Internet of Things protocol security automatic analysis method and system based on formal verification
A protocol security and formal verification technology, which is applied in the field of automatic analysis of IoT protocol security based on formal verification, can solve the problems that the correctness of protocol security cannot be determined, cannot be extended, and the interaction of IoT protocols is complex. The effect of realizing systematic safety analysis and reducing manual burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be noted that the following embodiments are intended to facilitate the understanding of the present invention, but do not limit it in any way.
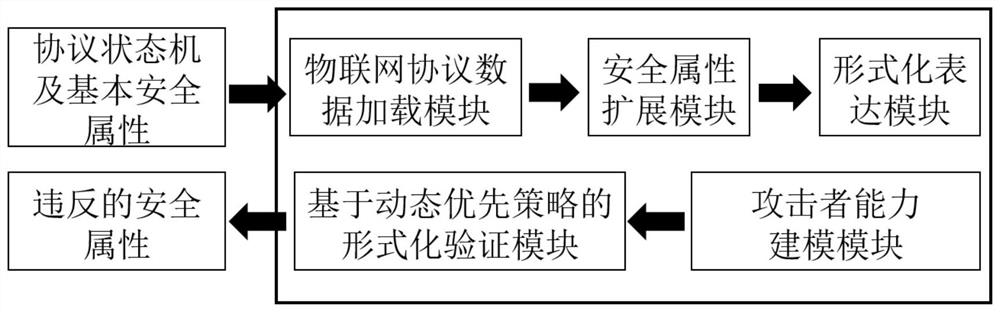
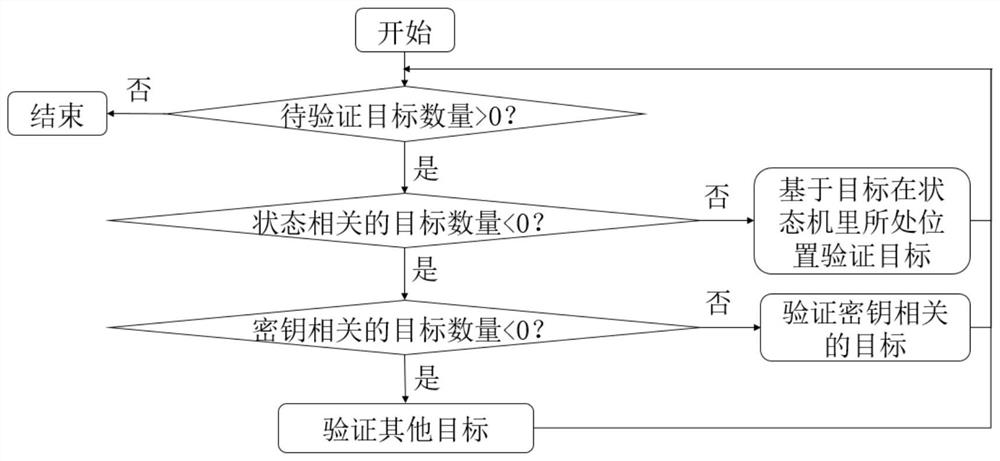
[0055] The present invention provides a method and system for automatic analysis of Internet of Things protocol security based on formal verification, which needs to be analyzed based on the protocol state machine and basic security attributes, wherein the protocol state machine can be automatically extracted through model learning and other methods , the basic security attributes are extracted through the protocol specifications summarized by researchers, and each protocol only needs to be extracted once. The method and system can automatically formalize the state machines of different protocols on multiple platforms, extend protocol security attributes, apply an attacker model, and implement fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com