Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
81results about How to "Protect information security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
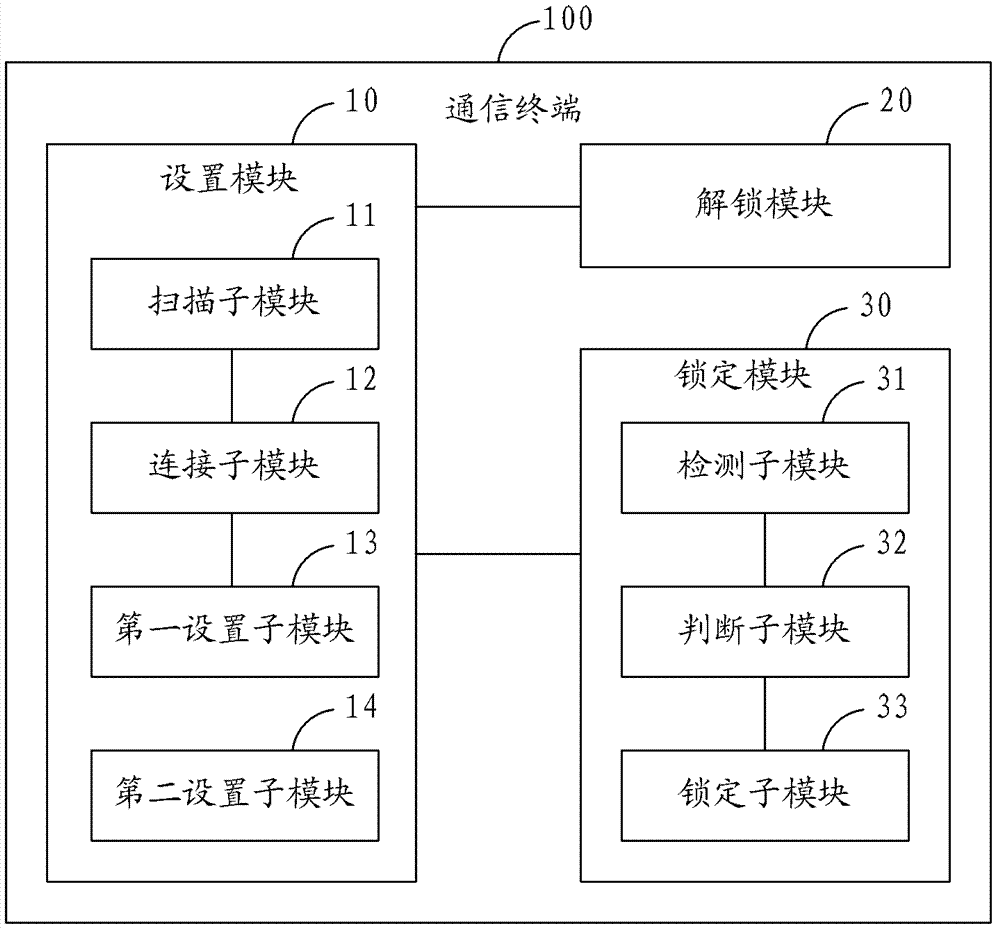
WiFi network-based unlocking or locking method and communication terminal
ActiveCN103369511AProtect information securityLock and unlock withConnection managementNetwork data managementWifi networkComputer hardware
The invention is suitable for the communication technology field and provides a WiFi network-based unlocking or locking method comprising the following steps: at least a WiFi network is set as an unlocking network or locking network of a communication terminal; when that the communication terminal is connected with the WiFi network is detected, the communication terminal is unlocked or locked; when that the communication terminal is disconnected with the WiFi network is detected, the communication terminal is locked or unlocked. Correspondingly, the invention also provides communication terminal. Thus, the WiFi network-based unlocking or locking method and the communication terminal are characterized in that convenience and practicality of communication terminal unlocking or locking operation can be realized.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
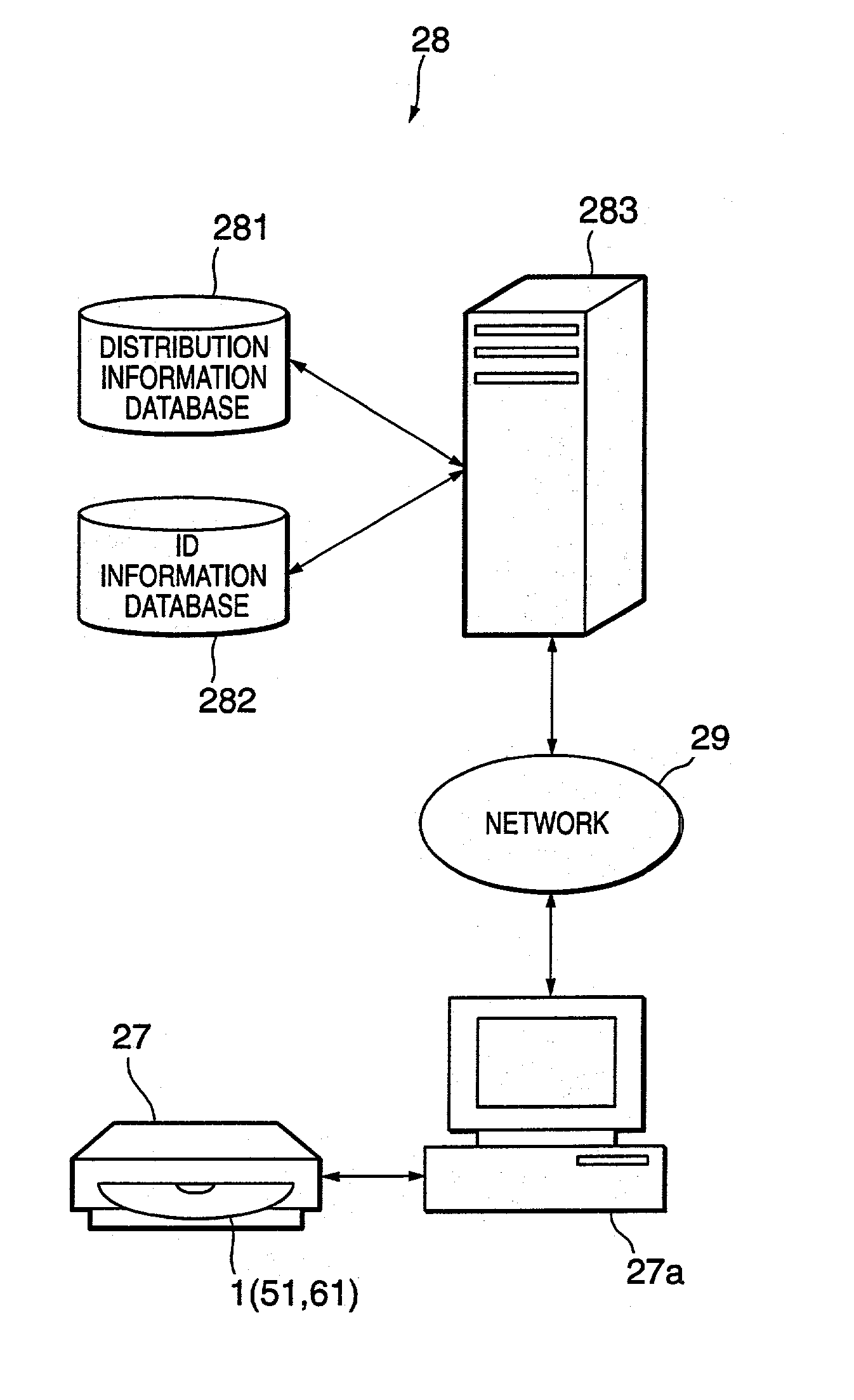
Information distribution method, information distribution system and information distribution apparatus
InactiveUS20020178145A1The certification process is reliableProtect information securityInformation arrangementDigital data processing detailsDistribution methodDistribution system
The present invention introduces an information distribution method capable of making an information distribution business for reliably authenticating a recording medium and distributing information in a prepaid manner. For this end, ID information recorded in a read-only area is read out from a disc-shaped recording medium having a read-only area and a recording and / or reading area. Judgment (or decision) is made whether or not information distribution to the recording medium is permitted based on the read-out ID information. The signal information distributed as a result of the judgment is recorded in the recording and / or reading area of the recording medium. The recording and / or reading area of the recording medium is rewritable. In case of reading the ID information out of the read-only area of the recording medium, erasing of recorded information for the recording and / or reading area is performed at the recording position for the ID information before reading the ID information.
Owner:SONY CORP
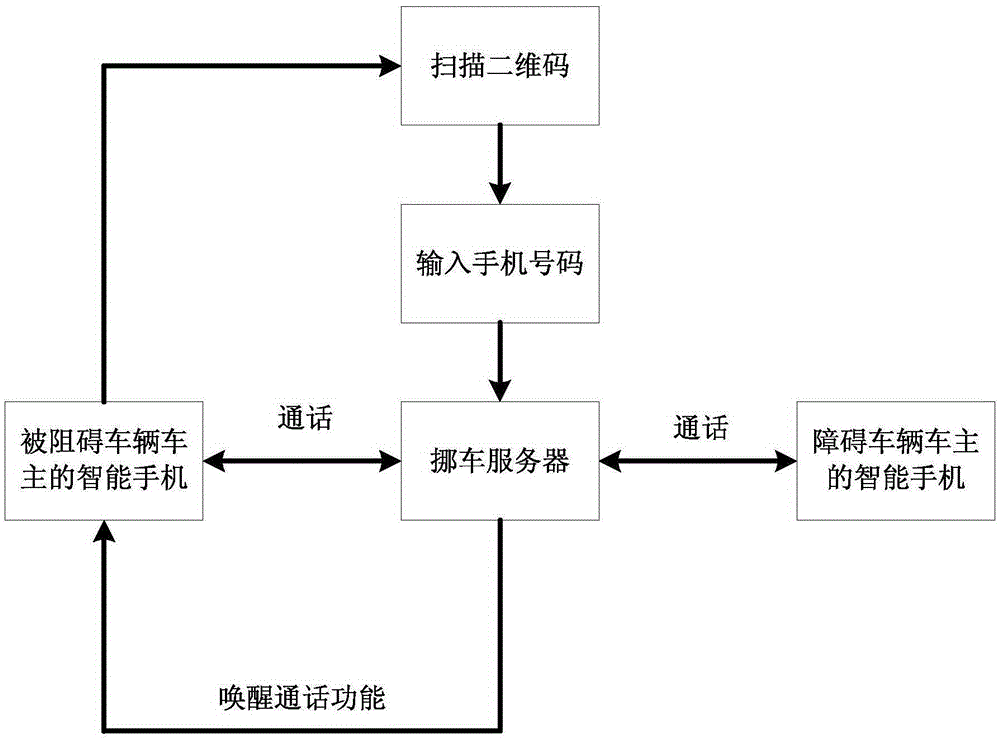
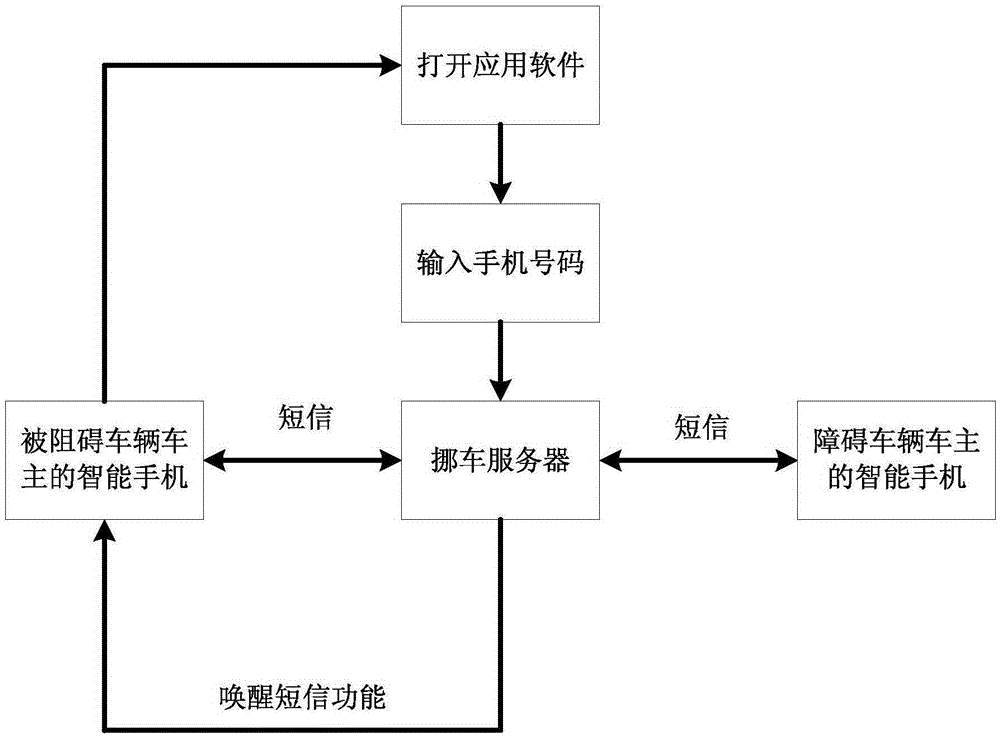
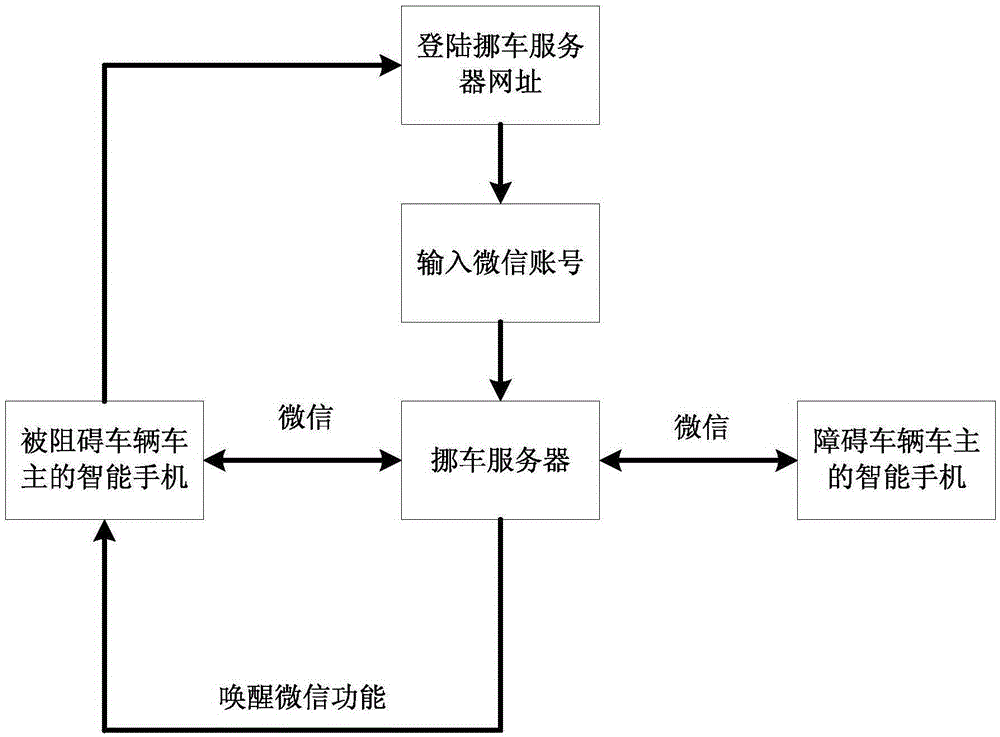
Communication method and system applied to vehicle moving
InactiveCN105430039AProtect privacy and securityProtect information securityTransmissionInformation securityReal-time computing
The invention discloses a communication method and a system applied to vehicle moving. When driving difficulty occurs, an owner of a blocked vehicle regards a vehicle-moving server platform as an intermediate medium so that the communication with an owner of a blocking vehicle is realized, and the problem of driving difficulty is solved in time. Besides, in a communication process of both vehicle owners, both of them cannot obtain information of the other so that individual privacy and information security of the owners are protected.
Owner:SHENZHEN VCYBER TECH
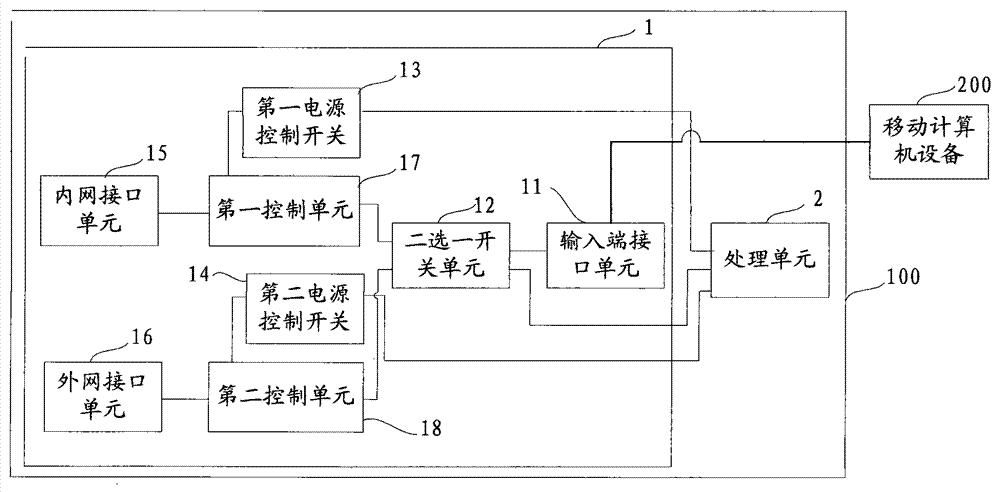
Secure access mode for intranet and extranet
InactiveCN103532978AProtect information securityImprove information securityData switching current supplyPower controlComputer equipment
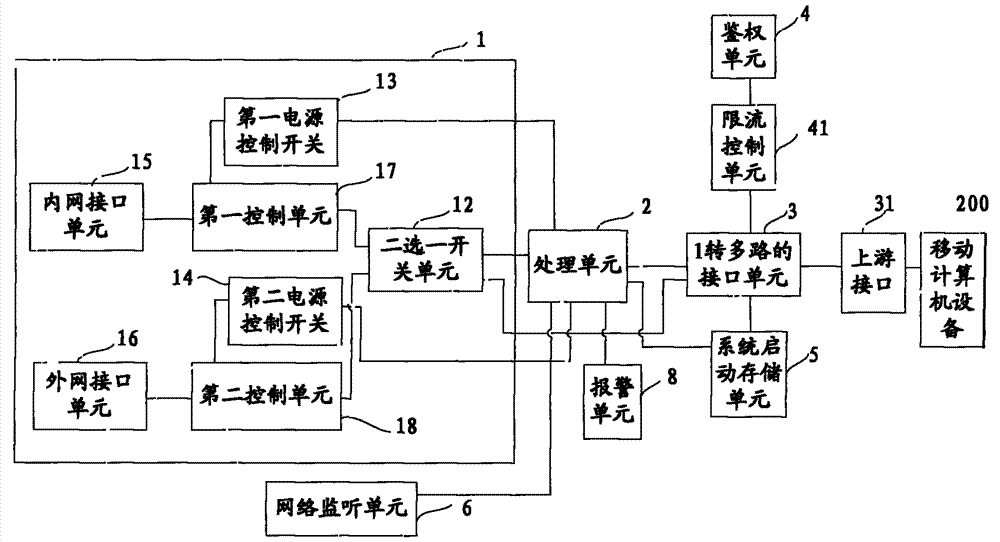
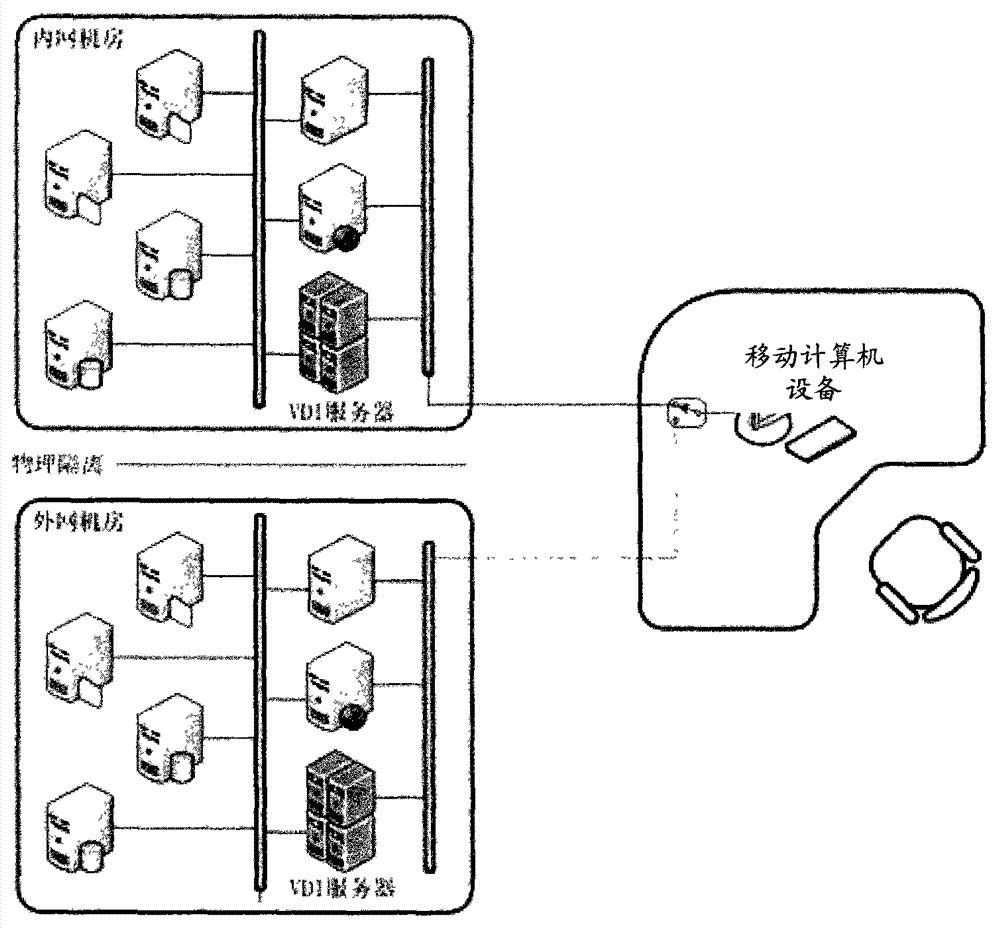
The invention provides a secure access mode for an intranet and an extranet. An input-end interface unit of intranet and extranet safety equipment is connected with a first control unit and a second control unit respectively through a two-channel switch unit; when mobile computer equipment selects an extranet mode, a processing unit controls the two-channel switch unit to gate the second control unit, switches on a second power control switch to enter an extranet system and switches off a first power control switch to cut off connection with an intranet system at the moment; and when the mobile computer equipment selects an intranet mode, the processing unit controls the two-channel switch unit to gate the first control unit, switches on the first power control switch to enter the intranet system and switches off the second power control switch to cut off connection with the extranet system at the moment. The secure access mode for the intranet and the extranet is used for realizing isolation and safety protection of the intranet and extranet systems, and information security of the intranet system can be protected effectively.
Owner:BEIJING AISIMENG TECH
Method, system and management center server for providing mobile service
InactiveUS20080045192A1Network flow can be loweredReduce in quantitySpecial service for subscribersTransmissionApplication serverMobile service
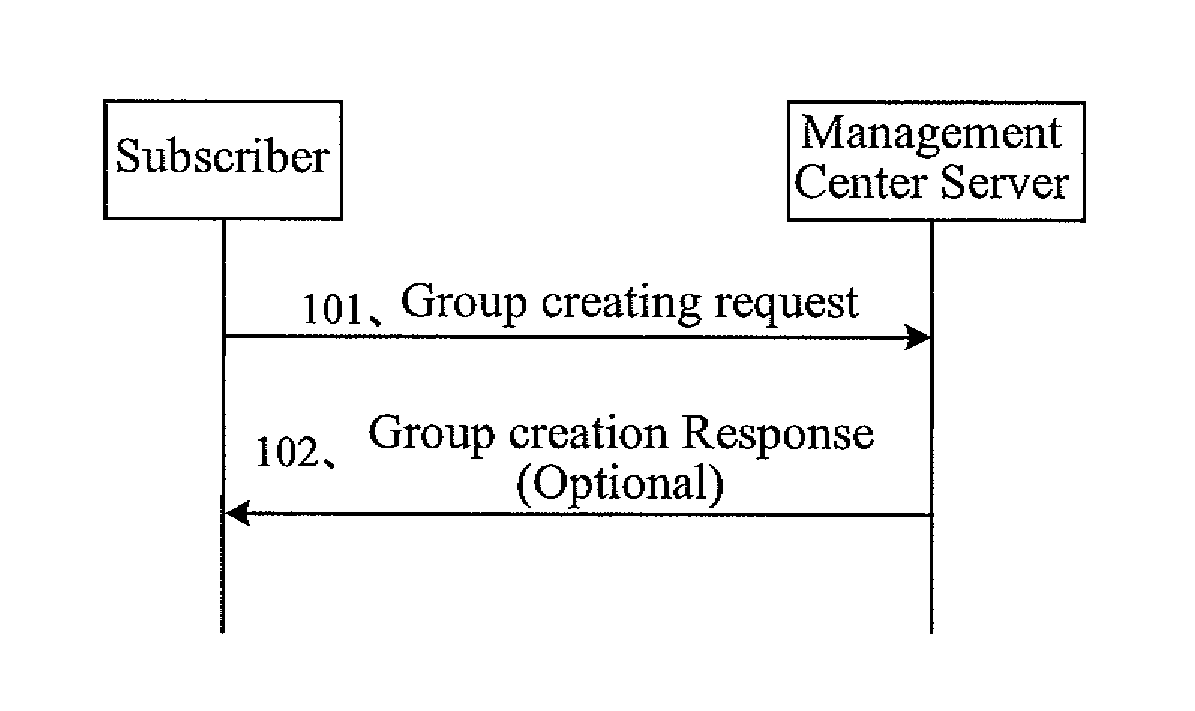
A method and a system for providing mobile service are disclosed. In the method, a management center server saves a group service subscription index; a service processing server receives a service message from a service application server, and sends a subscription verifying request containing the service ID and group ID to the management center server when it is resolved that the receiving party of the service message has a group ID; the management center server verifies whether the group has subscribed for the service according to the group service subscription index that is stored; and when the verification is passed, a service engine obtains the group user ID that pertains to the group ID and sends a service message to a user terminal. The invention further provides a management center server.
Owner:HUAWEI TECH CO LTD
Remote real-time monitoring method of big-bus operating status, fuel consumption and exhaust gas emission and monitoring system thereof
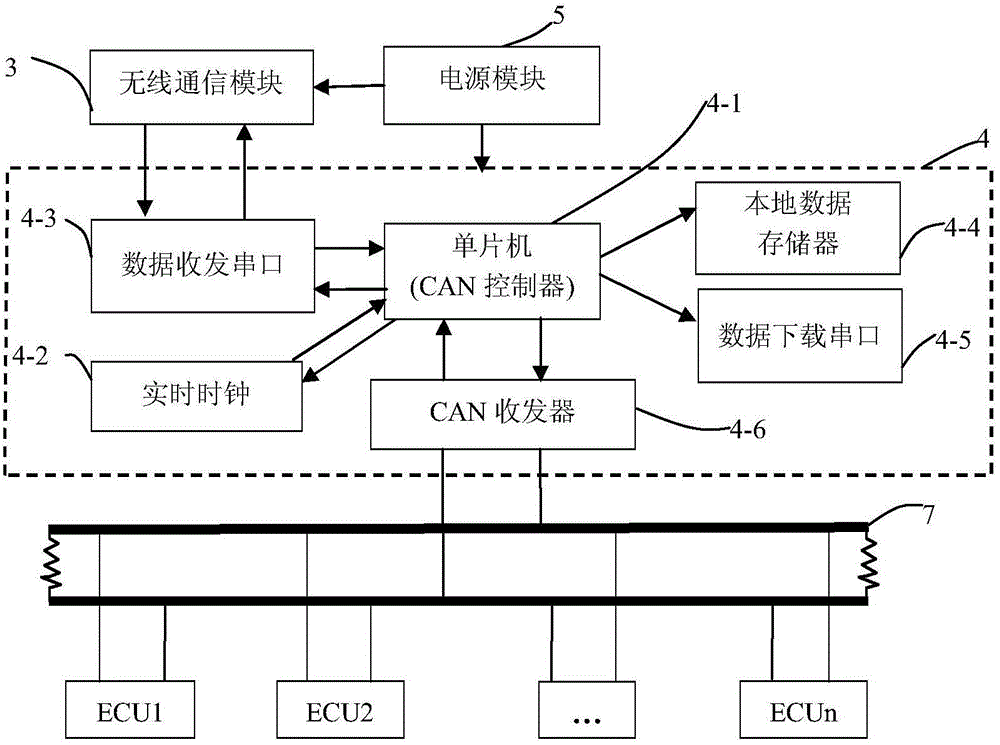
ActiveCN104601718AProtect information and system securityReduce network communication pressure and communication costsTransmissionData shippingForms Control
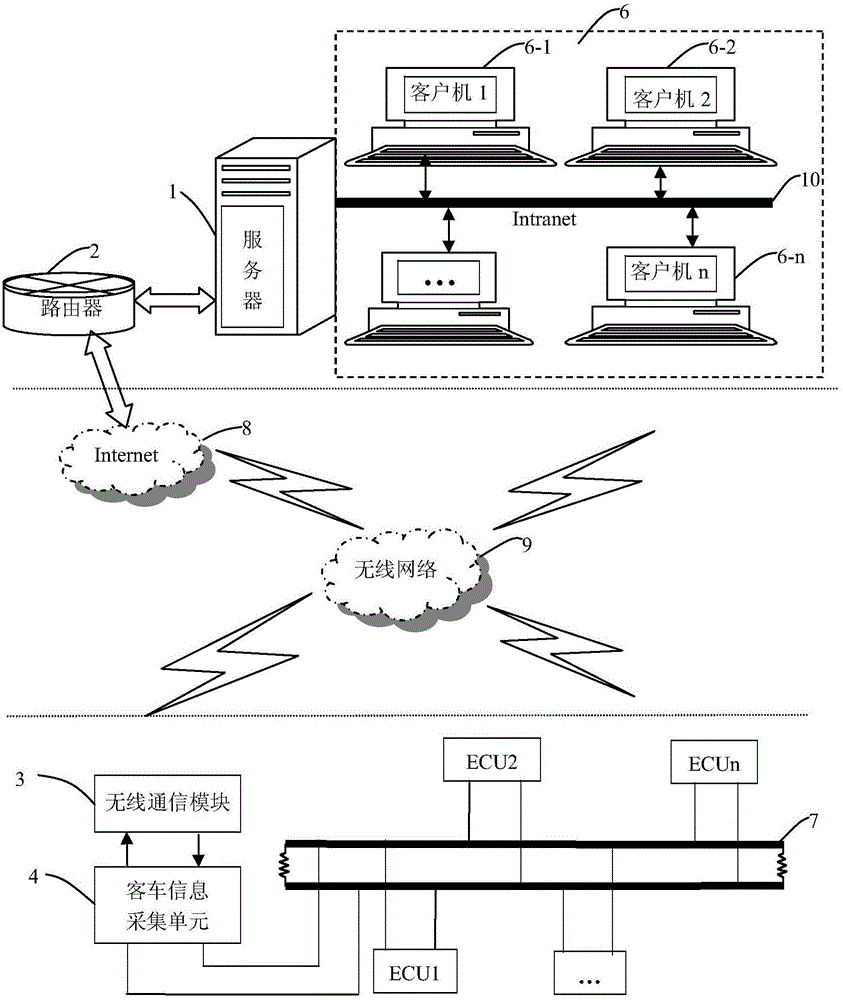
The invention discloses a remote real-time monitoring method of a big-bus operating status, fuel consumption and exhaust gas emission. The remote real-time monitoring method comprises the following steps: an online communication model is established between a server and a wireless communication module; user request information forms control instructions by the server, and the control instructions are transmitted to the wireless communication module through a router, an internet and a wireless network after being encrypted, and the encrypted control instructions are transmitted to a bus information acquisition unit through the wireless communication module; the encrypted control instructions are decrypted by the bus information acquisition unit, the big-bus operating status, and the fuel consumption and exhaust gas emission data are acquired from the CAN (Controller Area Network) bus of the big bus and processed, and the real-time data is encrypted and transmitted to the wireless communication module; the encrypted real-time data is transmitted to the server through the wireless communication module and decrypted through the server, the decrypted data is processed and accessed by the client of the user. The monitoring system comprises the server, the router, the wireless communication module installed on the big bus, the big-bus information acquisition unit and the power supply module.
Owner:XIHUA UNIV
Mobile payment encryption method based on near field communication (NFC)
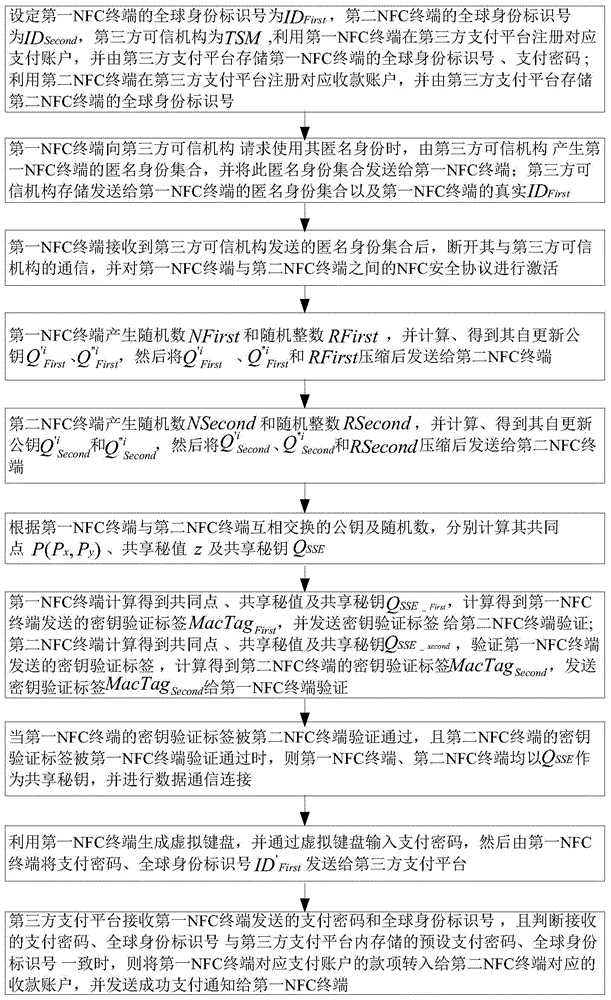
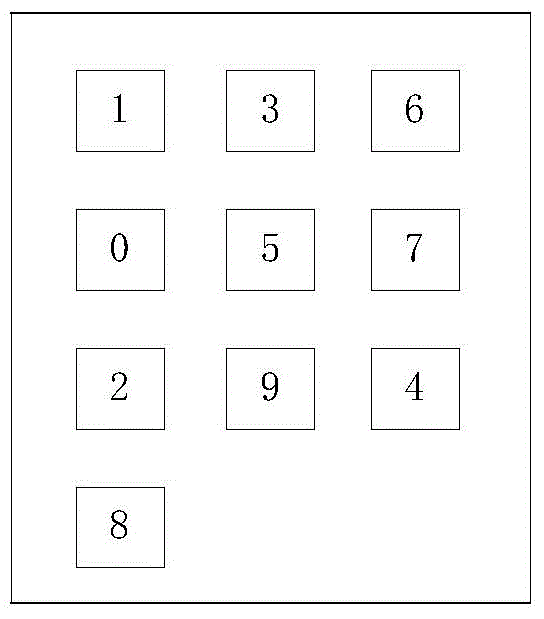
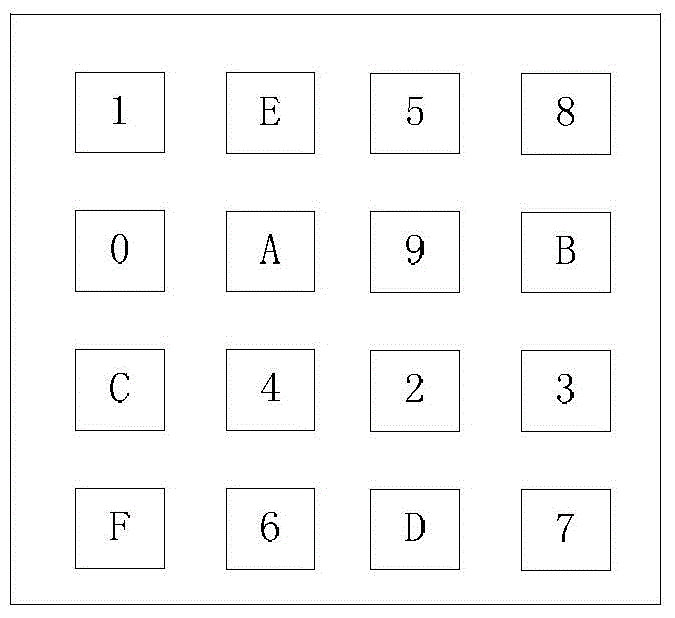
ActiveCN105228087AProtect privacy and securityProtect information securityWireless commuication servicesAnonymous user systemsThird partyPayment transaction
The invention relates to a mobile payment encryption method based on near field communication (NFC). The method comprises the following steps that: a first NFC terminal and a second NFC terminal store real IDs of the first NFC terminal and the second NFC terminal in a trusted service manager respectively, and the trusted service manager stores anonymous identities of the two NFC terminals; during mobile payment, the first NFC terminal and the second NFC terminal make requests of using the anonymous identities of the first NFC terminal and the second NFC terminal to the trusted service manager respectively, calculate self-update public keys and key verification tags of the first NFC terminal and the second NFC terminal, and transmit the calculated self-update public keys and key verification tags to other parties for verification; and when the key verification tags of the first NFC terminal and the second NFC terminal pass verification of the other parties and the self-update public keys are the same, the first NFC terminal and the second NFC terminal use the same self-update public keys as shared public keys of the two parties in order to finish a payment process. According to the method, encryption is performed between two communication parties with continuously-updated public keys, and the identities of the two communication parties are hidden with the anonymous identities, so that the privacies and information security of two payment transaction parties are effectively protected.
Owner:NINGBO UNIV
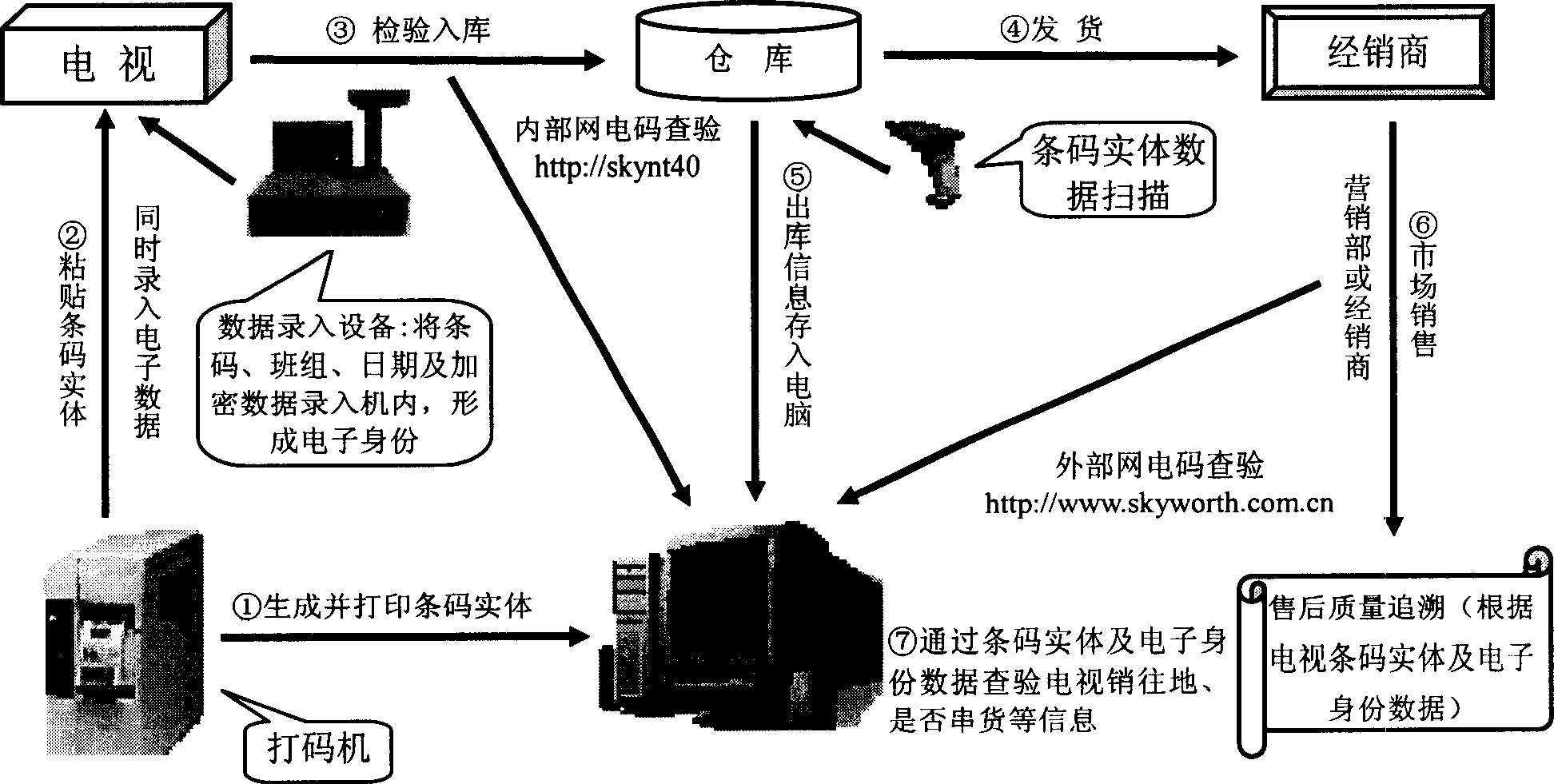
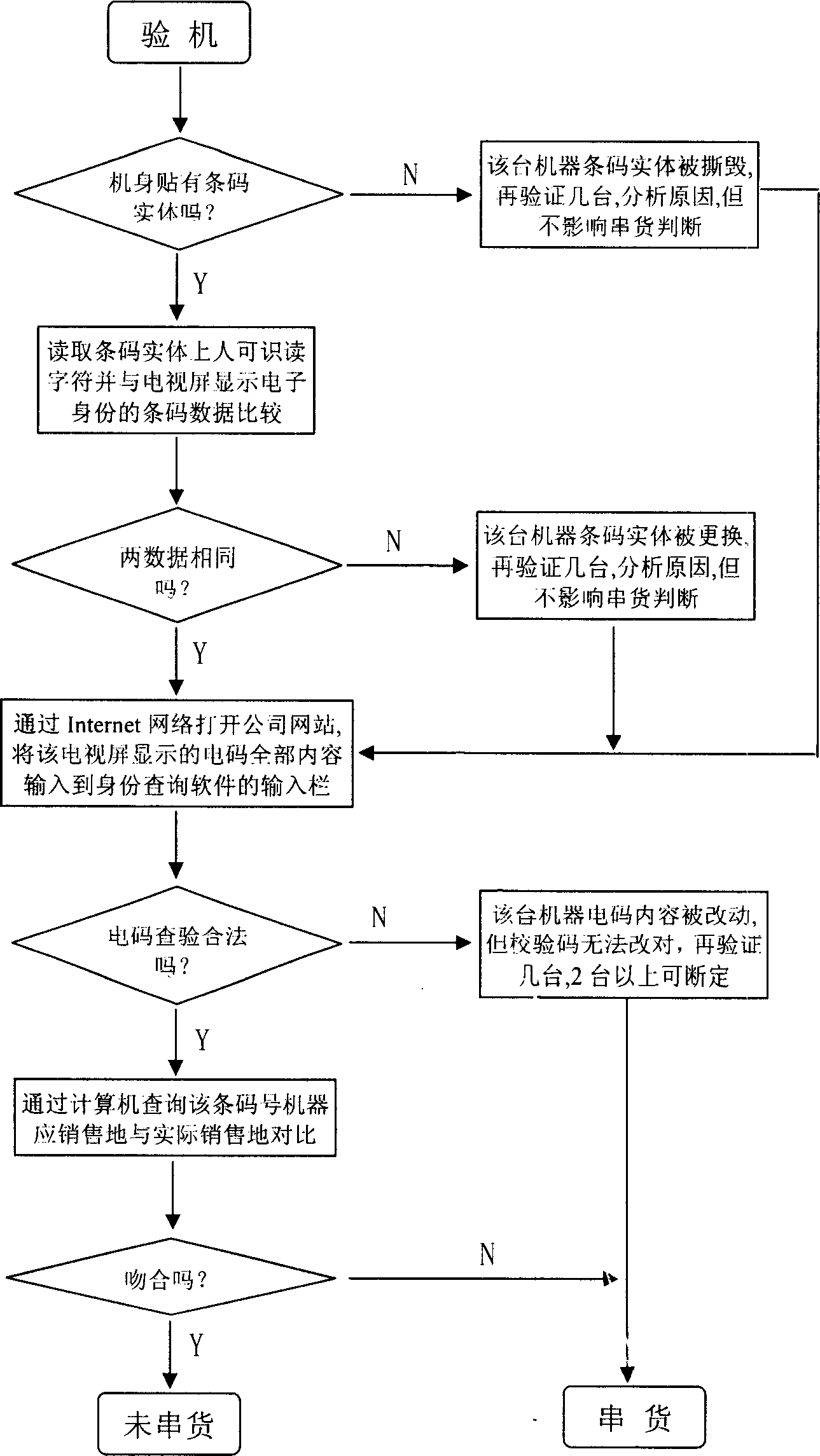
Method for storing and inquiring identity information of sale merchandise
InactiveCN1734450AAccurate authenticationPrevent cross-sellingSensing record carriersSpecial data processing applicationsModel NumberComputer science
The invention discloses an identity information storing and checking method of sales commodity, which comprises the following steps: a) sticking bar code on the commodity or package, whose basic information concludes commodity type+key component number +product sequence; b) transforming null symbol to datum of bar code and superimposing the group product and daily date datum of the commodity; c) disposing the datum with superimposing the step b) to obtain electric identity information encryptedly; d) inputting the information to storage unit of specific commodity; e) recording the information of electric identity, sales address where the commodity post and transportation in the computer datum.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
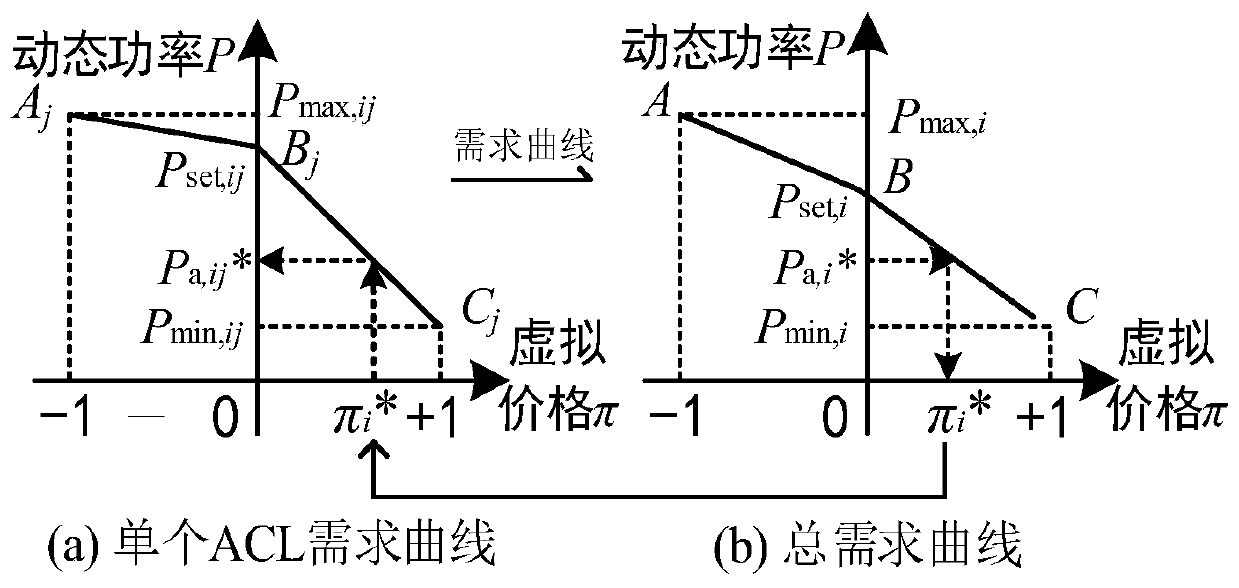
An information physical modeling and control method for aggregating large-scale air conditioner loads
ActiveCN109934470AProtect data privacyReduce communication costMechanical apparatusSpace heating and ventilation safety systemsHybrid systemOptimal scheduling
The invention relates to an information physical modeling and control method for aggregating large-scale air conditioner loads, and the method comprises the steps: the air conditioner loads is regarded as an information physical system (CPS) at a load layer, an air conditioner load probability control method based on a semi-Markov process is provided, and the locking time of an air conditioner canbe guaranteed and the diversity of a cluster state is kept; A hybrid system model is utilized to establish a coupling relation between the air conditioner load physical process and the control process, and autonomous control over the air conditioner load is achieved; In an aggregator layer, a coordination control method for aggregating air conditioner loads into virtual peak shaving units is provided based on a market balance mechanism, and the method can effectively protect user data privacy and remarkably reduce the communication cost. Meanwhile, the virtual peak regulation unit can providea quotation curve and regulation capacity similar to a conventional unit for scheduling, so that the virtual peak regulation unit participates in optimal scheduling of a power grid layer. Compared with the prior art, the method has the advantages of remarkably reducing the communication cost, facilitating optimal scheduling and the like.
Owner:SHANGHAI JIAO TONG UNIV
User ID authentication method and system based on quantum network
InactiveCN101854347AProtect information securityImprove transmission efficiency and transmission securityUser identity/authority verificationAuthentication systemUser authentication
The invention provides a user ID authentication method and system based on a quantum network, which comprises the following steps that: an authentication center issues an ID authentication card; a user sends an authentication request; a quantum communication protocol creates shared data; the user summates the shared data and calculates the bit error rate, and the authentication center selects part of the summated shared data as a polarization mode after determining that the bit error rate belongs to a preset threshold range; the authentication center sends a pseudo selection code and a correction code; the user calculates a selection code according to the pseudo selection code and the correction code so as to obtain an ID authentication code; the users mutually authenticate or the user authenticates with the authentication center; and the authentication center backups the authentication result. The user ID authentication method can effectively protect the private information of the user, and has the advantages of safety and reliability. The invention also provides a user ID authentication system based on the quantum network, which similarly can effectively protect the private information of the user, and has the advantages of safety and reliability.
Owner:朱律波
Cloud data security storage method and system
ActiveCN107453880APrevent Malicious LeakagePrevent unauthorized accessUser identity/authority verificationData informationCiphertext
The invention provides a novel cloud data security storage method and system, which can not only prevent the malicious disclosure of data information, but also provide a user with personal data security protection and prevent unauthorized access to personal data information by a server side or a service provider. In the invention, a symmetric key for encryption and decryption is generated jointly according to a password of identity authentication input by the user and verification information stored in the system to protect the data stored in the system. The password of identity authentication and personal data of the user are stored in the form of a cipher text in the cloud, and the personal privacy and information security are effectively protected.
Owner:国家康复辅具研究中心
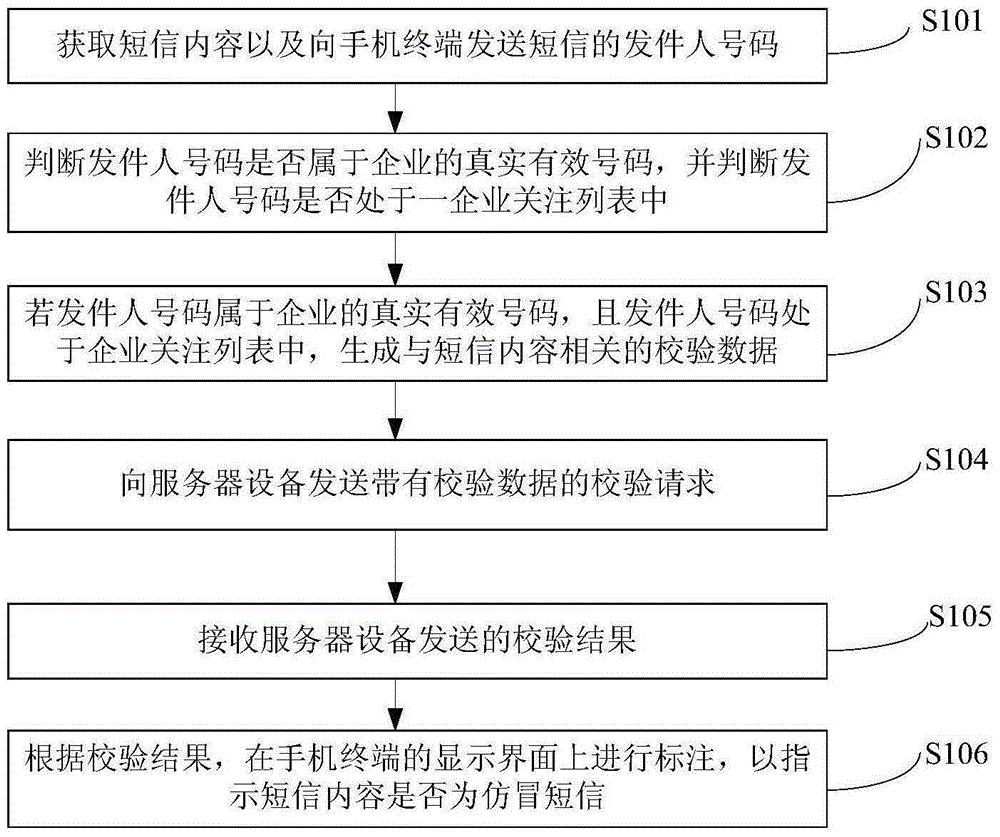
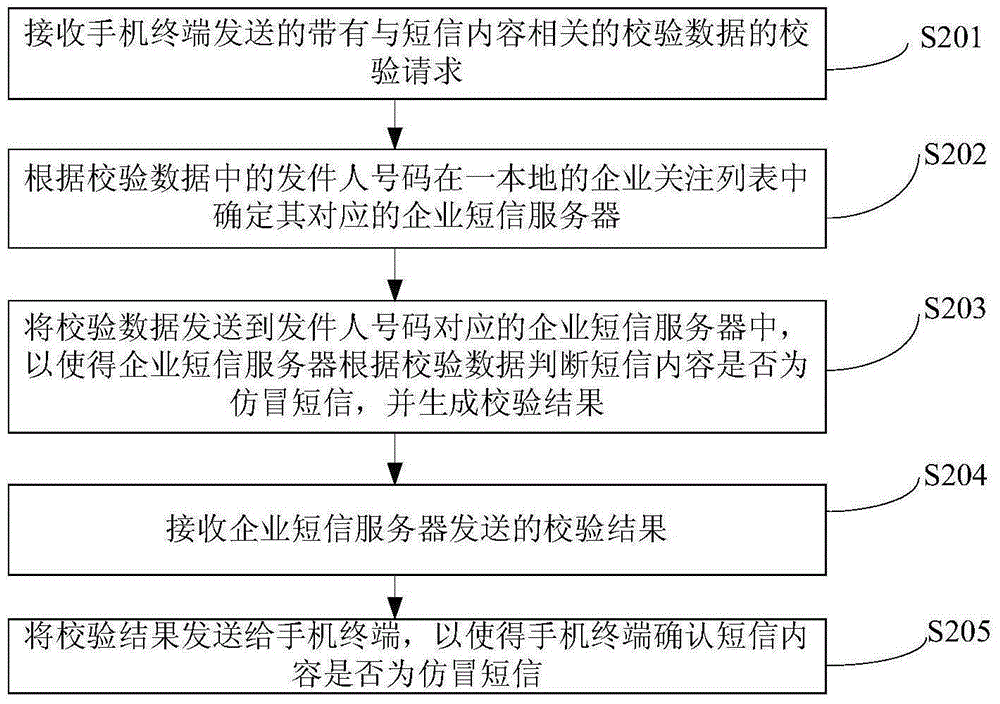
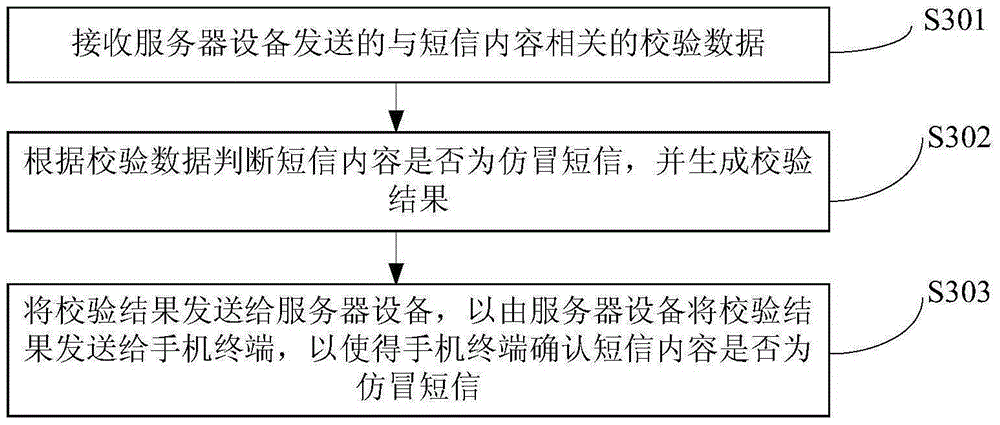
Counterfeit short message identification method, mobile phone terminal, server, and system
ActiveCN105933876AProtect information securityProtection securityMessaging/mailboxes/announcementsSecurity arrangementComputer terminalInformation security
The invention provides a counterfeit short message identification method, a mobile phone terminal, a server, and a system, relating to the technical field of information security. The method includes acquiring the short message content and sending the sender number of the short message to the mobile phone terminal; determining whether the sender number is a real effective number of an enterprise and whether the sender number is in an enterprise interest list; if the sender number is a real effective number of the enterprise and the sender number is in the enterprise interest list, generating the verification data related to the short message content; sending the verification request with the verification data to a server device; receiving the verification result transmitted by the server device; and based on the verification result, making a mark on the display interface of the mobile phone terminal to indicate whether the short message is a counterfeit message. Therefore, the problem that the counterfeit message is a big threat to the information and the property security of a mobile phone user can be solved.
Owner:CHINA UNIONPAY
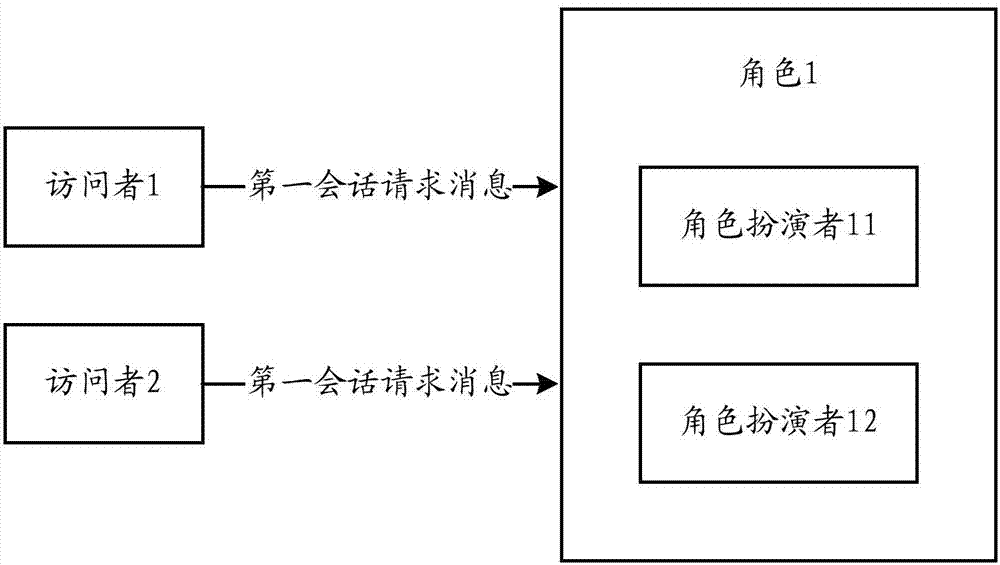
Method, server and system for carrying out instant session based on roles
ActiveCN107046496AProtect privacy and securityProtect information securityData switching networksClient-sideUser identifier
The invention discloses a method, server and system for carrying out instant session based on roles. The method comprises the following steps: pre-storing a corresponding relation between roles and user identifiers in a role relation database; receiving a first session request message sent by a client, wherein the first session request message comprises the user identifier corresponding to the client and target role information specified by the client; finding user identifiers corresponding to a target role from the role relation database according to the target role information; and establishing an exclusive group chat relation between the user identifier corresponding to the client and one or more user identifiers corresponding to the target role, receiving session information sent by the client corresponding to any user identifier in the exclusive group chat relation, and sending the session information to the exclusive group chat relation. By adoption of the scheme, each user initiating the session can privately carry out the instant session with the target role specified by the user, the session objective can be accomplished efficiently, and the privacy and the information security of the user are protected.
Owner:澜途集思生态科技集团有限公司
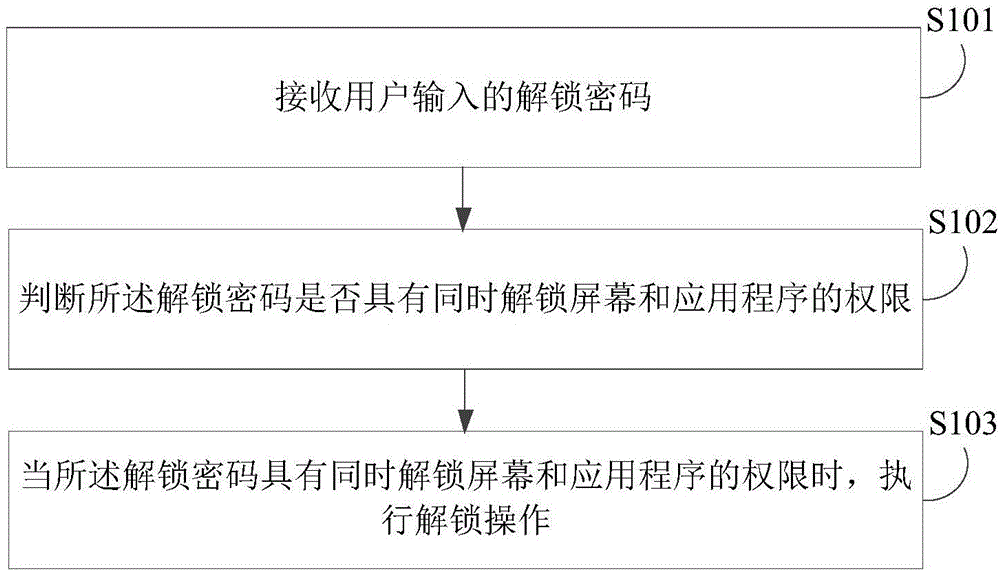
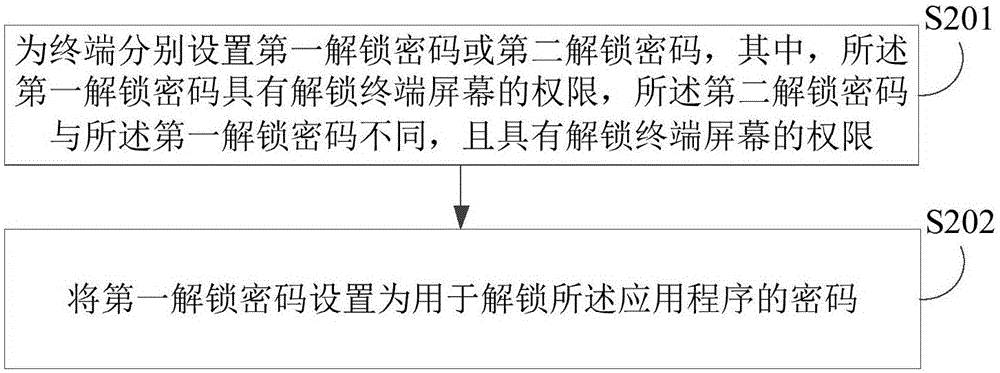
Unlocking method and device
InactiveCN106682463AProtect privacy and securityProtect information securityDigital data authenticationUser inputPassword
The invention discloses an unlocking method and device. The method comprises the steps that an unlocking password inputted by a user is received; the unlocking password is judged whether or not the password has the authority to unlock the screen and to run a program at the same time; when the unlocking password has the authority to unlock the screen and to run the program at the same time, an unlocking operation is executed. The method can set the unlocking methods of a terminal screen and an application program according to the operational habits and preferences of the user, so that the user can unlock at the same time the terminal screen and the application programs, or unlock in sequence the terminal screen and the application programs; in this way, under the precondition of protecting the privacy of the user and information security, the method provides great conveniences for the user and helps to save time for the user.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
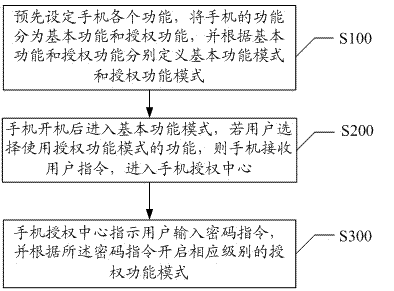
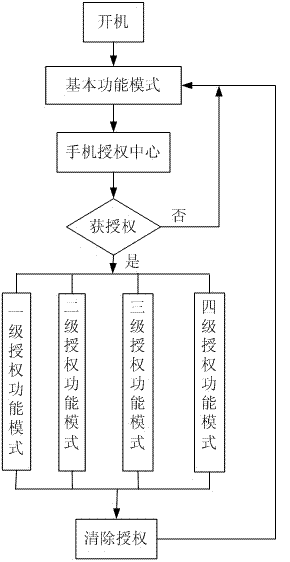
Method and system for realizing mobile phone information safety protection mechanism
InactiveCN102413243AProtect information securityImprove information securitySubstation equipmentEmbedded systemSpecific function
The invention discloses a method and system for realizing a mobile phone information safety protection mechanism. Through separating all functions of a mobile phone into basic functions and authorization functions in advance, basic function modes and authorization function modes are respectively defined according to the basic functions and the authorization functions, corresponding grade of authorization function mode is opened through a mobile phone authorization module according to a password of a user, so that the user uses a special mobile phone function, realizes intelligent safe management of the mobile phone function, and prevents others from using some specific functions under the condition of no authorization, thus information safety of the mobile phone is better protected.
Owner:SHENZHEN KONKA TELECOMM TECH
ESIM (Embedded SIM) card authentication method, eSIM card authentication device and terminal
InactiveCN105636043AProtect information securityProtection securitySecurity arrangementComputer hardwarePassword
The invention provides an ESIM (Embedded SIM) card authentication method, an eSIM card authentication device and a terminal. The eSIM card authentication method comprises the steps of verifying whether a received eSIM card password is in accordance with a preset authentication password based on a received service interaction request; and when the fact that the received eSIM card password is in accordance with the preset authentication password is determined, allowing the eSIM card to carry out service interaction with an operator. Through the technical scheme of the ESIM card authentication method, an authentication strategy of eSIM card binding and unbinding is perfected; and when a person meets with conditions such that a mobile phone is stolen, the eSIM card cannot carry out service interaction with the operator if the eSIM card password authentication is failed, and the eSIM card can be deadly locked, so that information and property safety of a user is protected, and the user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
H5 non-login user session tracking method
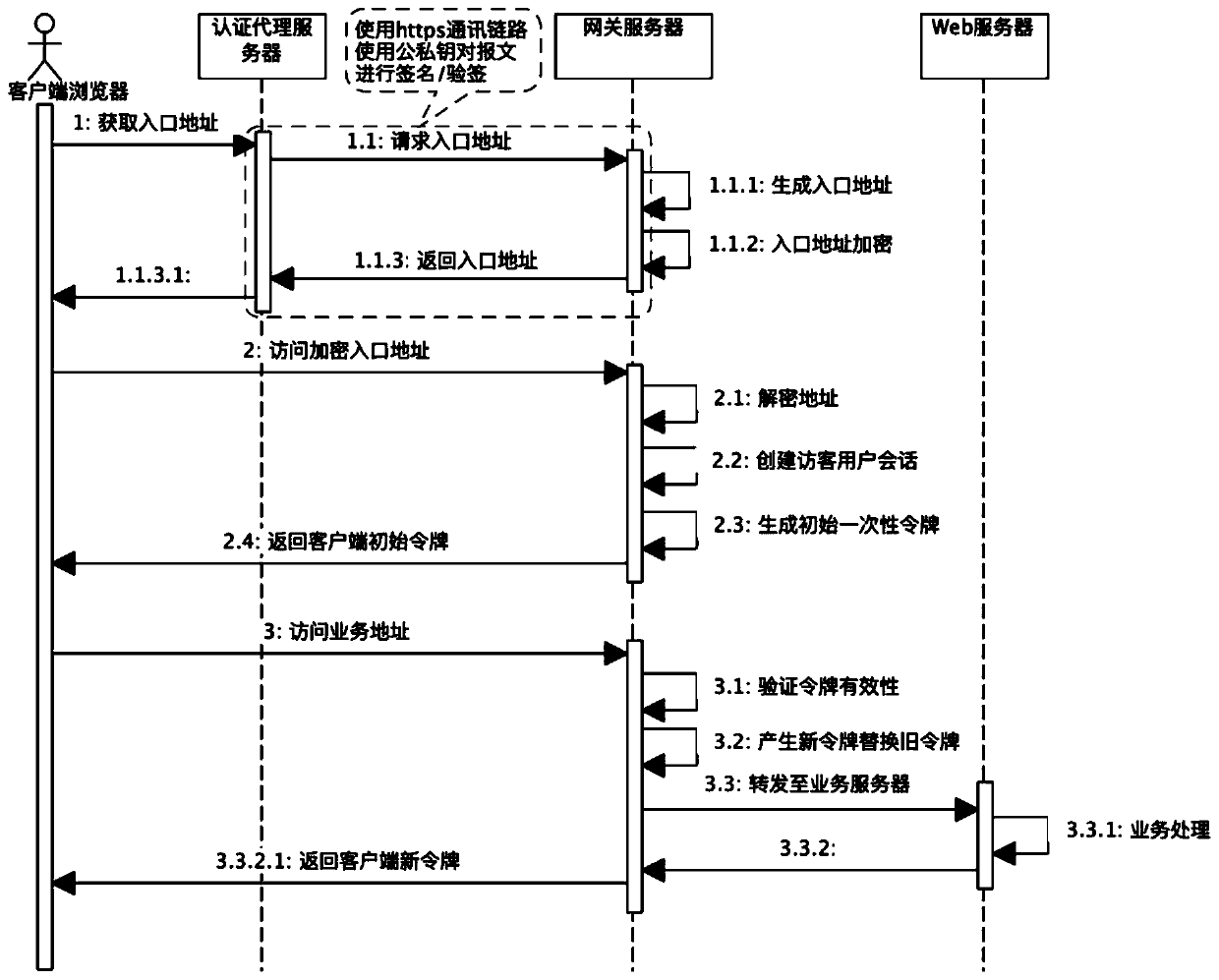
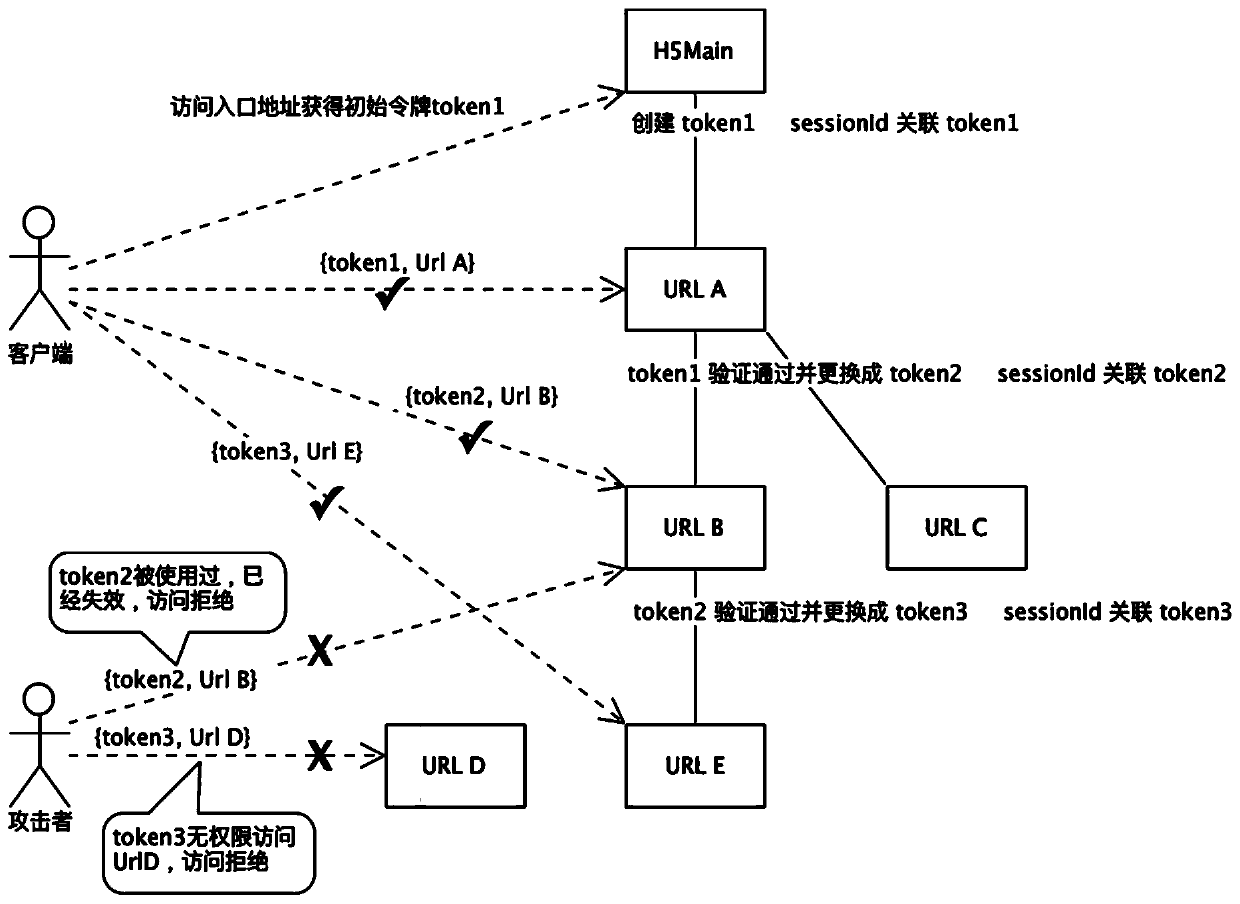
ActiveCN110933078AImprove interception rateProtect information security and operational securityTransmissionEngineeringServer-side
The invention relates to an H5 non-login user session tracking method. the method comprises: a server adopting a two-layer architecture design; the server generating an entry link address for creatinga user session; wherein the address is an entrance of all subsequent H5 services; a request for accessing the address needing to be authenticated by the server; after the user session is successfullycreated, the server issuing a one-time token to the client; wherein the token is used for user identity confirmation in the subsequent request process, sending the token to the server side along withthe user request, the token being immediately invalid after the server side passes the verification, and then the server side creating a new token and issuing the new token to the user for the next request to confirm the identity of the user. Compared with the prior art, effective user login can be realized in a scene that a client browser cannot provide user password input or other identity authentication capabilities, the illegal request interception rate of malicious attackers can be improved, and the development cost and the maintenance cost are reduced.
Owner:BANK OF COMMUNICATIONS
Network intrusion detection method, device and equipment
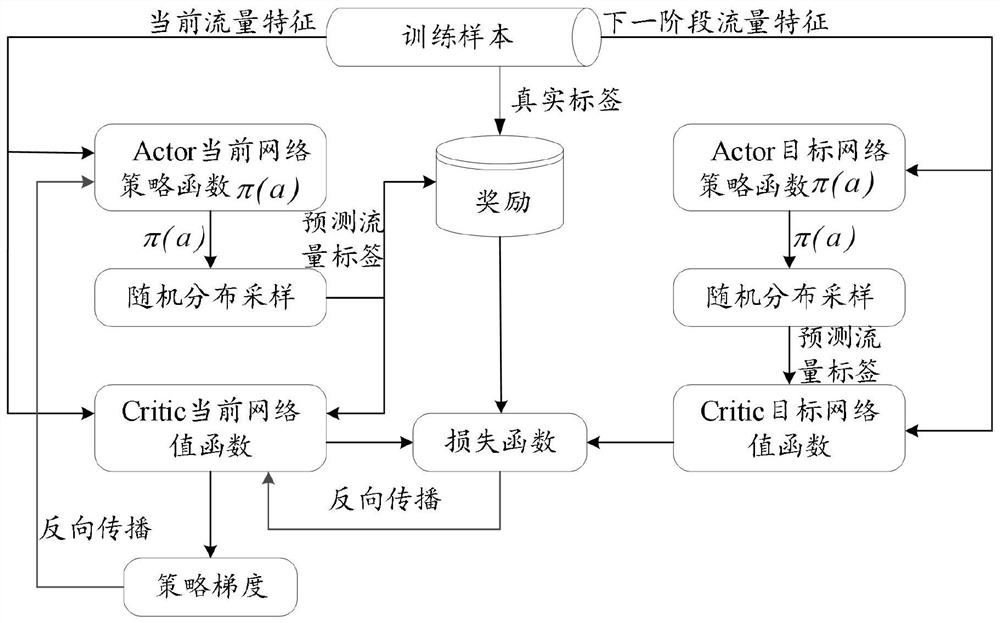
InactiveCN113179263AAddress imbalancesImprove detection accuracyNeural architecturesTransmissionInternet trafficSimulation
The invention discloses a network intrusion detection method based on a multi-agent depth deterministic strategy gradient model, and relates to the technical field of computer network security. The method comprises the steps of obtaining to-be-detected network flow data; inputting to-be-detected network traffic data into the neural network model based on the multi-agent depth deterministic strategy gradient, and detecting abnormal network traffic, wherein the determination of the neural network model based on the multi-agent depth deterministic strategy gradient comprises the following steps: obtaining a network traffic training sample; training an Actor network and a Critic network through a network traffic training sample by adopting a multi-agent depth deterministic strategy gradient; updating the Actor network parameters by adopting a strategy gradient; and updating the Critic network parameters by adopting a loss function. According to the multi-agent depth deterministic strategy gradient, a simple and rapid neural network is adopted, and the method is easier to deploy in a harsh network environment; and the detection accuracy of a small number of traffic samples can be improved in an adversarial learning mode.
Owner:ZHOUKOU NORMAL UNIV
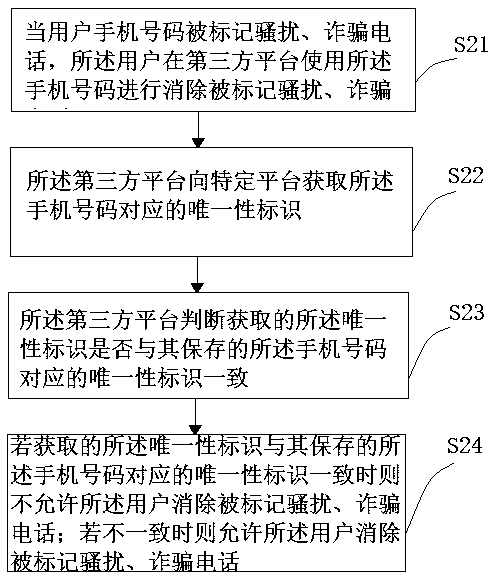
Method and system for protecting account security
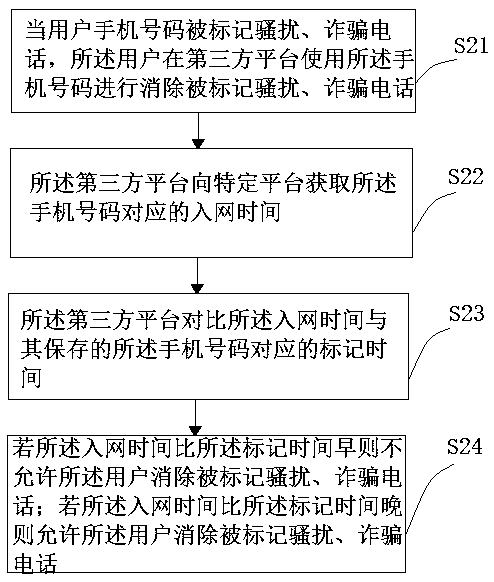
InactiveCN110636505AEnsure safetyScam Call EliminationTransmissionSecurity arrangementUnique identifierComputer security
The invention provides a method for protecting account security, and when the method is used for a third-party platform to send a push notification to a mobile phone number of a user, the method comprises the following steps: the step S11, the third-party platform acquires a unique identifier corresponding to the mobile phone number from a specific platform; S12, the third-party platform judges whether the obtained unique identifier is consistent with a stored unique identifier corresponding to the mobile phone number or not; and S13, if the acquired unique identifier is consistent with the stored unique identifier corresponding to the mobile phone number, the push notification is sent to the mobile phone number, and if the acquired unique identifier is not consistent with the stored unique identifier corresponding to the mobile phone number, the push notification is not sent to the mobile phone number. According to the embodiment of the invention, the third-party platform sends the push notification to the user, and the push notification is sent after inspection, thereby effectively protecting the user information and property safety.
Owner:王恩惠
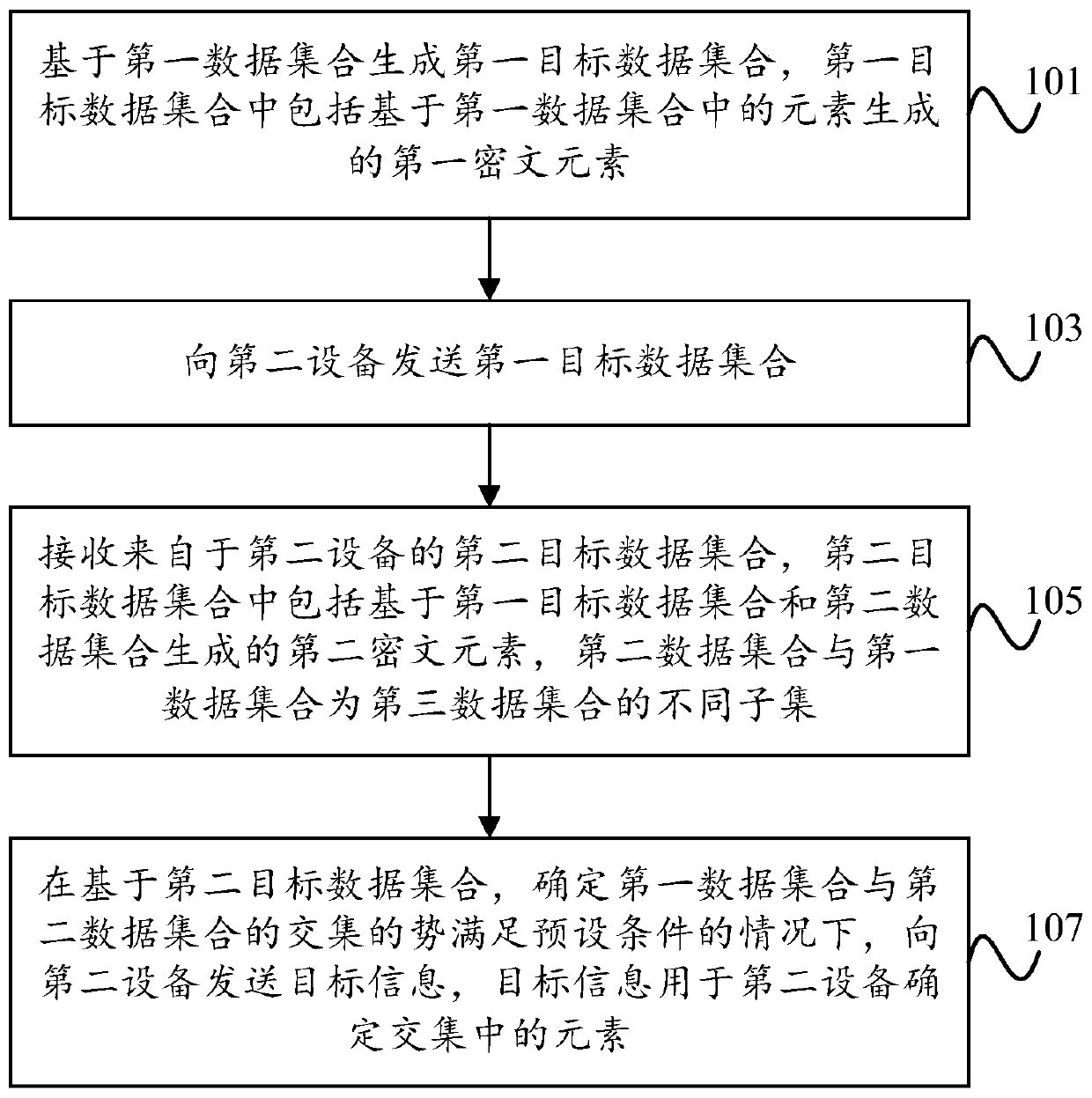
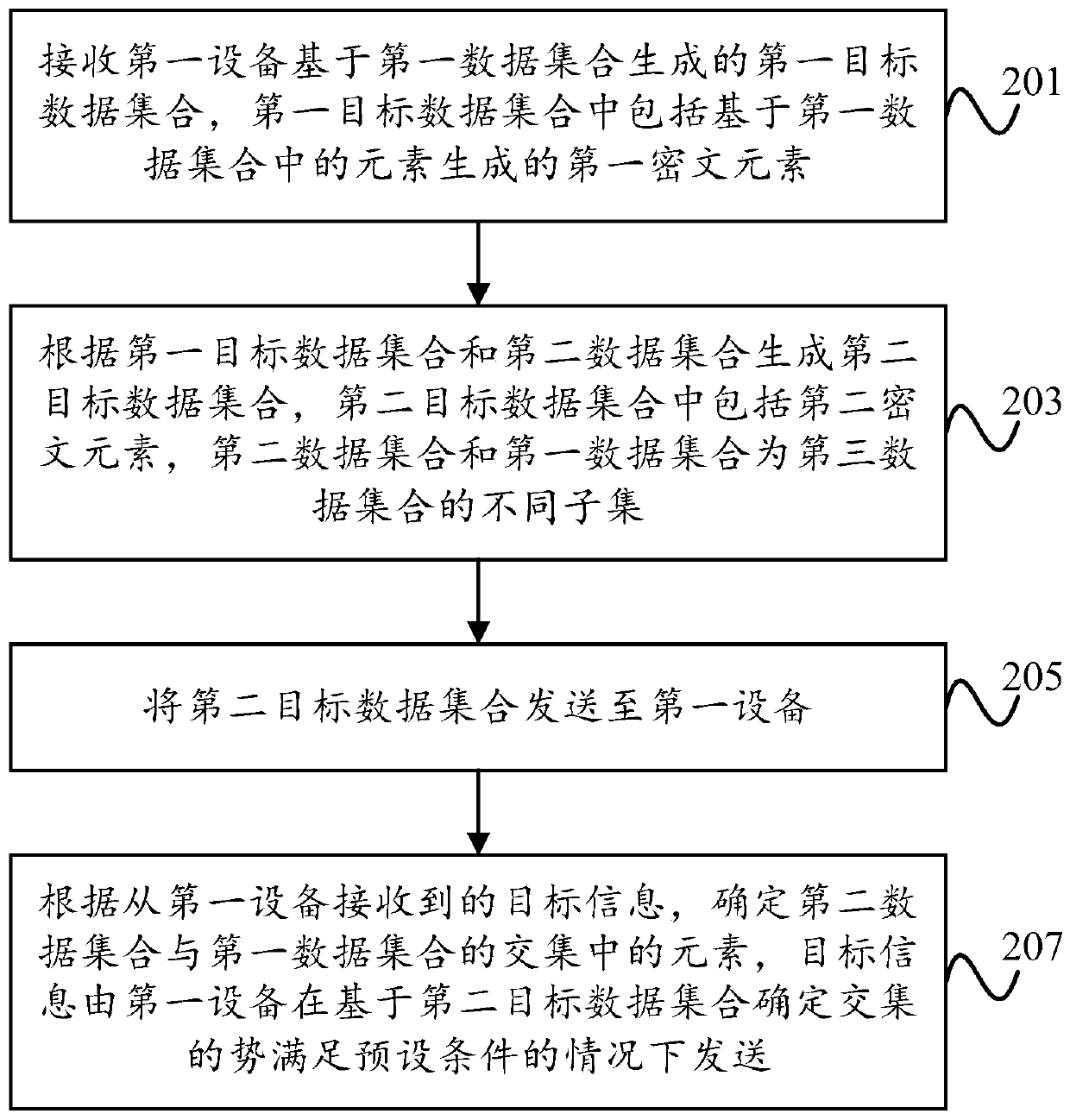
Data processing method and device
The invention discloses a data processing method, and the method comprises the steps: generating a first target data set based on a first data set, and enabling first target data set to comprise a first ciphertext element generated based on an element in the first data set; sending the first target data set to a second device; receiving a second target data set from thesecond device, the second target data set including a second ciphertext element generated based on the first target data set and the second data set, the second data set and the first data set being different subsets of a thirddata set; and under the condition that it is determined that the potential of the intersection of the first data set and the second data set meets a preset condition based on the second target data set, sending target information to the second device, wherein the target information is used for the second device to determine elements in the intersection.
Owner:ADVANCED NEW TECH CO LTD
Service terminal equipment capable of authenticating identities
InactiveCN107609380AIdentity securityProtect property and information securityCharacter and pattern recognitionDigital data authenticationRadio frequencyUser needs
The invention discloses service terminal equipment capable of authenticating identities. The service terminal equipment comprises a main cabinet, wherein the main cabinet is internally provided with acontroller; a touch display screen and a radio frequency card reader are arranged at the front of the main cabinet; an insertion port is formed in the radio frequency card reader; the controller is connected with each of the touch display screen and the radio frequency card reader; and an identification acquisition device which is connected with the controller is arranged at the front of the maincabinet. Before a service is carried out by a self-help terminal, a user needs to acquire own unique identity information through the identity acquisition device to authenticate that the user controls and executes other operations through the controller. According to the service terminal equipment, the problem that self-help service terminal authentication manner in the prior art is simple and has potential safety hazards is solved; and through applying the service terminal equipment capable of authenticating identities, identity authentication is carried out before services are carried out by the self-help terminal, so that the loss, of personal property and information, caused by single authentication manner is avoided.
Owner:四川聚典新业科技有限公司
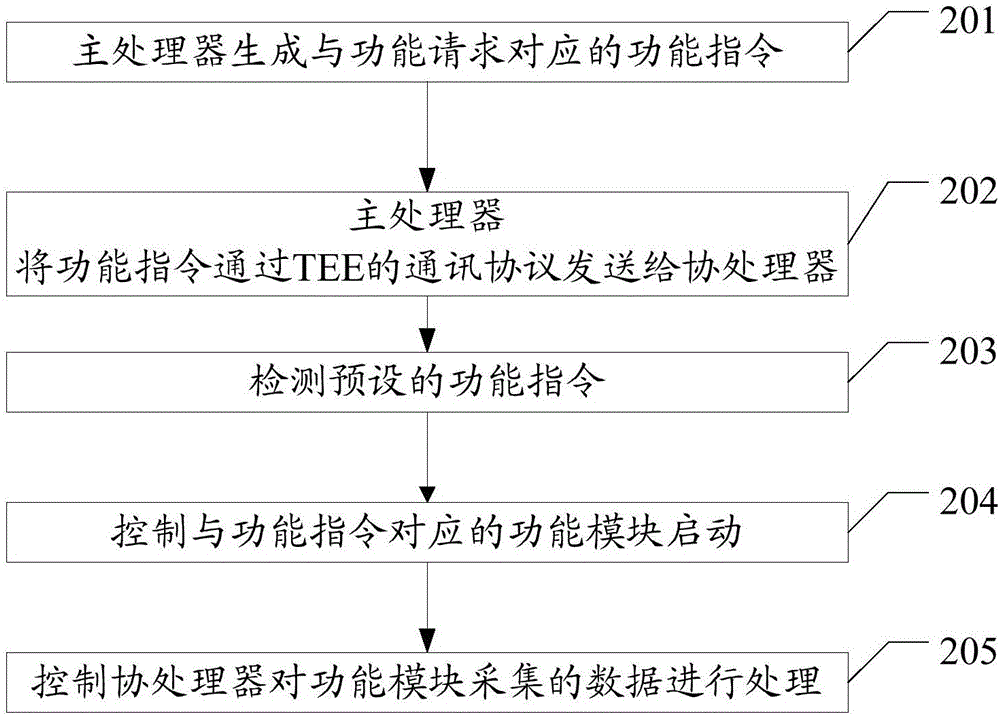
Data processing method and terminal
ActiveCN106815510AProtect information securityProtection securityInternal/peripheral component protectionDigital data authenticationOperational systemCoprocessor
The embodiment of the invention discloses a data processing method and a terminal. The data processing method and the terminal are used for protecting information and property safety of a user. The data processing method in the embodiment includes the steps that a terminal detects a preset function command in a credible execution environment TEE, wherein the TEE runs on a coprocessor of the terminal; when the preset function command is detected, and a function module corresponding to the function command is controlled to be started; the coprocessor is controlled to process data collected by the function module to complete the corresponding function. In the embodiment, as the TEE runs on the coprocessor, an operation system (OS) runs on a main processor, the TEE running environment and the OS running environment are subjected to hardware insulation, hackers are difficult to make an attack to the TEE and difficult to seek the security vulnerability in the OS, and the information and the property safety of the user are protected.
Owner:MEIZU TECH CO LTD
Terminal alarming method, terminal and computer readable storage medium
InactiveCN108052812AProtect information securityProtection securityInternal/peripheral component protectionDigital data authenticationComputer terminalInformation security
Embodiments of the invention disclose a terminal alarming method, a terminal and a computer readable storage medium. The method comprises the steps of detecting whether a state of the terminal meets afirst preset condition or not, wherein the state of the terminal includes an environment position state of the terminal and a running state of the terminal; it is detected that the state of the terminal meets the first preset condition, starting an anti-theft mode of the terminal; detecting whether contact information of a user and the terminal meets a second preset condition or not, wherein thecontact information comprises a fingerprint contact area of the user and a terminal screen, and fingerprint information of contact of the user and the terminal; and if the contact information meets the second preset condition, starting an alarming prompt. According to the terminal alarming method, the terminal and the computer readable storage medium disclosed by the embodiments of the invention,an alarm can be given to remind the user when it is detected that the terminal is in a stolen scene, so that the information and property security of the user is protected and the user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Information safety protecting method, information safety protecting device and server device
InactiveCN101593250AProtect information securityNo harmPlatform integrity maintainanceMalwareSoftware
The invention discloses an information safety protecting method, an information safety protecting device and a server device. The information safety protecting method comprises the steps: judging whether project software is in a preserved list or not; if so, distributing a first authority to the project software; and otherwise, distributing a second authority which is lower than the first authority to the project software. The invention can effectively prevent damaging a system by new malicious software.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
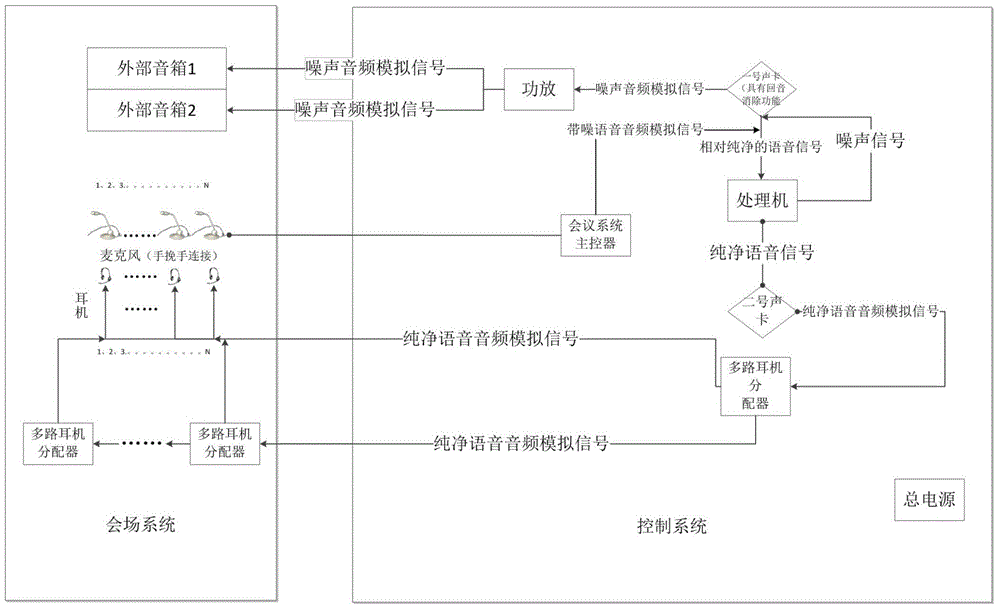
Audio conference safe secrecy system and method using echo cancellation function
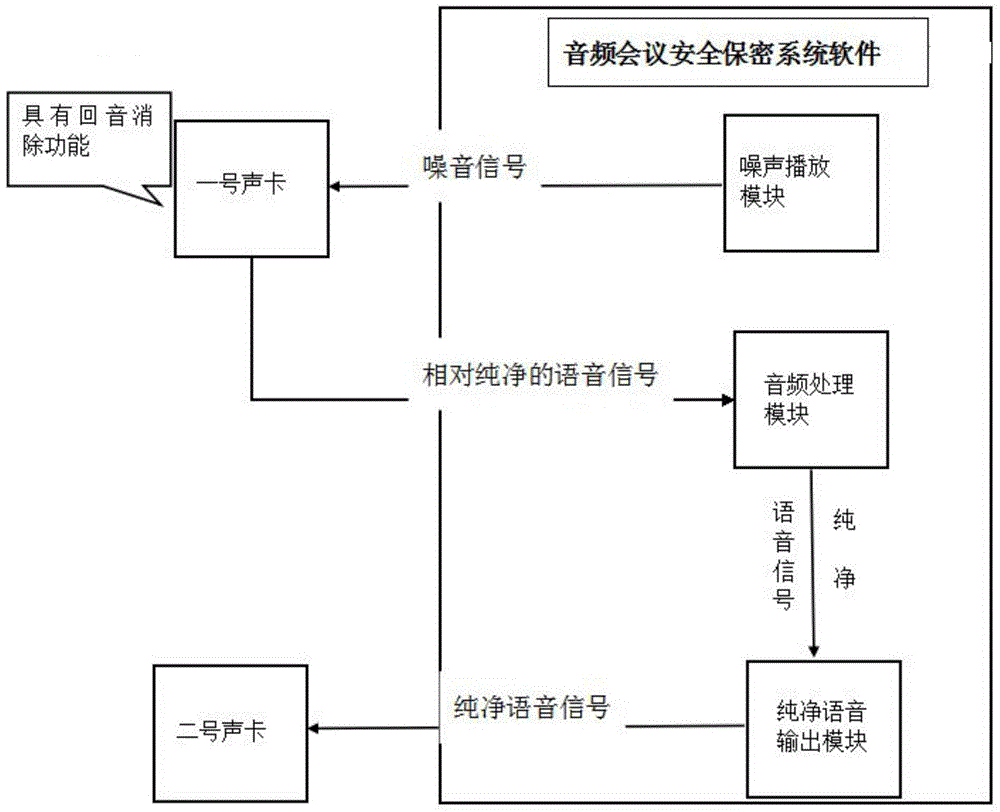
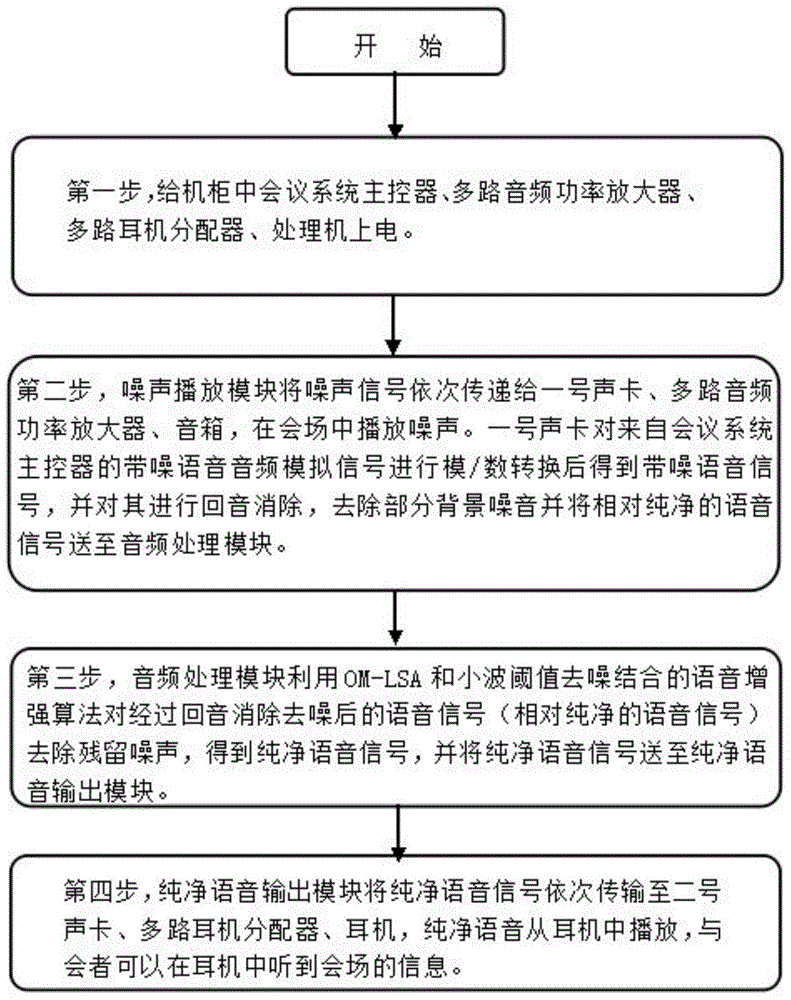
ActiveCN104538039AProtect information securityImplement the decryption processTwo-way loud-speaking telephone systemsSpeech analysisLoudspeakerMeeting place
The invention discloses an audio conference safe secrecy system and method using an echo cancellation function. The system is composed of a control system and a meeting place system. The control system is composed of a processor, a multi-path headset distributor, a conference system master controller and a multi-path audio power amplifier. The meeting place system is composed of a loudspeaker box, a headset and a microphone. The processor is provided with two sound cards and audio conference safe secrecy software, wherein the first sound card has the echo cancellation function. The software is composed of a noise playing module, an audio processing module and a pure voice output module. The method includes the steps that the audio conference safe secrecy software plays noise and collects and transmits voice with noises to the first sound card for echo cancellation and noise reduction, and the audio processing module removes residual noise of voice signals subjected to echo cancellation and noise reduction. The audio conference safe secrecy system and method resolve the problems that the anti-eavesdrop measure of anti-eavesdrop equipment is simplex, and the spreading range of sound waves is not controllable, and can effectively guarantee that the conference content is not eavesdropped and communication is not affected.
Owner:NAT UNIV OF DEFENSE TECH
Short message display method, short message display system, intelligent short message platform and short message assistant client side
InactiveCN105323735AProtect privacy and securityProtect information securityMessaging/mailboxes/announcementsSecurity arrangementPlaintextComputer hardware
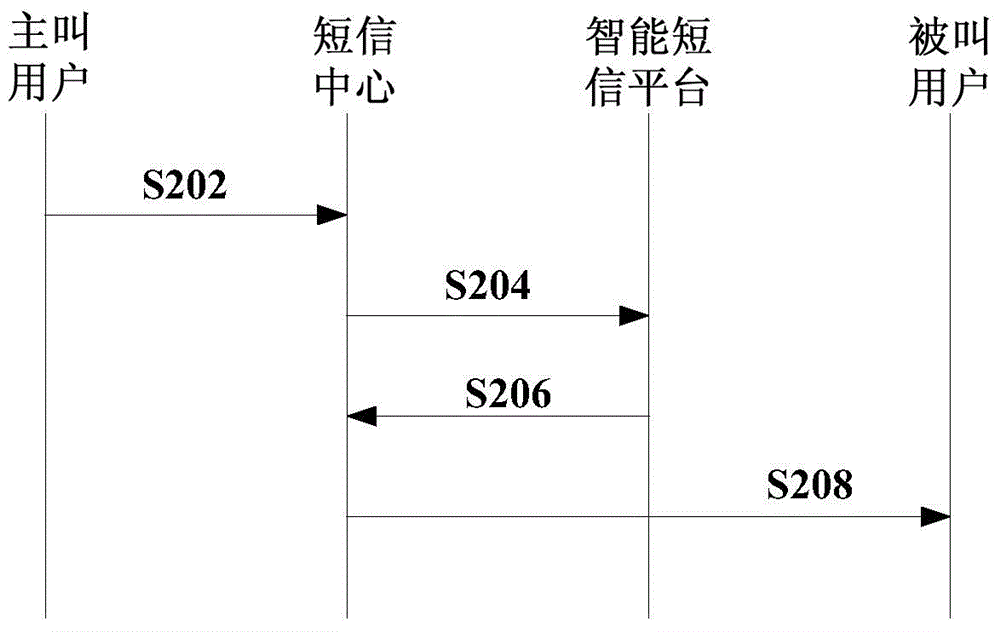
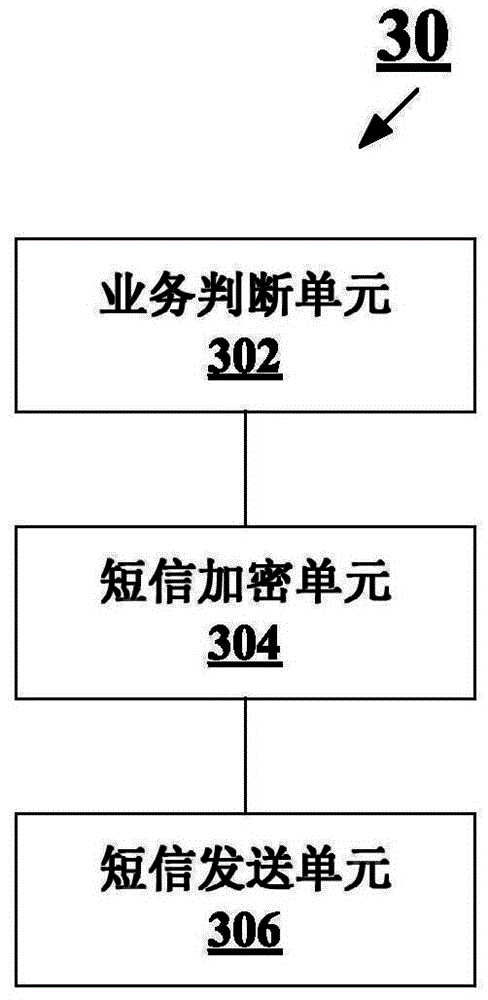
The invention relates to a short message display method, a short message display system, an intelligent short message platform and a short message assistant client side. The method comprises the following steps: responding to receiving of a short message, and judging whether a called number in the short message orders a secure short message service or not; encrypting the received short message if the called number orders the secure short message service, wherein a secret key for encryption is related to the called number; and sending the encrypted short message to a called user through a short message centre, such that the called user can view the plaintext of the short message after logging in the short message assistant client side. According to the invention, the privacy and the information safety of the called user are ensured.
Owner:CHINA TELECOM CORP LTD
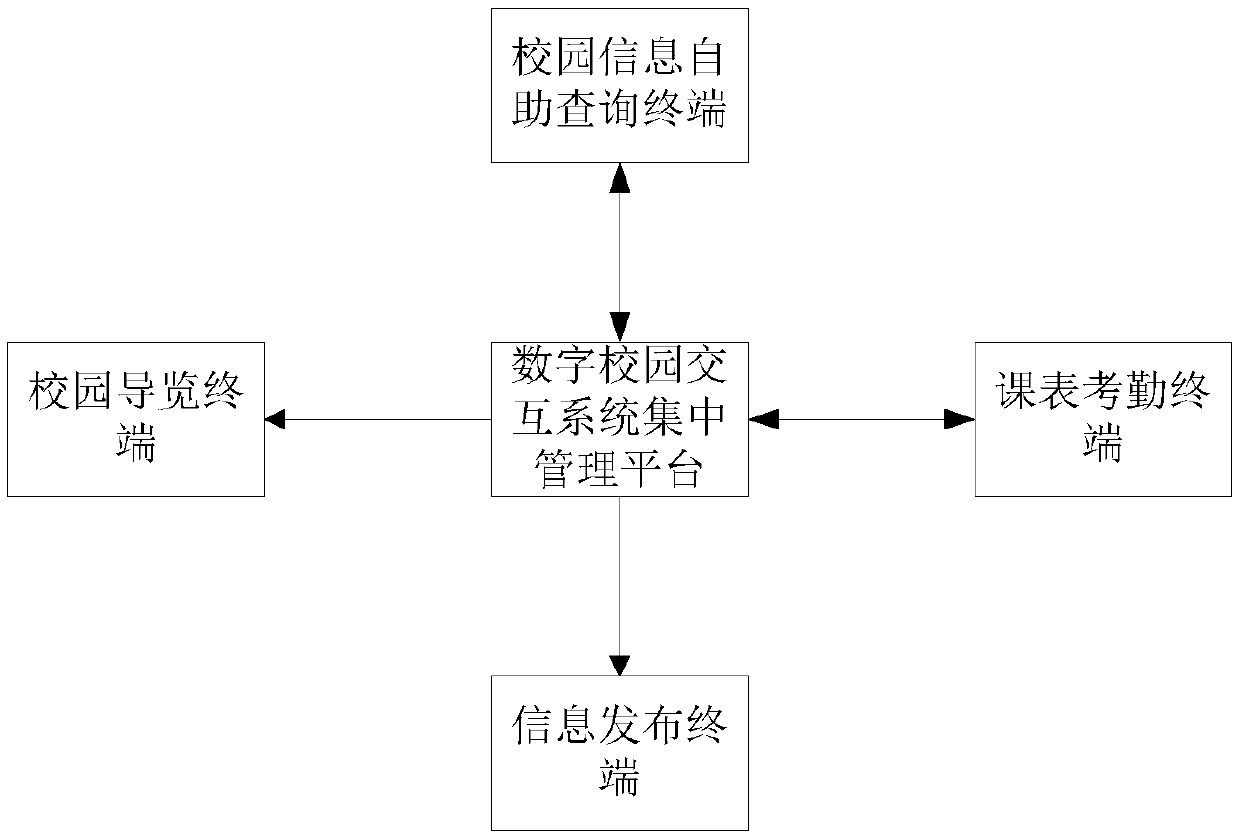
Campus digital management display device
InactiveCN107657561AOptimizationRaise the level of quality educationRegistering/indicating time of eventsData processing applicationsInteraction systemsInformation sharing
The invention discloses a campus digital management display device which includes a digital campus interaction system centralized management platform, and a campus tour terminal, a campus informationself-service query terminal, a class schedule attendance check terminal and an information release terminal which are connected with the digital campus interaction system centralized management platform. The problems of unreasonable allocation of teaching resources and backward management in the prior art are solved. A campus digital management display device is provided, which integrates information release, information sharing, teaching resource management and teaching resource optimization. The device can help schools to optimize the allocation of teaching resources and quickly enhance thelevel of quality-oriented education.
Owner:四川聚典新业科技有限公司
Data processing method, device and system
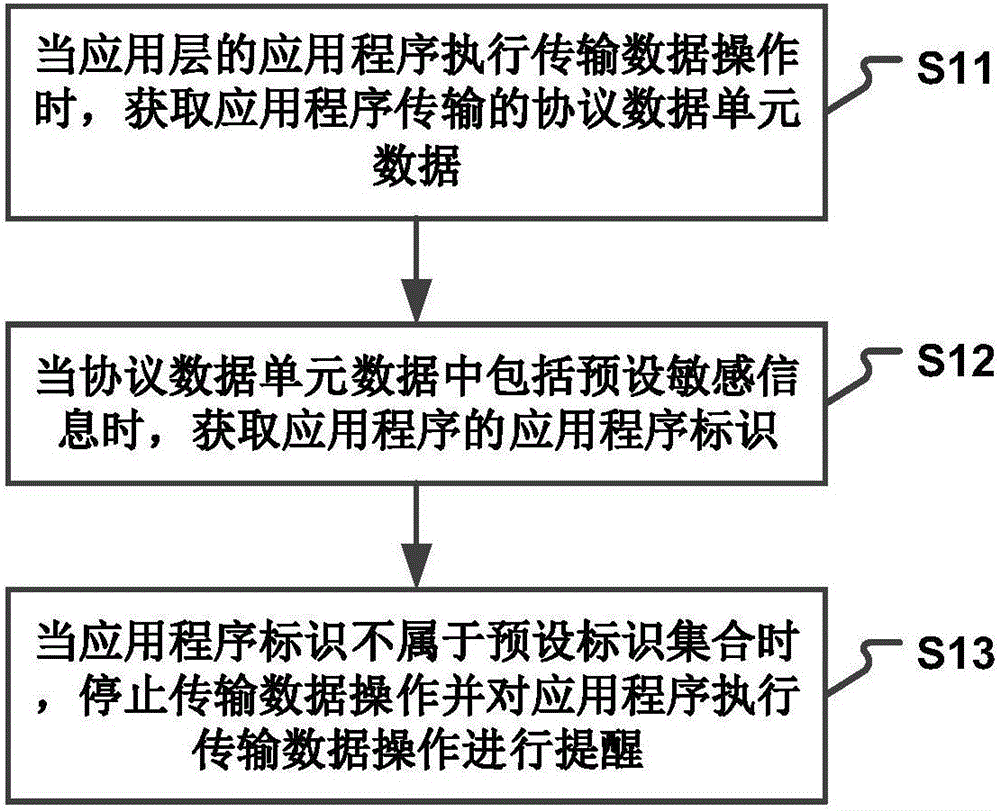
InactiveCN106101105APrevent theftImprove user experienceTransmissionData operationsApplication software
The invention relates to a data processing method, device and system. The method comprises the following steps: when an application of an application layer executes a data transmission operation, acquiring protocol data unit data transmitted by the application; when the protocol data unit data include preset sensitive information, acquiring an application identifier of the application; and when the application identifier does not belong to a preset identifier set, stopping the data transmission operation and instructing the application to execute the data transmission operation. Through the technical scheme, sensitive information in a terminal can be prevented from being stolen by Trojan programs or phishing websites; a user can easily and accurately get the Trojan programs hidden in the terminal; and the information security and property security of the terminal user are protected. Moreover, on the basis of not influencing the work of trusted applications, the information intercepting accuracy and the suspicious Trojan program identification accuracy are increased; the sensitive information of the user is protected from being leaked; and the user experience of the terminal is improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Method and system for protecting account security
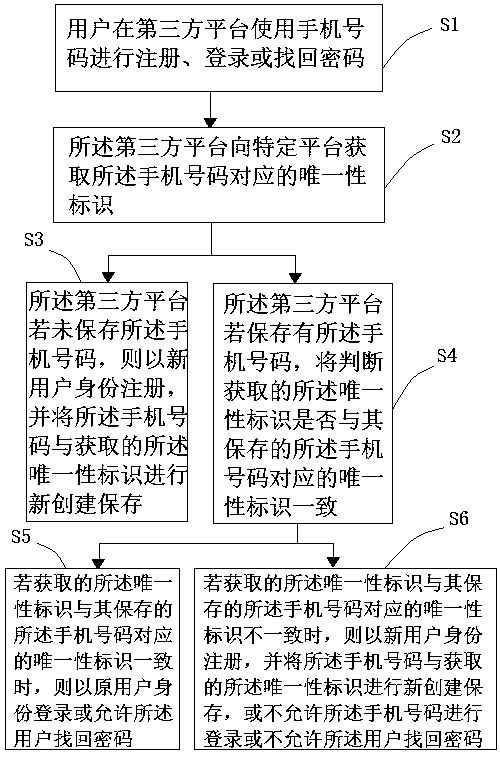
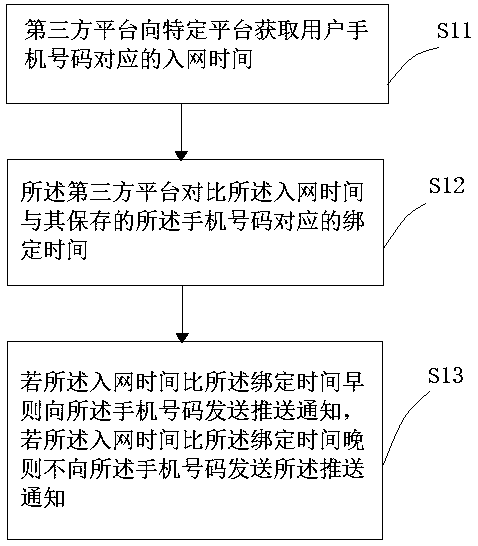
InactiveCN110880973AAvoid lostEnsure safetyKey distribution for secure communicationMessaging/mailboxes/announcementsMobile Telephone NumberThird party
The invention provides a method for protecting account security. The method comprises the following steps: S1, a user registers, logs in or retrieves a password by using a mobile phone number on a third-party platform; S2, the third-party platform registers with a new user identity if the mobile phone number is not stored, and acquires network access time corresponding to the mobile phone number from a specific platform if the mobile phone number is stored; S3, the third-party platform compares the network access time with binding time corresponding to the stored mobile phone number, and the step S4 or the step S5 is executed; S4, if the network access time is earlier than the binding time, the identity of the original user is logged in or the user is allowed to retrieve the password; andS5, if the network access time is later than the binding time, a new user identity is registered and the mobile phone number and the new binding time are created and stored, or not the mobile phone number is not allowed to log in or retrieve the password. Through the method, the security problem of the user account is greatly and effectively protected.
Owner:王恩惠
Penetration attack preventing liquid crystal touch screen
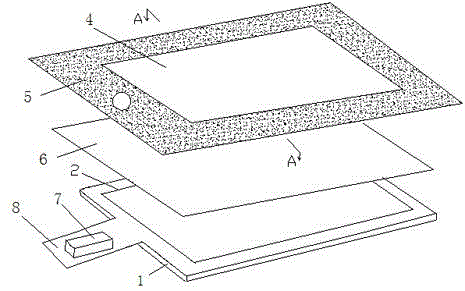
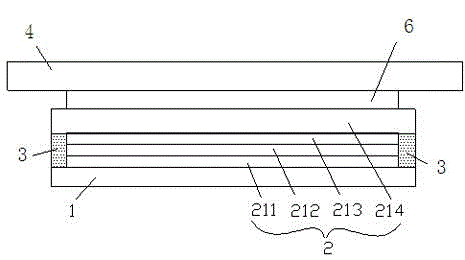
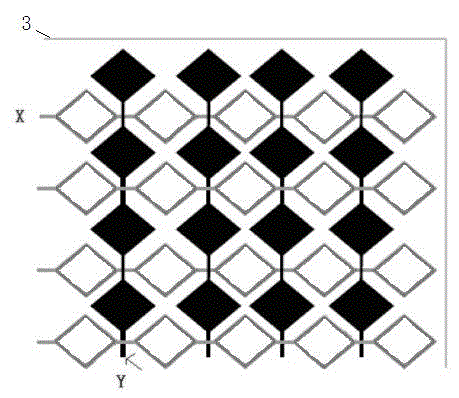
ActiveCN102750037AProtect information securitySimple structureNon-linear opticsInput/output processes for data processingLiquid crystalElectric signal
The invention relates to a penetration attack preventing liquid crystal touch screen, comprising a liquid crystal touch screen. The penetration attack preventing liquid crystal touch screen is characterized in that N coil circuits are arranged on the liquid crystal touch screen; when the coil circuit is opened, the change of an electric signal of the coil circuit triggers an alarm mechanism; and N is a natural number. According to the invention, the penetration attack preventing liquid crystal touch screen has a protective device capable of preventing penetration attack; therefore, parts for preventing the penetration attack are reduced so that the cost is reduced; and system reliability is improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com