Man-machine fusion security authentication method based on wearable equipment
A wearable device and authentication method technology, applied in the field of identity authentication, can solve the problem that identity is easily impersonated or replaced by others
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below in conjunction with the accompanying drawings.
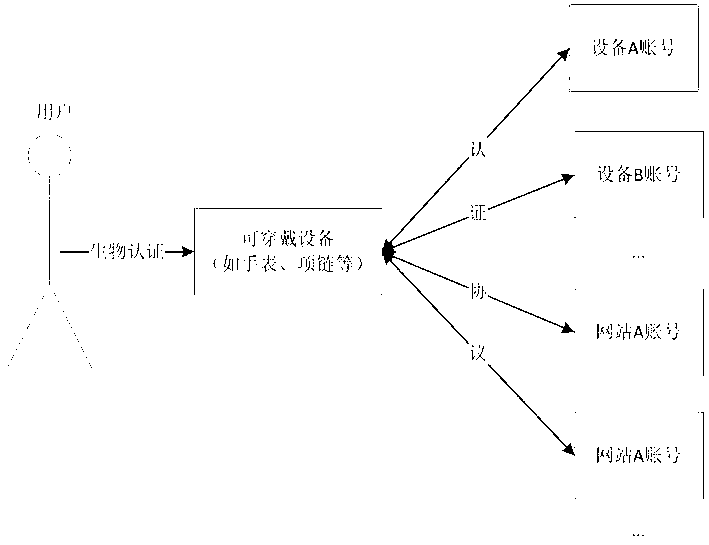
[0043] like figure 1 , the user first registers with the wearable device and stores personal digital identity information into the wearable device. Subsequently, when the user wishes to log in to other devices or websites, the wearable device first authenticates the current user through biometric matching. After confirming that the current user is a legitimate user, the wearable device can initiate an authentication request to other devices or networks, and use the user's personal digital identity information stored in it to pass the authentication.
[0044] In the present invention, the user needs to train the wearable device before using the wearable device for security fusion authentication. During training, the wearable device obtains the user's biological information through its built-in sensors, such as the user's bioelectricity, pulse phase, iris, gait, fing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com