Automatic analysis system and method for malicious code
A malicious code, automatic analysis technology, applied in the field of malicious code automatic analysis system, to achieve the effect of improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
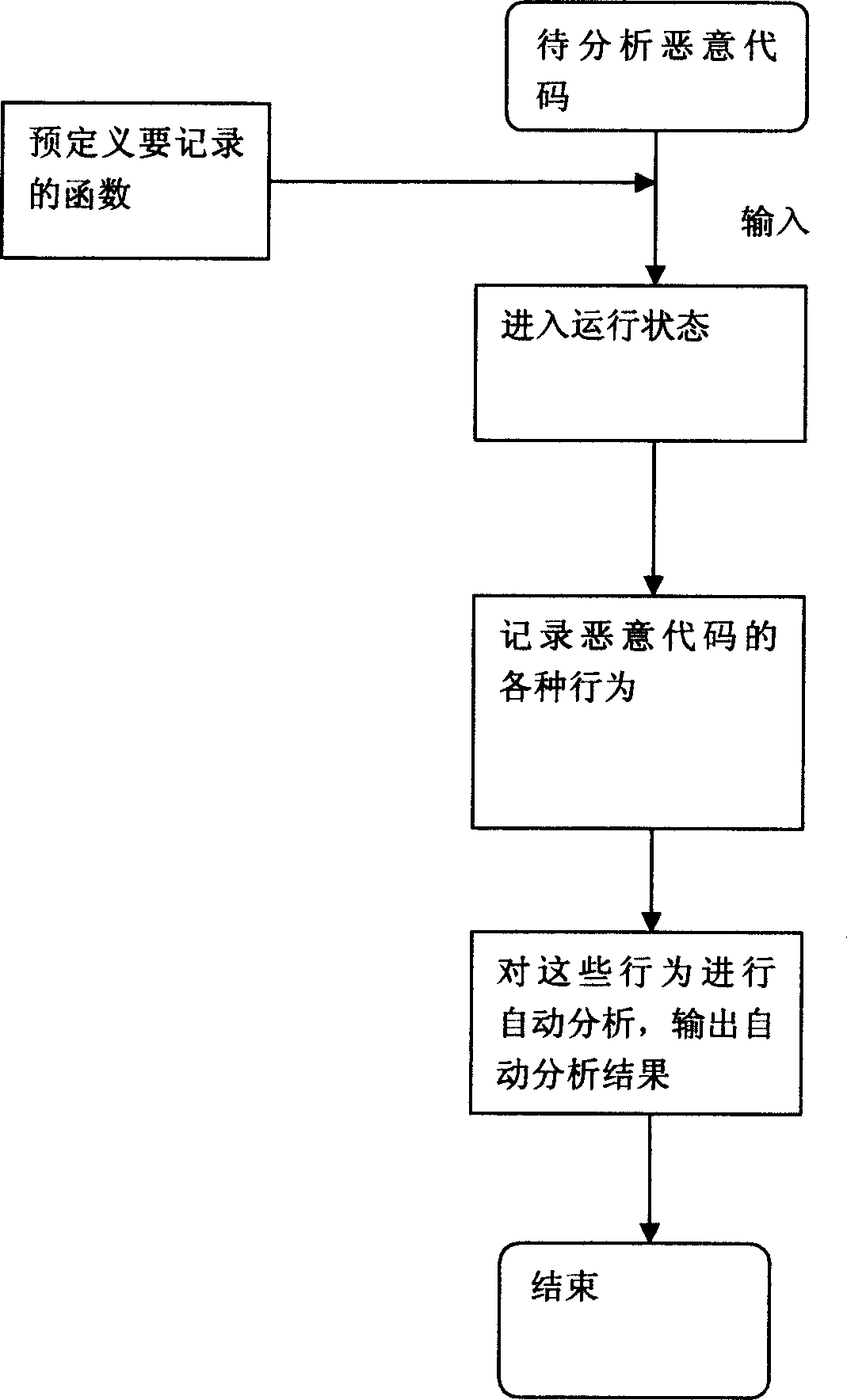
[0028] Such as figure 1 As shown in the figure, before the malicious code runs, the user first needs to define a batch of functions. Generally, normal applications rarely use these functions, or there is no need to use these functions, and the probability of using these functions by malicious code is quite high.
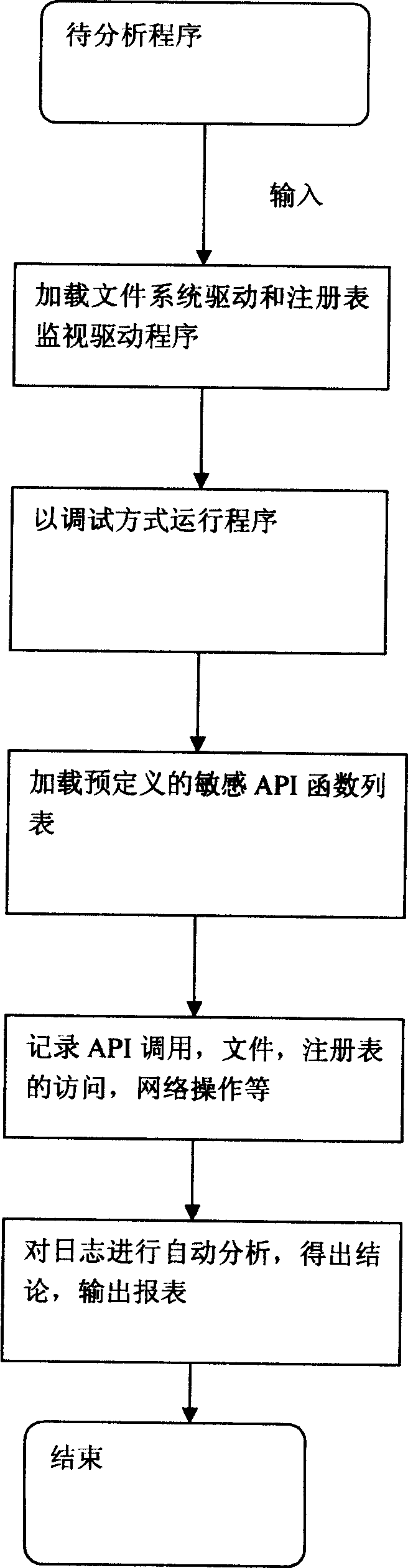
[0029] Before the system starts analysis, it will load all API (Application programming interface) (application programming interface) function lists from the database. When the malicious code calls the above-mentioned user-defined sensitive functions, it will record the function calls.
[0030] When the API function is loaded, the system will load the driver to record the access and operation of files, registry and network by malicious code.
[0031] When the malicious code finishes running, the system will automatically analyze its mechanism based on various behaviors recorded during the running of the malicious code.
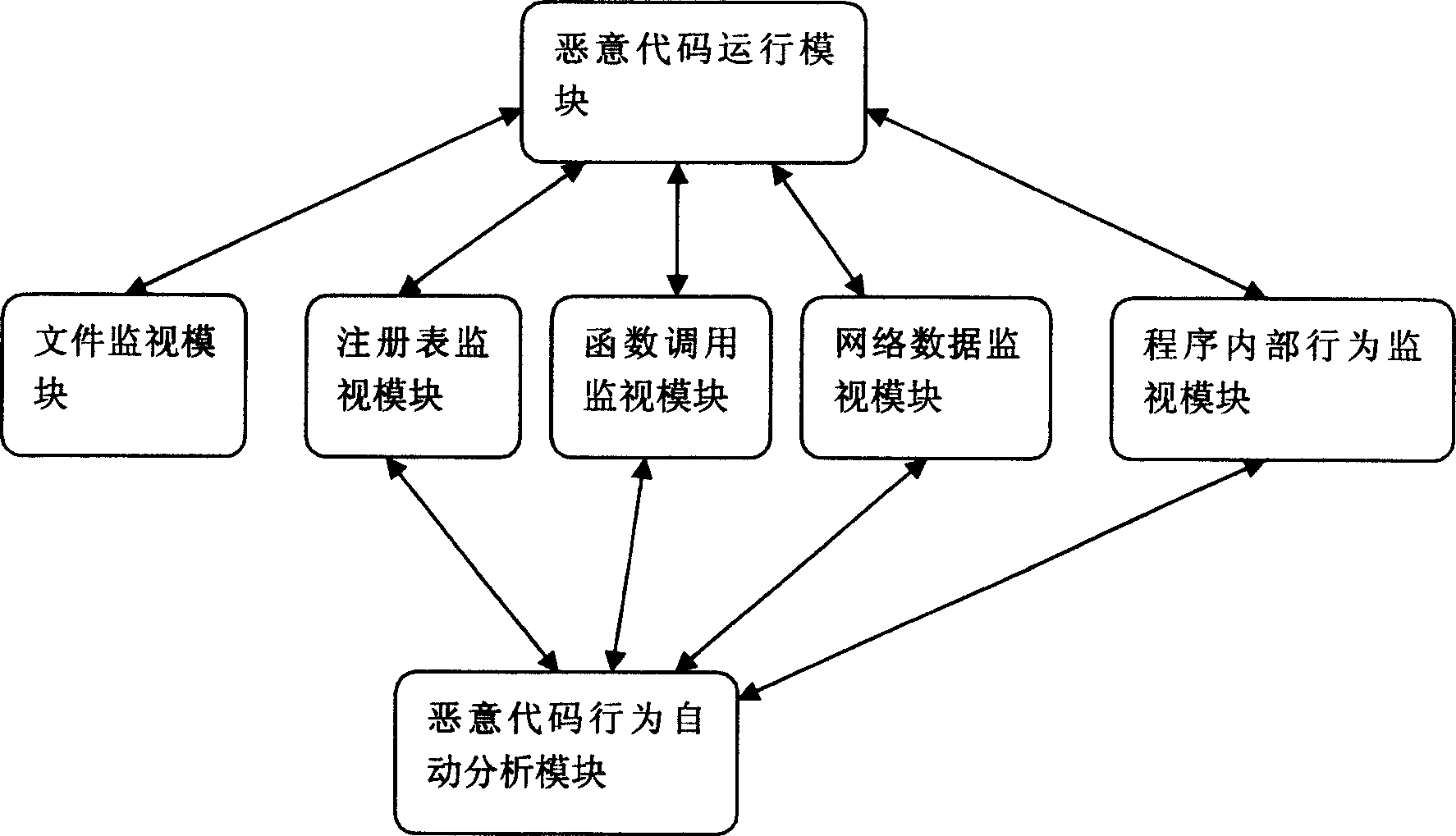
[0032] figure 2 It is a relationship diagr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com