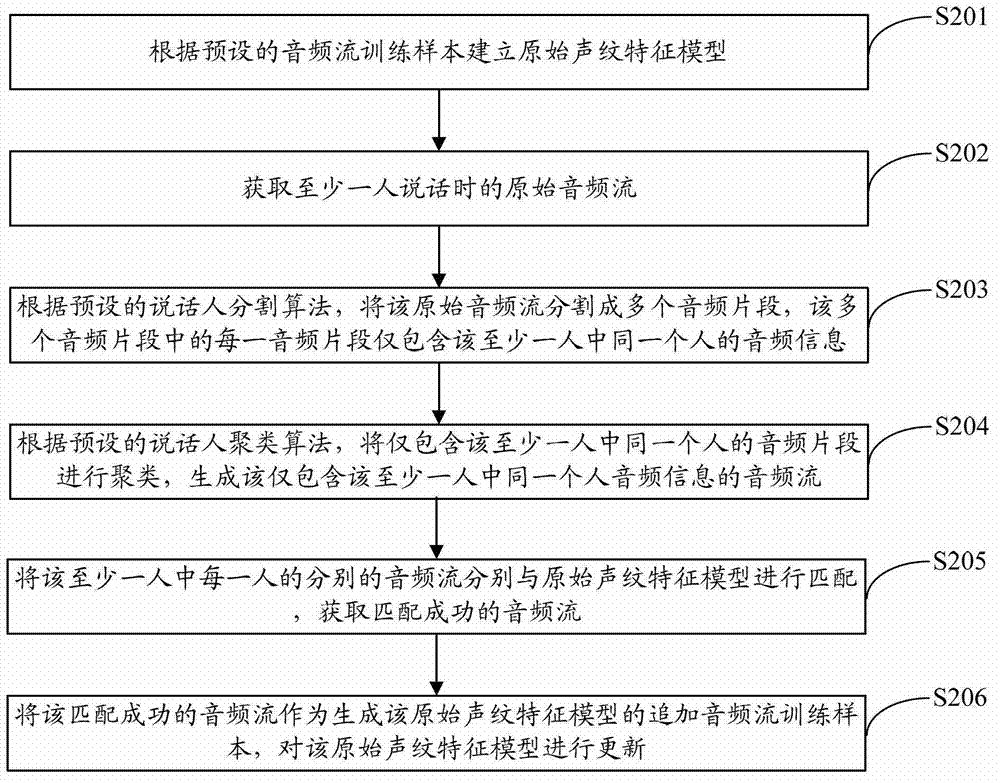
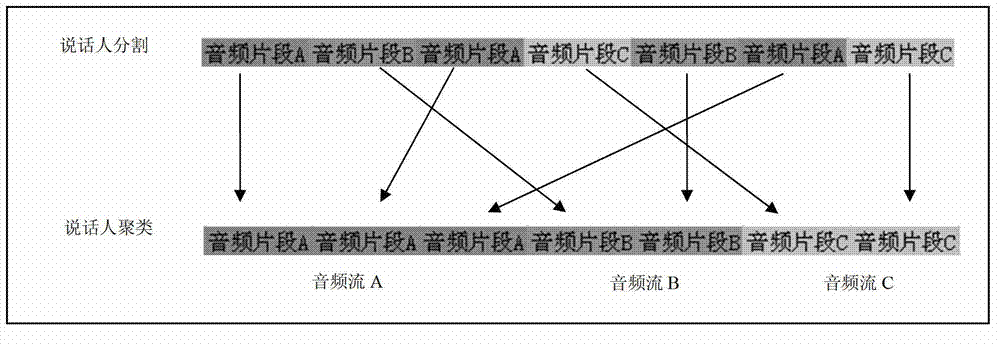
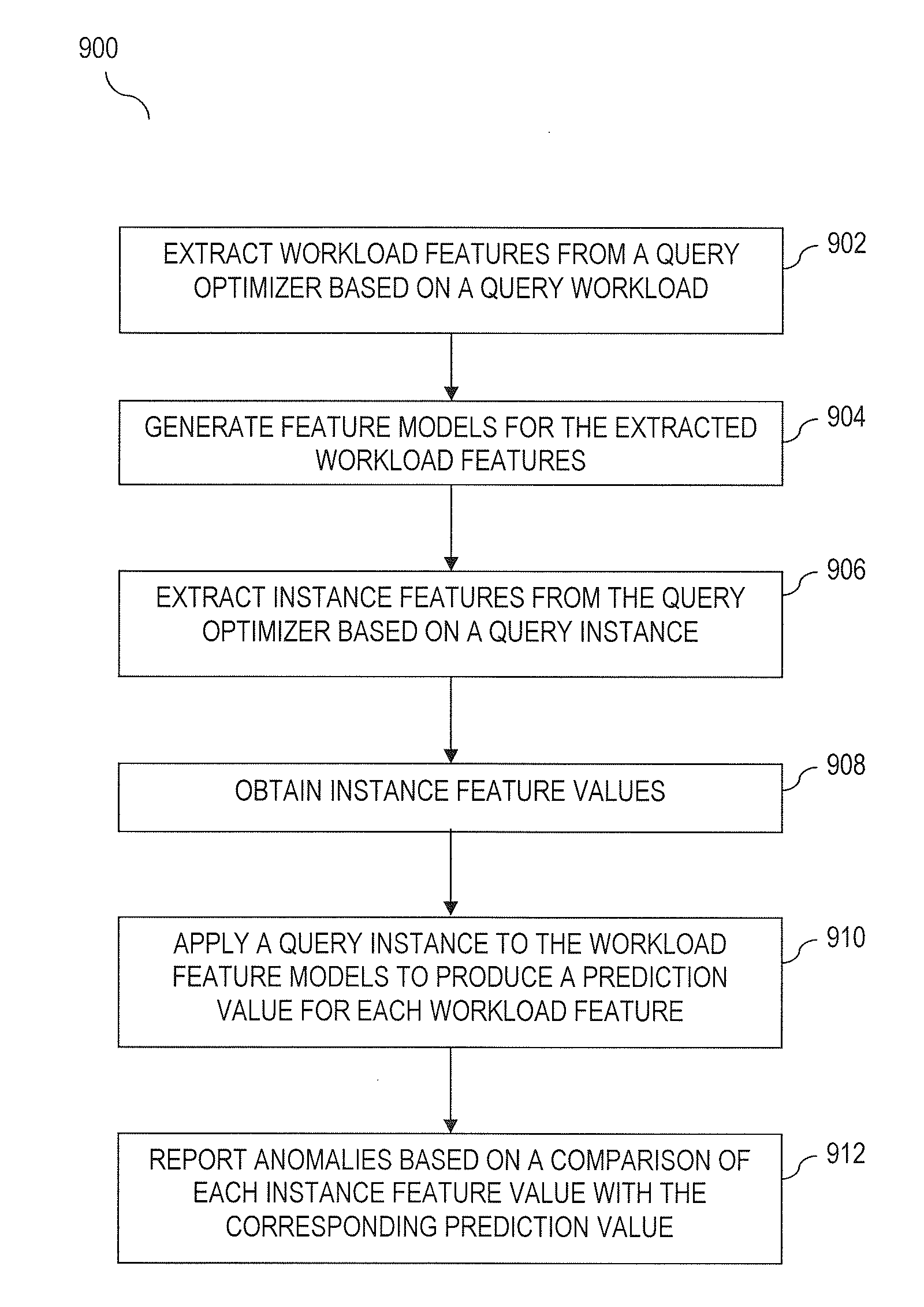
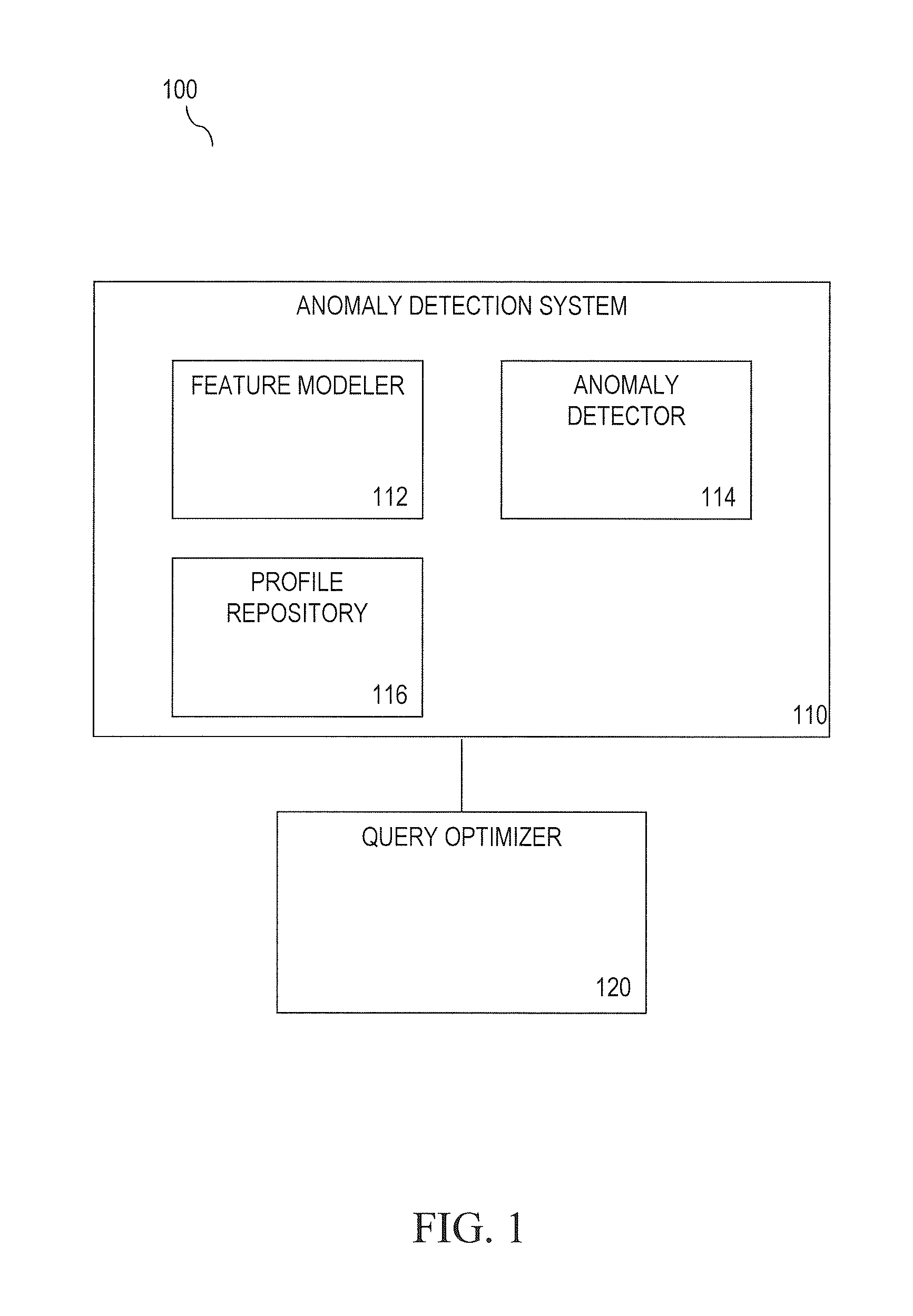
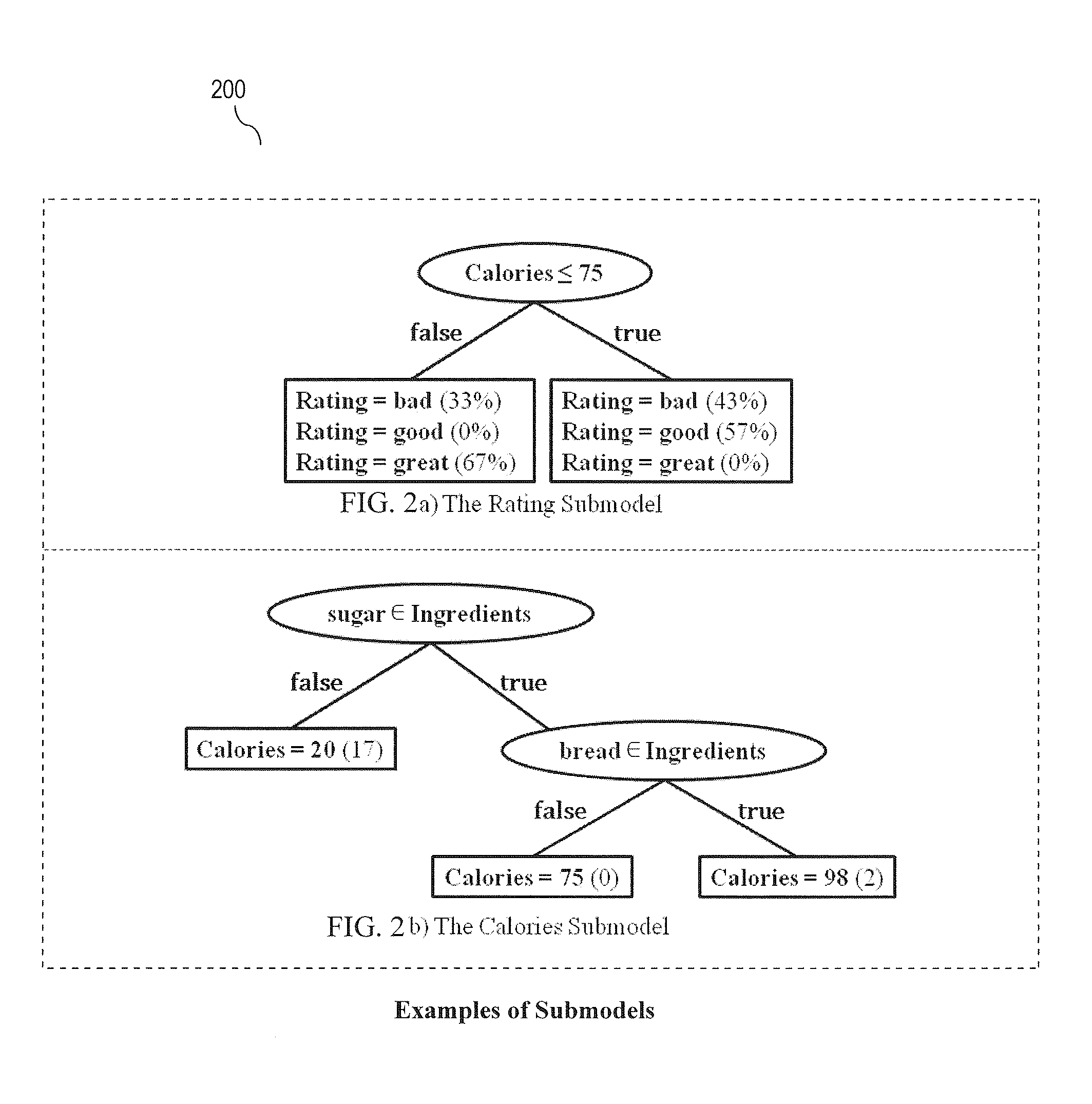
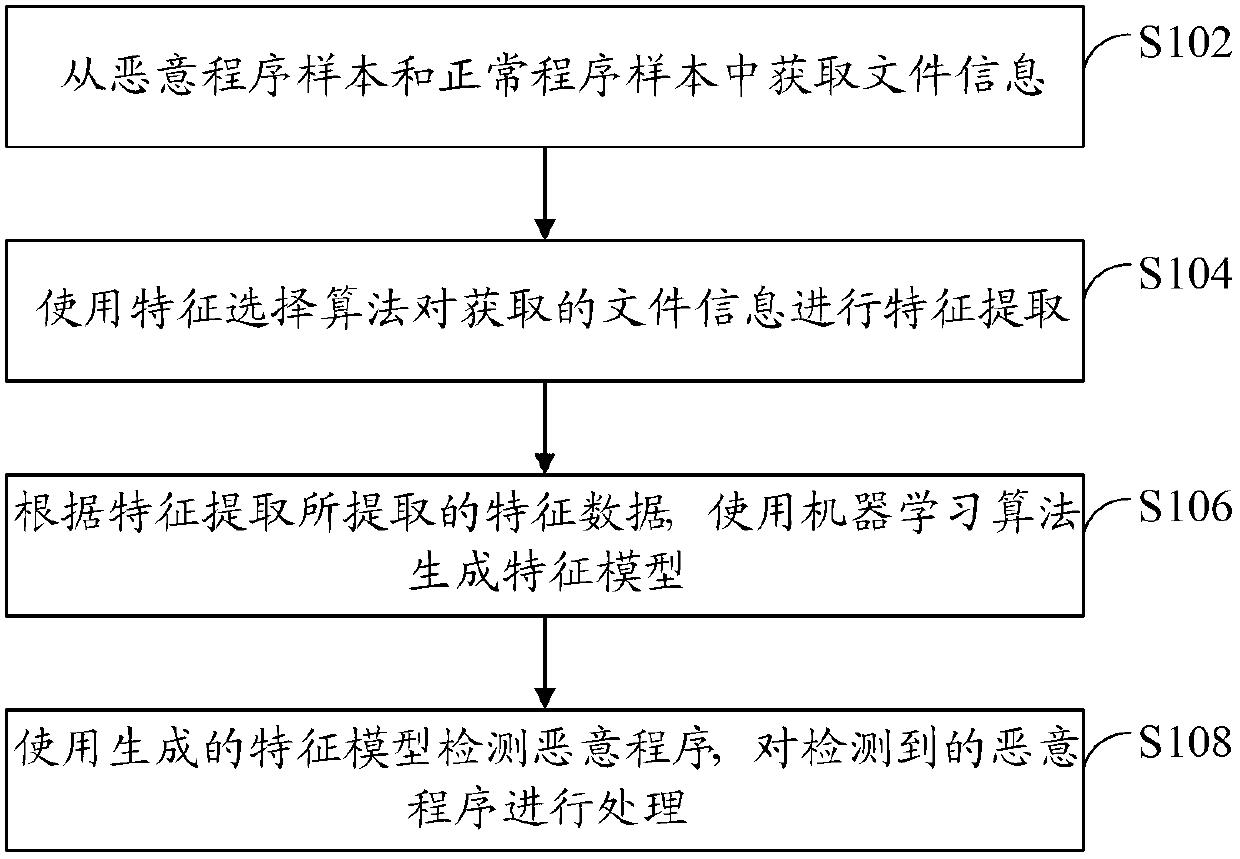
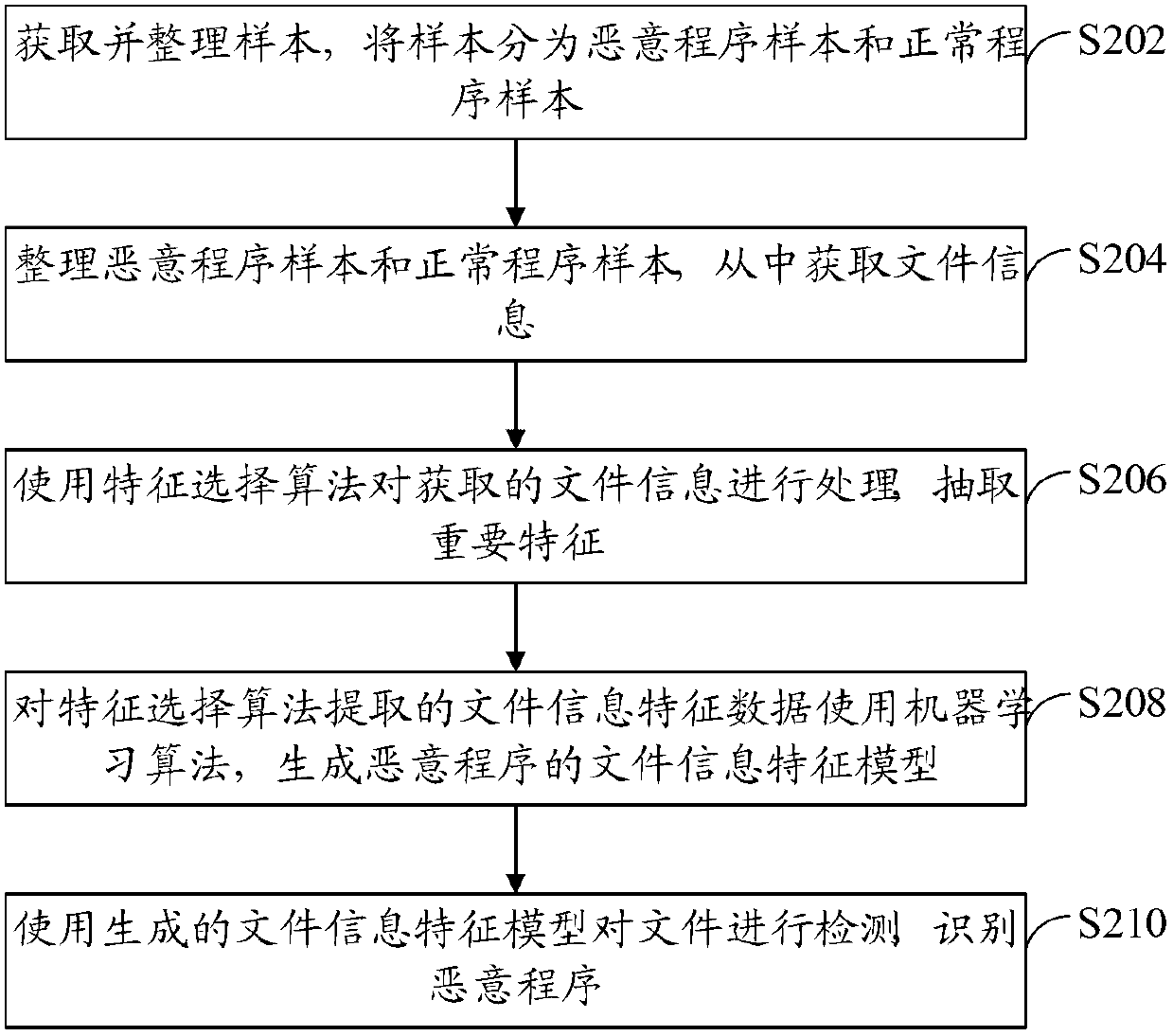
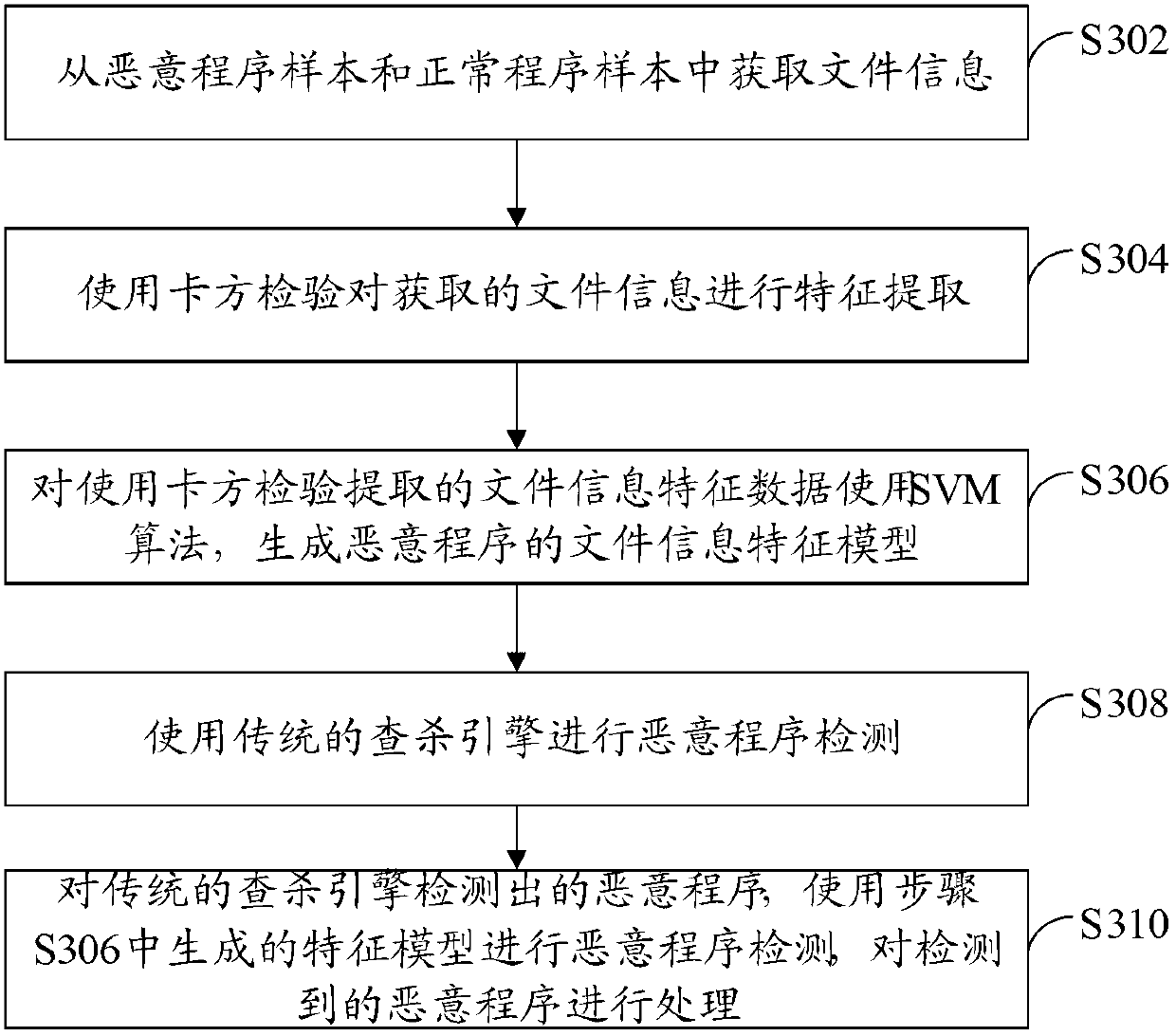
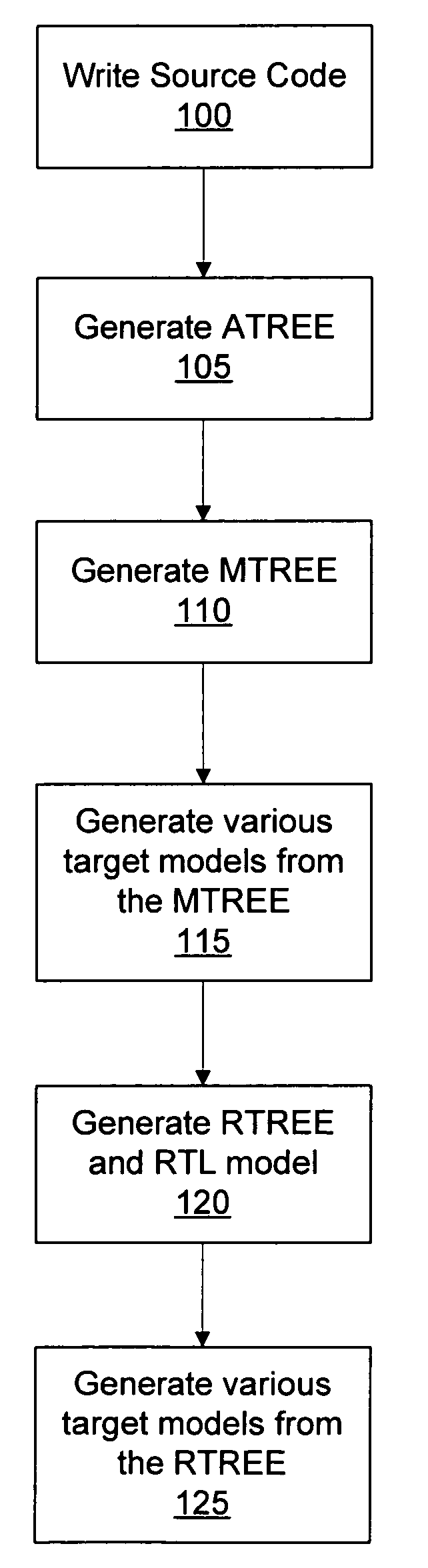
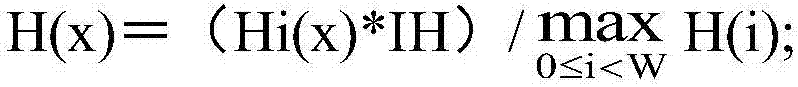Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
638 results about "Feature model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In software development, a feature model is a compact representation of all the products of the Software Product Line (SPL) in terms of "features". Feature models are visually represented by means of feature diagrams. Feature models are widely used during the whole product line development process and are commonly used as input to produce other assets such as documents, architecture definition, or pieces of code.
Software fault management system
InactiveUS6012152ASupervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsInformation repositoryManagement information systems
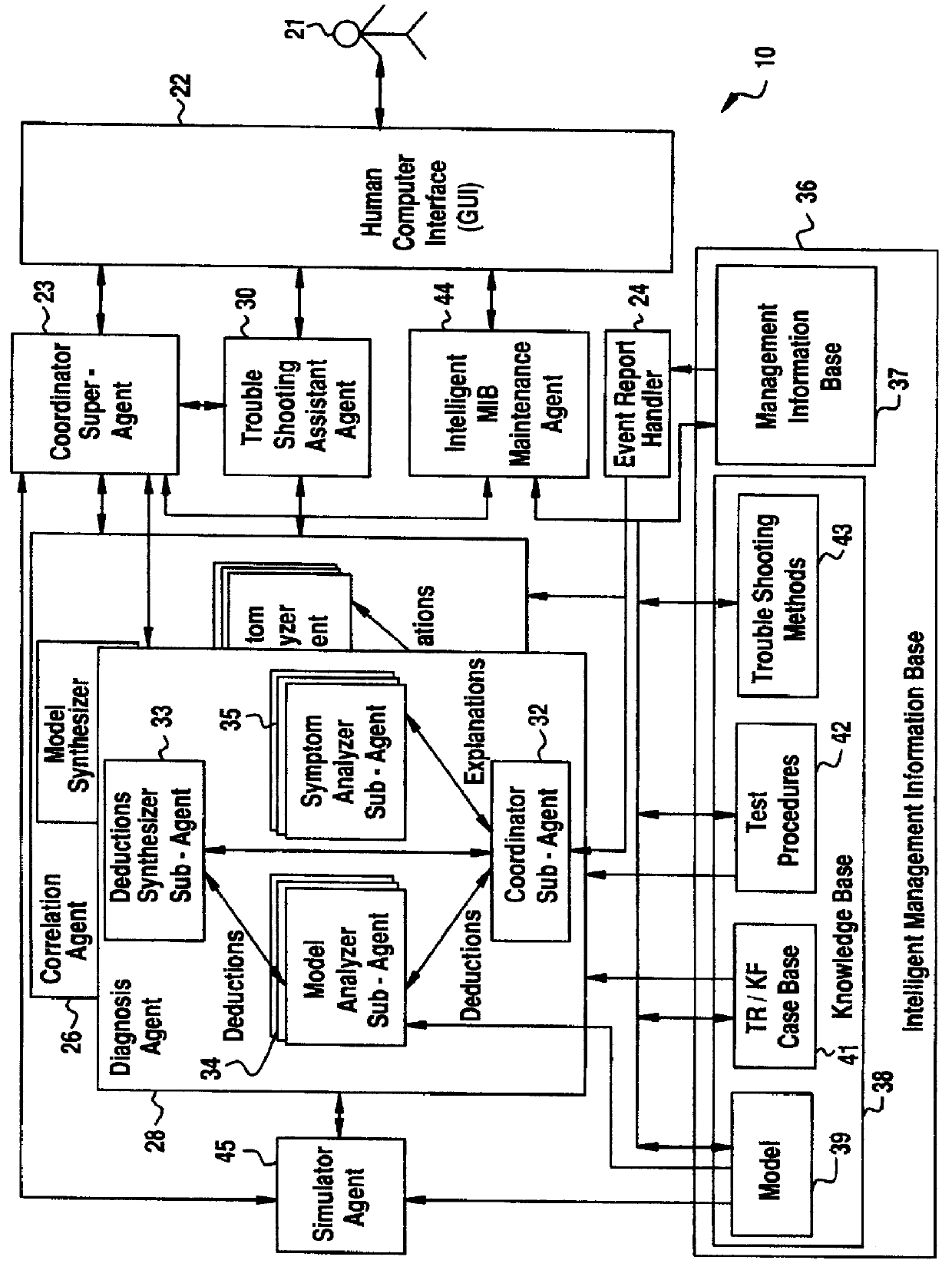
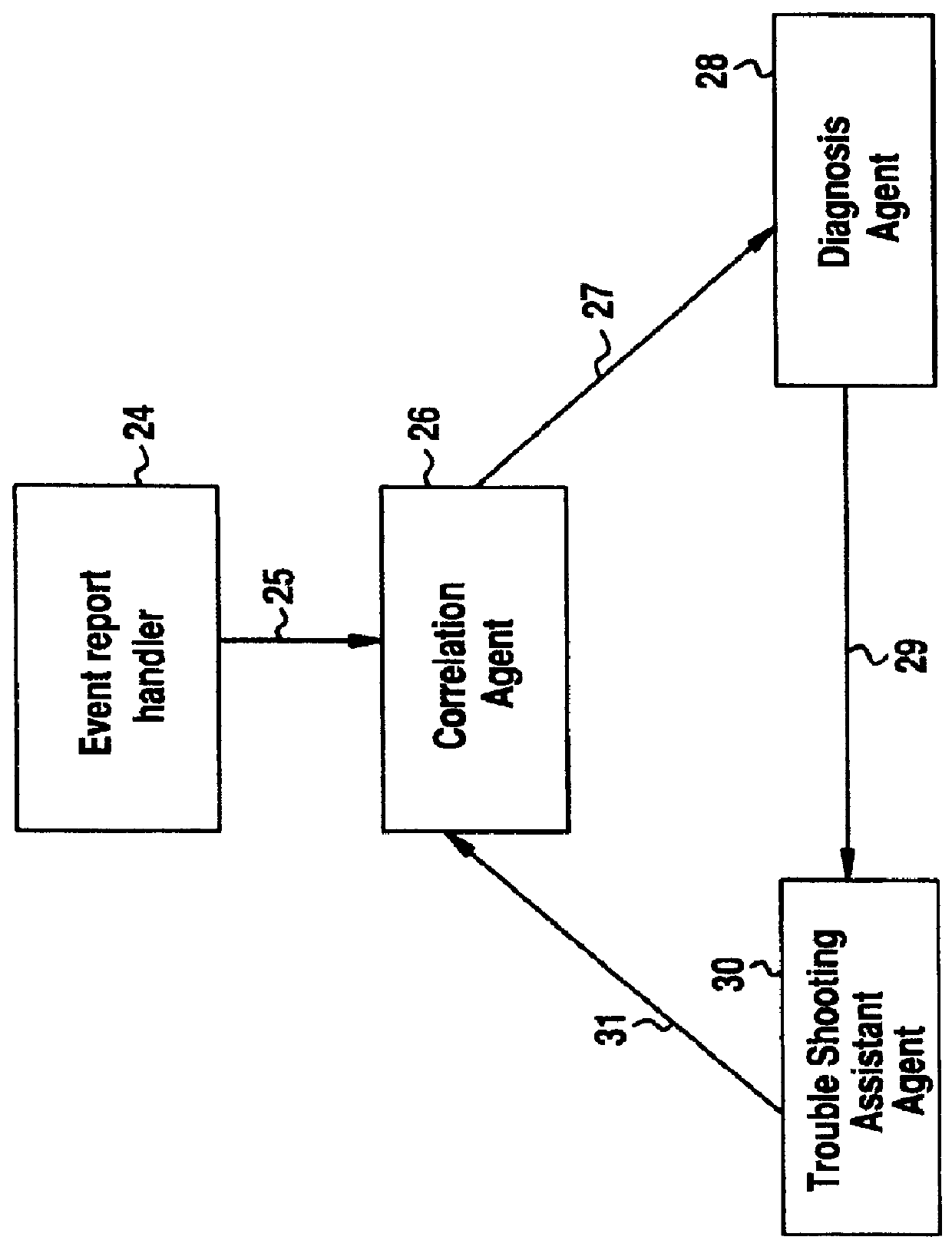
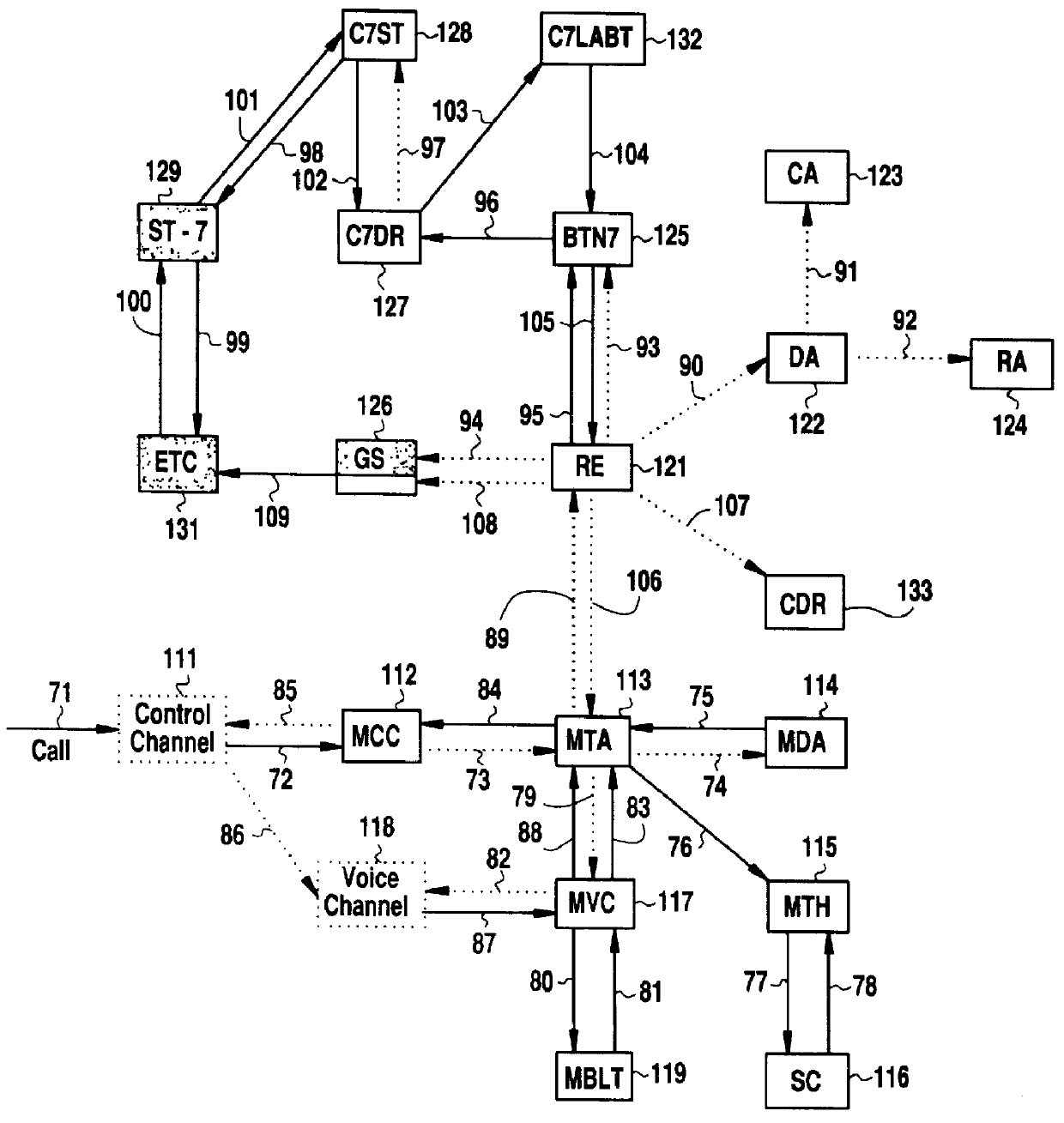
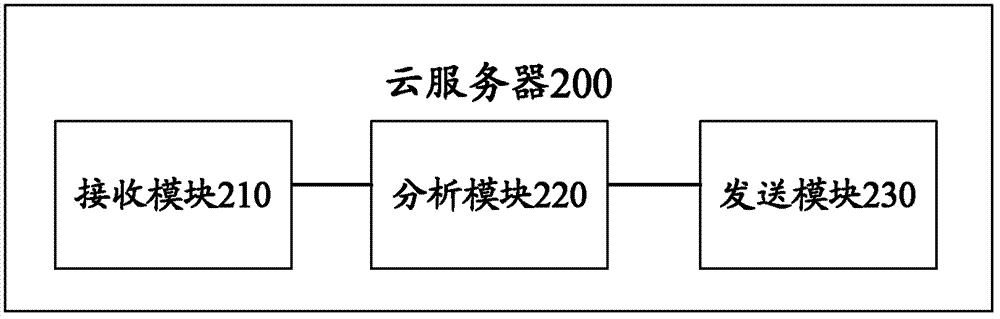
A Software Fault Management (SFM) system for managing software faults in a managed mobile telecommunications network. The SFM system includes an Intelligent Management Information Base (I-MIB) comprising a Management Information Base (MIB) and a Knowledge Base (KB) having a functional model of the managed network and a trouble report / known faults (TR / KF) case base. The SFM system also includes an intelligent multi-agent portion having a plurality of agents which process the software faults utilizing the functional model from the I-MIB, case-based information, and other management information. The I-MIB and the intelligent multi-agent portion are compliant with Telecomunications Management Network (TMN) principles and framework. Fault management is both proactive and reactive. The SFM system is made independent of technology-specific implementations by representing the underlying switch design knowledge in a modular and changeable form which is then interpreted by the intelligent multi-agent portion. A clear separation is maintained between the generic procedural inference mechanisms and agents, and the specific and explicit models of the different network elements of a mobile telecommunications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
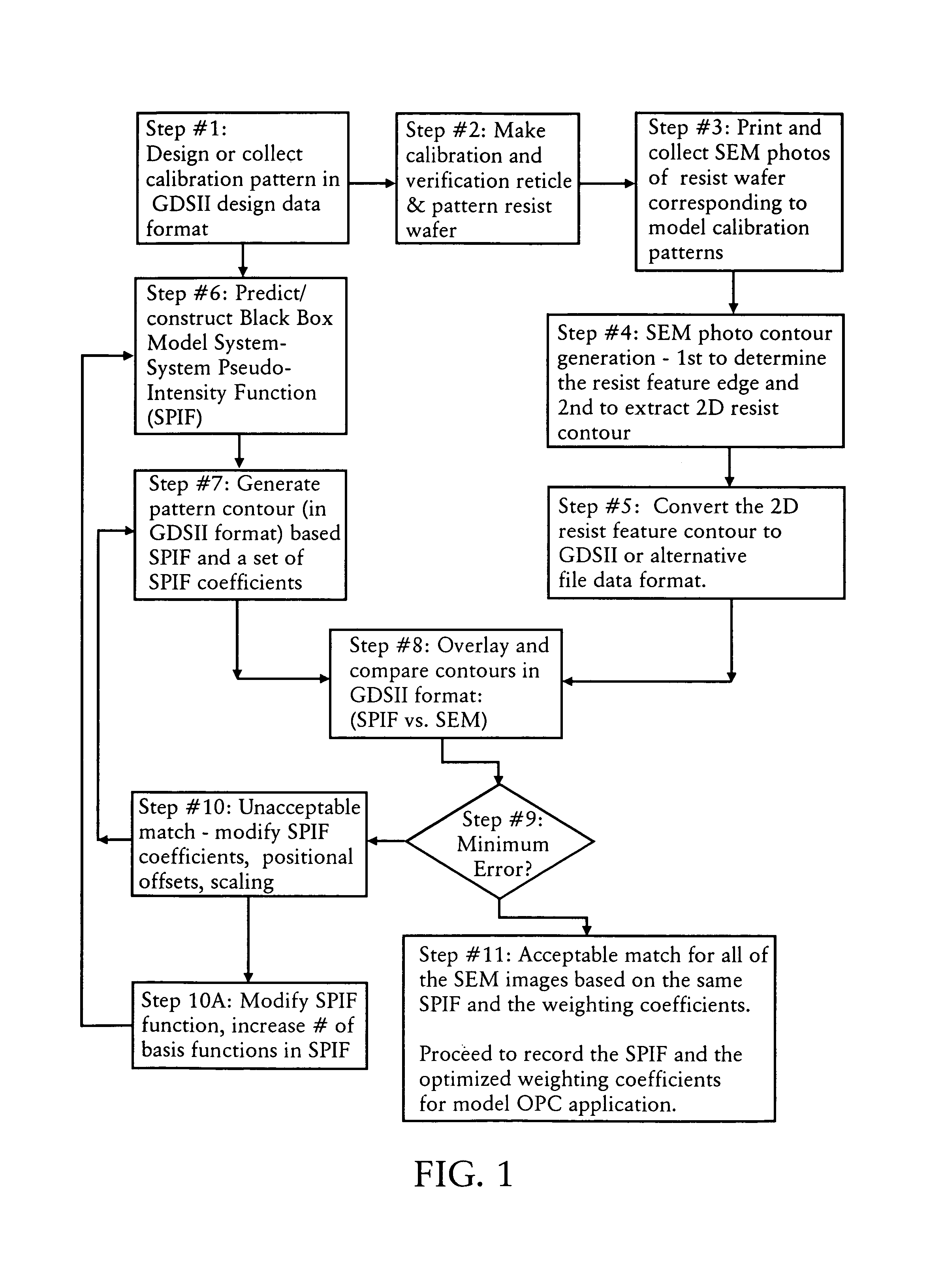
Method of two dimensional feature model calibration and optimization
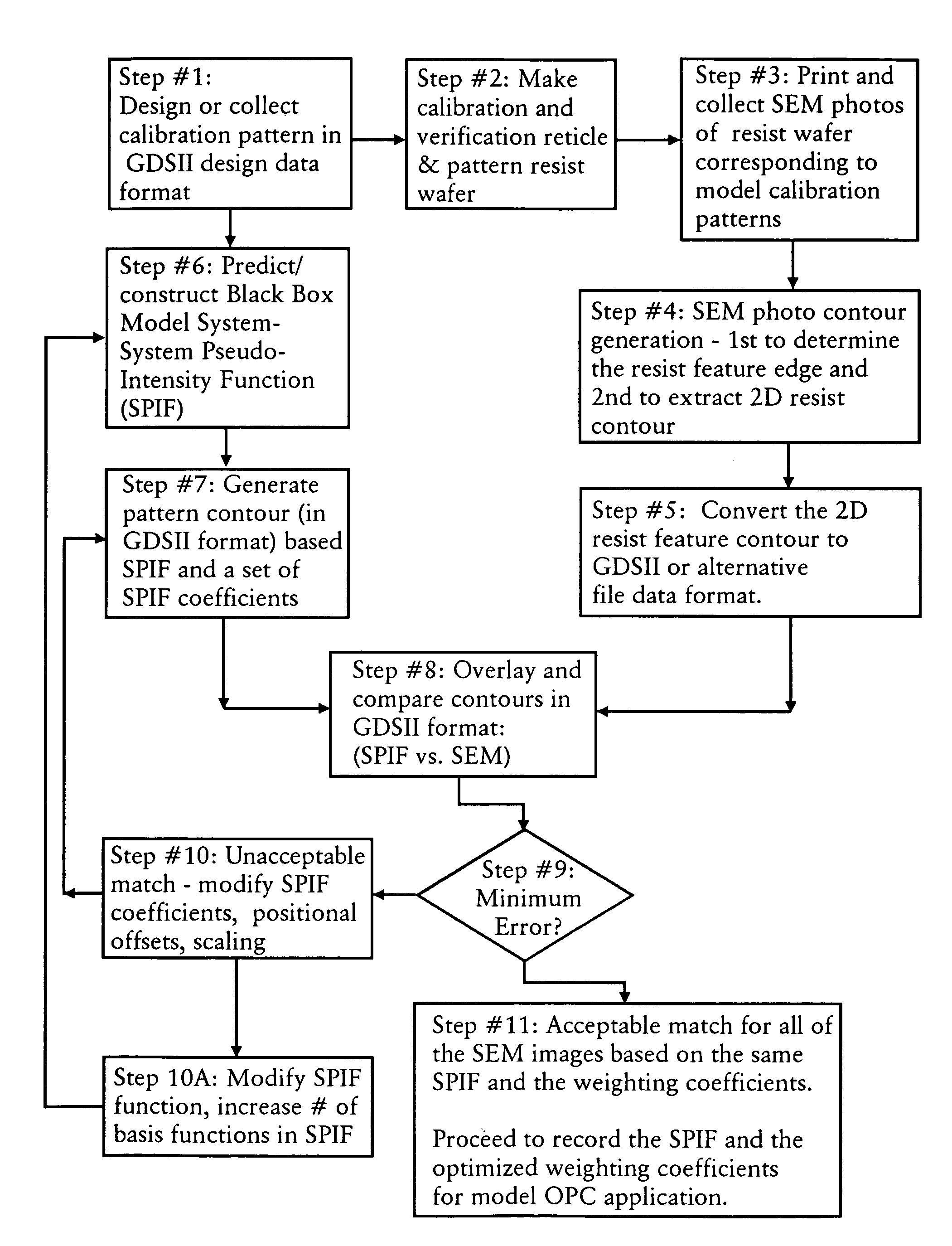
InactiveUS7175940B2Minimize proximity effectAccurate performanceSemiconductor/solid-state device manufacturingCharacter and pattern recognitionPattern recognitionData format
A method for generating a photolithography mask for optically transferring a pattern formed in the mask onto a substrate utilizing an imaging system. The method includes the steps of: (a) defining a set of calibration patterns, which are represented in a data format; (b) printing the calibration patterns on a substrate utilizing the given imaging system; (c) determining a first set of contour patterns corresponding to the calibration patterns imaged on the substrate; (d) generating a system pseudo-intensity function, which approximates the imaging performance of the imaging system; (e) determining a second set of contour patterns by utilizing the system pseudo-intensity function to define how the calibration patterns will be imaged in the substrate; (f) comparing the first set of contour patterns and the second set of contour patterns to determine the difference therebetween; (g) adjusting the system pseudo-intensity function until the difference between the first set of contour patterns and the second set of contour patterns is below a predefined criteria; and (h) utilizing the adjusted system pseudo-intensity function to modify the mask so as to provide for optical proximity correction.
Owner:ASML NETHERLANDS BV
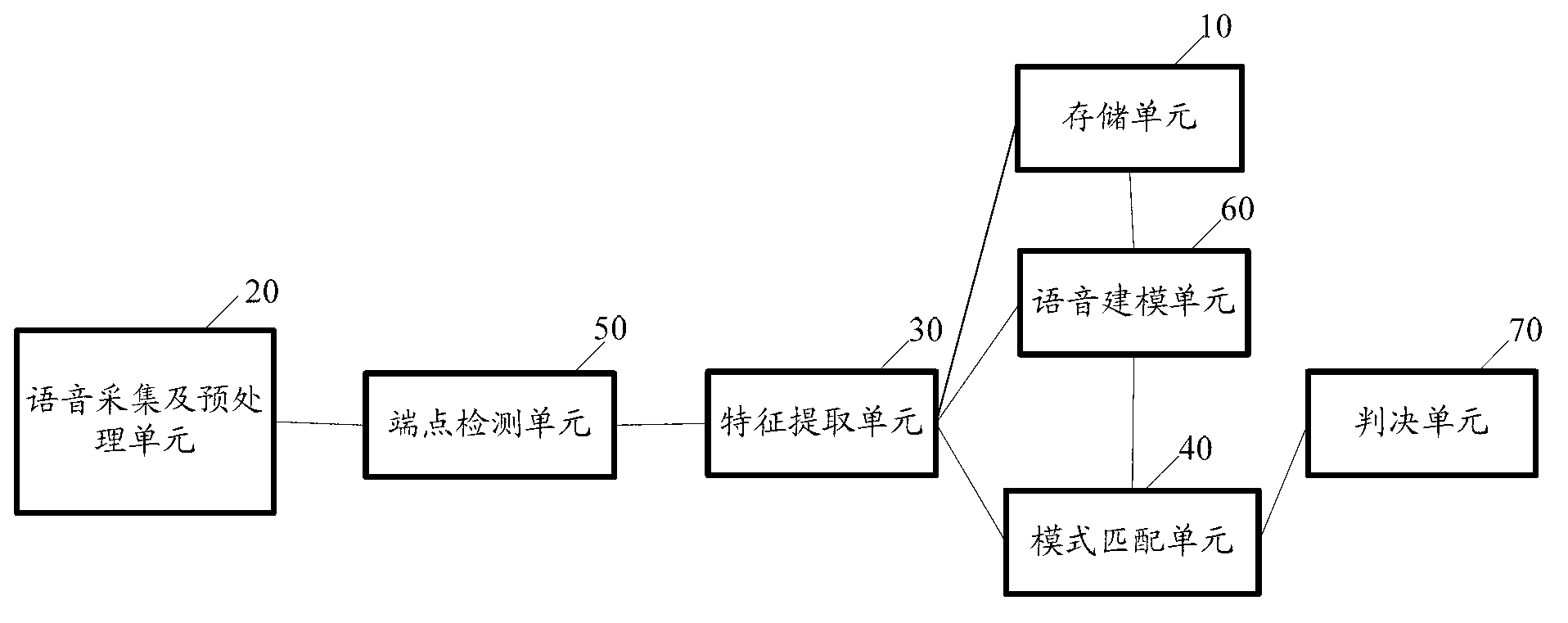
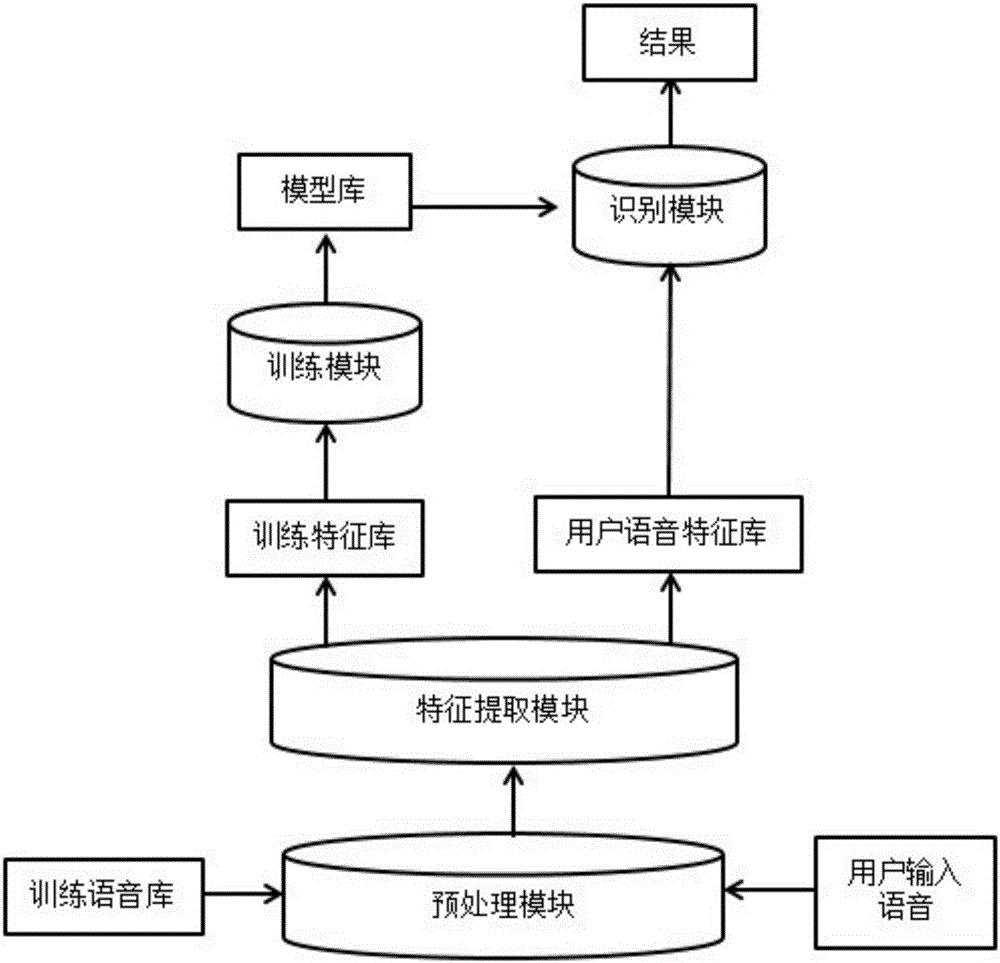
Voice recognition system
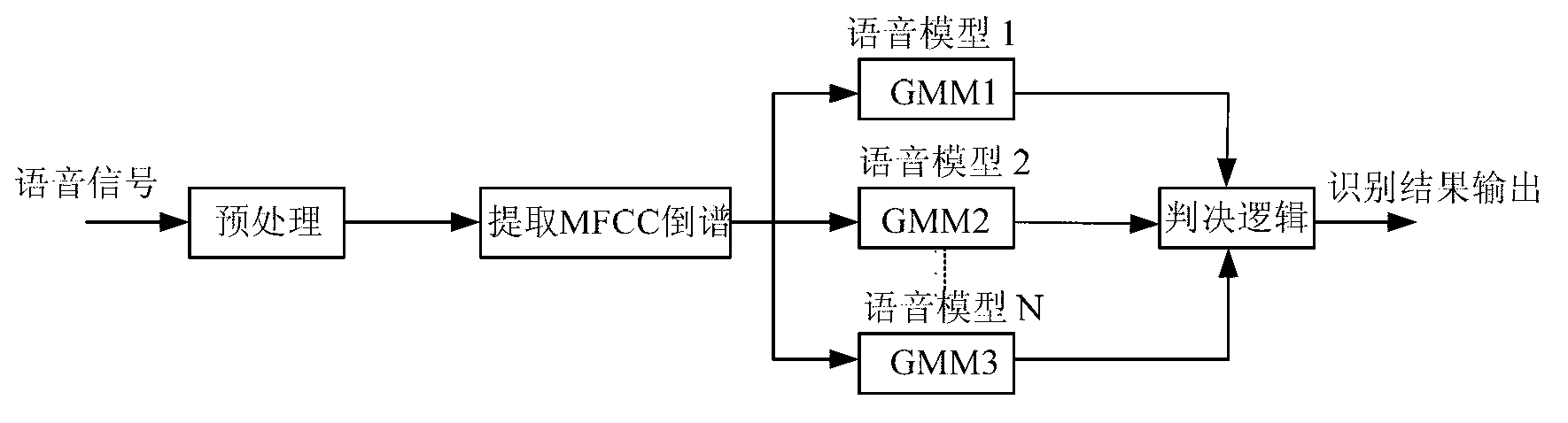
ActiveCN103236260AImprove detection reliabilityRealize the recognition functionSpeech recognitionMel-frequency cepstrumPattern matching
The invention provides a voice recognition system comprising a storage unit, a voice acquisition and pre-processing unit, a feature extraction unit and a pattern matching unit, wherein the storage unit is used for storing at least one user's voice model; the voice acquisition and pre-processing unit is used for acquiring a to-be-identified voice signal, transforming the format of the to-be-identified voice signal and encoding the to-be-identified voice signal; the feature extraction unit is used for extracting voice feature parameters from the encoded to-be-identified voice signal; and the pattern matching unit is used for matching the extracted voice feature parameters with at least one voice model so that the user to which the to-be-identified voice signal belongs is identified. Based on the voice generation principle, voice features are analyzed, MFCC (mel frequency cepstrum coefficient) parameters are used, a speaker voice feature model is established, and speaker feature recognition algorithms are achieved, and thus, the purpose to improve speaker detection reliability can be achieved, and the speaker identification function can be finally realized on an electronic product.
Owner:BOE TECH GRP CO LTD +1
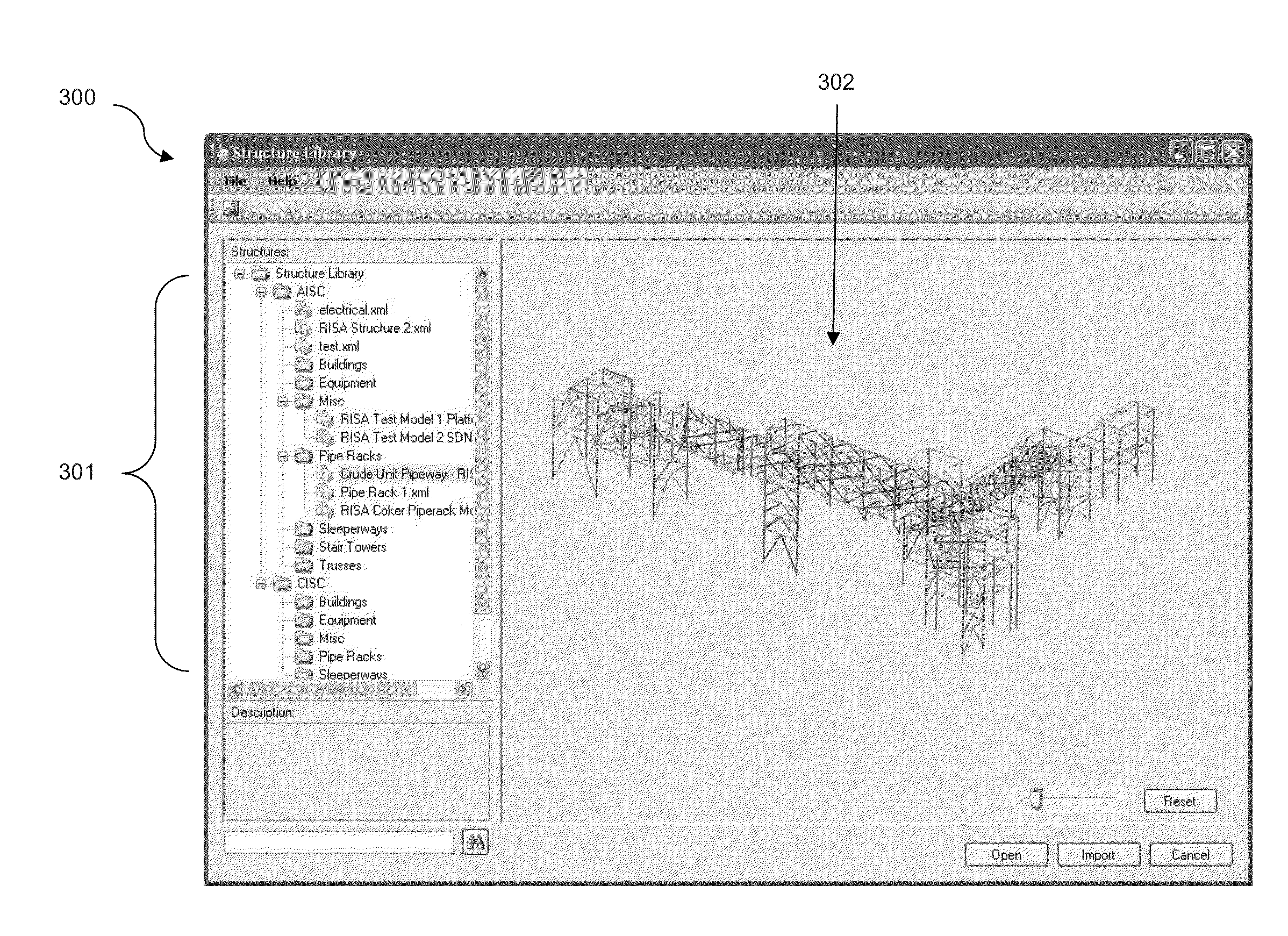
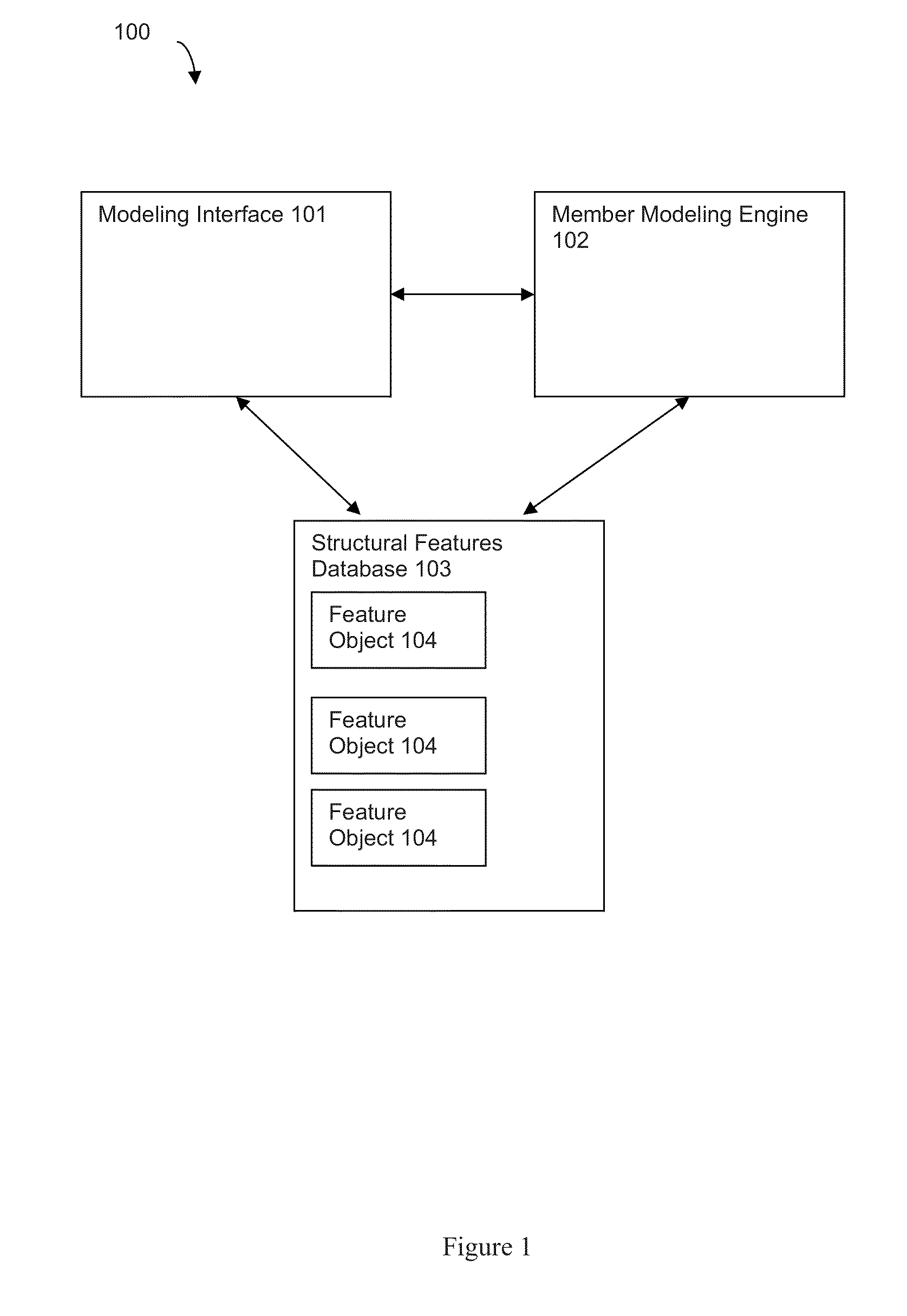
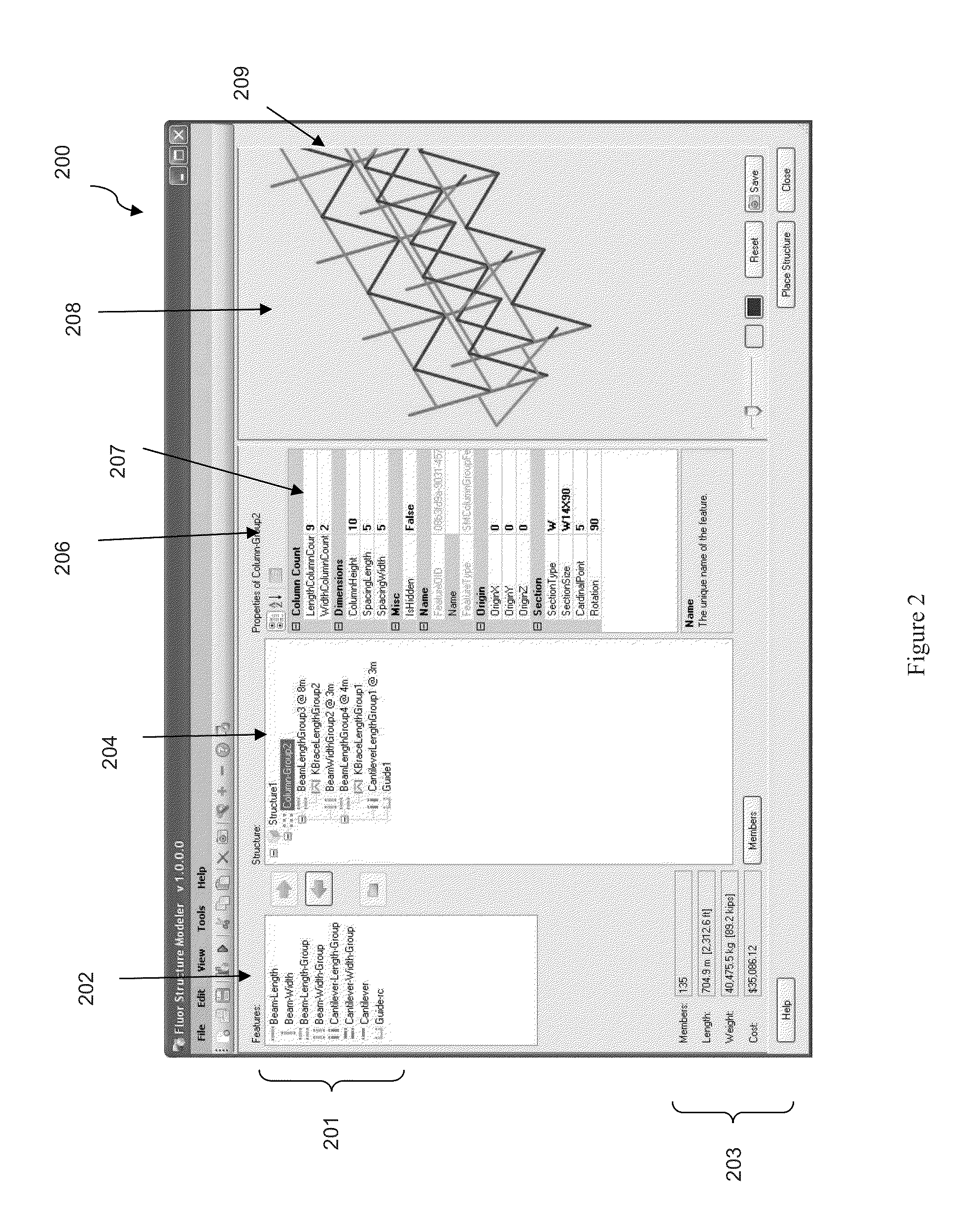
Feature-based rapid structure modeling system
InactiveUS20130317786A1Increased complexityGeometric CADAdditive manufacturing apparatusObject basedModel engine
A feature-based rapid modeling system that enables a user to construct structural feature models from feature objects representing structural features. The interface enables the rapid construction by allowing for the use of group- and pattern-based feature objects, and by allowing a user to select feature objects based on object properties and object relationship properties, including hierarchical properties. A modeling engine constructs member models based on the feature models, which can be exported to a structure library. The models in the structure library can be imported into new projects, eliminating the need to repeat the construction of the model.
Owner:FLUOR TECH CORP
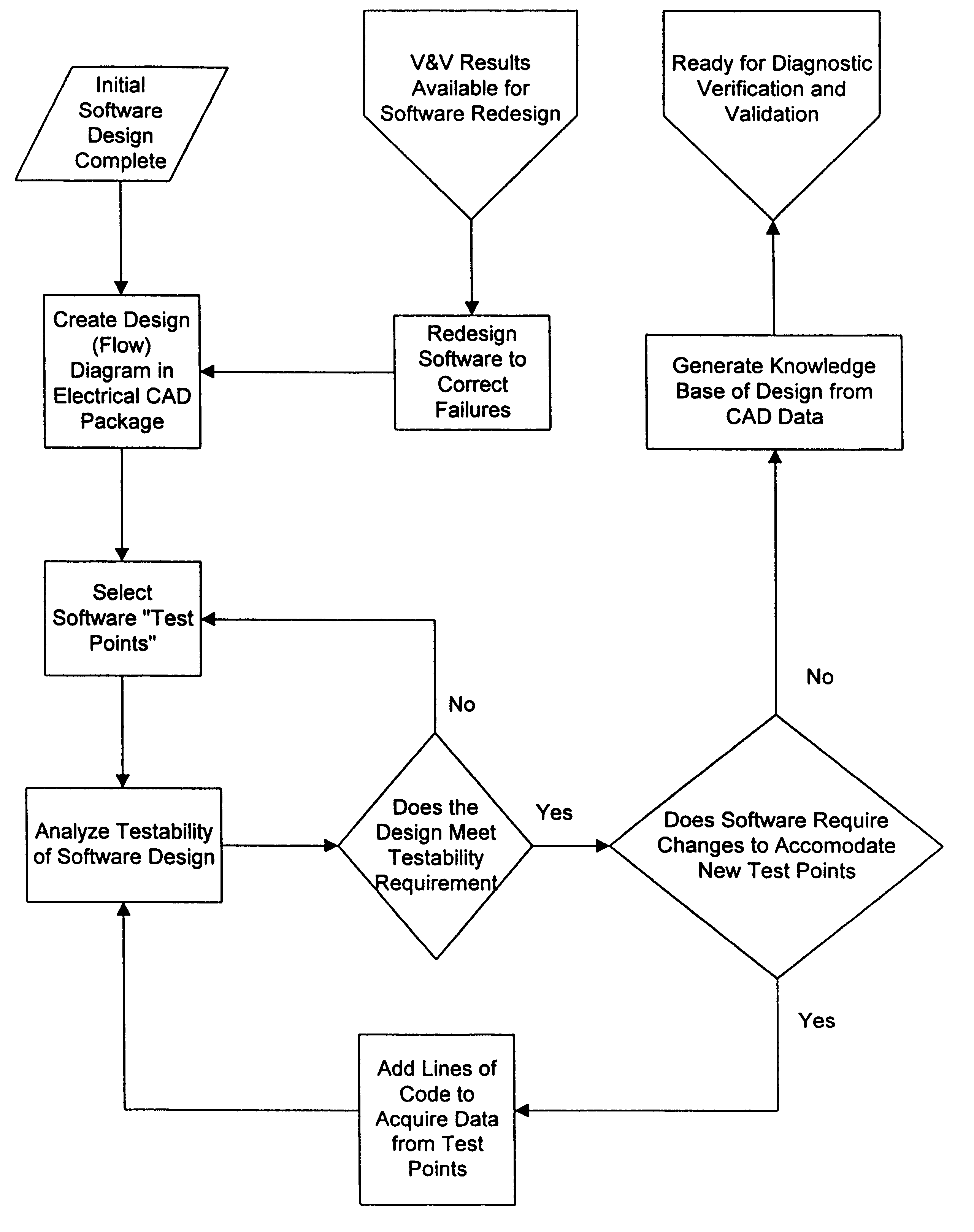
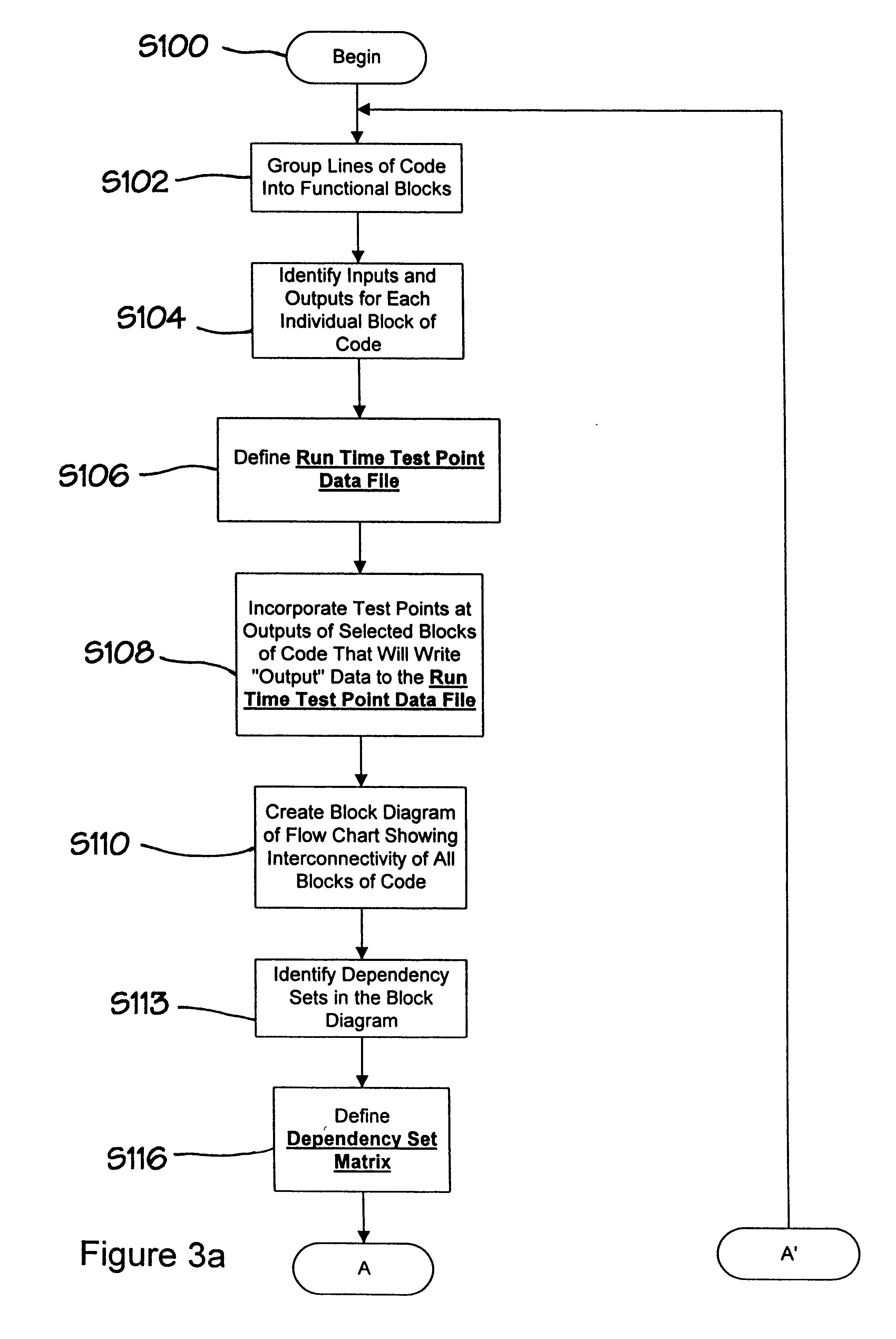
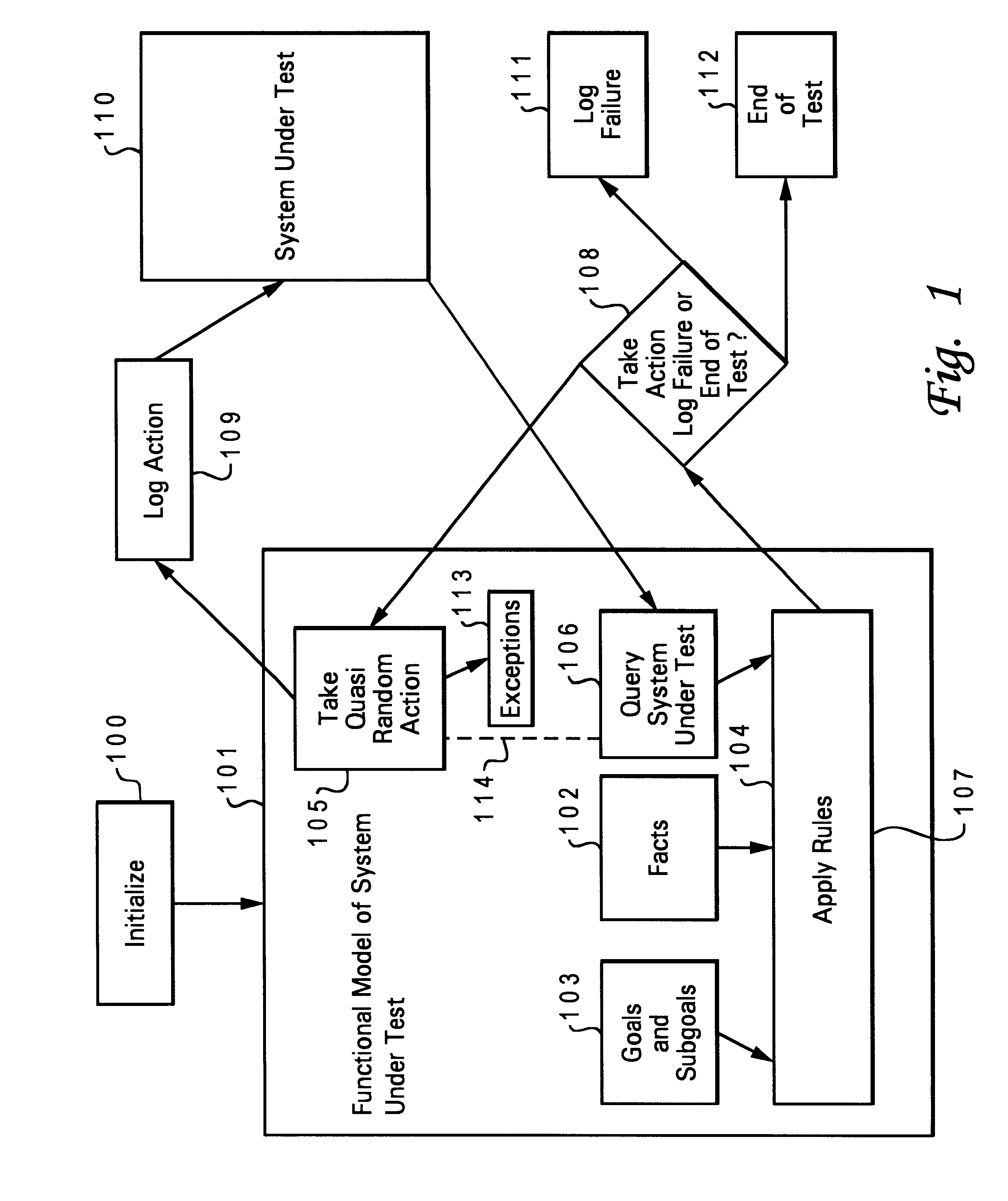
Method and apparatus for debugging, verifying and validating computer software
InactiveUS6173440B1Software testing/debuggingProgram loading/initiatingSoftware designVerification procedure
A new approach for software debugging, verification and validation is disclosed. The present invention utilizes a knowledge-based reasoning approach to build a functional model of the software code for identifying and isolating failures in the software code. The knowledge-based reasoning approach of the present invention uses the software design, which is preferably based upon a flow chart or block diagram representation of the software functionality, to build the functional model. The software block diagram contributes to the functional model by defining the inputs and outputs of the various blocks of code, as well as defining data interconnections between the various blocks of code. In accordance with a method of the present invention, test points are strategically inserted throughout the code, and each test point is associated with a corresponding block of code. Expected values of the test points for an expected proper-operation execution of the computer program are generated. The computer program is then executed on a computer, and the actual values of the test points from the program execution are compared with the expected values of the test points. Failed test points which do not agree with corresponding expected values are determined. The functional model, which includes information functionally relating the various test points to one another, is then used to isolate the failed test points to one or more sources of failure in the code.
Owner:MCDONNELL DOUGLAS
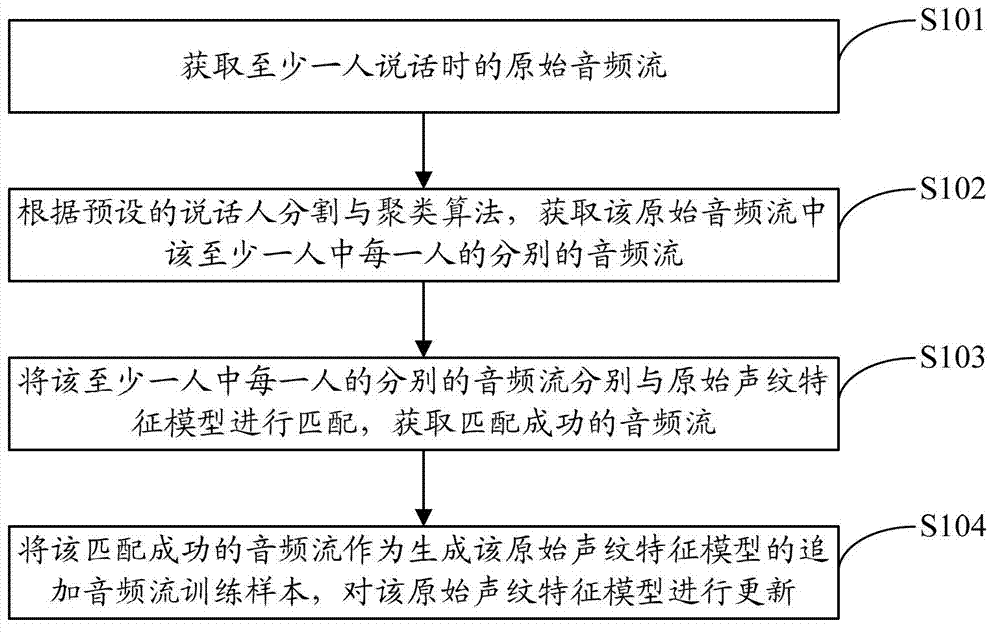
Method for updating voiceprint feature model and terminal
The invention is suitable for the technical field of voice recognition and provides a method for updating a voiceprint feature model. The method comprises the following steps of: obtaining an original audio stream of at least one speaker, and obtaining the audio stream of each speaker in the at least one speaker in the original audio stream according to a preset speaker segmentation and clustering algorithm; matching the respective audio stream of each speaker in the at least one speaker with an original voiceprint feature model, so as to obtain the successfully-matched audio stream; and using the successfully-matched audio stream as an additional audio stream training sample used for generating the original voiceprint feature model, and updating the original voiceprint feature model. According to the invention, the valid audio stream during a conversation process is adaptively extracted and used as the additional audio stream training sample, and the additional audio stream training sample is used for dynamically correcting the original voiceprint feature model, thus achieving a purpose of improving the precision of the voiceprint feature model and the accuracy of recognition under the premise of high practicability.
Owner:HUAWEI DEVICE CO LTD
Anomaly Detecting for Database Systems
ActiveUS20110271146A1Digital data information retrievalFault responseAnomaly detectionQuery optimization
Methods, systems and computer program products for detecting anomalies for a database system are provided. A method may include extracting workload features from a query optimizer based on a query workload and generating feature models for the extracted workload features. The method may also include extracting instance features from the query optimizer based on a query instance. Instance feature values may be obtained. The method may further include applying a query instance to the workload feature models to produce a prediction value for each workload feature. Anomalies may be reported based on a comparison of each instance feature value with a corresponding prediction value. A system for detecting anomalies for a database system may include a query optimizer, a feature modeler and an anomaly detector.
Owner:MITRE SPORTS INT LTD
Feature modeling in a finite element model
ActiveUS6941255B2Accurate representationSmall amount of calculationGeometric CADComputation using non-contact making devicesFinite element techniqueElement model
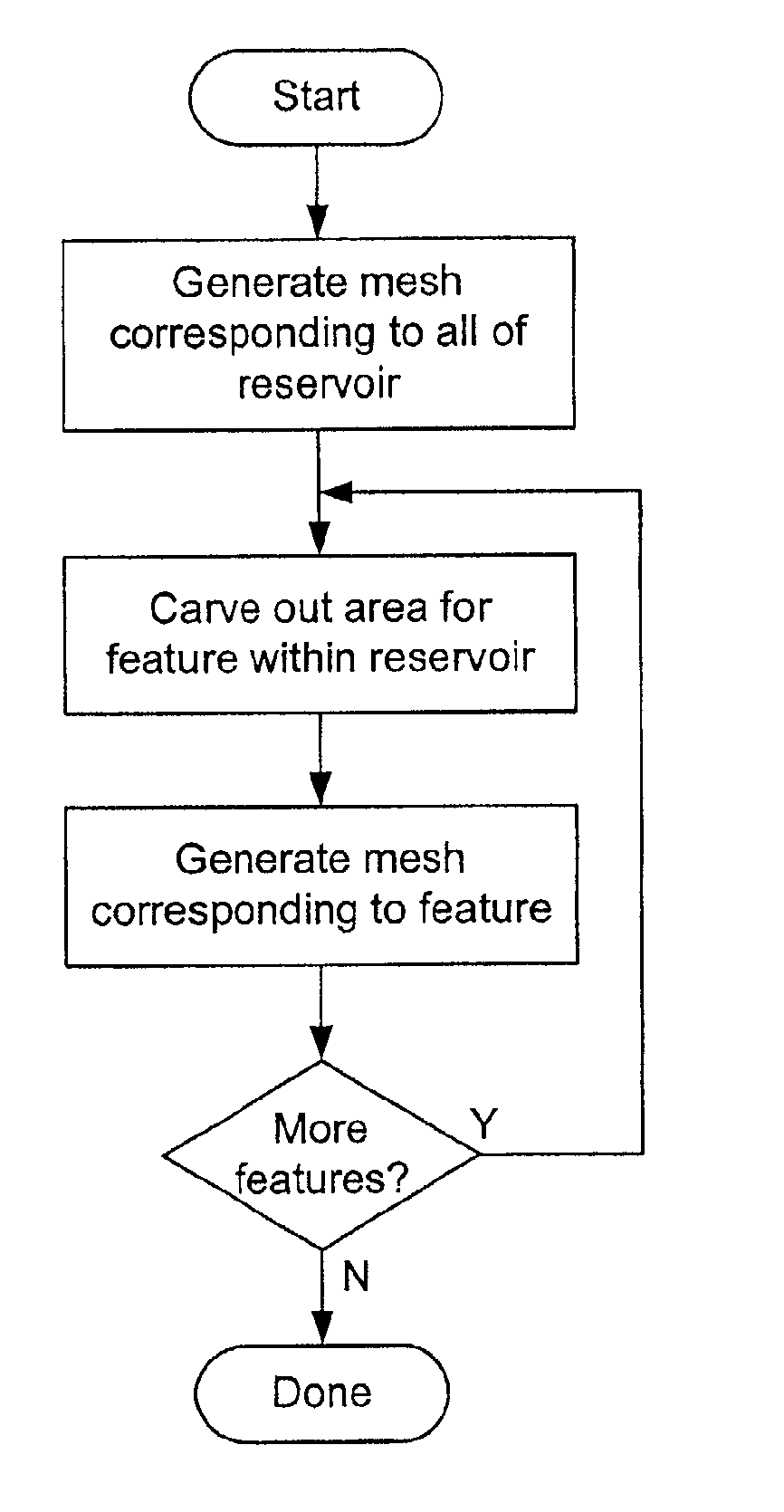
A method for simulating a physical system using finite element techniques, wherein two or more distinct models corresponding to distinct regions within the modeled system are solved, each with a corresponding evaluator. Nodes which lie on the boundaries between the models may have different values corresponding to the different models. When a particular model is solved, the evaluator for that model is used to obtain the appropriate values for each of these common nodes. In one embodiment, a first model is defined, then a region corresponding to a particular feature within the system is carved out of it. A finite element model corresponding to the feature is then inserted into the region. The finite elements may be adapted to share nodes on the boundaries between them.
Owner:LANDMARK GRAPHICS
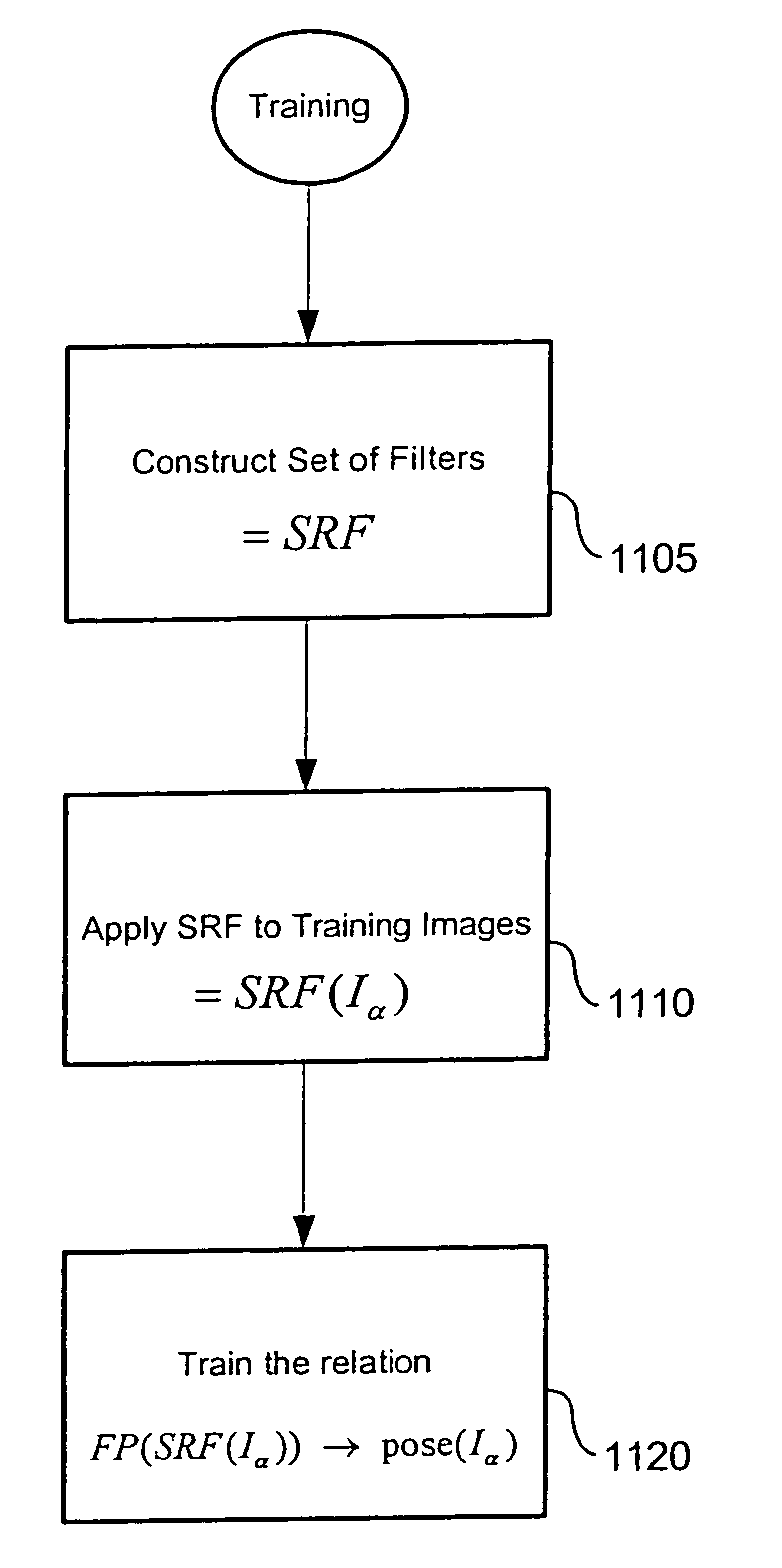
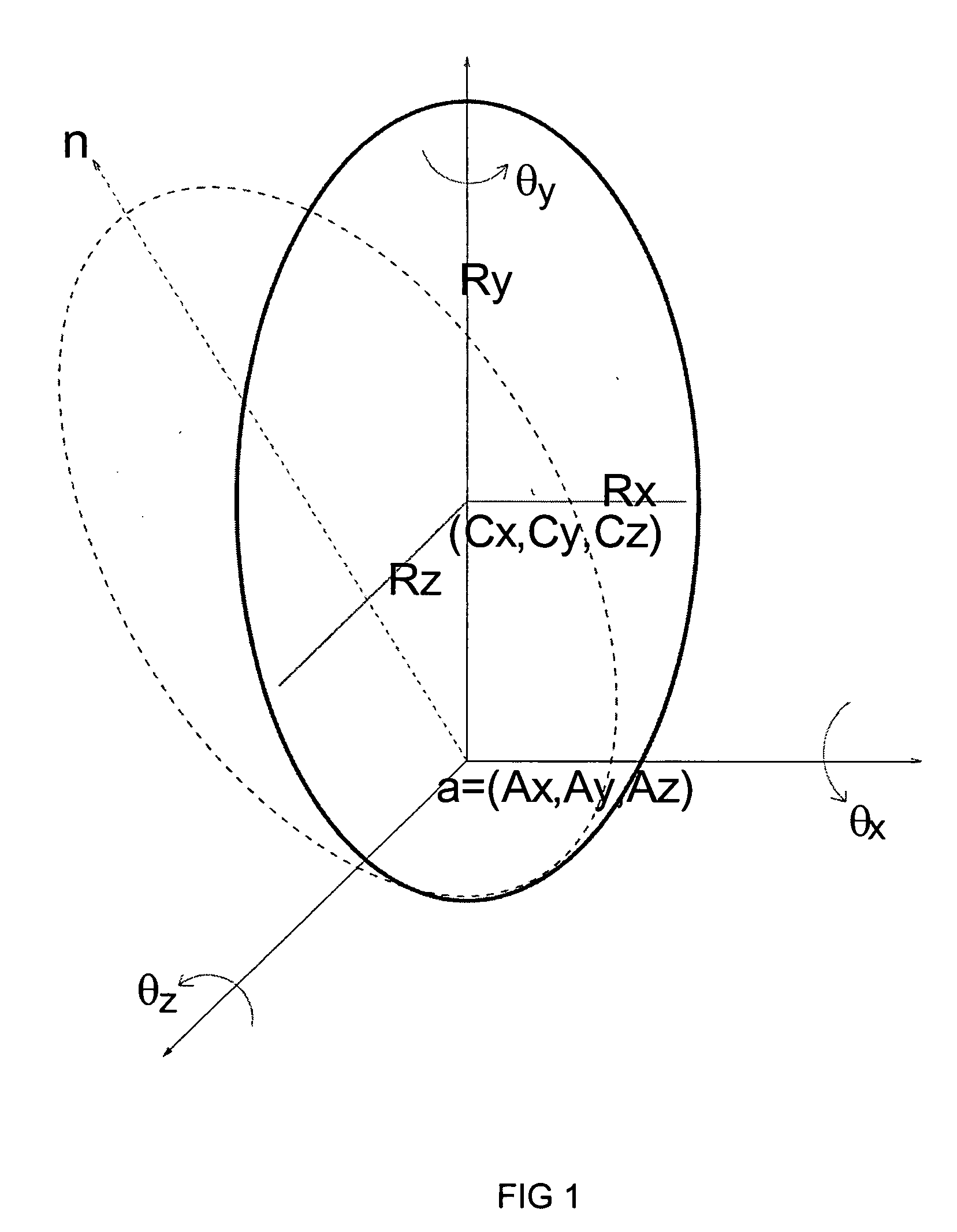
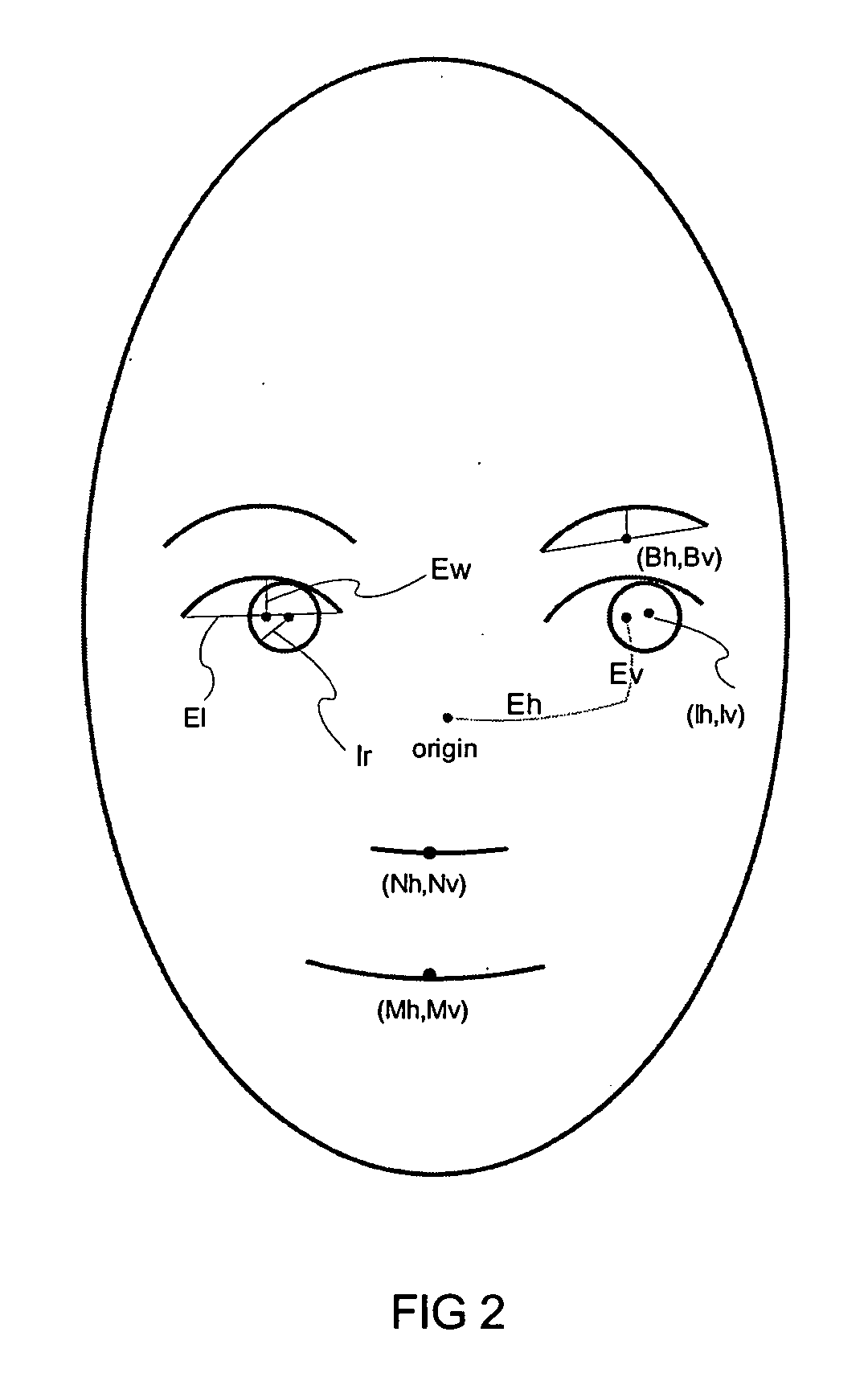
Estimating facial pose from a sparse representation
ActiveUS20050180626A1Accurate estimateGood estimateCharacter and pattern recognitionPattern recognitionSparse model
A method for accurately estimating a pose of the human head in natural scenes utilizing positions of the prominent facial features relative to the position of the head. A high-dimensional, randomly sparse representation of a human face, using a simplified facial feature model transforms a raw face image into sets of vectors representing the fits of the face to a random, sparse set of model configurations. The transformation collects salient features of the face image which are useful to estimate the pose, while suppressing irrelevant variations of face appearance. The relation between the sparse representation of the pose is learned using Support Vector Regression (SVR). The sparse representation, combined with the SVR learning is then used to estimate a pose of facial images.
Owner:NEC CORP
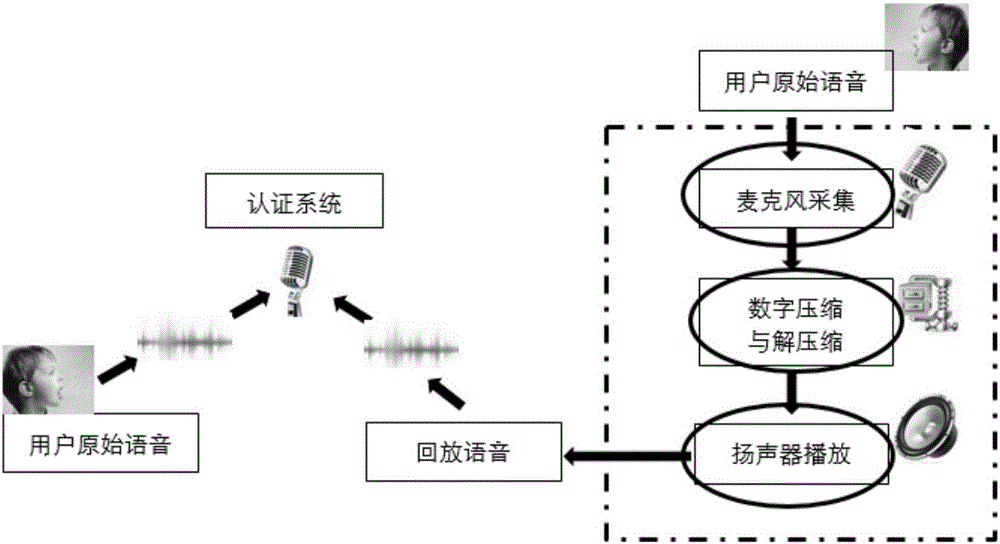
Replay attack detection method based on distortion features of speech signals introduced by loudspeaker
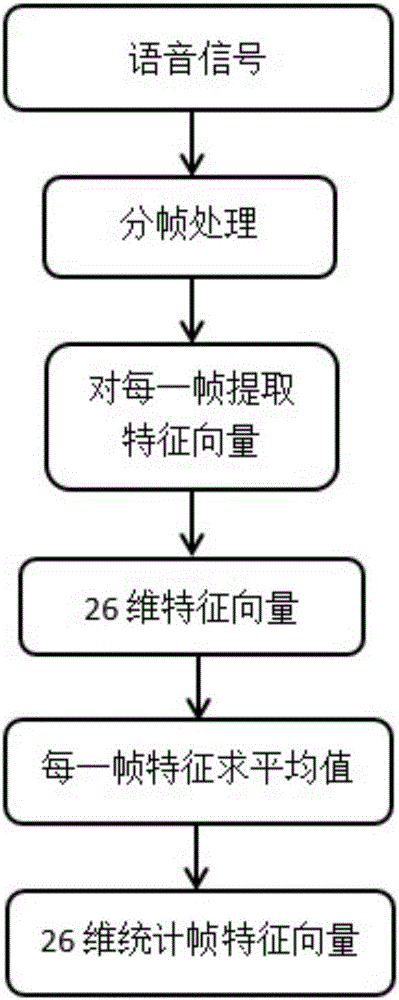
InactiveCN106297772AEfficient detectionSpeech recognitionTransmissionNonlinear distortionFeature vector
The invention discloses a replay attack detection method based on the distortion features of speech signals introduced by a loudspeaker. The method includes the following steps that: speech signals to be detected are pre-processed, and noised speech frames in the speech signals to be detected are reserved; feature extraction is carried out on each noised speech frame in the pre-processed speech signals, so that speech signal linear distortion and nonlinear distortion feature-based feature vectors can be obtained; the average value of the feature vectors of all the noised speech frames is obtained, and statistical feature vectors can be obtained, and the feature model of the speech signals to be detected is obtained; the feature vectors of a training speech sample are extracted, so that a training speech feature model can be obtained, the training speech feature model is utilized to train an SVM (Support Vector Machine model), so that a speech model library can be obtained; and SVM mode matching is performed on the feature model of the speech signals to be detected and the trained speech model library, and a decision result can be outputted. With the replay attack detection method of the invention adopted, real-time and effective detection of replayed speech can be realized.
Owner:WUHAN UNIV
Mobile terminal, and system and method for suspicious behavior detection and judgment
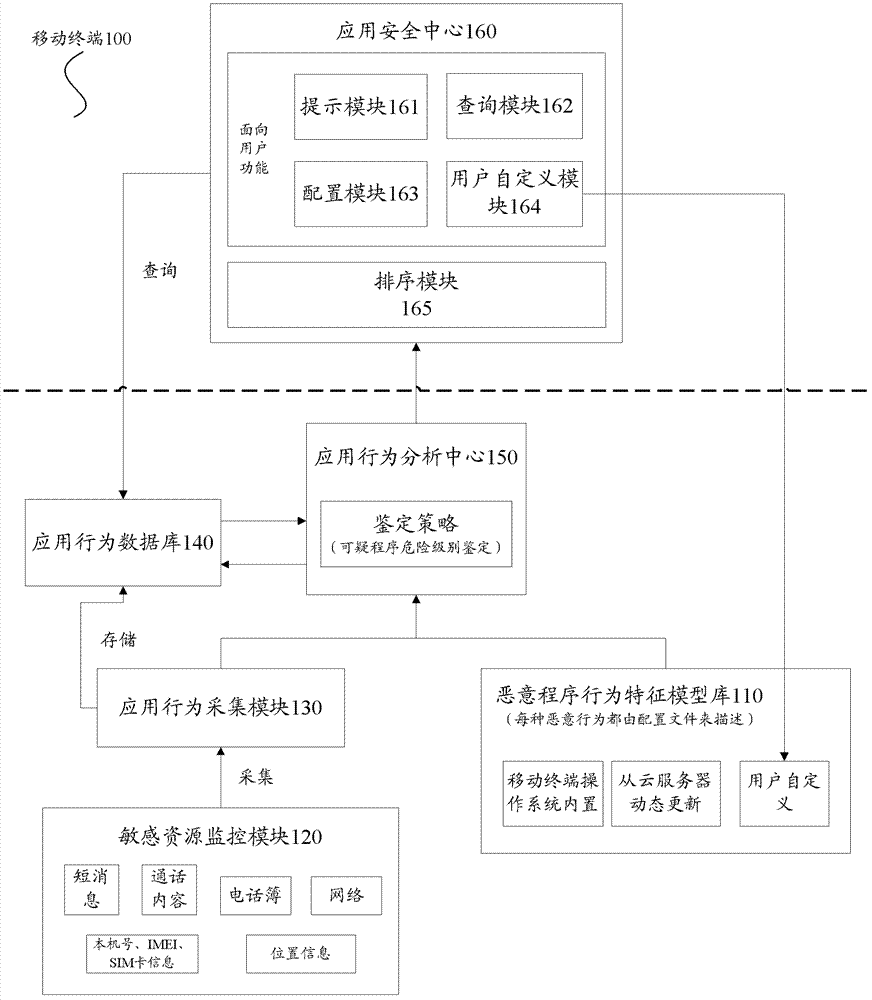
ActiveCN103368904AExtensive range of securityData synchronizationSubstation equipmentTransmissionAnalysis centerComputer terminal
The invention provides a mobile terminal which comprises a malicious behavior feature model base used for storing malicious behavior models; a sensitive resource monitoring module used for monitoring access of an application program to sensitive resource; an application behavior acquisition module used for acquiring a corresponding sensitive behavior according to monitored behavior data; an application behavior database used for storing the sensitive behavior; an application behavior analysis center used for receiving the sensitive behavior, invoking the malicious behavior models in the malicious behavior feature model base and judging whether a behavior corresponding to the sensitive behavior is a malicious behavior; and an application security center used for querying the sensitive behavior, sorting application program accesses corresponding to the sensitive behavior in order of malicious degree and setting warning levels of the application program accesses. The invention further provides a suspicious behavior detection and judgment system and a suspicious behavior detection and judgment method. The mobile terminal, the suspicious behavior detection and judgment system and the suspicious behavior detection and judgment method of the invention have the advantage of being capable of providing safety guarantee for application programs and preventing and monitoring malicious behaviors.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Residential house chart building structure intelligent recognition and functional area automatic planning and designing method
ActiveCN106528904ABest Functional Area DivisionGood effectGeometric CADSpecial data processing applicationsStructure recognitionEngineering
The present invention discloses a residential house chart building structure recognition and functional area planning and designing method and system. The method comprises a first step of acquiring a residential unit vector diagram, wherein the residential vector diagram comprises walls and doors and windows, and walls and doors and windows form closed rooms; a second step of acquiring specific information about usage, walls and windows and doors of each closed room; and a third step of selecting a reference wall, traversing all walls, and recognizing building structures and planning and designing the functional areas in the closed rooms sequentially according to feature models of the residential building structure and the functional area structure, so as to form a residential vector diagram with all functional area names. According to the method, the functional areas beneficial to living are divided optimally by combining the feature models of the residential building structure and the functional area structure only according to the residential unit diagram or the residential unit vector diagram. The divided optimal functional areas are a reference for users or are used in household design later, and deliver a good effect.
Owner:陈志静 +1
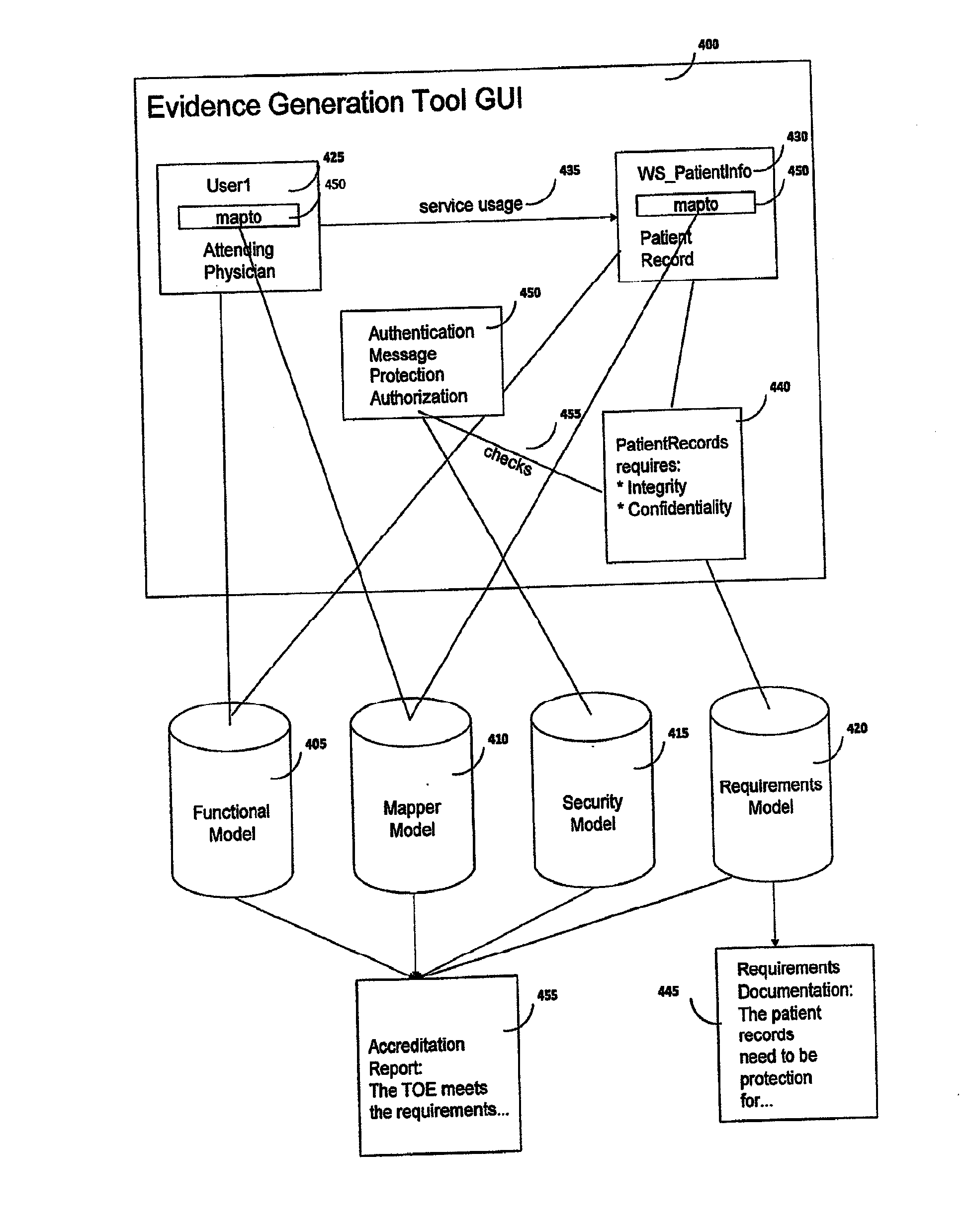
Method and system for rapid accreditation/re-accreditation of agile it environments, for example service oriented architecture (SOA)
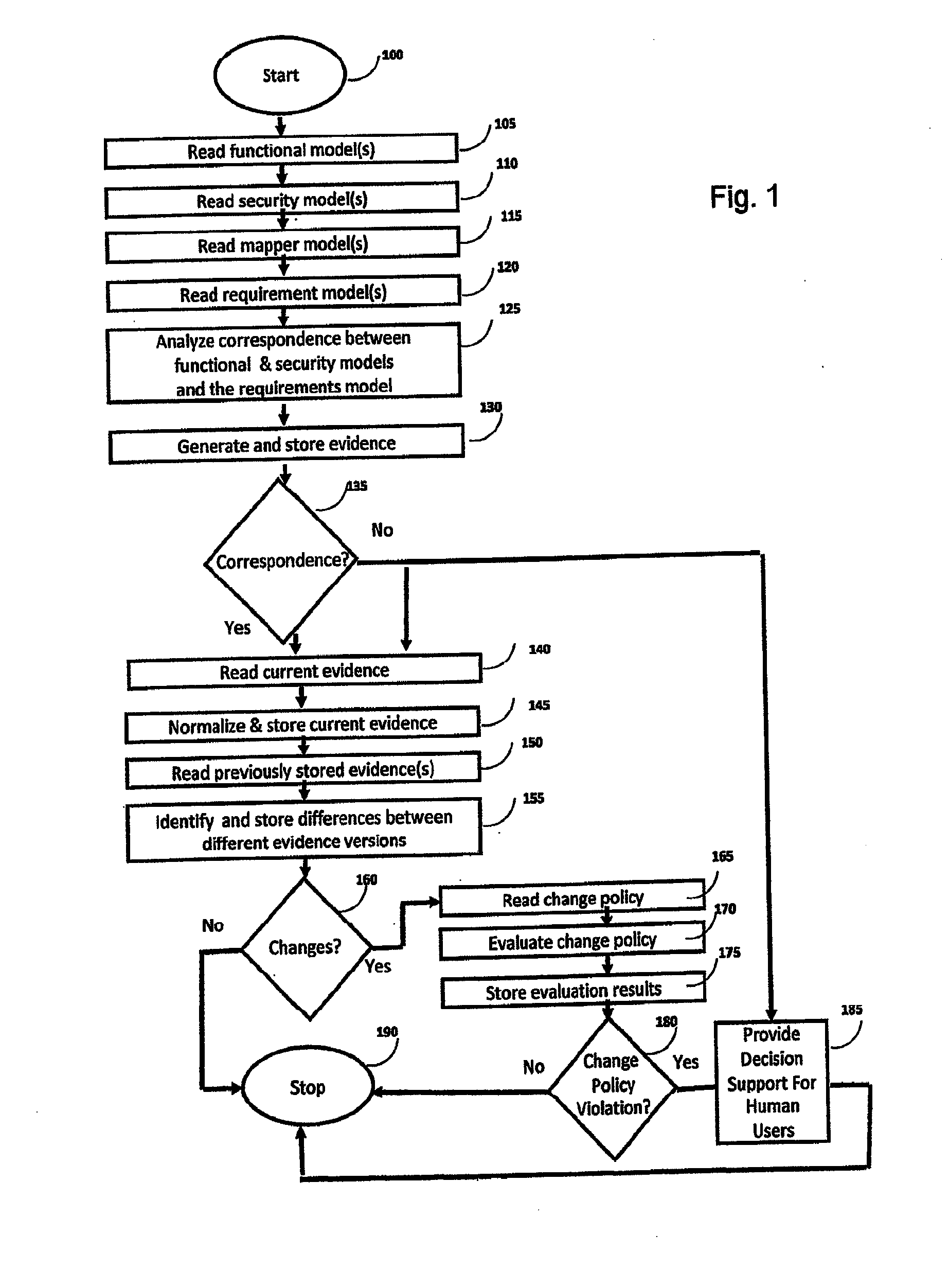
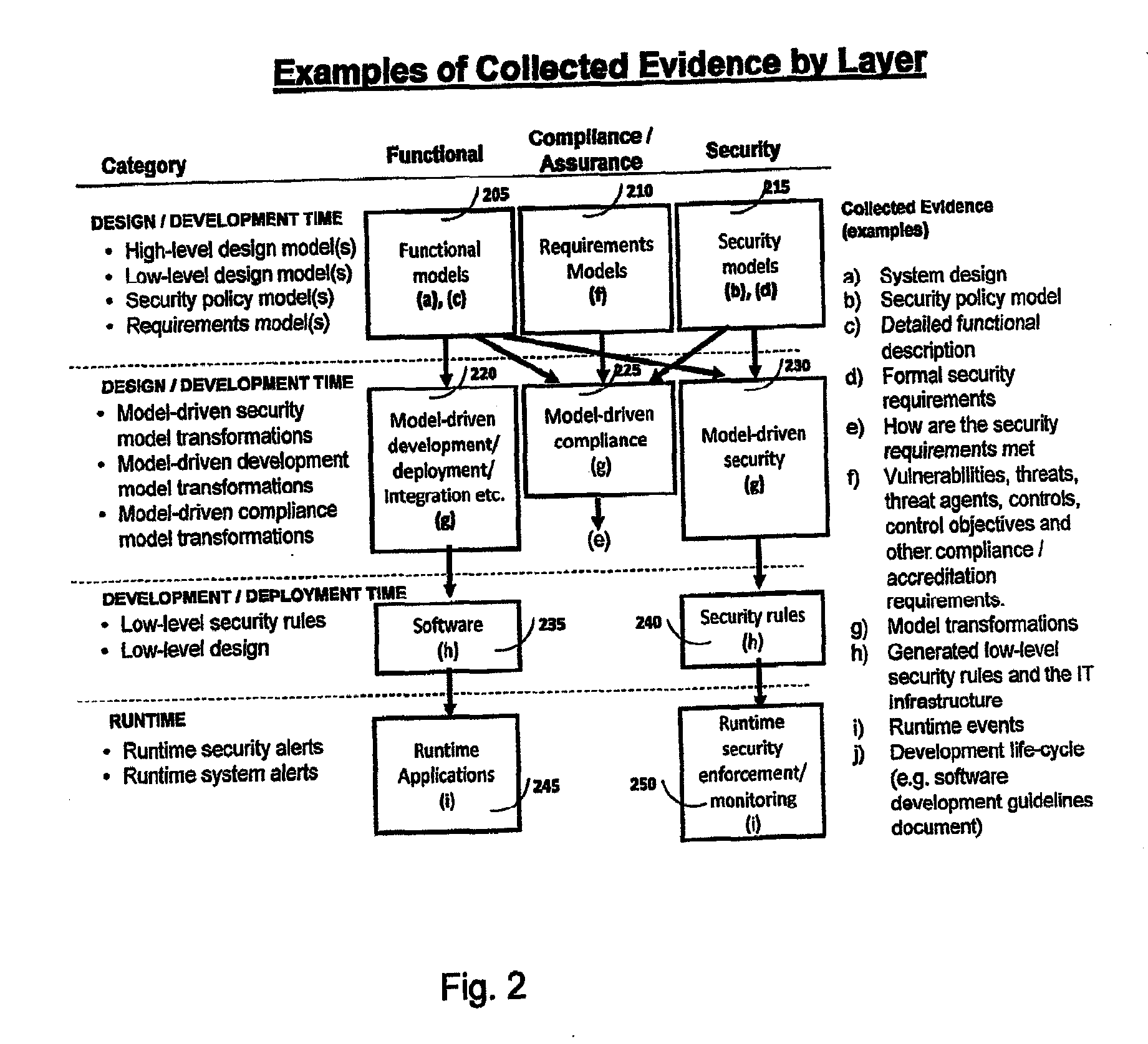
A system and method for managing and analyzing security requirements in reusable models. At least one functional model, at least one security implementation model, at least one requirement model, and meta models of the models are read by a reader. A correspondence between the functional model, security implementation model, and the requirements model is analyzed, whereby the correspondence indicates that compliance / security / accreditation requirements defined in the requirement model match with security objectives implemented by controls defined by the security implementation model. Next, it is determined whether correspondence is or is not given based on the analysis of the correspondence and then evidence is generated based on the analysis of the correspondence and the determination and the impact of changes is analyzed.
Owner:OBJECTSECURITY
Vehicle positioning and speed measuring method based on dynamic video feature of vehicle
InactiveCN104021676AWide speed rangeA large amount of detection informationImage analysisDetection of traffic movementVideo monitoringVehicle dynamics
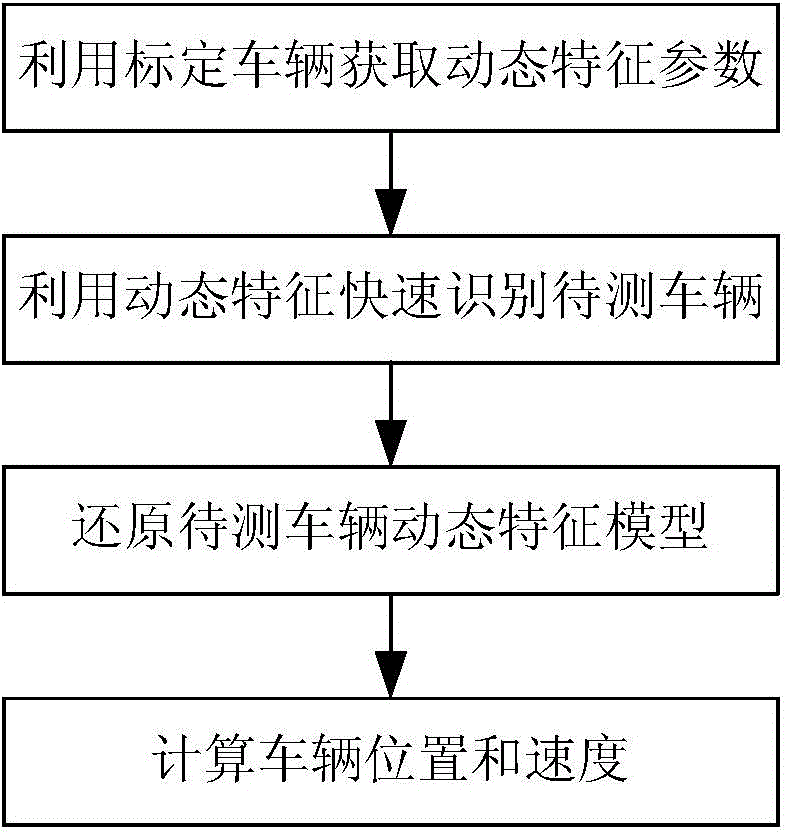
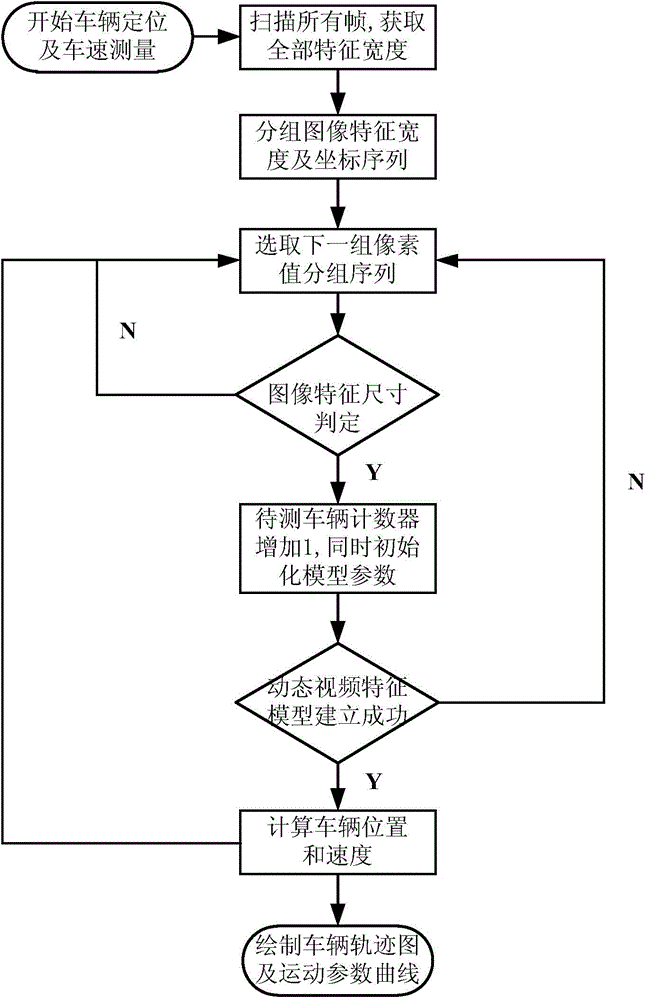
The invention relates to a vehicle positioning and speed measuring method based on the dynamic video feature of a vehicle, belonging to the technical field of intelligent transportation and close-range photogrammetry. The vehicle positioning and speed measuring method comprises the following steps: judging the vehicle dynamic video feature size in a video image within any time quantum in one video monitoring system according to vehicle dynamic feature parameters extracted from the video image which calibrates a vehicle traveling process, and reconstructing and reducing a dynamic video feature model of a to-be-measured vehicle traveling process corresponding to each image frame; and calculating an actual position and a vehicle speed value sequence corresponding to each image frame in the to-be-measured vehicle traveling process according to a mapping relation between the dynamic variation characteristic of the image feature size of a vehicle to be measured and the actual vehicle movement parameters, and thus acquiring the actual position and traveling speed information of the vehicle. The vehicle positioning and speed measuring method is easy to realize and high in accuracy, and is applicable to the demands of various vehicles on speed measurement in a road traffic video monitoring system.
Owner:SHANGHAI JIAO TONG UNIV
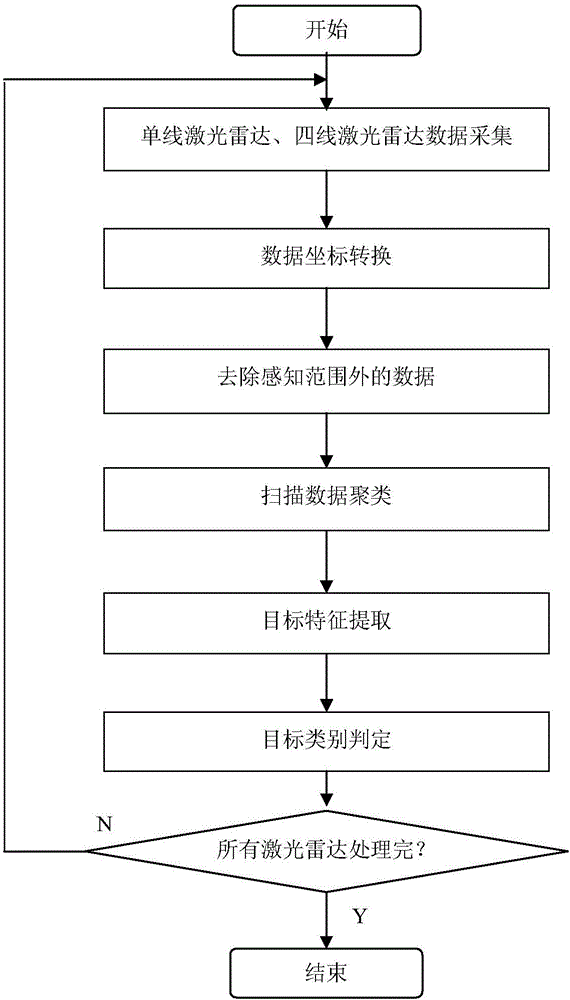
Intelligent vehicle multi-laser radar fusion recognition method based on target features
ActiveCN105701479AImprove perceptionSolve problems such as lossImage enhancementImage analysisRadarPattern perception
The present invention provides an intelligent vehicle multi-laser radar fusion recognition method based on target features, relates to the field of intelligent vehicle environment perception. The method comprises the following steps: 1, performing pretreatment of collected data, extracting target geometric features and determining the type of the target; 2, calculating the geometry conformability degree of the target, and performing target matching according to the geometry conformability degree; 3, fusing the target geometric features through adoption of a method based on distance weight fusion; 4, tracking the target through adoption of a multi-feature target tracking method, and obtaining the relative movement features of the target; 5, obtaining the absolute movement features of the target through adoption of the vehicle movement features collected by a global positioning system; 6, correcting the type of the target according to the absolute movement features of the target and a target feature model; and 7, performing rasterization of the target features, and performing grid expression. The intelligent vehicle multi-laser radar fusion recognition method based on target features is configured to fuse the multi-laser radar through adoption of target features to improve the target recognition capability of a system and enhance the safety of a vehicle in the driving process.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
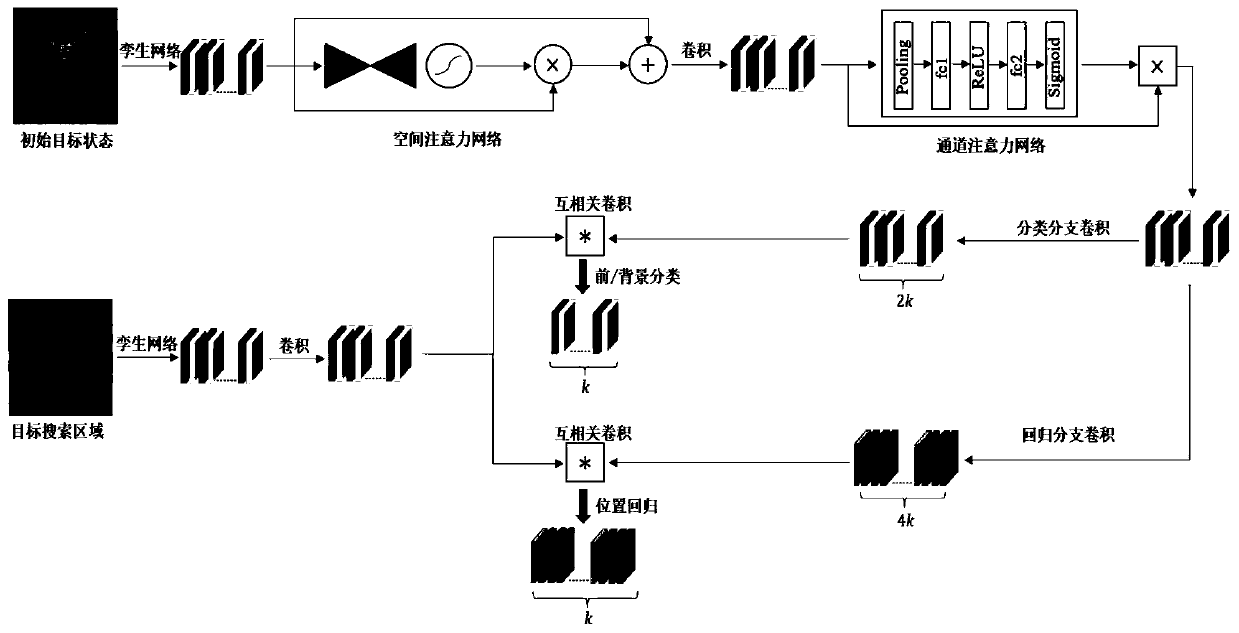
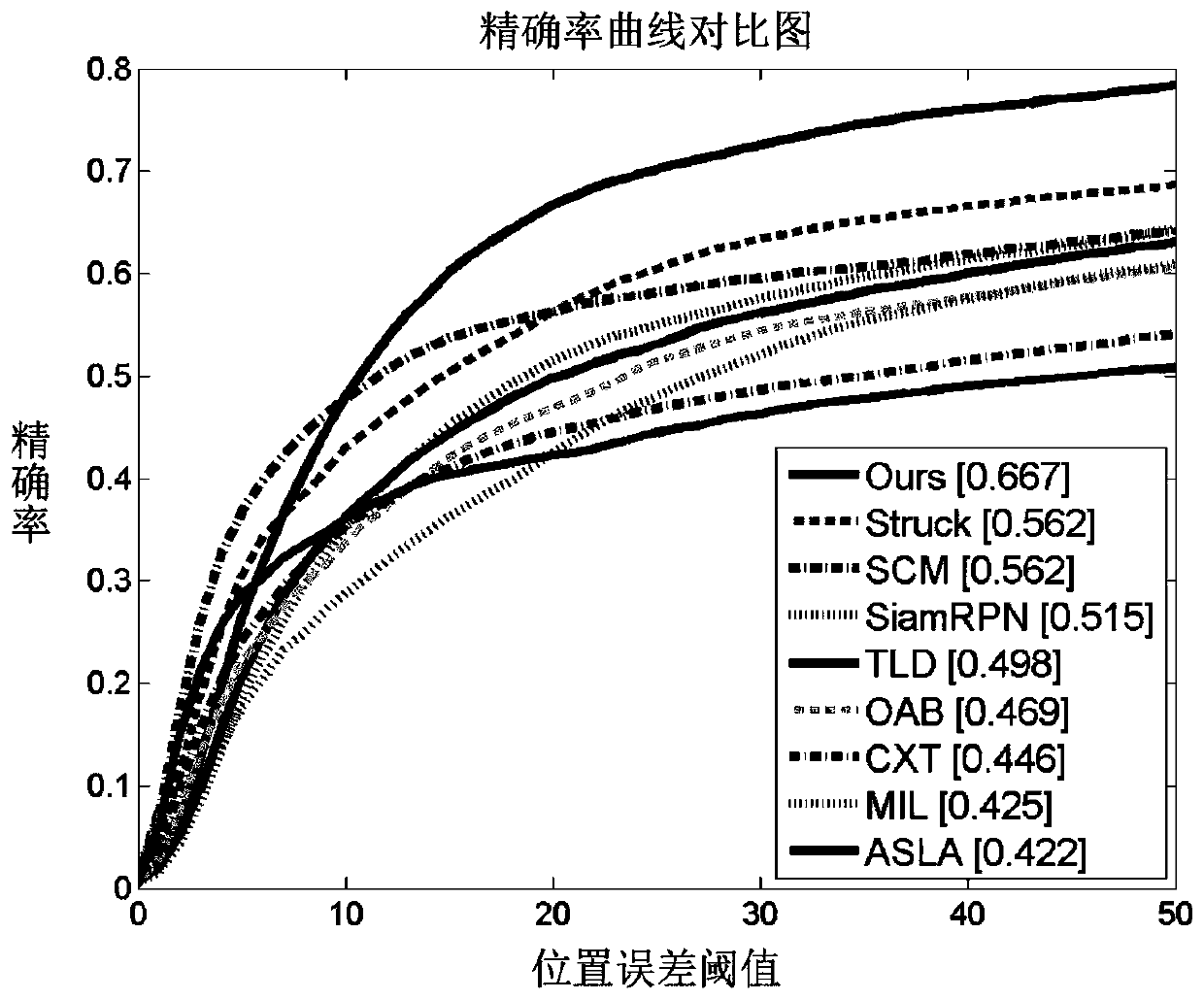
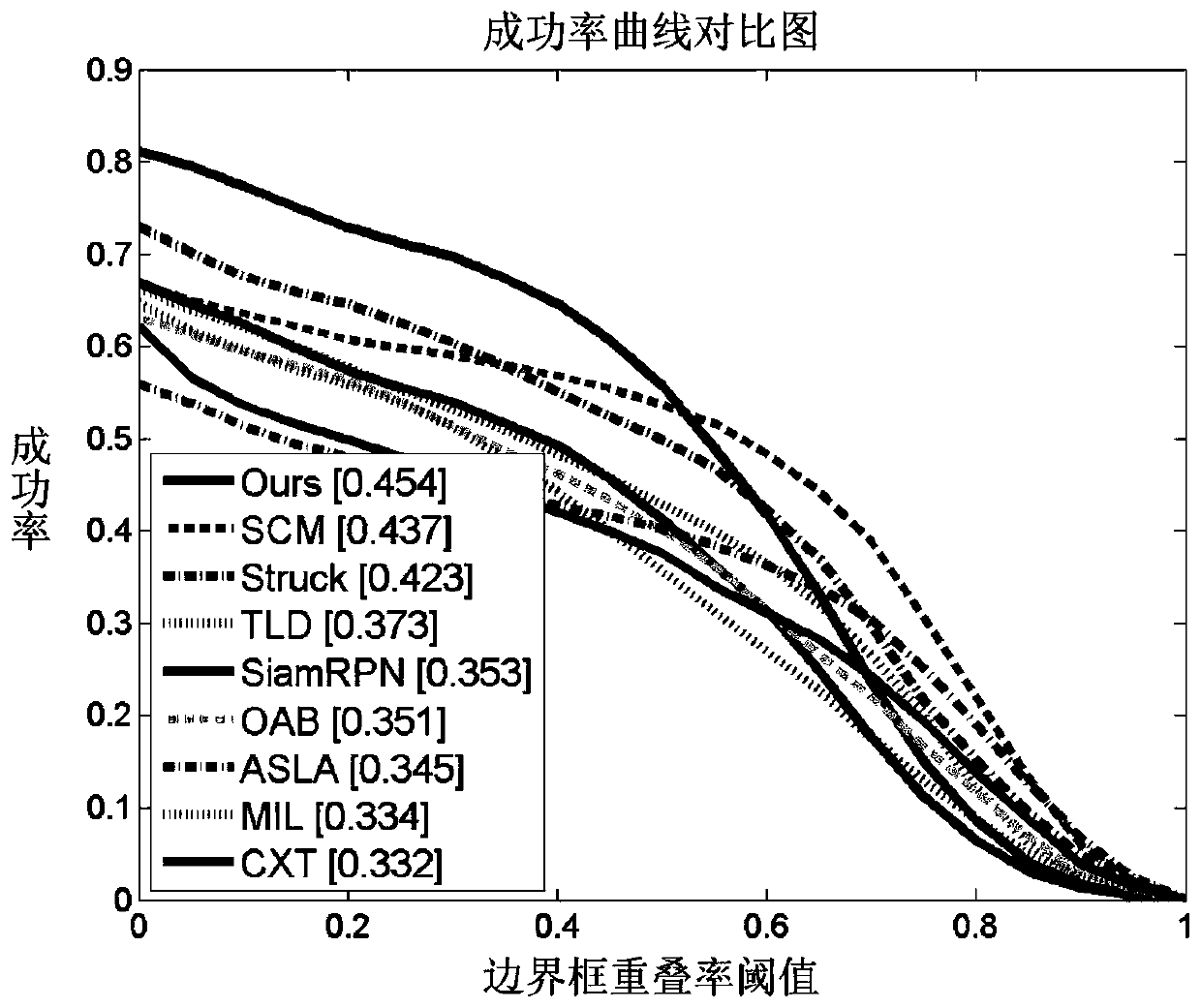
Twin candidate region generation network target tracking method based on attention mechanism
ActiveCN110335290AImprove discrimination abilityImprove accuracyImage enhancementImage analysisPattern recognitionImaging processing
The invention relates to a twin candidate region generation network target tracking method based on an attention mechanism, and belongs to the technical field of image processing. The twin candidate region generation network target tracking method comprises the following specific steps: 1, extracting initial target template features and target search region features by using a twin network; 2, constructing a spatial attention network to enhance a target template foreground and suppress a semantic background; 3, constructing a channel attention network to activate strong correlation characteristics of the target template, and eliminating redundancy; and 4, constructing a candidate region generation network to realize multi-scale target tracking. The twin candidate region generation networktarget tracking method has the advantages that the attention mechanism is used for constructing the adaptive target appearance feature model; the target foreground is enhanced; the semantic backgroundis inhibited; and the difference features of the target foreground and the interference background are highlighted; redundant information is removed, so that the efficient appearance feature expression capacity is obtained, and the target drifting problem is effectively relieved.
Owner:DALIAN UNIV OF TECH
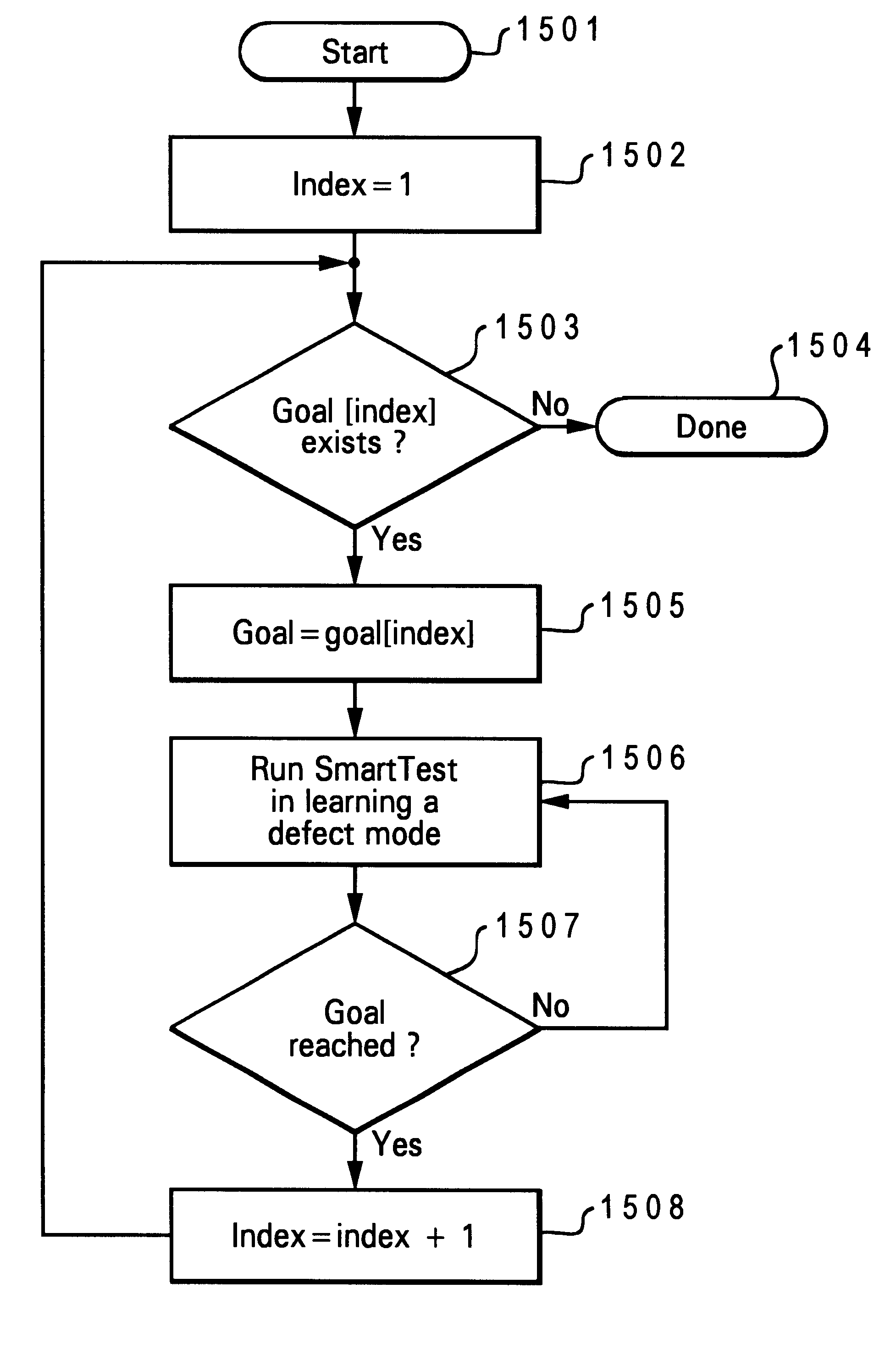
Method and apparatus for training an automated software test
InactiveUS6349393B1Efficient testingSoftware testing/debuggingSpecific program execution arrangementsSystem under testFeature model
An automated software test is provided which includes a functional model of a system to be tested. The automated software test is utilized to operate a system under test in accordance with specified facts, goals and rules. Quasi-random actions are taken within the system in accordance with specified rules and facts until a defined goal has been accomplished. Training the automated software test is accomplished by specifying a particular goal, i.e. identifying a particularly known defect, and thereafter running the test in a quasi-random fashion until the particular goal has been achieved. The number and nature of actions required to achieve that goal are logged and the process is then repeated until the shortest path required to achieve that goal has been determined. The log of actions which eventually reach a particularly defect may also be utilized a probable cause tree structure for future analysis.
Owner:IBM CORP
Malicious program detection method and scan engine
ActiveCN102779249AImprove accuracyImprove efficiencyComputer security arrangementsFeature extractionFeature data
The invention provides a malicious program detection method and a scan engine. The malicious program detection method includes: obtaining file information from a malicious program sample and a normal program sample, wherein the file information includes file names and file paths; using the feature selection algorithm to perform feature extraction for the obtained file information; using the machine learning algorithm to generate a feature model according to feature data extracted in feature extraction; and using the feature model to detect malicious programs and process detected malicious programs. By aid of the malicious program detection method and the scan engine, effective searching and killing of the malicious programs are achieved.
Owner:三六零数字安全科技集团有限公司
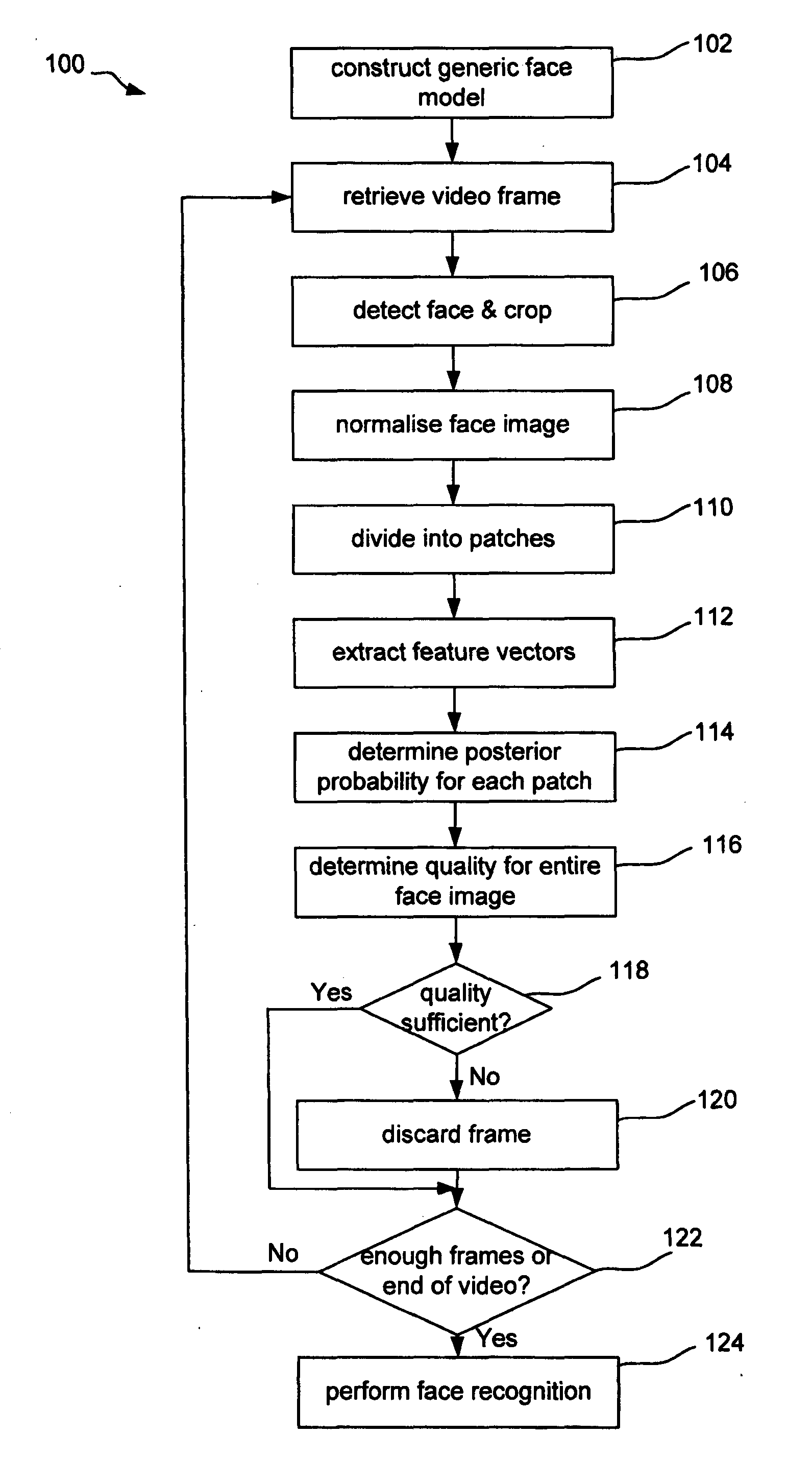
Image quality assessment
ActiveUS20140044348A1Quality improvementProbability is accurateCharacter and pattern recognitionPattern recognitionImaging quality
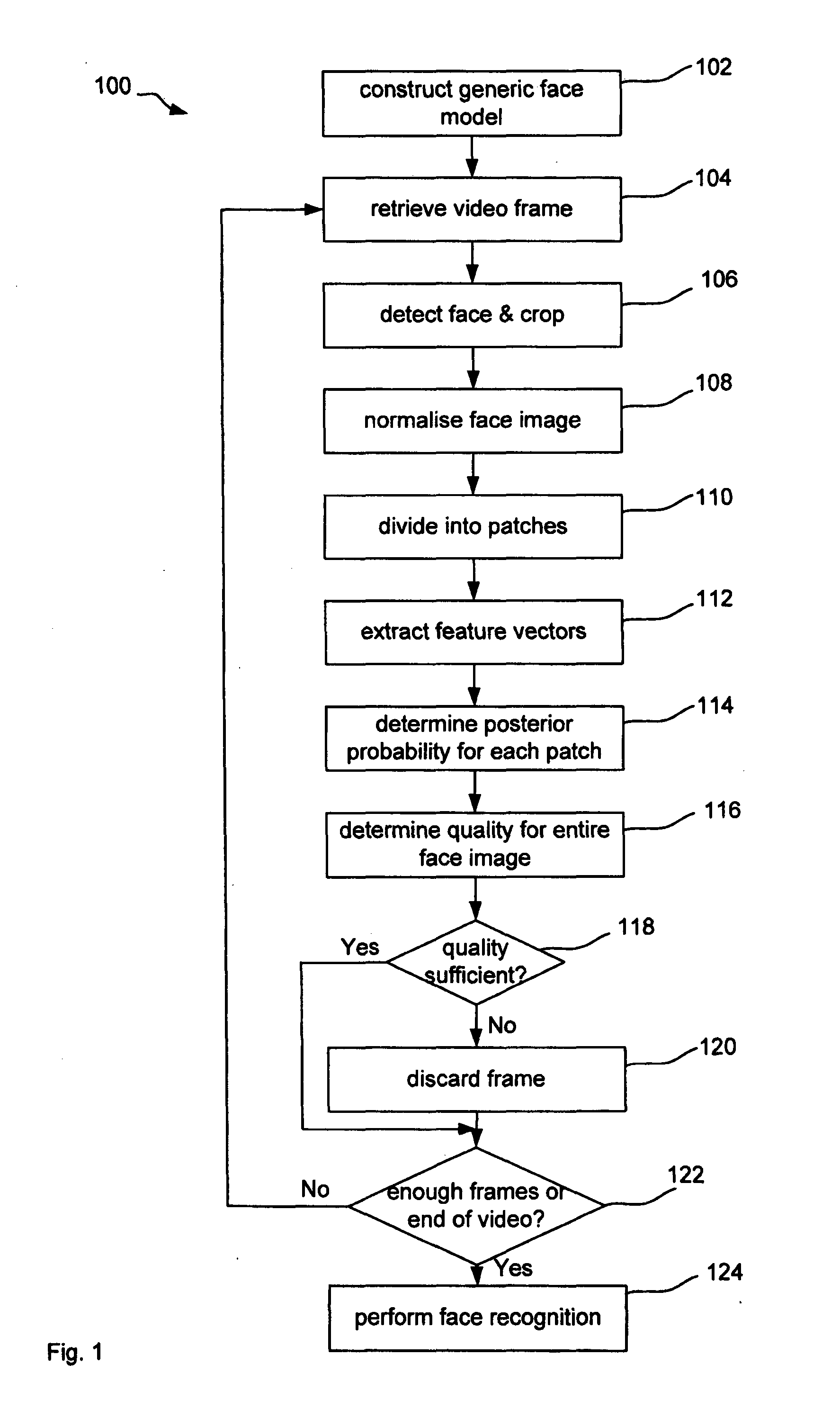
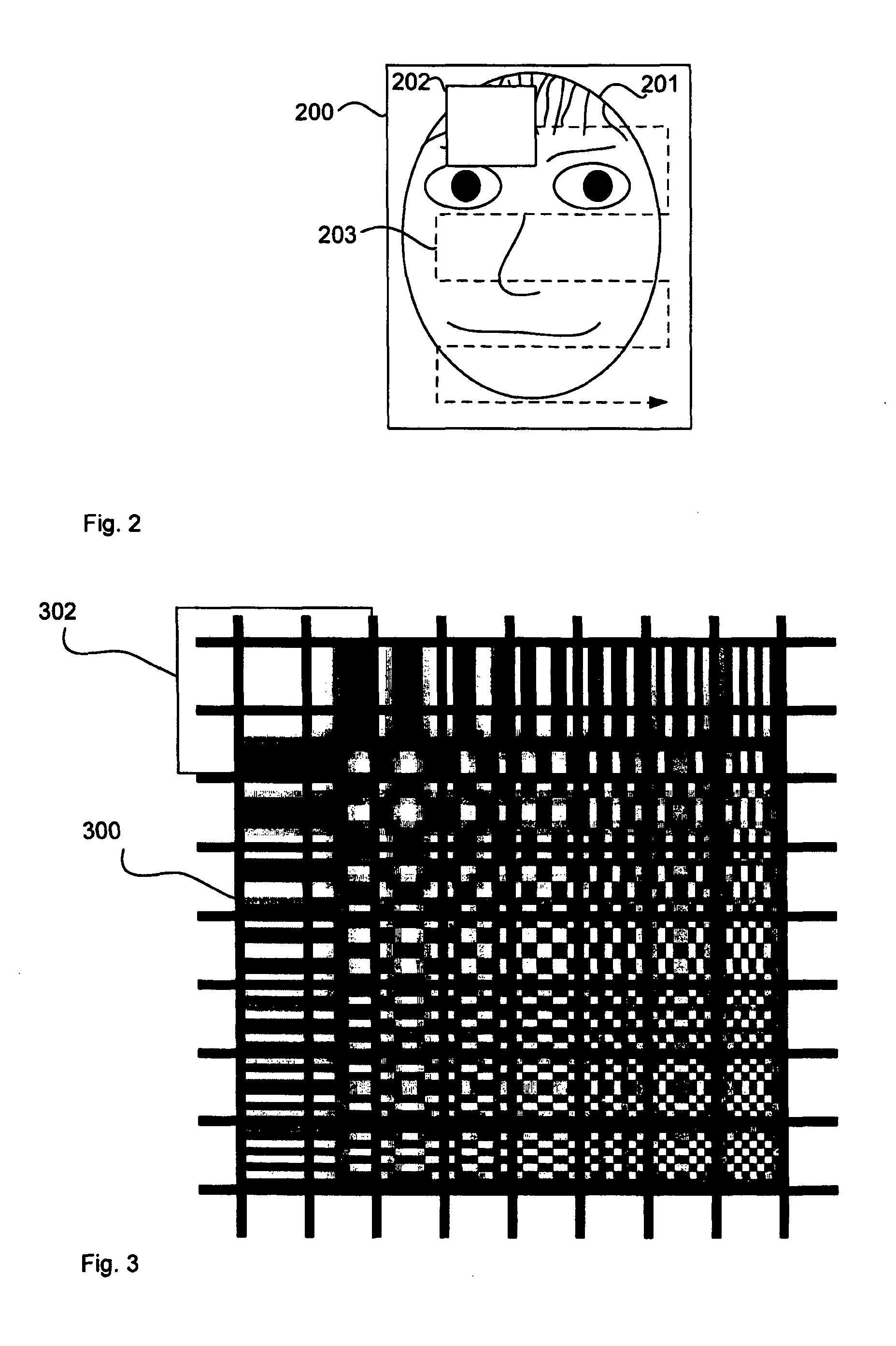
This disclosure concerns image quality assessment. In particular, there is described a computer implemented method, software, and computer for assessing the quality of an image. For example but not limited to, quality of the image of a face indicates the suitability of the image for use in face recognition. The invention comprises determining (112) a similarity of features of two or more sub-images of the image (608) to a model (412) of the object which is based on multiple training images (612) of multiple different objects of that type. The model (412) is comprised of sub-models (406) and each sub-model (406) corresponds to a sub-image of the image (608). Determining similarity is based on the similarity of features of each sub-image to features modelled by the corresponding sub-model. It is an advantage that no input parameters are required for quality assessment since the quality of the image can be determined from only the similarity between the image and the same, therefore single generic, model.
Owner:IOMNISCIENT
Real-time recommendation system and method based on Spark
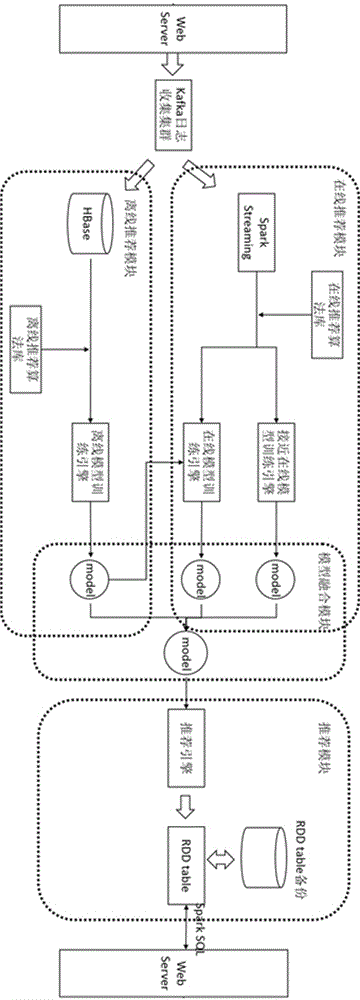
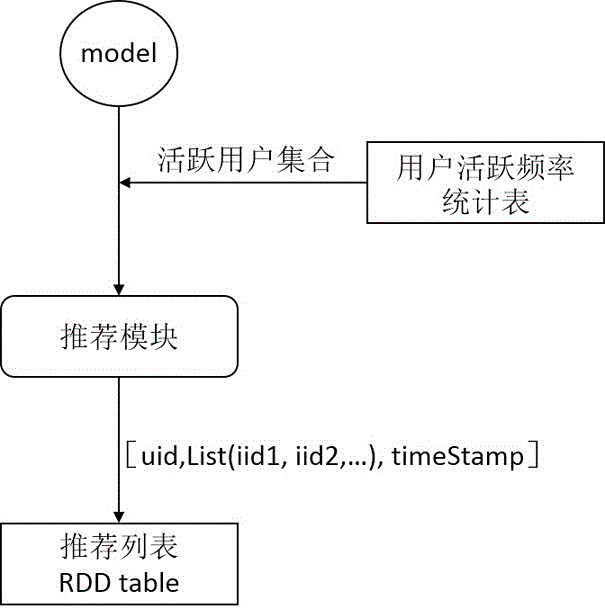
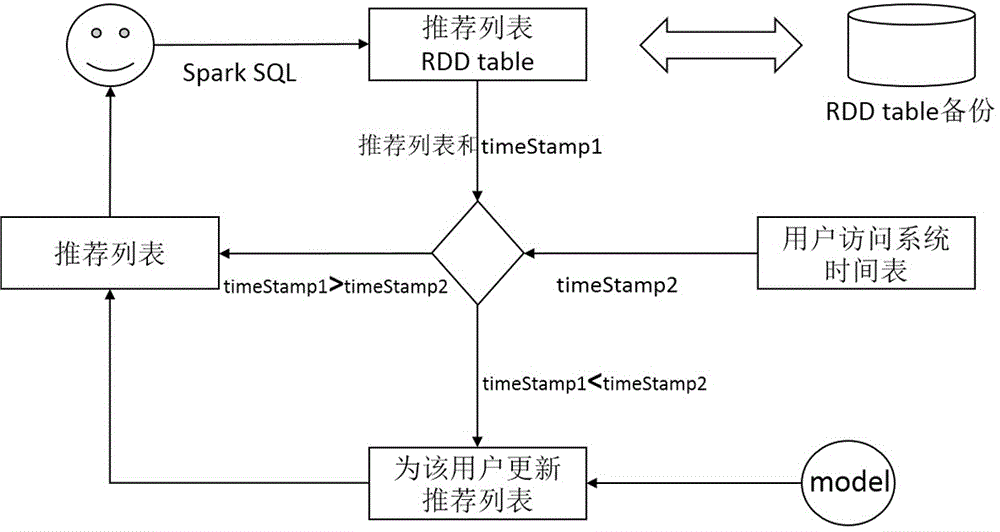
ActiveCN106126641AImprove real-time performanceImprove training efficiencySpecial data processing applicationsOnline modelData collecting
The invention discloses a real-time recommendation system and method based on Spark. A stacked recommendation system framework based on Spark is constructed, and comprises a data collecting module, an offline recommendation module, an online recommendation module and a recommendation module. The offline recommendation module is used for selecting a corresponding recommendation algorithm from an offline recommendation algorithm library according to user configuration parameters to train user behavior data, and a user feature model is obtained; the online recommendation module is used for sending the user behavior data to corresponding algorithms in an online recommendation algorithm library for training, and an increment user feature model is obtained; an online model training engine is used for adopting the user feature model obtained through training as a basic model, carrying out incremental updating through a current increment recommendation algorithm and the newly received user behavior data, and a newest user feature model is obtained. The recommendation module is used for updating a user recommendation list in combination with an inertia updating mechanism according to the user feature model. The accuracy and timeliness of the recommendation result can be effectively improved.
Owner:UNIV OF SCI & TECH OF CHINA
Software project development method and device
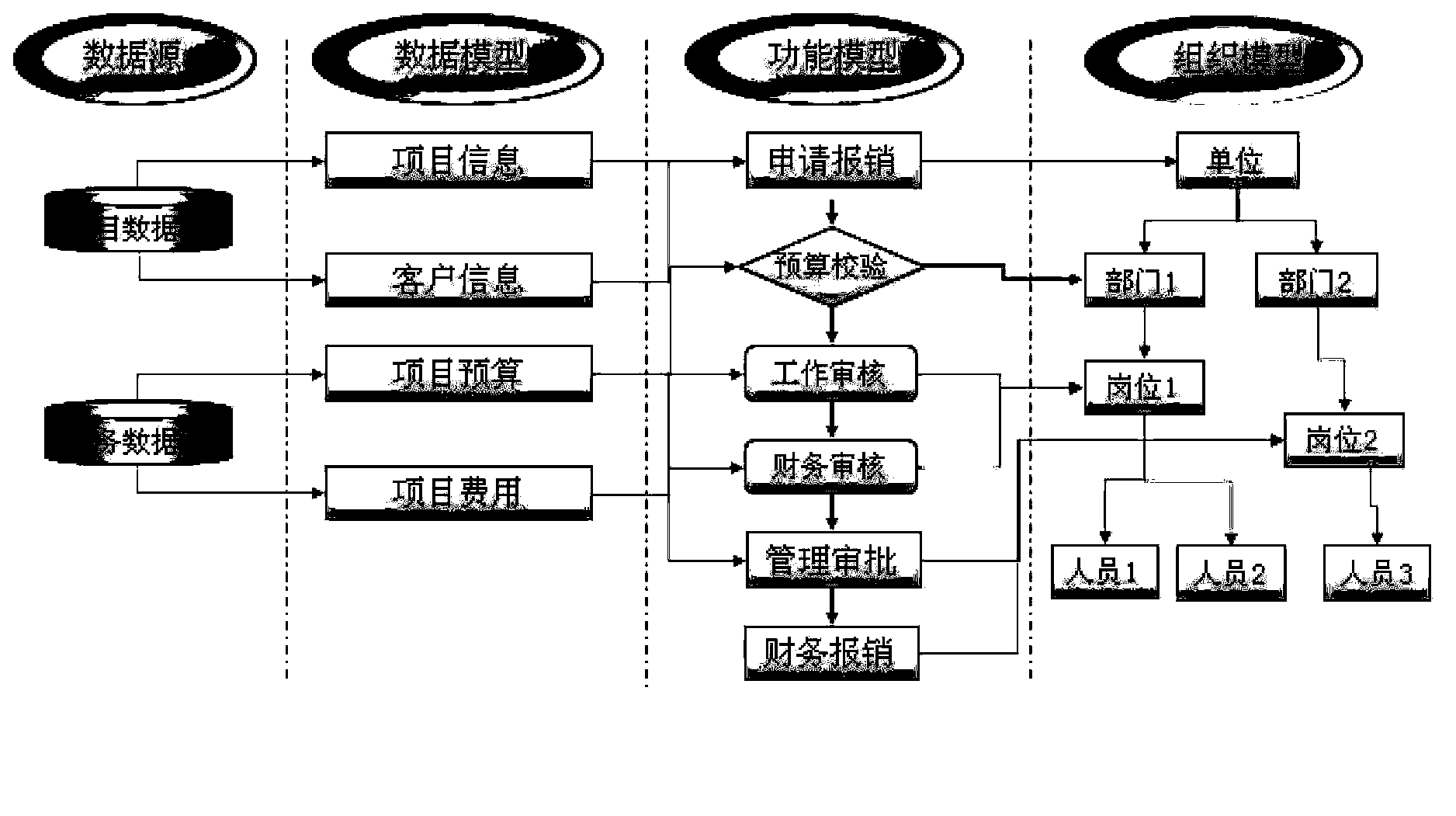
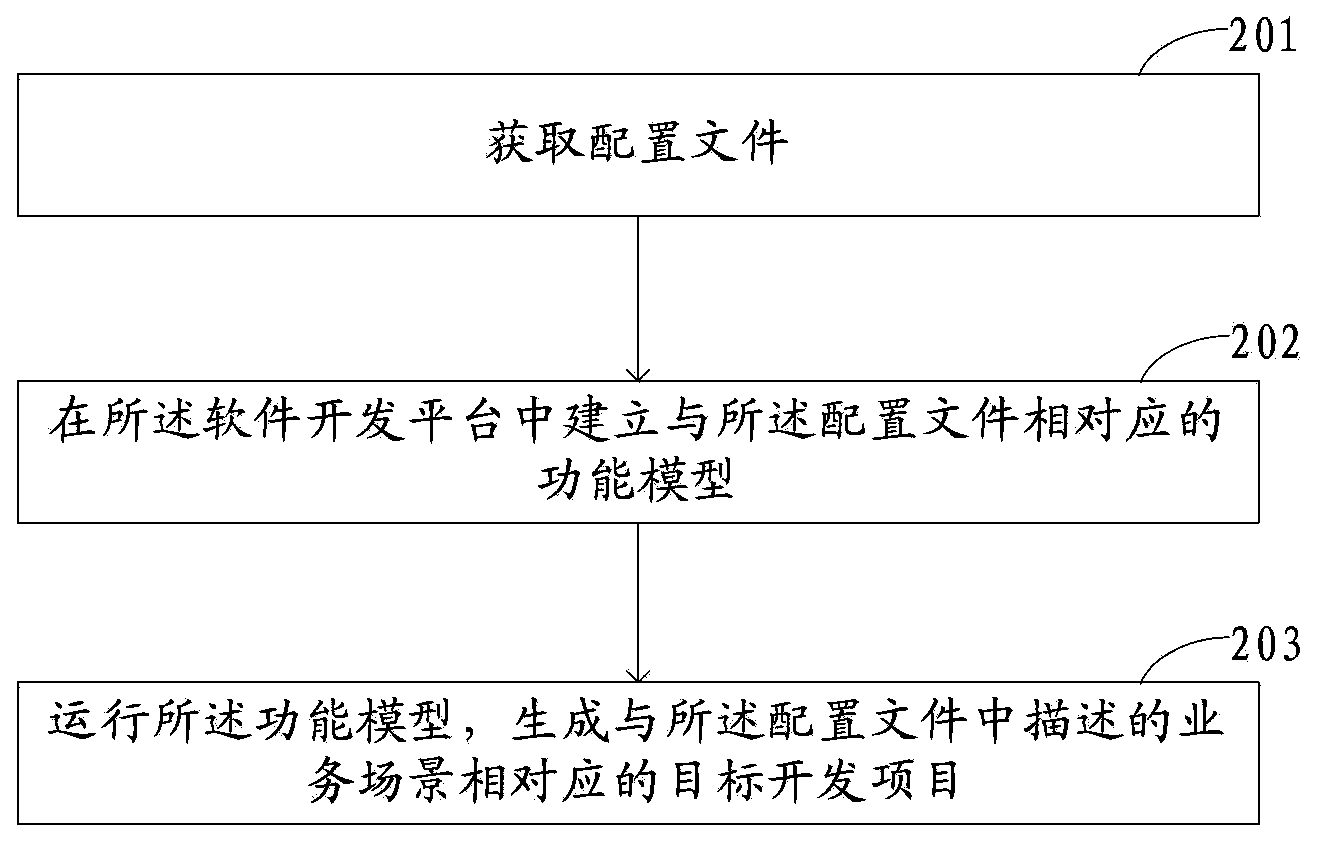
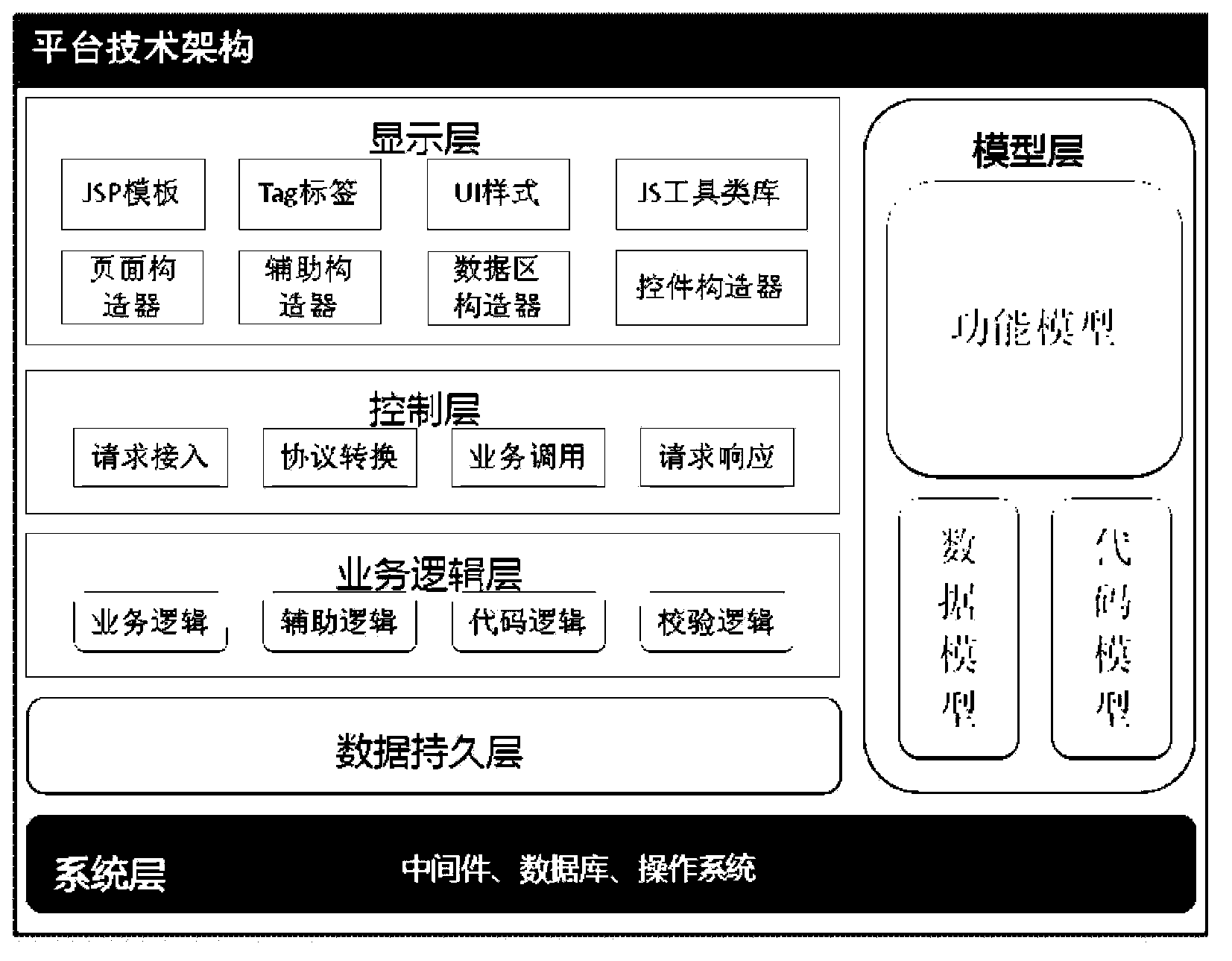
ActiveCN104111826AShort processReduce labor costsSpecific program execution arrangementsData operationsData source
The invention discloses a software project development method and device which is applied to a software development platform. The software development platform is provided with a function model template capable of establishing function models. The software project development method includes acquiring configuration files containing header configuration information of target development projects, page layout configuration information, service logic configuration information, data operation area configuration information, page data source relation configuration information, toolbar configuration information and external resource configuration information; establishing the corresponding function models of the configuration files, wherein the function models include header entries, page layout items, service logic items, data operation area items, page data source relation items, toolbar items and external resource items; running the function models and generating the target development projects corresponding to service scenes described in the configuration files.
Owner:杭州新世纪电子科技有限公司
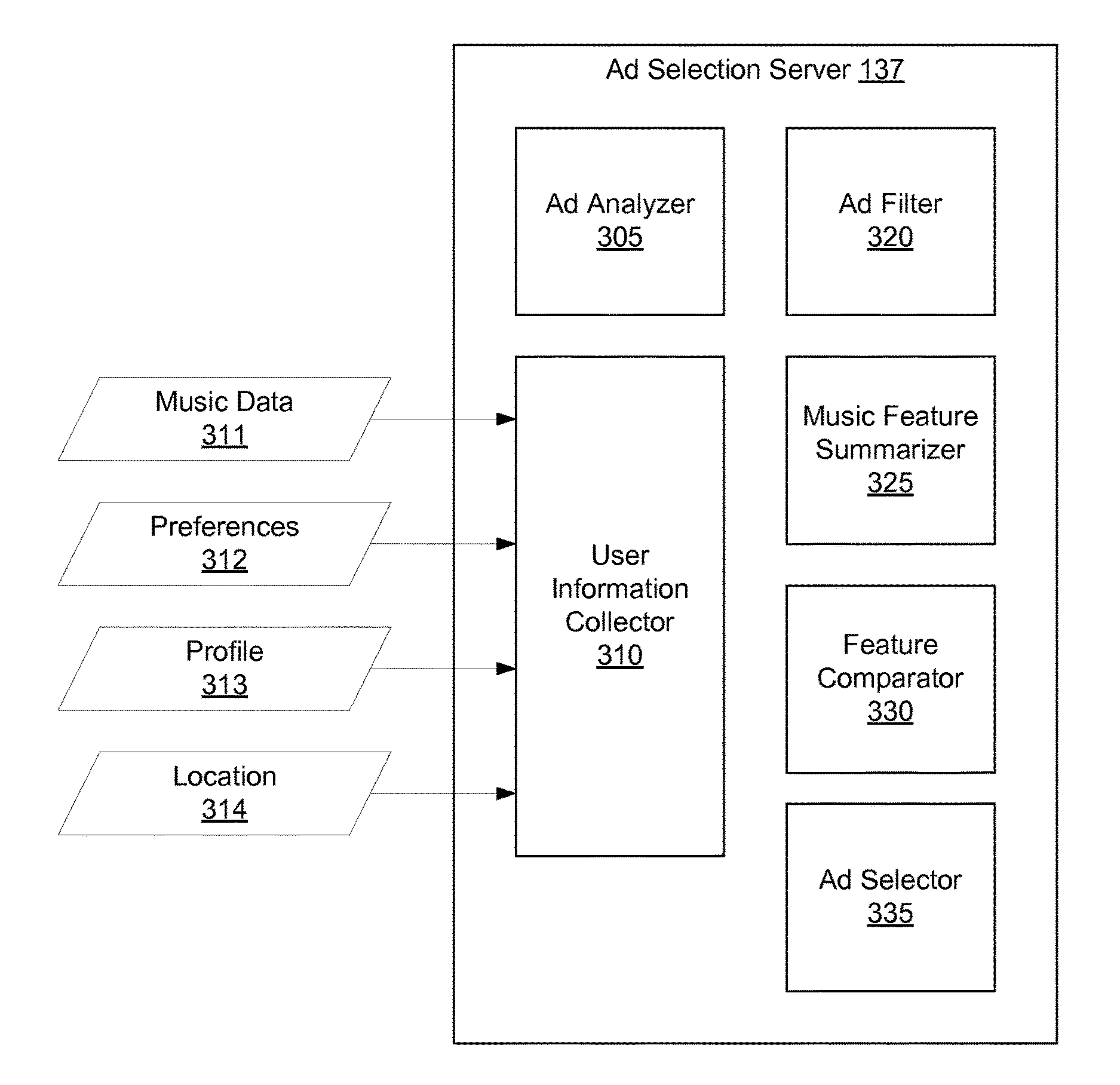
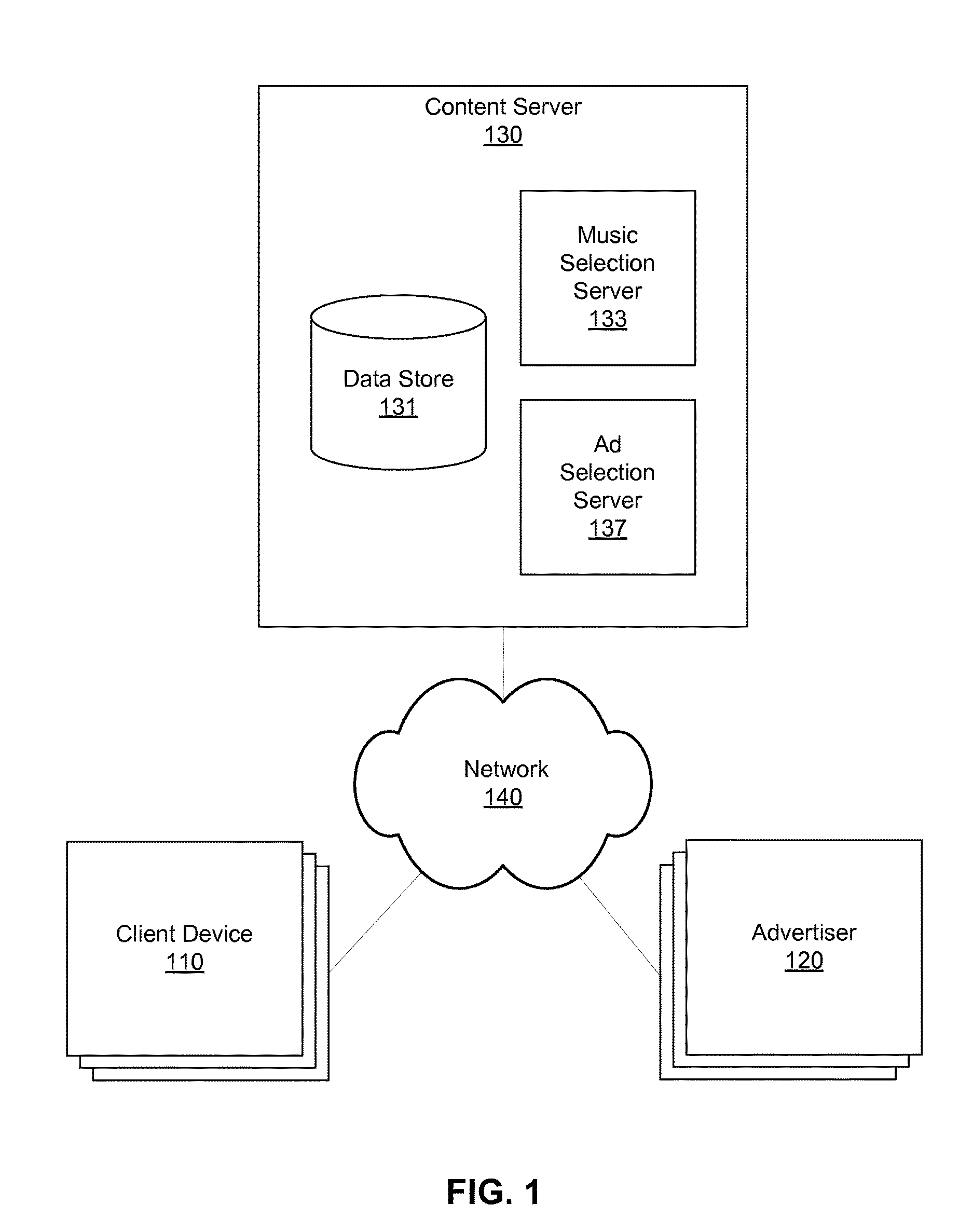
Relating Acoustic Features to Musicological Features For Selecting Audio with Similar Musical Characteristics
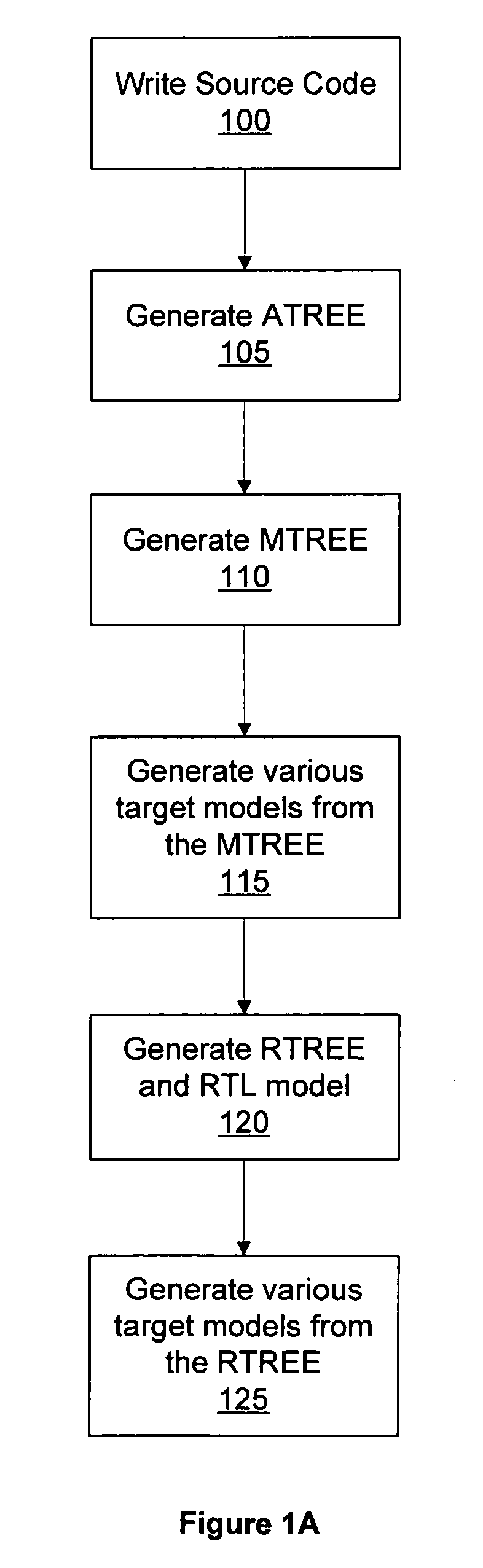
A content server uses a form of artificial intelligence such as machine learning to identify audio content with musicological characteristics. The content server obtains an indication of a music item presented by a client device and obtains reference music features describing musicological characteristics of the music item. The content server identifies candidate audio content associated with candidate music features. The candidate music features are determined by analyzing acoustic features of the candidate audio content and mapping the acoustic features to music features according to a music feature model. Acoustic features quantify low-level properties of the candidate audio content. One of the candidate audio content items is selected according to comparisons between the candidate music features of the candidate audio advertisements and the reference music features of the music item. The selected audio content is provided the client device for presentation.
Owner:PANDORA MEDIA
Method and system for gesture recognition and man-machine interaction based on 2D video sequence
InactiveCN104992171AStable and reliable identificationStable and reliable trackingInput/output for user-computer interactionCharacter and pattern recognitionFrame sequenceVideo sequence
The invention discloses a method and a system for gesture recognition and man-machine interaction based on a 2D video sequence. The method comprises the steps of S1, acquiring a monocular 2D video frame sequence image, and extracting moving foreground in the image; S2, detecting a human hand in the moving foreground, and constructing a joint feature model of the human hand; S3, predicting a location area where a human hand target emerges, searching and positioning the human hand target in the location area by using the joint feature model of the human hand, and acquiring the location of the human hand in the current frame; S4, judging the type of the current operating mode according to the location of the human hand in the current frame; and S5, tracking the human hand, recognizing the posture and the gesture of the human hand in the current operating mode, converting the posture and the gesture into a corresponding instruction so as to realize man-machine interaction. The man-machine interaction method disclosed by the invention not only can realize target hand selection at a complicated background, but also can realize high-accuracy and high-stability tracking for the human hand.
Owner:WUXI YSTEN TECH
Method for identifying benign and malignant lung nodules based on multi-dimensional information
InactiveCN103745227AFit the mindsetAccurate featuresImage analysisCharacter and pattern recognitionMulti dimensionalFeature modeling
The invention discloses a method for identifying benign and malignant lung nodules based on multi-dimensional information. The method comprises the following steps: 1, representing a three-dimensional nodule in a two-dimensional way; 2, building a feature model; 3, building a fuzzy classifier; 4, evaluating the classifying performance. The method has the beneficial effects that accurate feature modeling is crucial to the identification of benign and malignant lung nodules. More objective bases are laid for the identification of the benign and malignant lung nodules by adopting imaging diagnosis features, common shapes and textual features in image processing, and patient information, feature extraction is performed on a two-dimensional image generated on the basis of a helical scanning technology, and a novel method is adopted for feature modelling, so that the extracted features are more accurate. In the method, a fuzzy C-means (FCM) clustering algorithm is adopted for identifying benign and malignant status of a suspected nodule, and a probability indicating the suspected nodule is benign or malignant is given, so that the method is more accordant with the thinking mode of a doctor.
Owner:SHENYANG AEROSPACE UNIVERSITY
Commodity management method and system based on image recognition technology
ActiveCN107292248AImprove the efficiency of obtaining product informationLow costCharacter and pattern recognitionResourcesPattern recognitionImaging Feature
The invention discloses a commodity management method based on the image recognition technology, and the method comprises the following steps: obtaining a commodity display image; extracting the first-level image features of each commodity at different shelf layers in the commodity display image; carrying out the matching of the first-level image features according to a preset first-level image feature model, and generating a first matching value according to a matching result; judging whether the first matching value is greater than a preset first matching threshold value or not: obtaining the commodity information if the first matching value is greater than the preset first matching threshold value, or else extracting second-level image features of each commodity in the commodity display image, carrying out the matching of the second-level image features according to a preset second-level image feature model, and obtaining the commodity information according to a matching result; generating a commodity information report according to the obtained commodity information, and displaying the commodity information report. The invention also provides a commodity management system based on the image recognition technology. The method can achieve the automatic recognition of the commodity information of commodities on each shelf in a shop, and can improve the obtaining efficiency of the commodity information, and reduce the cost.
Owner:GUANGZHOU LOYA INT MARKET INFORMATION RES
A page generation method facing to Web application system
ActiveCN101676910AAdd customizable operationsIncrease flexibilitySpecial data processing applicationsDatabase interfaceWeb application
The invention discloses an automatic page generation method facing to Web application system. The method adopts Unified Modeling Language (UML) modeling technology and Extensive Makeup Language (XML) technology, and adopts FMDP model. The method includes steps of: generating a function model, an inner model, a database interface model and an expression model of the Web application system; generating system customized information based on the models, and concentrating in documents in format of XML to store in the system server terminal; and providing client subscriber a function of conveniently modifying the original customized information based on the customization needs. Customization of the Web application system is realized in the genuine meaning by the invention, and customized Web application system can be quickly generated by using the invention, and regulation of system demand can be realized on the premise of avoiding recompilation of the whole system, to improve the development efficiency of the Web software.
Owner:PEKING UNIV +2
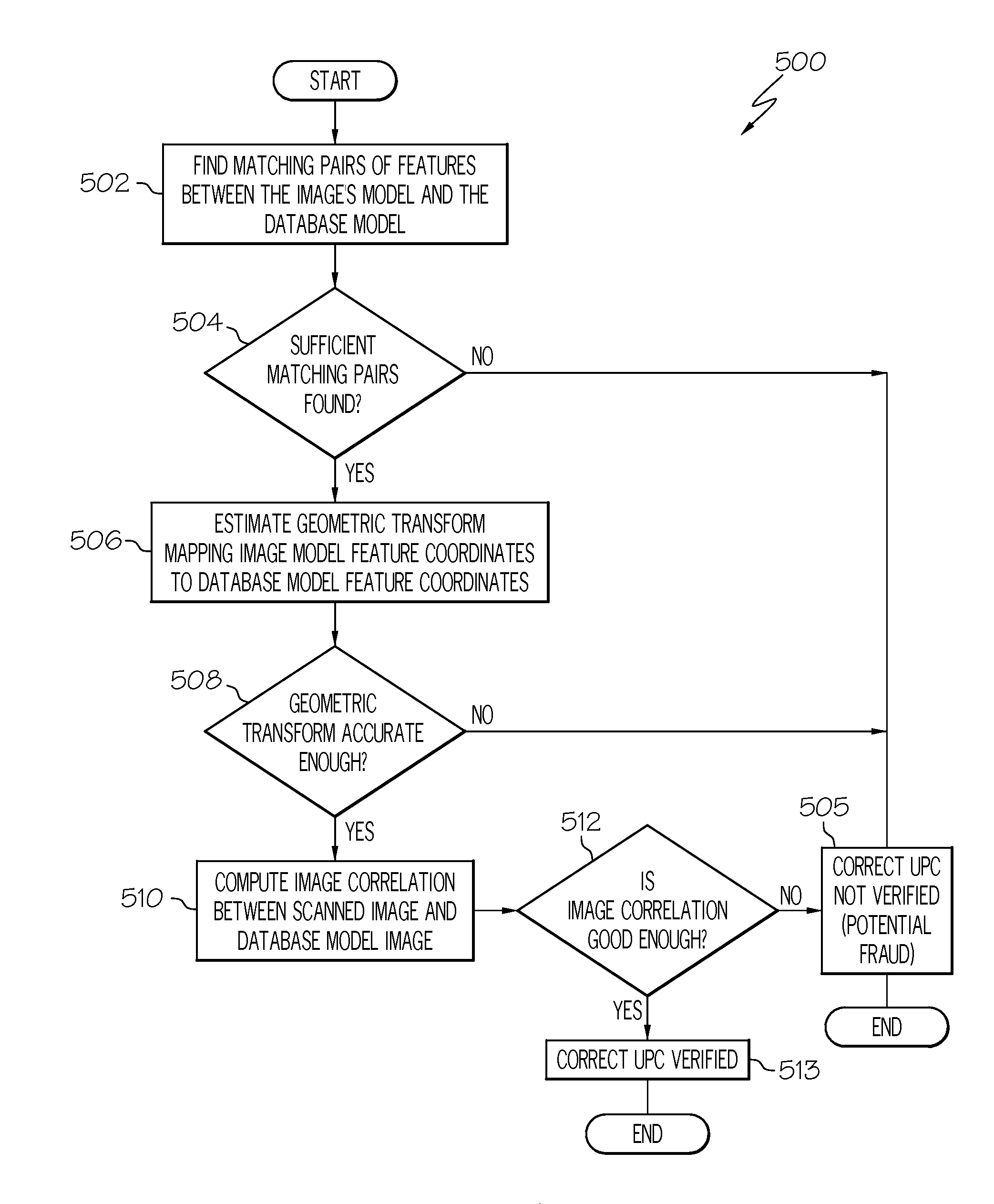
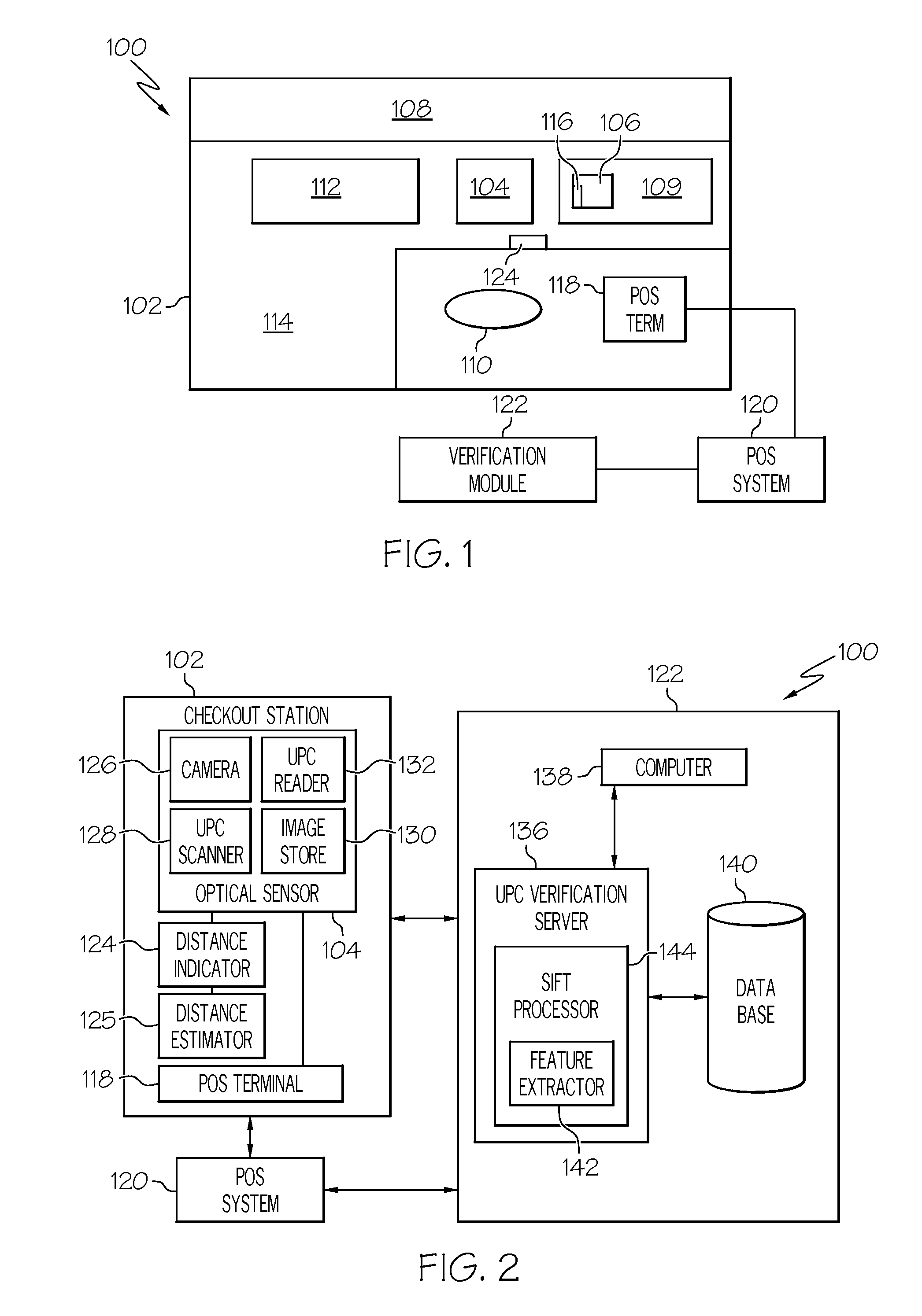
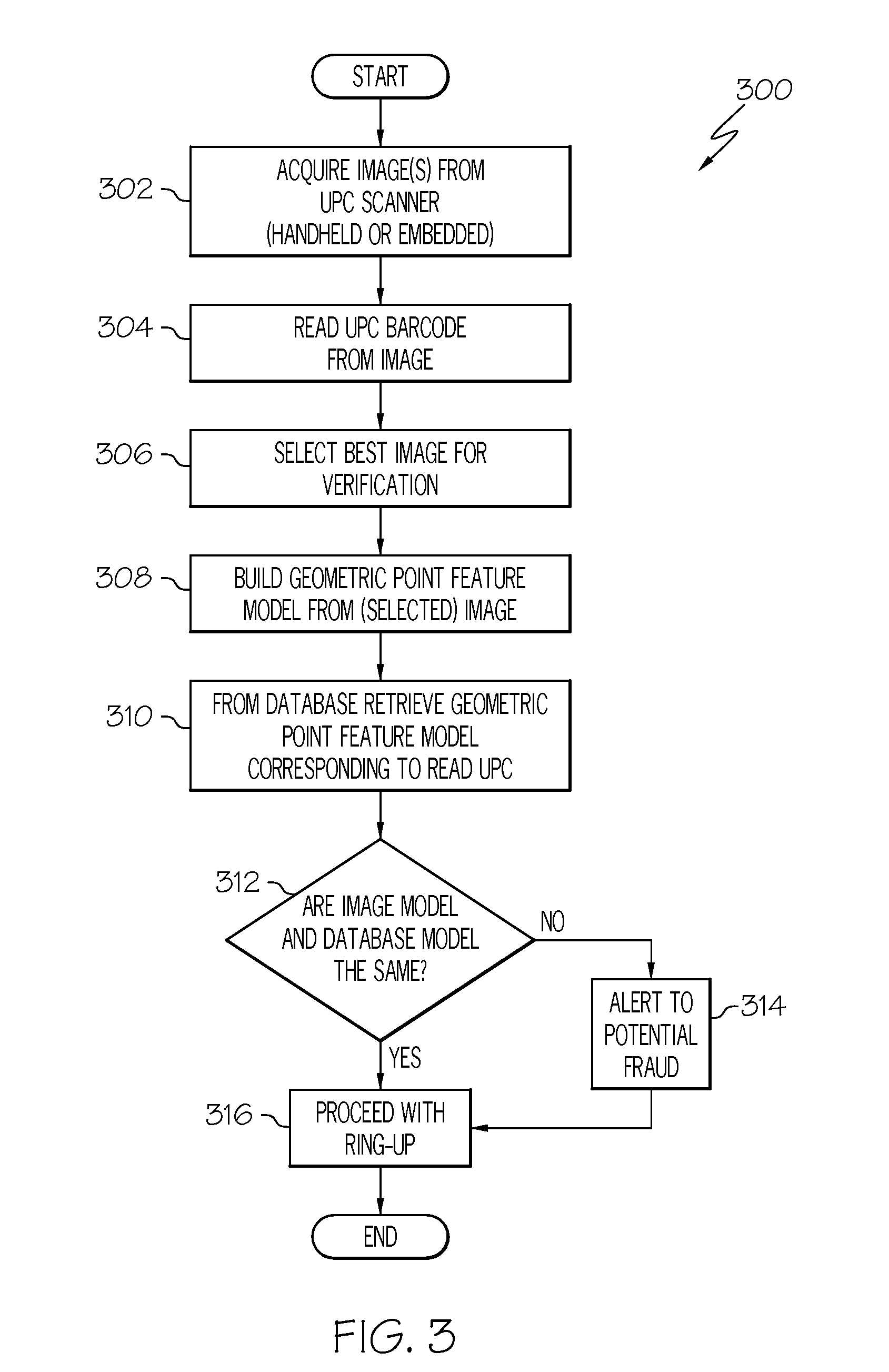
UPC substitution fraud prevention
A system and method for detecting fraudulent identification tags, such as Universal Product Codes (UPC) applied to goods to be purchased is disclosed. Images of the goods to be purchased and corresponding feature models are stored in a database. When a customer desires to purchase an item containing a UPC, a scanned image of the item about to be purchased may be acquired and a feature model of the scanned image may be created. The system may retrieve from the database the image and feature model previously stored for the item associated with the just-scanned UPC. A variety of image processing techniques may be used to compare the scanned and database images and / or the scanned and database feature models. In one embodiment, these image processing techniques may include determining a geometric transformation that maps the features of the scanned image onto the features of a database model.
Owner:DATALOGIC ADC
Random voiceprint certification system, random voiceprint cipher lock and creating method therefor
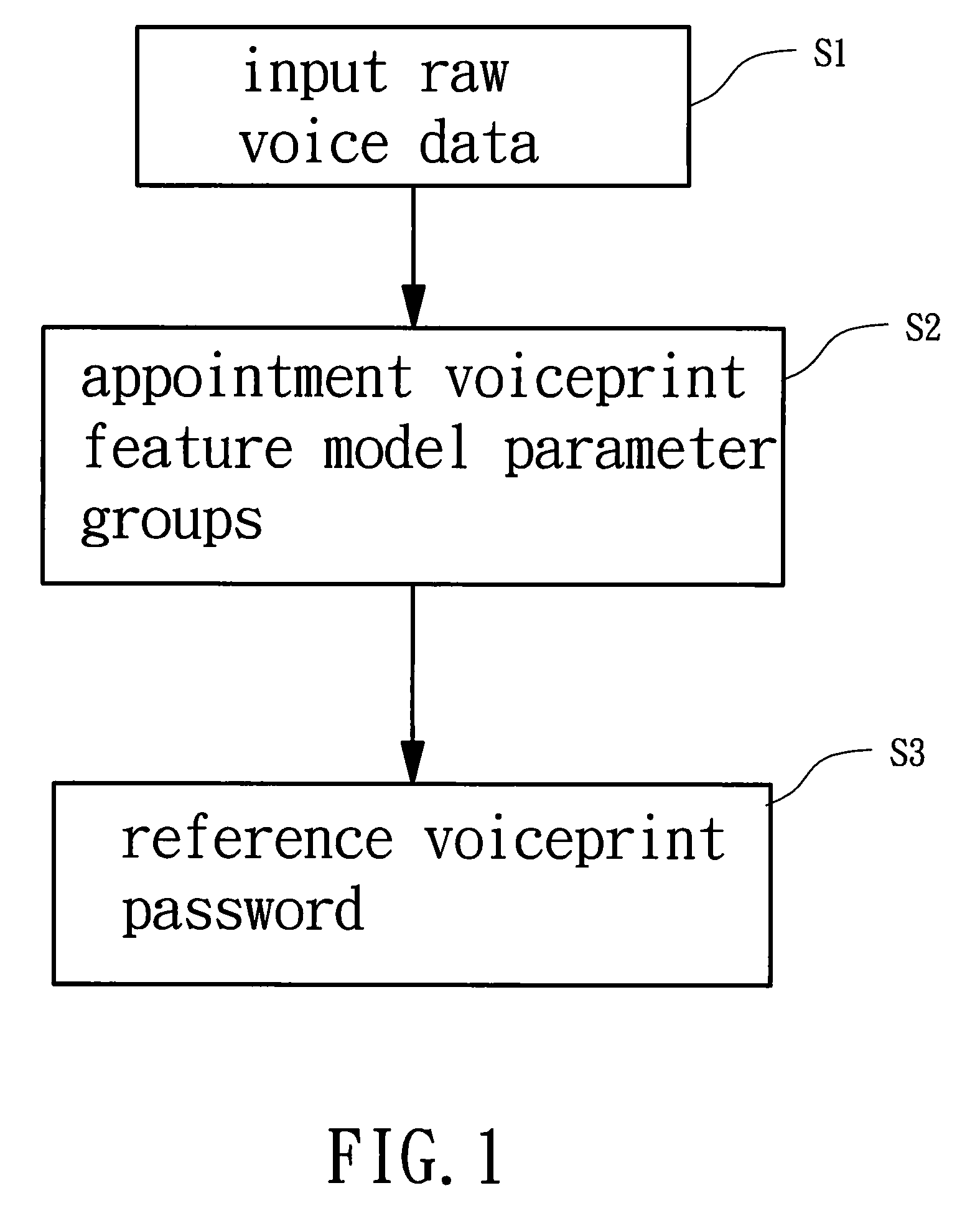
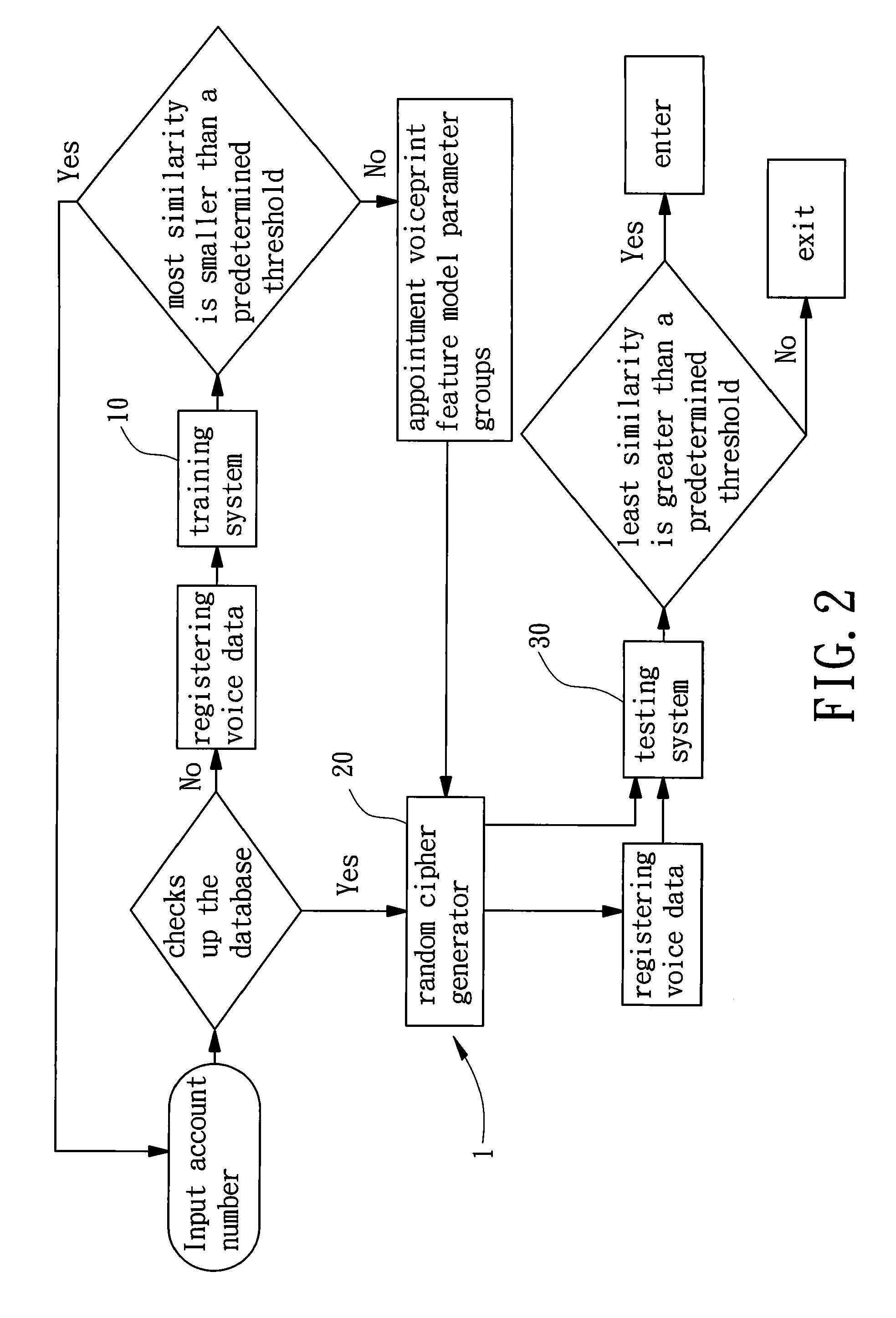
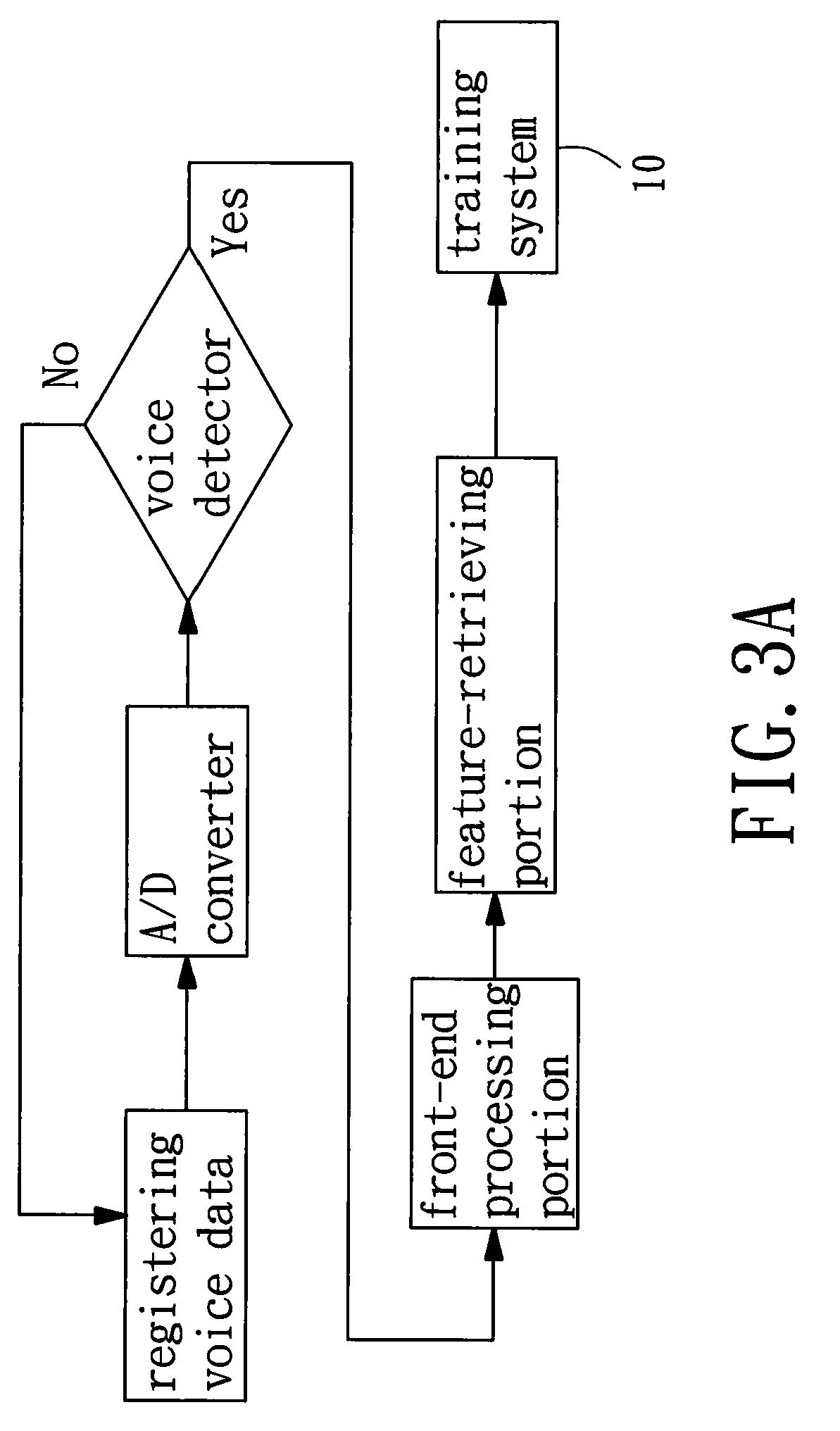
InactiveUS20100017209A1Improve reliabilityReliability of the random voiceprint certification system can be improvedDigital data authenticationSecret communicationPasswordSecret code
The present invention provides a random voiceprint certification system comprises a training system, a random cipher generator, and a testing system, which is employed to process training or testing operation for the input raw voice data. In training voice, the training system obtains an appointment voiceprint feature model parameter groups from the input raw voice data. From the appointment voiceprint feature model parameter groups several voiceprint characteristic units are obtained and at least one reference voiceprint password, which is for the testing system to carry out the voice testing operation is built. In processing testing voice, the random cipher generator generates randomly at least one reference voiceprint password from the voiceprint characteristic units of the appointment voiceprint feature model parameter groups to build the random voiceprint cipher lock. The present invention generates randomly one or several reference voiceprint passwords. The random voiceprint certification system is built completely to form the random voiceprint cipher lock. Therefore, the effect of not easy for illegal invasion can be achieved.
Owner:TOP DIGITAL
Building integrated circuits using a common database
InactiveUS7363610B2Improved performance per watt of power consumptionCAD circuit designSoftware simulation/interpretation/emulationComputer architectureHigh-level programming language
Systems and methods for designing and generating integrated circuits using a high-level language are described. The high-level language is used to generate performance models, functional models, synthesizable register transfer level code defining the integrated circuit, and verification environments. The high-level language may be used to generate templates for custom computation logical units for specific user-determined functionality. The high-level language and compiler permit optimizations for power savings and custom circuit layout, resulting in integrated circuits with improved performance per watt of power consumption.
Owner:NVIDIA CORP
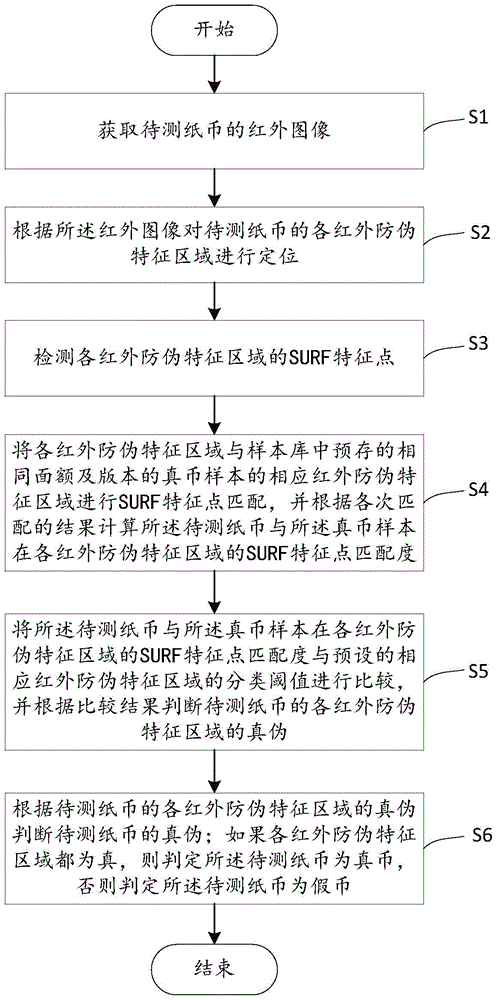
Paper currency recognition method and system
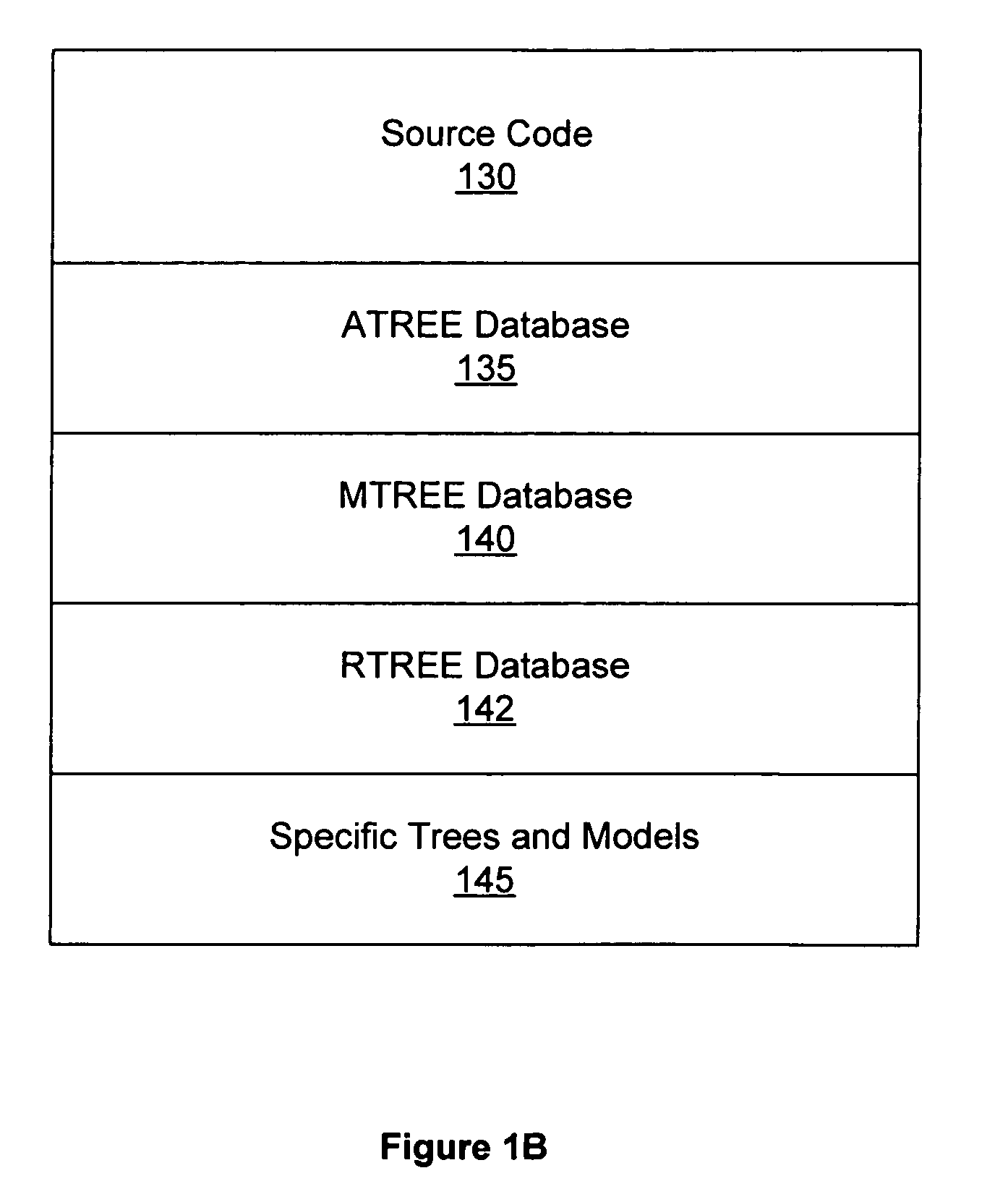
ActiveCN104318257AAvoid detectionLess distracting factorsPaper-money testing devicesCharacter and pattern recognitionPattern recognitionImaging processing
The invention relates to the technical field of image processing, in particular to a paper currency recognition method and system. On the basis of a speeded-up robust feature (SURF) and model matching, each infrared anti-counterfeiting feature area of paper currency to be tested is subjected to SURF point detection, and then, the infrared anti-counterfeiting feature area is matched with a corresponding feature model of a real paper currency sample so as to realize a purpose of judging the authenticity of the paper currency to be tested. Compared with the prior art, the invention avoids detection to areas which do not exhibit practical meanings to a detection result on the paper currency, interference factors are reduced, and a detection result is more accurate. Meanwhile, detection calculated amount is reduced, and detection speed is quickened.
Owner:SHENZHEN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com