Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
138 results about "Logical process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
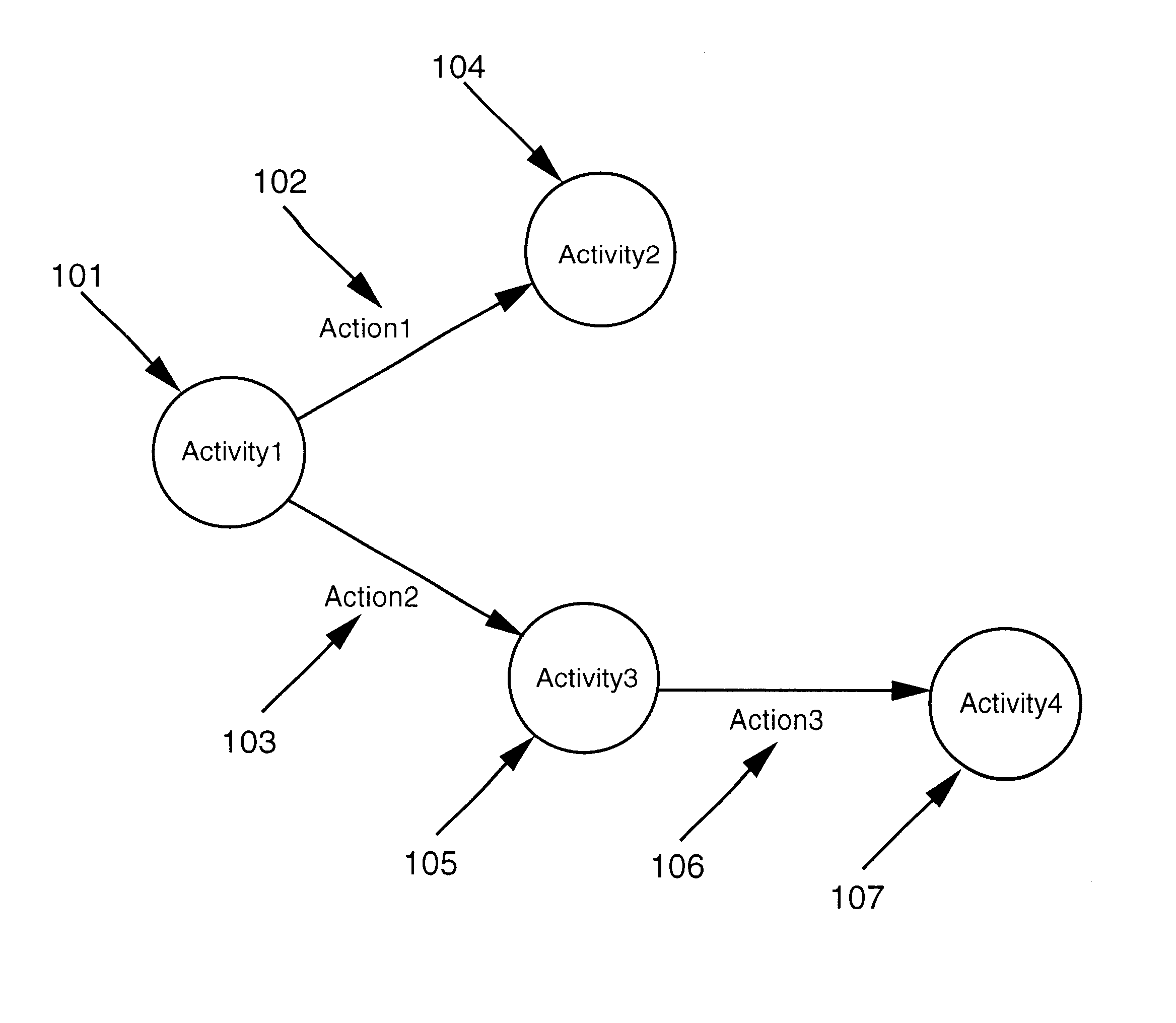
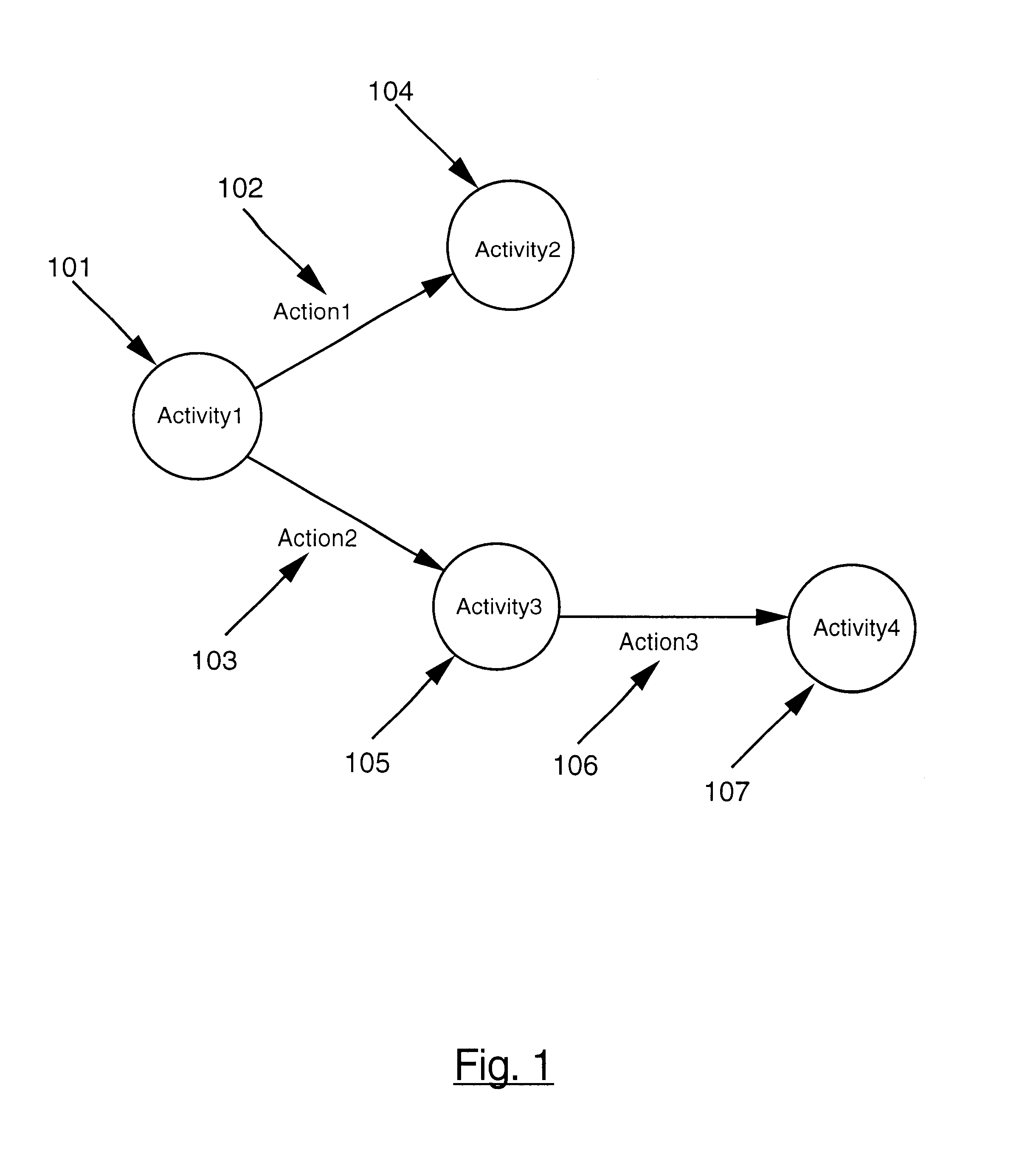
Logical Process Modeling. Logical Process Modeling is the representation of a business process, detailing all the activities in the process from gathering the initial data to reaching the desired outcome.
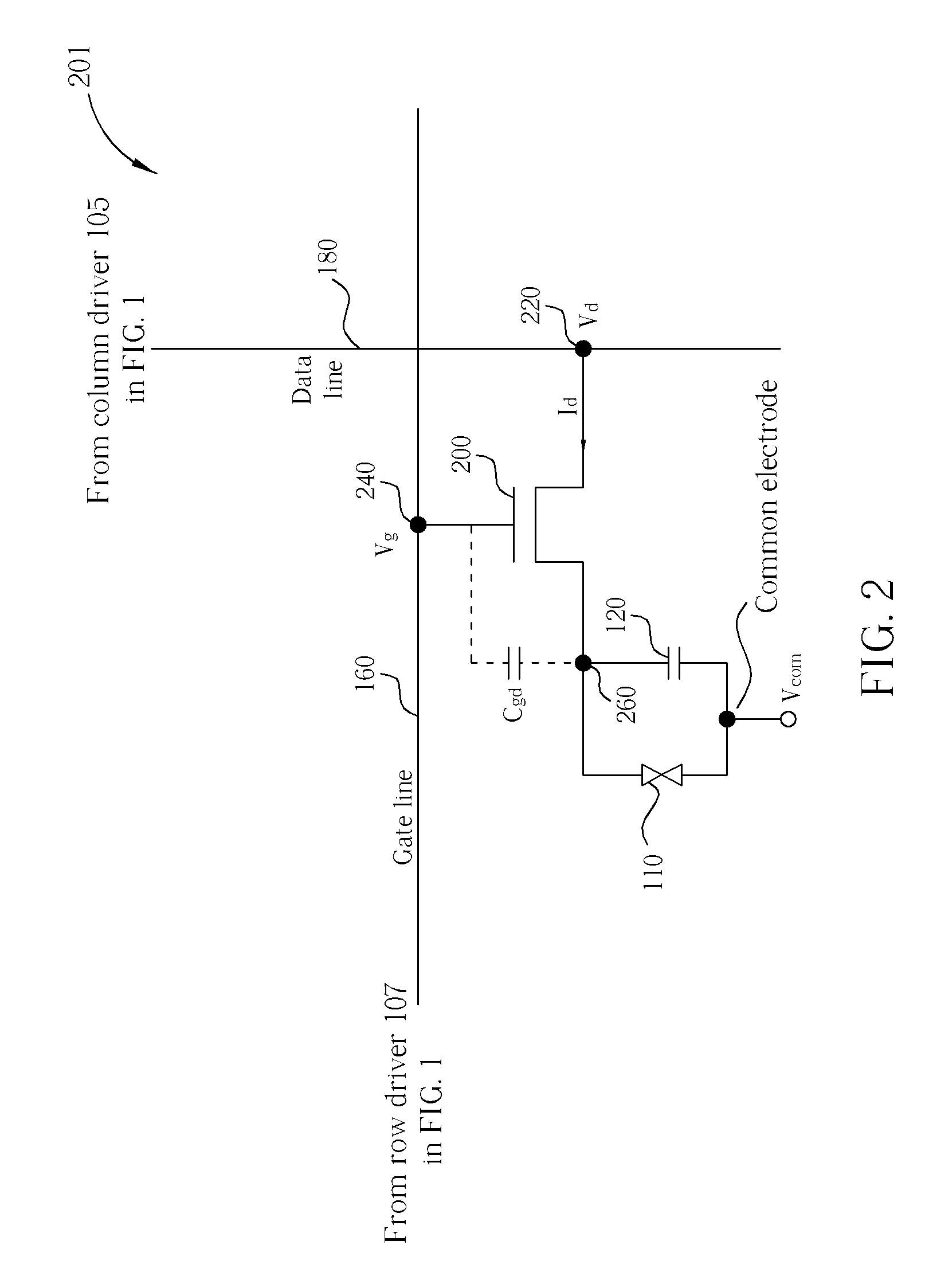
Secure communications system for collaborative computing
InactiveUS6901448B2Improve scalabilityEliminate points of failureSpecial service provision for substationMultiple digital computer combinationsCommunications systemPrivate network
A method of distributed collaborative computing is provided. The method includes: partitioning a collaboration function into sub-functions; assigning at least one said sub-function to each of a plurality of logical processes; associating a respective management process with each of said plurality of logical processes, said logical processes configured so that each said logical process is capable of communicating with every other said logical process through said respective management process; communicating between said logical processes using said respective management processes; and monitoring said respective management processes with a single supervisor process; wherein said communicating employs a secure protocol on a dedicated network.
Owner:CISCO TECH INC
Solution builder wizard
InactiveUS20060228654A1Photoprinting processesVisual/graphical programmingGraphicsGraphical user interface
A computing solution is defined by displaying to a user in a graphical user interface a palette of icons representing available computing system components for potential use in a computing solution, each of which has an associated partially-defined behavioral model. The partially-defined behavioral models contain configurable behavioral and interface parameters. When the user selects one or more of the computing system components on the palette, an instance of each selected component is created, placed, arranged and displayed in a design area. The user can then define connections between each instance of component in the design area, which triggers predetermined logical processes to prompt the user for inputs to complete the partially-defined models for each instance of component. Finally, system solution behavioral model is created or saved comprising a collection of configured component instance behavioral models.
Owner:IBM CORP
Non-Volatile Memory Embedded In A Conventional Logic Process And Methods For Operating Same
InactiveUS20070279987A1Minimizes probabilityHighly optimized SoCSolid-state devicesRead-only memoriesBit lineFowler nordheim
A non-volatile memory system including an array of cells, each having an access transistor and a capacitor sharing a floating gate. The access transistors in each row are fabricated in separate well regions, which are independently biased. Within each row, the source of each access transistor is coupled to a corresponding virtual ground line, and each capacitor structure is coupled to a corresponding word line. Alternately, the source of each access transistor in a column is coupled to a corresponding virtual ground line. Within each column, the drain of each access transistor is coupled to a corresponding bit line. Select memory cells in each row are programmed by band-to-band tunneling. Bit line biasing prevents programming of non-selected cells of the row. Programming is prevented in non-selected rows by controlling the well region voltages of these rows. Sector erase operations are implemented by Fowler-Nordheim tunneling.
Owner:MOSYS INC
System for improving overall battery life of a GSM communication device
InactiveUS20070184836A1Extend battery lifeMaximizing lifetime of battery cellPower managementEnergy efficient ICTDefinite periodLogical process
Disclosed is a system for improving the overall battery life of a GSM device according to an optimization mechanism for suspending neighbor-cell scanning in a GSM wireless communication system, the system having a wireless device including: (a) a Central Processing Unit (CPU) executing software programs intended to comply with GSM protocol specifications; (b) an RF transmission unit and an RF reception unit functioning either independently or as a single unit; (c) a specialized Digital Signal Processor being able to process received signal at a corresponding receiving antenna and offering estimates of the received signal level and quality; (d) a logic process by which the mobile terminal powers off an RF module thereof for a definite period of time and wakes up at a pre-determined interval to listen to paging messages transmitted thereto; and (e) firmware / software performing neighbor cell monitoring in compliance with a protocol mandated by GSM standards.
Owner:SAMSUNG ELECTRONICS CO LTD
Lightweight directory access protocol workflow management system
InactiveUS7133833B1Easy to shareOffice automationSpecific program execution arrangementsLogical processDirectory Access Protocol
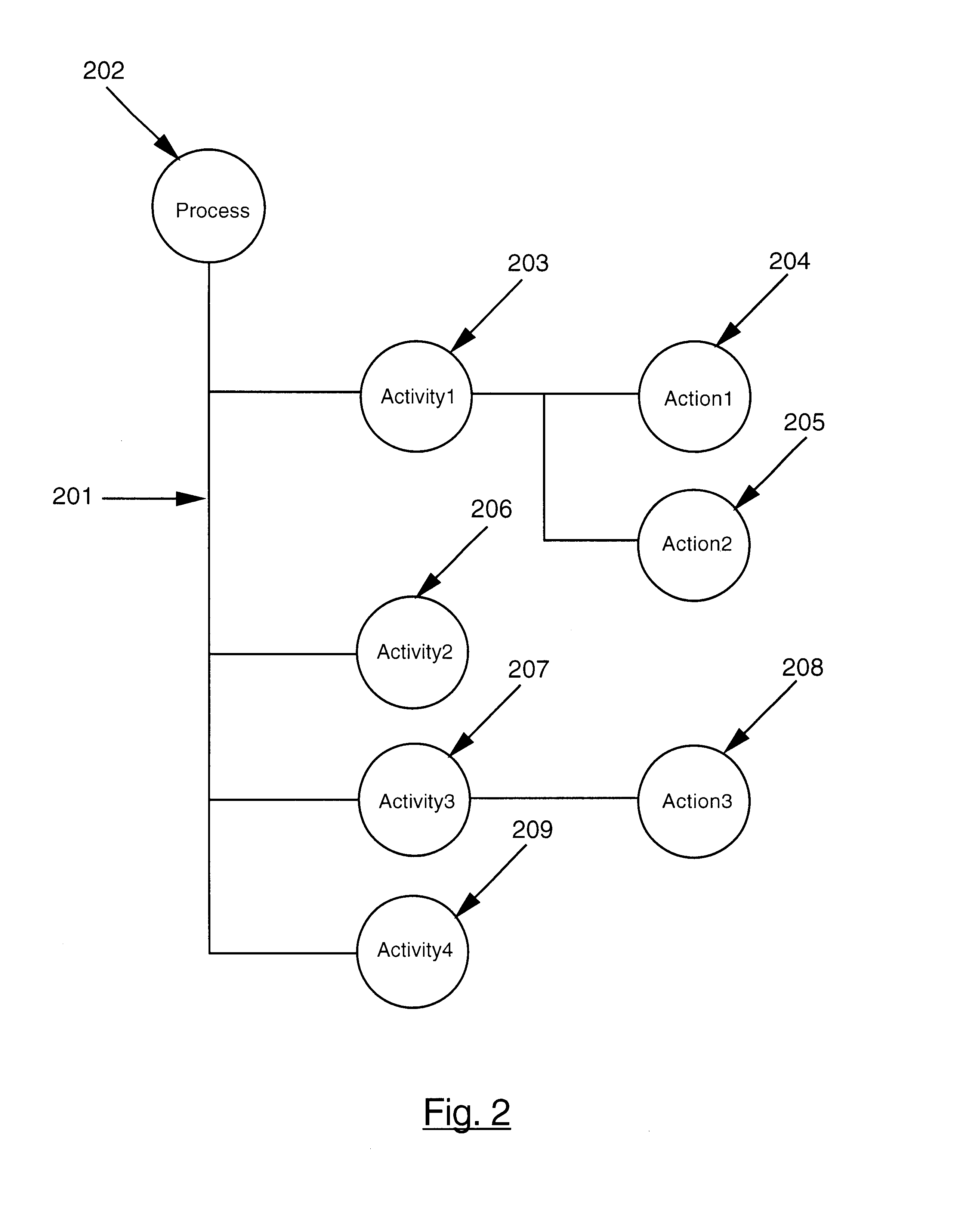
A lightweight directory access protocol workflow management system. The invention converts a logical process into a reusable Lightweight Directory Access Protocol (LDAP) directory representation. The directory representation is a hierarchical tree structure where each process element in the process is represented as an LDAP directory entry and is assigned a unique distinguished name and is stored in a Directory Server database or filesystem. The tree structure of the LDAP representation allows the sharing of LDAP trees or subtrees among users. The LDAP trees and subtrees can be remotely located and distributed among different LDAP servers. Another preferred embodiment of the invention provides a graphical user interface for creating a Workflow process definition which is comprised of process elements: activities; actions; and entry / exit points. The user constructs a Workflow process using the process elements, logically interrelating each activity. Once the Workflow process is defined it is converted into an LDAP directory representation and stored in a Directory Server database or filesystem.
Owner:META PLATFORMS INC
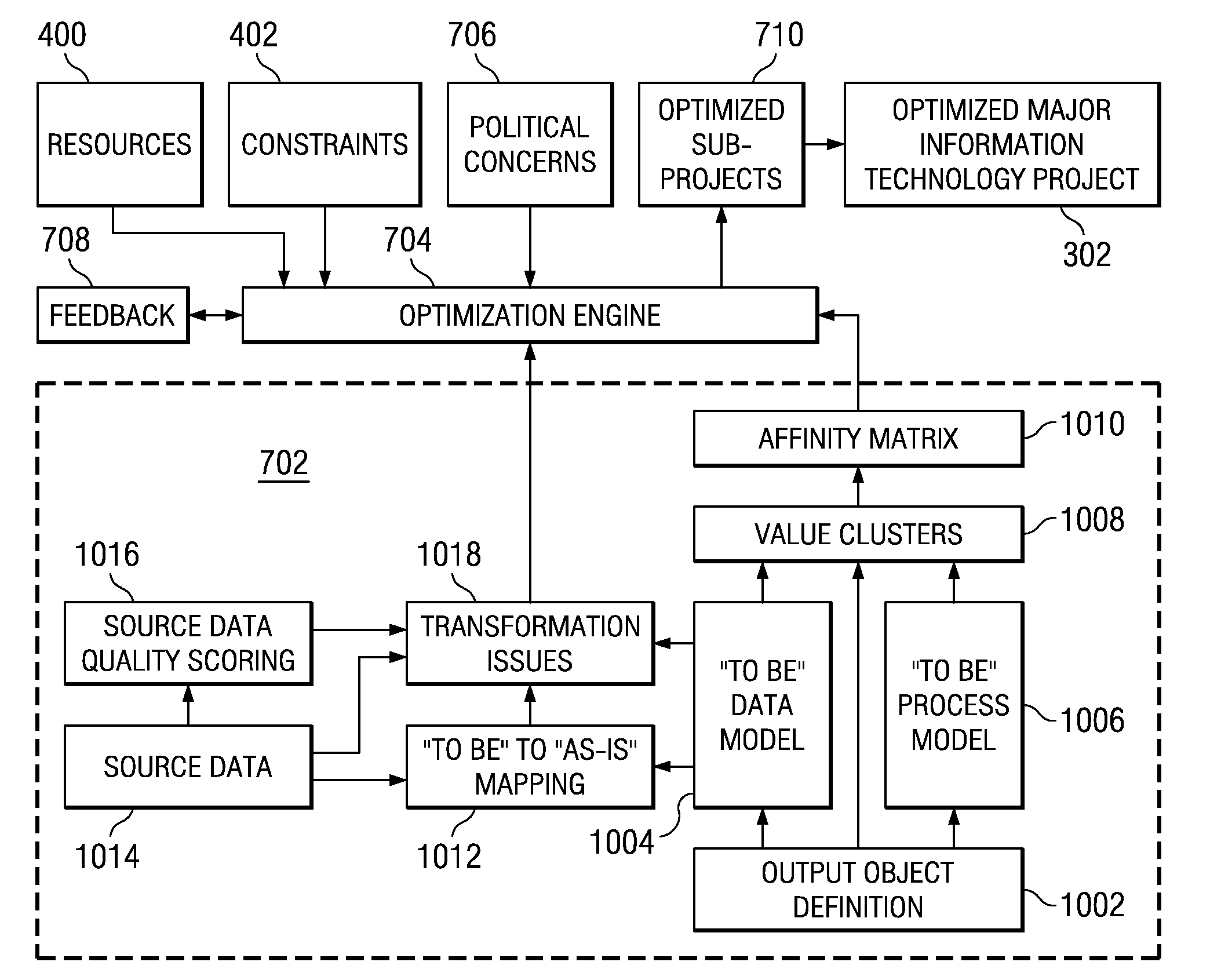
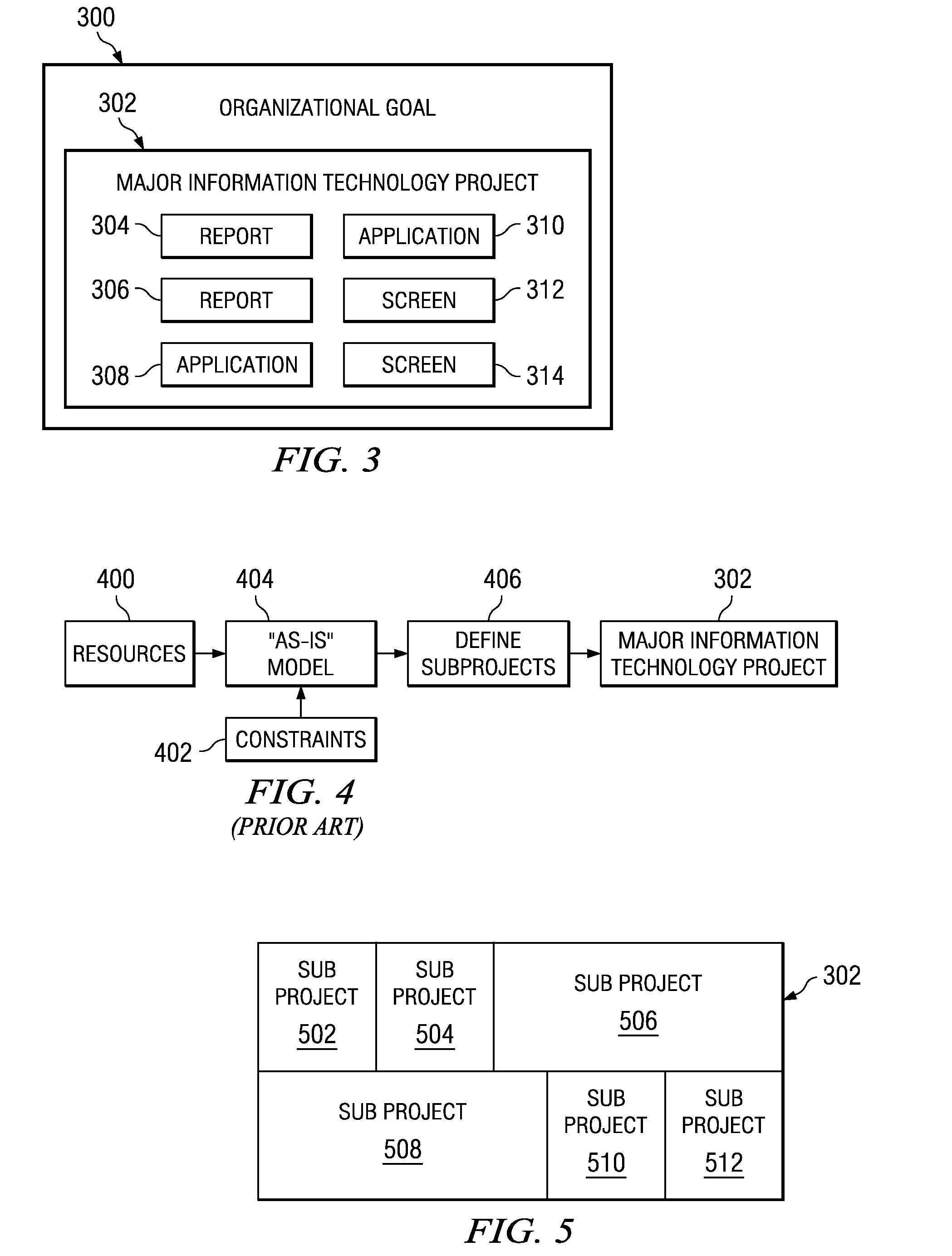
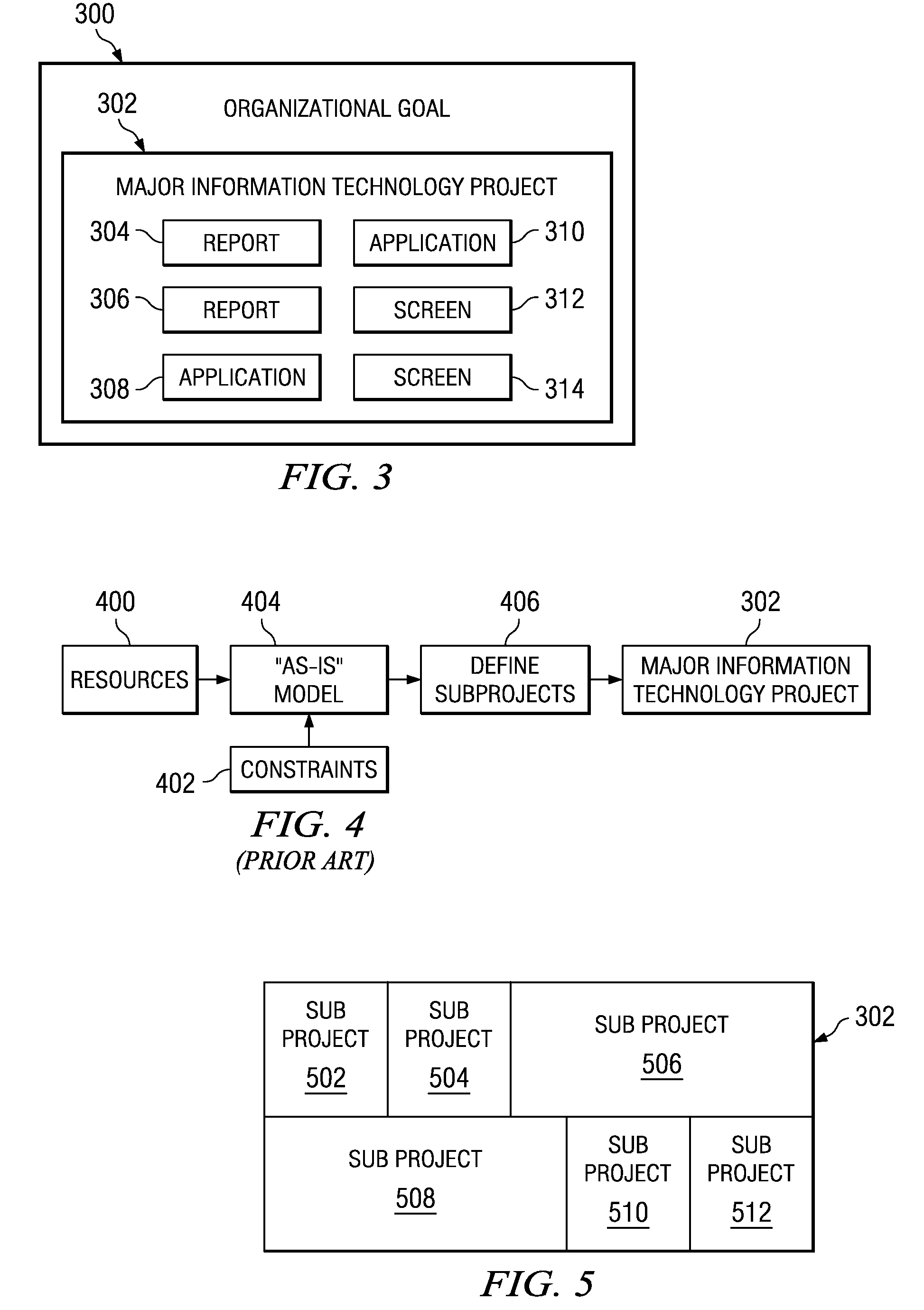
System and method for optimizing project subdivision using data and requirements focuses subject to multidimensional constraints
A computer-implemented method for creating optimized sub-projects for a project. Boundary conditions, input regarding output objects, and input regarding “as-is” data sources are received. The output objects are decomposed into data objects and logical processes used to create the output objects. Value clusters are determined. The data objects are organized into “to be” data structures and the “to be” which are mapped to the “as-is” data sources. Additional processes are determined for moving data from a source to a target. An affinity matrix is created based on the value clusters. Finally, an optimization operation is executed with an optimization engine to produce the optimized sub-projects. The optimization engine takes as inputs the above information.
Owner:IBM CORP
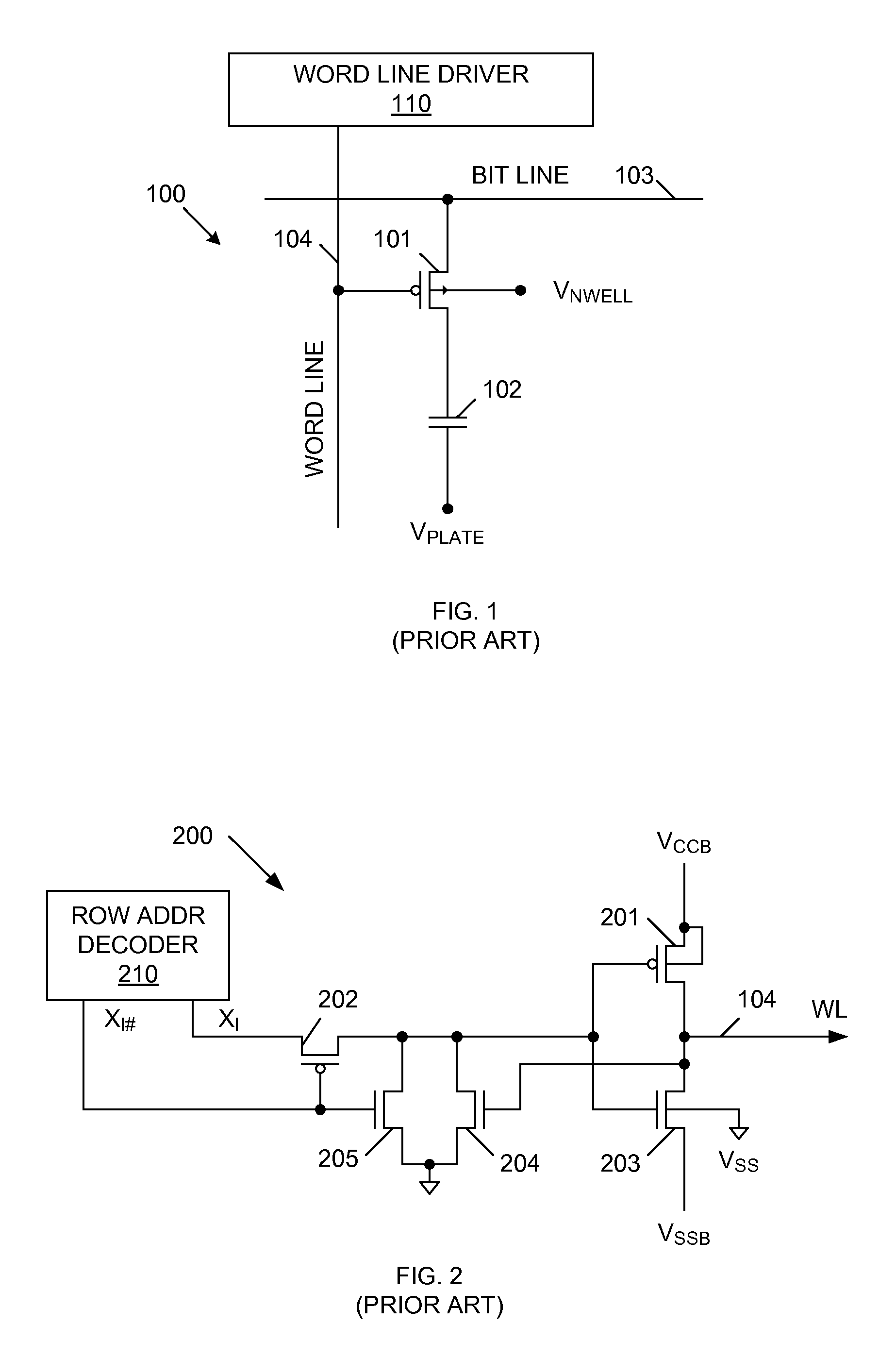
Word line driver for DRAM embedded in a logic process
InactiveUS20060291321A1Avoid flowSolid-state devicesDigital storageElectrical polarityLogical process
A word line driver is provided for accessing a DRAM cell embedded in a conventional logic process. The DRAM cell includes a p-channel access transistor coupled to a cell capacitor. The word line driver includes an n-channel transistor located in a p-well, wherein the p-well is located in a deep n-well. The deep n-well is located in a p-type substrate. A word line couples the drain of the n-channel transistor to the gate of the p-channel access transistor. A negative boosted voltage supply applies a negative boosted voltage to the p-well and the source of the n-channel transistor. The negative boosted voltage is less than ground by an amount equal to or greater than the threshold voltage of the p-channel access transistor. The deep n-well and the p-type substrate are coupled to ground. The various polarities can be reversed in another embodiment.
Owner:INVENSAS CORP
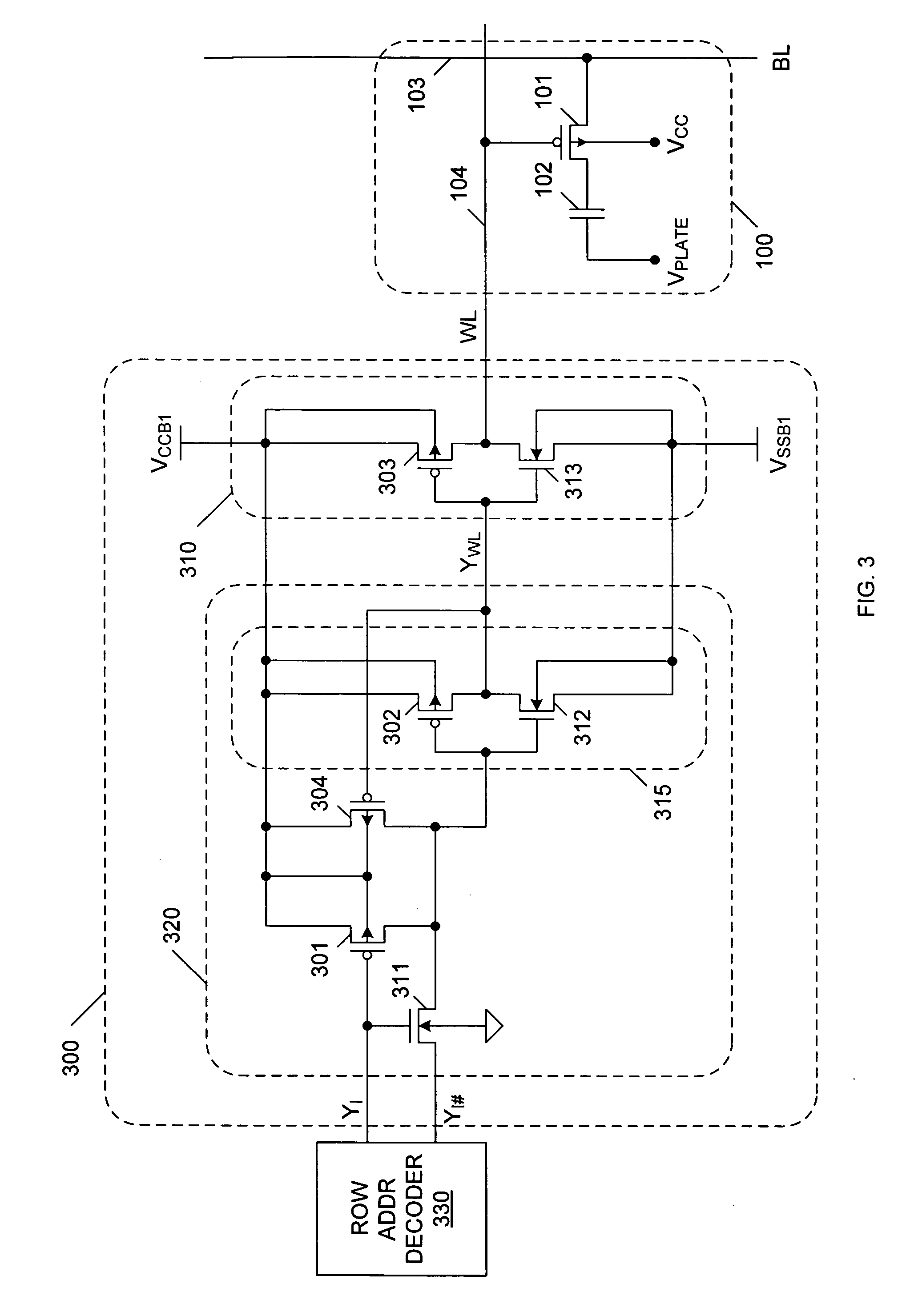
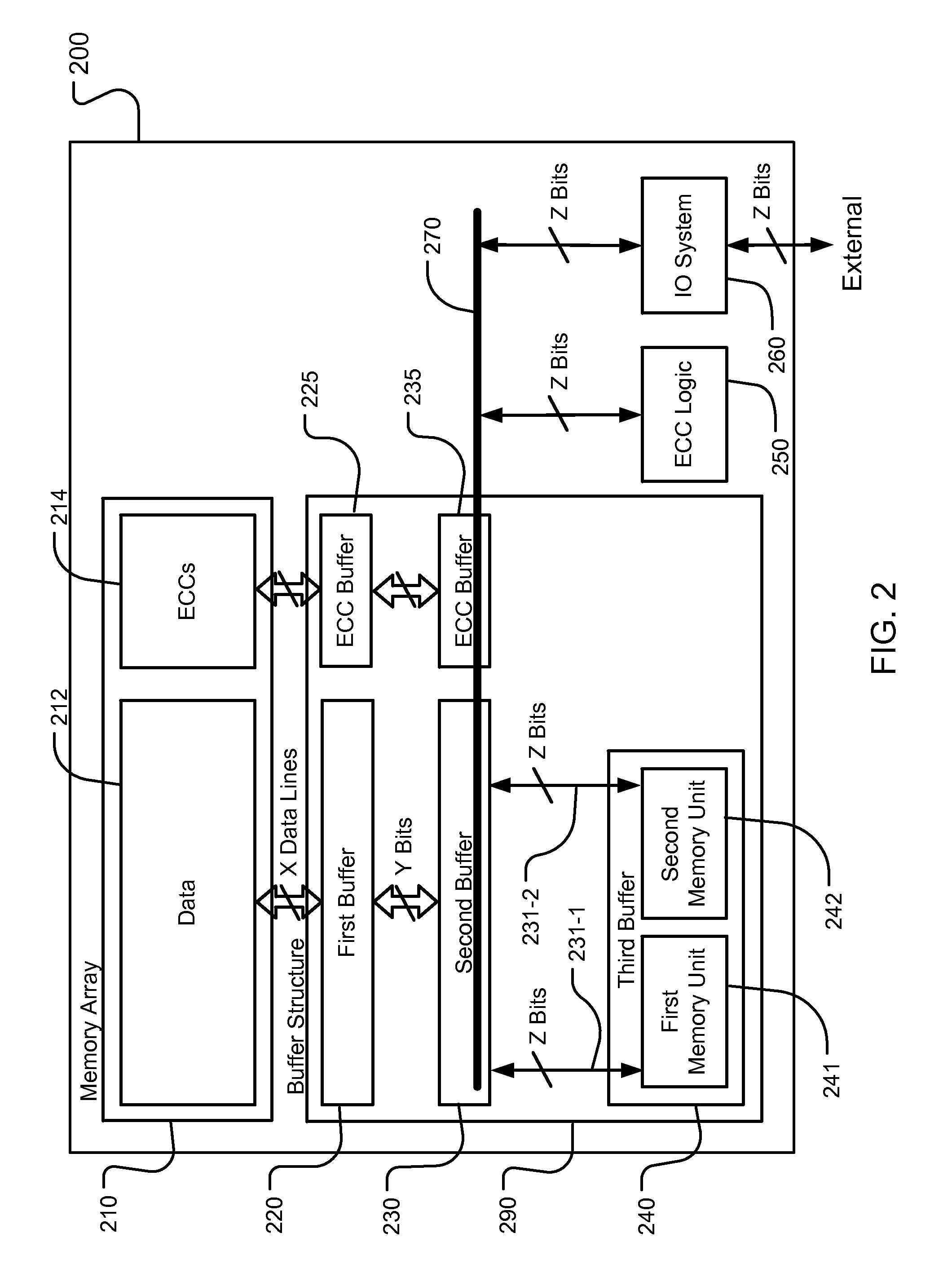
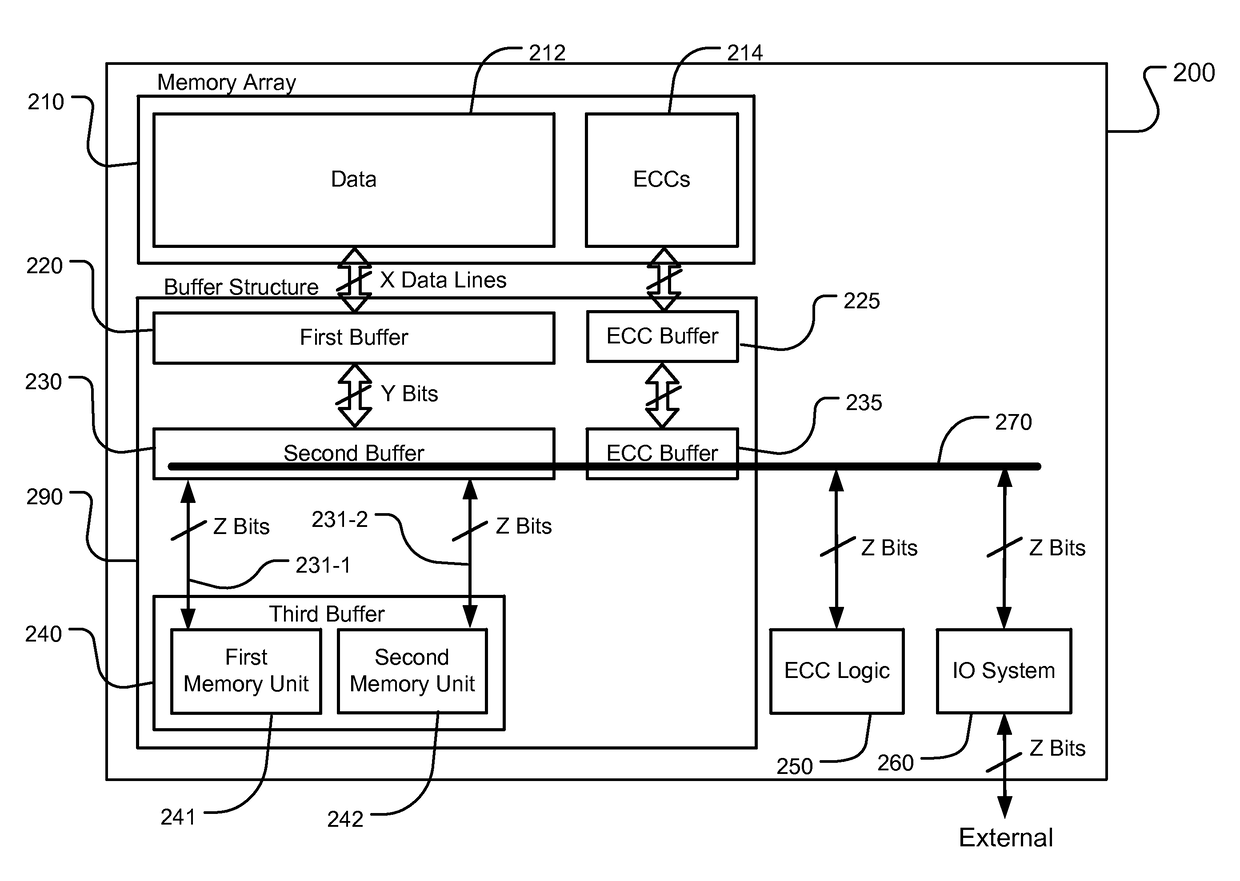
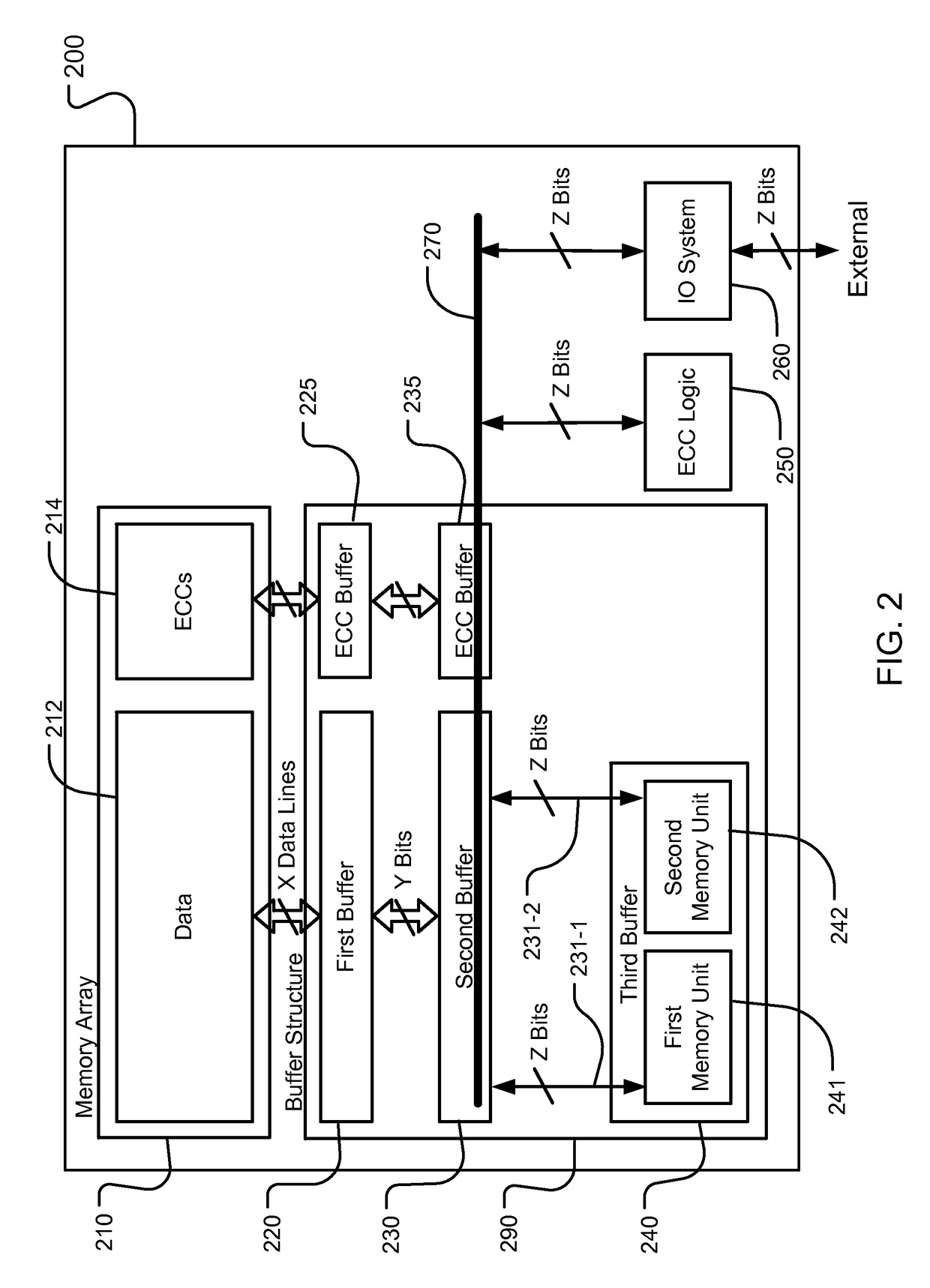
Storage scheme for built-in ecc operations
A device includes a memory array storing data and error correcting codes ECCs corresponding to the data, and a multi-level buffer structure between the memory array and an input / output data path. The memory array includes a plurality of data lines for page mode operations. The buffer structure includes a first buffer having storage cells connected to respective data lines in the plurality of data lines for a page of data, a second buffer coupled to the storage cells in the first buffer for storing at least one page of data, and a third buffer coupled to the second buffer and to the input / output data path. The device includes logic coupled to the multi-level buffer to perform a logical process over pages of data during movement between the memory array and the input / output path through the multi-level buffer for at least one of page read and page write operations.
Owner:MACRONIX INT CO LTD
Processing related data from information sources
InactiveUS20110010346A1Increase development costsAvoid difficult choicesData processing applicationsDigital data information retrievalLogical processData mining
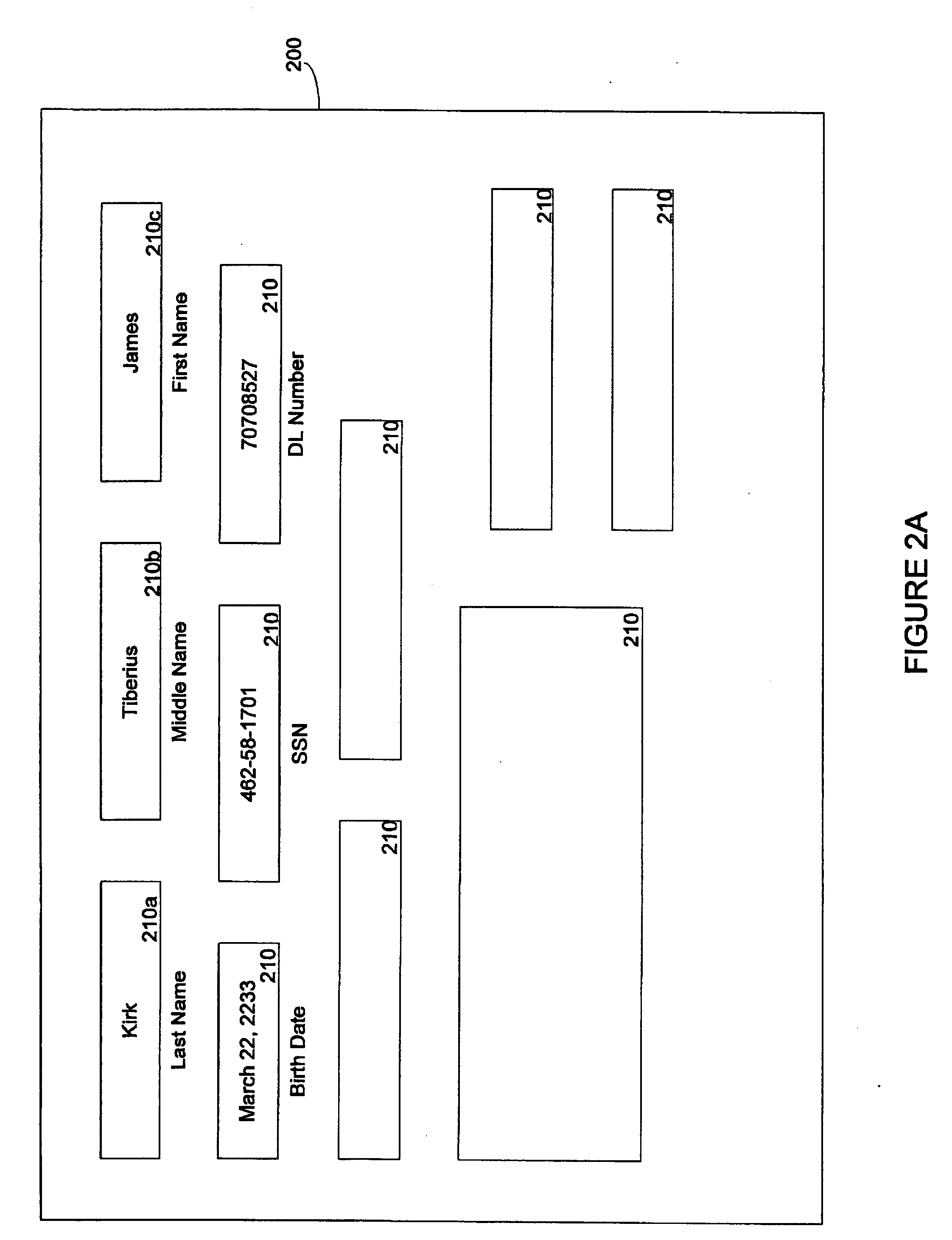
Systems and methods for managing data are disclosed. Embodiments of the present invention may allow attribute values associated with data records to be assembled and presented in a unified manner. More particularly, embodiments of the present invention may utilize a set of locally stored identity information associated with a data record to determine a set of logical procedures operable to retrieve values for one or more non-identity attributes from a remote location. Furthermore, other embodiments of the present invention may apply a logical procedure to the values of the attributes corresponding to data records to select one or more values of one or more attributes of the data records.
Owner:IBM CORP
Method and System for Service Provisioning
InactiveUS20110010728A1Easy to useBridging the gapDigital data information retrievalDigital data processing detailsInterface layerLogical process
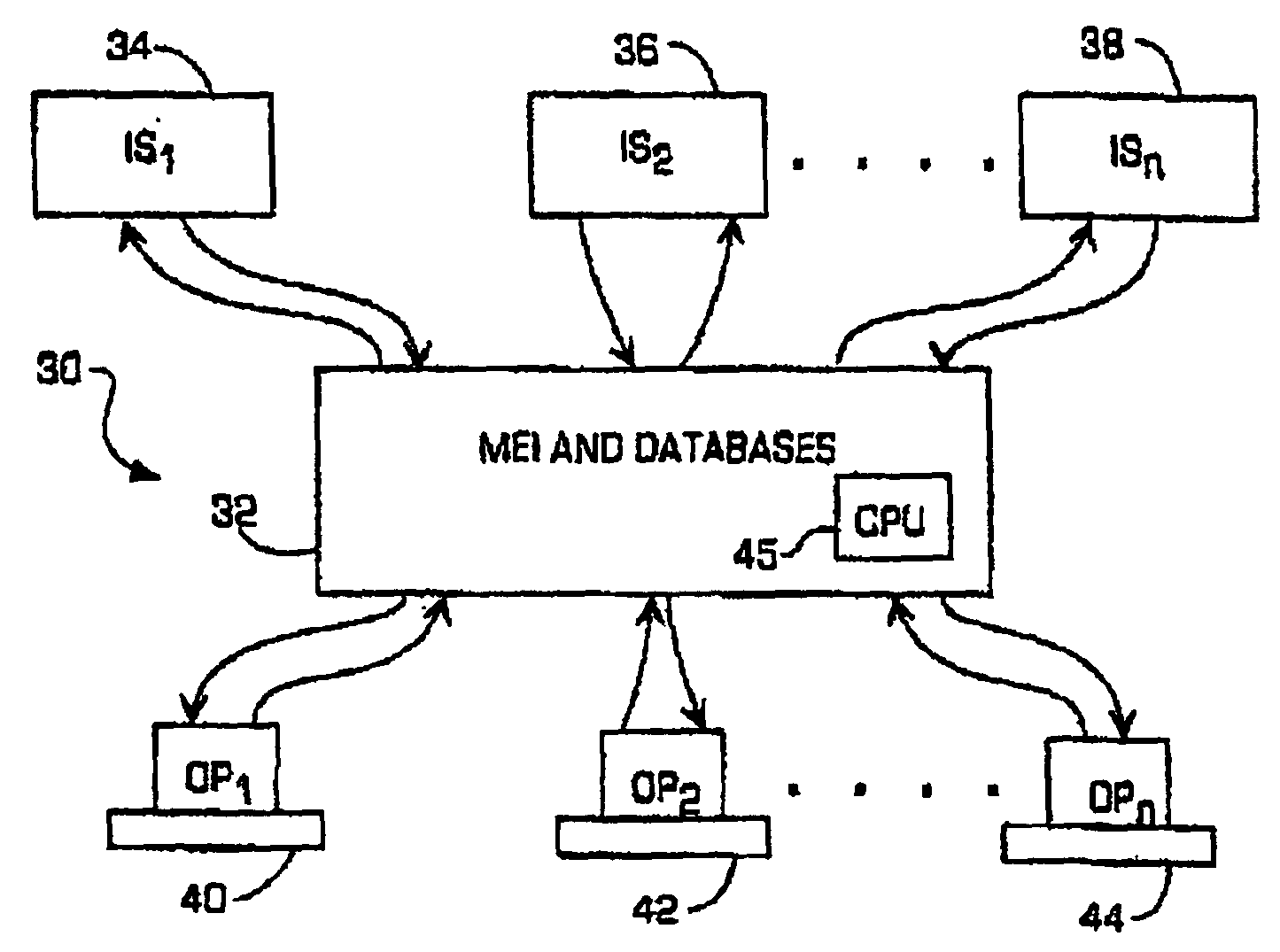
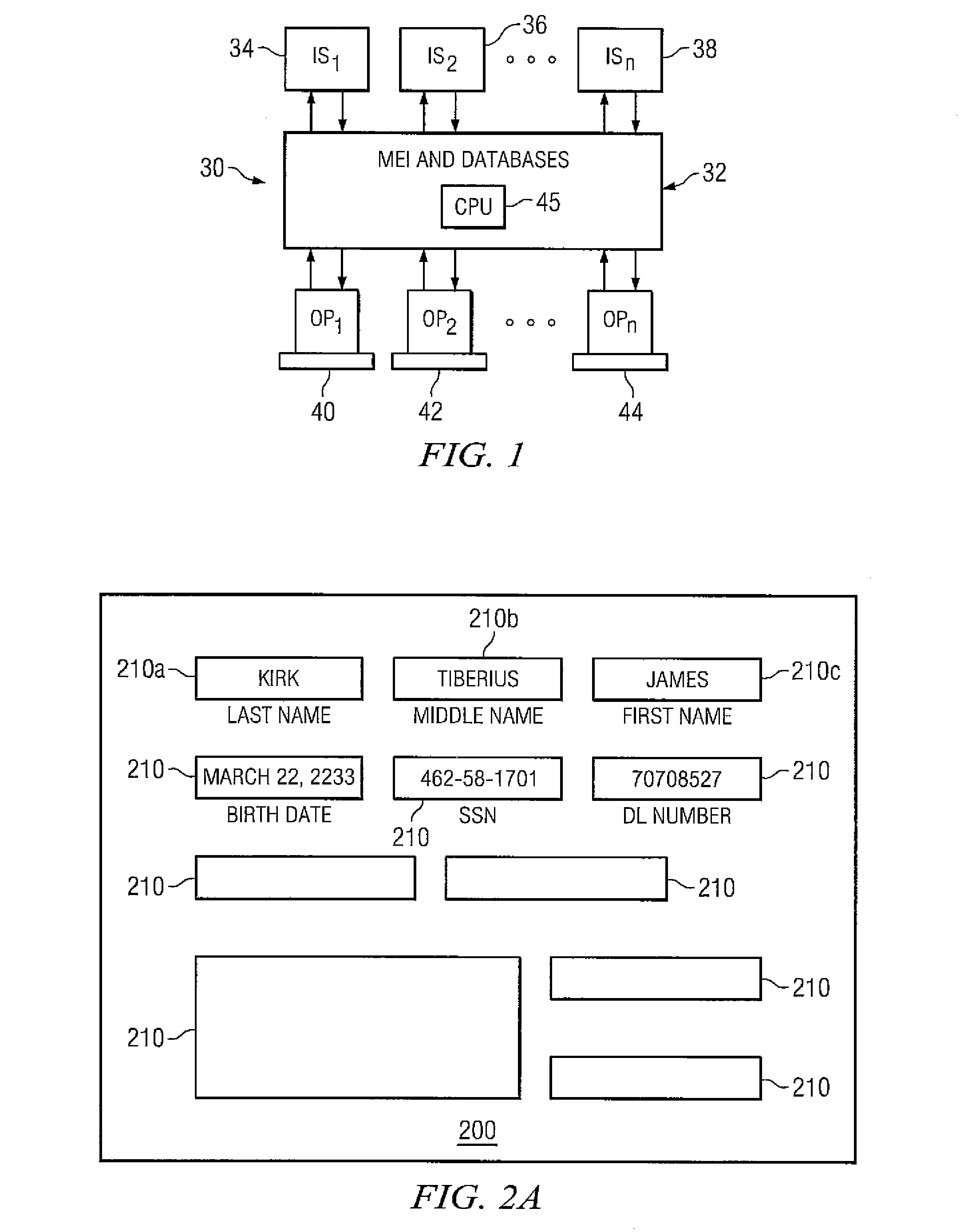
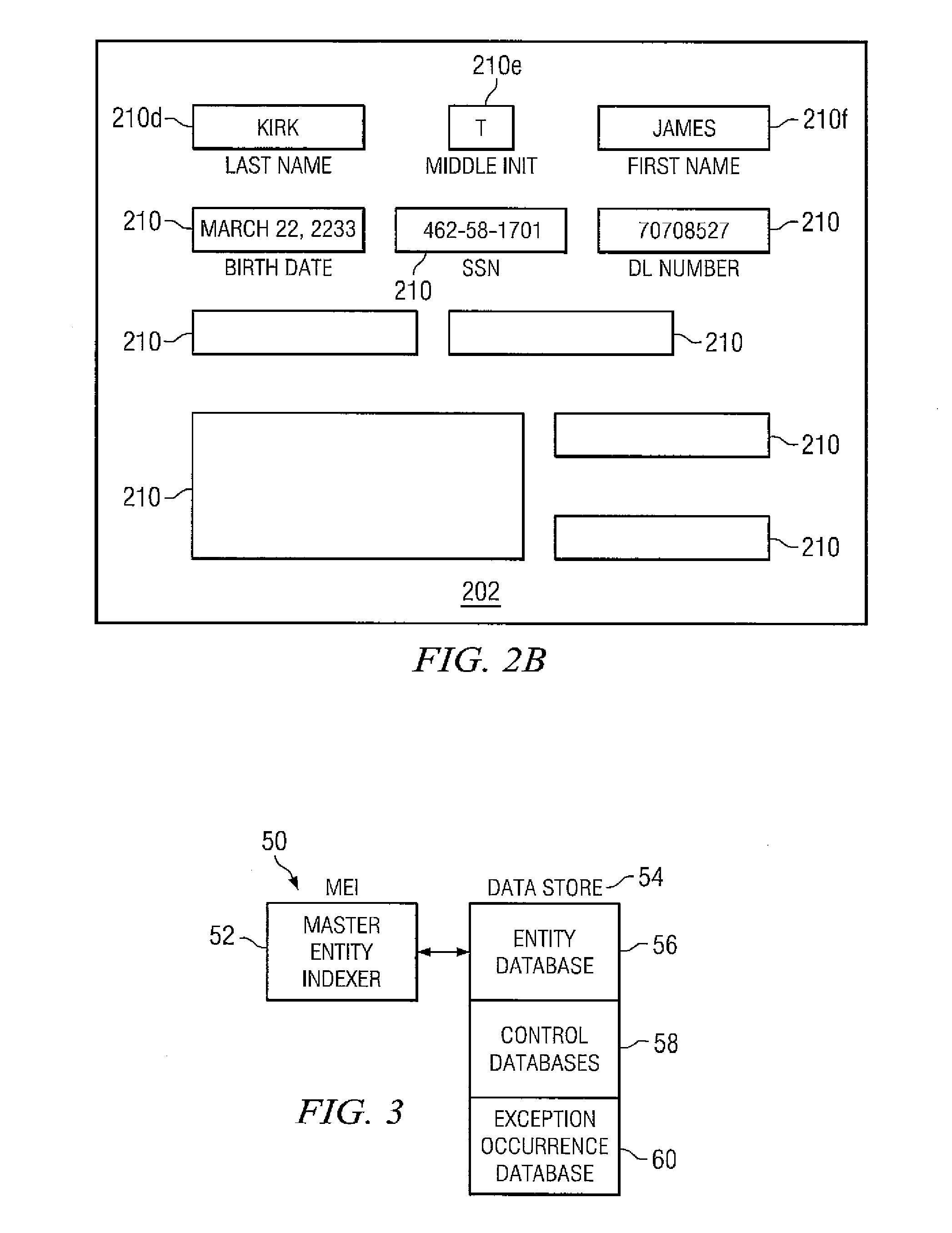
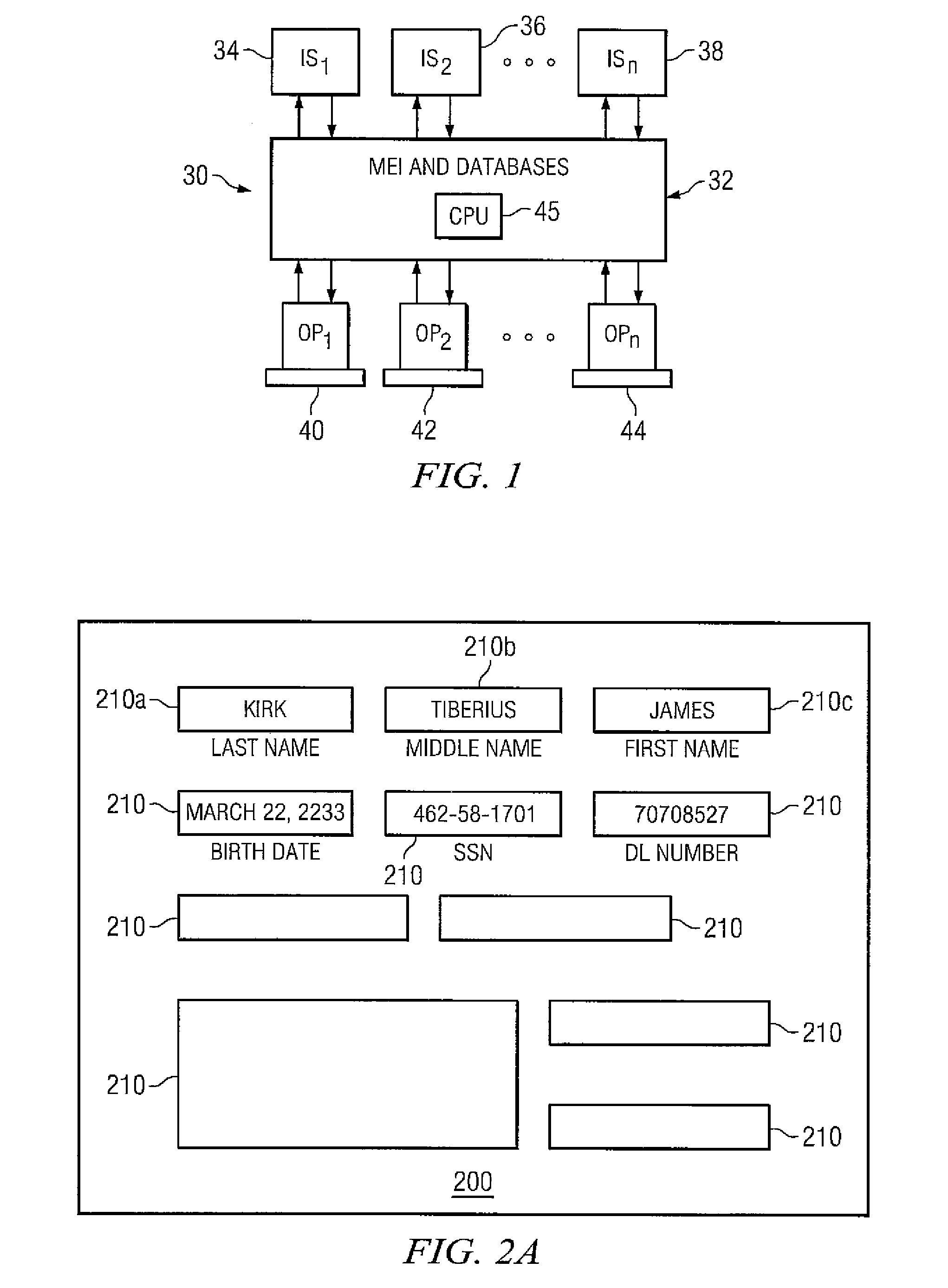
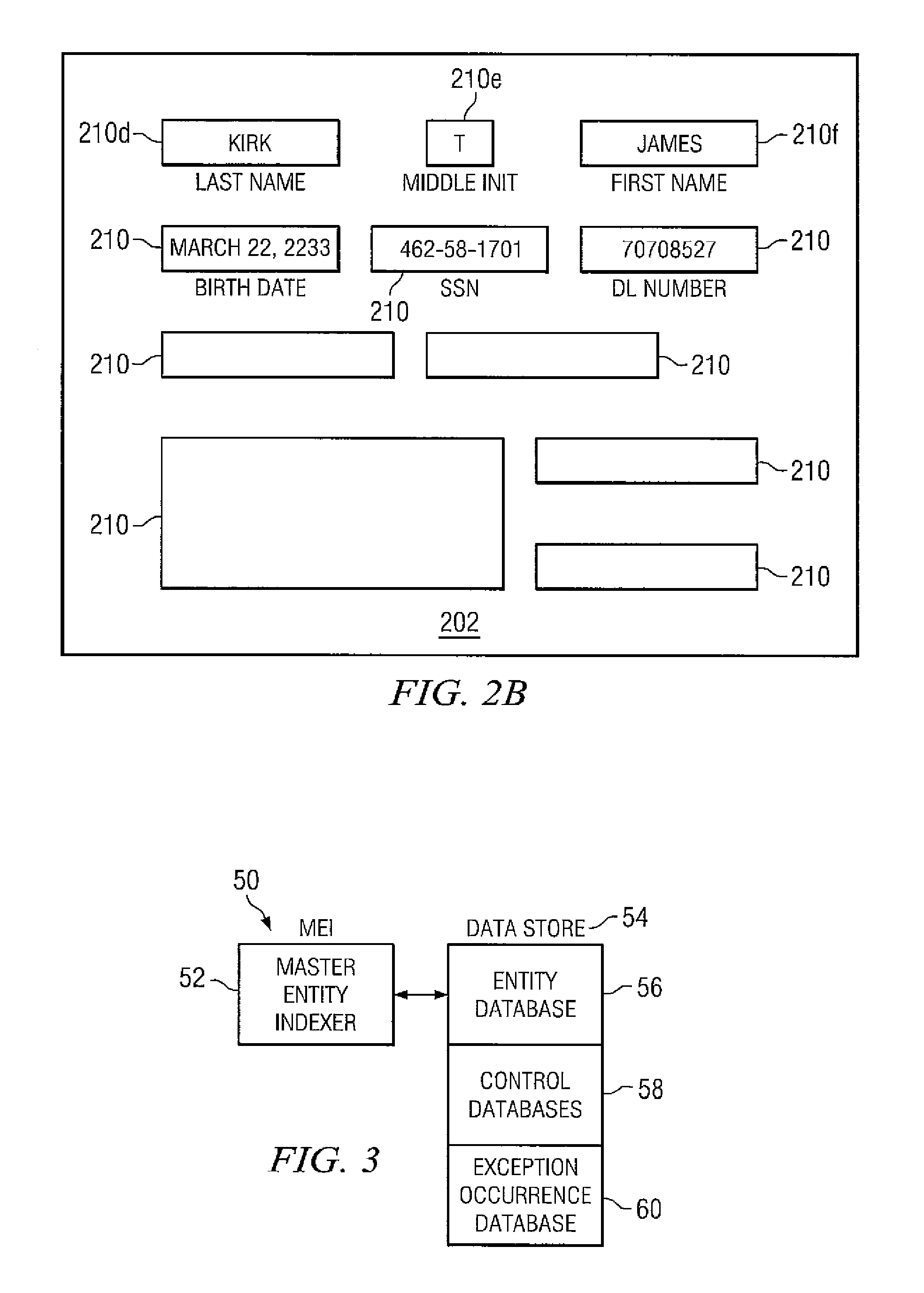
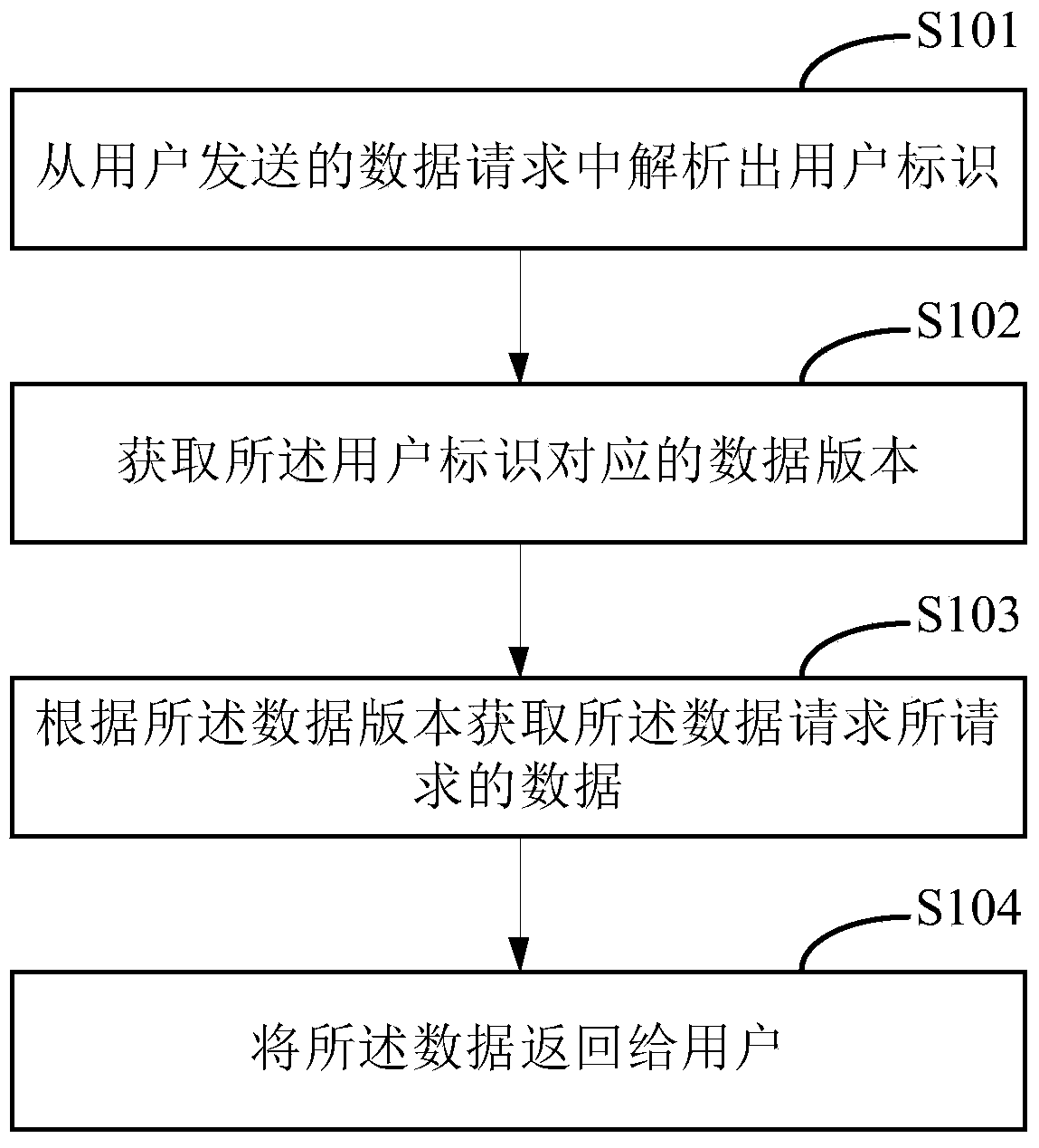
Embodiments disclosed herein provide systems and methods that can bridge the gap between business operations and data management operations. An interface layer provides customizable interfaces for interactions with a master entity index (MEI) system to accomplish association, storage, management or processing of data records based on user-defined business service operations. The interface layer allows a user to define business services, operations, and logical procedures according to a desired data model such that the inputs and outputs for each operation of the service correspond to the particular needs of the user and allow different terminology to be employed by the user.
Owner:AIRBNB
Service provisioning
InactiveUS8423514B2Easy to useBridging the gapDigital data information retrievalDigital data processing detailsInterface layerData management
Embodiments disclosed herein provide systems and methods that can bridge the gap between business operations and data management operations. An interface layer provides customizable interfaces for interactions with a master entity index (MEI) system to accomplish association, storage, management or processing of data records based on user-defined business service operations. The interface layer allows a user to define business services, operations, and logical procedures according to a desired data model such that the inputs and outputs for each operation of the service correspond to the particular needs of the user and allow different terminology to be employed by the user.
Owner:AIRBNB
Automatically managing mapping and transform rules when synchronizing systems
A method and associated system for managing rules that synchronize operations of a source system and a target system. A set of linked worksheets is generated as a function of the internal logic of the synchronization rules and of worksheets that represent data models of the source and target systems. These generated worksheets describe and relate data elements of the data models, extrinsic data that is stored externally to the source and target systems, and logical procedures performed by the synchronization rules. When the source data model, the target data model, or a logical procedure is revised, the linked worksheets are updated in response to the revision and these updates automatically propagate across the synchronization rules and across other components of the source system, the target system, and the synchronization mechanism.
Owner:IBM CORP
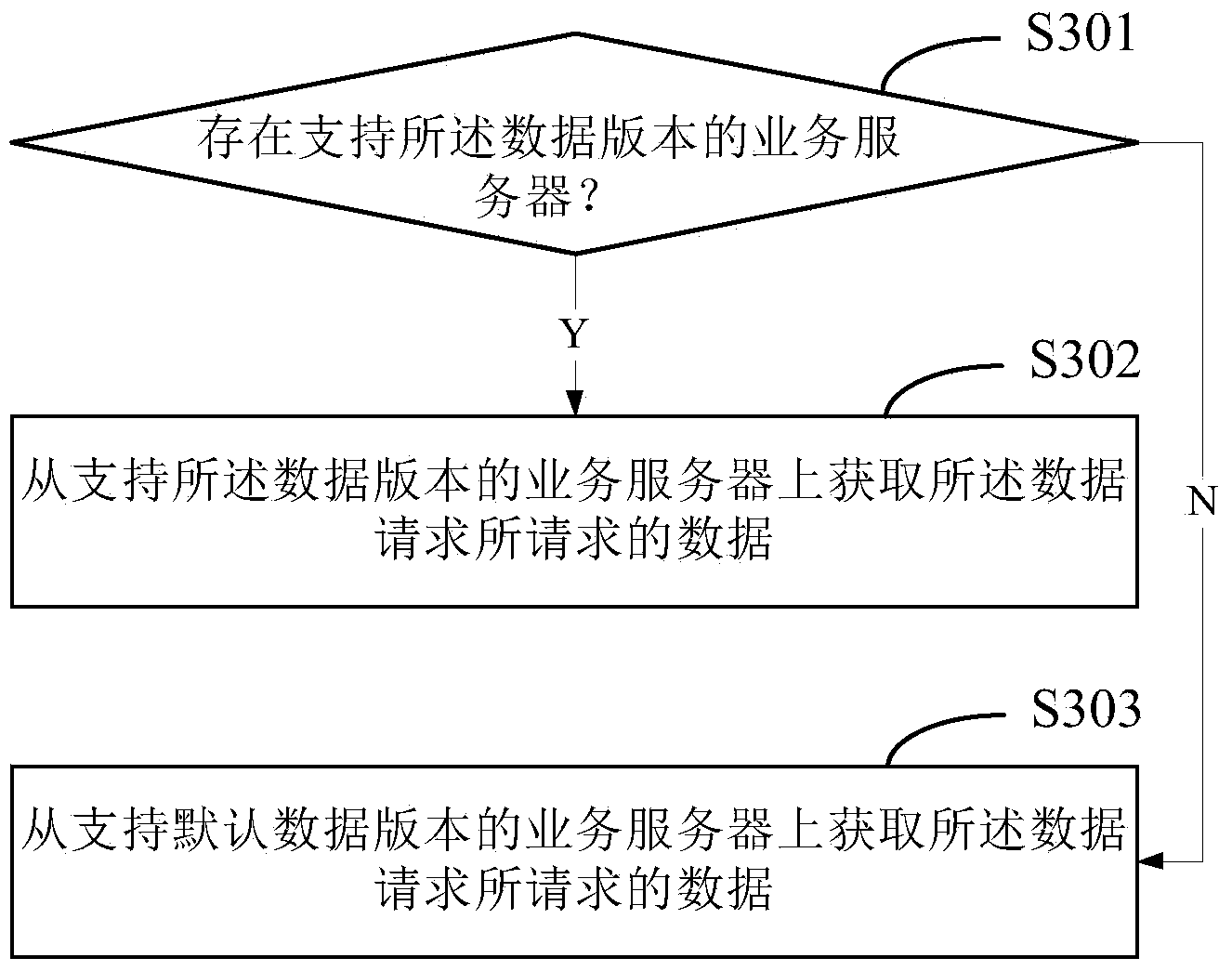
Data acquiring method and device
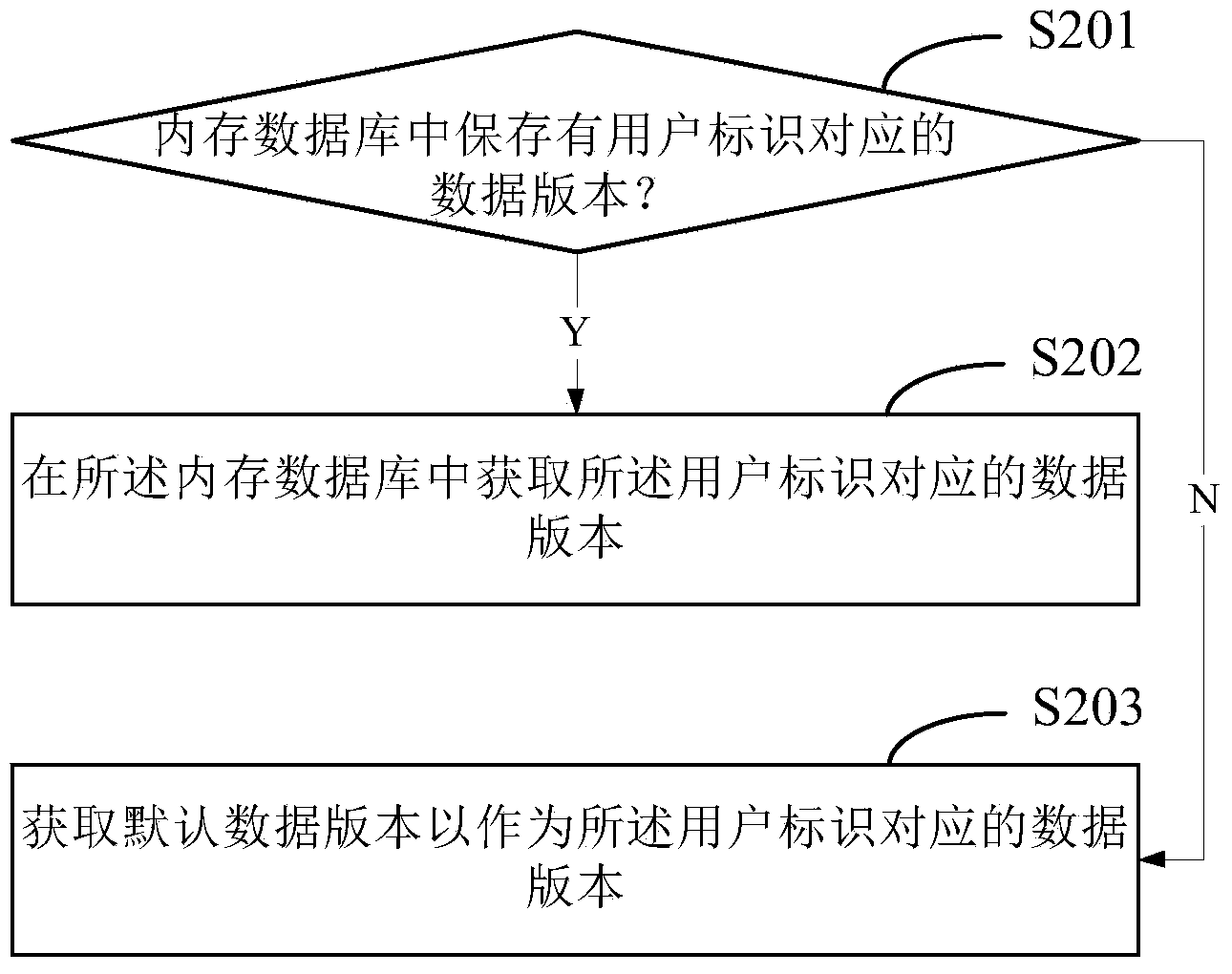
ActiveCN104317914AImprove usabilityPersistent storageWeb data indexingProgram loading/initiatingUsabilityLogical process
The invention relates to a data acquiring method and device. The data acquiring method includes analyzing data requests transmitted by users to obtain user identifiers; acquiring data versions corresponding to the user identifiers; acquiring the data requested by the data requests according to the data versions; feeding the data back to the users. During gray distribution, the logic process obtained by the data versions are separated from storage of the data versions, any distribution objects can be appointed, and usability is high.
Owner:XIAOMI INC
Security system for replicated storage devices on computer networks
ActiveUS7146499B2Improve responsivenessImprove system performanceKey distribution for secure communicationDigital data processing detailsNetwork addressingNetwork address
Through associating each data partition within a replicated storage domain of networked storage devices with one of multiple secret keys shared with a file manager, a credential is issued from the file manager to a client requesting access to a partition. The credential includes a network address for the partition to which the client is to direct its actions. The storage device periodically confirms with the file manager the validity of the shared secret keys. Through logical process and evaluations applied to issuing the credential and determining the address of the partition to be included in each credential, the file manager may invalidate partitions individually, provide load balancing between access of original and replica partitions, and provide security functions such as isolation of partitions for access by and tracking of unauthorized users, or for testing purposes.
Owner:IBM CORP
Word Line Driver For DRAM Embedded In A Logic Process
A word line driver is provided for accessing a DRAM cell embedded in a conventional logic process. The DRAM cell includes a p-channel access transistor coupled to a cell capacitor. The word line driver includes an n-channel transistor located in a p-well, wherein the p-well is located in a deep n-well. The deep n-well is located in a p-type substrate. A word line couples the drain of the n-channel transistor to the gate of the p-channel access transistor. A negative boosted voltage supply applies a negative boosted voltage to the p-well and the source of the n-channel transistor. The negative boosted voltage is less than ground by an amount equal to or greater than the threshold voltage of the p-channel access transistor. The deep n-well and the p-type substrate are coupled to ground. The various polarities can be reversed in another embodiment.
Owner:MOSYS INC
System and method for optimizing project subdivision using data and requirements focuses subject to multidimensional constraints
Owner:INT BUSINESS MASCH CORP
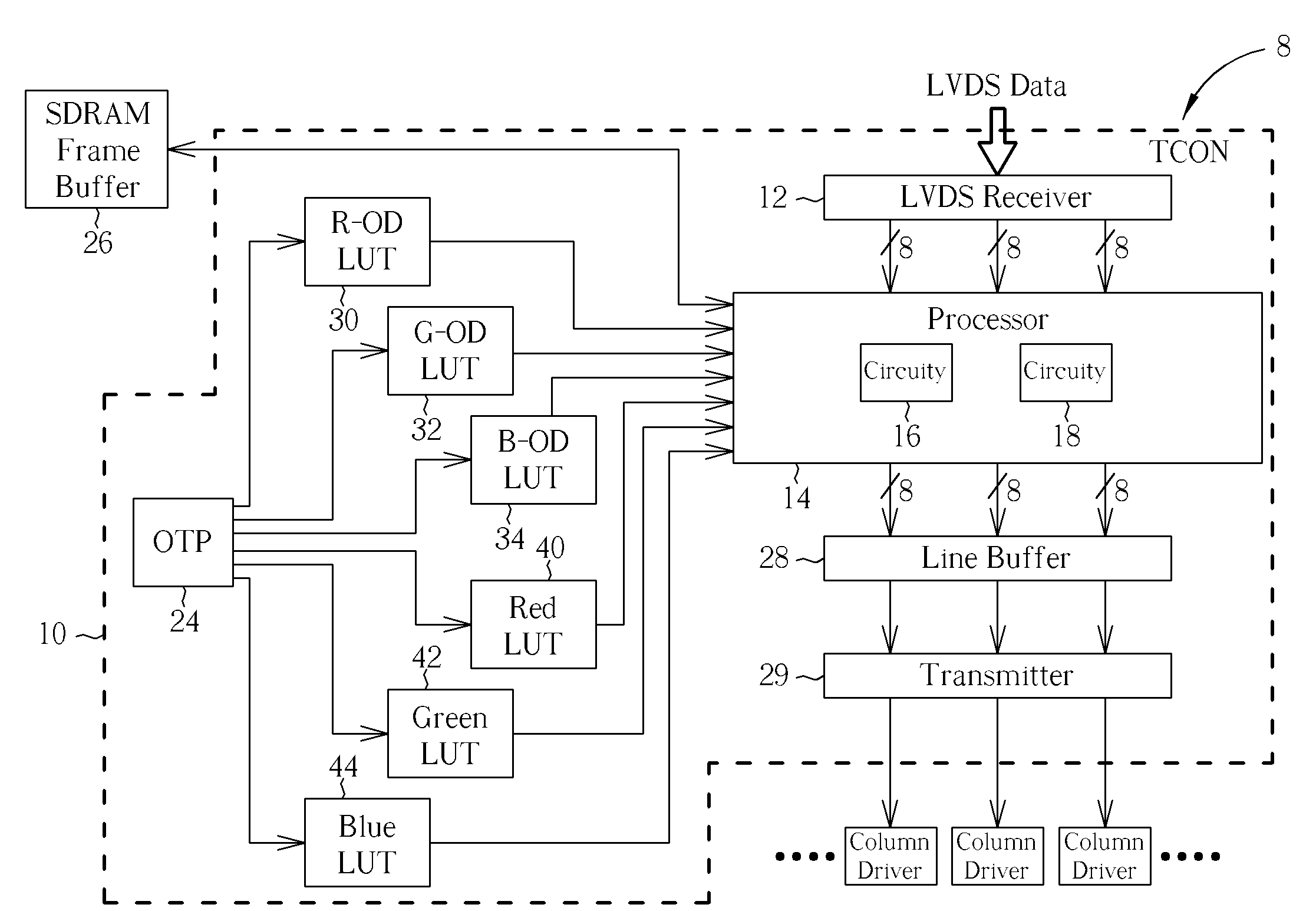
Programmable nonvolatile memory embedded in a timing controller for storing lookup tables
A timing controller in an LCD has an OTP memory—a one time programmable nonvolatile memory or a MTP memory—a multiple time programmable nonvolatile memory embedded in for storing lookup tables of overdrive functions, dynamic contrast adjustments, independent RGB Gamma curve corrections, and data conversion of cyclic DAC functions. The logic process of the OTP memory and the logic process of the timing controller are completely compatible, and the logic process of the MTP memory only needs two or three photomask processes more than the logic process of the timing controller.
Owner:EMEMORY TECH INC
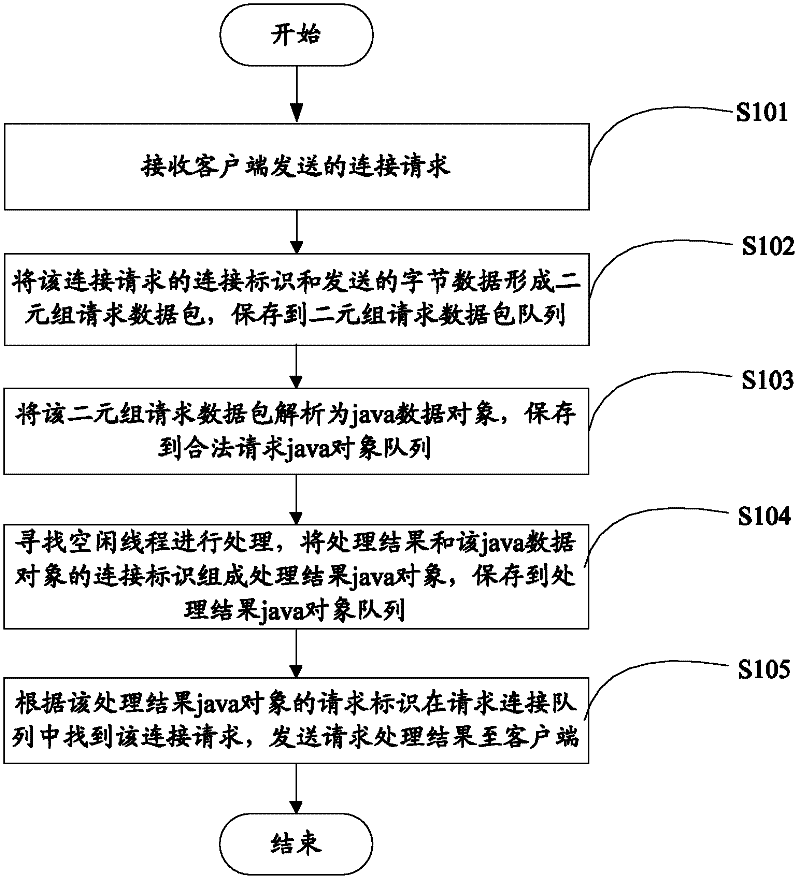
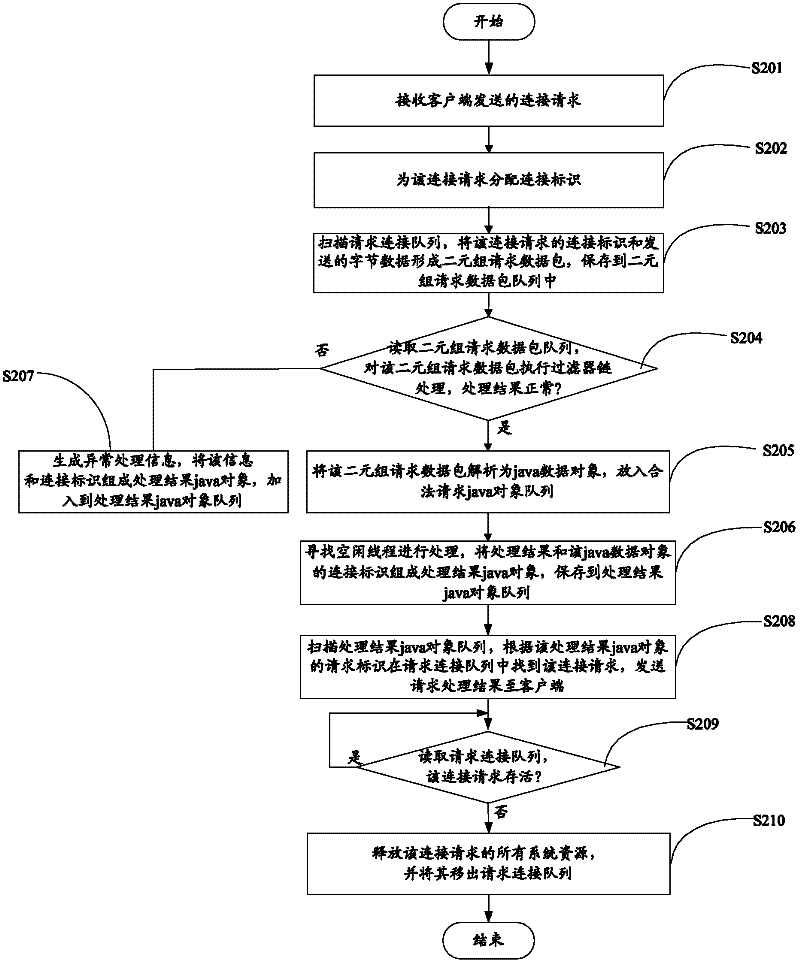
Server and data processing method thereof
InactiveCN102340545AReduce dependencyProcessing speedData switching networksNetwork packetLogical process
The invention provides a server and a data processing method thereof. The method comprises the following steps of: receiving a connection request from a client; forming a two-tuple request data packet by using a connection identifier of the connection request and transmitted byte data, and storing the two-tuple request data packet to a two-tuple request data packet queue; resolving the two-tuple request data packet into a java data object, and storing the java data object to a legal request java object queue; searching for an idle thread of a corresponding type according to the request type of the java data object for processing, forming a processing result java object by using a processing result and the connection identifier, and storing the processing result java object to a processing result java object queue; and finding the connection request from a requested connection queue according to the connection identifier, and transmitting the processing result to the client. By the technical scheme provided by the invention, the processing speed of a system is high, a thread and a code are less dependent, upgrading and maintaining are convenient, and the logical process of the system can be extended to different service rules and service logics without modification.
Owner:SHENZHEN WUJU SCI TECH
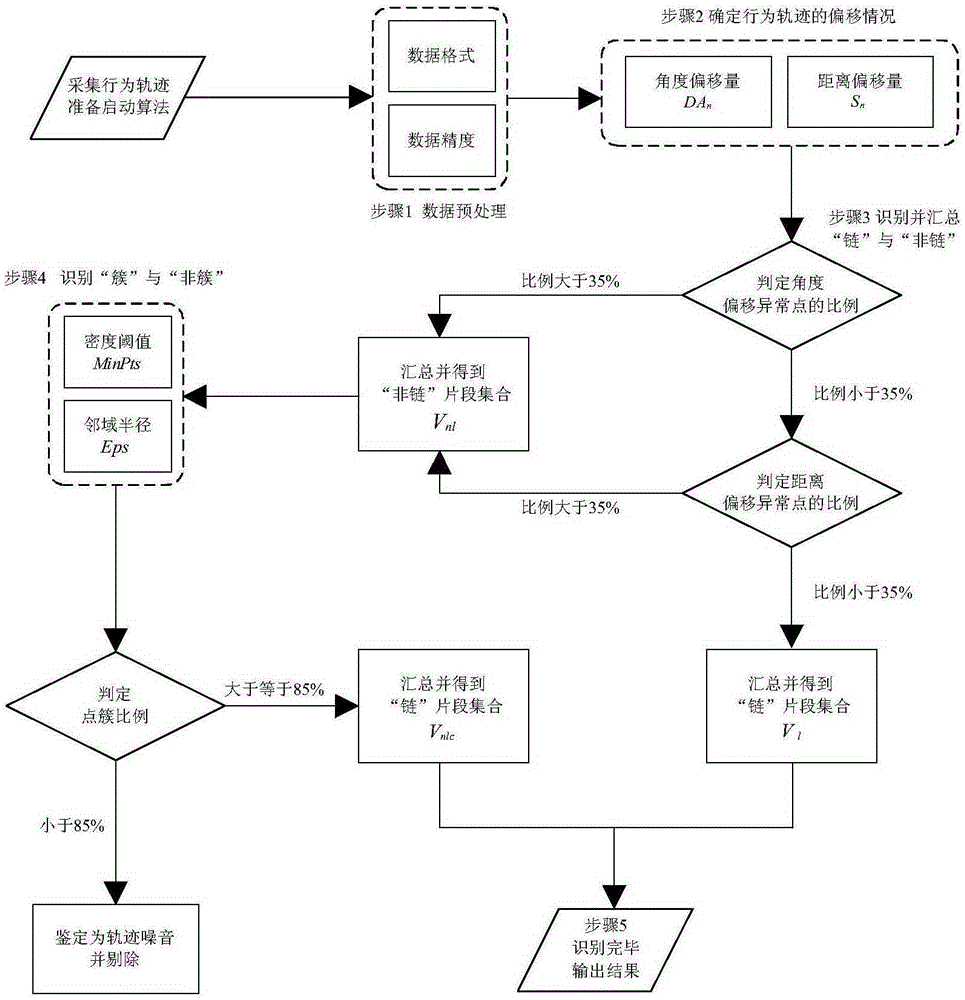
Smart-phone track chain-cluster identification method considering sequential DBSCAN
ActiveCN105206041AMake up for the lack of recognition of timing featuresHigh precisionRoad vehicles traffic controlSpecial data processing applicationsPoint clusterData acquisition
The invention discloses a smart-phone track chain-cluster identification method considering sequential DBSCAN. The method comprises that data collection and preprocessing are carried out; the sequential angle offset of behavior track points is calculated; the sequential distance offset of the behavior track points is calculated; chains and non-chains are identified and gathered according to rules; and whether a non-chain segment belongs to a point cluster is determined by using DBSCAN, and outputs an analysis result. The logical process of the behavior track identified by the human eyes is integrated with the DBSCAN by providing the two indexes, namely the sequential angle offset and the sequential distance offset, the disadvantage that a traditional algorithm cannot identify sequential features is overcome, and the accuracy of behavior track chain-cluster identification is improved.
Owner:SOUTHEAST UNIV
Remote inversion method of internal action logic of protection device
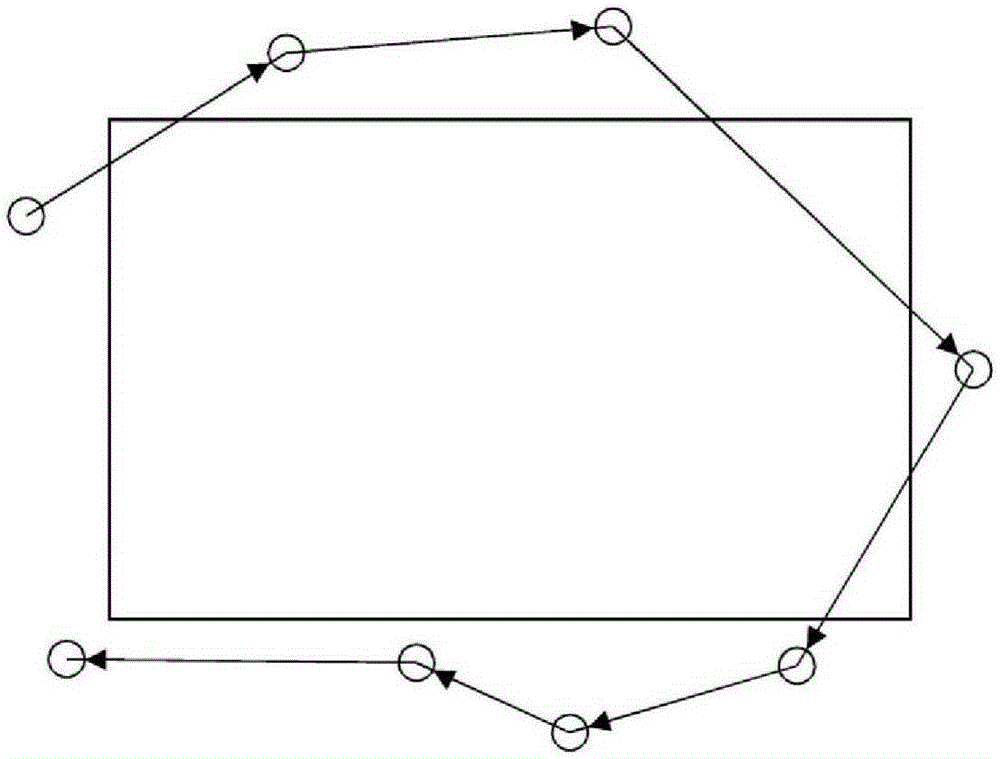
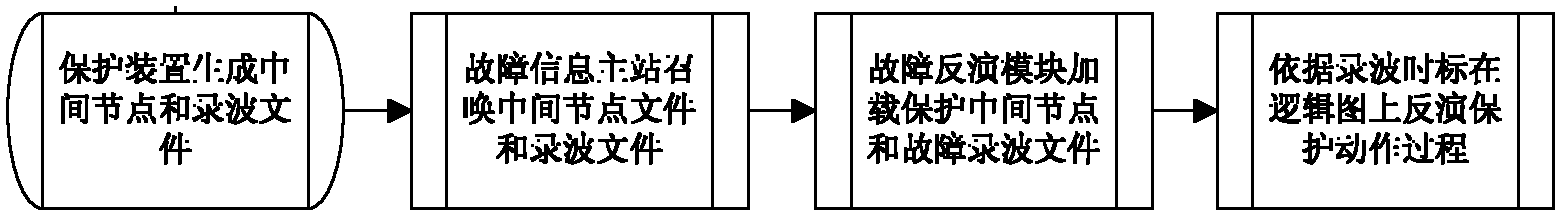
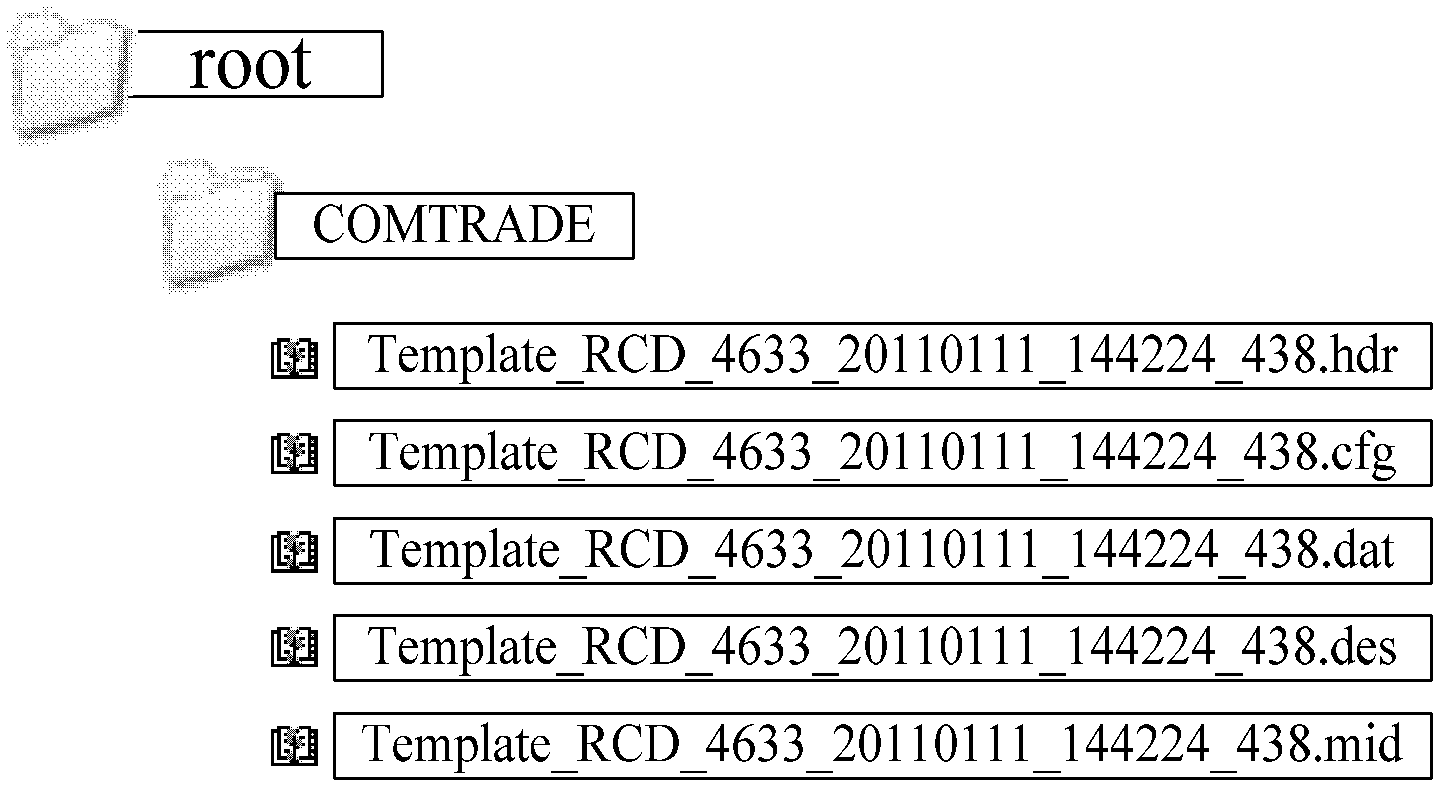
ActiveCN102496930AFast information routeAccurate Information ApproachInformation technology support systemAc network circuit arrangementsElectric power systemLogical process
The invention provides a realization method in which intermediate node information correlated to an internal action logic of a relay protection device is uploaded and a visual logic diagram is combined to invert a protection process of the internal logic when there is a fault at a power grid. The provided method can be applied to a power grid fault information system. And the method comprises the following steps that: when there is a fault at a power grid, internal logic operation information of a relay protection device is processed to generate an intermediate node file that can describe the fault in detail; according to an IEC61850-8-1 protocol, the relay protection device uploads the intermediate node file and a fault wave-recording COMTRADE file to a remote fault information master station; and a visual application module loads the intermediate node file, the protection logic diagram file and the COMTRADE fault wave-recording file to demonstrate a protection logic operation situation in the whole fault process. According to the invention, a visual observation means is provided for inversion of an accident in a power system; and a rapid, accurate, and high efficient informational way is provided for accident localization and a fault analysis; therefore, an action process of a relay protection device is hyalinized and the visibility is realized.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Delay calculation method based on game movement logic client and server synchronization
ActiveCN102769616AAvoid negative effectsAvoid tampering with game dataTransmissionGame playerLogical process
The invention provides a delay calculation method based on game movement logic client and server synchronization. The delay calculation method comprises the steps that: a game player sends a movement request on a client; the client calculates a time point K; a server is requested to carry out movement logic calculation at the time point K; the client and the server simultaneously carry out the movement logic calculation at the time point K; and the server sends a calculation result to the client; and the client obtains the calculation result sent by the server, and checks the calculation result of the client and the calculation result of the server, wherein an inertia motion value which is not controlled by the game player is given for a role controlled by the game player in a game. With the adoption of the delay calculation method provided by the invention, not only can the phenomenon of modifying game data by using a plug-in tool and the like be effectively avoided, but also the negative effects caused by the network delay in a client and server synchronization calculation movement logic process can be effectively avoided.
Owner:ZHUHAI KINGSOFT ONLINE GAME TECH CO LTD
System for managing logical process flow in an online environment
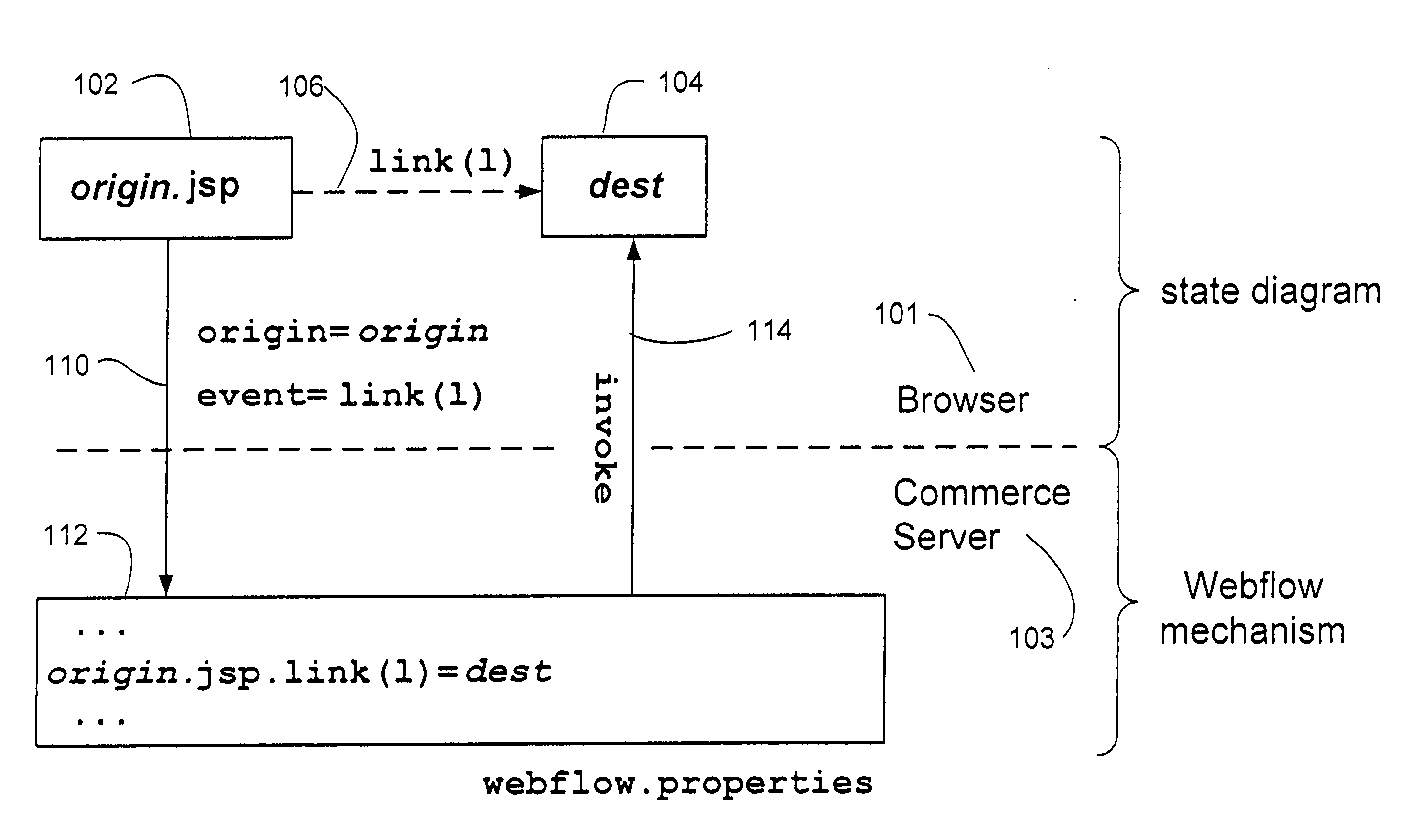
InactiveUS7051069B2Reduce usageProgramming languages/paradigmsProgram controlWeb siteError processing
The invention uses a state machine to control the flow throughout a Web site including the execution of business logic, error handling and dispatching based on both user and programming events. This state machine is used as input to a flow processor and therein guides the system. The flow processor controls a series of online functions including HTML links, HTML form submissions, form processing, business logic execution, and business logic exceptions into one simple-to-manage element. Any required change to the logic flow of the system can be made by modifying just the flow processor itself, without necessary changes to the referenced online functions.
Owner:ORACLE INT CORP
Storage scheme for built-in ECC operations
A device includes a memory array storing data and error correcting codes ECCs corresponding to the data, and a multi-level buffer structure between the memory array and an input / output data path. The memory array includes a plurality of data lines for page mode operations. The buffer structure includes a first buffer having storage cells connected to respective data lines in the plurality of data lines for a page of data, a second buffer coupled to the storage cells in the first buffer for storing at least one page of data, and a third buffer coupled to the second buffer and to the input / output data path. The device includes logic coupled to the multi-level buffer to perform a logical process over pages of data during movement between the memory array and the input / output path through the multi-level buffer for at least one of page read and page write operations.
Owner:MACRONIX INT CO LTD
System for improving overall battery life of a GSM communication device
InactiveUS7761122B2Minimal impactExtend battery lifeEnergy efficient ICTPower managementDefinite periodEngineering
Disclosed is a system for improving the overall battery life of a GSM device according to an optimization mechanism for suspending neighbor-cell scanning in a GSM wireless communication system, the system having a wireless device including: (a) a Central Processing Unit (CPU) executing software programs intended to comply with GSM protocol specifications; (b) an RF transmission unit and an RF reception unit functioning either independently or as a single unit; (c) a specialized Digital Signal Processor being able to process received signal at a corresponding receiving antenna and offering estimates of the received signal level and quality; (d) a logic process by which the mobile terminal powers off an RF module thereof for a definite period of time and wakes up at a pre-determined interval to listen to paging messages transmitted thereto; and (e) firmware / software performing neighbor cell monitoring in compliance with a protocol mandated by GSM standards.
Owner:SAMSUNG ELECTRONICS CO LTD
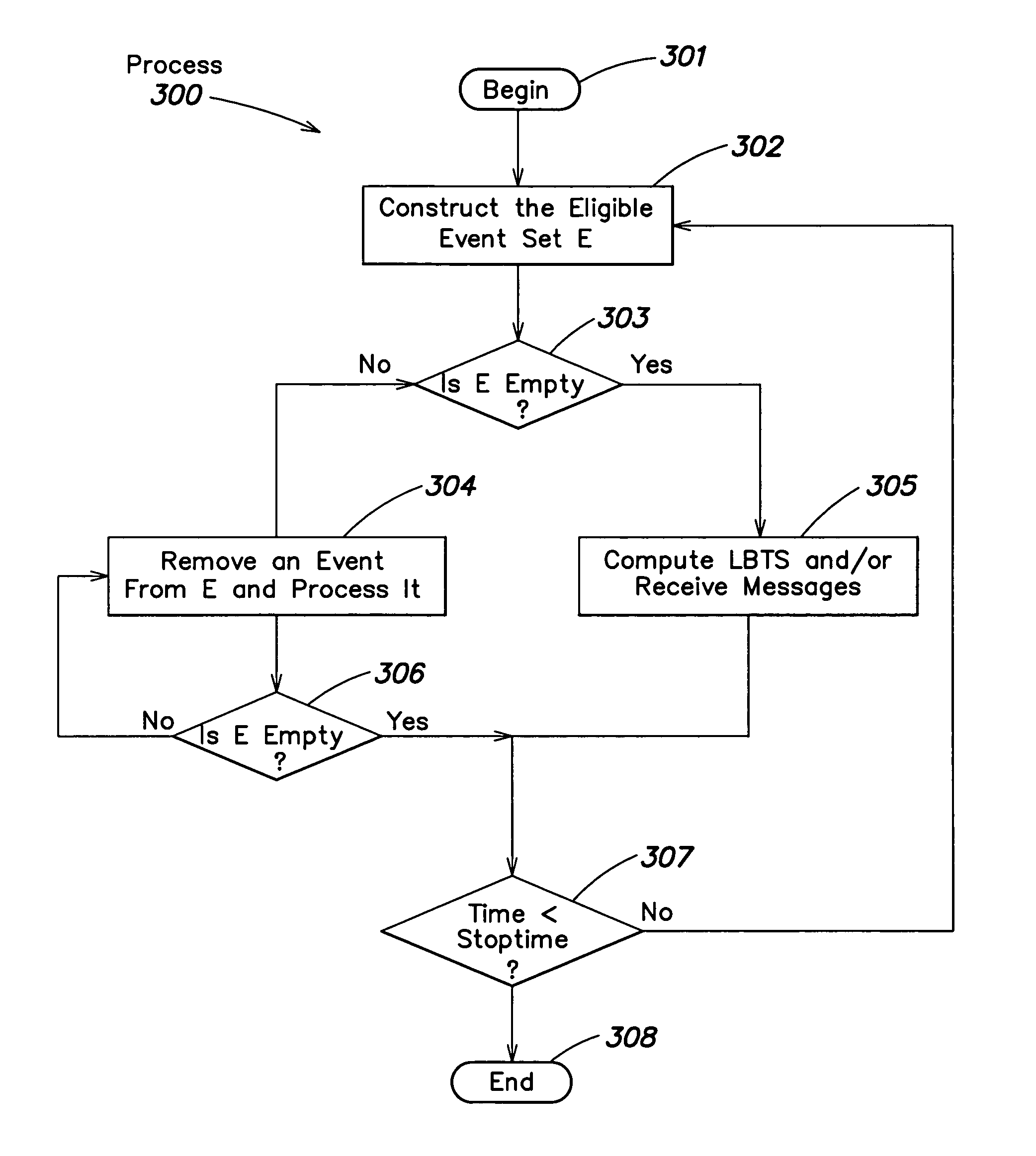
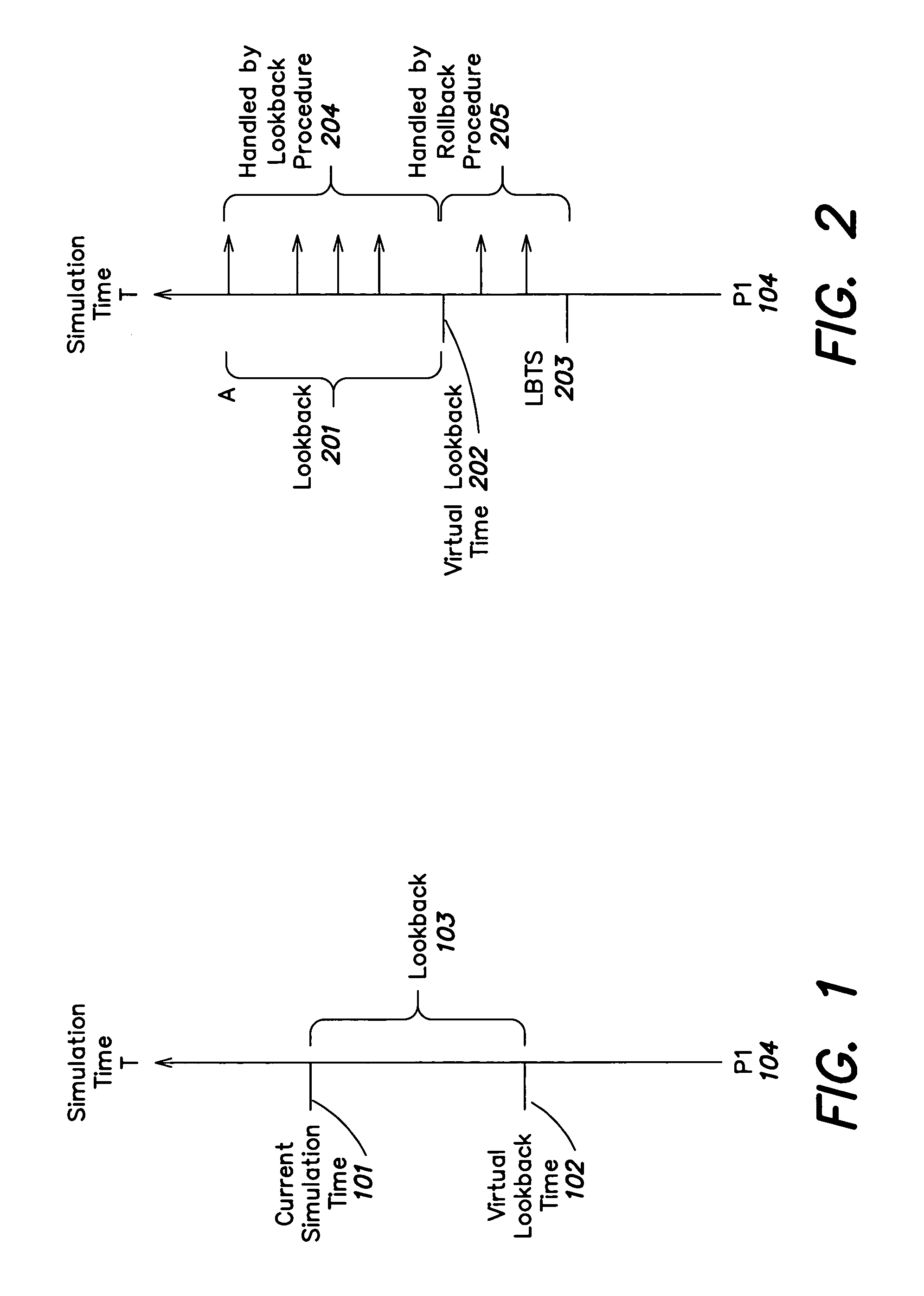
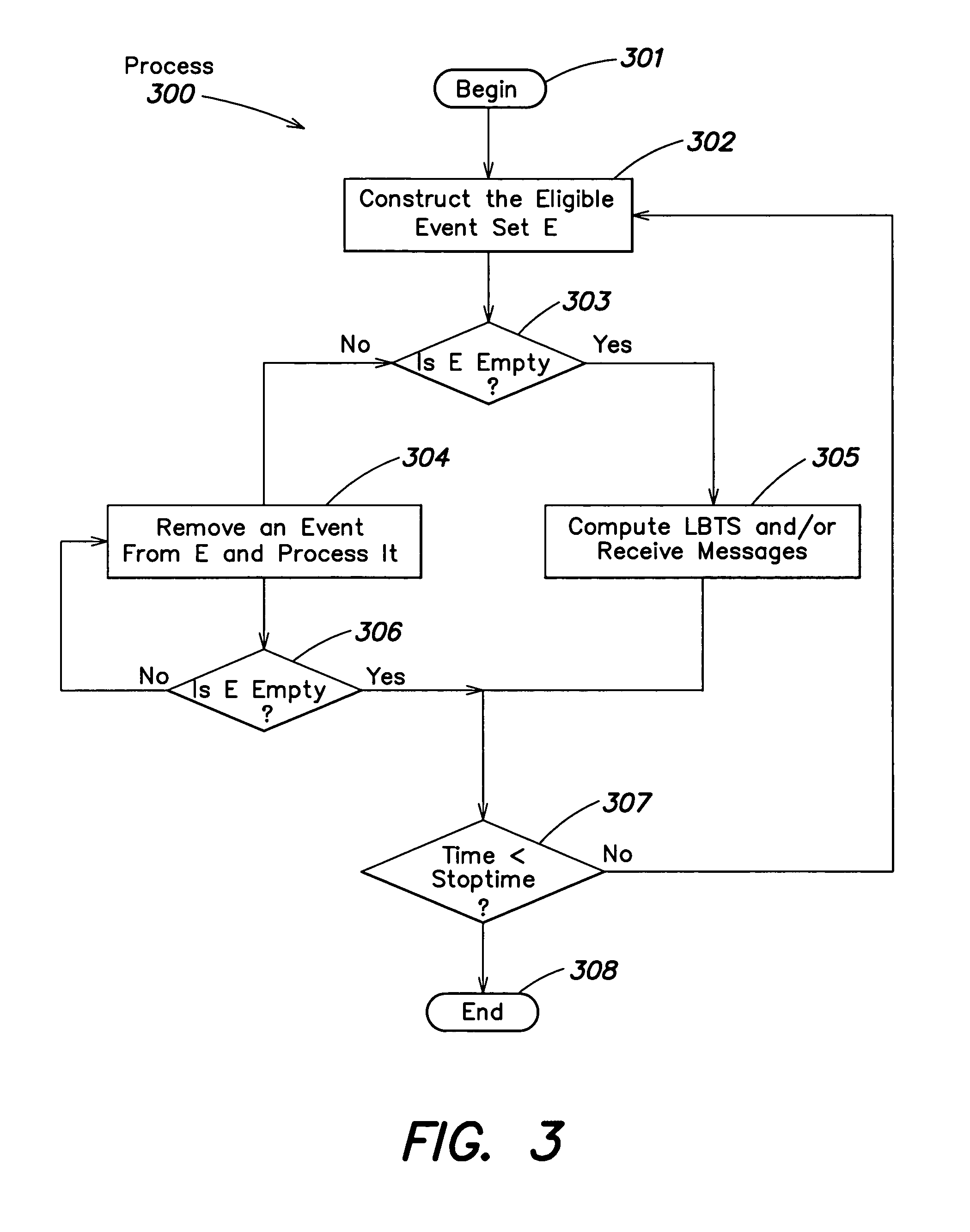
Discrete event simulation system and method
Lookback is defined as the ability of a logical process to change its past locally (without involving other logical processes). Logical processes with lookback are able to process out-of-timestamp order events, enabling new synchronization protocols for the parallel discrete event simulation. Two of such protocols, LB-GVT (LookBack-Global Virtual Time) and LB-EIT (LookBack-Earliest Input Time), are presented and their performances on the Closed Queuing Network (CQN) simulation are compared with each other. Lookback can be used to reduce the rollback frequency in optimistic simulations. The relation between lookahead and lookback is also discussed in detail. Finally, it is shown that lookback allows conservative simulations to circumvent the speedup limit imposed by the critical path.
Owner:RENESSELAER POLYTECHNIC INST
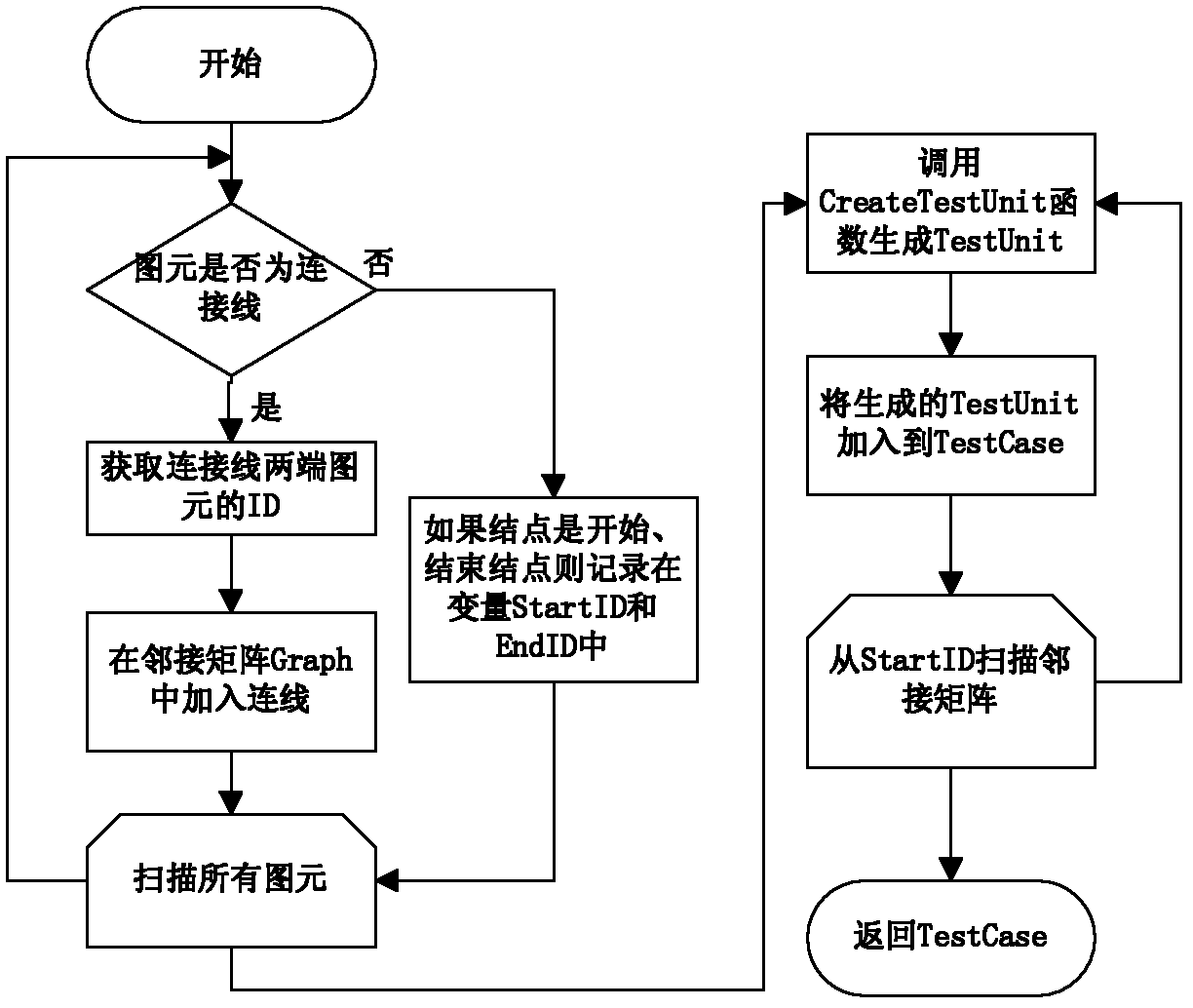
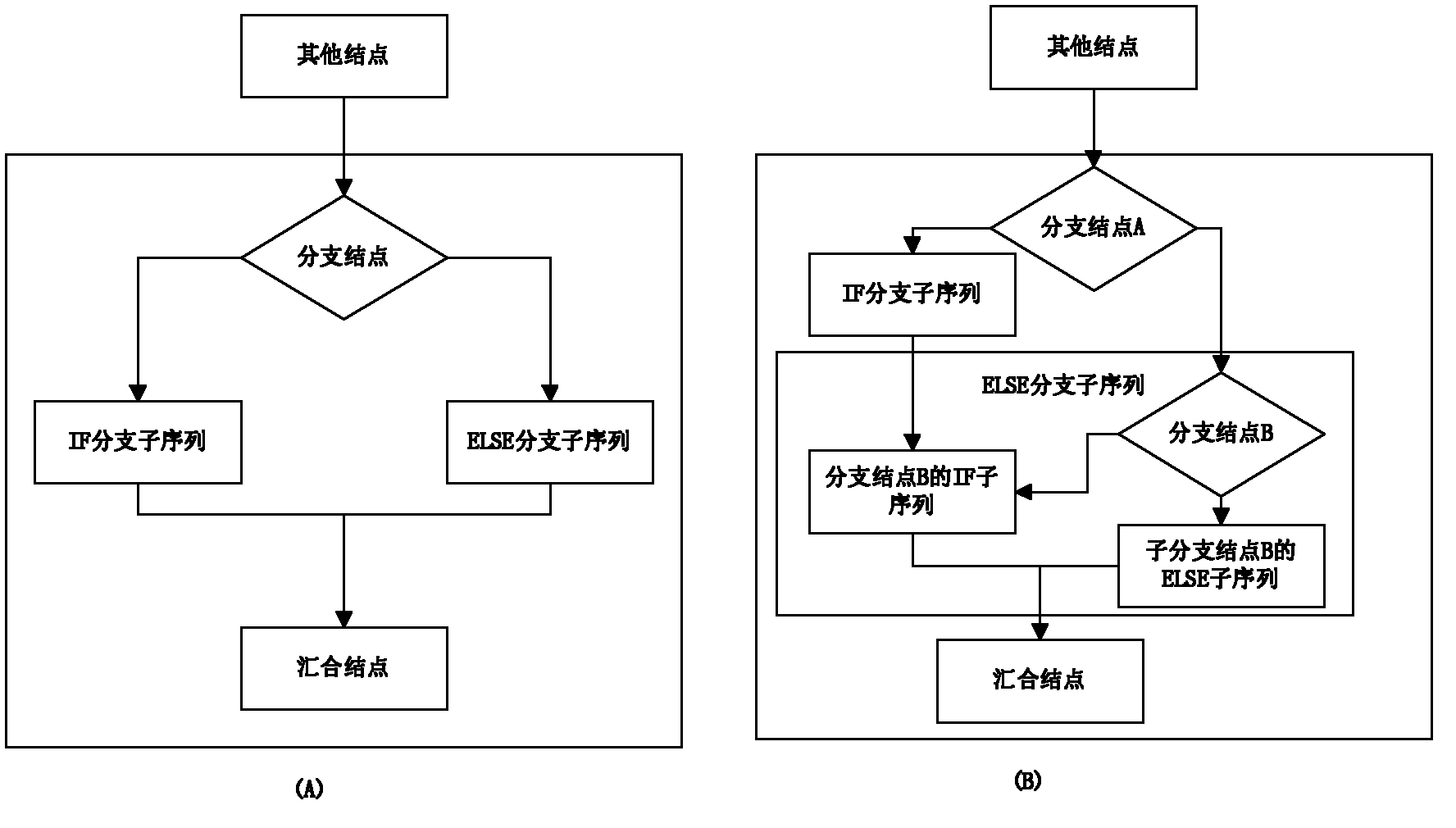
Method for generating test case by using flow chart
InactiveCN102662644AEasy to understandSimple designSpecific program execution arrangementsDirected graphTopological order
The invention discloses a method for generating a test case by using a flow chart. The method comprises the steps that : all graphic elements are read through in the flow chart after validity check is carried out for the flow chart to obtain graphic element IDs at both ends of connection lines; a directed graph adjacent matrix with start points and end points, start nodes and end nodes of all the connection lines is established; test units are generated by starting from a StartID in a topological order for every graphic element except connection line graphic elements and are added to the test case in order; subsequent node IDs are checked by utilizing the adjacent matrix till an end node EndID is checked; the test units are mapped to test steps; after the test steps are generated, the corresponding test step is carried out from the start nod in the test case by mapping each time when each test unit is obtained, thereby corresponding operation is run till the end nod is met. The method is characterized in that a program logic process and a program data flow direction are manifested in the form of a flowchart in the executing process of the text case; the method is easy for understanding and design.
Owner:ZHEJIANG UNIV
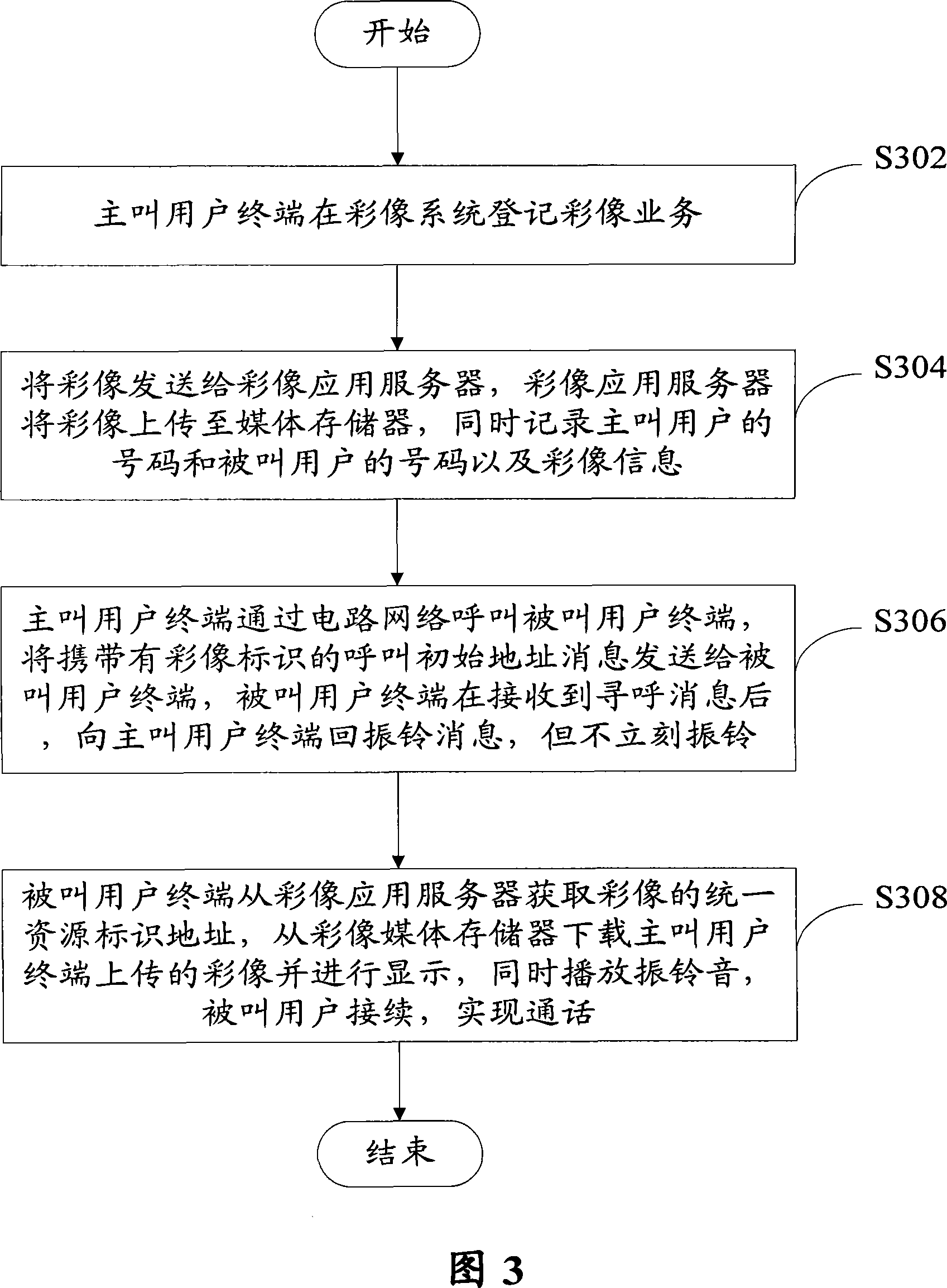
Multi-medium color-image system and method for transmitting multi-medium color image during process of talk
InactiveCN101076151AEasy to operateImplement identity authenticationSpecial service for subscribersClosed circuit television systemsColor imageWeb site
The system comprises: a color image application server used for making service logical process and user's operation process; a color image memory used for saving the color images provided by user and providing download resource; a Web server used for providing Web site and system management site; and an integrated interface message processor used for providing interaction with the peripheral interfaces; wherein, said devices are connected via IP network.
Owner:ZTE CORP
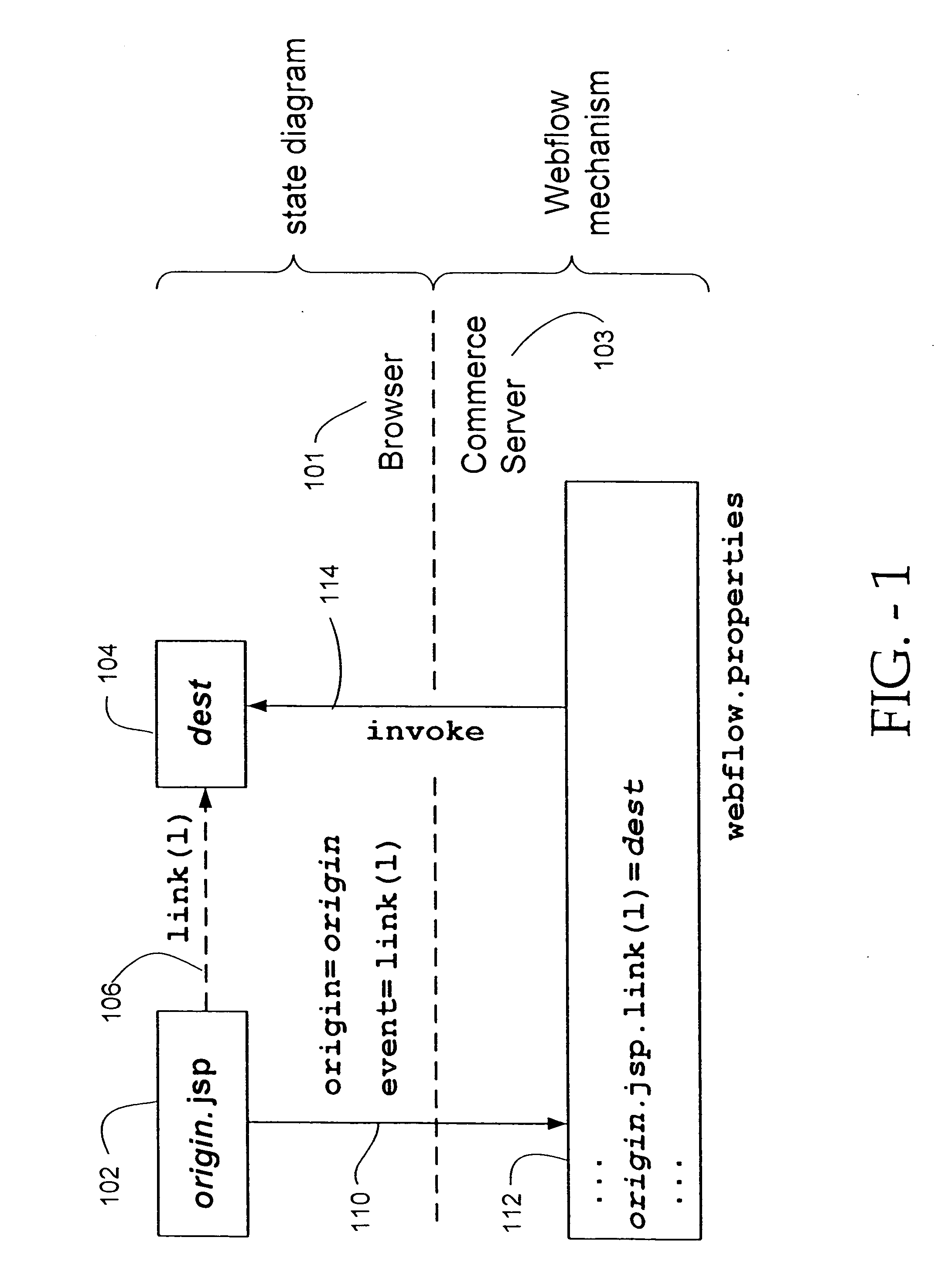
System for managing logical process flow in an online environment
InactiveUS20060143267A1Programming languages/paradigmsMultiple digital computer combinationsWeb siteError processing
The invention uses a state machine to control the flow throughout a Web site including the execution of business logic, error handling and dispatching based on both user and programming events. This state machine is used as input to a flow processor and therein guides the system. The flow processor controls a series of online functions including HTML links, HTML form submissions, form processing, business logic execution, and business logic exceptions into one simple-to-manage element. Any required change to the logic flow of the system can be made by modifying just the flow processor itself, without necessary changes to the referenced online functions.
Owner:ORACLE INT CORP
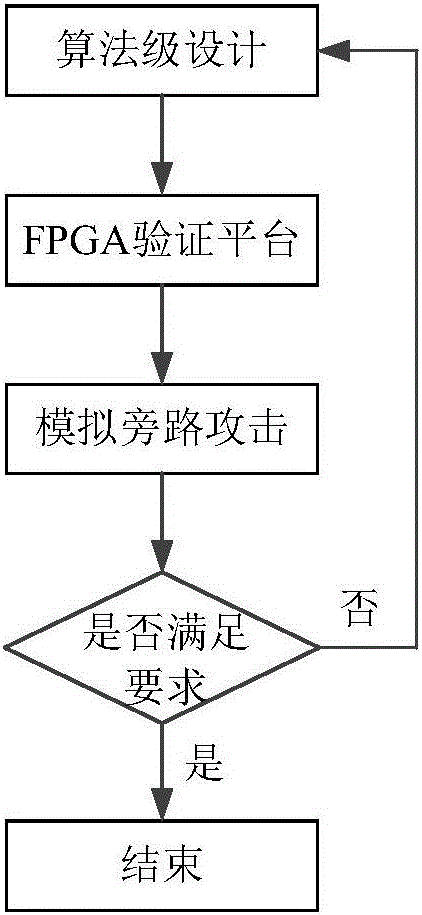
On-chip power supply network verification method for side channel attack
ActiveCN106817215AIntuitive and usable attack defense capability evaluation resultsLow costEncryption apparatus with shift registers/memoriesPlaintextValidation methods
The invention discloses an on-chip power supply network verification method for a side channel attack. The method comprises: logical synthesis and physical design processing is carried out on a register transmission level netlist file of a chip to obtain a transistor level netlist file; according to the obtained transistor level netlist file, a circuit model including a power supply network and a load is established; according to a generated plaintext-ciphertext data pair and a corresponding secret key, a logic process for encryption operation execution on the chip is simulated to obtain a current waveform file of the load; on the basis of the circuit model and the current waveform file of the load, a physical process for encryption operation execution on the chip is simulated to obtain a power consumption curve of the chip; according to the obtained power consumption curve, a side channel attack is carried out on the chip to obtain a guess secret key of the attack; and on the basis of the obtained guess secret key, a side channel attack result is analyzed and an anti-side channel attack capability of the power supply network is verified. The method has advantages of low cost, high accuracy, and reduced design verification period.
Owner:TSINGHUA UNIV
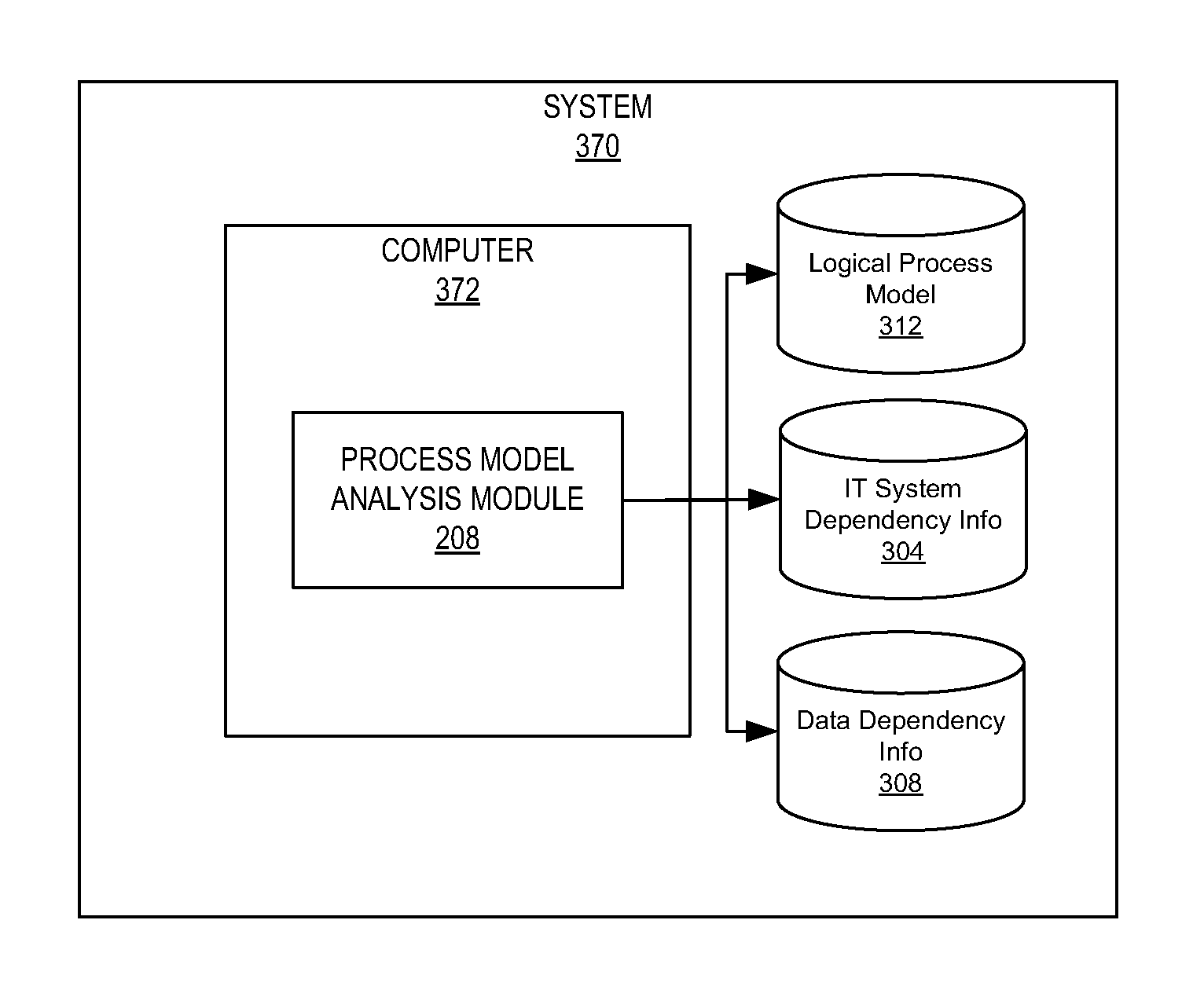
Accounting for data dependencies in process models, analysis, and management
A method and system comprising a process model analysis module to perform analysis of a process supported by a process system. The analysis is performed based on process information which includes a logical process model defining a series of activities. The process model information further includes IT system dependency information which includes datastore dependency information indicative of datastores which are accessed in execution of respective activities. The process model information also includes data dependency information indicative of dependency of process activities on data in the one or more datastores.
Owner:HCL AMERICA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com