Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
95 results about "Trust region" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In mathematical optimization, a trust region is the subset of the region of the objective function that is approximated using a model function (often a quadratic). If an adequate model of the objective function is found within the trust region, then the region is expanded; conversely, if the approximation is poor, then the region is contracted. Trust-region methods are also known as restricted-step methods.
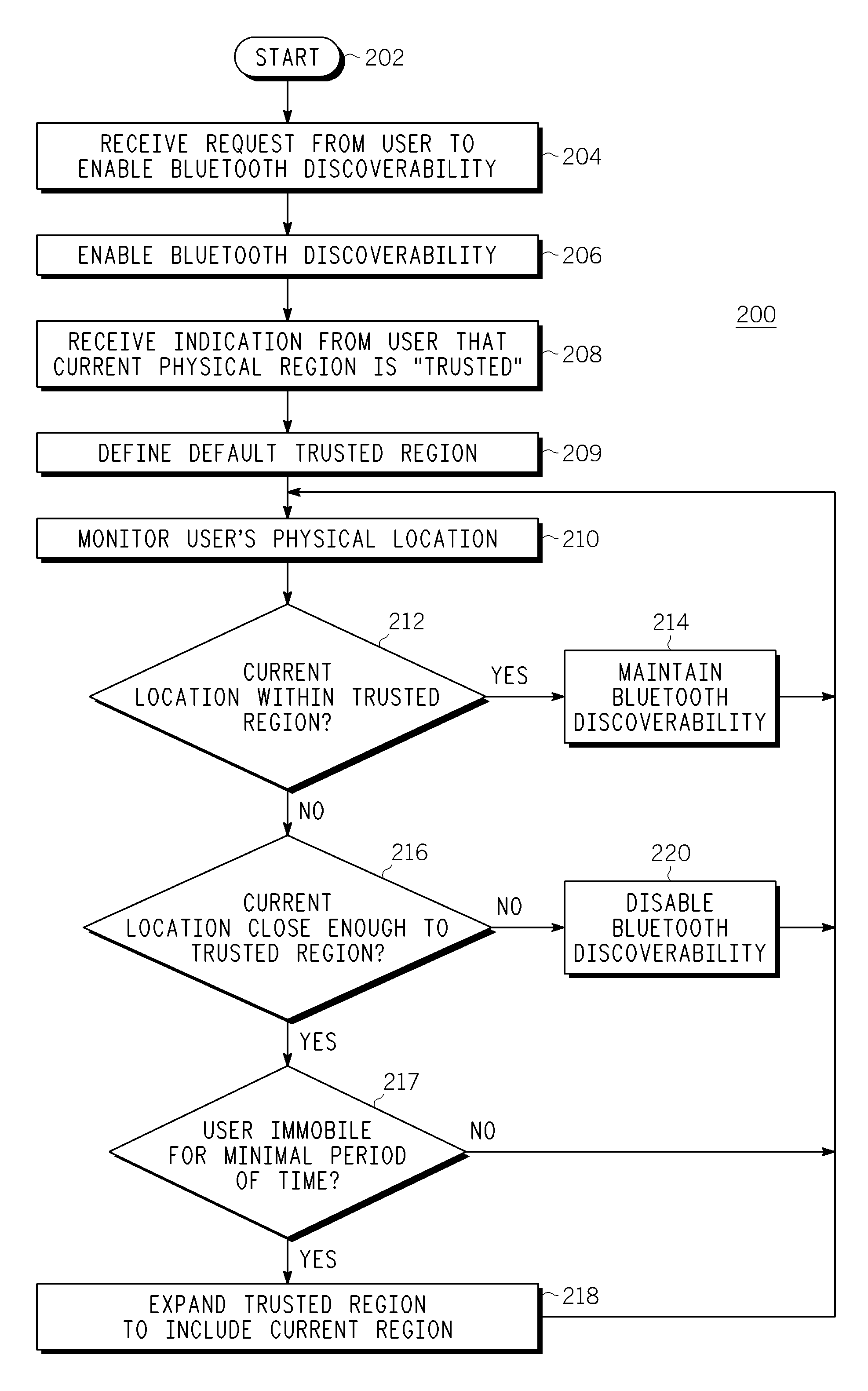
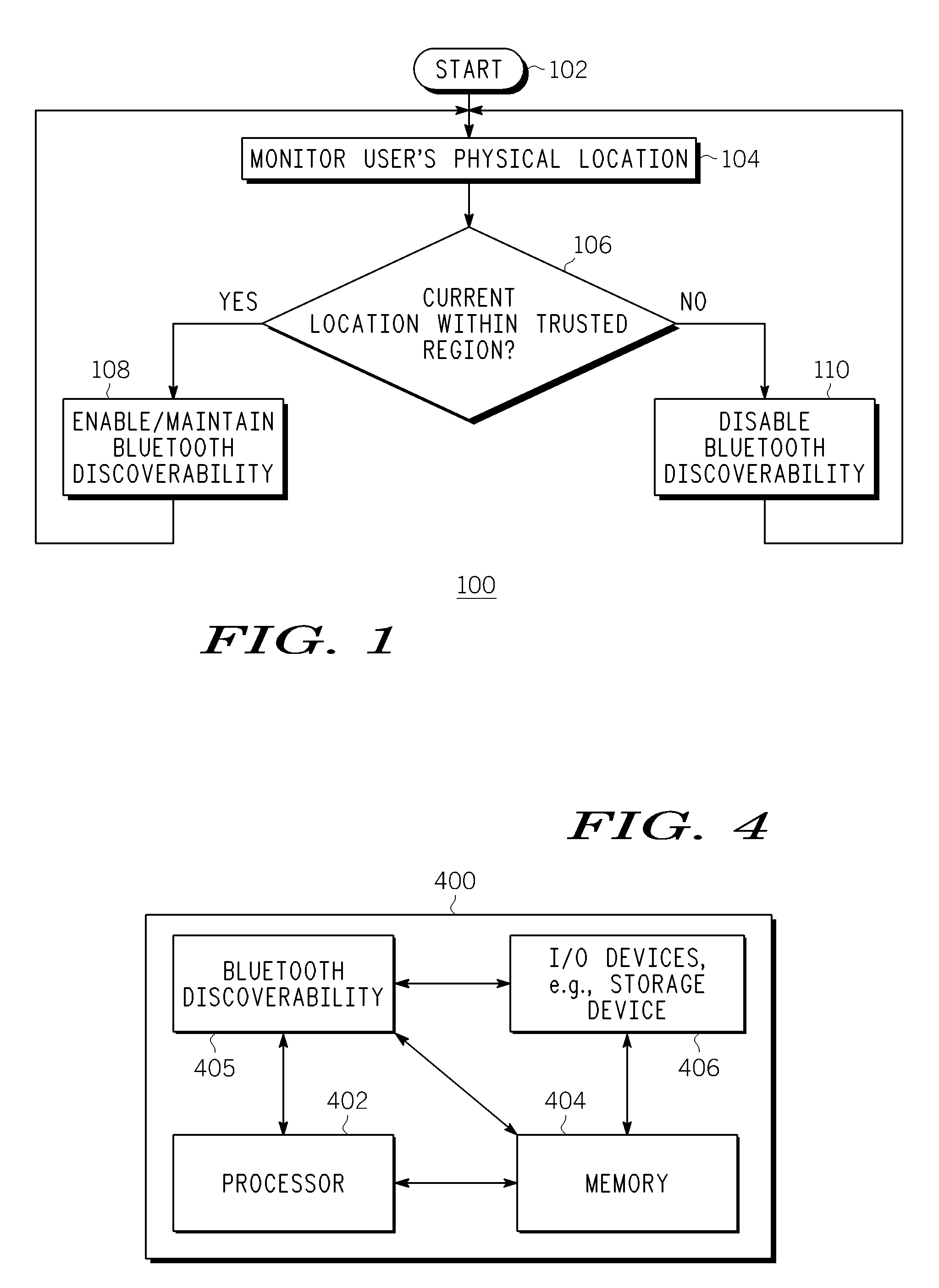
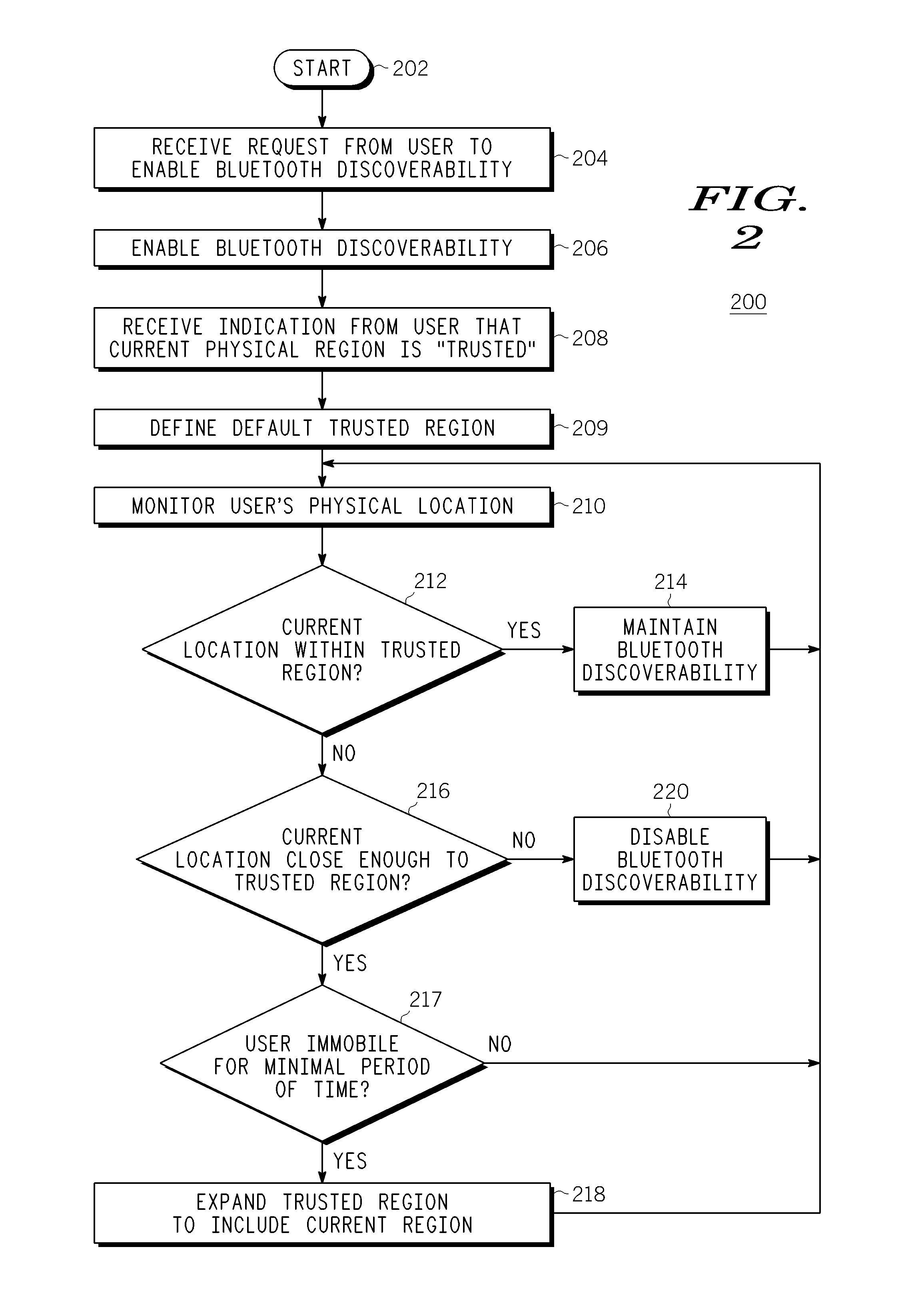
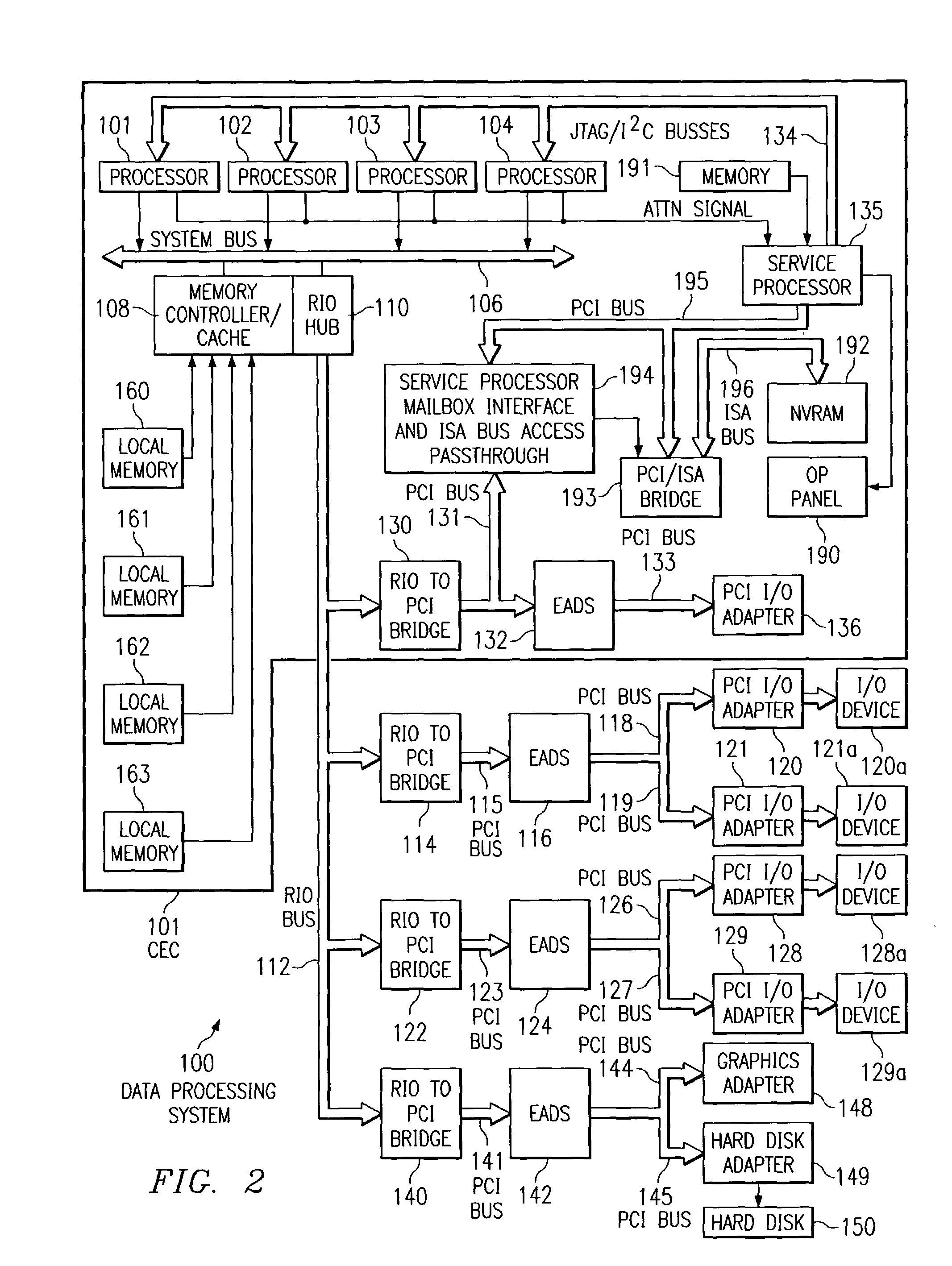
Method and Apparatus for Bluetooth Discoverability Using Region Estimation
InactiveUS20080214202A1Radio/inductive link selection arrangementsLocation information based serviceDiscoverabilityTrust region
Embodiments of the invention generally provide a method and apparatus for Bluetooth discoverability using region estimation. One embodiment of a method for controlling Bluetooth discoverability of a wireless device includes monitoring the physical location of the wireless device and enabling Bluetooth discoverability if the current physical location of the wireless device is within a trusted region or disabling Bluetooth discoverability if the current physical location of the wireless device is outside of the trusted region.
Owner:GENERAL INSTR CORP
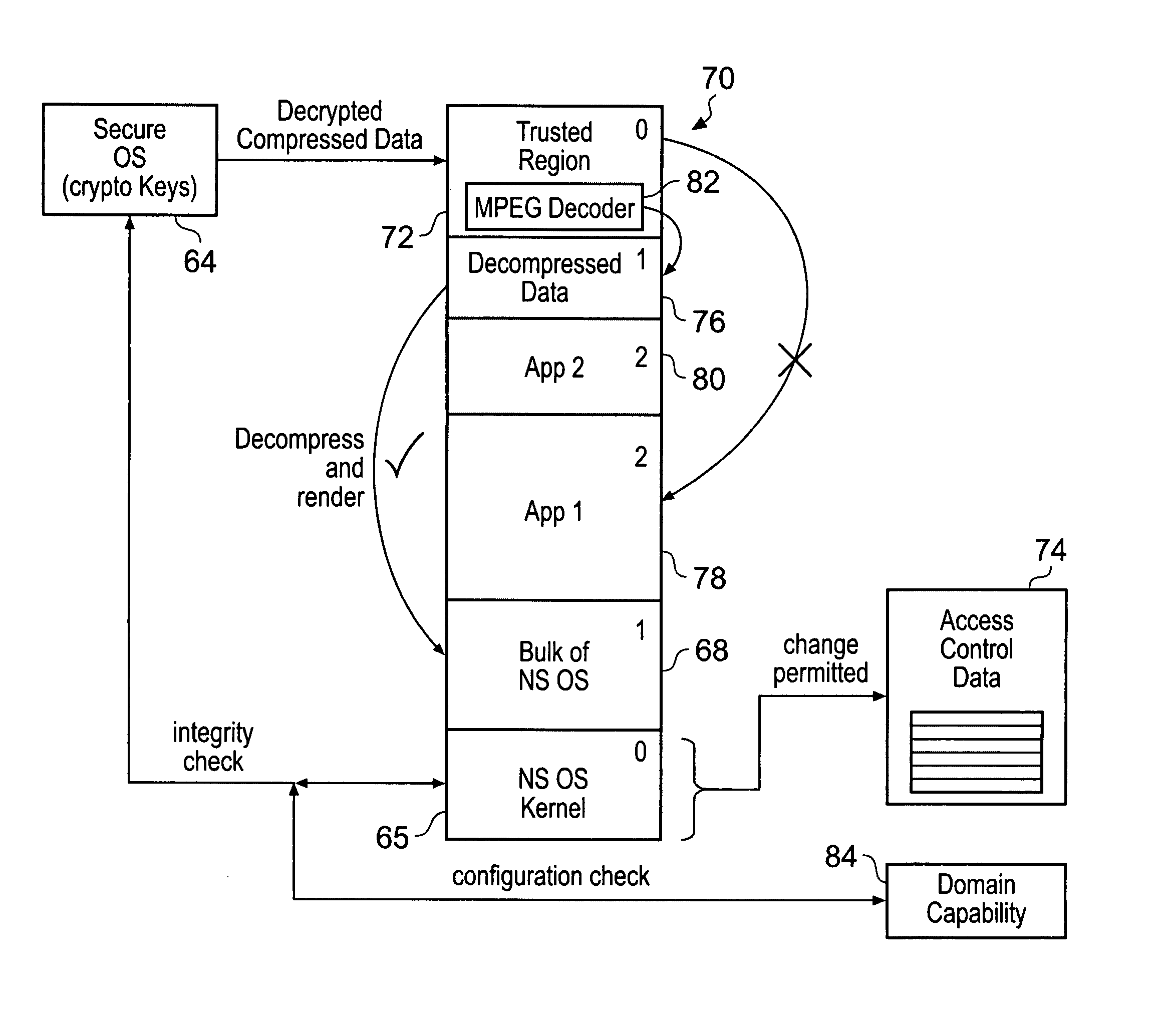
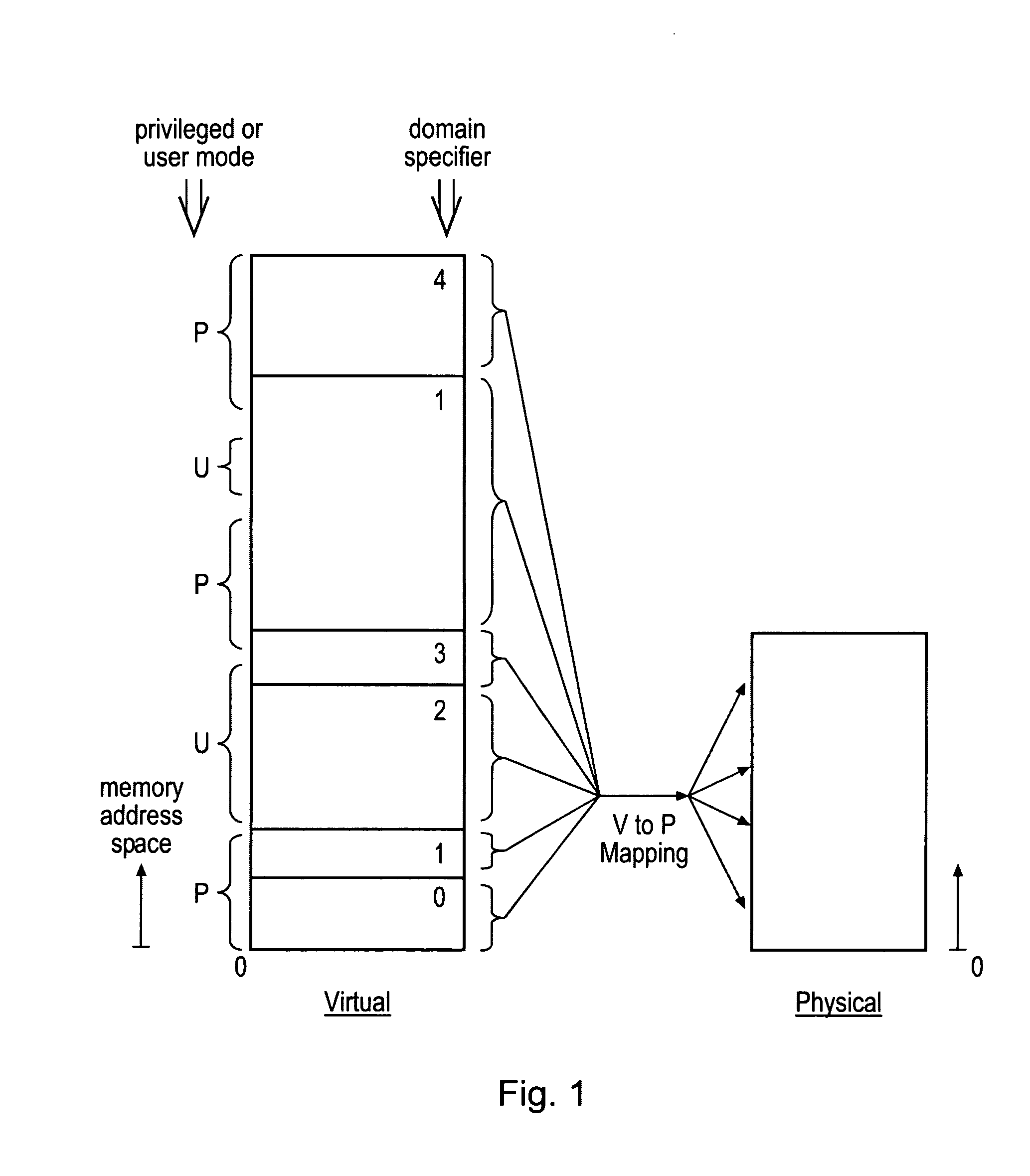
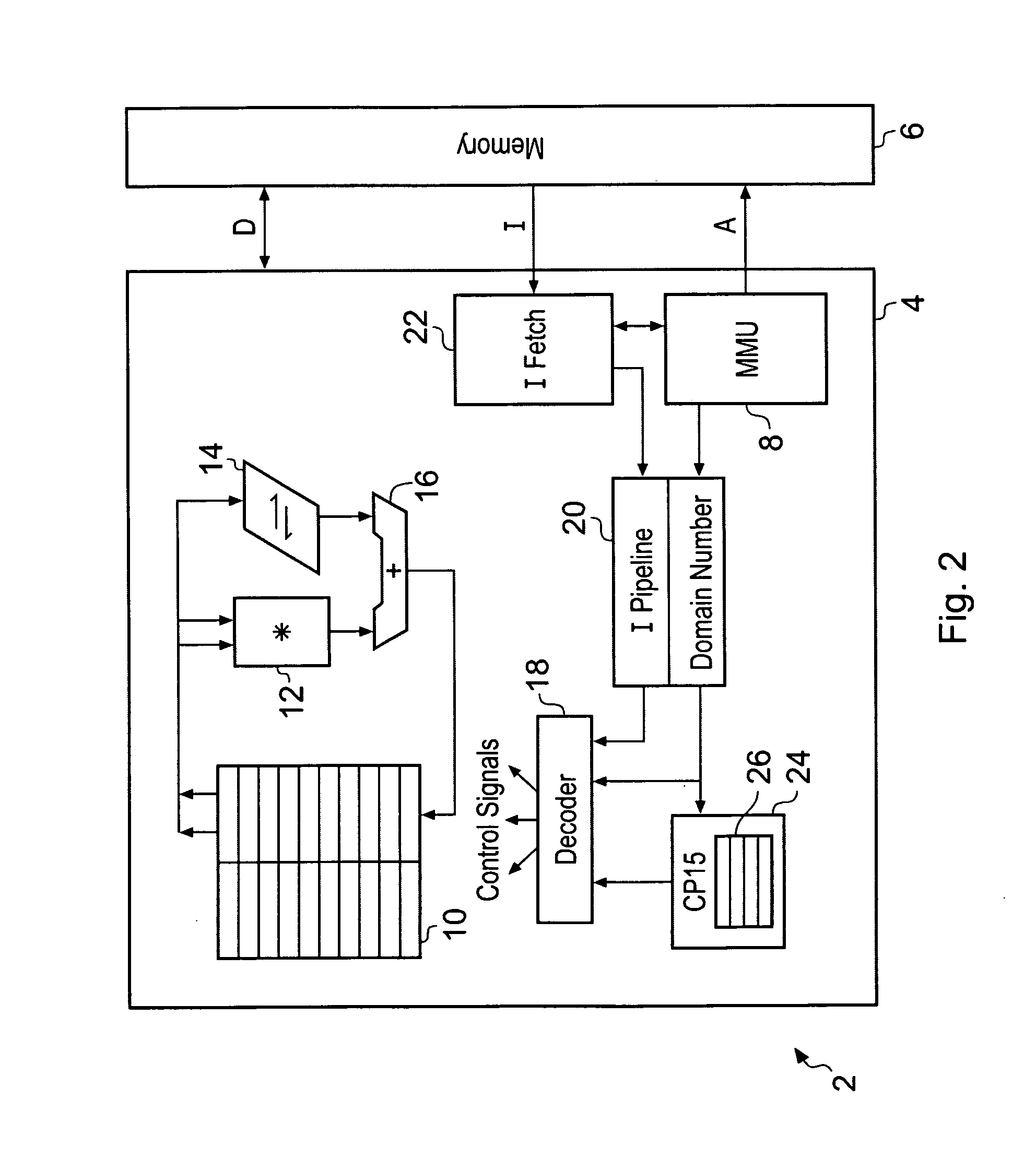
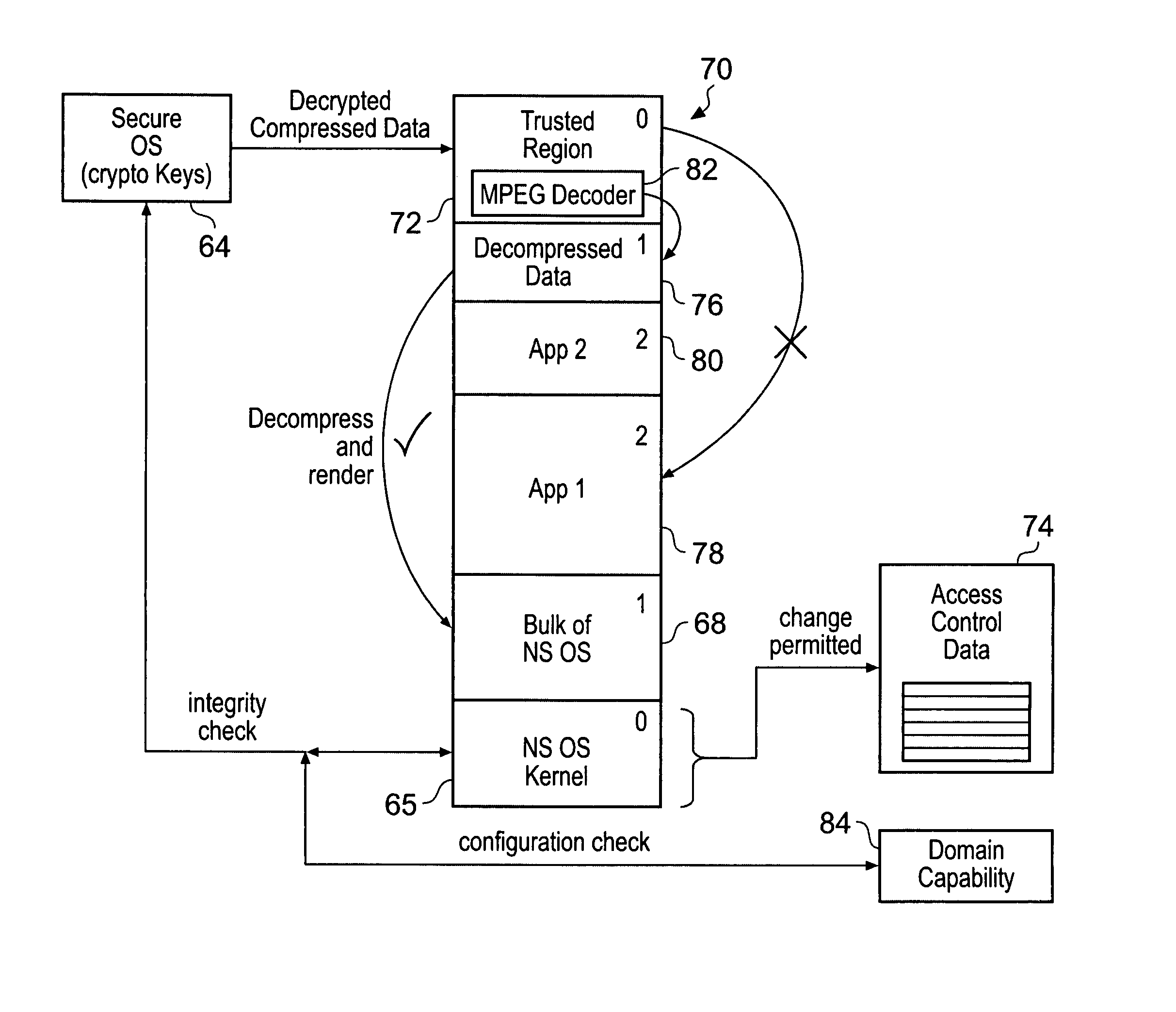
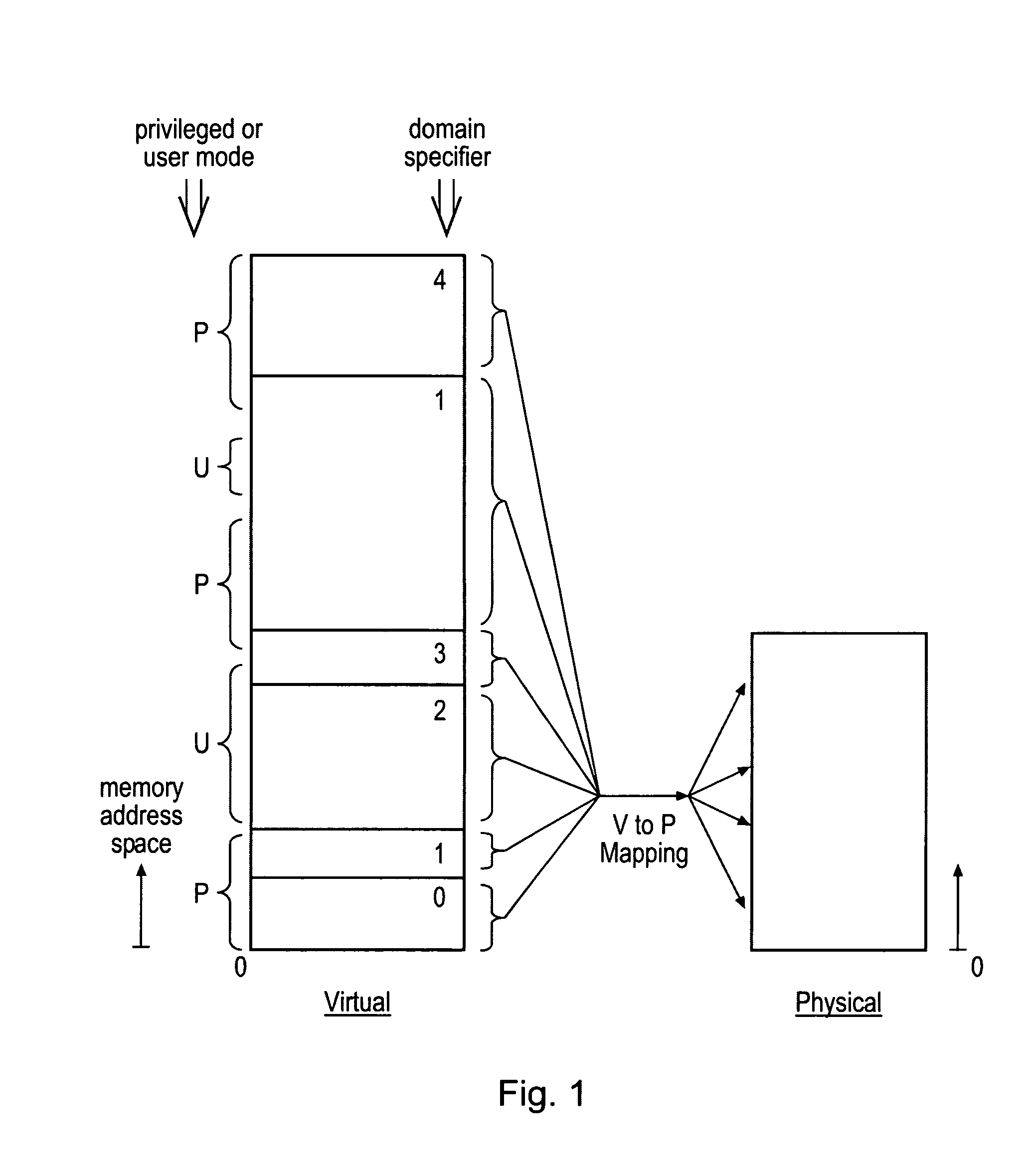
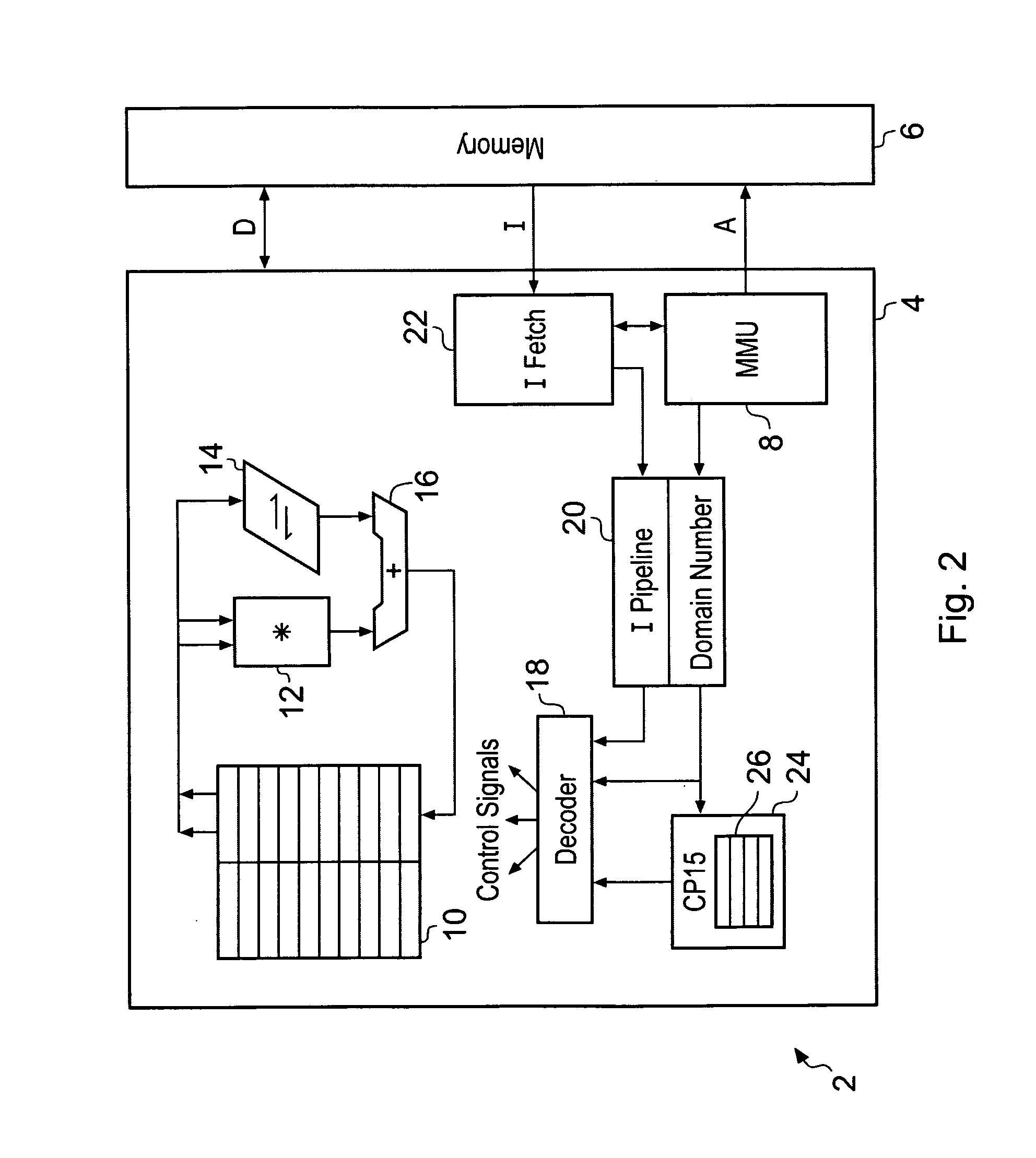
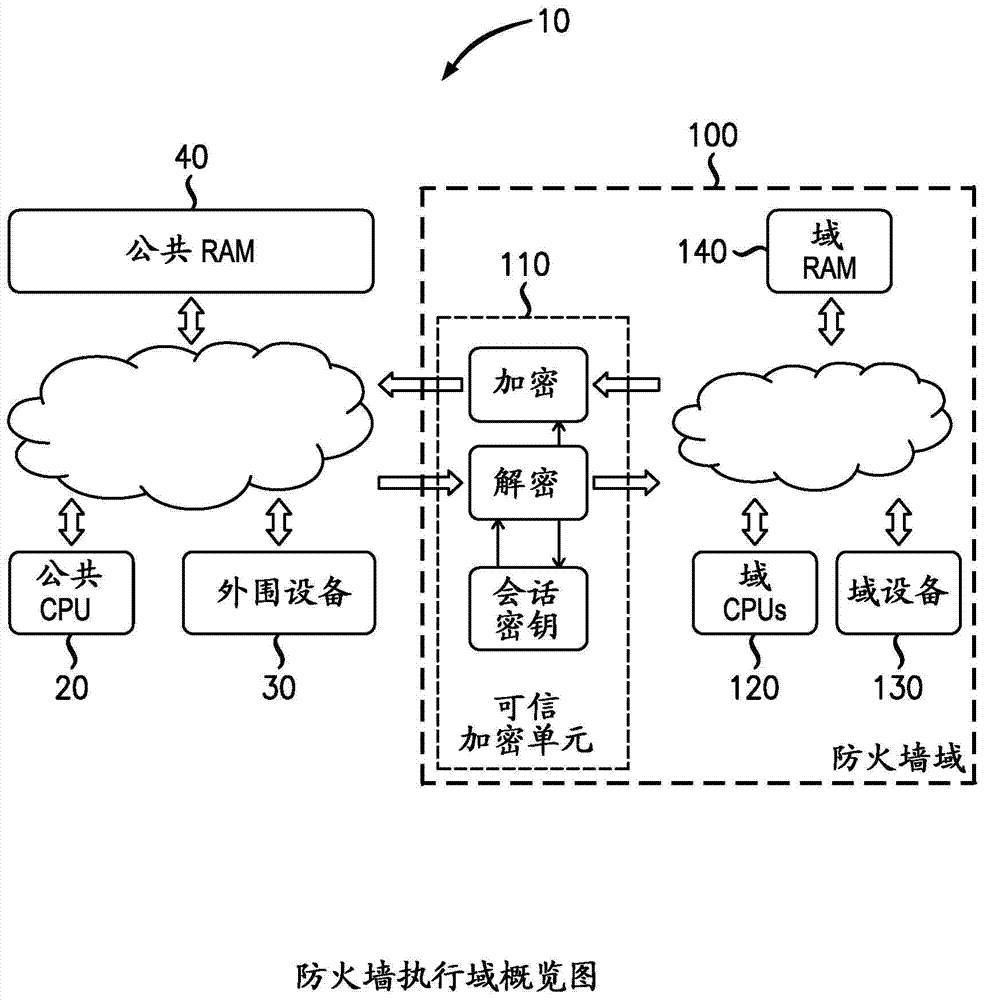
Memory domain based security control with data processing systems
ActiveUS20080250217A1Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
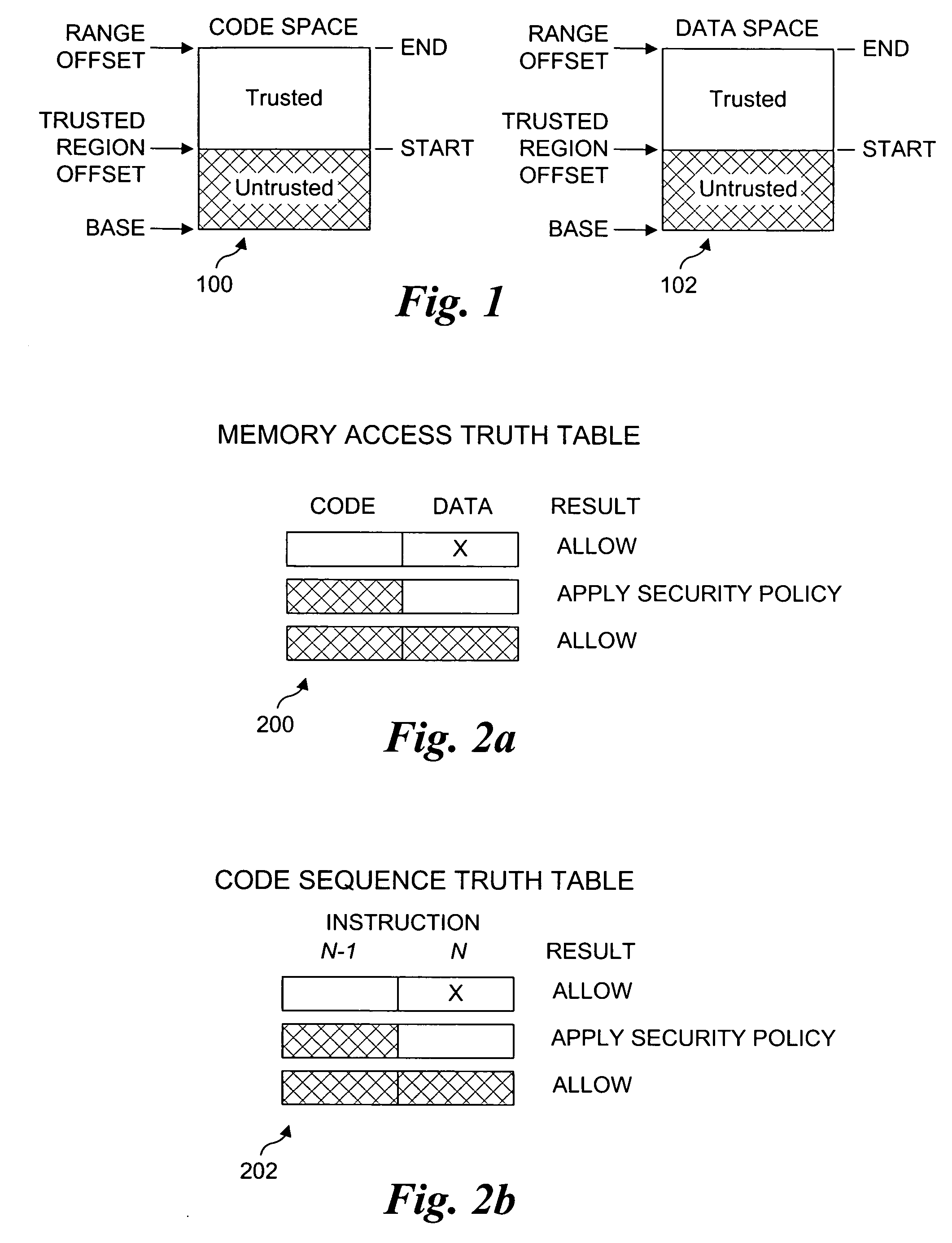
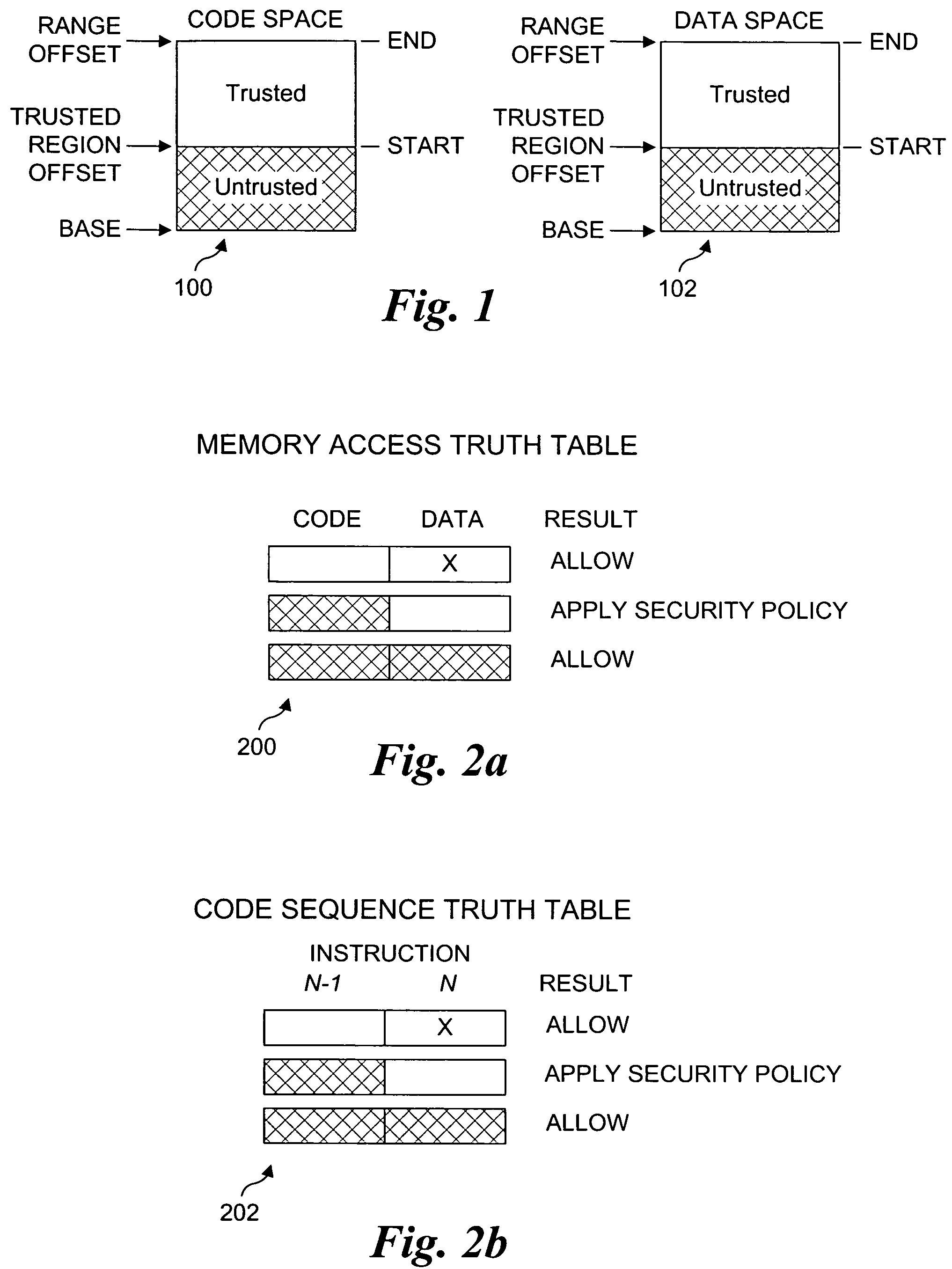
Processor extensions and software verification to support type-safe language environments running with untrusted code
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
Processor extensions and software verification to support type-safe language environments running with untrusted code
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
Memory domain based security control with data processing systems
ActiveUS7966466B2Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
Depth camera hand-eye calibration method based on CALTag and point cloud information
The invention discloses a depth camera hand-eye calibration method based on CALTag and point cloud information, and the method comprises the steps: building a mathematic model of hand-eye calibration,and obtaining a hand-eye calibration equation AX = XB; then, using a CALTag calibration board for replacing a traditional checkerboard calibration board so thatthe recognition precision of the pose of the calibration board is improved, and meanwhile calculating a matrix A in a hand-eye calibration equation; solving a matrix B by combining the obtained matrix A and the positive kinematics of themechanical arm, and a hand-eye calibration equation A * X = X * B is solved based on the Lie group theory; and finally, obtaining a calibration matrix more suitable for a three-dimensional visual scene based on a trust region reflection optimization iterative algorithm by utilizing the obtained point cloud depth information. The method can accurately determine the coordinate transformation of thepoint cloud coordinate system and the robot coordinate system, is high in grabbing precision, and is suitable for an application scene that a mechanical arm grabs an object in three-dimensional vision.
Owner:XI AN JIAOTONG UNIV
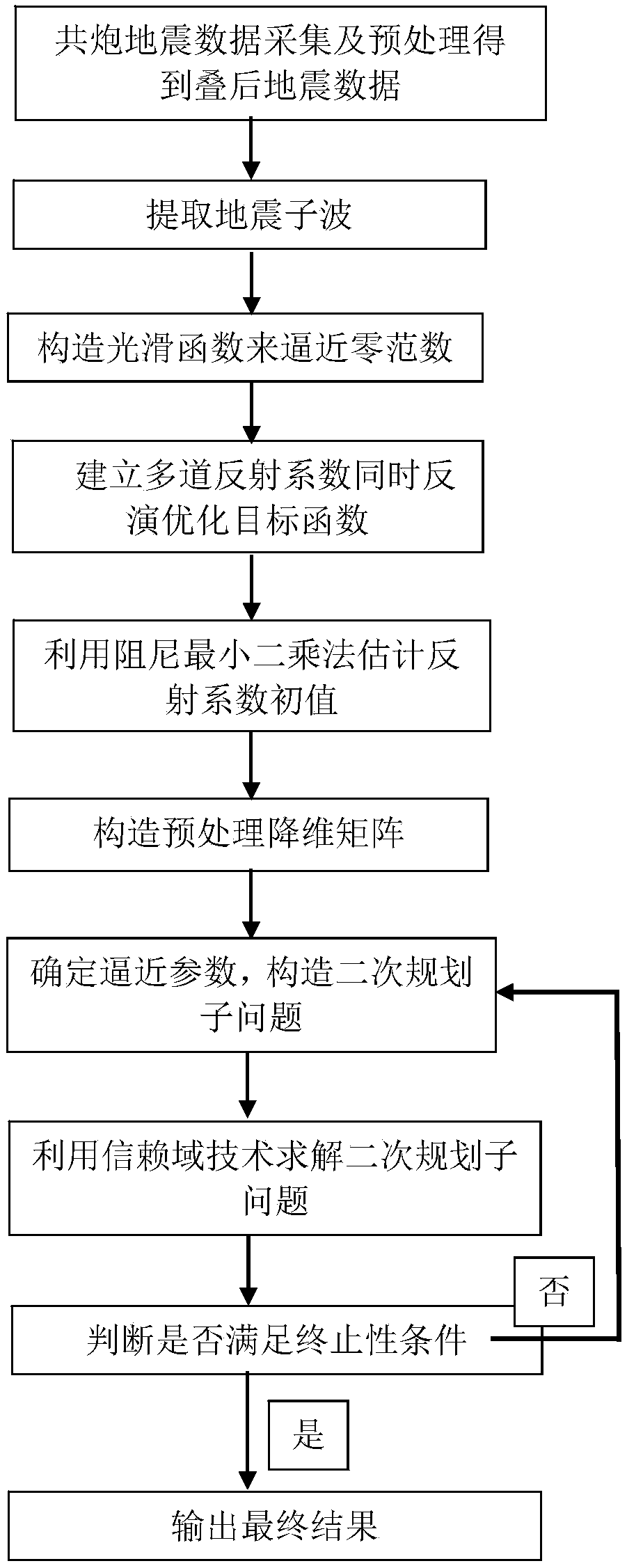
Multichannel seismic record reflection coefficient sequence simultaneous inversion method
ActiveCN107589448AGlobal convergenceHas a superlinear rate of convergenceSeismic signal processingSpatial correlationHypothesis
The invention discloses a multichannel seismic record reflection coefficient sequence simultaneous inversion method. The method thoroughly considers sparse characteristics of a formation reflection coefficient sequence and spatial transverse continuity of seismic channels, a parameterized exponential function is used to measure the sparsity of the reflection coefficient sequence, and a corresponding constrained optimization objective function is built. Firstly, based on the characteristics of a convolution model and the sparsity hypothesis of the reflection coefficients, on the premise of notlosing any information, a dimension reduction preprocessing matrix is designed, and the dimension of the constrained objective function is reduced; and then, a trust region sequential quadratic programming algorithm is used for high-efficiency solution. The algorithm has global convergence and a super linear convergence rate, the calculation efficiency is high, and the inversion precision is high.Compared with the traditional single-channel seismic record deconvolution algorithm, the algorithm of the invention has a more stable and reliable inversion result as the spatial correlation of the seismic channels is considered.
Owner:XI AN JIAOTONG UNIV
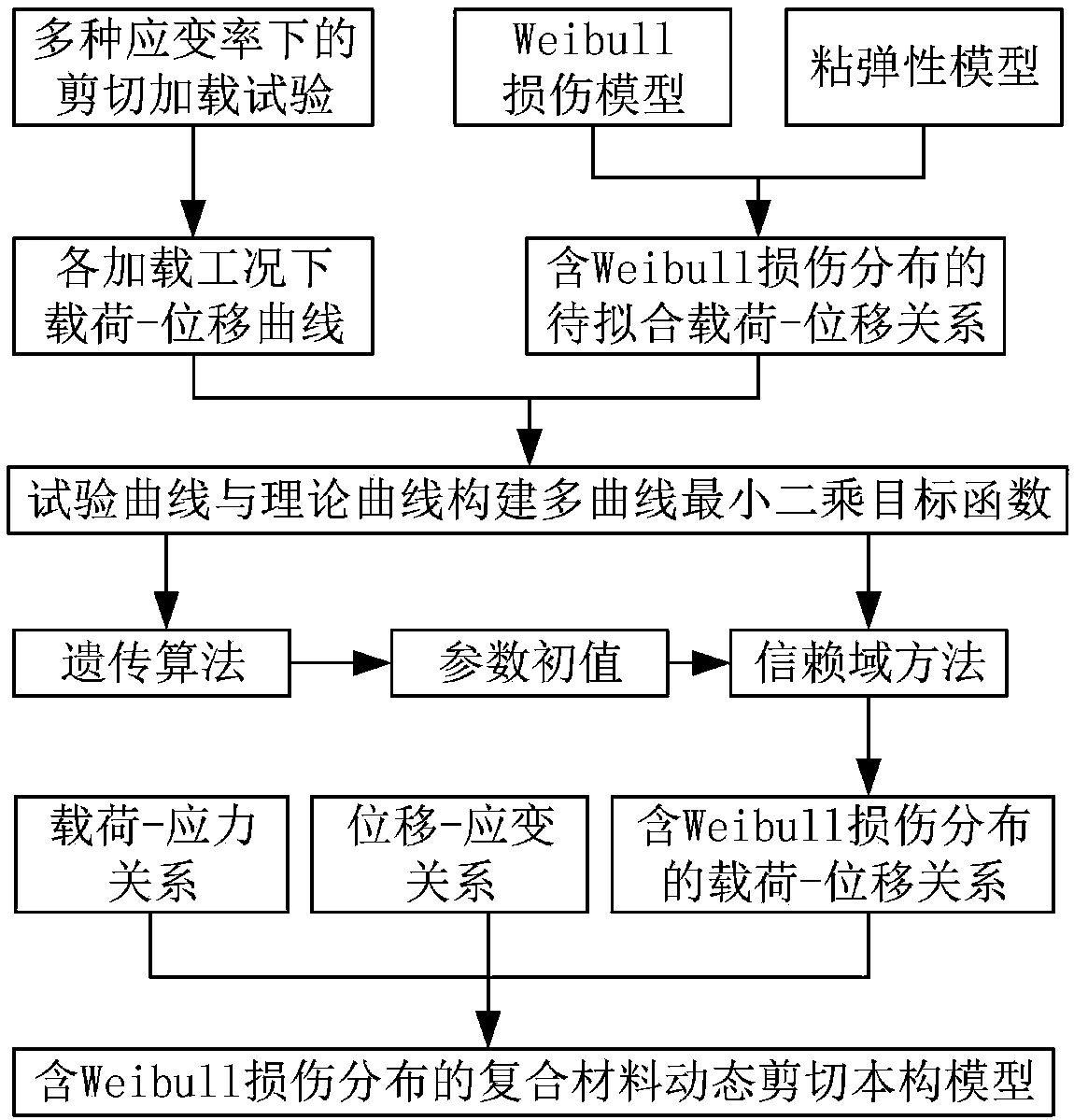
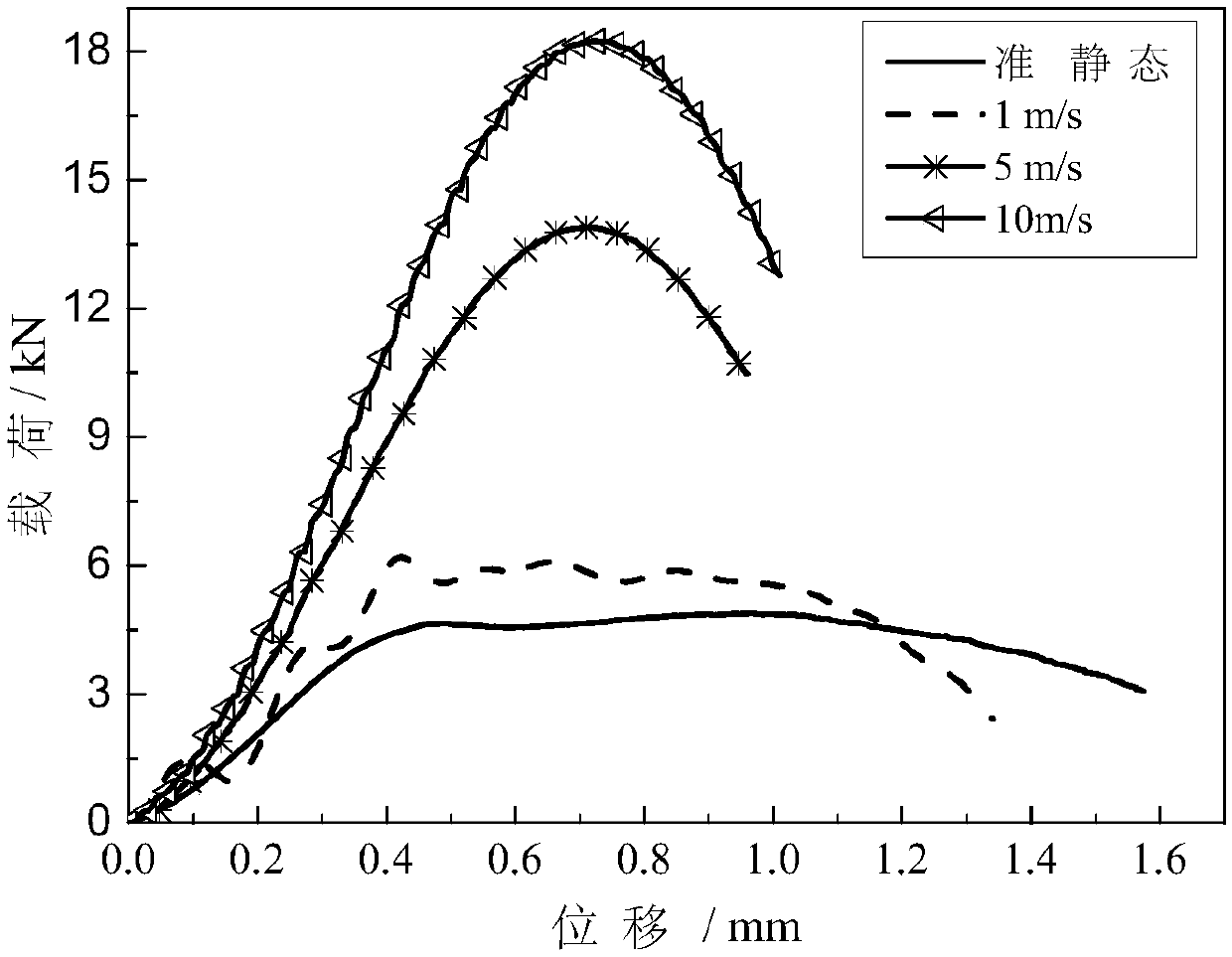
Construction method for dynamic shear constitutive model of fiber-reinforced composite material
ActiveCN107633120AUniqueness guaranteedGuaranteed accuracyGeometric CADDesign optimisation/simulationGenetic algorithmEngineering
The invention discloses a construction method for a dynamic shear constitutive model of a fiber-reinforced composite material. The method comprises the steps of 1, completing shear tests of the fiber-reinforced composite material under various strain rate loading working conditions to obtain a load-displacement curve under each working condition; 2, combining a Weibull damage model with a viscoelastic model to deduce a to-be-fitted load-displacement relation containing Weibull damage distribution; 3, constructing a multi-curve least-square objective function according to the load-displacementcurves and the load-displacement relation; 4, obtaining an initial value of a to-be-fitted parameter by use of a genetic algorithm, searching in the vicinity of the obtained initial value of the parameter through a trust-region method to finally obtain a high-precision parameter value and the determined load-displacement relation containing the Weibull damage distribution; and 5, deducing the dynamic shear constitutive model of the composite material containing the Weibull damage distribution according to a load-stress relation, a displacement-strain relation and the load-displacement relation. According to the construction method for the dynamic shear constitutive model of the fiber-reinforced composite material, a reliable basis can be provided for numerical simulation calculation of thefiber-reinforced composite material under the dynamic working conditions.
Owner:SOUTHEAST UNIV
Method and device for establishing full-waveform inversion model for geophysics parameters
InactiveCN105549079AImprove inversion accuracyImprove efficiencySeismic signal processingAdjoint state methodWave field
The invention provides a method and device for establishing a full-waveform inversion model for geophysics parameters. The method comprises following steps: residual values of real wave-fields and initial model observation wave-fields are calculated; by use of the residual values, gradients of an objective function to model parameters are calculated through an adjoint state method; A Hessian matrix is calculated by use of variations of the model parameters and variations of the gradients By use of the gradients and the Hessian matrix, trust region sub-problems are established through performing second-order expansion calculation to the objective function according to Taylor's formula; the trust region sub-problems are solved through a conjugate gradient method to obtain solutions, namely the probe step length of the next iteration, of the trust region sub-problems; updates of the model parameters and trust region radii are performed on the basis of the trust region algorithm to obtain the full-waveform inversion model of geophysics parameters. By use of the method and device, a high fidelity velocity model is obtained.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
Flow calculation method suitable for microgrids in various operation modes
InactiveCN105514971AAddress diversityGood practical engineering application valueEnergy industryAc network circuit arrangementsAlgorithmControl engineering
The invention discloses a microgrid flow model suitable for various operation modes, and a calculation method. The invention discloses a flow calculation method suitable for microgrids in various operation modes, and the method comprises the steps: forming five types of microgrid operation modes and four types of nodes according to two types of basic operation modes and three types of control strategies of a microgrid; enabling the microgrid flow calculation in five types of different operation modes to be divided into two types of flow calculation; building a unified flow model; and proposing an LM-TR (Levenberg Marquardt method combined with trust region technique, LM-TR) flow algorithm for solving. The method does not need the jacobian matrix of a flow equation to be nonsingular, has global convergence, is small in dependence on initial values of unknown variables, effectively improves the convergence of flow calculation, and can solve a problem that the convergence of flow calculation of a microgrid system is difficult because that the jacobian matrix is singular or there is no balance point. Moreover, the method can process various types of nodes conveniently, and can solve a problem of the diversity of microgrid flow calculation in different operation modes. The method is suitable for the flow calculation of the microgrid in various operation modes, and is good in engineering application value.
Owner:XIANGTAN UNIV
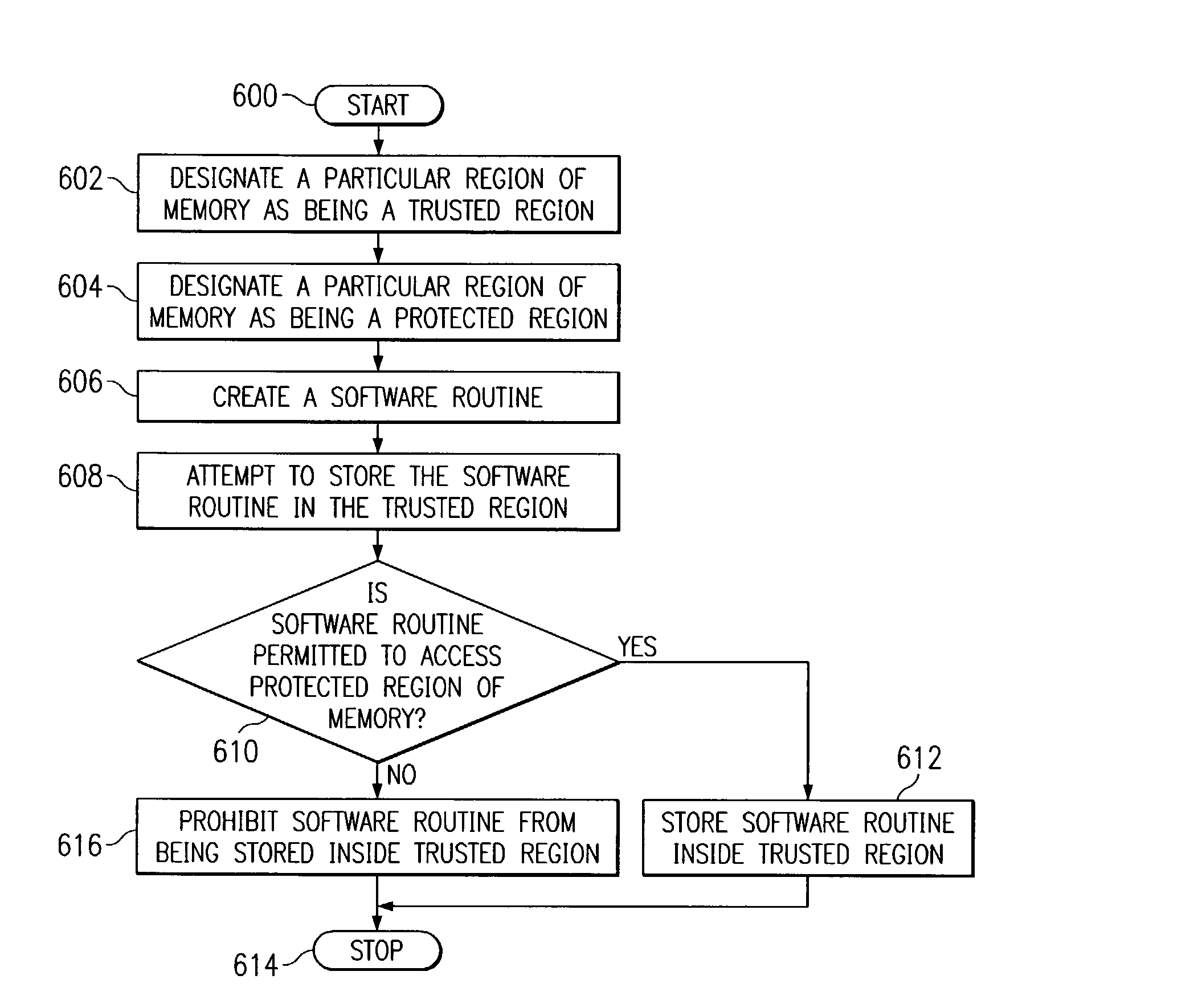
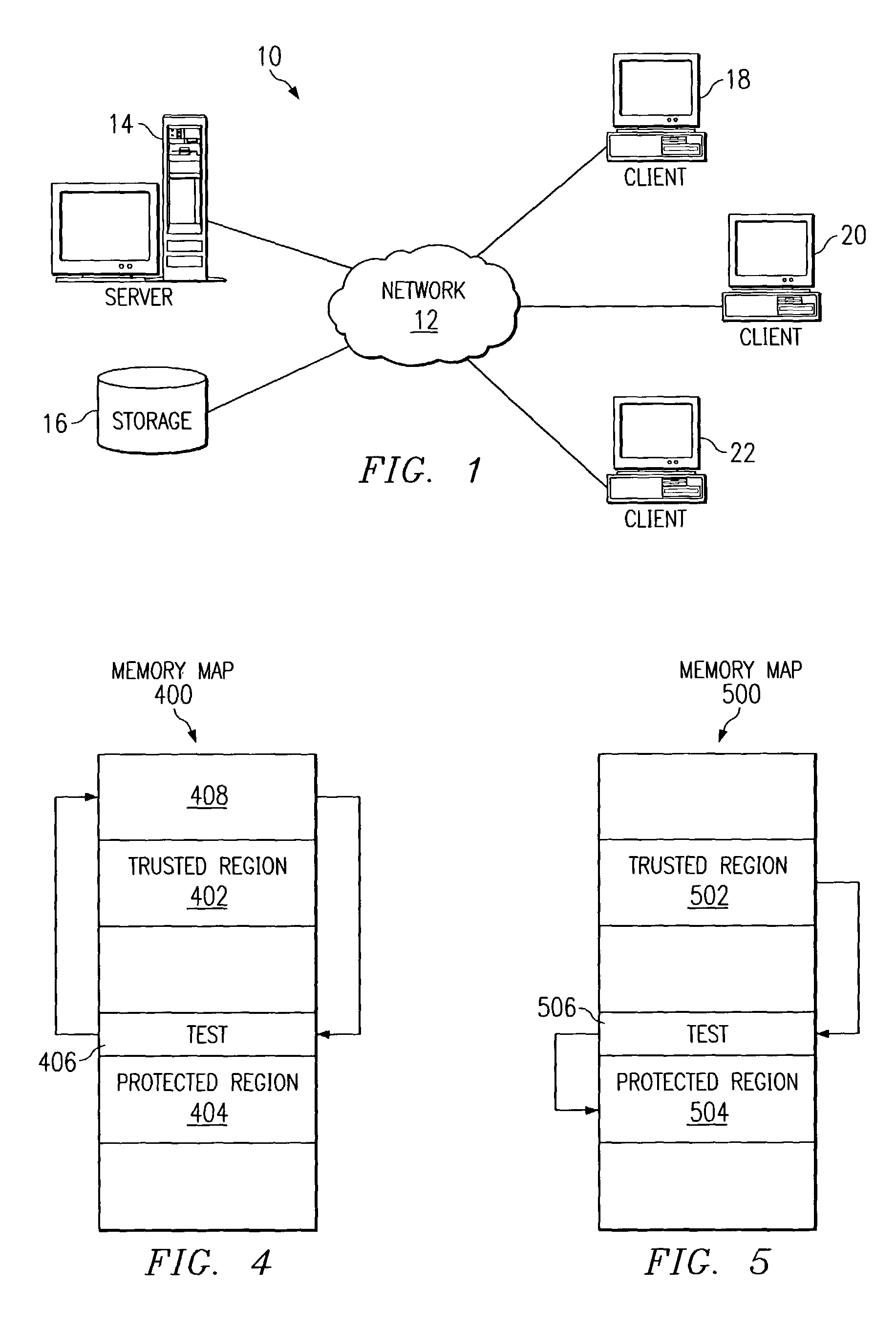
System, method, and computer program product for prohibiting unauthorized access to protected memory regions
InactiveUS7266658B2Volume/mass flow measurementUnauthorized memory use protectionInternet privacyTrust region
A system, method, and computer program product are disclosed for prohibiting unauthorized access to a protected region of memory. A protected region of memory and a trusted region of memory are both specified. A call to access a location within the protected region of memory is received. An origination location of the call is then determined. In response to a determination that the origination location is within the trusted region, the call is permitted to access the protected region of memory. In response to a determination that the origination location is outside of the trusted region, the call is prohibited from accessing the protected region of memory.
Owner:IBM CORP
Error compensation method of three-axis magnetic field sensor connected to underwater vehicle in strap-down mode
InactiveCN104166169AElectric/magnetic detectionAcoustic wave reradiationClassical mechanicsTrust region
The invention belongs to the field of underwater geomagnetic aided navigation and particularly relates to an error compensation method of a three-axis magnetic field sensor connected to an underwater vehicle in a strap-down mode. The error compensation method comprises the steps of obtaining a geomagnetic modulus gradient measured value of a carrier at a certain attitude through the three-axis magnetic field sensor connected to the underwater vehicle in the strap-down mode; obtaining a set of geomagnetic modulus gradient measured values and carrier attitude angle information corresponding to the measured values; substituting the obtained geomagnetic modulus gradient measured values Fm at different attitudes into an equation including the carrier induced magnetic field coefficient matrixes; using a trust region method to estimate unknown parameters in error matrixes in the equation; obtaining error elements in the error matrixes and further obtaining the error matrixes; substituting the obtained error matrixes into the equation including the carrier induced magnetic field coefficient matrixes to compensate the geomagnetic measured values. By means of the error compensation method, the problem that a selected inappropriate initial point possibly causes iteration divergence and accordingly a correct estimation result cannot be obtained.
Owner:HARBIN ENG UNIV
System and method for inhibiting unauthorized access to protected memory region
A system, method, and computer program product are disclosed for prohibiting unauthorized access to a protected region of memory. A protected region of memory and a trusted region of memory are both specified. A call to access a location within the protected region of memory is received. An origination location of the call is then determined. In response to a determination that the origination location is within the trusted region, the call is permitted to access the protected region of memory. In response to a determination that the origination location is outside of the trusted region, the call is prohibited from accessing the protected region of memory.
Owner:IBM CORP
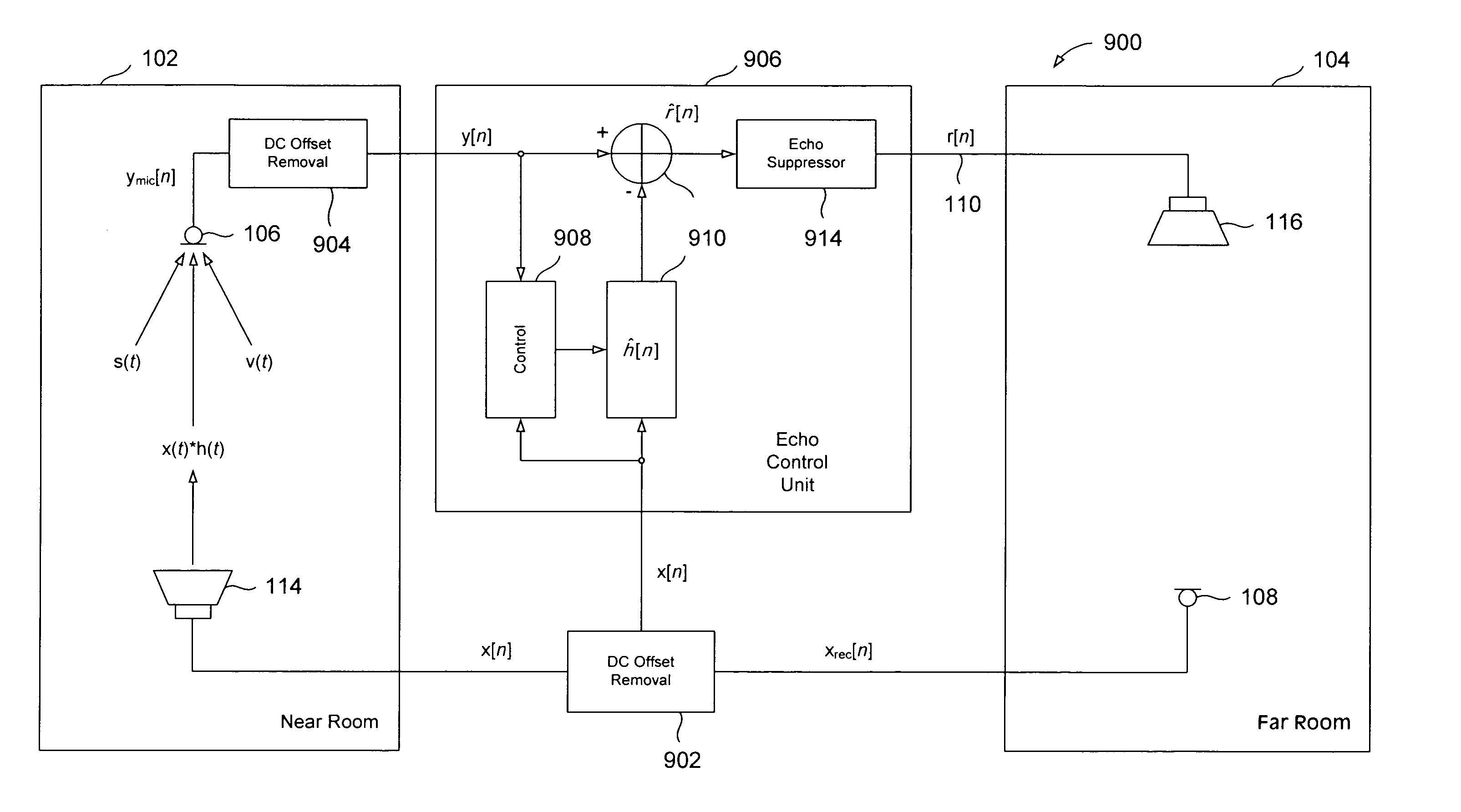
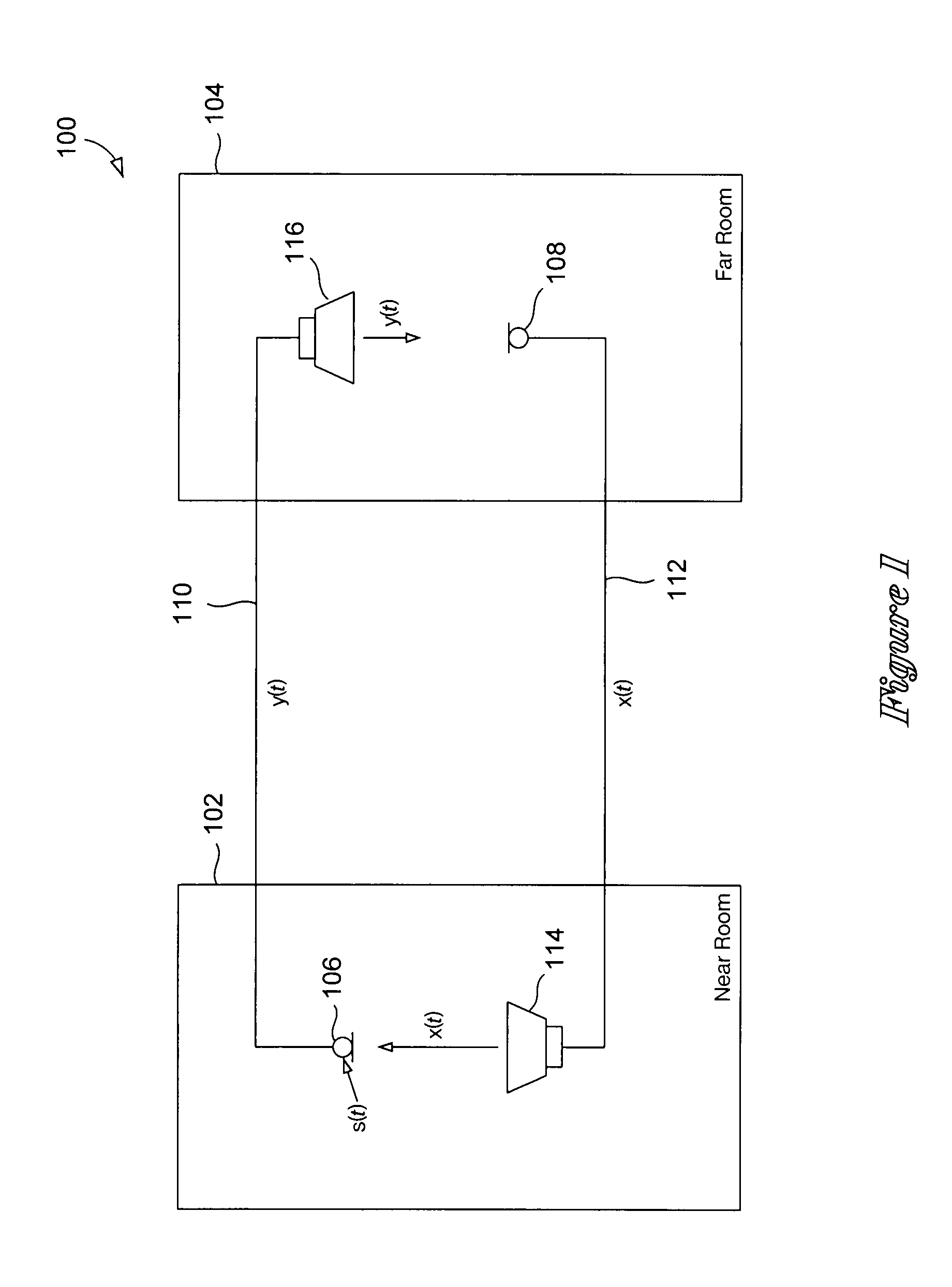
Methods and systems for reducing acoustic echoes in communication systems
ActiveUS20070253565A1Interconnection arrangementsPublic address systemsCommunications systemTrust region
Various embodiments of the present invention are directed to methods and systems that reduce acoustic echoes in audio signals in accordance with changing conditions at first and second locations that are linked together in a communication system. In particular, one embodiment of the present invention relates to a method for determining an approximate impulse-response vector for canceling an acoustic echo resulting from an audio signal transmitted from the first location to the second location. This method includes forming a trust region within a search space based on computing a recursive specification vector defining the trust region. The method also includes computing a recursive shadow-impulse-response vector that lies substantially within the trust region, and computing the approximate impulse-response vector based on the recursive shadow-impulse-response vector and the recursive specification vector.
Owner:HEWLETT PACKARD DEV CO LP
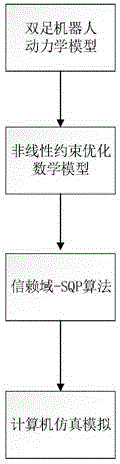
Nonlinear model predictive control-based trust region-SQP method for gait optimization of biped robot
InactiveCN106814610AImprove computing efficiencyThe solution method is simpleAdaptive controlOptimal controlGait
The invention relates to the field of the gait optimization control for a biped robot and particularly relates to a model predictive control-based trust region-SQP method for the gait optimization of the biped robot. Based on the nonlinear model predictive control technology, the trust region-SQP method is adopted to realize the superlinear convergence rate and the global convergence fast-solving optimal control, so that the optimal movement gait of the biped robot is realized. Since the nature of an objective function is poor, a significant amount of time is spent in determining a searching step length. Therefore, the real-time performance is invalid. According to the technical scheme of the invention, based on the nonlinear model predictive control technology, a robot dynamics model is converted into a non-linear optimization model, and the trust region-SQP method having fast convergence characteristics is provided. In this way, the optimal control, which realizes the real-time performance, is solved. The method overcomes the defect that the real-time performance cannot be realized during the solving process of a traditional controller. The method can be applied to multi-degree-of-freedom biped robots and provides references for the real-time control solutions of multi-degree-of-freedom biped robots.
Owner:CHANGCHUN UNIV OF TECH
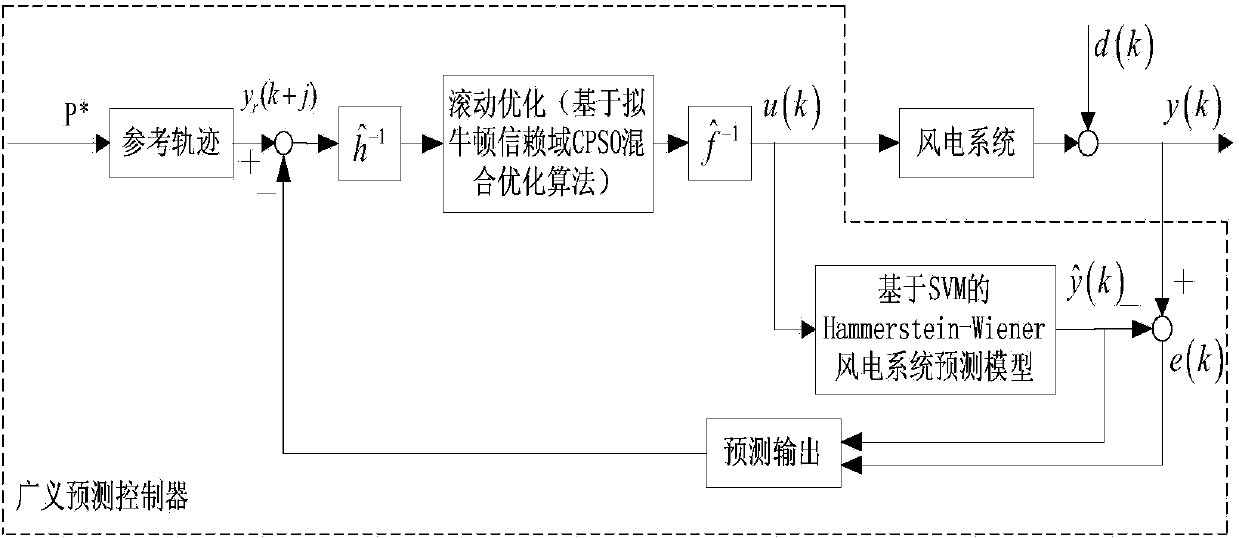
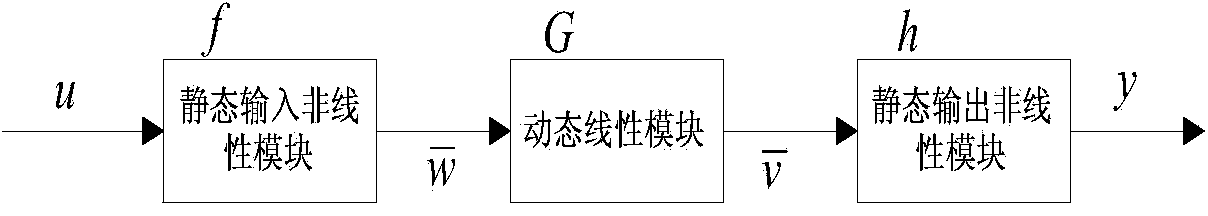
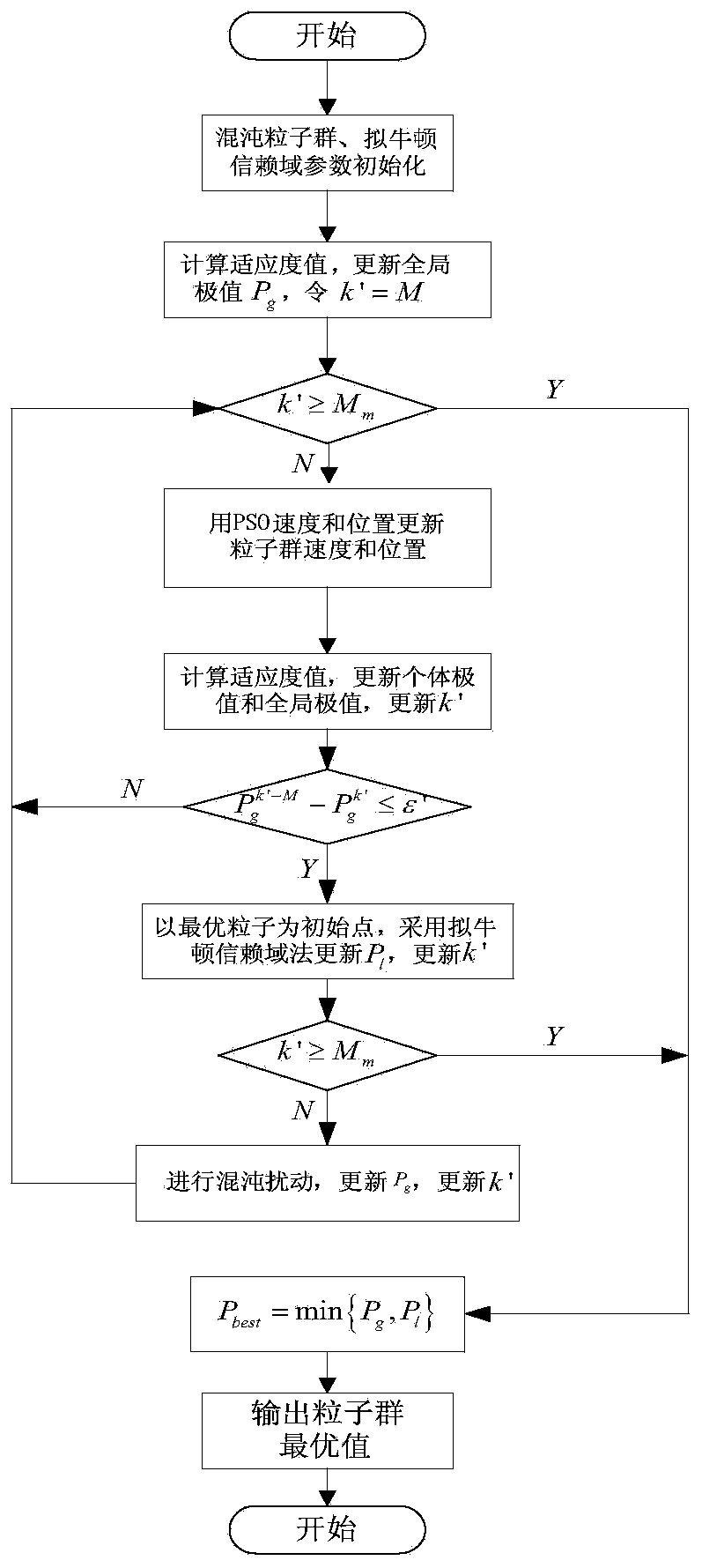
Constant power generalized predictive control method for wind power generator set based on Hammerstein-Wiener model
ActiveCN104500336ARealize constant power controlReduce development costsWind motor controlMachines/enginesElectricityConstant power
The invention relates to a constant power generalized predictive control method for a wind power generator set based on a Hammerstein-Wiener model. The constant power generalized predictive control method comprises the following steps: acquiring enough sample data inputted and outputted by a wind power generation system in real time, establishing the Hammerstein-Wiener wind power generator prediction model based on a least squares support vector machine and obtaining the power multi-step prediction output of a wind power generator through model identification; outputting and calculating a quadratic performance index subjected to generalized predictive control through a multi-step prediction output and reference trajectory of the wind power generation system; carrying out rolling optimization on the quadratic performance index by adopting a quasi-Newton trust region CPSO (Chaos Particle Swarm Optimization) hybrid optimization algorithm, outputting a pitch angle controlled quantity u(k) capable of enabling the performance index to be smallest; newly acting the obtained pitch angle controlled quantity u(k) on the wind power generation system, obtaining the next time of multi-step prediction output and carrying out cyclic predictive control. According to the constant power generalized predictive control method, the hardware development cost is reduced, the approximation accuracy and the rolling optimization efficiency of the prediction model on the output power of a non-linear wind power generator are improved, and the constant-power control above the rated wind speed of the wind power generator is realized.
Owner:JIANGSU UNIV OF SCI & TECH
Method for controlling video coding flow rate of monitoring video sending end
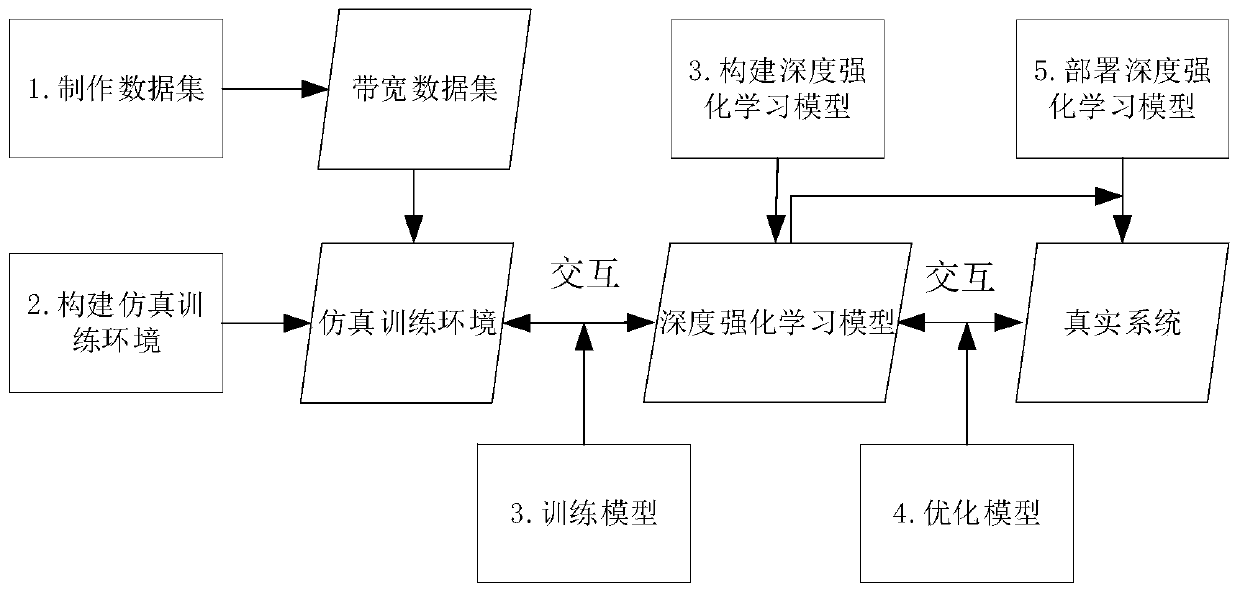
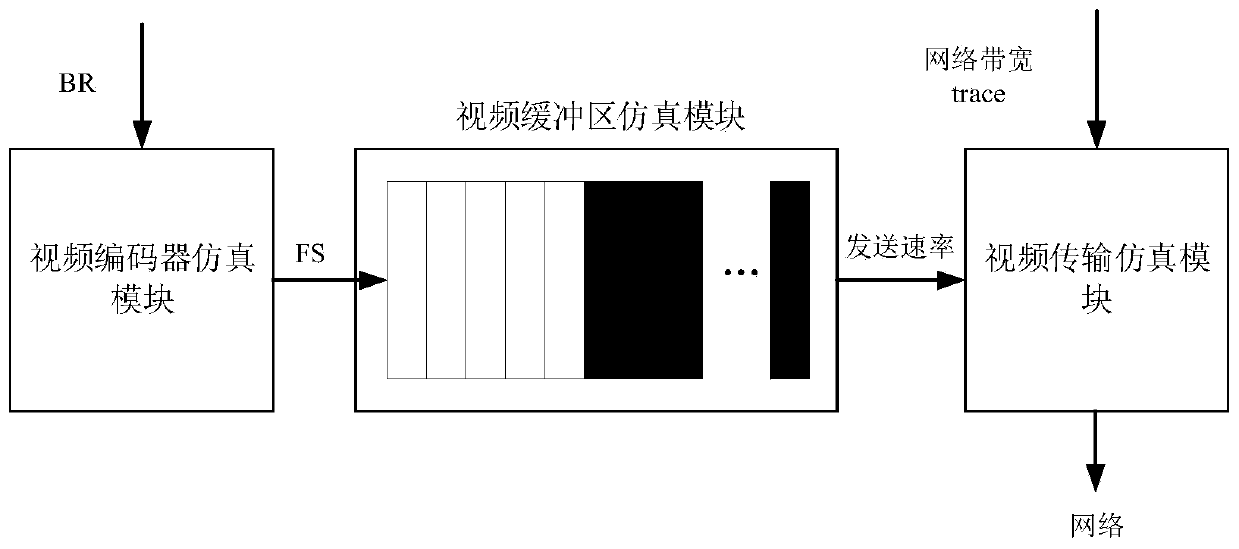
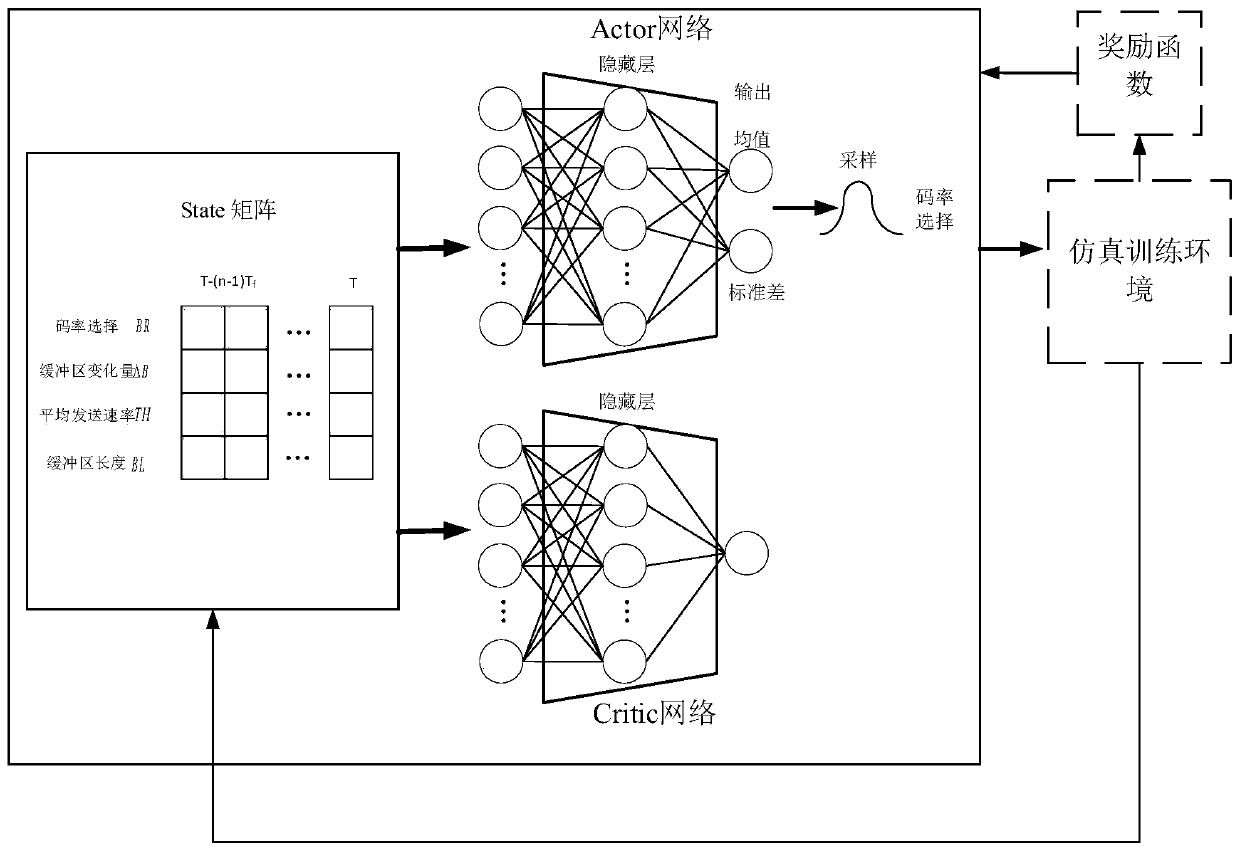
ActiveCN111031387ATroubleshoot encoding flow rate control issuesGuaranteed generalization abilityNeural architecturesSelective content distributionData setVideo encoding
The invention discloses a method for controlling the video coding flow rate of a monitoring video sending end. The method mainly comprises the steps of (1) collecting a real-time available bandwidth data set of a video sending scene network; (2) constructing a simulation training environment of a monitoring video sending end by utilizing the real bandwidth data, determining the highest available bandwidth for sending the monitoring video in real time by the training environment according to the real bandwidth data, taking the highest available bandwidth as the sending rate of the video, and receiving the code rate selected by the deep reinforcement learning model to adjust the encoding code rate of an encoder; (3) constructing a continuous action output deep reinforcement learning model based on a trust region, and training the model by utilizing a simulation environment; (4) putting the trained model into a monitoring video, integrating the monitoring video into a real environment forinteraction, and carrying out online training optimization; and (5) integrating the optimized deep learning model to a monitoring video sending end, and making an encoding rate decision of an encoderof the sending end. According to the invention, the coding flow rate control problem of the monitoring video sending end is solved by using deep reinforcement learning.
Owner:NANJING UNIV
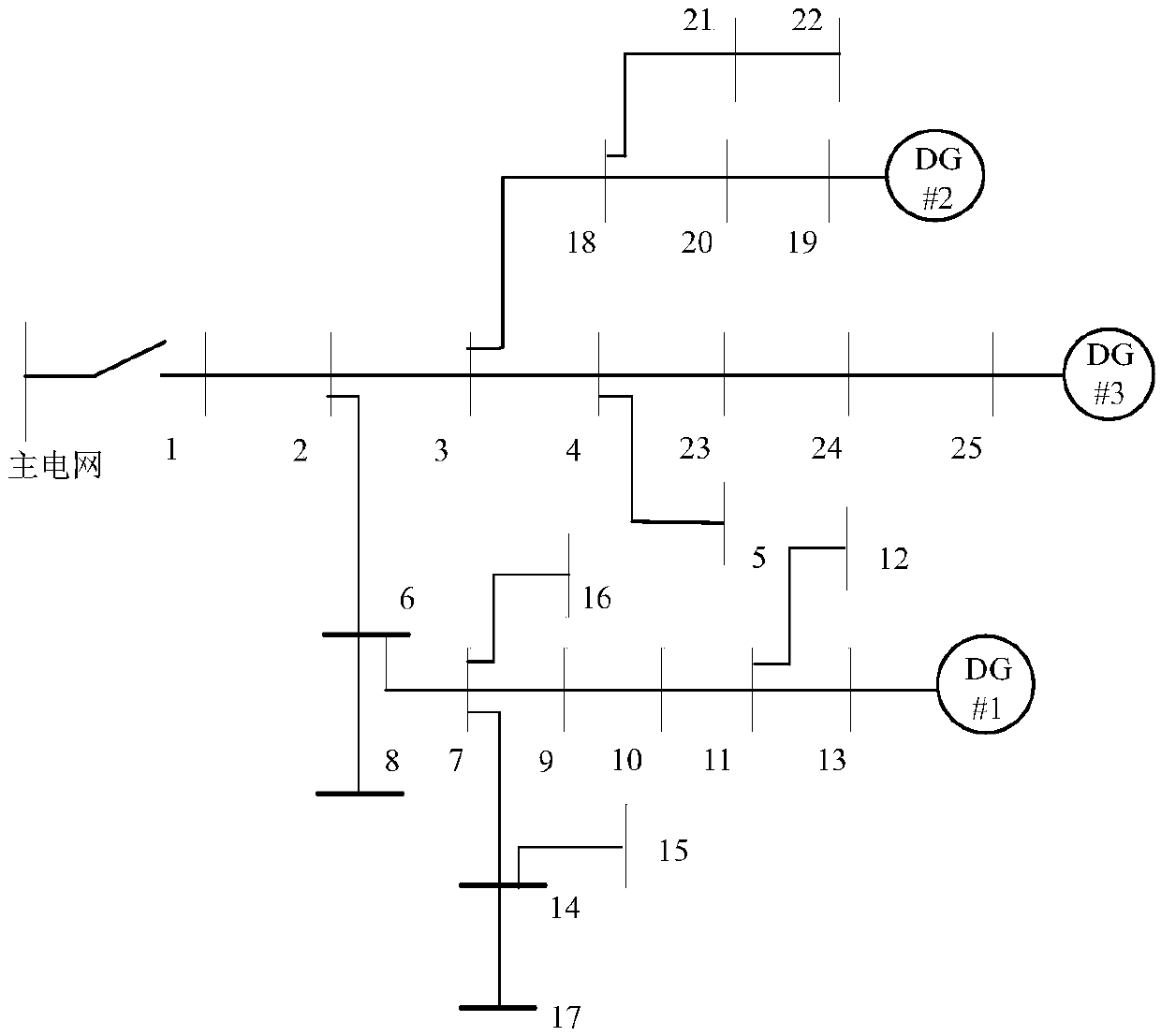
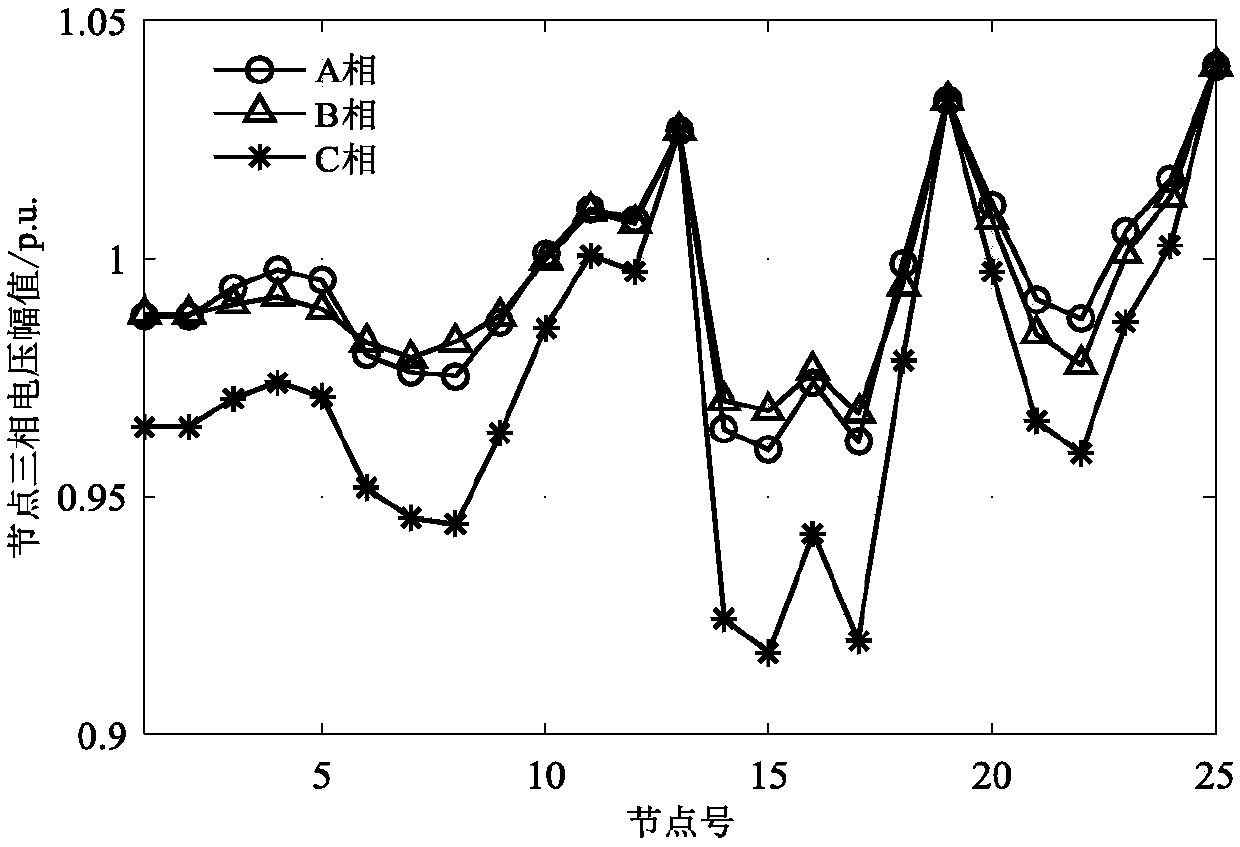
Three-phase power flow analysis method for droop control island micro-grid
InactiveCN108683191AFast convergenceSmall amount of calculationAc networks with different sources same frequencyPower flowEngineering
The invention discloses a three-phase power flow analysis method for a droop control island micro-grid. The method comprises steps of: firstly establishing the three-phase models of a droop control DG, a load and a circuit element in an island micro-grid, calculating the node admittance matrix Y of a system, writing the node power balance equation of the droop control island micro-grid, and obtaining three-phase power flow equations; then deriving the modified equation of the three-phase power flow equations during the solution of a Newton method and a calculation formula of a Jacobian matrixJ; and finally calculating droop node power and branch power and outputting a power flow calculation result. The method solves the problem that the trust region method has a large calculated amount and the conventional Newton method is difficult in convergence in the three-phase power flow method for a droop control island micro-grid in the prior art.
Owner:XIAN UNIV OF TECH
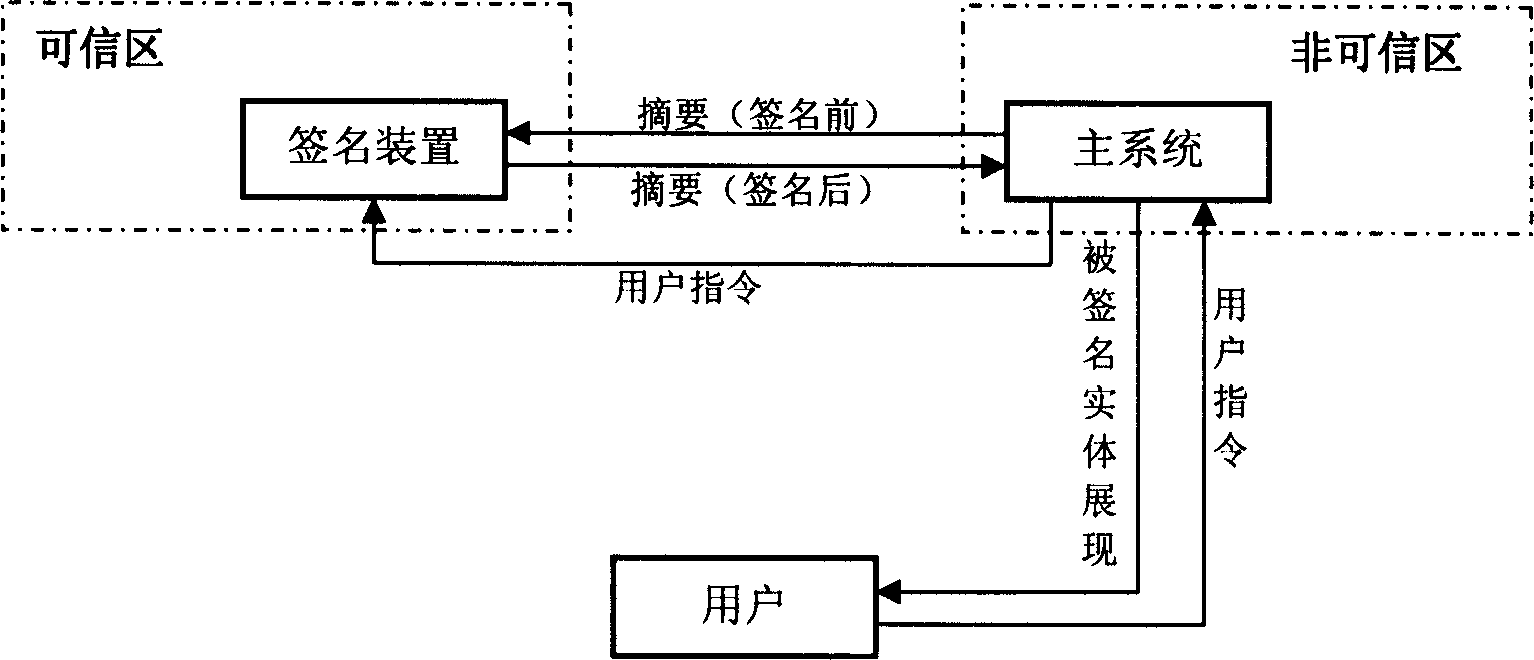
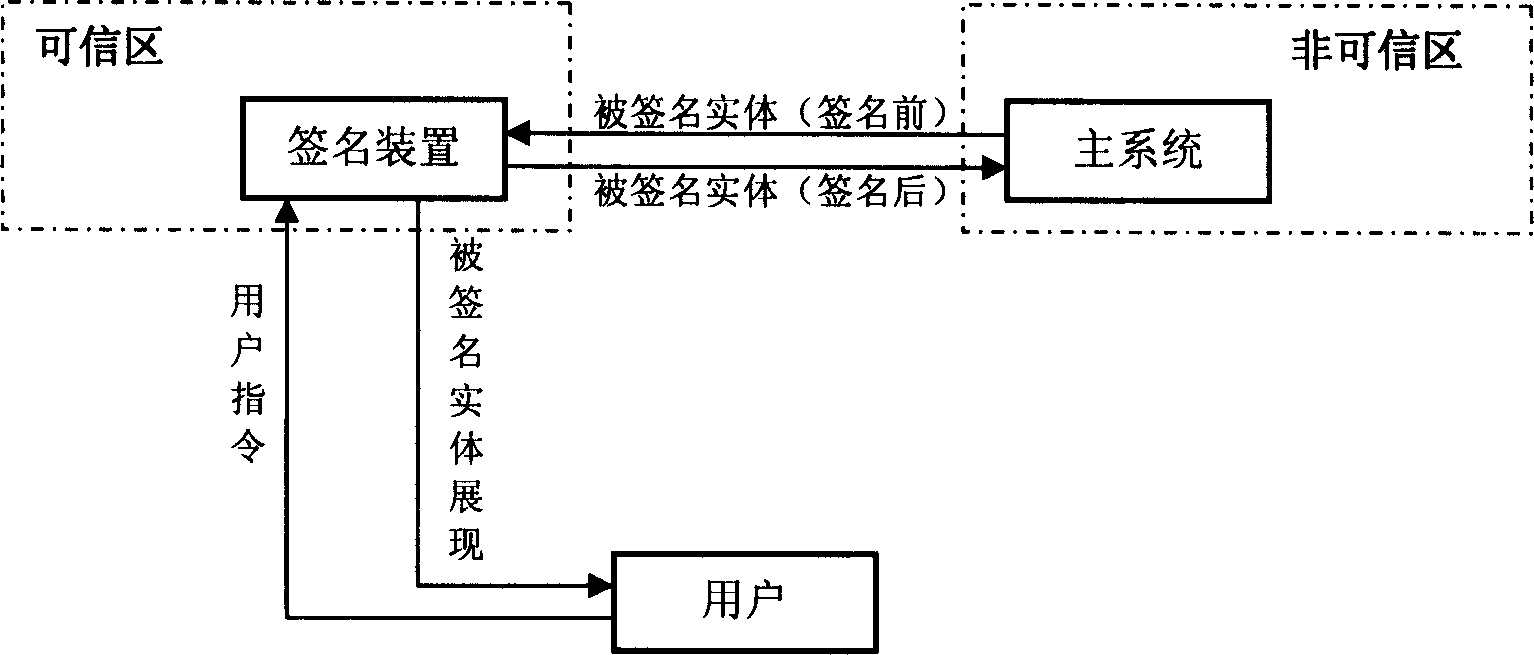
Sign device and method of digital sign
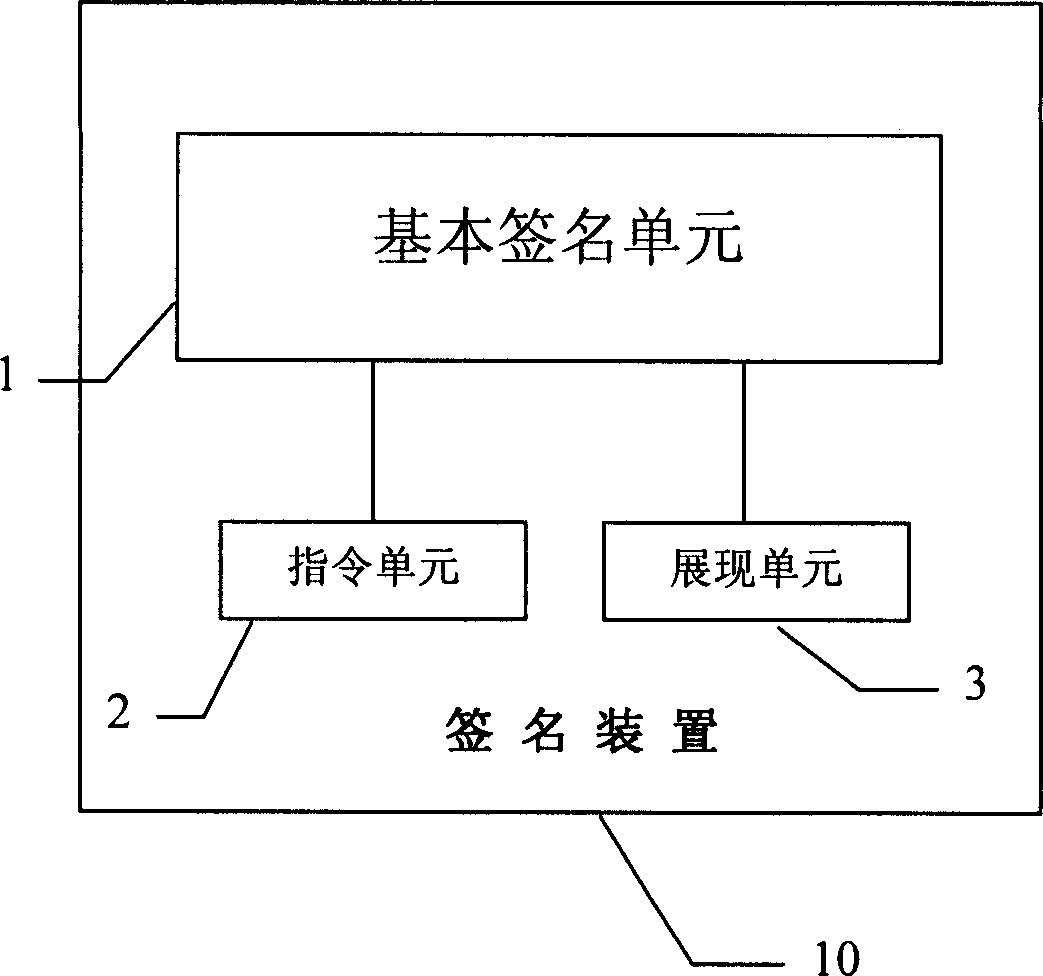
InactiveCN1794631APrevent tamperingAvoid substitutionUser identity/authority verificationInstruction unitTransfer procedure
This invention provides a signature device and a method for digital signature, in which, said device includes basic signature unit, which is a digital signature device signing names digitally for signed entities, in which, said device also includes an instruction unit used in receiving instructions of signing or refusing signature and sending said instruction to the basic signature unit, which operates according to the instruction and the sending of the instruction, generation of the abstracts and the display of the signed entity are put up in trust regions completely.
Owner:李代甫
Aircraft system optimization method based on dynamic multi-model fusion
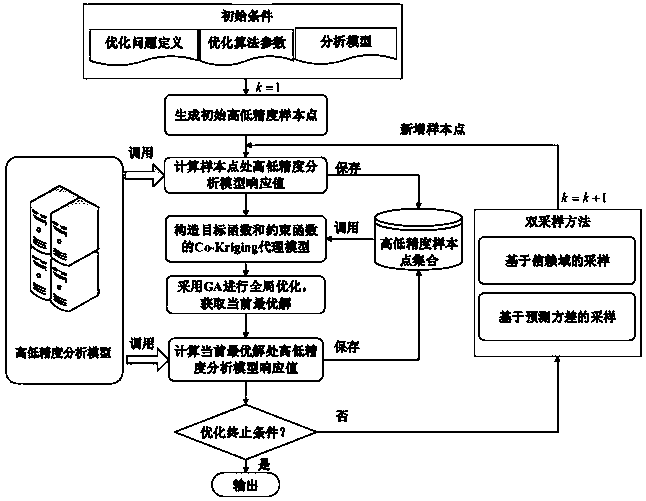
ActiveCN108491668AShorten the design cycleOvercome the inability to take full advantage of multi-source information responsesGeometric CADSpecial data processing applicationsSystems designTrust region
The invention discloses an aircraft system optimization method based on dynamic multi-model fusion, and belongs to the technical field of multidisciplinary optimization in aircraft design. The methodincludes the steps: fusing high-and-low-accuracy analysis models in aircraft system design by a Co-Kriging method, and replacing an original model to perform optimization design; updating and managinga Co-Kriging surrogate model by a double sampling method in the optimization process; improving local convergence ability of optimizing search through trust region sampling, improving global exploration ability of an optimizing process through predictive variance sampling, and guiding the optimizing process to rapidly converge an optimal solution. The method can overcome the shortcomings that a traditional optimization method can only process single-accuracy analysis model and is high in optimization cost, multi-source response information cannot be sufficiently utilized and the like, simulation models with different accuracies in aircraft system design can be efficiently fused and optimized, and the aircraft system optimization method is of great significance for reduction of aircraft system design optimization cost, improvement of system design performance and the like.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
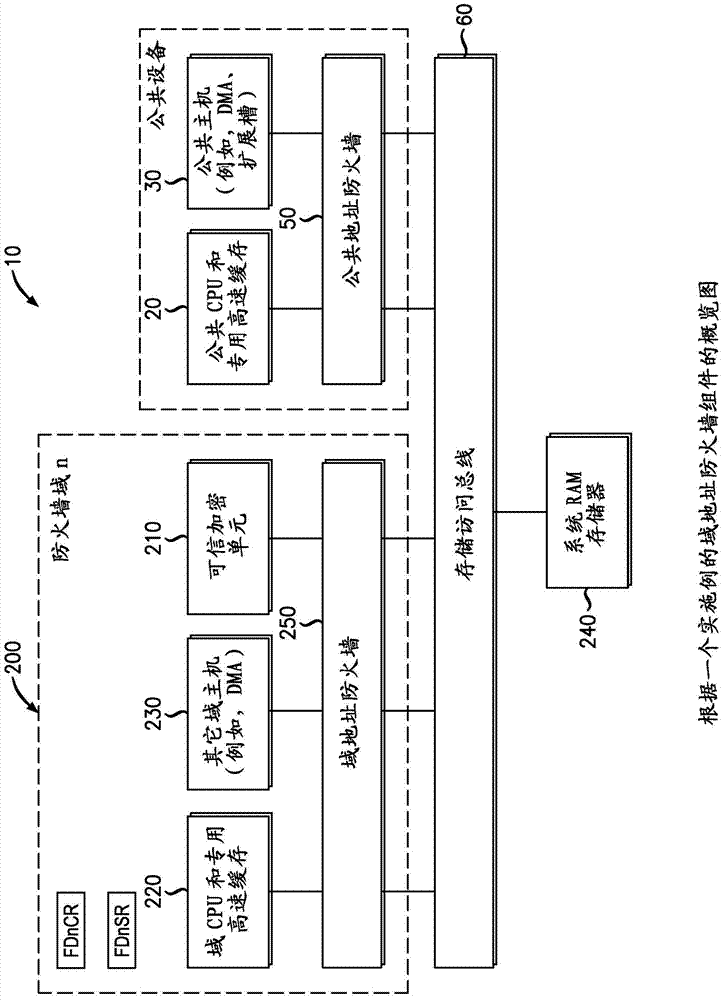
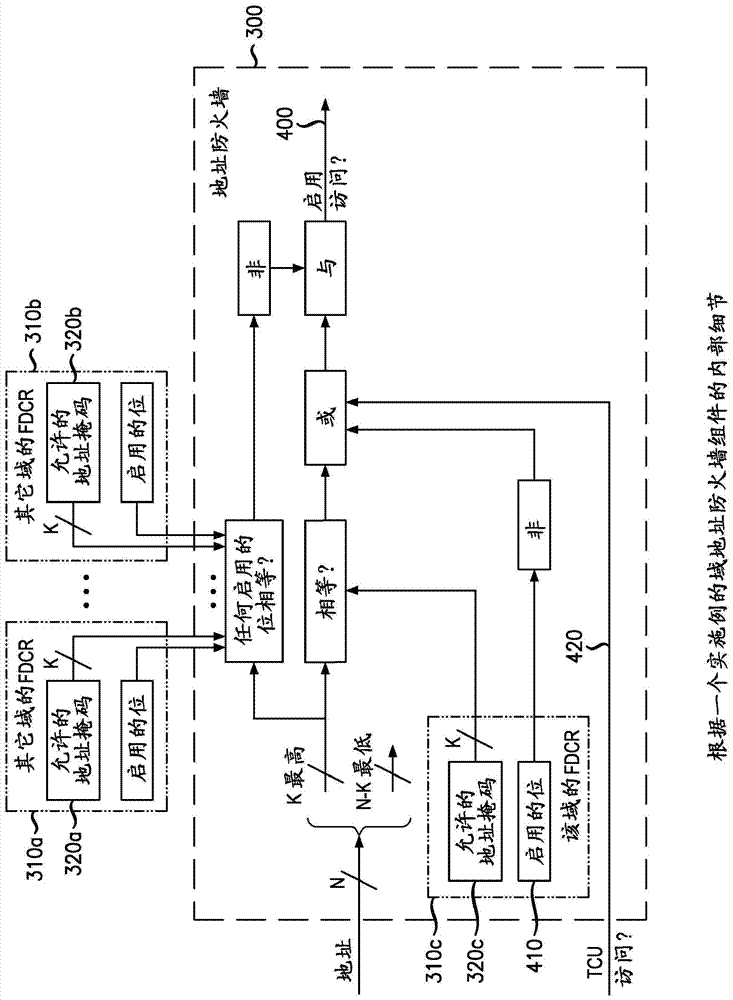
Secure data processing
InactiveCN104335549AUnauthorized memory use protectionInternal/peripheral component protectionMemory busTrust region
A secure data processing apparatus and method are disclosed. The secure data processing apparatus is operable to securely process user data provided by a user. The secure data processing apparatus comprises: a trusted domain (200) comprising a trusted bus coupled with a trusted data processing apparatus (220) operable to process incoming user data received over the trusted bus and to generate outgoing user data; a trusted domain controller (210) coupling the trusted bus with an untrusted bus of an untrusted domain, the trusted domain controller (210) being operable to ensure that encrypted incoming user data received over the untrusted bus is decrypted and provided over the trusted bus as the incoming user data and to ensure that outgoing user data is encrypted and provided over the untrusted bus as encrypted outgoing data; and a data store access controller (250) coupling the trusted domain controller (210) and the trusted data processing apparatus (220) with a memory bus (60) of a data store (240), the data store access controller (250) being operable to restrict successful requests to use the data store (240) received from the trusted domain controller (210) and the trusted data processing apparatus (220) to those addressed to a trusted region of the data store (240). By providing a data store access controller (250), it is possible to constrain memory that can be accessed by each device operable to generate access cycles to a data store (240), and a trusted domain (200) can be implemented within a general computing system. The constraint can be implemented by interposing a special component, referred to as an "address firewall" (250), or data store access controller (250), between each hardware element able to access the main RAM memory (240) and a memory bus (60).
Owner:ALCATEL LUCENT SAS
Diffracted wave field extraction method and device
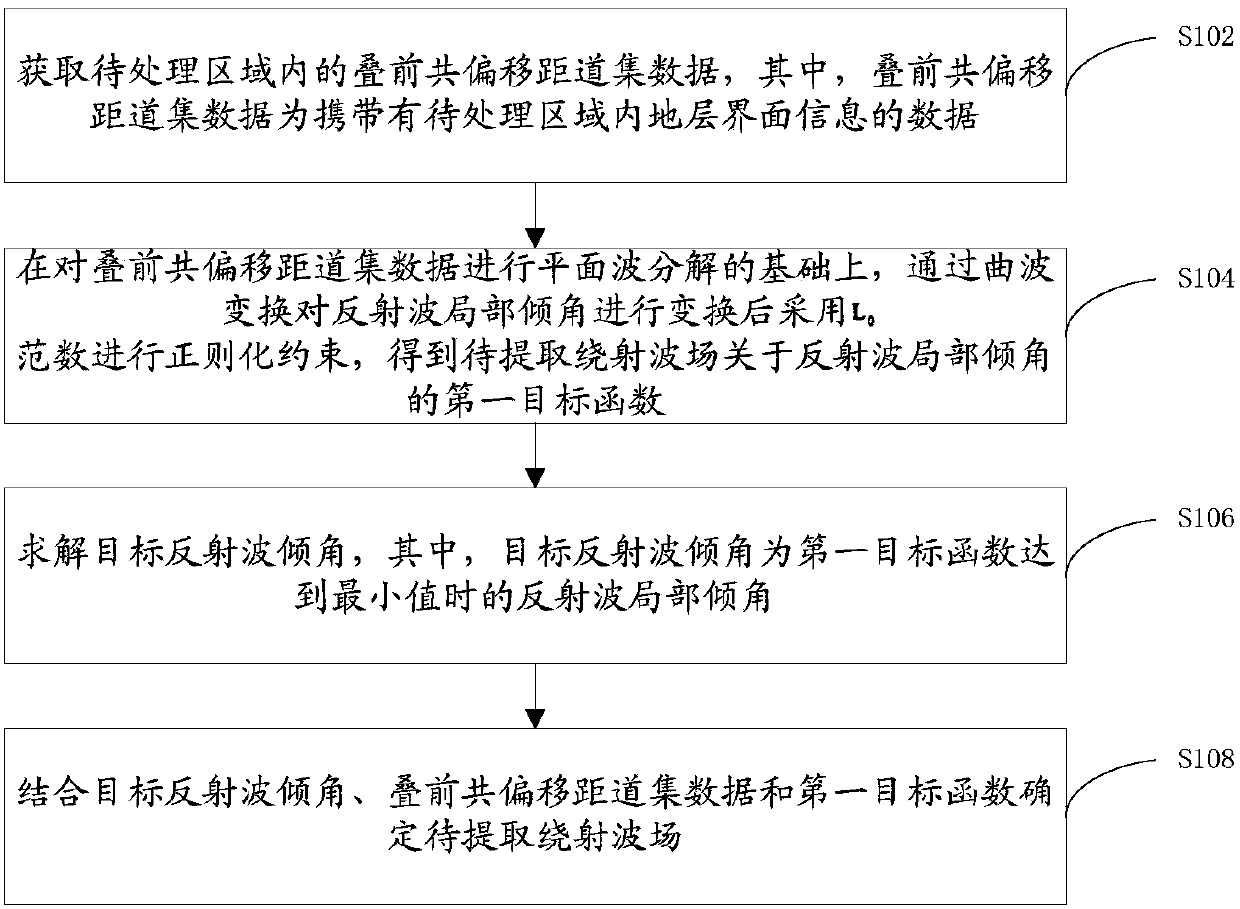
ActiveCN107942374ADestabilizationAlleviate the technical problem of poor precision of diffracted wavesSeismic signal processingReflected wavesWave field
The invention provides a diffracted wave field extraction method and device, and relates to the technical field of diffraction field extraction. The method includes: obtaining a pre-stack common-offset gather data in an area to be processed, wherein the pre-stack common-offset gather data carries the stratum interface information in the area to be processed; on the basis of plane wave decomposition on the pre-stack common-offset gather data, transforming the local dip angle of a reflected wave by curvelet transform and then performing regular constraint by using the L0 norm so as to obtain thefirst objective function of the diffracted wave field to be extracted relative to the local dip angle of the reflected wave; and solving the target reflection wave dip angle by a trust region algorithm, wherein the target reflection wave dip angle is the reflection wave dip angle when the first objective function reaches the minimum; and determining the diffraction wave field to be extracted by combining the target reflected wave dip angle, the pre-stack common-offset gather data and the first objective function. The method and device alleviate a technical problem that the diffraction wave extracted by the traditional diffraction wave extraction method is poor in accuracy.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
Robot cable modeling method under curved surface constraint
ActiveCN109977433AThe mechanical model is reasonableGuaranteed solution accuracyDesign optimisation/simulationSpecial data processing applicationsMathematical modelMechanical models
The invention relates to a robot cable modeling method under curved surface constraint. The method comprises the following steps of simplifying the cross section of an operation robot constraint cableinto a circular cross section; statically analyzing the simplified cable to obtain a cable nonlinear mechanical model; discretizing by adopting a finite difference method to obtain a discretized mathematical model; adding a cable curved surface constraint, a fixed-length condition constraint and a boundary condition constraint in an operation robot space; and solving the constrained discrete mathematical model by using a nonlinear least square algorithm based on trust region strategy adjustment to obtain Euler parameters and mechanical properties of all cable discrete points. According to a solving result, the correctness and reasonability of the method are verified; and the form of the high-precision operation robot cable is fitted by using the Euler parameters obtained through solving,so that the effectiveness and correctness of the method are verified, the mechanical properties of robot cable discrete points are obtained, and important support is provided for weakening the stableparting of the high-precision operation robot joint.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Robot cable modeling method under hoop constraint
ActiveCN109977434AHigh-precision operating mechanicsDesign optimisation/simulationSpecial data processing applicationsMathematical modelMechanical models
The invention relates to a robot cable modeling method under hoop constraint. The method comprises the following steps: simplifying the cross section of an operation robot constraint cable into a circular cross section; statically analyzing the simplified constraint cable of the operation robot to obtain a cable nonlinear mechanical model; discretizing by adopting a finite difference method to obtain a discretized mathematical model; adding a cable clamp constraint, a fixed-length condition constraint and a boundary condition constraint in an operation robot space; and solving the constraineddiscrete mathematical model by using a nonlinear least square algorithm based on trust region strategy adjustment to obtain Euler parameters and mechanical properties of all cable discrete points. According to the invention, the three-dimensional coordinates of each discrete point of the cable are calculated based on the Euler parameters in the solving result of the robot cable model under the constraint of the hoop; the geometrical shape of the cable is fitted by adopting cubic spline curves, so that the mechanical property of each discrete point of the high-precision operation robot cable isobtained, and an important theoretical support is provided for the stability analysis of the robot joint.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Phase shift optimization method for IRS-assisted downlink multi-user communication system
ActiveCN113114317AImprove throughputReduce complexityRadio transmissionTransmission monitoringMain diagonalMean square error matrix
The invention belongs to the technical field of mobile communication, and particularly relates to a phase shift optimization method for an IRS auxiliary downlink multi-user communication system, which comprises the following steps of: establishing an IRS auxiliary communication system model of a mobile user, and calculating the phase shift of the IRS auxiliary communication system model based on a relationship between a mean square error matrix of an optimal decoding matrix and channel capacity; constructing a channel capacity optimization model of the IRS auxiliary communication system by taking channel capacity maximization as a target; solving an optimal decoding matrix, an auxiliary matrix and a precoding matrix in the channel capacity optimization model, and constructing an IRS phase shift optimization model according to the channel capacity optimization model and a known matrix thereof; solving the IRS phase shift optimization model by adopting a Riemannian trust region method to obtain an optimal phase shift, and setting the optimal phase shift as a main diagonal element of an IRS phase shift matrix. According to the method, under the condition that throughput is not lost, complexity is greatly reduced, and the channel capacity obtained through the method is larger than that obtained through a traditional method under the same condition.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
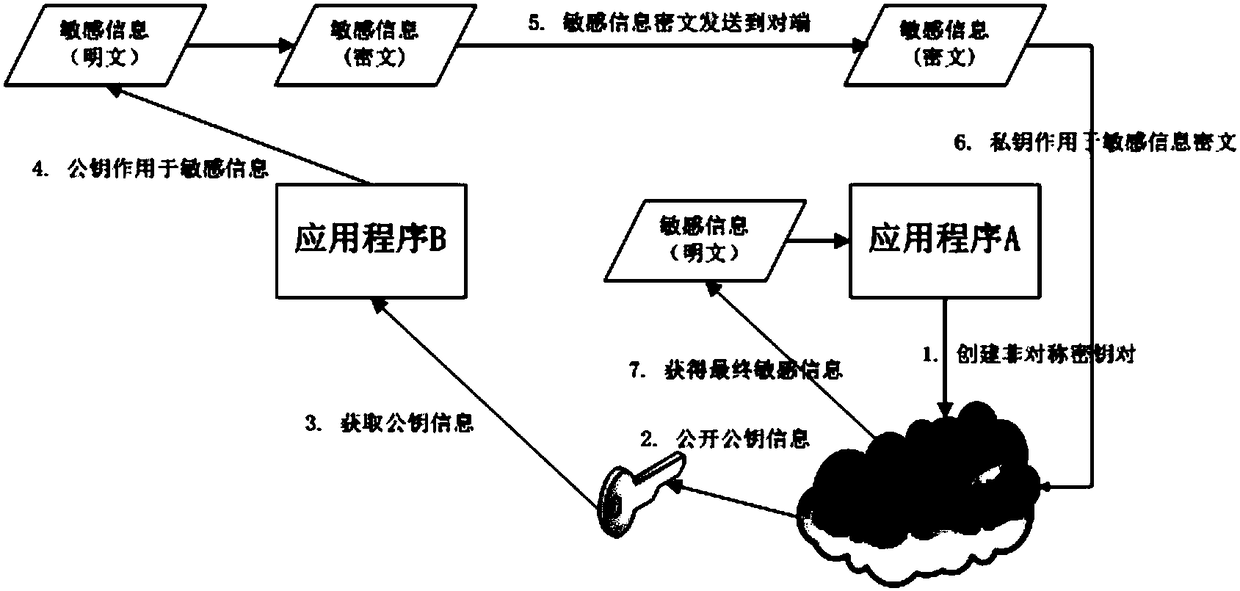
Safety communication method between Android application programs based on trusted execution environment
InactiveCN108156143AProtection securityImprove security levelKey distribution for secure communicationPublic key for secure communicationSecure communicationCommunications security
The invention discloses a safety communication method between Android application programs based on a trusted execution environment. The method comprises the following steps: a data receiver application program creates an asymmetric key pair in a safety trusted region, and opens a public key of the created asymmetric key pair to the public; the data sender application program acquires the public key opened by the receiver application program, and adopts the acquired public key as the sensitive data, enables the sensitive data to form ciphertext data, and then sends the ciphertext data to the data receiver application program; the data receiver application program receives the ciphertext data sent by the data sender application program, and decrypts the received ciphertext data by adoptingthe private key of the created asymmetric key pair, thereby acquiring the final sensitive data. Through the safety communication method disclosed by the invention, the data communication security between the Android application programs is protected, the safety level of the sensitive data communication is improved, and the user information is protected to the greatest extent.
Owner:上海格尔安全科技有限公司
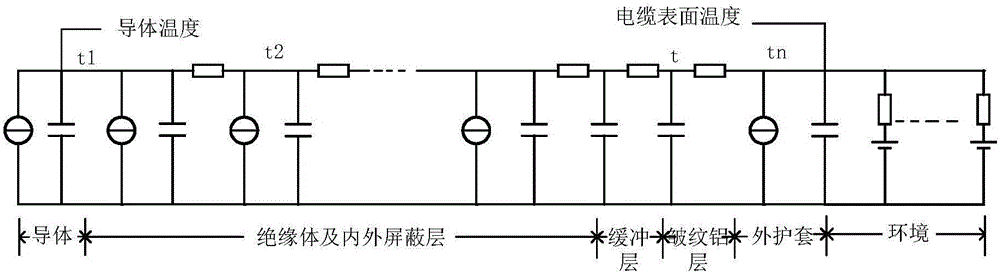
Rapid cable temperature calculation method based on parameter fitting
ActiveCN105787191AThe solution is not easy to obtainSolve insulation problemsComputer aided designComplex mathematical operationsPartial differential equationEngineering
The invention provides a rapid cable temperature calculation method based on parameter fitting.The method includes the steps that firstly, according to cable laying characteristics, a heat circuit method is adopted, a transient cable temperature heat circuit model for parameter fitting is established, and a cable temperature differential equation is listed and written; aiming at a certain specific working condition of a cable, the cable gets into a zero initial state, rated currents are applied to the cable, and the cable core and surface temperatures of the cable generated when the cable temperature reaches a stable state are measured; according to the actually-measured cable core and surface temperatures of the cable, heat capacity and heat resistance heat parameters in the cable differential equation are fit through a trust region algorithm; finally according to the fit heat parameters, a cable temperature transient heat circuit is solved, the cable temperature is obtained, and a calculation equation is simplified.According to the rapid cable temperature calculation method based on parameter fitting, transient heat parameters of a conversion model can be rapidly acquired in combination with the actually-measured temperatures under the rated transmission capacity of the cable, the simplified calculation equation of the cable core and surface temperatures of the cable is obtained, and the purpose of rapidly calculating the cable temperature is achieved.
Owner:CHINA THREE GORGES UNIV
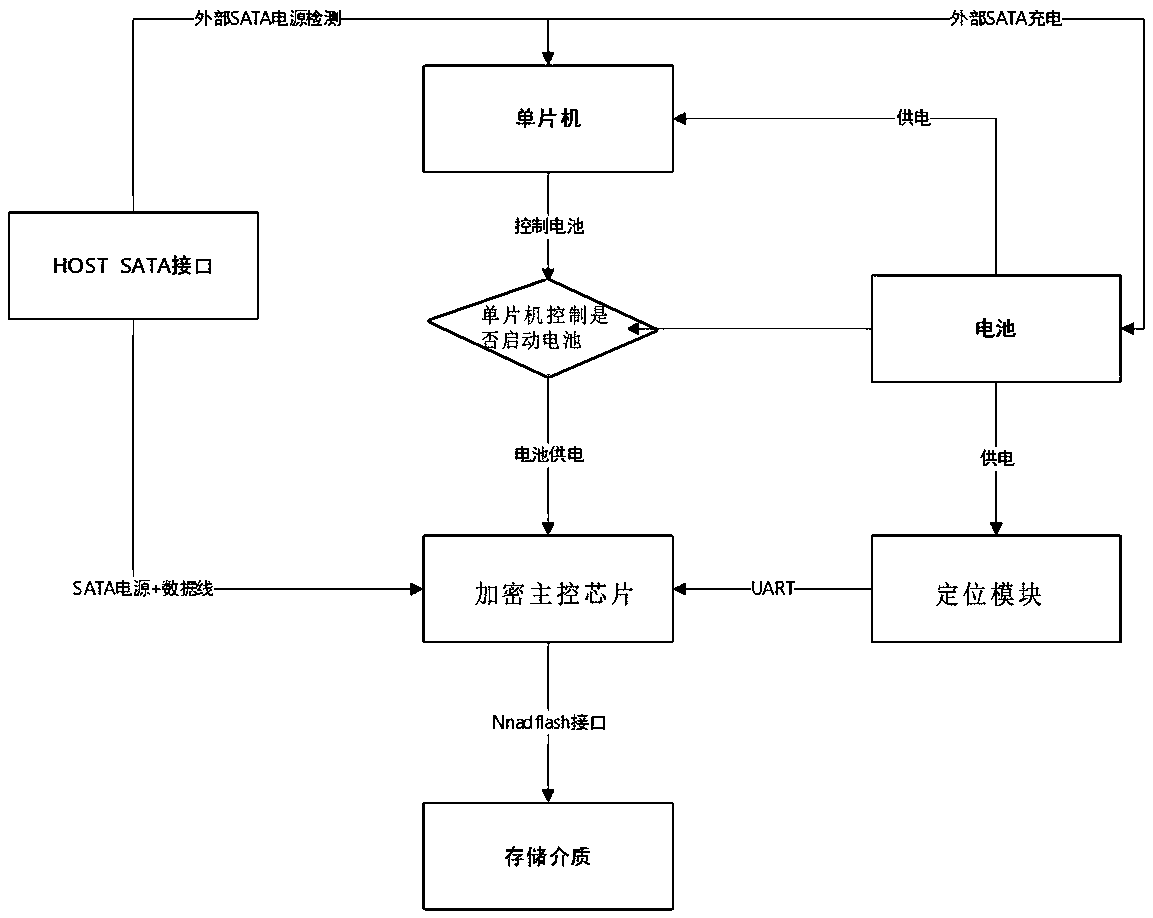
Mobile encrypted hard disk with electronic fence function, and encryption method
InactiveCN108388810ADigital data protectionInternal/peripheral component protectionMicrocomputerMicrocontroller
The invention discloses a mobile encrypted hard disk with an electronic fence function, and an encryption method. The encrypted hard disk comprises an encryption main control chip and a storage mediumconnected with the encryption main control chip; a trusted region and / or an illegal region is arranged in the encryption main control chip; the encryption main control chip is connected with a locating module for detecting the position of the mobile encrypted hard disk; the encryption main control chip regularly performs polling on the locating module to obtain position information, thereby judging whether the mobile encrypted hard disk is located in the trusted region or the illegal region; the encrypted hard disk further comprises an offline power supply module; the offline power supply module comprises a battery, a battery management chip and a single-chip microcomputer; the battery is connected with the battery management chip; connection points between the battery and the battery management chip are connected to the encryption main control chip and the locating module through different PMOS transistors respectively; and a gate pole of the PMOS transistor connected with the encryption main control chip is connected to an I / O port of the single-chip microcomputer.
Owner:SHANDONG SINOCHIP SEMICON
Calibration method and device of three-dimensional laser scanning system, and computer equipment
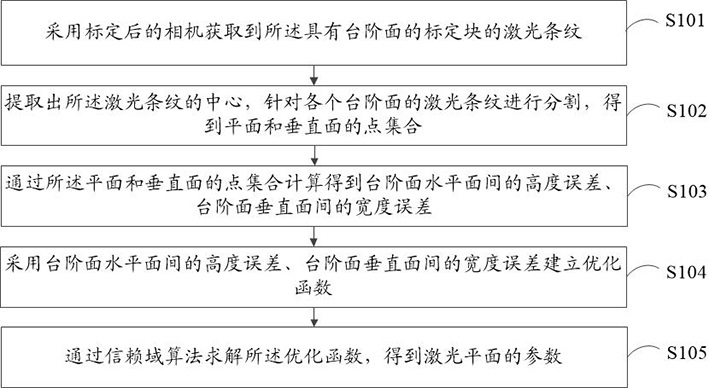
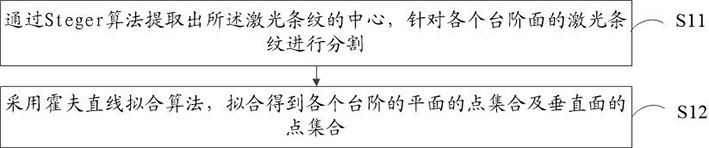
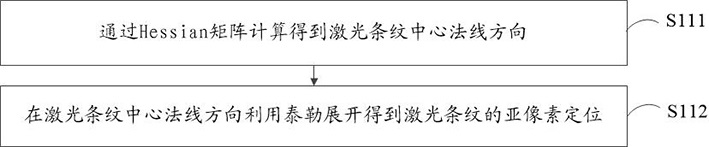
ActiveCN113494893AImprove efficiencyEasy to operateImage analysisUsing optical meansLaser transmitterVertical plane
Embodiments of the invention provide a calibration method and device for a three-dimensional laser scanning system, and computer equipment. The three-dimensional laser scanning system comprises a camera, a laser transmitter and a calibration block with step surfaces. The calibration method comprises the following steps: acquiring laser stripes of the calibration block with the step surfaces by adopting the camera which has been calibrated; extracting the center of the laser stripes, and segmenting the laser stripes on each step surface to obtain point sets of planes and vertical planes; calculating height errors between the horizontal planes of the step surfaces and width errors between the vertical planes of the step surfaces through the point sets of the planes and the vertical planes; establishing an optimization function by adopting the height errors between the horizontal planes of the step surfaces and the width errors between the vertical planes of the step surfaces; and solving the optimization function through a trust region algorithm to obtain parameters of a laser plane. According to the invention, the calibration and parameter optimization of a line laser three-dimensional measurement system can be completed only by using one step surface, operation is simple, efficiency is high, the method is suitable for field operation, and a result is accurate.
Owner:深圳广成创新技术有限公司
Two-stage planning algorithm of electromagnetics scheme for double-winding continuous coil power transformers
The invention discloses a novel optimization computation theory and algorithm for double-winding continuous coil power transformers. Optimization computation of a transformer includes two stages; in the first stage, value spaces determined by core diameter and a number of windings is traversed, coil height is used as an auxiliary variable, a standard short-circuit impedance value is used as a known condition, each value space is computed to judge whether a solution space exists or not, and if yes, locally optimal solutions and target function values are computed for the solution space; in the second stage, the locally optimal solutions are used as center points to determine a variation range of a design variable and construct a trust region, and reciprocals of the target function values of the locally optimal solutions are used as trust levels; the trust regions of high trust levels form a trust region set, each trust region in the set is traversed and locally searched to find out all locally optimal solutions, and a globally optimal solution is obtained finally. By making full use of solution space characteristics in transformers, the algorithm is direct, reliable and highly computationally efficient.
Owner:ZHONGYUAN ENGINEERING COLLEGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com