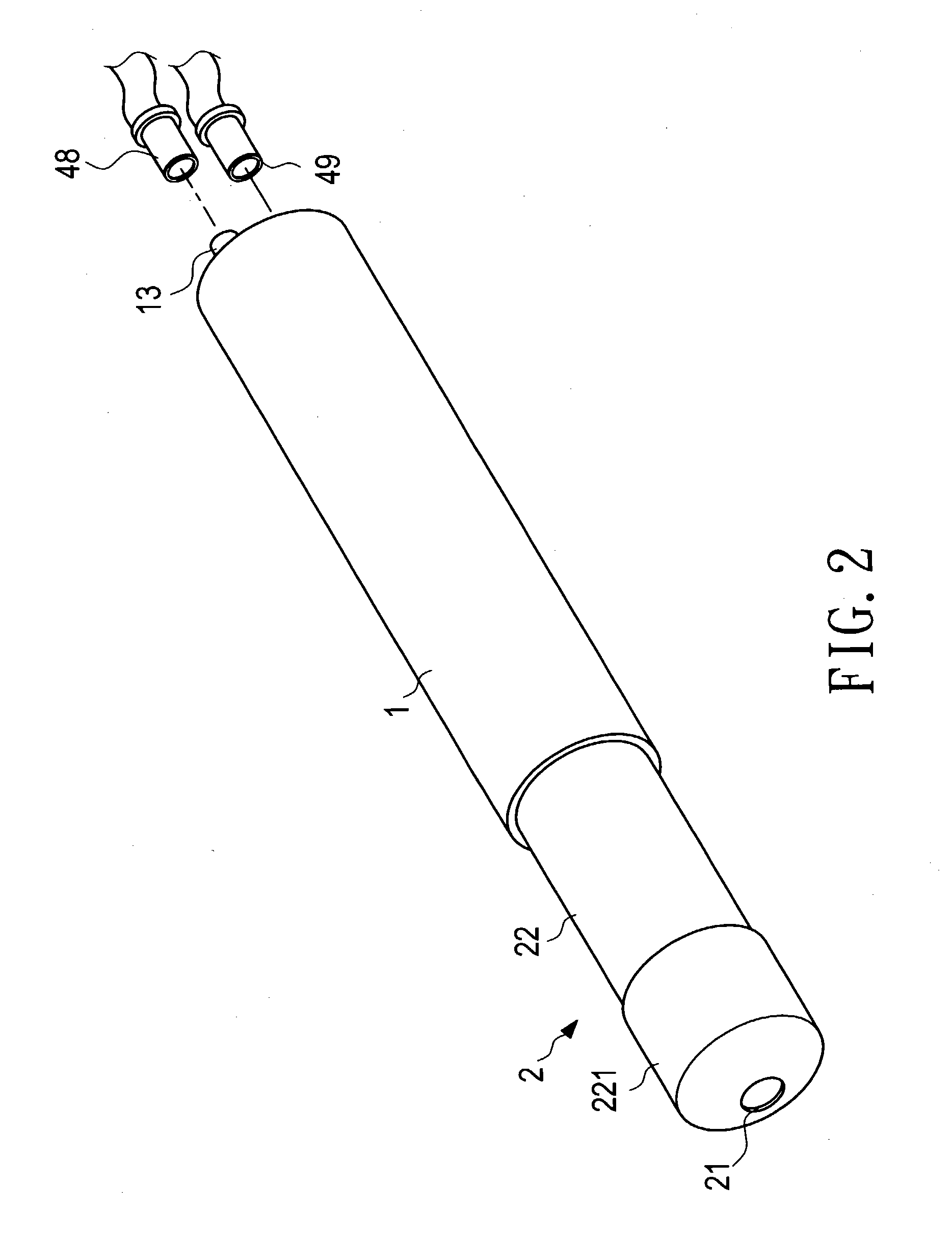
InactiveUS20050015055A1Improve protectionMinimizes probabilityAutomatic syringesMedical devicesEngineeringSlide plate
A sterilized safety syringe comprises a syringe tube, a protective cover, a sterilizer, and an air compressor. The protective cover is slid into a guide slot of the syringe tube with several sliding plates whose rear ends are closely in contact with the wall of the guide slot with their annular flanges. The syringe tube are equipped with several air conducting pipes which are connected with corresponding air feeding pipes of the air compressor. A plug is formed at the rear end of the sterilizer to be plugged into a drilled hole formed on the protective cover. Due to existence of perfectly effective sterilizer, the medical staffs never have to worry about infectant contamination brought about from inadvertent contact with the patient body fluid.
Owner:YANG CHANG MING
Resource allocation scheduling method for a cellular communication system
InactiveUS20050282550A1High efficiencyIncrease frequency reuse rateNetwork topologiesBroadcast service distributionFrequency bandCellular communication systems
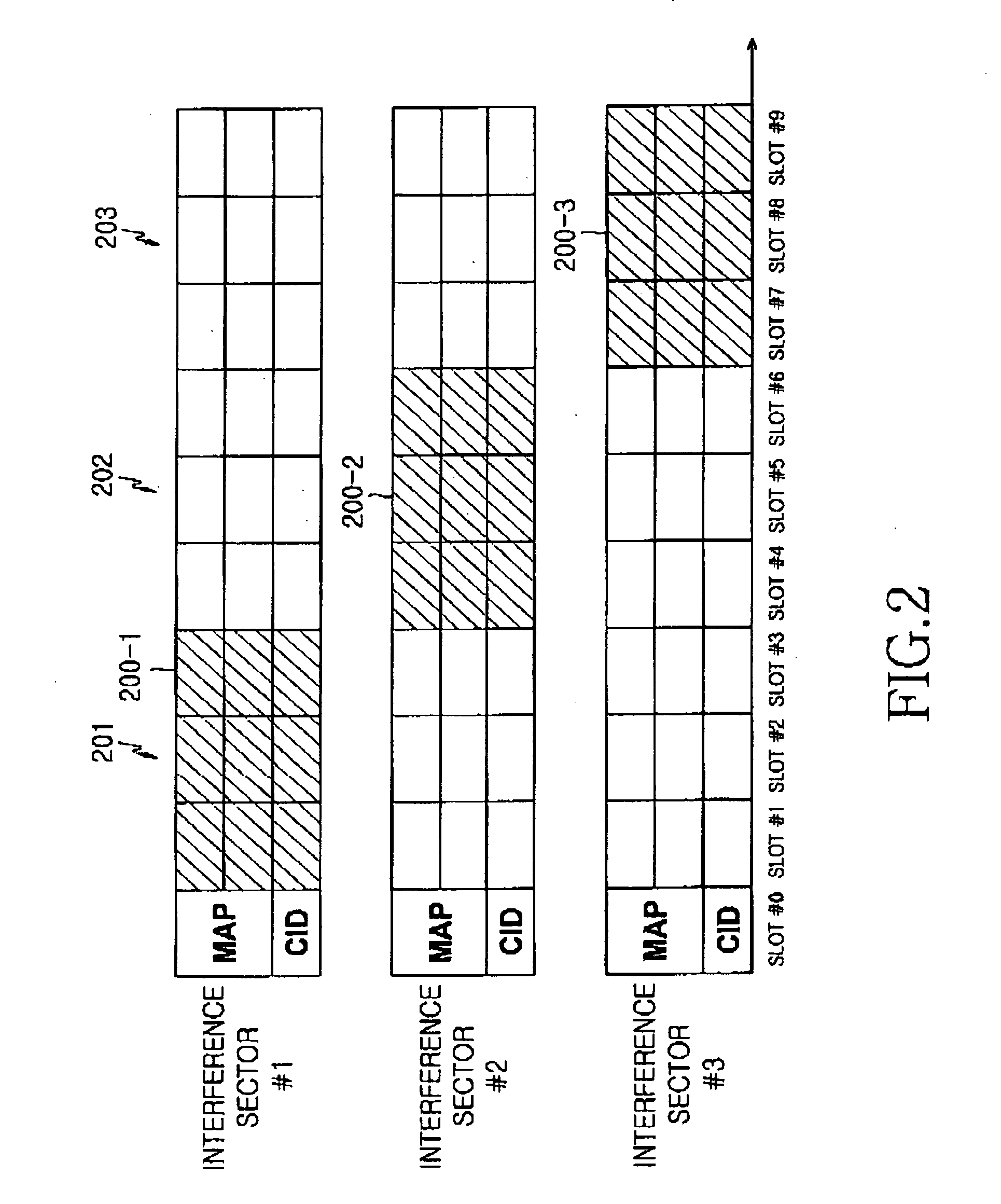
A resource allocation scheduling method for a cellular communication system that can avoid interference between cells. The method includes dividing a frequency band of a system into frames each having preferential allocation blocks and general allocation blocks on a time axis, classifying terminals in each cell into groups of terminals vulnerable to interference and terminals non-vulnerable to interference, and allocating resources by terminal groups according to priority orders given to the terminal groups. The preferential allocation resources designed to have the orthogonality to the interference cells, i.e., sectors, on the time axis are allocated to the terminals vulnerable to the interference, and the remaining resources are allocated to the terminals non-vulnerable to the interference.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Communications network system and method for routing based on disjoint pairs of paths
InactiveUS6804199B1Raise the possibilityMinimizes probabilityError preventionTransmission systemsCost metricHigh bandwidth
Owner:SPRINT CORPORATION
Front-loading adjustable safety utility knife with safety quick-release lock
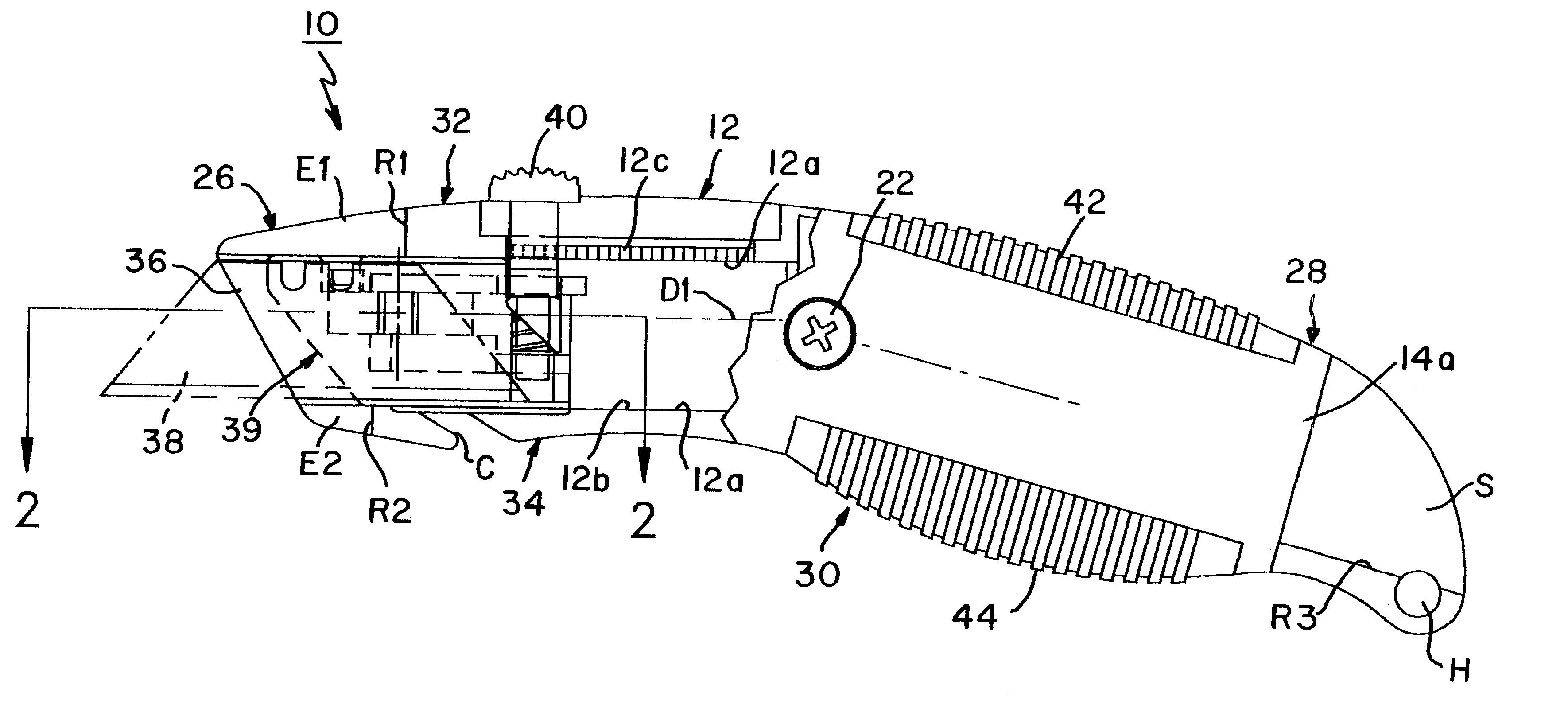
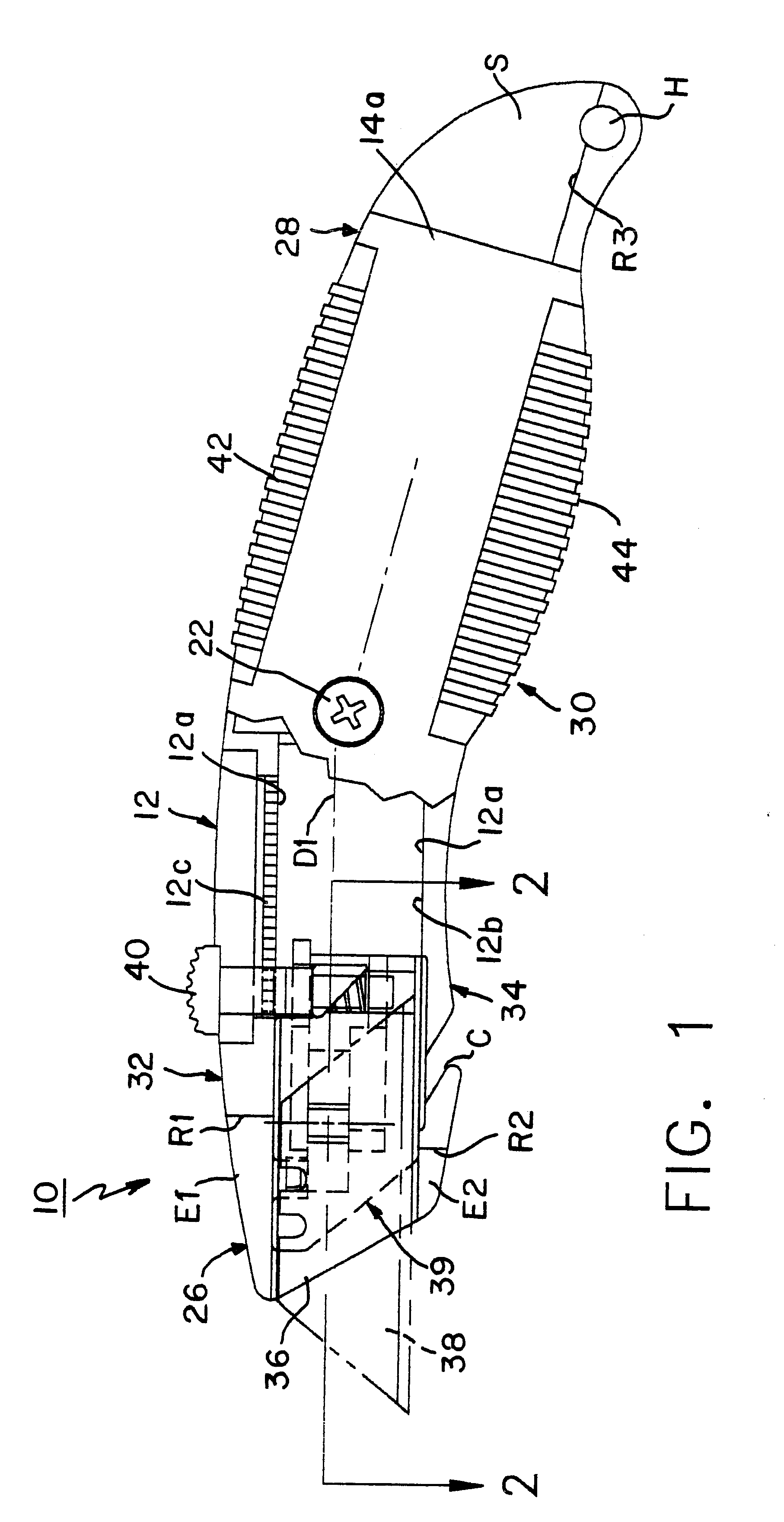
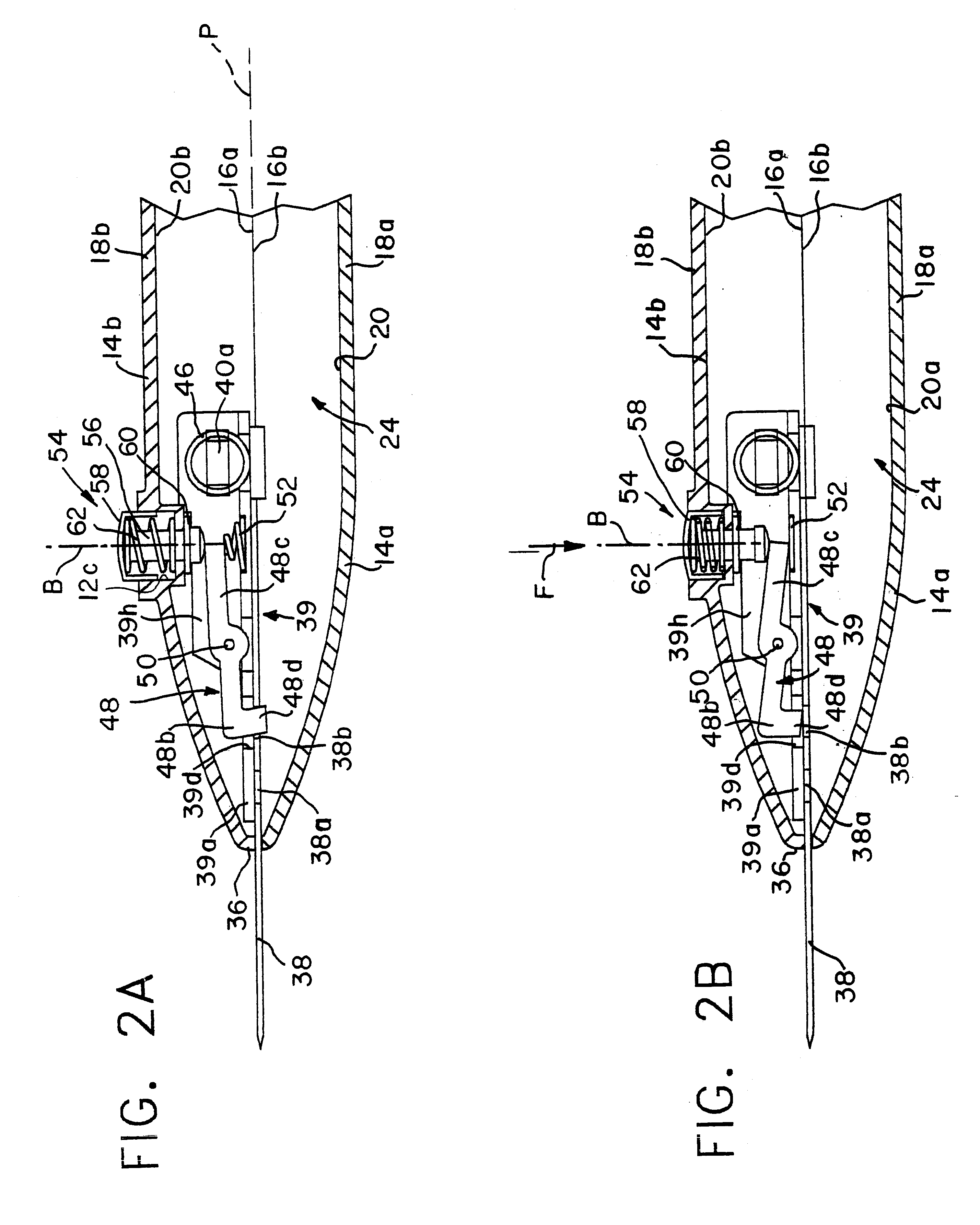
InactiveUS6357120B1Easy constructionReduce manufacturing costThrusting weaponsWeapon componentsInternal cavityFront loading
An adjustable safety utility knife includes an elongated ergonomically shaped handle formed of two elongate shell members each having a peripheral edge and an outer generally convex surface and an inner generally concave surface. The shell members are fastened at the peripheral edges along a vertical parting plane to form an elongated internal cavity. The handle defines a front end, a back end and an intermediate portion suitable for being gripped by a user and also defining top and bottom surfaces extending along opposite sides of the shell members along the peripheral edges. The handle has a slot-like aperture at the front end substantially aligned with the parting plane and dimensioned for passage of a flat cutting blade therethrough. A guide element within the elongated cavity guides the cutting blade between a first position for safely storing the blade fully inside the cavity and a second position for selectively extending the blade beyond the aperture to expose at least a portion thereof. A manually operated button is arranged on the top surface and coupled to the guide element for selectively moving the blade between the first and second positions. The guide element includes a carriage within the elongated internal cavity for supporting a flat cutting blade and guide elements on at least one of the inner generally concave surfaces for guiding the carriage and cutting blade carried thereby between the first and second positions. The carriage includes a locking element for normally locking a cutting blade mounted thereon to substantially fix the cutting blade against relative longitudinal movements between the cutting blade and carriage. The locking element includes an unlocking element the actuation of which releases the cutting blade to permit relative longitudinal movements between the cutting blade and the carriage. A blade release element on one of the shell members actuates the unlocking element when manual force is applied thereto, whereby application of a force on the release element releases the cutting blade and enables it to be withdrawn through the front end aperture.
Owner:OLYMPIA IND +1
Method and system for providing a fault tolerant display unit in an electronic device
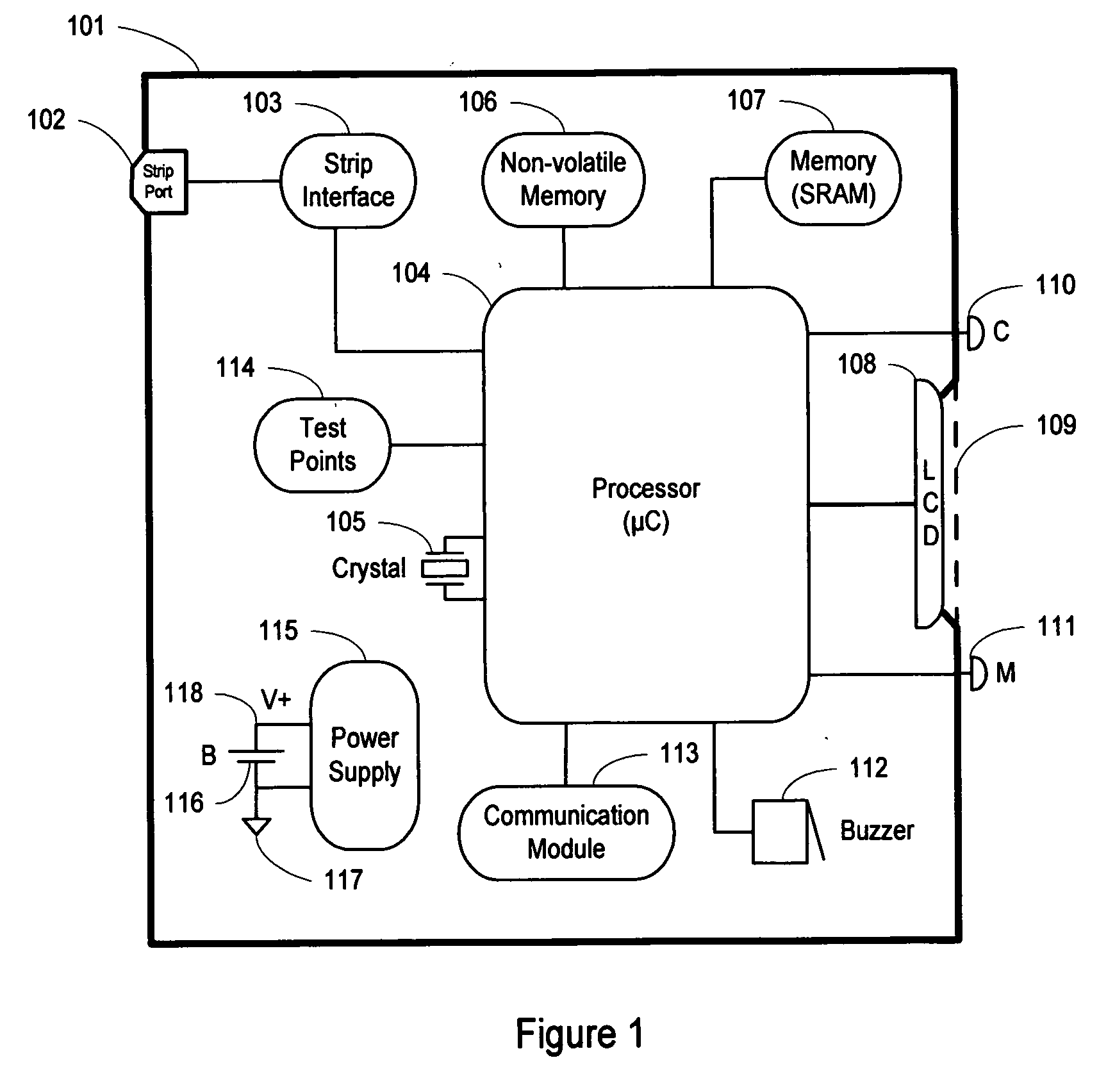
ActiveUS20070176867A1Minimize probabilityReduce effectLocal control/monitoringStatic indicating devicesGlucose meter deviceEngineering
Method and apparatus for providing a fault tolerant display unit for an electronic device such as a glucose meter, including display unit, and a controller unit operatively coupled to the display unit, the controller unit configured to control the display unit to display an information, where when a failure mode of the display unit occurs, the display unit is configured to display a modified information, where the modified information is different from the information for display under the control of the controller unit, is provided.
Owner:ABBOTT DIABETES CARE INC
Collision prevention method for RFID system and RFID system
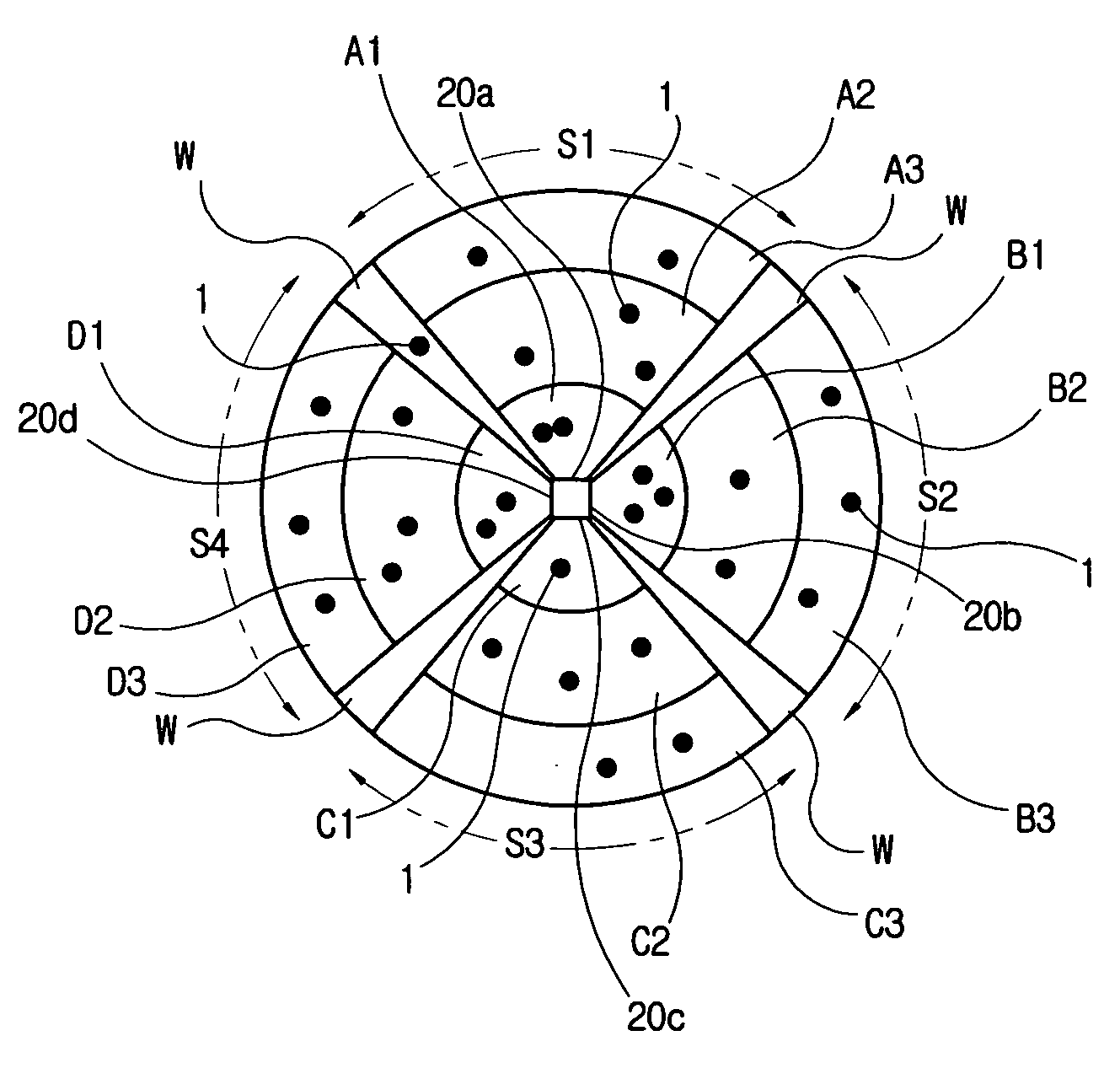
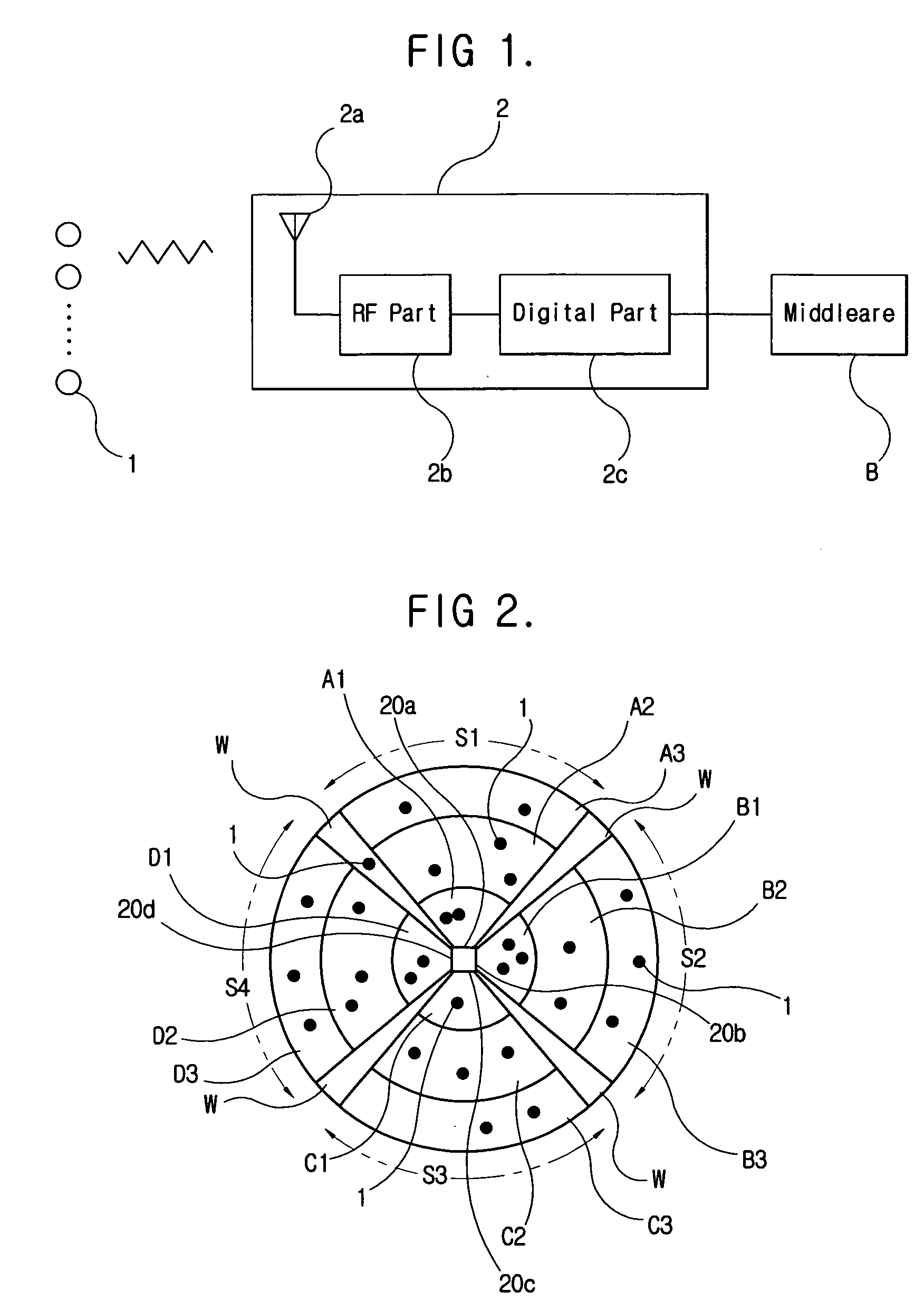
InactiveUS20060012465A1Minimizes probabilityImprove communication distanceMemory record carrier reading problemsSubscribers indirect connectionEngineeringTime-Consuming
The present invention relates to a collision prevention method for a RFID system and a RFID system to minimize the collision of response signals by using sector antennas and controlling the power. The present invention comprises the steps of: separating plural tags in a space by setting up plural number of sector antennas; setting up the output stages of the power of each sector antenna to be increased in plural sequential stages; and reading a tag belonging to the output range by selecting a first sector antenna and transmitting minimum power among the set up stages. The present invention considerably reduce the collision probability of response signals of tags by dividing the tags in a space when a reader reads or writes tag information. The present invention also minimizes the time consumed to read / write tags and improves the communication distance and capacity.
Owner:NESSLAB
Method & apparatus for an interlocking control device
ActiveUS20090143928A1Improve securityImprove operational flexibilityDigital data processing detailsPoint-signal interlocking arrangmentsChange managementEngineering
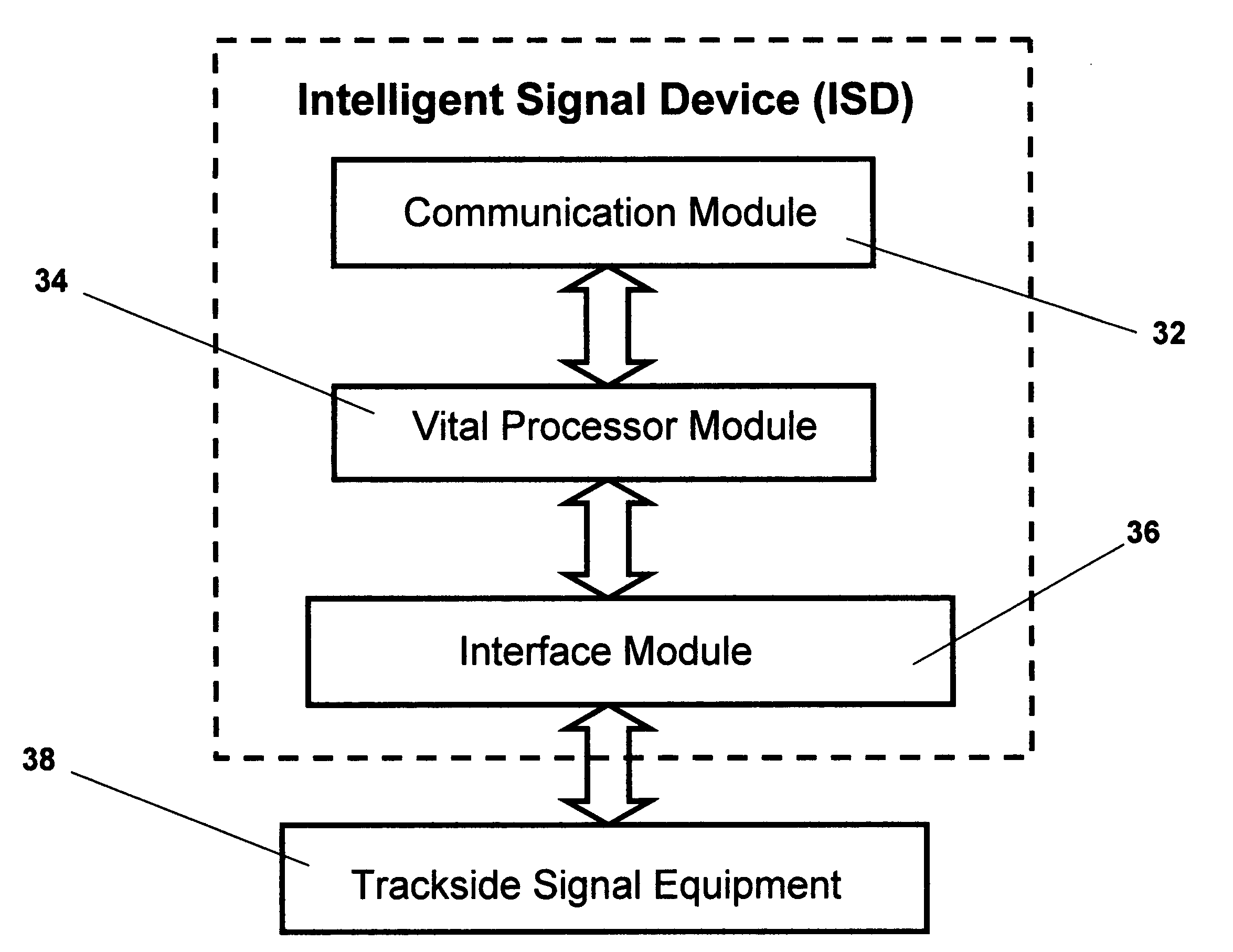
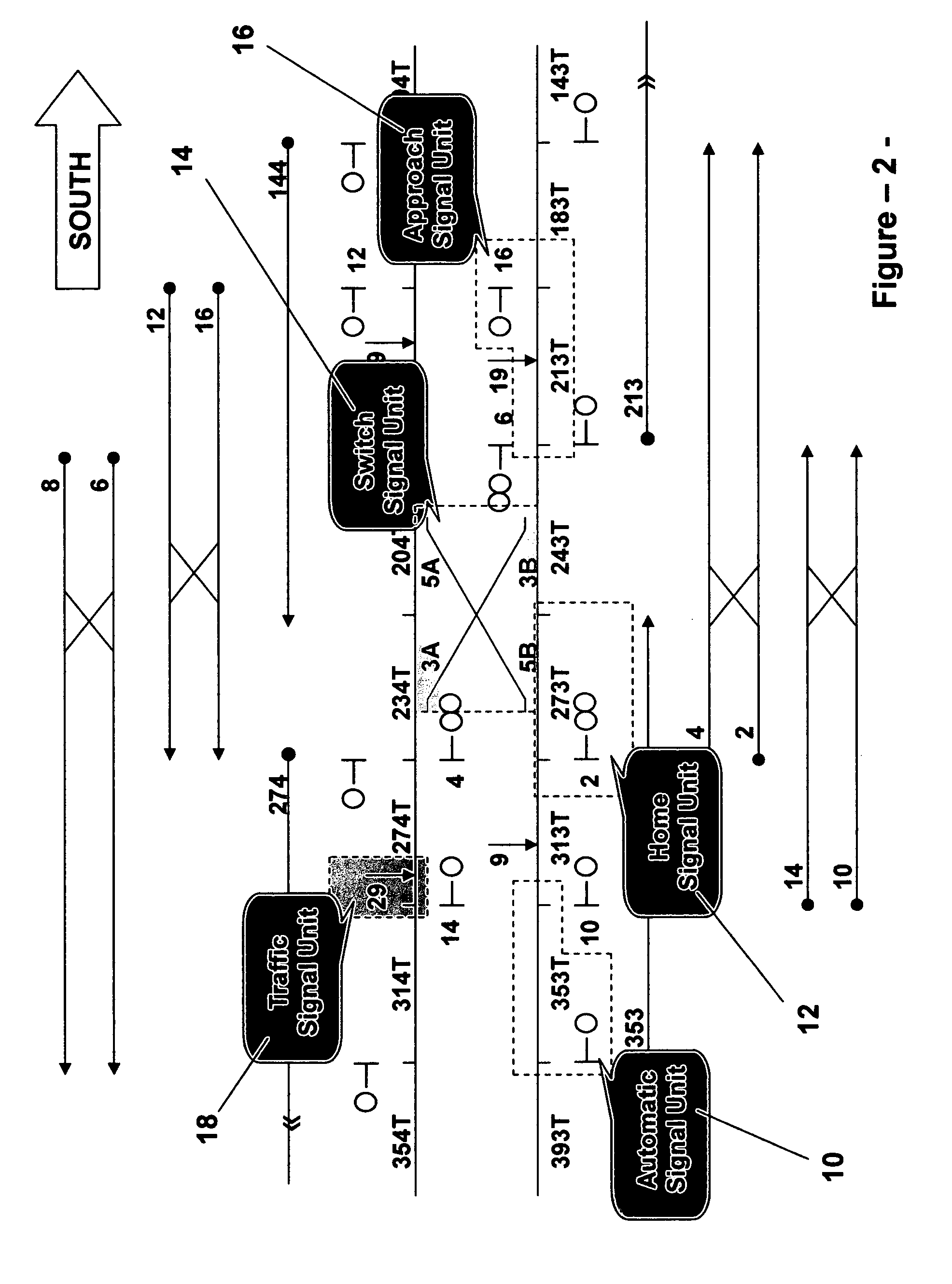
A distributed interlocking device, architecture and process are disclosed, and are based on segregating the vital logic for a signal installation by type of signal equipment. A plurality of intelligent signal devices is disclosed, wherein each intelligent signal device is used to control a basic signal unit. In turn, a signal unit includes a set of signal apparatuses that are geographically and logically interrelated. An intelligent signal device receives data related to the states of other signal devices, determines and controls its own operational states, and communicates its own operational states to other devices.A generic intelligent signal device is also disclosed, and is based on a parameterization approach that incorporates a plurality of vital parameters into the vital logic of the device. The device is then customized to a site specific location by activating the appropriate parameters for that location. In addition, a plurality of new concepts, and signal control functions are provided, and include a vital change management process, and a failure recovery scheme based on dynamic reconfiguration of home and distant control functions.
Owner:SIEMENS IND INC
Wearable Apparatus, System and Method for Detection of Cardiac Arrest and Alerting Emergency Response
ActiveUS20170172424A1Minimizes probabilityReduce probabilityElectrocardiographyBlood flow measurement devicesCardiorespiratory arrestBlood circulating
The disclosure provides wearable cardiac arrest detection and alerting device that incorporates a non-invasive sensor based on optical and / or electrical signals transmitted into and received from human tissue containing blood vessels, and that transcutaneously quantifies the wearer's heart rate. The heart-rate quantification enables the detection of the absence of any heart beat by the wearable detection and alerting device indicative of the occurrence of a cardiac arrest, wherein the heart is no longer achieving effective blood circulation in the individual wearing the device. The display on the wearable cardiac arrest detection and alerting device may include the elapsed time since the time of detection of a heart rate that is below a predetermine lower limit value, i.e., the detected occurrence of a cardiac arrest event.
Owner:CARDIAC ARREST TECH LLC
Non-Volatile Memory Embedded In A Conventional Logic Process And Methods For Operating Same
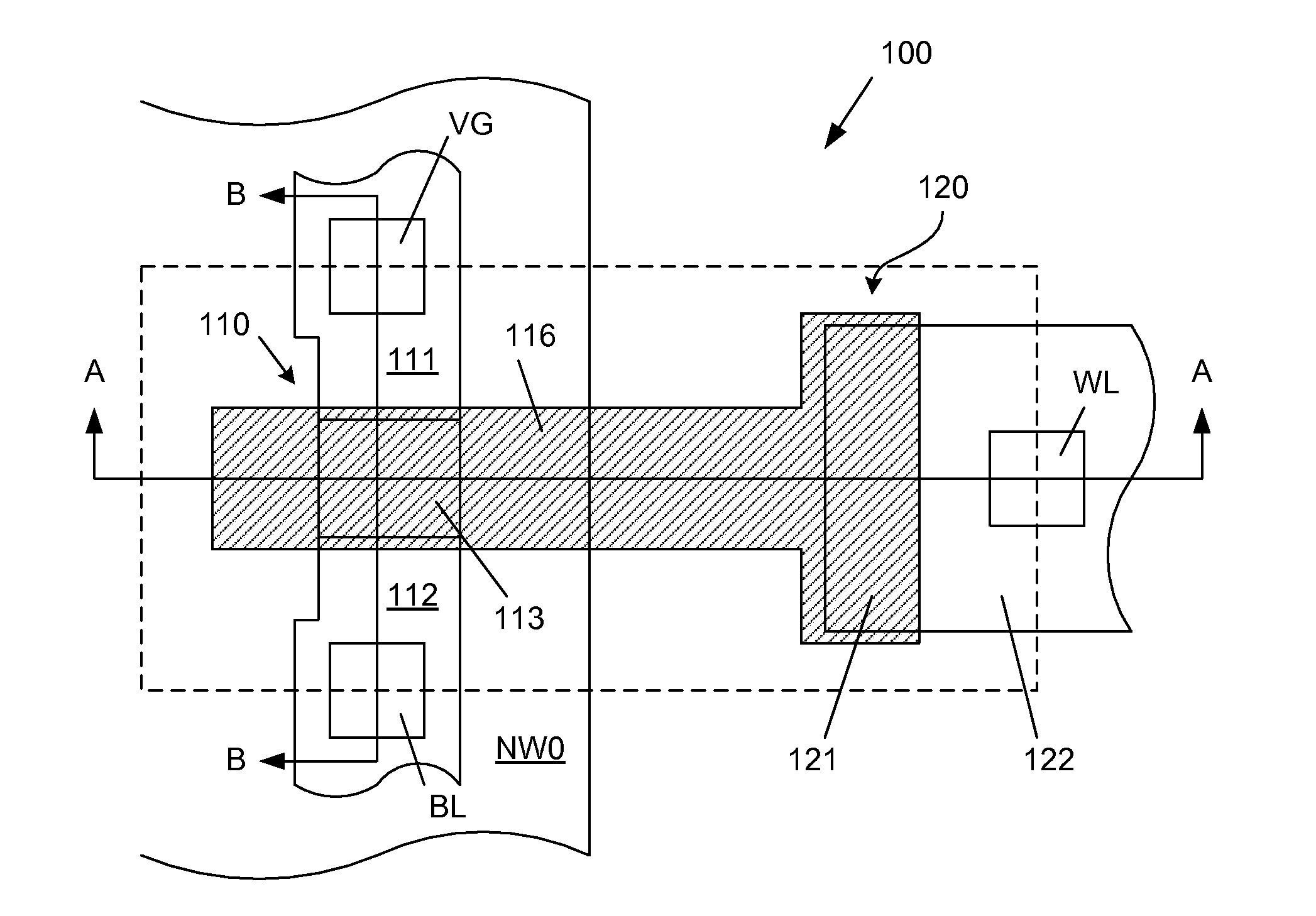
InactiveUS20070279987A1Minimizes probabilityHighly optimized SoCSolid-state devicesRead-only memoriesBit lineFowler nordheim
A non-volatile memory system including an array of cells, each having an access transistor and a capacitor sharing a floating gate. The access transistors in each row are fabricated in separate well regions, which are independently biased. Within each row, the source of each access transistor is coupled to a corresponding virtual ground line, and each capacitor structure is coupled to a corresponding word line. Alternately, the source of each access transistor in a column is coupled to a corresponding virtual ground line. Within each column, the drain of each access transistor is coupled to a corresponding bit line. Select memory cells in each row are programmed by band-to-band tunneling. Bit line biasing prevents programming of non-selected cells of the row. Programming is prevented in non-selected rows by controlling the well region voltages of these rows. Sector erase operations are implemented by Fowler-Nordheim tunneling.
Owner:MOSYS INC
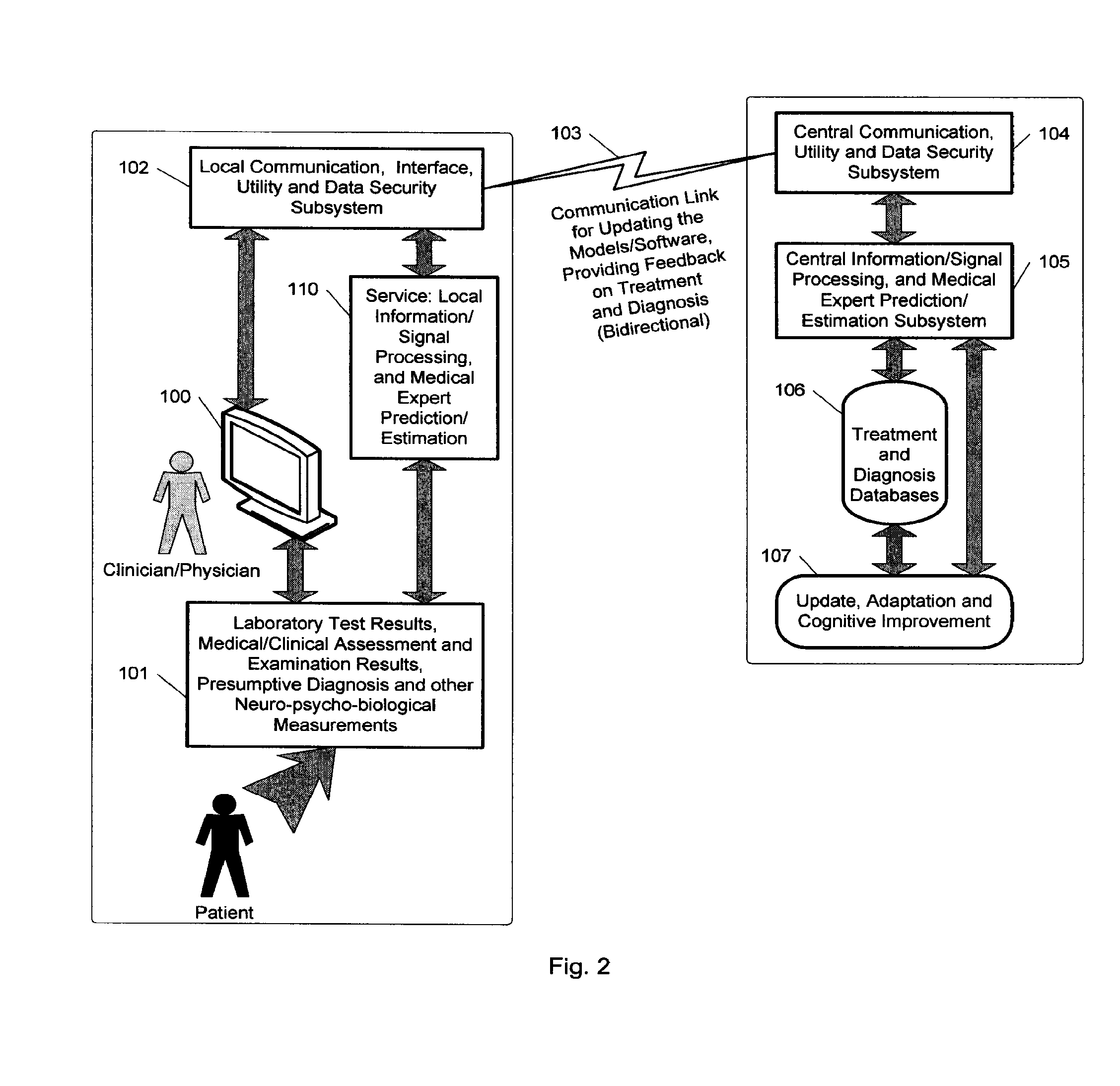
Expert system for determining patient treatment response
ActiveUS8655817B2Improve performanceMinimize complexityElectroencephalographyMedical data miningDiseaseInformation processing
A medical digital expert system to predict a patient's response to a variety of treatments (using pre-treatment information) is described. The system utilizes data fusion, advanced signal / information processing and machine learning / inference methodologies and technologies to integrate and explore diverse sets of attributes, parameters and information that are available to select the optimal treatment choice for an individual or for a subset of individuals suffering from any illness or disease including psychiatric, mental or neurological disorders and illnesses. The methodology and system can also be used to determine or confirm medical diagnosis, estimate the level, index, severity or critical medical parameters of the illness or condition, or provide a list of likely diagnoses for an individual suffering / experiencing any illness, disorder or condition.
Owner:DIGITAL MEDICAL EXPERTS
Method and system for blindly detecting a discontinuously transmitted shared channel, in particular blind high speed shared control channels detection
InactiveUS7688915B2Reduce loss rateReduce probabilityOther decoding techniquesCode conversionDigital dataControl channel
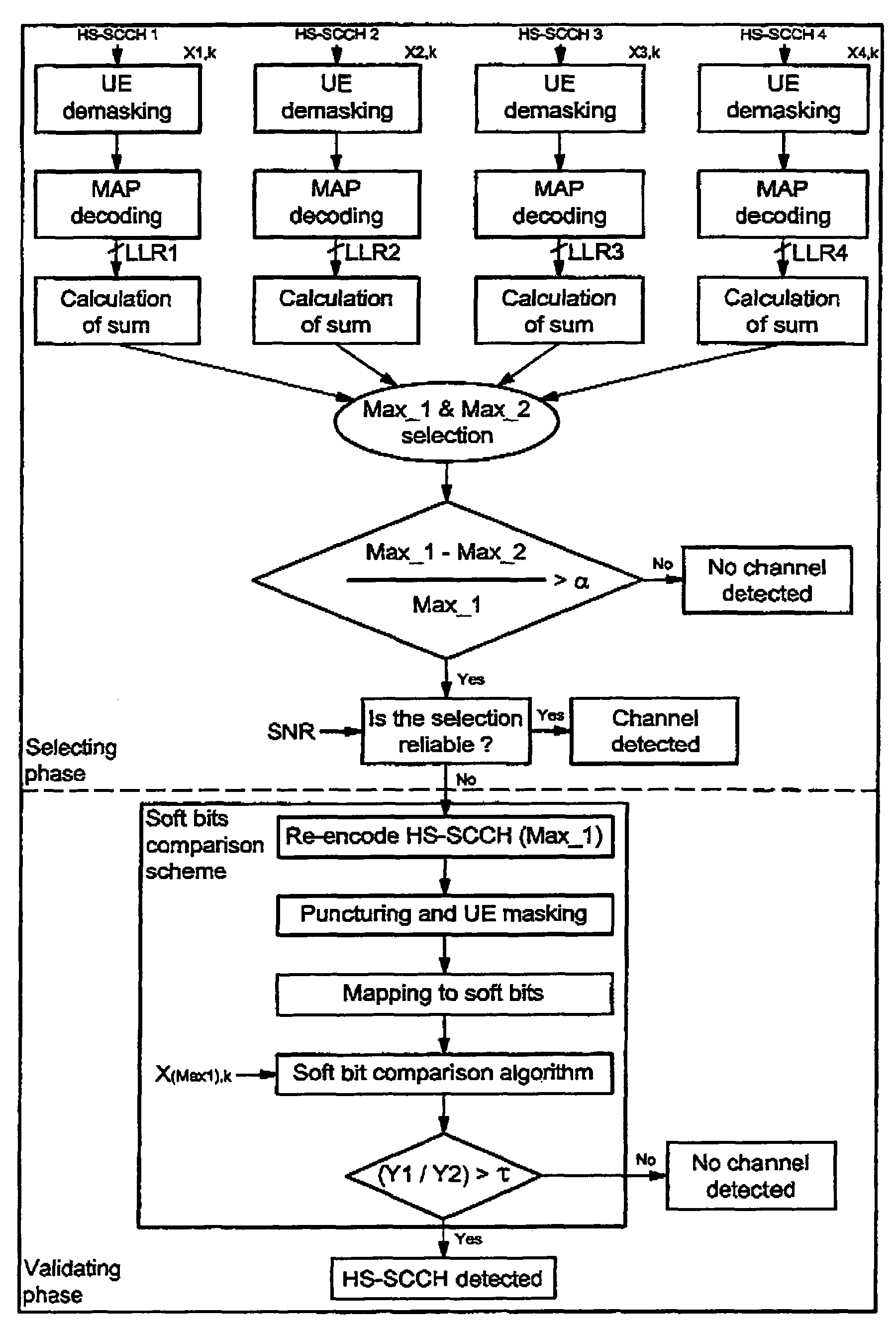
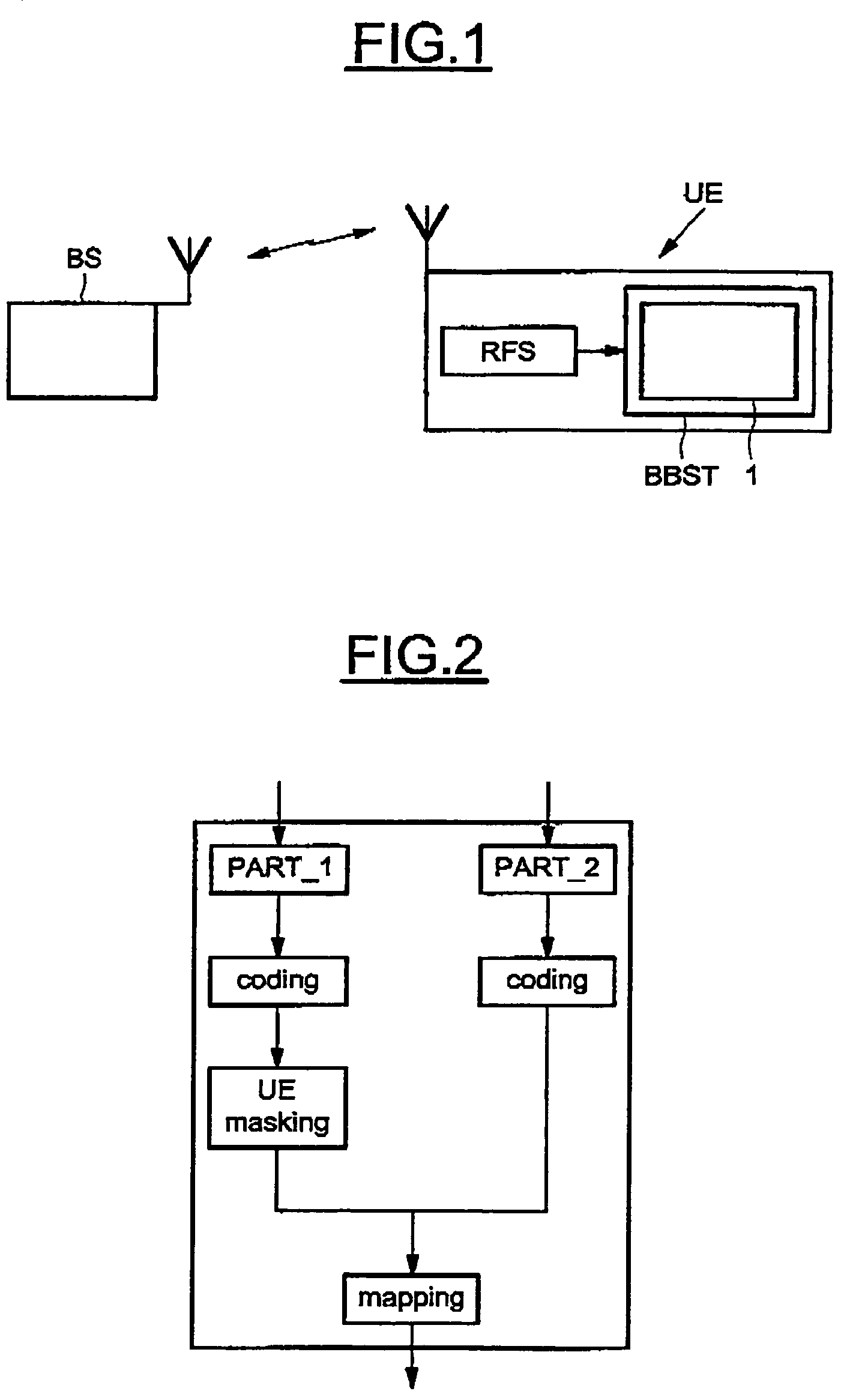
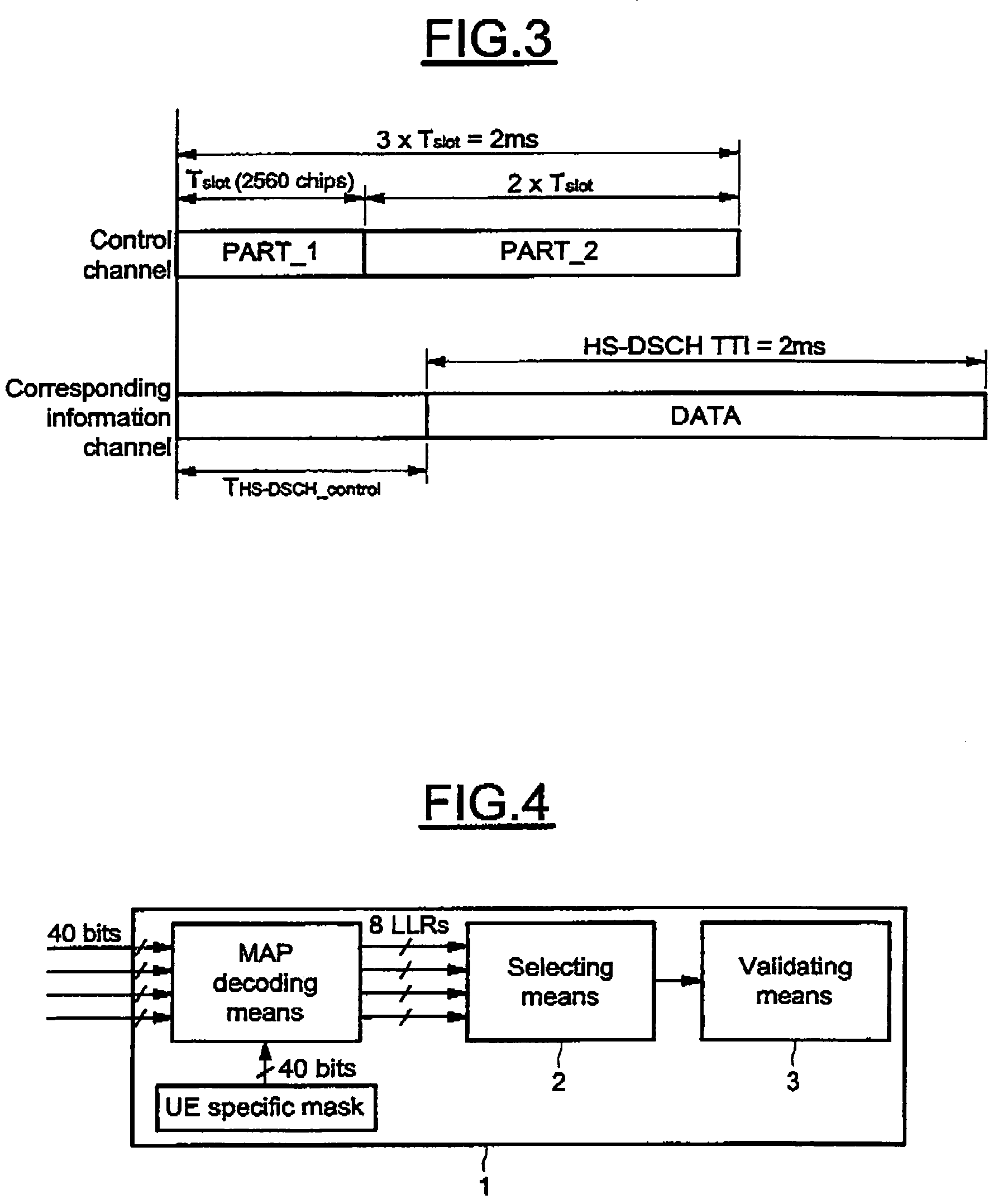
A method for detecting an eventual channel intended to a designated user equipment among n channels received by the designated user equipment during a given duration, each channel received during the duration carrying encoded data masked with an identifier associated to a user equipment. The method includes a selecting phase having a demasking step demasking the received masked encoded data of each channel with the identifier of the designated user equipment, a decoding step decoding the demasked encoded data of each channel to obtain a set of digital decoded data for each channel, a calculating step calculating, from each set of digital decoded data, a global information representative of a confidence in digital data received on the physical channel, and a detecting step detecting the channel from all the global information.
Owner:SNO WAY INT +1
Method and system for controlling the development of biological entities
InactiveUS20060057555A1Avoid mistakesOptimizationBioreactor/fermenter combinationsBiological substance pretreatmentsMarking outComputer science
A method and system are presented for use in controlling the processing of components, e.g. biological entities. Each component is assigned with a unique machine readable identification mark. Data records are provided representative of matching sets of the identification marks relating to at least two associated components. Each component-containing holder may be provided with the unique machine readable identification mark assigned to the biological entity in the holder. This enables to identify whether the biological entities to be processed relate to the matching set or not.
Owner:I M T INTERFACE MULTIGRAD TECH LTD
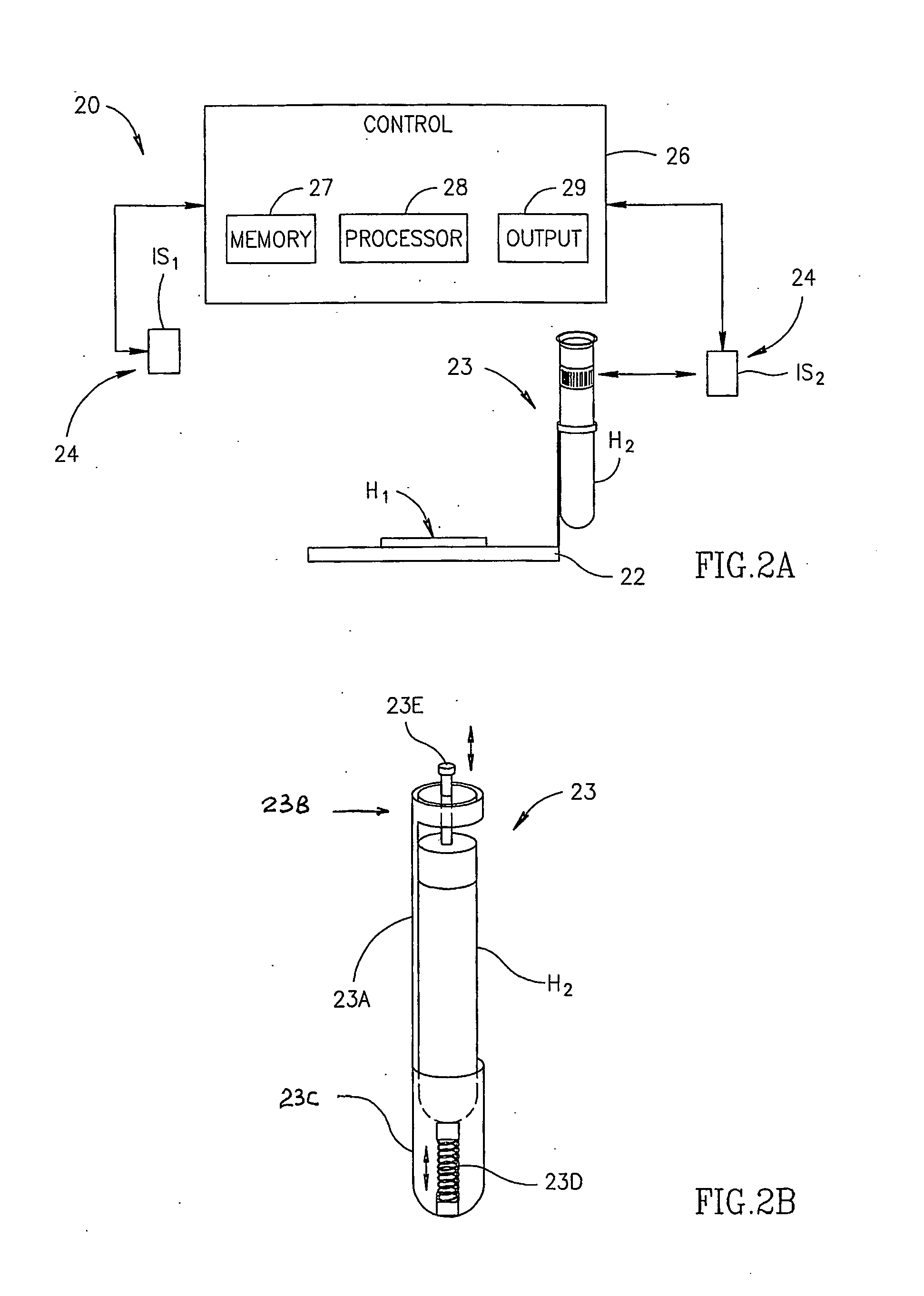
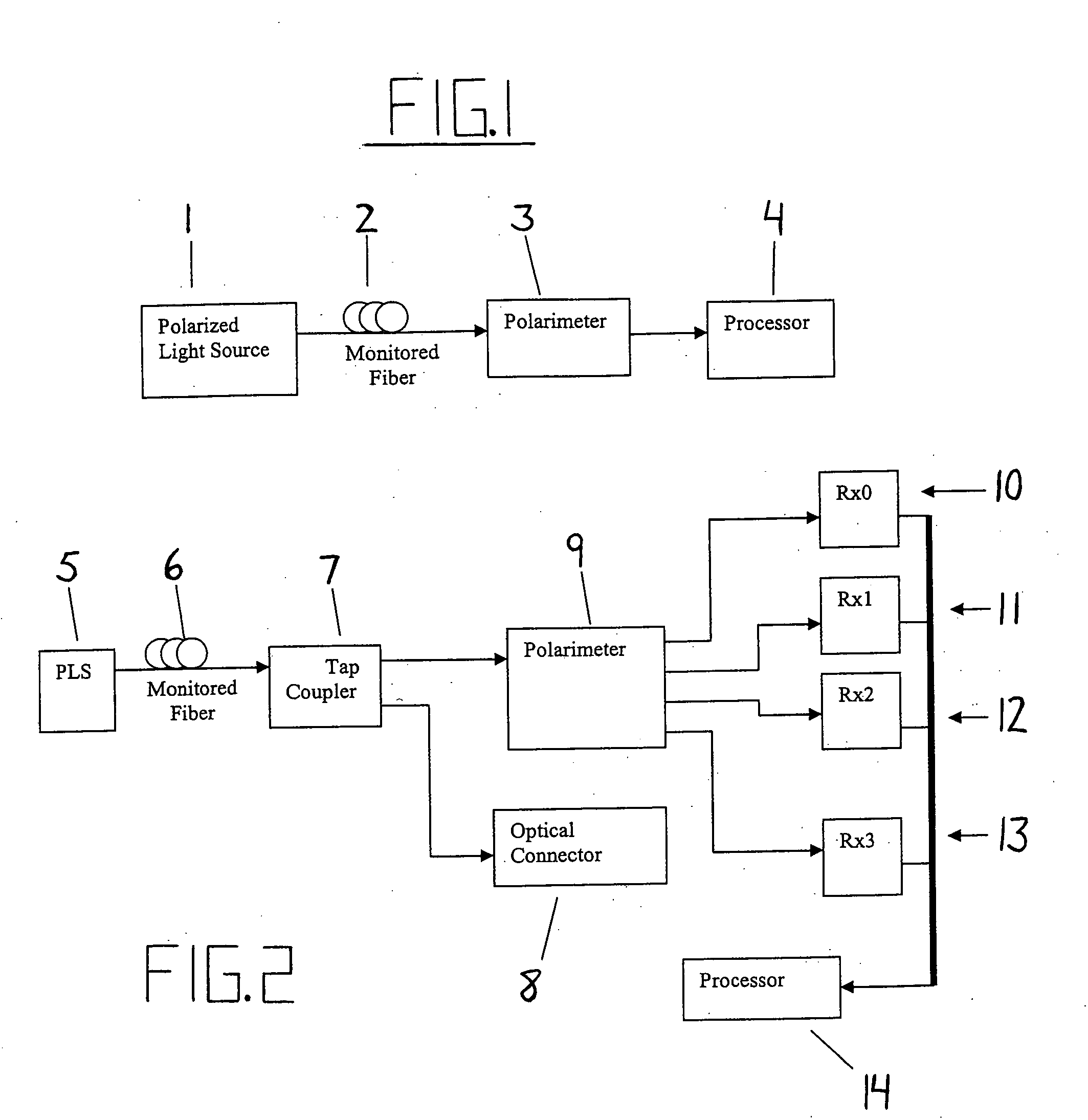
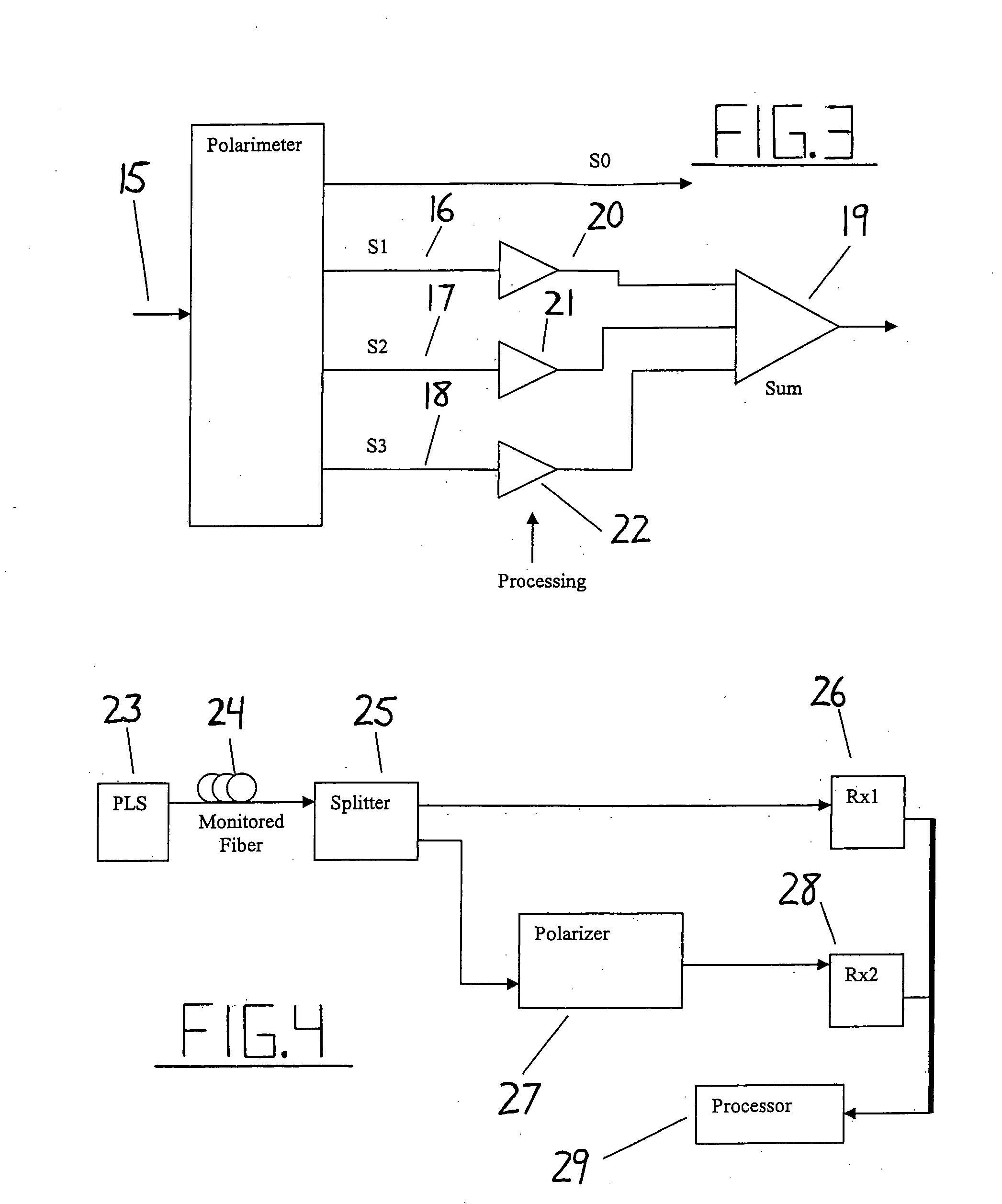
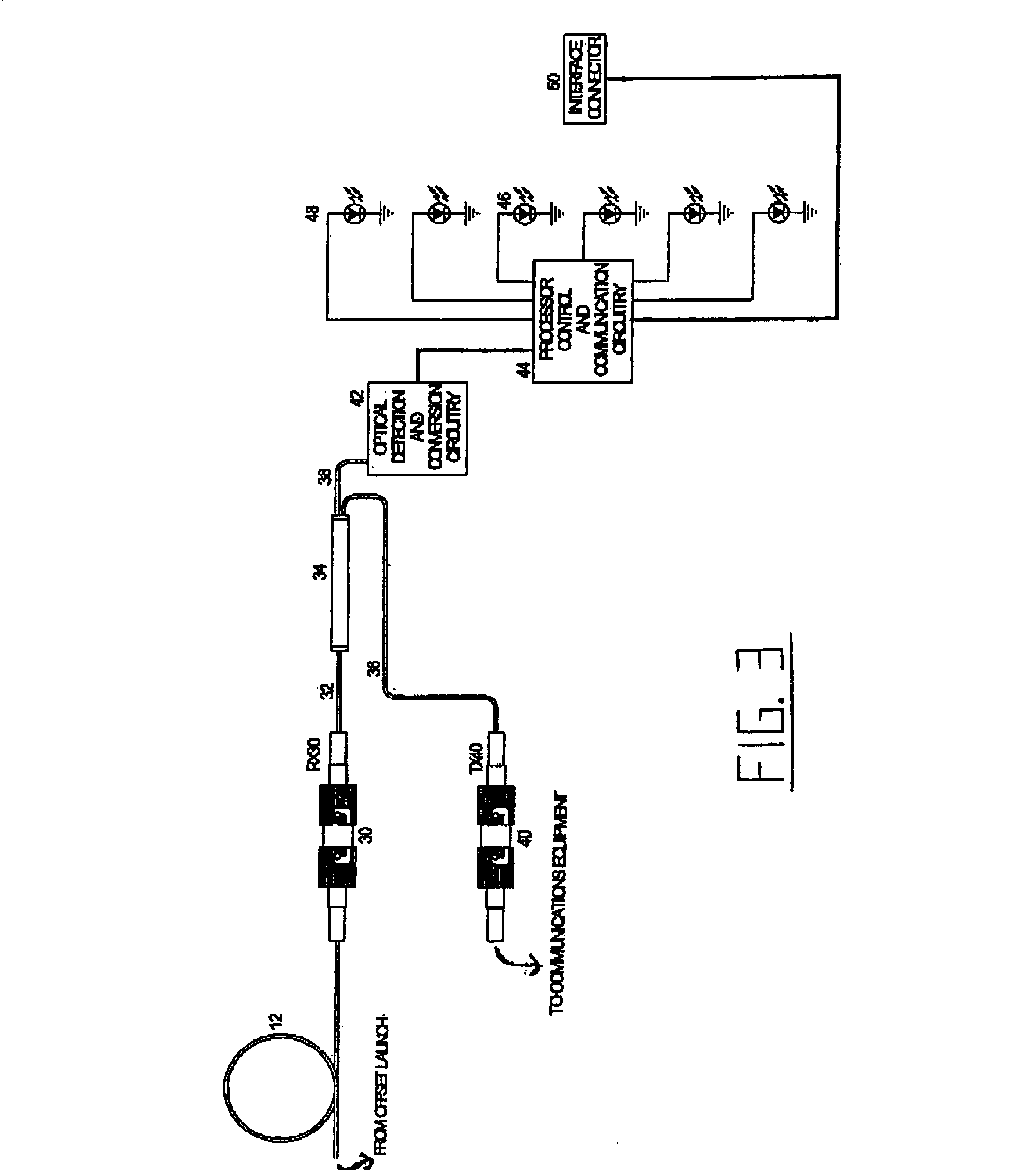
Intrusion detection system for use on single mode optical fiber using a simplified polarimeter
ActiveUS20060153491A1Overcome limitationsMaximum sensitivityElectromagnetic transmission optical aspectsLight polarisation measurementPolarimeterPolarizer
A telecommunications optical fiber is secured against intrusion by detecting manipulation of the optical fiber prior to an intrusion event. This can be used in a non-locating system where the detection end is opposite the transmit end or in a locating system which uses Fresnel reflections and Rayleigh backscattering to the transmit end to detect and then locate the motion. The Rayleigh backscattering time sliced data can be stored in a register until an intrusion event is detected. The detection is carried out by a polarization detection system which includes an optical splitter which is manufactured in simplified form for economic construction. This uses a non-calibrated splitter and less than all four of the Stokes parameters. It can use a polarimeter type function limited to linear and circular polarization or two linear polarizers at 90 degrees.
Owner:NETWORK INTEGRITY SYST
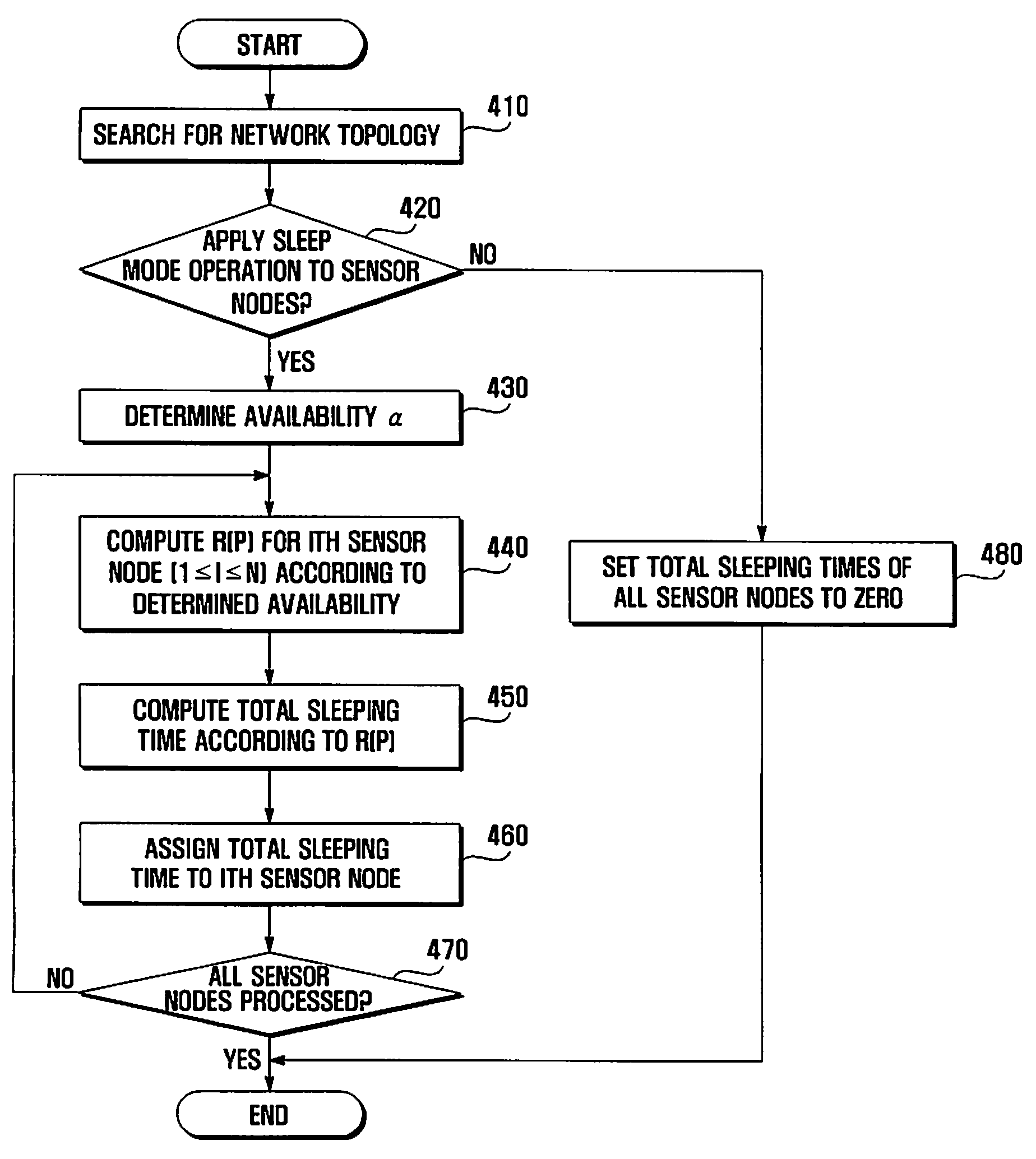
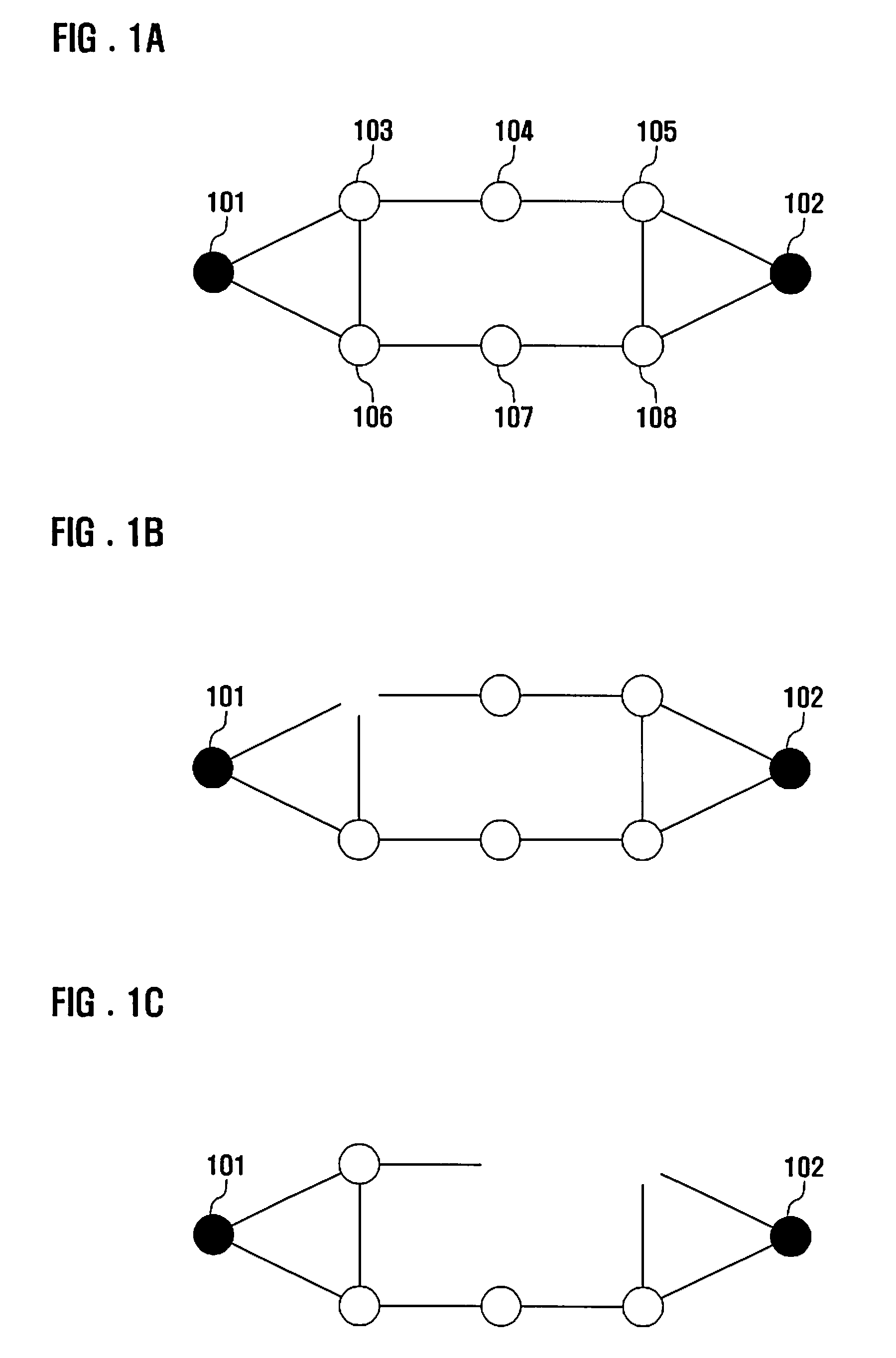
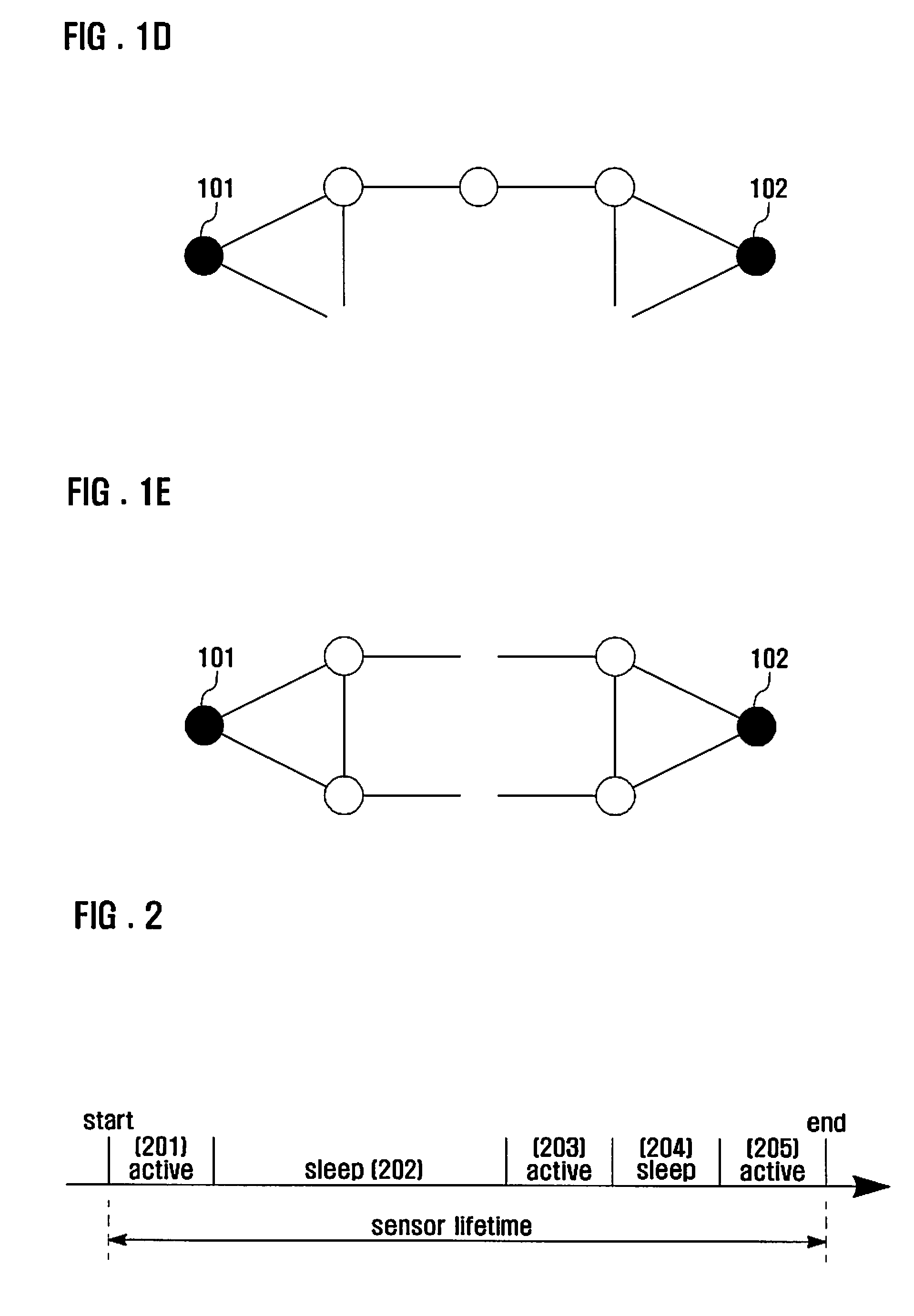
Method and system for extending lifetime of sensor nodes in wireless sensor network
InactiveUS20090216349A1Extended service lifeMinimizes operation probabilityProgramme controlEnergy efficient ICTLine sensorSleep time
A method and system are provided that extend the lifetime of sensor nodes in a wireless sensor network while ensuring network availability. An availability level is set for ensuring network connectivity corresponding to importance of network connectedness. An operation probability that a sensor node is in operation is calculated. A total sleeping time of the sensor node is calculated that minimizes the operation probability while maintaining the availability level.
Owner:SAMSUNG ELECTRONICS CO LTD +1
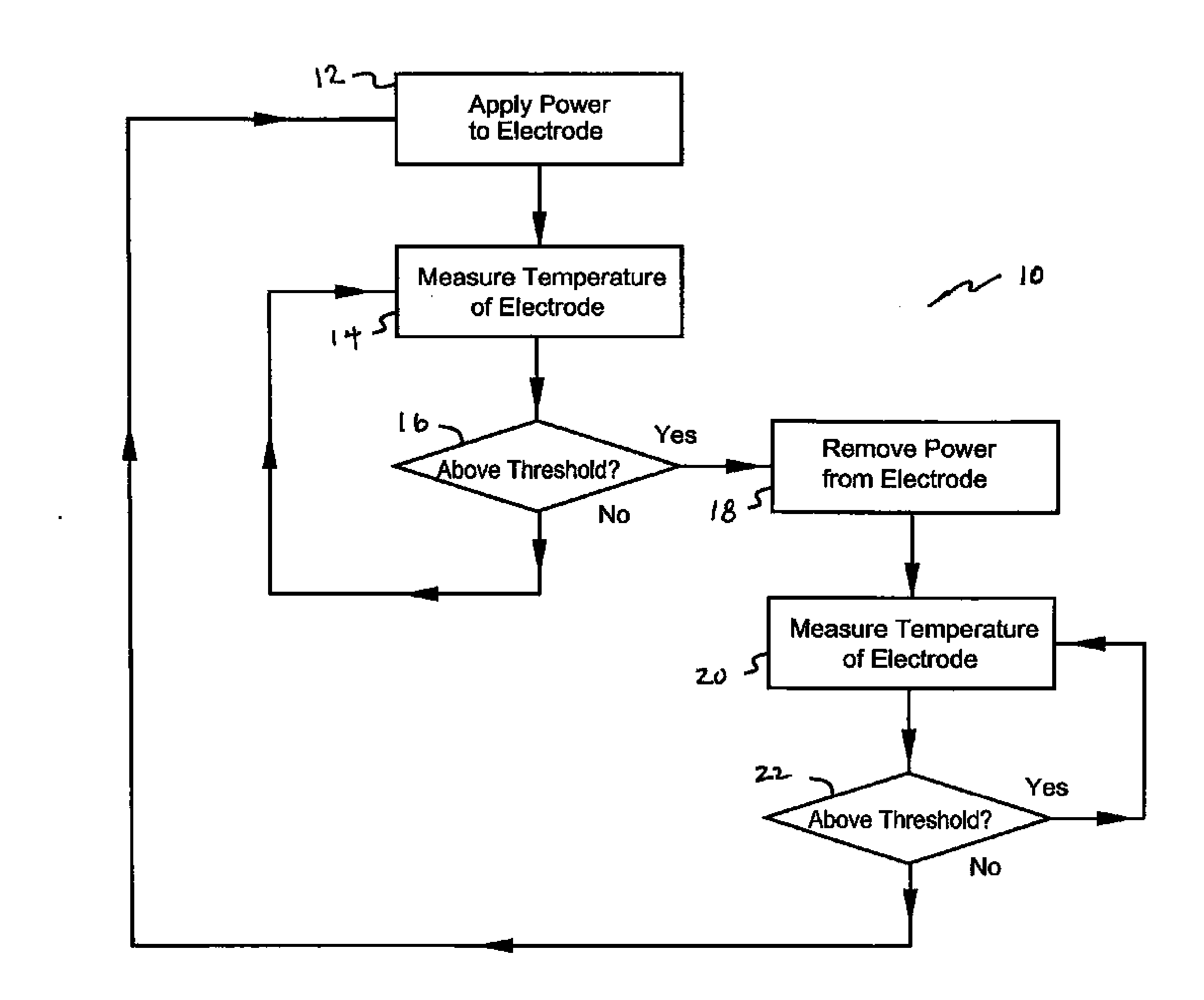
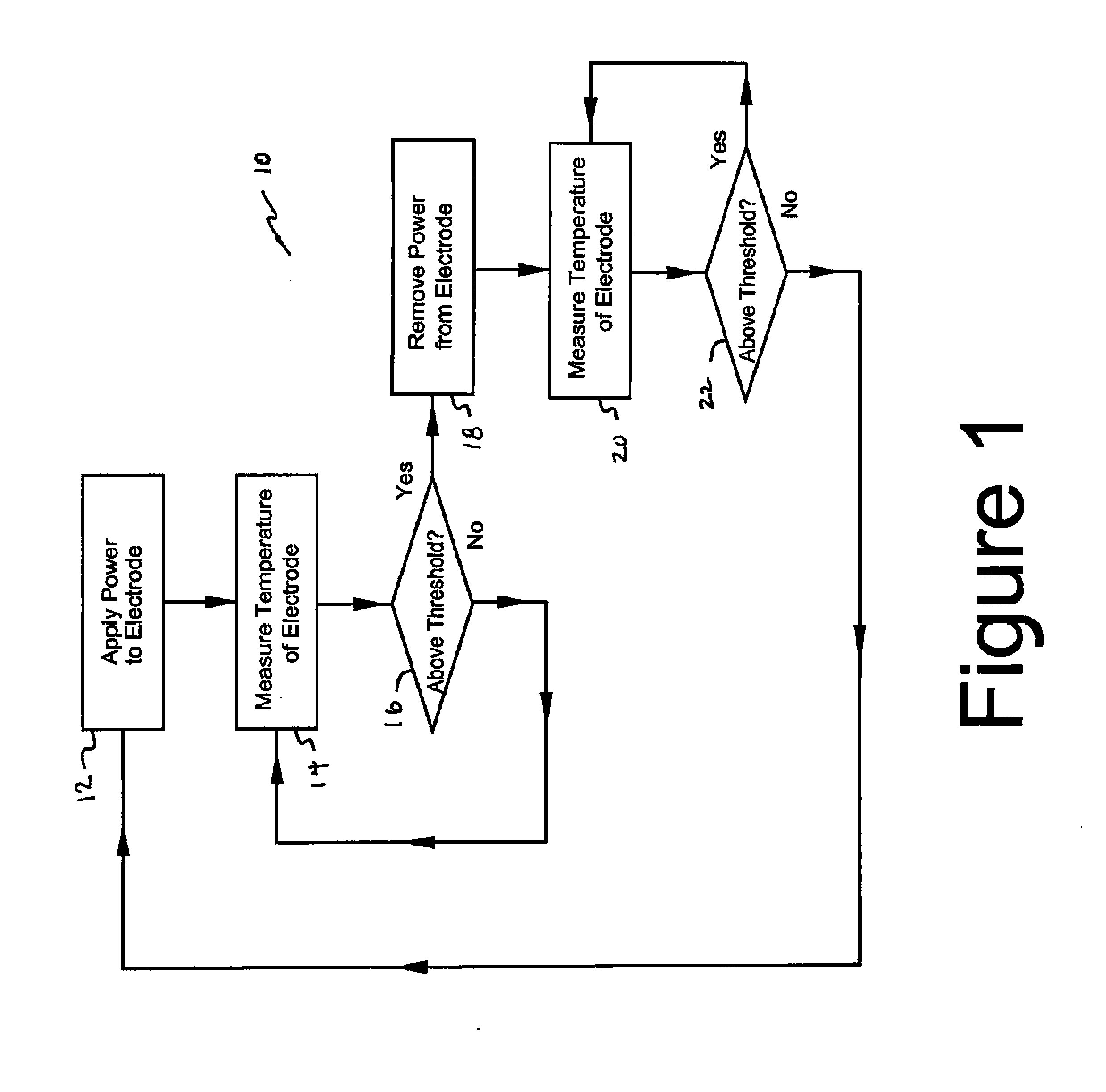
Temperature responsive ablation RF driving for moderating return electrode temperature
InactiveUS20090187183A1Reduce the possibilityMinimizes probabilityDiagnosticsSurgical systems user interfaceMedicineBiomedical engineering
The inventive method for ablating a tissue mass associated with a human or animal patient being treated comprises positioning an ablating electrode in a tissue mass to be ablated. A plurality of return electrodes are positioned on the patient. Electrical energy is applied between the return electrodes and the ablating electrode. The temperature of the return electrodes is measured to generate a temperature measurement signal which is used to control ablation current through the return electrodes.
Owner:ACESSA HEALTH INC +1
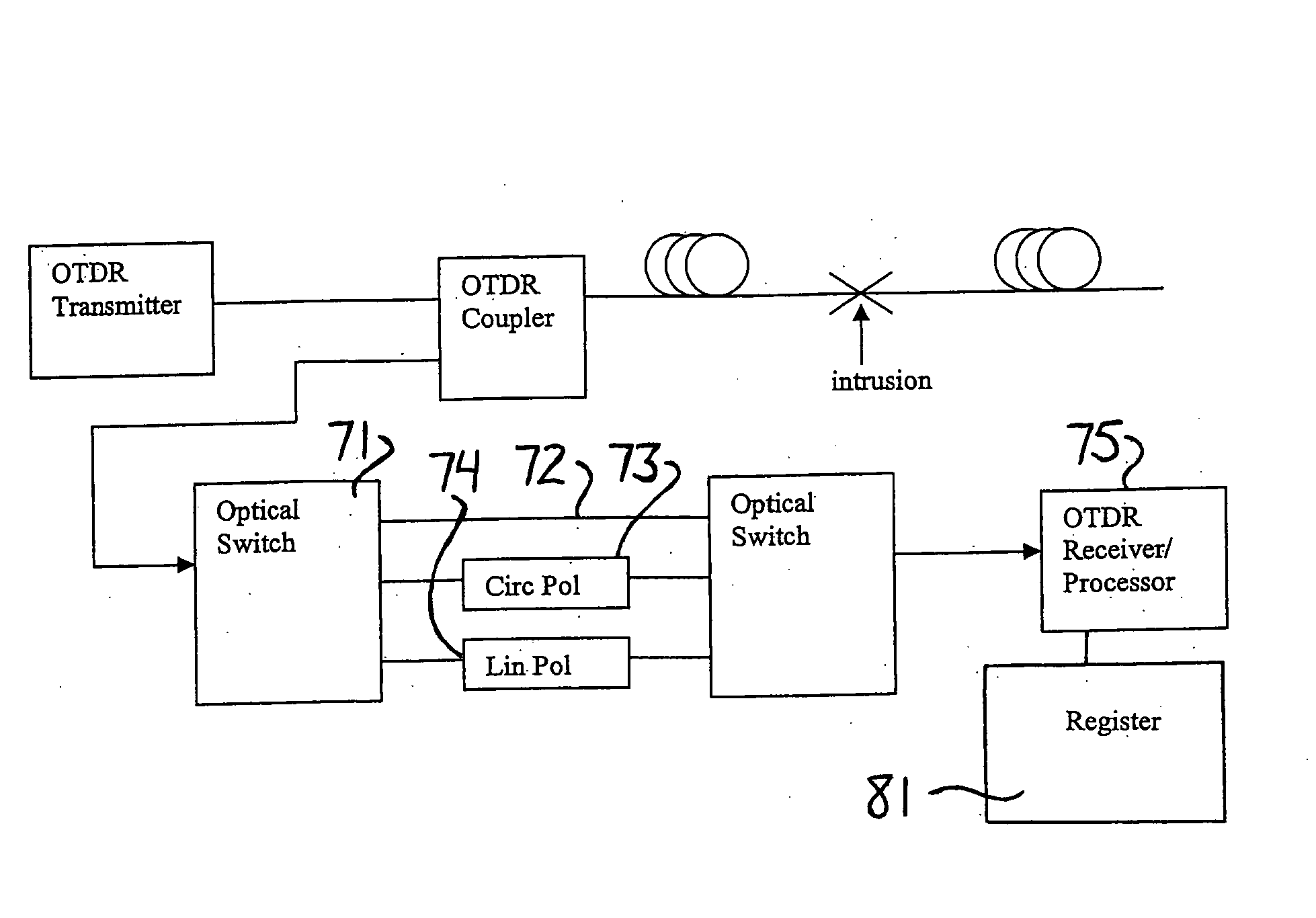
Intrusion detection system for use on an optical fiber using a translator of transmitted data for optimum monitoring conditions
ActiveUS7092586B2Maximum sensitivityRapid location and interceptionCoupling light guidesFibre mechanical structuresFiberSpectral width
A method and system of intrusion detection system for a multimode fiber optic cable. A light signal is launched into the cable fiber to establish a narrow spectral width, under-filled non-uniform mode field power distribution in the cable. A small portion of the higher order signal modes arriving at the remote end of the cable is sampled by use of a coupler and monitored for transient changes in the mode field power distribution. The power distribution changes with physical disturbance of the cable. When those changes are detected as being characteristic of fiber intrusion, the system activates an alarm. This method can sense and alarm any attempt to access the optical fibers in a fiber optic communication cable. In preferred embodiments, the active signal of a multimode optical fiber is monitored for both signal degradation and transient power disturbance patterns that could indicate fiber damage or physical intrusion. A translator can be provided in an existing optical fiber system in which the data signals are translated in wavelength and / or launch conditions to optimize the monitoring signals in an otherwise non-optimized system.
Owner:NETWORK INTEGRITY SYST
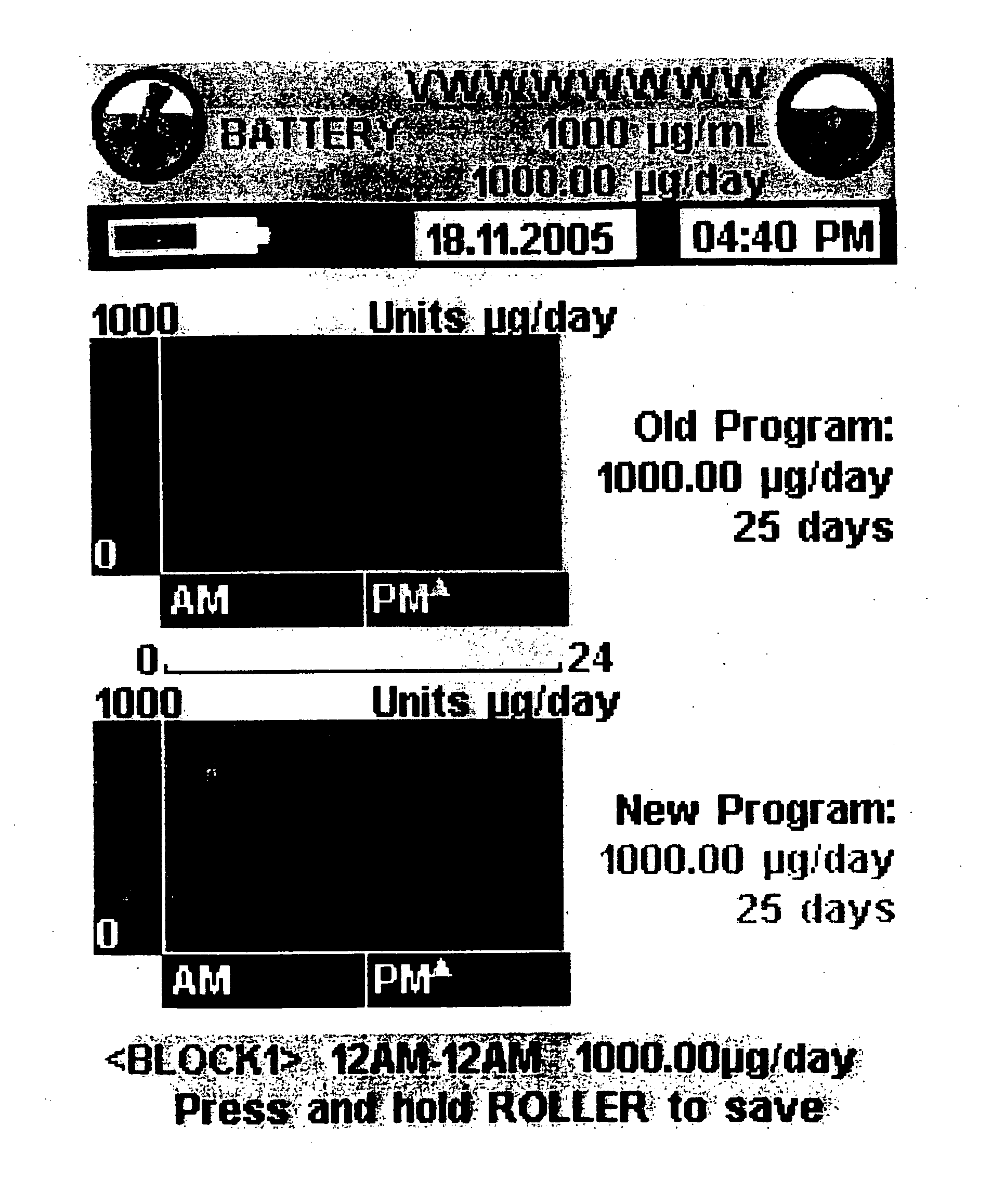
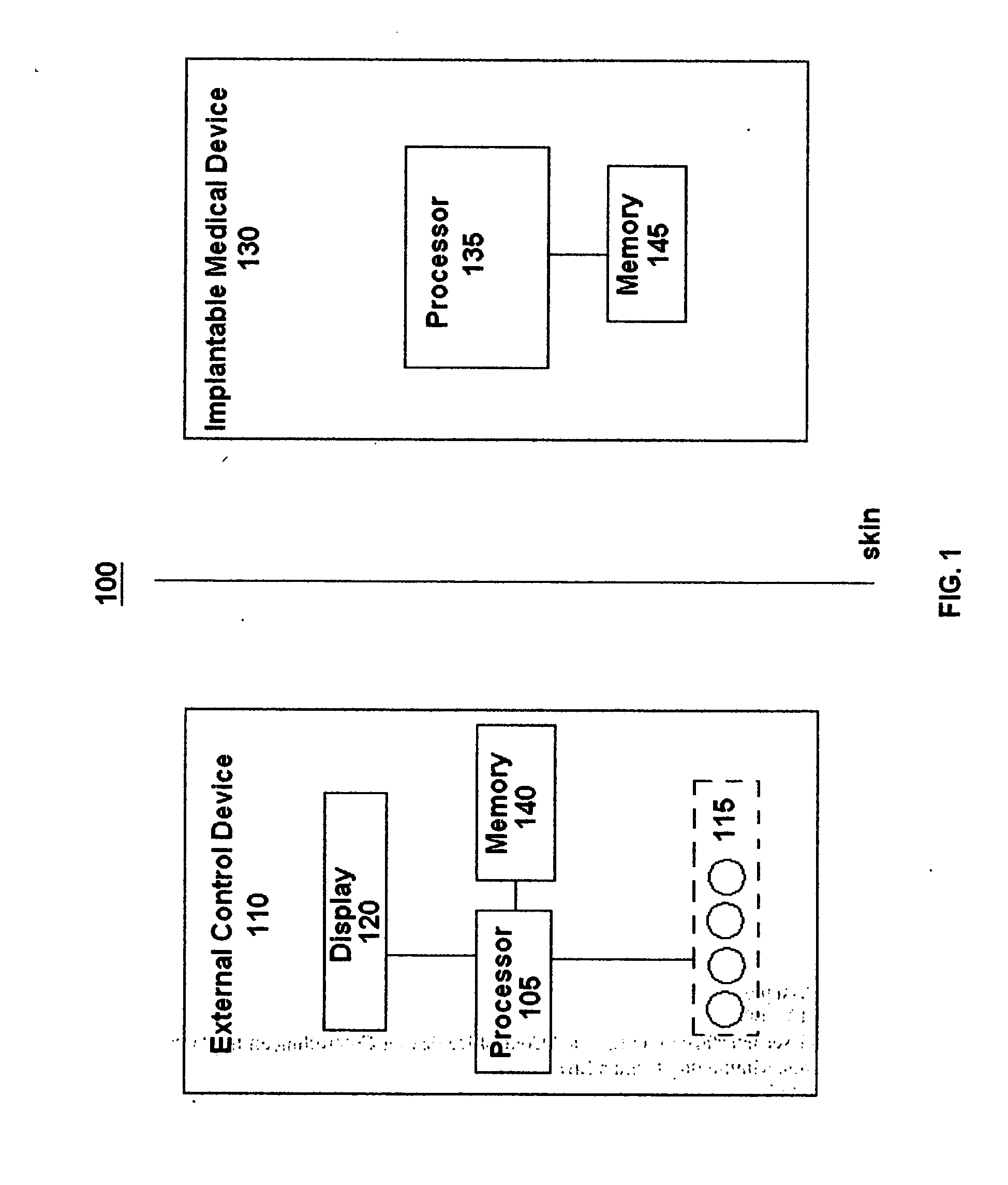
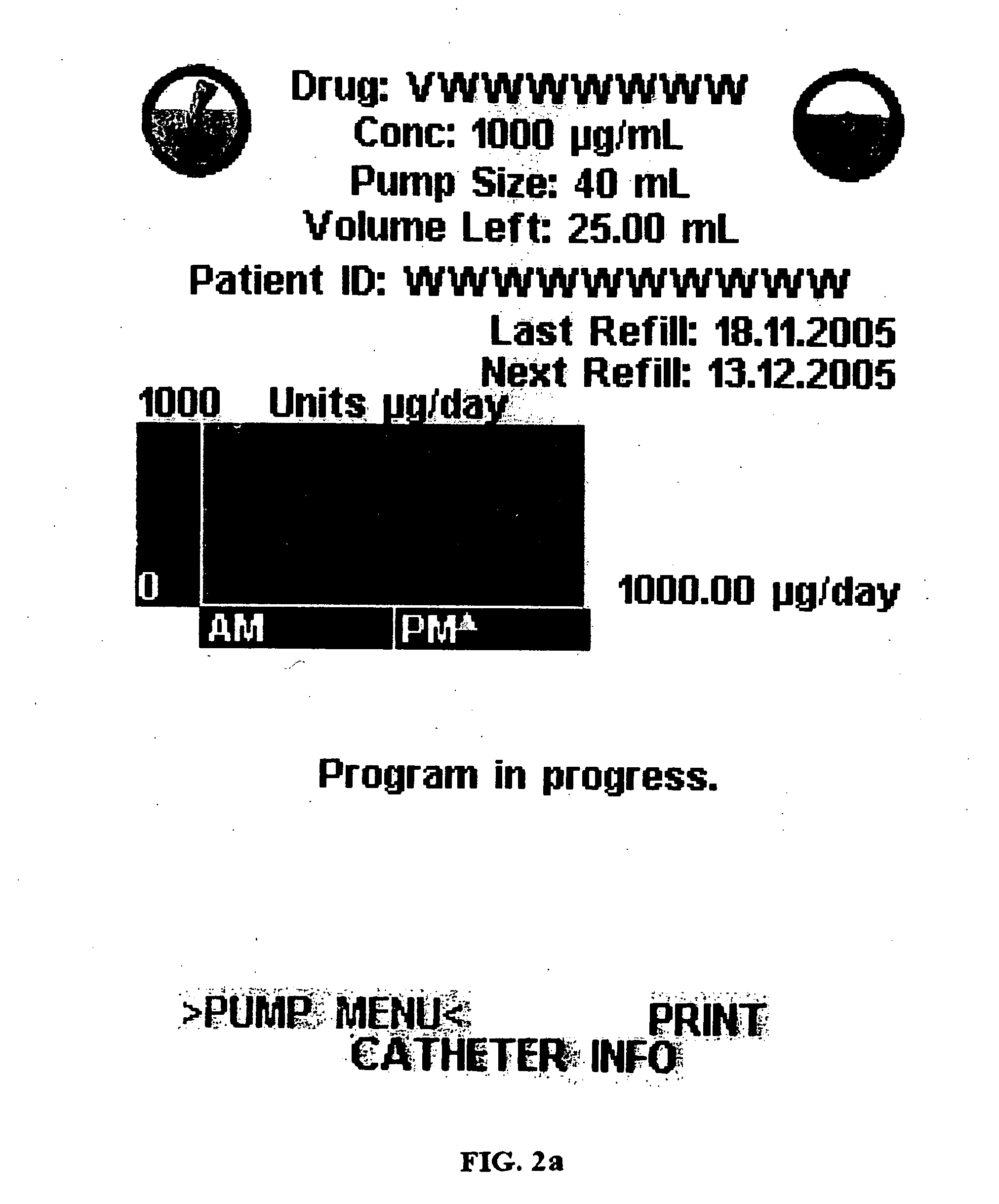
Graphical user interface of an external control device for controlling an implantable medical device while minimizing human error
InactiveUS20070245258A1Reduces and minimizes potentialAccurate operationElectrotherapyLocal control/monitoringGraphicsArabic numerals
A graphical user interface of an external control device for controlling operation of an implantable medical device while minimizing the occurrence of human error. The graphical user interface displays the operating parameter of the implantable medical device simultaneously as an Arabic numeral and a graphical representation. When a parameter value is adjusted, the current and adjusted values are simultaneously displayed as both an Arabic numeral and graphical representation. Other means are described for increasing the probability of detection of an error during entry of an operating parameter value prior to implementation. Execution of the graphical user interface is subject to interruption. When function of the graphical user interface programming is restored operation resumes from that which it left off prior to interruption.
Owner:CODMAN NEURO SCI
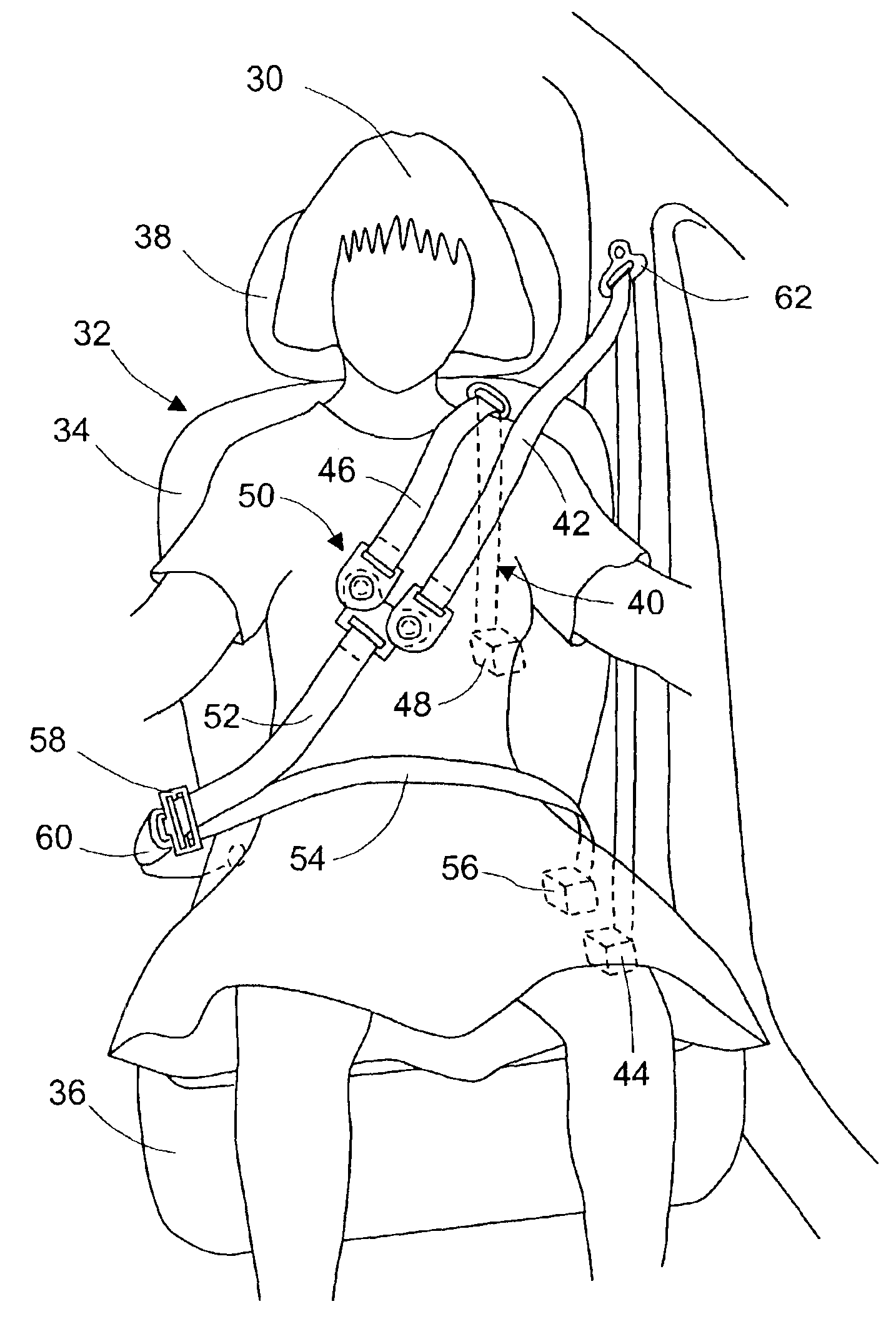
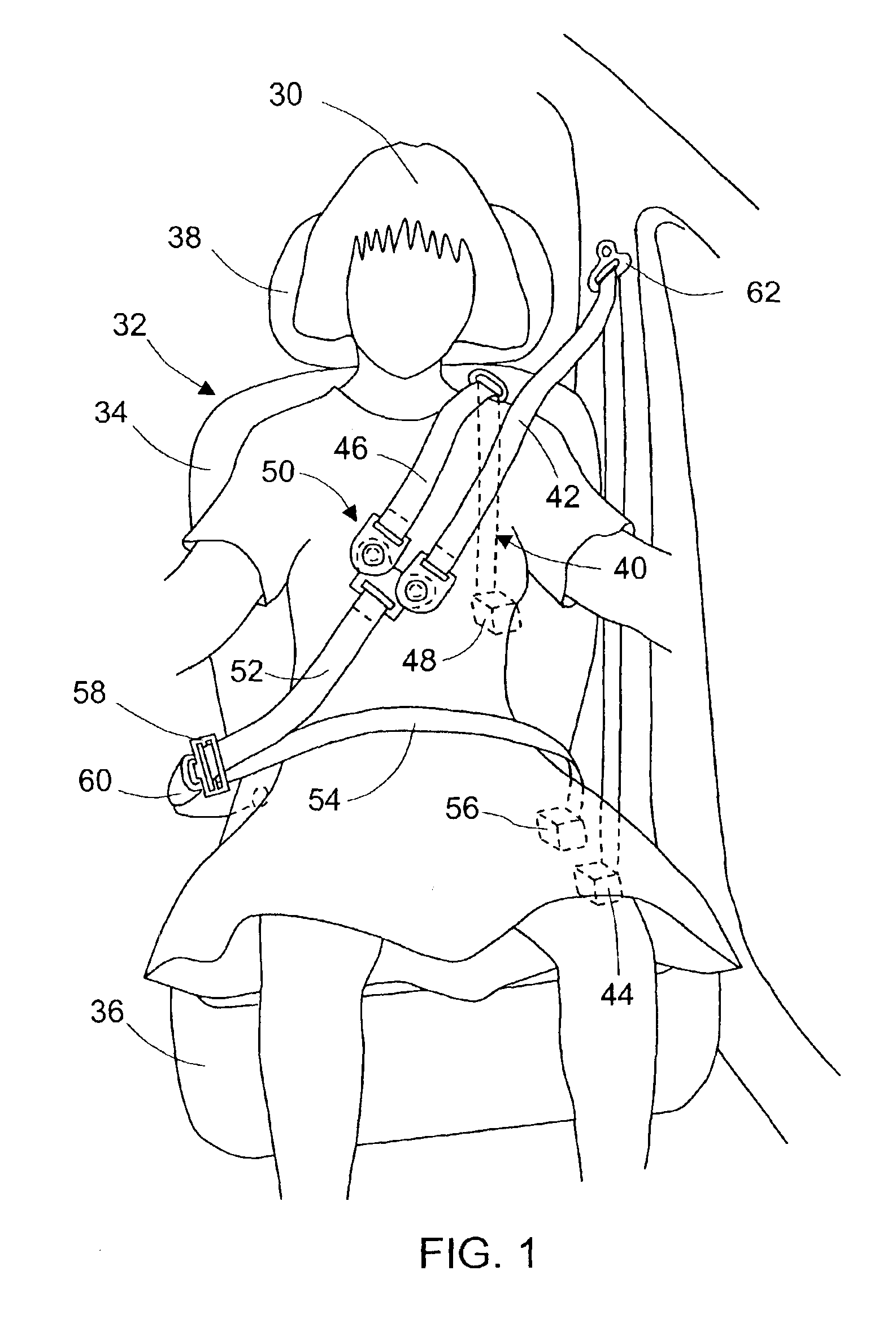
Seat belt restraint system with double shoulder belts
InactiveUS6871876B2Improve distributionMinimizes probabilityBelt control systemsSemi-passive restraint systemsBand shapeSeat belt
A seat-belt-restraint-system (40) for a vehicle occupant (30) seated in a vehicle seat (32). Seat-belt-restraint-system (40) includes two shoulder belts (42) and (46), a middle portion belt (52), a seat belt buckle (60), a seat belt latch (58), a connect mechanism (50), and a lap belt (54). The upper end of shoulder belt (42) is extendable and retractable to the upper portion of the vehicle adjacent the occupant's shoulder. The upper end of shoulder belt (46) is extendable and retractable to the upper portion of seatback (34) adjacent the occupant's shoulder. The lower ends of both shoulder belts (42) and (46) lead to connect mechanism (50). The first end of middle portion belt (52) leads to connect mechanism (50). The second end of middle portion belt (52) is connected to the first end of lap belt (54). The second end of lap belt (54) is anchored to the vehicle and disposed on the outboard side of occupant (30). Connect mechanism (50) interconnects the lower ends of both shoulder belts (42) and (46) and the first end of middle portion belt (52). Seat belt latch (58) has a webbing loop, through which middle portion belt (52) is threaded, such that seat belt latch (58) is slidable along middle potion belt (58). Seat belt buckle (60) is anchored to the vehicle and disposed on the inboard side of the occupant (30) for lockably receiving seat belt latch (58).
Owner:XU ZHAOXIA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com