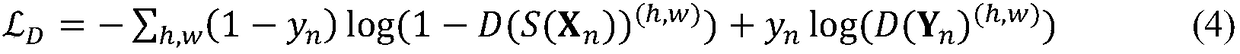Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
114 results about "Classful network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
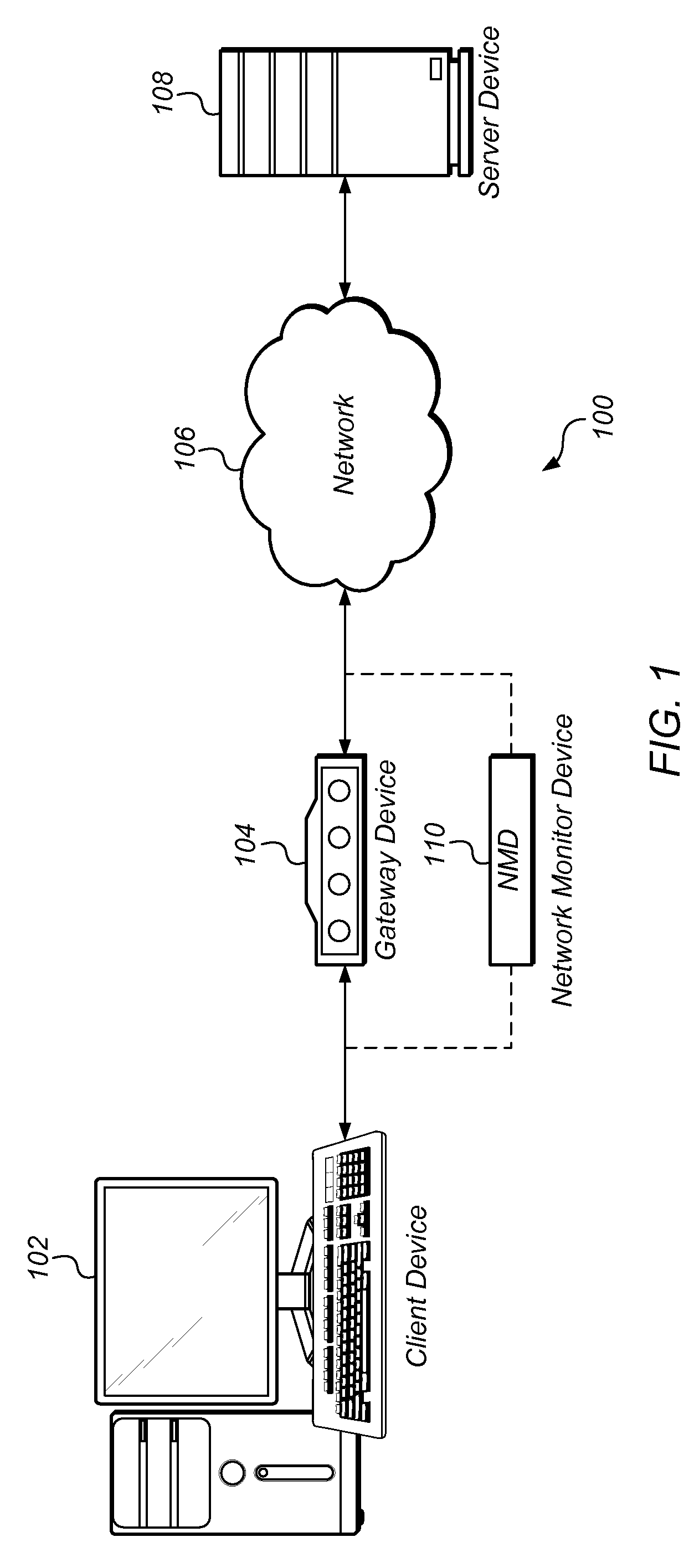
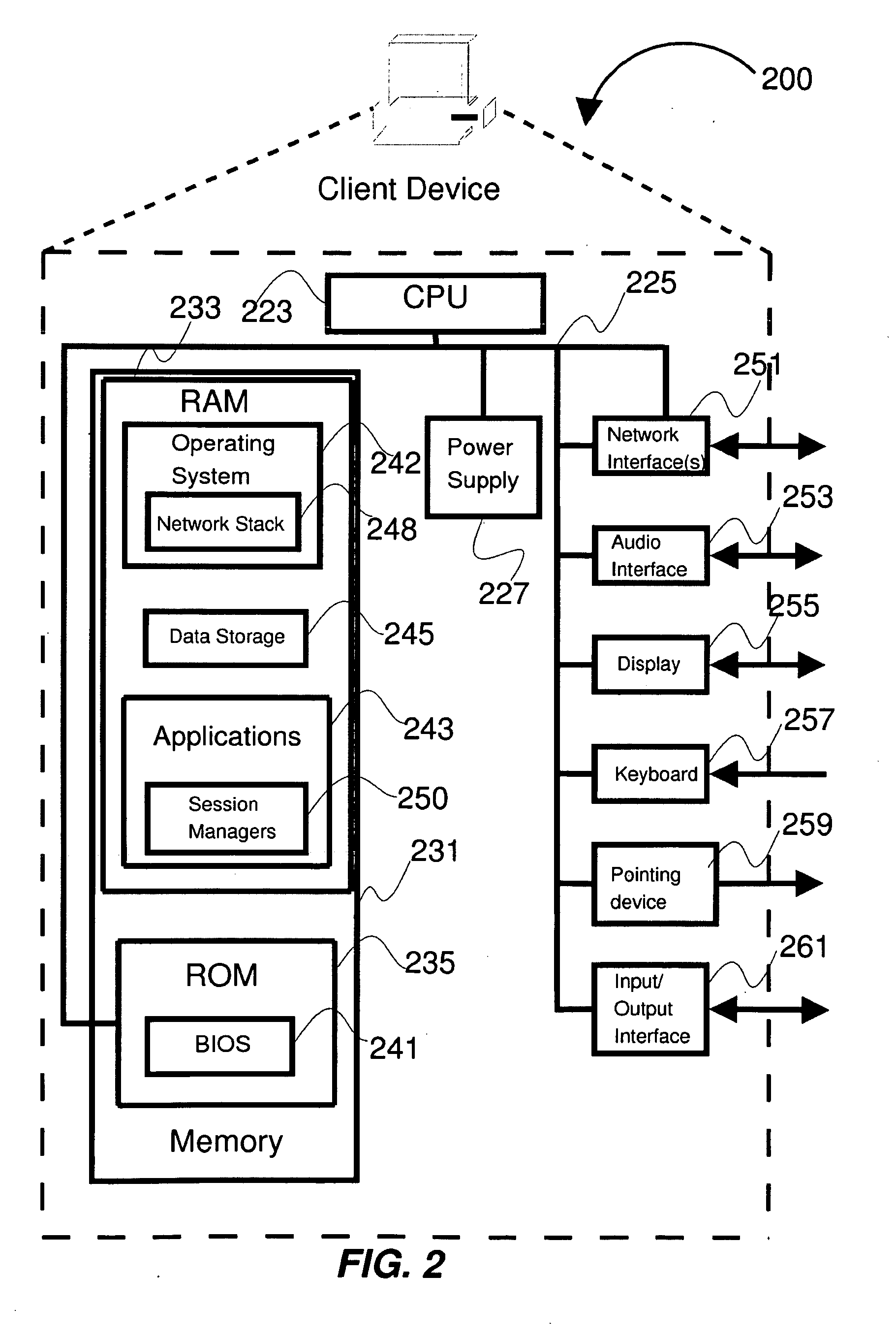
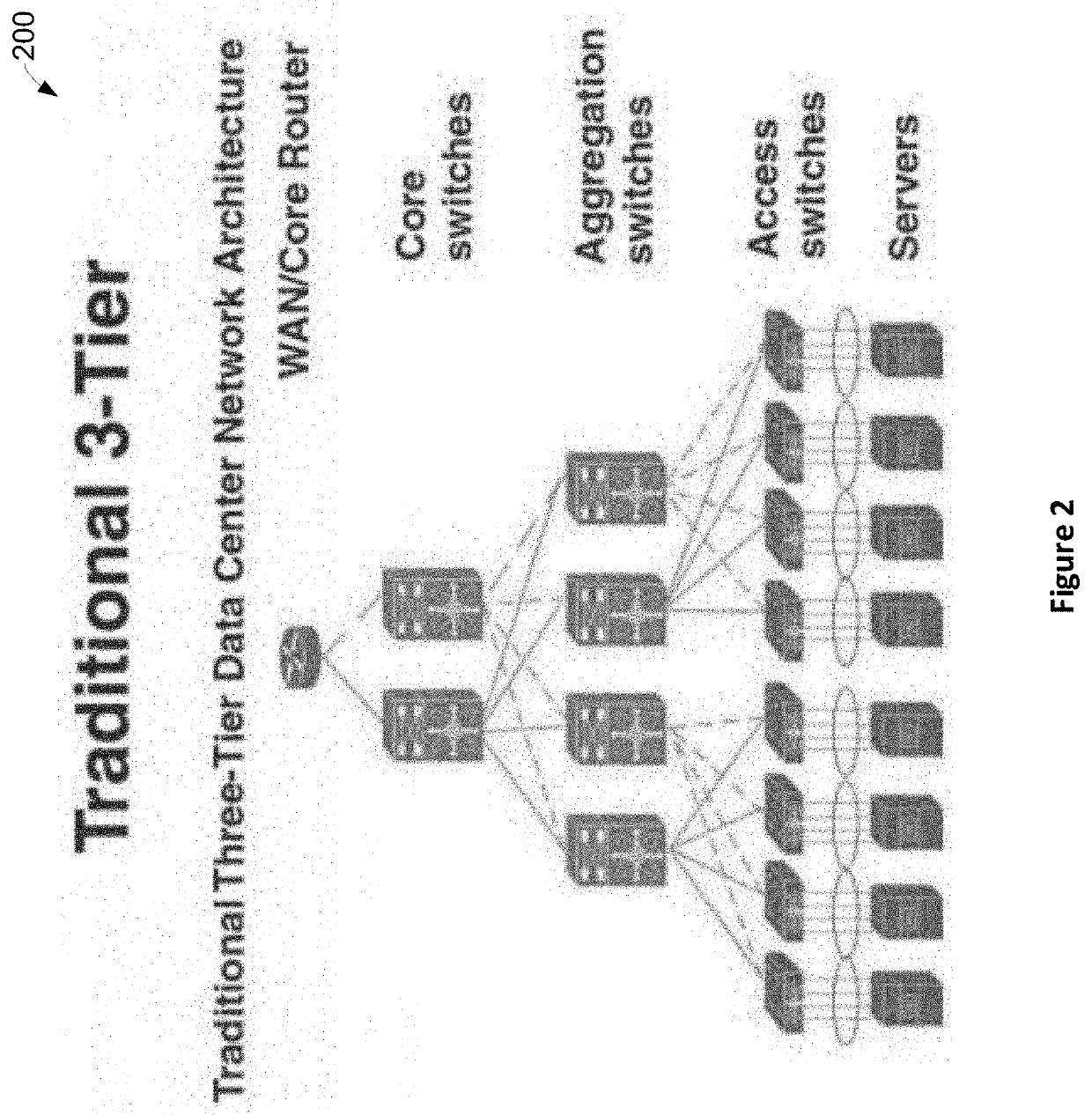
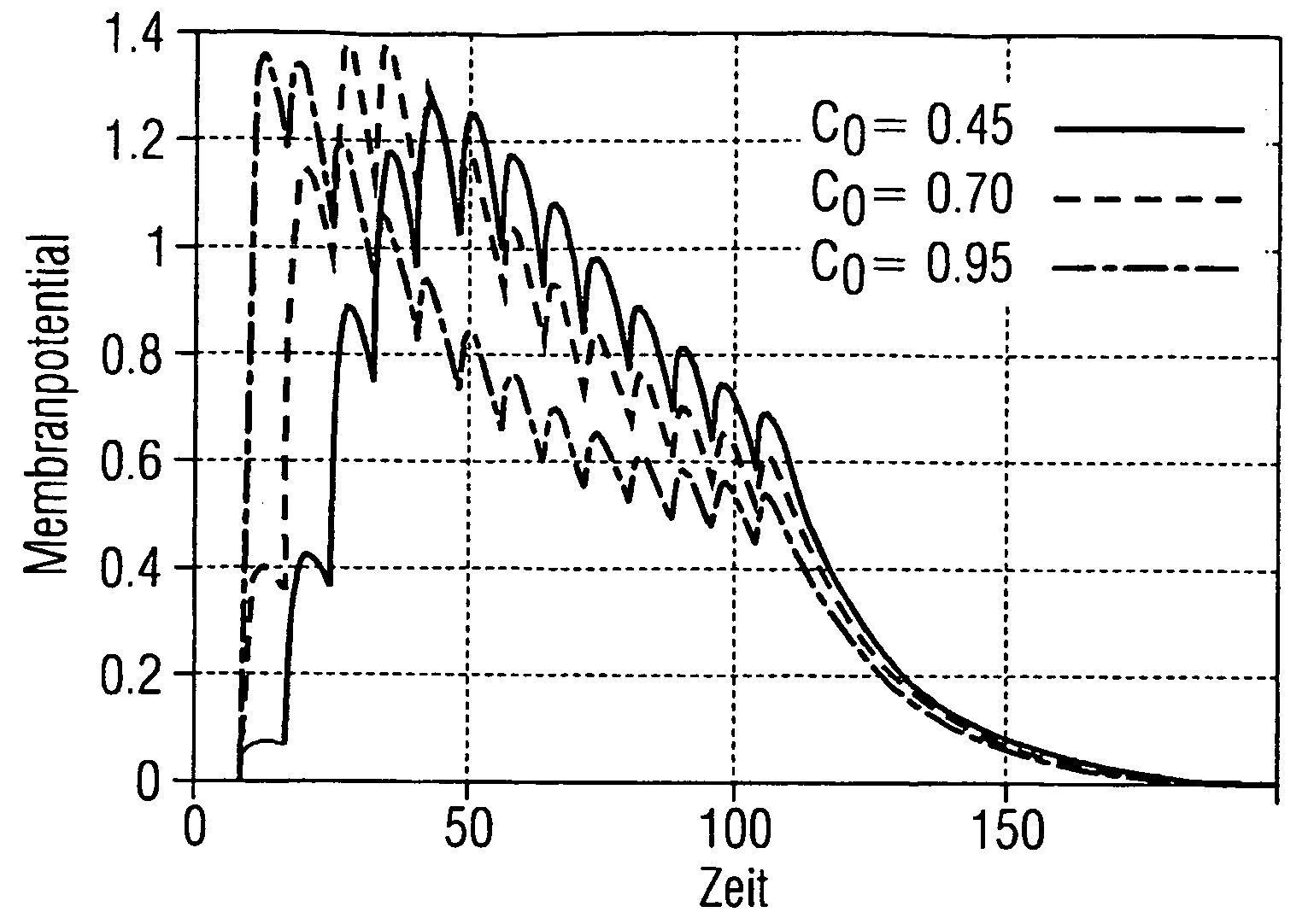
A classful network is a network addressing architecture used in the Internet from 1981 until the introduction of Classless Inter-Domain Routing in 1993. The method divides the IP address space for Internet Protocol version 4 (IPv4) into five address classes based on the leading four address bits. Classes A, B, and C provide unicast addresses for networks of three different network sizes. Class D is for multicast networking and the class E address range is reserved for future or experimental purposes.
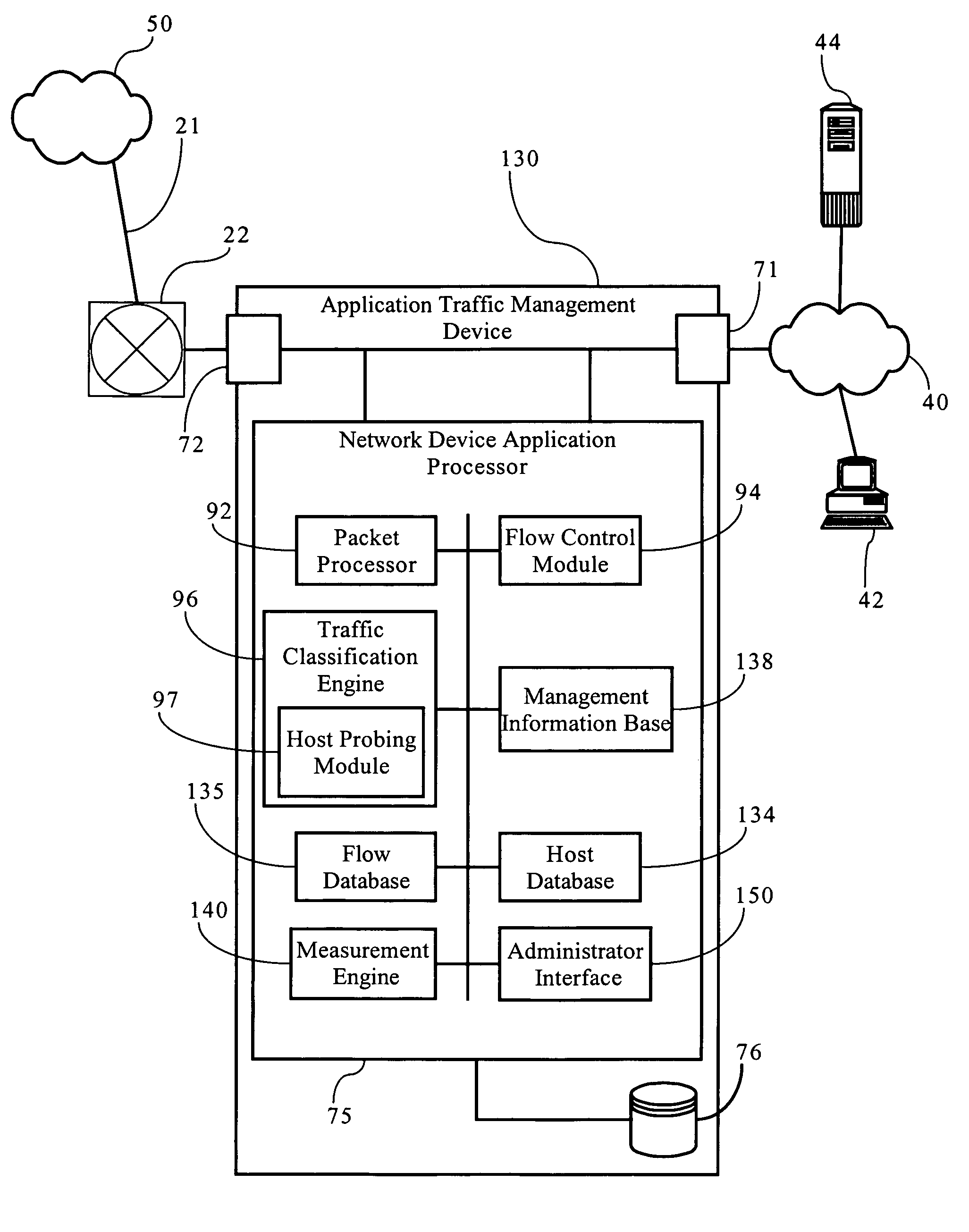
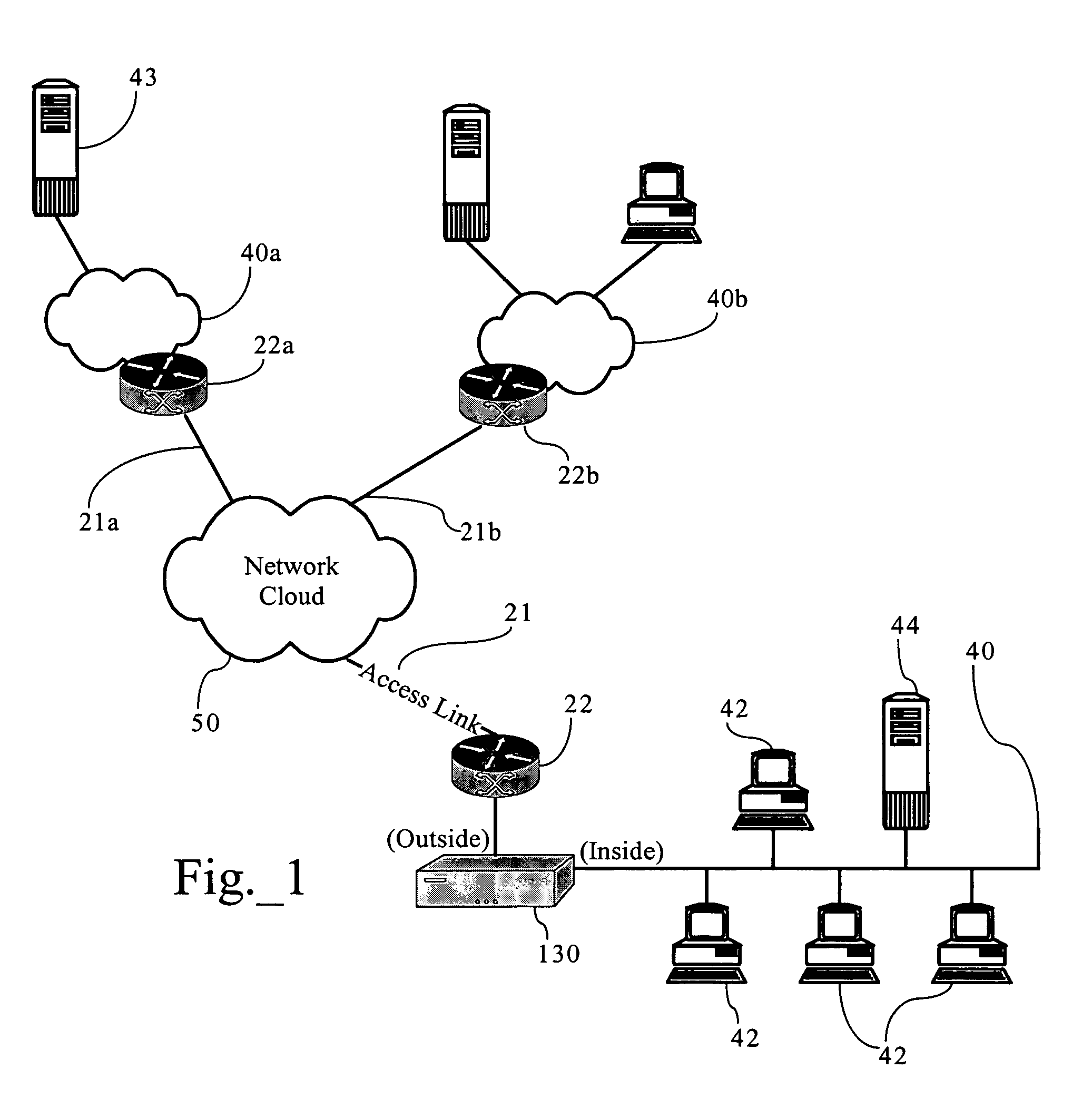
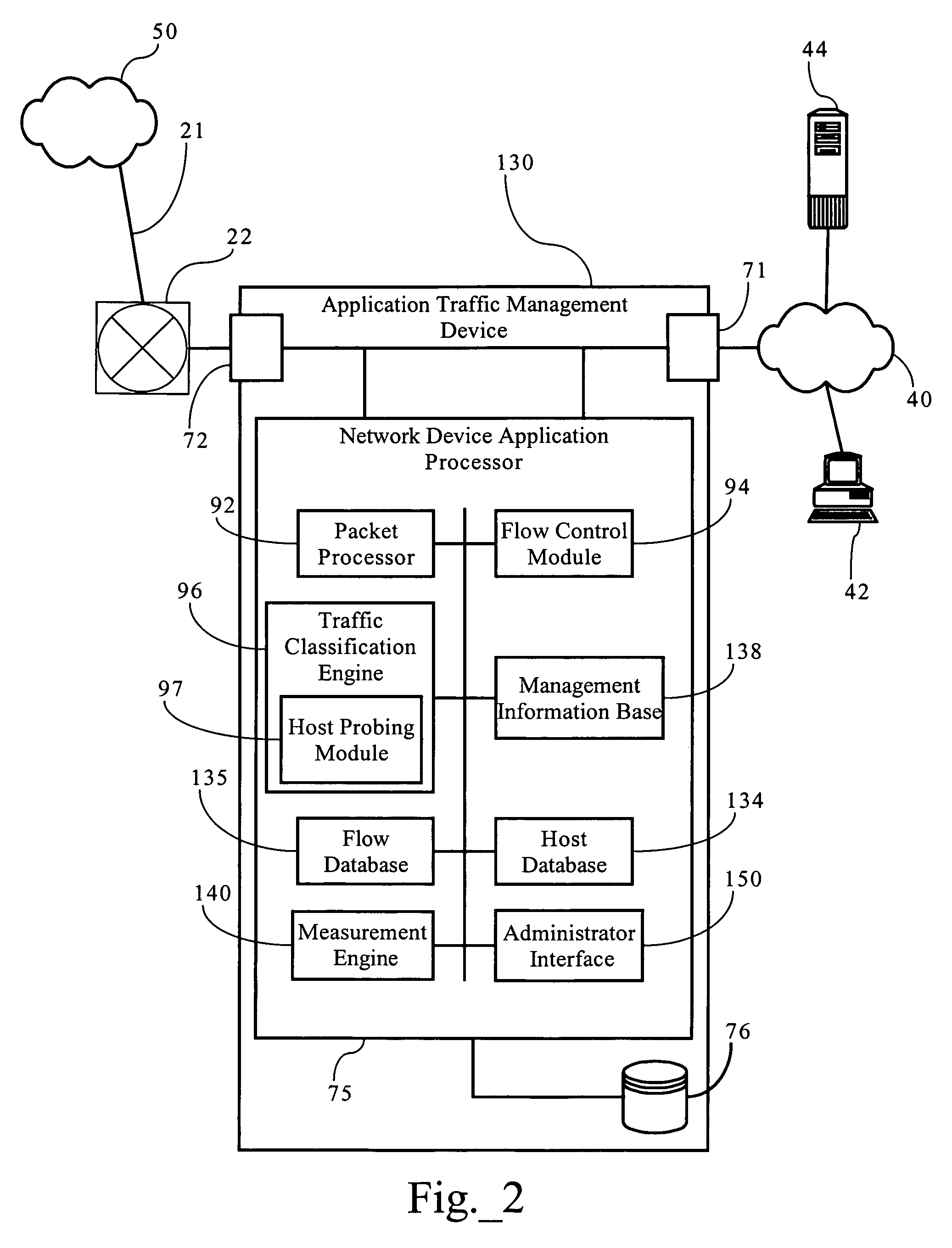
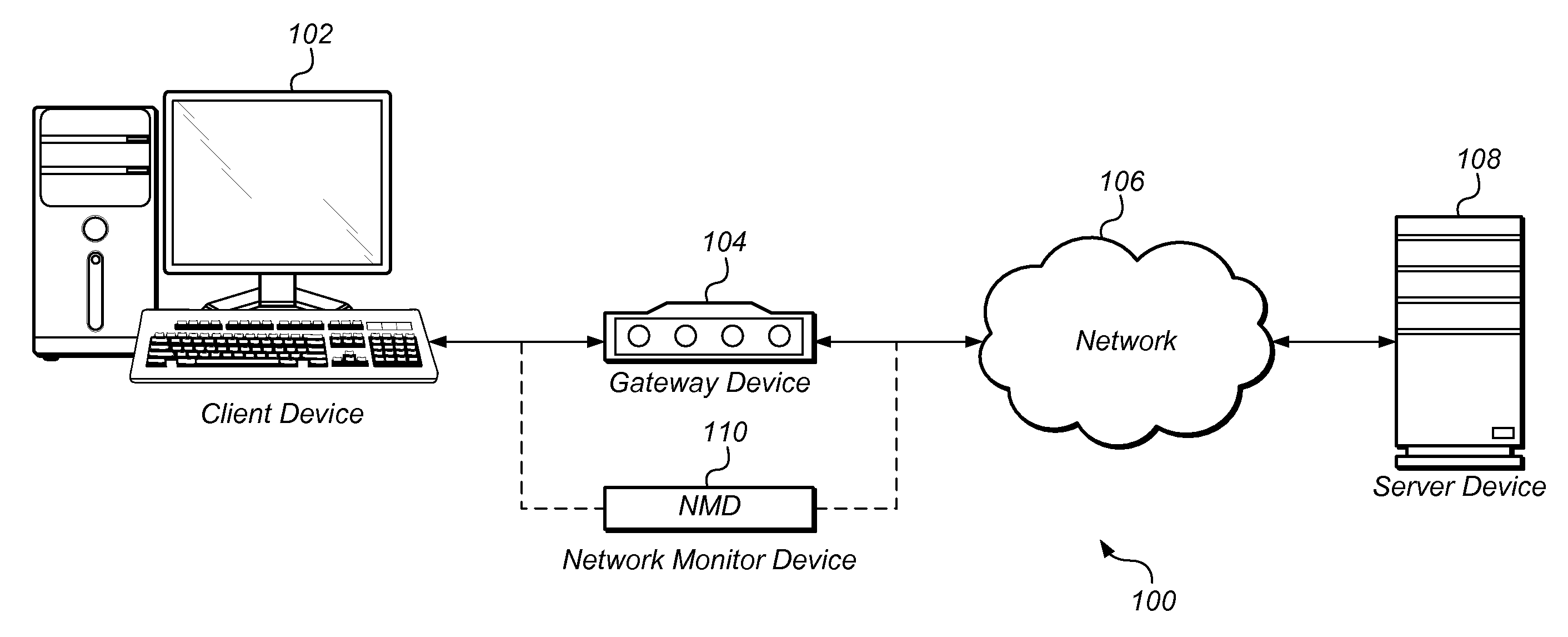
Probing hosts against network application profiles to facilitate classification of network traffic
Methods, apparatuses and systems directed to a network traffic classification mechanism that probes hosts against one or more network application profiles to facilitate identification of network applications corresponding to data flows traversing a network.
Owner:CA TECH INC
Adaptive Network Traffic Classification Using Historical Context
Adaptive network traffic classification using historical context. Network traffic may be monitored and classified by considering several attributes using packet filters, regular expressions, context-free grammars, rule sets, and / or protocol dissectors, among other means and by applying a variety of techniques such as signature matching and statistical analysis. Unlike static systems, the classification decisions may be reexamined from time to time or after subsequent processing determines that the traffic does not conform to the protocol specification corresponding to the classification decision. Historical context may be used to adjust the classification strategy for similar or related traffic.
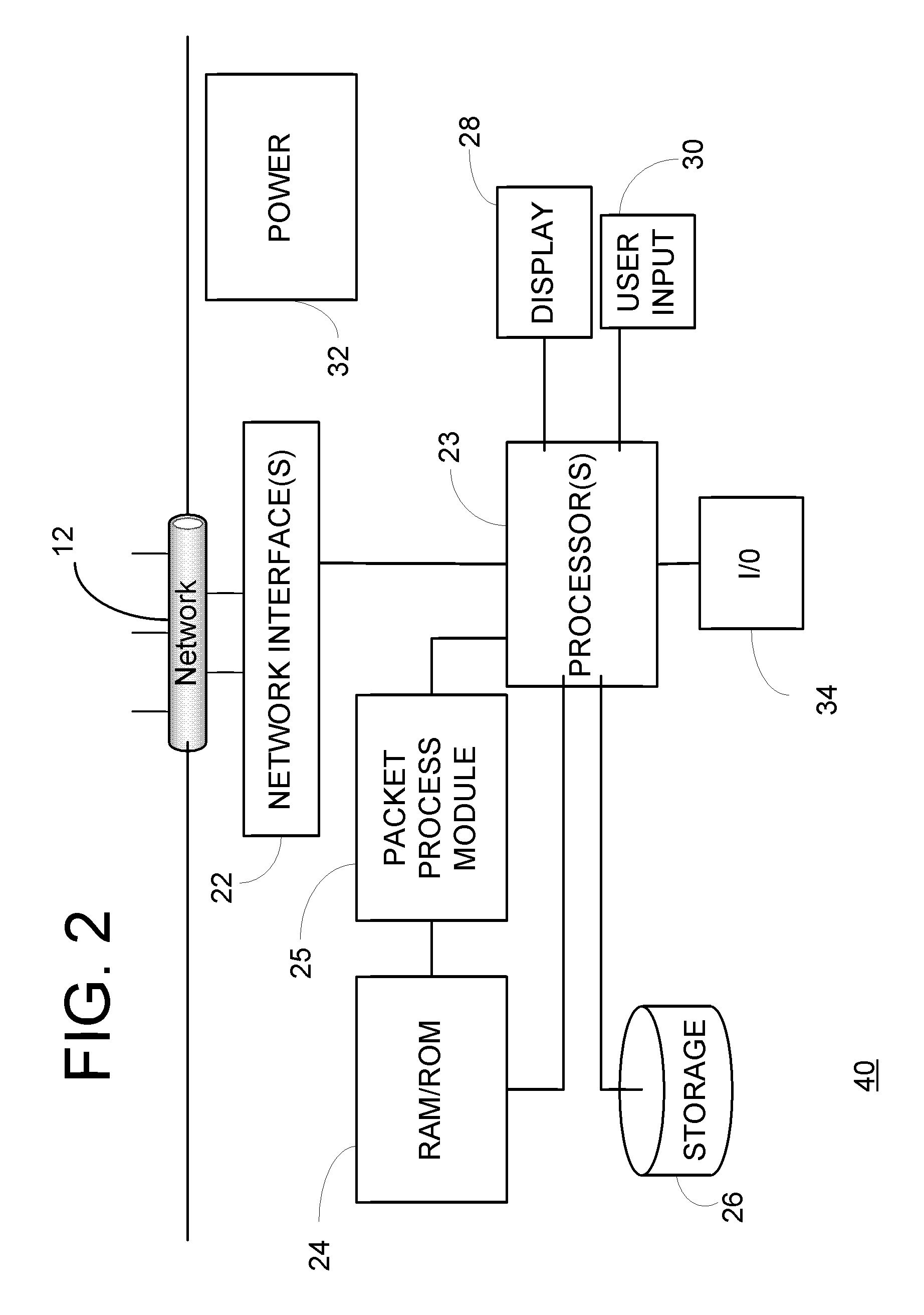
Owner:EXTRAHOP NETWORKS
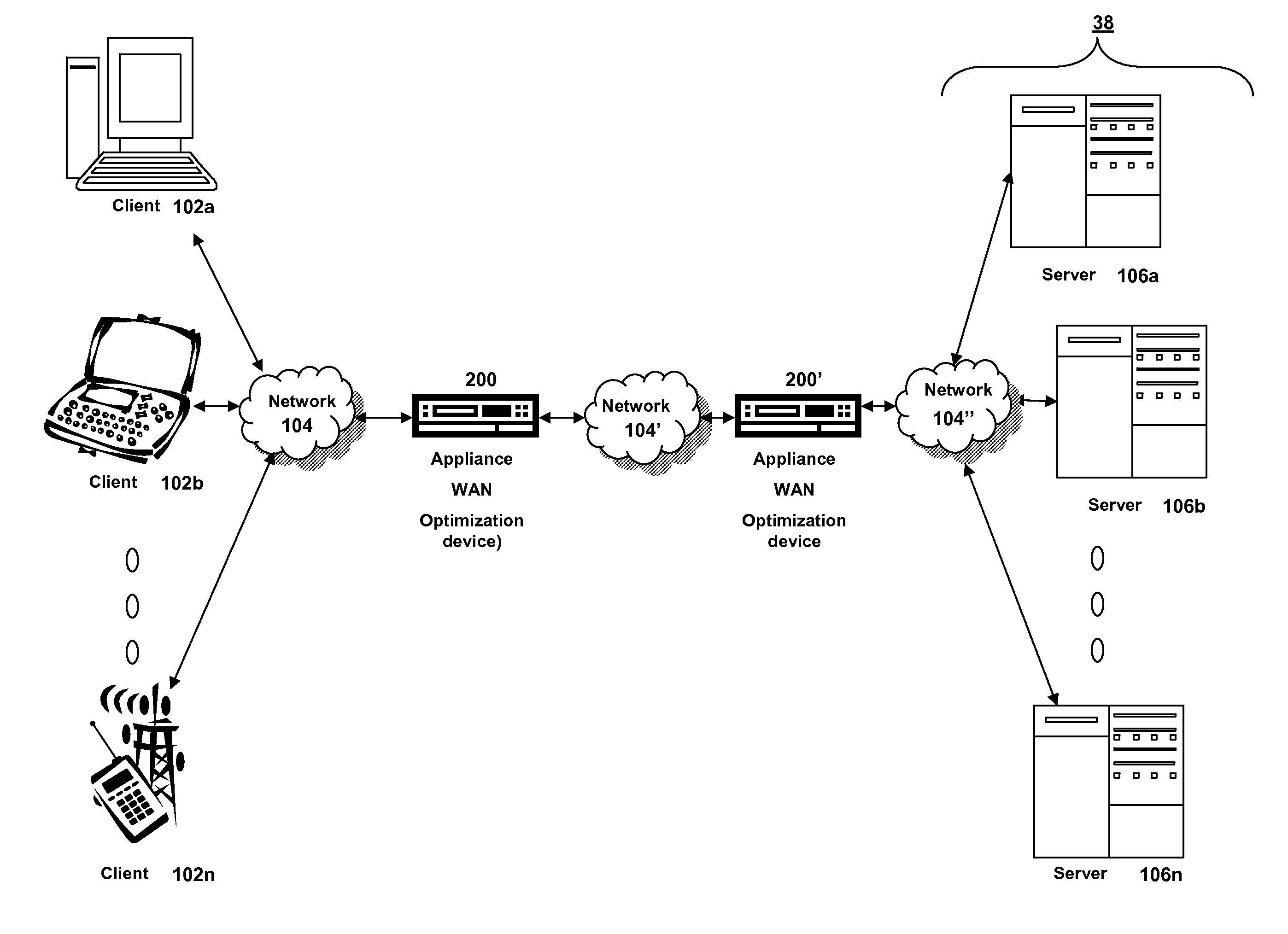
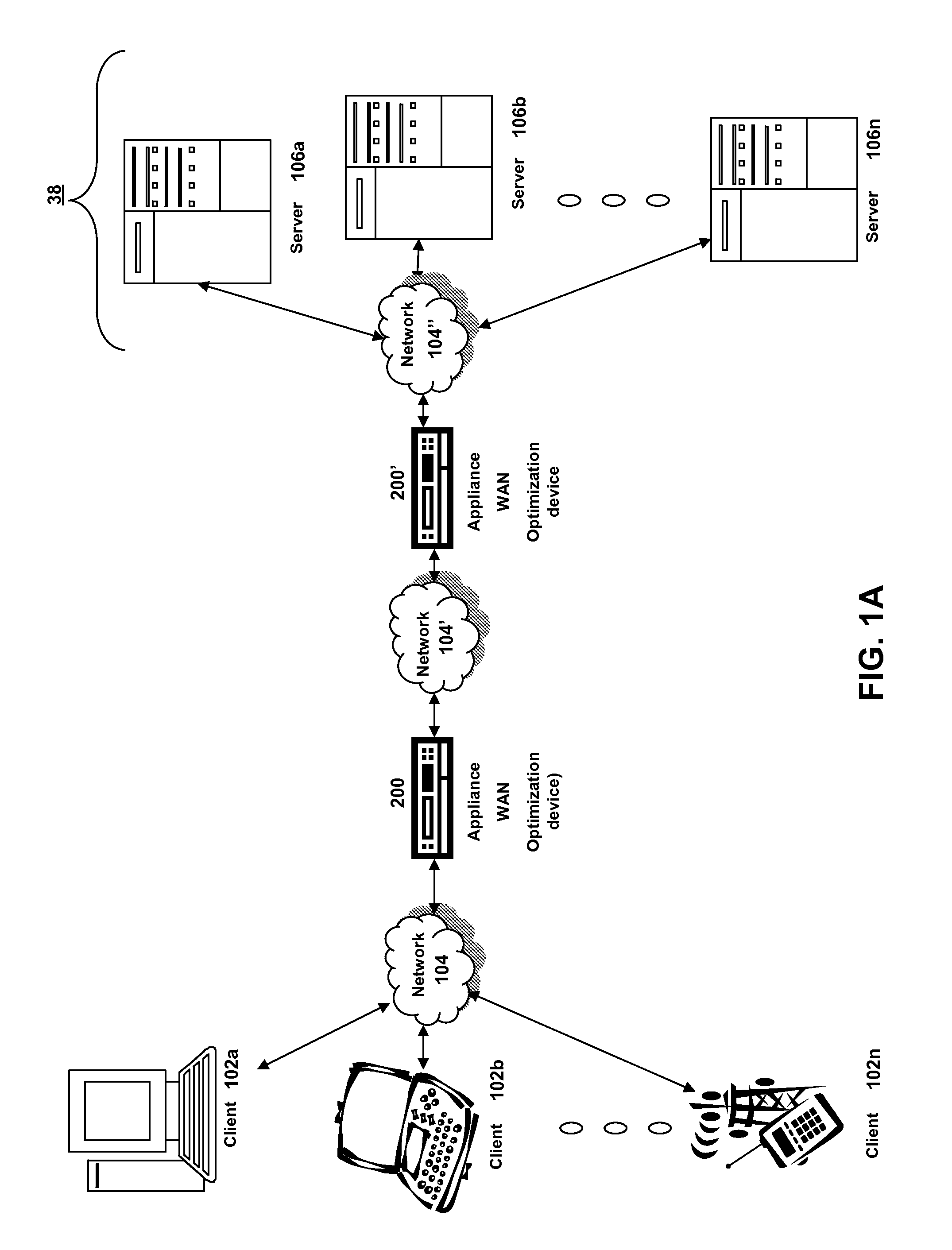
Systems and methods for quality of service of ica published applications
ActiveUS20120042060A1Improve network performanceNetwork performance can be enhanced and optimizedDigital computer detailsTransmissionQuality of serviceTraffic capacity
The present invention is directed towards systems and methods for providing discovery of applications for classification of a network packet for performing QoS and acceleration techniques. Remote display protocol traffic associated with a new application not previously included in a list of predetermined applications may be parsed for application information, and the new application may be added to the application list. The remote display protocol traffic may then be classified according to the new application, and network performance may be enhanced and optimized by providing QoS and acceleration engines with packet- or data-specific information corresponding to the newly identified application.
Owner:CITRIX SYST INC
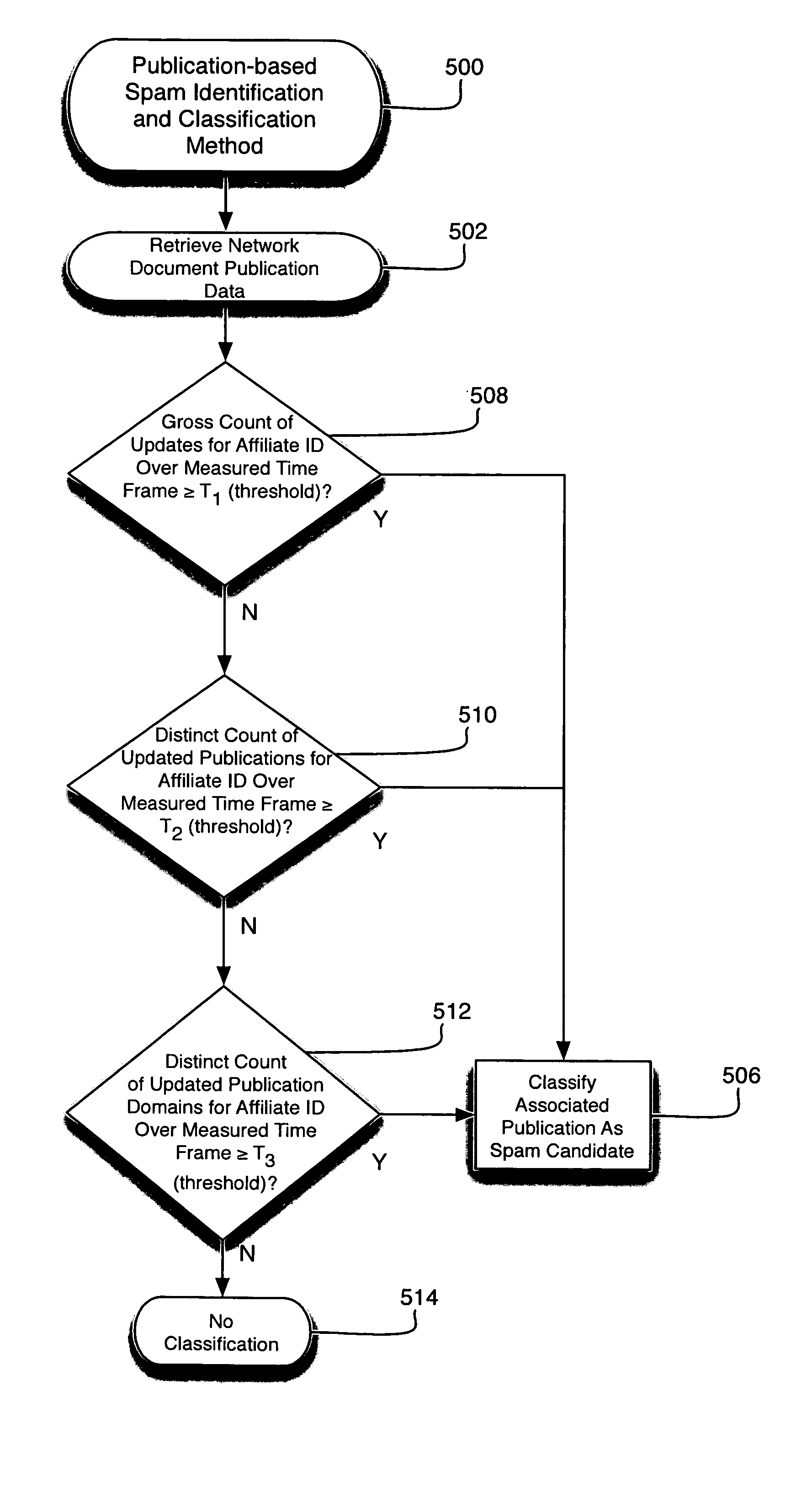
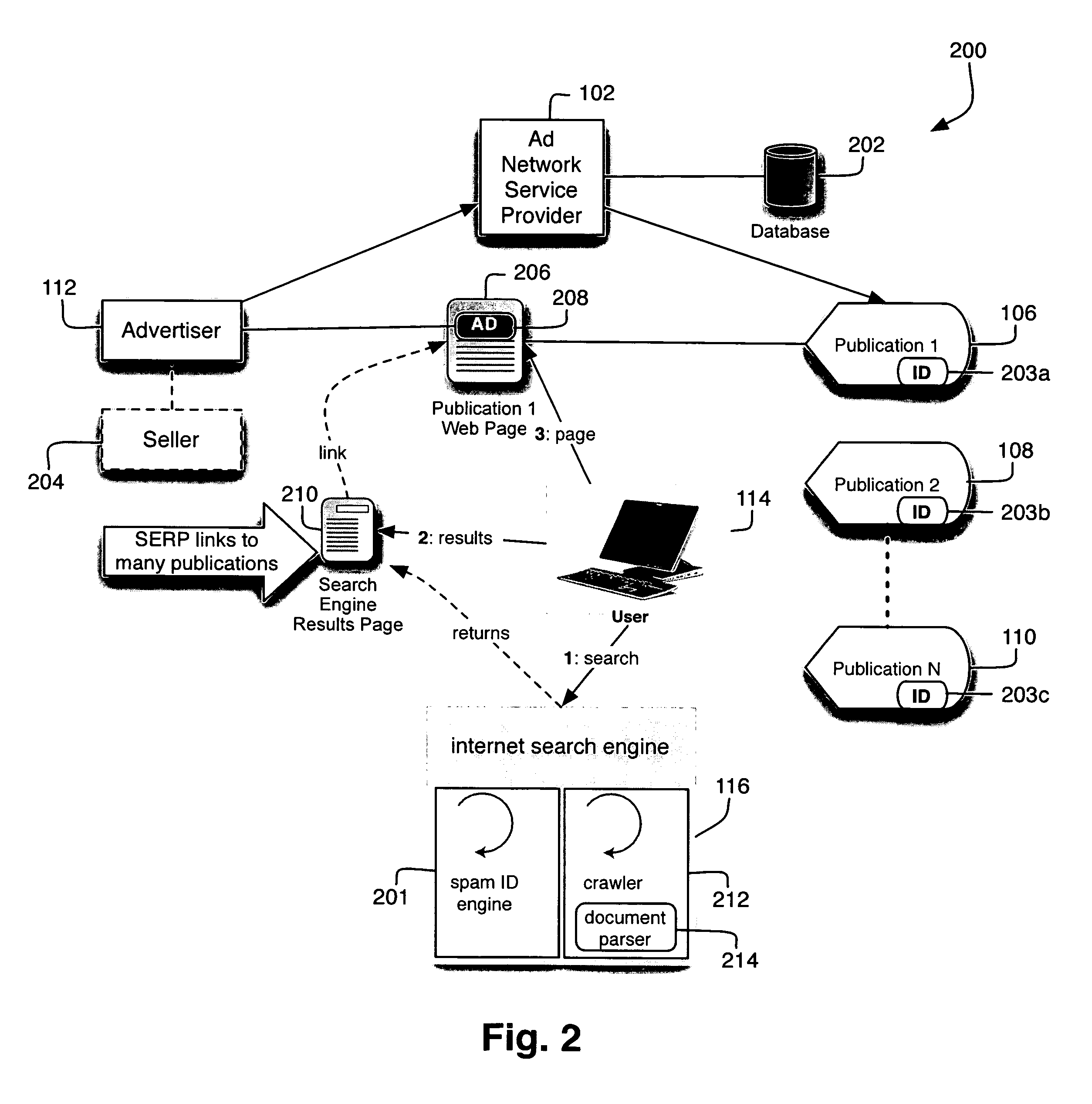
Method and apparatus for identifying and classifying network documents as spam
InactiveUS20070078939A1Web data indexingMultiple digital computer combinationsSpammingPaper document
Disclosed are methods and apparatus, including computer program products, implementing and using techniques for methods and apparatus, including computer program products, implementing and using techniques for identifying and classifying a network document as a spam candidate. In one aspect of the present invention, a network document is retrieved. Affiliate identification information is identified in the network document. One or more publications are associated with the identified affiliate identification information. Publication data for the network document is determined according to the identified affiliate identification information and the identified one or more publications. When it is determined that the publication data satisfies a condition indicative of spam, the network document is classified as a spam candidate.
Owner:TECHNORATI
Method and apparatus for adaptively classifying network traffic
ActiveUS7203963B1Minimal compute resourceMemory loss protectionError detection/correctionTraffic capacityNetwork addressing
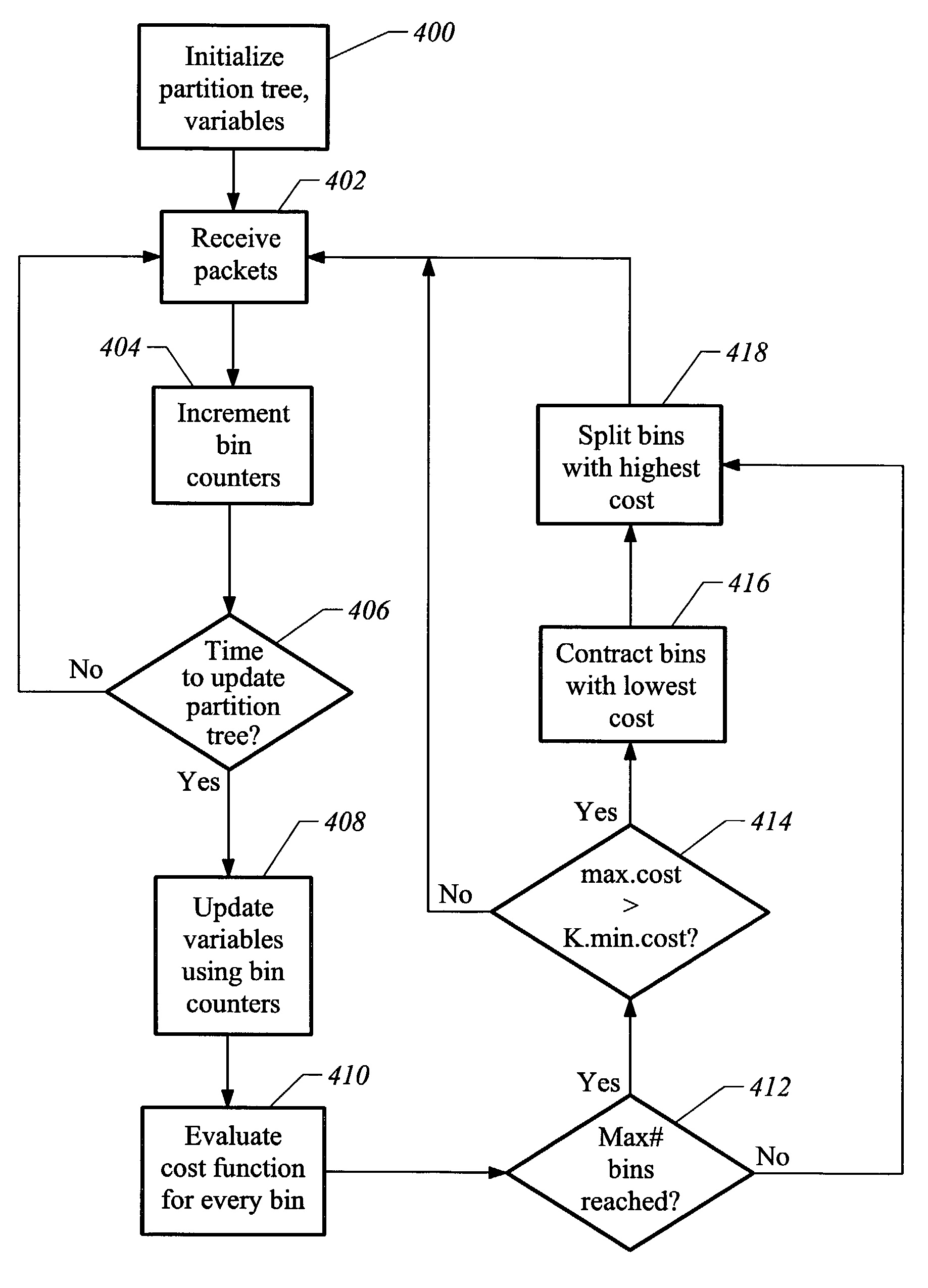
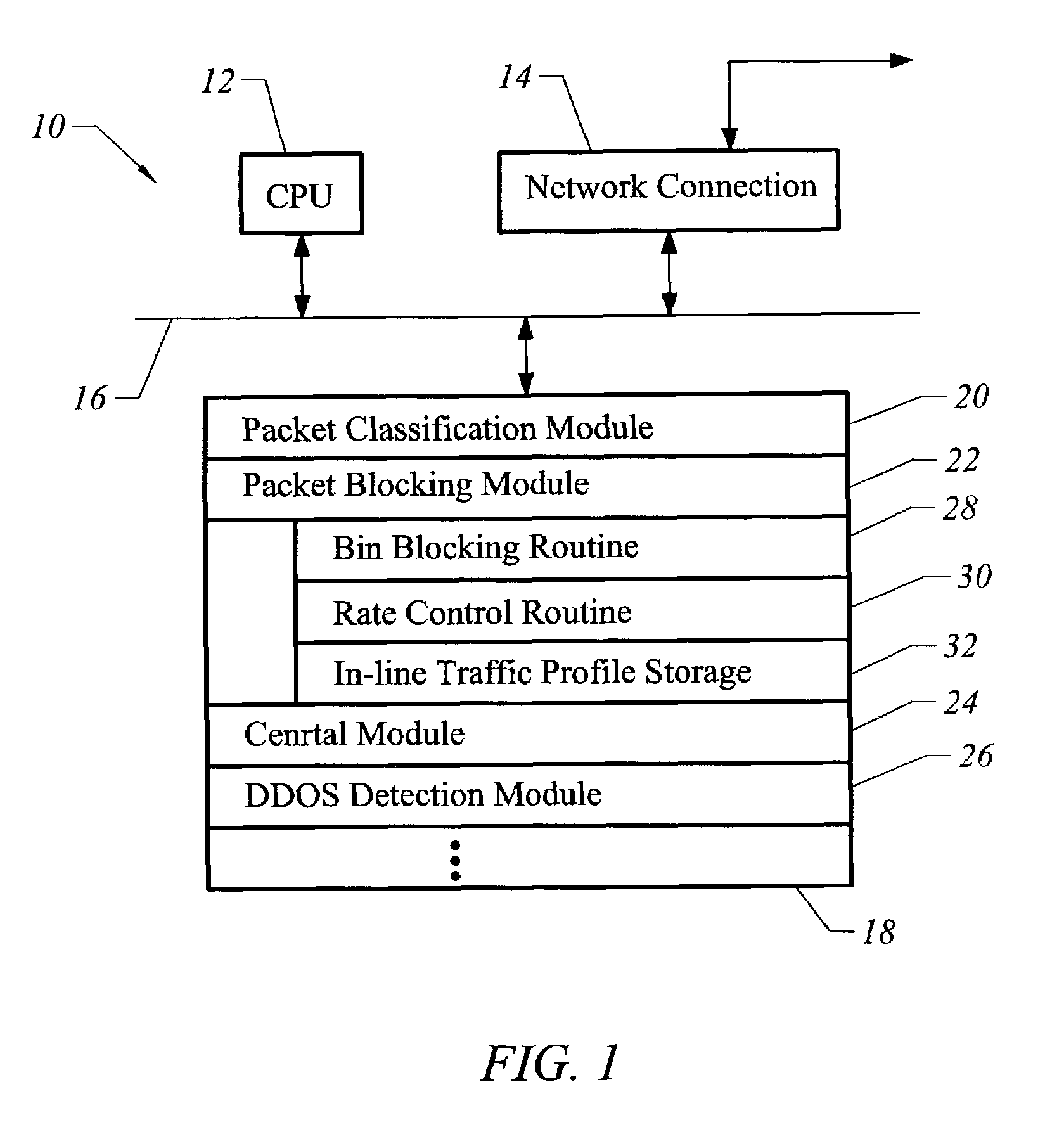
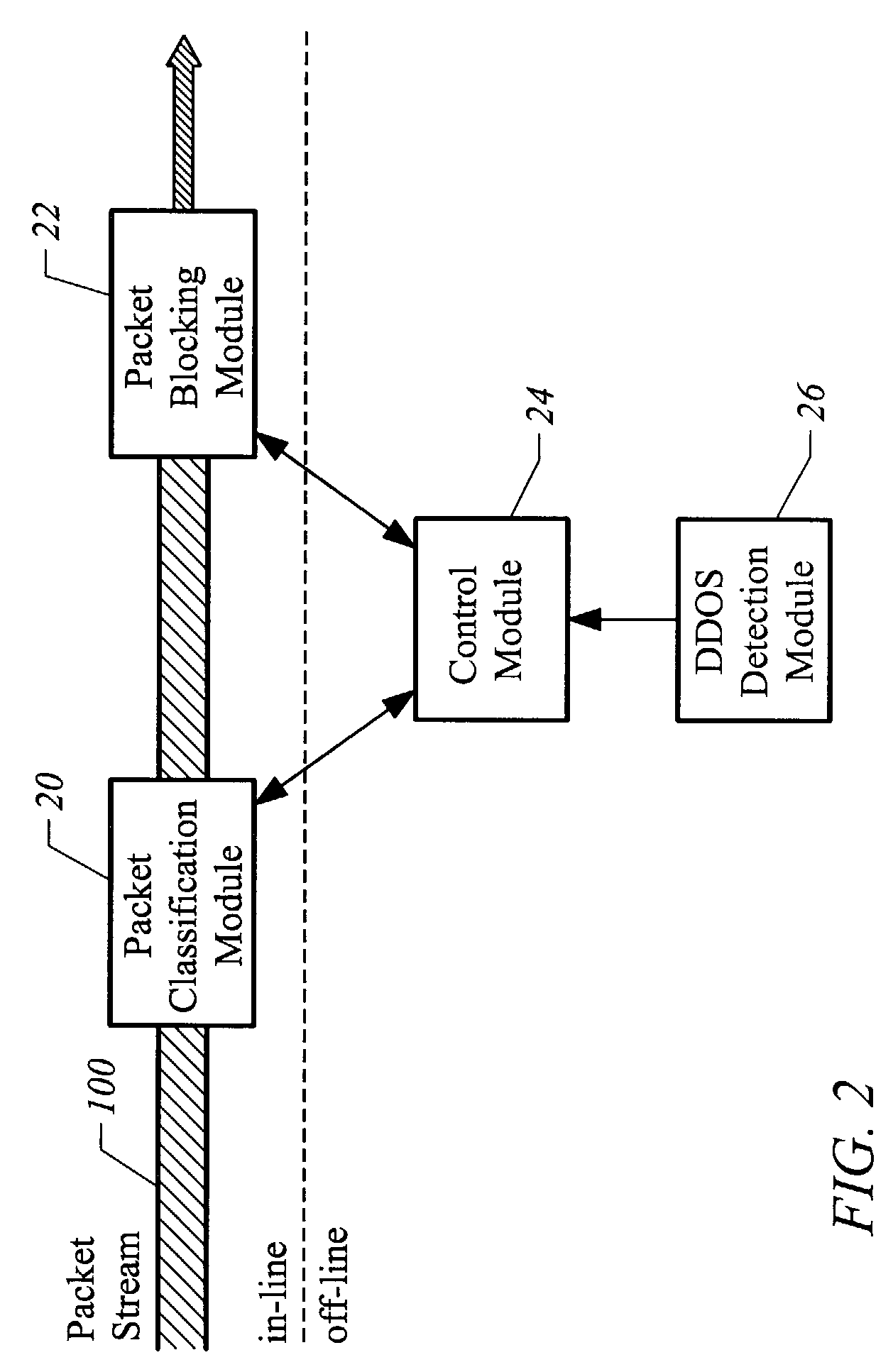
A method of adaptively classifying information using a binary tree comprises establishing a binary tree including a set of binary sequences each representing one or more network addresses. Once network traffic is received having identifiers describing network traffic sources, the identifiers are correlated to binary sequences within the binary tree. A revision metric is formed based on this correlating, and the binary tree is then revised according to this revision metric.A method of blocking a DDOS attack comprises establishing a binary tree including a set of binary sequences, each of these binary sequences representing one or more network addresses. When network traffic is received having identifiers describing network traffic sources, the identifiers are correlated to binary sequences within the binary tree. Once a DDOS attack notification signal is received, a selected binary tree path within the binary tree is identified as a low cost blocking path within the binary tree. Network traffic correlated to a binary sequence corresponding to the selected binary tree path is blocked.
Owner:MCAFEE LLC
Search method of a roaming service
InactiveUS20080194253A1Shorten the overall cycleAssess restrictionRadio/inductive link selection arrangementsPublic land mobile networkNetwork service
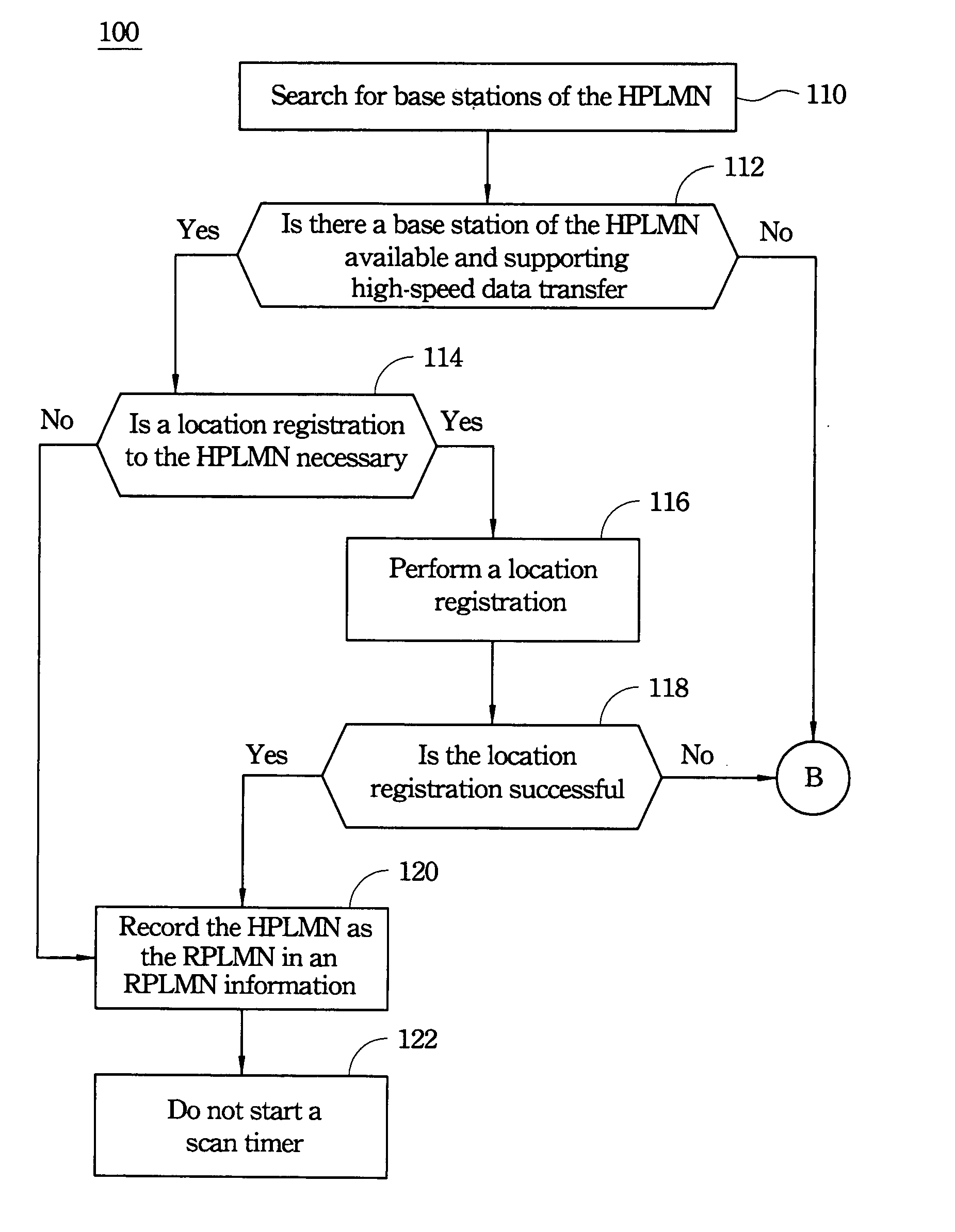
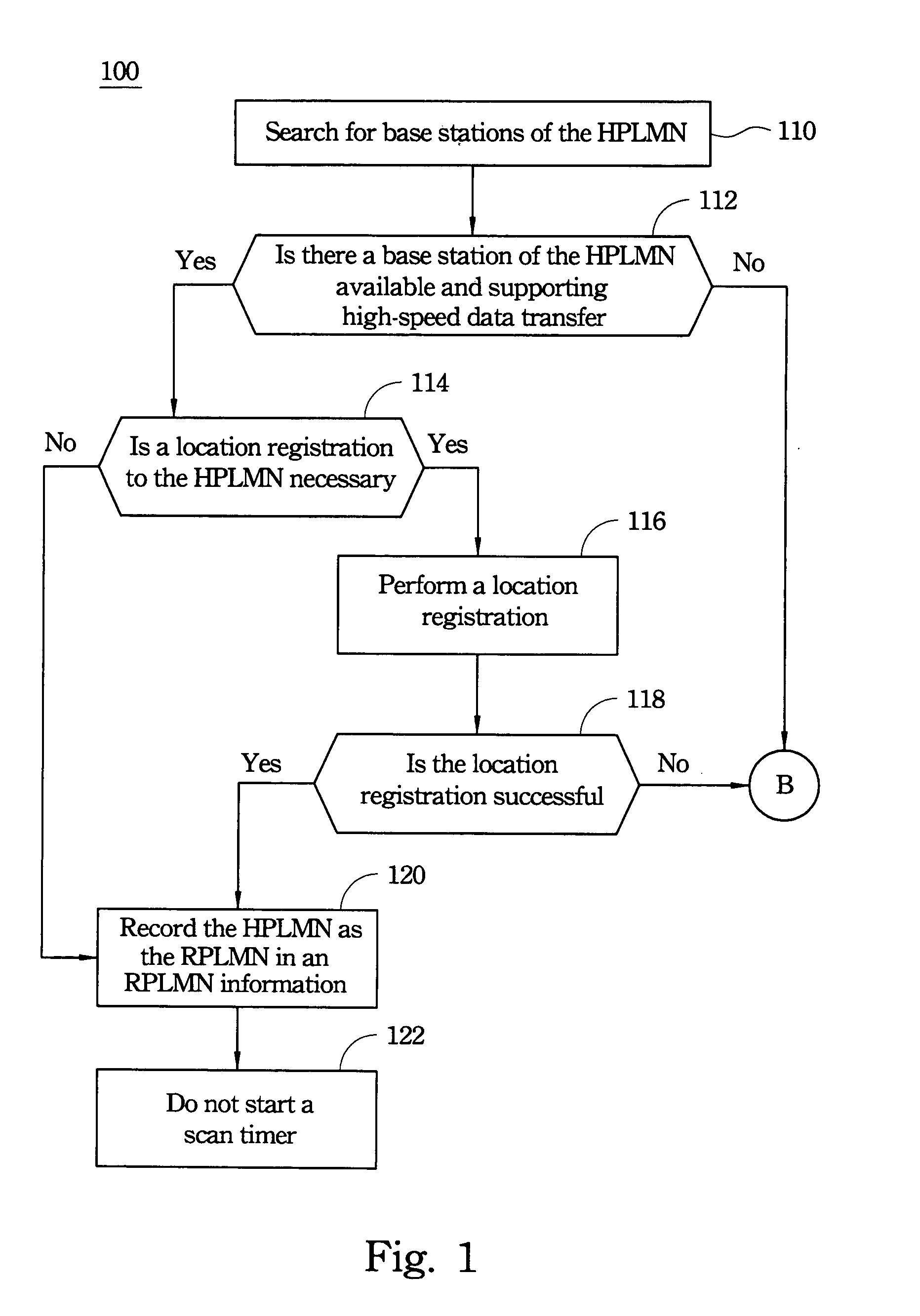
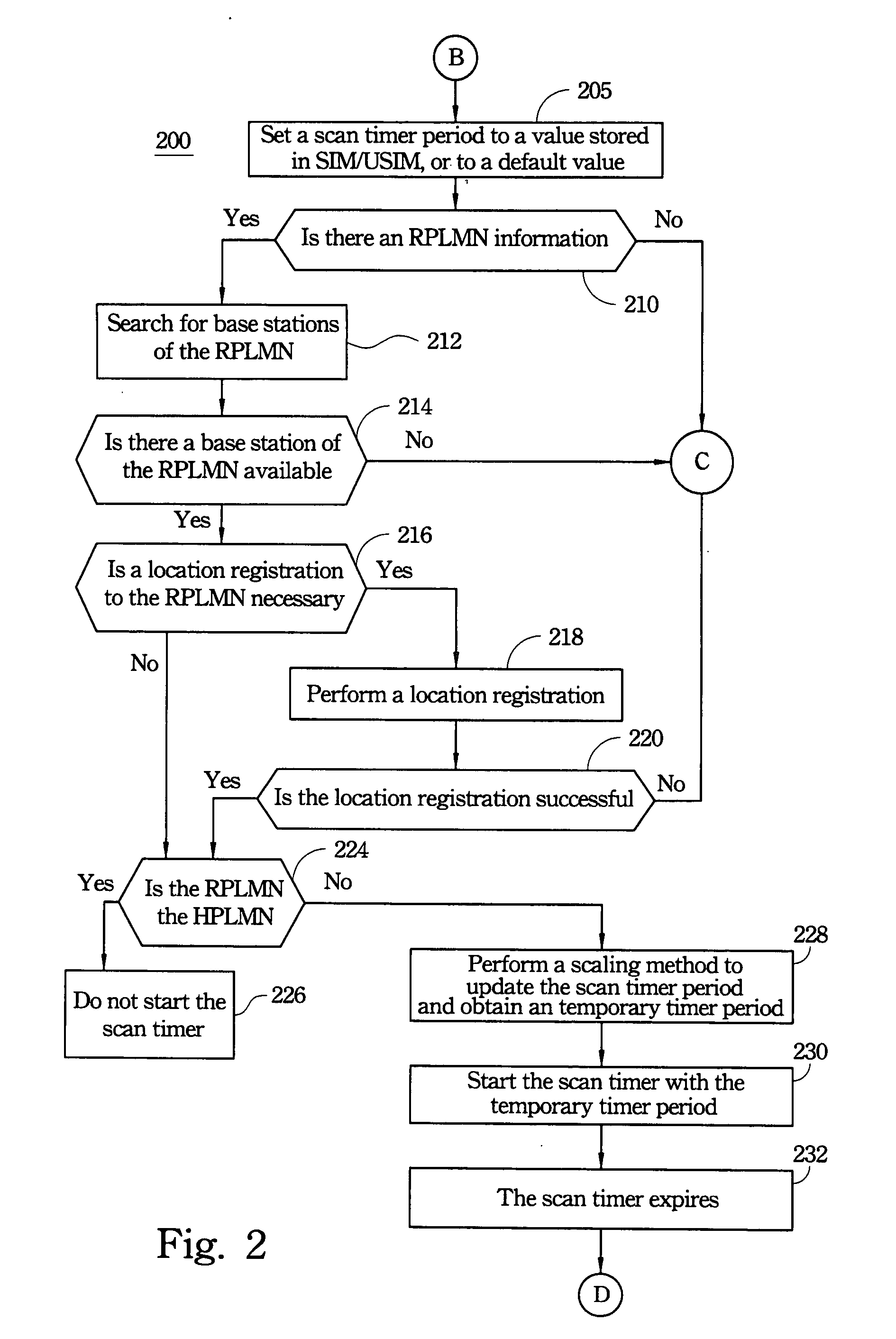
A search method of a roaming service for registering a mobile station to a network service includes searching for a home public land mobile network (HPLMN) when the mobile station is first switched on or recovering from lack of service, or sorting an available public land mobile network (PLMN) list, or using a scaling method to obtain a temporary timer period for a periodic search. Sorting the available PLMN list includes sorting according to a location-based order of preferred PLMNs, or sorting according to a data transfer speed supported by each PLMN. The scaling method includes examining a change ratio in the available PLMN list, or a data transfer speed of the RPLMN, or a status of Mobile Country Code (MCC) in order to obtain the temporary timer period.
Owner:BANDRICH
Systems and methods of data flow classification
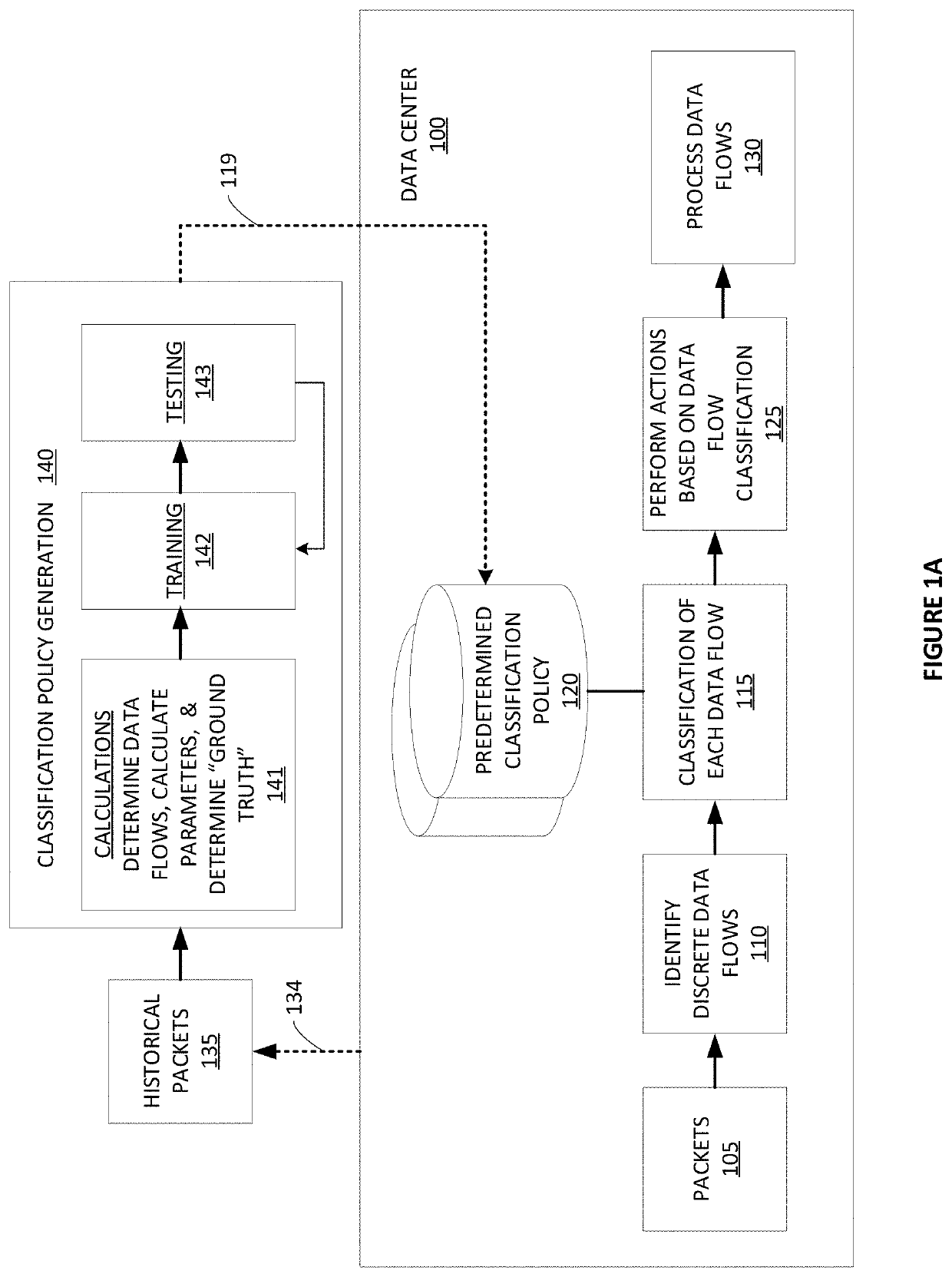
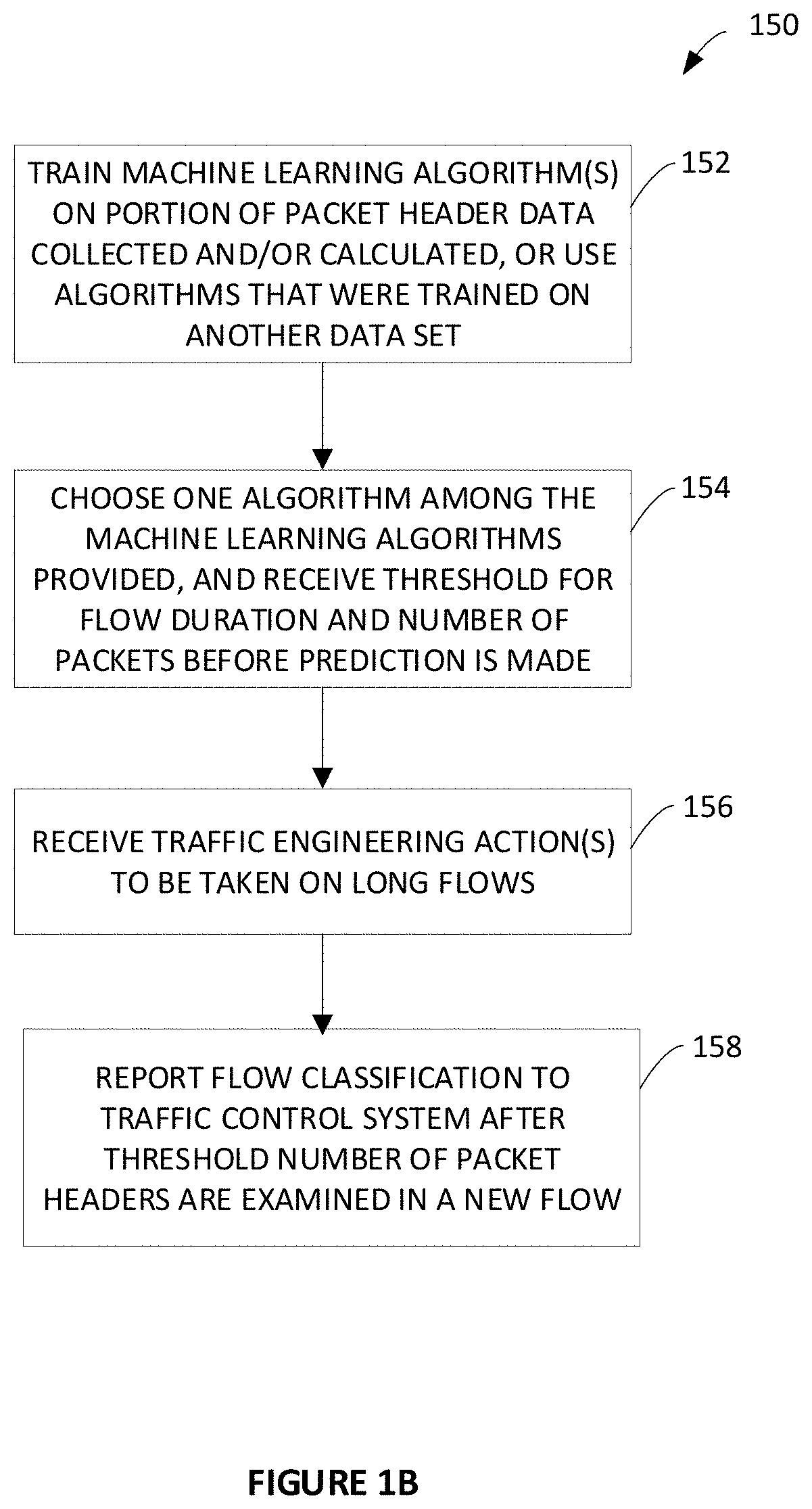
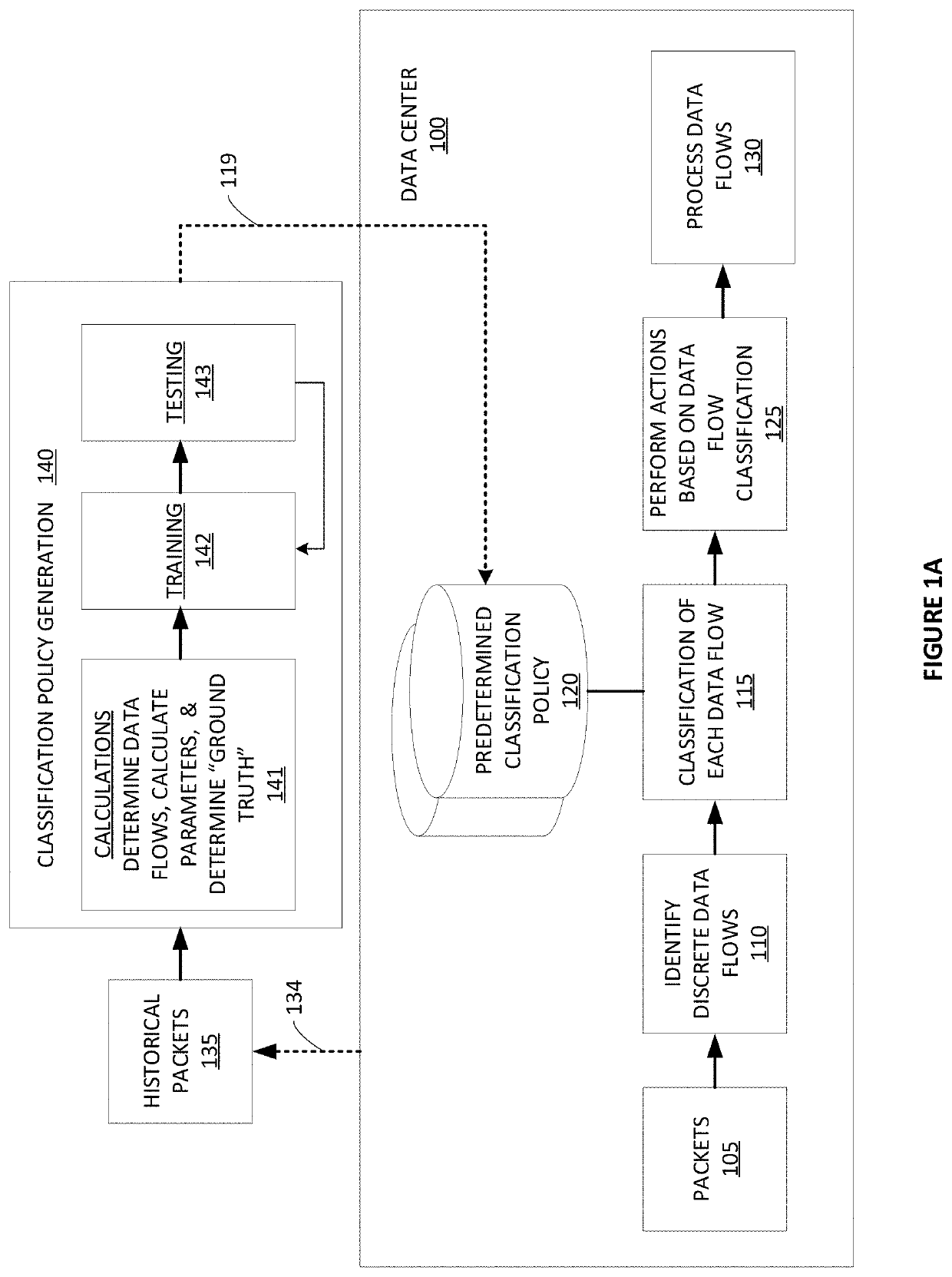
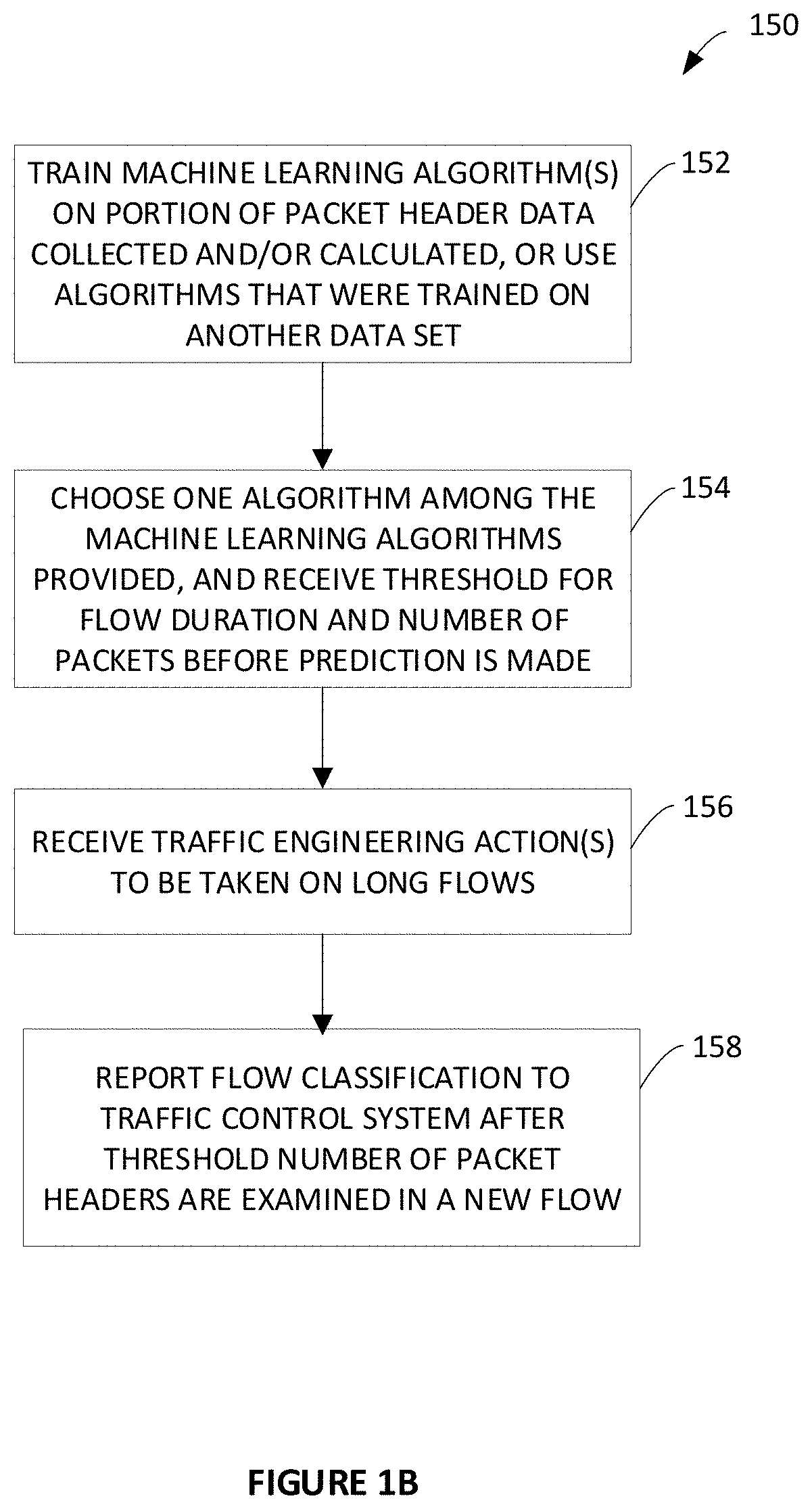
Systems and methods of classifying data flows being communicated on a network by one or more network elements. One method includes creating a table including information of packet timestamps and pre-defined packet header fields, grouping packets into data flows based on information in the table, assigning flow identifiers to each data flow, determining a plurality of feature / characteristic sets having one or more features and / or one or more characteristics of the data flows, determining one or more classifiers to predict flow labels using the plurality of feature / characteristic sets, and generating a classification policy that includes the one or more classifiers to classify data flows on the network. The method can also include storing the classification policy in at least one non-transitory computer medium that is accessible by a network element that is classifying data flows on the network, and using the classification policy to classify data flows.
Owner:XAXAR INC
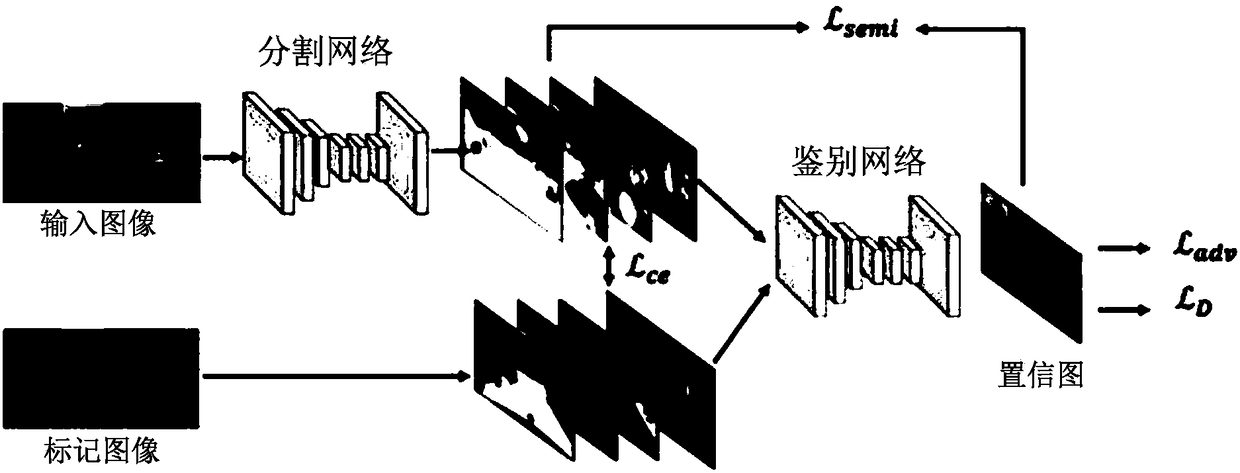
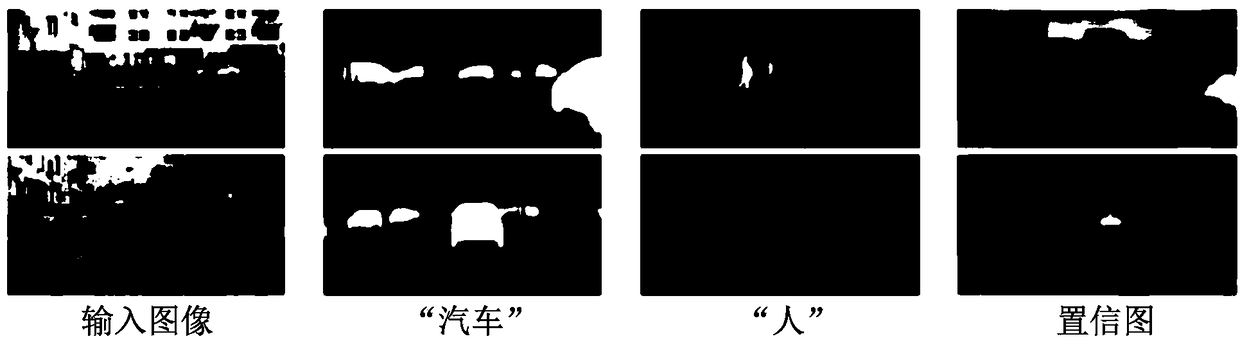
Adversarial-network-based semi-supervised semantic segmentation method
InactiveCN108549895ACharacter and pattern recognitionNeural architecturesAdversarial networkImage matching
The invention proposes an adversarial-network-based semi-supervised semantic segmentation method comprising two parts of network construction and a training process. To be specific, a ResNet-101-model-contained DeepLab-v2 frame pretrained in an ImageNet database is used as a segmentation network; a last classification network layer is removed and the space between last two convolutional layers ischanged from 2 to 1; an extended convolutional network is employed to increase a receiving domain and spatial Pyramid pooling is used after the last layer; and a full convolutional network is used asan authentication network and an up sampling network is used for adjusting an output image matching the size of an input image again. According to the invention, on the basis of the adversarial network, a semi-supervised semantic segmentation method is provided; the full convolution discriminator allows the system to carry out semi-supervised learning and an additional supervision signal is provided, so that the performance of image semantic segmentation is improved.
Owner:SHENZHEN WEITESHI TECH
Network intrusion detection method and device based on multi-network model and electronic equipment
ActiveCN111553381AEasy to identifyImprove recognition accuracyCharacter and pattern recognitionNeural architecturesFeature vectorDecision model
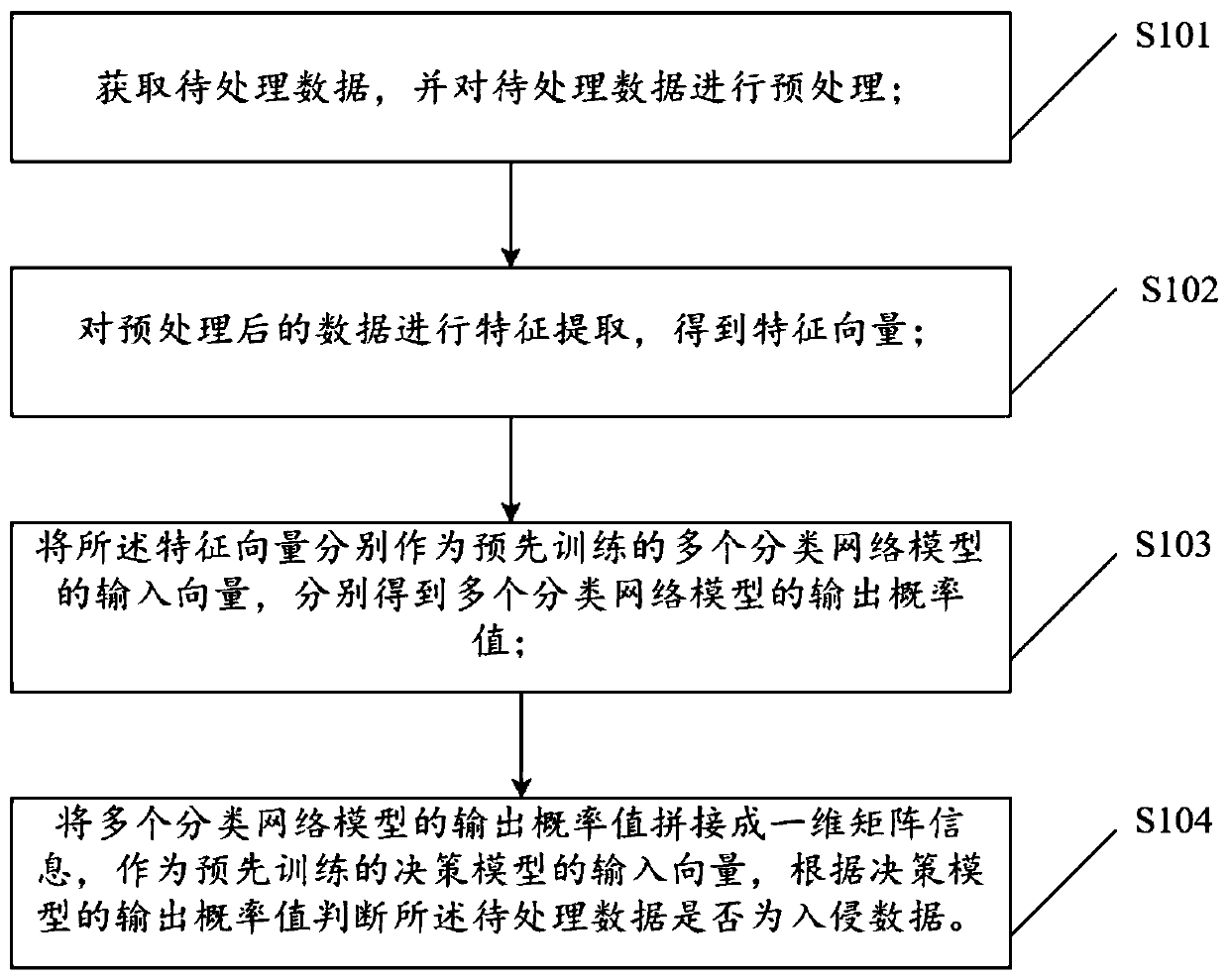
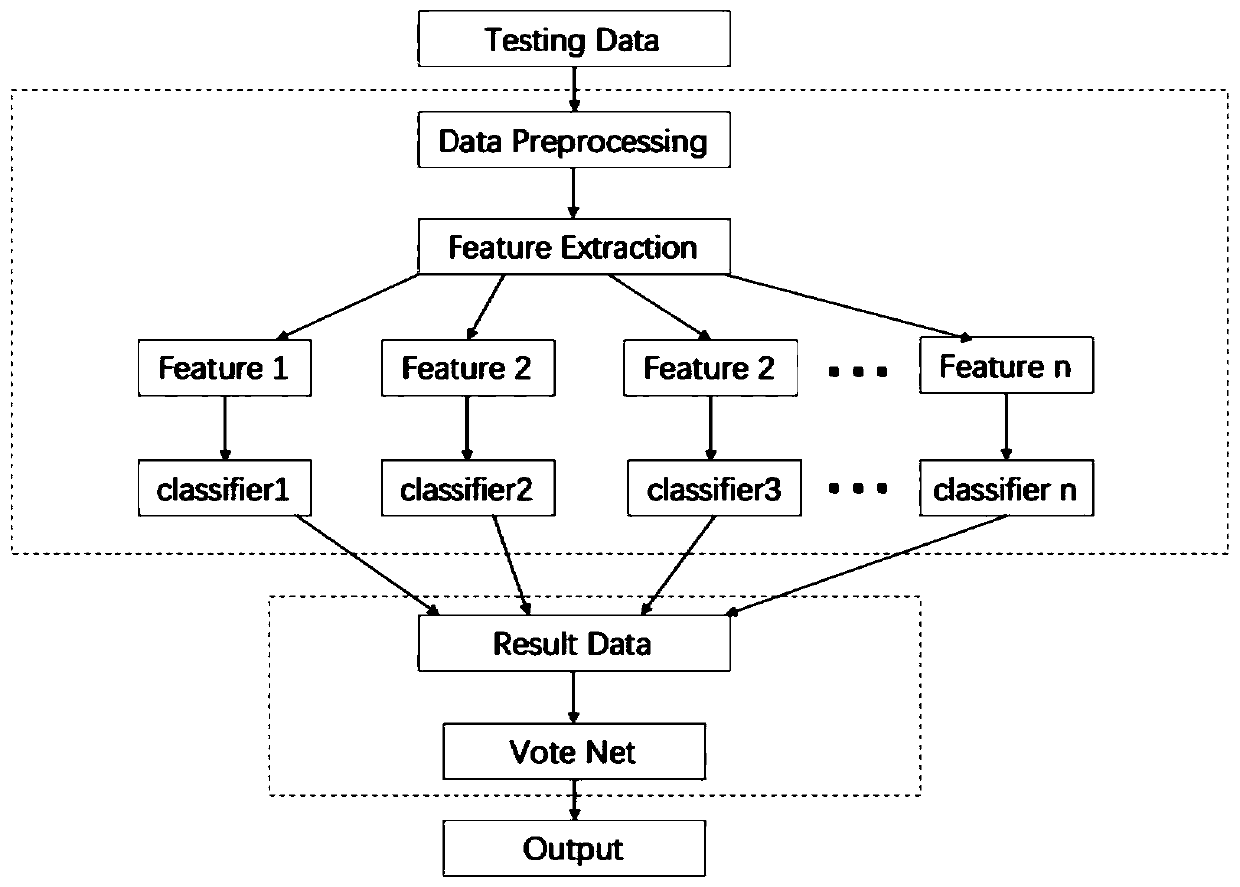
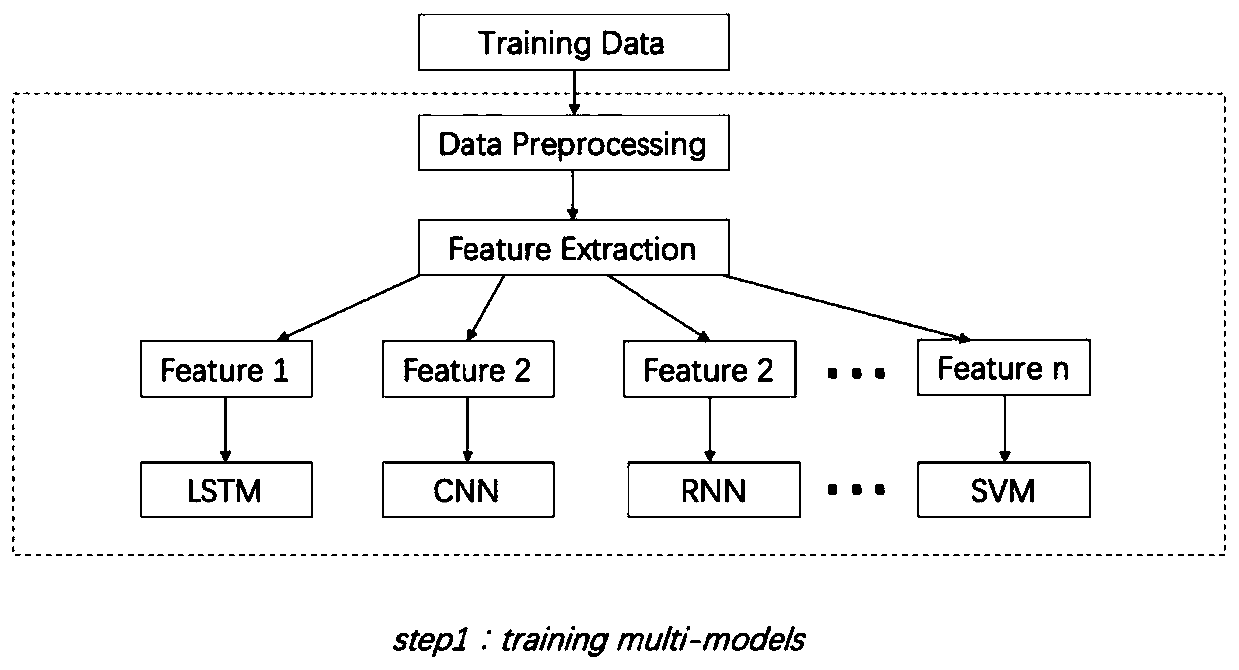
The invention discloses a network intrusion detection method and device based on a multi-network model and electronic equipment, and the network intrusion detection method comprises the steps: obtaining to-be-processed data, and carrying out the preprocessing of the to-be-processed data; carrying out feature extraction on the preprocessed data to obtain a feature vector; respectively taking the feature vectors as input vectors of a plurality of pre-trained classification network models to respectively obtain output probability values of the plurality of classification network models; and splicing the output probability values of the plurality of classification network models into one-dimensional matrix information, taking the one-dimensional matrix information as an input vector of a pre-trained decision model, and judging whether the to-be-processed data is intrusion data or not according to the output probability values of the decision model. According to the network intrusion detection method based on the multiple network models, multiple model algorithms are effectively combined together, and the respective advantages are brought into play together, and the recognition accuracyis improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Classification processing method and network equipment for multi-protocol label switching service
ActiveCN101014008AImprove search efficiencyFlexible Business Processing ClassificationNetworks interconnectionDifferentiated servicesMulti protocol
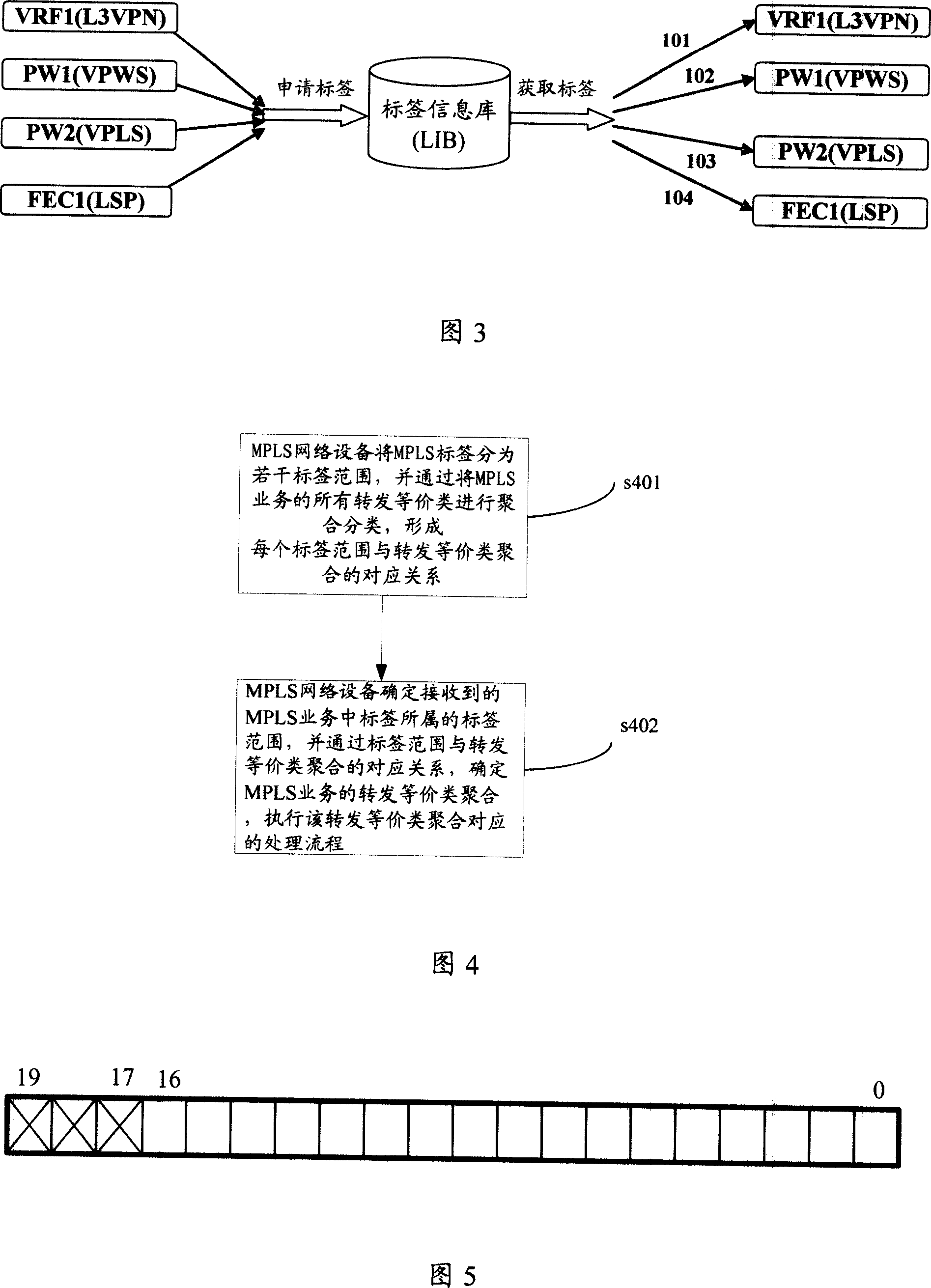
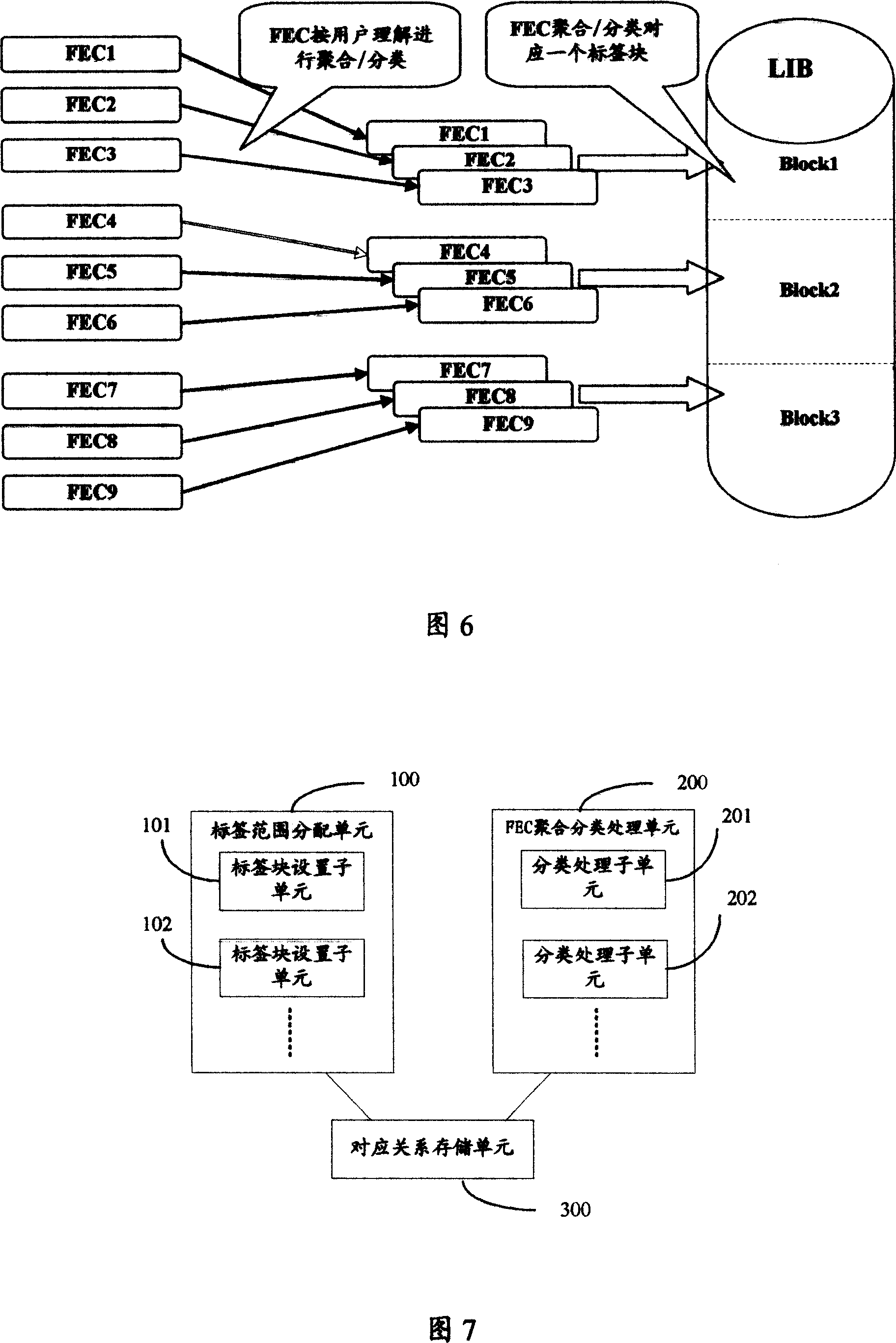
The invention discloses one MPLS business sort process method, wherein, the device divides the MPLS label into several sections through all sort of all transfer business to form each label range the equal polymer relationship; MPLS network device determines received label range through the relation between label range and transfer to determine transfer polymer and to execute relative process. The invention also discloses one multi-agreement label exchange business network device.
Owner:NEW H3C TECH CO LTD
Method of application classification in Tor anonymous communication flow
ActiveCN104135385AReduce loadImplement application classificationData switching networksTraffic capacitySequence alignment algorithm
The invention discloses a method of application classification in Tor anonymous communication flow, which mainly solves the problem of acquisition of upper-layer application type information in the Tor anonymous communication flow and relates to the correlation technique, such as feature selection, sampling preprocessing and flow modeling. The method comprises the following steps of: firstly, defining a concept of a flow burst section by utilizing a data packet scheduling mechanism of Tor, and serving a volume value and a direction of the flow burst section as classification features; secondly, preprocessing a data sample based on a K-means clustering algorithm and a multiple sequence alignment algorithm, and solving the problems of over-fitting and inconsistent length of the data sample through the manners of value symbolization and gap insertion; and lastly, respectively modeling uplink Tor anonymous communication flow and downlink Tor anonymous communication flow of different applications by utilizing a Profile hidden Markov model, providing a heuristic algorithm to establish the Profile hidden Markov model quickly, during specific classification, substituting features of network flow to be classified into the Profile hidden Markov models of different applications, respectively figuring up probabilities corresponding to an uplink flow model and a downlink flow model, and deciding the upper-layer application type included by the Tor anonymous communication flow to be classified through a maximum joint probability value.
Owner:南京市公安局
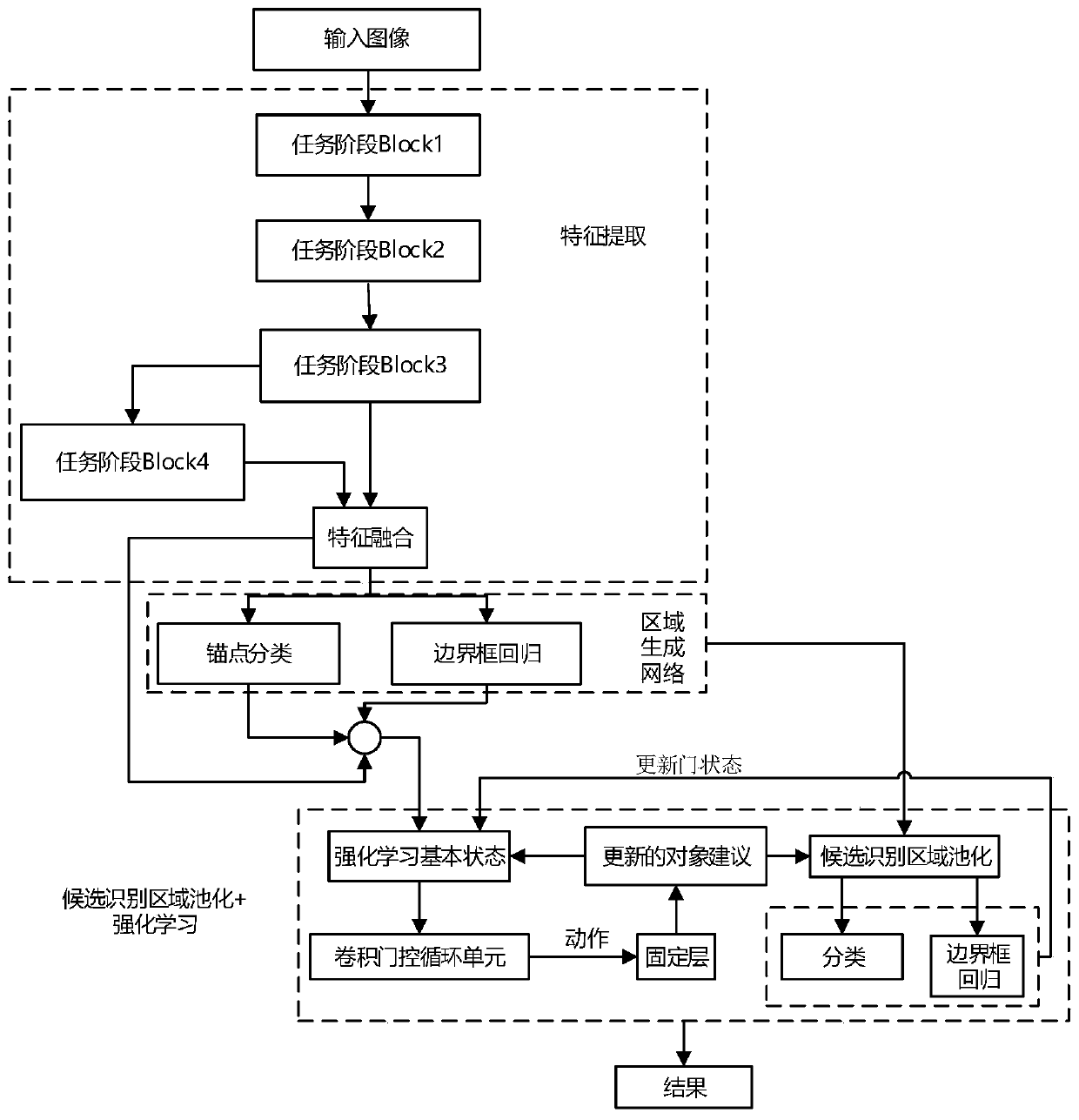
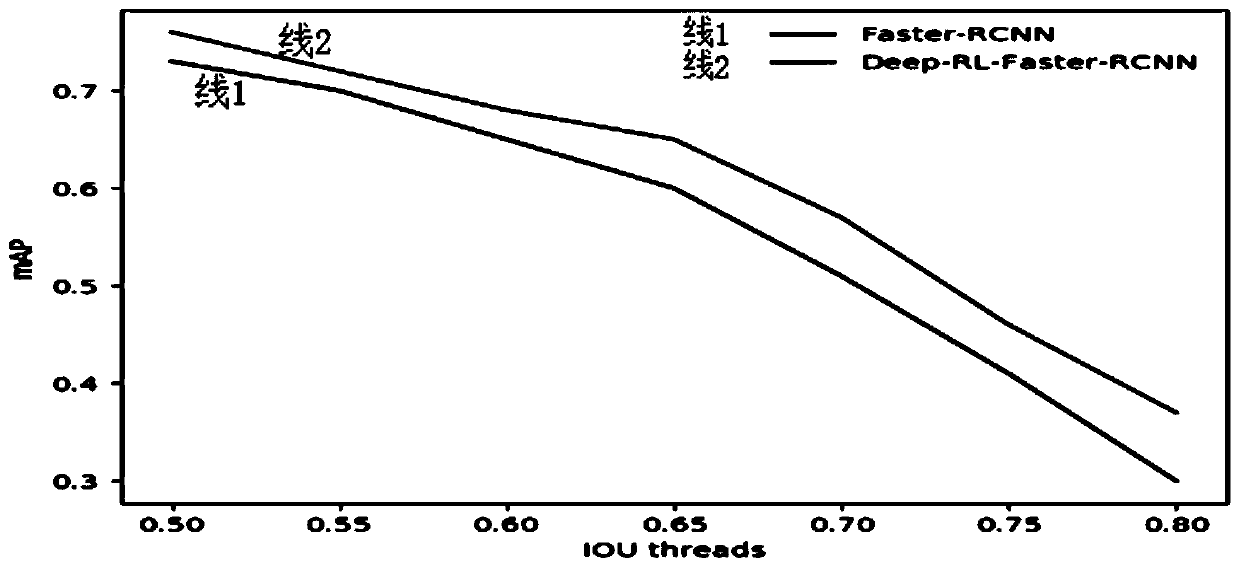
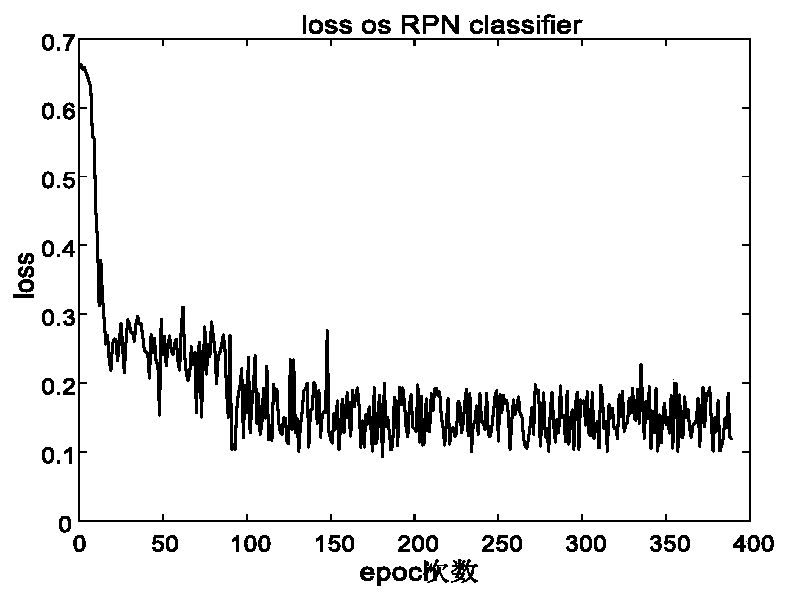
Faster-RCNN target object detection method based on deep reinforcement learning
ActiveCN111476302AAvoid the problem of low spatial resolutionPrecise positioningCharacter and pattern recognitionNeural architecturesAlgorithmEngineering
The invention discloses a Faster-RCNN target object detection method based on deep reinforcement learning. The comprises the steps: storing the state of the regional suggested network RPN at each moment by adopting an experience pool of deep reinforcement learning, outputting two actions by adopting a convolution gating circulation unit, selectively executing corresponding actions by adopting a random strategy, and removing redundant detection boxes by adopting a self-defined non-maximum suppression method to obtain a detection box closest to a labeling box; classifying the detection frames byadopting a classification network, and carrying out quadratic regression on the detection frames to realize detection and identification of the target object. By adopting the technical scheme, the target positioning is accurate, and the target detection precision is high.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY +1
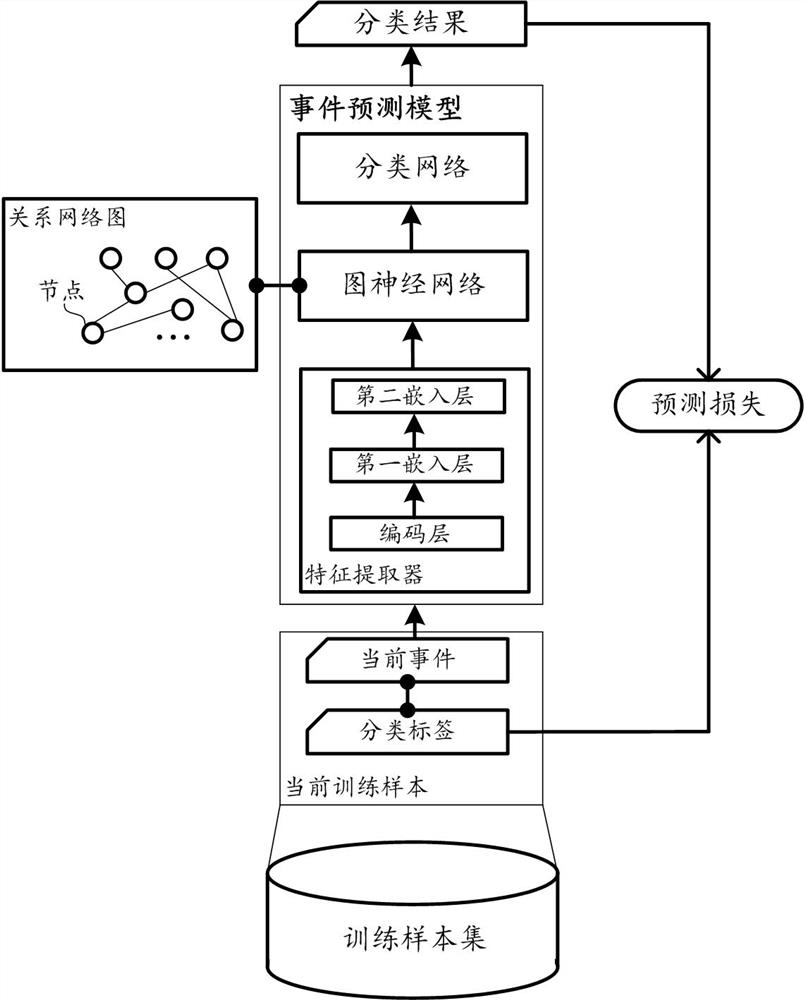
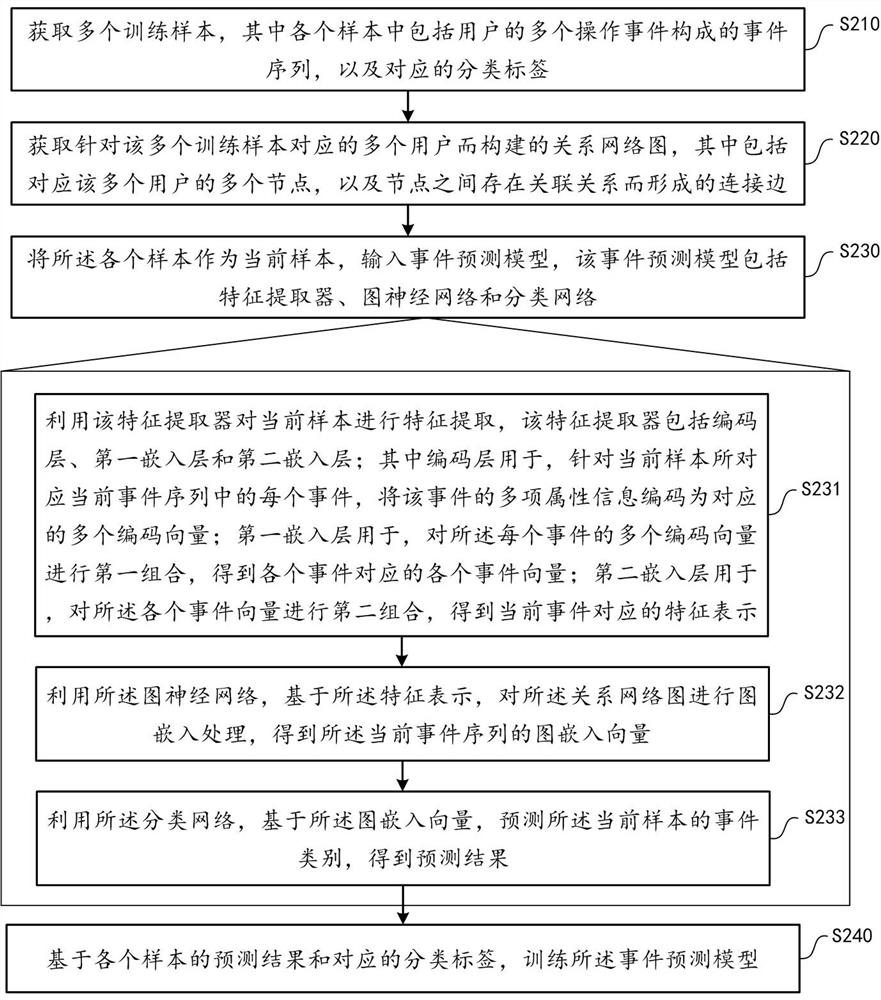
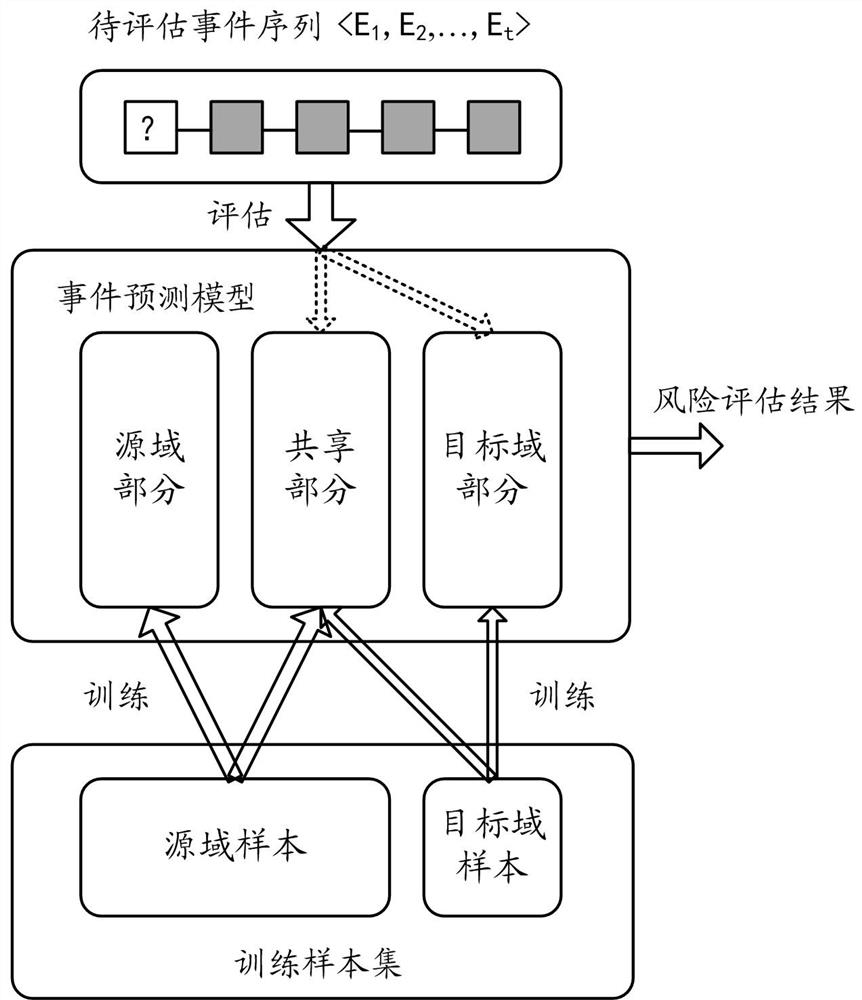
Method and device for training event prediction model
ActiveCN111814977AEffective graph embedding processingAccurate representationCharacter and pattern recognitionMachine learningFeature extractionEngineering
The embodiment of the invention provides a method for training an event prediction model, the method can be applied to a transfer learning scene, and data isolation and privacy security protection ofa source domain participant and a target domain participant are realized by setting a neutral server, wherein the source domain participant deploys a source domain feature extractor, the target domainparticipant deploys a target domain feature device, and a model sharing part in an event prediction model is deployed in a neutral server and specifically comprises a sharing feature extractor, a graph neural network and a classification network. For any participant, feature extraction is performed on a sample in a local domain by utilizing a feature extractor of the local domain to obtain localdomain feature representations, and the local domain feature representation is processed by using the current parameters of the model sharing part obtained from the server to obtain a corresponding event classification result, model updating based on the event classification result and the local domain sample is performed, and an updating result of the model sharing part is uploaded to the serverto enable the server to perform centralized updating.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
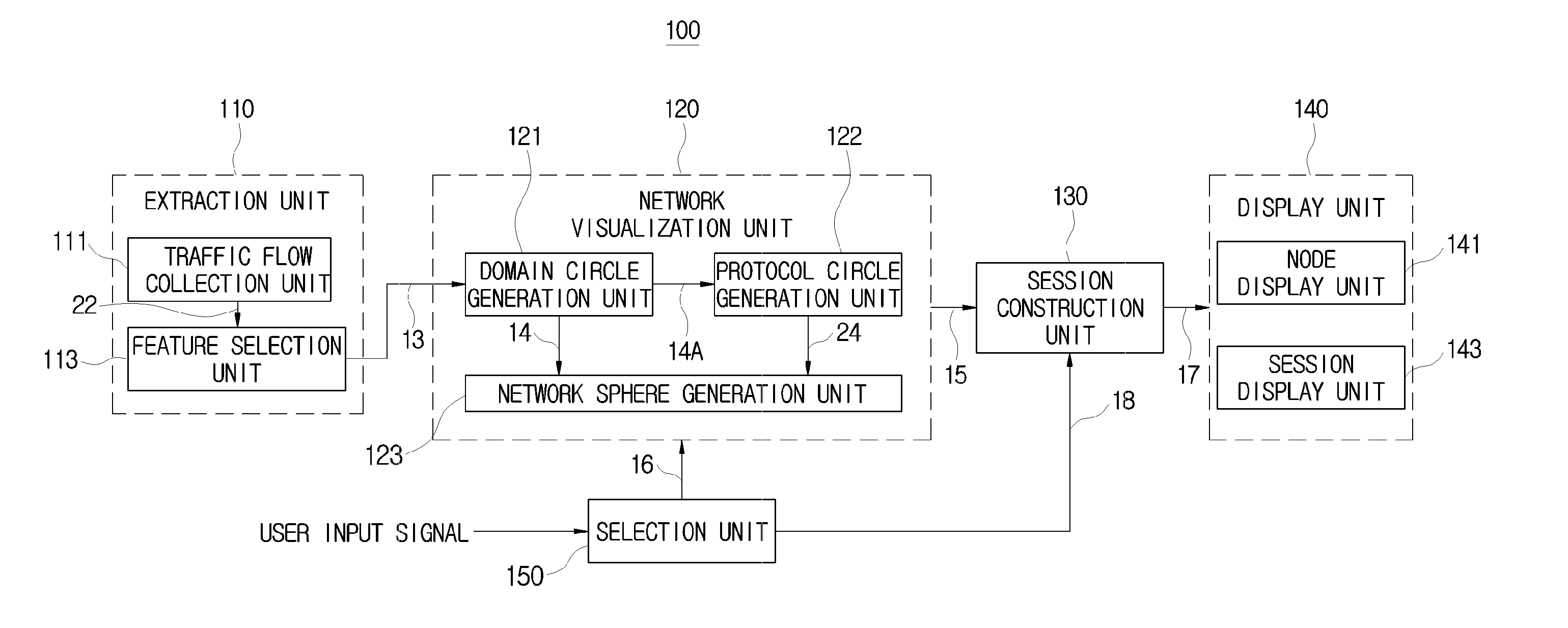
Apparatus and method of displaying network security situation
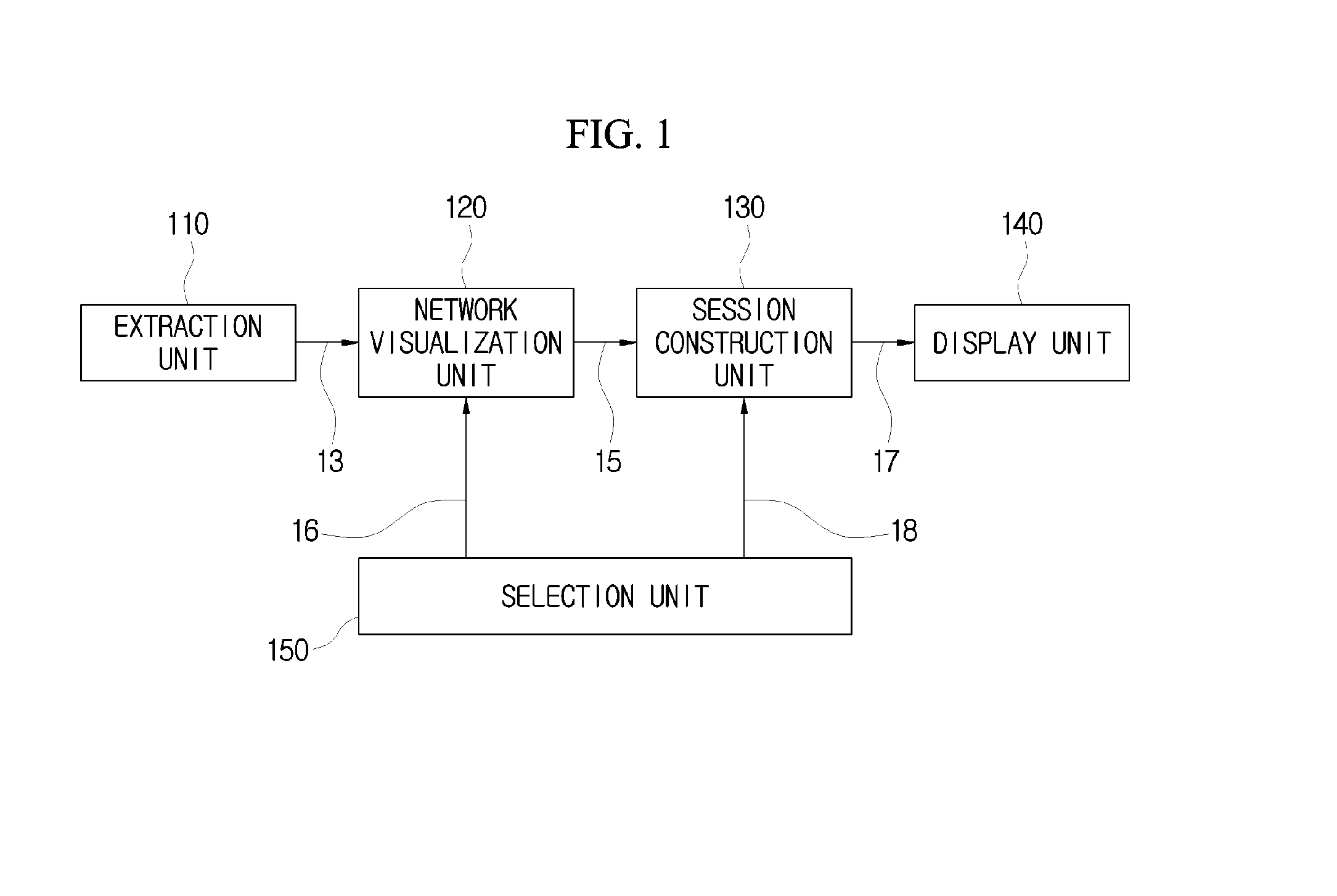
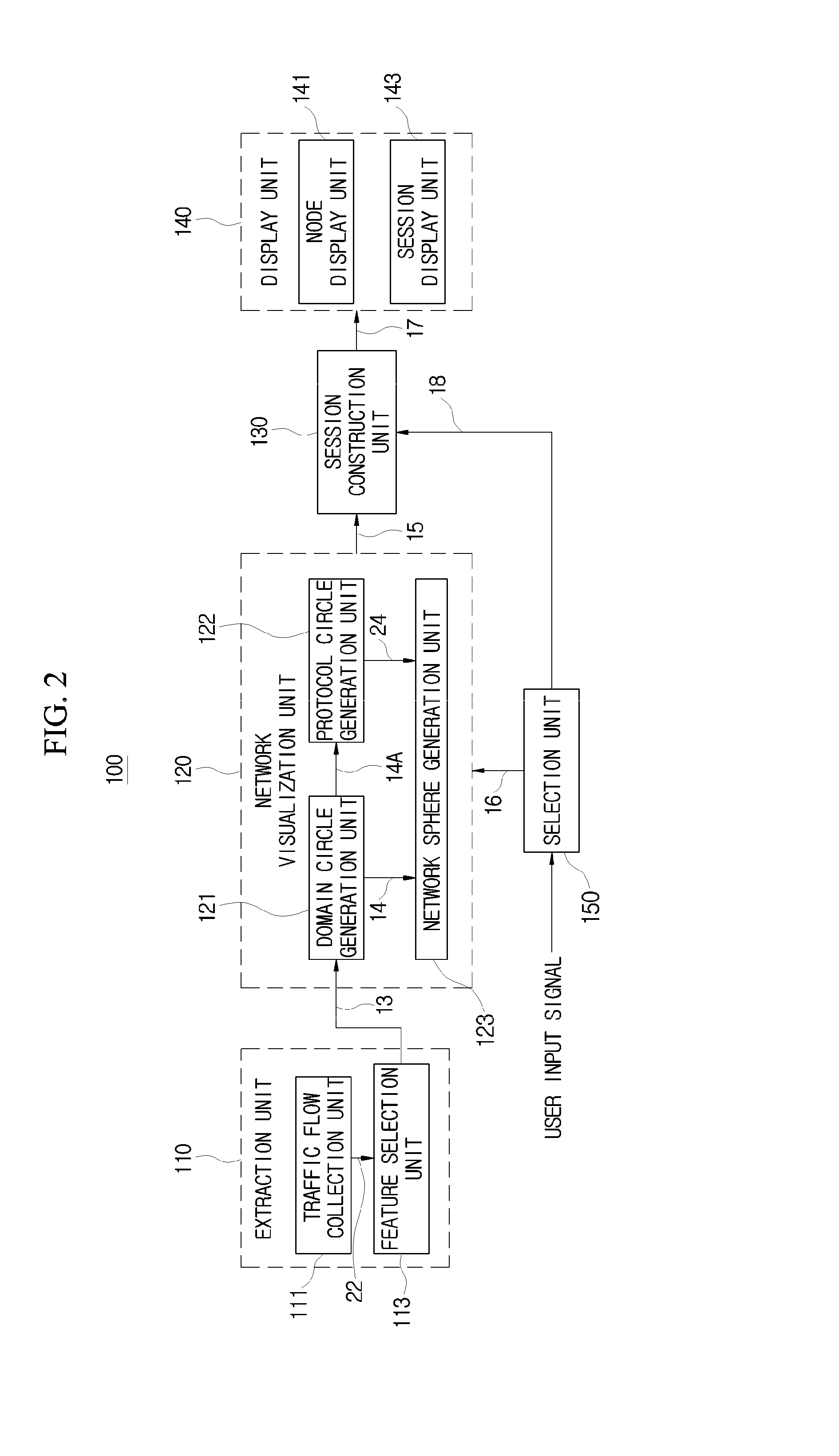
An apparatus and method of displaying a network security situation is provided. The apparatus includes an extraction unit configured to classify a characteristic factor including IP addresses of a transmission node and a reception node from a traffic flow, a network visualization unit configured to generate a domain circle visualizing each of a transmission domain and a reception domain as a circle shape by mapping the IP addresses of the transmission node and the reception node to points on circumference as one to one, arrange the generated domain circle on an axis, and visualize each of a transmission network area and a reception network area as a sphere shape, a session construction unit configured to a session of the visualized transmission network area and reception network visually, and a display unit configured to display the session which is visually constructed.
Owner:ELECTRONICS & TELECOMM RES INST
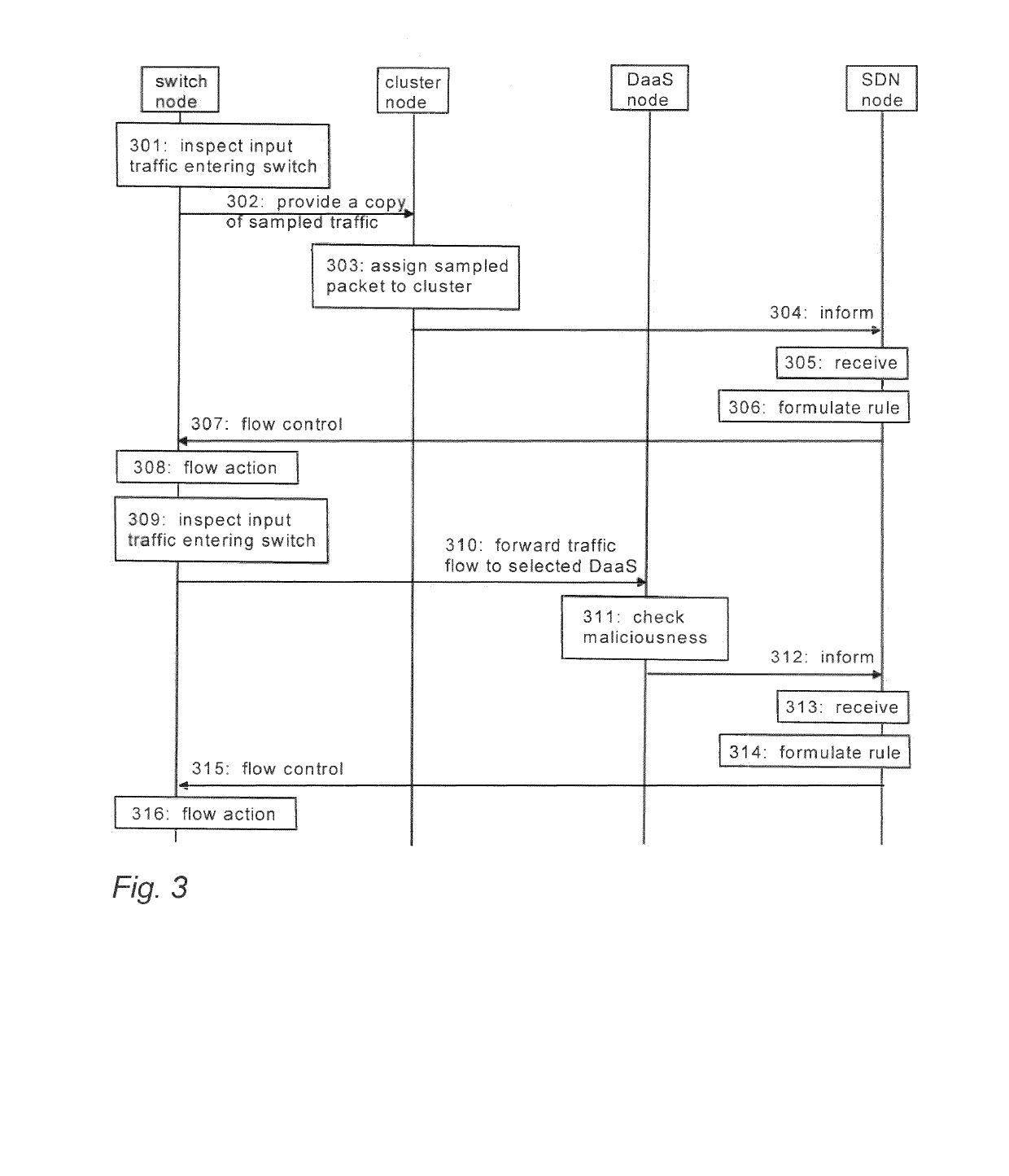
Anomaly Detection in Software Defined Networking
ActiveUS20190215305A1Network traffic/resource managementTransmissionCommunications systemNetwork packet
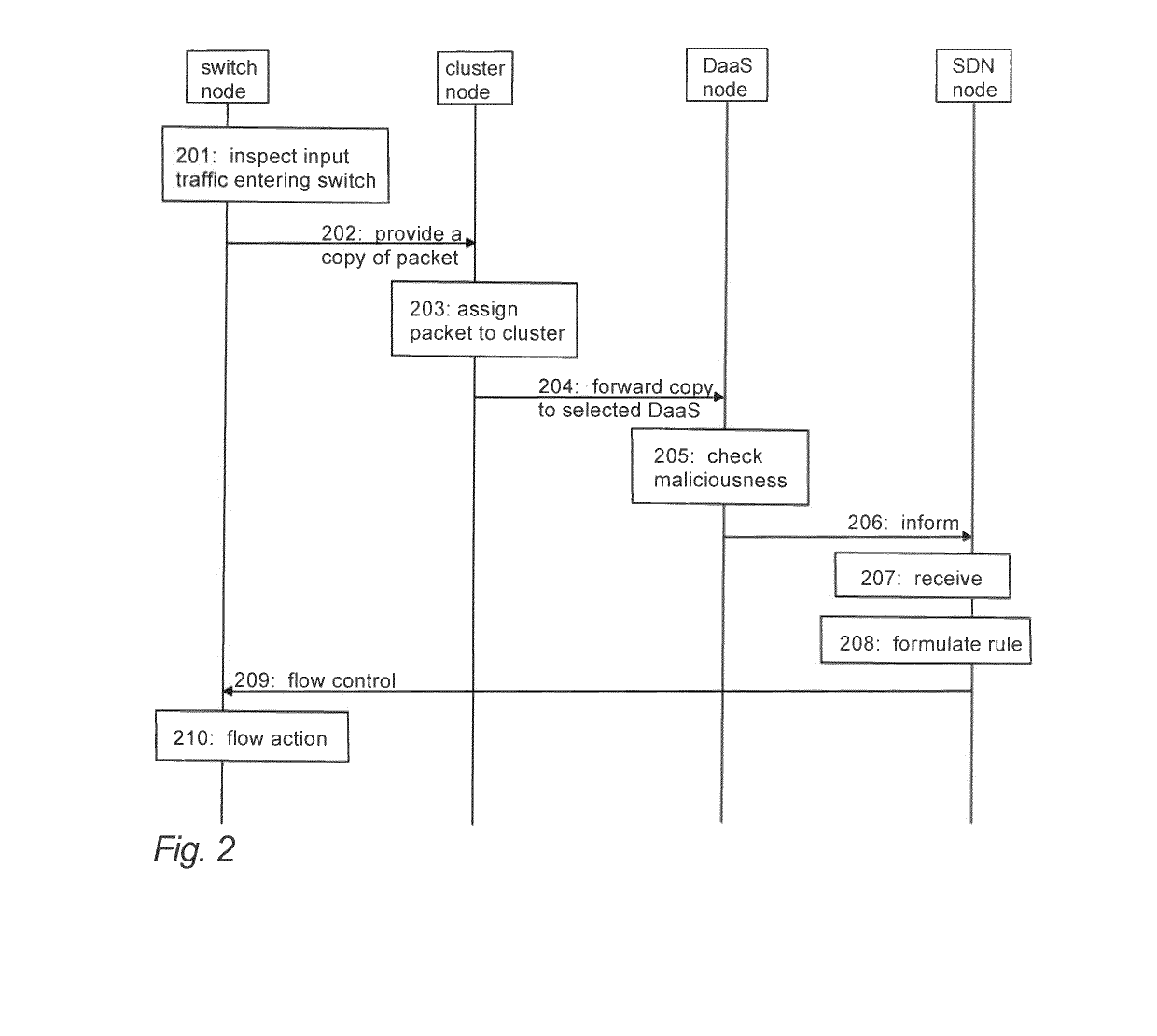
A network apparatus of a communication system classifies traffic flows containing packets based on packet features. The network apparatus provides a copy of a packet contained in a traffic flow to a cluster node, and controls the cluster node to select at least one detector node based on the features of the packet and to forward said copy to the selected detector node to find out based on said copy whether the packet is malicious or not. In response to receiving from the detector node a flow indication on the traffic flow, the network apparatus controls a switch node to perform at least one flow control action on the traffic flow, the action including one or more of flow removal, flow modification and flow installation
Owner:NOKIA SOLUTIONS & NETWORKS OY
Deep fake face video positioning method based on space-time fusion
ActiveCN113011357AOvercoming the problem of reduction in recognition accuracyImprove the accuracy of false identification classificationCharacter and pattern recognitionNeural architecturesTime domainTask network
The invention discloses a deep fake face video positioning method based on space-time fusion. The method comprises the following steps: (1) constructing a convolutional neural network; (2) constructing a classification network fusing time domain and space domain features; (3) constructing a segmentation positioning task network; (4) constructing a reconstruction task network; (5) constructing a multi-task fusion network; (6) generating a multi-task fusion loss function; (7) generating a training set; (8) training the multi-task fusion network; (9) identifying and positioning the deeply-forged face video. According to the method, the classification network fusing the time domain and space domain features is constructed to extract the features, more complete intra-frame and inter-frame features can be extracted, and higher accuracy is obtained; meanwhile, the multi-task fusion loss function used for training the multi-task fusion network is constructed, and the accuracy of the multi-task fusion network is improved. The problem that generalization ability and function completeness are affected due to the fact that no attack category exists and tasks are simplified is solved.
Owner:XIDIAN UNIV
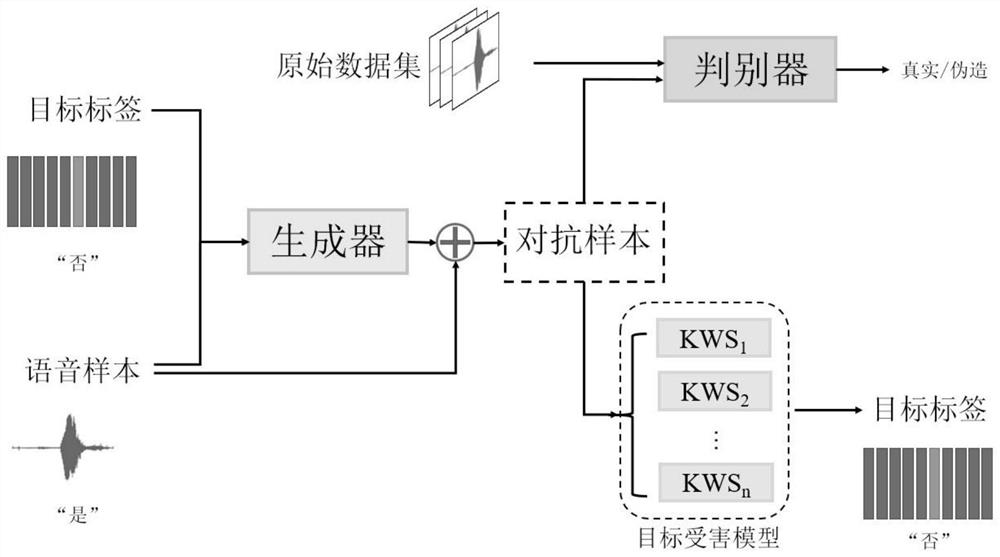
Adversarial sample attack method for voice keyword classification network
PendingCN112216273AQuick buildAnti-sample attack implementationSpeech recognitionNeural architecturesPattern recognitionAttack
The invention discloses an adversarial sample attack method for a voice keyword classification network. The adversarial sample attack method comprises the following steps: (1) selecting training dataand a target tag of trained batch sizes according to a training strategy; (2) inputting the data and the tags into a generator G, generating adversarial disturbance, and constructing a corresponding adversarial sample; (3) respectively inputting the generated adversarial samples into a discriminator D and a target victim model to obtain corresponding losses, calculating the corresponding losses, and updating parameters of the network; (4) repeating steps (1) to (4) until a training stop condition is met, and finally obtaining a trained model; and (5) using the model, loading model parameters,and inputting a voice sample and the target tag to quickly generate an adversarial sample. By using the method provided by the invention, the adversarial sample attack based on the voice keyword classification network application in a real-time scene can be realized.
Owner:东南数字经济发展研究院
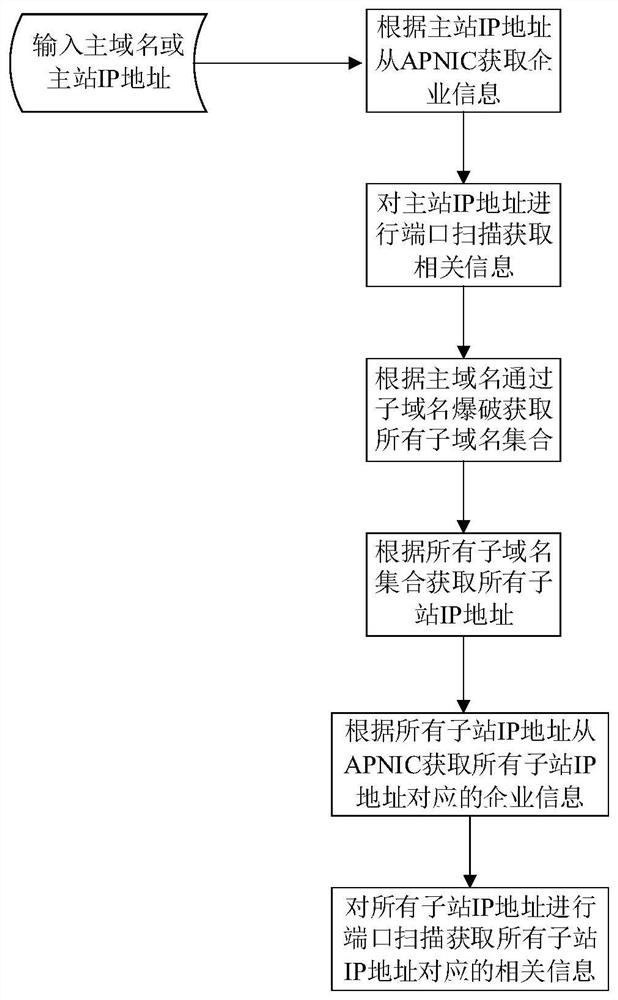
Network asset information collection and monitoring system
The invention provides a network asset information collection and monitoring system, and belongs to the field of network security. The method comprises the following steps: performing sub-domain nameblasting on a main domain name to obtain a sub-domain name set; further, obtaining all network asset information corresponding to all IP addresses through ipwhois and port scanning; and classifying all IP addresses and all domain names, comparing all network information acquired by the IP addresses with open services with all network asset information acquired by the IP address of the master station, taking multiple values, classifying and inputting the multiple values into a useful network asset information list of the to-be-checked enterprise, and completely inputting other types of classifications. Middleware scanning is performed on a useful network asset information list, a vulnerability list corresponding to middleware information is pulled, and a vulnerability alarm is given. According to the invention, the classified network asset information in units of enterprises can be obtained through simple main domain name input, the network assets are subjected to security monitoring, the steps are simplified, and the method is simple and easy to implement.
Owner:广州锦行网络科技有限公司
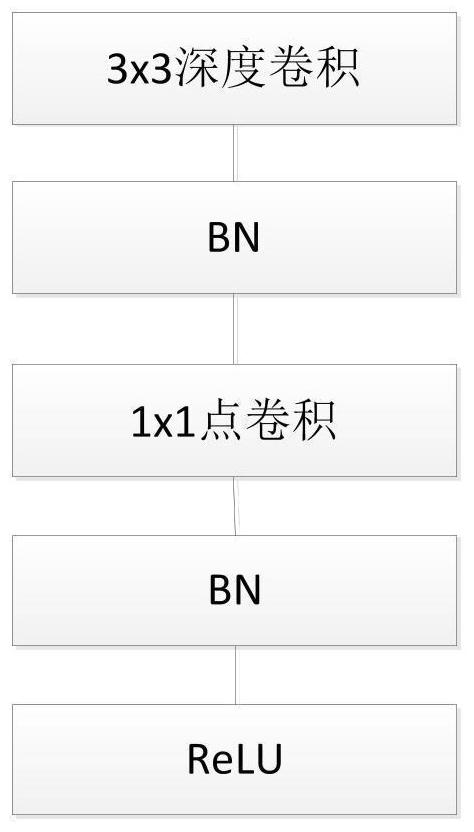
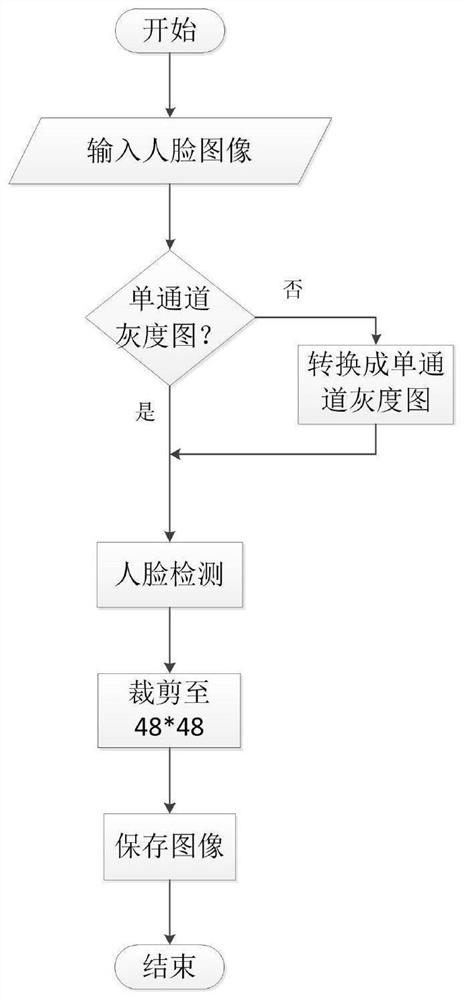
Facial expression recognition method of improved MobileNet model
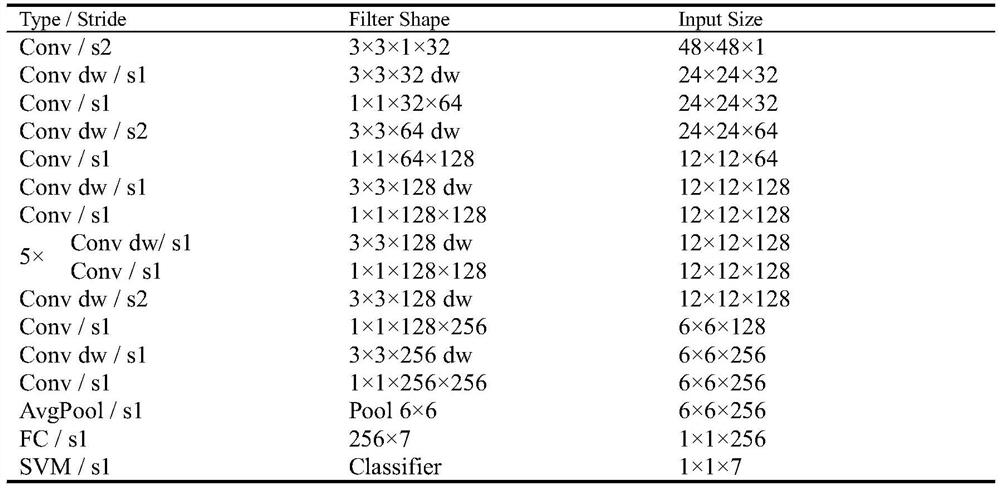
ActiveCN111860046ANeural architecturesAcquiring/recognising facial featuresActivation functionData set
According to the improved MobileNet network model provided by the invention, the network is further simplified by combining the characteristics of facial expression recognition under the condition ofkeeping the lightweight integral structure of the MobileNet, so that the network receives a 48 * 48 single-channel grayscale picture. In order to reduce the network calculation amount, a depth separable convolution layer in the MobileNetV1 model is reserved. Meanwhile, in order to solve the problem of information loss possibly caused by introduction of a nonlinear activation function after a deepconvolution layer, the nonlinear activation function is directly abandoned after the deep convolution layer, and linear output mentioned in MobileNetV2 is adopted. The network model uses a linear support vector machine to classify facial expressions into a network model. Finally, compared with MobileNetV1 and MobileNetV2, the parameters of the network model are greatly reduced. According to the model, an experiment is carried out on a CK + data set, and good recognition performance is achieved on a test set.
Owner:SICHUAN UNIV
Network information data popularity calculation method
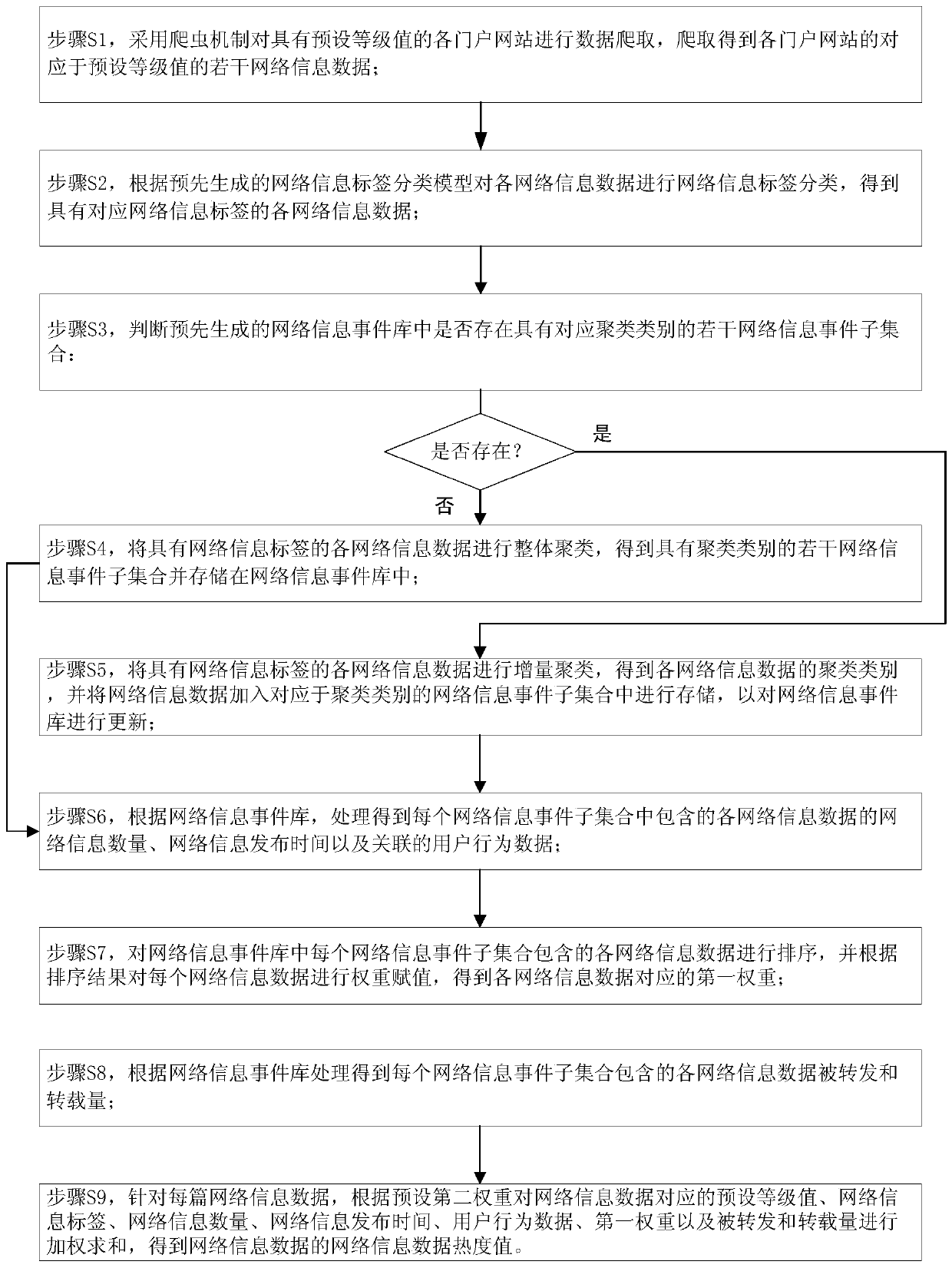
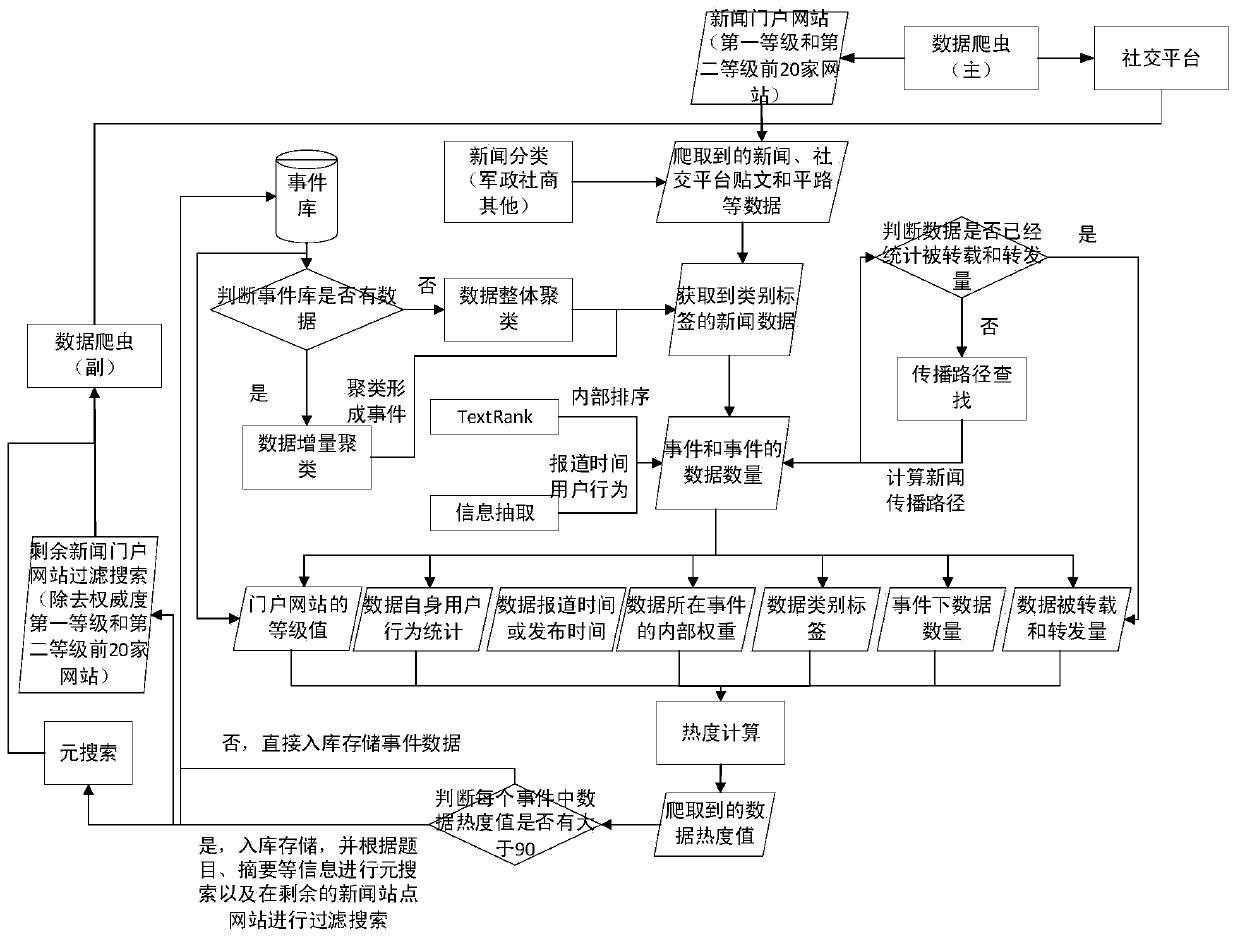
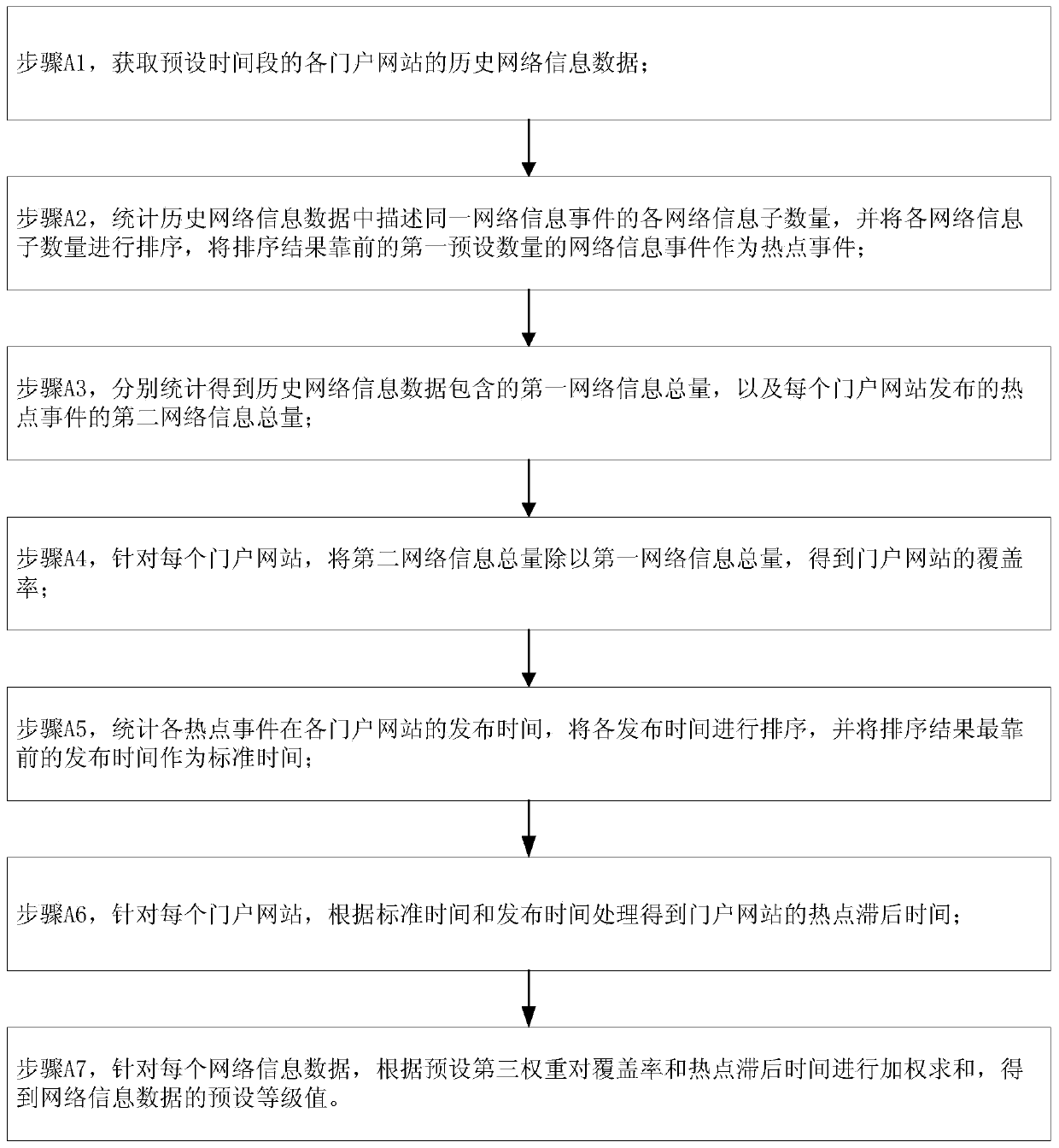
ActiveCN111324789AComprehensive heat valueWide coverageWeb data indexingOther databases clustering/classificationInformation quantityData mining
The invention discloses a method for calculating popularity of network information data, which relates to the technical field of computers and comprises the following steps of: crawling web portals with preset grade values to obtain a plurality of pieces of network information data; performing network information label classification; carrying out overall clustering when the network information event library has a plurality of network information event subsets, otherwise, carrying out incremental clustering; counting the network information quantity, the network information release time and the user behavior data in each network information event subset; sorting and assigning each piece of network information data of each network information event subset to obtain a first weight; processing to obtain the forwarded and reshipped quantity of each network information data; and carrying out weighted summation on the preset grade value, the network information label, the network informationquantity, the network information report time, the user behavior data, the first weight, the forwarded quantity and the transshipment quantity to obtain a network information data popularity value. According to the method, multiple influence factors are considered, and the network information data popularity value is more comprehensive and reasonable.
Owner:创新奇智(上海)科技有限公司
VLSI architecture and implementation for single cycle insertion of multiple records into a priority sorted list
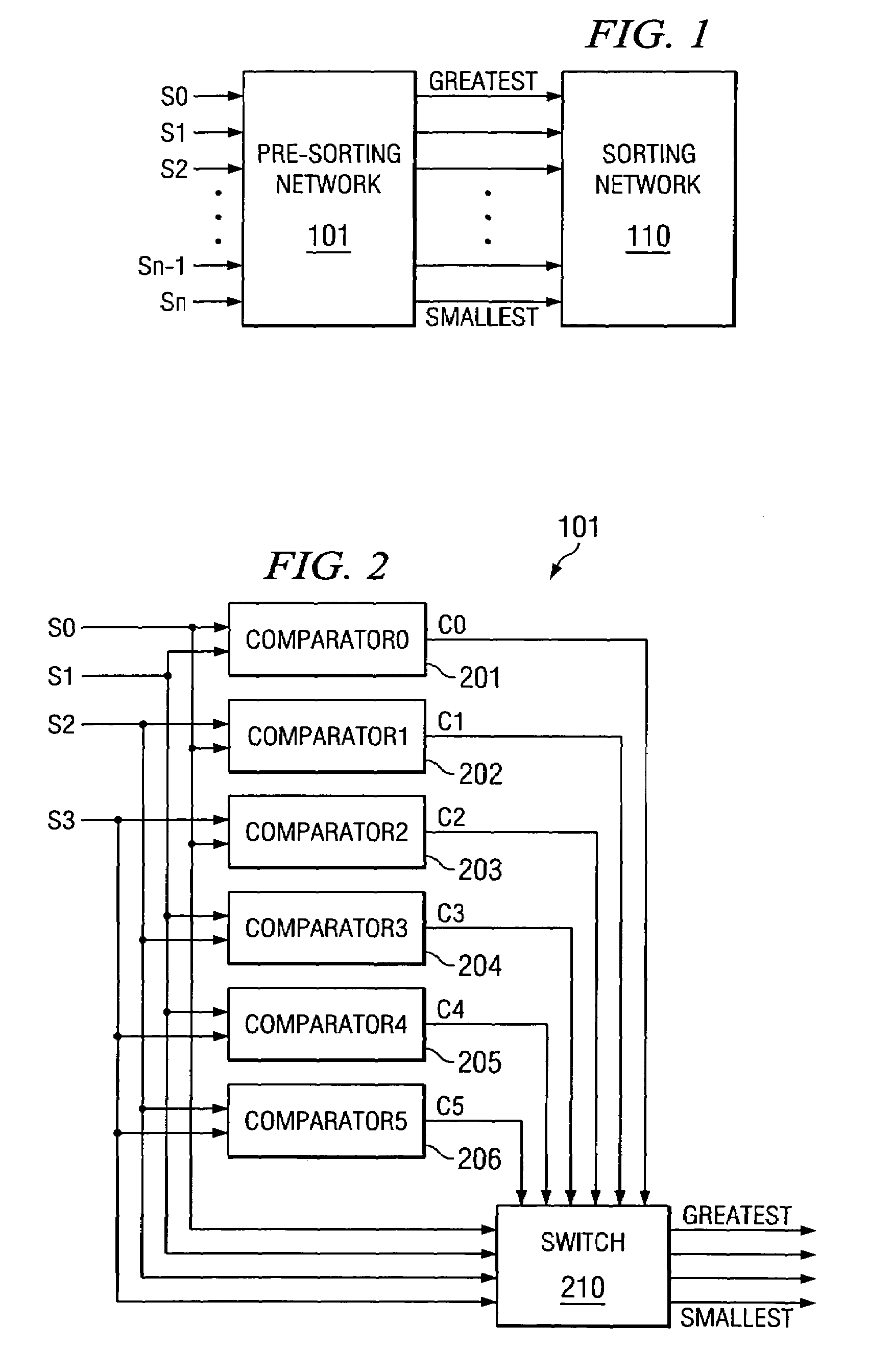
ActiveUS7281009B2Data processing applicationsVolume/mass flow measurementComputer architectureVlsi architecture
A data processing apparatus simultaneously sorts n input data words into a sorted list of m list entries. The apparatus includes a pre-sorting network sorting the n input data words and a sorting network storing up to m list entries and storing respective input data words into the m list entries. The pre-sorting network includes a set of comparators for each unique pair of input data words, and a set of n multiplexers outputting a selected one of the n input data words, and a decoder circuit controlling the multiplexers responsive to the comparisons. The sorting network includes m basic units storing current list entries ordered from greatest to least. Each cycle the basic units selecting for storage the current list entry, a current list entry of a basic units storing greater list entries or one of the input data words.
Owner:TEXAS INSTR INC
Systems and methods of data flow classification
Systems and methods of classifying data flows being communicated on a network by one or more network elements. One method includes creating a table including information of packet timestamps and pre-defined packet header fields, grouping packets into data flows based on information in the table, assigning flow identifiers to each data flow, determining a plurality of feature / characteristic sets having one or more features and / or one or more characteristics of the data flows, determining one or more classifiers to predict flow labels using the plurality of feature / characteristic sets, and generating a classification policy that includes the one or more classifiers to classify data flows on the network. The method can also include storing the classification policy in at least one non-transitory computer medium that is accessible by a network element that is classifying data flows on the network, and using the classification policy to classify data flows.
Owner:XAXAR INC
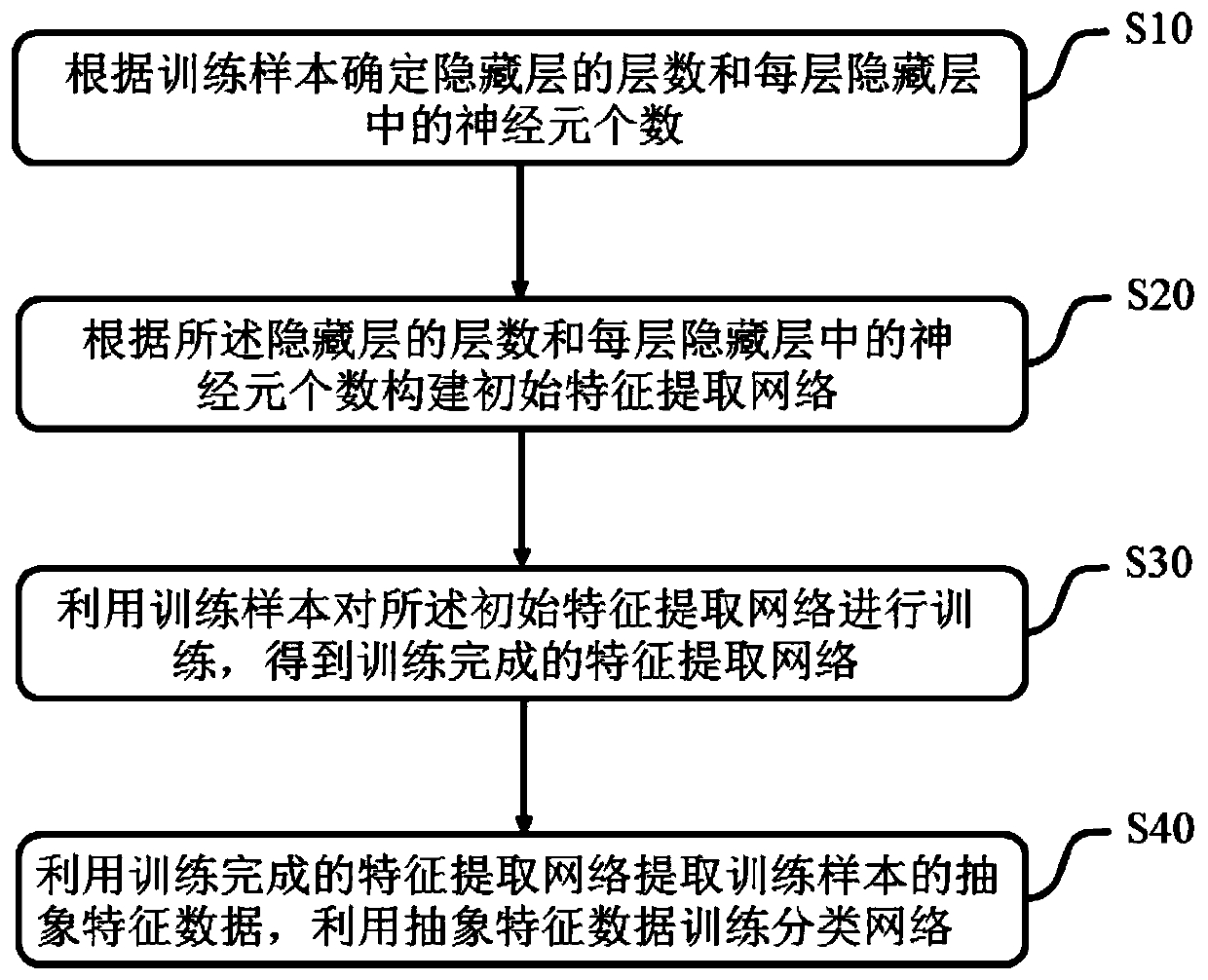
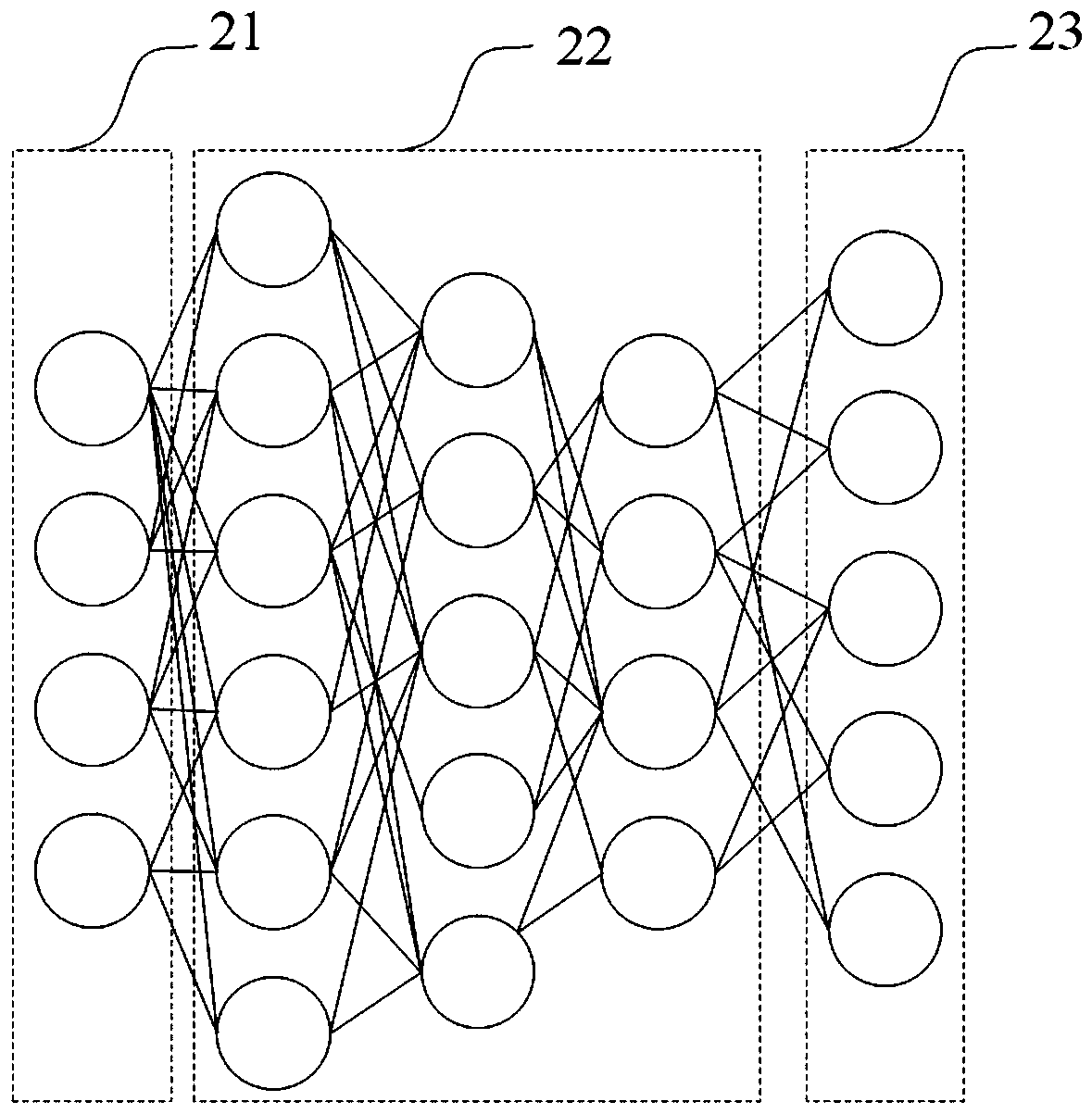
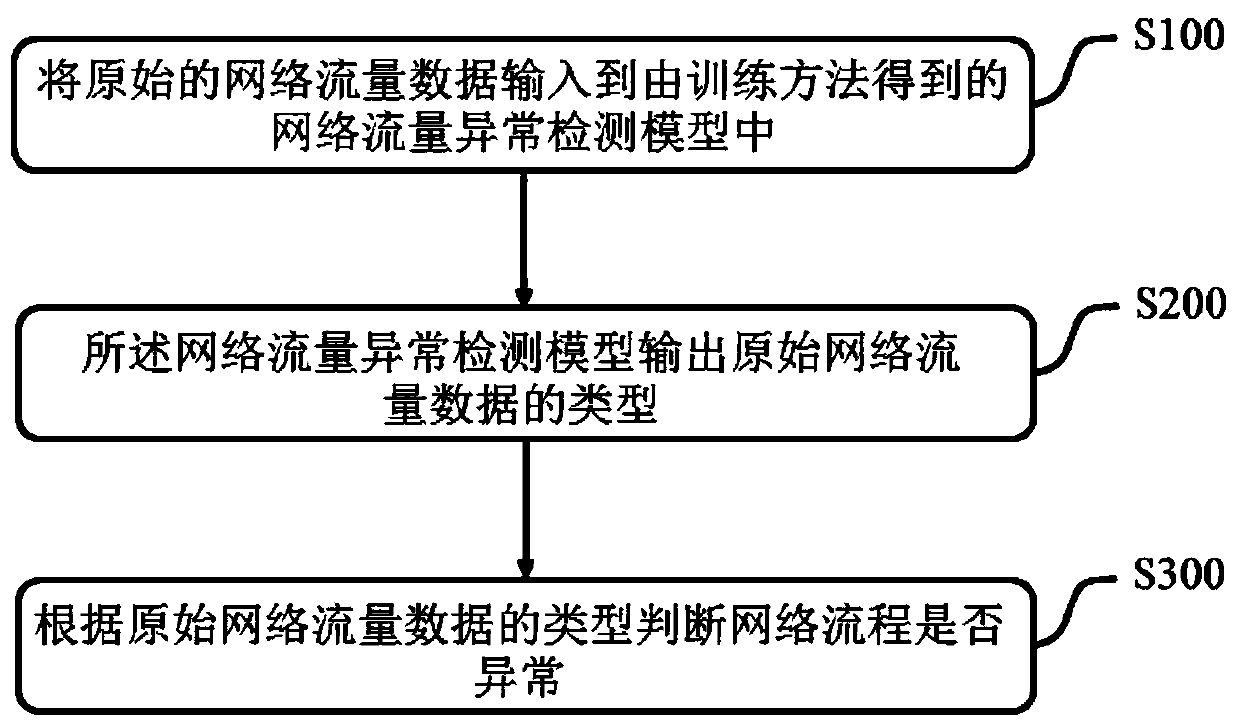
Training method and detection method of network traffic anomaly detection model
InactiveCN111064721AReduce generalization errorShorten detection timeCharacter and pattern recognitionNeural architecturesGeneralization errorHidden layer
The invention discloses a training method and a detection method of a network traffic anomaly detection model. The network traffic anomaly detection model comprises a feature extraction network and aclassification network, and the training method comprises the following steps: determining the number of hidden layers and the number of neurons in each hidden layer according to a training sample; constructing an initial feature extraction network according to the number of the hidden layers and the number of neurons in each hidden layer; training the initial feature extraction network by using atraining sample to obtain a trained feature extraction network; extracting abstract feature data of a training sample by using the trained feature extraction network, and training a classification network by using the abstract feature data so as to complete training of a network traffic detection model. The network structure can adapt to network flow data, the situation that the structure of a detection model is too complex and too simple is avoided, and therefore, generalization errors are reduced, the detection time can be obviously shortened, and the detection accuracy can be obviously improved.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
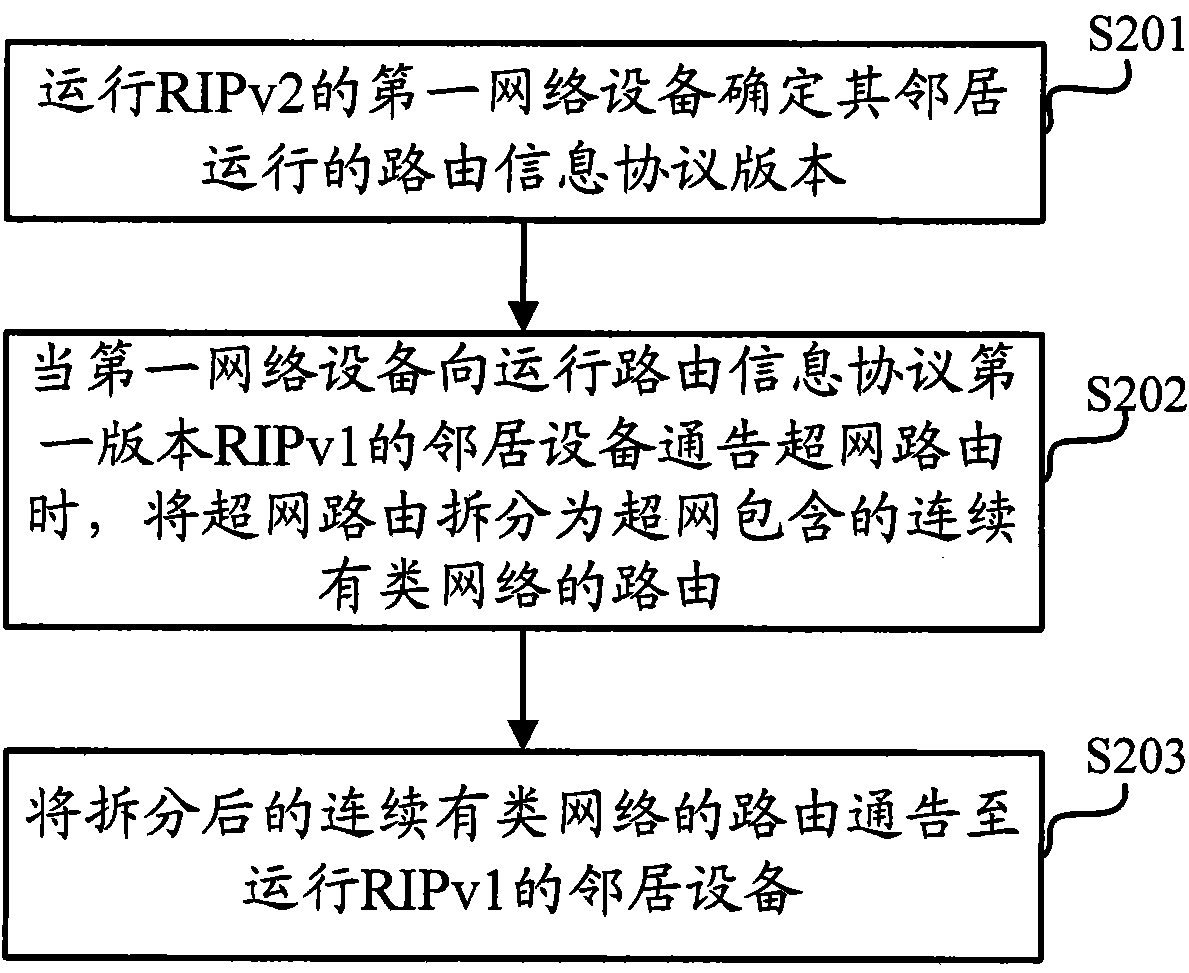
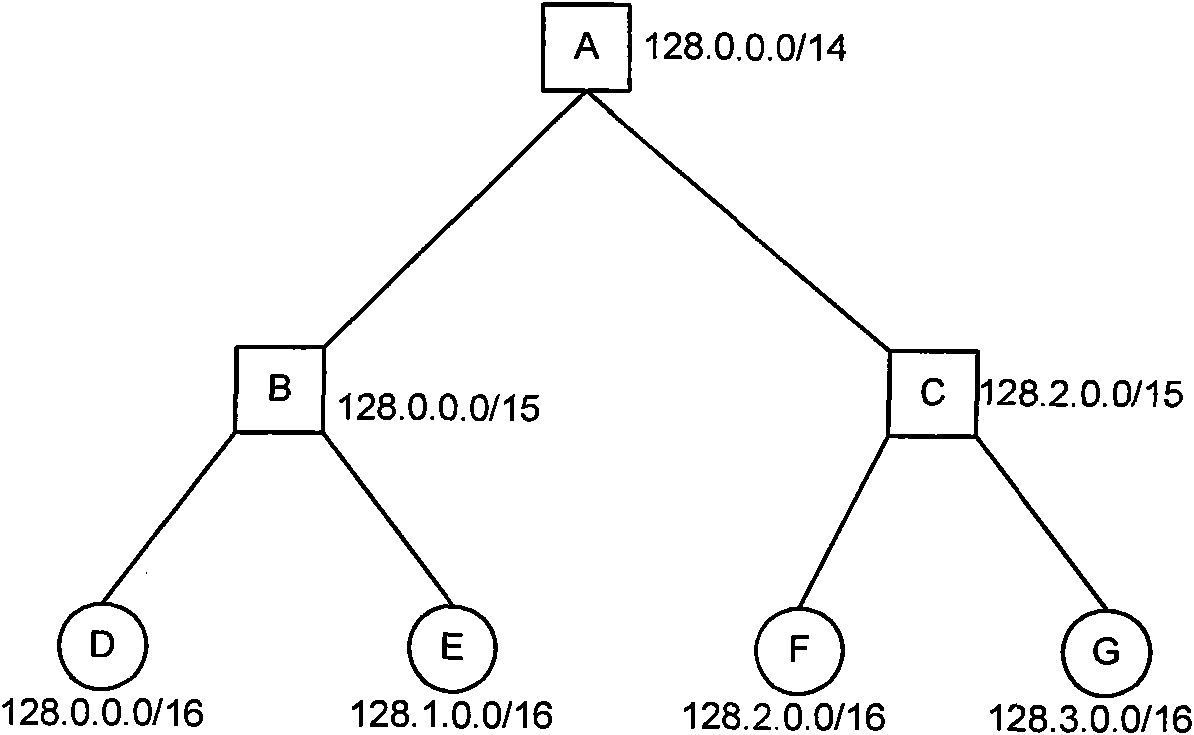
Route advertising method and network equipment
ActiveCN101789930AAvoid routing black holesData switching networksRouting Information ProtocolComputer science
The invention discloses a route advertising method and network equipment, wherein the method comprises the following steps: determining route information protocol versions run by all neighborhood equipment by first network equipment running a second version RIPv2 (Routing Information Protocol version 2) of a route information protocol; and splitting a hypernet route into continuous routes of classful networks contained in a hypernet and advertising the split continuous routes of the classful networks to the neighborhood equipment running RIPv1 (Routing Information Protocol version 1) through the first network equipment when the first network equipment advertises the hypenet routes to the neighborhood equipment running the RIPv1 (Routing Information Protocol version 1) of the route information protocol. The invention can ensure that equipment running the RIPv1 (Routing Information Protocol version 1) can correctly learn all continuous routes of the classful networks contained in the hypernet in a network running the RIPv1 protocol and the RIPv2 protocol, thereby avoiding the problem of route black hole.
Owner:BEIJING ZHIGU TECH SERVICE
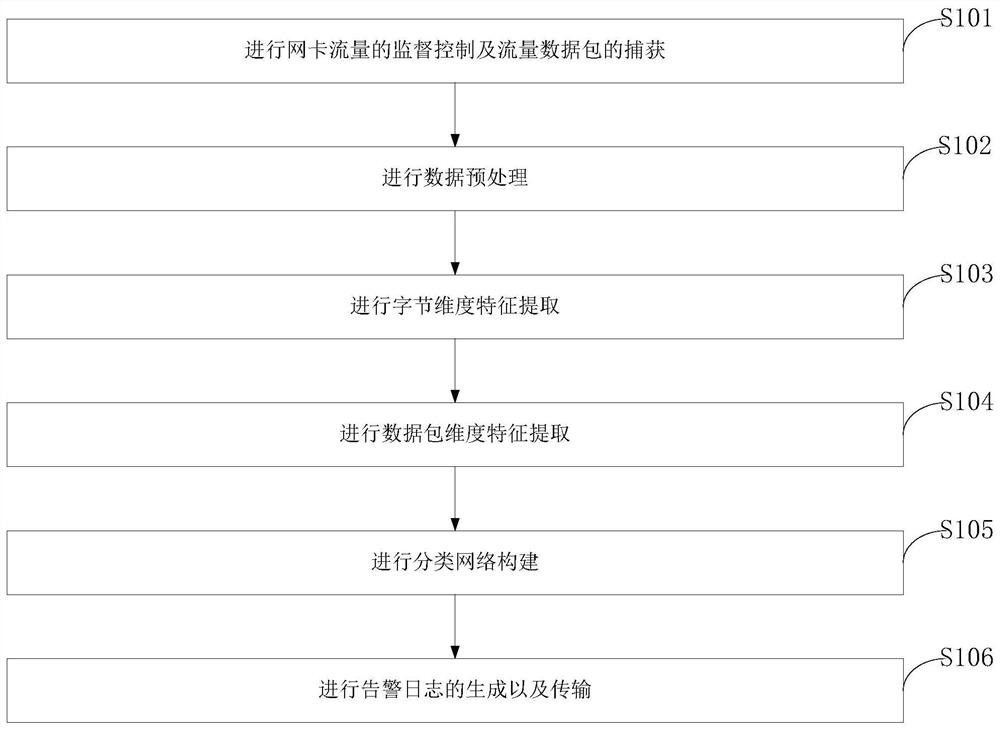
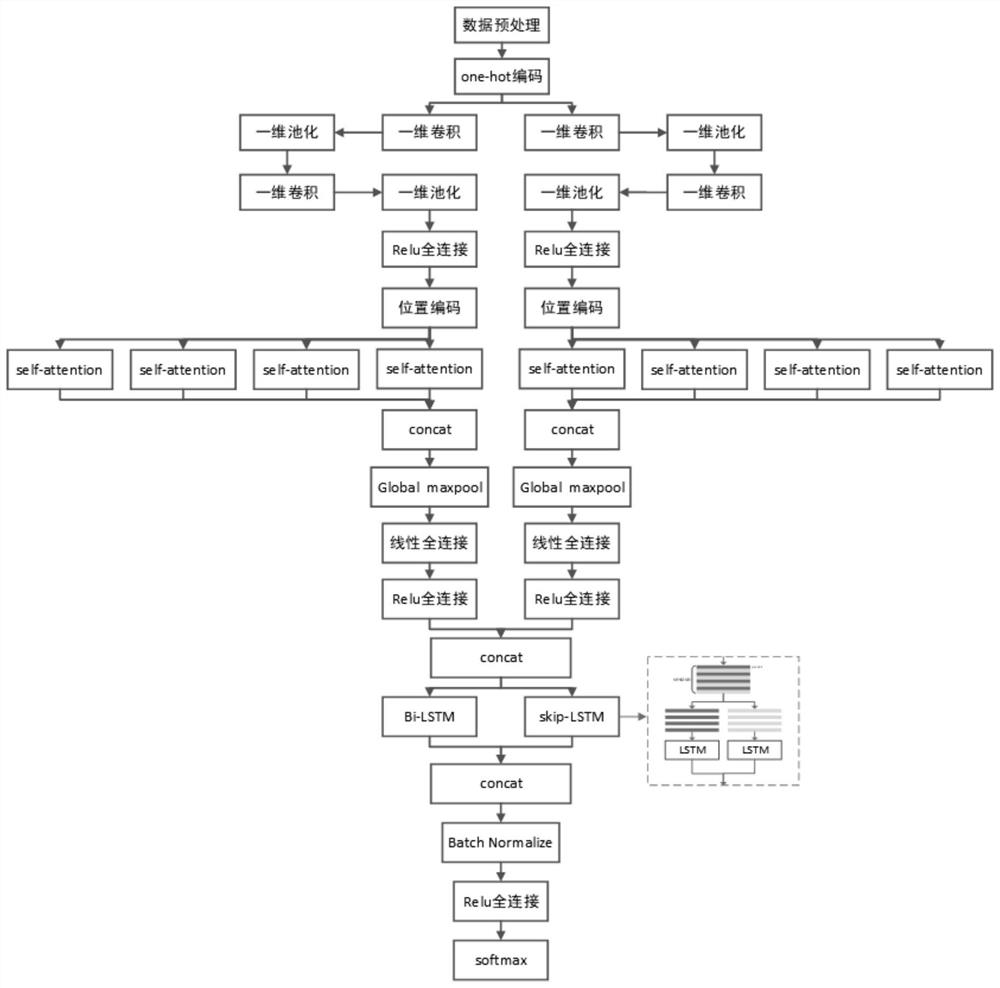
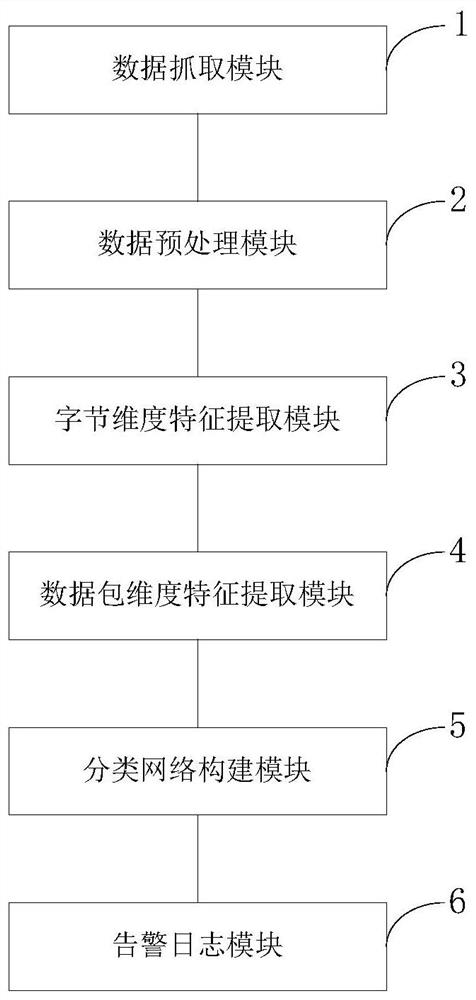
Encrypted malicious traffic detection method, detection system and computer equipment
ActiveCN113472809AStrong generalizationImprove classification effectNeural architecturesTransmissionData packAttack
The invention belongs to the technical field of malicious traffic detection, and discloses an encrypted malicious traffic detection method, a detection system and computer equipment, wherein the method comprises the steps of: supervising and controlling network card traffic and capturing traffic data packets; performing data preprocessing; carrying out byte dimension feature extraction; carrying out data packet dimension feature extraction; constructing a classification network; and generating and transmitting an alarm log. The invention provides a C&C encrypted malicious traffic detection method, and particularly relates to a deep learning detection model for C&C encrypted malicious traffic. The C&C traffic is traffic which utilizes an encryption technology and a multi-stage attack mode at the same time. The model has good generalization performance, and attack instructions outside a training set can be detected. The model has good classification performance, and malicious traffic types with high similarity can be distinguished.
Owner:HUAZHONG UNIV OF SCI & TECH
Multi-model fusion training method and device and text classification method and device
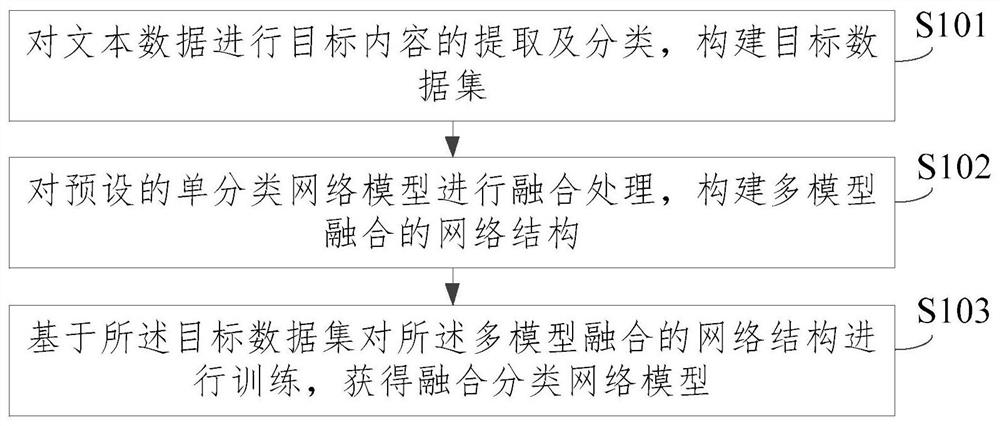
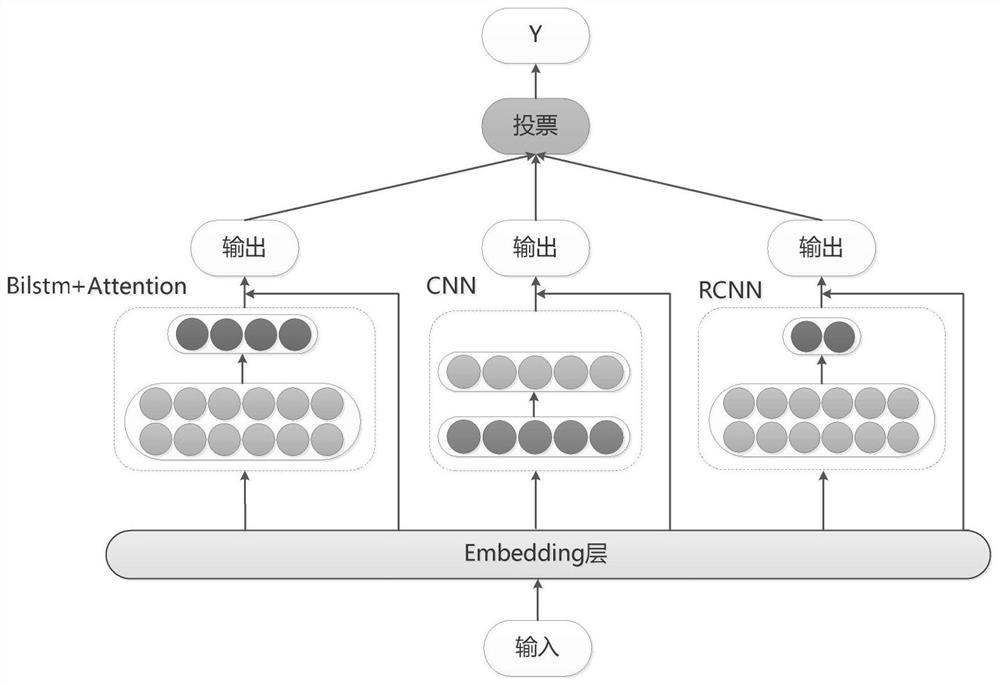
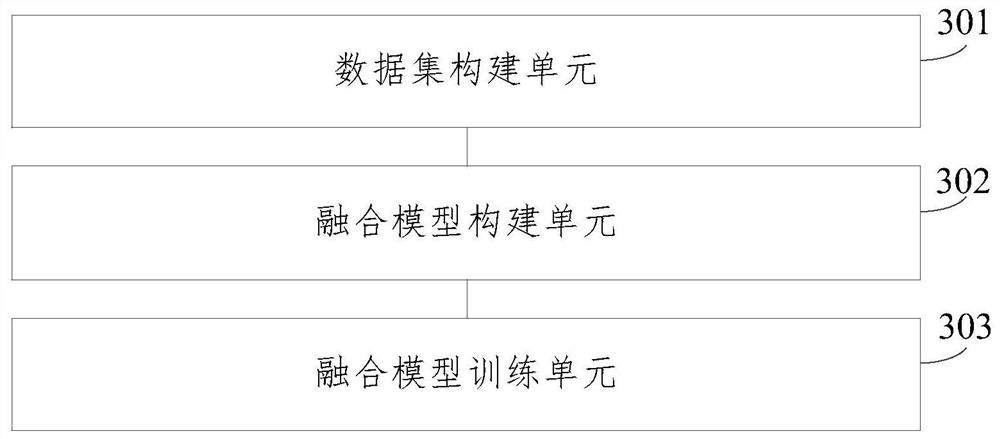
InactiveCN112329824AImprove training efficiencyImprove recognition accuracySemantic analysisCharacter and pattern recognitionData setClassification methods
The embodiment of the invention provides a multi-model fusion training method and a text classification method and device. The multi-model fusion training method comprises the steps: performing targetcontent extraction and classification on text data, and constructing a target data set; performing fusion processing on a preset single classification network model, and constructing a multi-model fusion network structure; and training the multi-model fusion network structure based on the target data set to obtain a fusion classification network model. According to the multi-model fusion trainingmethod disclosed by the embodiment of the invention, the single classification network model can be fused with the learning ability of other models, and the generalization ability of the single classification network model is improved, so that the training efficiency and the recognition accuracy of the model are effectively improved.
Owner:北京中科智加科技有限公司
Method for classifying the traffic dynamism of a network communication using a network that contains pulsed neurons, neuronal network and system for carrying out said method
InactiveUS20050105463A1Reliable classificationClear computing effortError preventionFrequency-division multiplex detailsTraffic capacityNerve network
A method classifies the traffic dynamism of a network communication using a network that contains pulsed neurons. Traffic data of the network communication are used as the input variables of the neuronal network. Temporal clusters obtained by processing the pulses are used as the output variables of the neuronal network. The traffic dynamism is classified by a synaptic model whose dynamism depends directly on the exact clocking of pre- or post-synaptic pulses.
Owner:SIEMENS AG
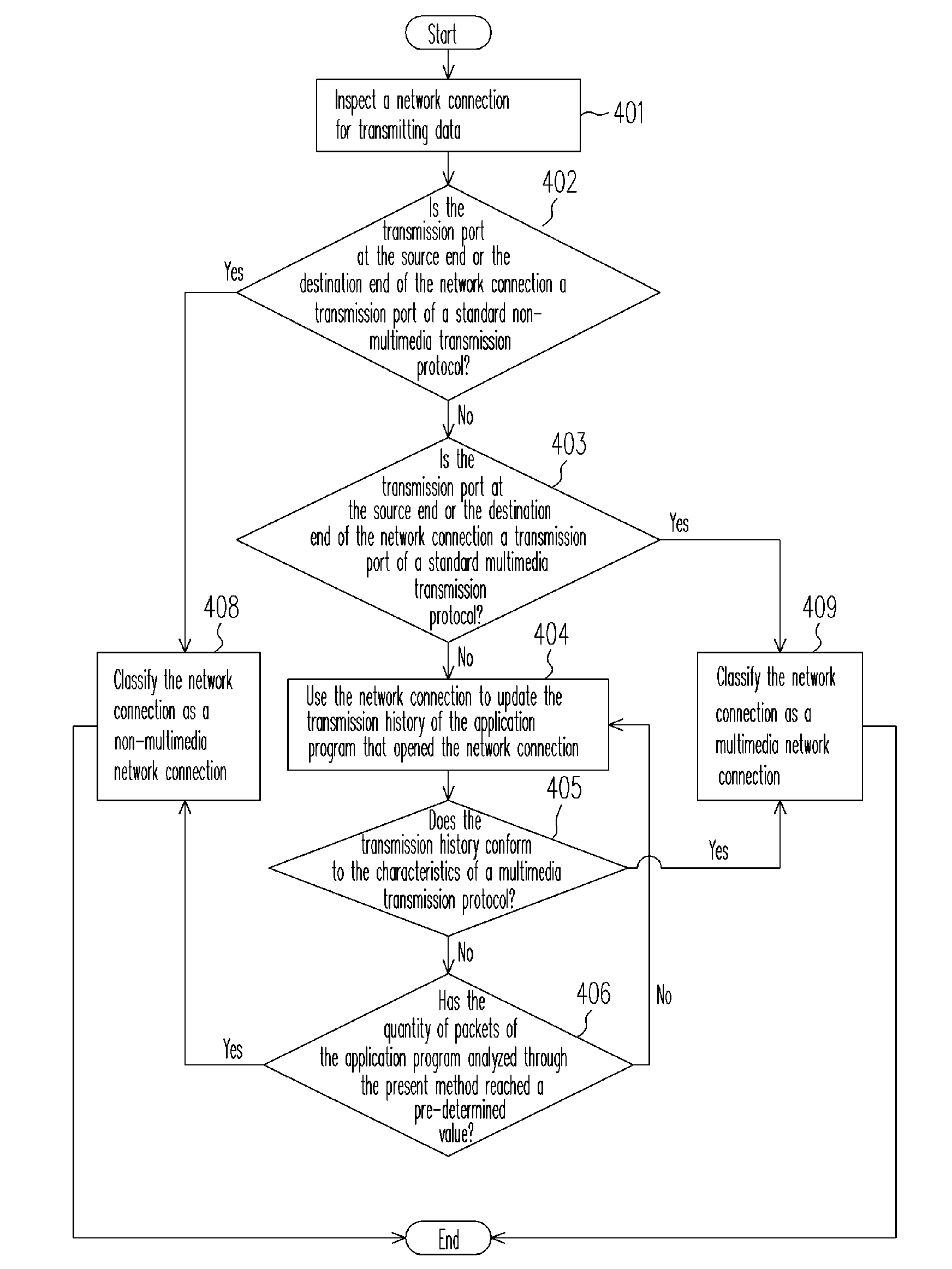
Method for classifying network connections and transmitting multimedia data
InactiveUS7516233B2Save transmission bandwidthImprove transmission efficiencyError preventionFrequency-division multiplex detailsNetwork connectionNetwork packet
A data transmission method for classifying network connections and transmitting multimedia data is described. After distinguishing multimedia connections from non-multimedia connects, multimedia packets are classified and consolidated into packet groups and then the packet groups are transmitted. The method for transmitting multimedia data comprises the following steps. First, determine whether a connection is used for transmitting multimedia data or not. If it does, the packets are consolidated into a packet group. Finally, forward the packet group according to a predetermined order after the packet group is assembled.
Owner:COMPAL ELECTRONICS INC
Method and apparatus for the discrimination and storage of application specific network protocol data from generic network protocol data
Discrimination of application specific network traffic from other from general or unclassified network traffic is provided. Users may specify particular applications or data strings to be monitored.
Owner:JOHN FLUKE MFG CO INC
Data processing method and related device
The embodiment of the invention discloses a data processing method, which is applied to the field of artificial intelligence, and comprises the steps of obtaining a to-be-compressed network and a plurality of pieces of data, with the to-be-compressed network being a classification network; inputting the plurality of data into the to-be-compressed network to obtain a plurality of first output results, with the plurality of first output results being in one-to-one correspondence with the plurality of data; determining a one-hot one hot label corresponding to each first output result in the plurality of first output results; respectively determining a first similarity between each first output result in the plurality of first output results and the one-hot label; and according to the first similarity corresponding to each first output result in the plurality of first output results, determining at least one piece of target data in the plurality of pieces of data, with the at least one piece of target data being used for compressing the to-be-compressed network. Through the method, a large amount of data similar to the original training data of the to-be-compressed network can be obtained, and therefore it is guaranteed that network compression can be effectively achieved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com