Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
304 results about "Bandwidth limitation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
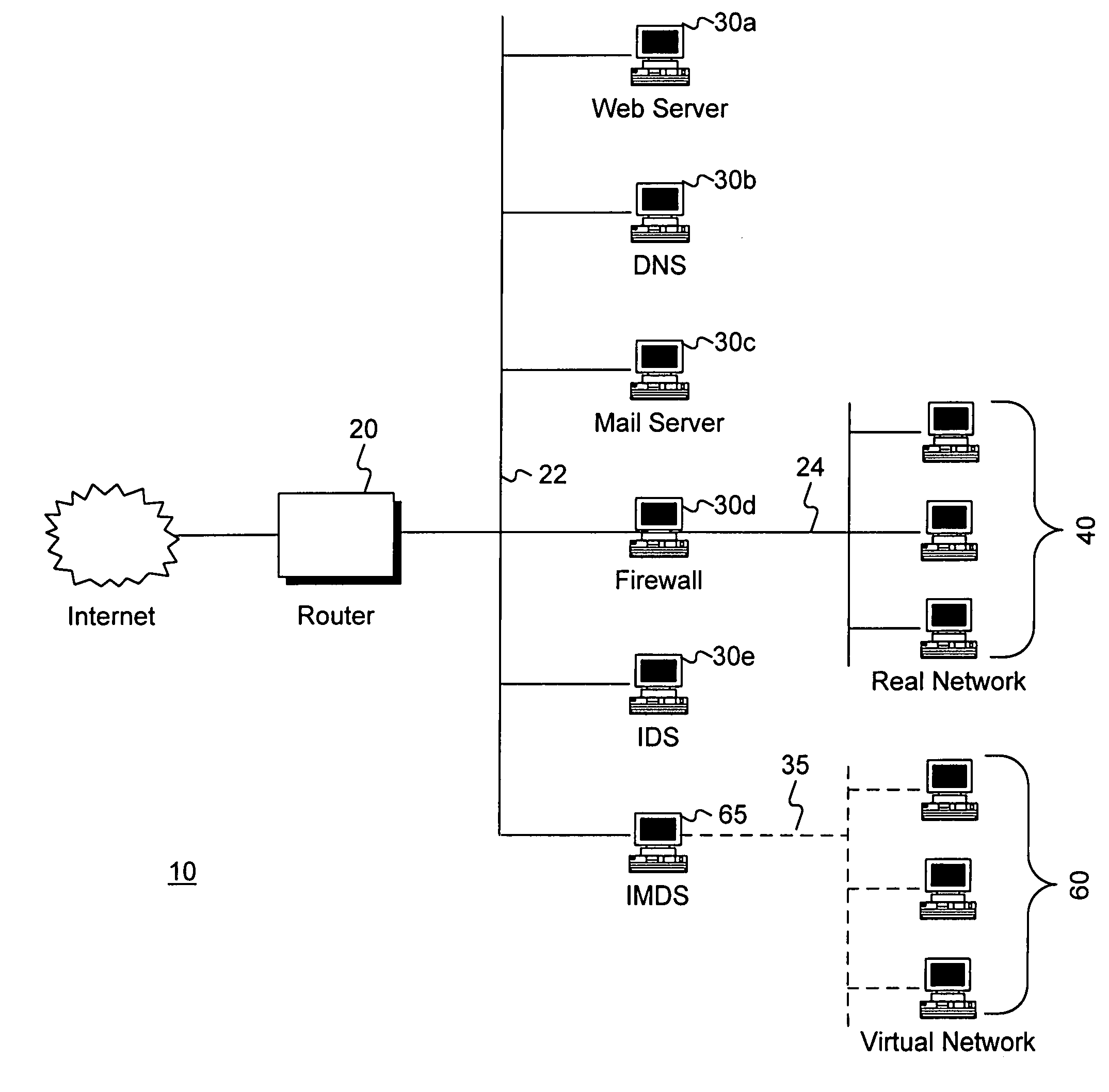
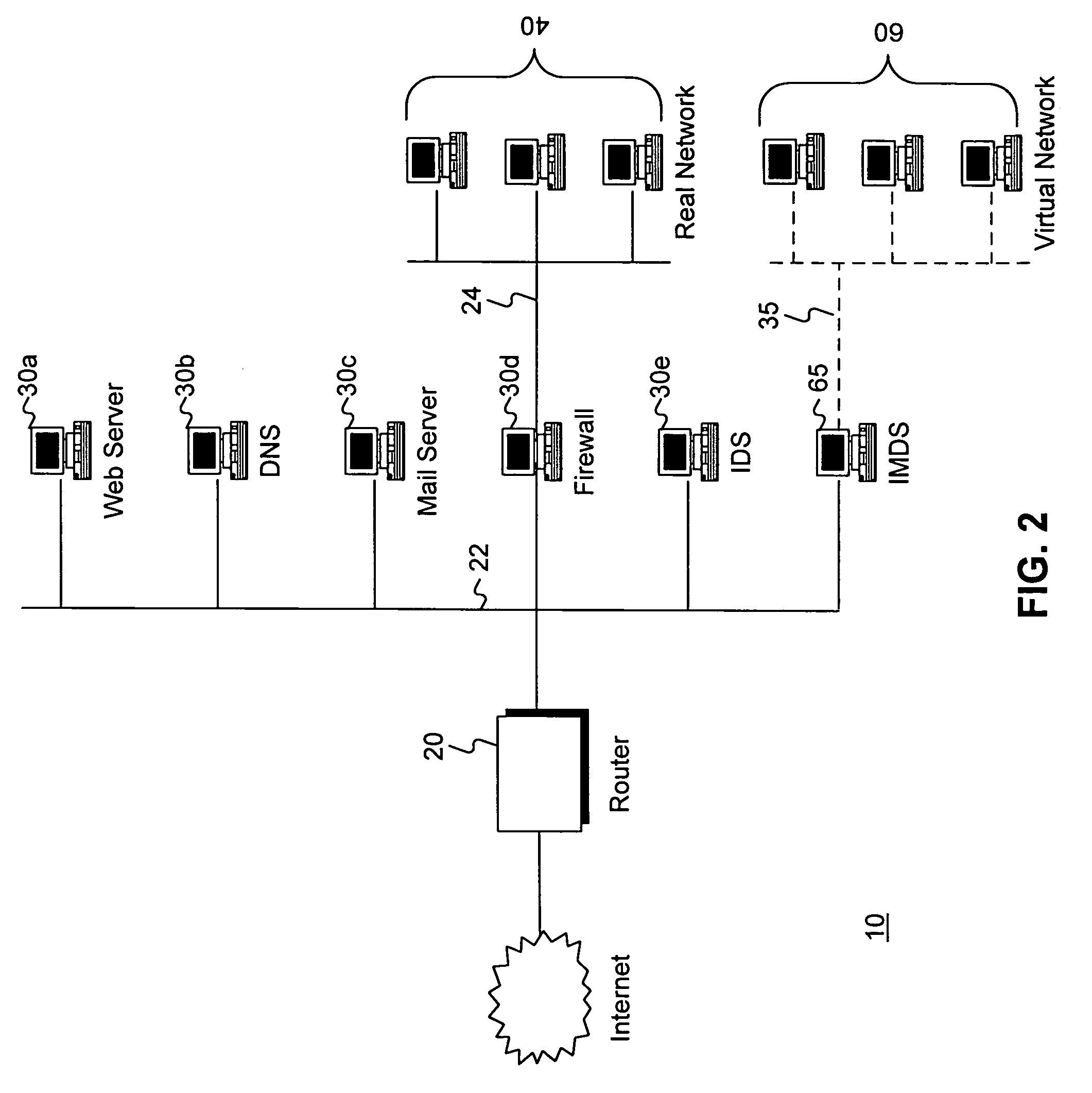
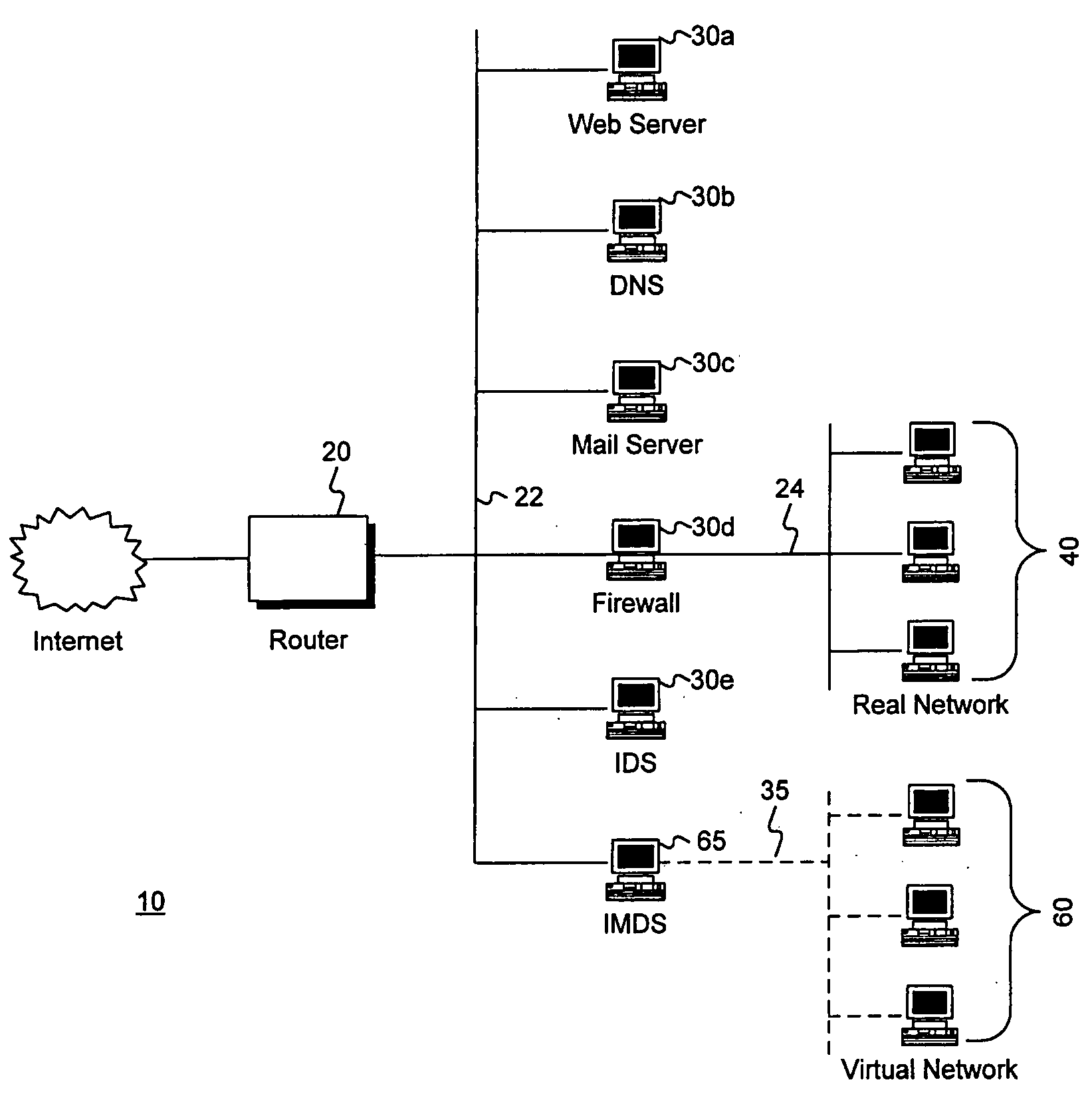
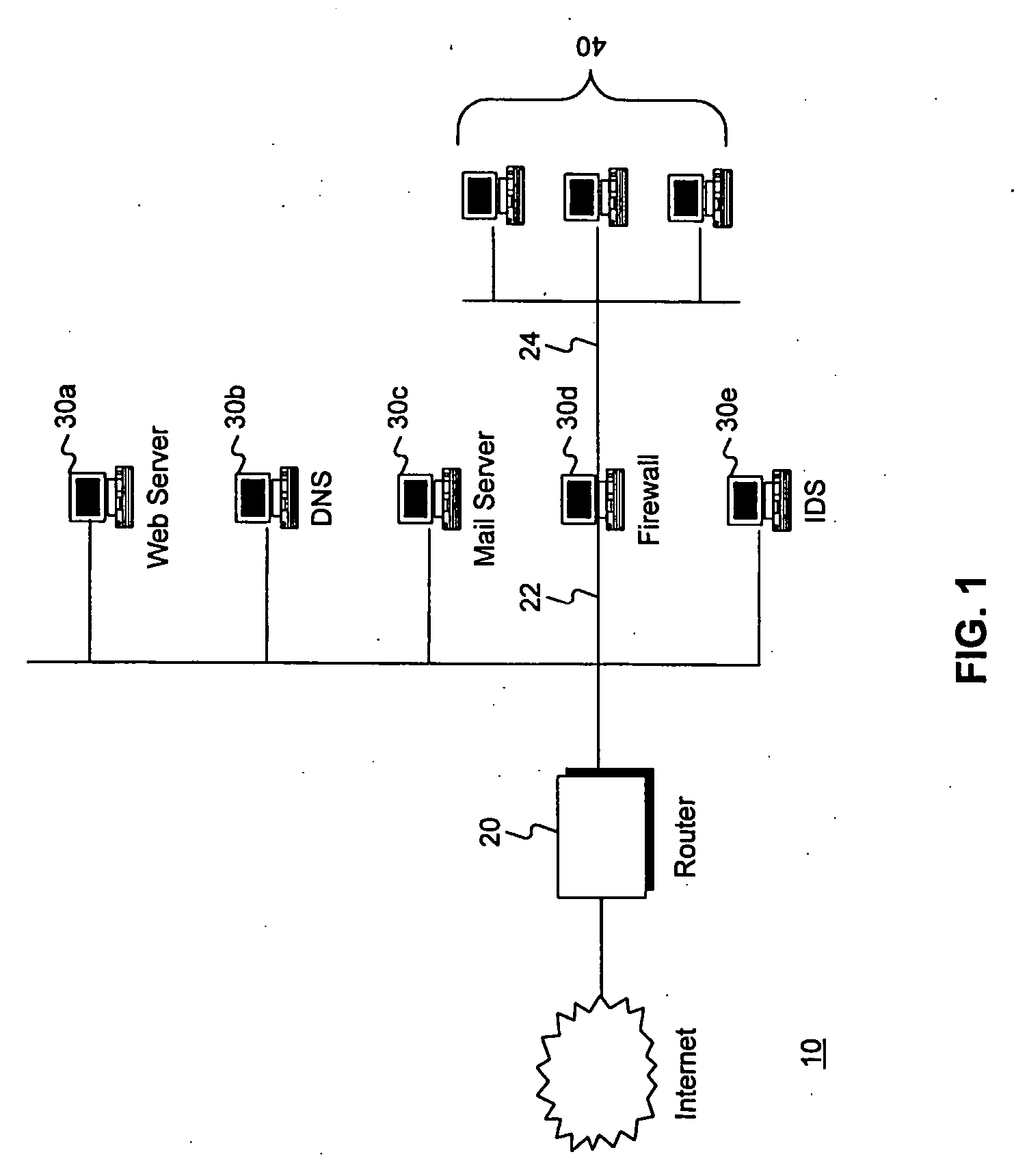
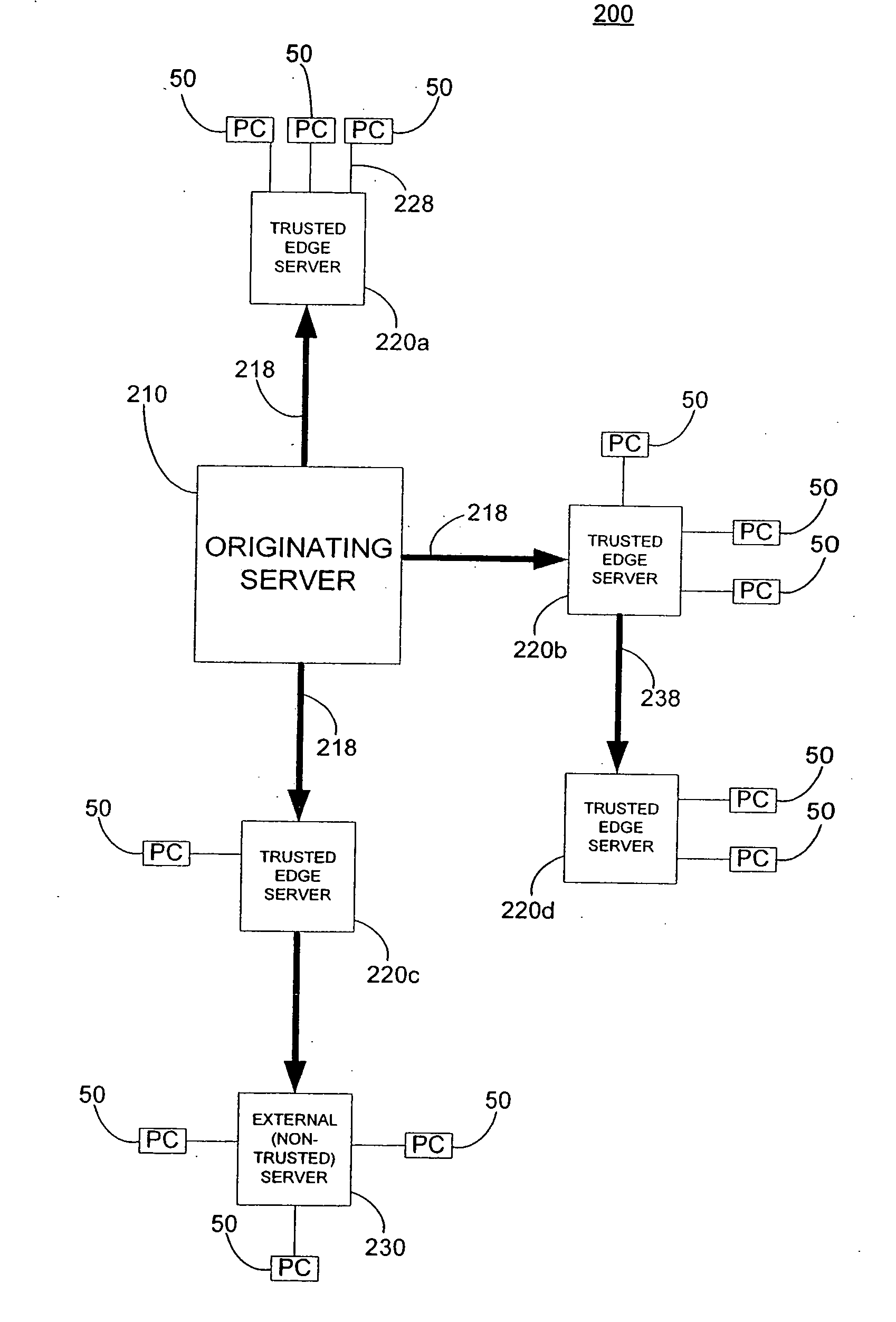
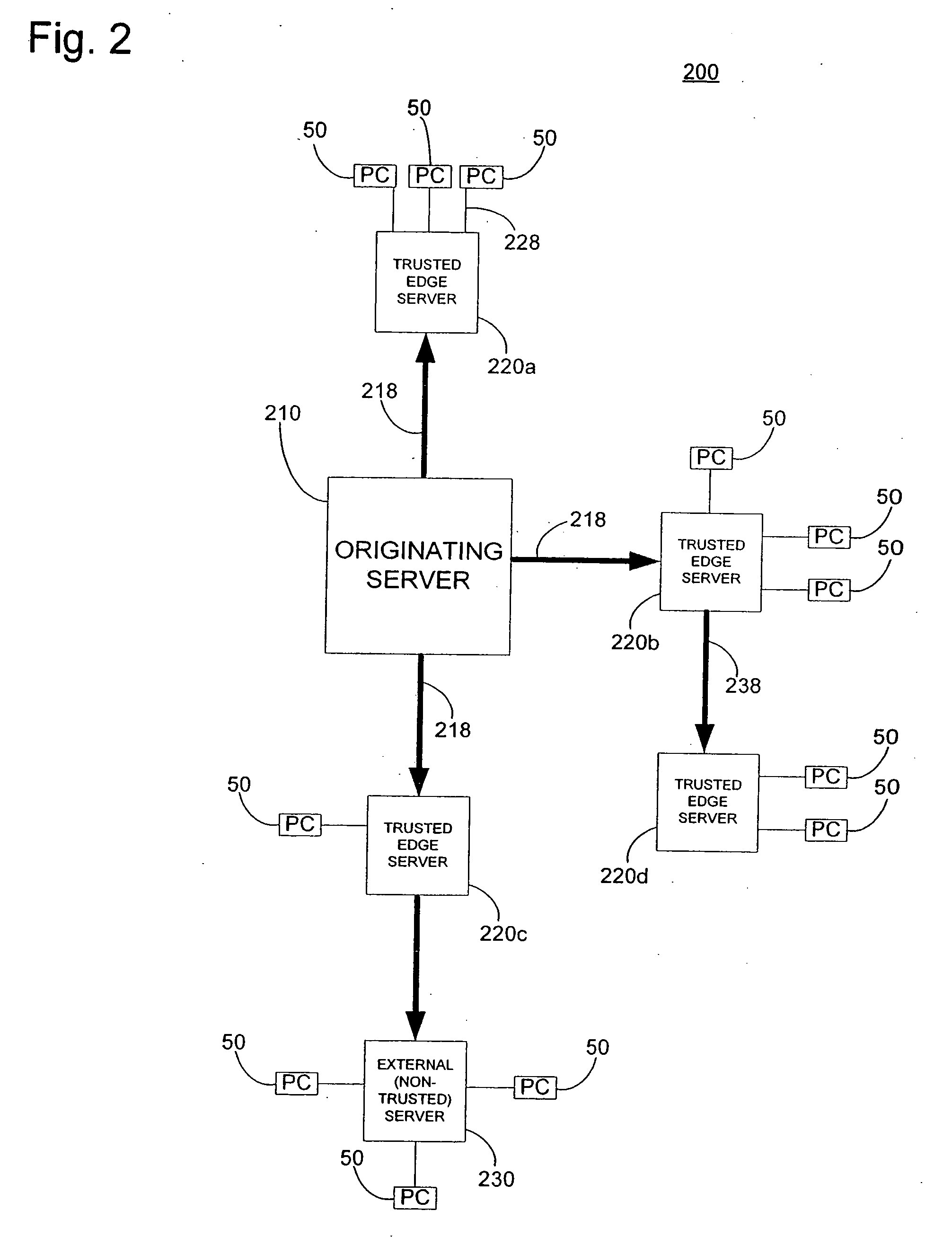
Intrusion and misuse deterrence system employing a virtual network
InactiveUS7240368B1Improve securityEasy to implementMemory loss protectionError detection/correctionIp addressBandwidth limitation
A method and apparatus is disclosed for increasing the security of computer networks through the use of an Intrusion and Misuse Deterrence System (IMDS) operating on the network. The IMDS is a system that creates a synthetic network complete with synthetic hosts and routers. It is comprised of a network server with associated application software that appears to be a legitimate portion of a real network to a network intruder. The IMDS consequently invites inquiry and entices the intruder away from the real network. Simulated services are configured to appear to be running on virtual clients with globally unique, class “C” IP addresses. Since there are no legitimate users of the virtual network simulated by the IMDS, all such activity must be inappropriate and can be treated as such. Consequently, the entire set of transactions by an intruder can be collected and identified rather than just those transactions that meet a predefined attack profile. Also, new exploits and attacks are handled just as effectively as known attacks, resulting in better identification of attack methodologies as well as the identification and analysis of new attack types. Since the IMDS only has to be concerned with the traffic going to its simulated hosts it additionally eliminates the bandwidth limitation that plagues a traditional intrusion detection system (IDS).
Owner:VERIZON SERVICES GROUP +2
Content delivery for client-server protocols with user affinities using connection end-point proxies
ActiveUS20050125553A1Services signallingMultiple digital computer combinationsBandwidth limitationIndependent data
In a network supporting transactions between clients and servers over a network path having operating characteristics to overcome, data is transported to overcome the operating characteristics using user affinities and dynamic user location information to selectively preload data, or representations, signatures, segments, etc. of data, in order to overcome the one or more operating characteristic. Examples of operating characteristics to overcome include bandwidth limitations, errors and latency. The dynamic location information can be stored in data structures accessible by agents of a data server and the data structures are populated based on user activities with respect to proxies associated with user locations, or the dynamic location information can be obtained implicitly as proxies maintain connections after termination by clients and the use of those maintained connections for preloading of data for the users associated with those clients. The data being preloaded can be protocol-specific data or protocol-independent data.
Owner:RIVERBED TECH LLC
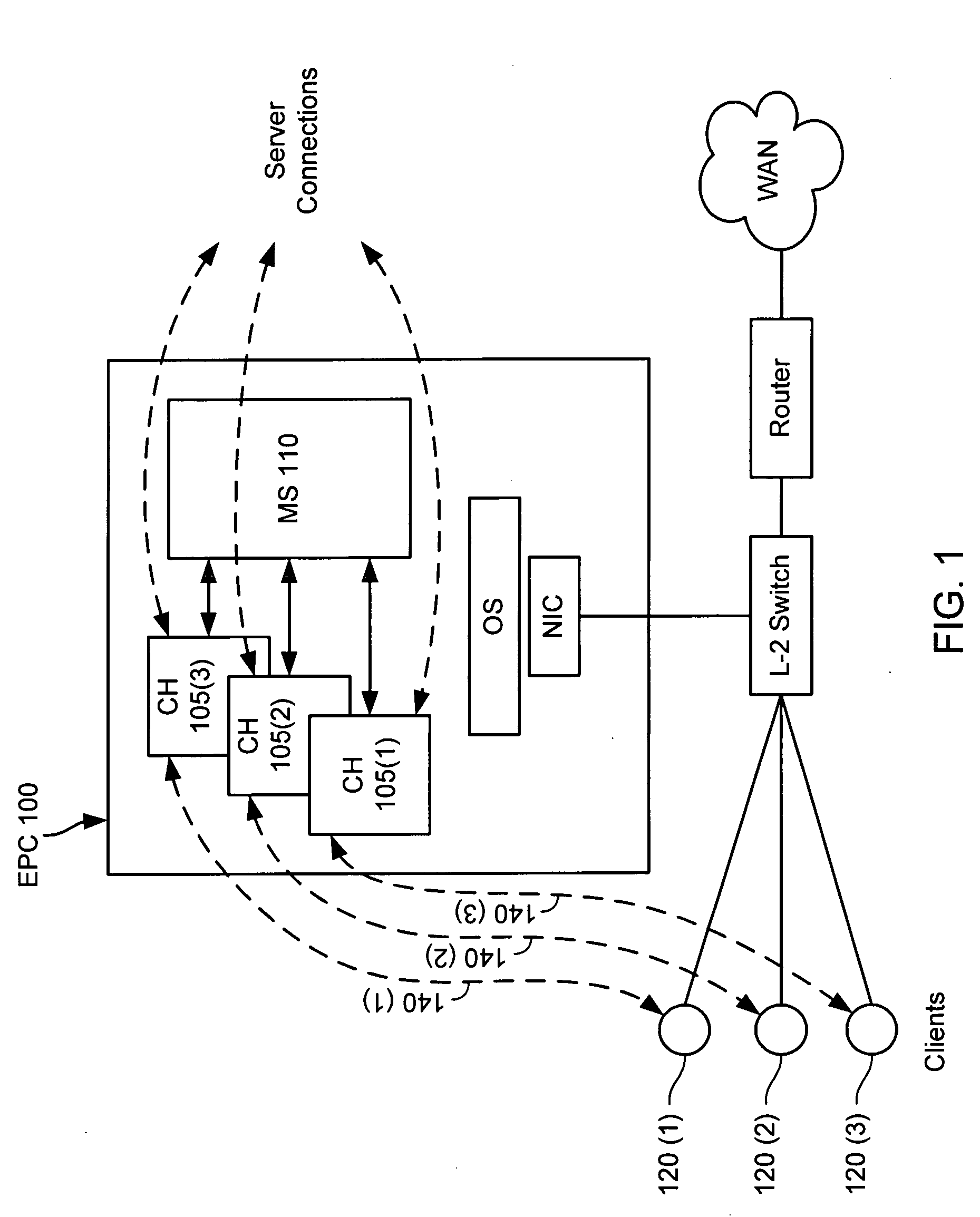
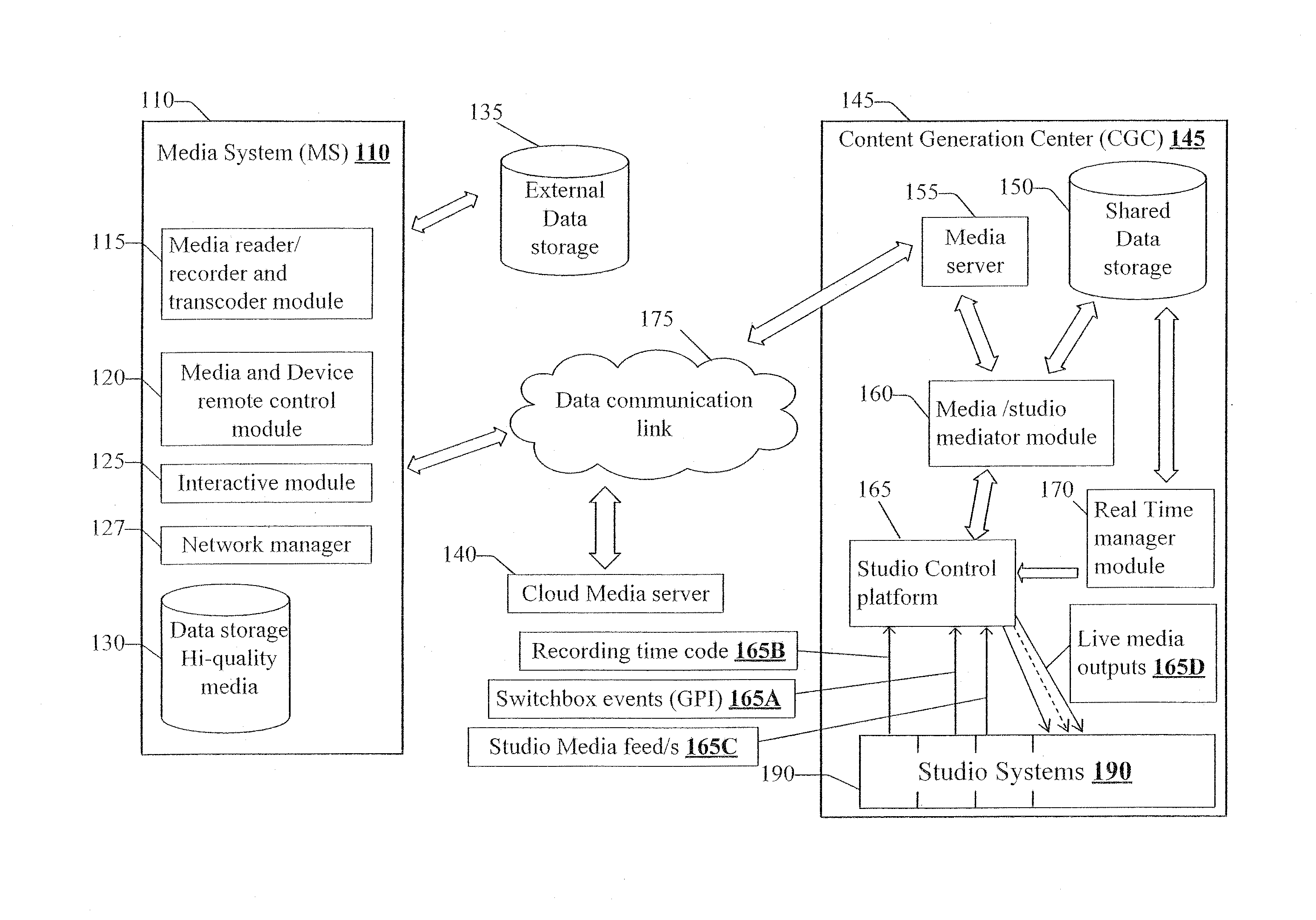
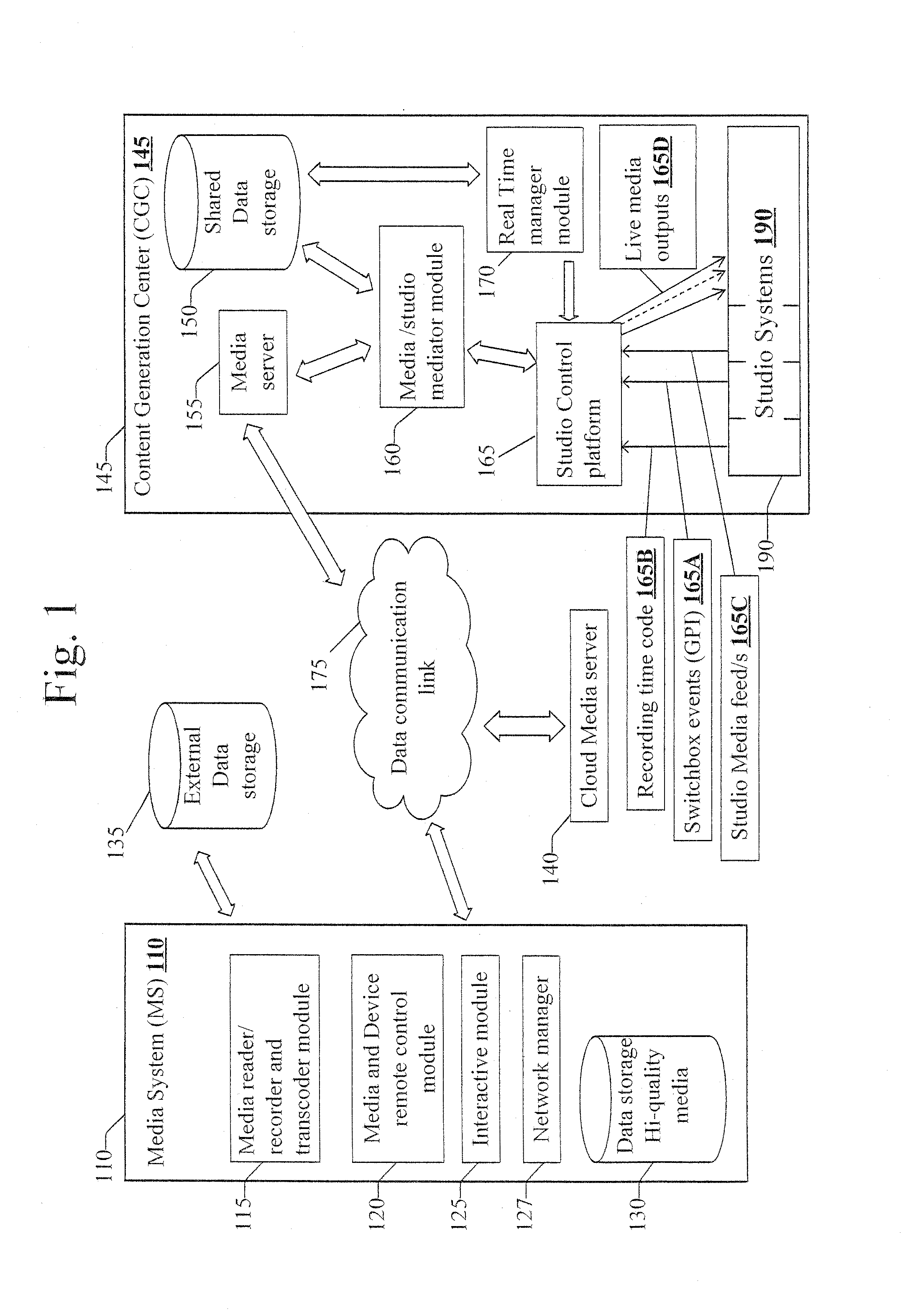
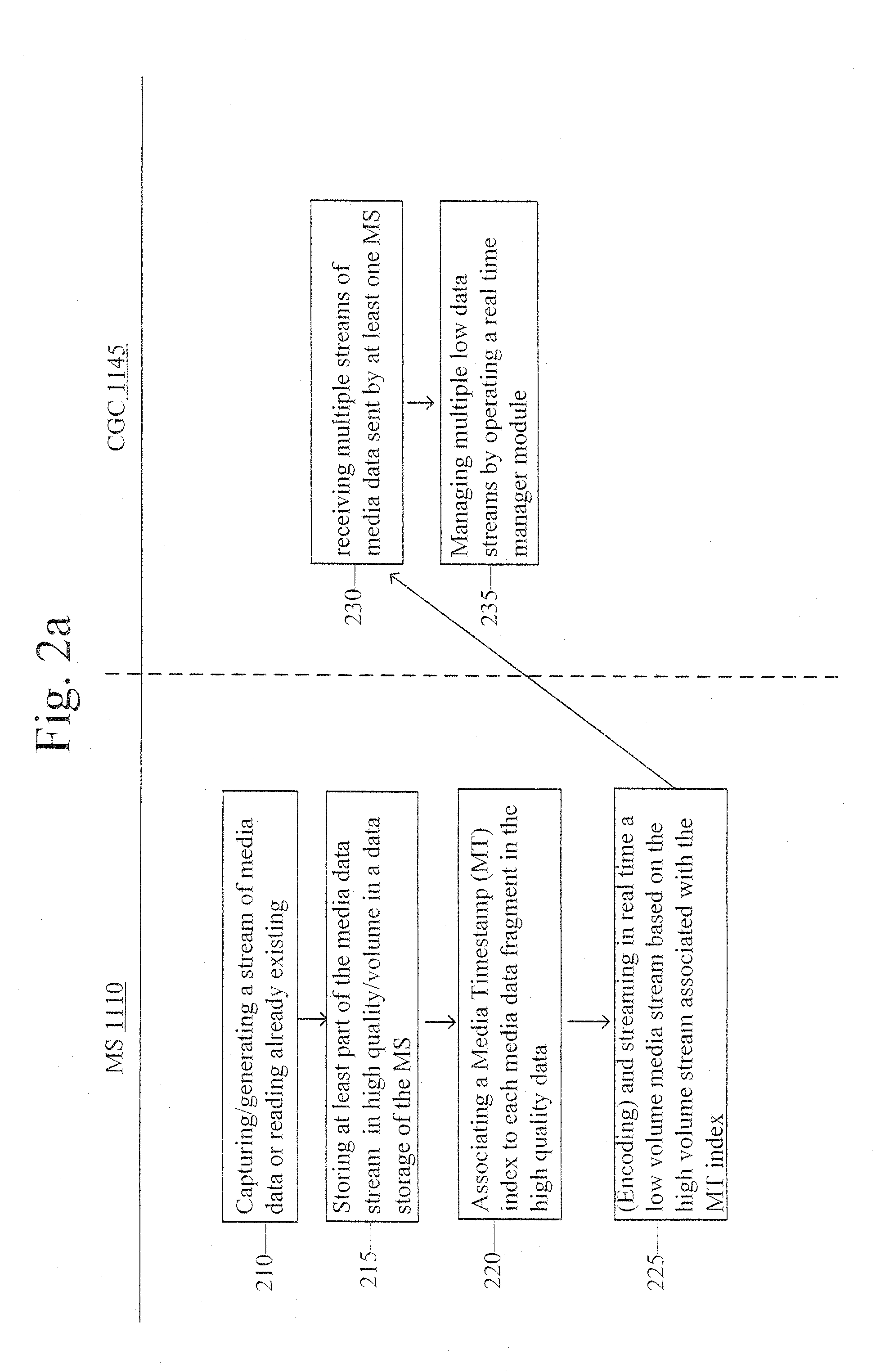
Method and system for central utilization of remotely generated large media data streams despite network bandwidth limitations
ActiveUS20130290557A1Quality improvementImprove practicalityElectronic editing digitised analogue information signalsMultiple digital computer combinationsData streamComputer network
A computerized method for integrating media streams from a multiplicity of media systems over at least one network into a single media product at high media technical quality, the method comprising the steps of, at certain media systems from among the multiplicity thereof: a. Generating a low volume (LV) media stream representation from a high volume media stream, where the low volume stream's bit-rate is different from the high volume stream's bit-rate; b. streaming the low volume media stream to a content generation center via a data communication network; c. Maintaining high volume local data as a high volume media stream in a storage medium coupled to at least one of the media systems; and d. maintaining mapping information between the low volume stream and the high volume local data for enabling access to media portions in the high volume media stream storage, which correspond based on LV stream time.
Owner:MOBILATV
DYNAMIC QoS IN A NETWORK DISTRIBUTING STREAMED CONTENT
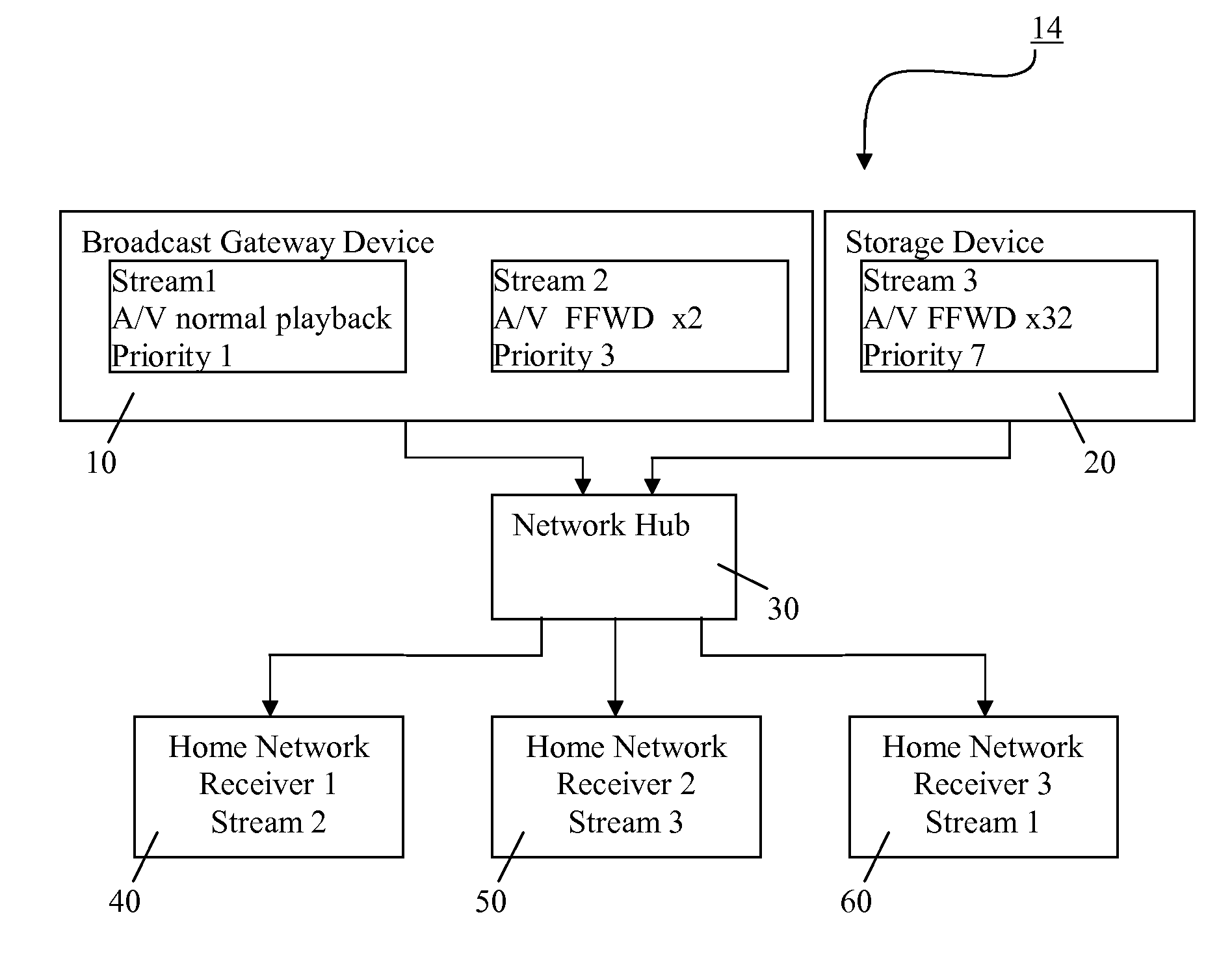
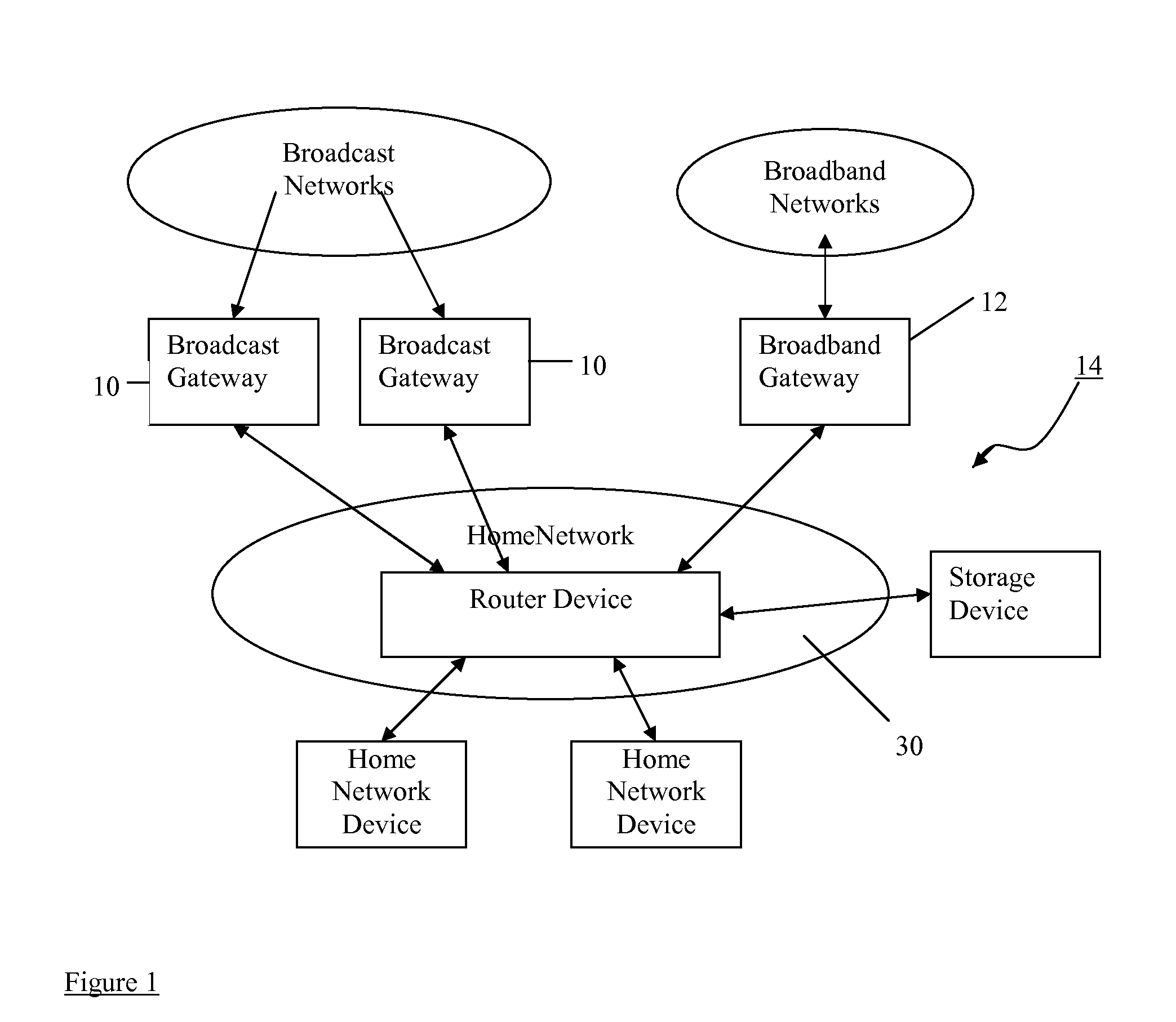
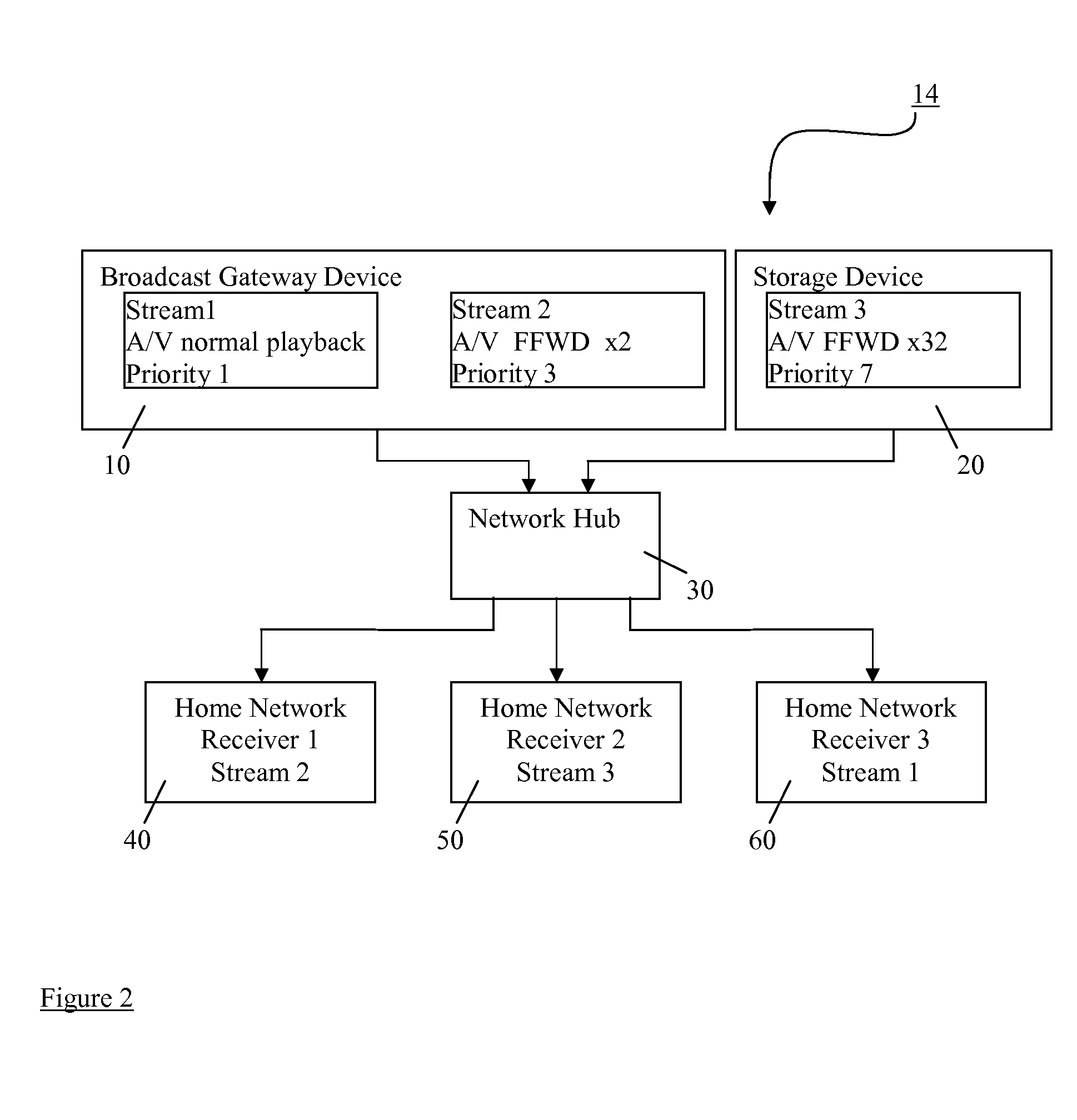
ActiveUS20110179455A1Lower throughput rateLow priorityEnergy efficient ICTClosed circuit television systemsHard disc driveComputer network
In a home network a number of receiving devices are connected to receive streamed audio visual content from one or more sources by way of a network hub. One source is a set top box, having a hard disc drive, which provides a real time broadcast stream, stream 1, as well as a recorded output stream, stream 2. Another source is local storage which is capable of outputting its stored content, stream 3, at x32 normal speed, that is, fast forward. If there are bandwidth limitations on the network then the receiver (receiving the fast forward stream 3 will experience errors. When errors are detected, the receiver sends a message back to the source which then takes action to reduce the bit rate of its output stream.
Owner:DISH TECH L L C
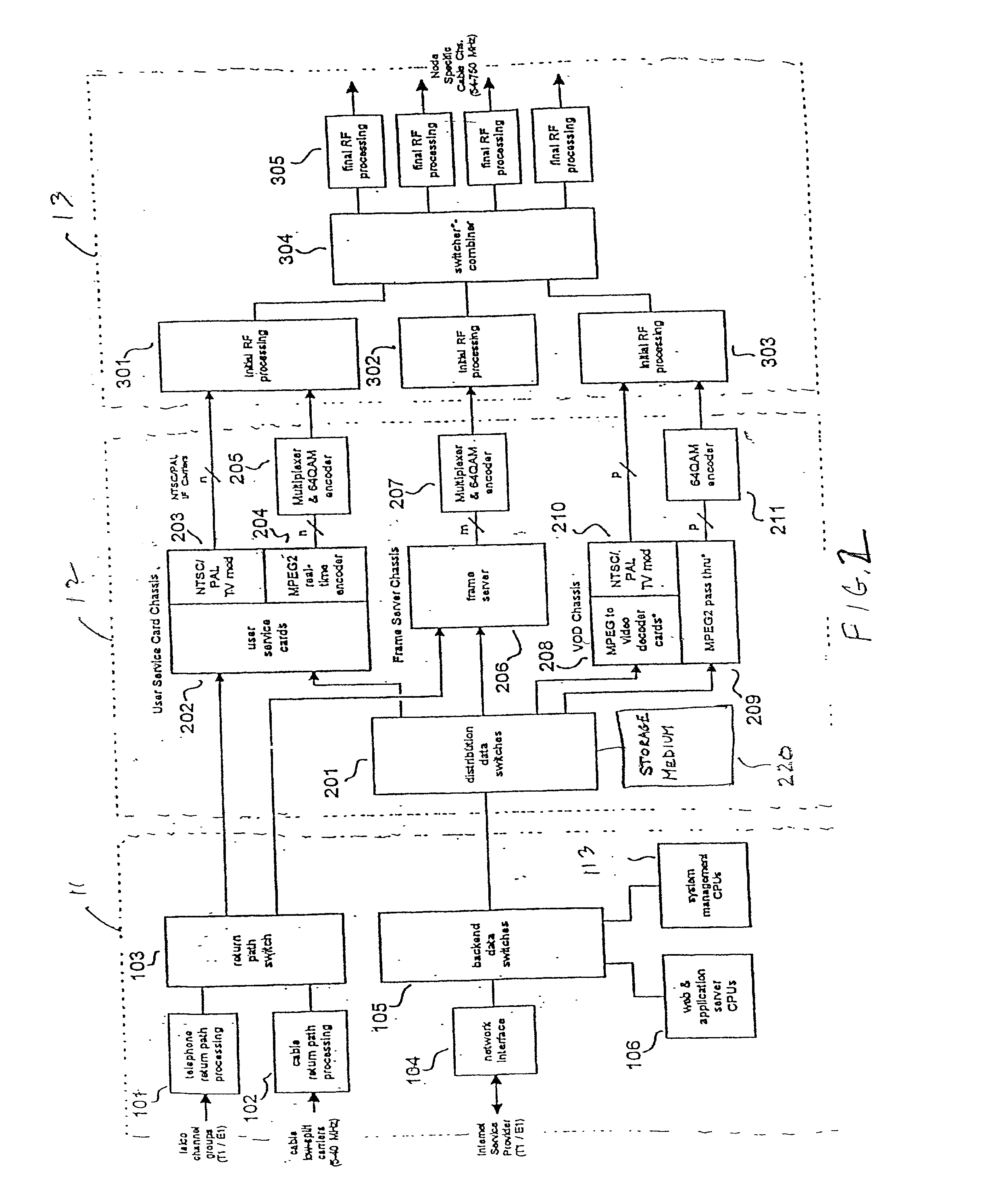
High capacity, low-latency multiplexer
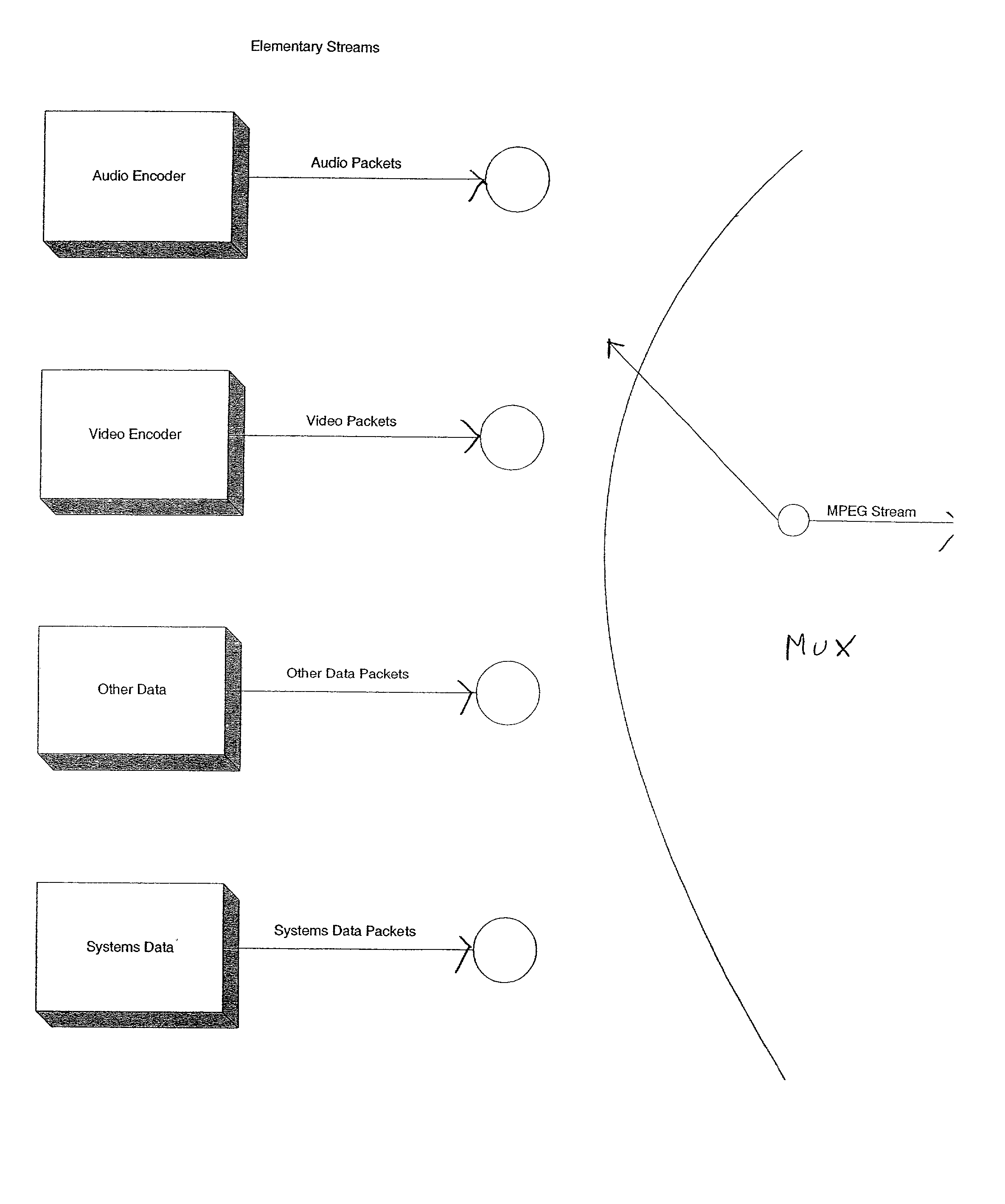
InactiveUS20020080267A1Color television with pulse code modulationPulse modulation television signal transmissionData streamFrame time
A method for multiplexing compressed video data streams where the time for sending portions of a video frame are adjusted to reduce latency. If a compressed frame cannot be delivered in the appropriate frame time, due to bandwidth limitations, the frame is broken into parts and a part is sent in an earlier frame time. This method allows complete frames to be available at a receiver at the correct time. Accurate methods of deriving clock signals from the data stream are also described.
Owner:ACTIVE VIDEO NETWORKS INC
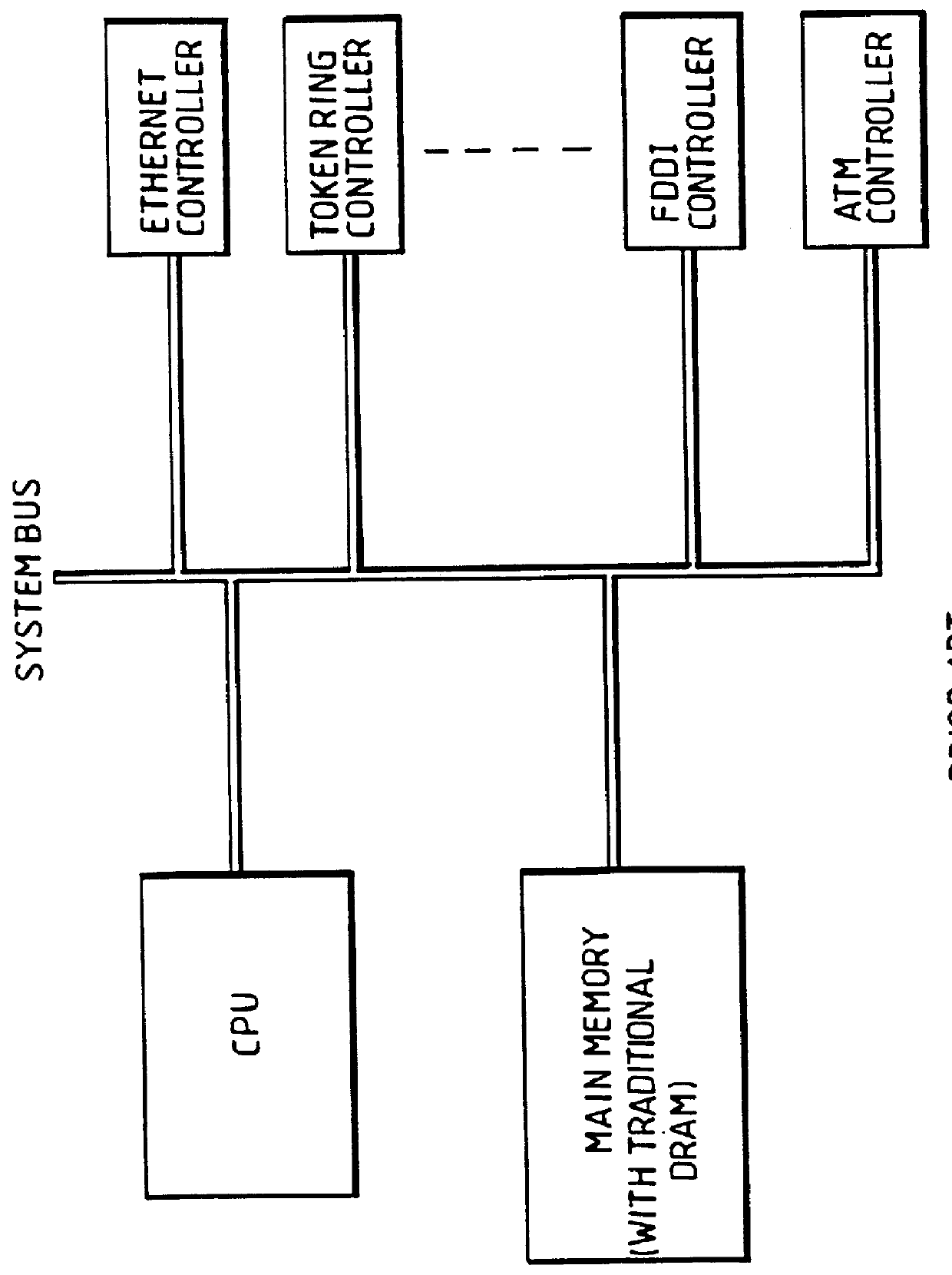
Multi-port internally cached DRAM system utilizing independent serial interfaces and buffers arbitratively connected under a dynamic configuration to allow access to a common internal bus
InactiveUS6108725AImprove system performanceLow costMemory adressing/allocation/relocationCathode-ray tube indicatorsGraphicsComputer architecture
A novel low cost / high performance multi-port internally cached dynamic random access memory architecture called 'AMPIC DRAM', and consequentially a unique system architecture which eliminates current serious system bandwidth limitations, providing a means to transfer blocks of data internal to the chip, orders of magnitude faster than the traditional approach, and with the chip also interconnecting significantly higher numbers of resources with substantially enhanced performance and at notably lower cost. Through use of a system configuration based on this novel architecture and working equally efficiently for both main memory functions and as graphics memory, thus providing a truly low cost, high performance unified memory architecture.
Owner:CHATTER MUKESH
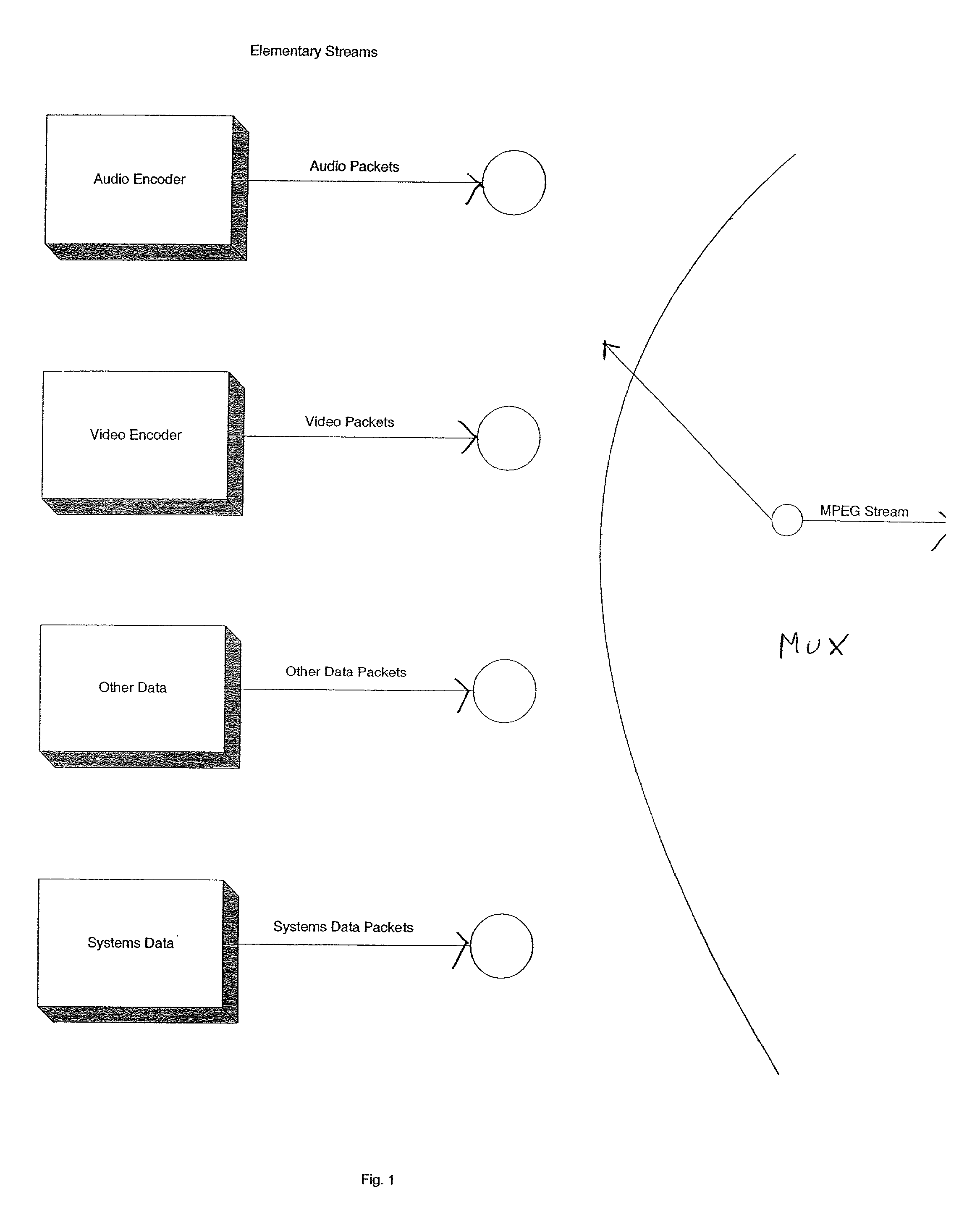
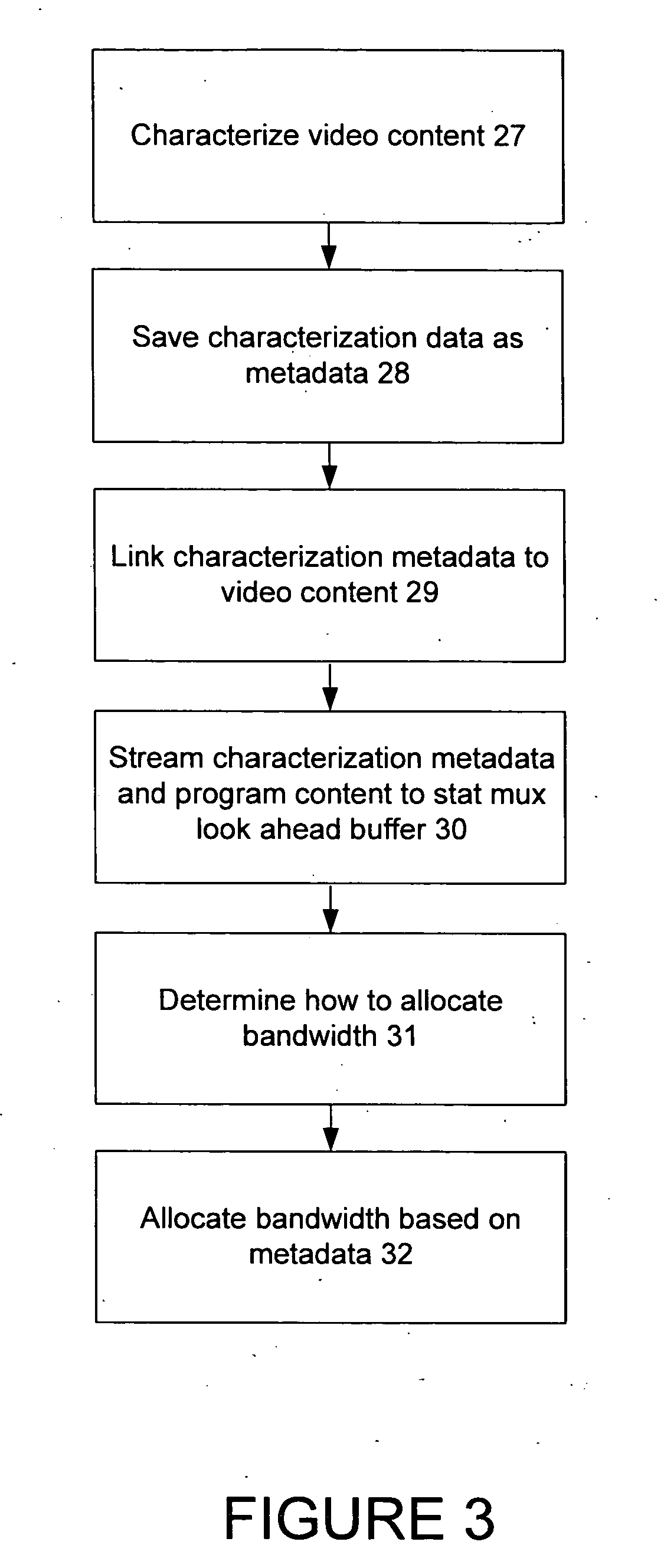
Statistical remultiplexer performance for video on demand applications by use of metadata
ActiveUS20060067362A1Improve performanceLower latencyError preventionFrequency-division multiplex detailsBandwidth limitationComputer science
The present invention improves the performance of video on demand (VOD) in a digital cable system. A statistical remultiplexer (stat mux) acquires metadata that statistically describes the bandwidth characteristics of each VOD channel. When the metadata indicates that the VOD channel will require more bandwidth than is available, the stat mux can re-encode or re-compress other streams or the VOD stream streams to meet the bandwidth limitation. The metadata is generated off-line and streamed out ahead of the VOD program content. The stat mux includes a minimal length buffer for storing VOD program content that when combined with the metadata enables a viewer to randomly access VOD program content without noticeable latency. When a VOD function request is received from the viewer, the previously supplied metadata is used to allocate bandwidth rather than waiting for a look-ahead buffer to acquire a sufficient amount of future VOD program content.
Owner:TRITON US VP ACQUISITION CO
Virtual video call method and terminals
InactiveCN103647922AEasy to adjustImprove experienceTwo-way working systemsAcquiring/recognising facial featuresPattern recognitionBandwidth limitation
The invention provides a virtual video call method and terminals. The method comprises the steps of collecting a video image of a first terminal user; performing facial recognition on the video image so as to obtain facial expression information; sending the facial expression information to a second terminal which establishes call connection with a first terminal, and enabling the facial expression information to be used for enabling the second terminal to synthesize and display video images according to the facial expression information and a facial image model pre-arranged on the second terminal. According to the method, a facial recognition technology is utilized to extract the facial expression information at a sending end such as the first terminal, and synthesis and restoration of the facial image are achieved at a receiving end such as the second terminal according to the sent facial expression information and a pre-arranged facial image module; due to the fact that the volume of transmitted facial expression data is extremely small, the volume of the data transmitted in the video call process is greatly reduced, video call is smoother, and the influence on the video call caused by network bandwidth limitation or flow limitation is reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Broadband polarized antenna including magnetodielectric material, isoimpedance loading, and associated methods
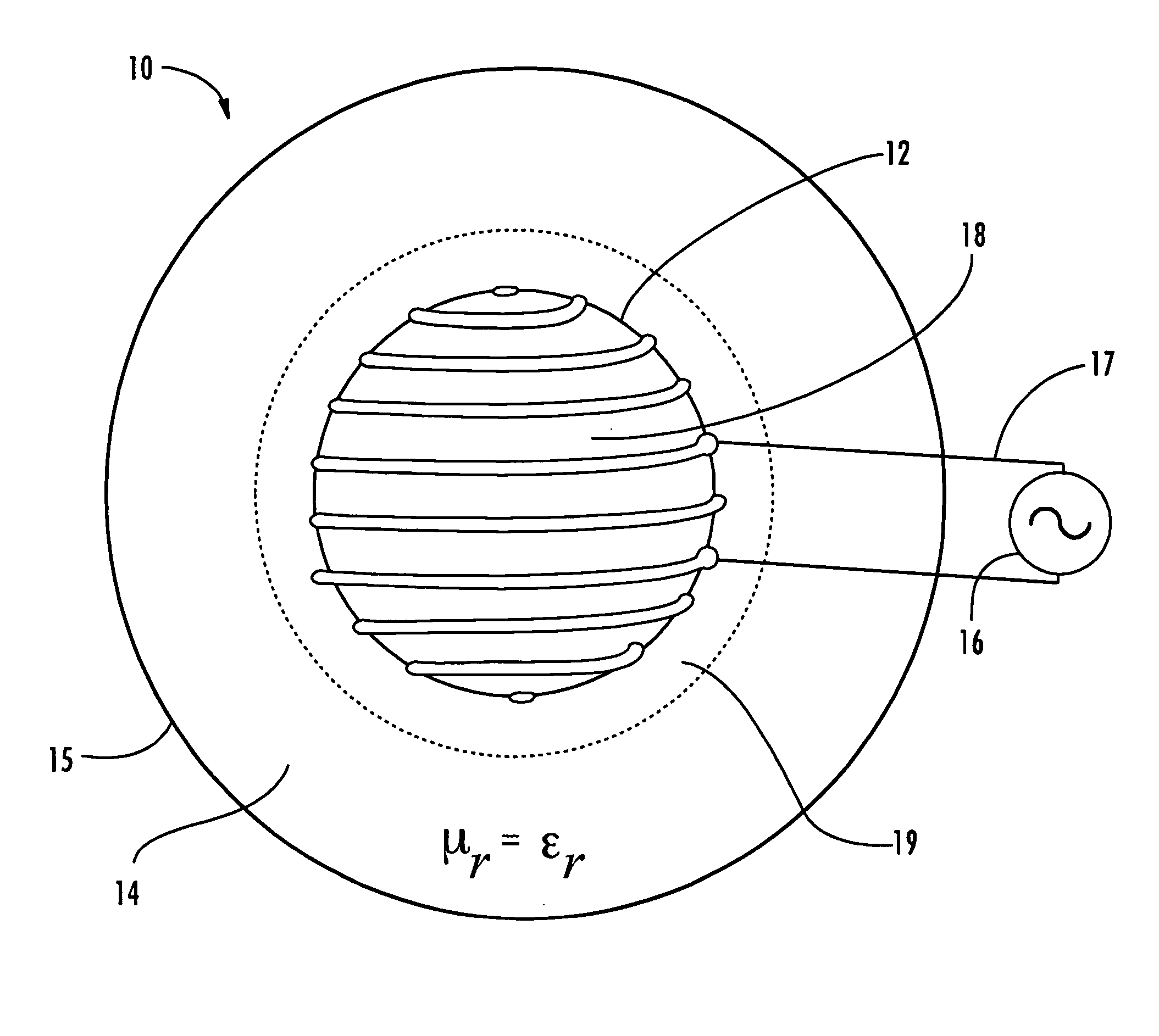
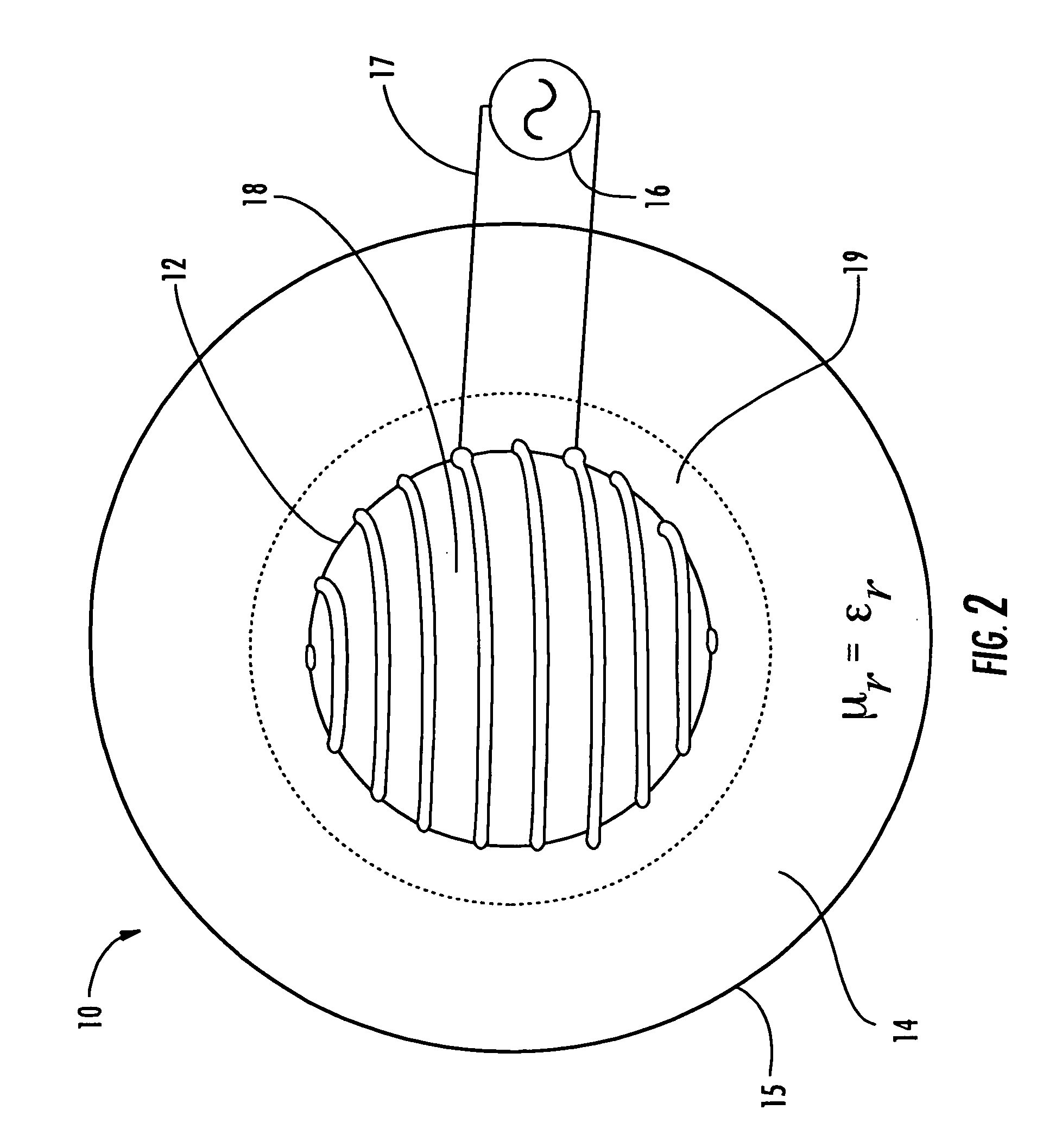
ActiveUS20070188397A1Loop antennas with ferromagnetic coreProtective material radiating elementsMiniaturizationBandwidth limitation
The broadband small antenna has equal magnetic electric proportions, circular polarization, and an isoimpedance magnetodielectric (μr≡εr) shell for controlled wave expansion. The shell is a radome without bandwidth limitation, with reflectionless boundary conditions to free space, providing loading and broad bandwidth antenna size miniaturization. The system is spherically structured based upon size, quality (Q) and bandwidth.
Owner:HARRIS CORP
Digital video surveillance
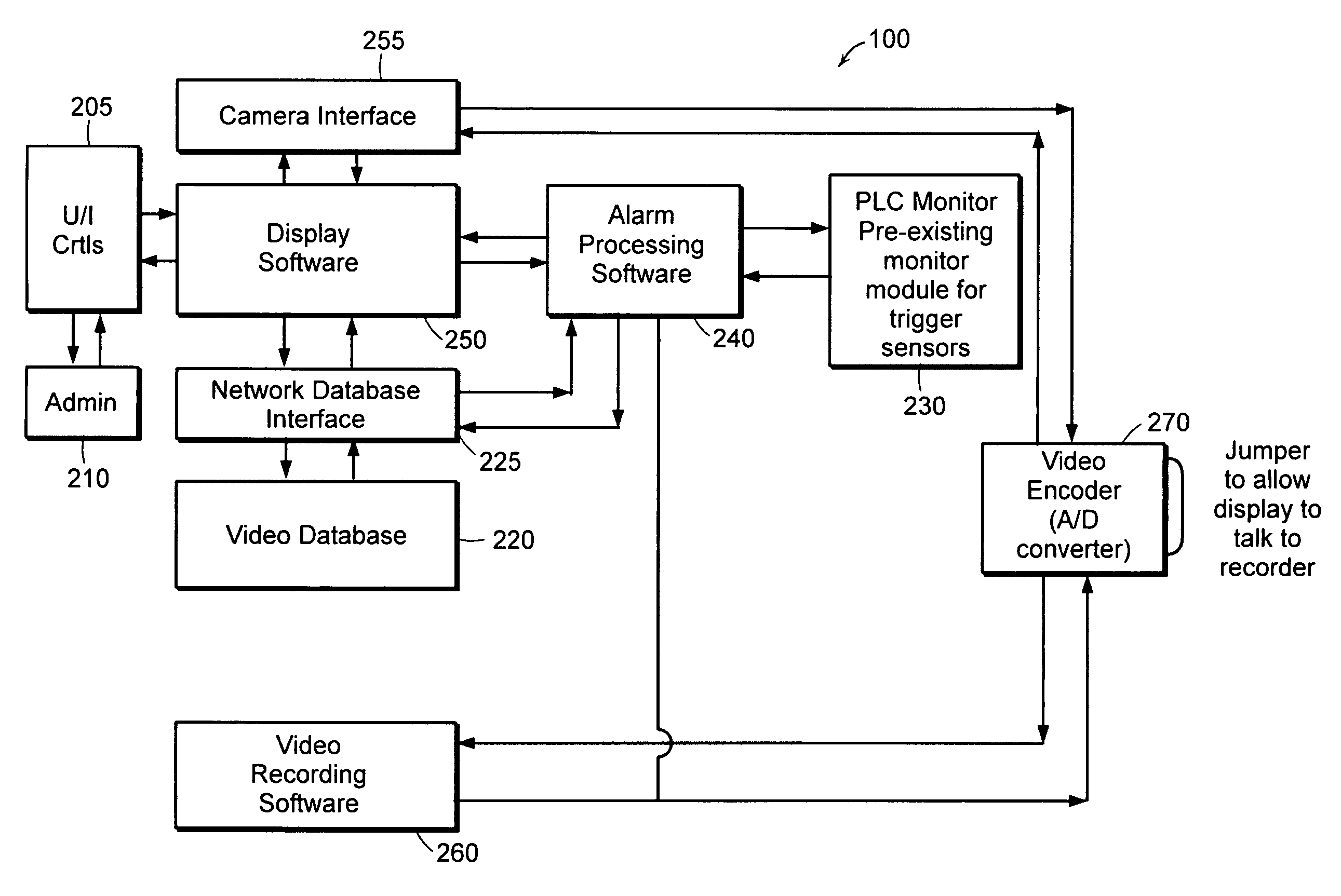
InactiveUS20050162268A1Reduce needConvenient access controlFrequency-division multiplex detailsTime-division multiplexDigital videoDigital data
A control system for use with one or more video surveillance cameras forming a video surveillance system. The control system includes a video database module wherein a database entry includes at least one sensor condition defining an alarm state for each camera. Additionally, there is an alarm condition module that receives one or more sensor signals from one or more sensors associated with a camera and retrieves the sensor condition defining an alarm state for the camera. The alarm condition module outputs an alarm signal if the alarm condition module determines that the one or more sensor signals meets the one or more sensor conditions. The control system is modular and may be distributed in a network environment. The control system also monitors the network bandwidth and can adjust the throughput of digital data representing the digital images in order to avoid any bandwidth limitations.
Owner:INTERGRAPH SOFTWARE TECH
Client capability adjustment
ActiveUS20090259766A1Multiple digital computer combinationsTransmissionBandwidth limitationClient-side
Mechanisms are provided to detect device client capabilities associated with screen size, video and audio codec support, bandwidth limitations, and memory limitations. A content server can intelligently select a media stream for transmission to the device using the client capability information for the device. In some instances, the content server presents prioritized selections to a user and the user can choose the optimal media stream.
Owner:TIVO CORP
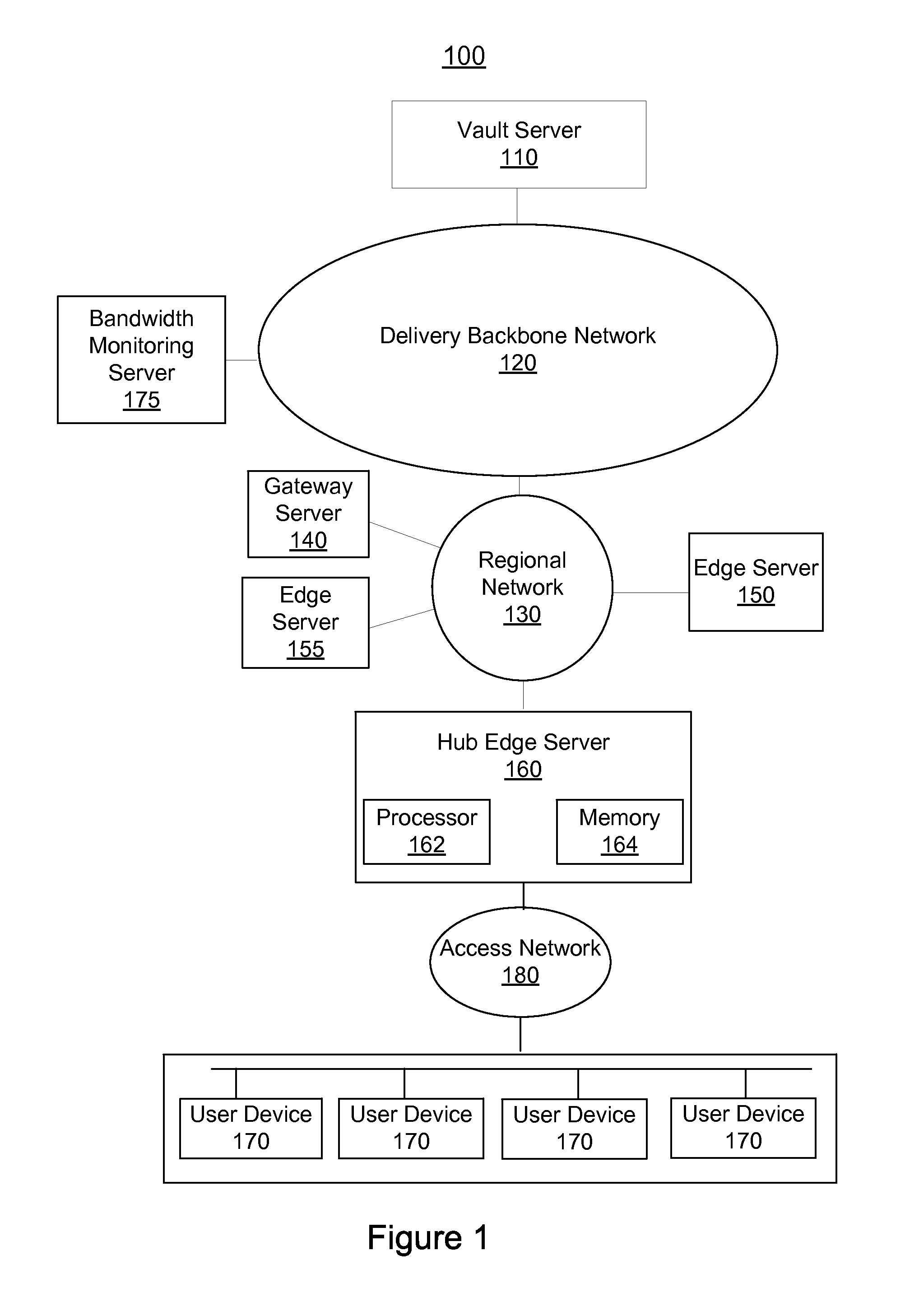
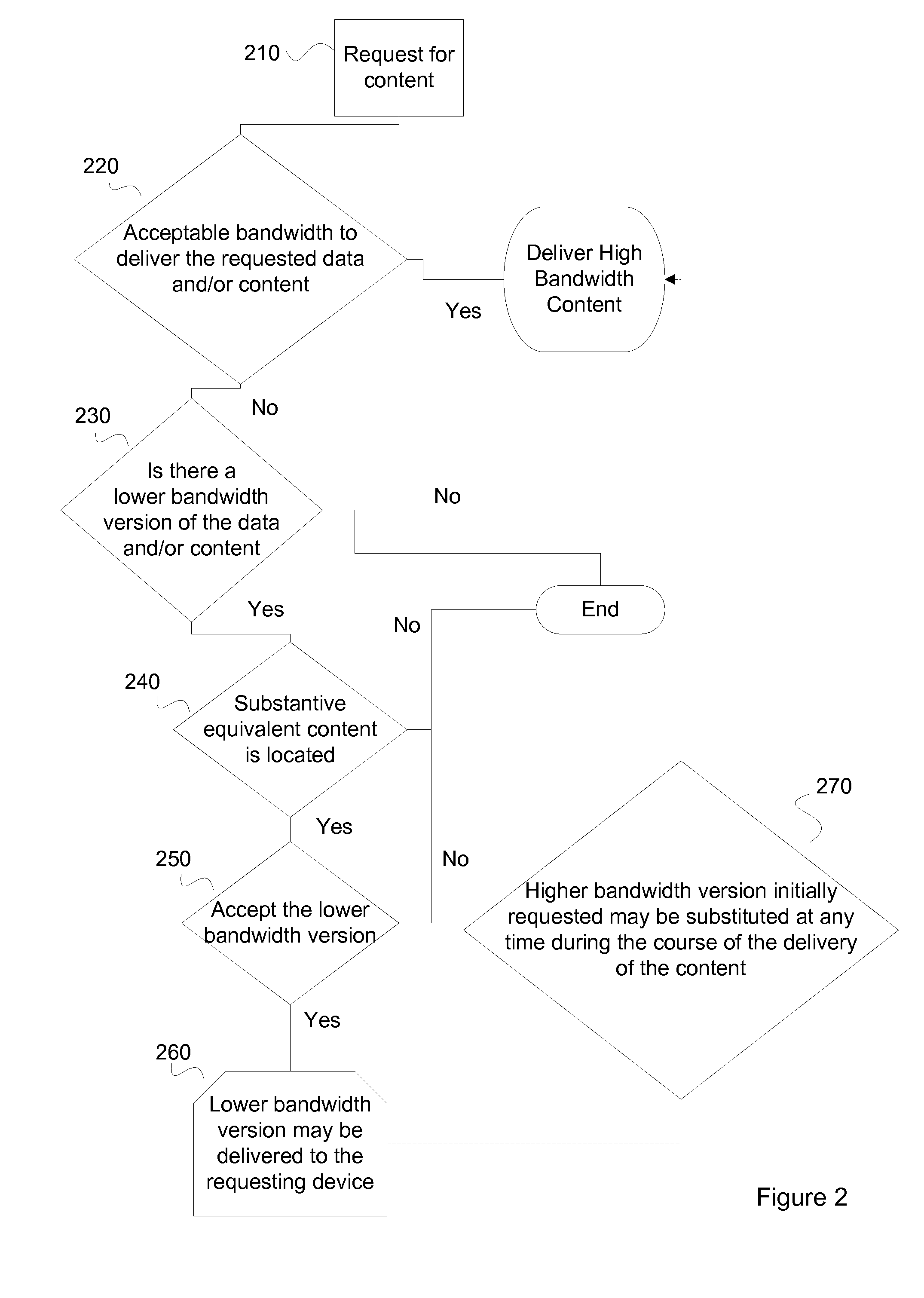
Controlling Delivery of Requested Content Based on Delivery Bandwidth Limitations
ActiveUS20140082212A1Multiple digital computer combinationsTransmissionHigh bandwidthBandwidth limitation
A device, computer readable medium, system and method for overcoming bandwidth limitations is disclosed for determining that a bandwidth limitation is related to preventing delivery of content, identifying a version of the content capable of being transmitted over a lower bandwidth, querying a device requesting delivery of the content for an indication of acceptability of a lower bandwidth version of the content instead of a higher bandwidth version, and based on an affirmative response to the querying, causing delivery of the lower bandwidth version.
Owner:COMCAST CABLE COMM LLC
Ethernet confirming access method
InactiveCN1403952ABandwidth controlEnsure normal communicationData switching networksSpecial data processing applicationsOperational systemAccess method
The Ethernet confirming access method is a wideband access method for computer network. The present invention adopts unique double web page server technology, and performs the access control and bandwidth limitation via the user access list operation. The unique forced entrance guard technology can re-orient the unauthorized user request imperatively. The present invention realizes the conformation, authorization, charge and bandwidth limitation of users via web page confirming process without needing any client end software, and this simplifies the user's operation, is independent with the user's operation platform and can operate simple and practically.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Electronic content distribution management methods and systems
InactiveUS20060074968A1Reduce the impactQuickly and automatically resolveData switching networksSpecial data processing applicationsCommunications systemTelecommunications link
Methods and systems for managing electronic content distribution are provided. Transmission of electronic content on a communication link responsive to a request received from a communication device may be precluded by the transmission of other electronic content, due to bandwidth limitations on the communication link, for example. An electronic content query is transmitted to the communication device if termination of transmission of the other electronic content on the communication link is detected, and transmission of electronic content specified in a response to the electronic content query is then initiated. Connections within a communication system may be managed in a similar fashion, with an electronic content query being transmitted to a communication device which has requested a connection when termination of an existing connection for the communication device is detected. In some embodiments, transmission of the electronic content query is controlled on the basis of a flag stored in a data structure.
Owner:ALCATEL LUCENT SAS
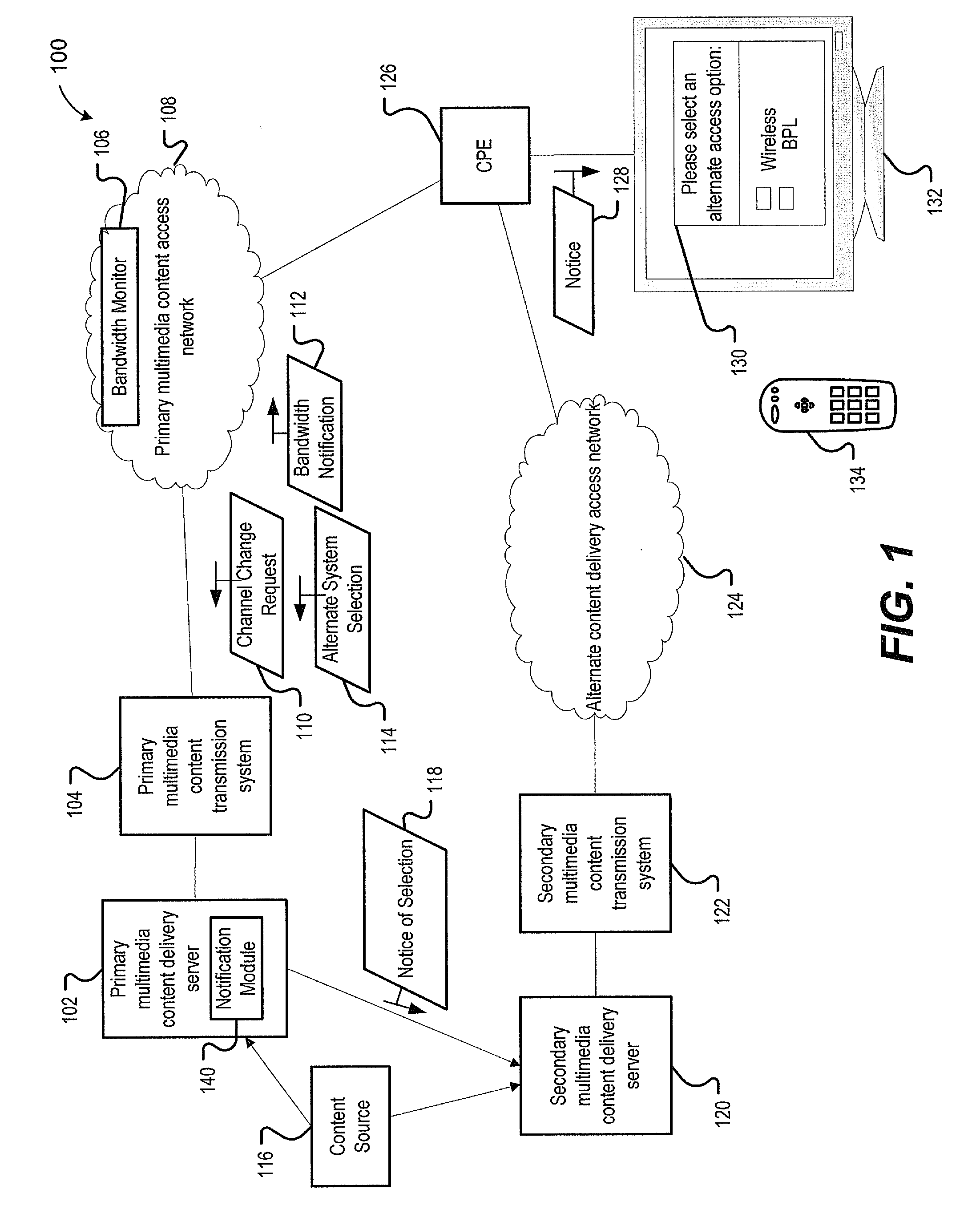
Channel Change Via An Alternate Multimedia Content Delivery System
Methods and systems are disclosed to perform a channel change via an alternate multimedia content delivery system. A particular method includes detecting a request to perform a channel change at a customer premise equipment (CPE) device. The method also includes sending the request to a server of a primary multimedia content delivery system that supports delivery of content to the CPE device. The method further includes receiving a bandwidth limitation message from the server. The method includes generating a notification for display at a display device coupled to the CPE device. The notification prompts a user with respect to delivery of content over one or more alternate multimedia content delivery systems in response to the requested channel change.
Owner:AT&T INTPROP I L P
Enforcement of network service level agreements
A service level agreement may be imposed by a service provider, such as an Internet service provider, that may include, e.g., a volume limitation and a bandwidth limitation. One or more limitations of the service level agreement may be enforced or modified in response to a triggering event. For example, a bandwidth limitation on a network subscriber may be enforced or modified based on how much data is consumed by the subscriber.
Owner:GILAT SATELLITE NETWORKS +1
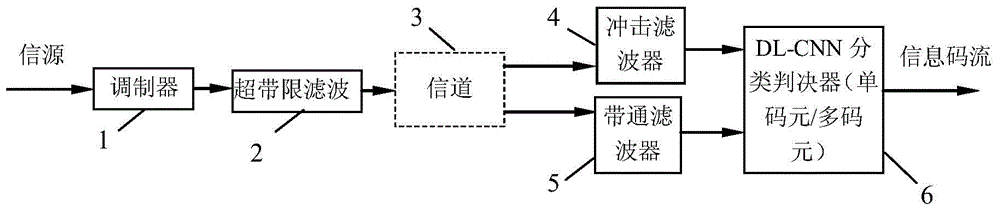
DL-CNN (deep leaning-convolutional neutral network) demodulator for super-Nyquist rate communication
ActiveCN104811276AIncrease profitLower noise figureError preventionBandpass filteringBandwidth limitation
The invention discloses a DL-CNN (deep learning-convolutional neutral network) demodulator for super-Nyquist rate communication. For digitally modulated signals via a strict band-limited channel and even more than Nyquist rate bandwidth limitation, the demodulator directly extracts signal features including intersymbol interference from received signal samples subjected to filtering by a shock filter or an ordinary bandpass filter at the receiving end by the aid of a CNN, the CNN is trained by the aid of DL, and associated decision is made by adopting a single symbol element or multiple symbols, so that the signal samples can be classified by the DL-CNN under the higher intersymbol interference environment, intersymbol interference demodulation of the super-Nyquist rate modulation signals is realized, and good modulation performance and higher adaption capability are achieved as compared with a conventional amplitude integral judgment modulator.
Owner:SOUTHEAST UNIV
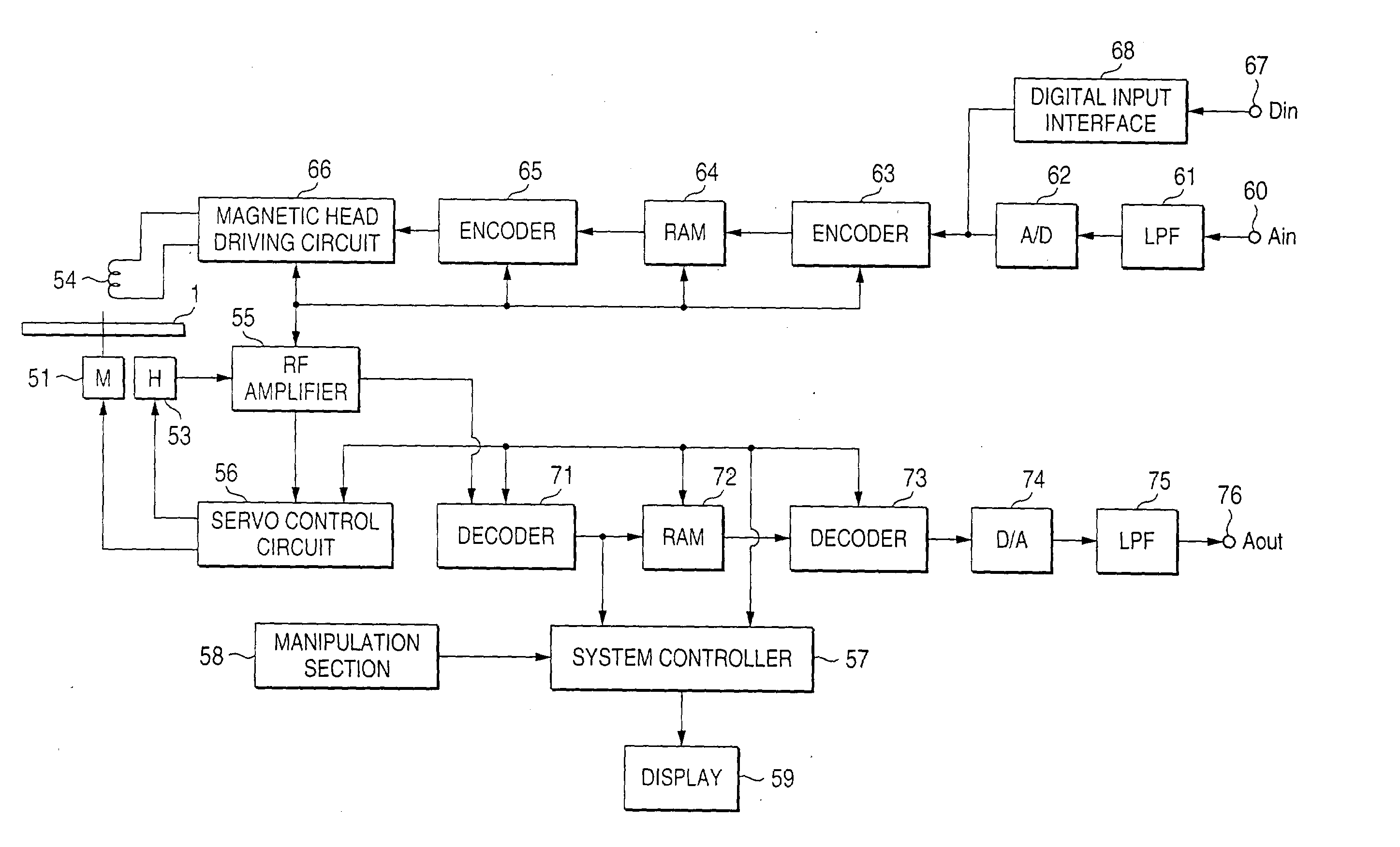
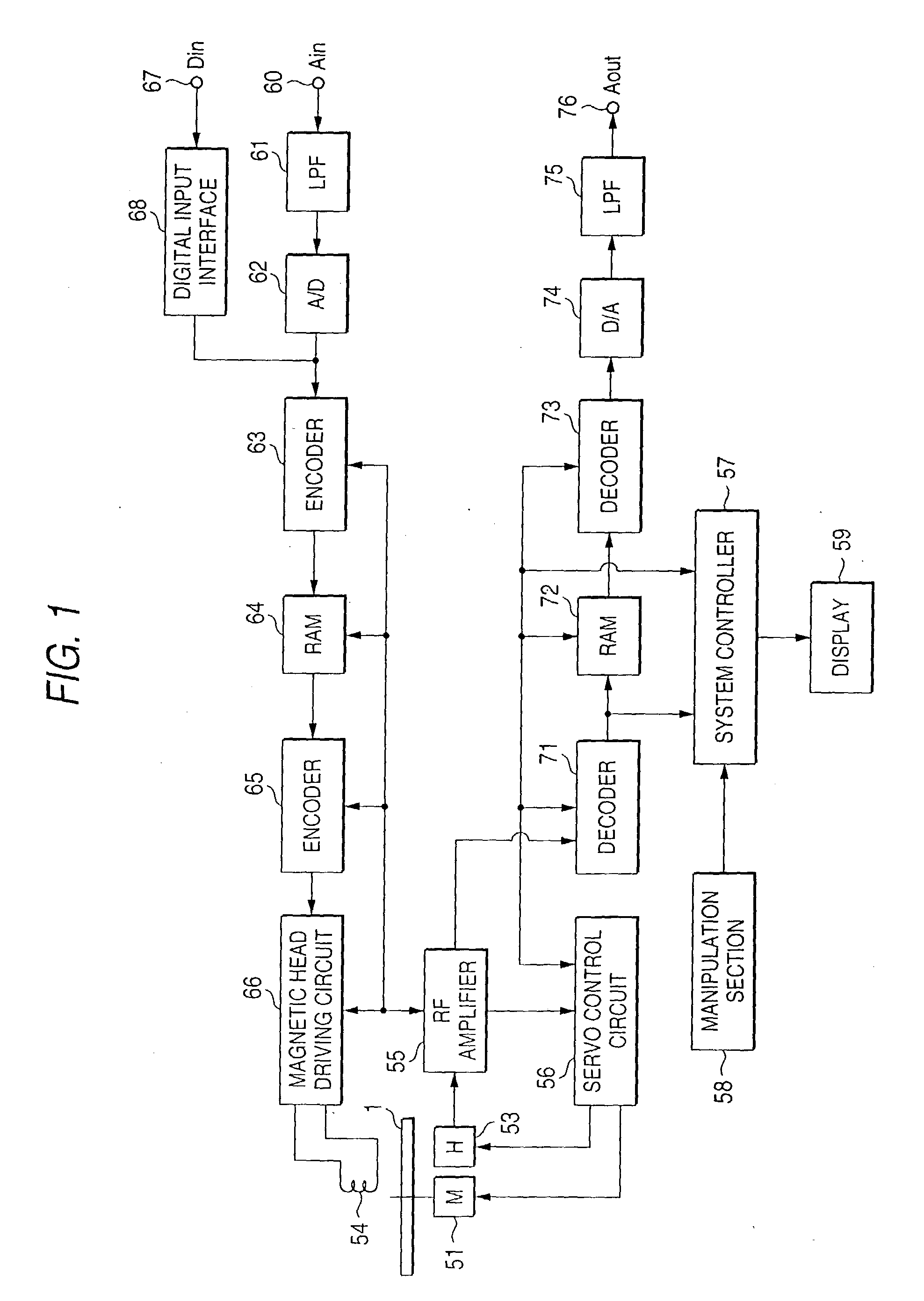
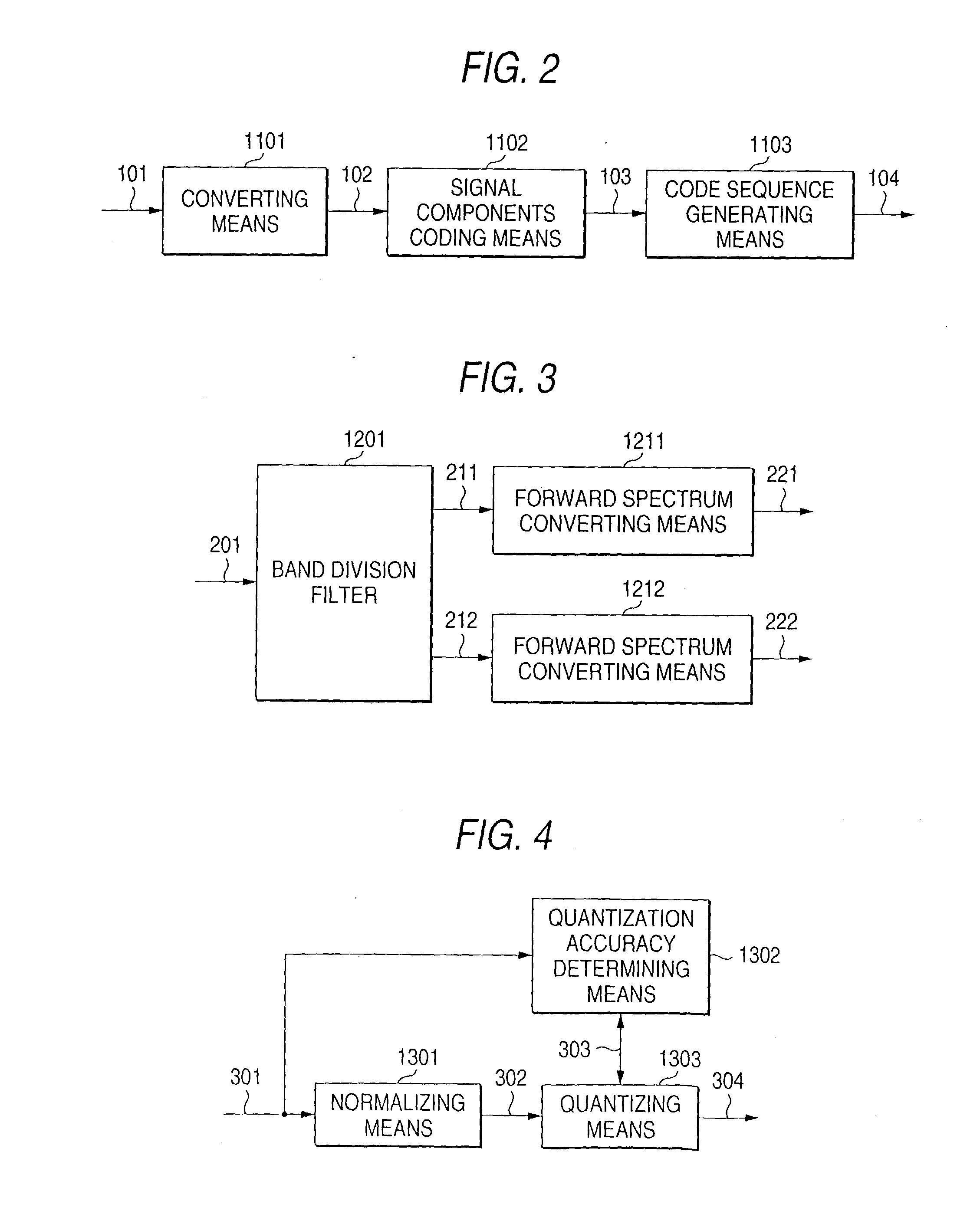
Signal reproducing method and device, signal recording method and device, and code sequence generating method and device
InactiveUS20030190155A1Restoring dataTelevision system detailsElectric signal transmission systemsBandwidth limitationDummy data
It is intended to remove a risk of illegal high quality restoration while enabling trial viewing of contents such as music, to make it possible to reproduce contents with high quality by acquiring a relatively small amount of data, and to make it possible to implement hardware at a lower cost. To generate trial listening data containing dummy data, a pseudo random number R is generated first. A remainder r of R divided by 128 is calculated. The remainder r is coded and incorporated into high sound quality restoration data. A bandwidth limitation region of trial listening data is replaced by dummy data starting from its rth bit. As a result, the head position of the dummy data in the trial listening data varies frame by frame, whereby the safety of the trial listening data can be increased.
Owner:SONY CORP
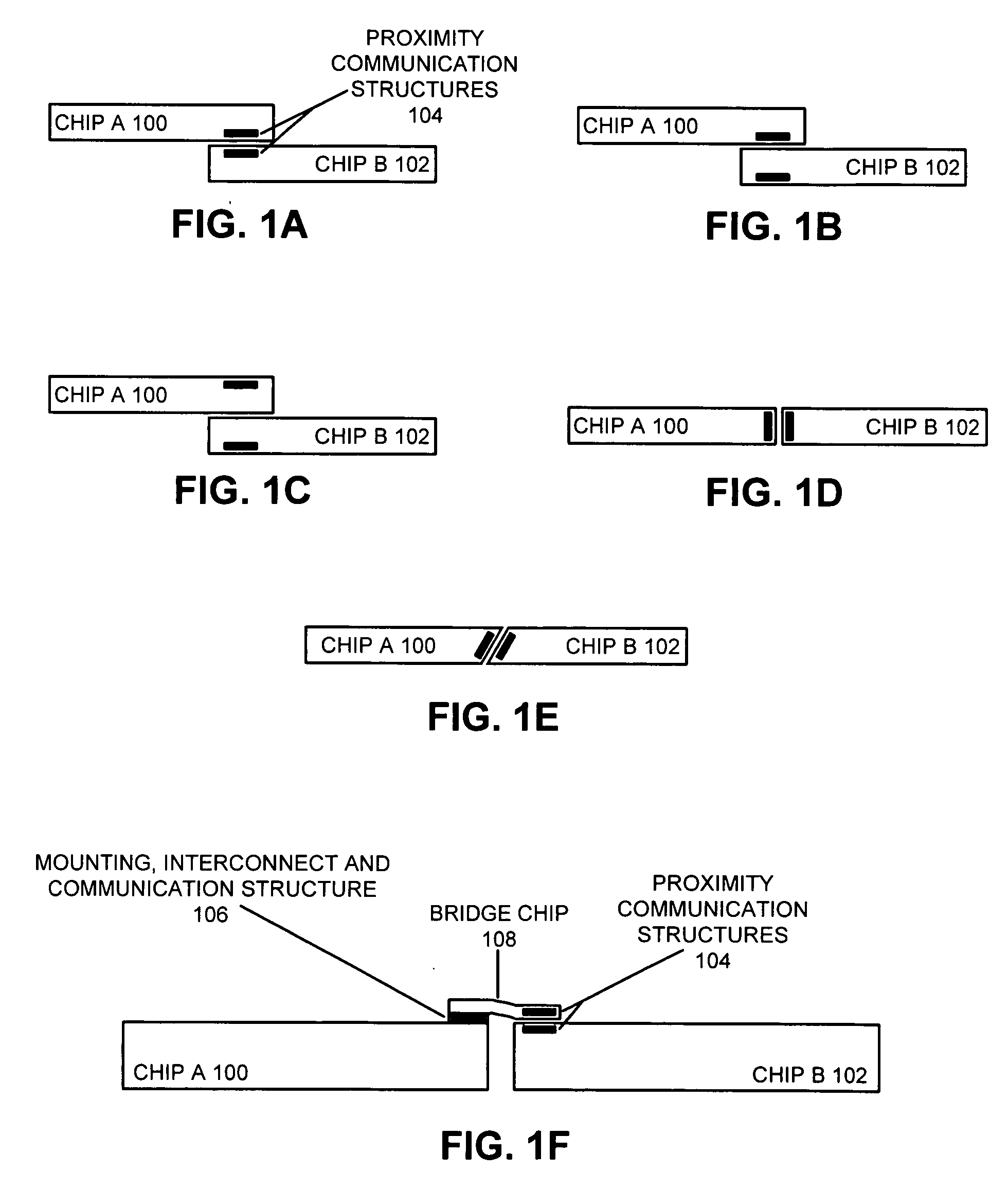
Structures and methods for a flexible bridge that enables high-bandwidth communication
ActiveUS20070043894A1Easy to optimizeAlleviating wireabilitySemiconductor/solid-state device detailsSolid-state devicesHigh bandwidthBandwidth limitation
One embodiment of the present invention provides a system that facilitates high-bandwidth communication using a flexible bridge. This system includes a chip with an active face upon which active circuitry and signal pads reside, and a second component with a surface upon which active circuitry and / or signal pads reside. A flexible bridge provides high-bandwidth communication between the active face of the chip and the surface of the second component. By matching the wire line size in the flexible bridge to the size of circuits and / or signal pads on the chip and on the second component, the system allows signals to be sent between the circuits on the chip and the second component without having to change the scale of the interconnect, thereby alleviating wireability and bandwidth limitations of conventional chip packaging technologies.
Owner:ORACLE INT CORP
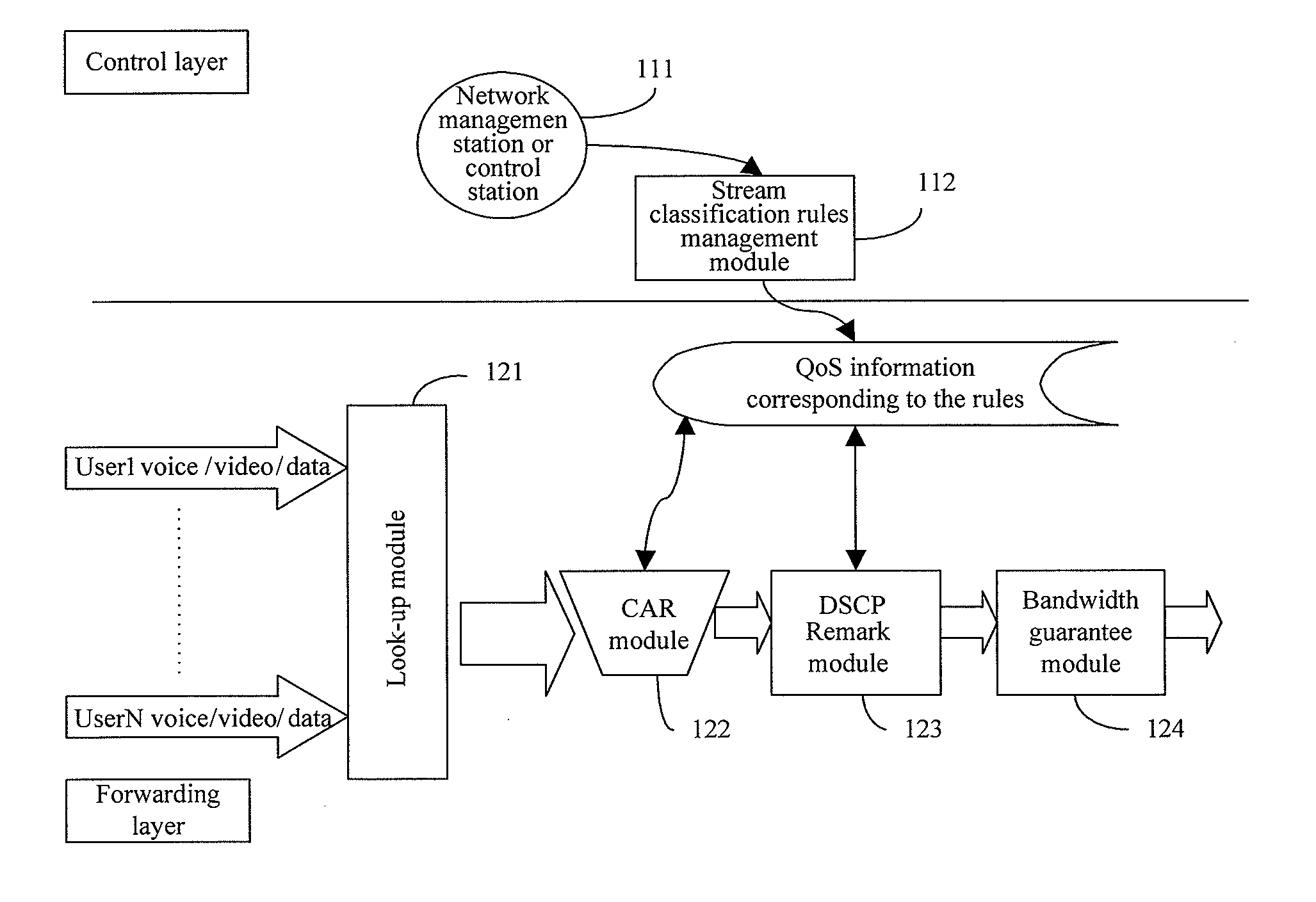
METHOD AND SYSTEM FOR PROVIDING QoS SERVICE
InactiveUS20080192753A1Intelligent control of user trafficsData switching by path configurationDomain nameData information
A method and system for providing QoS service includes analyzing signaling packets by which various soft terminals / hardware terminals register to a system and call the system, extracting the user signaling feature codes, such as the telephone number or domain name of the user and the audio, video and data information, from the signaling packet, and analyzing whether the system has been configured with the QoS information corresponding the signaling feature codes. If the matched configuration information of the user is found, the method and system perform bandwidth limitation and bandwidth guarantee according to the QoS information. In this way, the bandwidths of users do not interfere with each other, and the call quality of users are guaranteed.
Owner:HUAWEI TECH CO LTD
Apparatus and Method for Applying Unequal Error Protection During Wireless Video Transmission
ActiveUS20070198887A1High level of error protectionLess-error protectionError preventionPicture reproducers using cathode ray tubesWireless transmissionWireless video
Wireless transmission of high-definition video, whether essentially uncompressed or compressed, is prone to errors during reception due to the condition of the wireless link. To ensure video quality during changing link conditions it is desirable to ensure that those portions of the video that represent the more important components of the video signal, such as the lower special frequencies or most significant bits, are assured correct reception at the receiver. Bandwidth limitations of the wireless link affect the amount of data that can be sent over the link. Hence, using a high level error recovery for all of the information is not feasible. Accordingly, a method and apparatus for unequal error protection is disclosed that provides a higher level of error protection to the more important elements of the transmission while affording less error protection to the other elements of the transmission.
Owner:AMIMON
High speed arbitrary waveform generator
ActiveUS7535394B2Electric signal transmission systemsDigital-analogue convertorsDigital analog converterWave shape
A high-speed arbitrary waveform generator (AWG) that utilizes multiple digital-to-analog converters (D / A converters) and overcomes bandwidth limitations of individual D / A converters to produce high-speed waveforms.
Owner:TELEDYNE LECROY
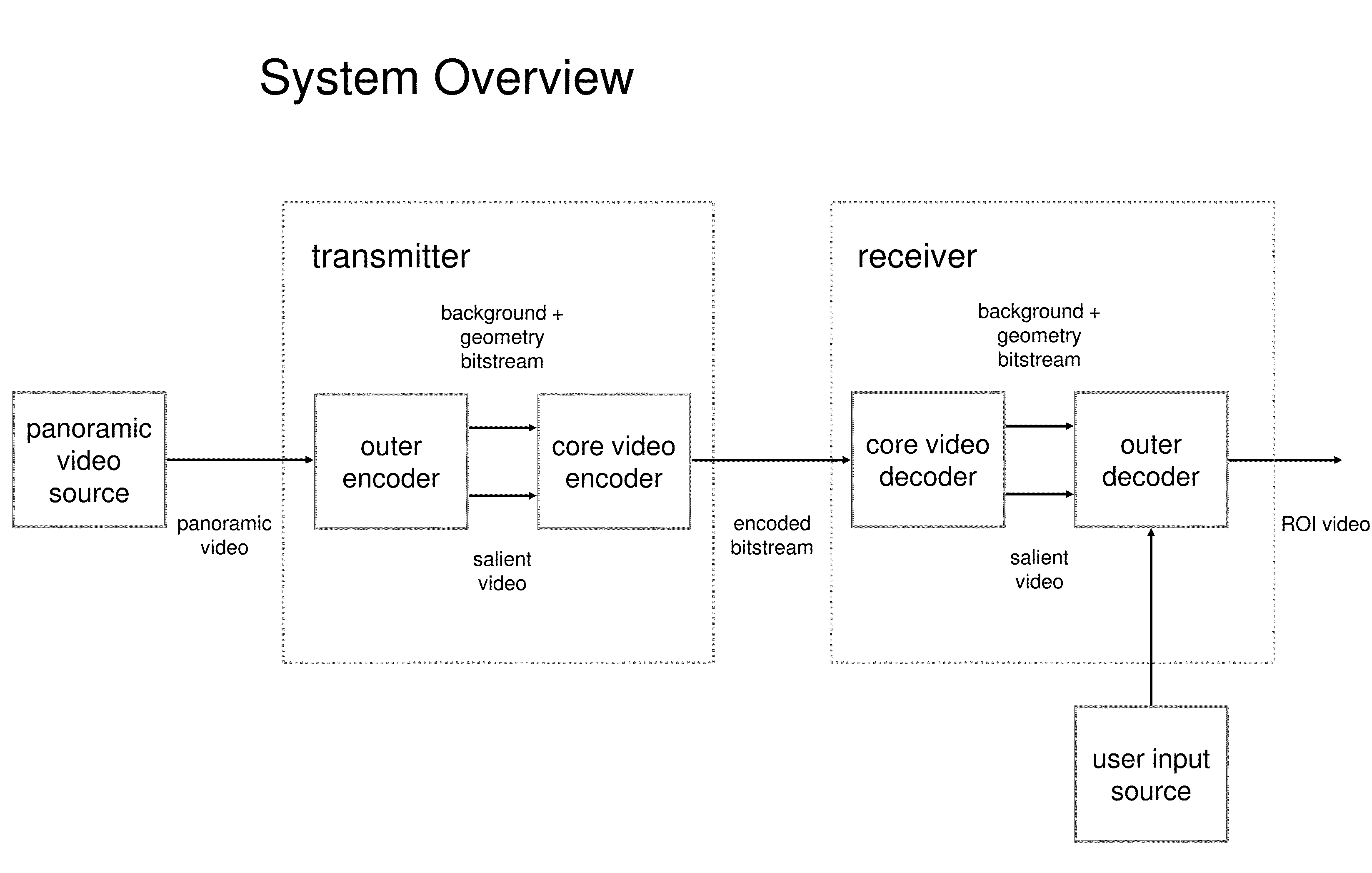
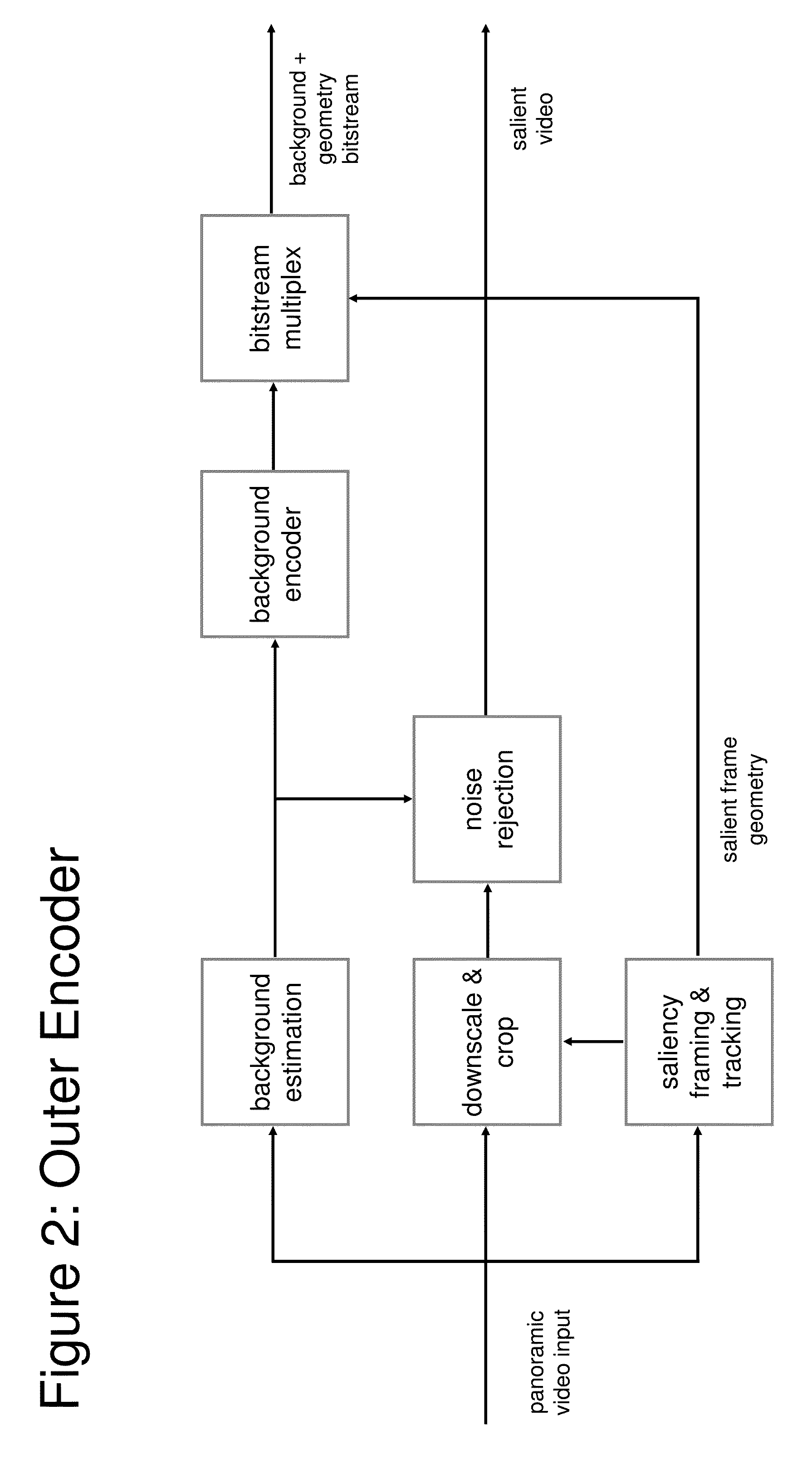
Video Transmission Based on Independently Encoded Background Updates
ActiveUS20160219241A1Enhanced videoTelevision system detailsColor television detailsComputer hardwareVideo transmission
Systems and methods are provided for alleviating bandwidth limitations of video transmission, enhancing the quality of videos at a receiver, and improving the VR / AR experience. In particular, an improved video transmission and rendering system is provided for generating high-resolution videos. The systems have therein a transmitter and a VR / AR receiver; the transmitter includes an outer encoder and a core encoder, while the receiver includes a core decoder and an outer decoder. The outer encoder is adapted to receive the video from a source and separately output a salient video and an encoded three-dimensional background, and the outer decoder is adapted to merge the background with the salient video thereby producing an augmented video. Also provided is a system that simulates pan-tilt-zoom (PTZ) operations without PTZ hardware. Further provided are methods for video transmission whereby a three-dimensional background model is generated, a background independently encoded, updated incrementally, and the background and the updates transmitted independently from the video.
Owner:HUDDLY AS
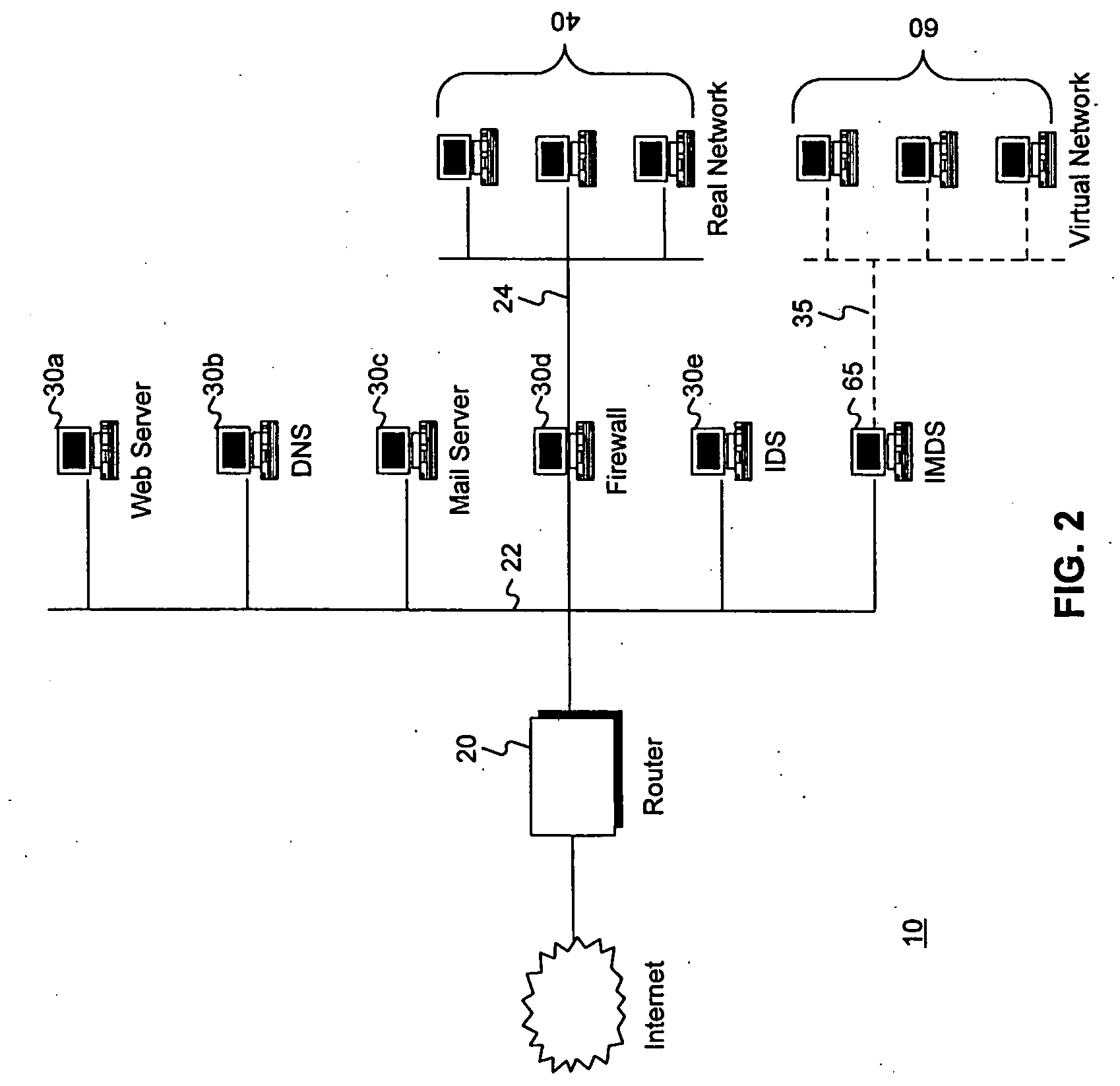
Intrusion and misuse deterrence system employing a virtual network
InactiveUS20050177871A1Improve securityEasy to implementMemory loss protectionUnauthorized memory use protectionIp addressBandwidth limitation
A method and apparatus is disclosed for increasing the security of computer networks through the use of an Intrusion and Misuse Deterrence System (IMDS) operating on the network. The IMDS is a system that creates a synthetic network complete with synthetic hosts and routers. It is comprised of a network server with associated application software that appears to be a legitimate portion of a real network to a network intruder. The IMDS consequently invites inquiry and entices the intruder away from the real network. Simulated services are configured to appear to be running on virtual clients with globally unique, class “C” IP addresses. Since there are no legitimate users of the virtual network simulated by the IMDS, all such activity must be inappropriate and can be treated as such. Consequently, the entire set of transactions by an intruder can be collected and identified rather than just those transactions that meet a predefined attack profile. Also, new exploits and attacks are handled just as effectively as known attacks, resulting in better identification of attack methodologies as well as the identification and analysis of new attack types. Since the IMDS only has to be concerned with the traffic going to its simulated hosts it additionally eliminates the bandwidth limitation that plagues a traditional intrusion detection system (IDS).
Owner:LEVEL 3 COMM LLC +2
Method and apparatus for limiting domain name server transaction bandwidth
ActiveUS7970878B1Reduce riskRecognition is intuitiveDigital data processing detailsData switching by path configurationDomain nameComputer network
A method of limiting domain name server (DNS) transaction bandwidth comprises intercepting one or more DNS packets, examining said one or more packets for the presence of a suspect transaction criterion and, if said suspect transaction criterion is present, implementing a transaction bandwidth limitation action.
Owner:CISCO TECH INC
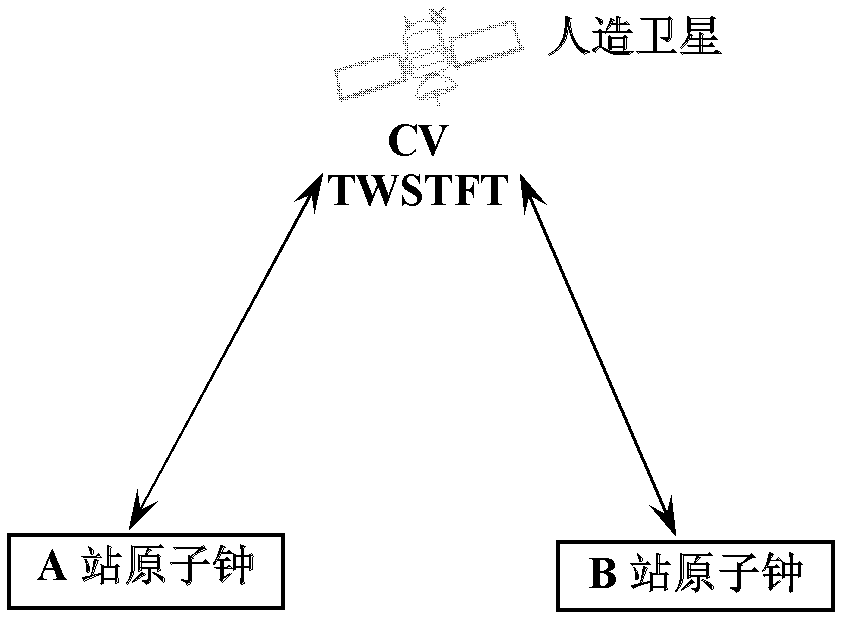
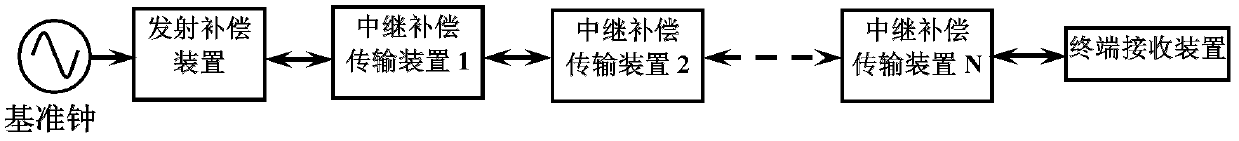
Atomic time signal transmission system and method
ActiveCN102307087APhase Noise CompensationHigh transfer accuracyFibre transmissionSynchronising arrangementUltrasound attenuationPhase noise
The invention provides an atomic time signal transmission system and method. In the system, an emitting compensation device at an emission end is used to modulate atomic time signals to be transmitted onto optical signals for transmission by optical fibers and compensate for phase noise introduced by transmitting the atomic time signals in optical fiber links; and a plurality of serially-connected relay compensation transmission devices in each relay end are utilized to further compensate for the phase noise introduced by transmitting the atomic time signals in the optical fiber links, thus locking phases of the atomic time signals transmitted to the far ends at the phase of a reference clock at the emission end. The technical scheme is used for solving the problems of the locking bandwidth limitation and signal attenuation of an over-long base-line atomic time signal transmission loop and improving the transmission distance and transmission accuracy of the atomic time signals greatly.
Owner:TSINGHUA UNIV
Bit rate adjustment in an adaptive streaming system
A method and apparatus for adaptively streaming multiple video bit streams through a network node is disclosed. In particular, a system is taught where at least one of the video bit streams is scaled in response to a bandwidth limitation or availability, where the selection of the bit stream selected for scaling in made in response to at least one of a user defined, service provider defined, and usage analysis defined priority list.
Owner:THOMSON LICENSING SA
Time-window-constrained multicast using connection scheduling
InactiveUS20060190598A1Reduce bandwidth and heterogeneous client limitationDelay minimizationDigital computer detailsSecuring communicationBandwidth limitationClient-side
A method of reducing bandwidth limitations to send events to a set of interested clients within a pre-defined time period as quickly and fairly as possible. The clients can be re-distributed among the servers in a network such that the delay due to server overloading is minimized by moving clients from an overloaded server to a server with available bandwidth. In addition, the latency of client-server communications can be incorporated into an estimation of download times, and the servers can then initiate delivery to respective clients based on those download times. By staggering the send times to account for heterogeneous latencies, more clients can receive the event at the same time, and a fairness of distribution can be achieved.
Owner:MICROSOFT TECH LICENSING LLC
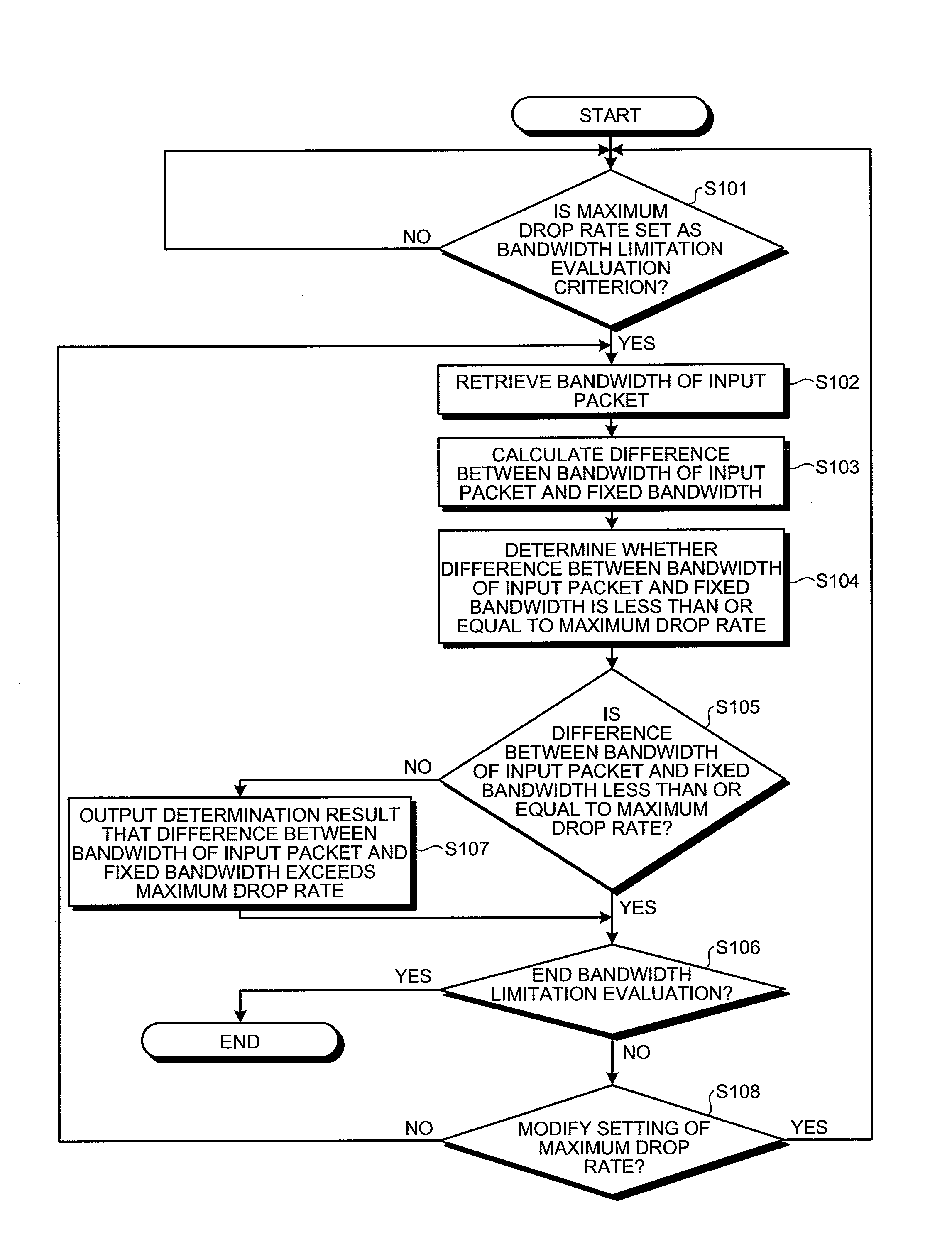
Communication relay device, communication relay method, and computer product
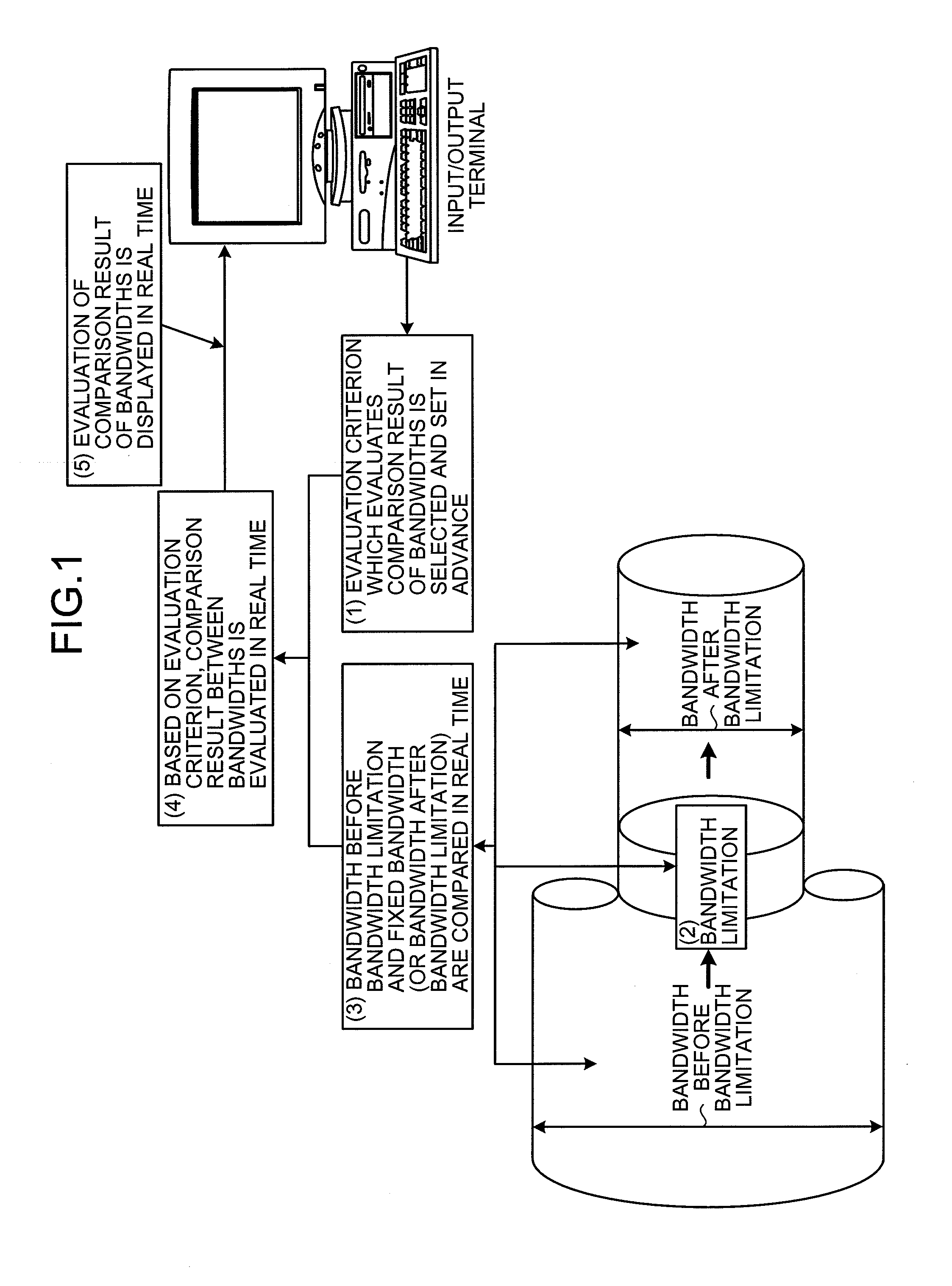
InactiveUS20080107036A1Solve problemsError preventionFrequency-division multiplex detailsCountermeasureBandwidth limitation
An evaluation criterion that evaluates a comparison result of a bandwidth before a bandwidth limitation and a bandwidth after the bandwidth limitation is selected and set in advance in a layer 2 (L2) switch device according to the present invention. An input packet is subjected to the bandwidth limitation and then output. The bandwidth before the bandwidth limitation and the bandwidth after the bandwidth limitation are constantly compared. Next, based on the preset evaluation criterion, the comparison result of the bandwidths is constantly evaluated. The evaluation result is output in real time to an input / output terminal such that the evaluation result can be displayed. When the bandwidth that is limited via the bandwidth limitation exceeds a maximum value of an admissible packet-dropping bandwidth that is set in advance, the excess is notified to a user in real time and the user can take quick countermeasures.
Owner:FUJITSU LTD
WiMAX system as well as device and method for defending DDoS attack
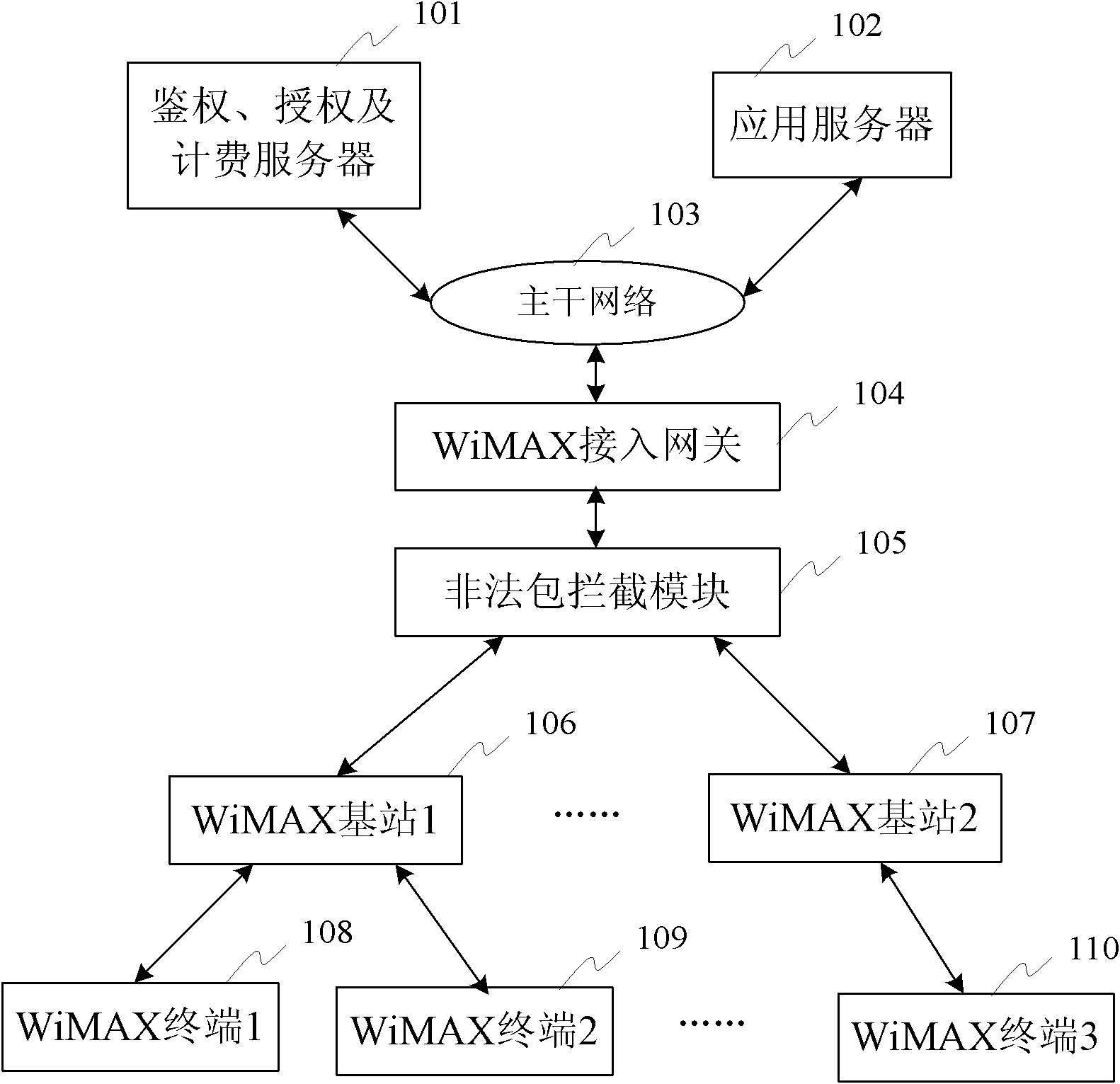
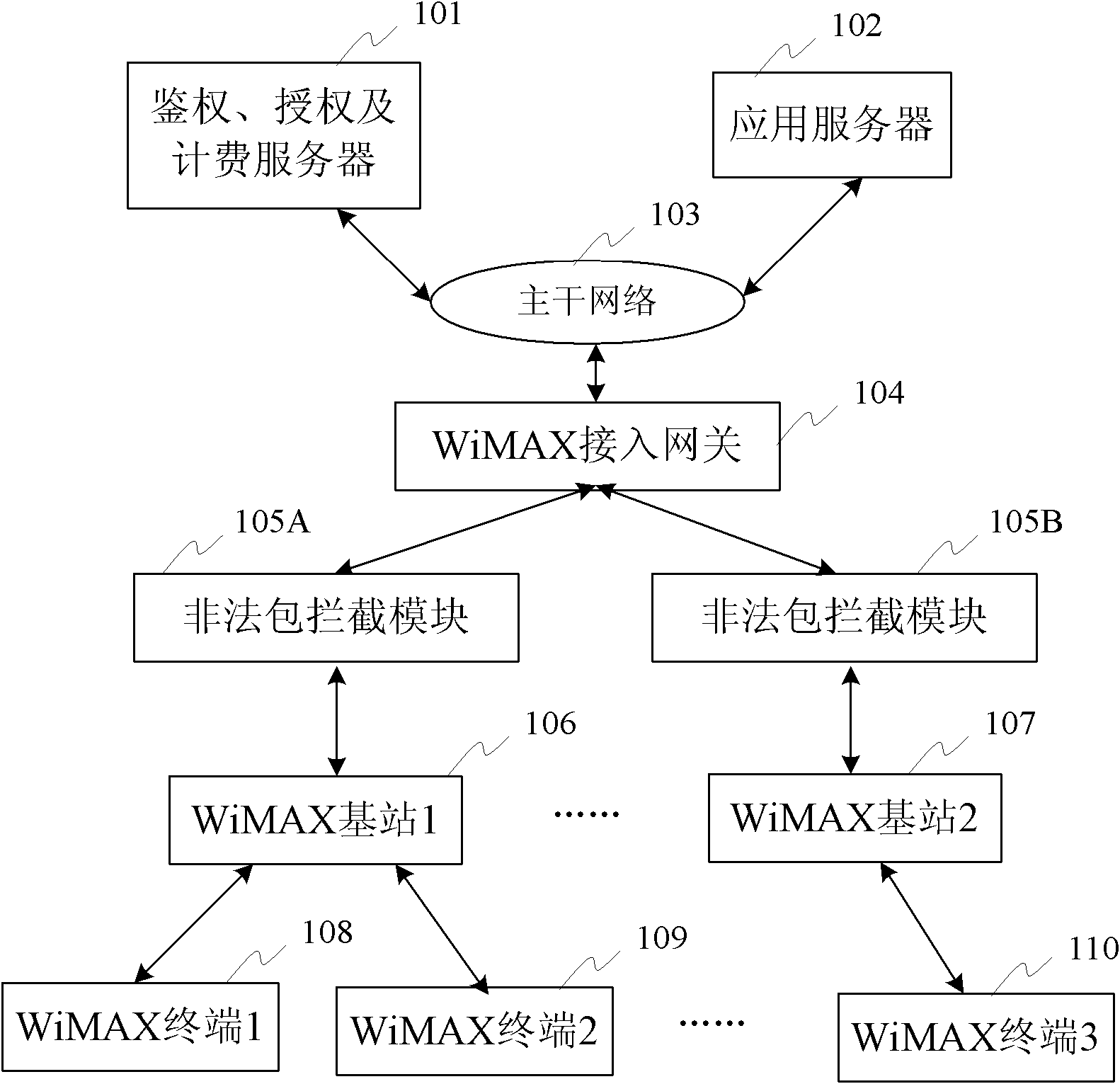
ActiveCN102026199AImprove securityGuarantee normal developmentTransmissionSecurity arrangementApplication serverBandwidth limitation
The invention discloses a WiMAX system as well as a device and a method for defending DDoS attack. The method comprises the following steps of: configuring one ore more illegal packet intercepting modules between a base station and an access gateway in the WiMAX system, and then carrying out legal detection to upstream data transmitted by a terminal through the base station by using the illegal packet intercepting modules, if judging that the upstream data is legal data, directly transmitting the upstream data to the access gateway and then transmitting to an application server by using a main network; and if judging that the upstream data is illegal data, intercepting the upstream data. The method is further used for notifying the base station to carry out bandwidth limitation to the terminal sending the illegal data after intercepting the illegal data, and then recording a detection log and generating alarm. The device and method can effectively defend DDoS attack launched by a large number of terminals in the network, thereby enhancing the safety of the network and ensuring the stability of a wireless network.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com