Method for improving neighbor discovery safety in IPv6 (Internet Protocol Version 6) environment and broadband access equipment
A technology for neighbor discovery and access equipment, applied in security devices, digital transmission systems, electrical components, etc., can solve problems such as difficulty in ensuring user data flow security, and achieve the effect of avoiding paralysis and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0044] This embodiment provides a technical solution on how to effectively prevent duplicate address detection DoS attacks.
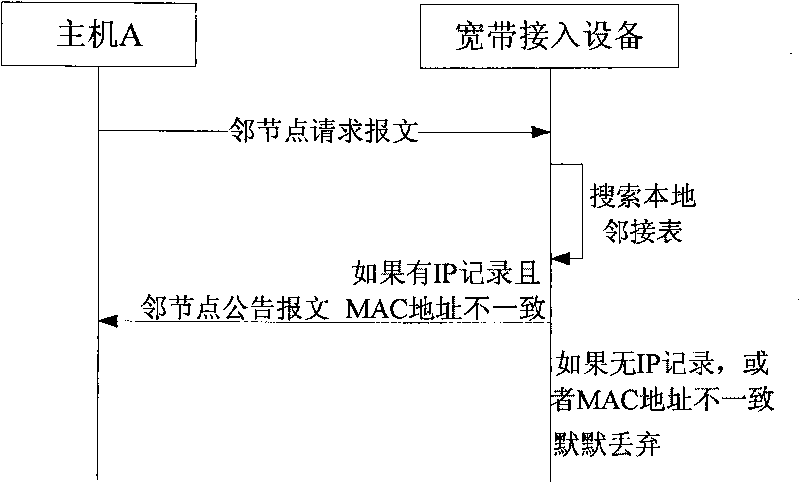
[0045] In the prior art IPv6ND process, a malicious attack node in a link can use the vulnerability of duplicate address detection to carry out DoS attacks, because the user's IPv6 address information will spread to other nodes in the link, and the malicious attack node can monitor the local All DAD packets of the link. The neighbor node request message sent by the user node of the present invention is not forwarded to other user lines, but is only uniformly controlled and replied by the broadband access equipment, so other users cannot attack through the ND request.
[0046] Below in conjunction with accompanying drawing, present embodiment is described in further detail:
[0047] The networking diagram of the broadband access network is as follows: figure 1 As shown, it includes a router, a broadband access device, and multiple user nodes connected ...
no. 2 example
[0063] This embodiment provides a technical solution on how to effectively prevent user IPv6 address information from spreading to other user lines.
[0064] The networking diagram of the broadband access network is the same as that of the first embodiment, for example figure 1 shown.
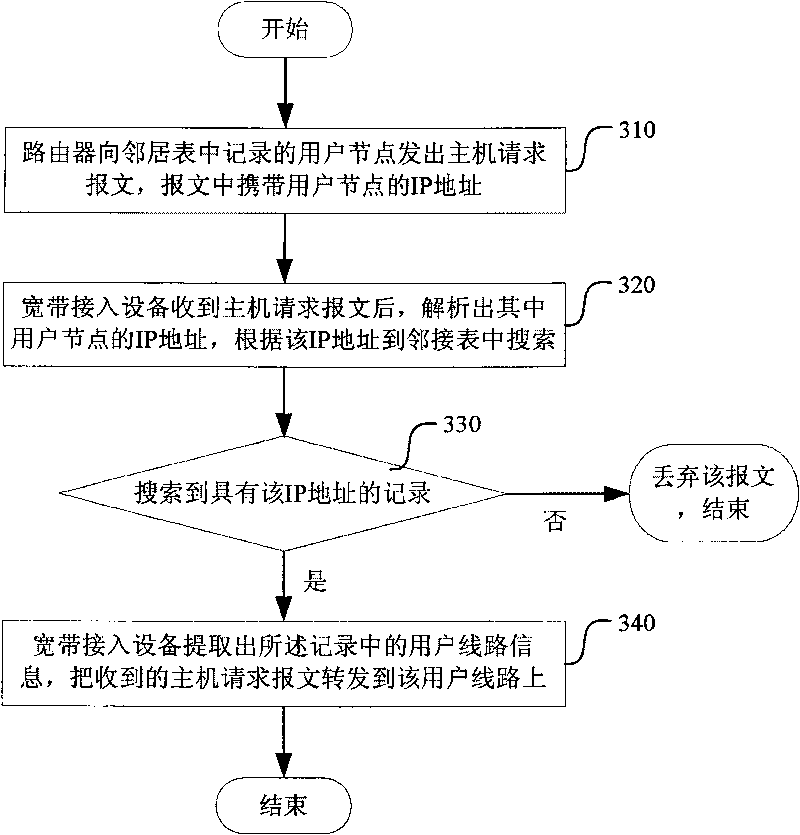
[0065] The router will periodically send a host request message (that is, initiate an ND request) to the user node recorded in the neighbor table, and the message carries the IP address of the user node.
[0066] The host request message is first sent to the broadband access device to which the user node belongs. In order not to spread the IP address of the user node to irrelevant user lines, the broadband access device must forward the host request message to the corresponding user line. After receiving the host request message, the user node sends a response to the router, carrying its own MAC address, and the router refreshes its neighbor table according to the content of the user node's re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com