Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
250 results about "Exact matching" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Exact Matching. The simplest version of matching is exact. This technique matches each treated unit to all possible control units with exactly the same values on all the covariates, forming subclasses such that within each subclass all units (treatment and control) have the same covariate values.
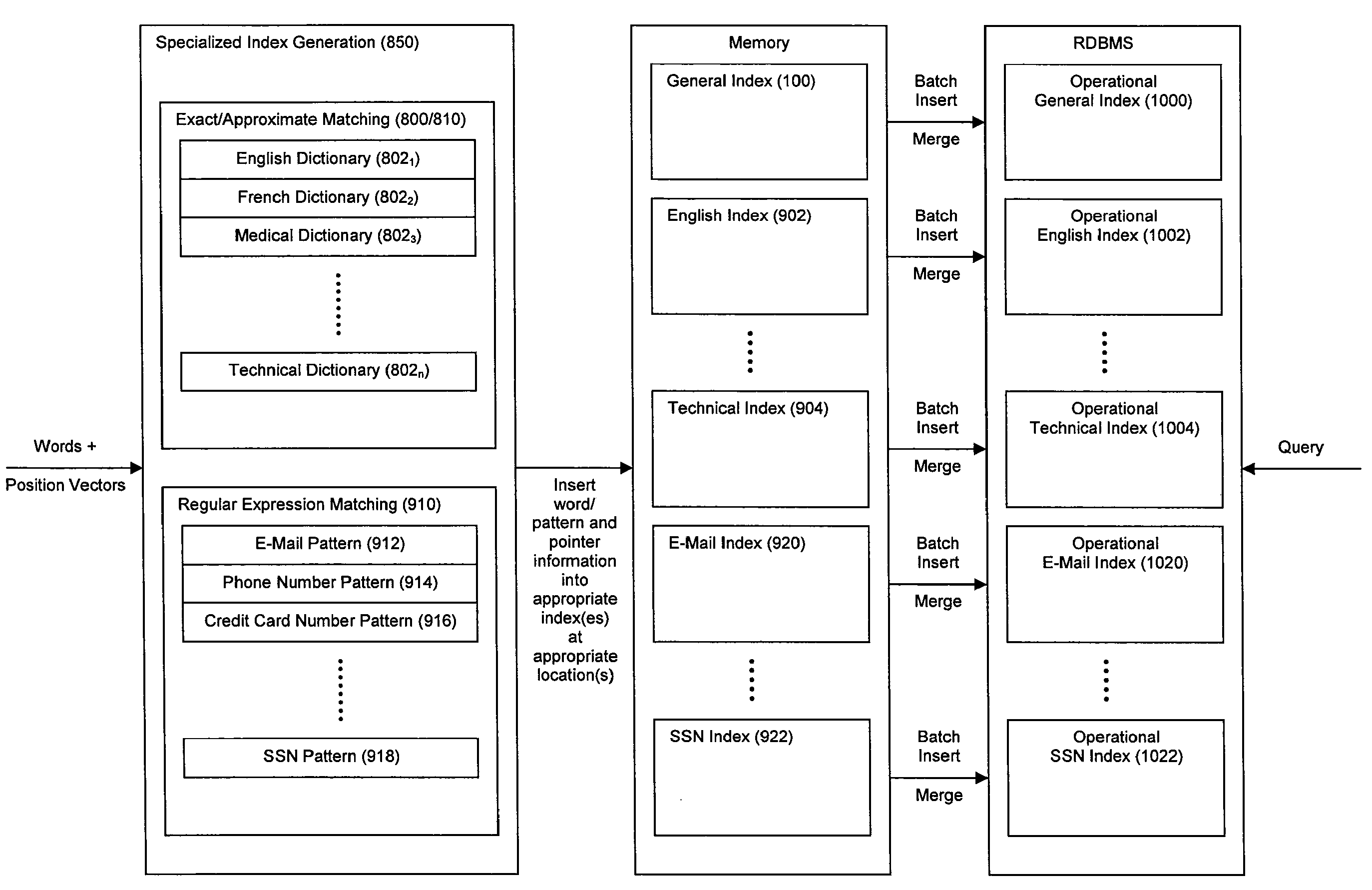
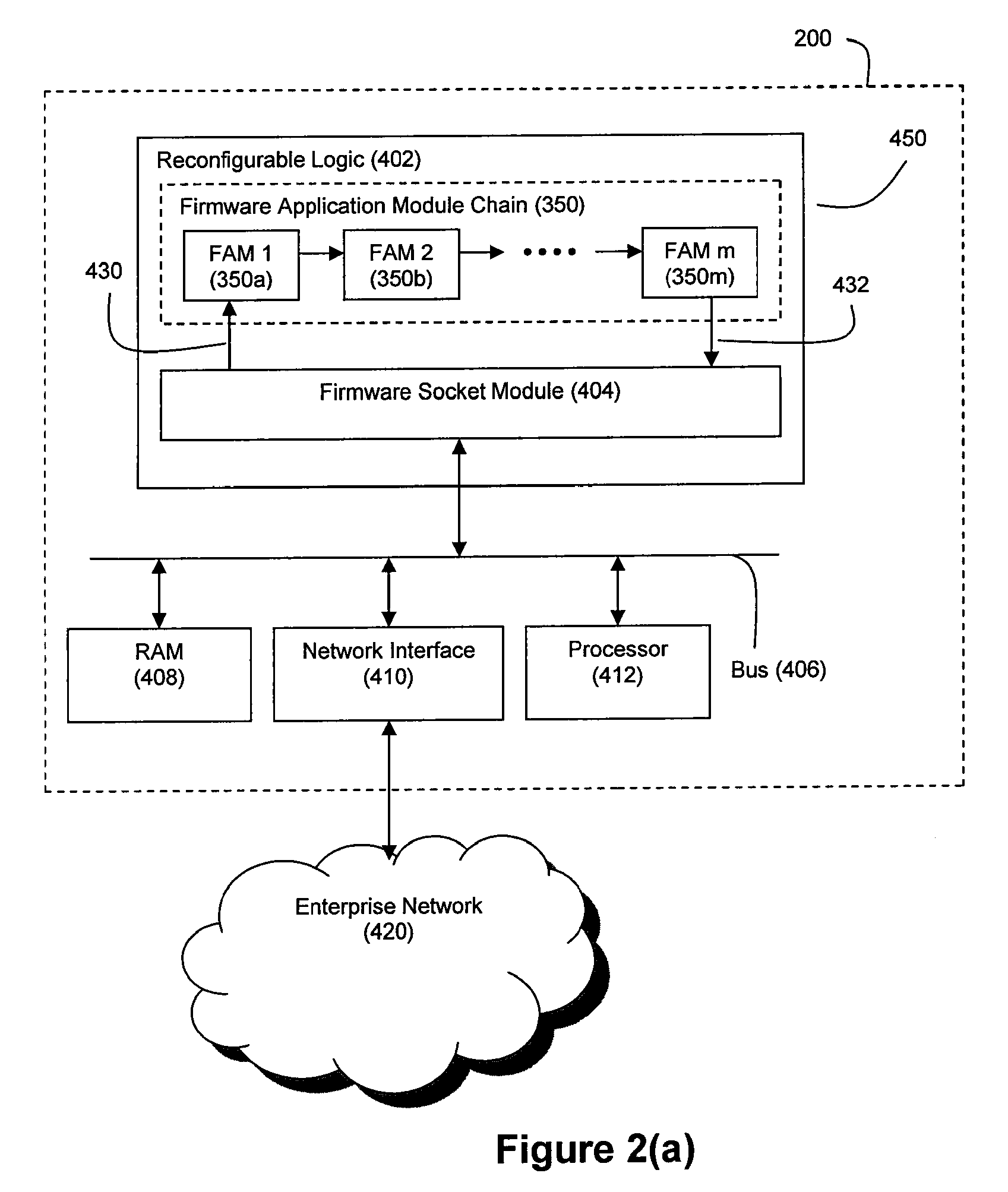
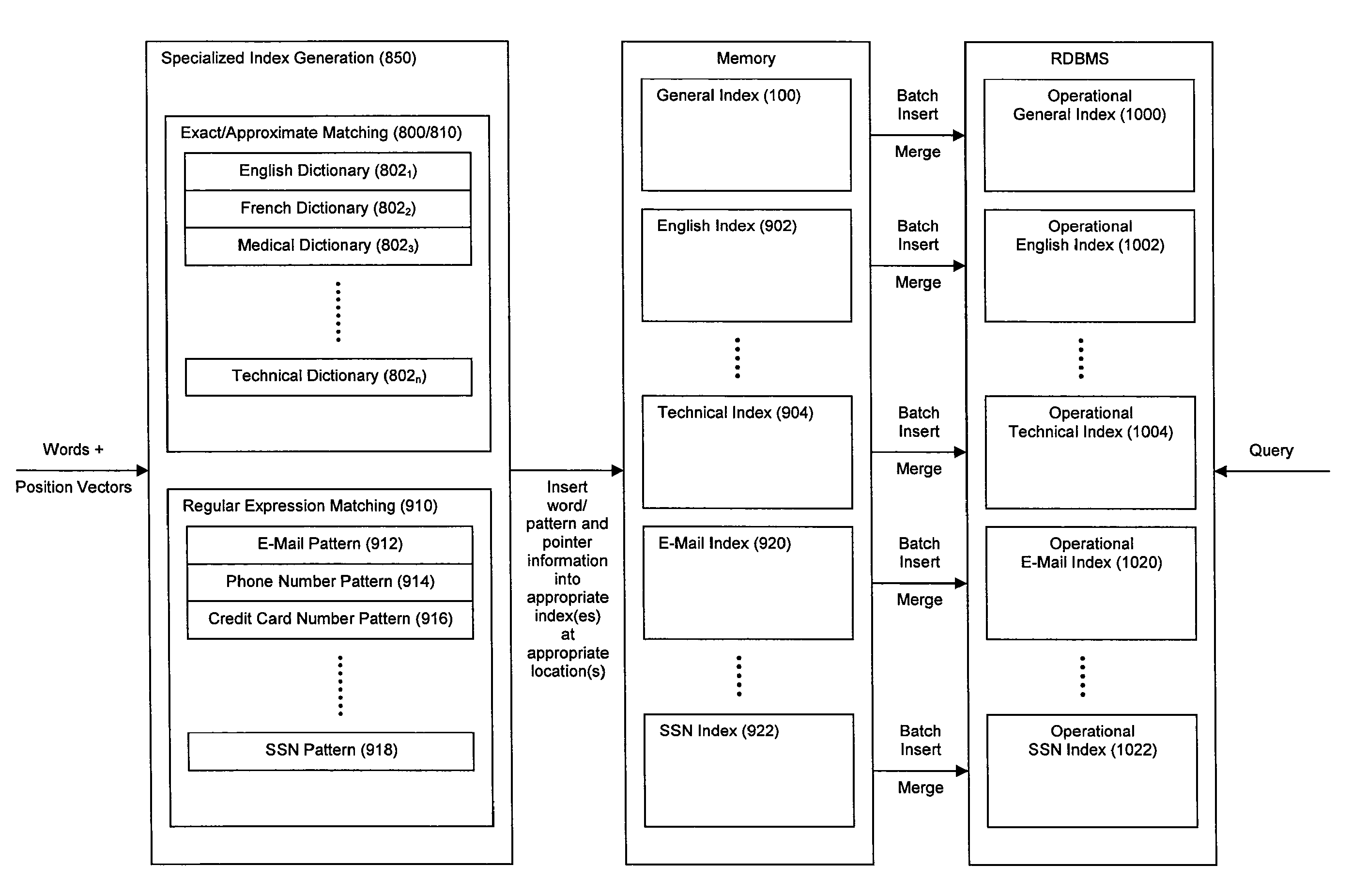
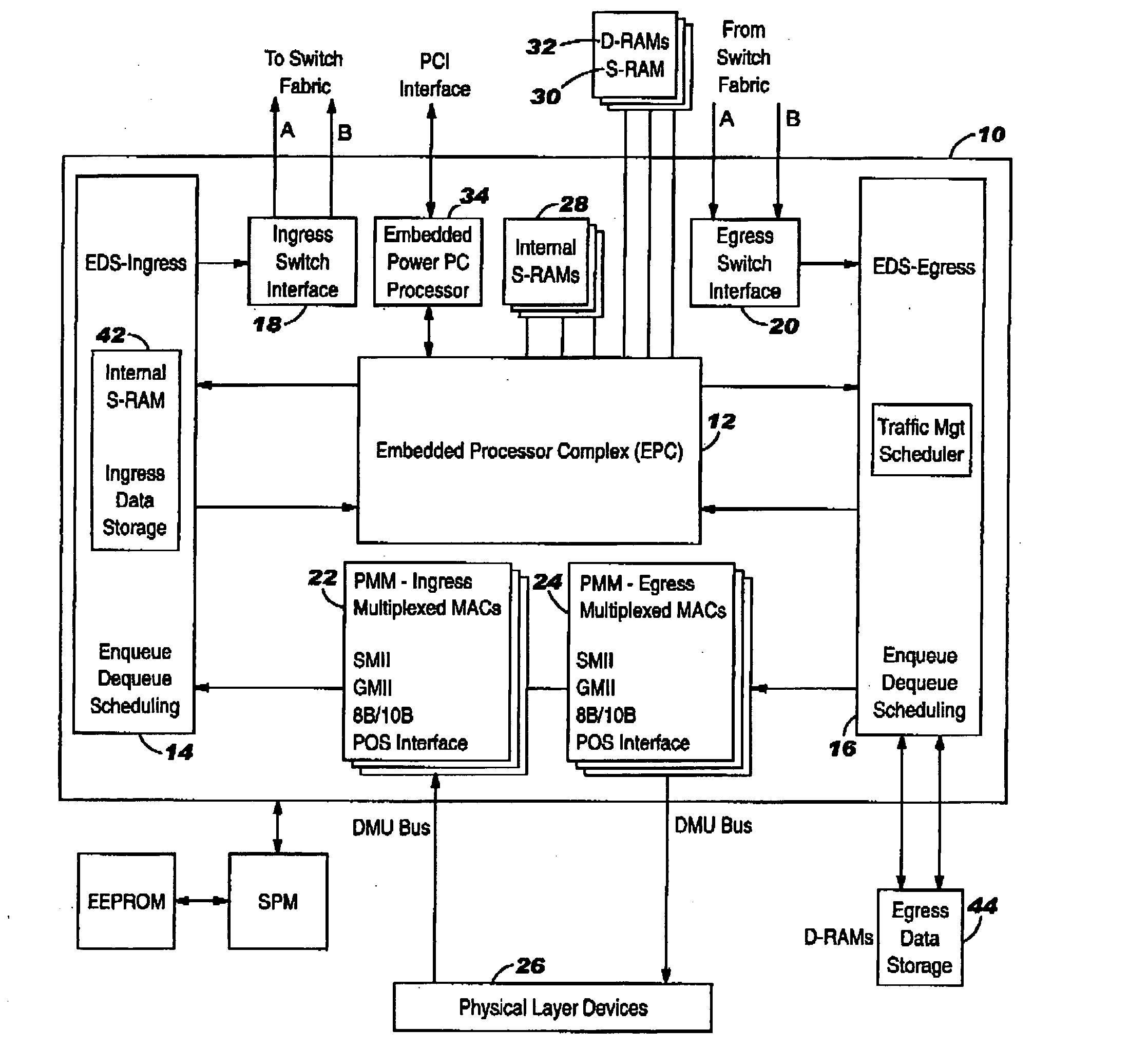
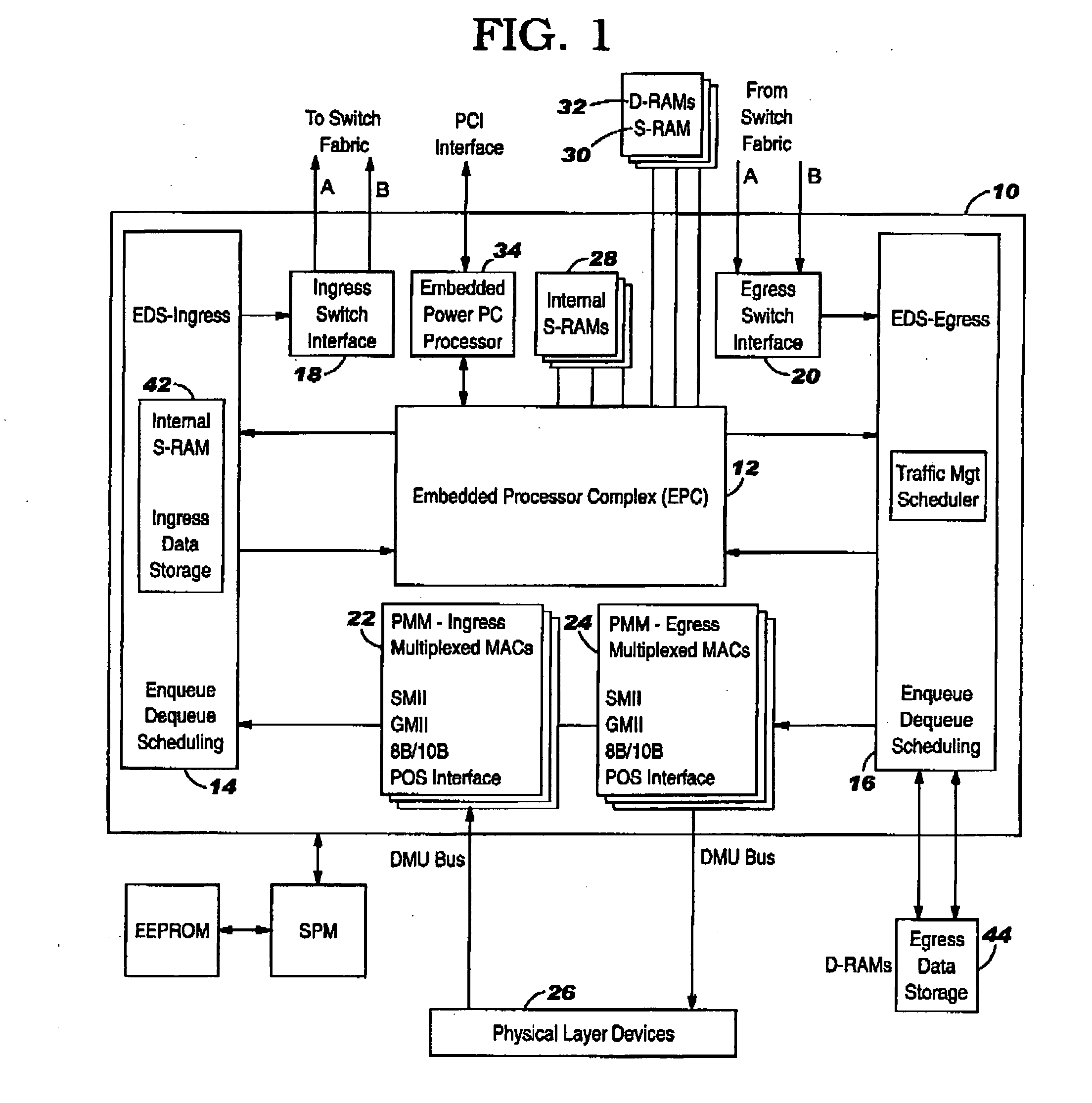
Method and System for High Performance Data Metatagging and Data Indexing Using Coprocessors
ActiveUS20080114725A1Robust and high performance data searchingHigh indexWeb data indexingFile access structuresData streamCoprocessor
Disclosed herein is a method and system for hardware-accelerating the generation of metadata for a data stream using a coprocessor. Using these techniques, data can be richly indexed, classified, and clustered at high speeds. Reconfigurable logic such a field programmable gate arrays (FPGAs) can be used by the coprocessor for this hardware acceleration. Techniques such as exact matching, approximate matching, and regular expression pattern matching can be employed by the coprocessor to generate desired metadata for the data stream.
Owner:IP RESERVOIR
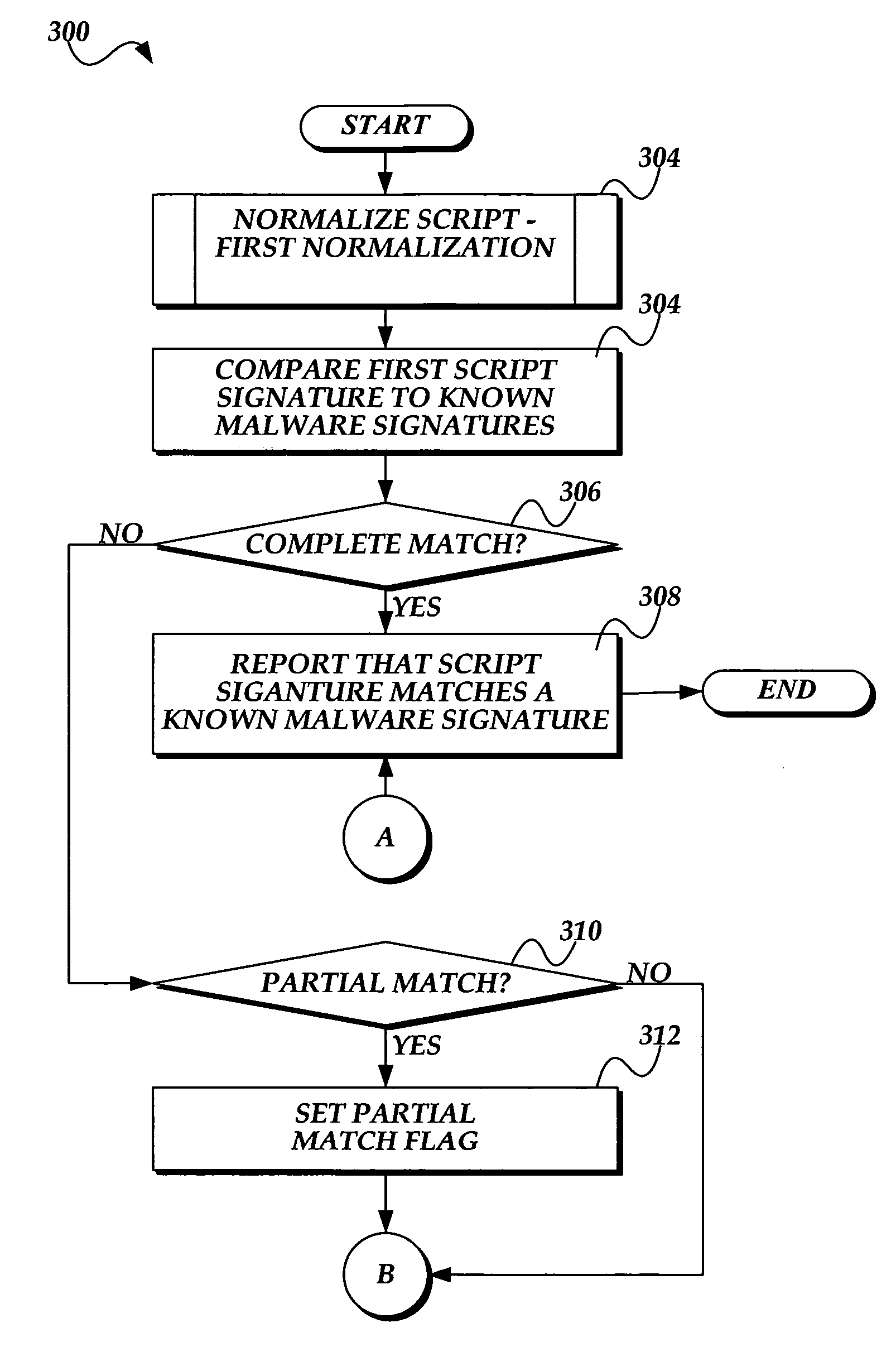
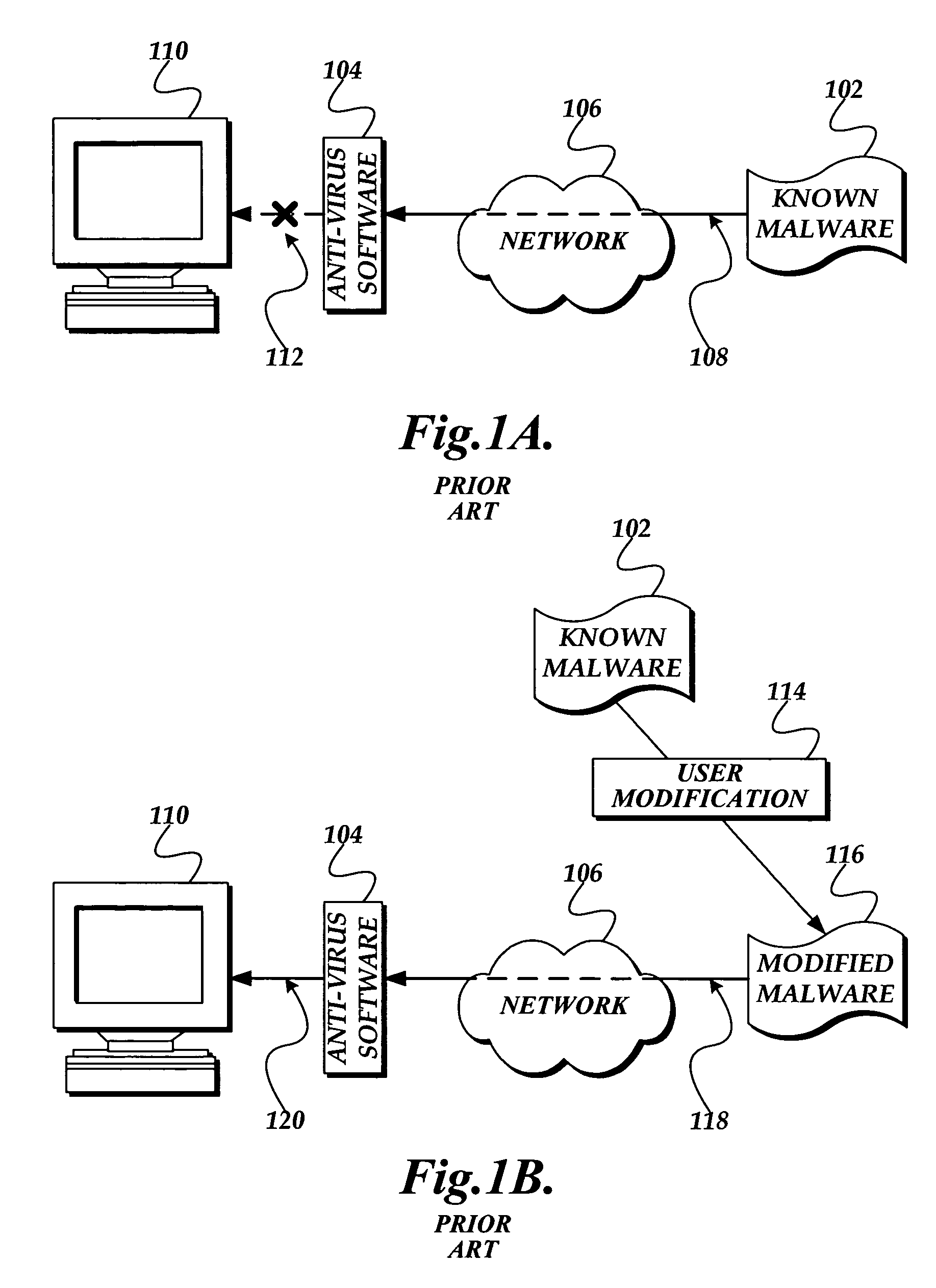
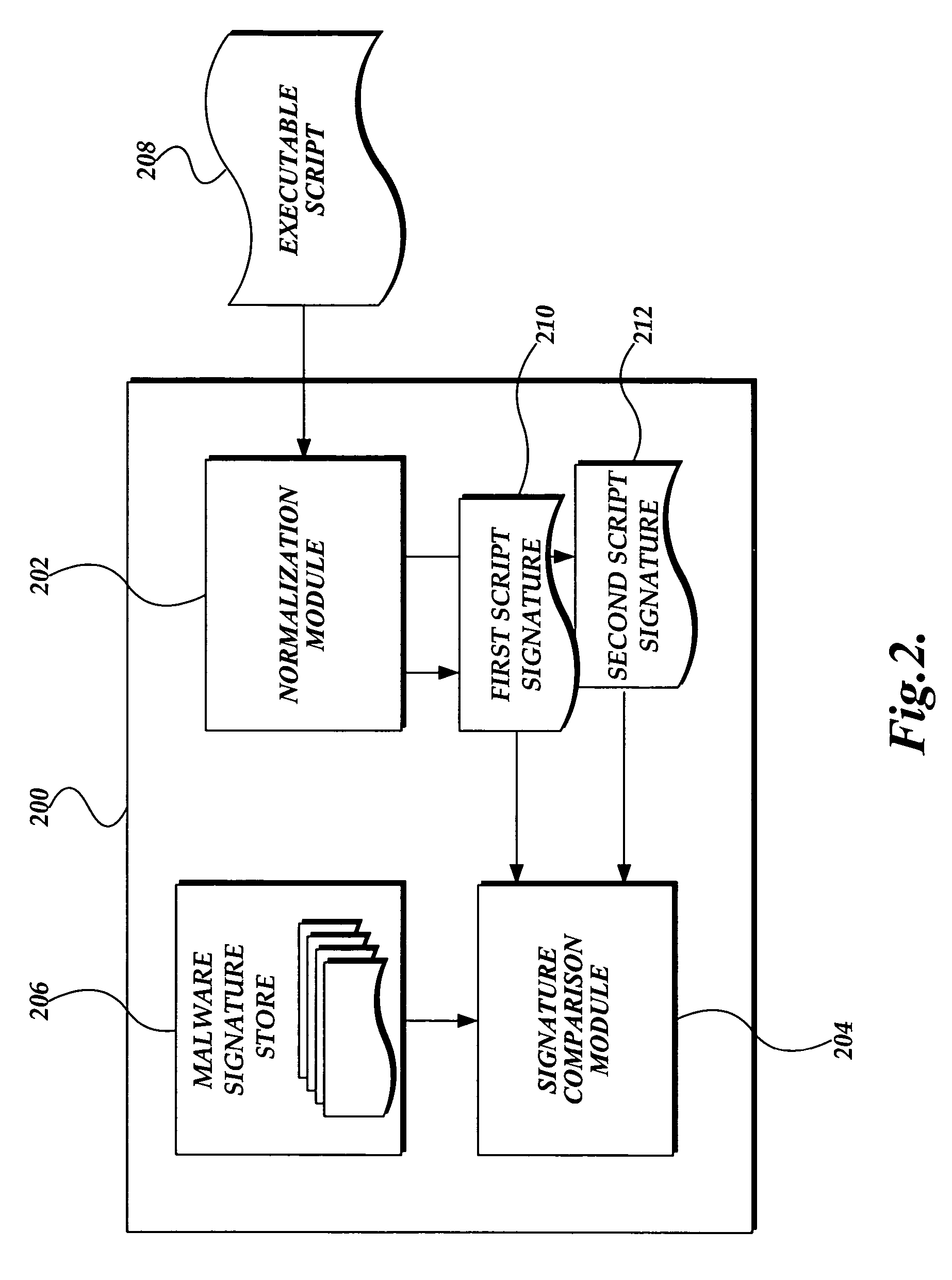
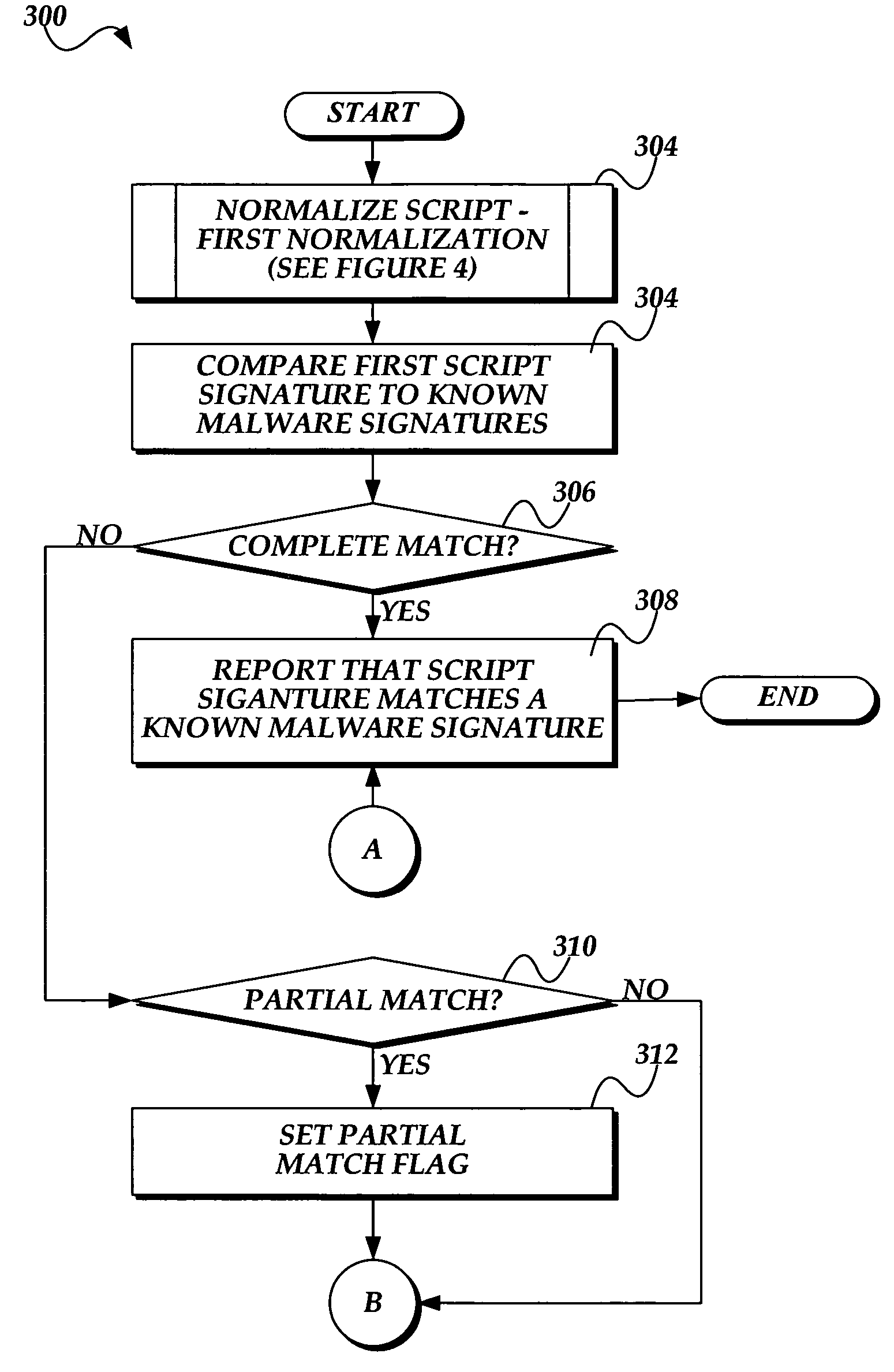
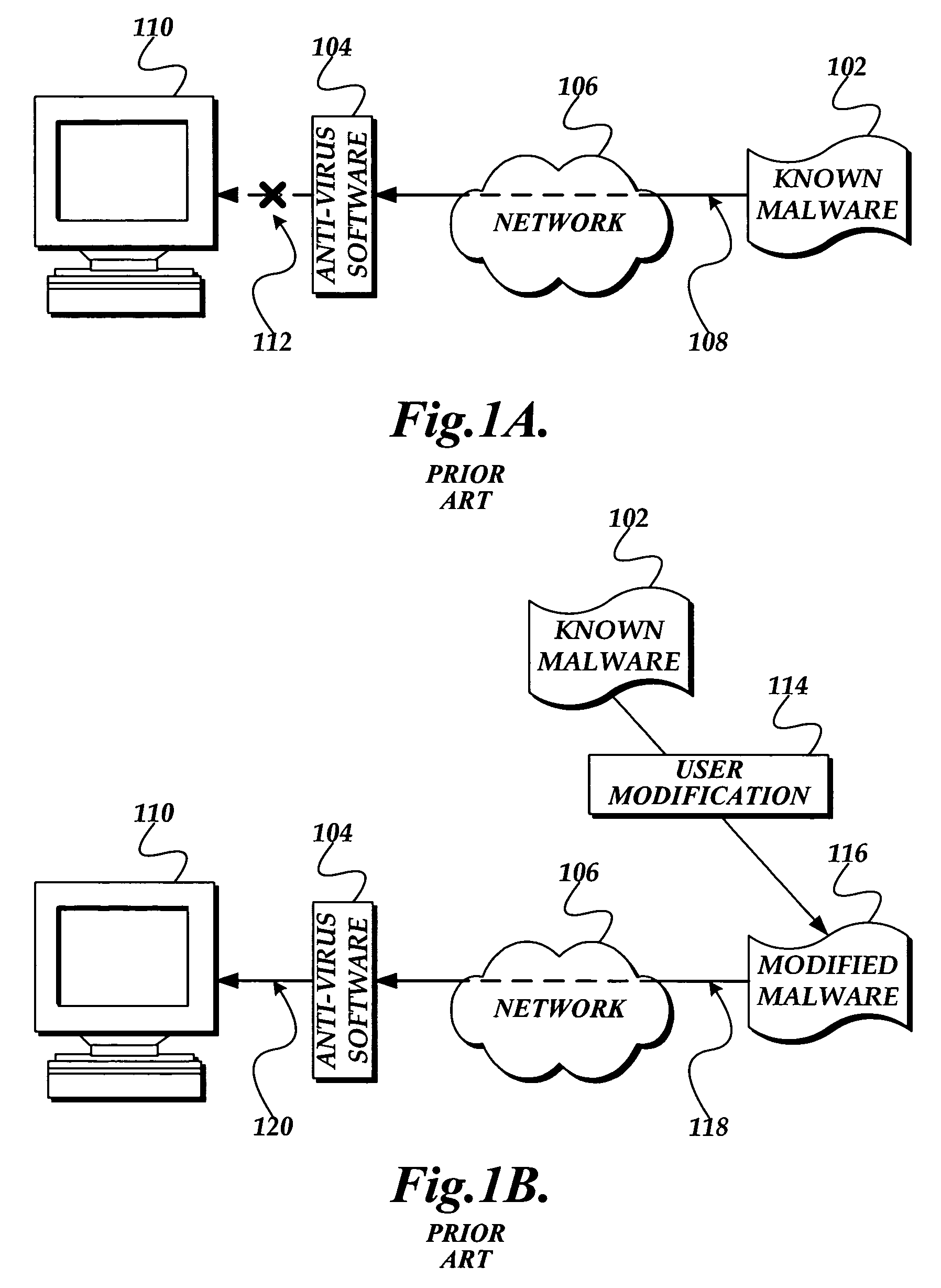
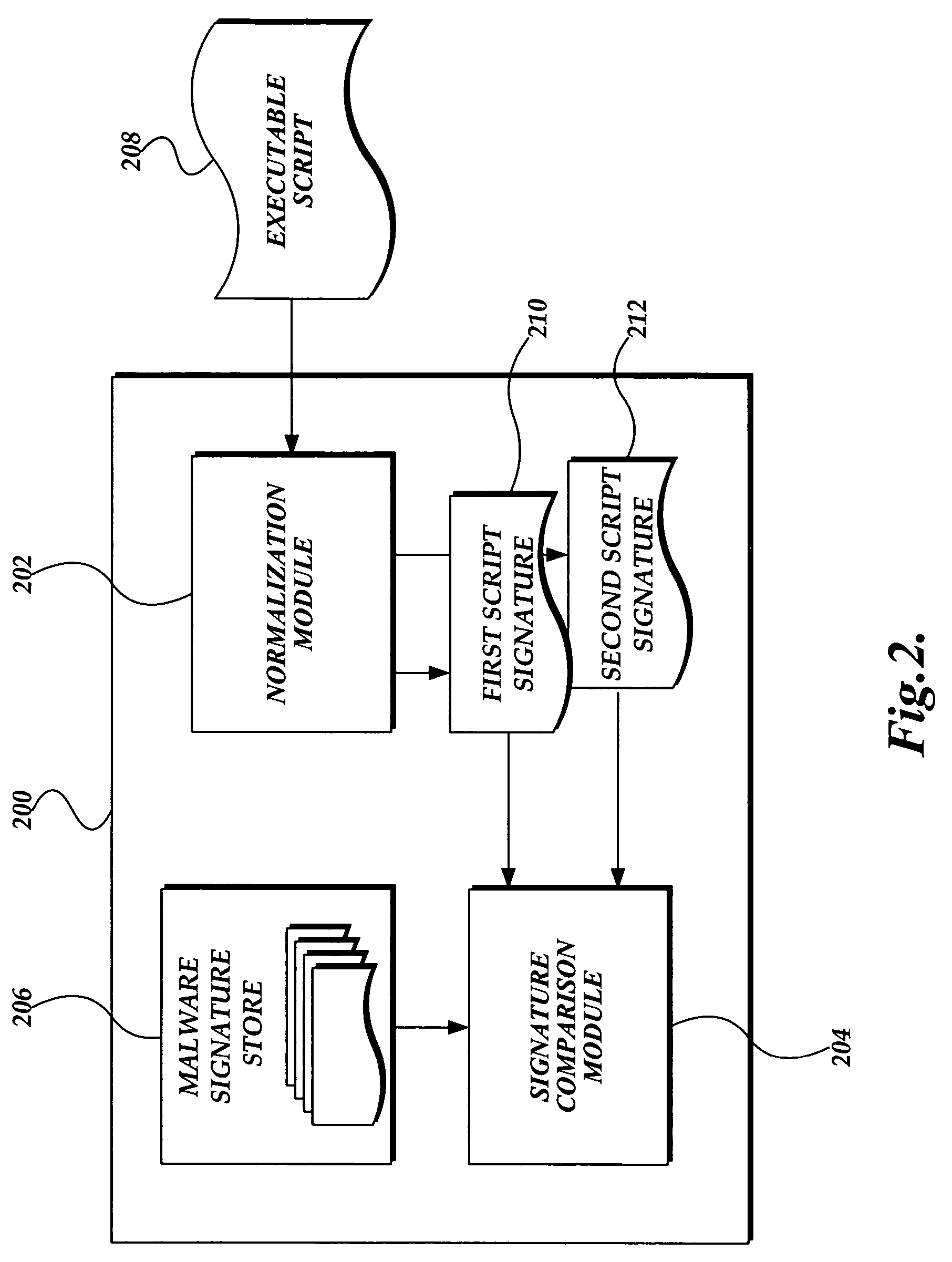
System and method for detecting malware in executable scripts according to its functionality
A malware detection system and method for determining whether an executable script is malware is presented. The malware detection system determines whether the executable script is malware by comparing the functional contents of the executable script to the functional contents of known malware. In practice, the executable script is obtained. The executable script is normalized, thereby generating a script signature corresponding to the functionality of the executable script. The script signature is compared to known malware script signatures in a malware signature store to determine whether the executable script is malware. If a complete match is made, the executable script is considered to be malware. If a partial match is made, the executable script is considered to likely be malware. The malware detection system may perform two normalizations, each normalization generating a script signature which is compared to similarly normalized known malware script signatures in the malware signature store.
Owner:MICROSOFT TECH LICENSING LLC
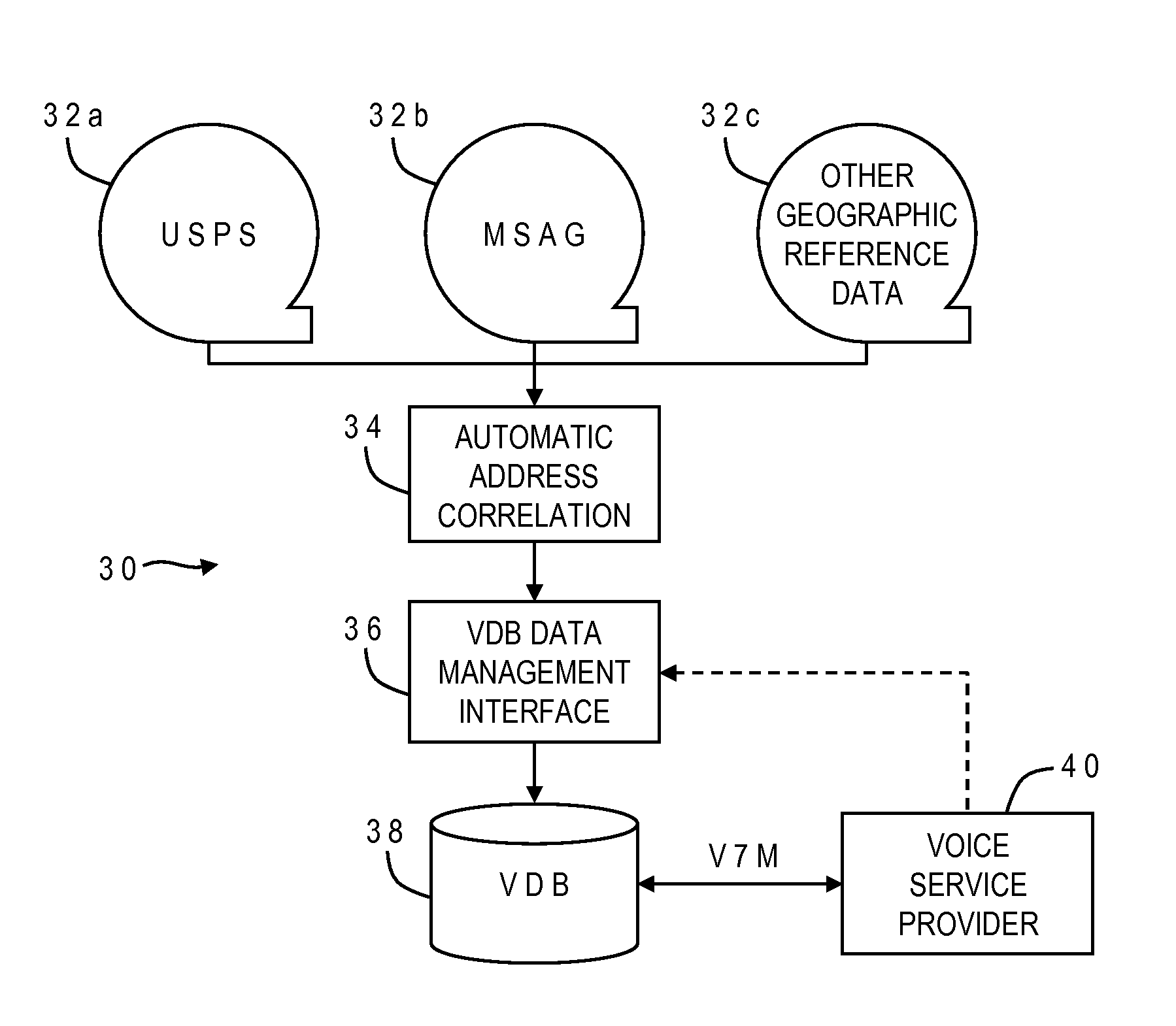
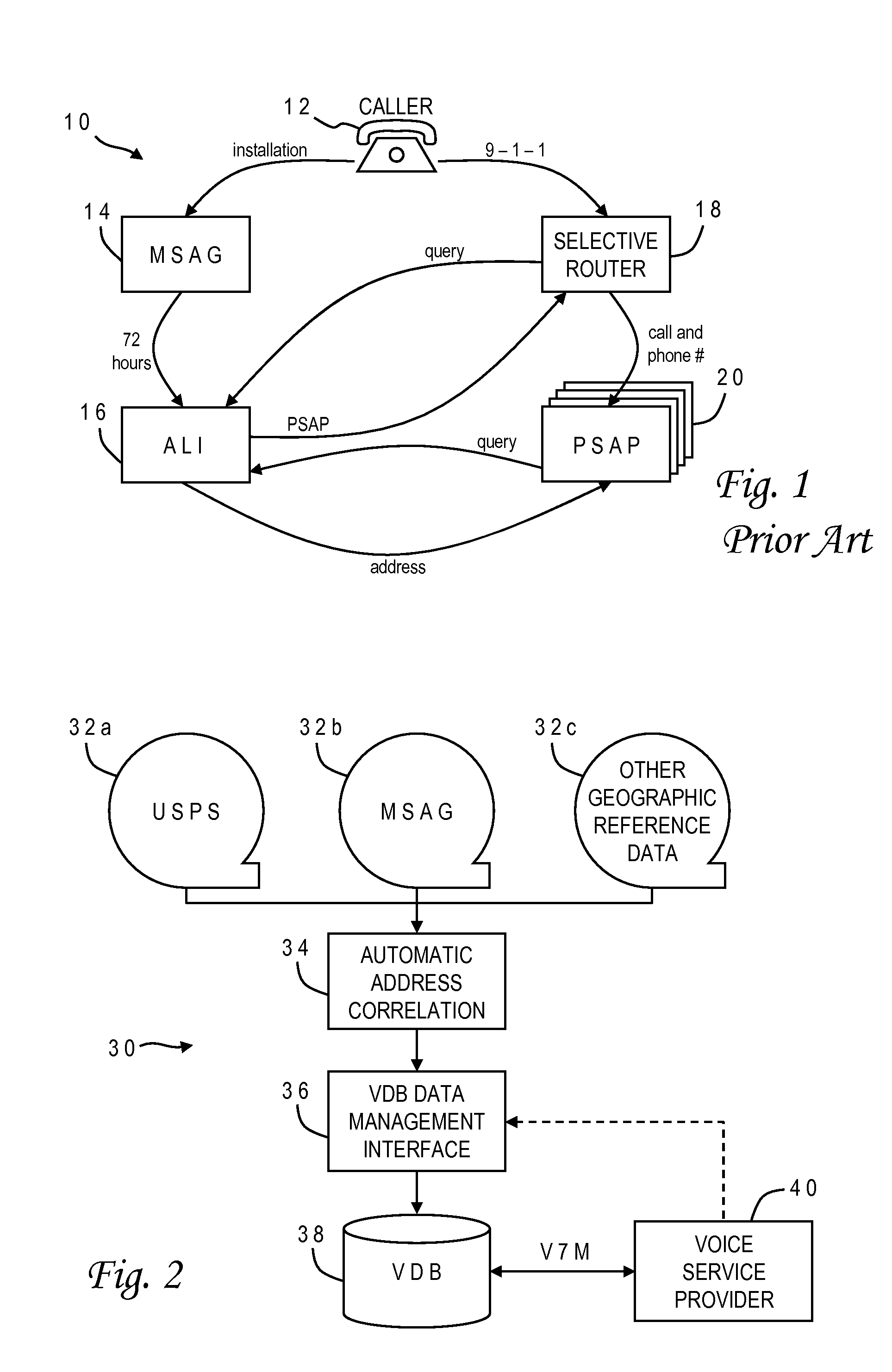
Method of building a validation database
InactiveUS20090094270A1Easy and quick correctionValid matchGeographical information databasesSpecial data processing applicationsExact matchData source
A validation database (VDB) is built from geographic reference data sources such as MSAG and USPS using automatic address correlation, and links between the records are stored in the VDB. The automatic address correlation employs multiple correlation algorithms, and a score is assigned to each link representing a confidence level. The score is based on a combination of results from the different algorithms. Links having a score representing a partial or exact match are used for address validation purposes. A management interface allows the VDB agent to edit master records and the links, including the score. A remote subscriber can request validation of a proposed address from the VDB, and may include match criteria with the request. If any matches are found, a validation reply is sent from the VDB to the subscriber with the corresponding MSAG records.
Owner:WEST SAFETY SERVICES INC
Associative database scanning and information retrieval
InactiveUS7181437B2Threshold may be loweredRaise the importanceData processing applicationsInput/output to record carriersMass storageExact match
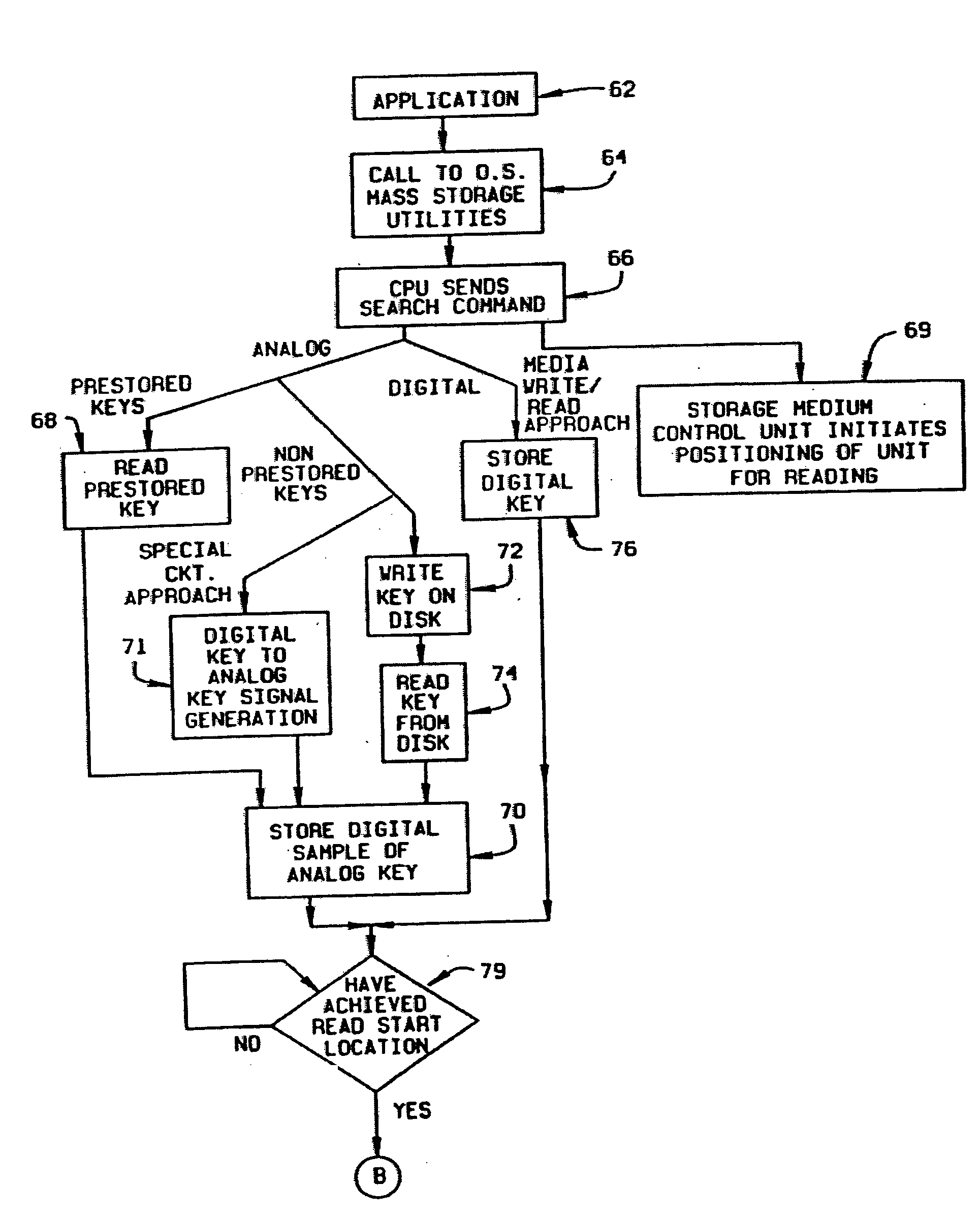
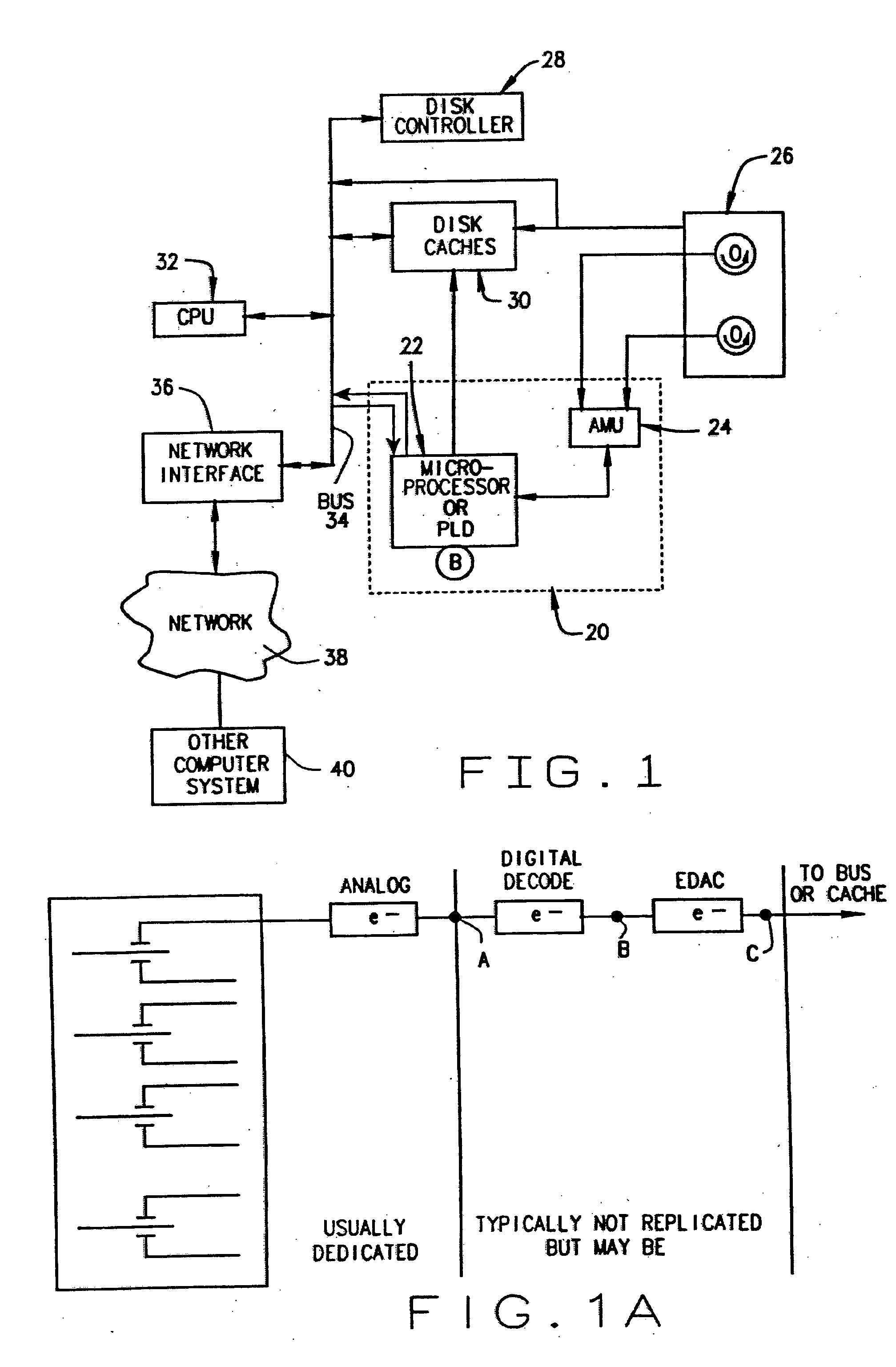
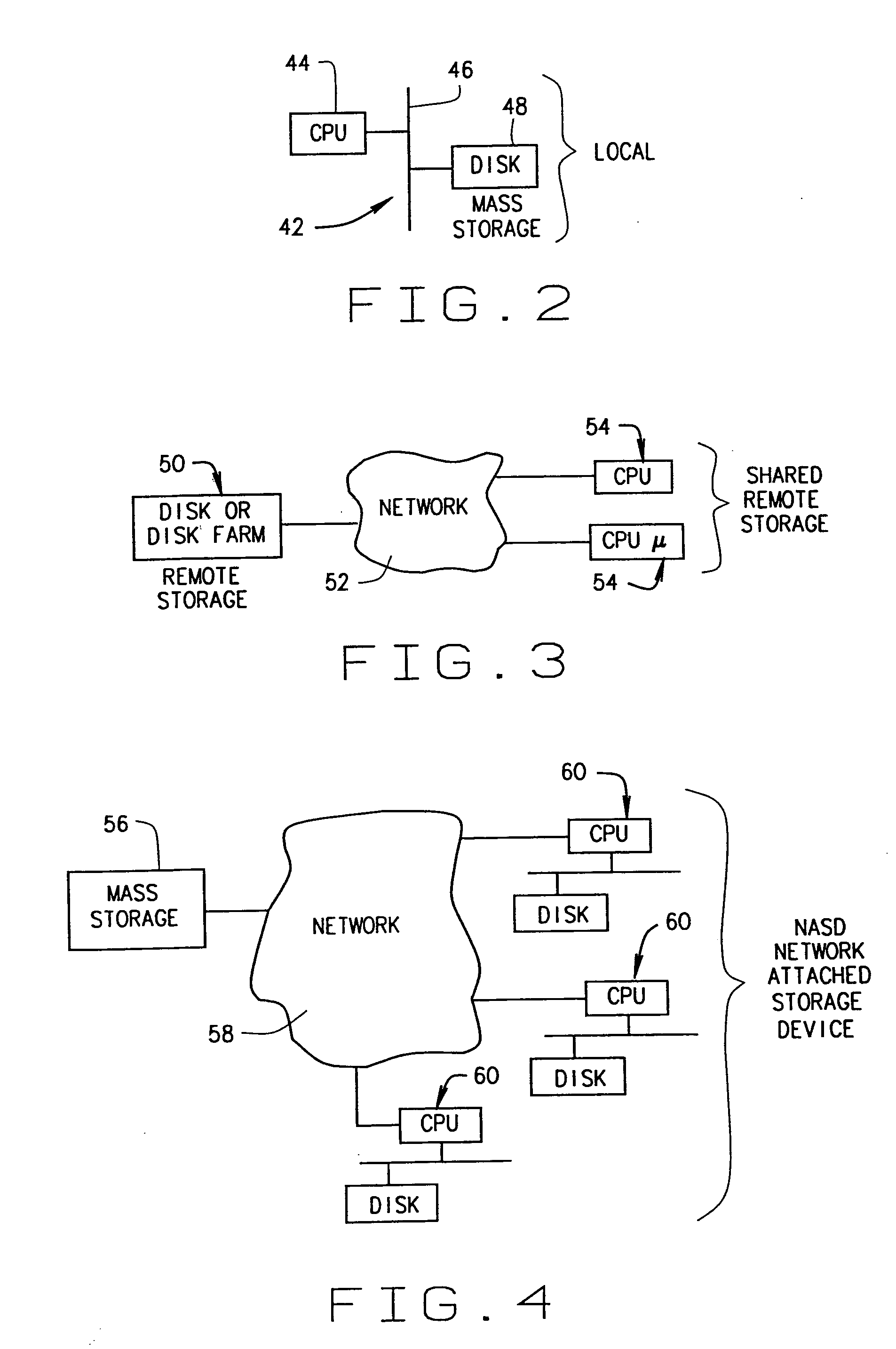
A method and device are disclosed for an associative and approximate, analog or digital scanning of databases that allows for the asynchronous accessing of data from a mass storage medium. The invention includes providing dedicated analog and digital circuitry and decision logic at the mass storage medium level for determining a key identifying the data of interest, continuously comparing the key to a signal generated from a reading of the data from the mass storage medium with an approximate or exact matching circuit to determine a pattern match, determining a correlation value between the key and the data as it is read in a continuous fashion, and determining a match based upon a preselected threshold value for the correlation value. The pattern matching technique eliminates any need to compare data based on its intrinsic structure or value, and instead is based on an analog or digital pattern. The key and data may be either analog or digital. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN.
Owner:IP RESERVOIR
Associative Database Scanning and Information Retrieval
InactiveUS20070118500A1Threshold may be loweredRaise the importanceData processing applicationsInput/output to record carriersMass storagePattern matching
A method and device are disclosed for an associative and approximate, analog or digital scanning of databases that allows for the asynchronous accessing of data from a mass storage medium. The invention includes providing dedicated analog and digital circuitry and decision logic at the mass storage medium level for determining a key identifying the data of interest, continuously comparing the key to a signal generated from a reading of the data from the mass storage medium with an approximate or exact matching circuit to determine a pattern match, determining a correlation value between the key and the data as it is read in a continuous fashion, and determining a match based upon a preselected threshold value for the correlation value. The pattern matching technique eliminates any need to compare data based on its intrinsic structure or value, and instead is based on an analog or digital pattern. The key and data may be either analog or digital. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN.
Owner:IP RESERVOIR
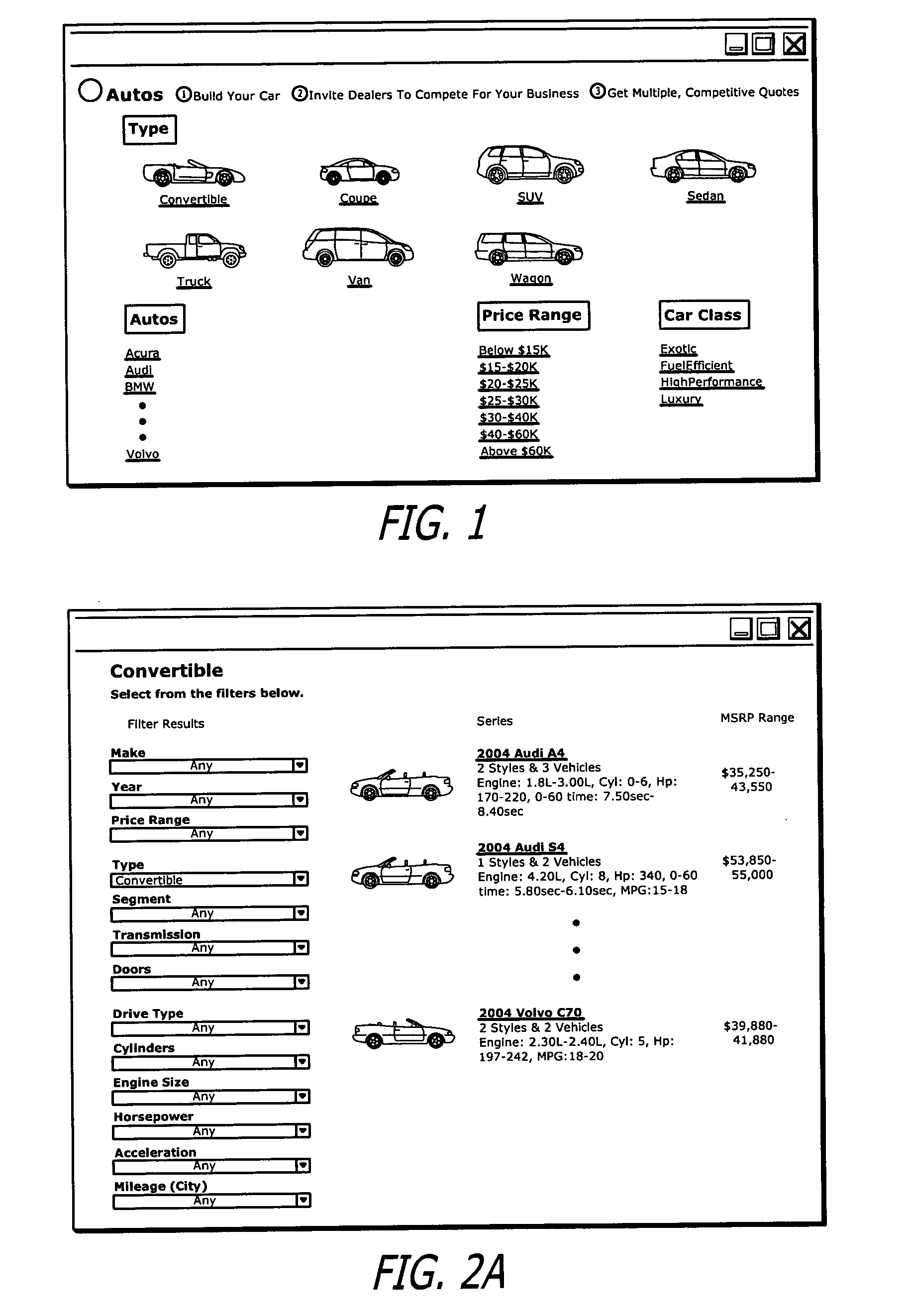
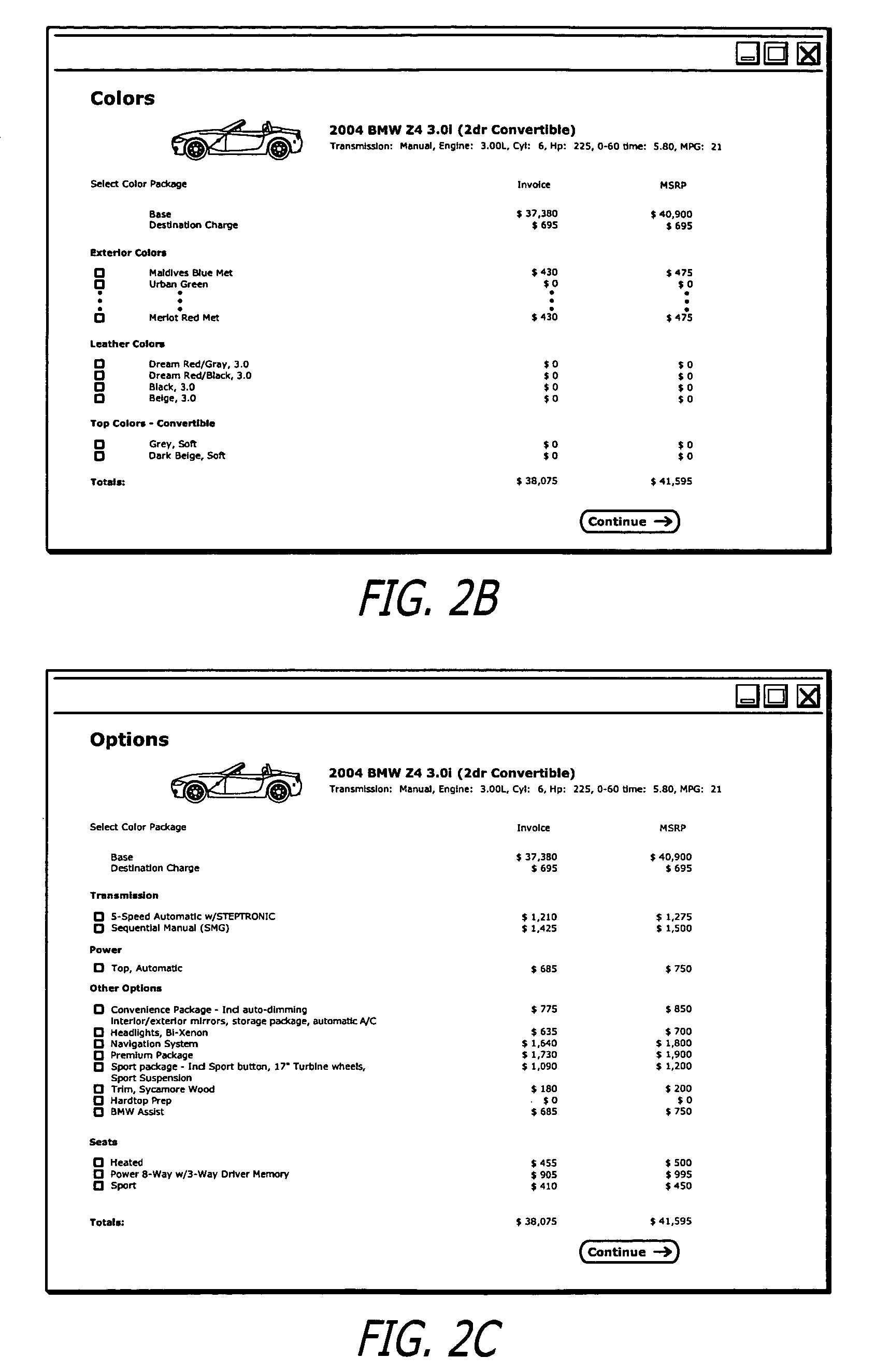
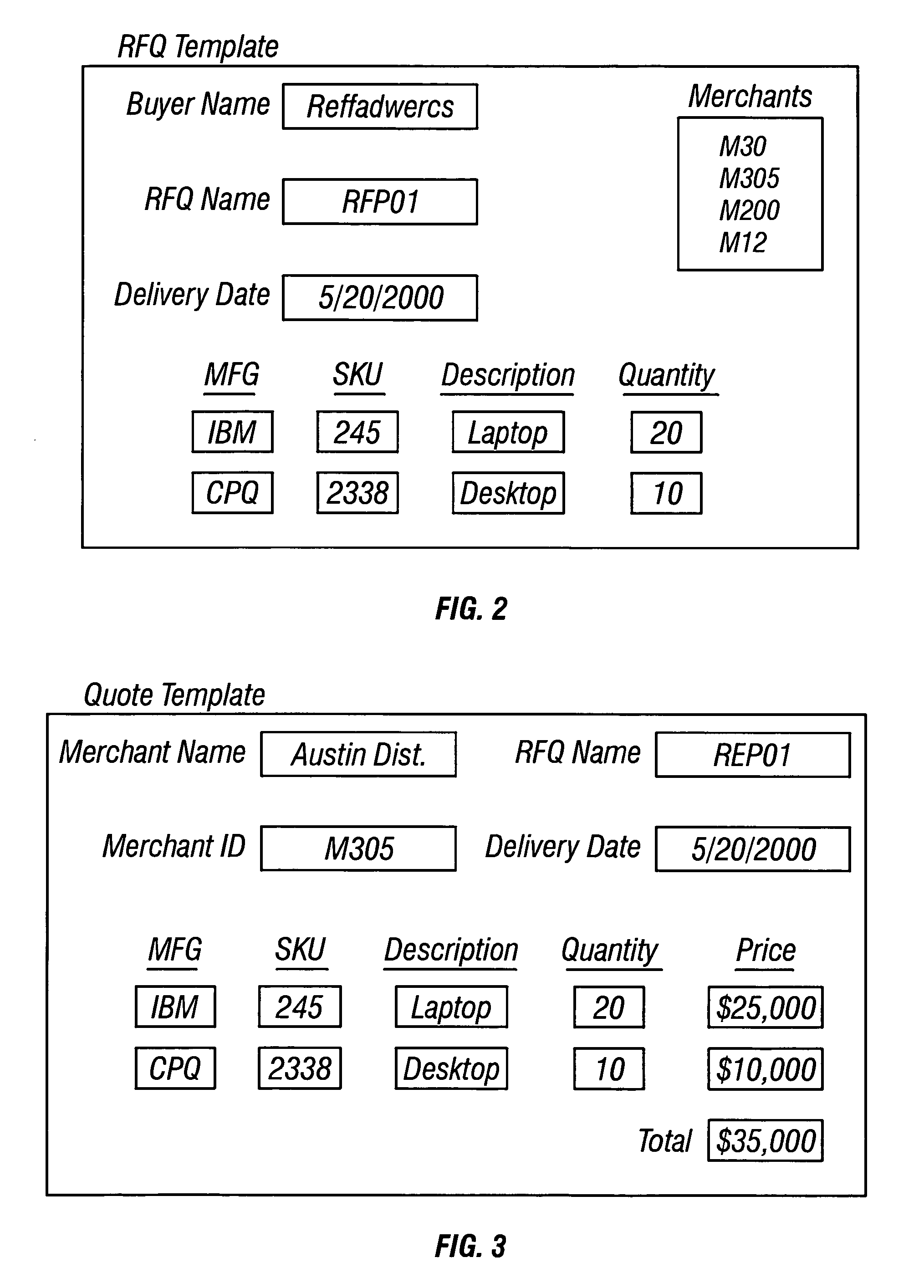
System and network for obtaining competitive quotes on user-configured articles
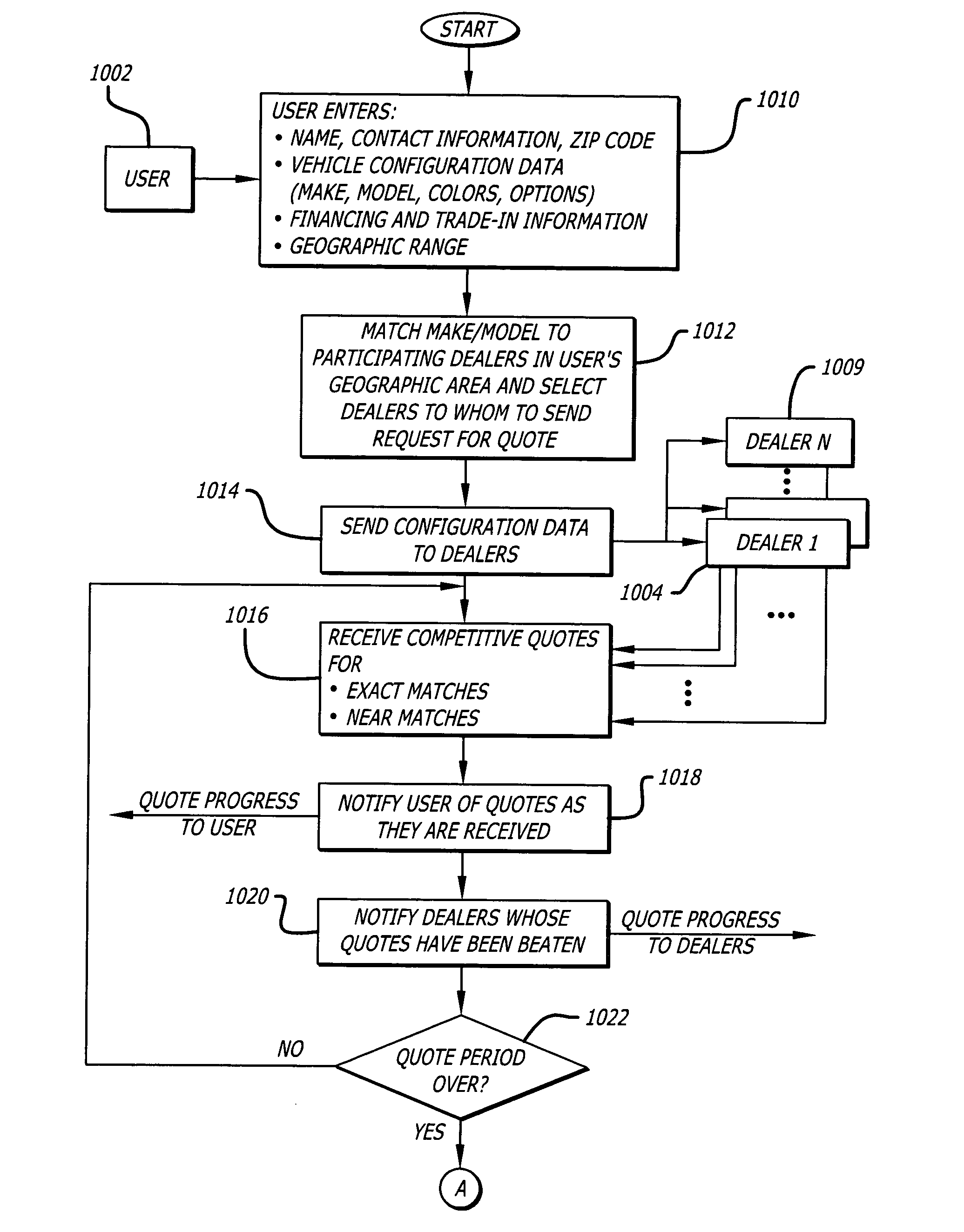
Configuration data received from a consumer regarding a configurable article such as an automobile in which the consumer is interested in purchasing is entered by the consumer and automatically forwarded to a number of participating dealers within the consumer's geographic area. The dealers can respond by quoting for an exact match of the article as configured or for a near exact match. The consumer is notified of the progress of quotes received as they are received. At the close of the quote period contact information is automatically exchanged between the consumer and the dealer who submitted the lowest exact match quote, and the dealer is charged a referral fee. The consumer can also request information regarding a selected non-exact match quote whereupon contact information is automatically exchanged between the consumer and the second dealer, and the second dealer is also charged a referral fee.
Owner:PRICEGRABBER COM
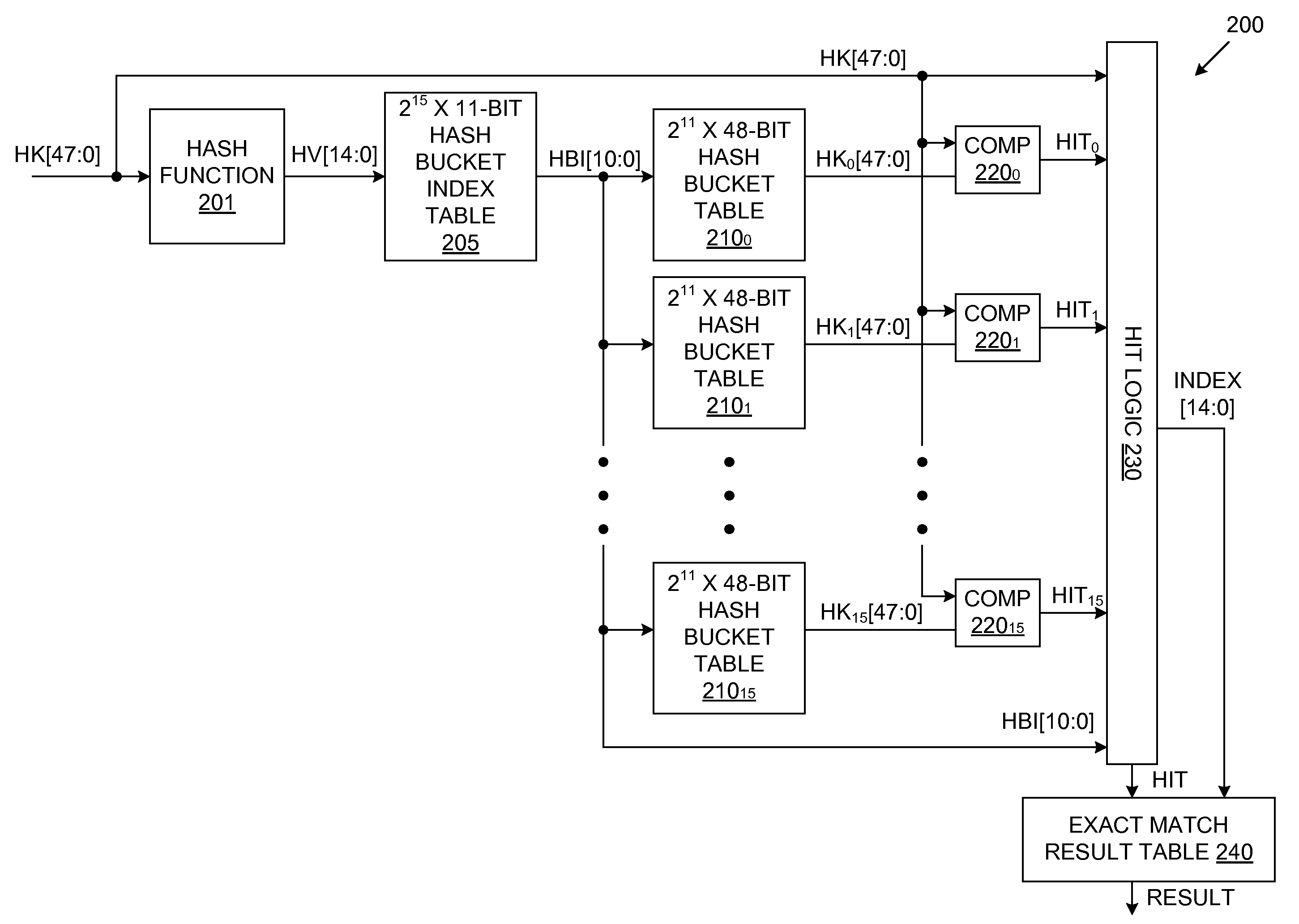
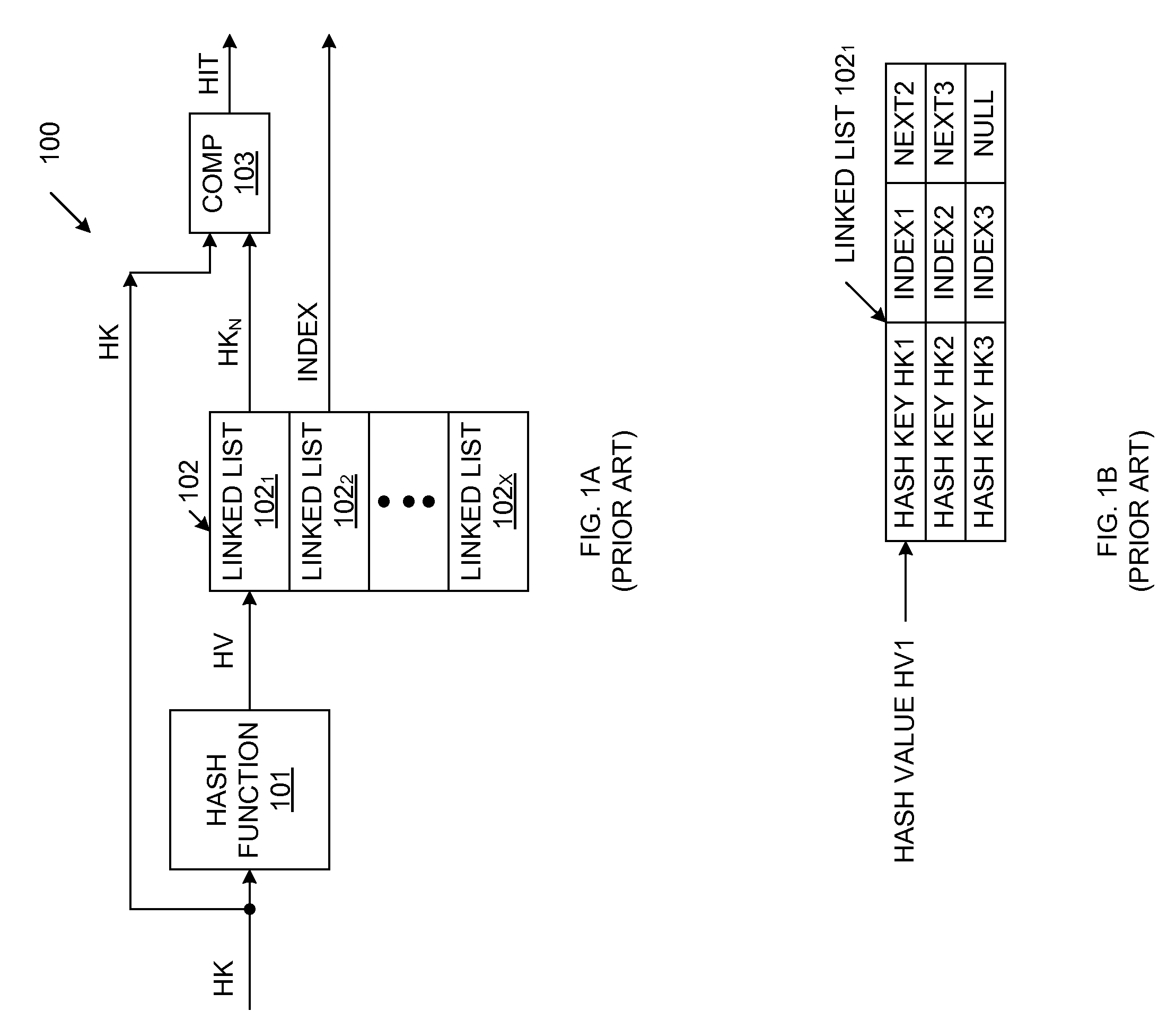
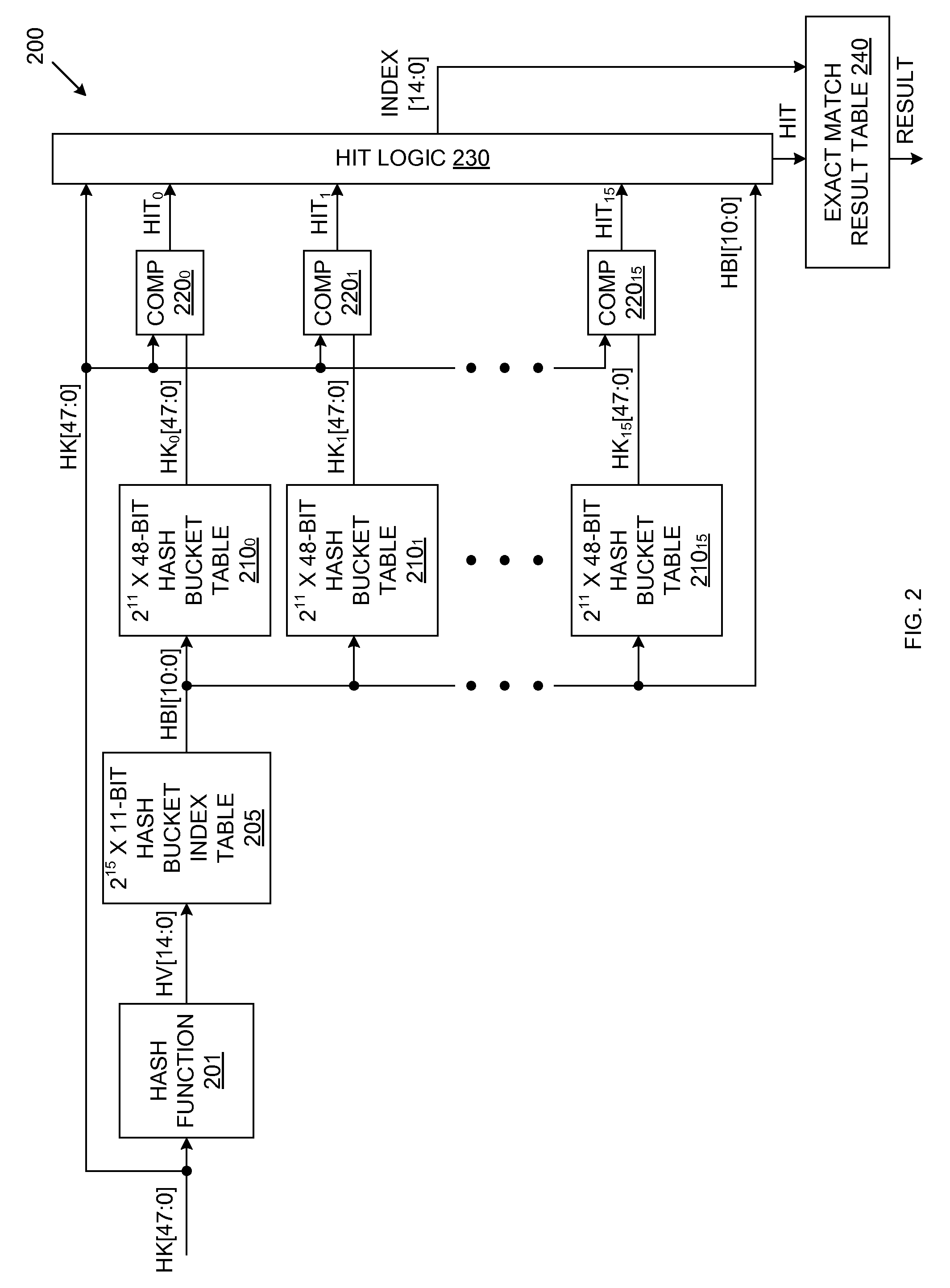
Exact Match Lookup Scheme
InactiveUS20110060876A1Digital data information retrievalData switching networksExact matchHash table
An exact match lookup system includes a hash function that generates a hash value in response to an input hash key. The hash value is used to retrieve a hash bucket index value from a hash bucket index table. The hash bucket index value is used to retrieve a plurality of hash keys from a plurality of hash bucket tables, in parallel. The retrieved hash keys are compared with the input hash key to identify a match. Hit logic generates an output index by concatenating the hash bucket index value with an address associated with the hash bucket table that provides the matching hash key. An exact match result is provided in response to the output index. A content addressable memory (CAM) may store hash keys that do not fit in the hash bucket tables.
Owner:AVAGO TECH INT SALES PTE LTD
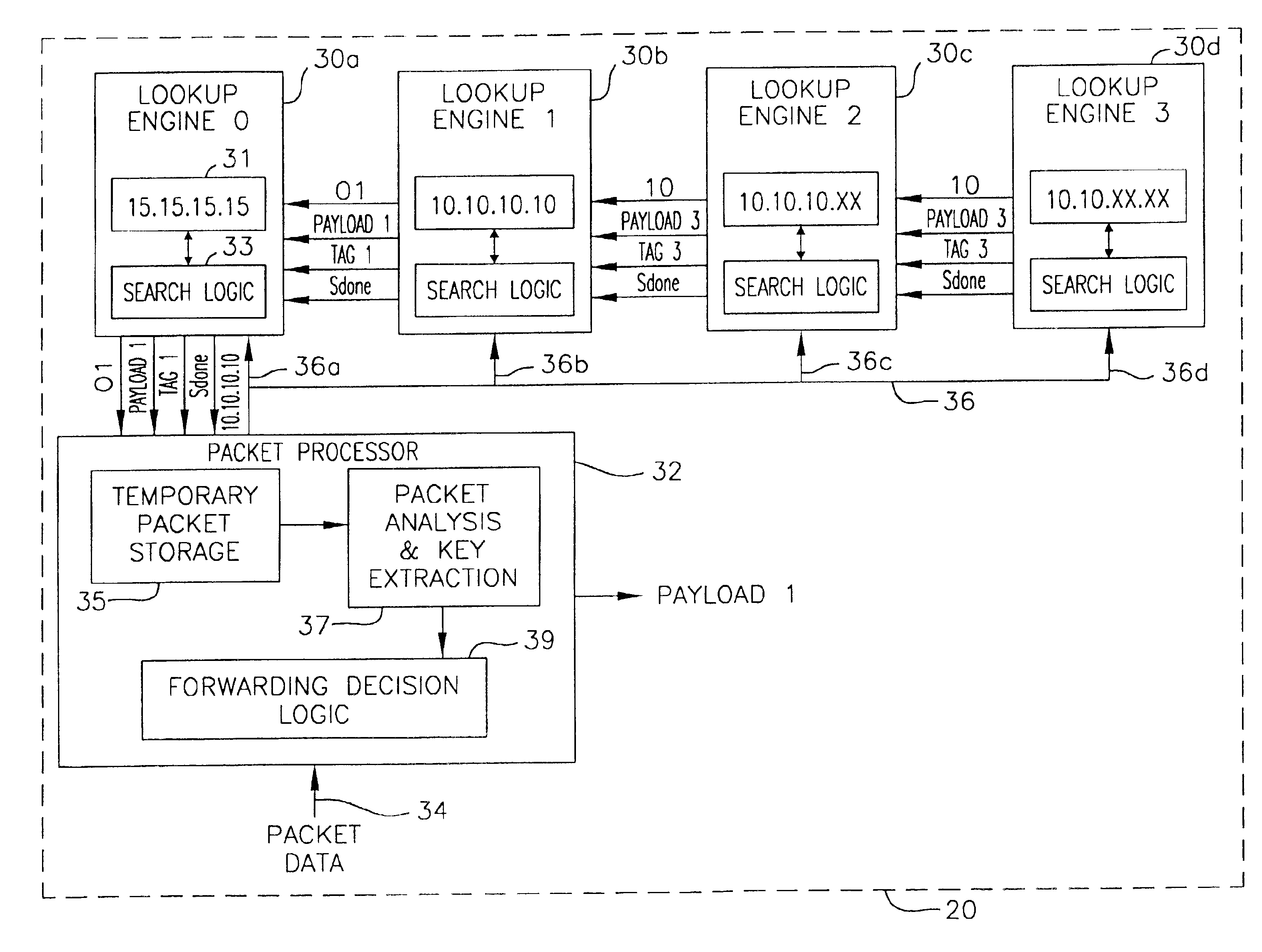
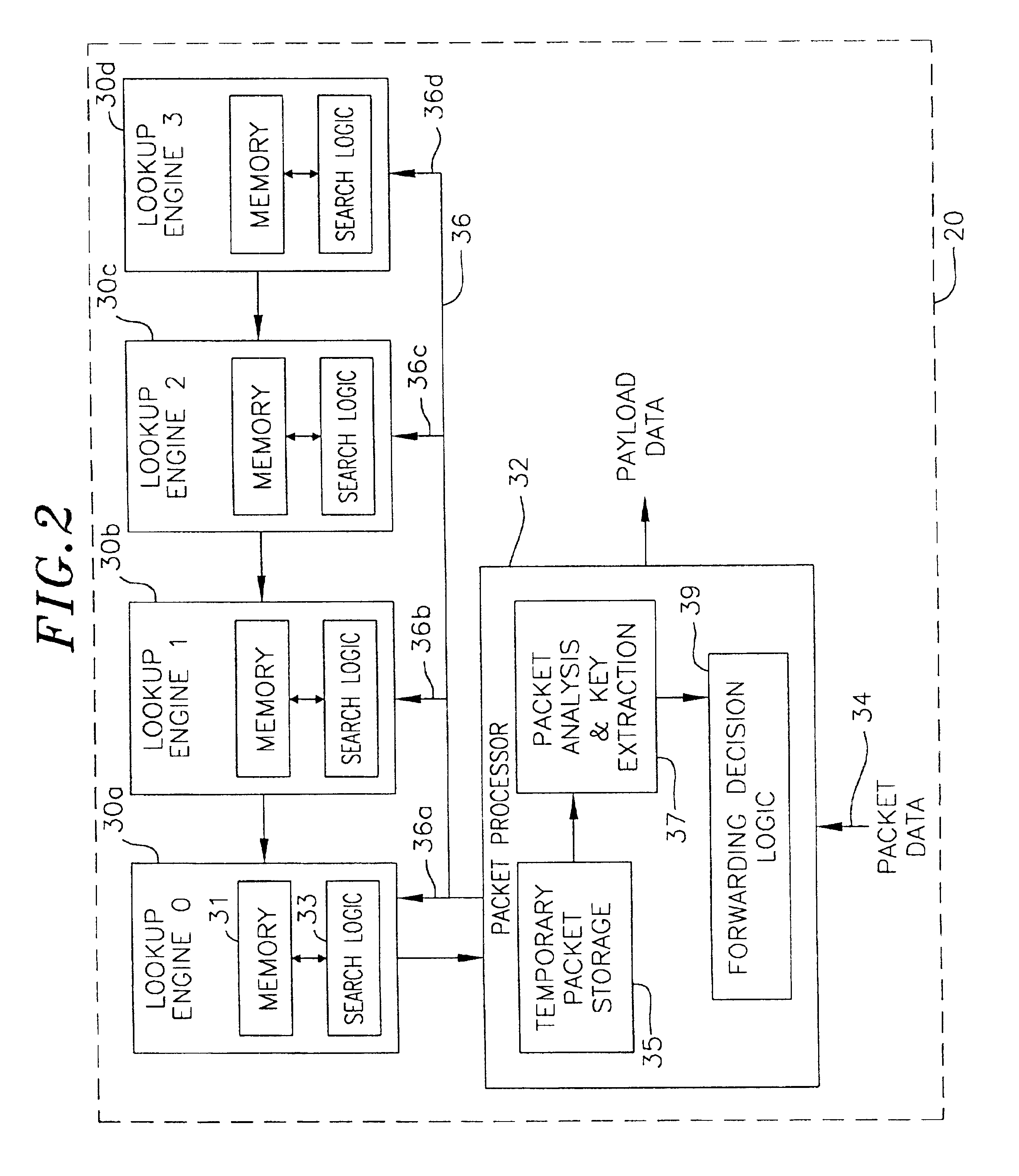
Stackable lookup engines
InactiveUS6957272B2Increase in sizeDigital computer detailsData switching by path configurationExact matchComputer science
Owner:ALCATEL INTERNETWORKING PE
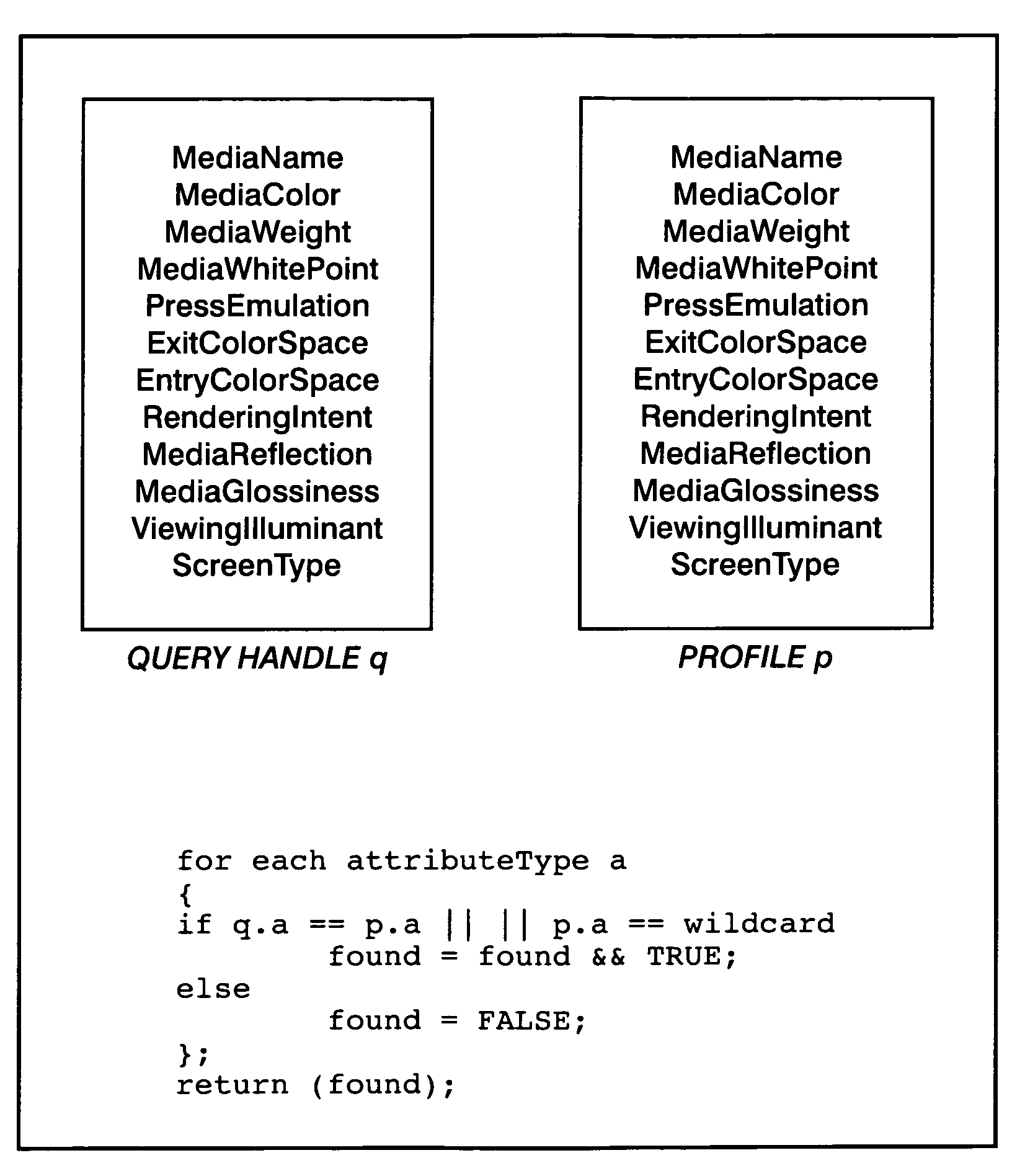
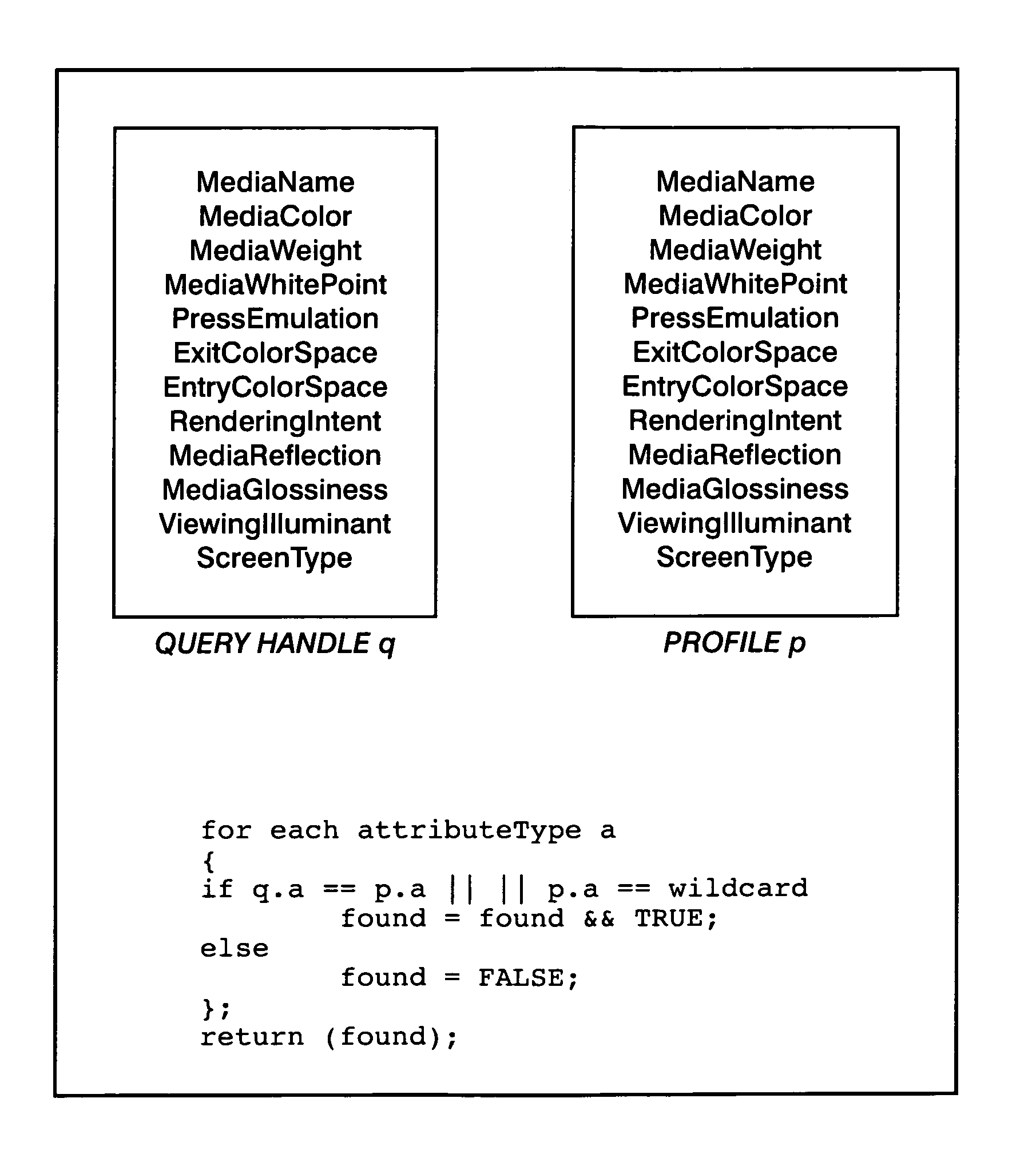
Simple mechanism for profile selection
In a system where the color space conversion process uses color profile look-up tables to select a profile for each of the possible attribute value combinations, assigning a value of wildcard to one or more attributes. In this case, if all of the values of one of the attributes can not be exactly matched, and that attribute has a wildcard value, the wildcard value is selected. The profile associated with the wildcard is designed to enable a reasonable color conversion in any case where an attribute calls for a particular value and the printer does not have a corresponding profile. The result is that the printer will most likely still print a reasonable image in the case where there is no matching profile.
Owner:XEROX CORP
Method and apparatus for filtering and/or sorting responses to electronic requests for quote
A method and apparatus for filtering and / or sorting responses to electronic requests for quotes for a product or products offered for sale includes comparing first data of each of a plurality electronic quotes to first data of an electronic request for quote. Each of the plurality of electronic quotes is classified as either a matching quote or a non-matching quote. After the quotes are classified, each classified quote is ranked, for example, by the total price of the product or products offered for sale. Classification into distinct categories is used to apply techniques to make quotes comparable. Inexact matches can be adjusted to allow comparison between exact matching quotes and the adjusted inexact matching quotes.
Owner:VERSATA SOFTWARE INC
Method and system for high performance data metatagging and data indexing using coprocessors
ActiveUS8326819B2Robust and high performance data searchingHigh indexWeb data indexingDigital data processing detailsData streamCoprocessor
Disclosed herein is a method and system for hardware-accelerating the generation of metadata for a data stream using a coprocessor. Using these techniques, data can be richly indexed, classified, and clustered at high speeds. Reconfigurable logic such a field programmable gate arrays (FPGAs) can be used by the coprocessor for this hardware acceleration. Techniques such as exact matching, approximate matching, and regular expression pattern matching can be employed by the coprocessor to generate desired metadata for the data stream.
Owner:IP RESERVOIR
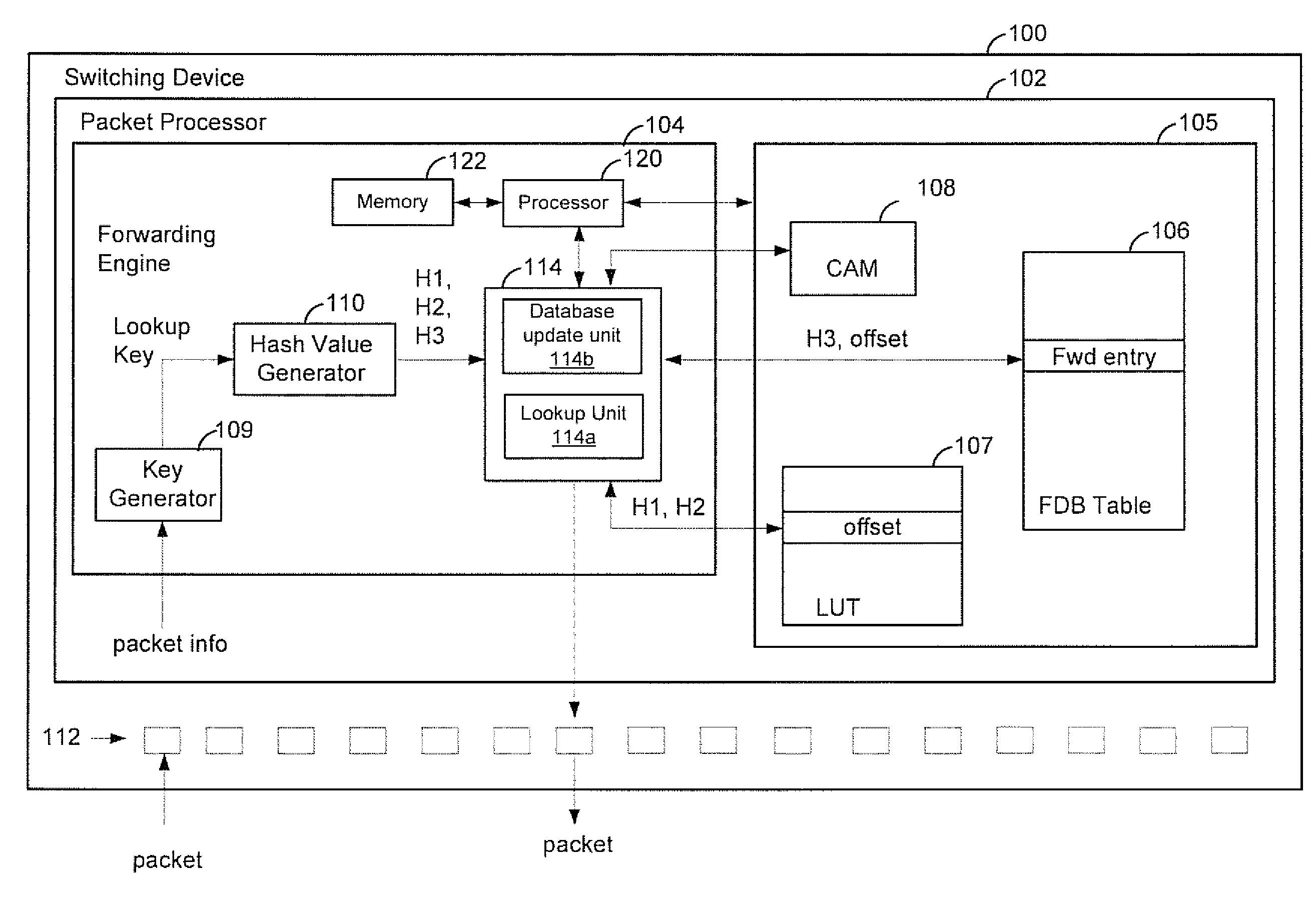
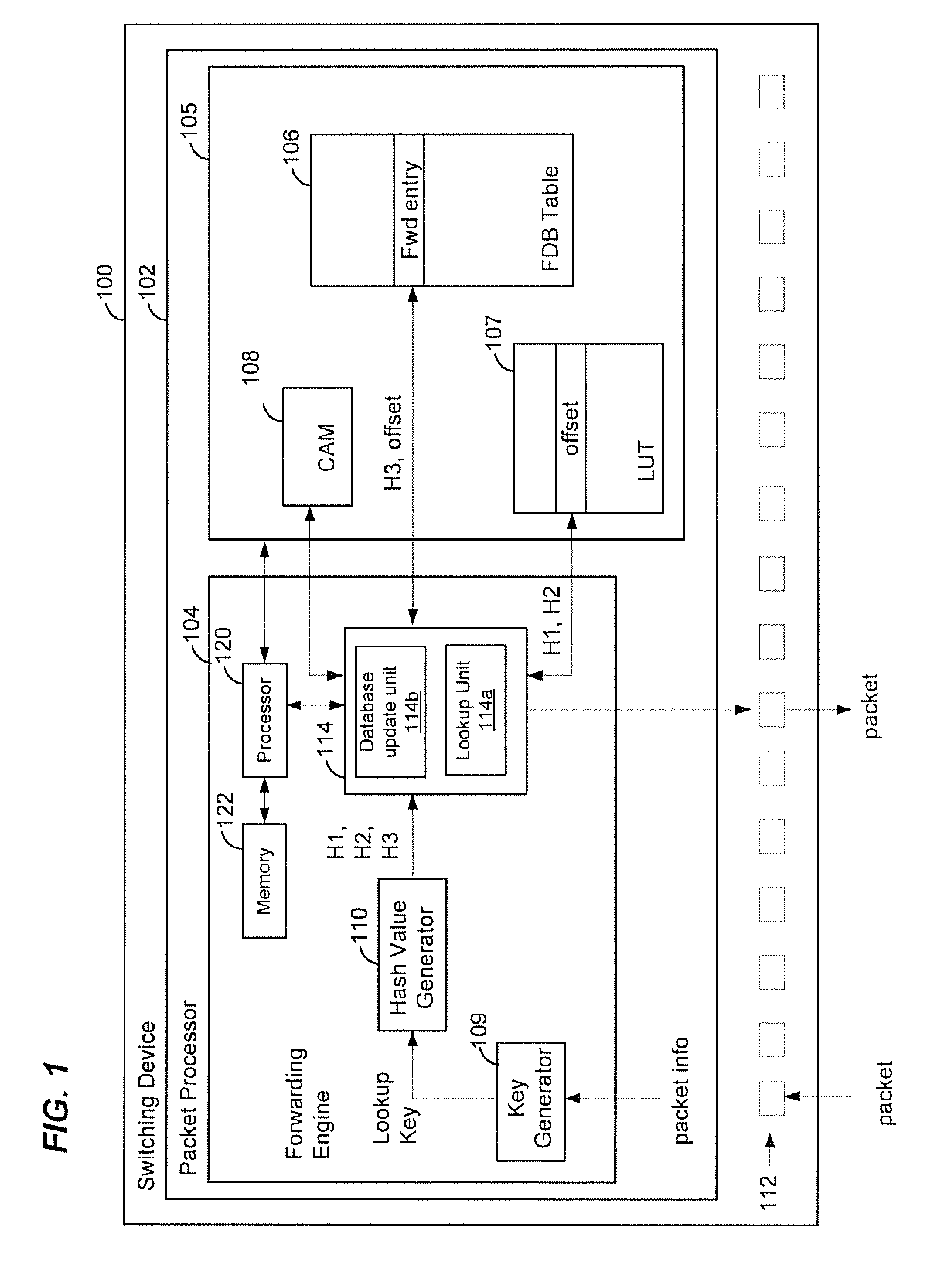
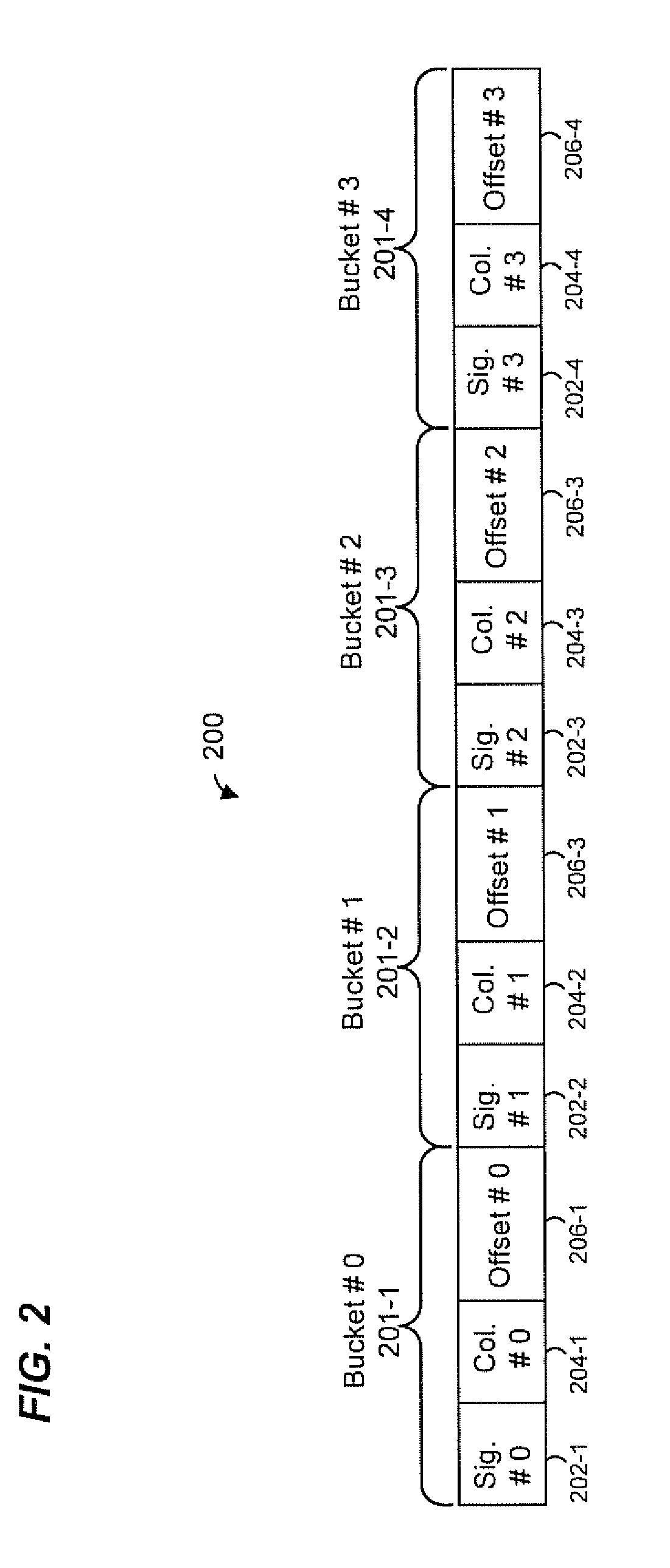
Exact match hash lookup databases in network switch devices
ActiveUS20140301394A1Data switching by path configurationSpecial data processing applicationsExact matchComputer hardware
In a method for forwarding packets in a network device a plurality of hash values is generated based on a lookup key. The plurality of hash values includes at least a first hash value generated using a first hash function, a second hash value generated using a second hash function and a third hash value generated using a third hash function. The third hash function is different from the first hash function and the second hash function. A lookup table is searched using the first hash value and the second hash value to determine an offset for the lookup key. Then, a forwarding table is searched using the third hash value and the offset determined for the lookup key to select a forwarding entry corresponding to the lookup key. The packet is forwarded to one or more ports of the network device based on the selected forwarding entry.
Owner:MARVELL ISRAEL MISL
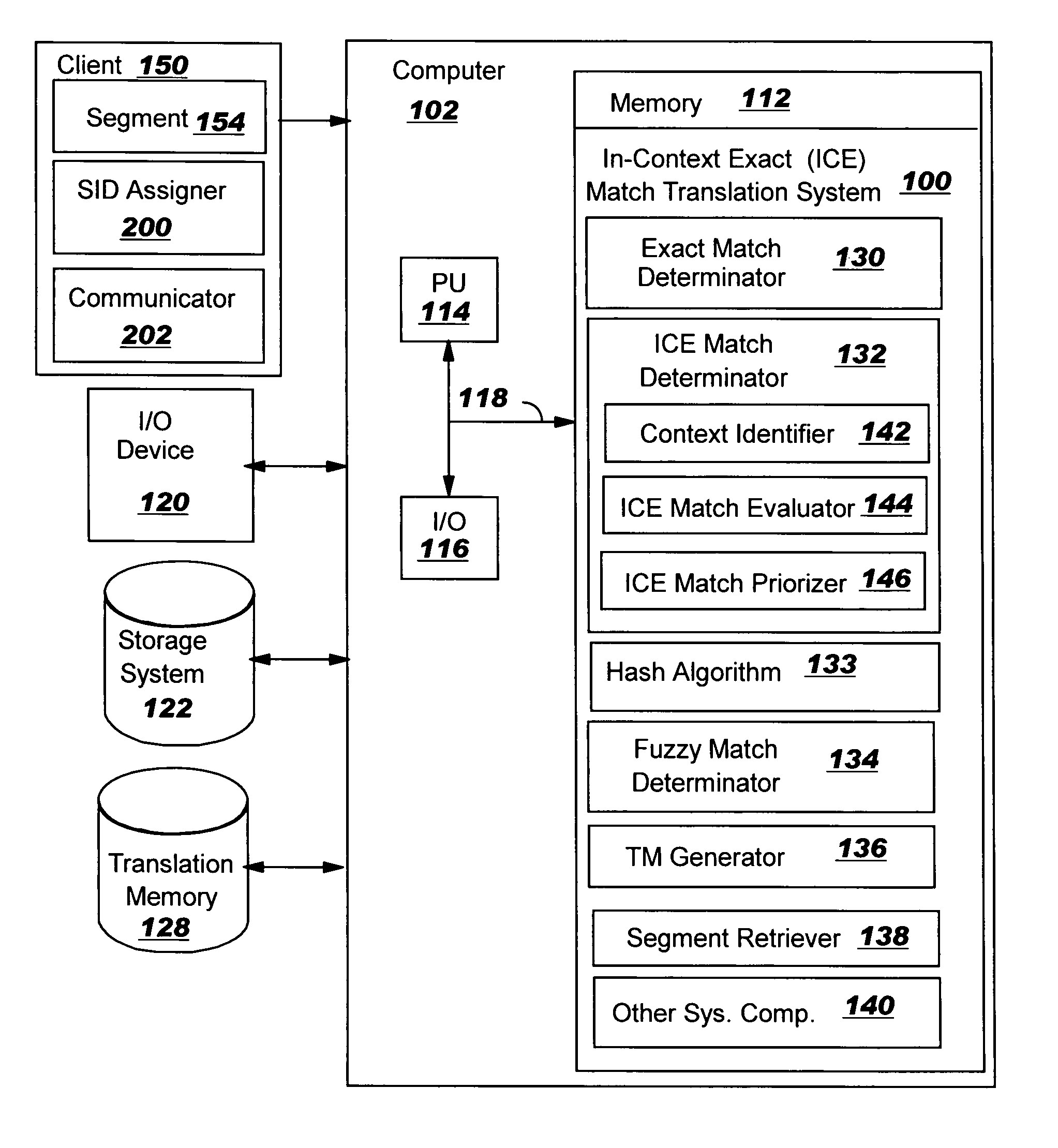
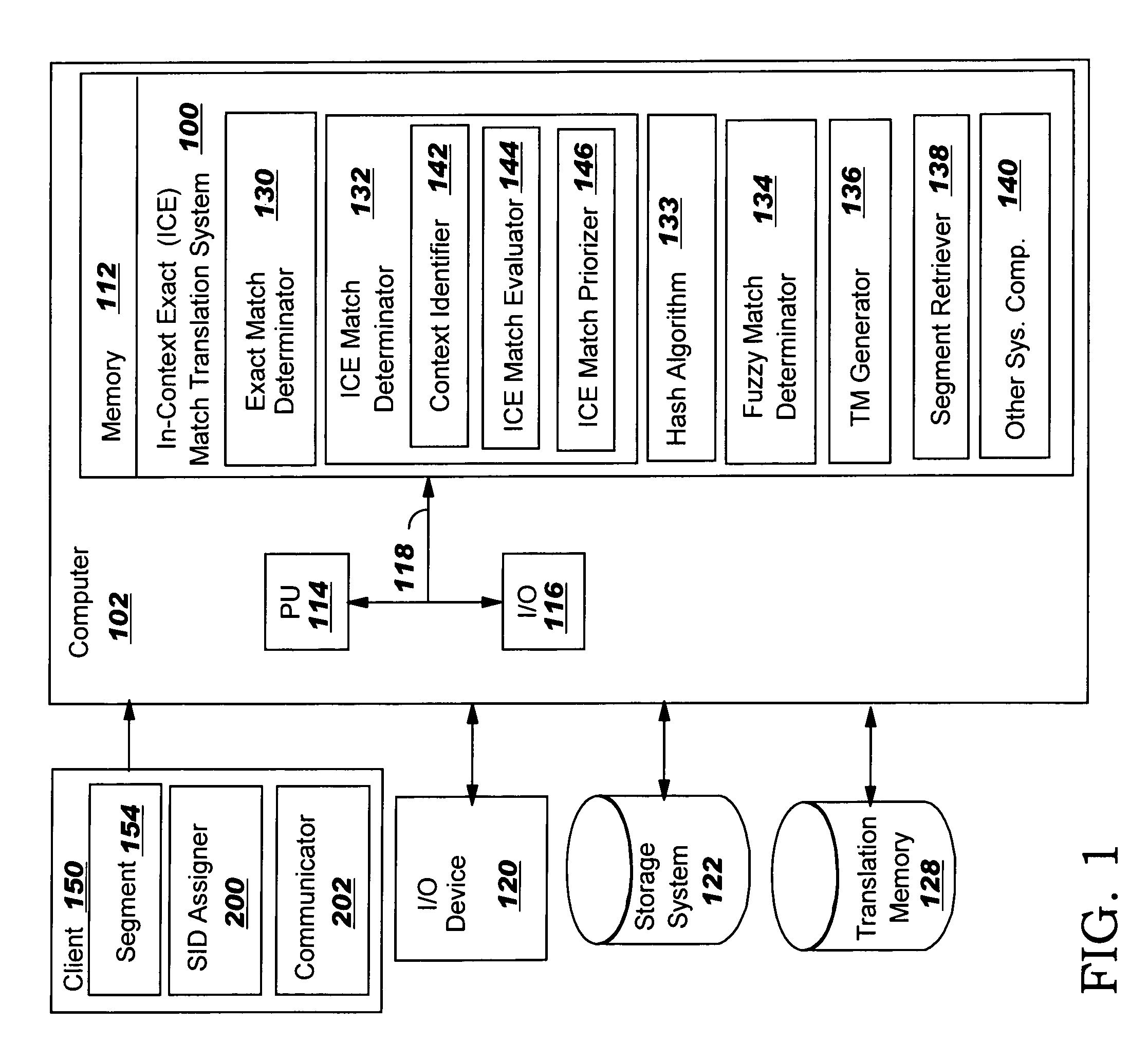
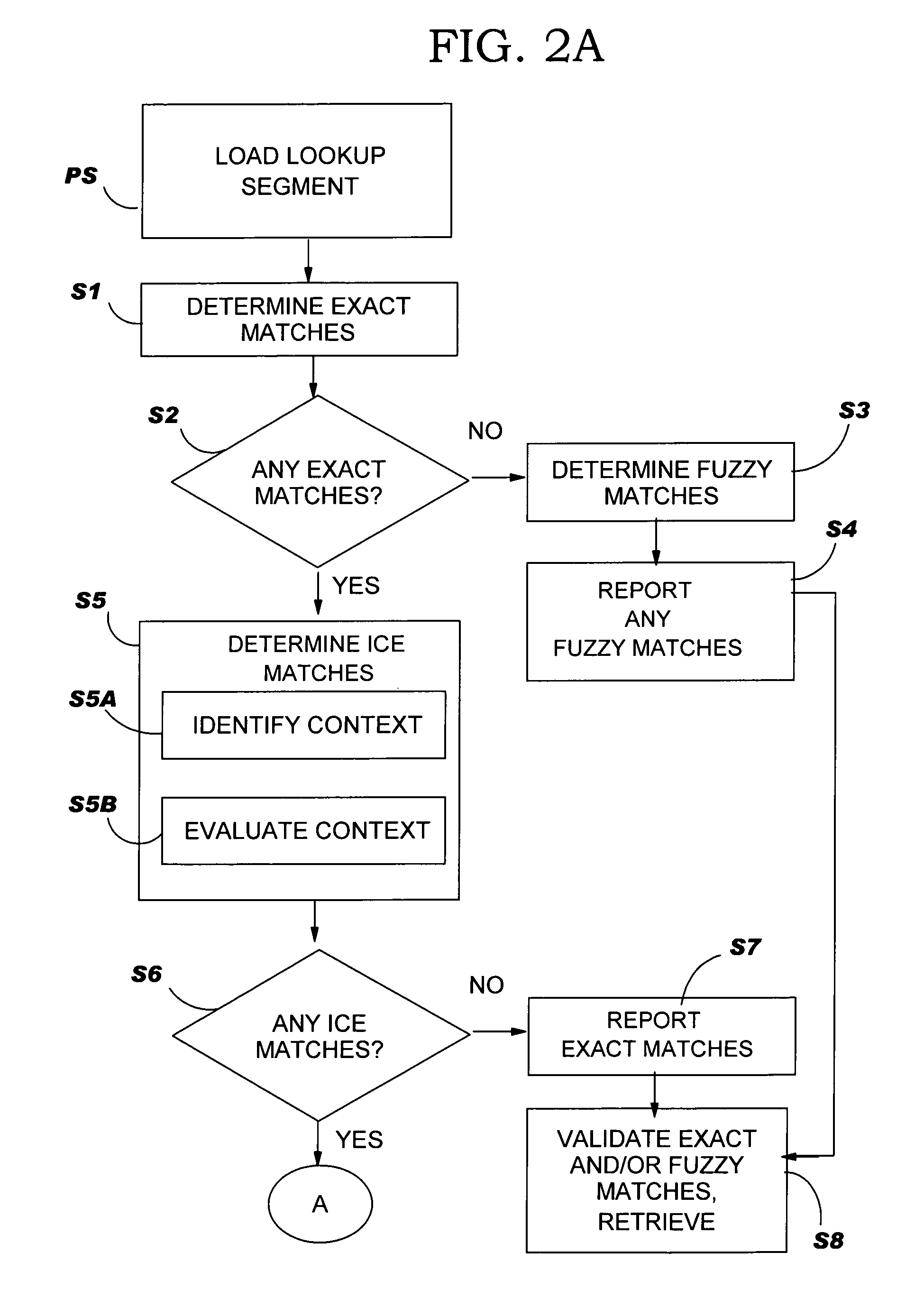
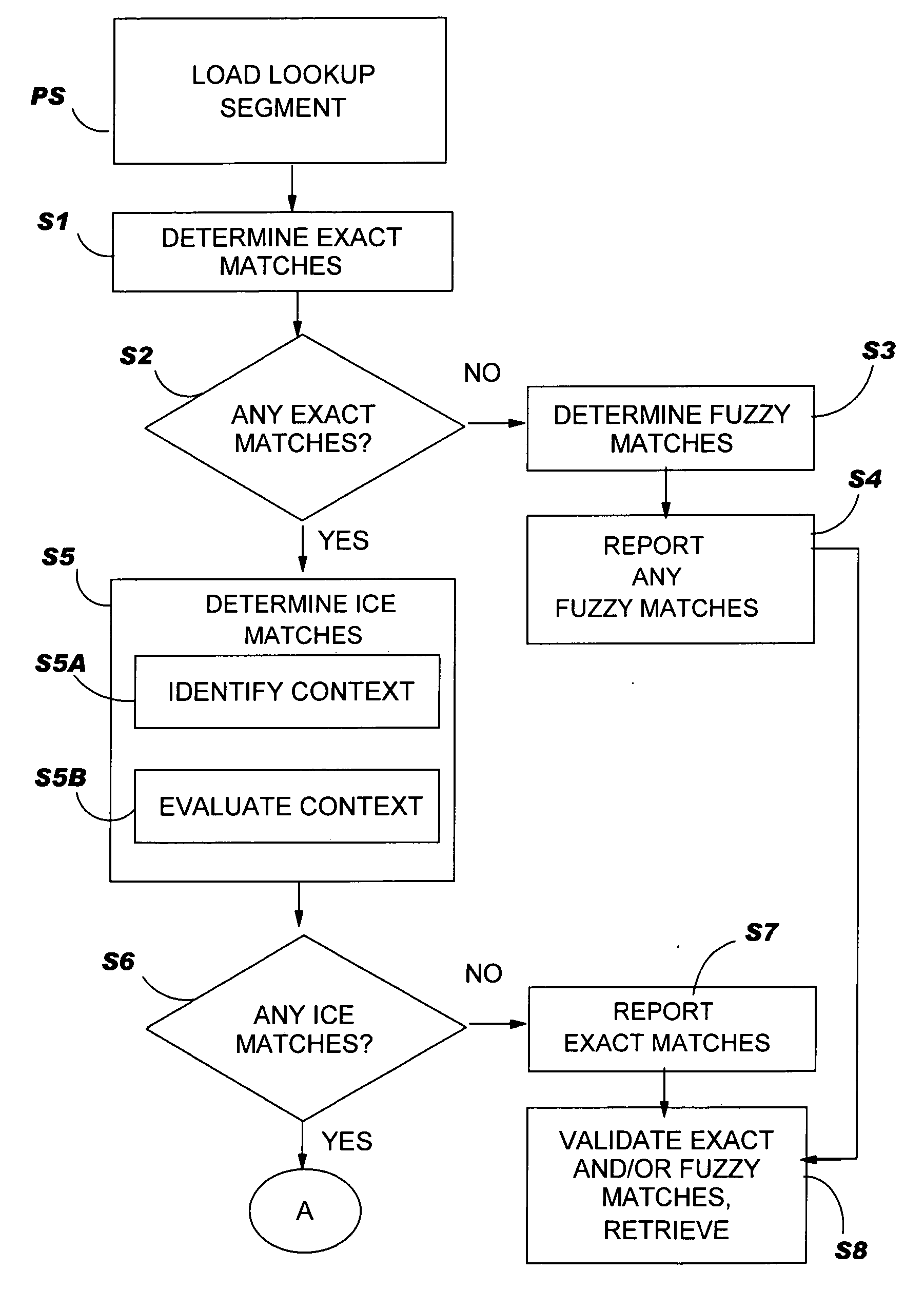
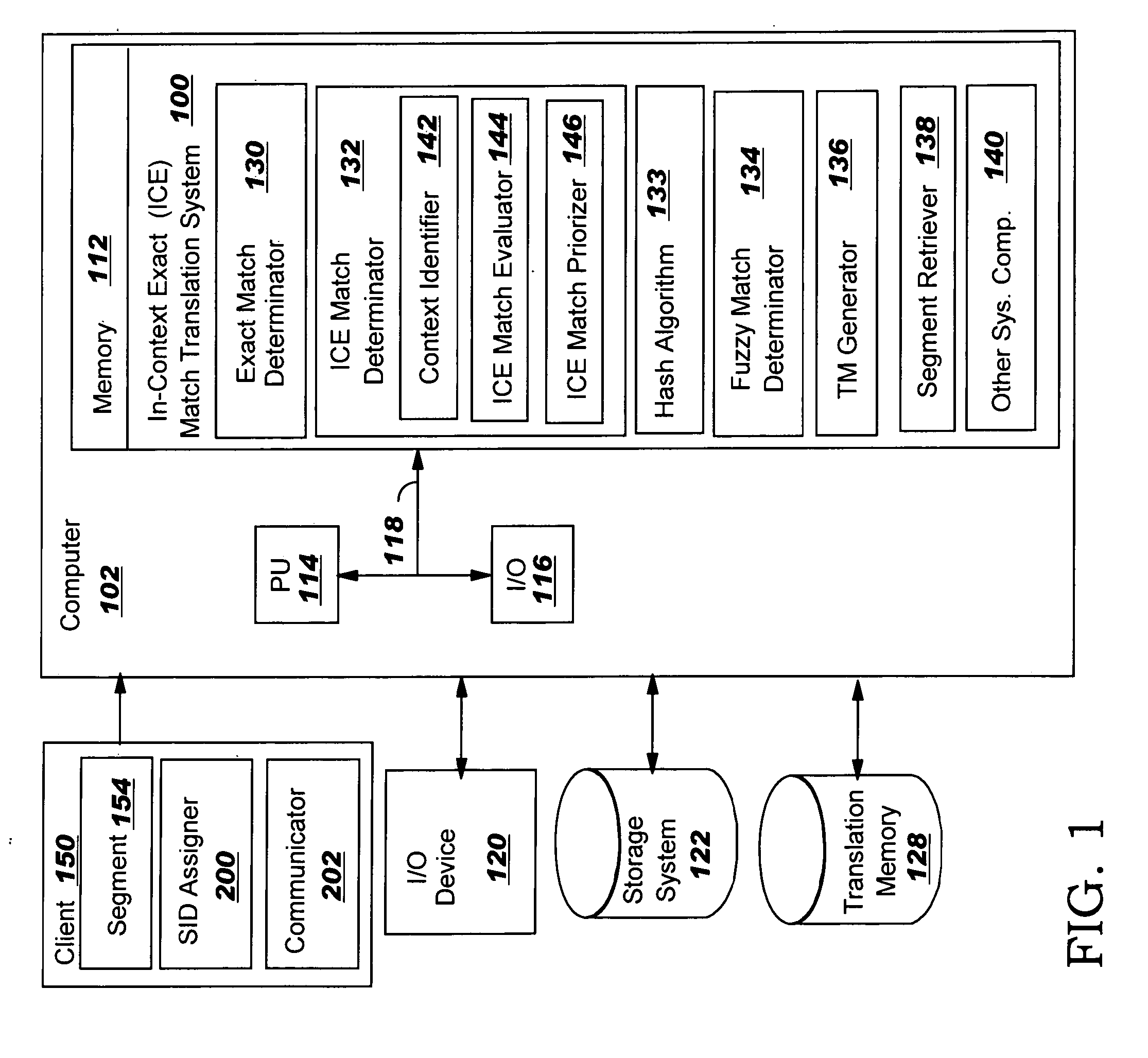
In-context exact (ICE) matching
ActiveUS7983896B2Reduce interventionNatural language translationDigital data information retrievalExact matchAlgorithm
Methods, systems and program product are disclosed for determining a matching level of a text lookup segment with a plurality of source texts in a translation memory in terms of context. In particular, the invention determines any exact matches for the lookup segment in the plurality of source texts, and determines, in the case that at least one exact match is determined, that a respective exact match is an in-context exact (ICE) match for the lookup segment in the case that a context of the lookup segment matches that of the respective exact match. The degree of context matching required can be predetermined, and results prioritized. The invention also includes methods, systems and program products for storing a translation pair of source text and target text in a translation memory including context, and the translation memory so formed. The invention ensures that content is translated the same as previously translated content and reduces translator intervention.
Owner:SDL INK
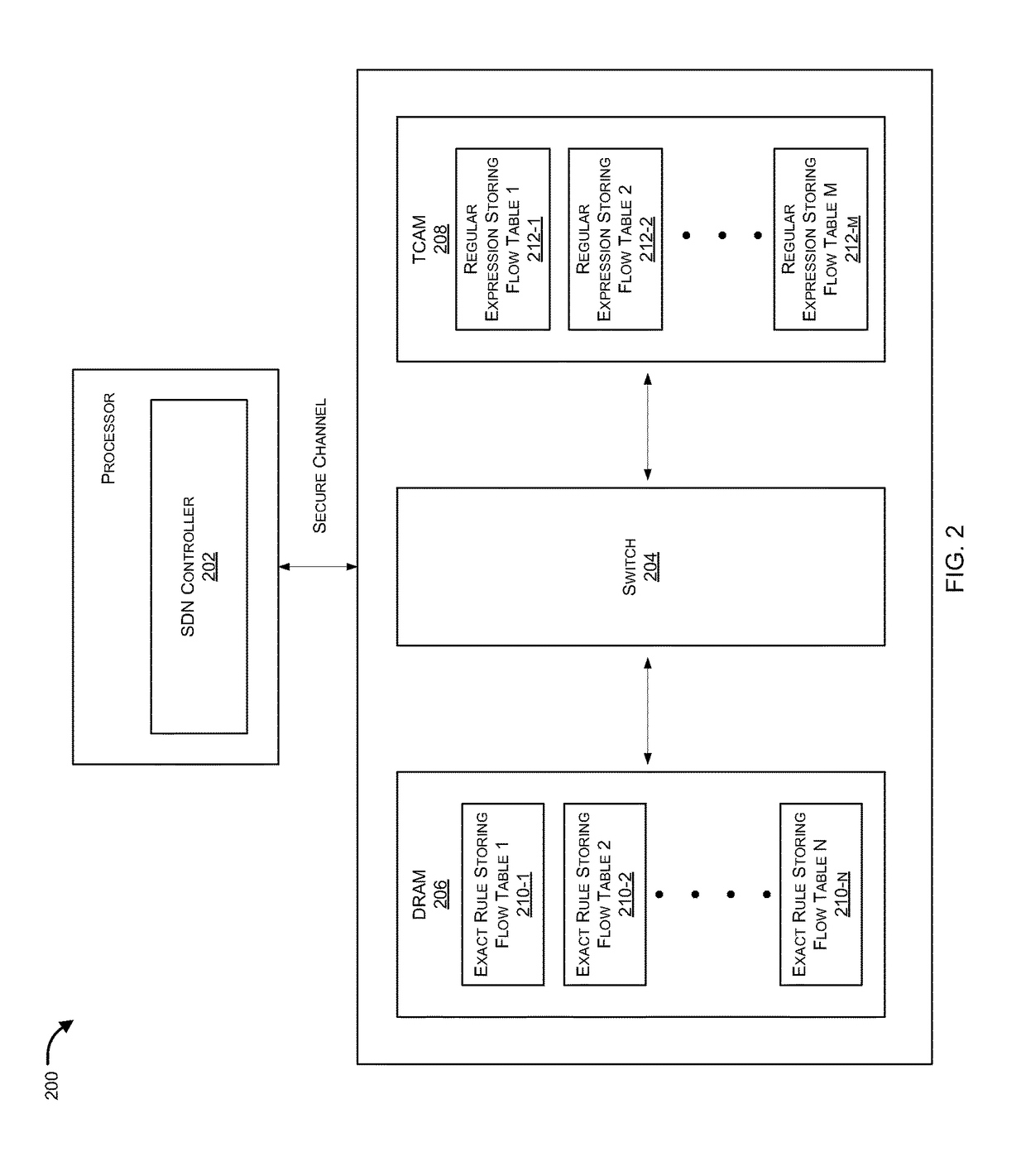
Flexible pipeline architecture for multi-table flow processing
Methods and systems for implementing scalable SDN devices having a flexible data path pipeline having multiple flow tables and a hybrid memory approach are provided. According to one embodiment, an SDN switch performs a method of storing a flow table within a memory device most suitable for the type of rules contained within the flow table. A flow table for use in connection with determining how to process a packet received by the SDN switch is received by the SDN switch. The flow table is stored within a DRAM device of the SDN switch when rules contained within the flow table include keys against which exact matching is performed with fields of the packet. The flow table is stored within a TCAM device of the SDN switch when rules contained within the flow table include keys against which regular expression-based matching is performed with the fields of the packet.
Owner:FORTINET
Fast accurate fuzzy matching
ActiveUS20080189279A1Accurately determineDigital data information retrievalDigital data processing detailsExact matchData mining
A computer-implemented technique for fuzzy matching. This works quickly yet accurately to determine if a given computer-readable record is represented, by exact match or pretty close match, in a large collection of computer-readable records. Further tools may be provided to assess the character of the match.
Owner:FAIR ISAAC & CO INC
Two-stage data validation and mapping for database access
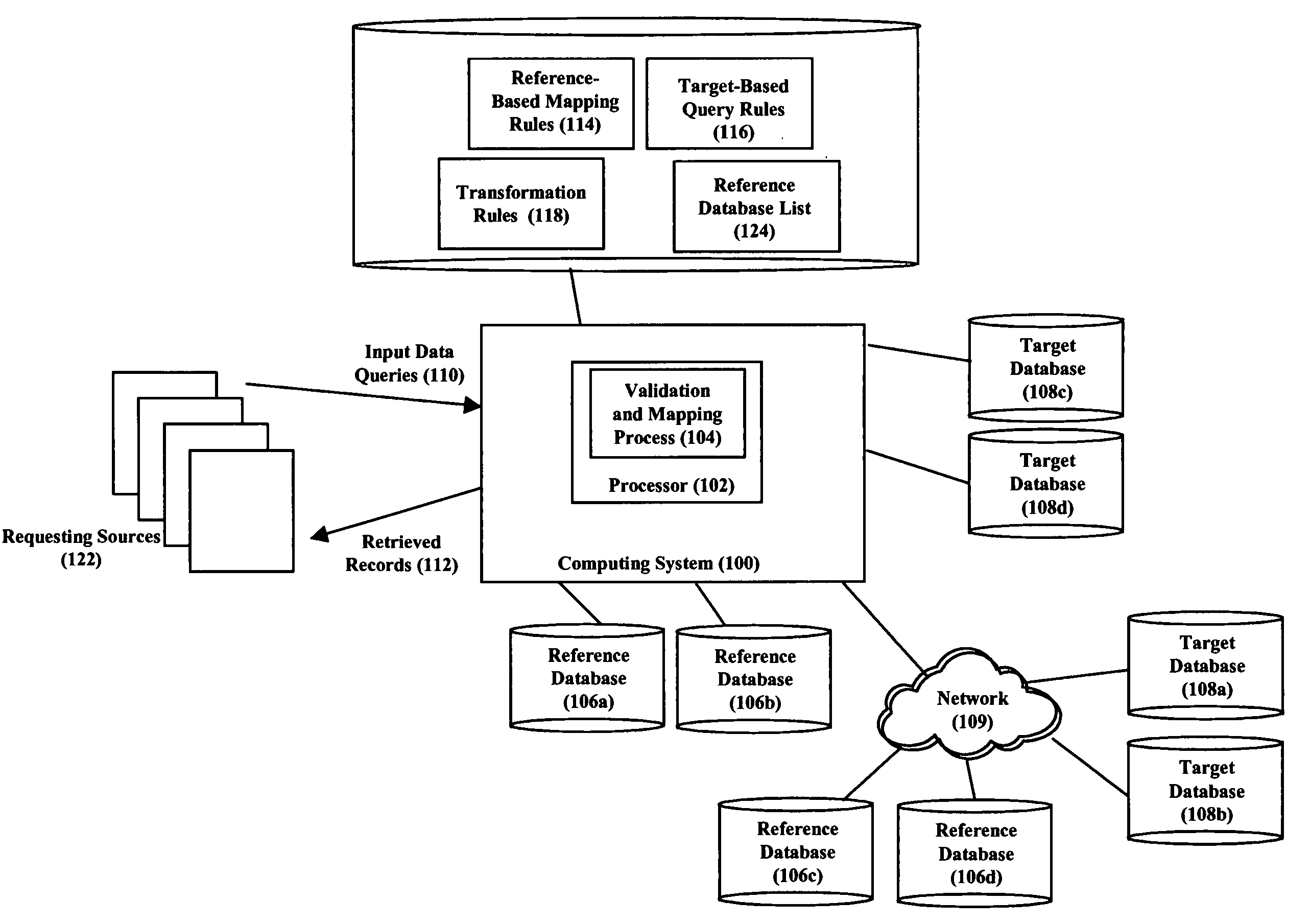
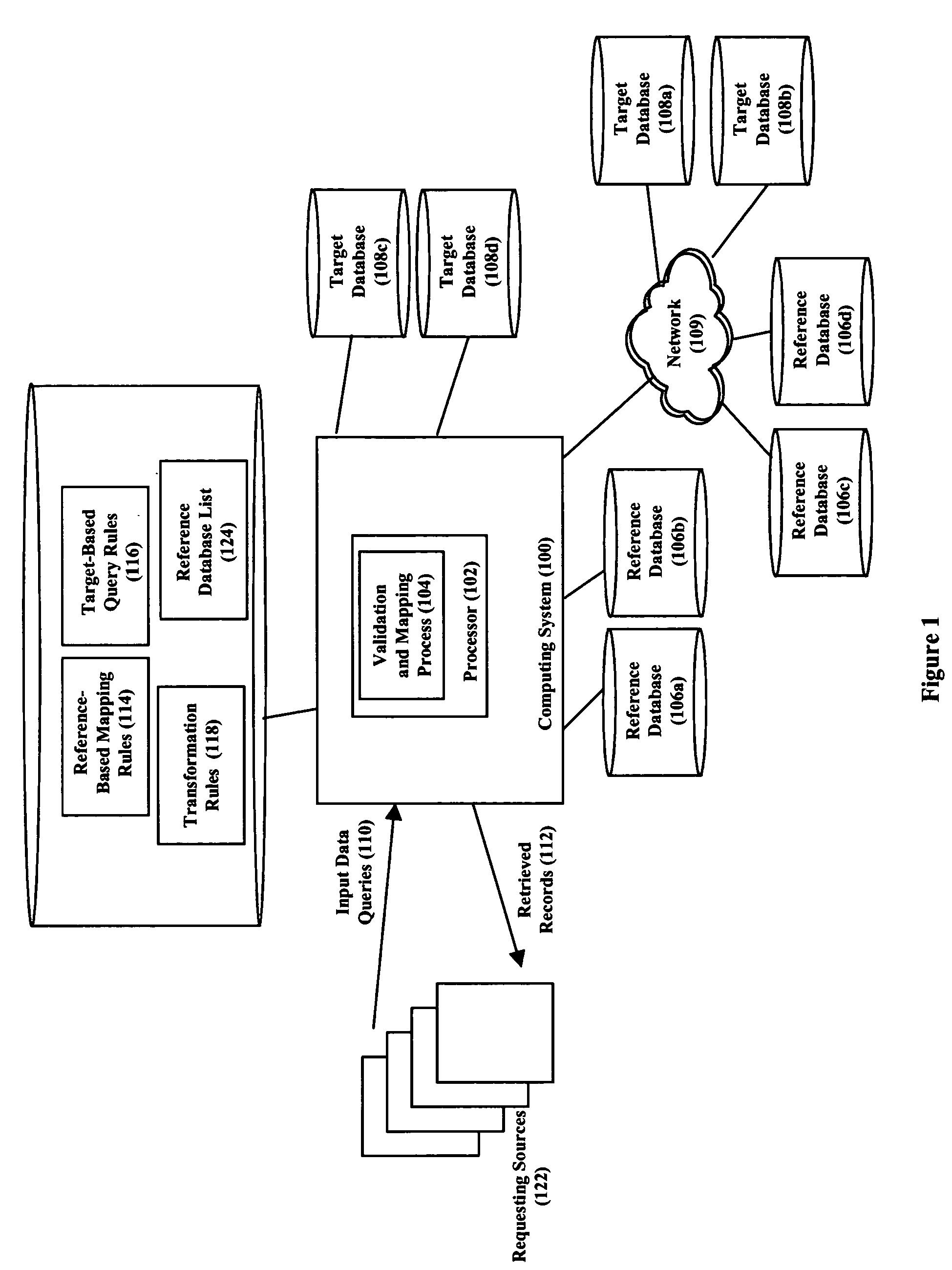
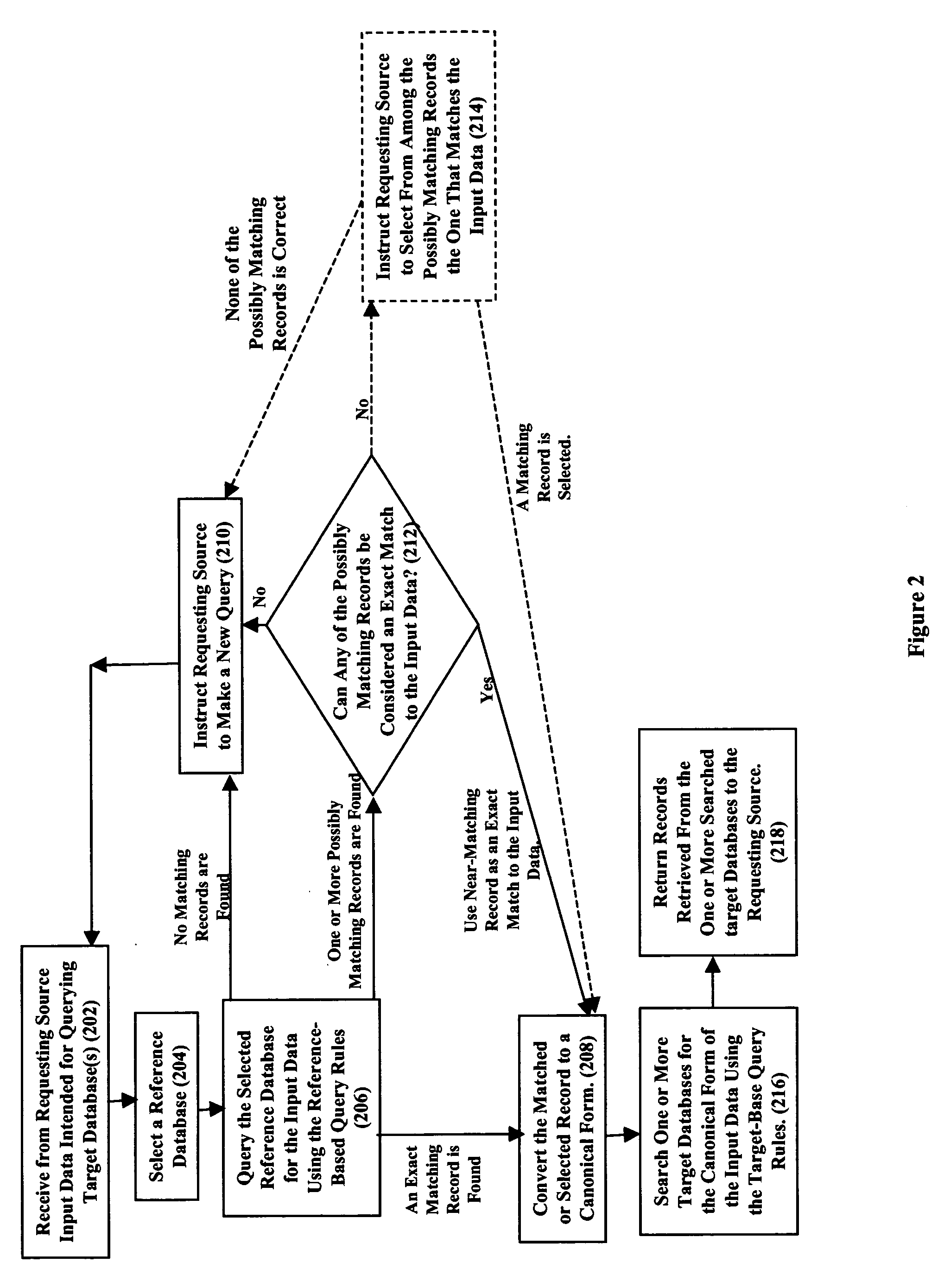
ActiveUS20050240569A1Reduce the numberReduce complexityDigital data information retrievalDigital data processing detailsData validationExact match
Input data queries directed at a plurality of target databases and originating from any of a plurality of sources are first converted to validated canonical forms, which are then used to query the target databases. Specifically, upon receiving an input data query, a relatively accurate reference database is selected based on the type of the input data. This reference is then queried for the input data with the intent of finding an exact matching record or a near-matching record that can be considered an exact match and thereby validating the input data. Otherwise, the requesting source is instructed to provide a new query. Once having a validated record, it is converted to a canonical form, which is then used to query the target databases intended to be searched. In a further embodiment, multiple reference databases are queried to determine a canonical form of the data or to determine multiple canonical forms of the data.
Owner:NYTELL SOFTWARE LLC
Device search system
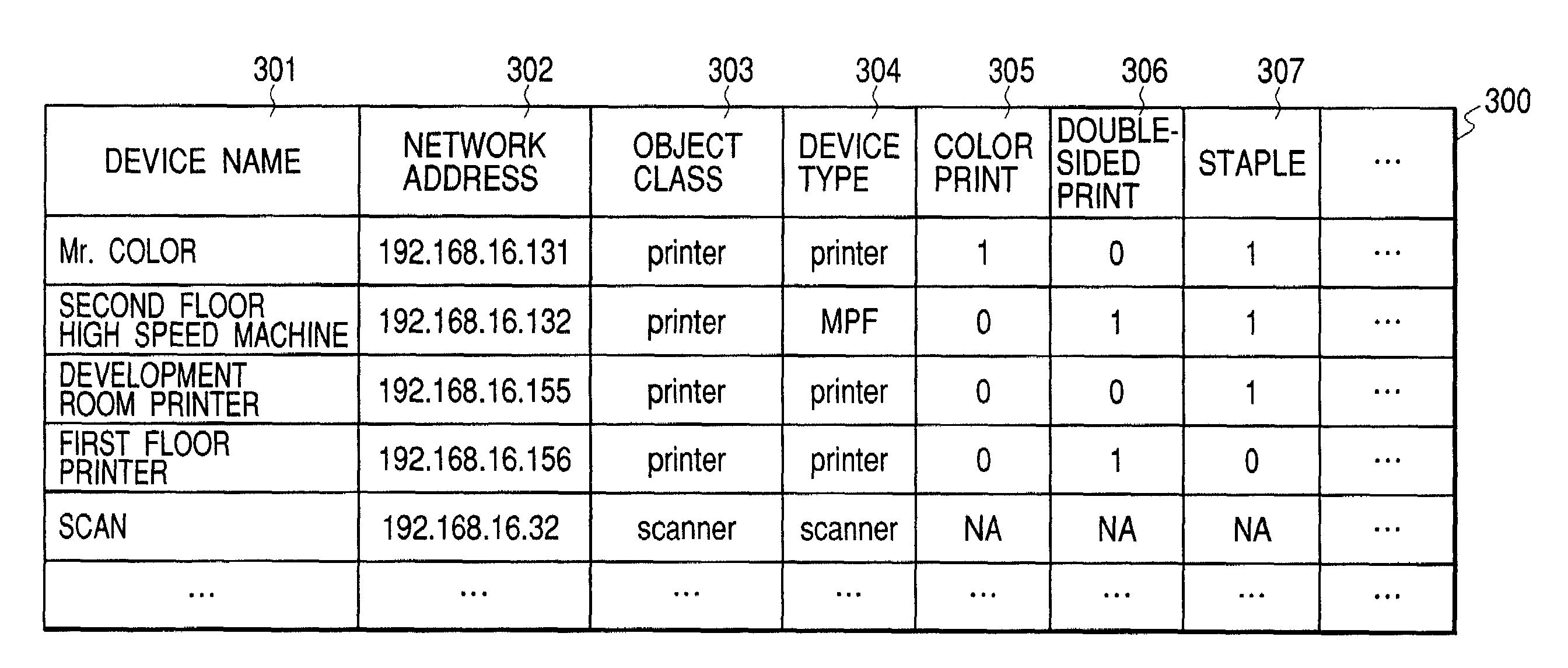
InactiveUS7085763B2Shorten the timeEasy to understandData processing applicationsDigital data information retrievalObject ClassExact matching
According to the present invention, a search condition can be moderated to easily understand a desired device without performing re-search, even if there is no device completely matching the search condition. An attribute of an object class is extracted out of the search condition designated by an operator to search a device meeting the attribute. A matching state of each attribute of the search condition first designated by the operator for a result obtained from the above search is visibly displayed.
Owner:CANON KK
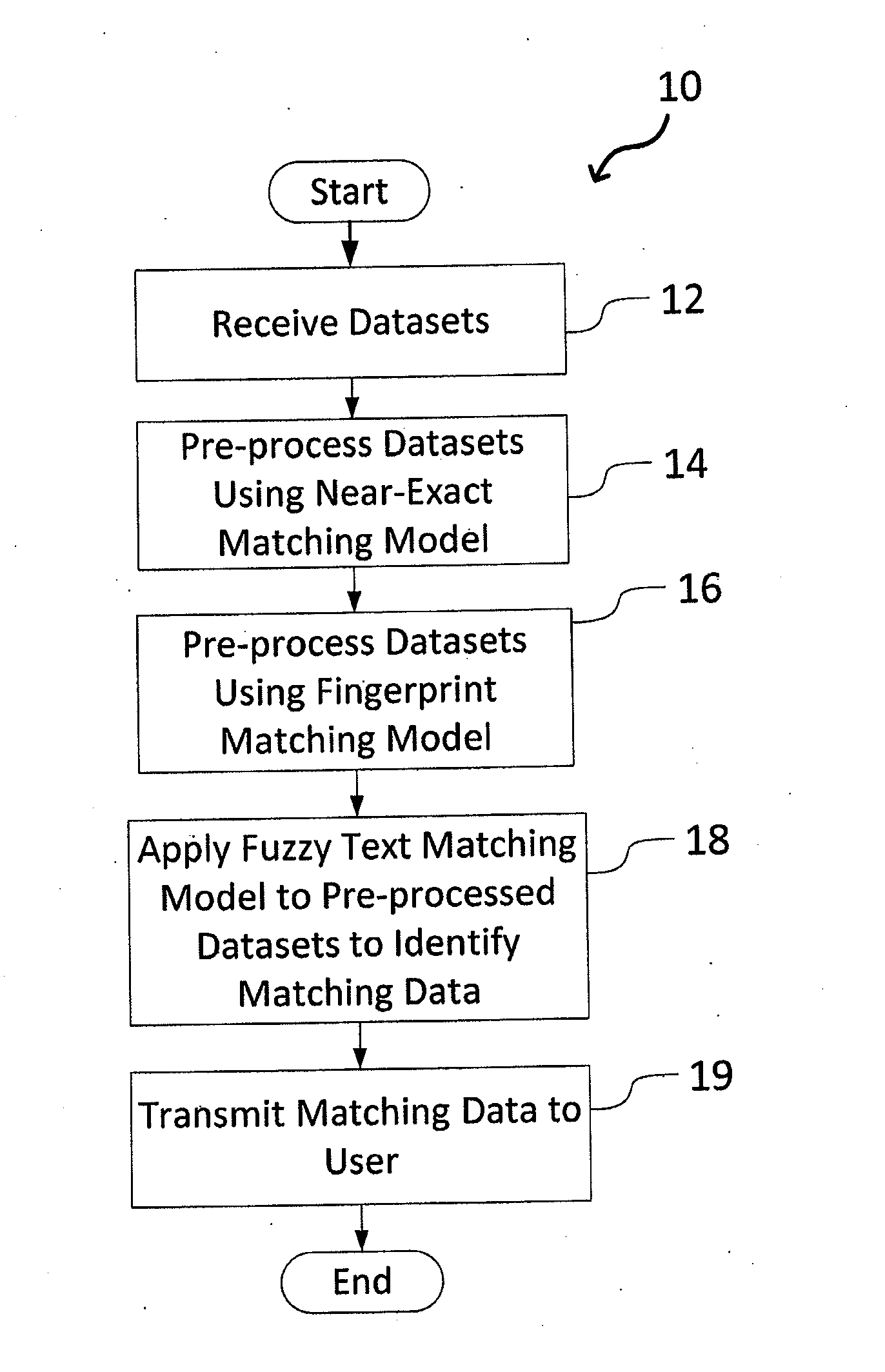
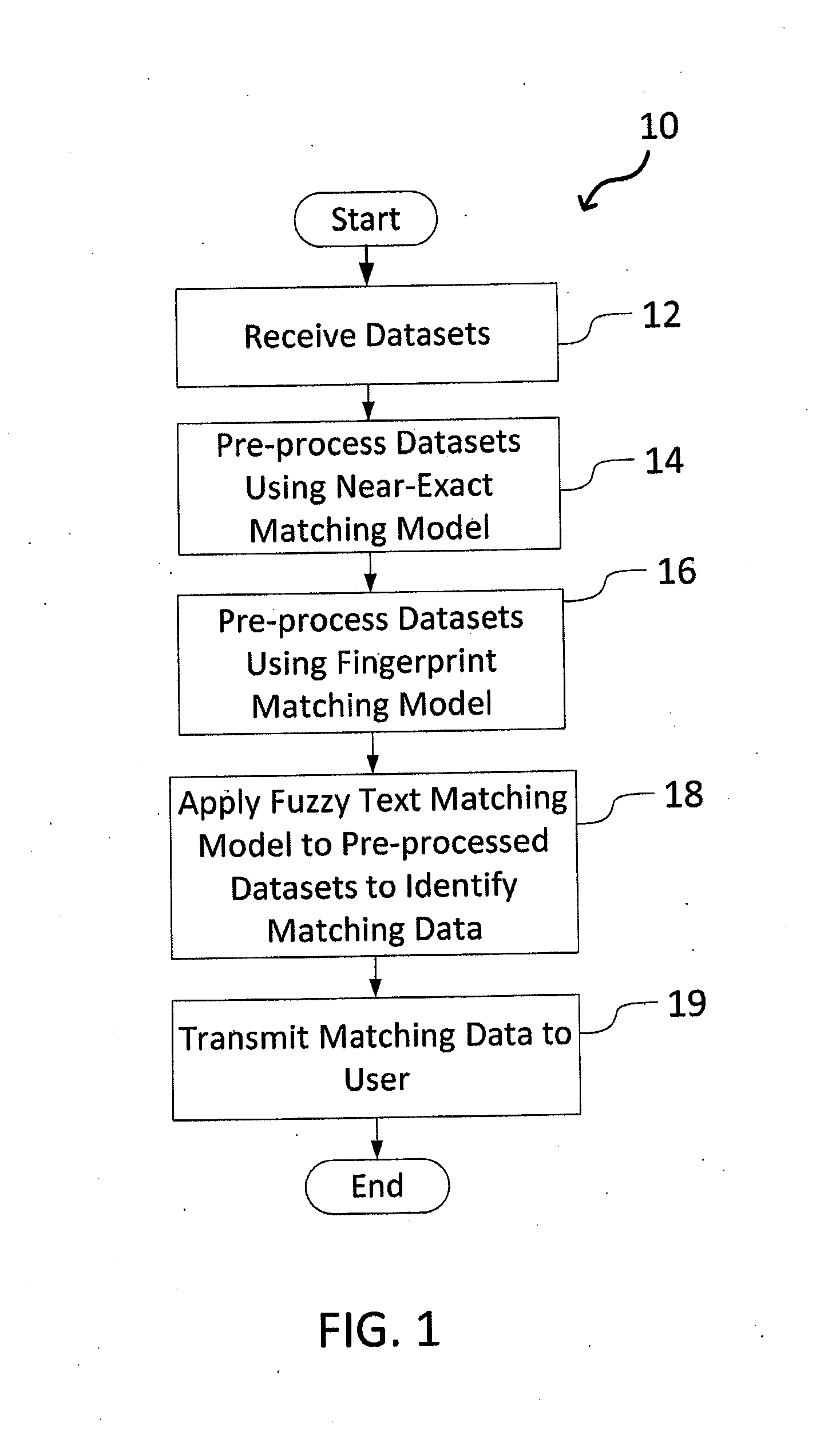
System and Method for Matching Data Using Probabilistic Modeling Techniques
InactiveUS20140052688A1Penalizing the similarity scoreFuzzy logic based systemsSpecific program execution arrangementsProbit modelExact match
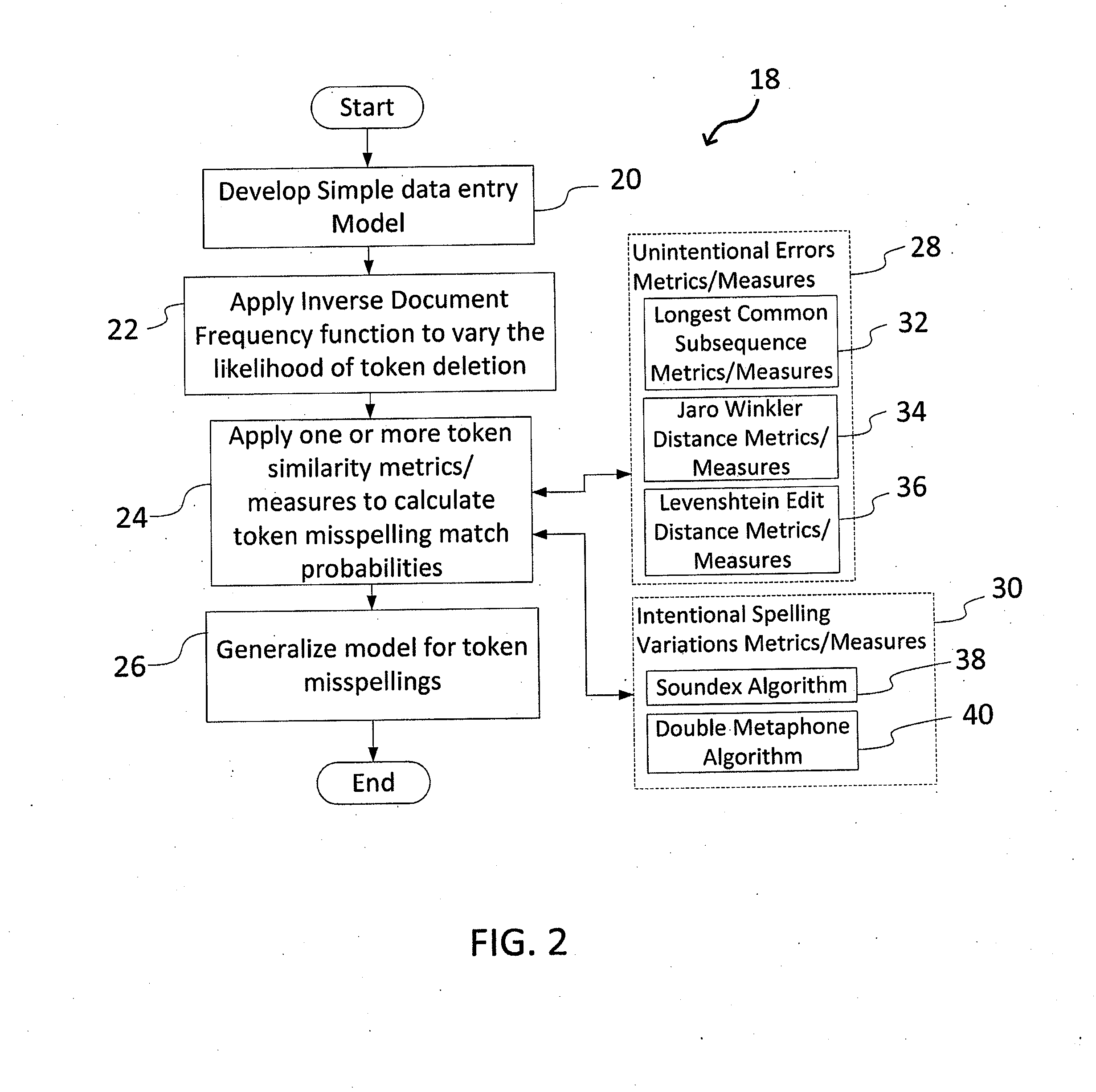
A system and method for matching data using probabilistic modeling techniques is provided. The system includes a computer system and a data matching model / engine. The present invention precisely and automatically matches and identifies entities from approximately matching short string text (e.g., company names, product names, addresses, etc.) by pre-processing datasets using a near-exact matching model and a fingerprint matching model, and then applying a fuzzy text matching model. More specifically, the fuzzy text matching model applies an Inverse Document Frequency function to a simple data entry model and combines this with one or more unintentional error metrics / measures and / or intentional spelling variation metrics / measures through a probabilistic model. The system can be autonomous and robust, and allow for variations and errors in text, while appropriately penalizing the similarity score, thus allowing dataset linking through text columns.
Owner:OPERA SOLUTIONS U S A LLC
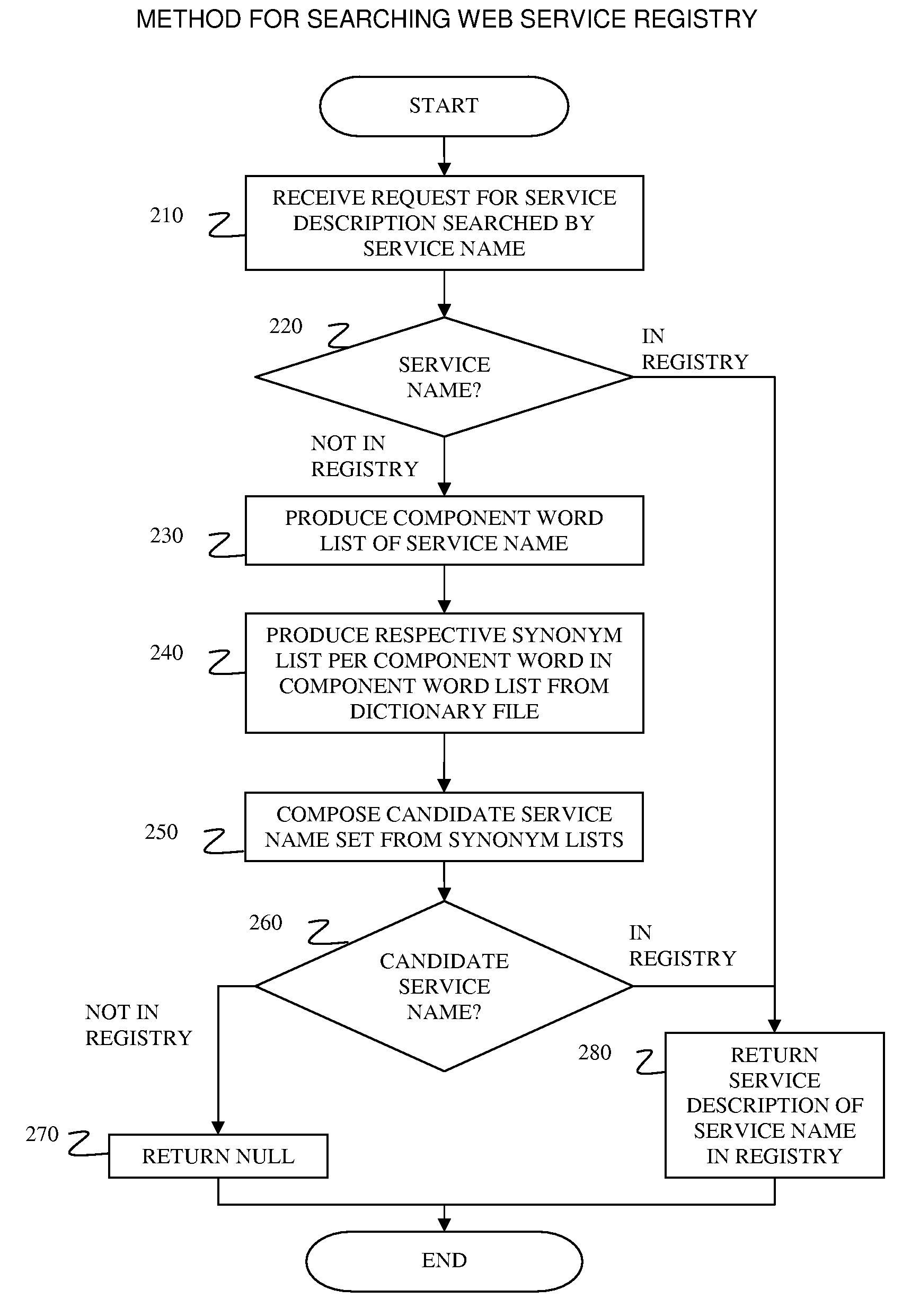
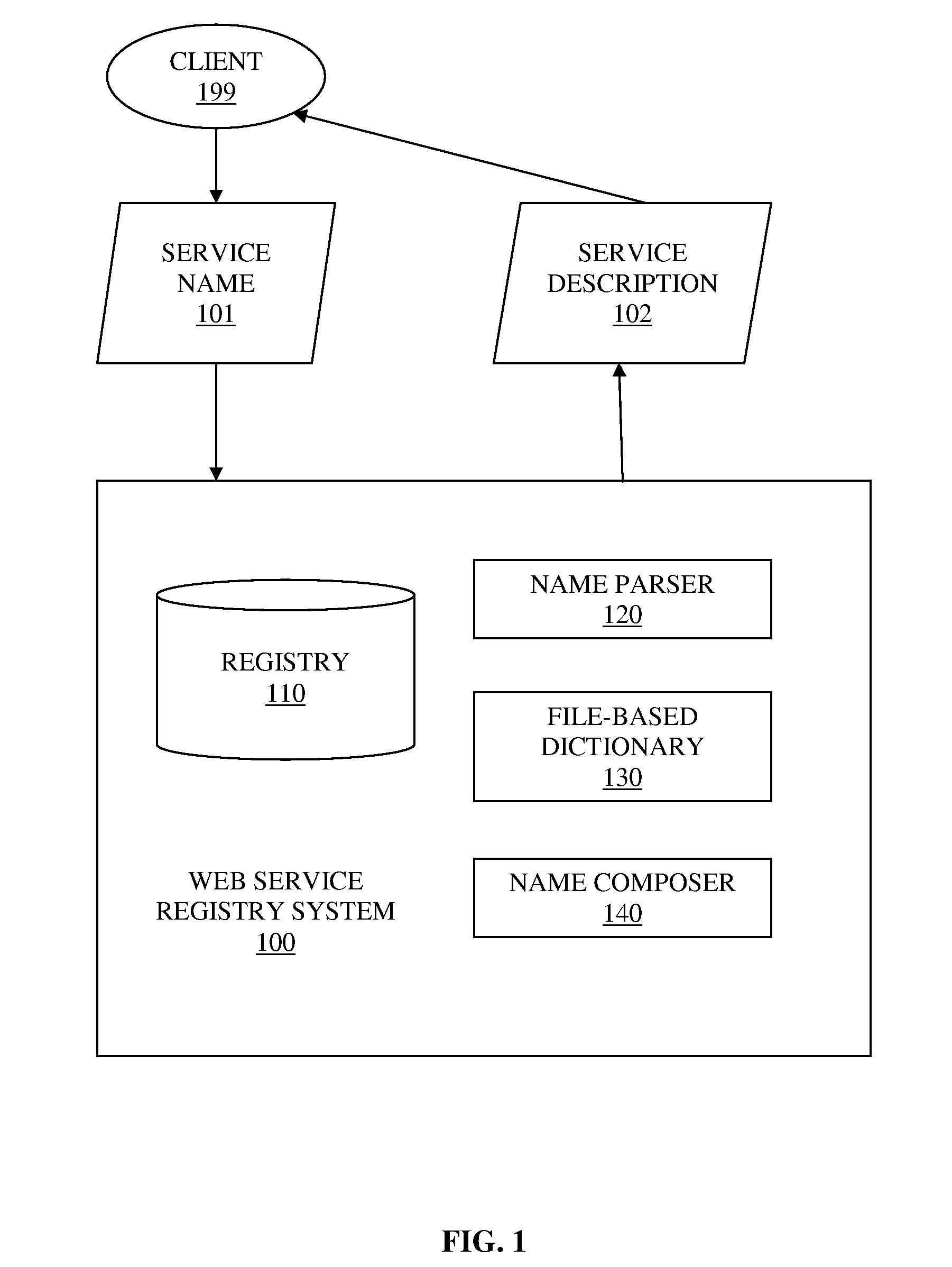
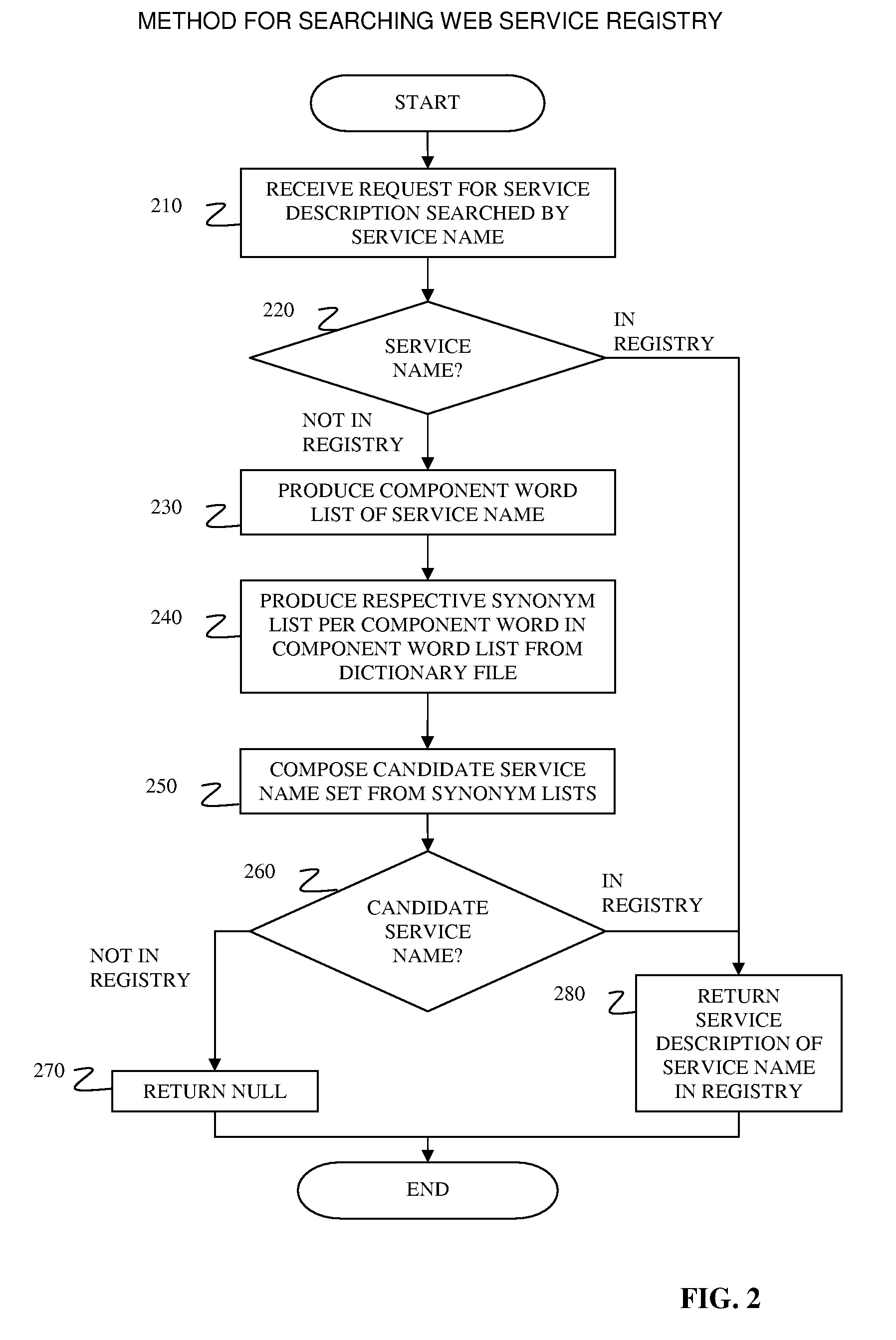
System and method for improving non-exact matching search in service registry system with custom dictionary
InactiveUS7966320B2Digital data information retrievalDigital data processing detailsWindows RegistryExact matching
A system and associated method for searching a service registry system with a service name. The service registry system receives a request to search a service description with the service name. The service registry system first searches a registry for a service identifier that matches the service name in the request, and if there is no matching service identifier, the service registry system composes at least one candidate service name from synonyms of respective component words that are comprised by the service name. The service registry system performs another search in the registry with said composed candidate service name for all composed candidate service names and service descriptions associated with any match are returned.
Owner:INT BUSINESS MASCH CORP
Method and apparatus for matching non-normalized data values
ActiveUS20080077573A1Good choiceAmount of timeData processing applicationsDigital data information retrievalExact matchUser input
Enables locating and merging potential data record matches. Enables locating duplicates through the definition of matching strategies. Each strategy may include transformations, matching rules and scoring thresholds to implement fuzzy matches that match closely related data records that are not exact matches. Performing a search allows for narrowing down the records to a desired set on which to apply a given matching strategy. Merging is performed on the potential duplicates thus located to consolidate data and remove duplicates. By narrowing down the records to a closely related set via a search, merging is simplified to work on a small number of closely related records, thus simplifying the process. The total matching score obtained via execution of match strategies may be utilized to determine which potential record(s) to merge for example. May utilize past user input to provide intelligent inputs for rules, tokens, weights, fields, parameters or any other past user input.
Owner:SAP AG
Method and device for speeding up matching of filter rules of firewalls
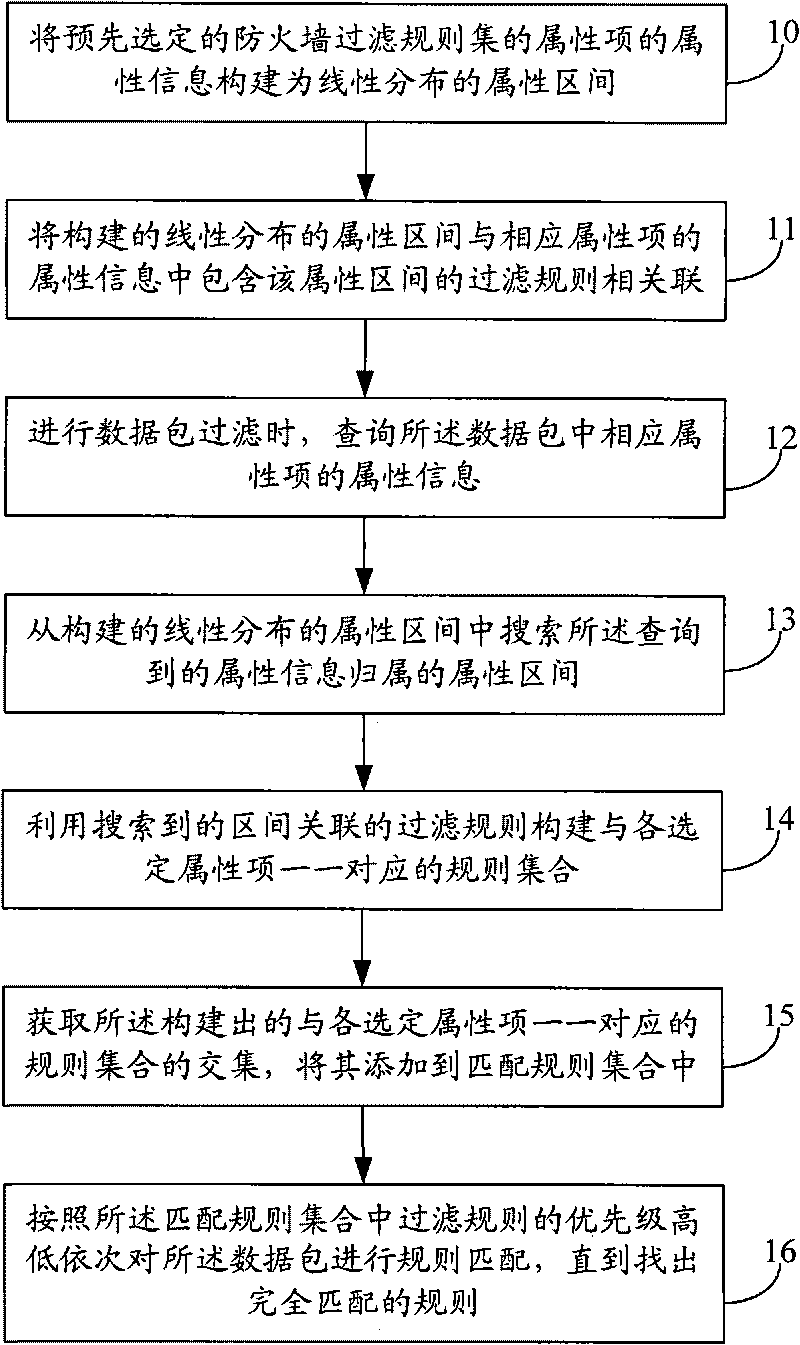
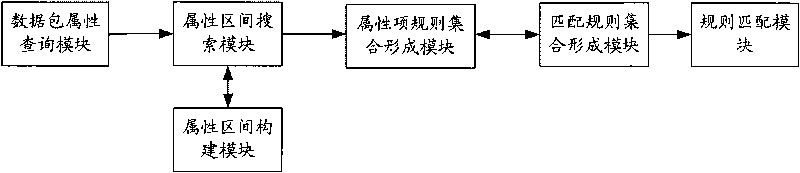
ActiveCN101753542ALow efficiencyNarrow down the set of matching rulesTransmissionSpecial data processing applicationsFiltrationNetwork packet
The invention discloses a method and a device for speeding up the matching of filter rules of firewalls, wherein the method comprises the steps: constructing attribute information of attribute items of a pre-selected firewall filter rule set to a linearly-distributed attribute interval, and associating the constructed attribute interval with the filter rules, containing the attribute interval, in attribute information of relative attribute items; querying the attribute information of the selected attribute items in data packets during the filtration of the data packets, searching the constructed attribute interval for the interval to which the queried attribute information belongs, and constructing rule sets corresponding one by one to the selected attribute items by using the searched interval-associated filter rules; acquiring the intersection of the constructed rule sets which are corresponding one by one to the selected attribute items and adding the intersection to a set of matched rules; and according to the priorities of the filter rules in the set of matched rules, sequentially performing rule matching on the data packets until the completely-matched rules are found out. The method and the device can enhance the efficiency of matching the filter rules of firewalls.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH
Gray-code-based distributed data layout method and query method
InactiveCN102890678AImplement aggregation queryImprove the efficiency of sequential accessSpecial data processing applicationsTheoretical computer scienceEngineering
The invention belongs to the technical field of a database, and discloses a gray-code-based distributed data layout method. The method comprises the steps of: dividing a range of each attribute into a plurality of equal portions; encoding according to a gray code order; marking a certain attribute value of a tuple comprising a plurality of attributes through the gray codes of the equal portions of the attribute value, namely an index code of the attribute value; forming an index key value of the tuple by mixing the index code of each attribute value in the tuple, wherein the tuple achieves the distributed data layout according to the order of the gray codes, the distributed data layout is deployed on a distributed system, the bitmap index of content perception is achieved at a host computer terminal of the system and the content perception is stored in a file name, and physical storage of data and statistical index of the data are achieved on a slave terminal of the system. The invention also discloses a query method employing the database formed by means of the method. The data layout obtained by the method can meet the requirements of data processing such as exact matching search, range search, multi-dimensional search, multi-attribute search and aggregated analysis, and the method is high in disc access efficiency.
Owner:EAST CHINA NORMAL UNIVERSITY
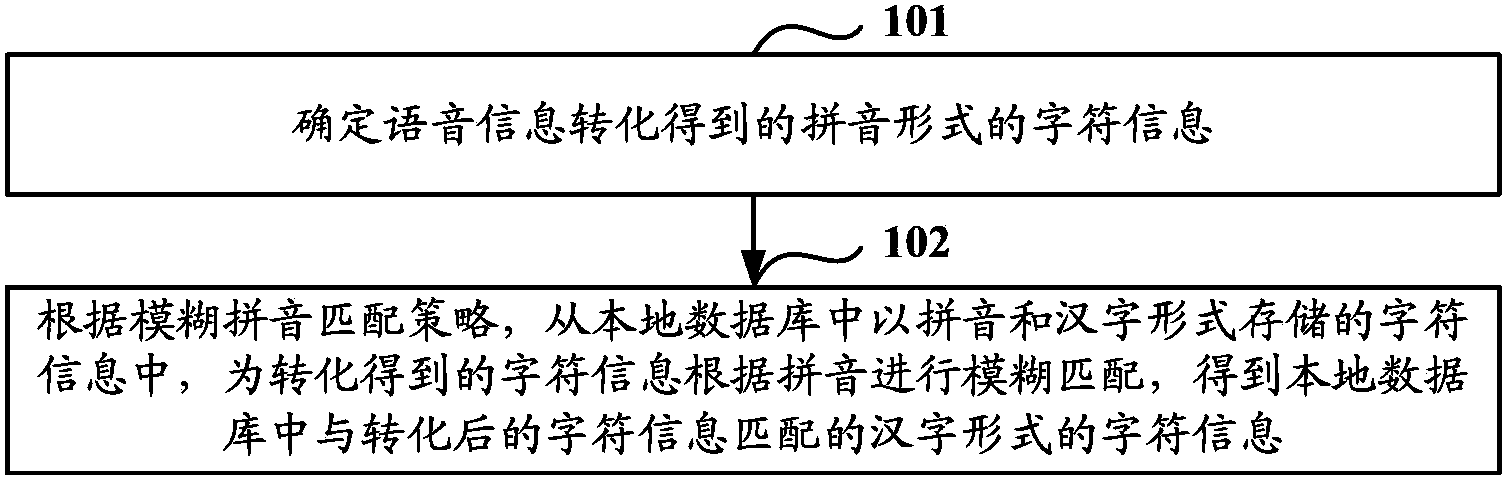
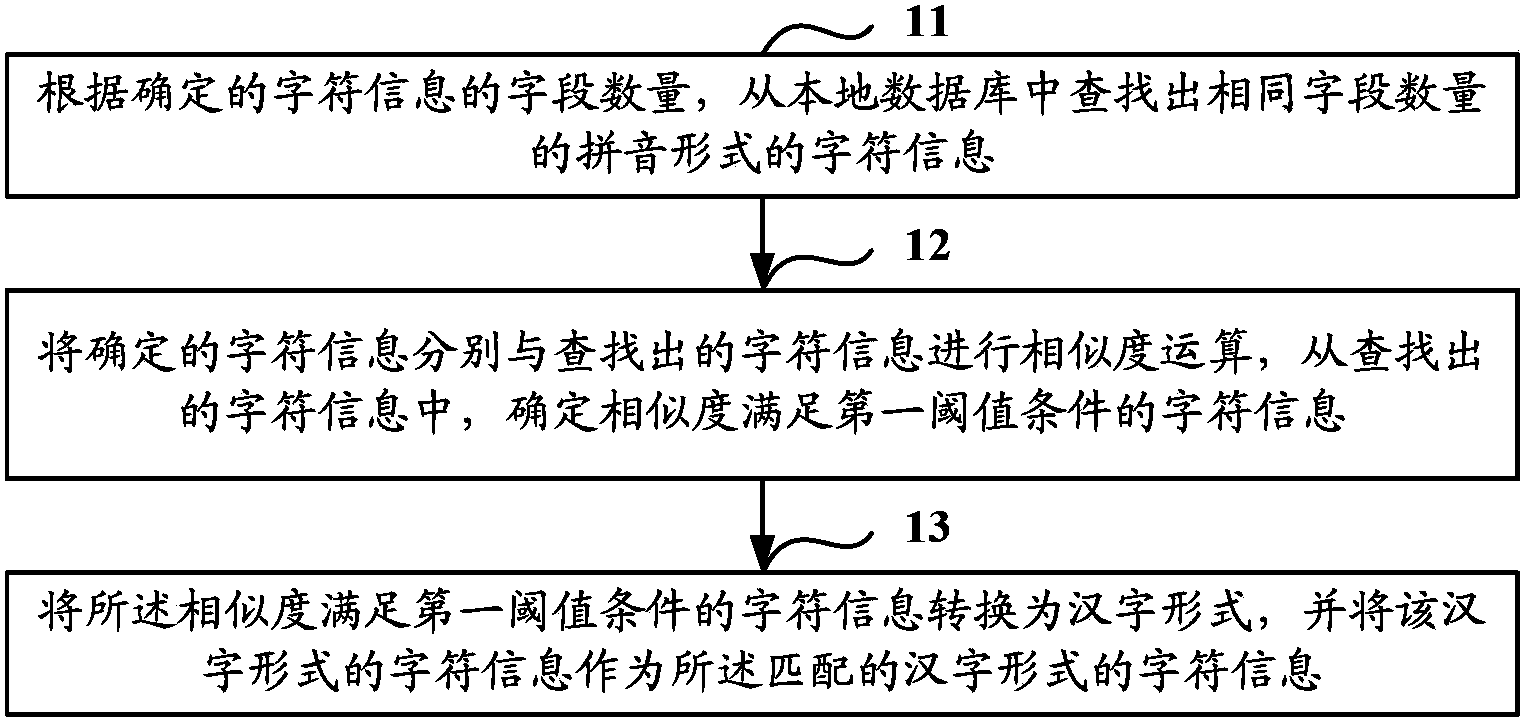
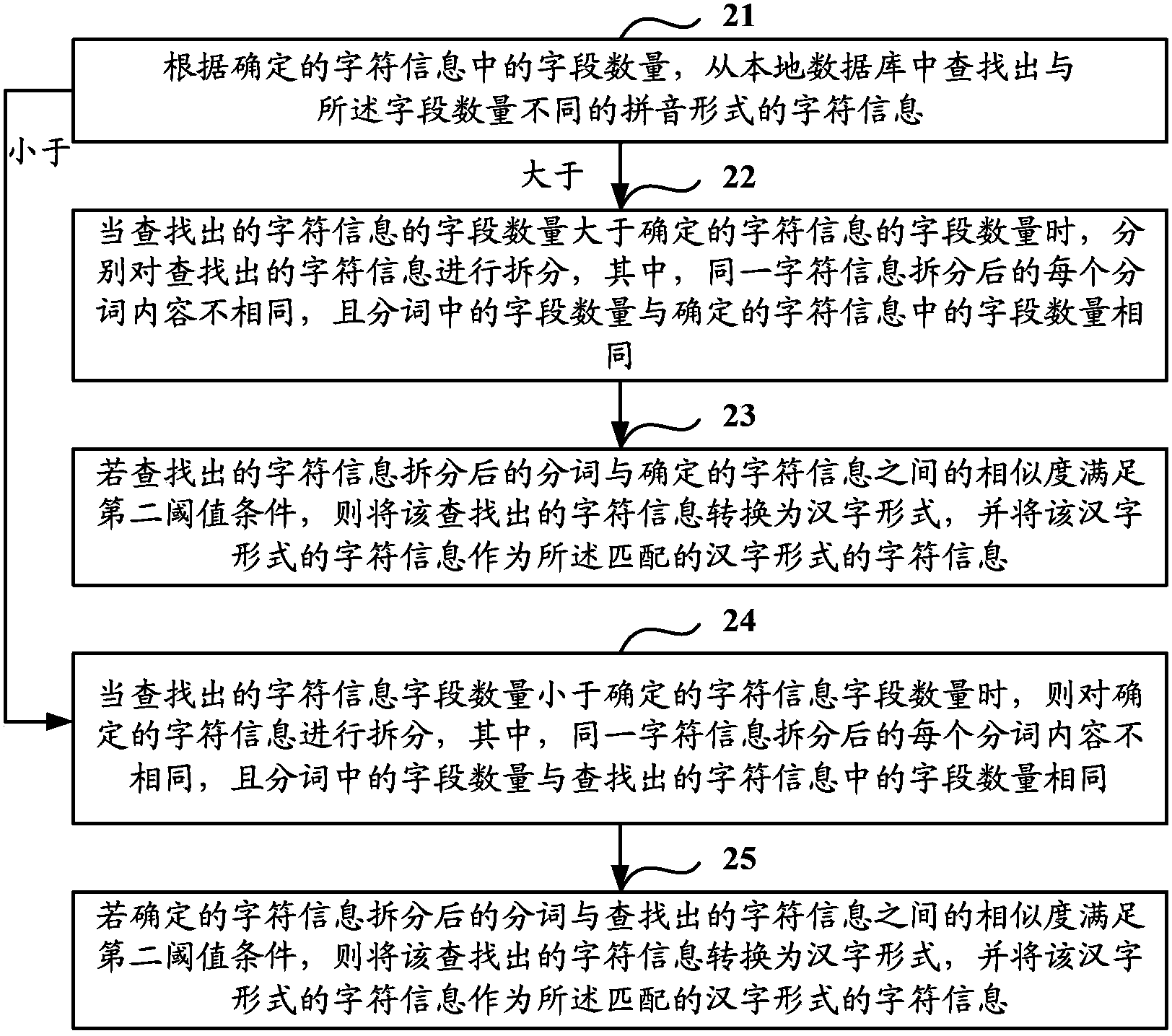
Method and device for matching based on voice recognition
ActiveCN103456297AImprove efficiencyImprove speech recognition rateSpeech recognitionChinese charactersSpeech sound
The invention discloses a method and a device for matching based on voice recognition. The method mainly includes determining character information, in an alphabetic form, converted from voice information; on the basis of a fuzzy matching strategy and according to alphabet, performing fuzzy matching to the converted character information of the character information stored in the alphabetic and Chinese character forms from a local database. As the single complete matching strategy applied in the prior art is expanded to the strategy of performing the fuzzy matching to the converted character information in the alphabetic form according to alphabet, voice recognition rate of the character information acquired by conversion is increased effectively, and further, the efficiency of the voice recognition technology is improved.
Owner:CHINA MOBILE COMM GRP CO LTD
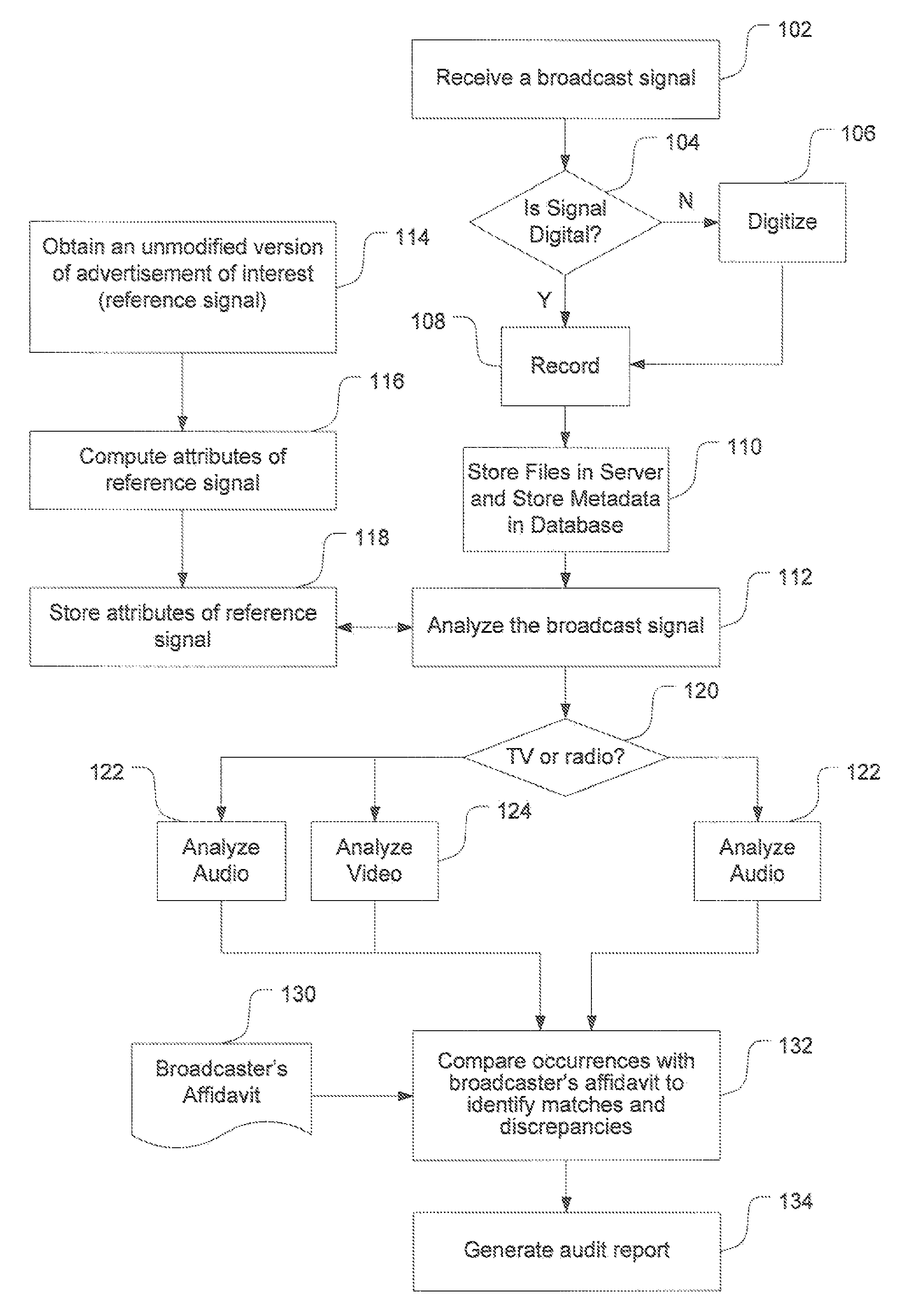
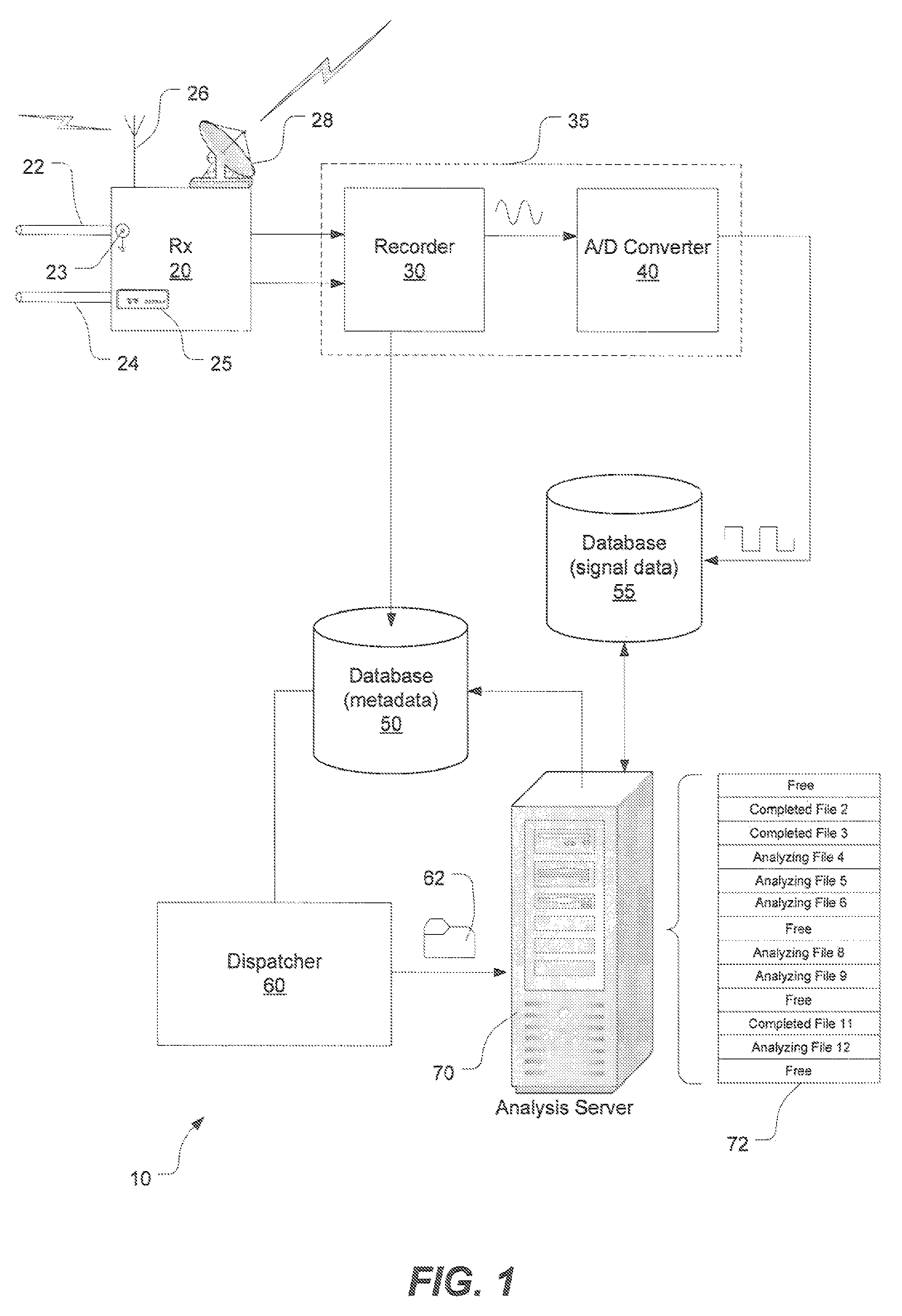
Method and System for automated auditing of advertising
InactiveUS7627878B2Analogue secracy/subscription systemsBroadcast components for monitoring/identification/recognitionStatistical correlationMinutiae
The timing and placement of advertising on TV, radio or other broadcast media can be automatically verified or audited by monitoring and recording channels of TV, radio or broadcast media by storing and tagging discrete portions of segments of the broadcast signals in a database. A controller, or “dispatcher” server, dispatches the files to an analysis server for performing various mathematical comparisons and statistical correlations on the audio and video signals for positively identifying one or more advertisements of interest. A report is generated, providing particulars about the airing times of the advertisement of interest and whether its content exactly matches the content of a reference advertisement used as the basis for the mathematical comparisons and correlations.
Owner:ELODA
System and method for detecting malware in executable scripts according to its functionality
A malware detection system and method for determining whether an executable script is malware is presented. The malware detection system determines whether the executable script is malware by comparing the functional contents of the executable script to the functional contents of known malware. In practice, the executable script is obtained. The executable script is normalized, thereby generating a script signature corresponding to the functionality of the executable script. The script signature is compared to known malware script signatures in a malware signature store to determine whether the executable script is malware. If a complete match is made, the executable script is considered to be malware. If a partial match is made, the executable script is considered to likely be malware. The malware detection system may perform two normalizations, each normalization generating a script signature which is compared to similarly normalized known malware script signatures in the malware signature store.
Owner:MICROSOFT TECH LICENSING LLC
Retrieval method and device for policy text, storage medium and electronic device
The invention provides a policy text retrieval method and device, a storage medium and an electronic device. According to the method, policy texts are classified; the theme type of the policy text isused as a retrieval label; when the user performs retrieval, corresponding tags are matched in the policy text based on a complete matching algorithm and a non-complete matching algorithm through thetags selected by the user, and an evaluation value of each label is counted; the retrieval results are arranged and displayed on the basis of the sum of the evaluation values of each policy text for all the tags, so that the problem that the relevancy between the retrieval mode for the policy text and the search keywords is low in the prior art is solved, and the technical effect of improving therelevancy between the retrieval results and the search words is achieved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Full match (FM) search algorithm implementation for a network processor
InactiveUS20050177552A1Reduce storage spaceData processing applicationsDigital data processing detailsHash functionTheoretical computer science
Novel data structures, methods and apparatus for finding a full match between a search pattern and a pattern stored in a leaf of the search tree. A key is input, a hash function is performed on the key, a direct table (DT) is accessed, and a tree is walked through pattern search control blocks (PSCBs) until reaching a leaf. The search mechanism uses a set of data structures that can be located in a few registers and regular memory, and then used to build a Patricia tree structure that can be manipulated by a relatively simple hardware macro. Both keys and corresponding information needed for retrieval are stored in the Patricia tree structure. The hash function provides an n->n mapping of the bits of the key to the bits of the hash key.
Owner:INT BUSINESS MASCH CORP
In-context exact (ICE) matching
InactiveUS20100262621A1Natural language translationDigital data information retrievalExact matchAlgorithm
Methods, systems and program product are disclosed for determining a matching level of a text lookup segment with a plurality of source texts in a translation memory in terms of context. In particular, embodiments of the present invention determines any exact matches for the lookup segment in the plurality of source texts, and determines, in the case that at least one exact match is determined, that a respective exact match is an in-context exact (ICE) match for the lookup segment in the case that a context of the lookup segment matches that of the respective exact match. The degree of context matching required can be predetermined, and results prioritized. The invention also includes methods, systems and program products for storing a translation pair of source text and target text in a translation memory including context, and the translation memory so formed. The invention ensures that content is translated the same as previously translated content and reduces translator intervention.
Owner:ROSS RUSS +3
User interface for search method and system
A user interface for searching records in a database is provided. Each record contains information regarding one or more categories. The user interface receives search criteria of one or more categories and provides search results comprising exact and / or non-exact matching records. A non-exact matching record has a relevance value representing the relevance of the record to the search query, the non-exact matching records being displayed in an ordering based on the relevance values. The user interface provides slider tools for receiving changes in a weight value or search criterion of an associated category. A new ordering of the non-exact matching records is displayed in real-time based on the new received weight values or search criterion. The user interface may also provide a mapping tool, a search-result selection function, and / or one or more drill down tools. The user interface may provide any tool or function alone or in any combination.
Owner:TRANSPARENSEE SYST
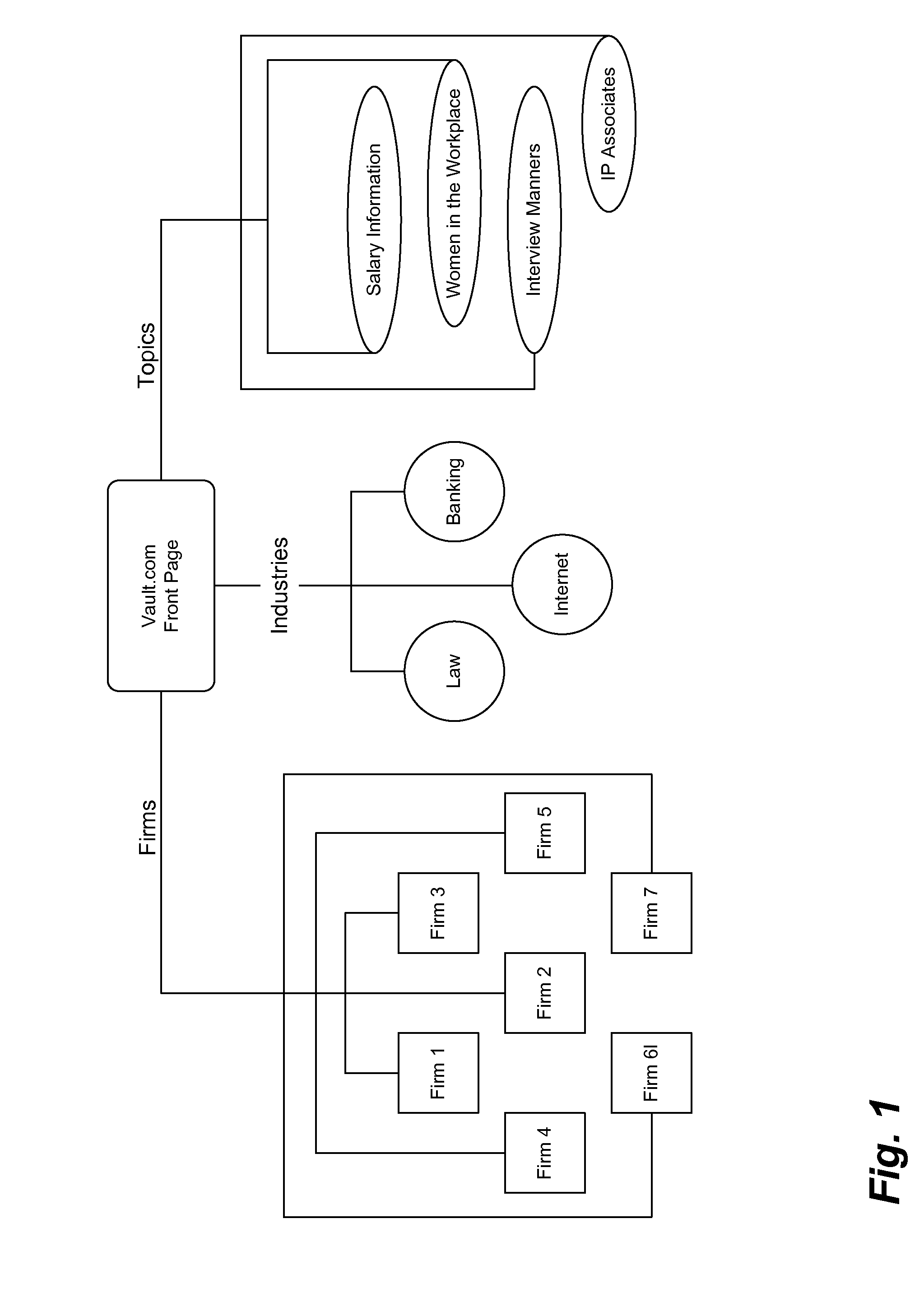
Category-based Advertisement
A hierarchical category system for organizing and displaying electronic advertisements is disclosed. Each electronic advertisement is assigned one or more categories from a hierarchical categorization system. Similarly, each available advertisement placement location is also provided with a category from the hierarchical categorization, system. Then, when displaying advertisements, the system attempts to locate advertisements that have matching categorizations. When no matching advertisement with an exact matching categorization can be found, the system will attempt to locate an advertisement from a more specific (child) category that is a sub category of the current category. However, the advertisement from the more specific (child) category must specify the broader category within its own allowable fall-back path.
Owner:R2 SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com