Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
845 results about "Encapsulated data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
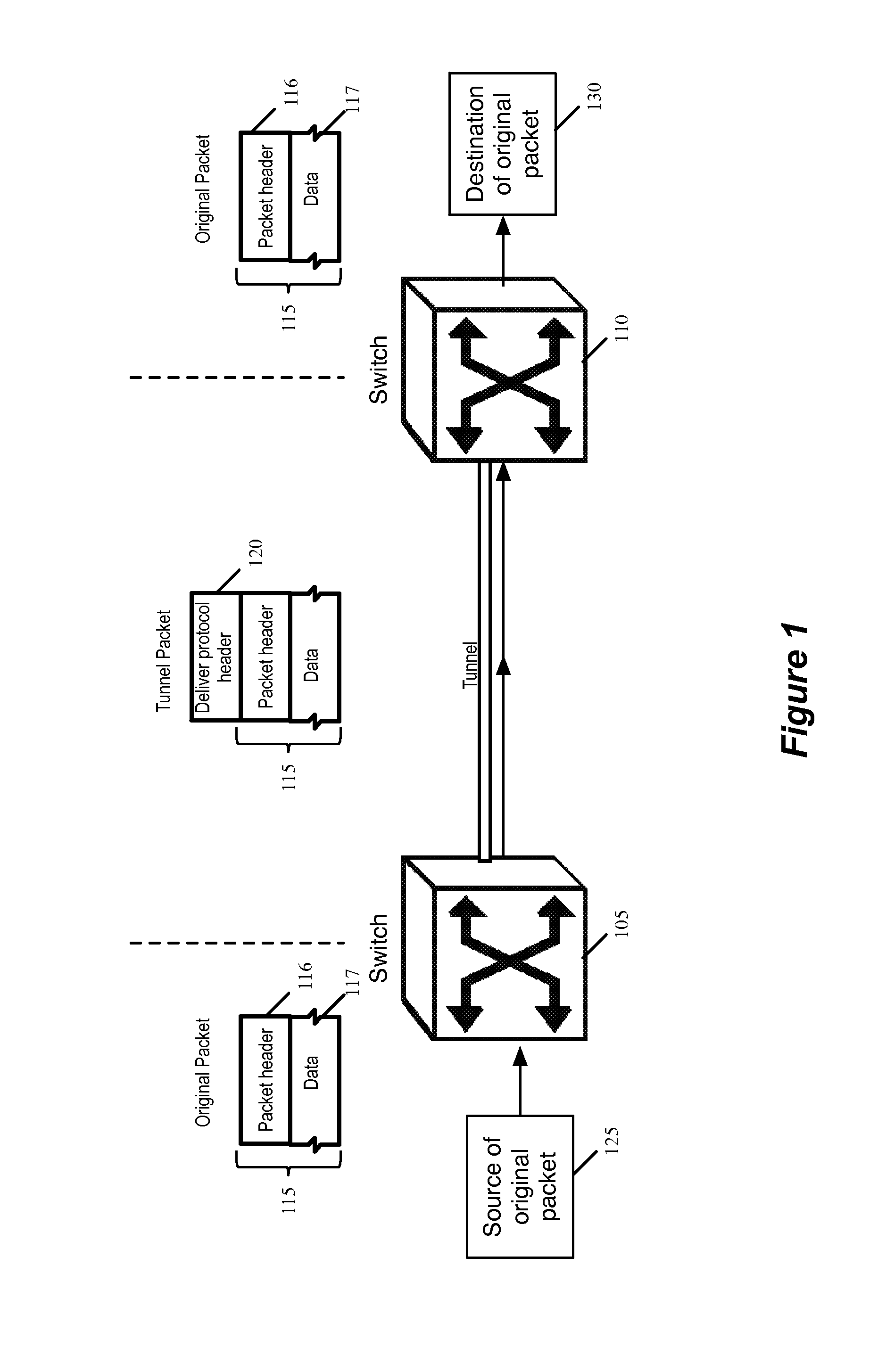
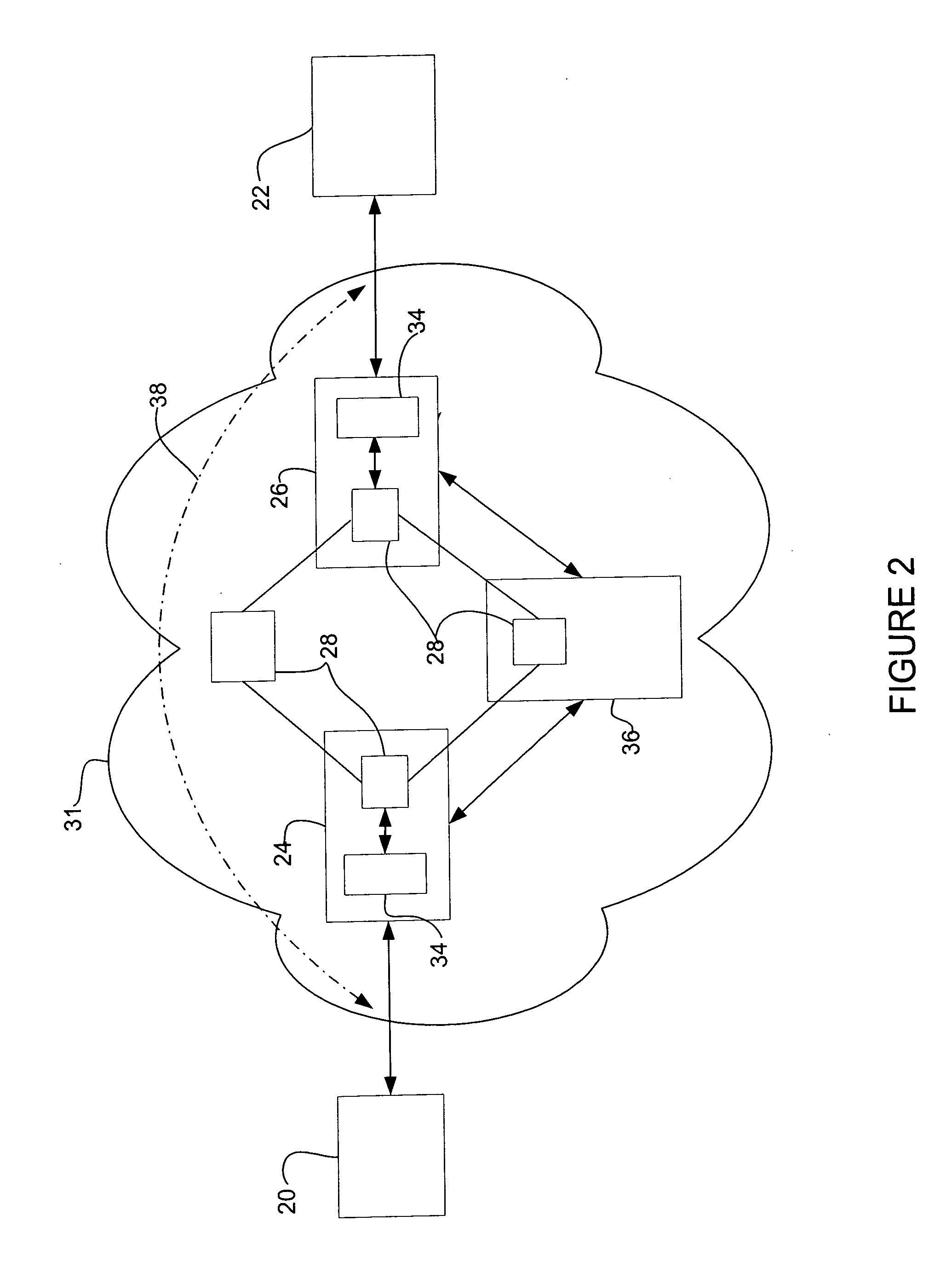
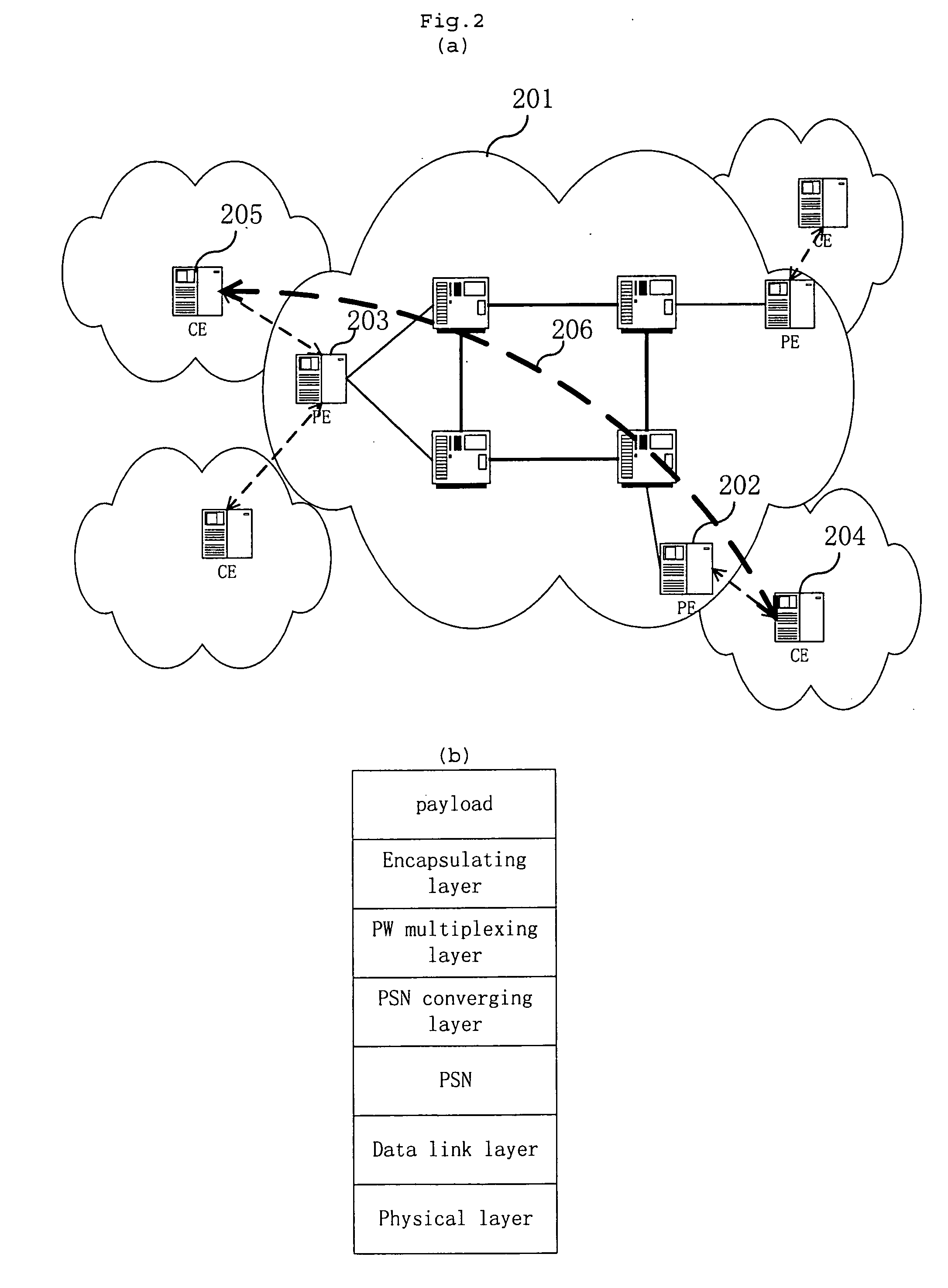
Data encapsulation refers to sending data where the data is augmented with successive layers of control information before transmission across a network.
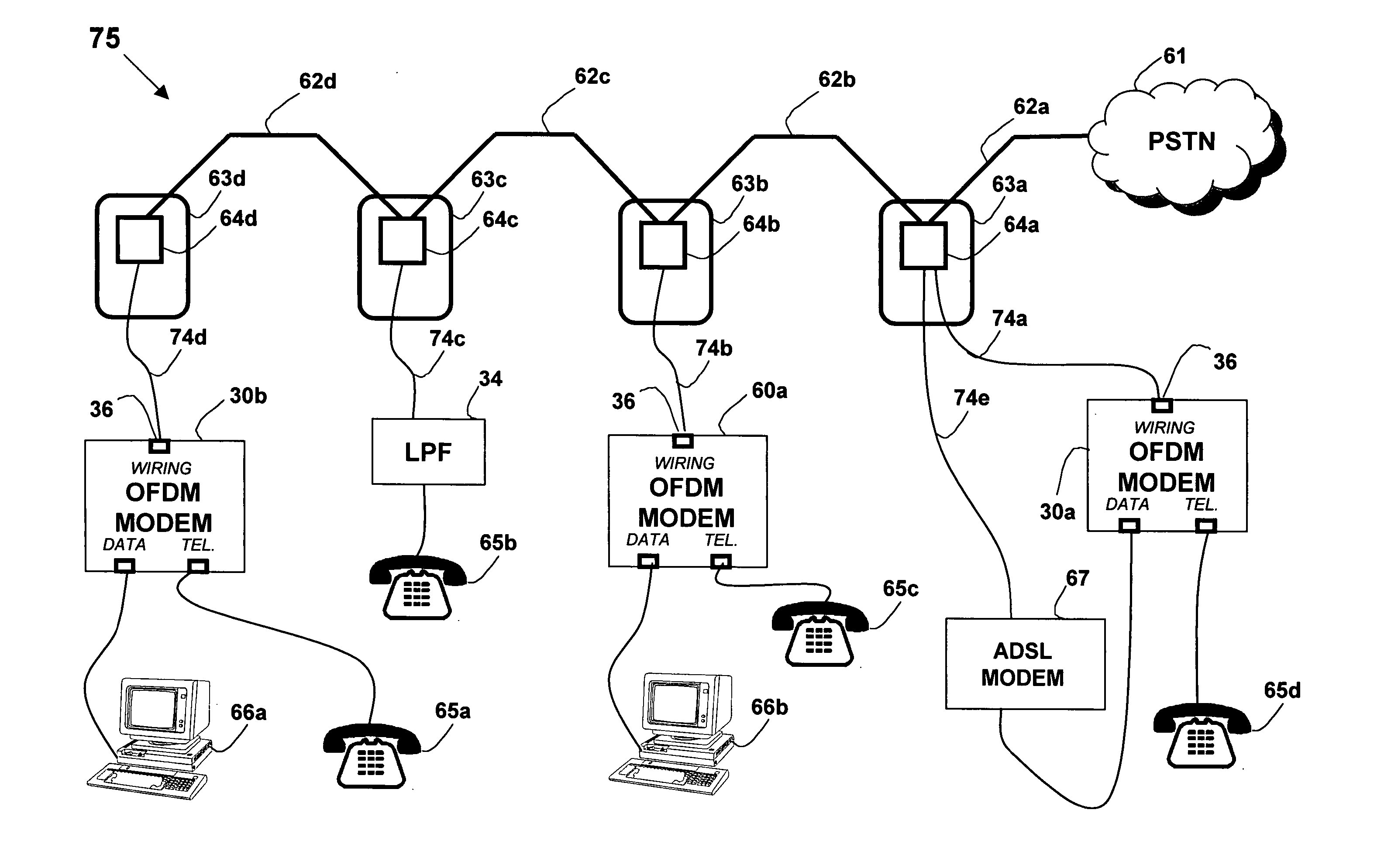
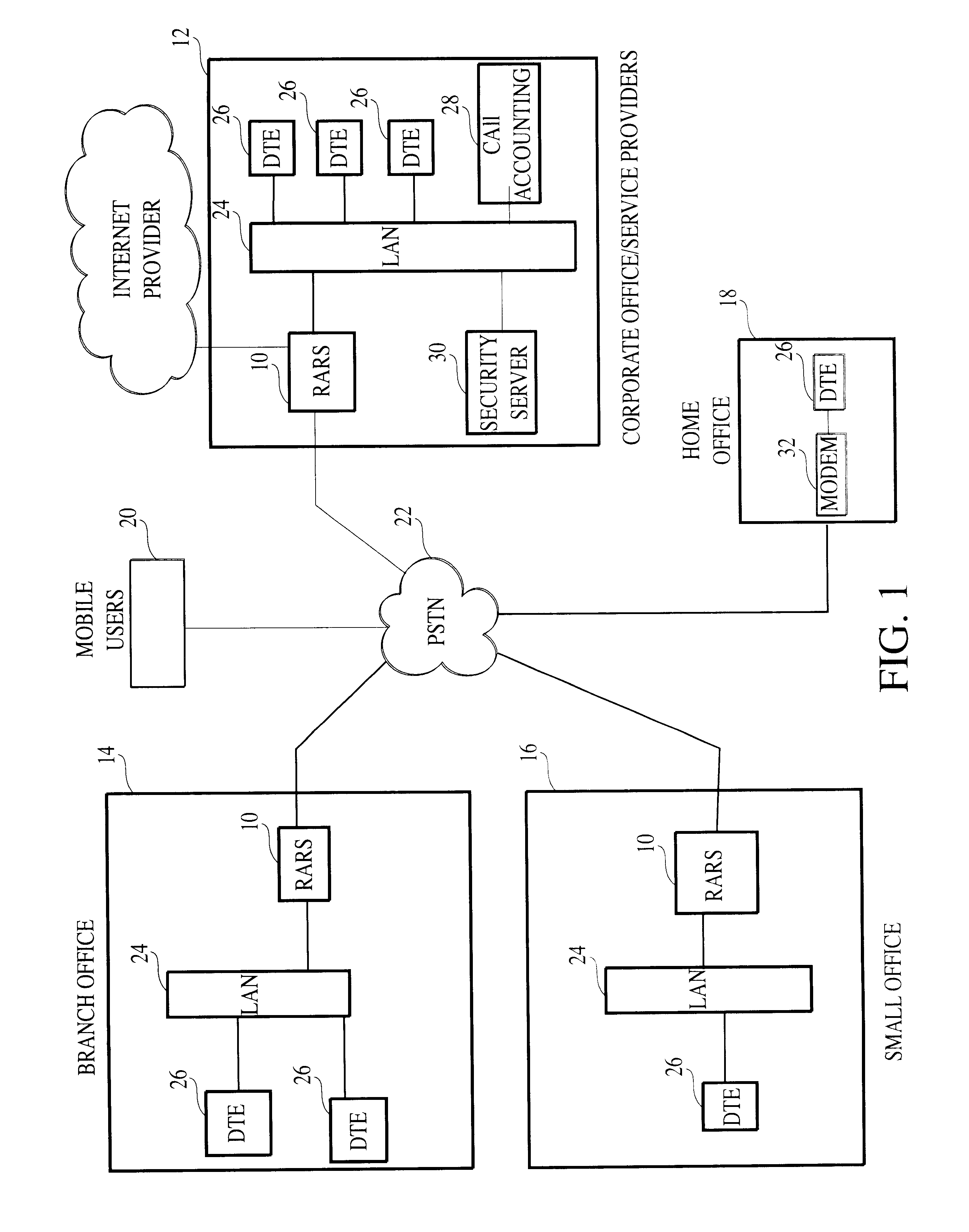
System and method for carrying a wireless based signal over wiring
InactiveUS20050249245A1Power distribution line transmissionFrequency-division multiplexData connectionModem device
A device, network and method wherein a standard wireless modem is coupled to wiring for carrying a wireless baseband signal that may be OFDM based, and may be directly generated by the wireless IF modem, or extracted from the modem RF signal. The wiring may be a building utility wiring, such as telephone, AC power or CATV wiring. The baseband signal is carried simultaneously with the utility service signal over the utility wiring using Frequency Division Multiplexing. The device may be enclosed with a data unit, a standalone dedicated enclosure, within an outlet or as a plug-in outlet adapter. Data units may couple the device by a wiring port such as standard data connector, or via wireless connection. The device may be locally powered or via a power signal carried over the wiring. This abstract is not intended to limit or construe the scope of the claims.
Owner:CORNING OPTICAL COMM WIRELESS
Method and apparatus for operating the internet protocol over a high-speed serial bus
InactiveUS6219697B1Efficiently and correctly determineDigital computer detailsTransmissionInternet protocol suiteTransport layer
A method and apparatus of integrating the IEEE 1394 protocol with the IP protocol in which the IEEE 1394 high speed serial bus operates as the physical and link layer medium and the IP operates as the transport layer. There are differences in the protocols which require special consideration when integrating the two protocols. The IEEE 1394 configures packets with memory information and the IP operates under channel based I / O thereby necessitating a modification of the data transfer scheme to accomplish IP transfers over the IEEE 1394. Further, due to differences in packet headers, the IEEE 1394 packet header is modified to encapsulate IP packets. Moreover, in order to determine network packets quickly and efficiently, an identifier is inserted in each network packet header indicating that the packet should be processed by the network. Finally, in order to support the ability to insert or remove nodes on the network without a loss of data, the IP interface must not be disturbed. This is accomplished by maintaining constant IP addresses across bus resets which are caused by insertion or removal of nodes from the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
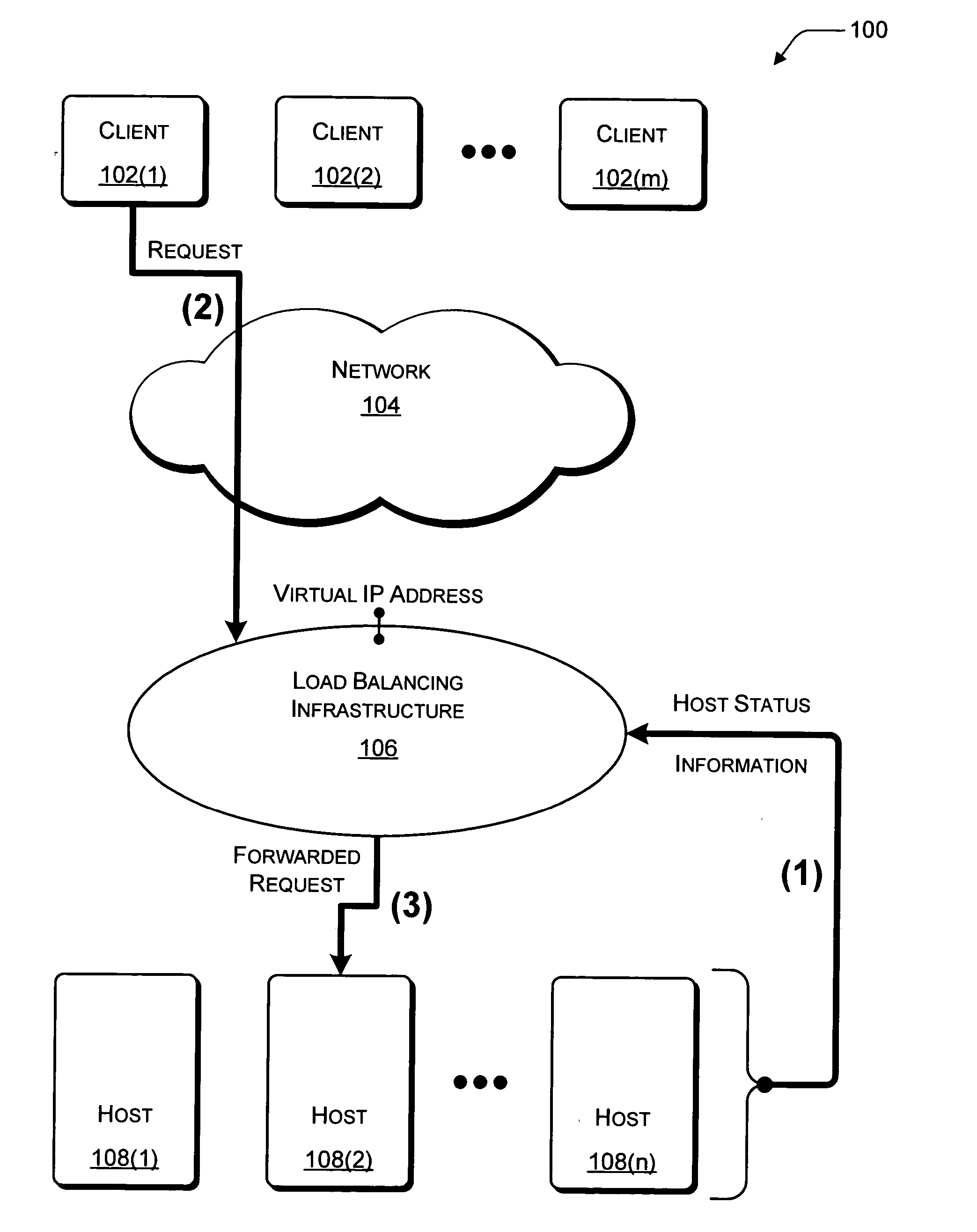
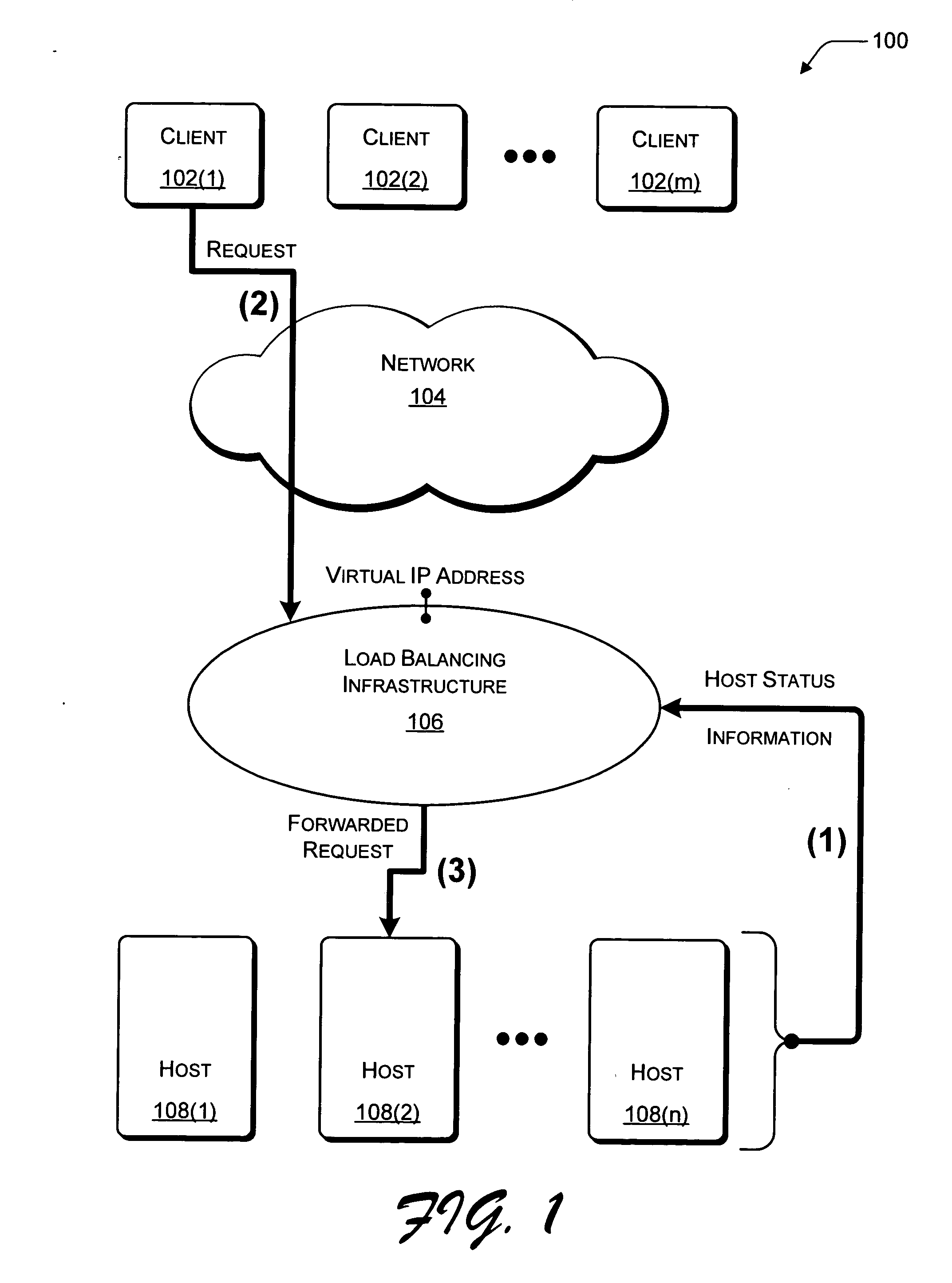
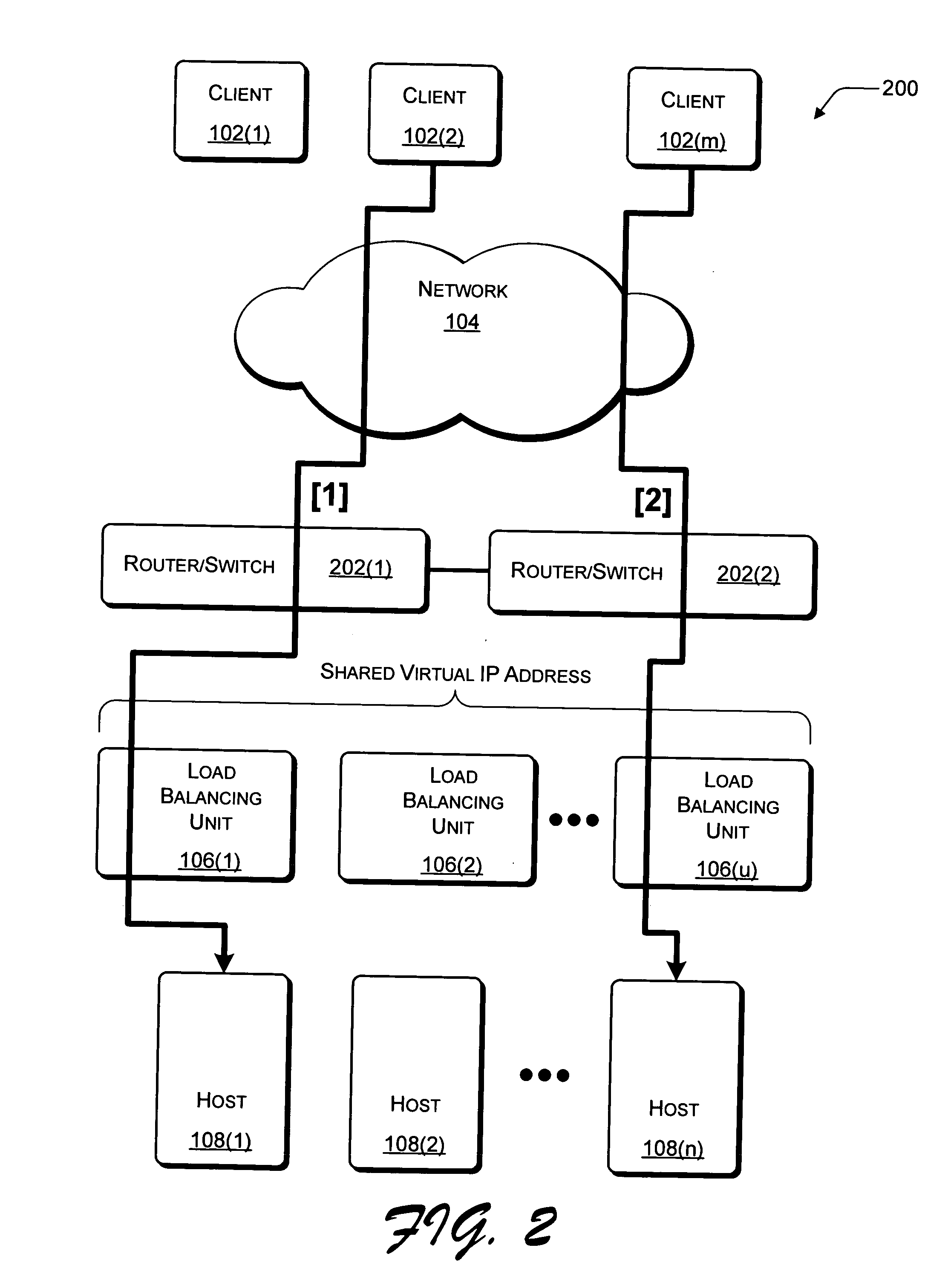
Network load balancing with connection manipulation
ActiveUS20050055435A1Multiple digital computer combinationsData switching networksEncapsulated dataProtocol stack
In an exemplary device implementation, a device includes: a connection migrator that is configured to migrate connections away from the device; the connection migrator capable of precipitating a compilation of protocol state for a connection across a protocol stack; the connection migrator adapted to aggregate the compiled protocol state with data for the connection into an aggregated connection state; the connection migrator further capable of causing the aggregated connection state to be sent toward a target device. In an exemplary media implementation, processor-executable instructions direct a device to perform actions including: obtaining at least a portion of a source / destination pair from a packet; accessing an encapsulation mapping table using the at least a portion of the source / destination pair to locate an encapsulation mapping entry; extracting a flow identifier from the encapsulation mapping entry; and replacing part of the packet with the flow identifier to produce an encapsulated packet.
Owner:MICROSOFT TECH LICENSING LLC
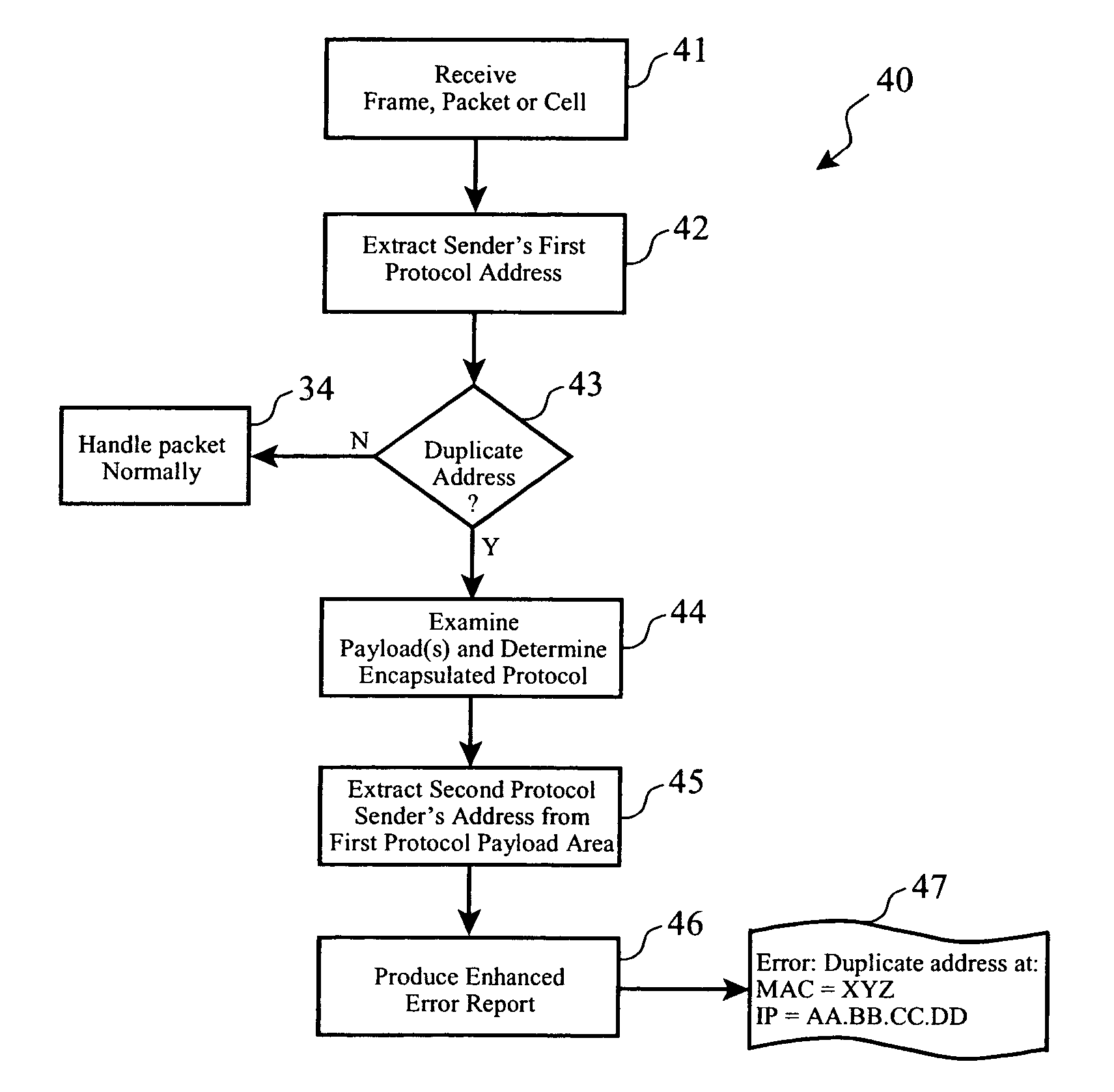
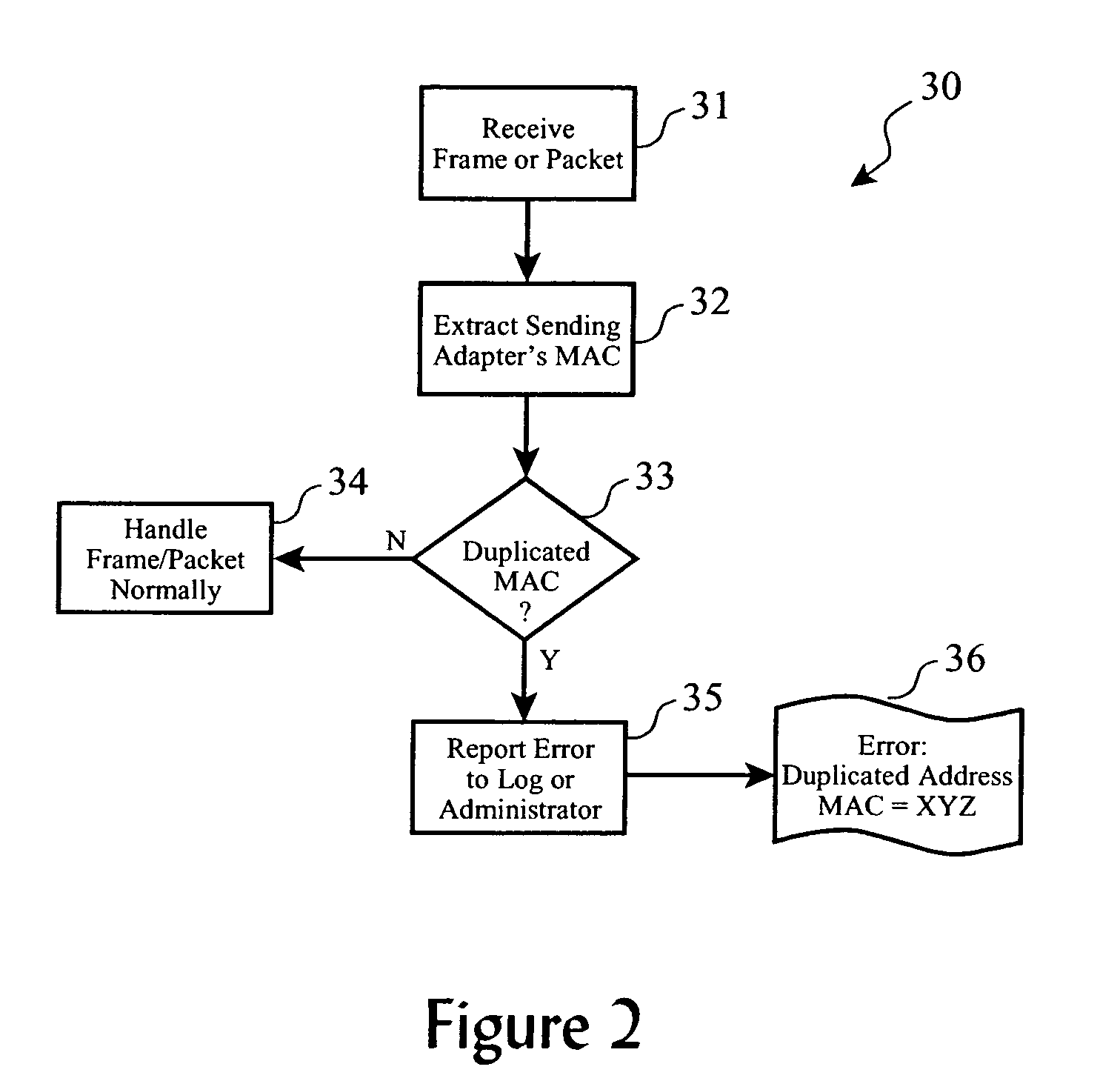
Duplicate network address detection
ActiveUS7246272B2Easy to detectError detection/correctionData switching by path configurationEncapsulated dataNetwork addressing
A plurality of data packets encoded according to a first protocol are received which encapsulate data encoded according to a second protocol. A first source address is extracted from the packets according to the first protocol, it is determined whether or not the first source address is a substantial duplicate of a known assigned address. If it is a duplicate, a second source address is extracted from the encapsulated data according to the second protocol, and the first source address and said second source address are provided in an enhanced error log so that a system administrator may correct the duplicate assigned address. Enhanced embodiments of the invention included analysis of data encapsulated by a third, fourth and subsequent protocols, and automatic determination of each protocol encoding format.
Owner:GOOGLE LLC
Multilink trunking for encapsulated traffic
InactiveUS20070098006A1Increase variabilityMinimize jitterEnergy efficient ICTTime-division multiplexFrame basedEncapsulated data
A node of a frame-based network has a group of outgoing links which are to be treated as an aggregated group of links. A frame distributor performs a distribution function on data frames which are intended for transmission on the group of links. The frame distributor determines if the data frame is an encapsulated data frame which forms part of a tunnelled traffic path across the network. If the data frame does form part of a tunnelled traffic path across the network, the frame distributor allocates the data frame to one of the group of links using at least part of an identifier from the header of the data frame. The identifier represents a service with which the data frame is associated, a customer or user of the data frame, or the tunnelled traffic path, which have greater variability than the backbone destination and source addresses.
Owner:RPX CLEARINGHOUSE
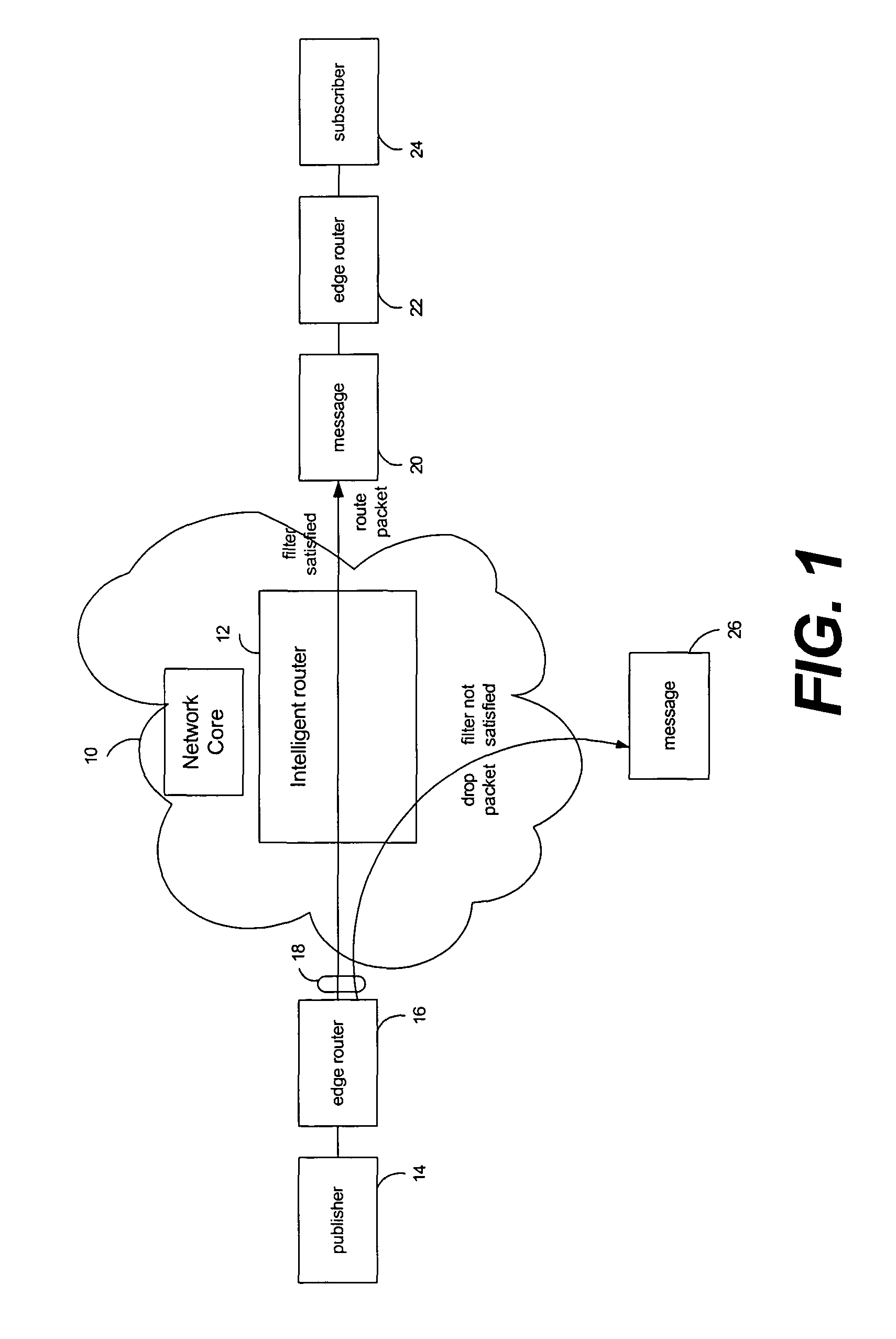
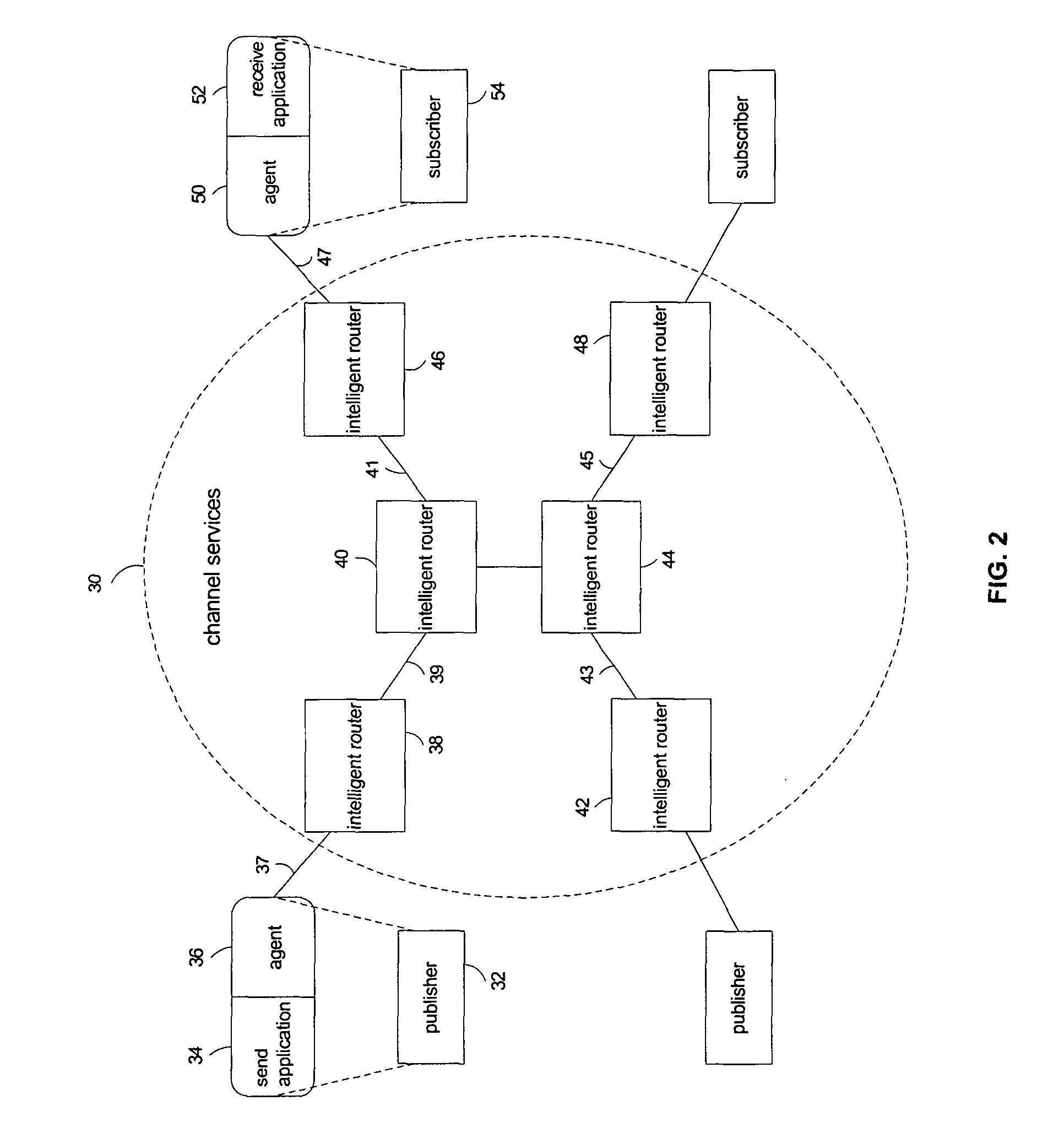
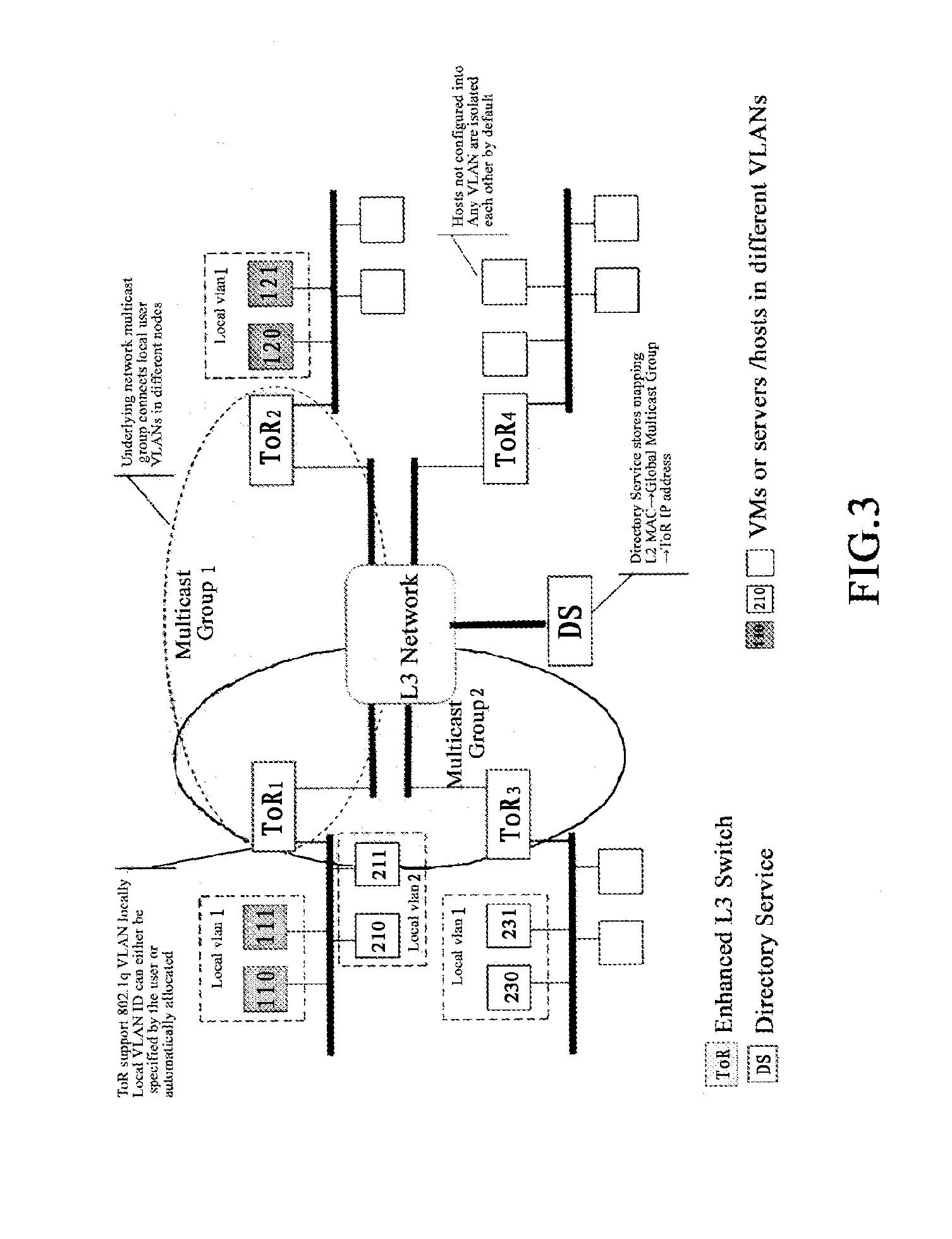
Caching with selective multicasting in a publish-subscribe network
ActiveUS7672275B2Efficient routingOvercome disadvantagesData switching by path configurationWireless commuication servicesRouting decisionEncapsulated data
Packet routing via payload inspection at routers in a core of a distributed network. Packets include subjects and attributes in addition to routing information. The subjects correspond with particular types of content for subscriptions, and the attributes encapsulate the data or content. The routers store filters corresponding with subscriptions to content. Upon receiving a packet, a router inspects the payload section of the packet containing the attributes in order to retrieve the attributes and apply them to the filters for the subscriptions. If an attribute satisfies a filter, the packet is routed to the next link. If the attributes do not satisfy the filters, the router discards the packet. These routing decisions are distributed among routers in the network core. The router locally caches the data in the network core.
Owner:PRECACHE
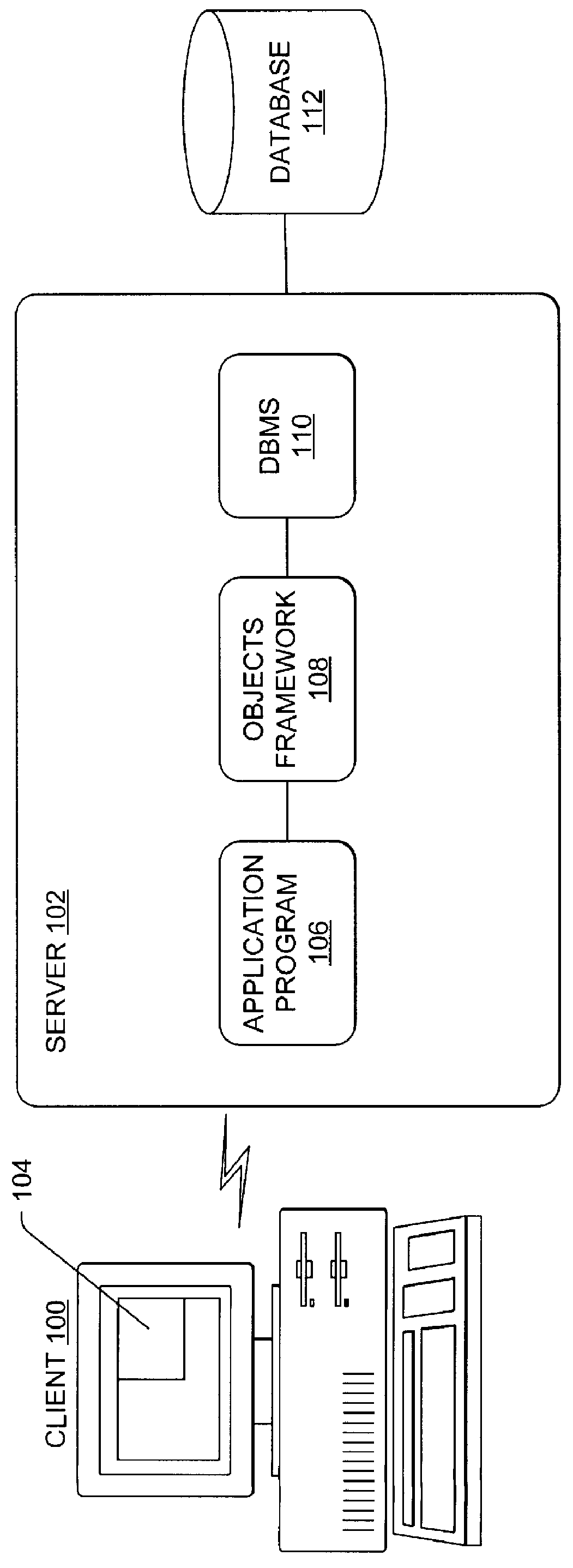
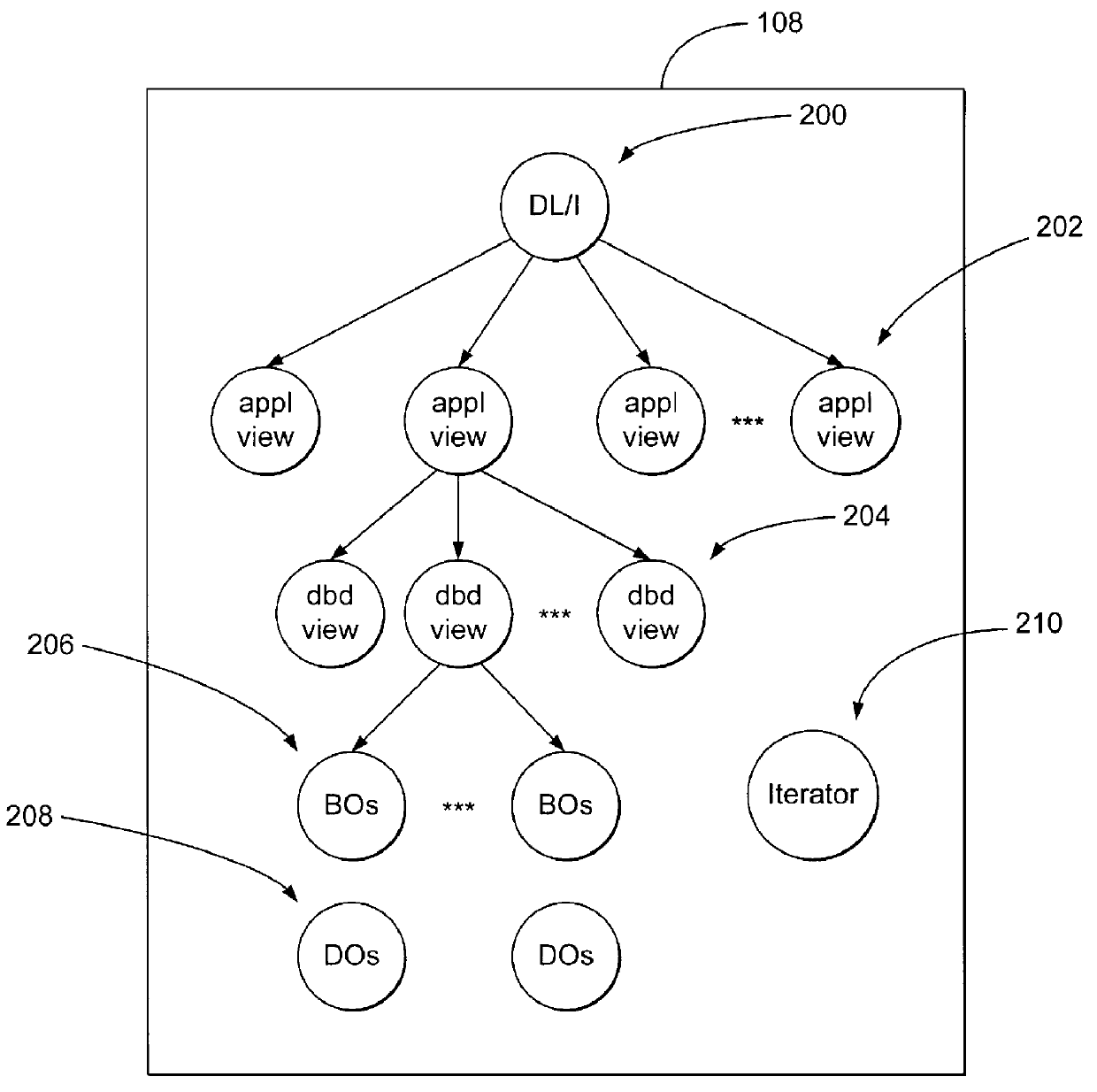
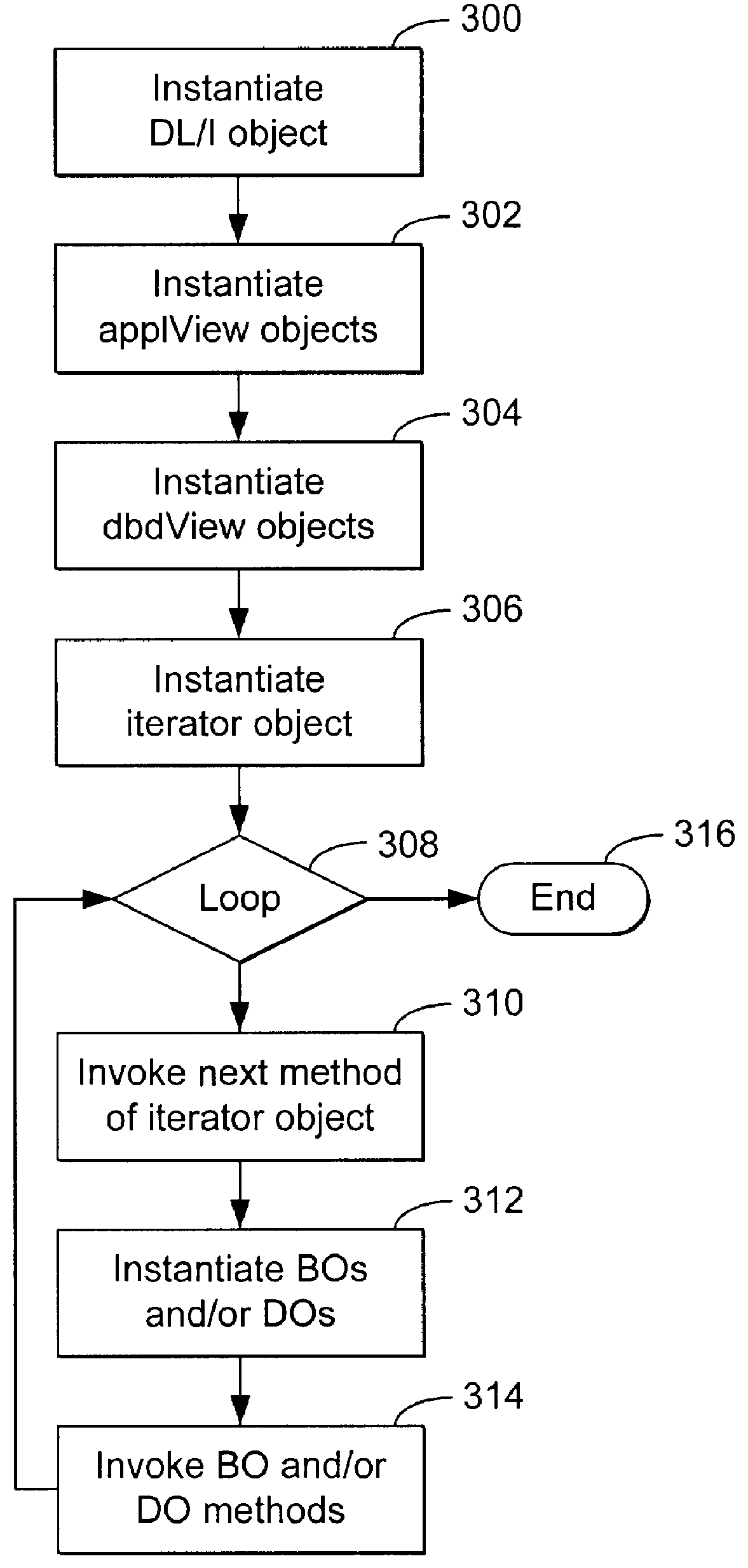
Command line interface for creating business objects for accessing a hierarchical database
InactiveUS6141660AData processing applicationsObject oriented databasesCommand-line interfaceEncapsulated data
A method, apparatus, and article of manufacture for generating class specifications for an object-oriented application that accesses a hierarchical database. The class specifications are generated using a command line interface of a class definition tool. A database description and a record layout associated with the hierarchical database are captured and associated to define a specification for the database. Class definitions are then generated from the database specification, wherein the class definitions are instantiated as objects in the objects framework that encapsulate data retrieved from the database.
Owner:IBM CORP
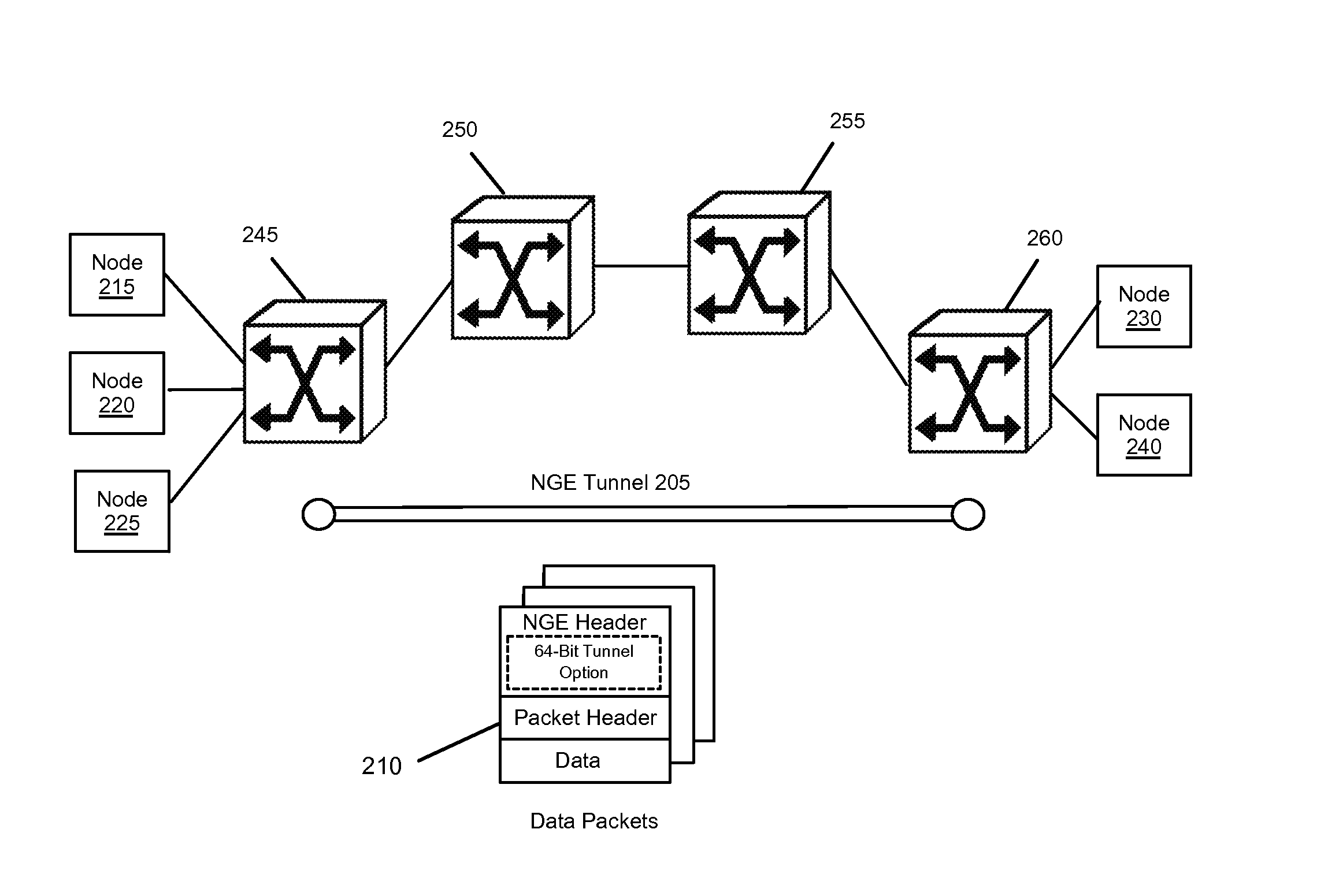
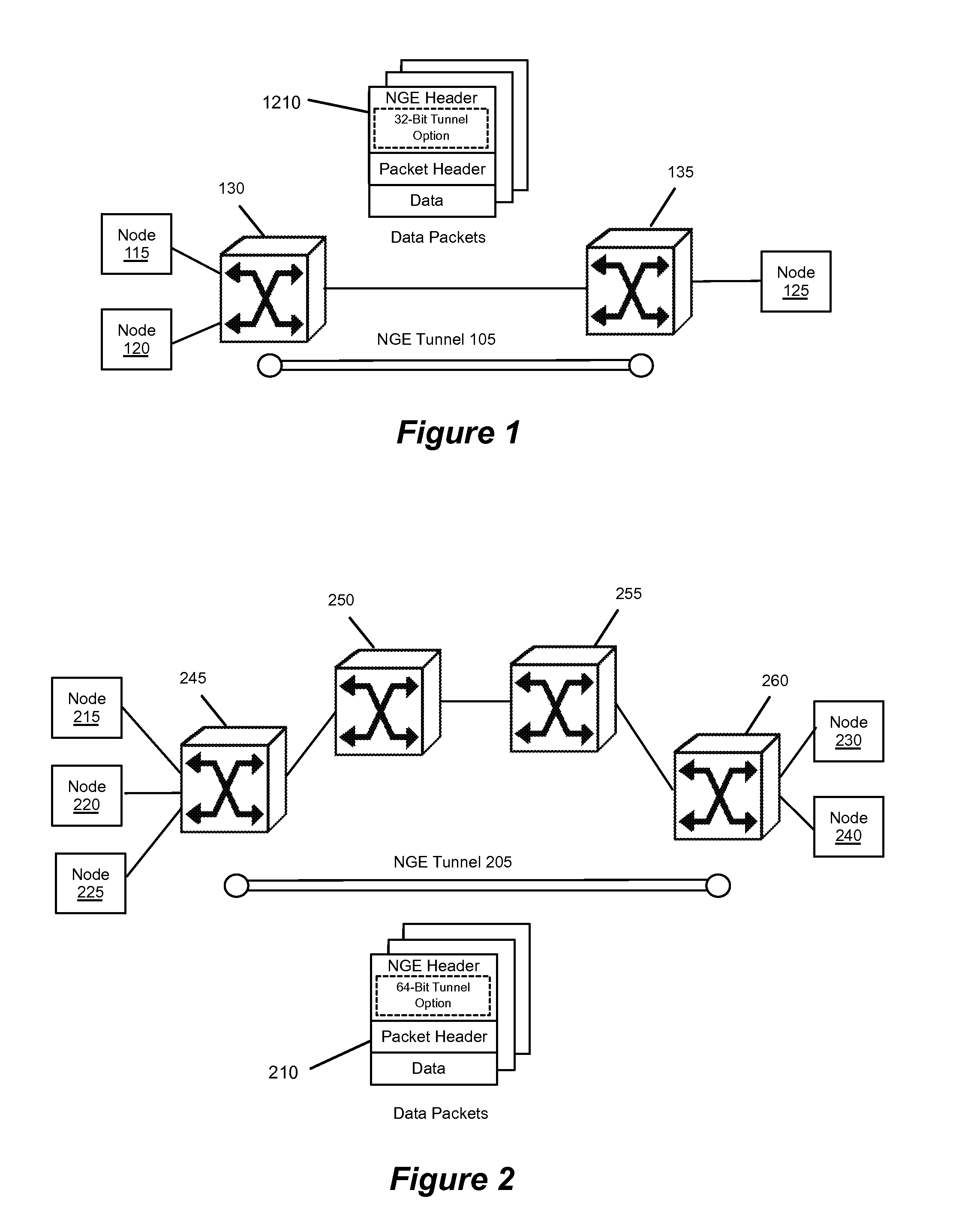
Encapsulating Data Packets Using an Adaptive Tunnelling Protocol
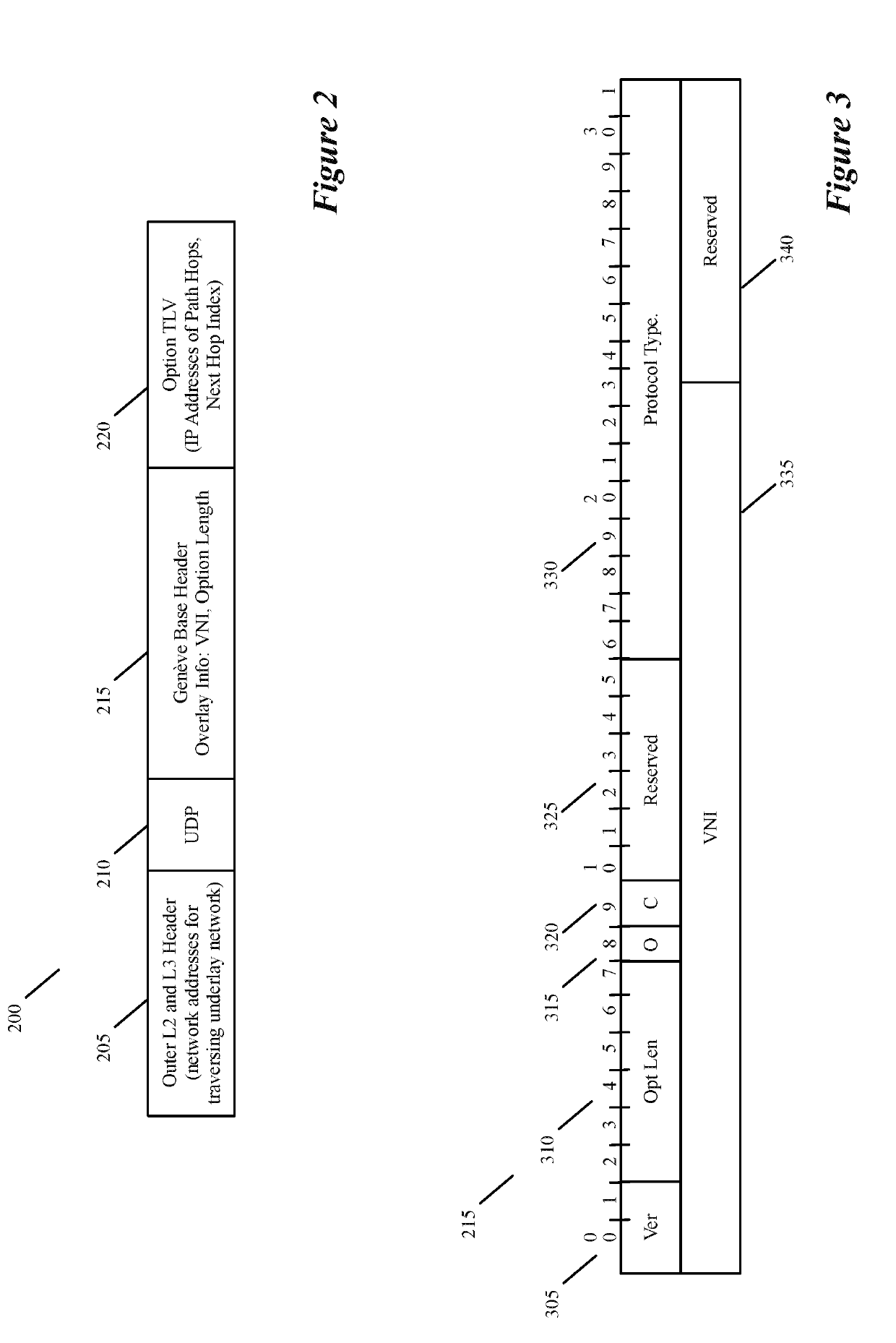
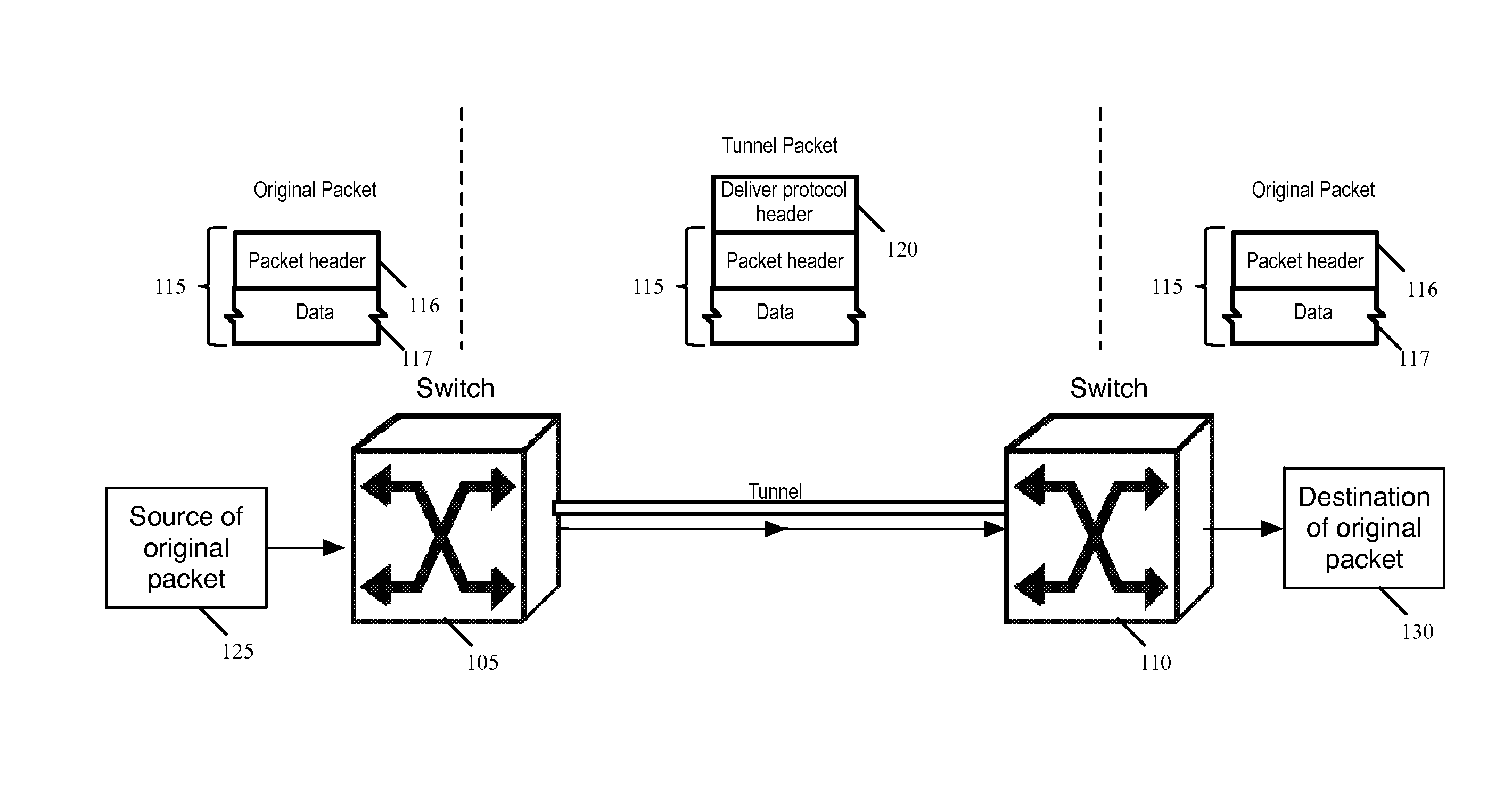
Some embodiments of the invention provide a novel method of tunneling data packets. The method establishes a tunnel between a first forwarding element and a second forwarding element. For each data packet directed to the second forwarding element from the first forwarding element, the method encapsulates the data packet with a header that includes a tunnel option. The method then sends the data packet from the first forwarding element to the second forwarding element through the established tunnel. In some embodiments, the data packet is encapsulated using a protocol that is adapted to change with different control plane implementations and the implementations' varying needs for metadata.
Owner:NICIRA
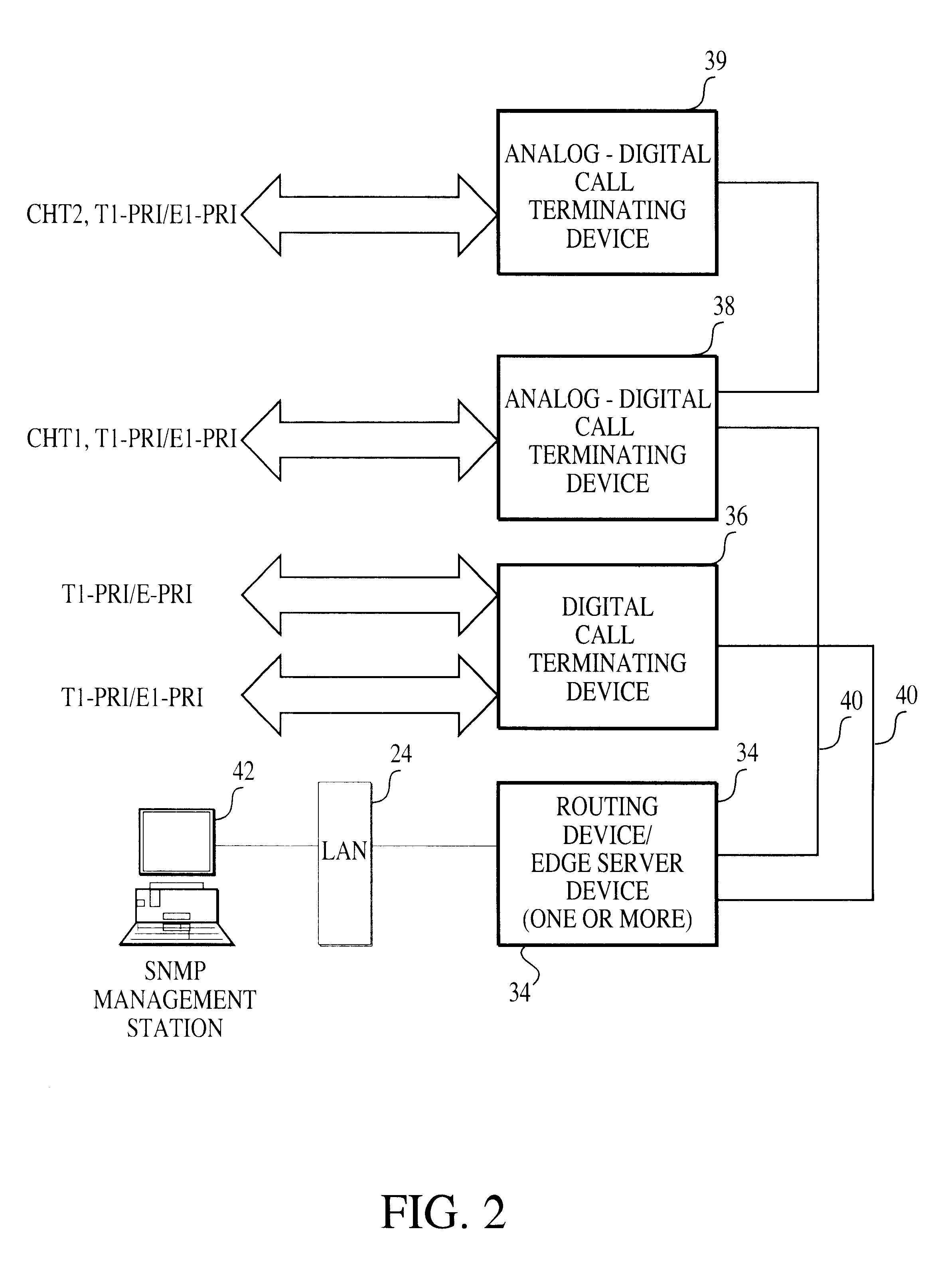
Methods and apparatus for encapsulating a frame for transmission in a storage area network
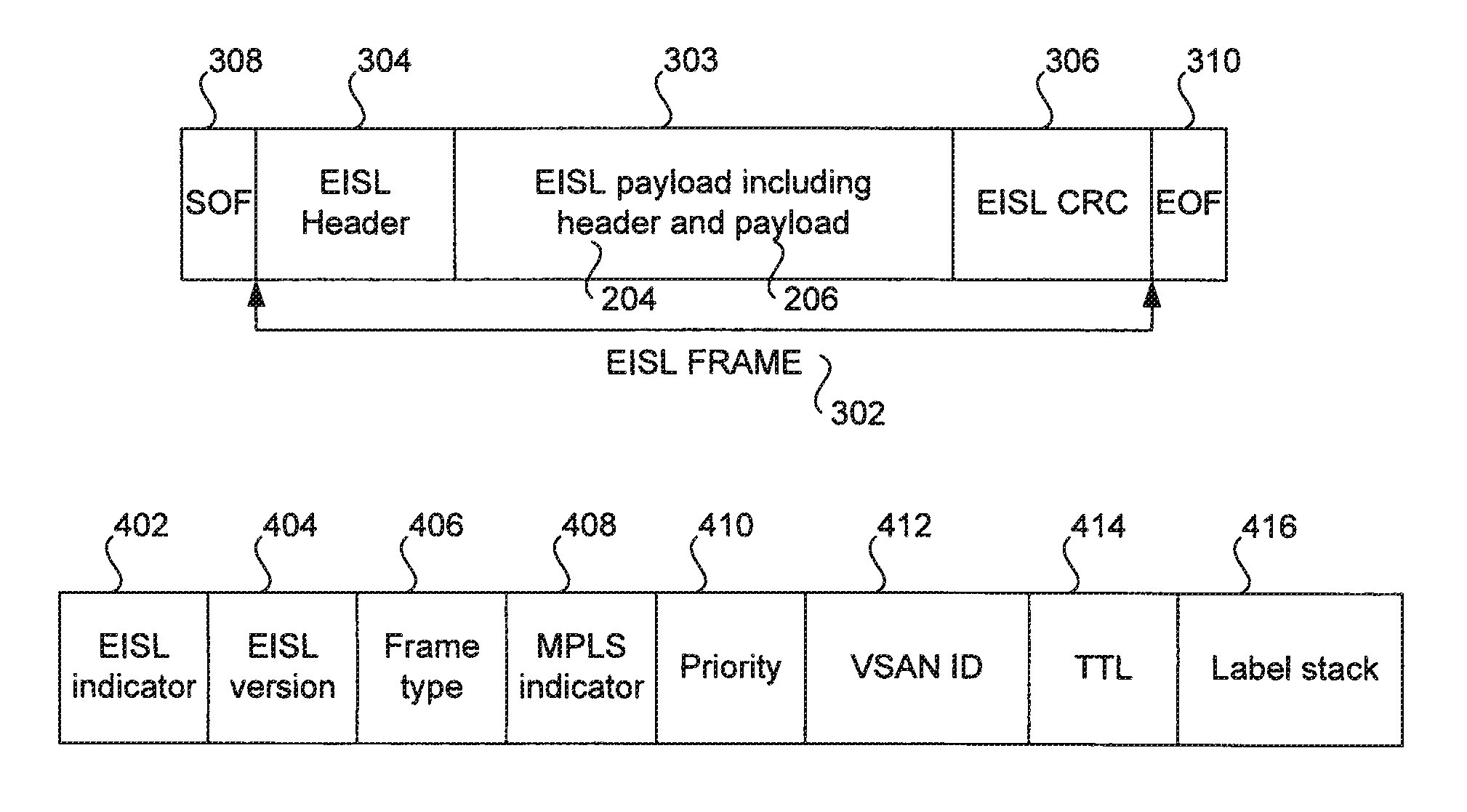
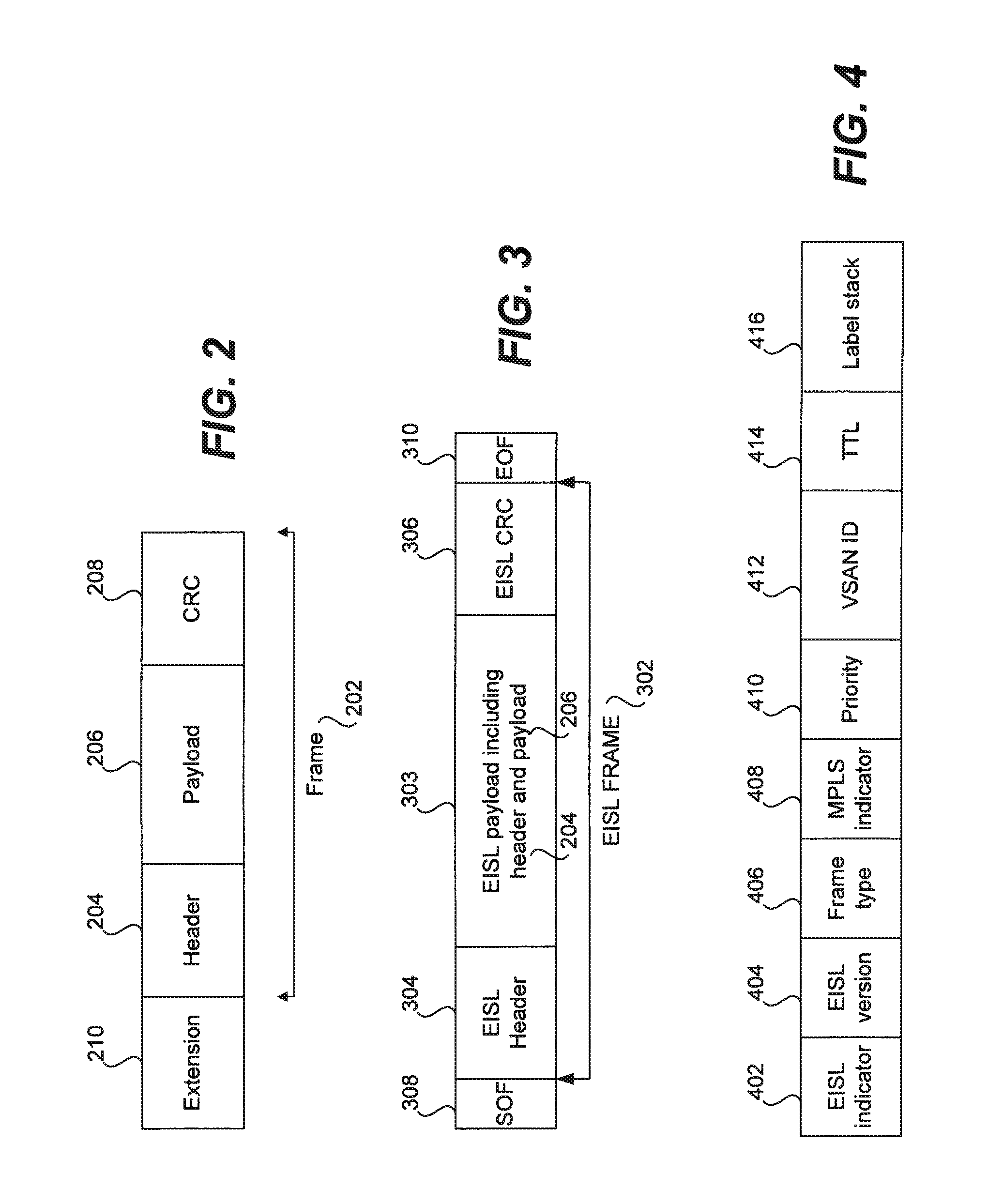
Methods and apparatus for encapsulating a packet or frame for transmission in a storage area network are disclosed. A packet or frame compatible with a standard protocol employed in the storage area network is received or generated. The packet or frame is then encapsulated with a virtual storage area network identifier. The packet or frame may further be encapsulated with at least one of a TTL value, MPLS information, and a type of traffic to be carried by the packet or frame. For instance, the type of traffic to be carried by the packet or frame may include Ethernet, Fibre Channel, and Infiniband. Once encapsulated, the encapsulated packet or frame is sent over the storage area network. For instance, the encapsulated packet or frame may be generated as well as transmitted by a switch over an inter-switch link in the storage area network.
Owner:CISCO TECH INC
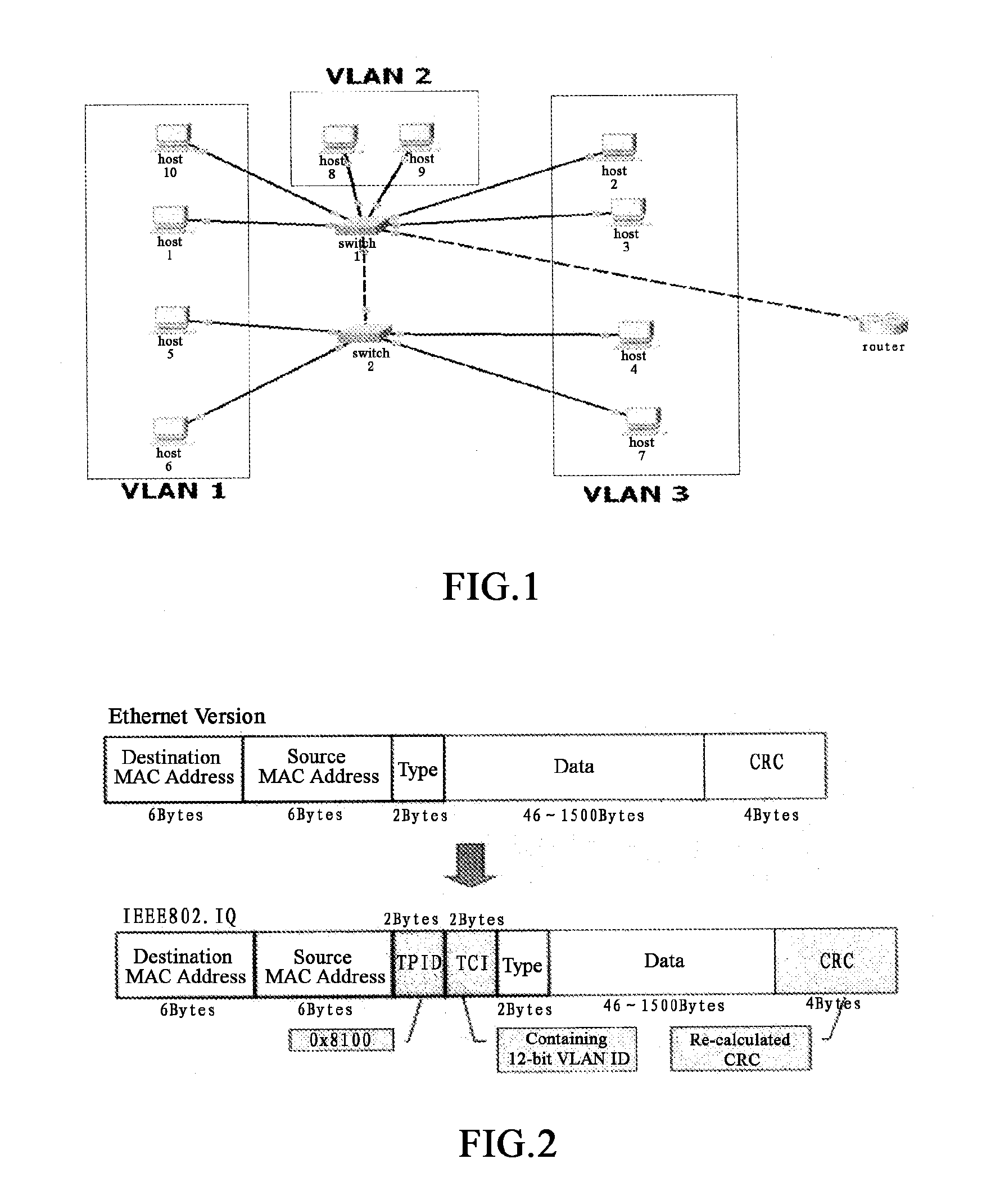
Method and apparatus for implementing a flexible virtual local area network
A method and apparatus for implementing a virtual local area network. The method includes determining a global virtual local area network for transmitting a data frame in response to receiving the data frame at a first switch, encapsulating the data frame based at least in part on said determination and transmitting it to at least one second switch over the determined global virtual local area network. The data frame is received at the second switch and an identifier of the global virtual local area network is obtained according to the data frame. Based at least in part on the identifier of the global virtual local area network, it is determined that which local virtual local area network served by the second switch the de-capsulated data frame can be sent to.
Owner:IBM CORP
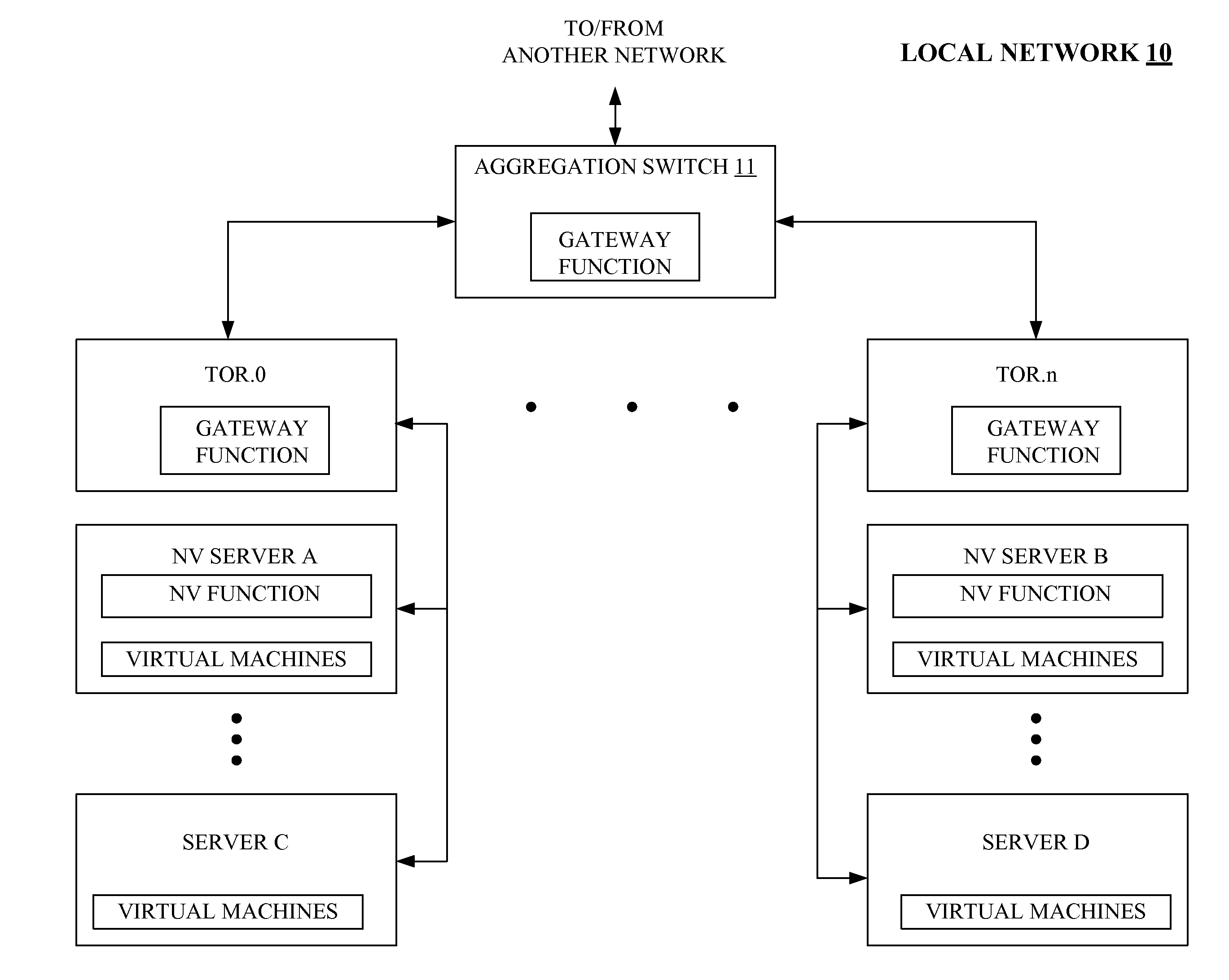
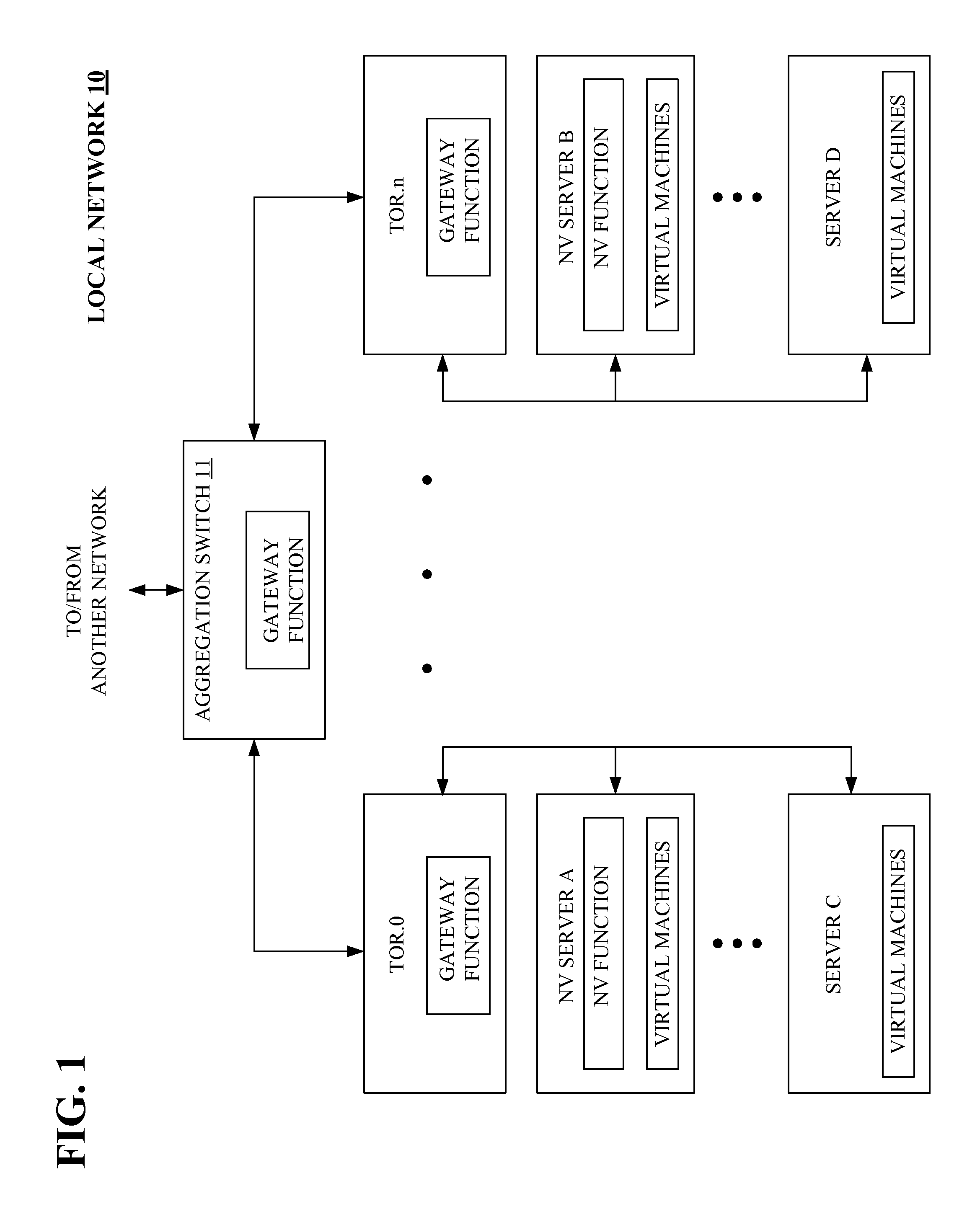
Network virtualization without gateway function
ActiveUS20130124750A1Multiple digital computer combinationsProgram controlEncapsulated dataData center
A local network, such as a data center, includes a plurality of servers each of which are linked to a network switch. Some of the plurality of servers are network virtualization capable and some are not. The network virtualization capable servers include functionality that encapsulates a data frame, generated by one network virtualization servers that is to be sent to another network virtualization capable server, with a network virtualization identity. In the event that a network virtualization server generates a data frame for transmission to a server that is not capable of network virtualization, the network virtualization capable server does not encapsulate the data frame with the network virtualization identity.
Owner:DELL MARKETING CORP
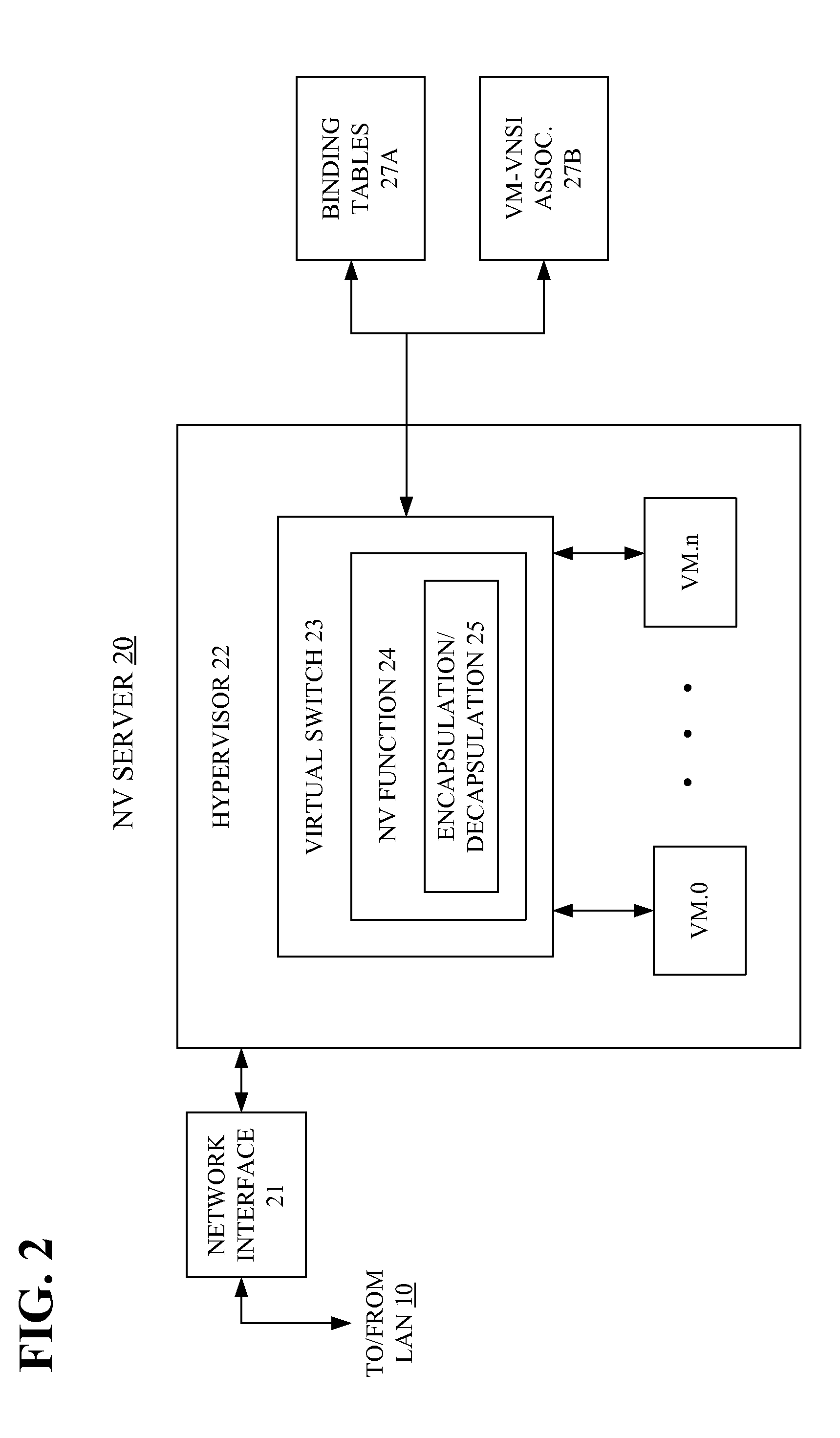
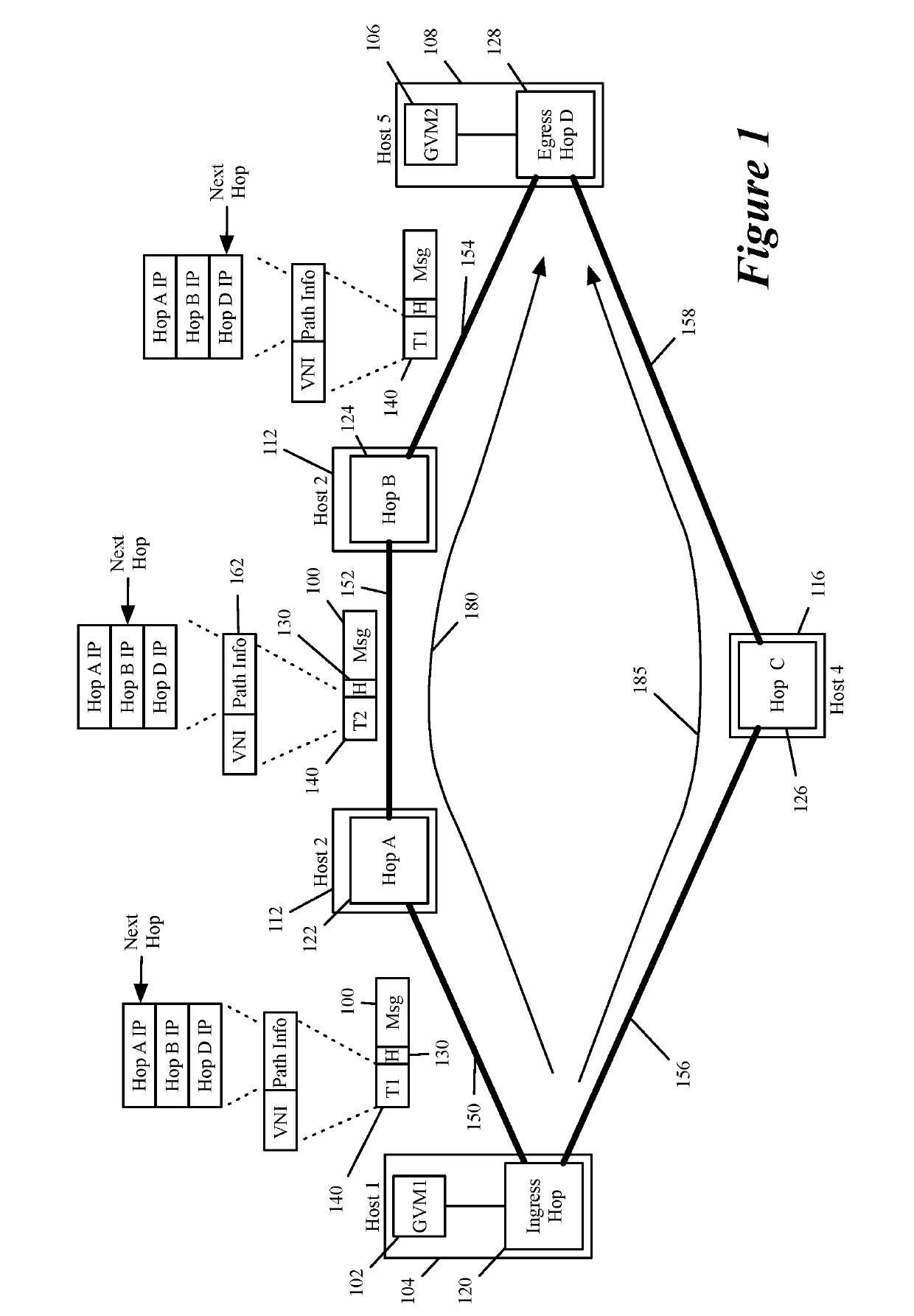
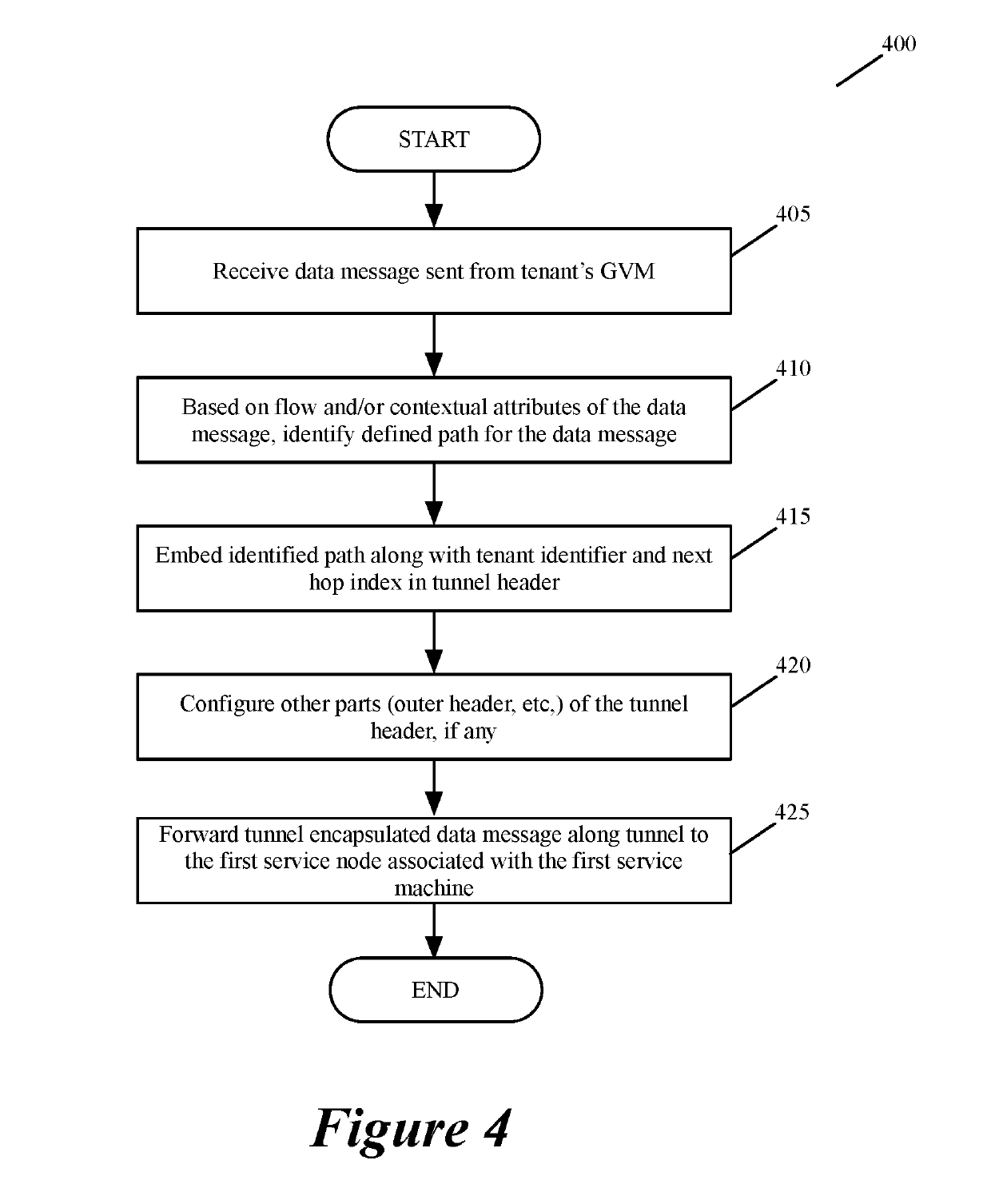
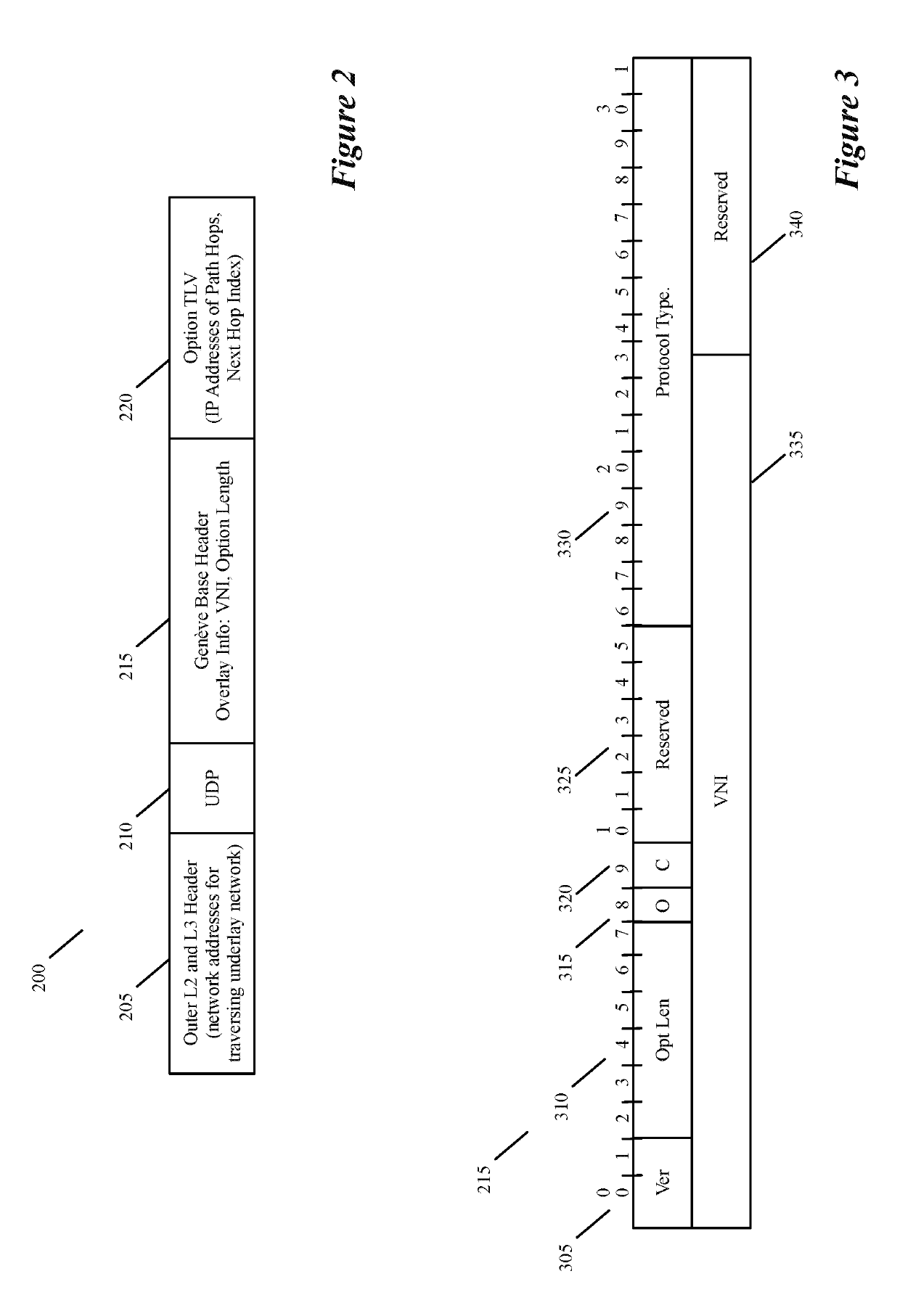
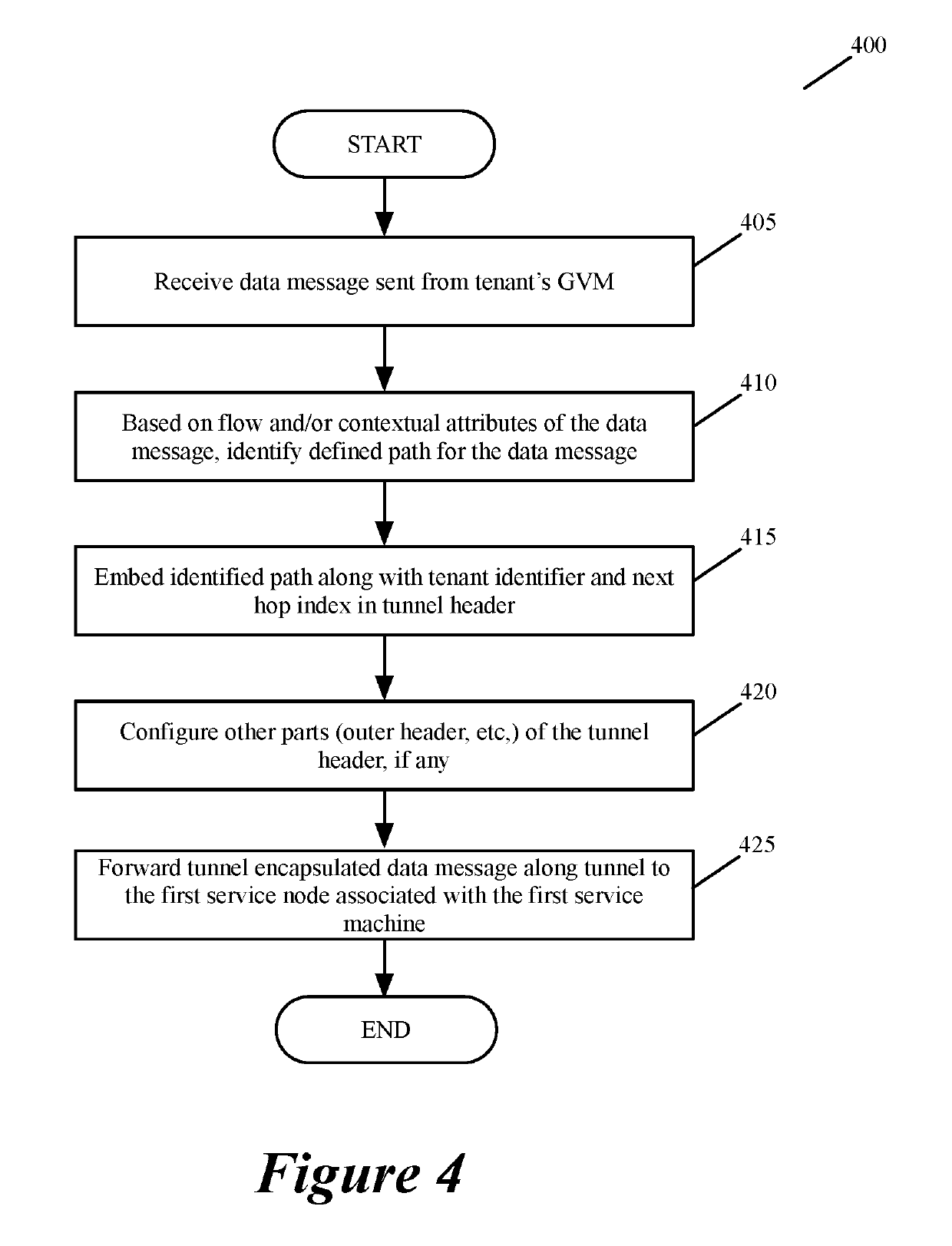
Specifying and utilizing paths through a network
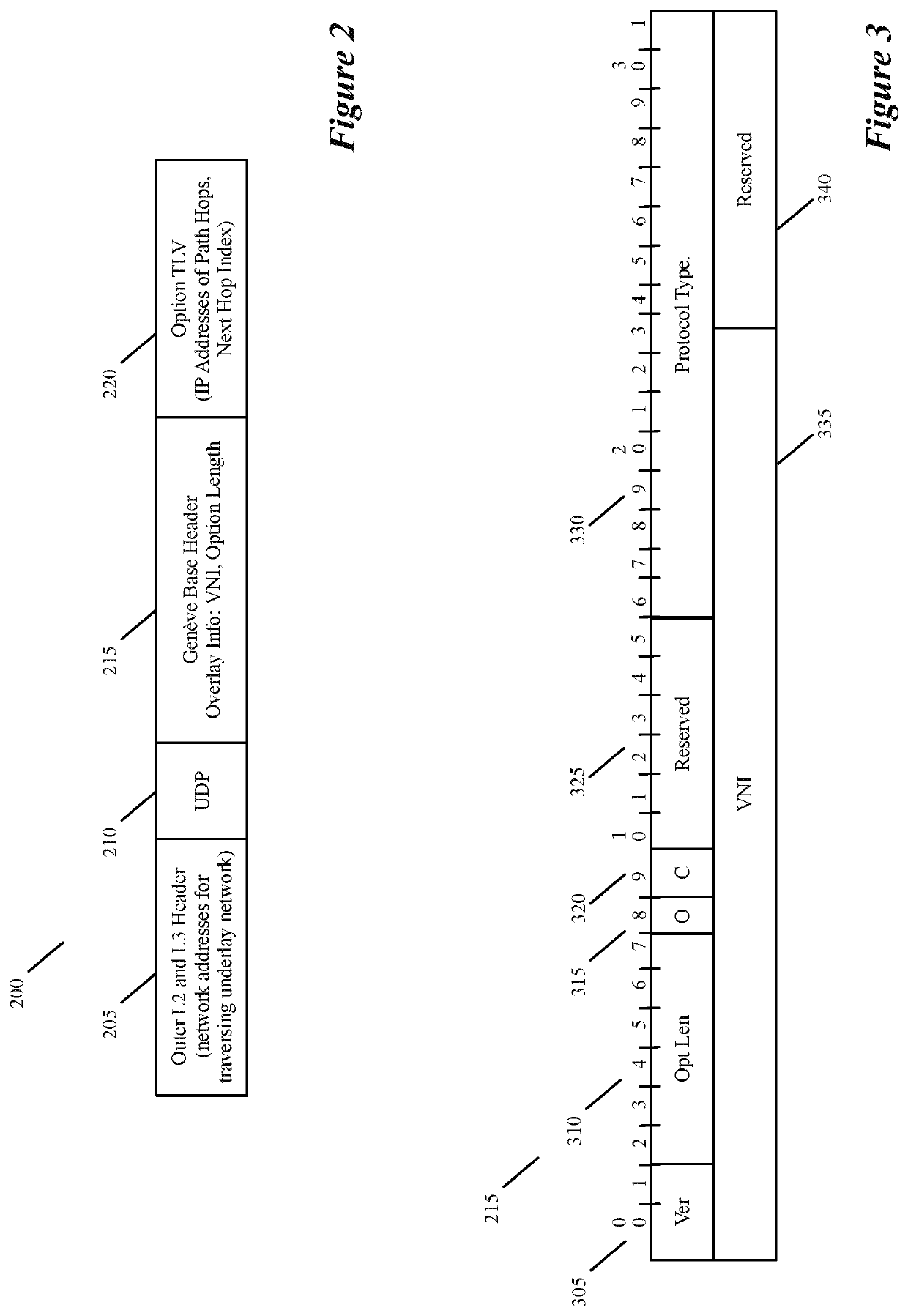
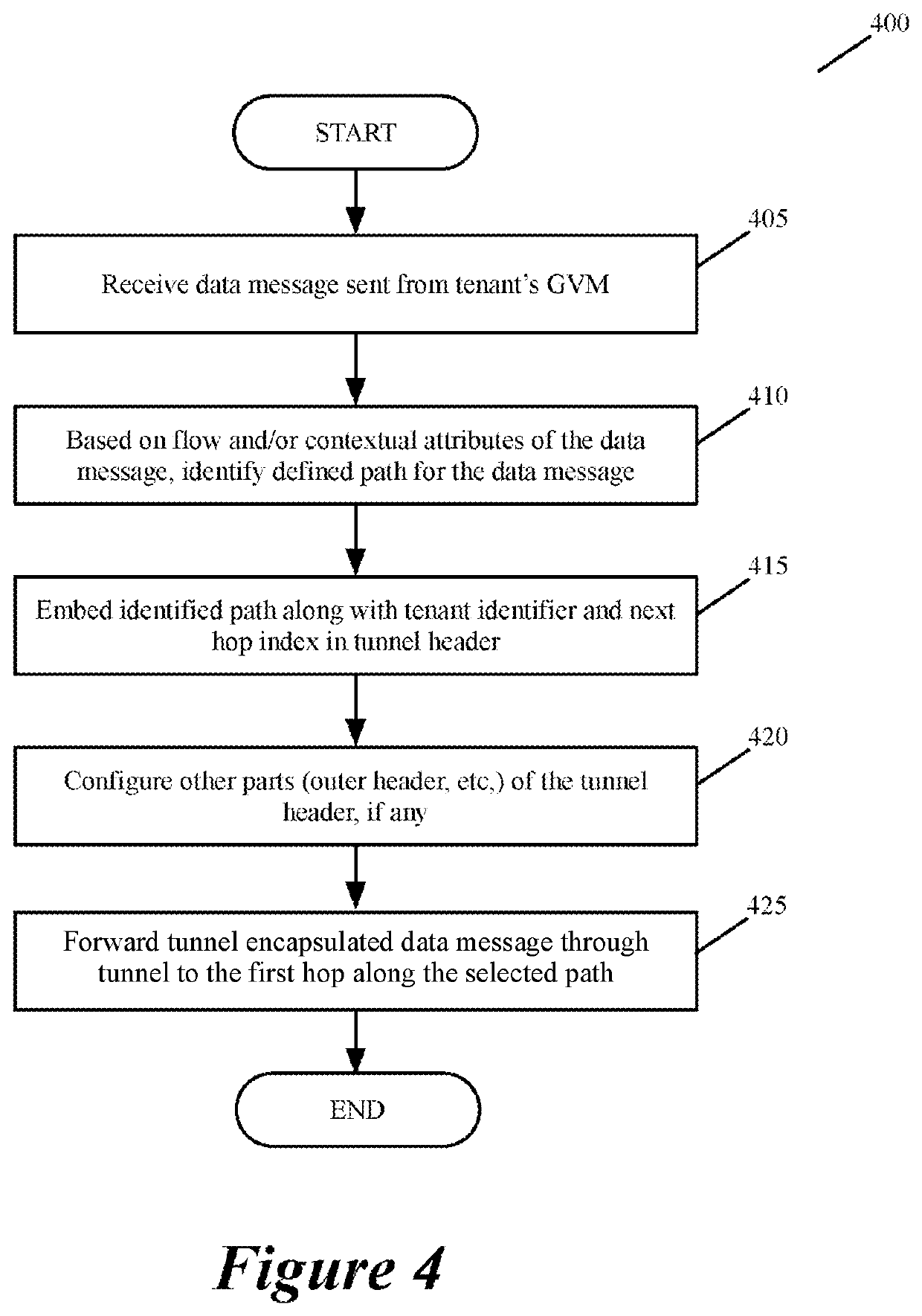
For a multi-tenant environment, some embodiments of the invention provide a novel method for (1) embedding a specific path for a tenant's data message flow through a network in tunnel headers encapsulating the data message flow, and then (2) using the embedded path information to direct the data message flow through the network. In some embodiments, the method selects the specific path from two or more viable such paths through the network for the data message flow.
Owner:NICIRA
Power-efficient address mapping scheme
InactiveUS20070140159A1Reduce power consumptionMaintained for very long times without compromising battery lifeEnergy efficient ICTTime-division multiplexPower efficientEncapsulated data
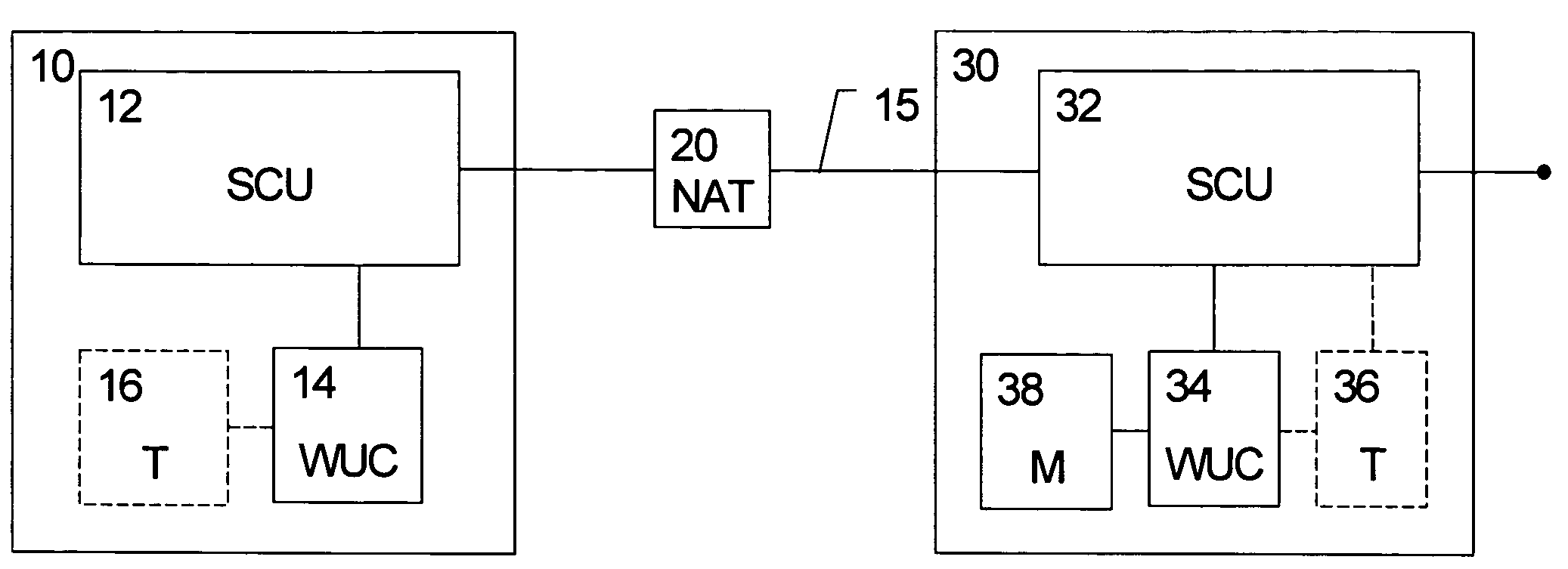
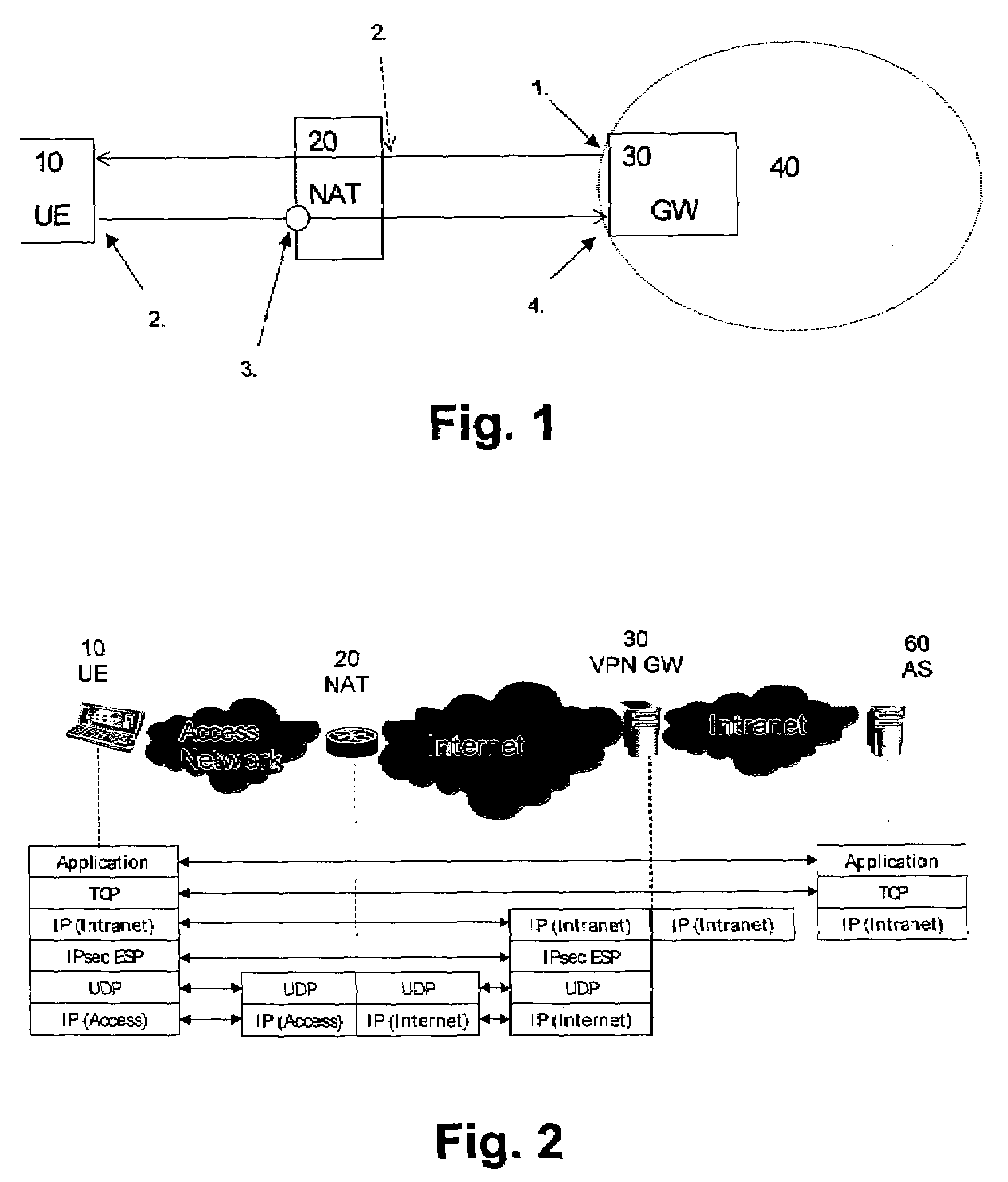
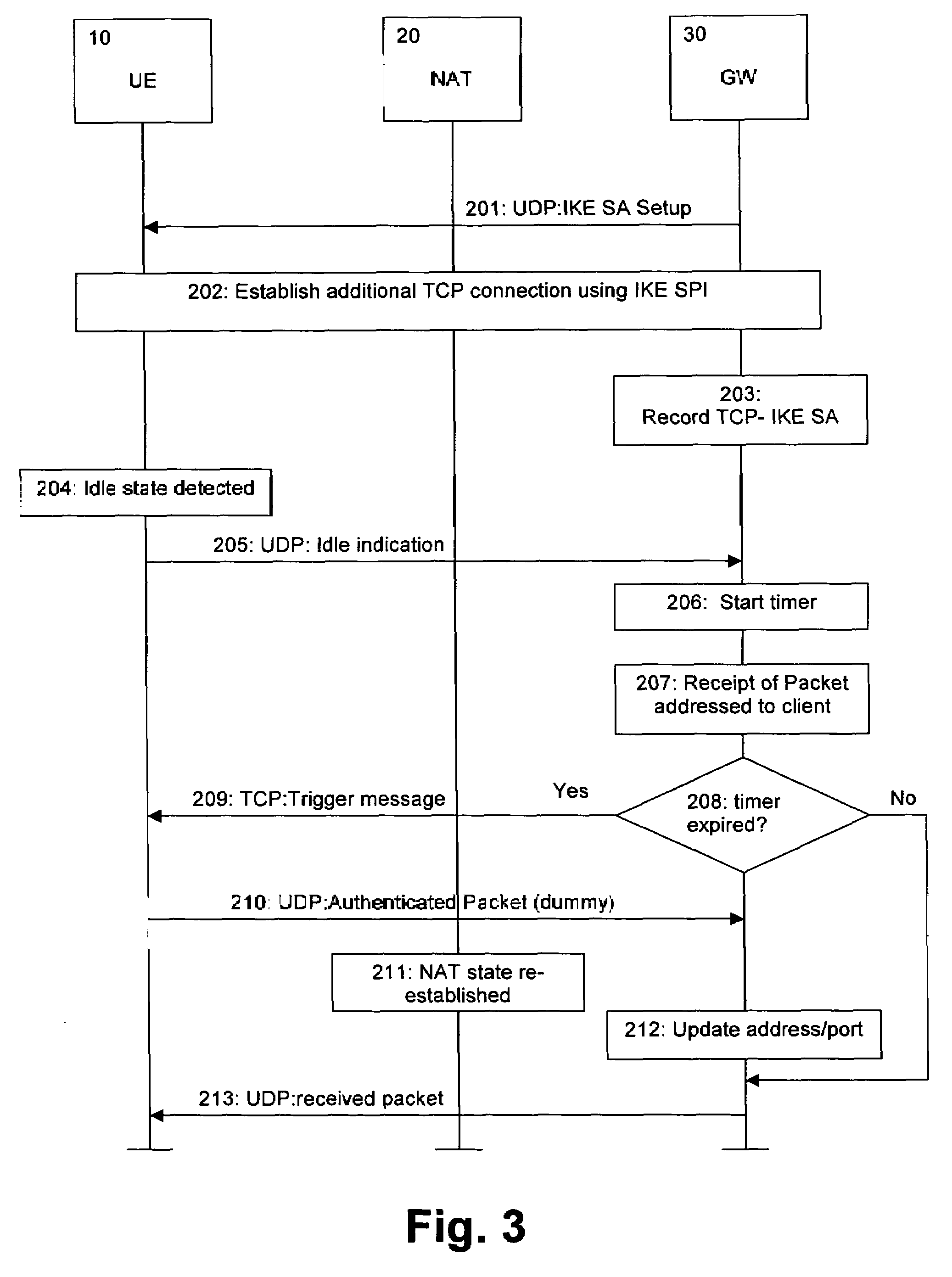
The present invention relates to a method, system, client device, gateway device and computer program product for maintaining a state information in an intermediate network function, wherein the state information expires after a predetermined idle period. Detecting means are provided for detecting an idle state of a connection. In response to the detecting means, a transport protocol used for encapsulating data is changed from a first protocol with a first predetermined idle period to a second protocol with a second predetermined idle period, said second predetermined idle period being longer than said first predetermined idle period. Alternatively, a connection parameter is provided to a device for a parallel second connection in a set-up negotiation via said first connection. This connection parameter is then used for setting up a parallel second connection to the device based on the second transport protocol used for encapsulating data with the second predetermined idle period. Then, an information linking the first and second connections is transmitted from the device to the data network, wherein the second connection is used for transmitting a wake-up notification to the device in response a detected idle state. Both alternatives provide the advantage of reduced keep-alive signaling and thus enhanced battery efficiency.
Owner:NOKIA CORP
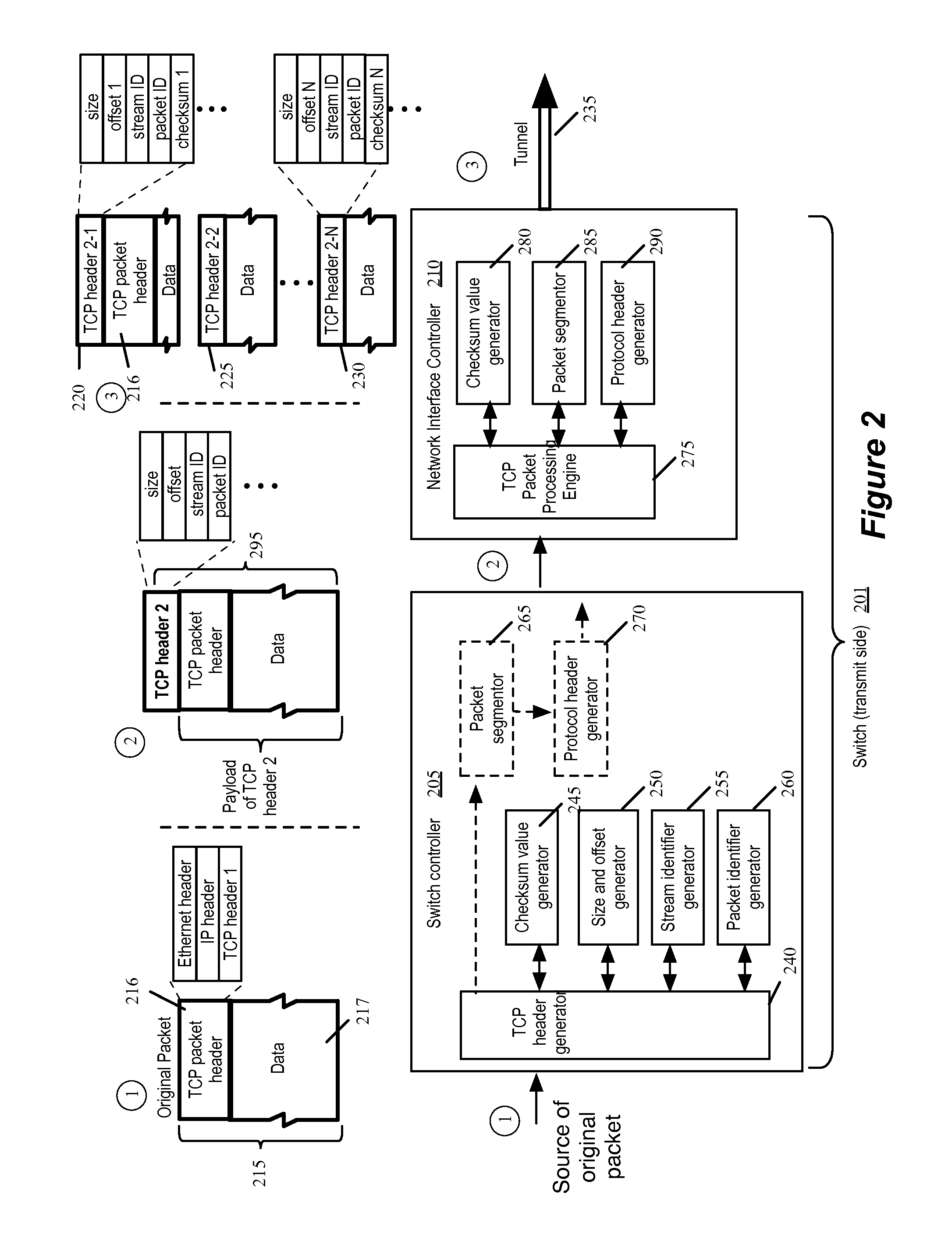
Method and apparatus for stateless transport layer tunneling
ActiveUS8825900B1Different performanceDigital computer detailsNetworks interconnectionData packTransport layer
Some embodiments of the invention provide a method of tunneling a data packet by encapsulating the data packet with a protocol header and specifying information in the fields of the header in a manner that a network switch can offload processing tasks to its network interface controller. The switch on a transmit side sends the processed data packet through the tunnel to another switch on a receive side. The two sides represent the two ends of the tunnel established between the two switches. Each of the transmit and received side switches is controlled by a switch controller, which in some embodiments is implemented as software. The switch controllers and network interface controllers together process the data packet which is being transferred through the tunnel between the switches.
Owner:NICIRA
Method and system for transporting data using pseudowire circuits over a bridged network
ActiveUS20060146832A1Time-division multiplexMultiple digital computer combinationsEncapsulated dataEdge node
Owner:CISCO TECH INC
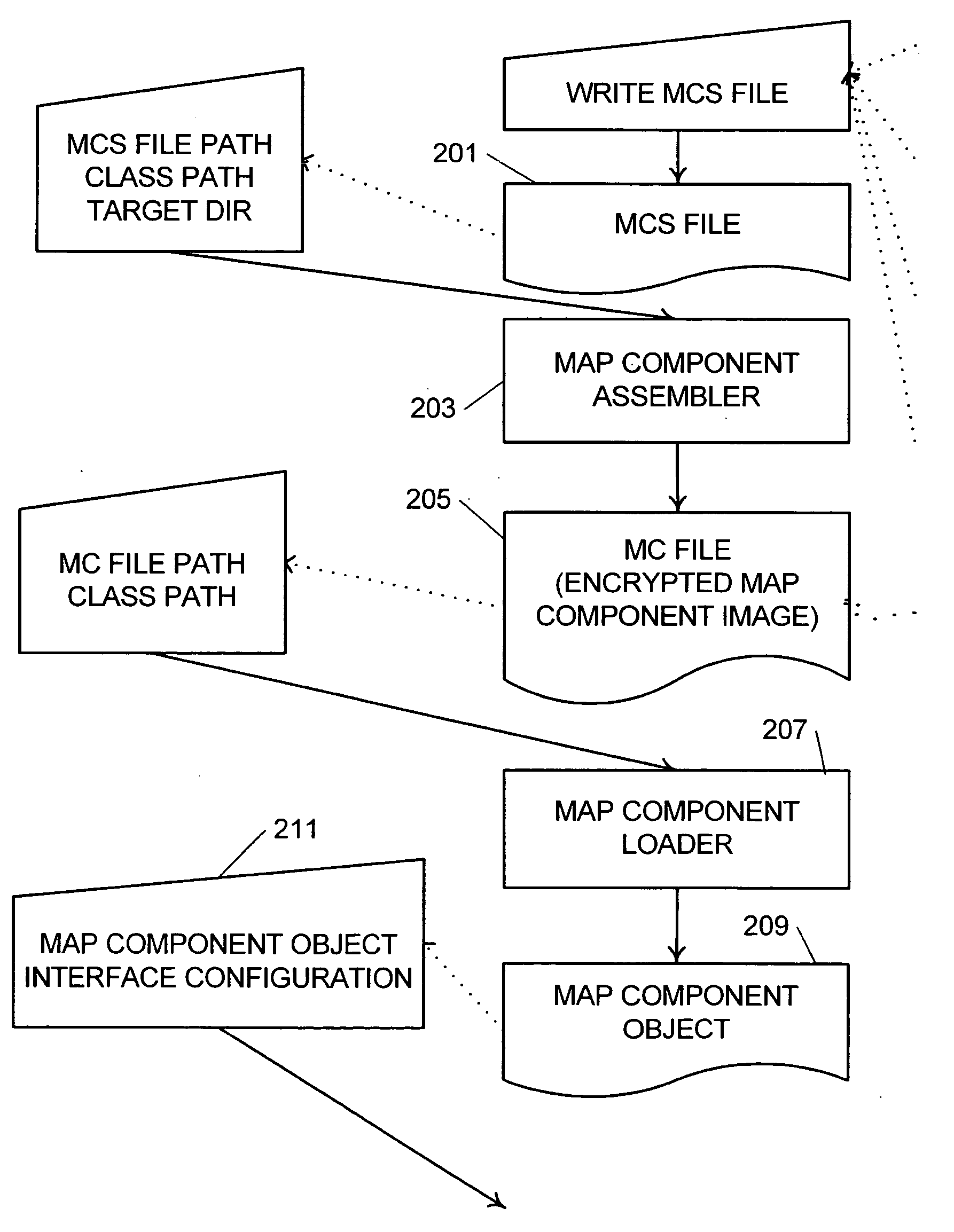
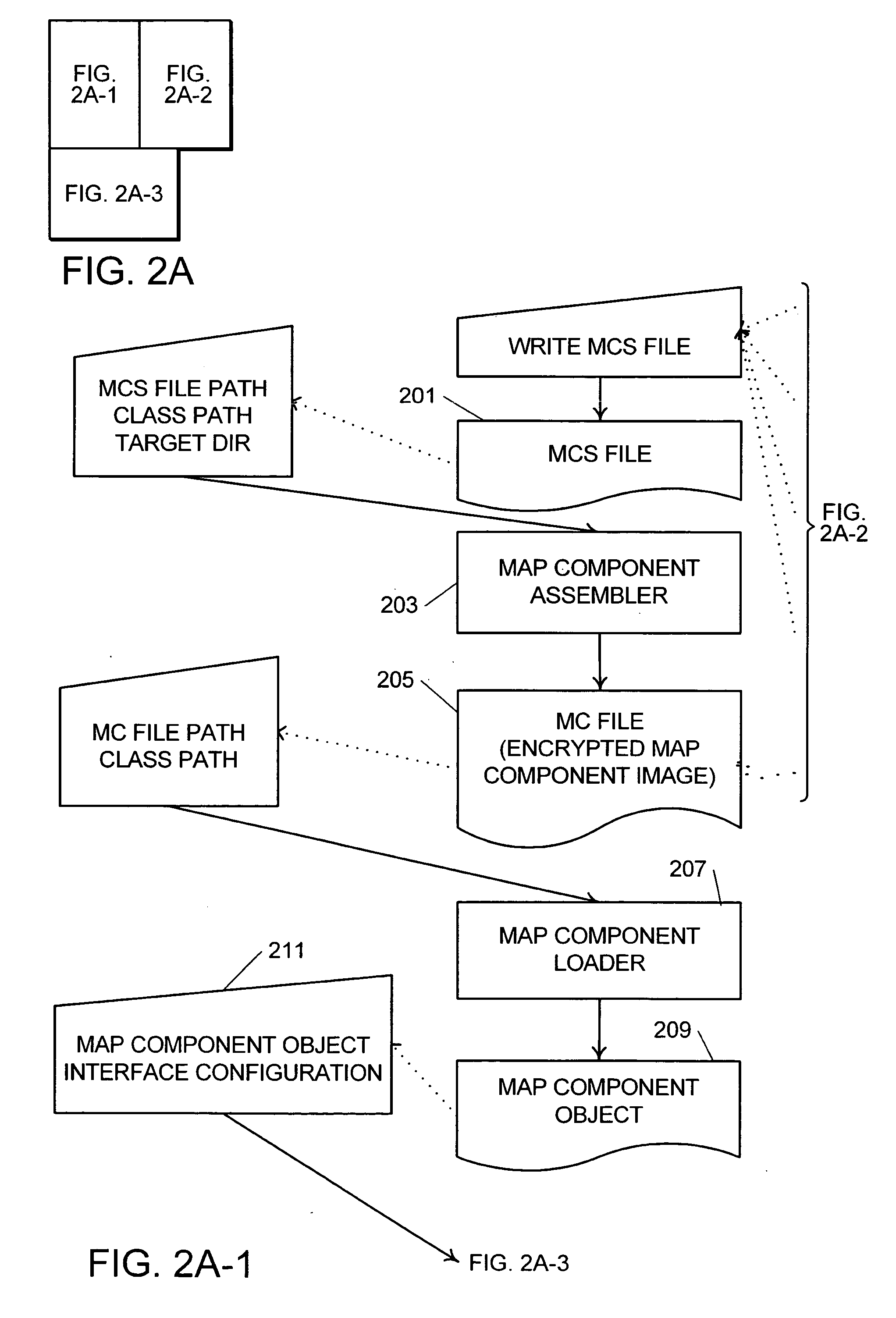
System and method for data transformation using dataflow graphs
ActiveUS20050097561A1Sufficient performanceDigital computer detailsMultiprogramming arrangementsData warehouseData stream
A system and method for managing data, such as in a data warehousing, analysis, or similar applications, where dataflow graphs are expressed as reusable map components, at least some of which are selected from a library of components, and map components are assembled to create an integrated dataflow application. Composite map components encapsulate a dataflow pattern using other maps as subcomponents. Ports are used as link points to assemble map components and are hierarchical and composite allowing ports to contain other ports. The dataflow application may be executed in a parallel processing environment by recognizing the linked data processes within the map components and assigning threads to the linked data processes.
Owner:ACTIAN CORP
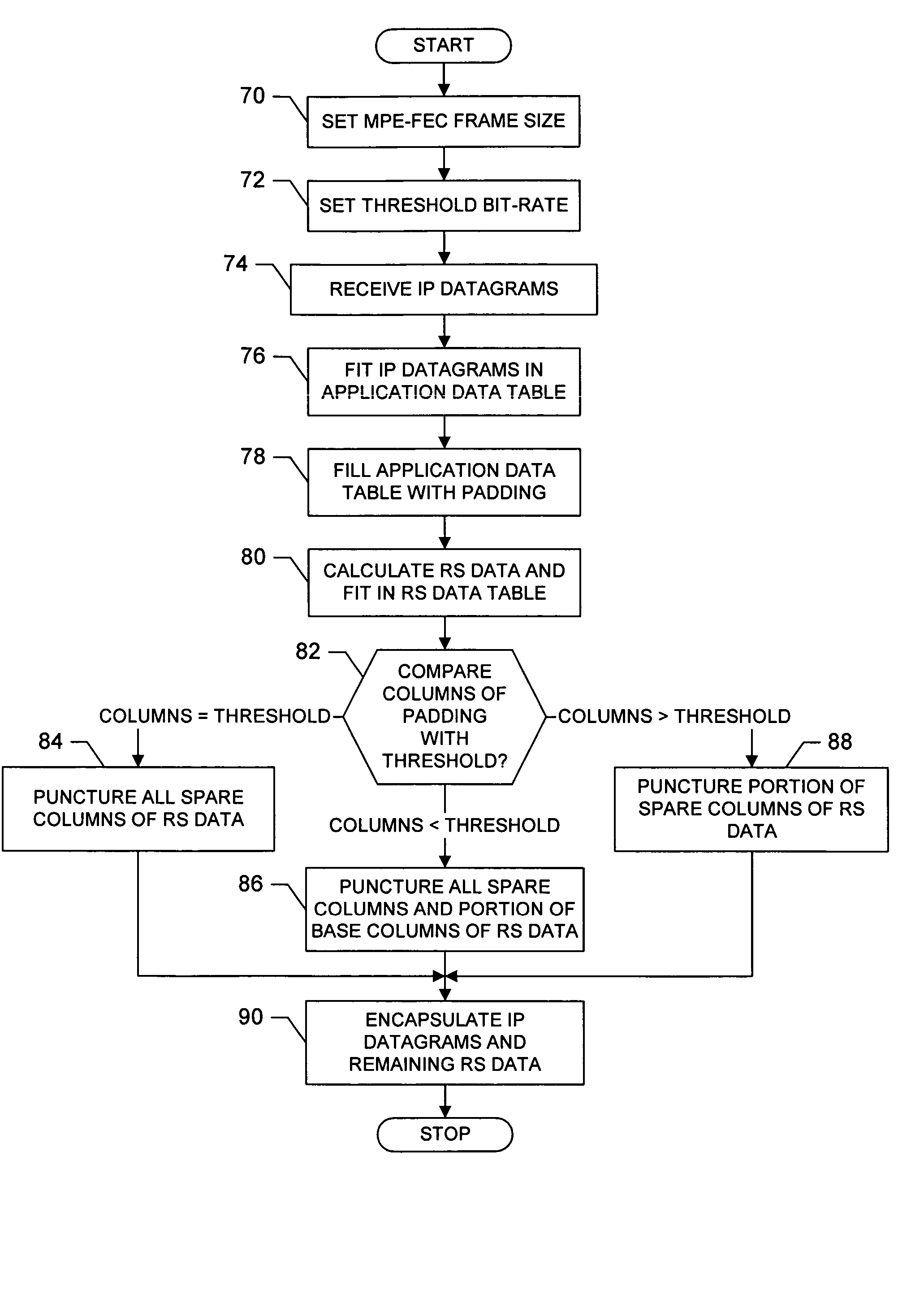
Encapsulator and an associated method and computer program product for encapsulating data packets
InactiveUS20060007953A1Reduce variationSpecial service provision for substationError preventionData packEncapsulated data
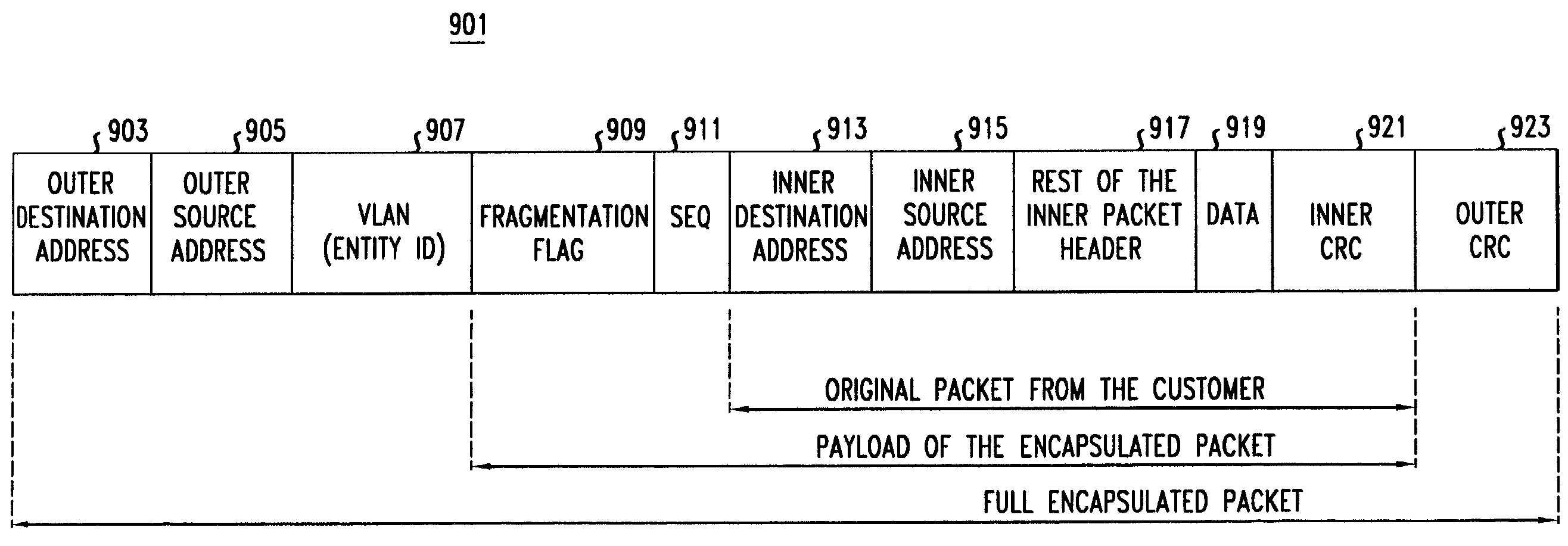
A method for encapsulating at least one data packet includes fitting at least one data packet into at least one column of an application data table of an array that also includes a coding data table having at least one column. Then, at least one remaining column of the application data table is filled with padding, and coding data is fit into at least one column of the coding data table of the array. At least one column of coding data is punctured based upon a comparison of a bit rate of incoming data packets and a threshold bit rate, with at least one column of coding data remaining after puncturing the column(s) of coding data. And after puncturing the column(s) of coding data, the data packet(s) in the column(s) of the application data table, and the at least one remaining column of coding data, are encapsulated.
Owner:NOKIA TECHNOLOGLES OY
System and method for design, procurement and manufacturing collaboration
ActiveUS7134096B2Facilitates componentImprove performanceData processing applicationsCAD network environmentEncapsulated dataElectronic component
A method for designing an electronic component includes receiving a device criteria (e.g., a parametric value, procurement value, etc.) from a designer, querying a database for devices corresponding to the device criteria, querying the database for procurement data and / or engineering data associated with the corresponding devices, presenting the devices to the designer based on the procurement data, and receiving input from the designer identifying one of the presented devices as a selected device. In a particular method, the returned devices are sorted based on one or more procurement values (e.g., manufacturer, price, availability, manufacturer status, etc.), and presented to the designer in a ranked list. Objects representative of the selected devices are then entered into a design file, and the objects are associated with the device's engineering and / or procurement data. In a particular embodiment, the objects are associated with the engineering data by embedding the engineering data in the file object. Optionally, data can be associated with the objects via links to the database. Types of engineering data that can be associated with design file objects include, but are not limited to, device footprint data, device pinout data, device physical dimension data, parametric data, and packaging data. Additionally, connection data and annotation data can be entered into the design file objects by the designer.
Owner:FLEXTRONICS AP LLC
Method of implementing PSEUDO wire emulation edge-to-edge protocol
InactiveUS20050129059A1Improve efficiencyQuality improvementTransmission systemsTime-division multiplexEncapsulated dataPseudo-wire
The present invention relates to PWE3-based communication and discloses a method of implementing PWE3 protocol, with the aim to implement PWE3 architecture over RPR-based MPLS PSN, provide protection and bandwidth sharing capability, and improve quality and efficiency of PWE3 architecture. Said method of implementing PWE3 protocol comprises the following steps: A. Encapsulate data frame on said PWE3 PSN layer into RPR data frame; B. Transmit said RPR data frame to the destination node through RPR; C. Decapsulate said RPR data frame into PSN layer data frame at said destination node.
Owner:HUAWEI TECH CO LTD
Encapsulation and decapsulation for data disintegration
ActiveUS8520855B1Digital data processing detailsUser identity/authority verificationEncapsulated dataOriginal data
A configuration for encapsulating data that is unreadable after a predetermined timeout. To encapsulate data a random data key is generated and split into shares. A threshold number of shares are needed to reconstruct the key. The shares are stored at random locations within one or more networks. Each location is configured to delete the stored data after a predetermined time period. Encapsulated data is created by creating a vanishing data object (VDO) comprising the encrypted data, and data sufficient to locate at least a threshold number of key shares from their stored locations. The VDO becomes inaccessible after enough shares of the data are deleted such that the data key cannot be restored. However, if prior to timeout a sufficient number of data key shares are located and retrieved the data key can be reconstructed. The reconstructed data key is then used to decrypt the original data.
Owner:UNIV OF WASHINGTON CENT FOR COMMERICIALIZATION
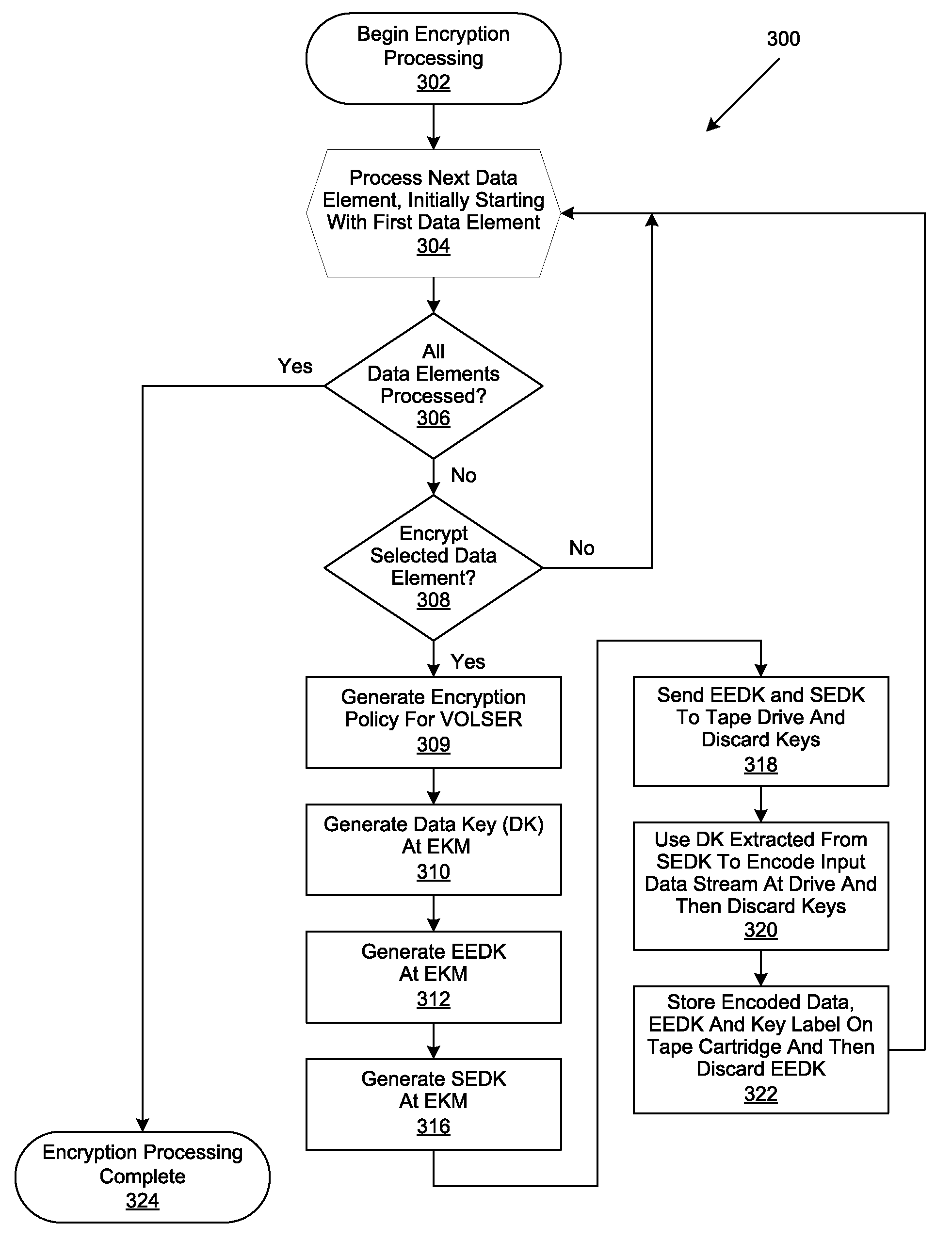
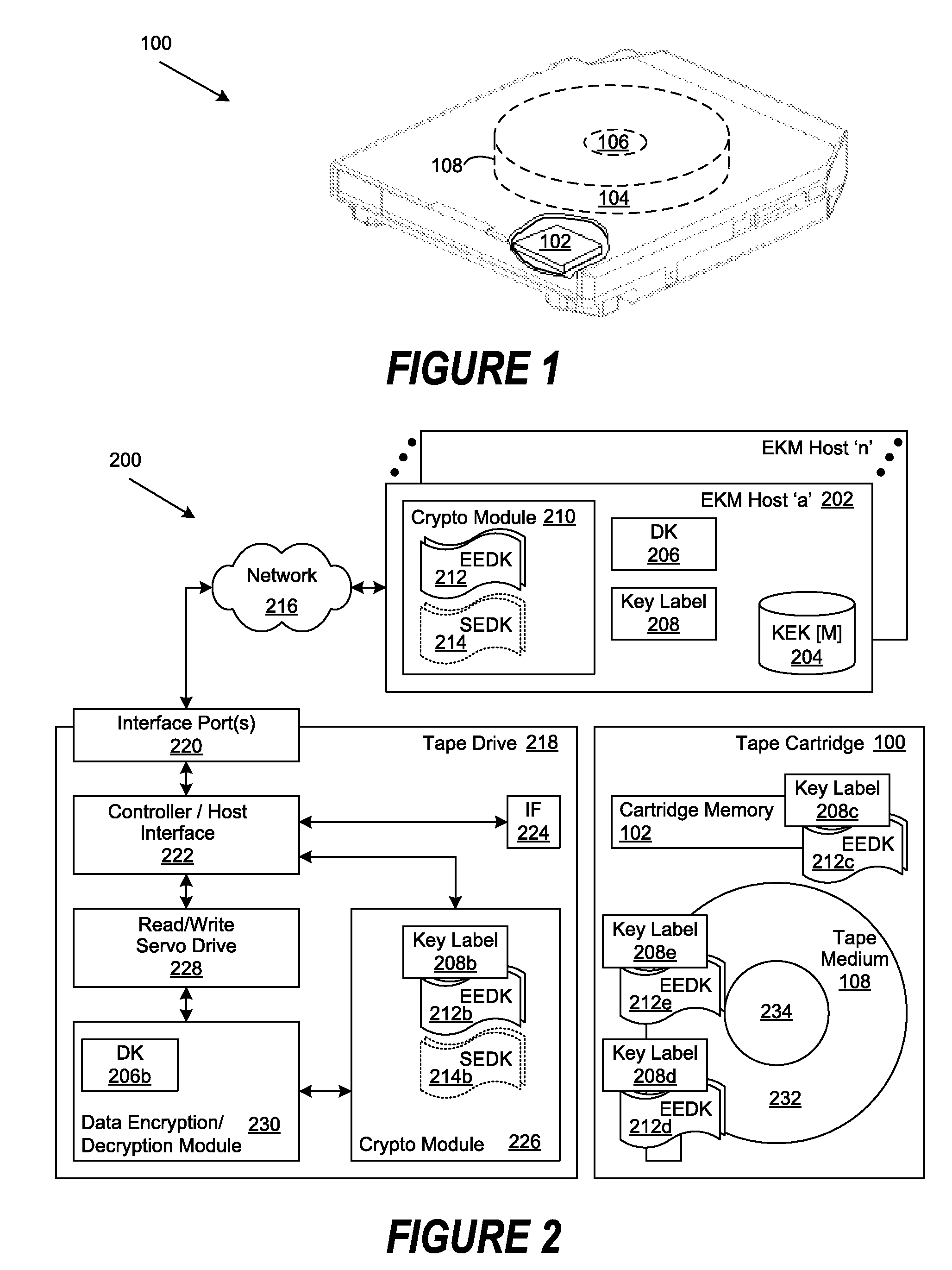
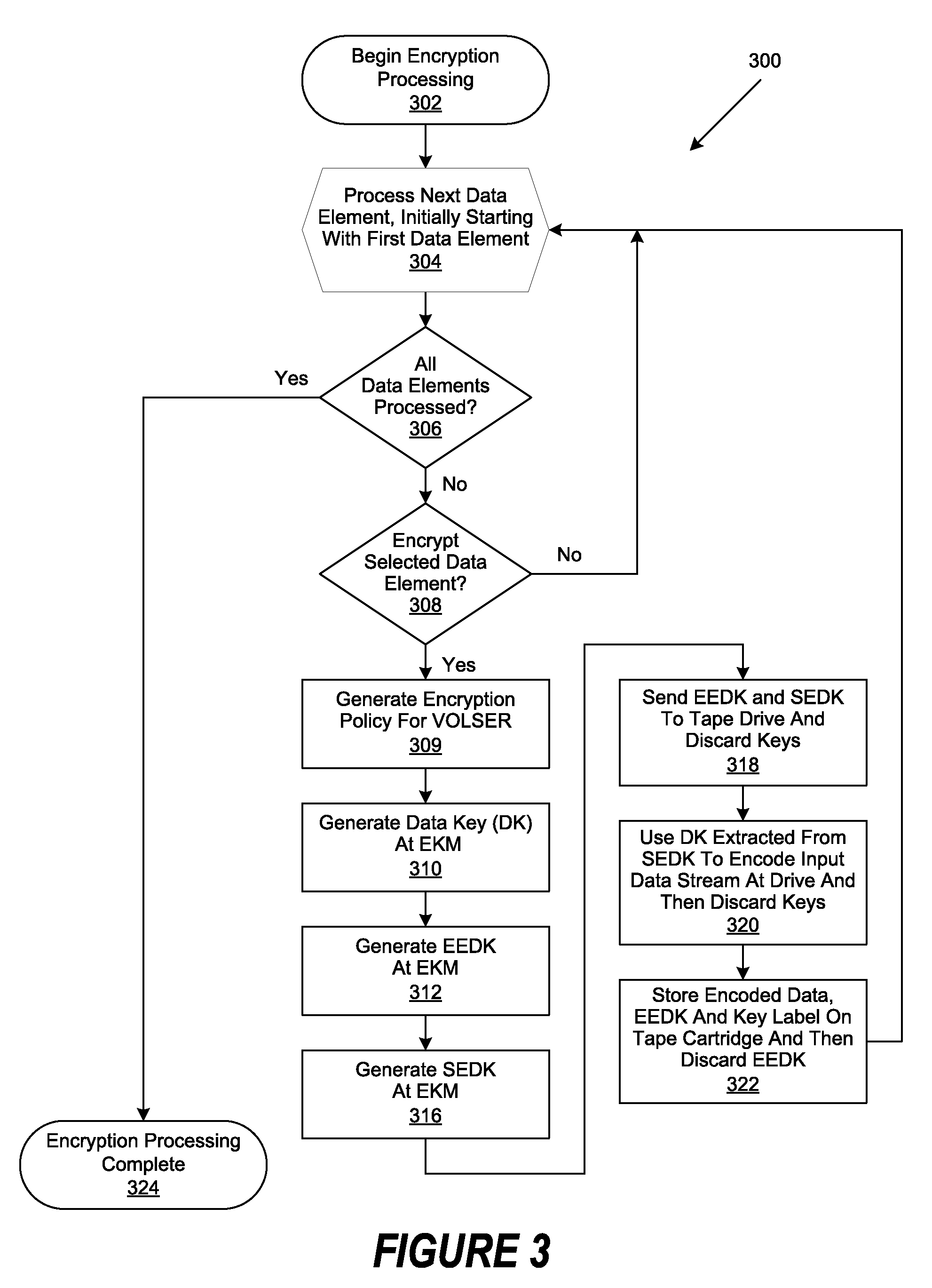
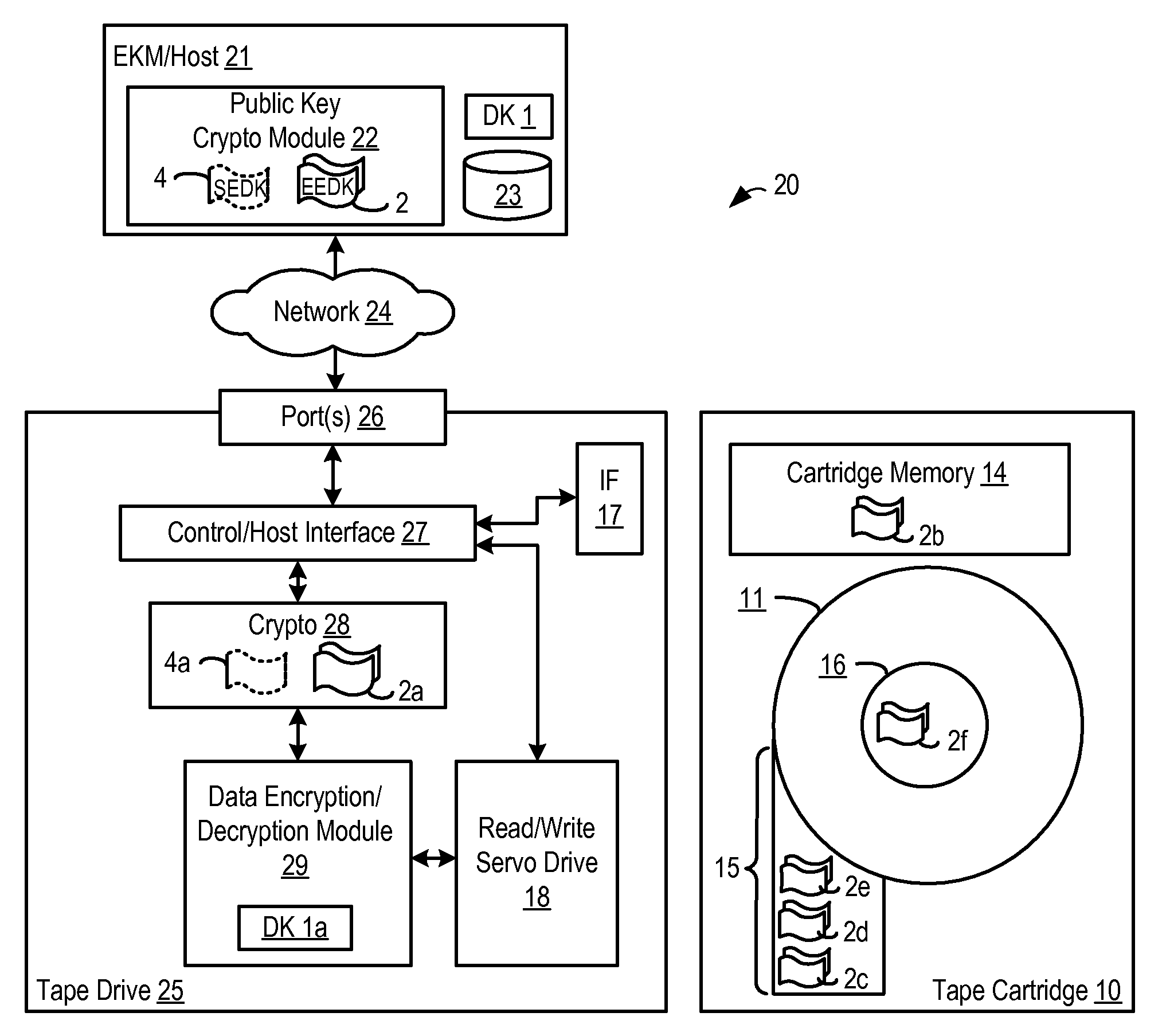
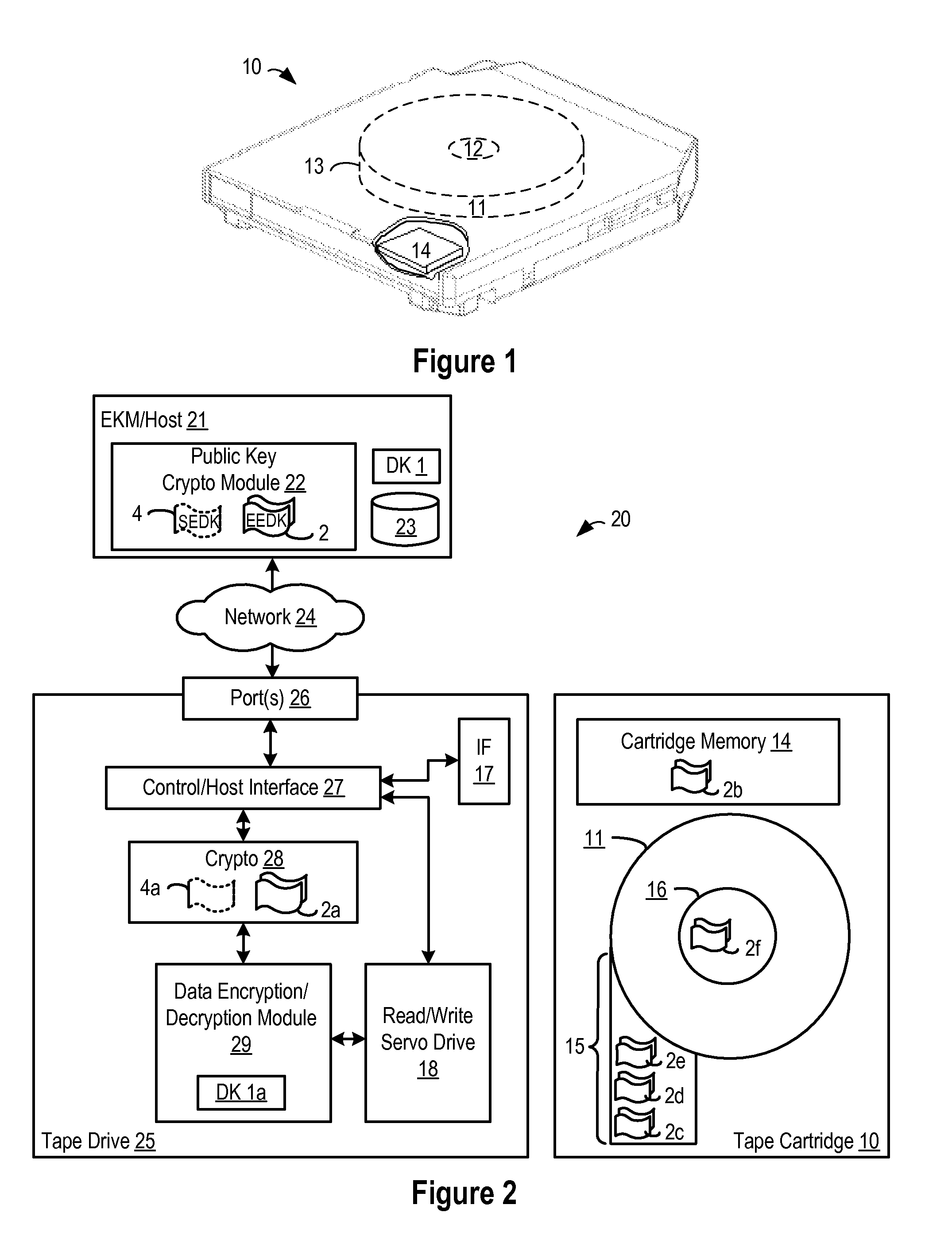
Retrieval and Display of Encryption Labels From an Encryption Key Manager
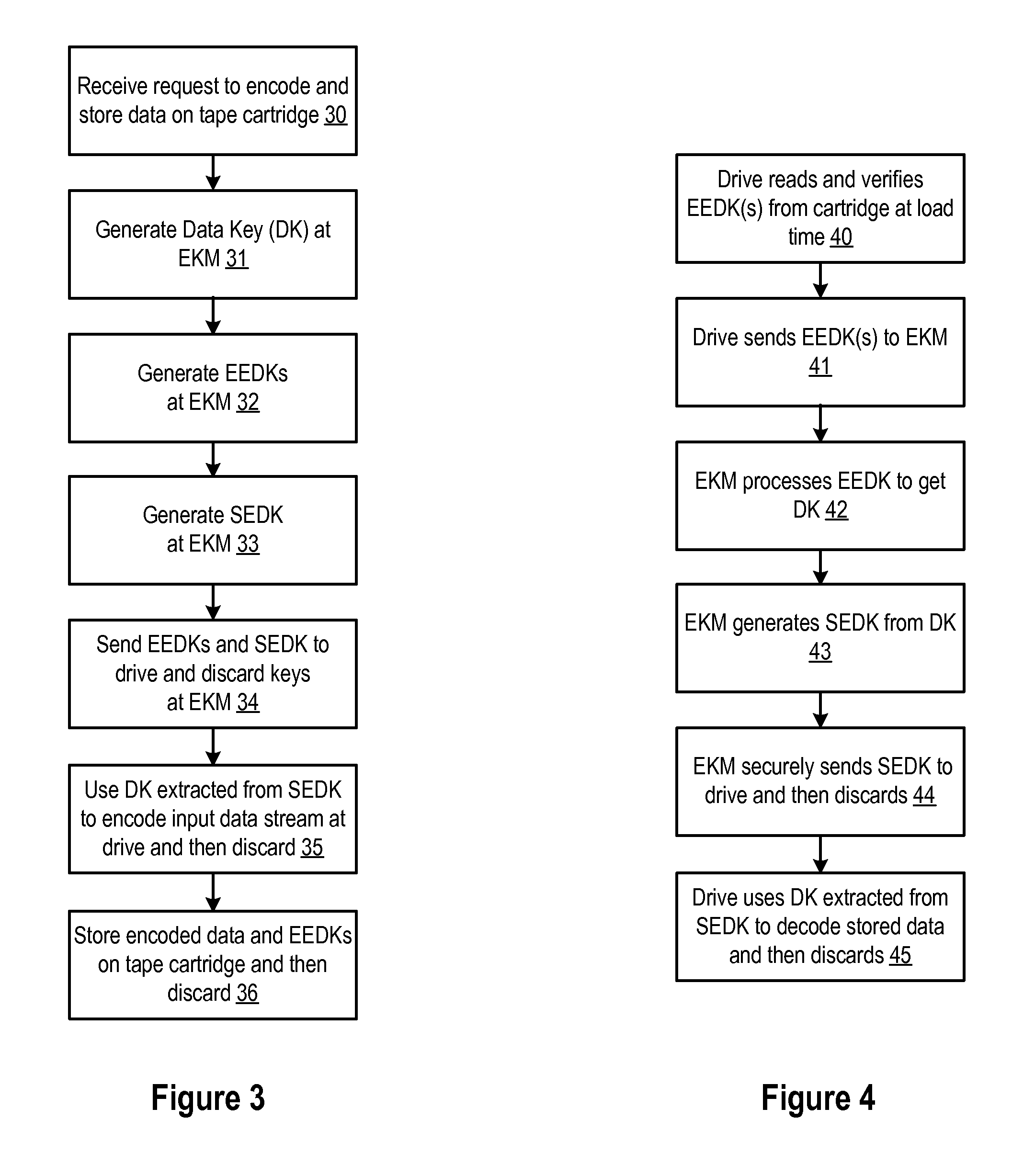
InactiveUS20080165973A1Safe storageKey distribution for secure communicationPublic key for secure communicationEncapsulated dataKey management
A method, system and program are provided for the retrieval of key label codes enabling access to encrypted data in a storage cartridge. An external key manager (EKM) wraps the data key used to encrypt the data with one or more encryption keys to form one or more encryption encapsulated data keys (EEDKs). The EEDK(s), which comprise a key label referencing the EKM containing their respective decryption key, are then stored on the storage cartridge along with the encrypted data. A key label list is generated and updated by querying one or more EKMs to collect the key labels they support. Once the key labels are collected, the existing list is purged and replaced with the new list of collected key labels. A key label is selected from the updated list and its associated EEDK is routed to the EKM containing the decryption key required to extract the data key it contains, which is then used to encode the data on the tape cartridge.
Owner:IBM CORP
Specifying and utilizing paths through a network
For a multi-tenant environment, some embodiments of the invention provide a novel method for (1) embedding a specific path for a tenant's data message flow through a network in tunnel headers encapsulating the data message flow, and then (2) using the embedded path information to direct the data message flow through the network. In some embodiments, the method selects the specific path from two or more viable such paths through the network for the data message flow.
Owner:NICIRA
Packet transmission method for mobile internet
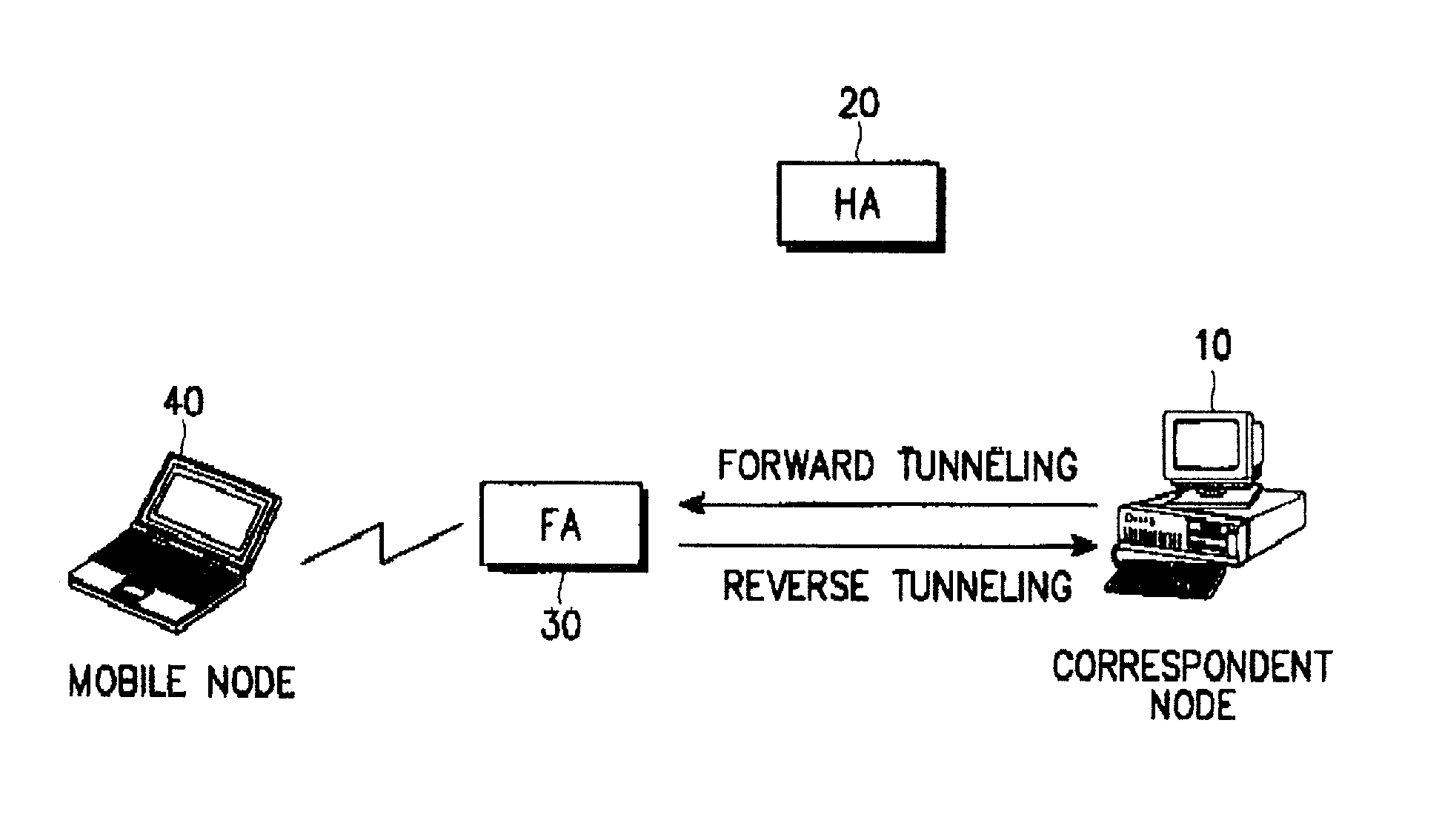
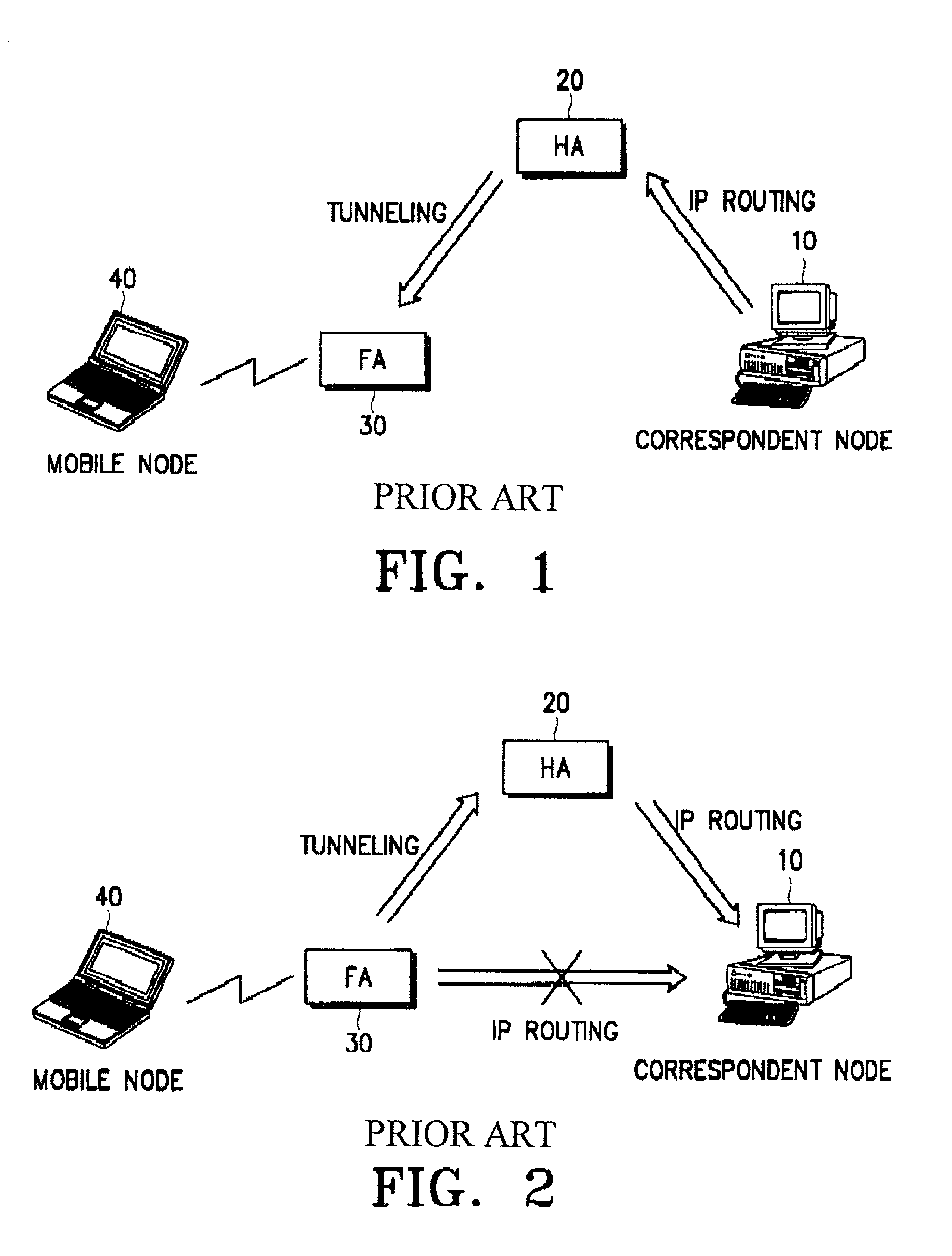
InactiveUS7161913B2Function is performedData switching by path configurationWireless network protocolsIp addressEncapsulated data
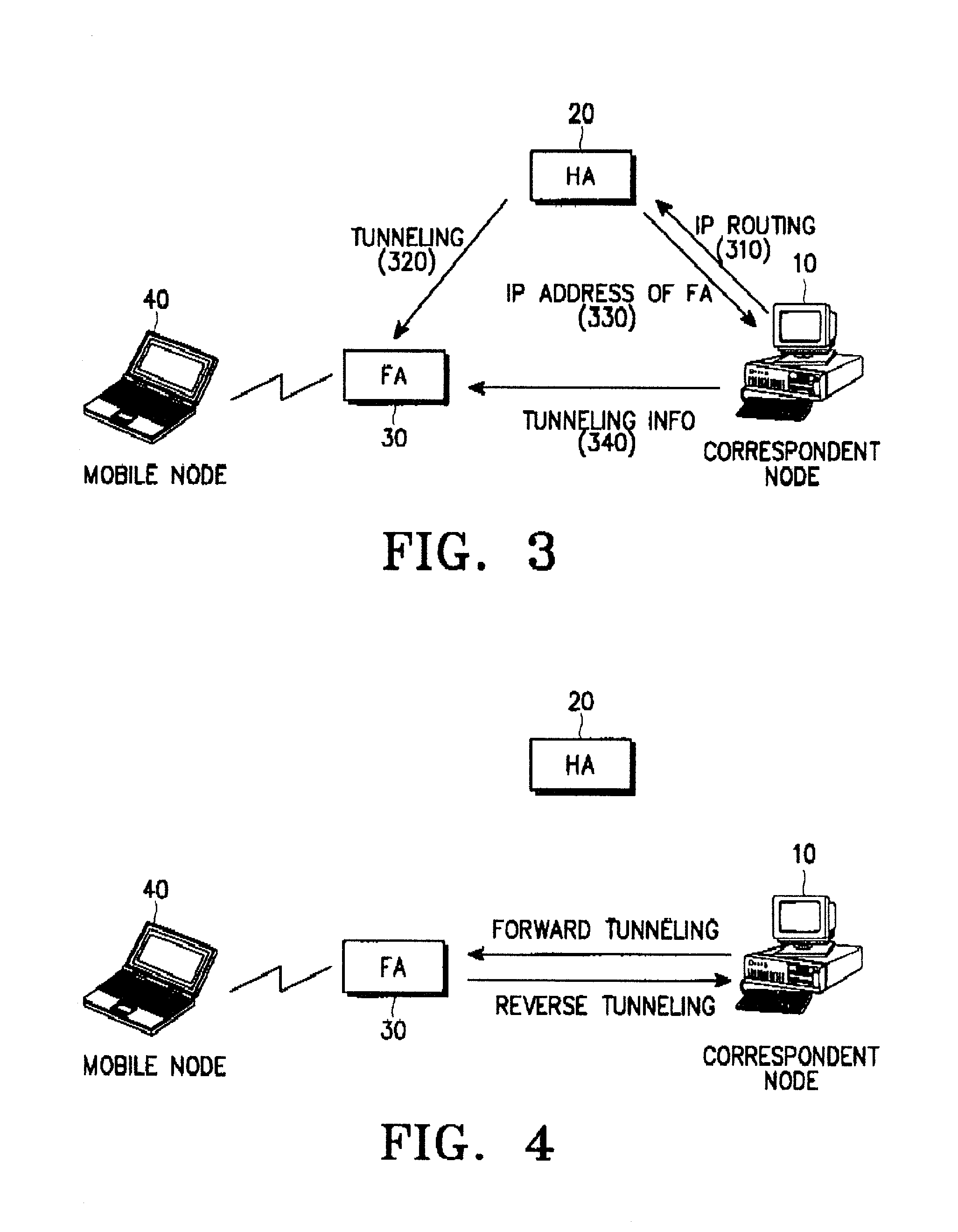
A method for transmitting a data packet from a mobile node to a correspondent node through a foreign agent while maintaining security is disclosed. A correspondent node transmits a first data packet for communication with a mobile node to the home agent. Upon receipt of the first data packet from the home agent, the foreign agent transmits the first data packet to the mobile node through a radio channel. The home agent transmits the IP address of the foreign agent to the correspondent node after transmitting the first data packet to the foreign agent. The correspondent node transmits tunneling indication information indicating whether it can decapsulate a data packet encapsulated by the foreign agent to the foreign agent after receiving the IP address of the foreign agent from the home agent. The foreign agent encapsulates subsequent data packets received from the mobile node with a tunneling IP header for reverse tunneling and transmits the encapsulated data packets to the correspondent node, after receiving the tunneling indication information from the correspondent node.
Owner:SAMSUNG ELECTRONICS CO LTD
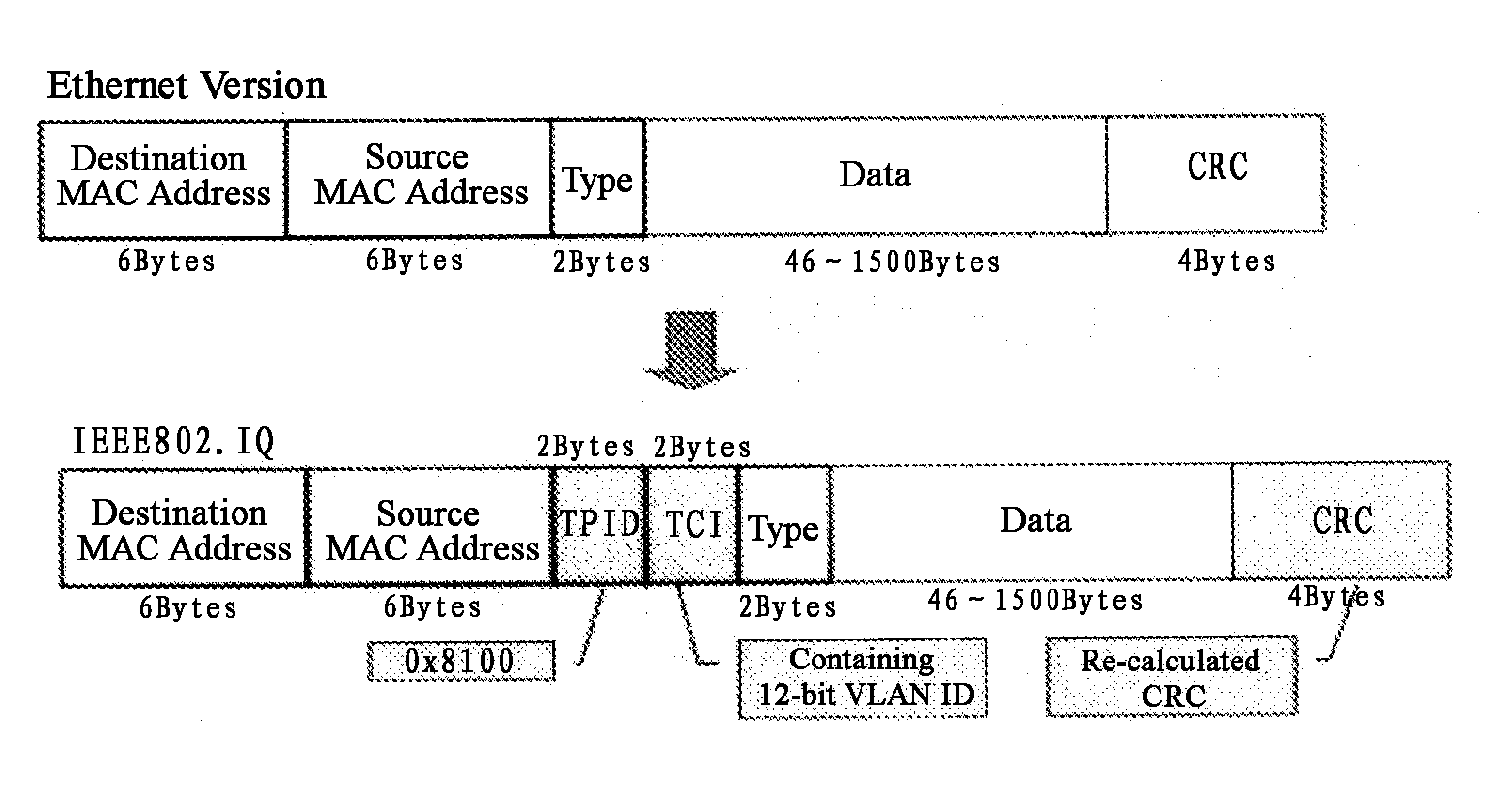
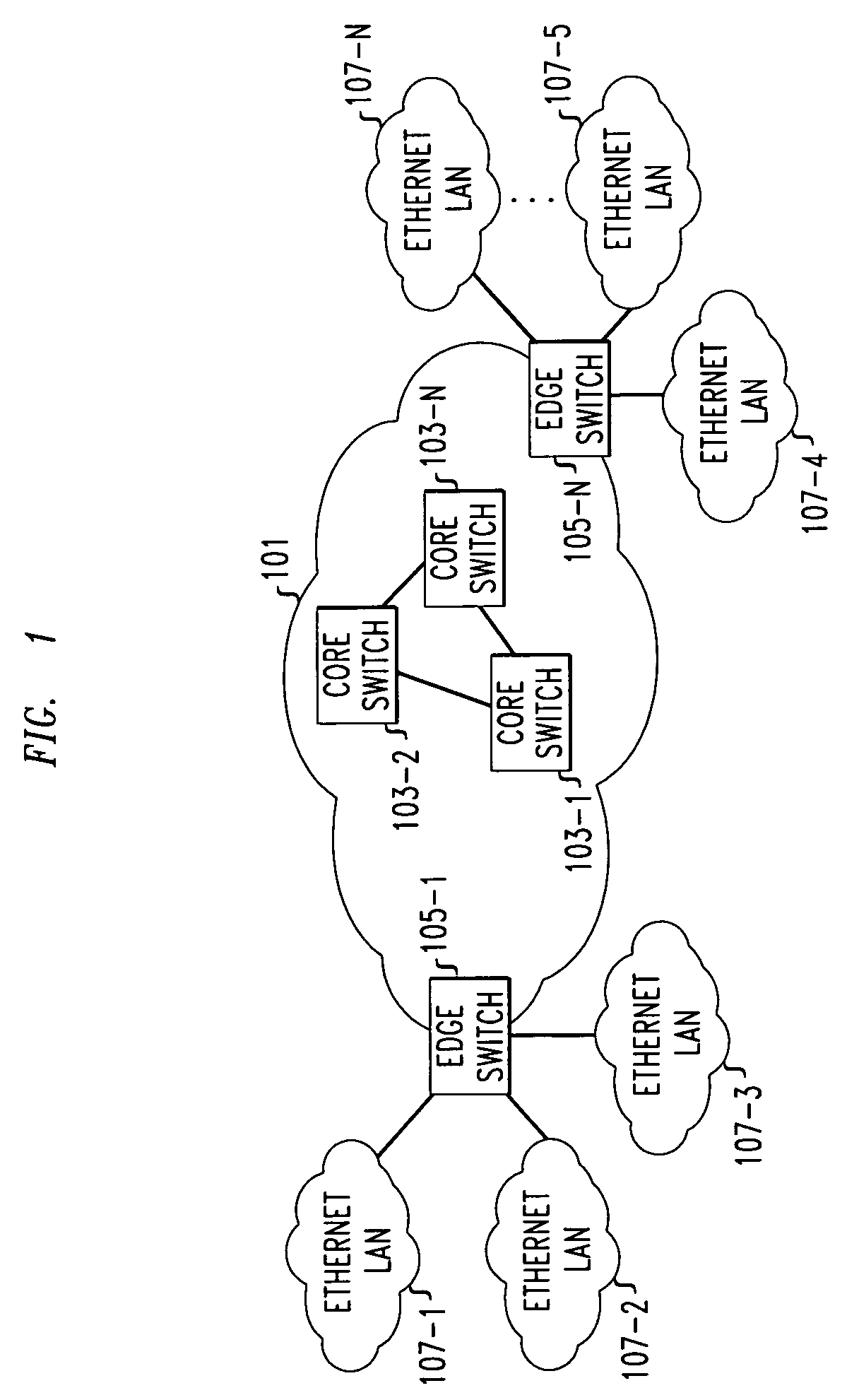
Ethernet packet encapsulation for metropolitan area ethernet networks
InactiveUS7130303B2Efficient mannerTime-division multiplexNetworks interconnectionEncapsulated dataMetro Ethernet
The problems of large tables in Ethernet switches used on a metropolitan area scale, and the exposure of the enterprise network topologies, can be avoided by encapsulating each original Ethernet packet, which originates in a first network of an entity, e.g., an enterprise, a customer, or a network service provider, within another Ethernet packet which is given a source address that identifies the new encapsulating packet as originating at a port of a switch that is located at the interface between the first network in which the original packet originated and a second Ethernet network, e.g., the metropolitan area Ethernet network, which is to transport the encapsulating packet. When the encapsulating packet would exceed the allowable Ethernet packet length, the original packet may be split up at the interface between the first and second network and the resulting parts encapsulated into two encapsulating packets.
Owner:LUCENT TECH INC
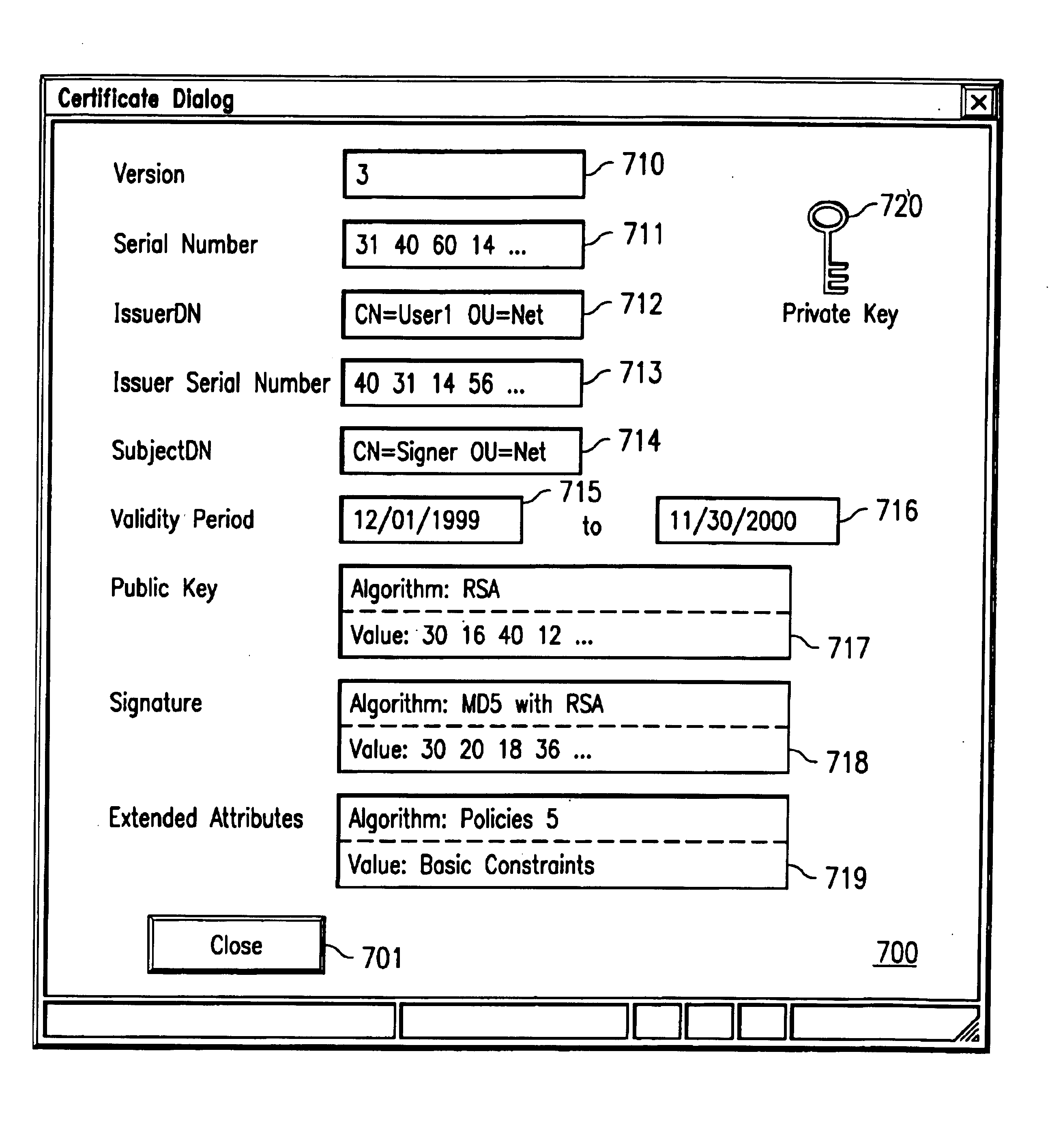
Method and system for presentation and manipulation of PKCS enveloped-data objects
InactiveUS6914985B1Public key for secure communicationUser identity/authority verificationData processing systemGraphics
A method and system for processing enveloped data objects in a data processing system. The enveloped data object may be formatted as defined by PKCS (Public Key Cryptography Standard) standards. An enveloped data object utility allows a user to view and edit the contents of data objects embedded within an enveloped data object via a graphical user interface. Graphical objects represent the data objects embedded within an enveloped data object. A user may drag and drop objects onto other objects within the enveloped data object, and the enveloped data object utility automatically performs the necessary encrypting operations. Logical associations between data objects contained within the enveloped data object are determined or created, and the logical associations are displayed using visual indicators. As data objects are added or deleted through user actions on the graphical objects, the visual indicators are updated.
Owner:PAYPAL INC
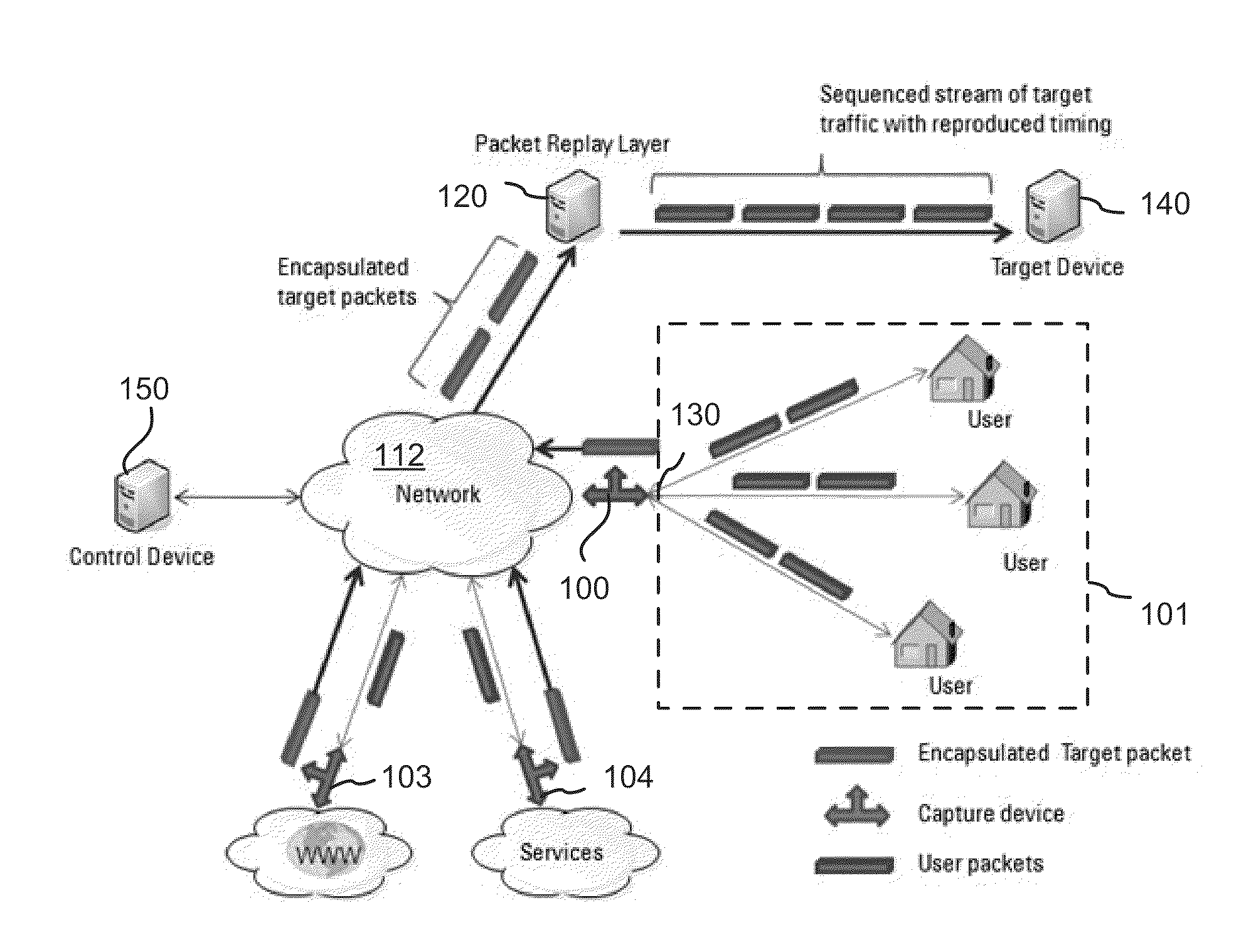
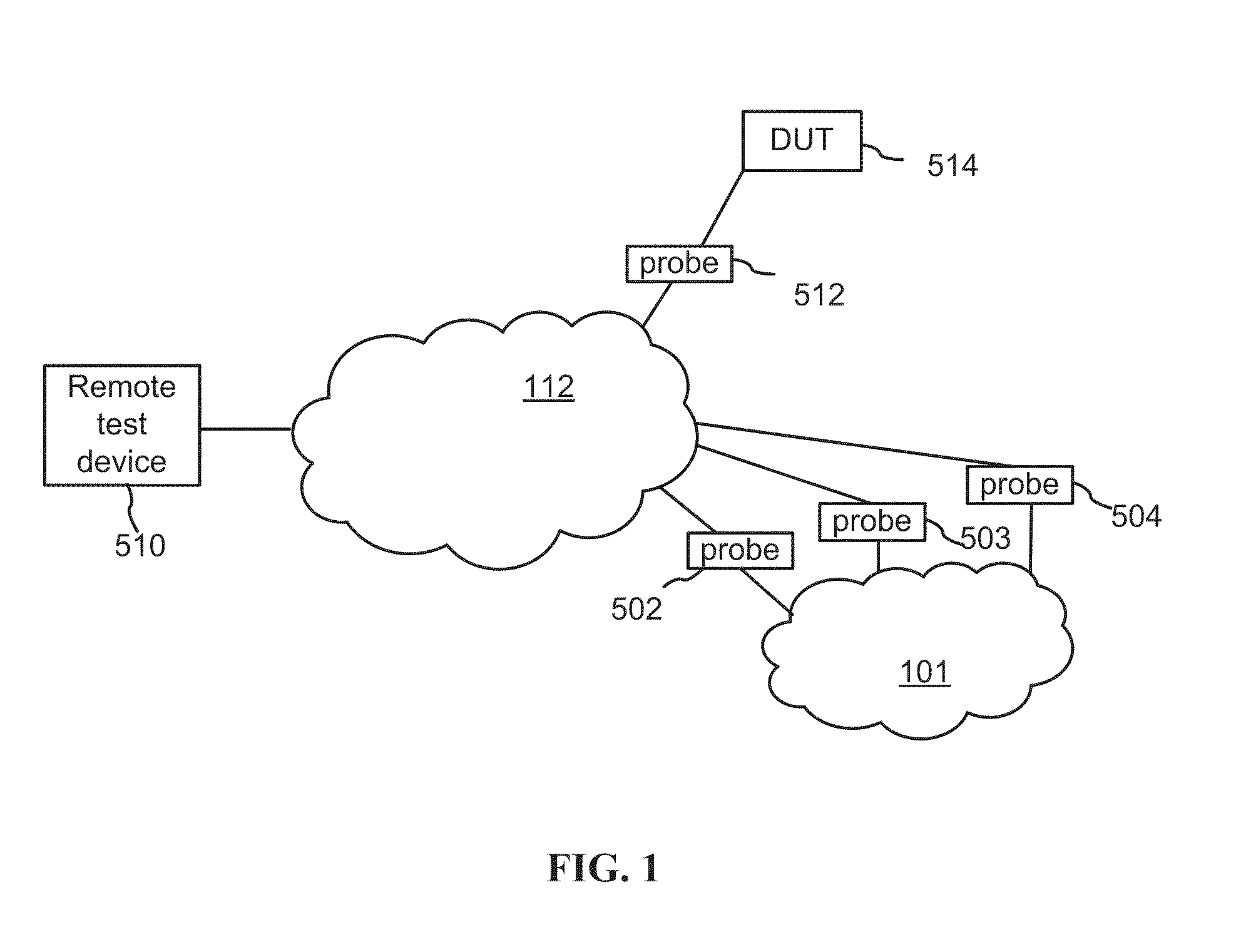
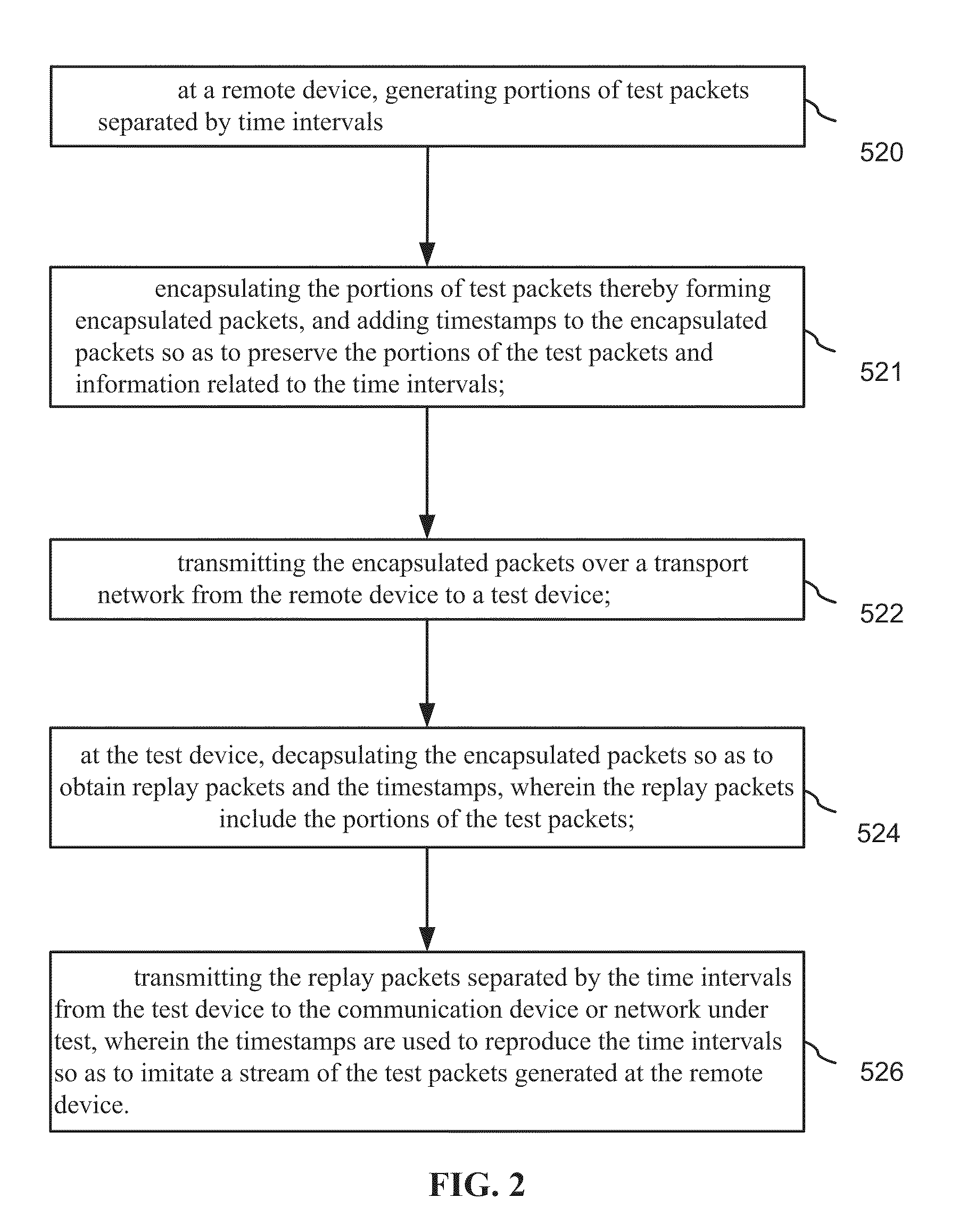
Method of remote active testing of a device or network
A test device includes a packet input receiver for receiving encapsulated packets from a network; a packet reader for extracting timing information from the encapsulated packets, and for decapsulating encapsulated packets so as to obtain test packets; a FIFO queue for storing the test packets; a packet controller for reading the test packets from the FIFO queue and writing the test packets into a de-jitter buffer in accordance with the timing information, the de-jitter buffer for storing the reordered test packets; and, a packet output generator for providing the test packets to a target device wherein time intervals between the test packets are reproduced using the timing information.
Owner:VIAVI SOLUTIONS INC
Distributed key store
InactiveUS20080063209A1Safe storageKey distribution for secure communicationInternal/peripheral component protectionEncapsulated dataEncryption
A method, system and program are provided for enabling access to encrypted data in a storage cartridge by wrapping the data key used to encrypt the data with one or more encryption keys (e.g., a public key from a public / private key pair) to form one or more encryption encapsulated data keys (EEDKs) and then storing the EEDK(s) on the storage cartridge along with the encrypted data. The encrypted data may be decoded by retrieving the EEDK from the storage cartridge, decrypting the EEDK with a decryption key (e.g., the private key from the public / private key pair) to extract the underlying data key, and then using the extracted data key to decrypt the encrypted data.
Owner:IBM CORP
Servers, Switches, and Systems with Virtual Interface to External Network Connecting Hardware and Integrated Networking Driver
Owner:PLURIBUS NETWORKS
System and method of transmitting content from a mobile device to a wireless display
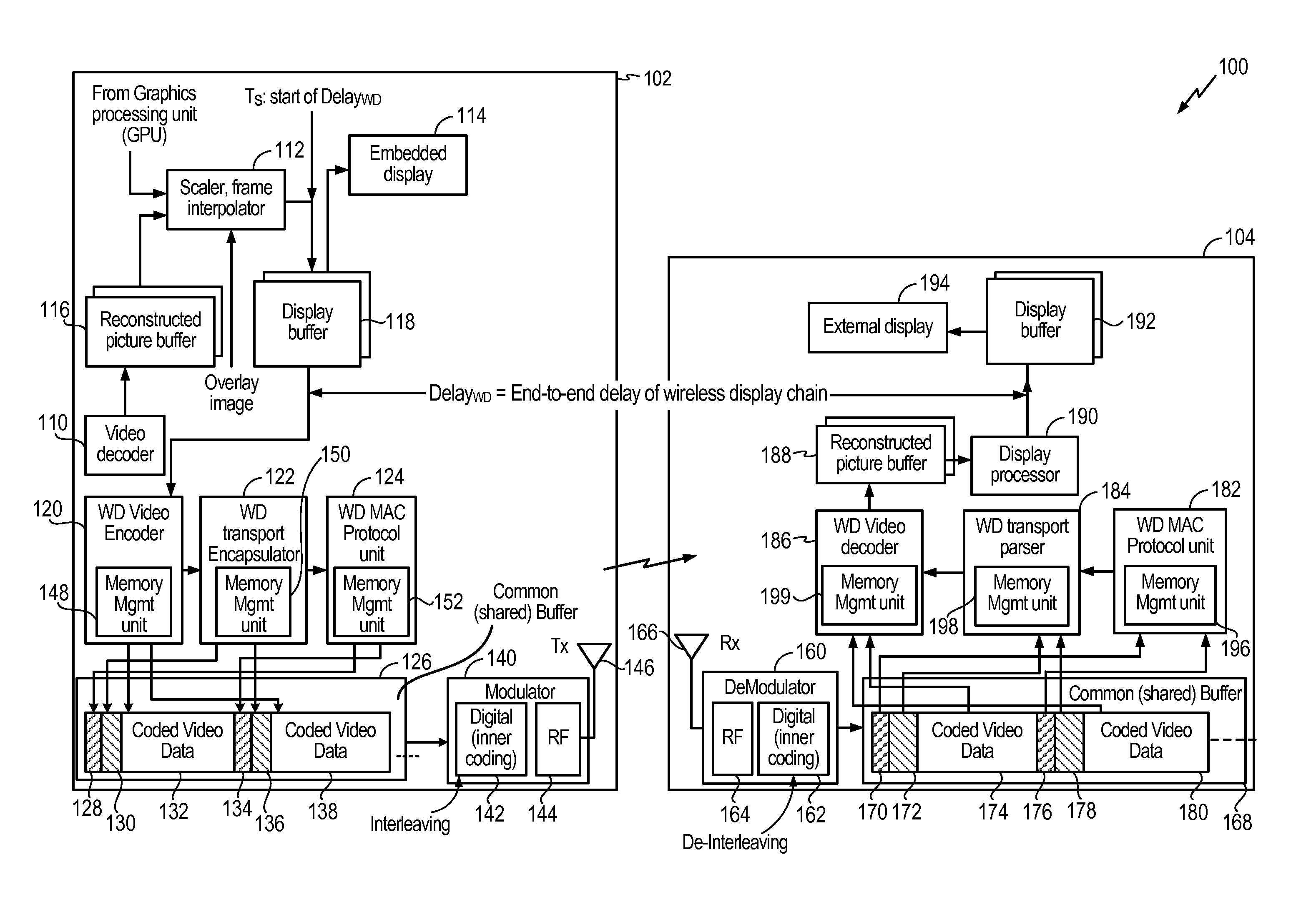
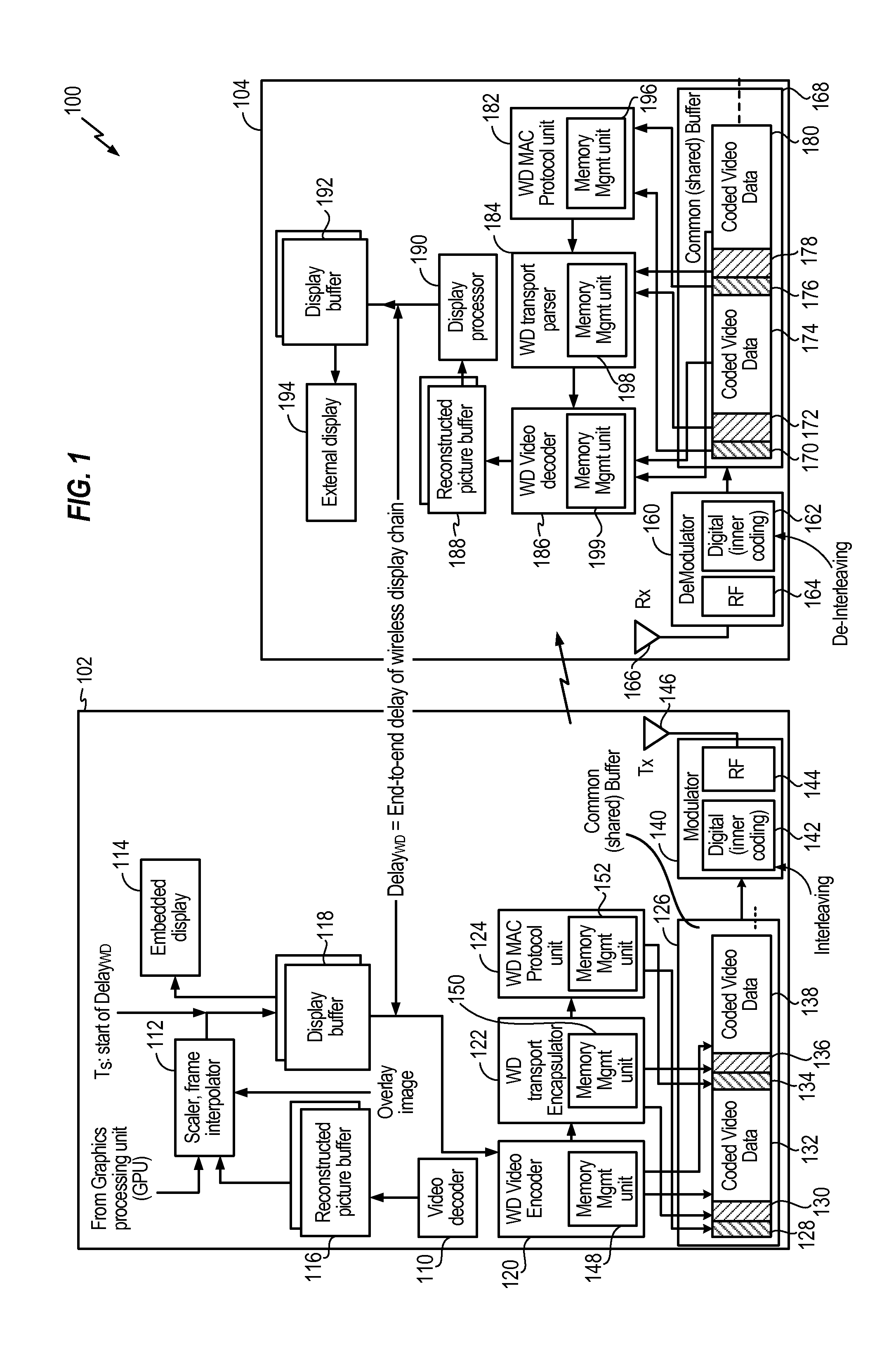
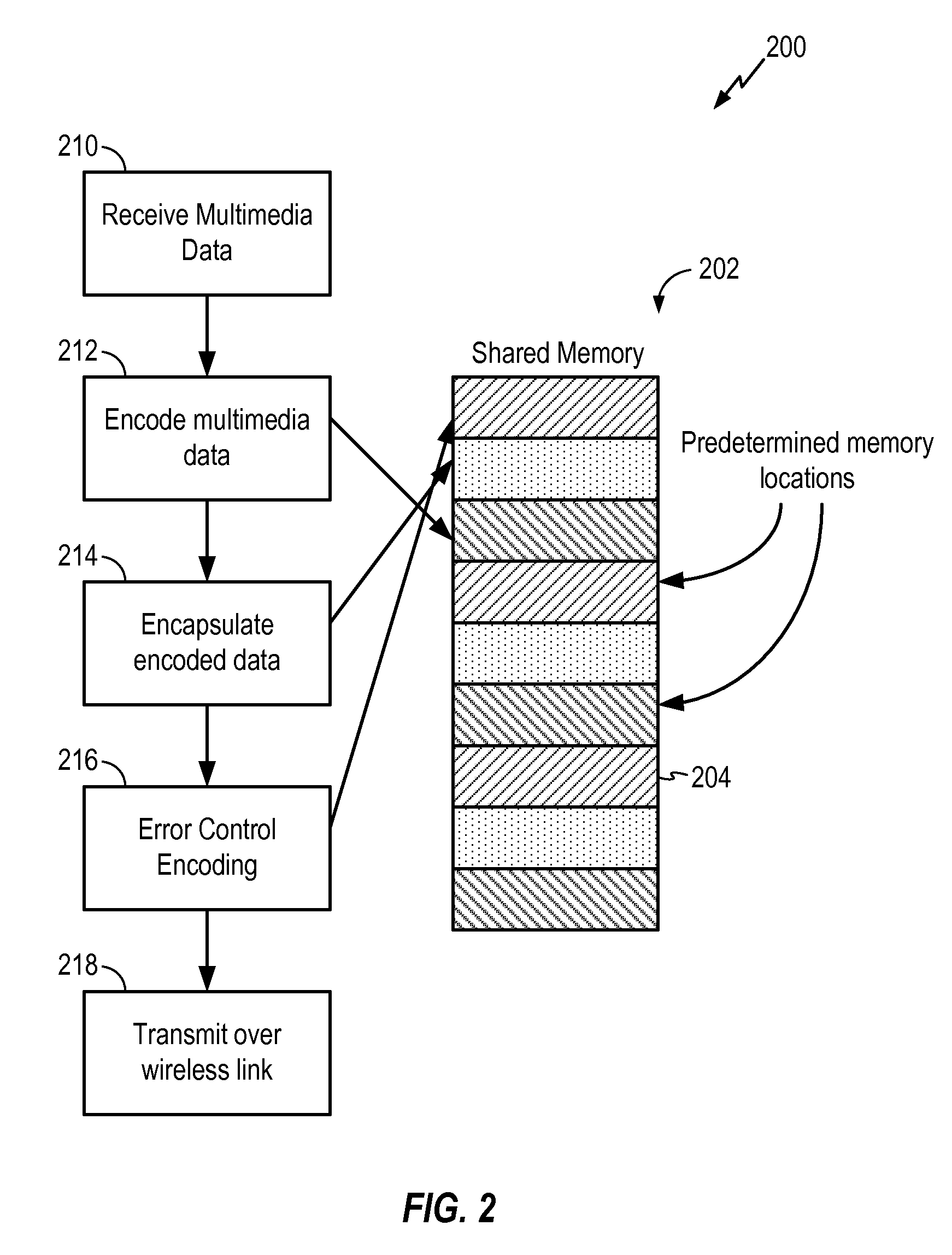
ActiveUS20110010607A1Special service provision for substationPulse modulation television signal transmissionEncapsulated dataDisplay device
A method of transmitting content to a wireless display device is disclosed. The method may include receiving multimedia data, encoding the multimedia data, and writing encoded multimedia data into a first predetermined memory location of a shared memory. Further, the method may include encapsulating the encoded multimedia data and writing encapsulation data into a second predetermined memory location of the shared memory. The method may also include calculating error control encoding and writing the error control encoding into a third predetermined memory location of the shared memory. Further, the method may include transmitting the encoded multimedia data, the encapsulation data, and the error control encoding to the wireless display device.
Owner:QUALCOMM INC
Specifying and utilizing paths through a network
For a multi-tenant environment, some embodiments of the invention provide a novel method for (1) embedding a specific path for a tenant's data message flow through a network in tunnel headers encapsulating the data message flow, and then (2) using the embedded path information to direct the data message flow through the network. In some embodiments, the method selects the specific path from two or more viable such paths through the network for the data message flow.
Owner:NICIRA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com