High-safety two-operating system mobile phone capable of resisting hackers and being used for Internet banking
A dual-operating system, operating system technology, applied in the direction of telephone communication, electrical components, branch equipment, etc., can solve problems such as user loss and complex application design.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The method of the present invention will be described in further detail below in conjunction with the accompanying drawings.
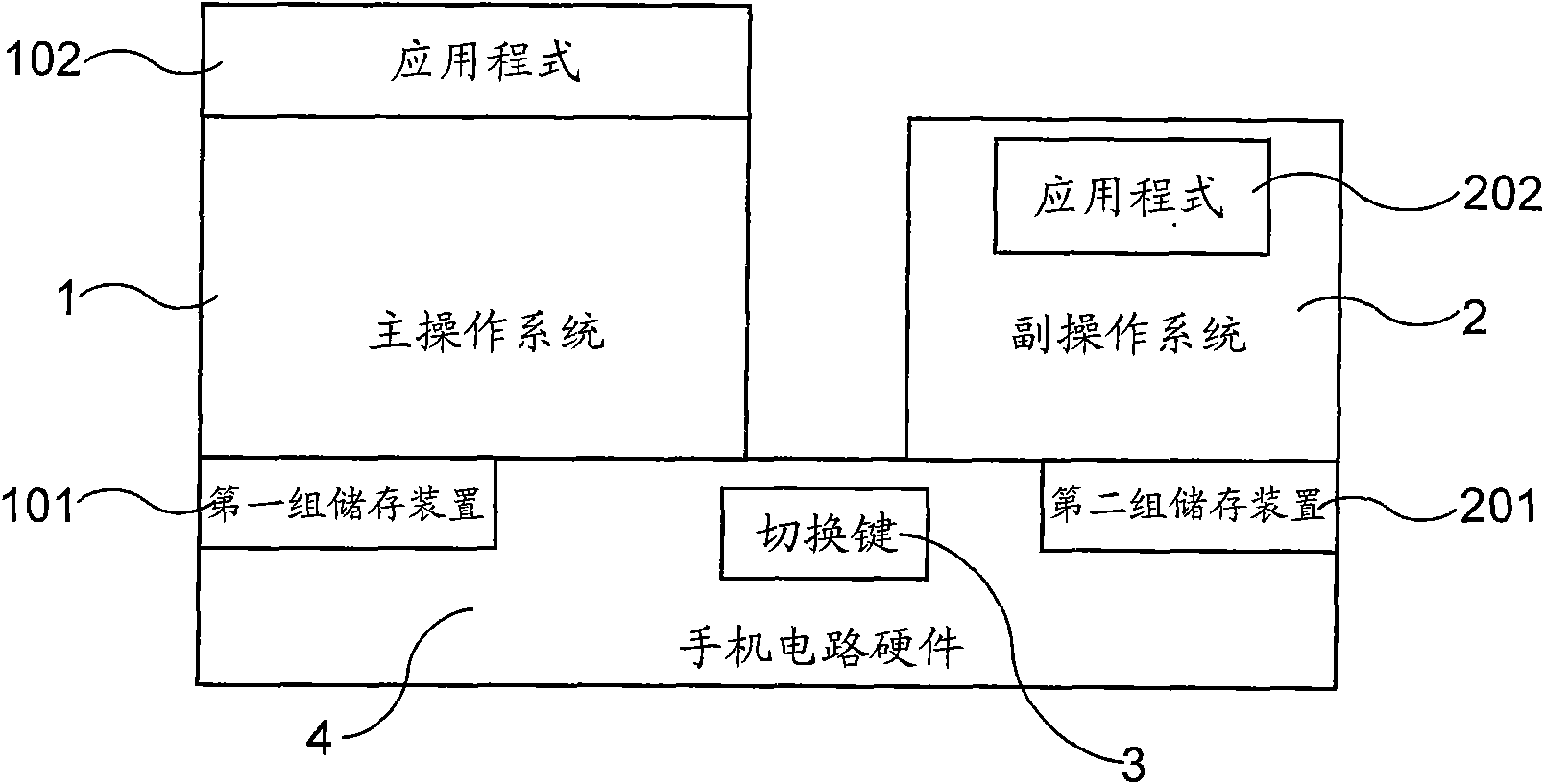
[0013] refer to figure 1 and figure 2 , figure 1 It is a schematic explanatory diagram of the main operating system (1) and the secondary operating system (2) of the dual operating system mobile phone of the present invention, figure 2 It is a visual schematic illustration of the dual-operating system mobile phone of the present invention, figure 1 and figure 2 The mobile phone shown in contains at least two mutually independent operating systems, including a main operating system (1) and a secondary operating system (2), and is provided with a switching key (3), wherein the main operating system (1) is mainly used for general mobile phones; the secondary operating system (2) is mainly used for processing some important data with high security level; the switch key (3) is mainly used for selecting the current operating system of the mobil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com