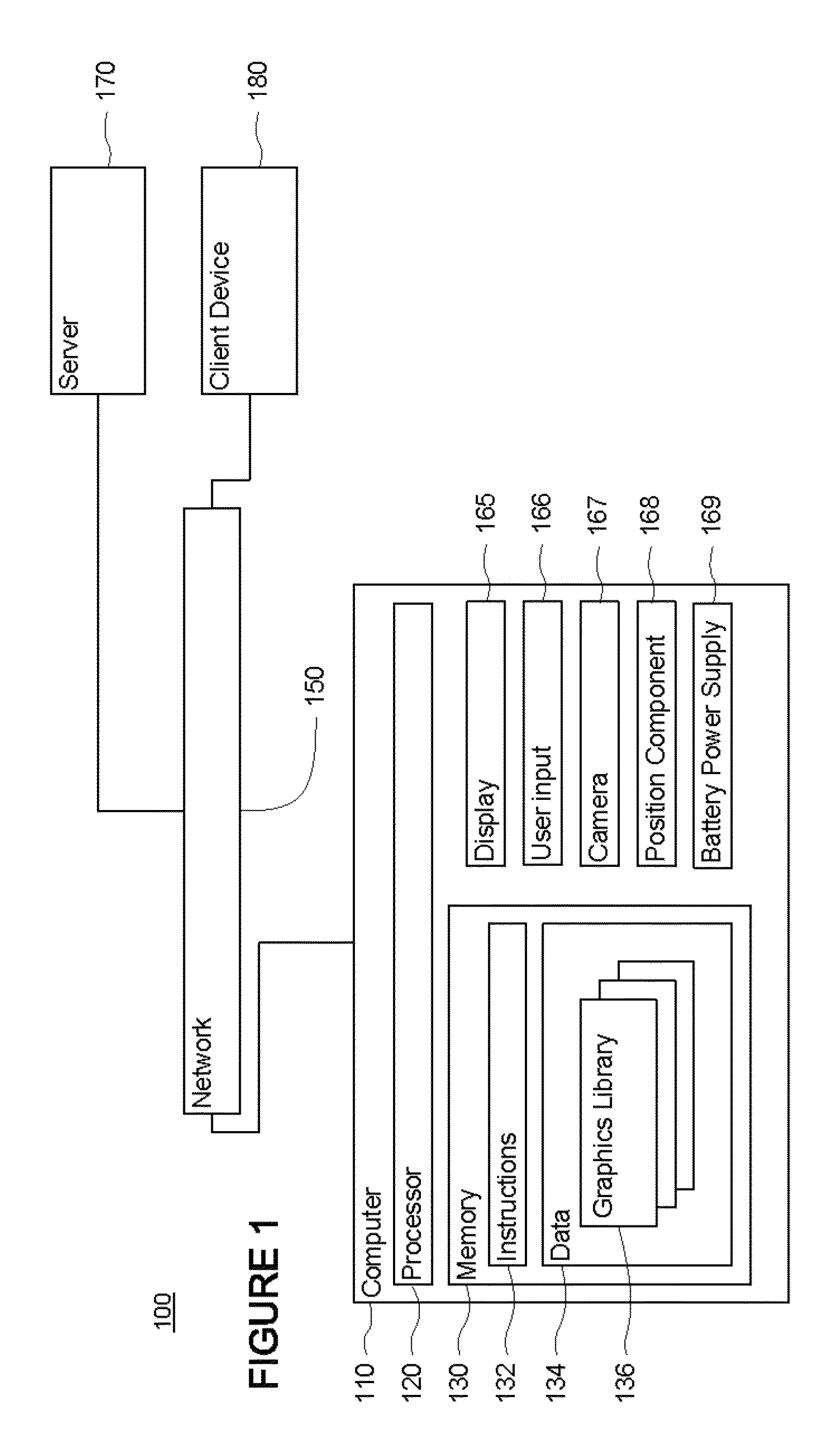
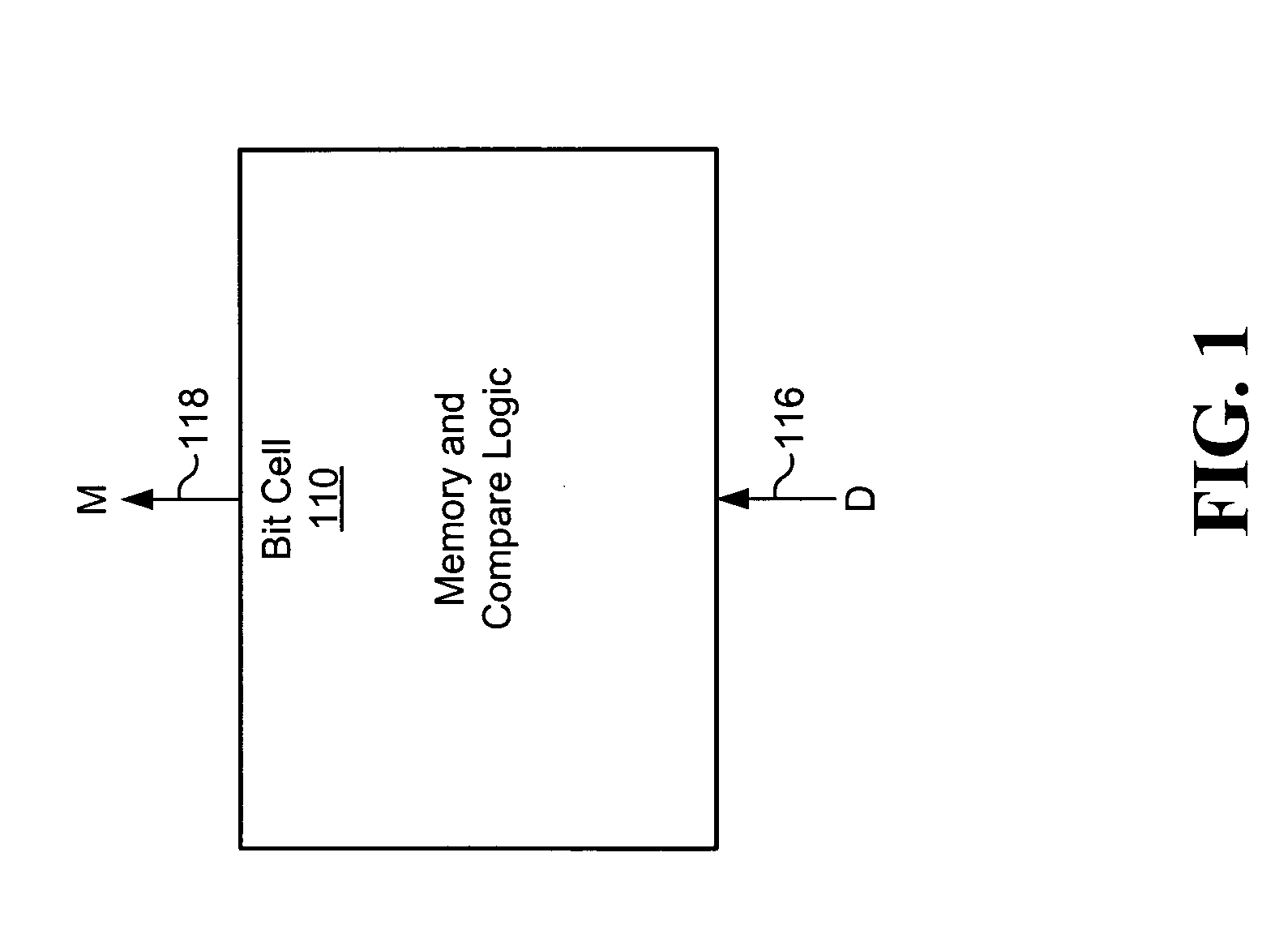
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42 results about "Bounds checking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
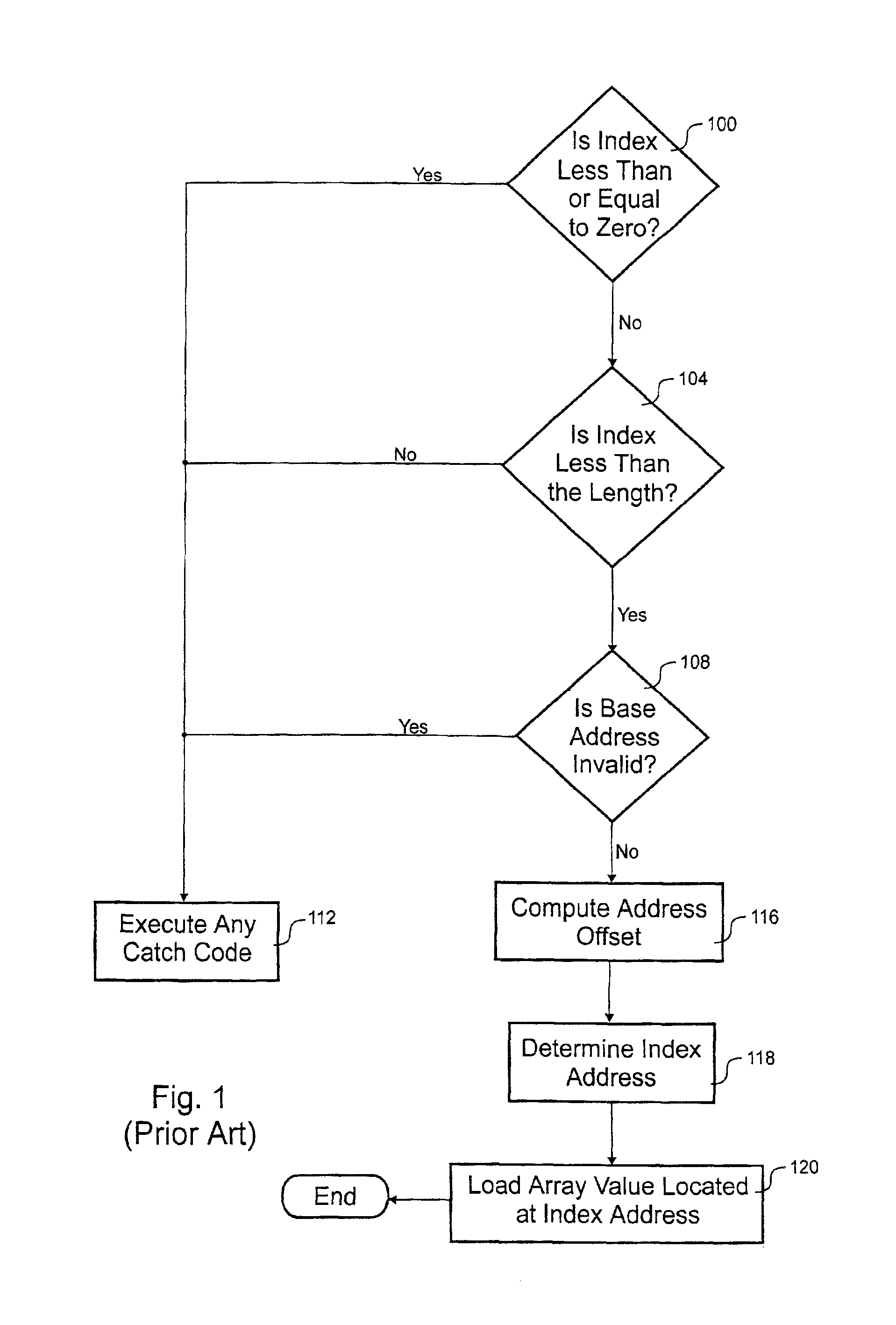
In computer programming, bounds checking is any method of detecting whether a variable is within some bounds before it is used. It is usually used to ensure that a number fits into a given type (range checking), or that a variable being used as an array index is within the bounds of the array (index checking). A failed bounds check usually results in the generation of some sort of exception signal.
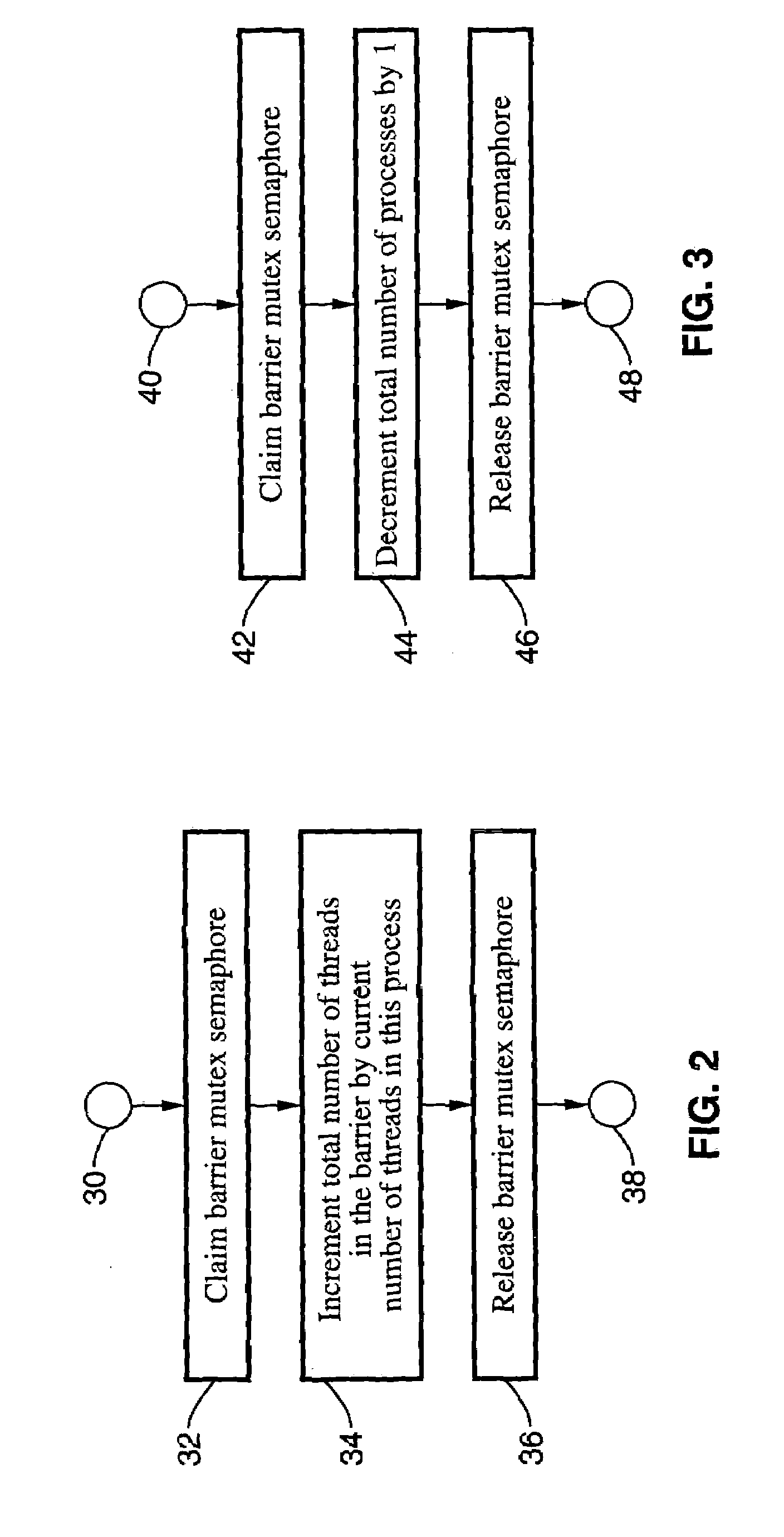
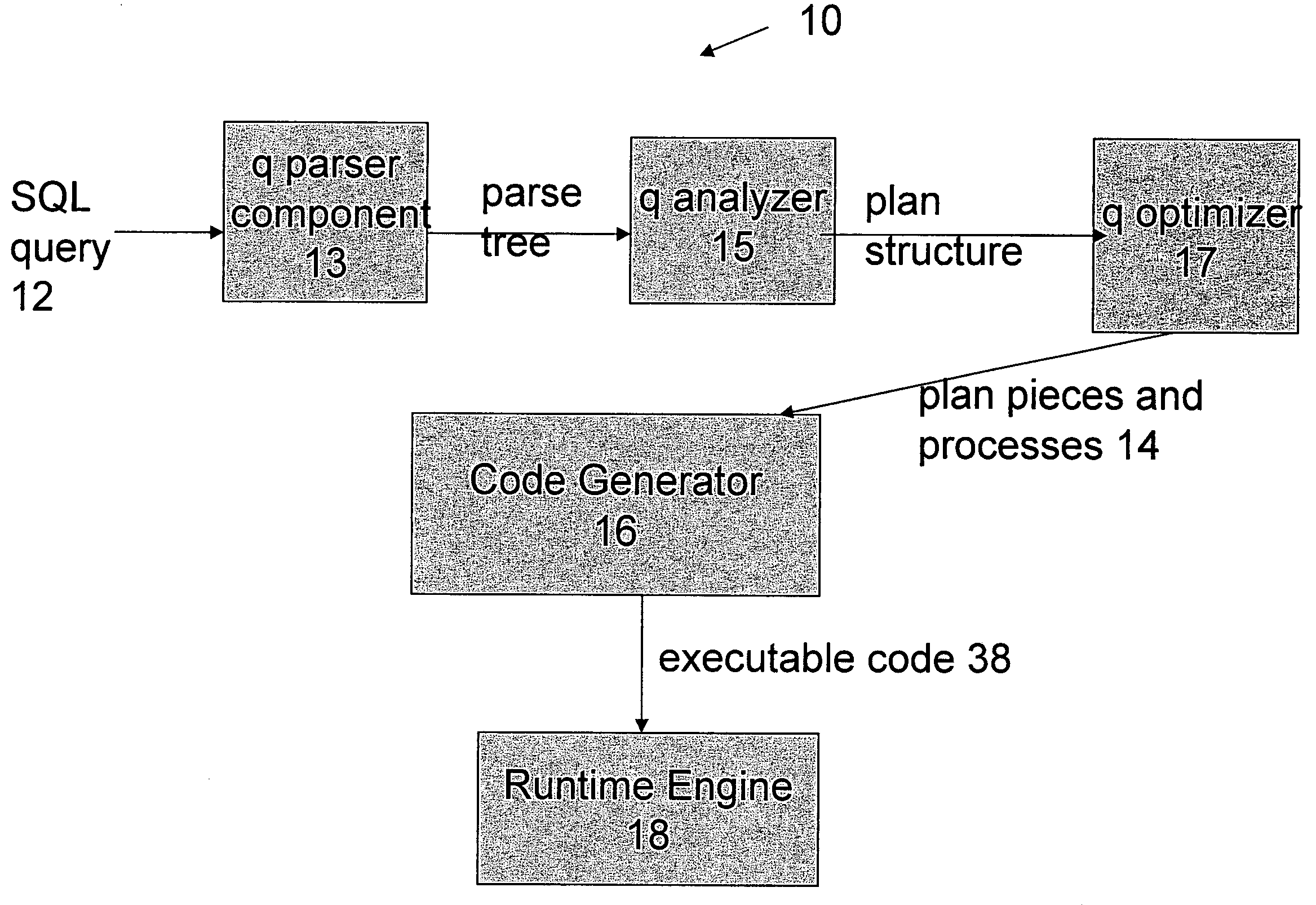
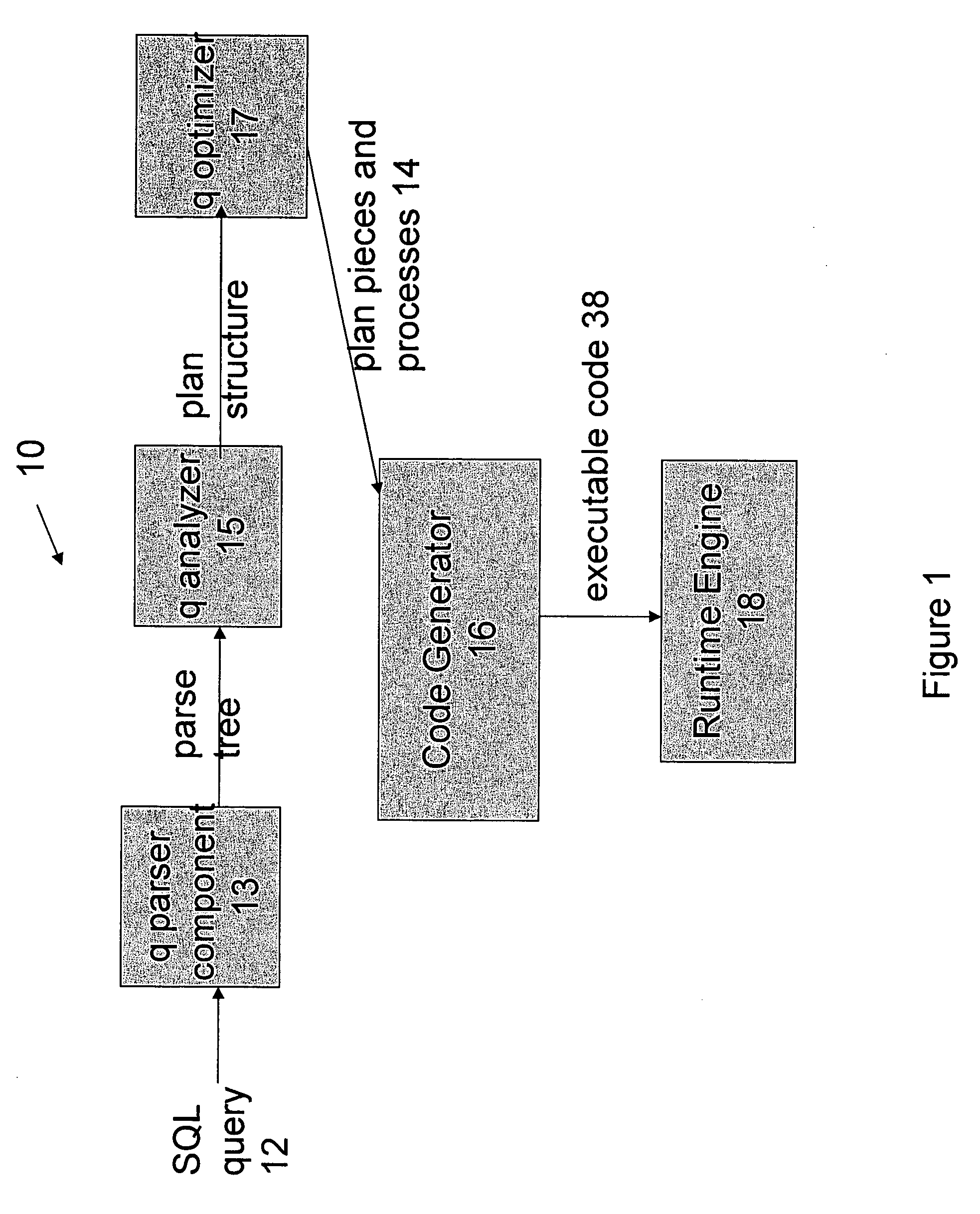
Optimized SQL code generation
ActiveUS7430549B2Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planCode generation
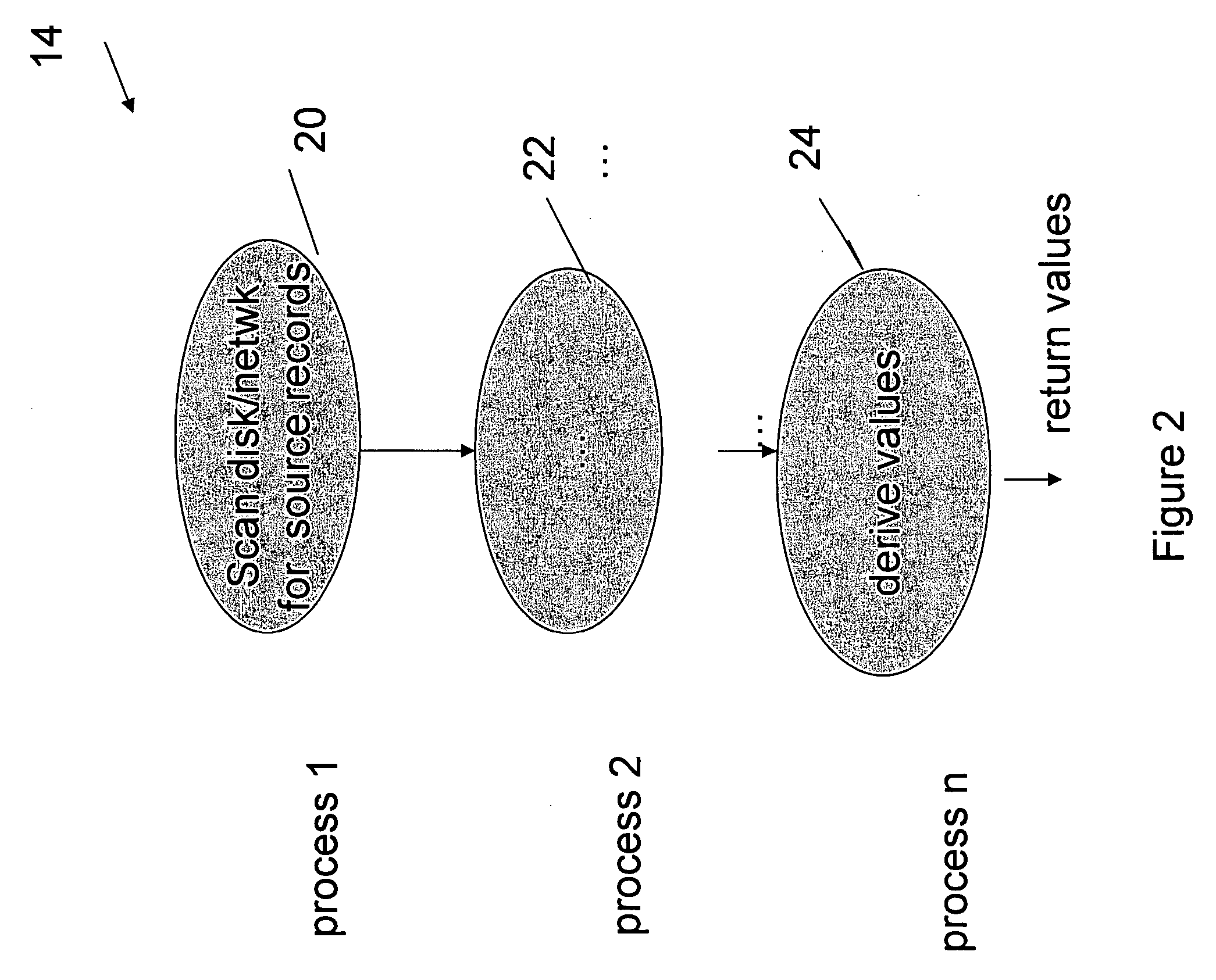
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:INT BUSINESS MASCH CORP
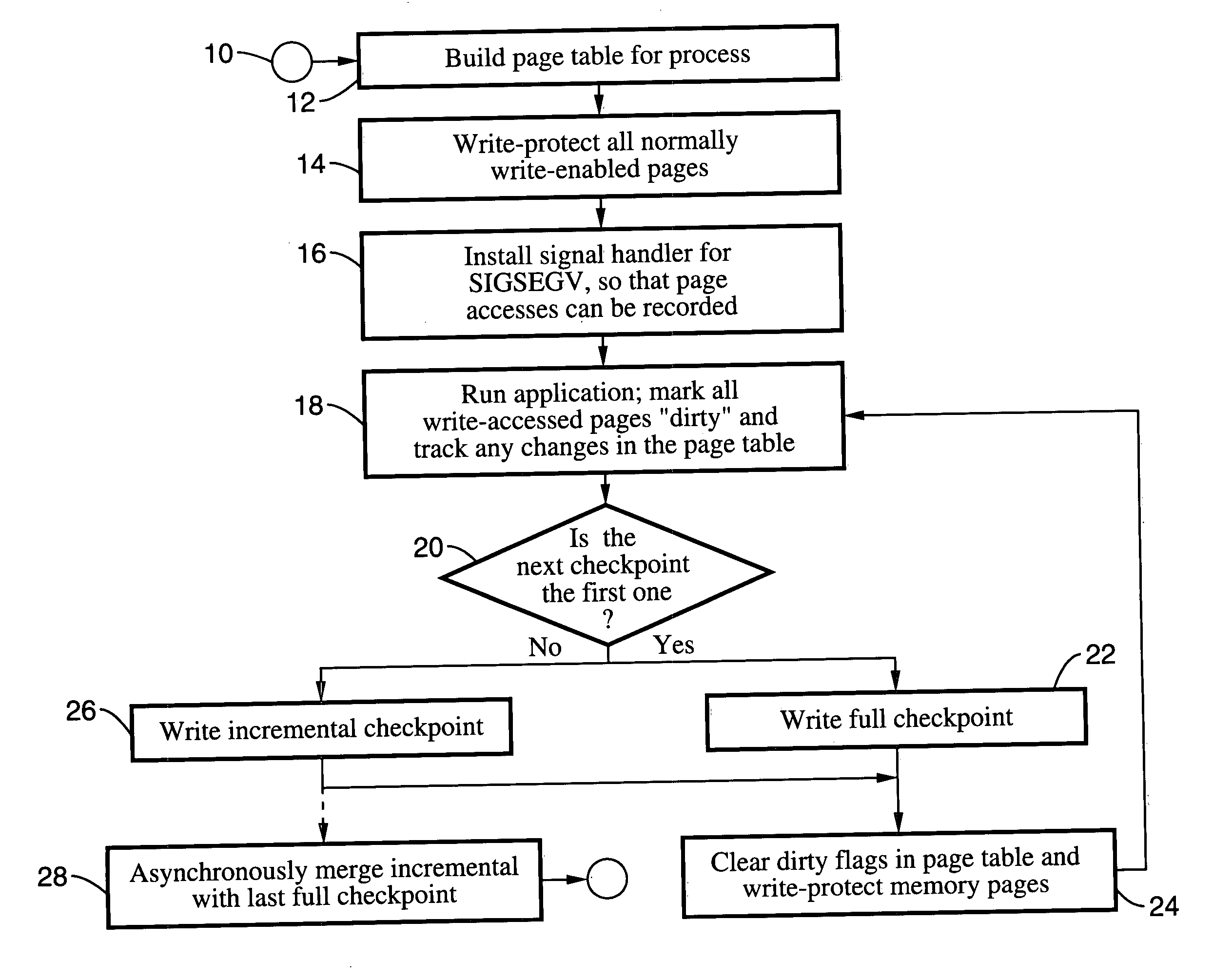
Method and system for providing transparent incremental and multiprocess checkpointing to computer applications
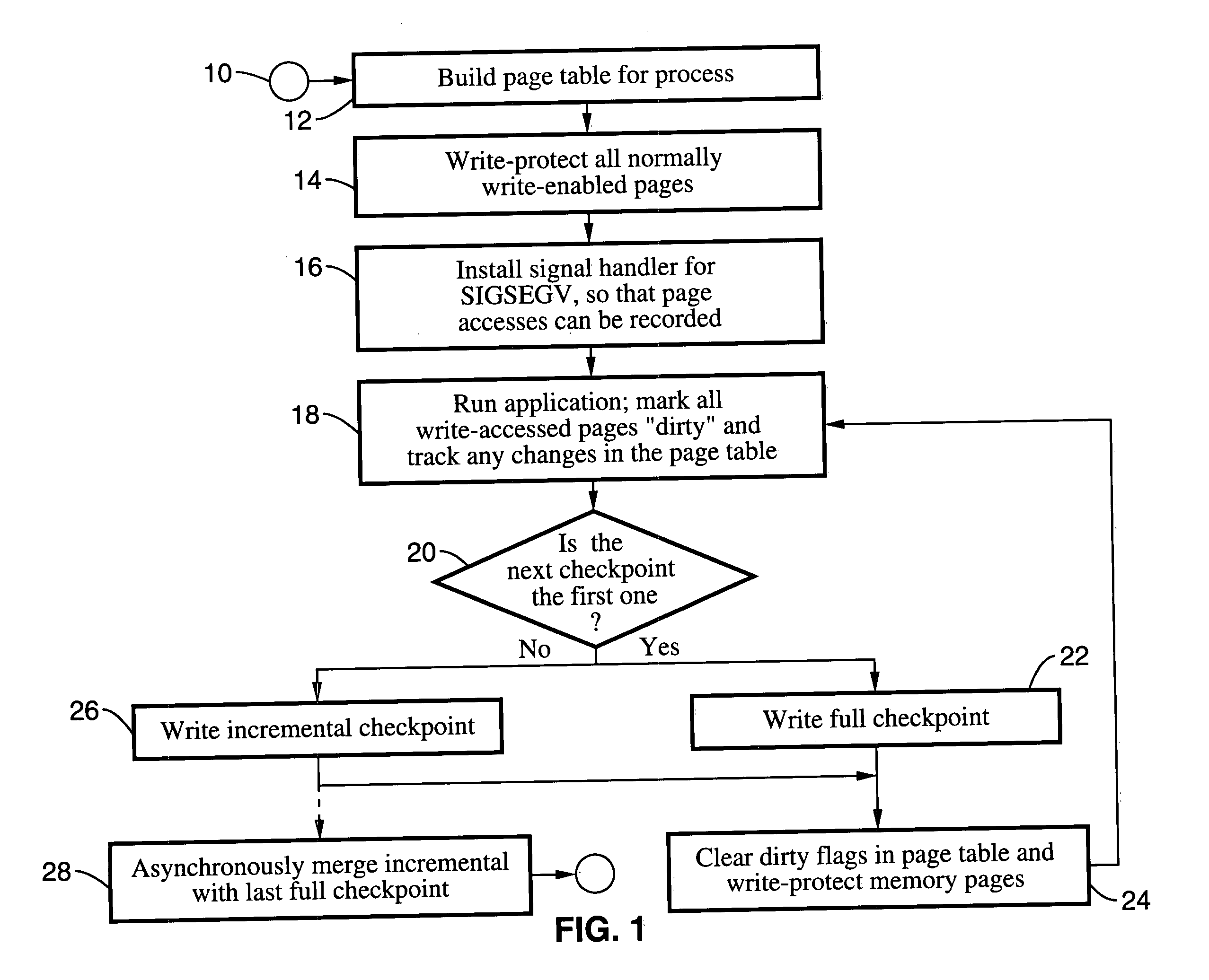
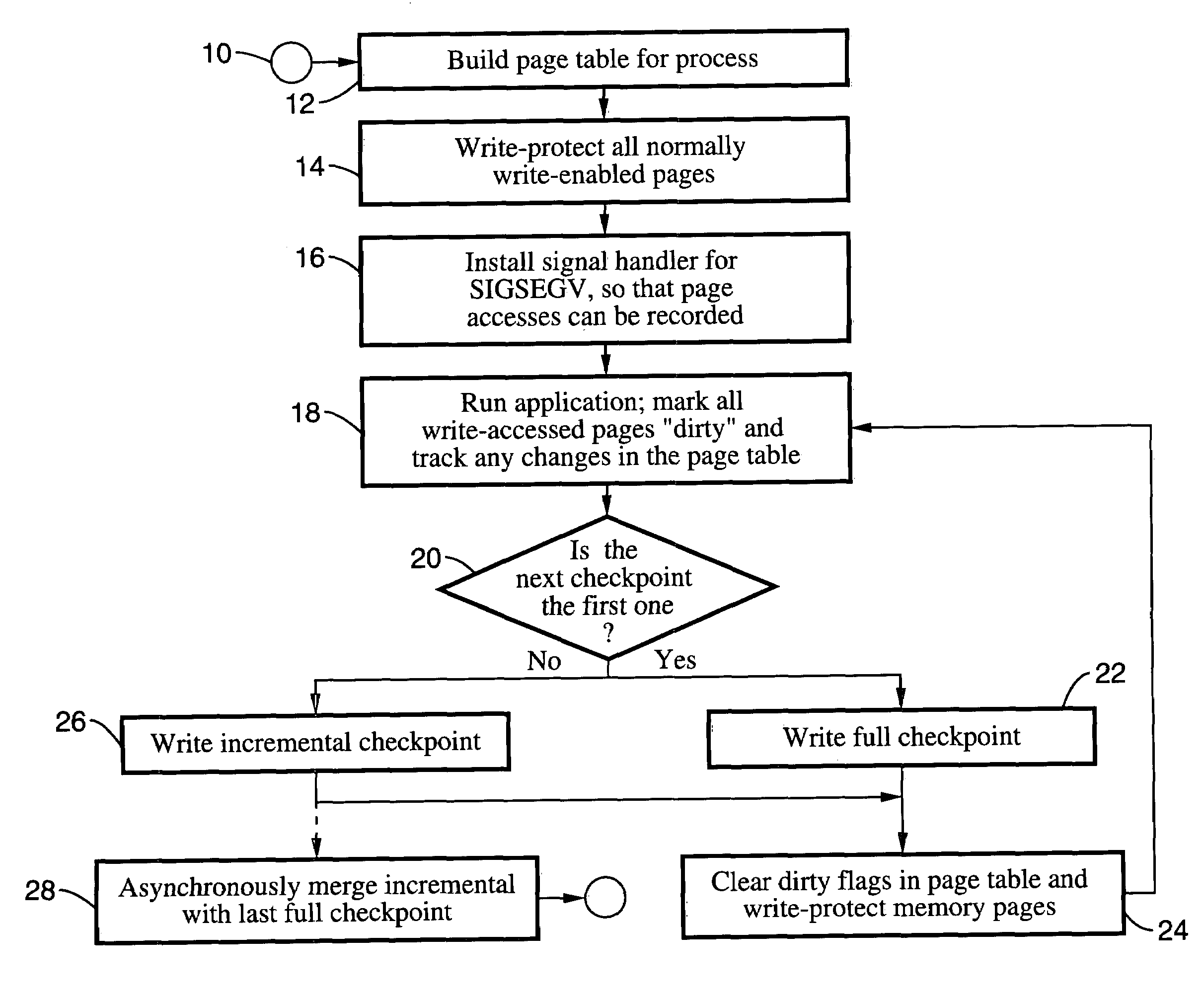
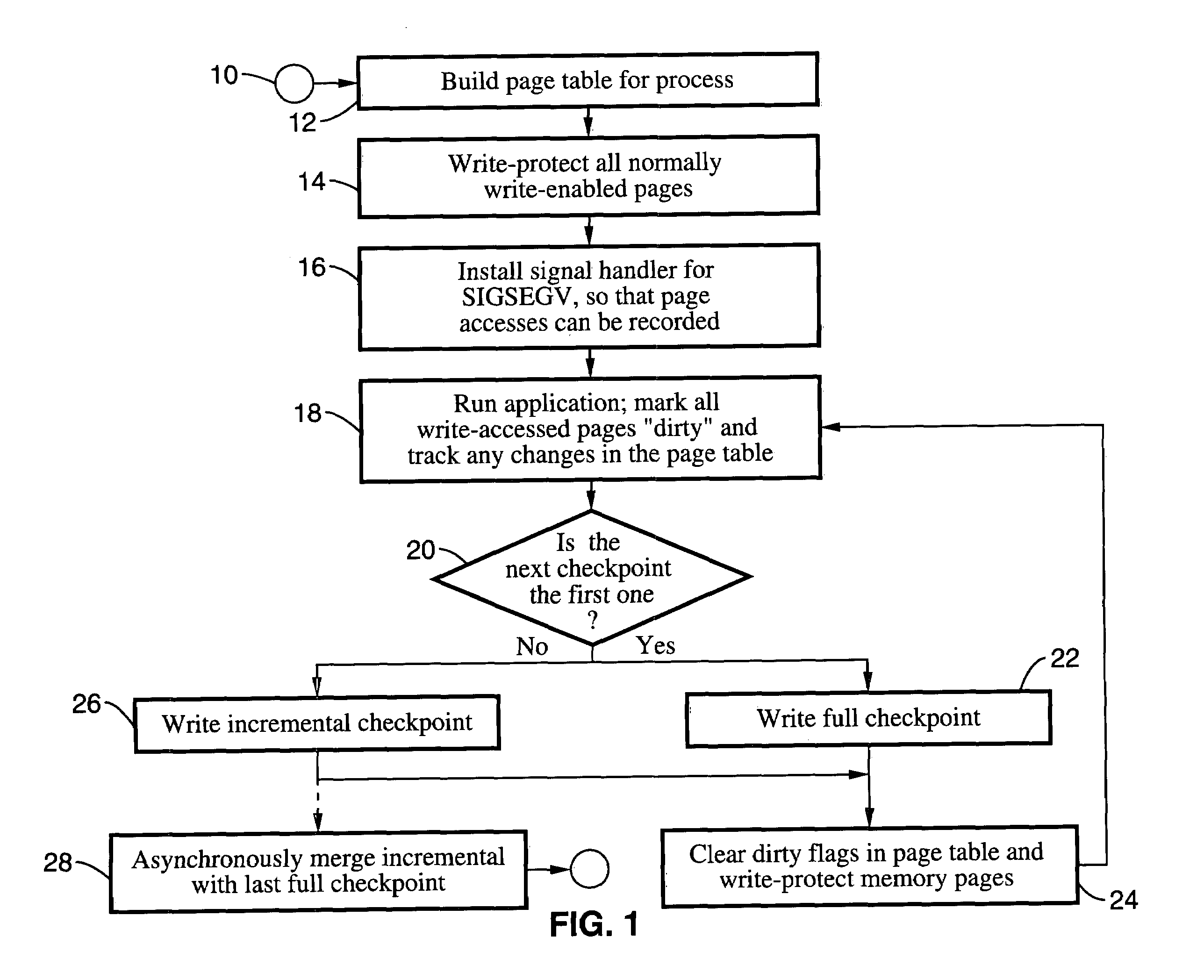
Incremental single and multiprocess checkpointing and restoration is described, which is transparent in that the application program need not be modified, re-compiled, or re-linked to gain the benefits of the invention. The processes subject to checkpointing can be either single or multi-threaded. The method includes incremental page-boundary checkpointing, as well as storage checkpointing of data files associated with applications to ensure correct restoration without the need to restore files for other application programs. Incremental and full checkpoints are asynchronously merged to ensure proper operation while reducing checkpointing delay. By way of example a user-level programming library is described for loading into the address space of the application in conjunction with a loadable kernel module (LKM) or device driver used to capture and restore process state on behalf of the application. These techniques are particularly well suited for use with high-availability (HA) protection programming.
Owner:RED HAT
Method and system for providing transparent incremental and multiprocess checkpointing to computer applications
Incremental single and multiprocess checkpointing and restoration is described, which is transparent in that the application program need not be modified, re-compiled, or re-linked to gain the benefits of the invention. The processes subject to checkpointing can be either single or multi-threaded. The method includes incremental page-boundary checkpointing, as well as storage checkpointing of data files associated with applications to ensure correct restoration without the need to restore files for other application programs. Incremental and full checkpoints are asynchronously merged to ensure proper operation while reducing checkpointing delay. By way of example a user-level programming library is described for loading into the address space of the application in conjunction with a loadable kernel module (LKM) or device driver used to capture and restore process state on behalf of the application. These techniques are particularly well suited for use with high-availability (HA) protection programming.
Owner:RED HAT
Optimized SQL code generation
ActiveUS20050027701A1Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planSQL
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:IBM CORP
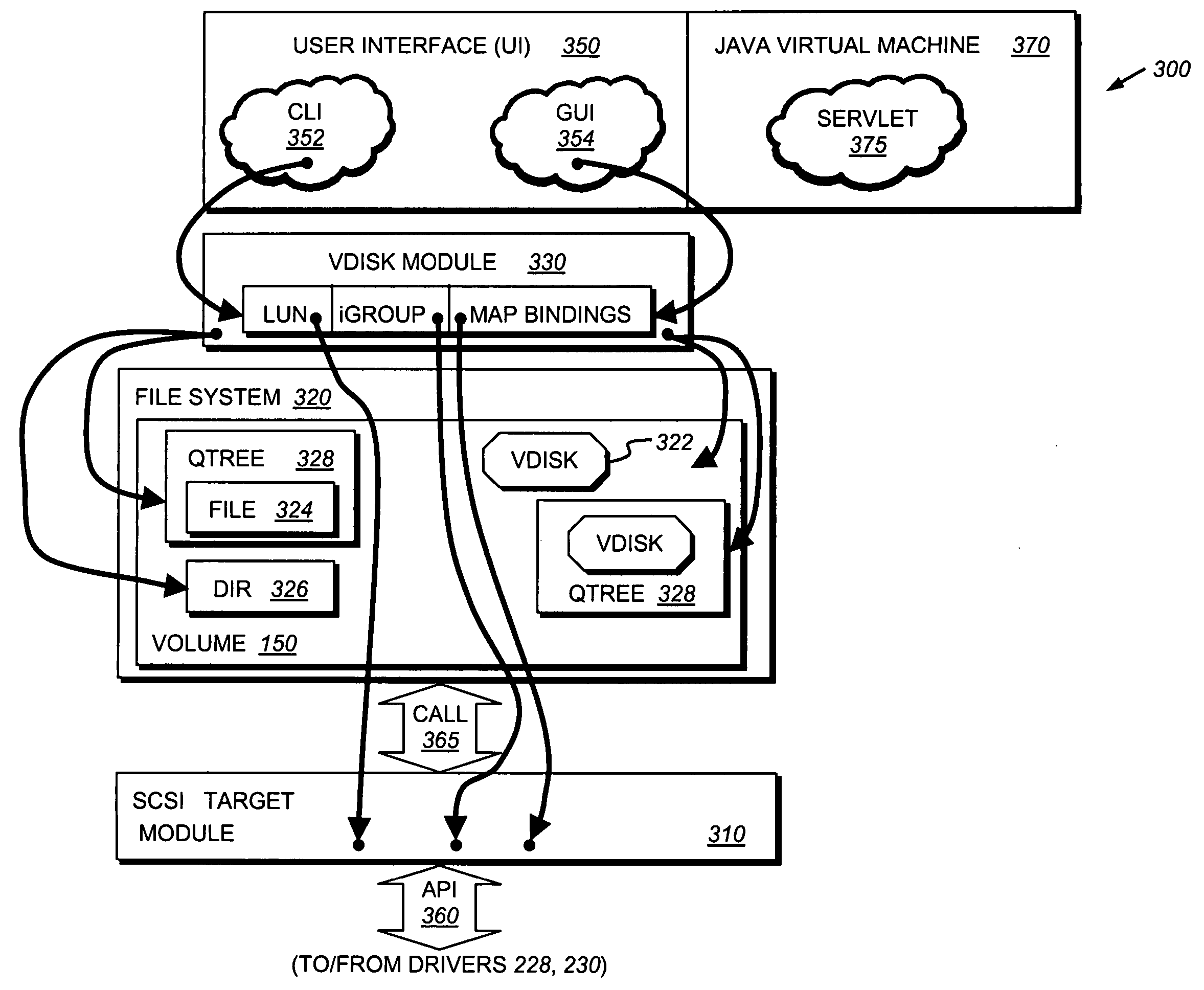
System and method for supporting block-based protocols on a virtual storage appliance executing within a physical storage appliance
InactiveUS20050228835A1Input/output to record carriersComputer security arrangementsOperational systemSecurity domain
An architecture provides the ability to create and maintain multiple instances of virtual servers, such as virtual filers (vfilers), within a server, such as a storage appliance. A vfiler is a logical partitioning of network and storage resources of the storage appliance platform to establish an instance of a multi-protocol server. Each vfiler is allocated a subset of dedicated units of storage resources, such as volumes or logical sub-volumes (qtrees), and one or more network address resources. Each vfiler is also allowed shared access to a file system resource of a storage operating system. To ensure controlled access to the allocated and shared resources, each vfiler is further assigned its own security domain for each access protocol. A vfiler boundary check is performed by the file system to verify that a current vfiler is allowed to access certain storage resources for a requested file stored on the filer platform.
Owner:NETWORK APPLIANCE INC
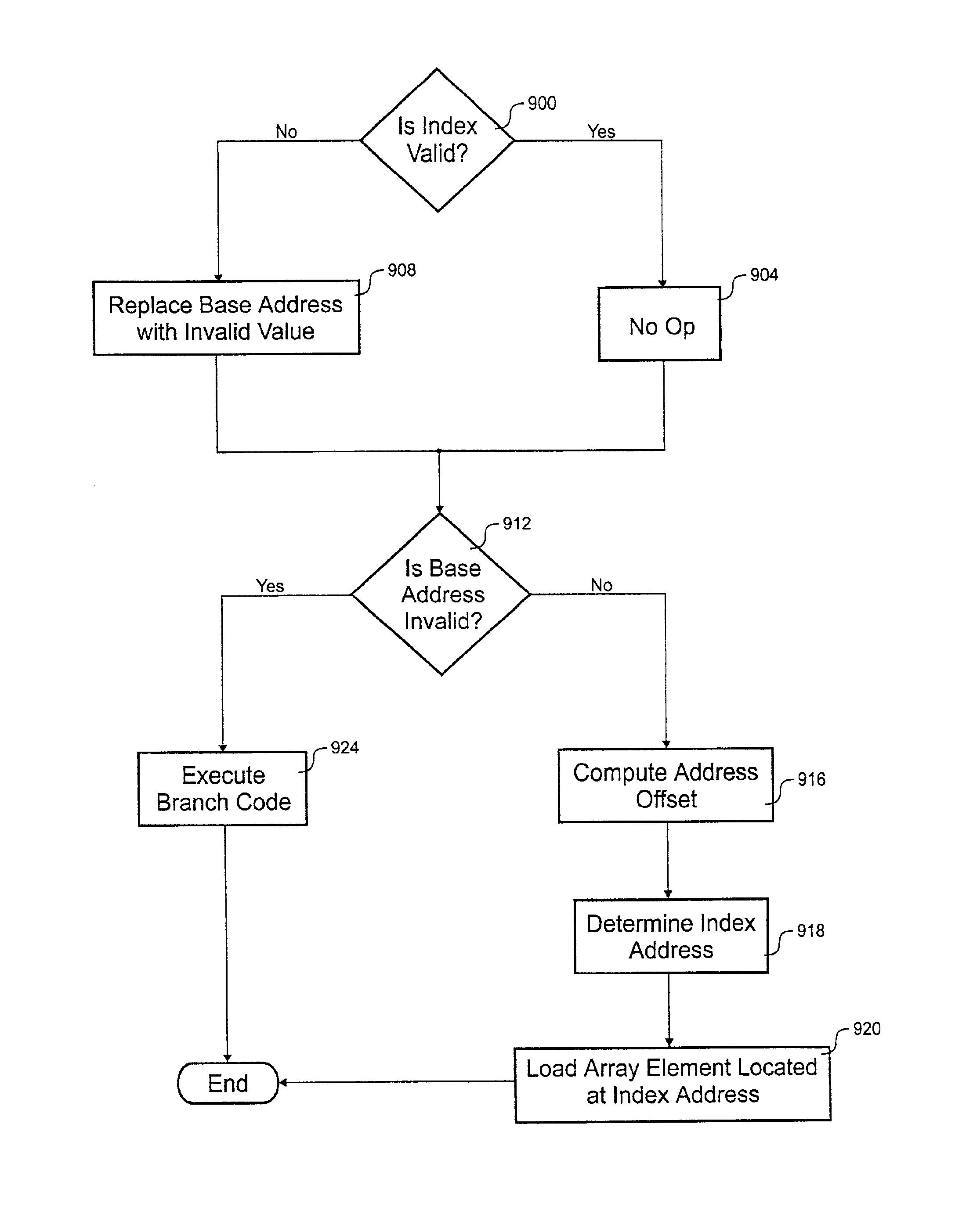
Method for optimizing array bounds checks in programs
A method and several variants for optimizing the detection of out of bounds array references in computer programs are described, while preserving the semantics of the computer program. Depending on the variant implemented, the program is divided at run-time or compile-time into two or more regions. The regions are differentiated by the number of checks that need to be performed at run-time on the array accesses within the region. In particular, some regions of the program will not need any array bounds checks performed at run-time, which will increase the speed at which the computer program executes. As well, the state of program variables at the time any out of bounds access is detected is the same as the state of the program variables would have been had the transformation not been performed. Moreover, the regions not needing any checks at run-time will be known at compile-time, enabling further compiler optimizations on the region. The variants of the method are distinguished by the number of regions created, the number of checks needed at run-time, and the size of the program that results from the optimization.
Owner:IBM CORP
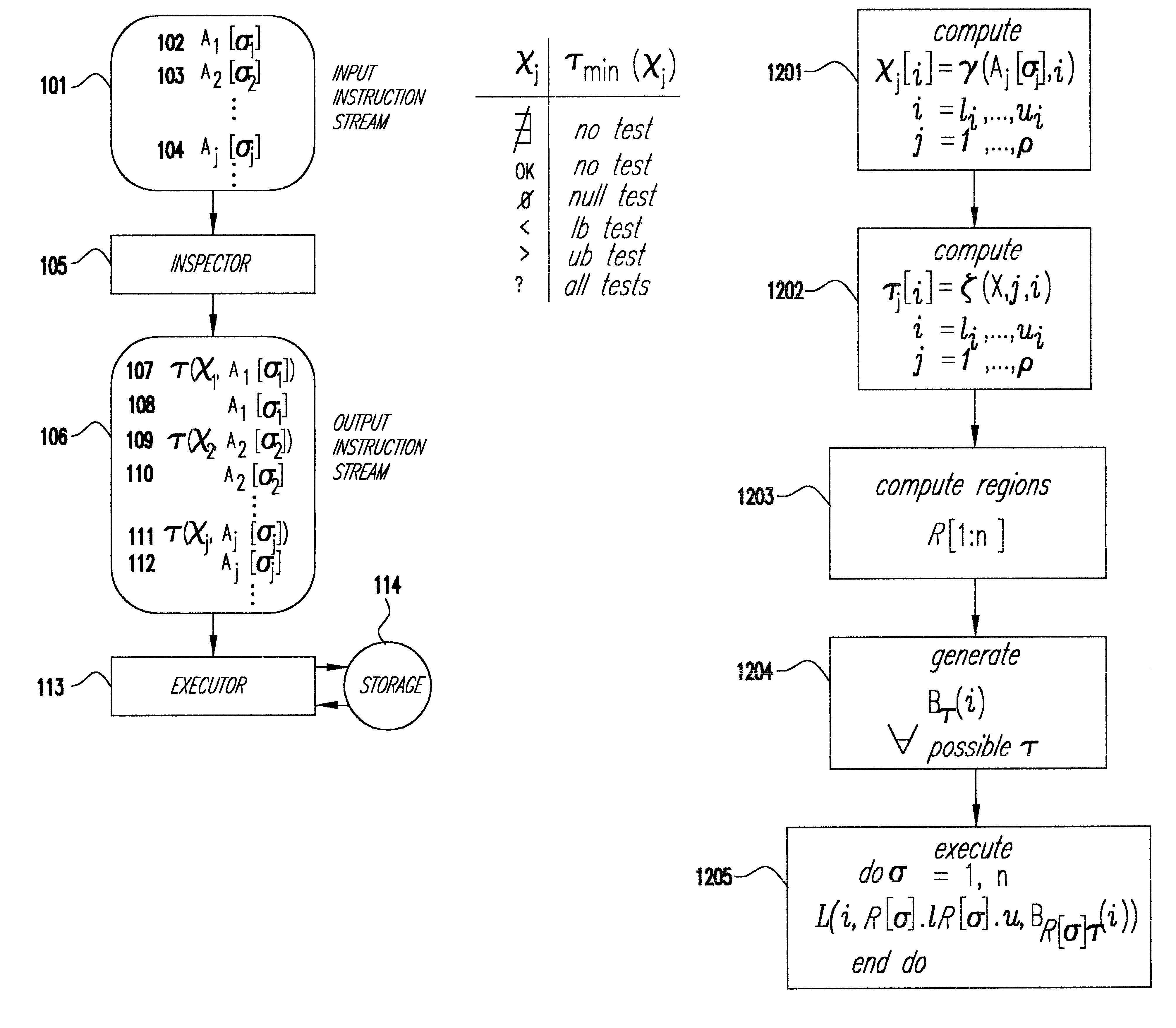
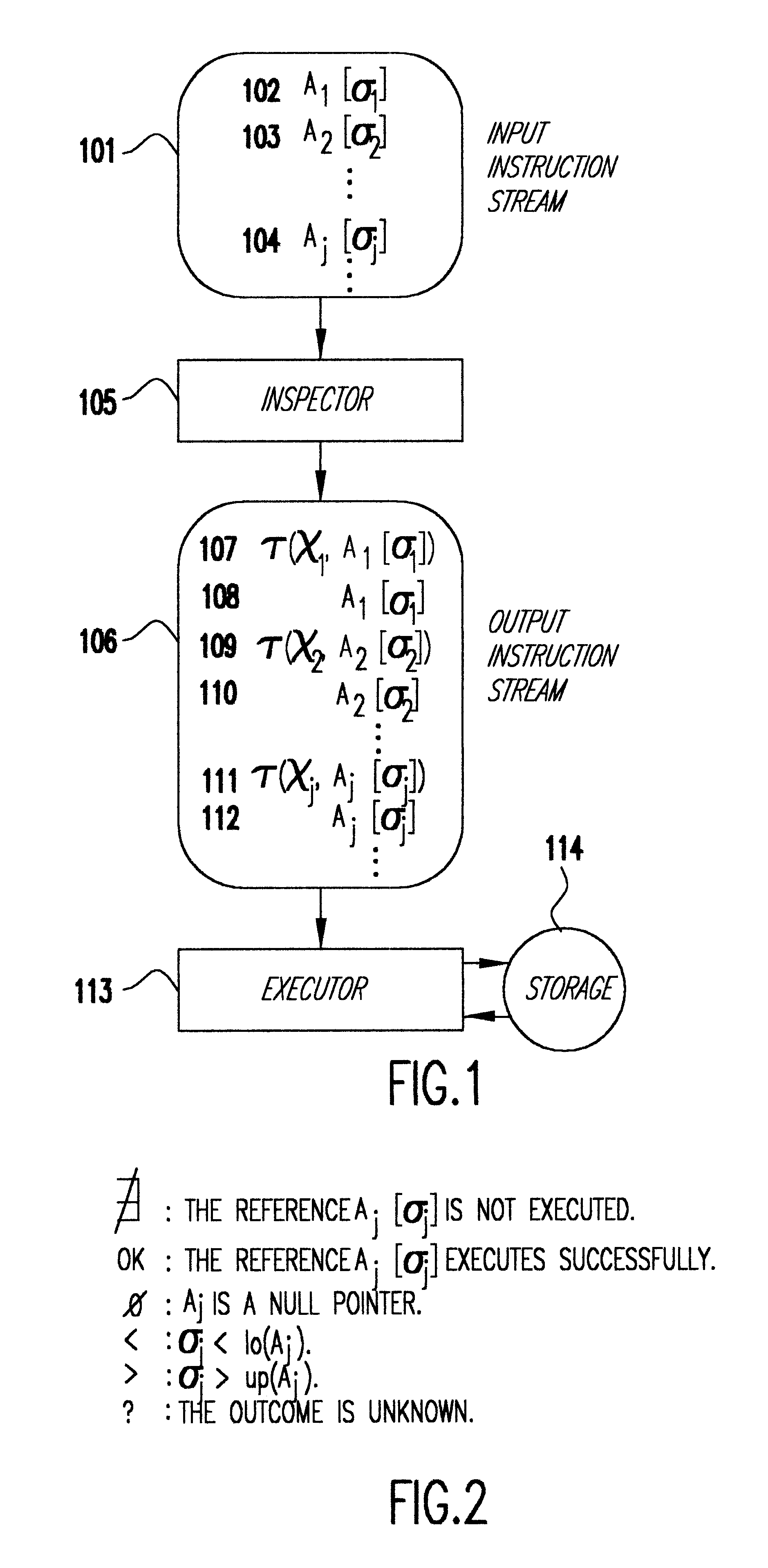
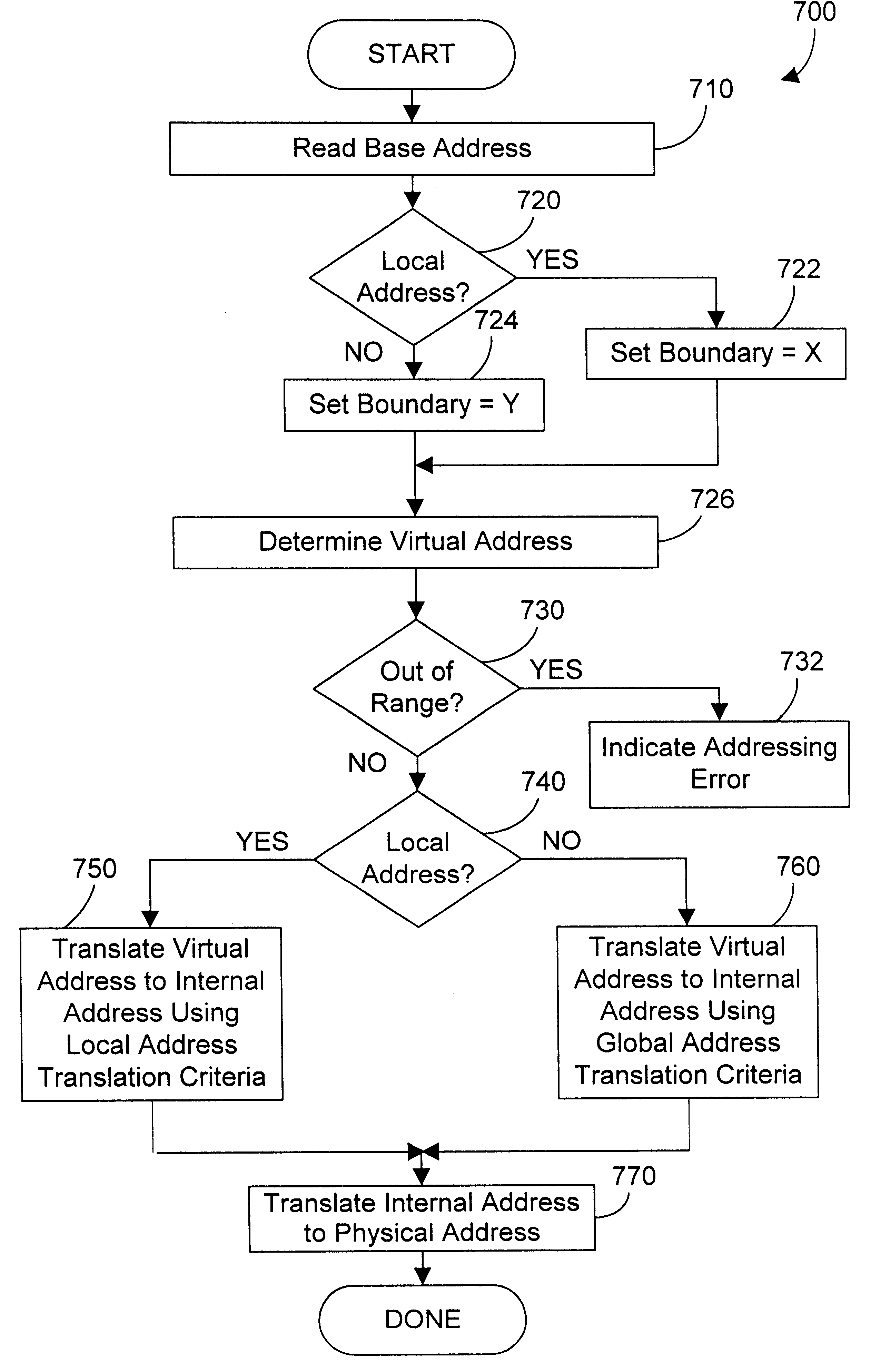
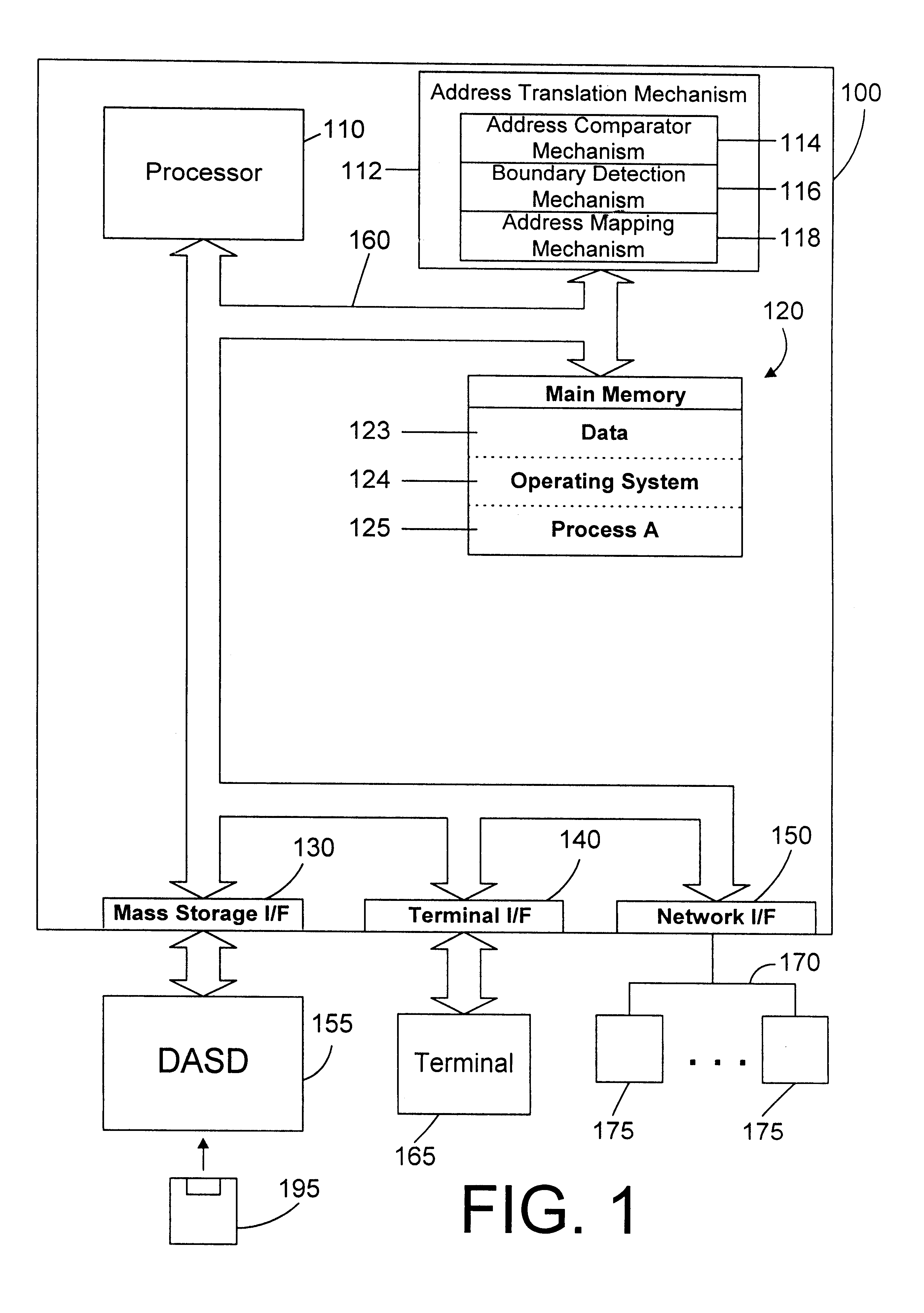
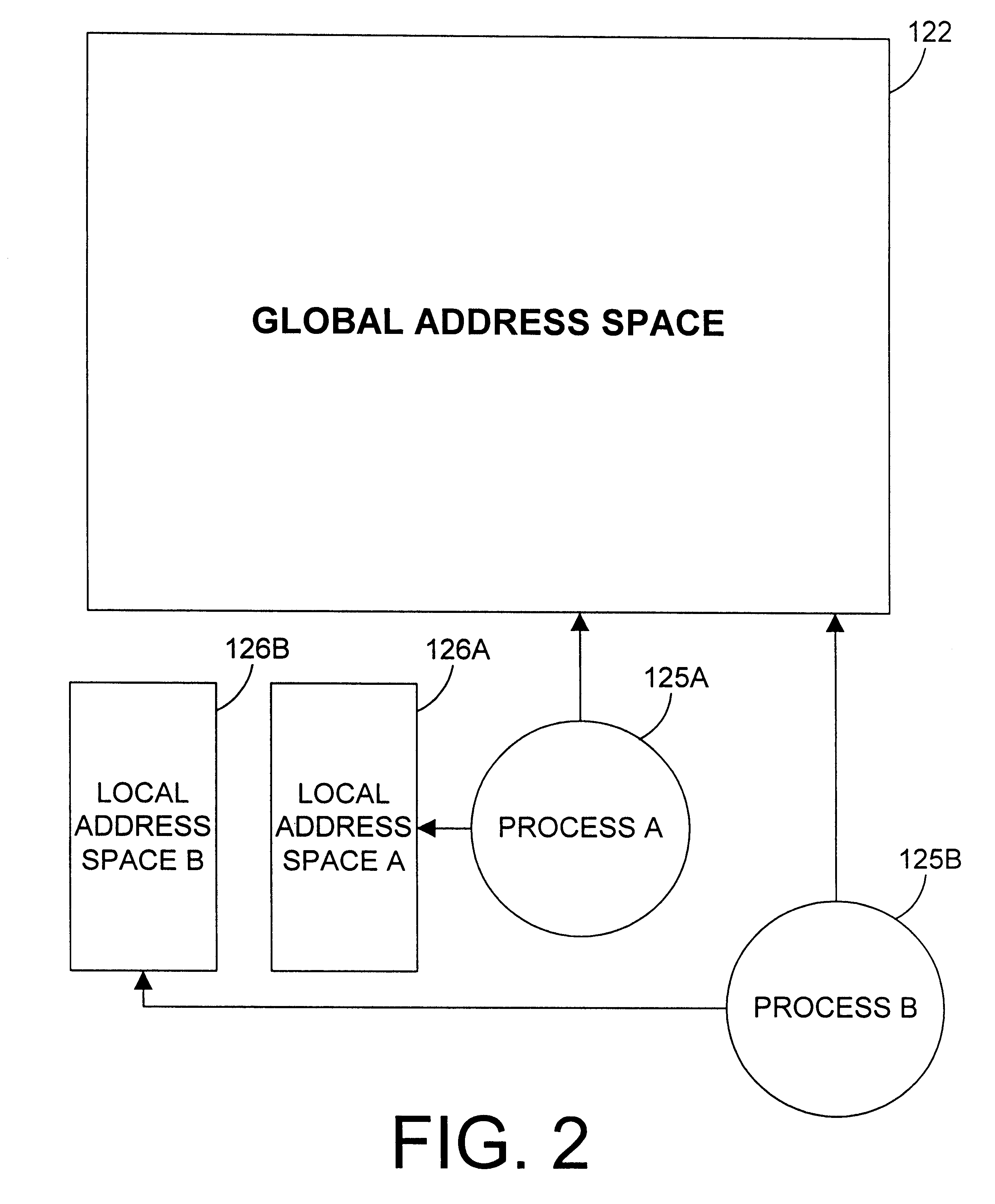
Apparatus and method for providing simultaneous local and global addressing with hardware address translation
InactiveUS6738889B2Good flexibilityMemory adressing/allocation/relocationDigital computer detailsGlobal address spaceParallel computing
An apparatus and method provide simultaneous local and global addressing capabilities. A global address space is defined that may be accessed by all processes. In addition, each process has a local address space that is local (and therefore available) only to that process. An address translation mechanism is implemented, preferably in hardware, to compare an address to defined addresses for local and global addressing and to detect when a virtual address computation result would go outside a boundary for the appropriate addressing scheme. The address translation mechanism maps a virtual address to a corresponding physical address, and uses different criteria depending on whether the address is local or global. The address translation mechanism allows an instruction to operate on both local and global addresses by determining at run-time which address space is referenced, and by performing the necessary translation and boundary checking for either global or local address space, whichever is accessed by the instruction. By providing both global and local addressing for the same instructions, the apparatus and method of the present invention provide great flexibility in addressing, allowing a computer program to benefit from the advantages of both addressing modes.
Owner:GOOGLE LLC
Processing architecture having an array bounds check capability
InactiveUS6892295B2Improve coding efficiencyOther printing matterLayered productsComputer architectureArray data structure
According to the invention, a method for processing data related to an array of elements is disclosed. In one embodiment, a method for processing data related to an array of elements is disclosed. In the process, a first value is loaded from a first location, and a second value is loaded from a second location. The first and second values are compared to each other. A predetermined value is optionally stored at a destination based upon the outcome of the comparison.
Owner:ORACLE INT CORP
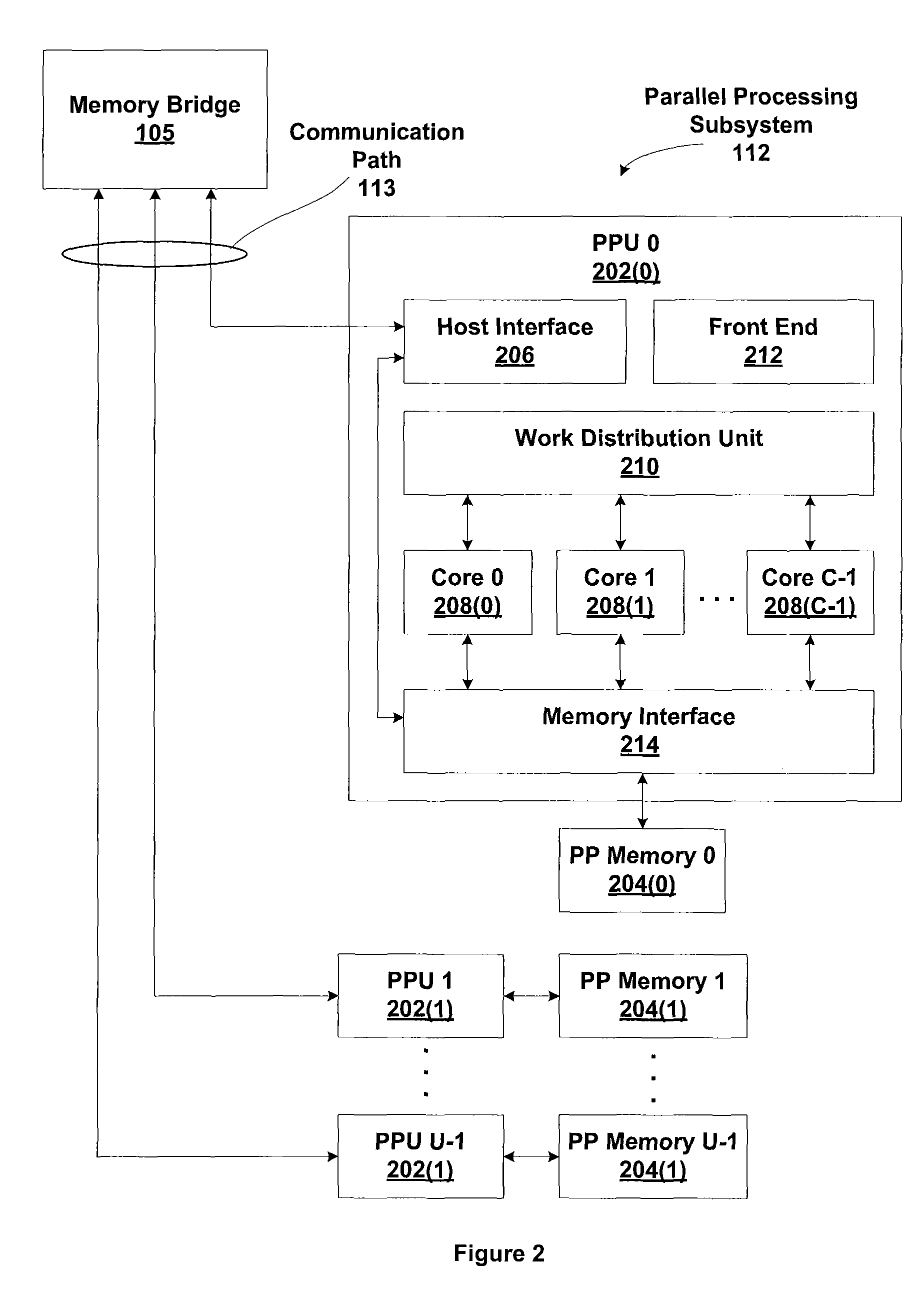
Architecture and instructions for accessing multi-dimensional formatted surface memory
Owner:NVIDIA CORP
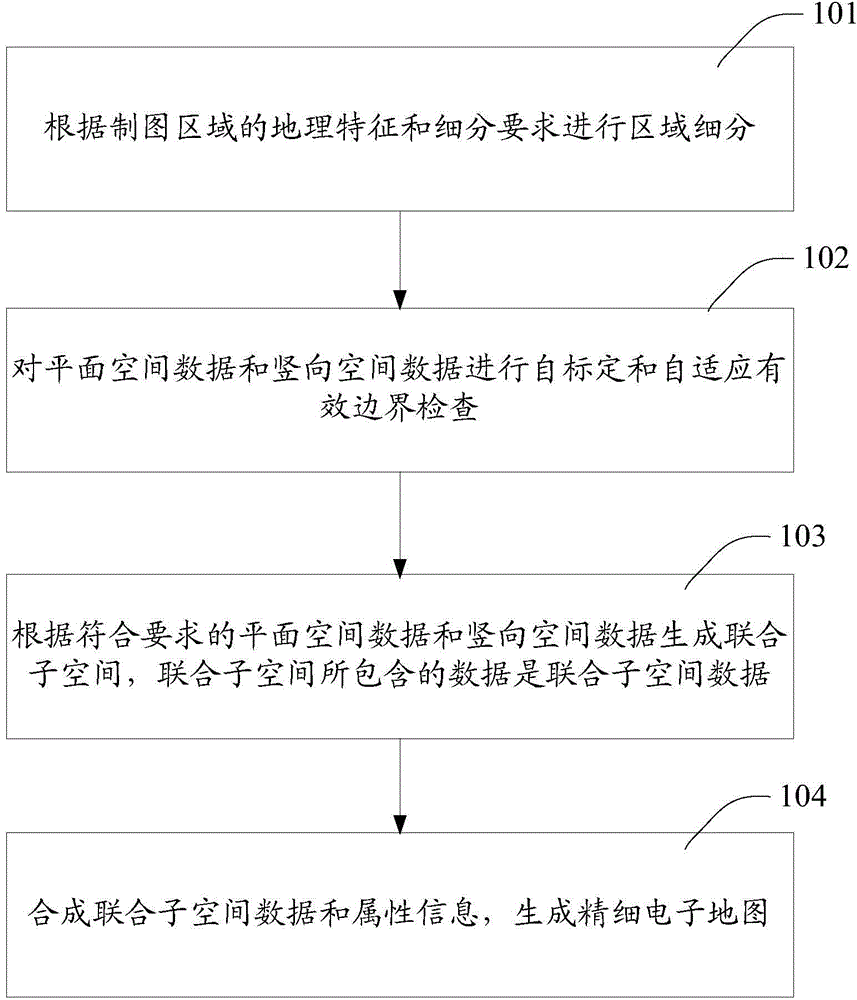
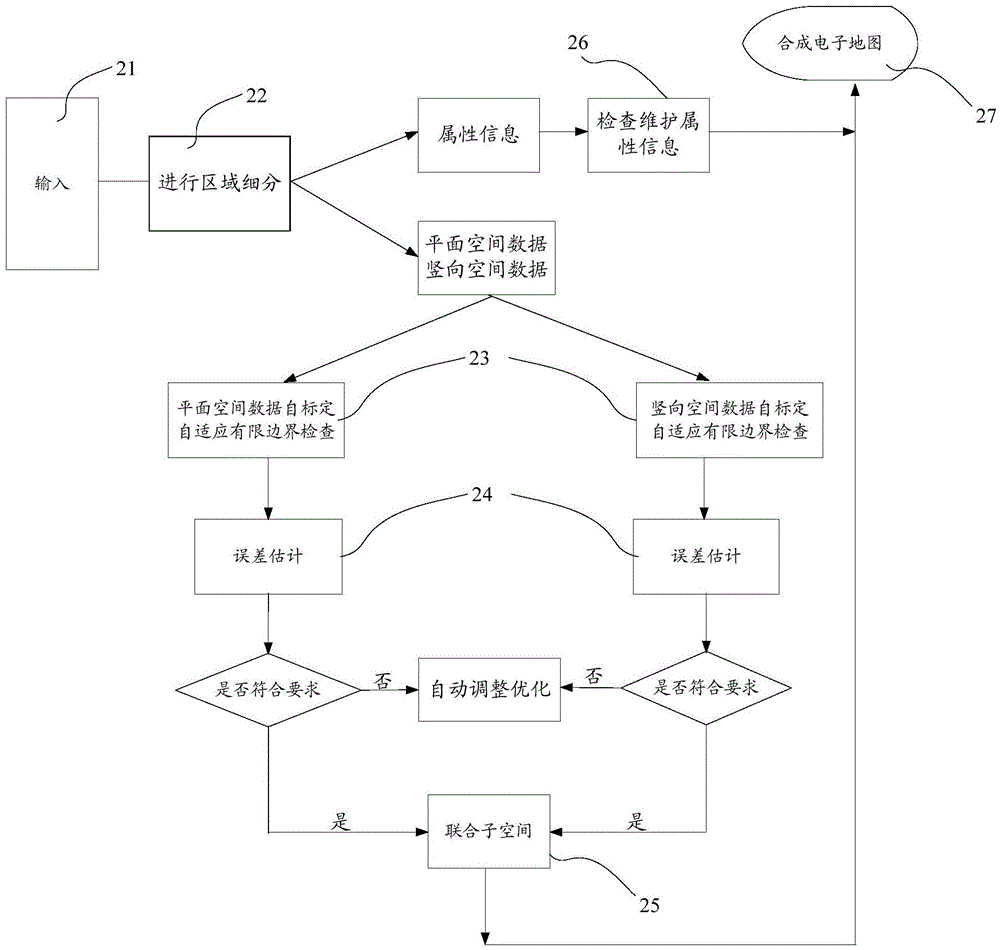
Detailed map construction method and device
ActiveCN104567893AReduce mistakesReduce error rateInstruments for road network navigationMaps/plans/chartsGeographic featureErrors and residuals
The embodiment of the invention provides a detailed map construction method and a detailed map construction device. The method comprises the following steps: performing area subdivision according to the geographic features of the map land and the subdivision requirements; performing self-calibration and self-adaption effective boundary checking to plane spatial data and vertical spatial data; generating united subspaces according to the plane spatial data and the vertical spatial data meeting the requirements, wherein data contained in the united subspaces are united subspace data; combining the united subspace data and attribute information to generate the detailed electronic map. The area subdivision is performed to reduce the dependency of the local data to the whole data; the self-calibration and self-adaption effective boundary checking are performed, the united subspaces are generated according to the plane spatial data and the vertical spatial data meeting the requirements, and in the process the self-adaption vector compositing method is fully utilized, so that the error and the error rate of the geometric topology in the manufacturing process can be reduced, and the precision of the electronic map can be improved.
Owner:NAVINFO
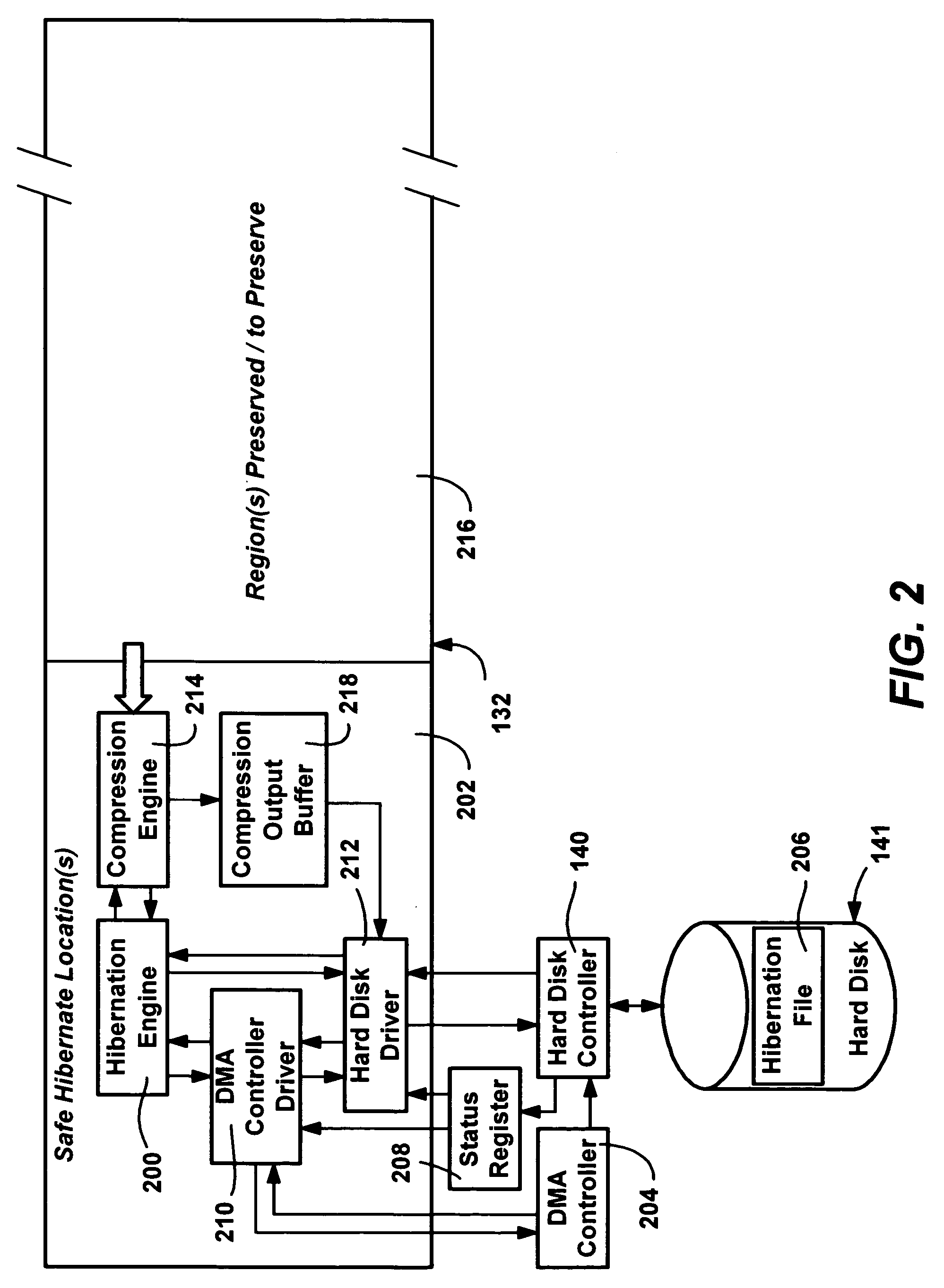
Hibernation of computer systems
InactiveUS20050097239A1Small sizeData transfer speed is fastInput/output to record carriersVolume/mass flow measurementComputer hardwareDirect memory access
An improved hibernation method and system, including the use of a modified DMA (Direct Memory Access) mode of transferring data to and from the disk. The use of DMA increases data transfer speed, while freeing the system processor to perform other tasks, including compressing / decompressing the data transferred to and from the disk. An improved decoder is also provided that reduces the number of bounds checks needed on average for typical compressed data by first guaranteeing that there is sufficient room to decode literals and small substrings, whereby bounds checking is not needed. A combination hibernation mode and a suspend mode is also provided that essentially maintains power to the RAM while transparently backing the RAM with the hibernation file, such that if power to the RAM is interrupted, the RAM contents are automatically restored from the hibernation file when power is restored.
Owner:MICROSOFT TECH LICENSING LLC
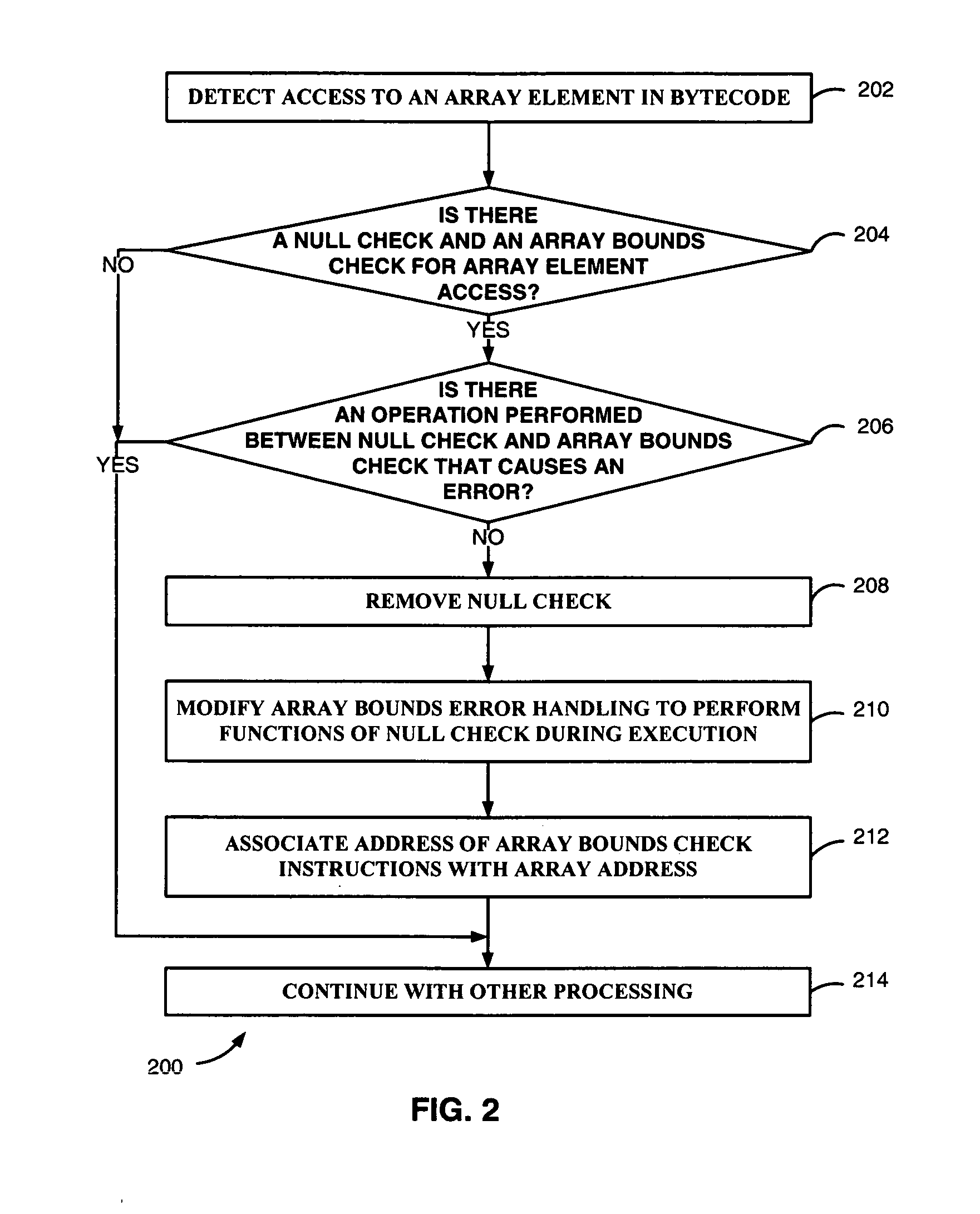
Modification of array access checking in AIX
InactiveUS20050257096A1Software engineeringError detection/correctionError processingParallel computing
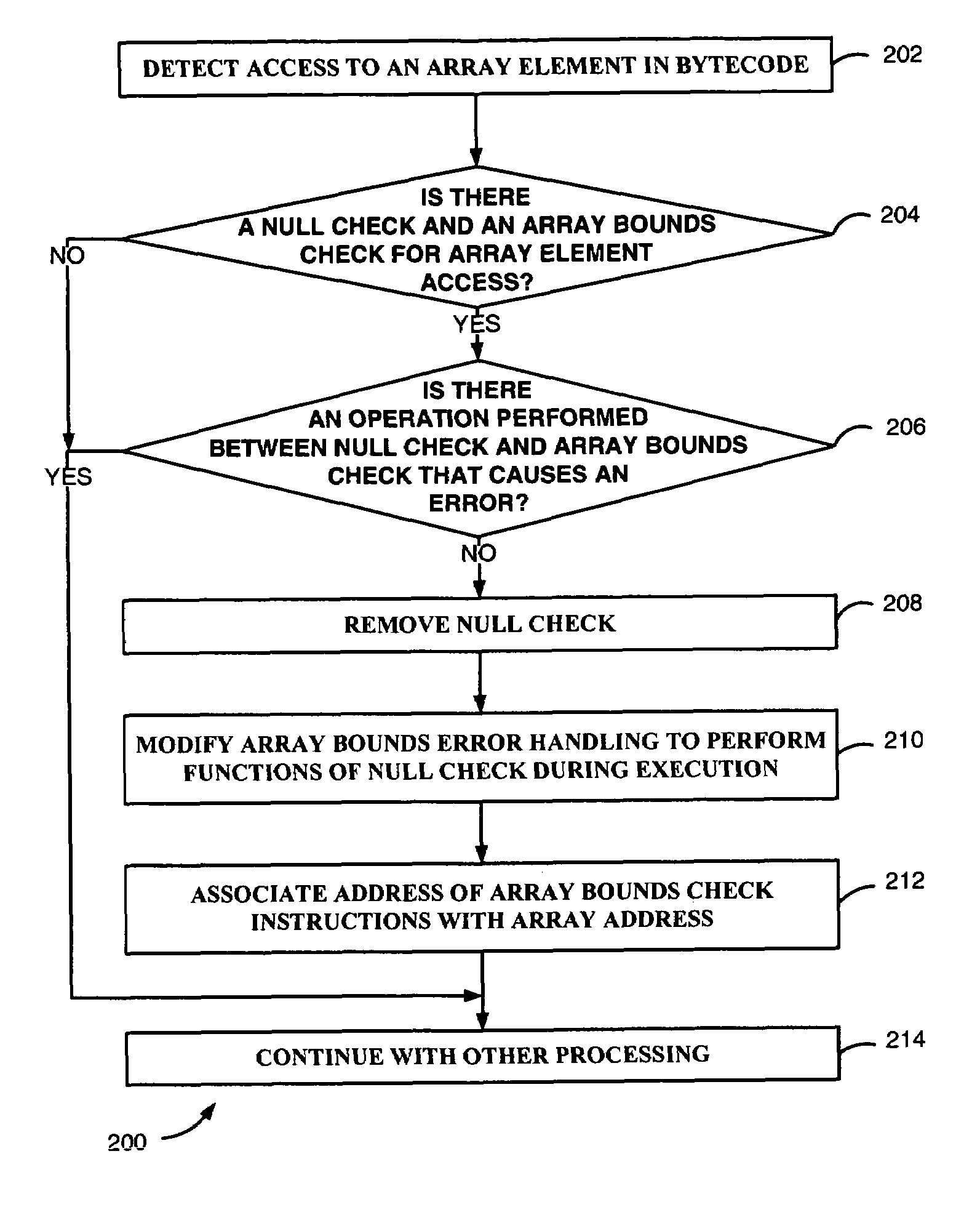
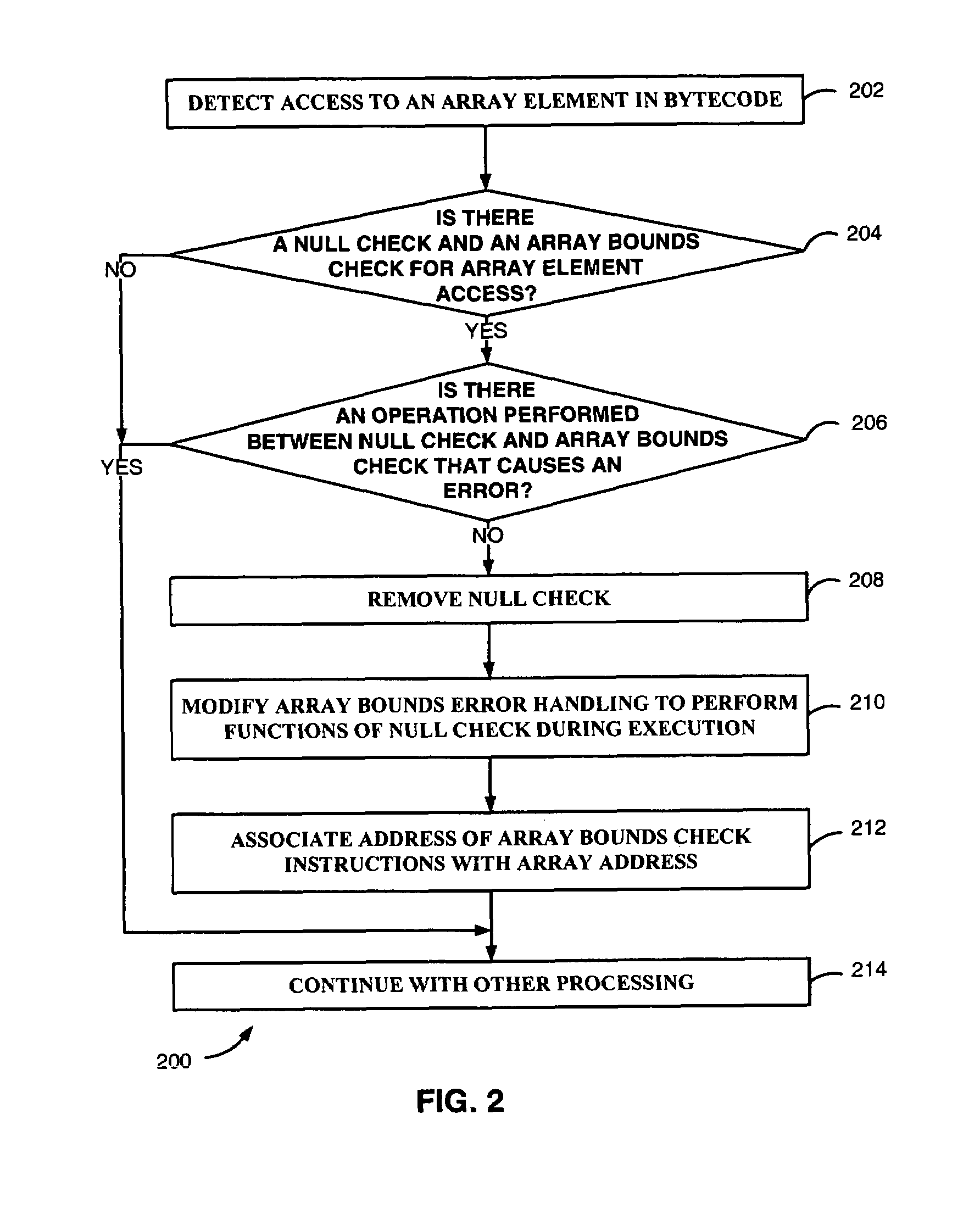
An error handling operation for checking of an array access in program code is modified during compilation thereof. A sequentially arranged null checking operation and array bounds checking operation for the array access are located. The array bounds checking operation has a corresponding error handling operation operable for setting an array bounds error. The located sequentially arranged null checking operation is removed. The corresponding error handling operation for the located sequentially arranged array bounds checking operation is modified to perform the removed null checking operation during execution of the program code.
Owner:IBM CORP
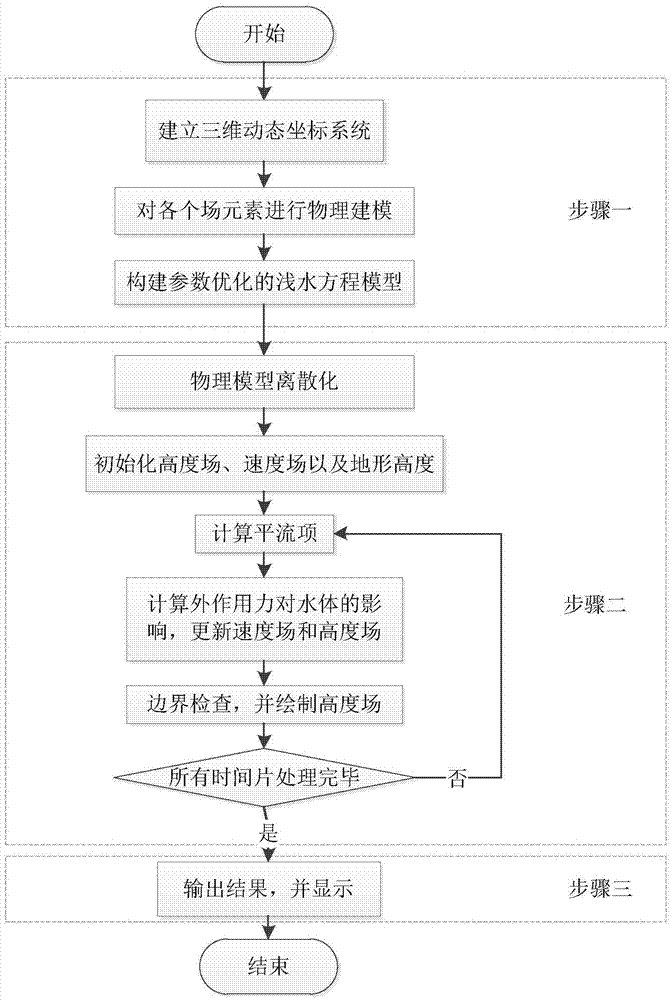
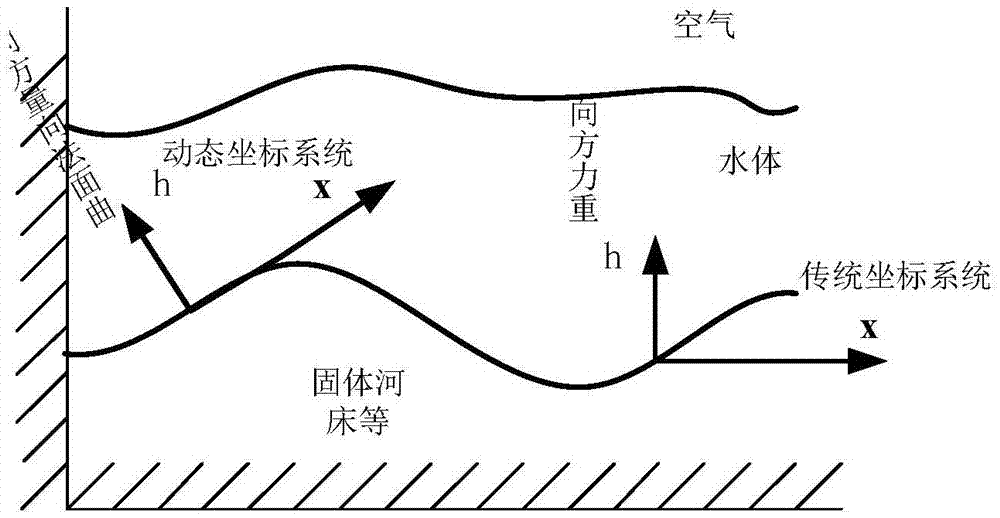
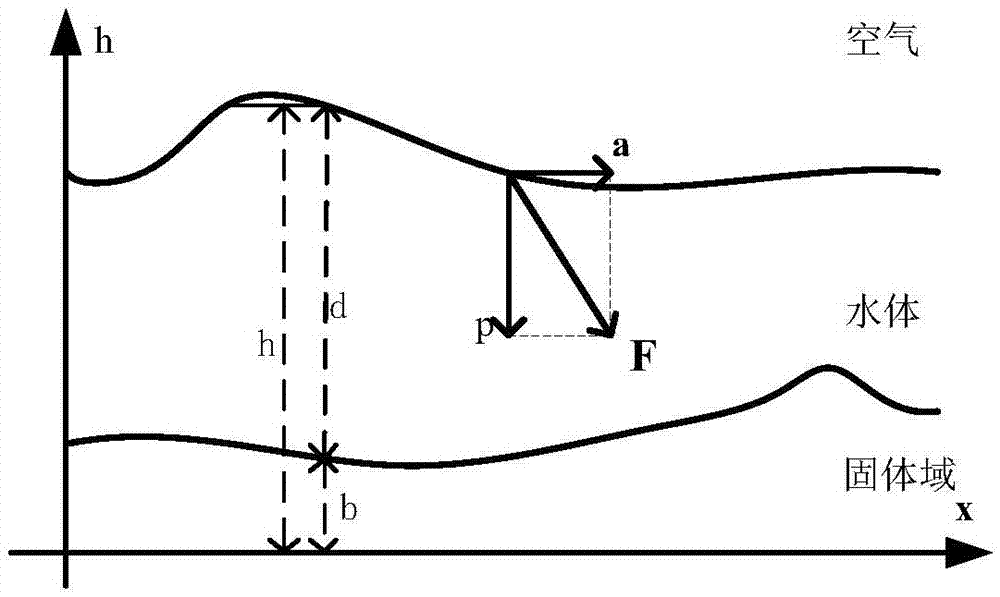
Water body modeling method for shallow water equation model with optimized parameters
ActiveCN106934192AImprove solution rateImprove stabilityInformaticsSpecial data processing applicationsReal-time simulationMethod of characteristics
The invention discloses a water body modeling method for a shallow water equation model with optimized parameters. According to the method, first, a three-dimensional dynamic coordinate system is constructed, and the shallow water equation model with optimized parameters is derived; when the model is solved, a reverse path tracking method and a method of characteristics are combined to solve an advective item in an equation, a vector projection method and a Fourier transformation method are combined to solve the effect of external acting force on a water body, and therefore a velocity field and a height field are updated; next, boundary check is performed, a boundary truncation method is adopted to process mesh points beyond a boundary; and last, the height field is drawn, and a next time period is processed cyclically. Compared with a traditional shallow water equation, when the contact surface between the water body and a solid is excessively steep, a water body model can be constructed more vividly and accurately, and the velocity of average 24.9 frame / second can be reached in the water body modeling simulation process; compared with a traditional method, the velocity is increased by 29.016%, and real-time simulation can be realized basically.
Owner:BEIHANG UNIV
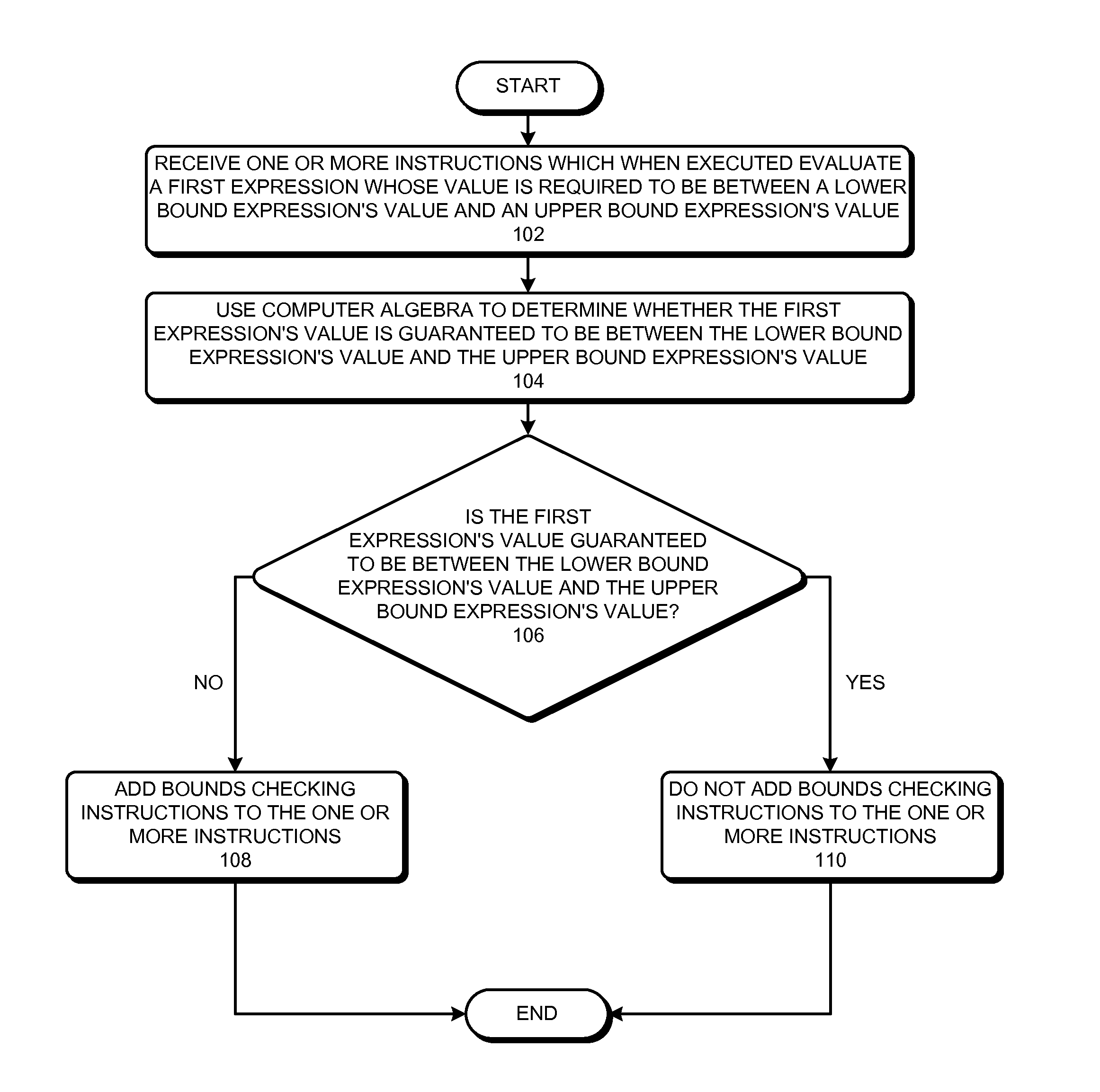
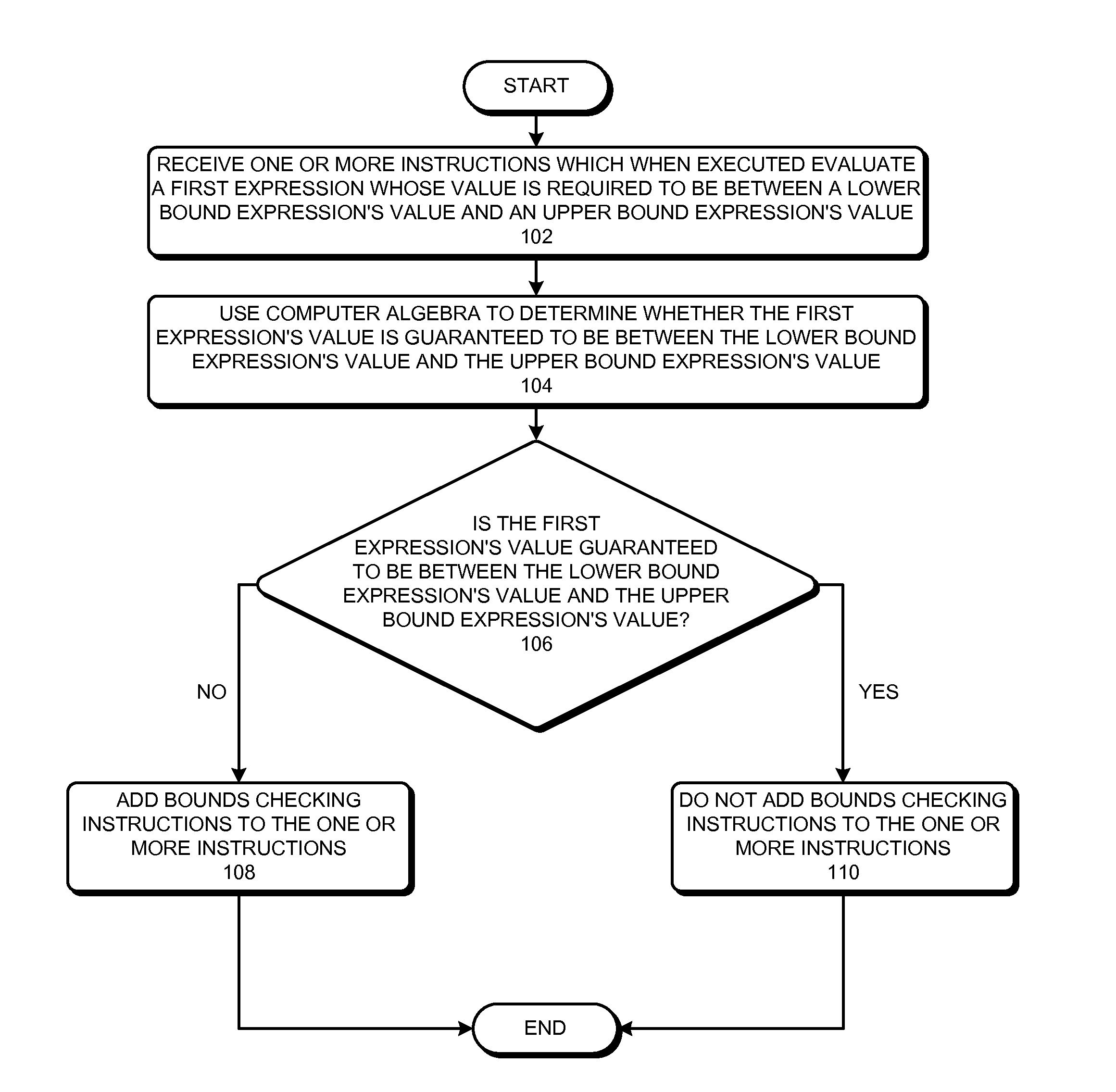
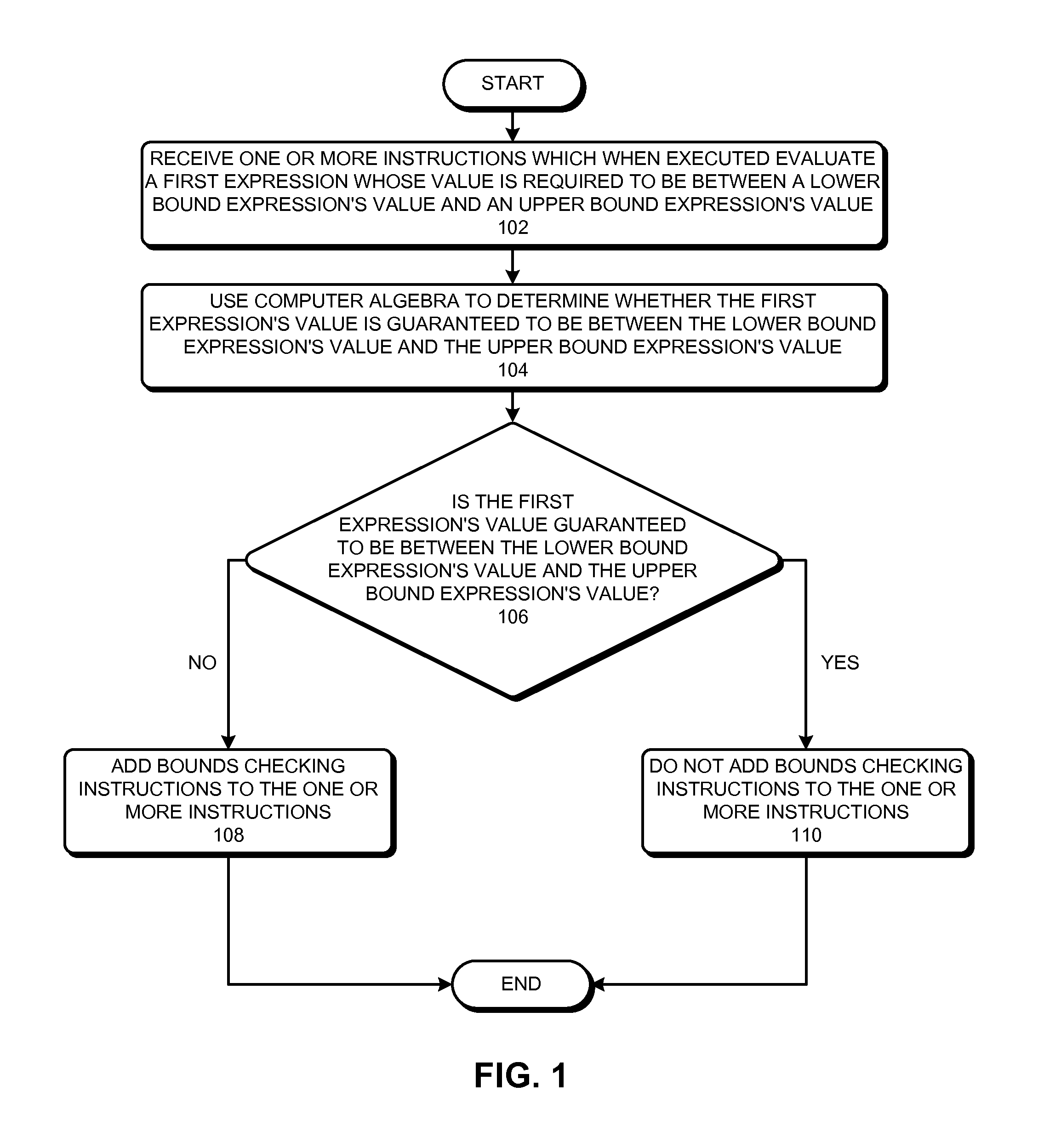
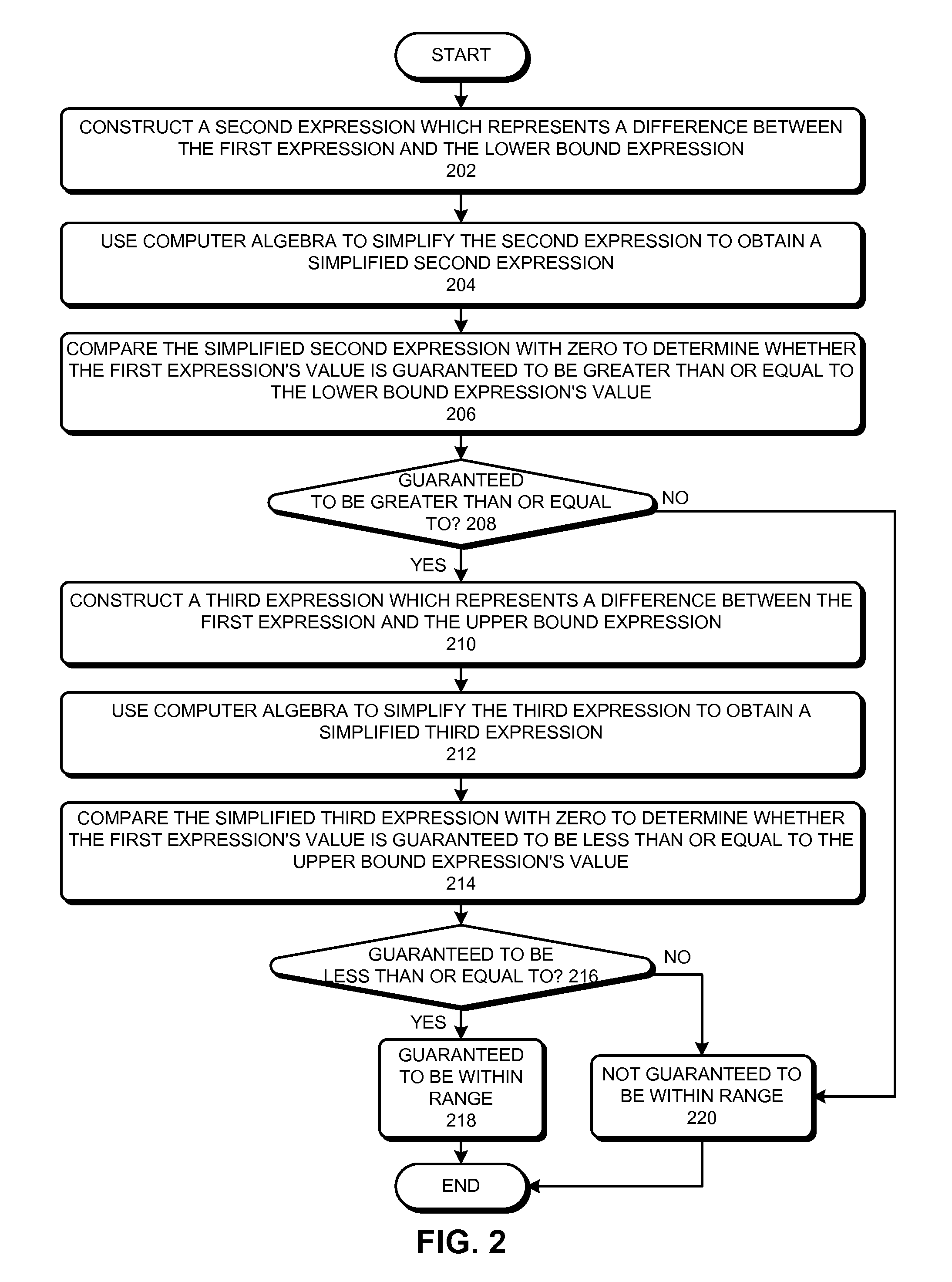
Optimizing bounds checking using computer algebra
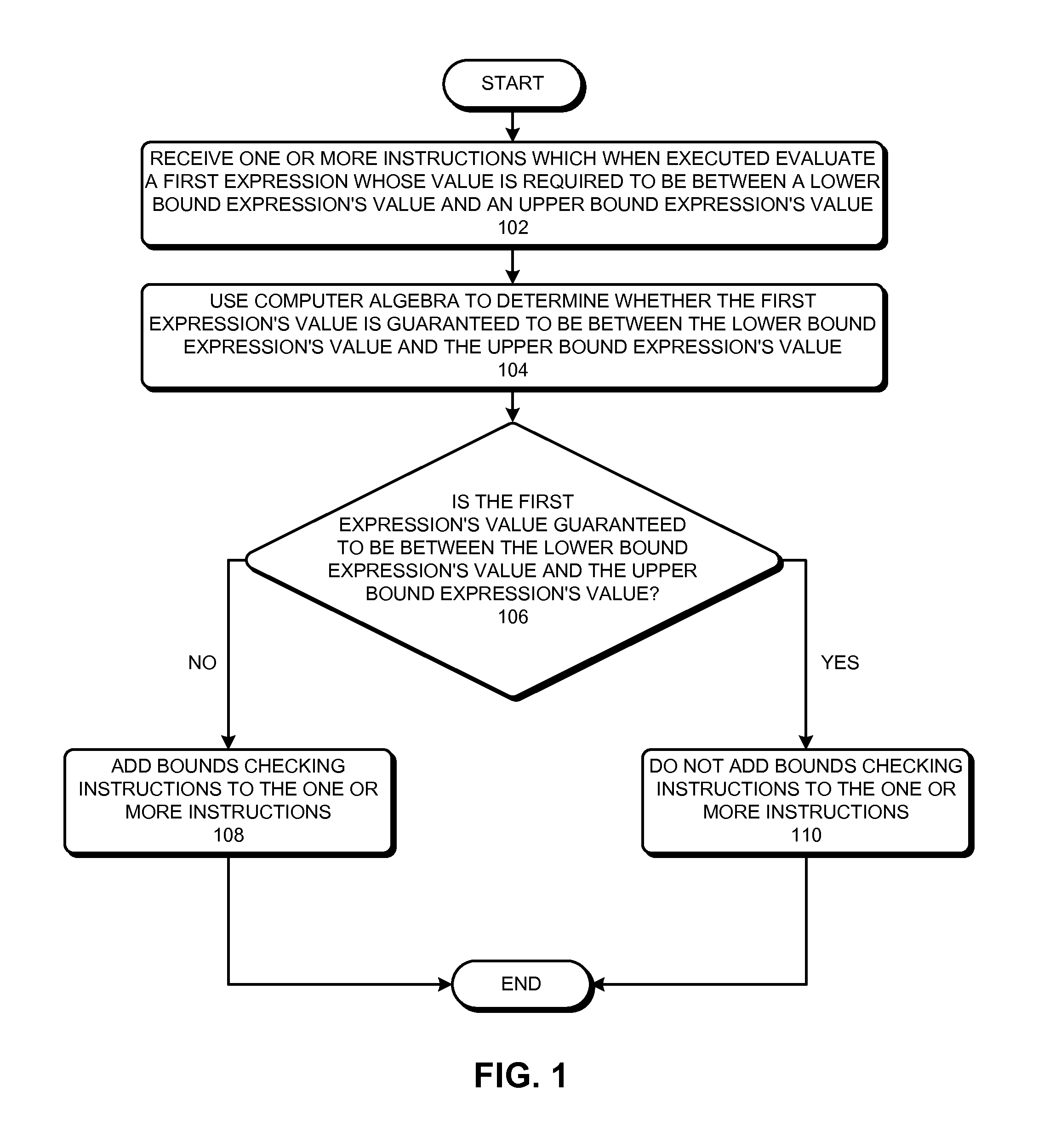
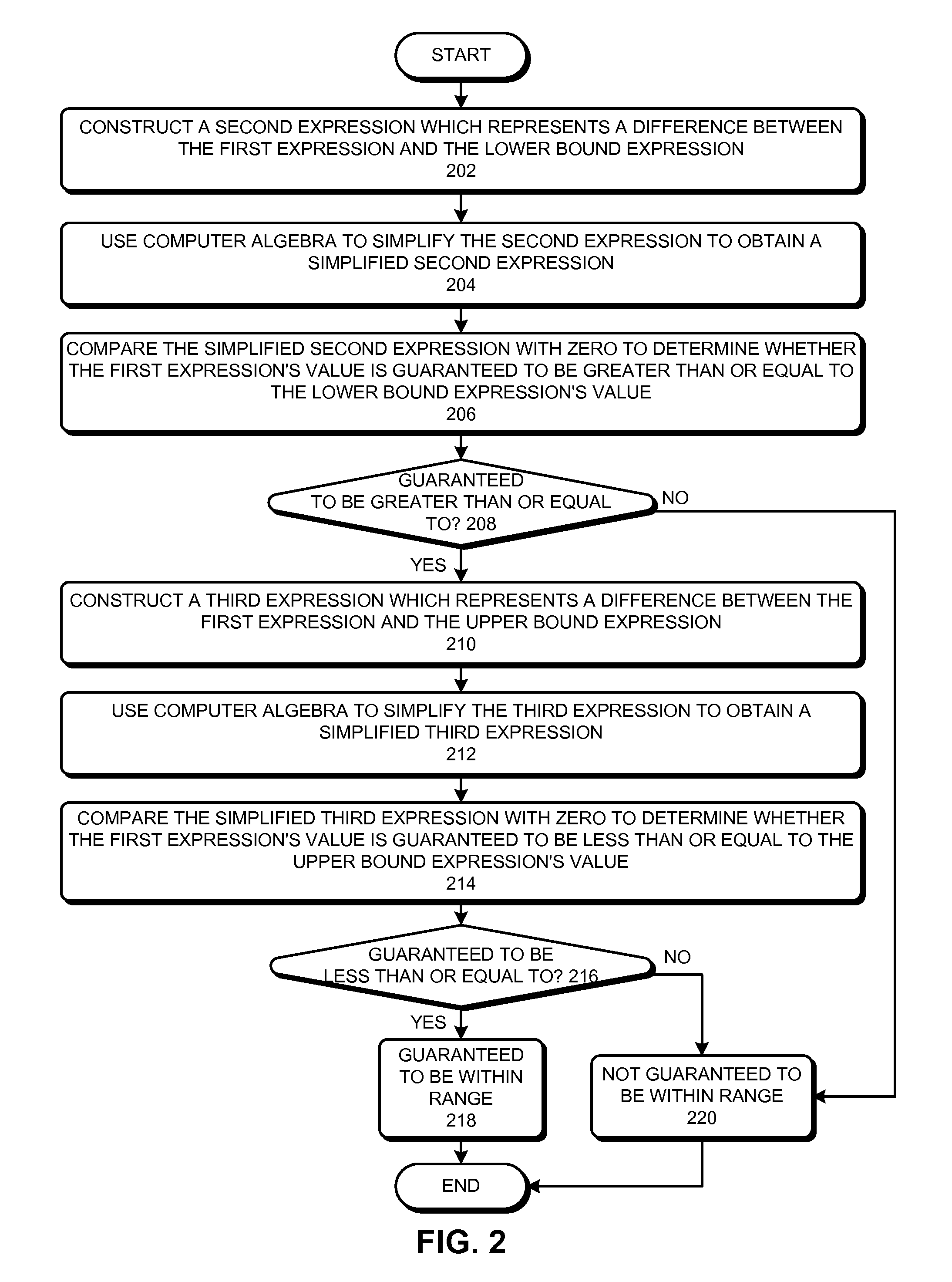
ActiveUS20110185341A1Reduce overheadError avoidanceSpecific program execution arrangementsLower limitAlgebraic optimization
Some embodiments of the present invention provide techniques and systems for optimizing bounds-checking During operation, the system can receive one or more instructions which when executed evaluate a first expression whose value is required to be between a lower bound expression's value and an upper bound expression's value, such that at least one of the following three values is not determinable before execution: the first expression's value, the lower bound expression's value, and the upper bound expression's value. Next, the system can use computer algebra to determine whether the first expression's value is guaranteed to be between the lower bound expression's value and the upper bound expression's value. If the system determines that the first expression's value is not guaranteed to be between the lower bound expression's value and the upper bound expression's value, the system can add bounds-checking instructions to the one or more instructions.
Owner:SYNOPSYS INC
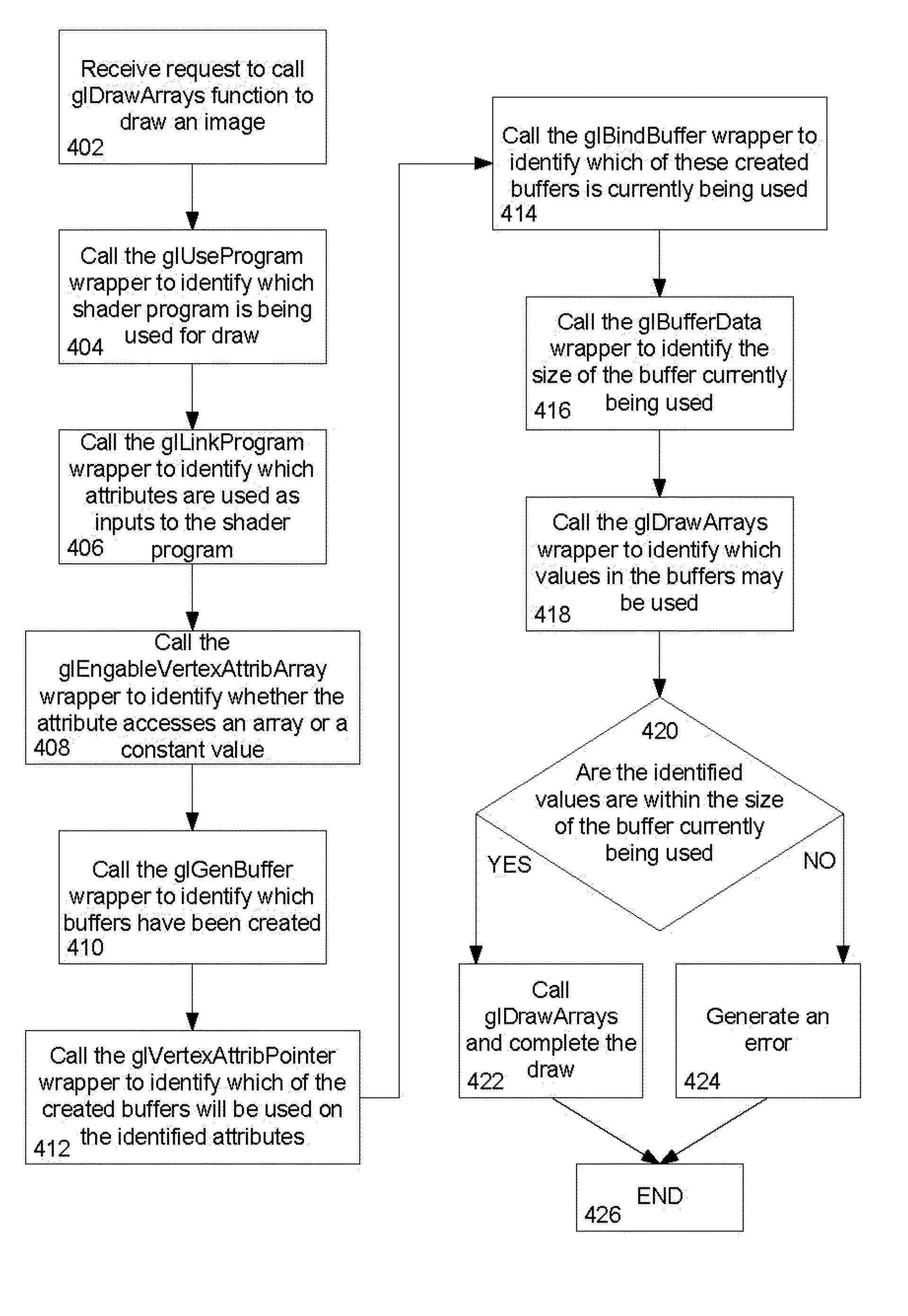
Vertex array access bounds checking
Aspects of the invention relate generally to validating array bounds in an API emulator. More specifically, an OpenGL (or OpenGL ES) emulator may examine each array accessed by a 3D graphic program. If the program requests information outside of an array, the emulator may return an error when the graphic is drawn. However, when the user (here, a programmer) queries the value of the array, the correct value (or the value provided by the programmer) may be returned. In another example, the emulator may examine index buffers which contain the indices of the elements on the other arrays to access. If the program requests a value which is not within the range, the emulator may return an error when the graphic is drawn. Again, when the programmer queries the value of the array, the correct value (or the value provided by the programmer) may be returned.
Owner:GOOGLE LLC
Conversion method of virtual and real addresses of many-core processor
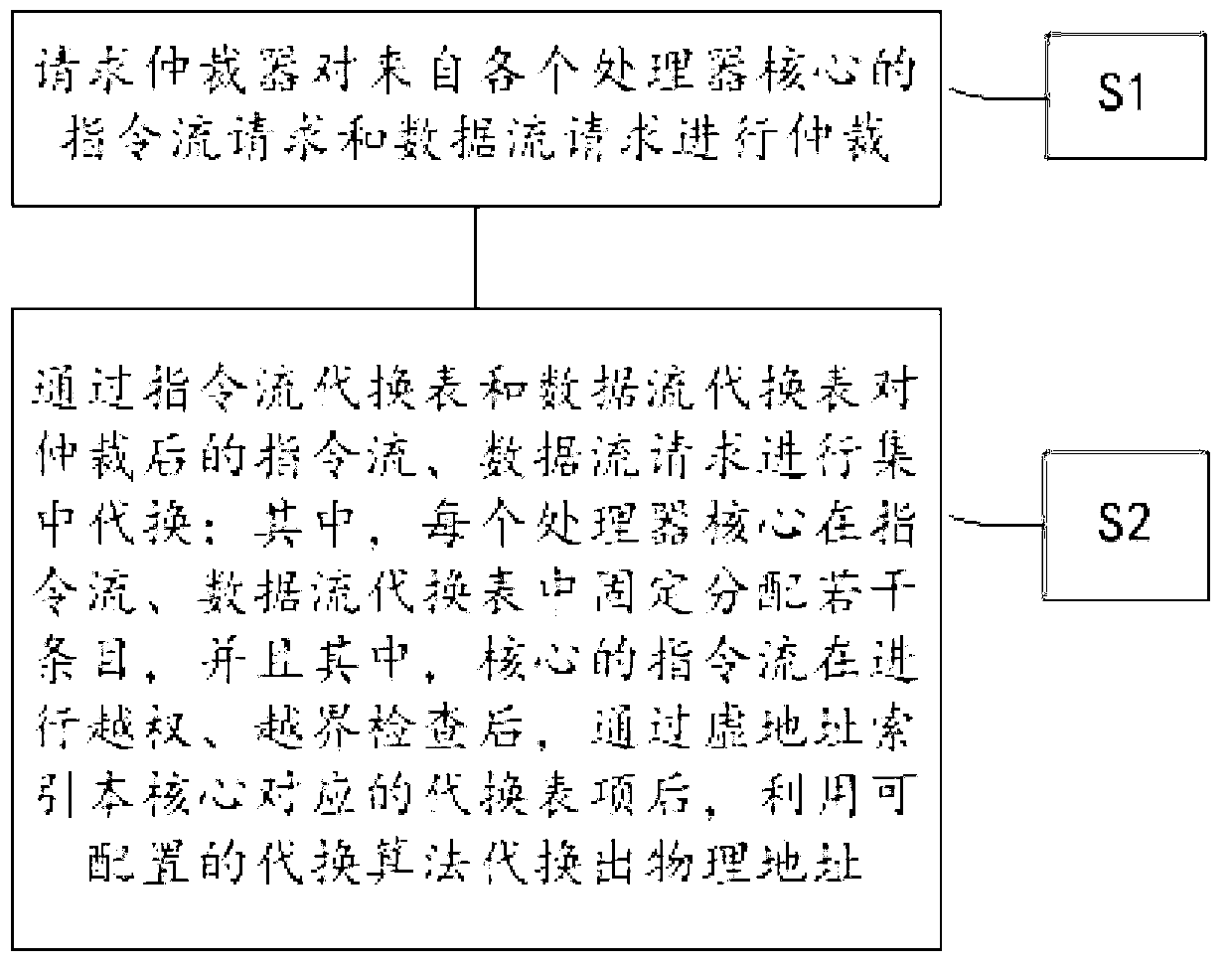
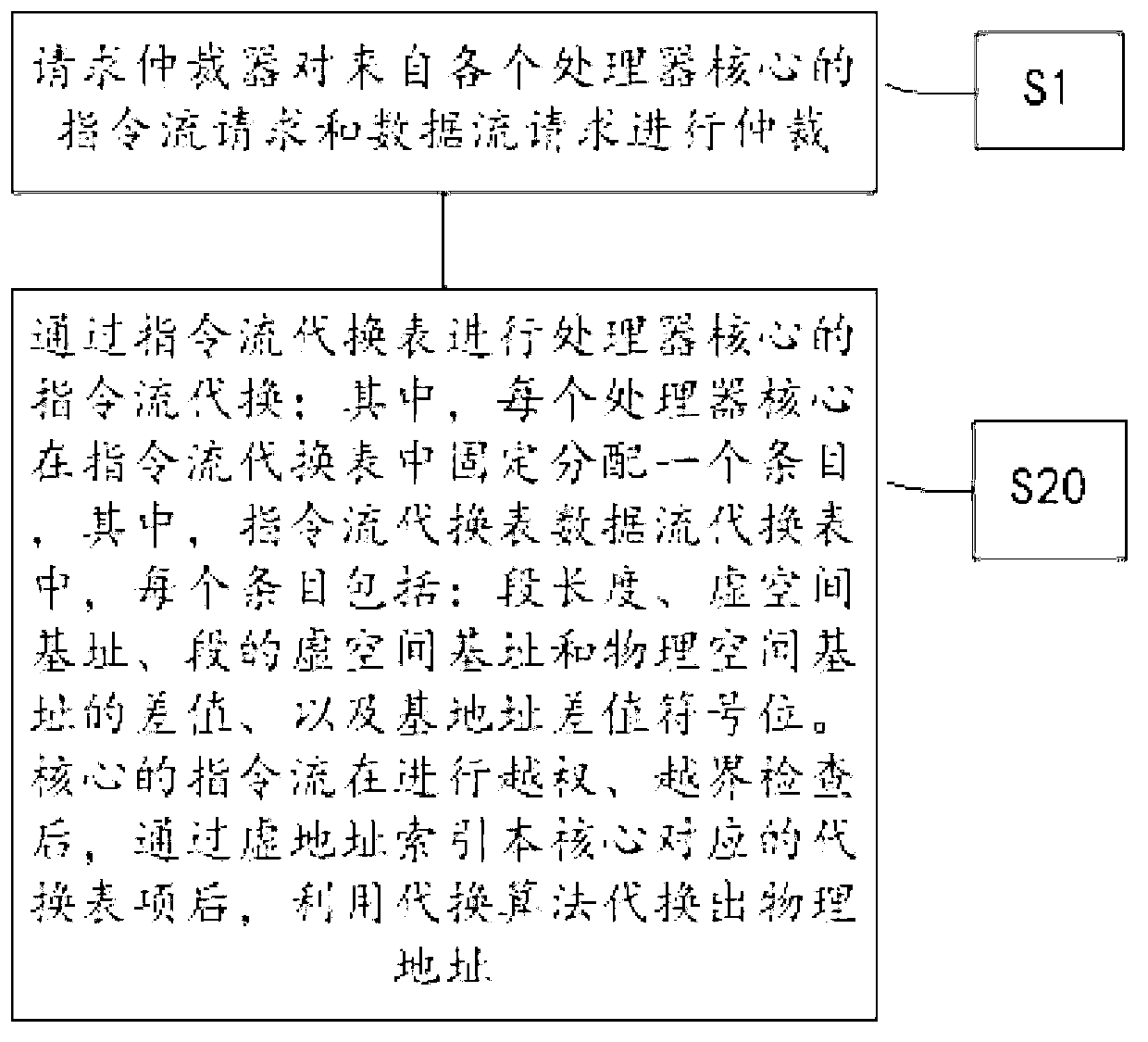
ActiveCN102929588ASupport configurationReduce overheadConcurrent instruction executionCache accessData stream
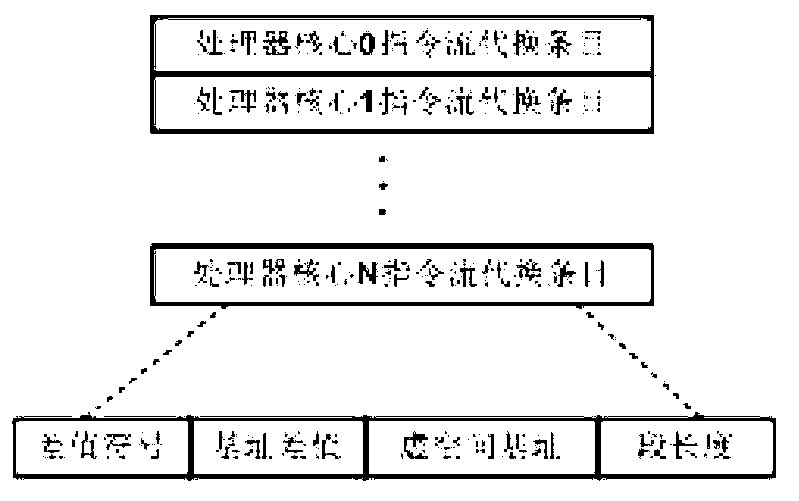
A conversion method of virtual and real addresses of a many-core processor comprises the following steps: step one, requesting an arbiter to arbitrate an instruction stream request and a data stream request from various processor cores; and step two, carrying out centralized substitution on an arbitrated instruction stream and an arbitrated data stream through an instruction stream substitution list and a data stream substitution list, wherein each processor core is fixedly distributed into a plurality of items in the instruction stream substitution list and the data stream substitution list, and after the instruction stream of the core is subjected to the unauthorized and bound check, and the substitution list item corresponding to the core is indexed by the virtual address, the physical address is substituted by a configurable substitution algorithm method, and the substitution list item comprises information on Cache consistency attribute configuration. The information on the Cache consistency attribute configuration comprises whether the arbitrated instruction stream and the arbitrated data stream can be cached to access, whether the cached strategy is subjected to direct writing or write-back, and whether the Cache access is subjected to write allocate.
Owner:JIANGNAN INST OF COMPUTING TECH
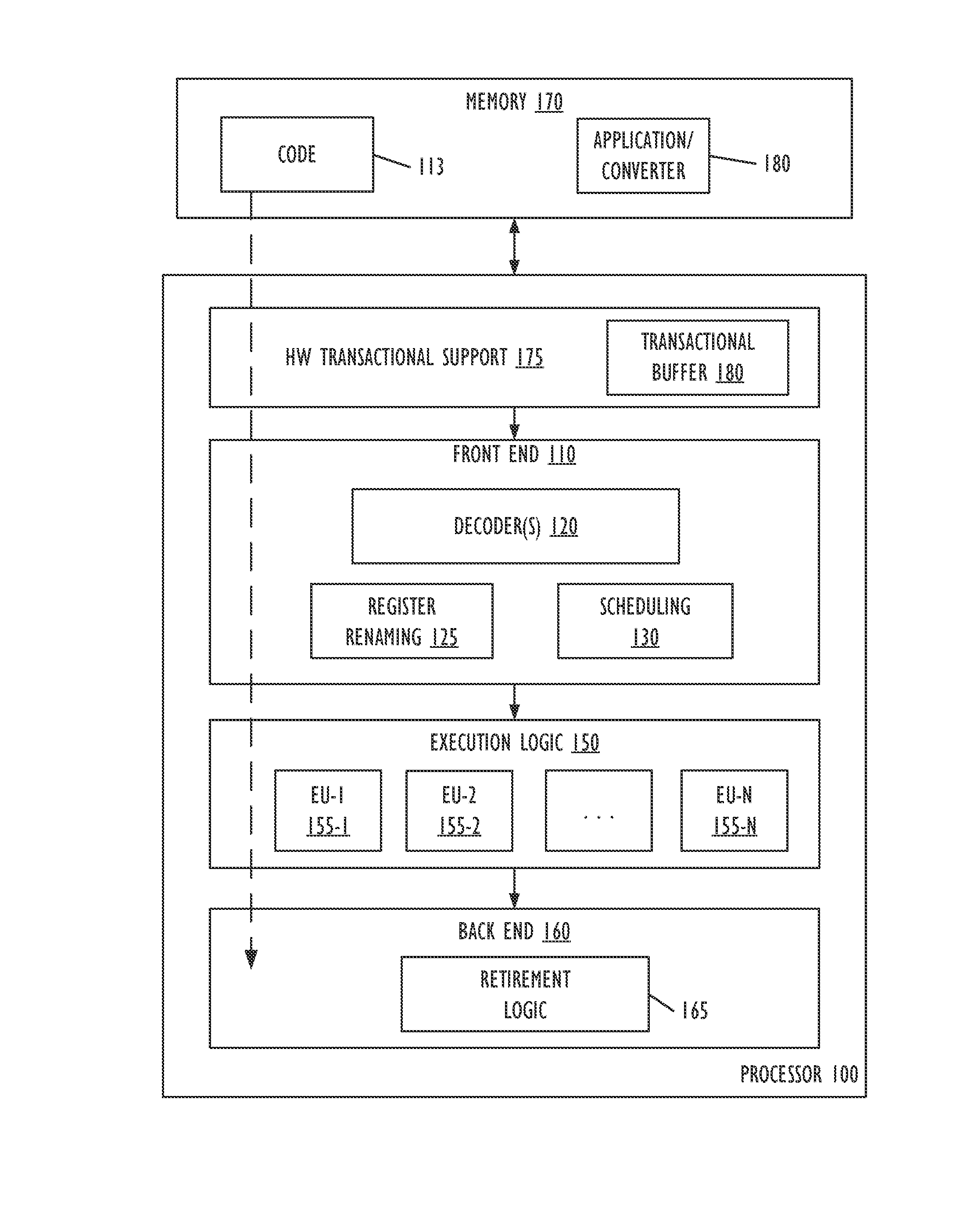
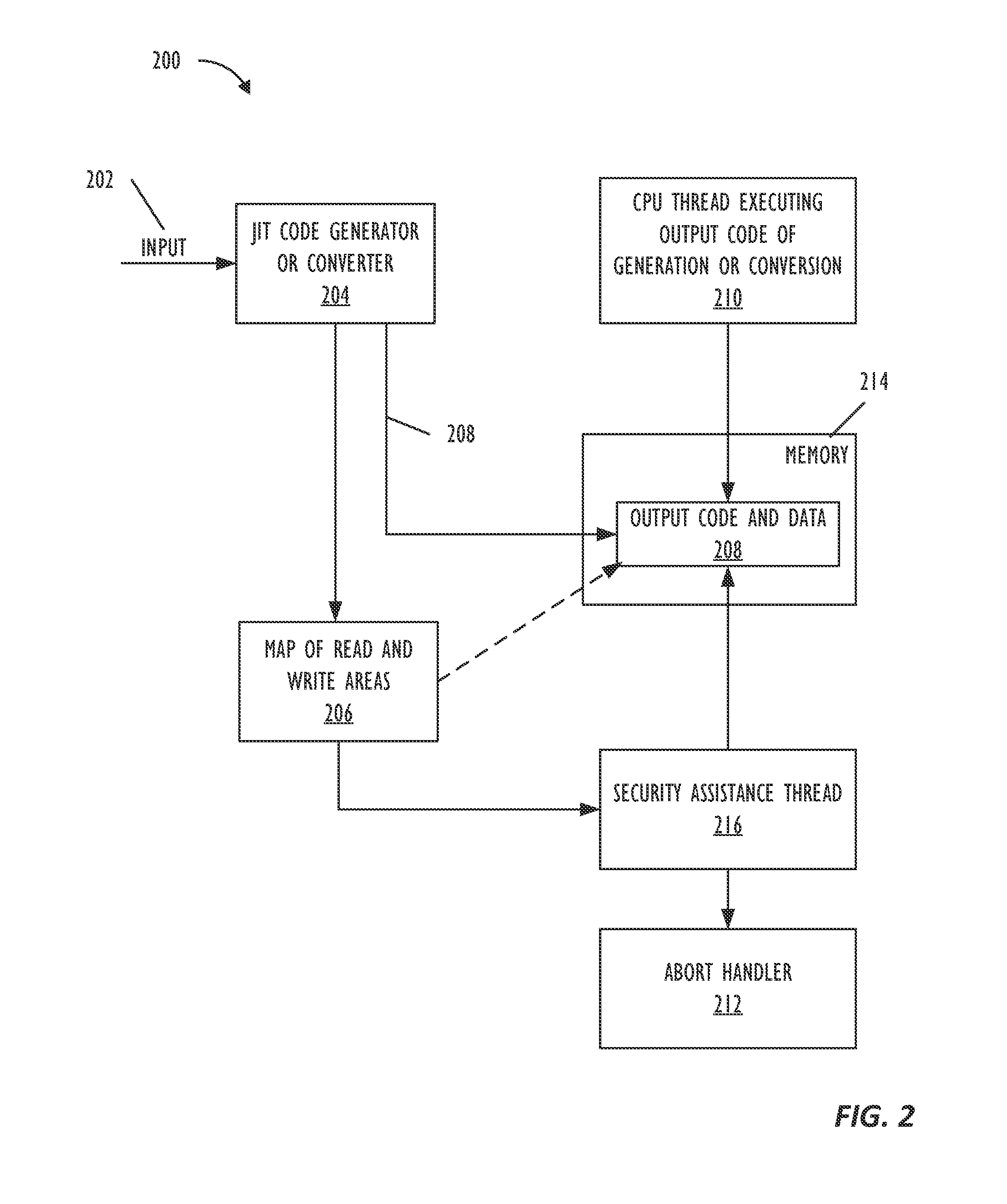
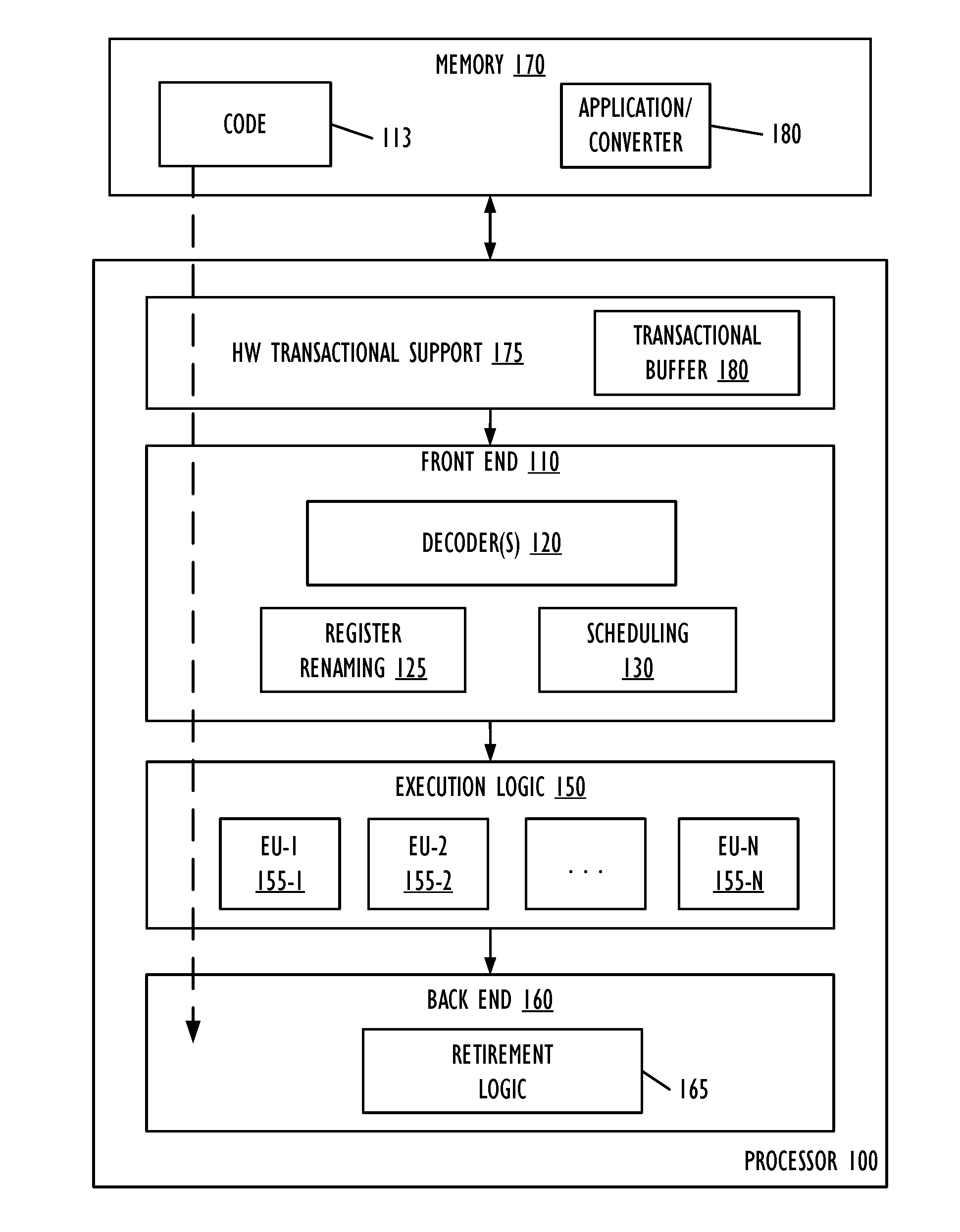
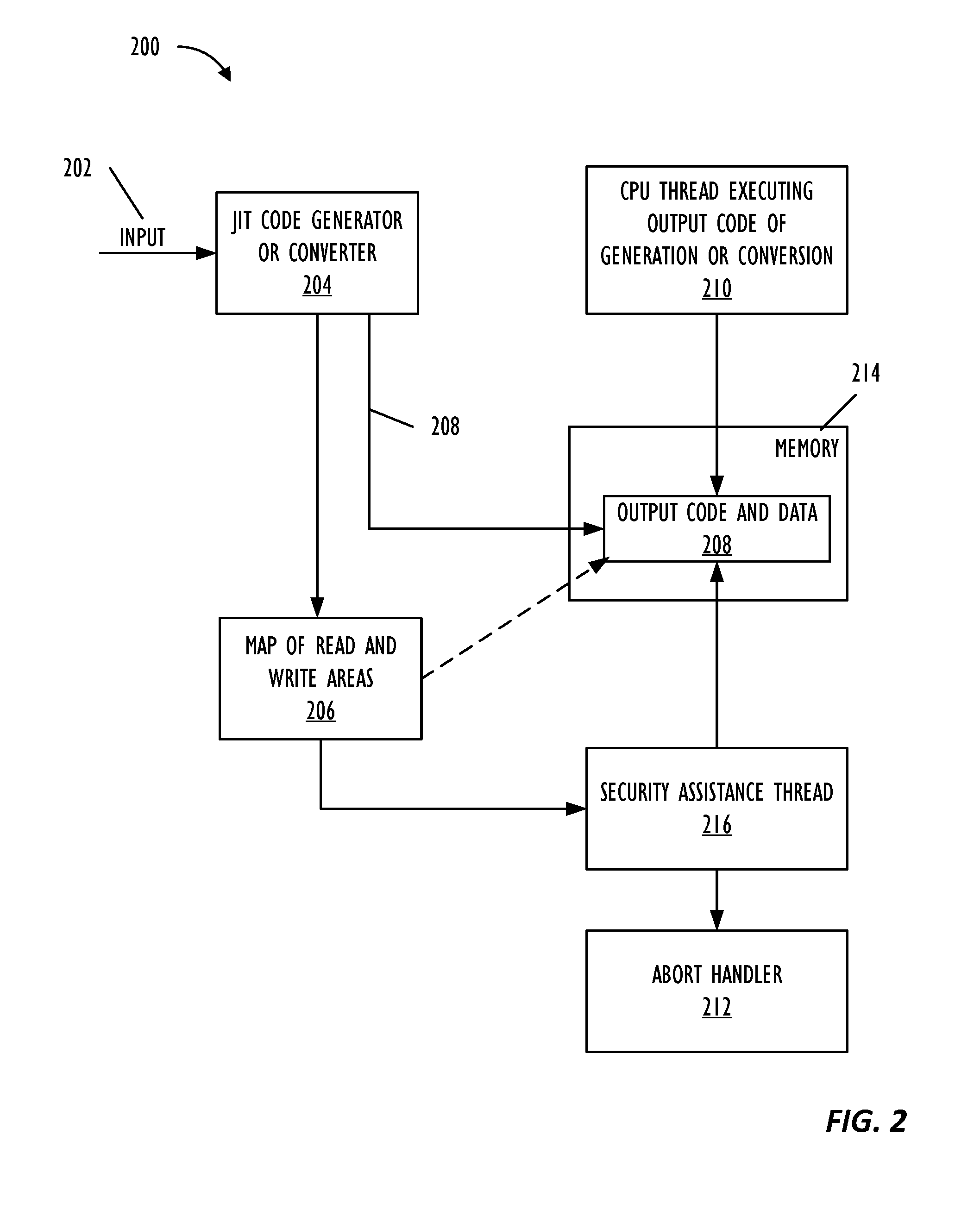
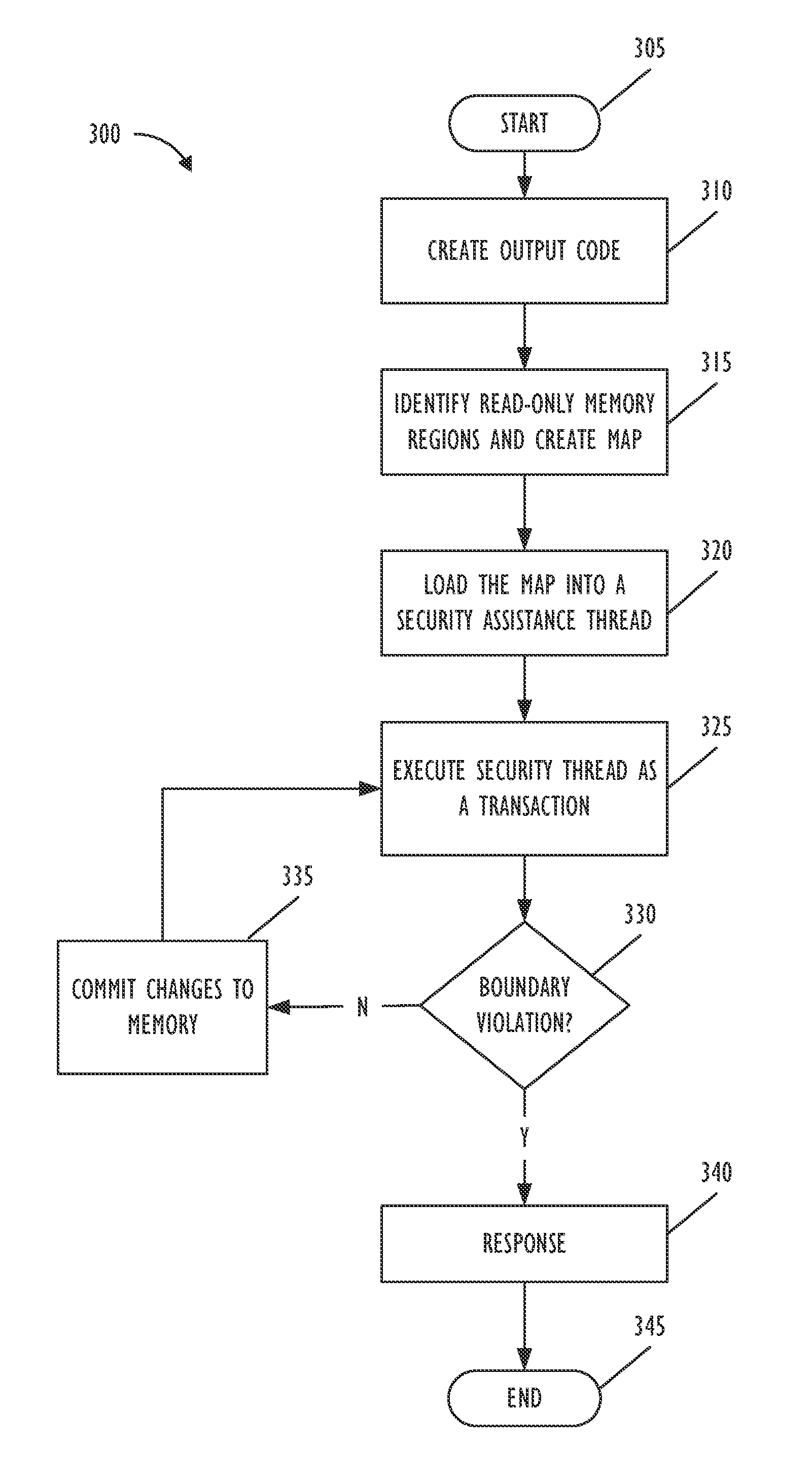
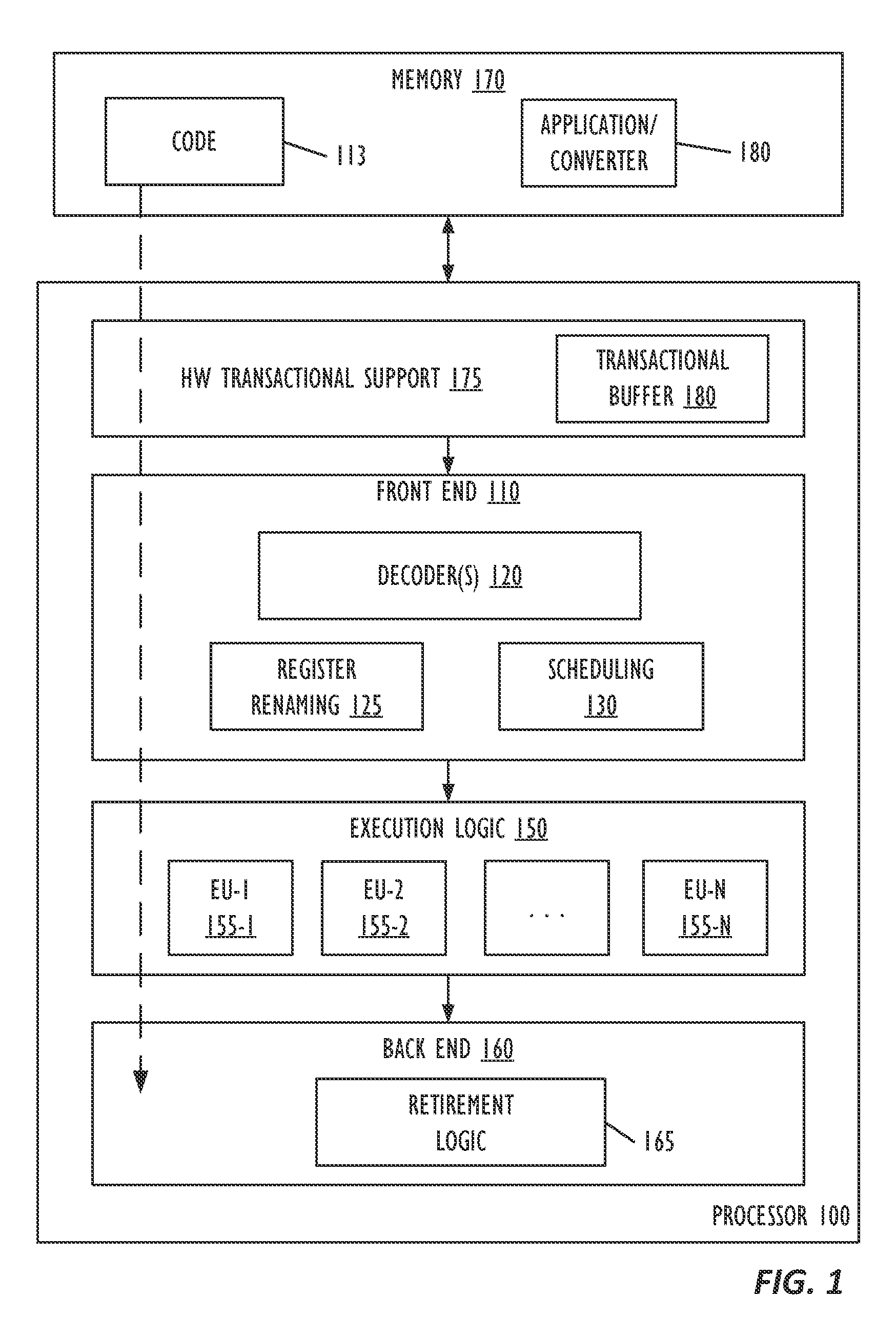
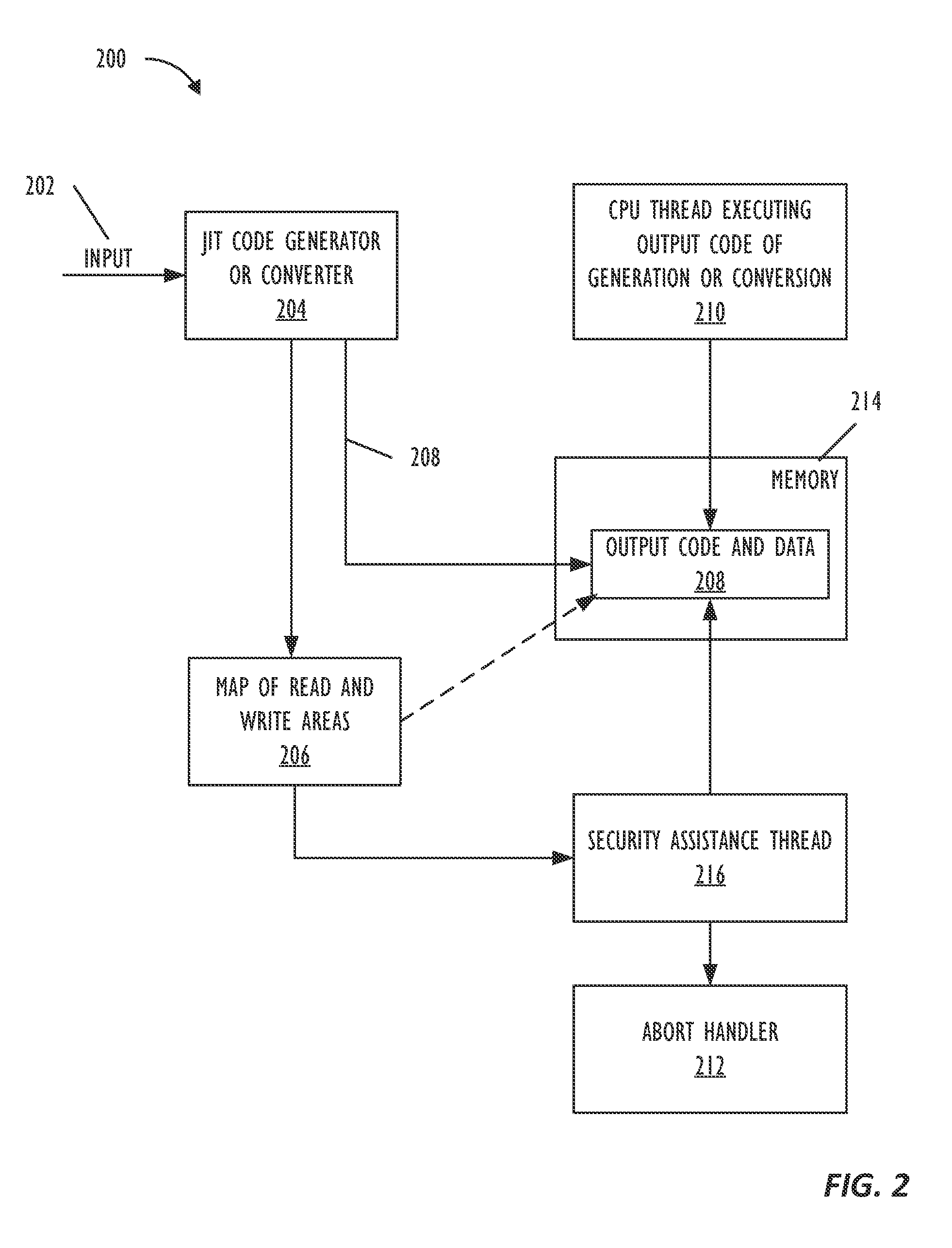
Real-time code and data protection via CPU transactional memory support
ActiveUS20160180085A1Memory architecture accessing/allocationMemory loss protectionParallel computingTransactional memory
A technique allows for memory bounds checking for dynamically generated code by using transactional memory support in a processor. The memory bounds checking includes creating output code, identifying read-only memory regions in the output code and creating a map that is provided to a security monitoring thread. The security monitoring thread executes as a transaction and determines if a transactional conflict occurs to the read-only memory region during parallel execution of a monitored thread in the output code.
Owner:MCAFEE LLC
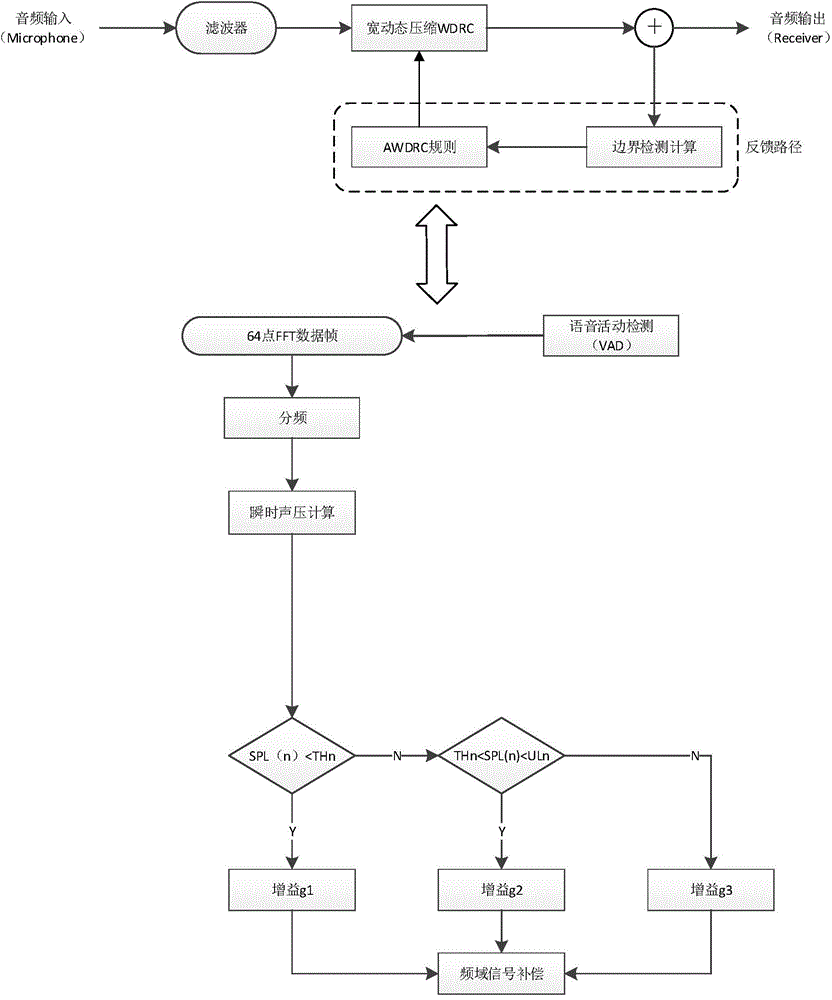
Wide-dynamic compression algorithm of digital hearing aid under noise condition
The invention provides a wide-dynamic compression algorithm of a digital hearing aid in a noise environment. The wide-dynamic compression algorithm comprises the following steps of (A) outputting a de-noised voice signal by means of a voice enhancement algorithm, (B) estimating a voice signal output feedback path, performing boundary checking calculation and performing calculation and output according to three self-adaptive wide-dynamic compression rules, (C) using an output obtained the step A and an output obtained the step B as an input of a wide-dynamic compression module to perform voice signal compression and amplification and improve signal-noise ratio. When the sound pressure level of an outside sound source is smaller than hearing threshold of a normal person according to a traditional compression algorithm, the hearing aid ordinarily does not start the compression algorithm, the output sound pressure level is set as 0, and therefore a part of information of audio signals is lost. By means of the wide-dynamic compression algorithm, the process is improved and optimized, the part of information of audio signals with the sound pressure level smaller than hearing threshold of the normal person is kept, and meanwhile a noise elimination function is provided.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
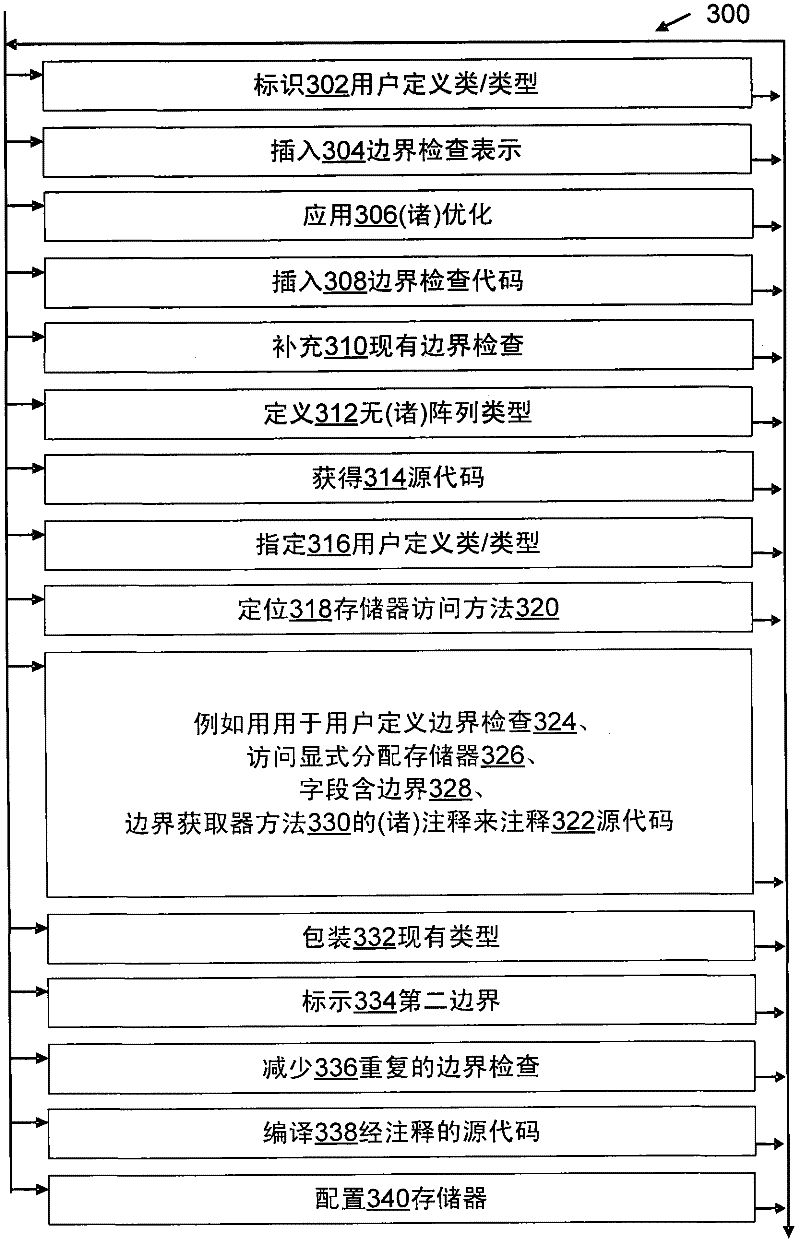
Compile-time bounds checking for user-defined types
ActiveCN102402451ATransformation of program codeProgram control using stored programsAccess methodManaged code
The present invention relates to a compile-time bounds checking for user-defined types. Compile-time optimized bounds checking of user-defined types is provided. A user-defined class has an annotated memory-accessing method, and an annotated bound-providing member such as an integer field containing a bound or a method that returns a bound when called. The user-defined-bounds check may supply bounds checking where the programming language has none, or it may supplement existing bounds checks, e.g., by wrapping a built-in array type or a garbage-collector-managed type. Bounds checking can be extended beyond arrays and other types whose layout is controlled by a compiler, allowing efficient systems programming in a managed code environment. A bounds-check representation is inserted by the compiler in intermediate language code. Optimization then reduces duplicative bounds checking.
Owner:MICROSOFT TECH LICENSING LLC
Modification of array access checking in AIX
InactiveUS7448029B2Error detection/correctionSoftware engineeringArray data structureError processing
An error handling operation for checking of an array access in program code is modified during compilation thereof. A sequentially arranged null checking operation and array bounds checking operation for the array access are located. The array bounds checking operation has a corresponding error handling operation operable for setting an array bounds error. The located sequentially arranged null checking operation is removed. The corresponding error handling operation for the located sequentially arranged array bounds checking operation is modified to perform the removed null checking operation during execution of the program code.
Owner:IBM CORP
Vertex array access bounds checking
InactiveUS9043515B1Drawing from basic elementsPlatform integrity maintainanceGraphicsArray data structure
Owner:GOOGLE LLC
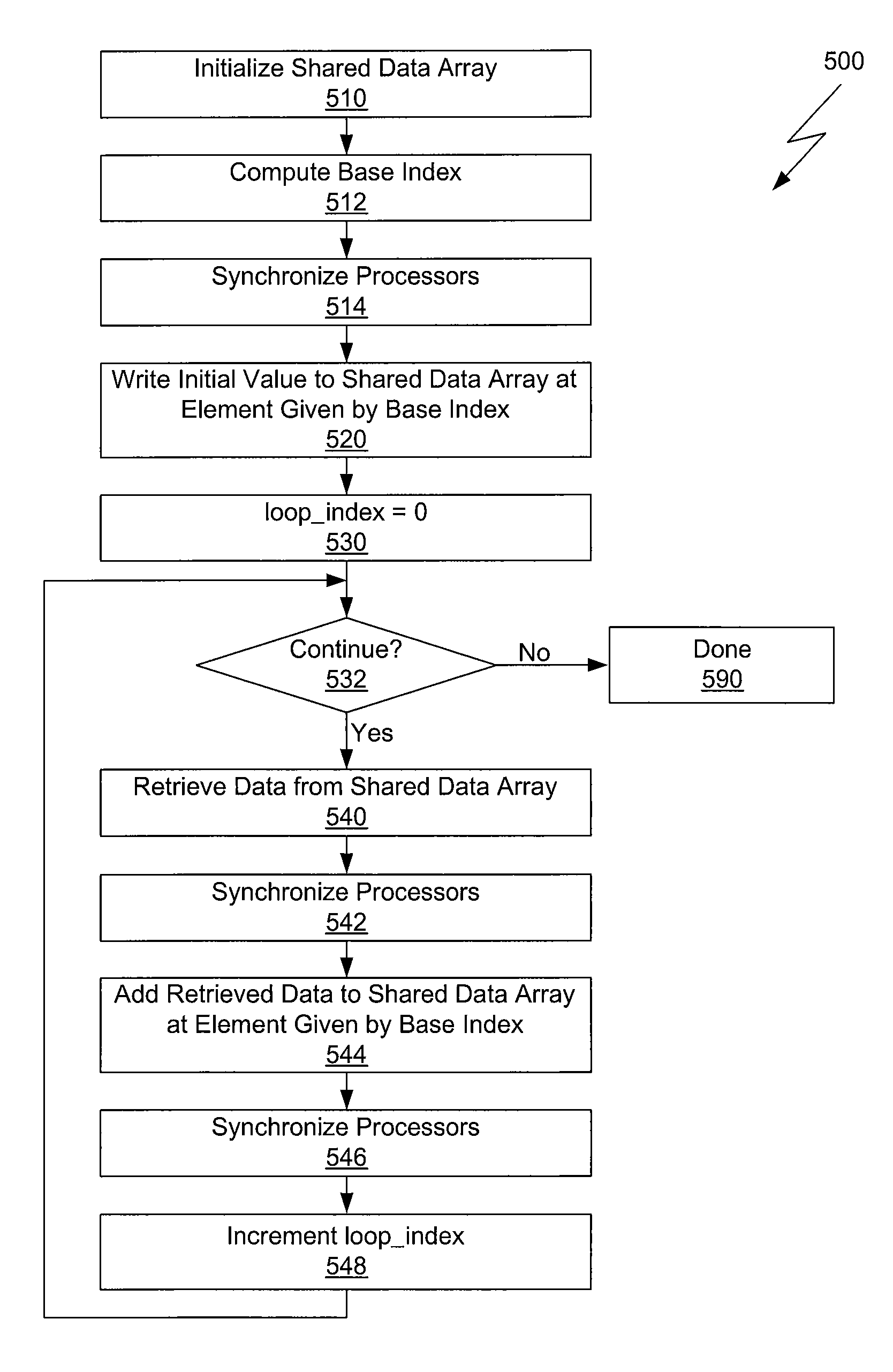
Instruction-efficient algorithm for parallel scan using initialized memory regions to replace conditional statements
ActiveUS8417735B1Improve computing efficiencyImprove efficiencyDigital computer detailsSpecial data processing applicationsArray data structureEfficient algorithm
One embodiment of the present invention sets forth a technique for performing a parallel scan operation with high computational efficiency in a single-instruction multiple-data (SIMD) environment. Each participating thread initially writes an extended region of a data array to initialize the region with an identity value. For example, a value of zero is used as the identity value for addition. The initialized region of the data array includes an initialized entry for every possible out of bounds index that may be computed in the normal course of the parallel scan operation. During the parallel scan operation each thread computes data array indices according to any technically appropriate technique. When a participating thread computes an index that would conventionally be out of bounds, the thread is able to retrieve an identity value from the initialized region of the data array rather than perform a bounds check that returns the identity value.
Owner:NVIDIA CORP
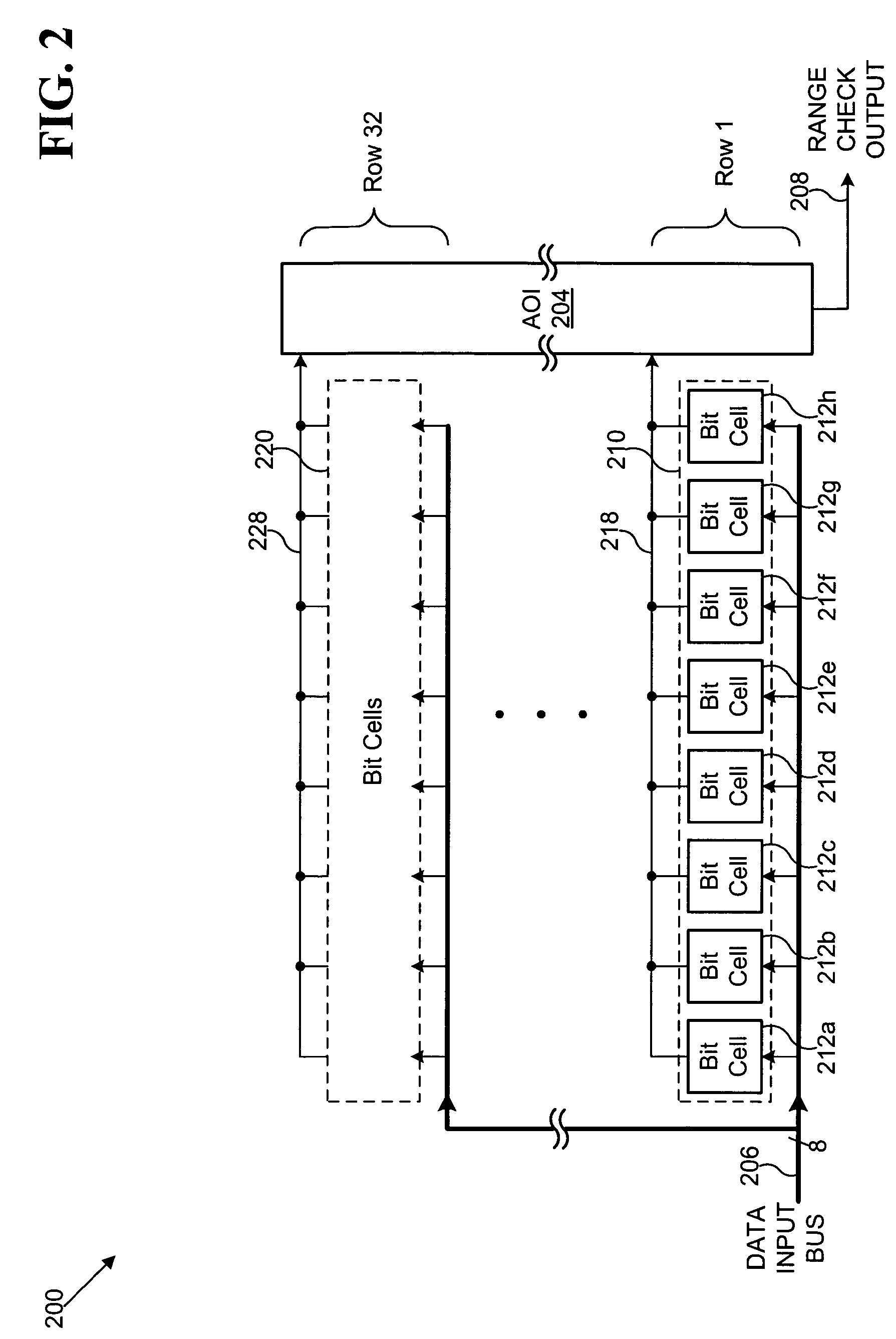
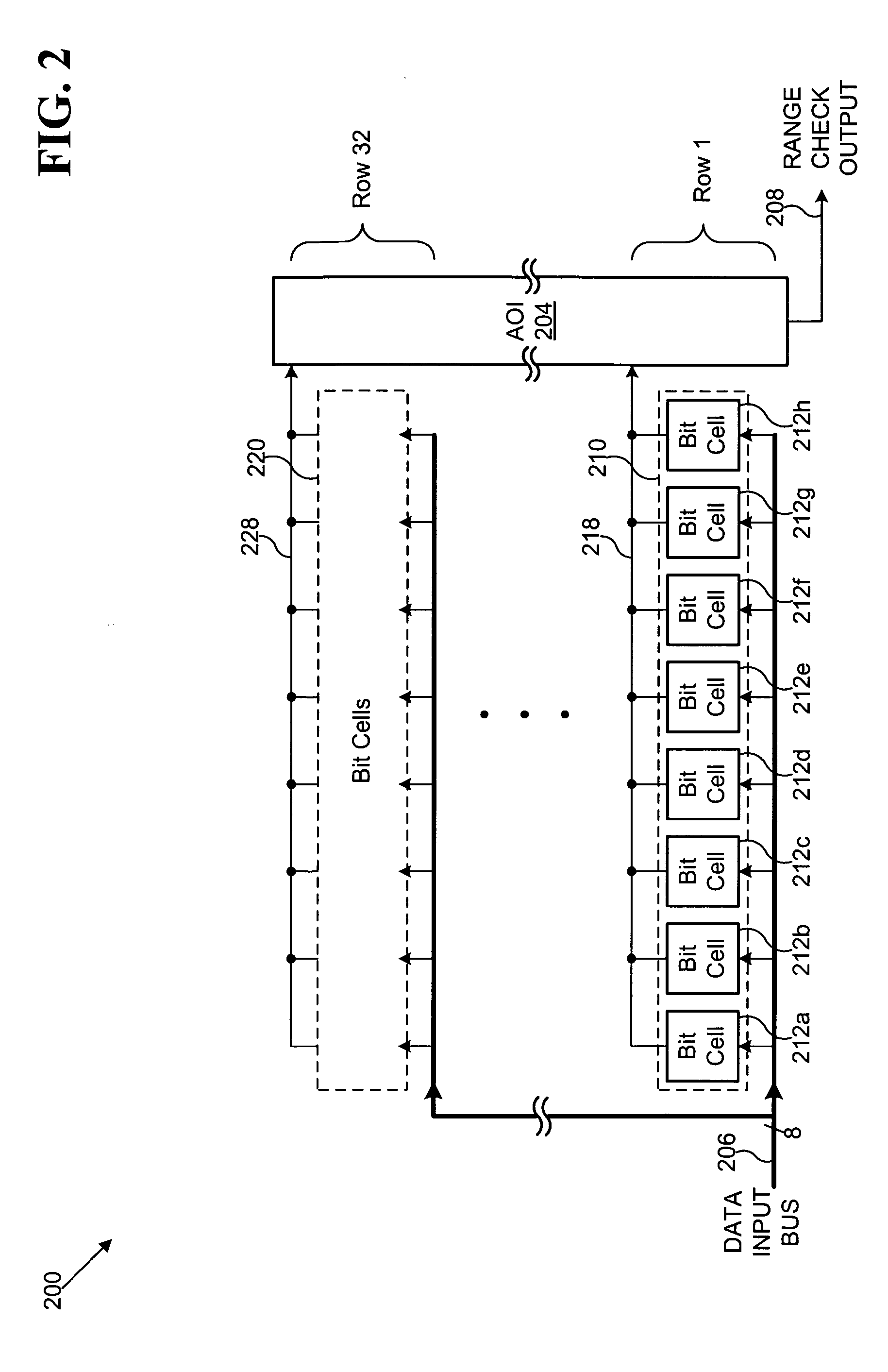
Range checking content addressable memory array
Owner:AVAGO TECH INT SALES PTE LTD
Real-time code and data protection via CPU transactional memory suppport
ActiveUS20170046196A1Memory architecture accessing/allocationUnauthorized memory use protectionParallel computingTransactional memory
A technique allows for memory bounds checking for dynamically generated code by using transactional memory support in a processor. The memory bounds checking includes creating output code, identifying read-only memory regions in the output code and creating a map that is provided to a security monitoring thread. The security monitoring thread executes as a transaction and determines if a transactional conflict occurs to the read-only memory region during parallel execution of a monitored thread in the output code.
Owner:MCAFEE LLC
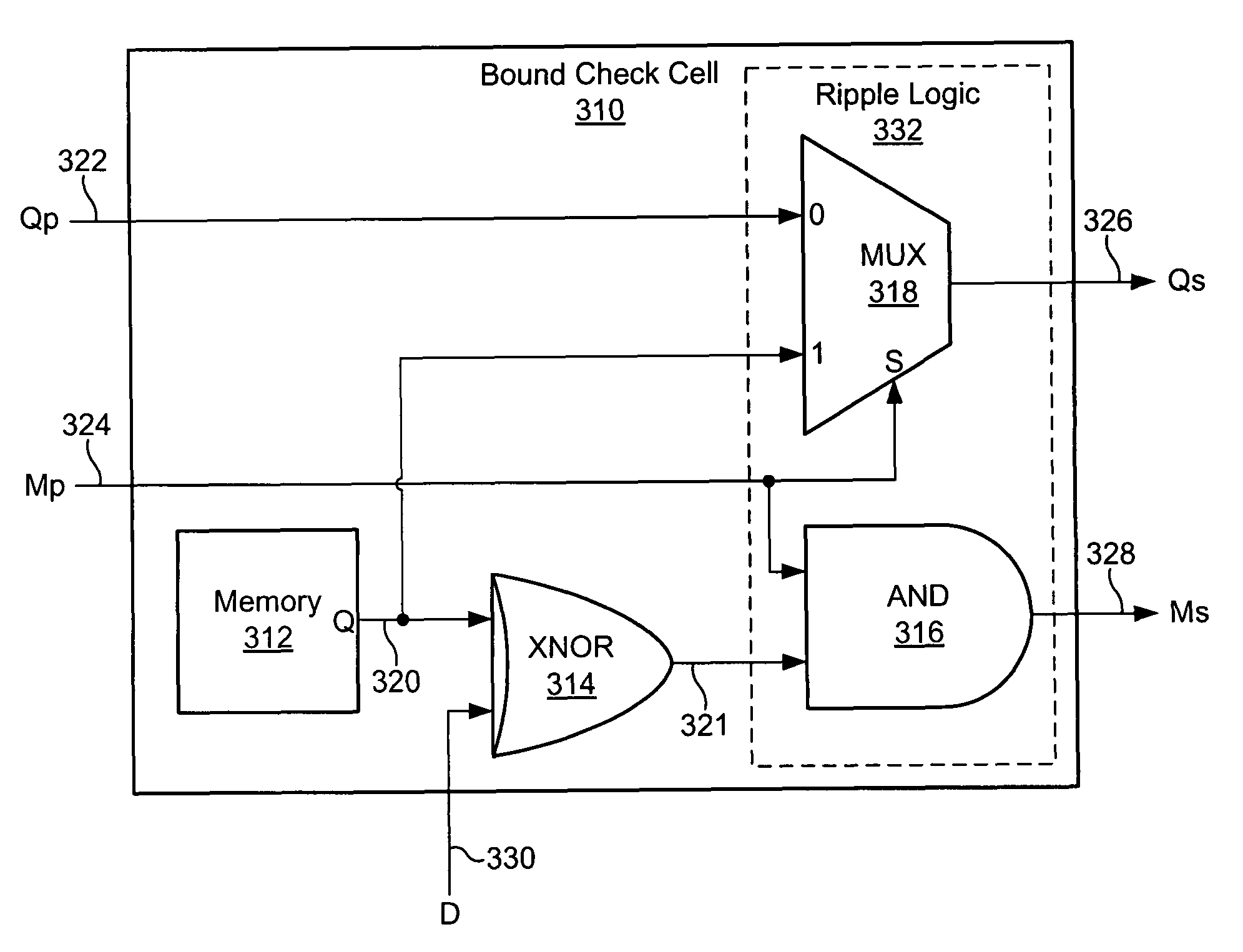
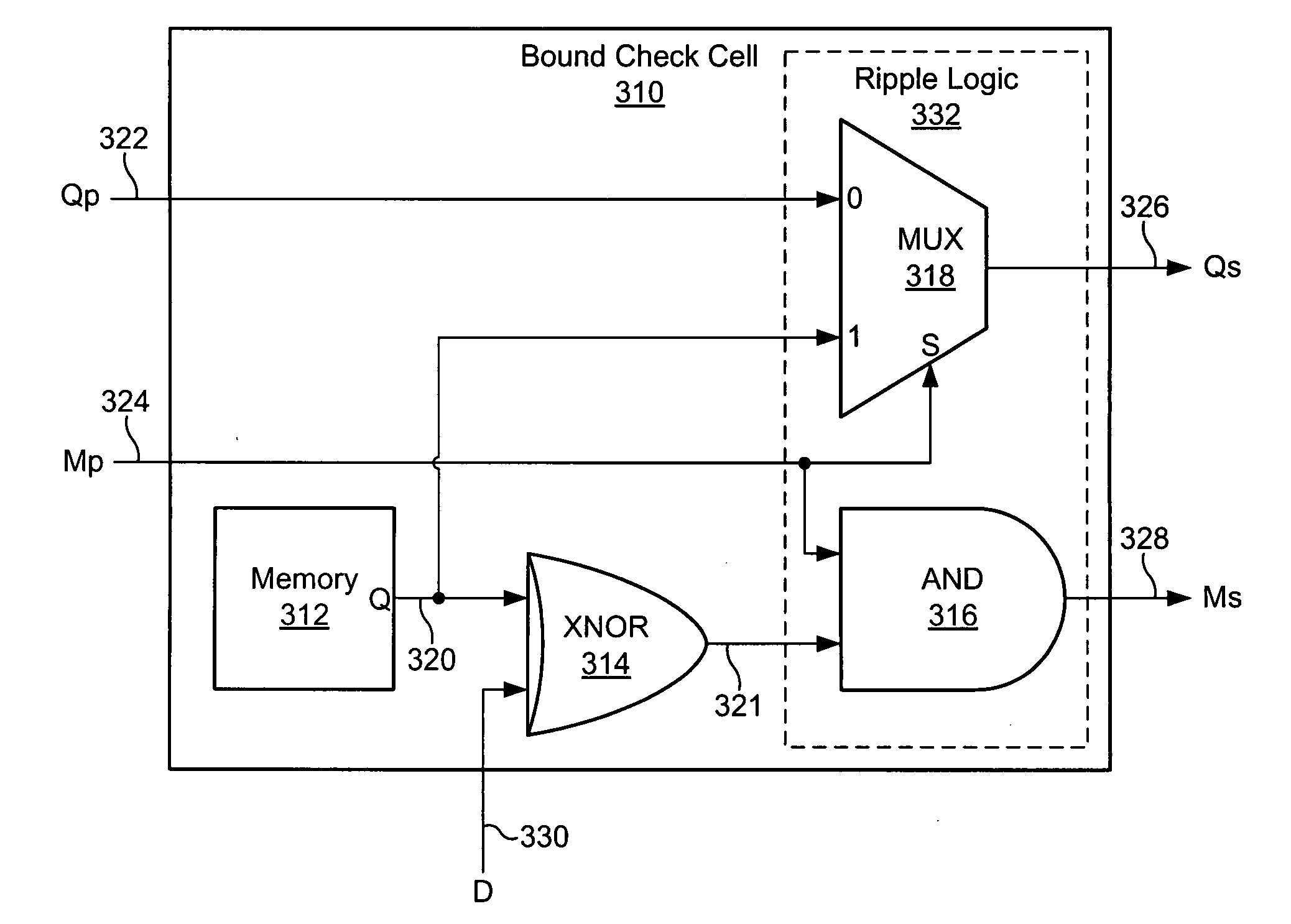
Range checking content addressable memory array
A disclosed embodiment is a range checking CAM array comprising a plurality of words, where each of the plurality of words comprises a plurality of bound check cells. Each of the plurality of bound check cells outputs a corresponding plurality of match signals and a corresponding plurality of bound check signals. The corresponding plurality of match signals and corresponding plurality of bound check signals are combined to produce a range check output indicating whether data on a data input bus is within a target range. The plurality of bound check cells may be coupled to form at least one cascade of bound check cells, where each cascade of bound check cells may be terminated at a ripple logic. The CAM array produces a final range check output based on the corresponding plurality of match signals and the corresponding plurality of bound check signals.
Owner:AVAGO TECH INT SALES PTE LTD
Optimizing bounds checking using computer algebra
ActiveUS8484613B2Reduce overheadError avoidanceSpecific program execution arrangementsTheoretical computer scienceBounds checking
Some embodiments of the present invention provide techniques and systems for optimizing bounds-checking During operation, the system can receive one or more instructions which when executed evaluate a first expression whose value is required to be between a lower bound expression's value and an upper bound expression's value, such that at least one of the following three values is not determinable before execution: the first expression's value, the lower bound expression's value, and the upper bound expression's value. Next, the system can use computer algebra to determine whether the first expression's value is guaranteed to be between the lower bound expression's value and the upper bound expression's value. If the system determines that the first expression's value is not guaranteed to be between the lower bound expression's value and the upper bound expression's value, the system can add bounds-checking instructions to the one or more instructions.
Owner:SYNOPSYS INC
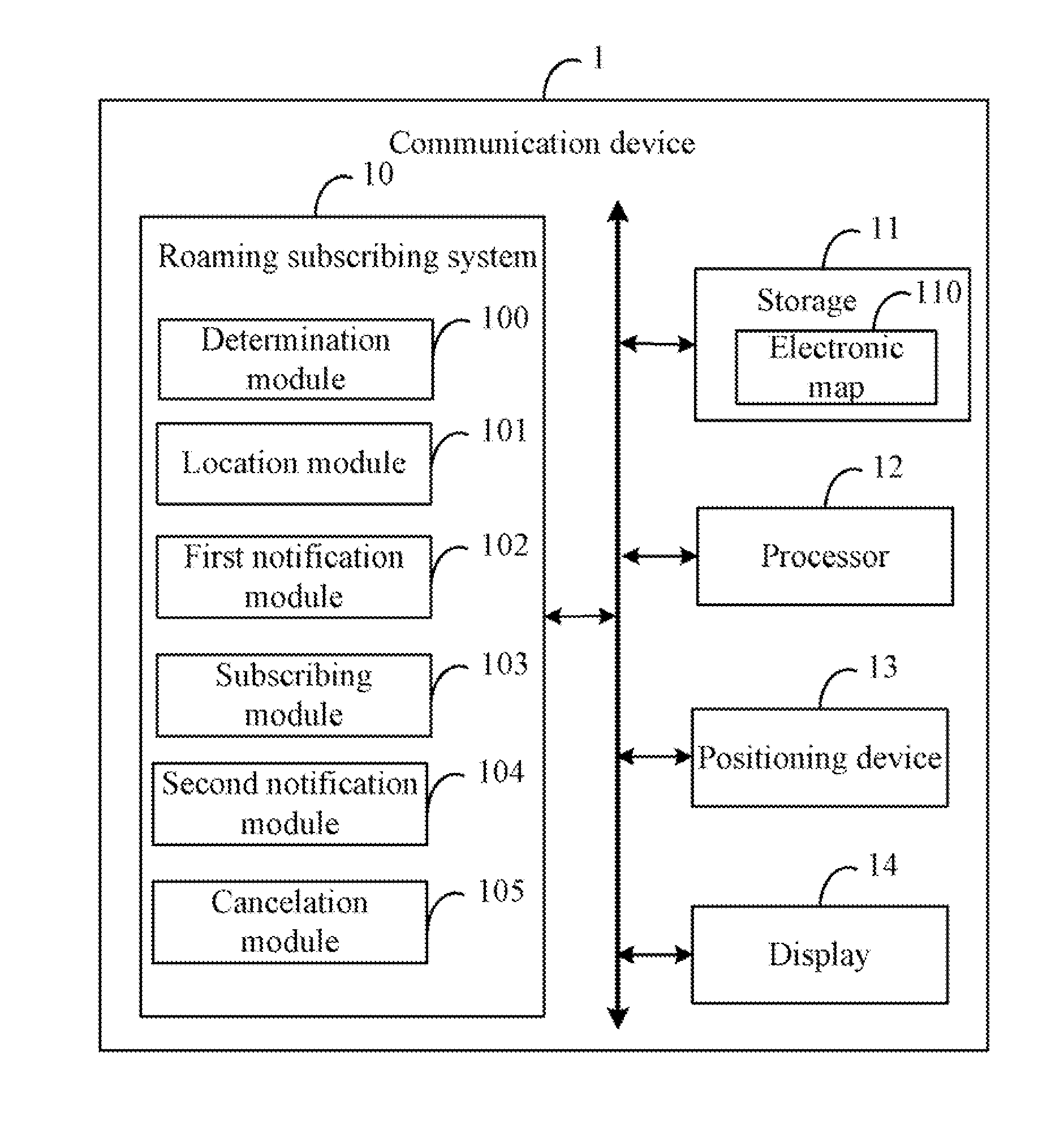
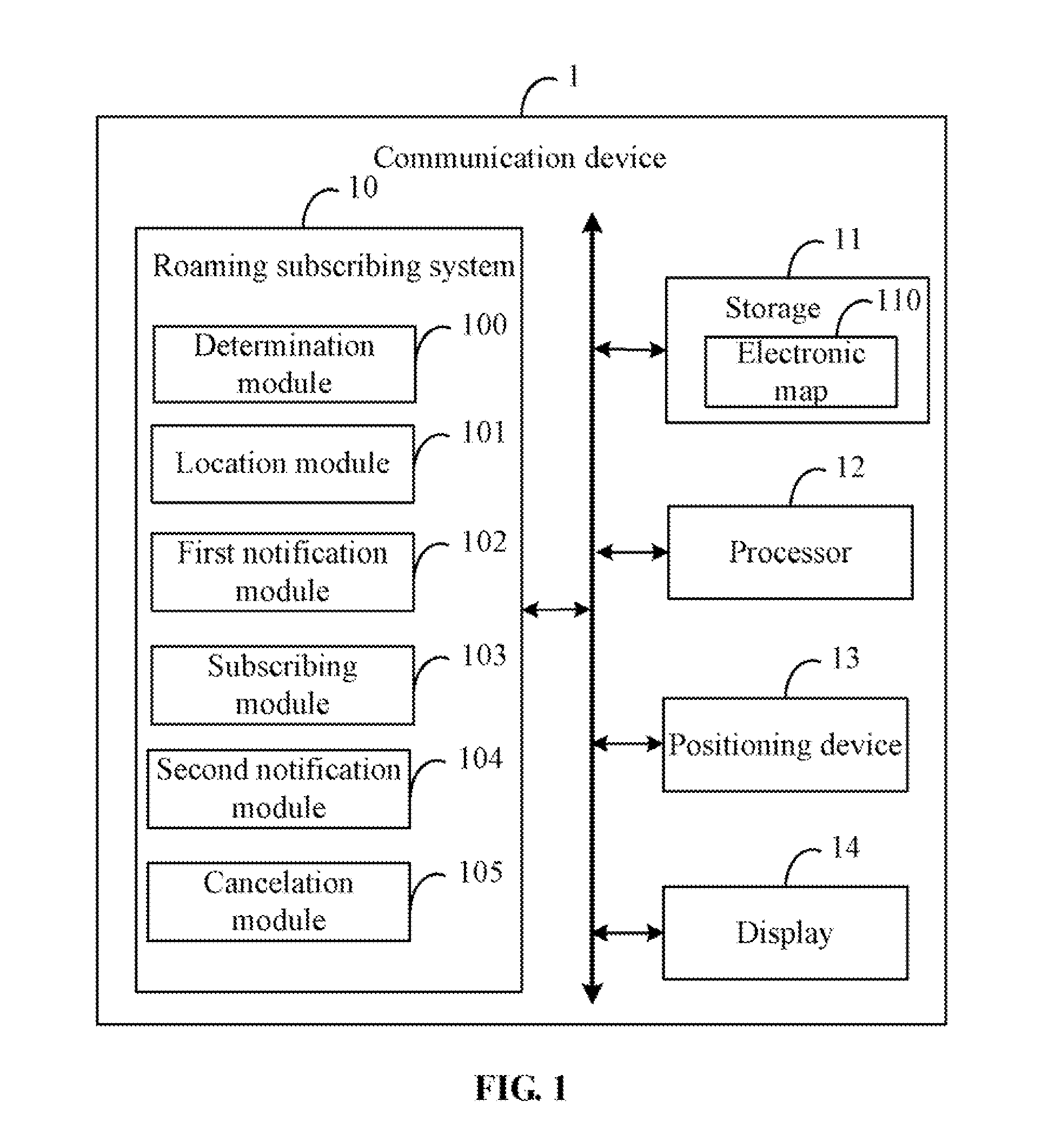
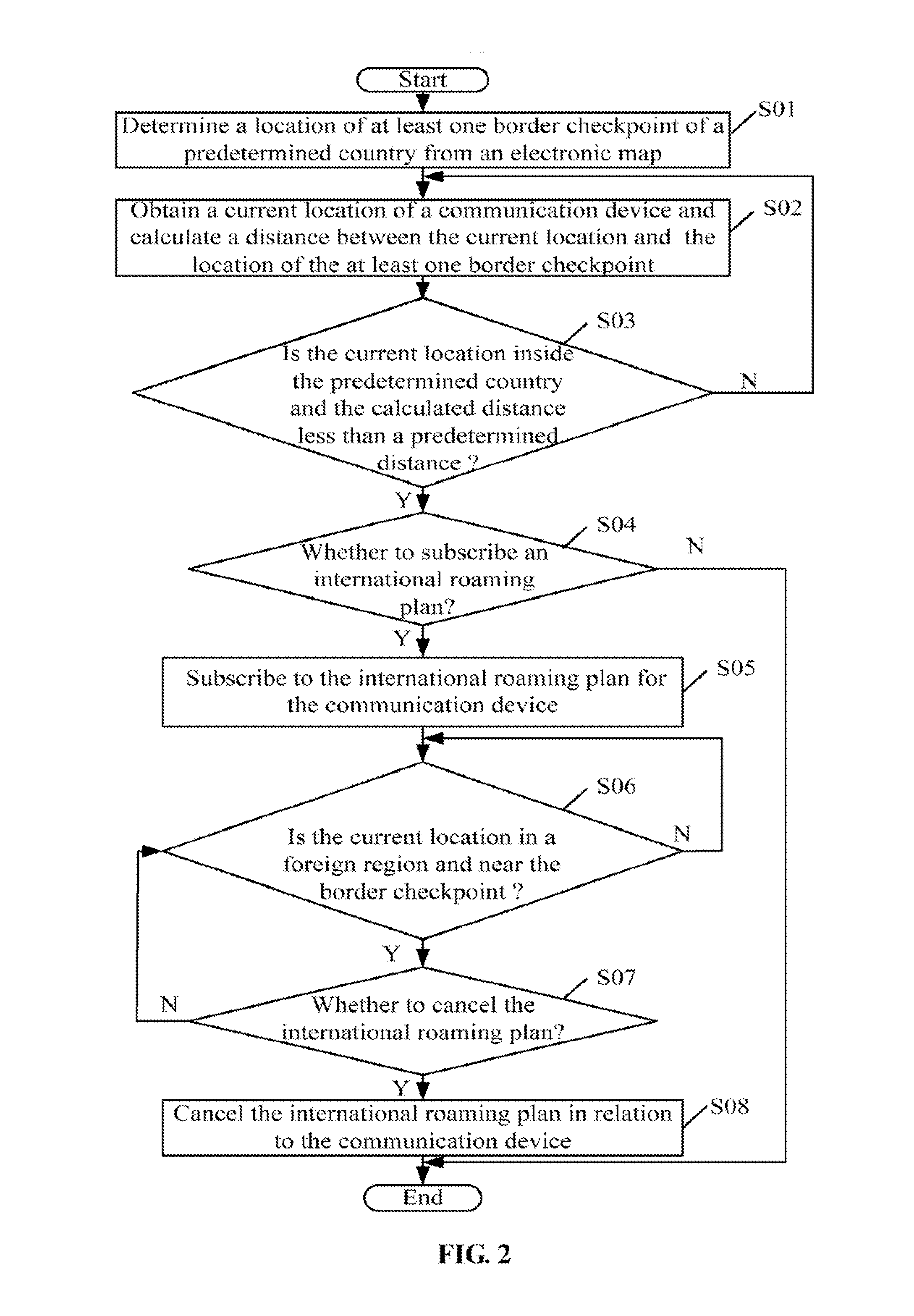
Apparatus and method for subscribing to international roaming plan for communication device
ActiveUS8977256B2Special service for subscribersWireless commuication servicesTelecommunicationsEngineering
Owner:FU TAI HUA IND SHENZHEN +1
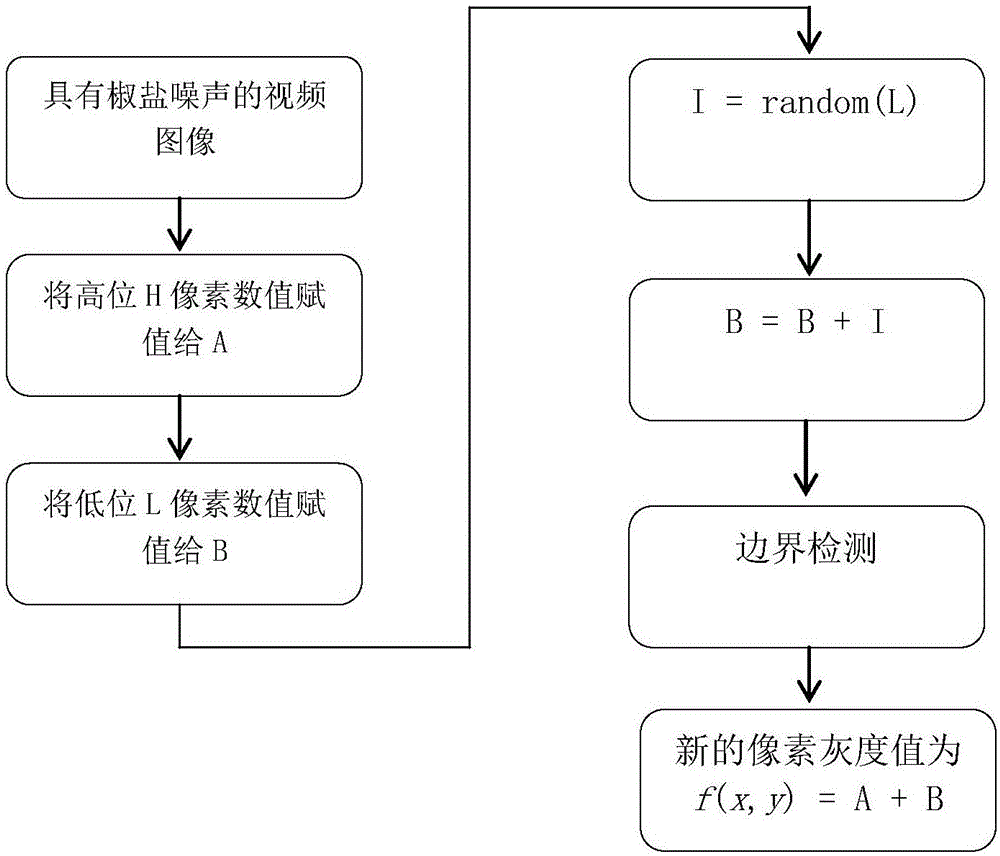
Method for suppressing salt-and-pepper noise based on image dithering
ActiveCN106683054AImprove visual effectsSuppress salt and pepper noiseImage enhancementImage analysisImaging processingVideo image
The invention discloses a method for suppressing salt-and-pepper noise based on image dithering. The method includes the following steps: inputting the pixel value of a certain pixel that obtains an image; determining a pixel bit number n, imparting the pixel values corresponding to the first H bits from high to low to a first temporary storage amount A; making L=n-H, and imparting the pixel value corresponding to L to a second temporary storage amount B; making I=random (L), I being a random integer between -2L-1 and 2L-1; making B=B+1; conducting boundary inspection on B value; imparting a new pixel value f (x, y)=A+B to the pixel at (x, y); repeating the aforementioned procedures on the entire image, and completing image processing. According to the invention, the method, by introducing random integers within a certain range to a low L of a video image, can suppress salt-and-pepper noise, makes the video image more smooth, and provides better vision effects.
Owner:NANJING UNIV OF SCI & TECH
Real-time code and data protection via CPU transactional memory support
ActiveUS9507938B2Memory architecture accessing/allocationPlatform integrity maintainanceParallel computingTransactional memory
A technique allows for memory bounds checking for dynamically generated code by using transactional memory support in a processor. The memory bounds checking includes creating output code, identifying read-only memory regions in the output code and creating a map that is provided to a security monitoring thread. The security monitoring thread executes as a transaction and determines if a transactional conflict occurs to the read-only memory region during parallel execution of a monitored thread in the output code.
Owner:MCAFEE LLC
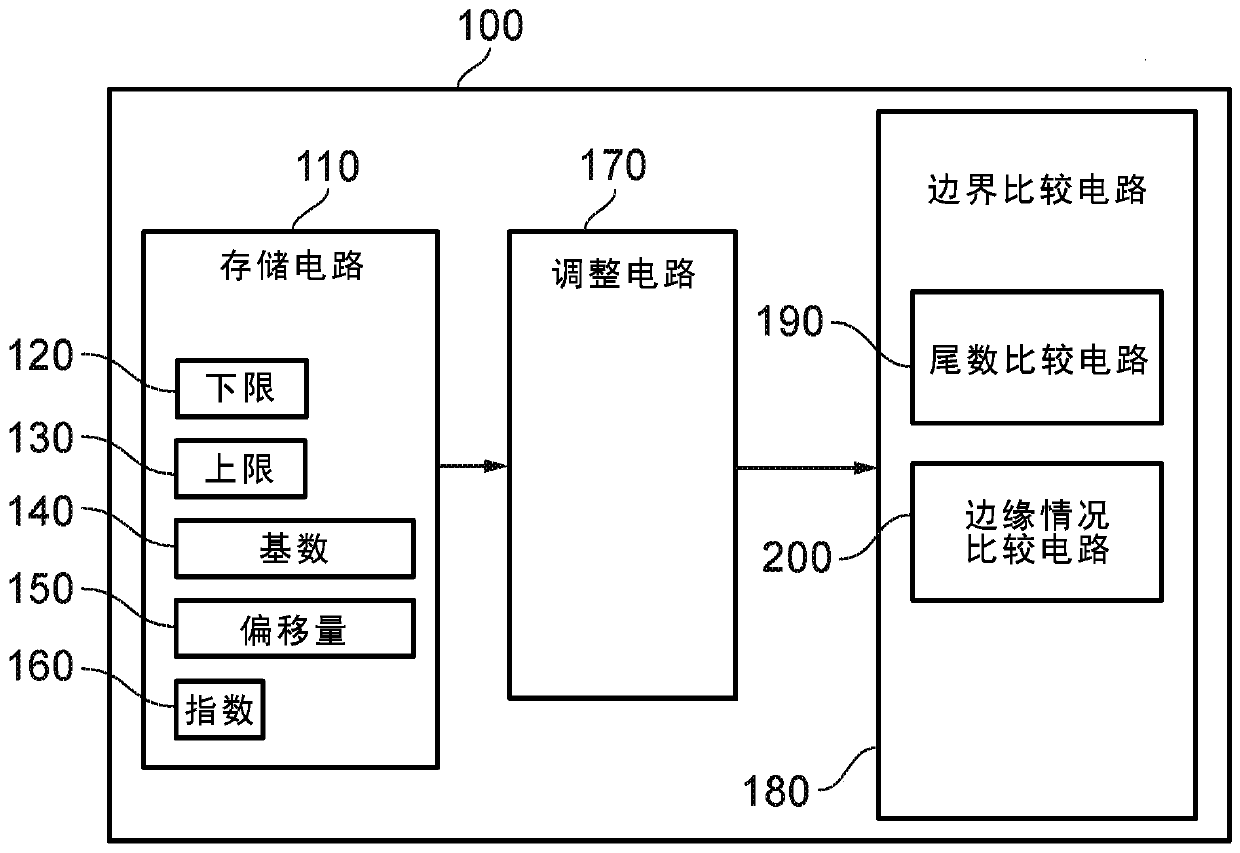
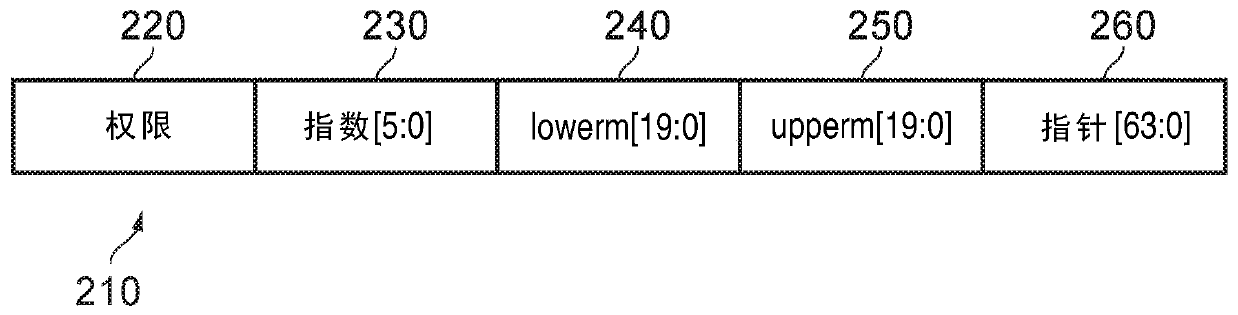
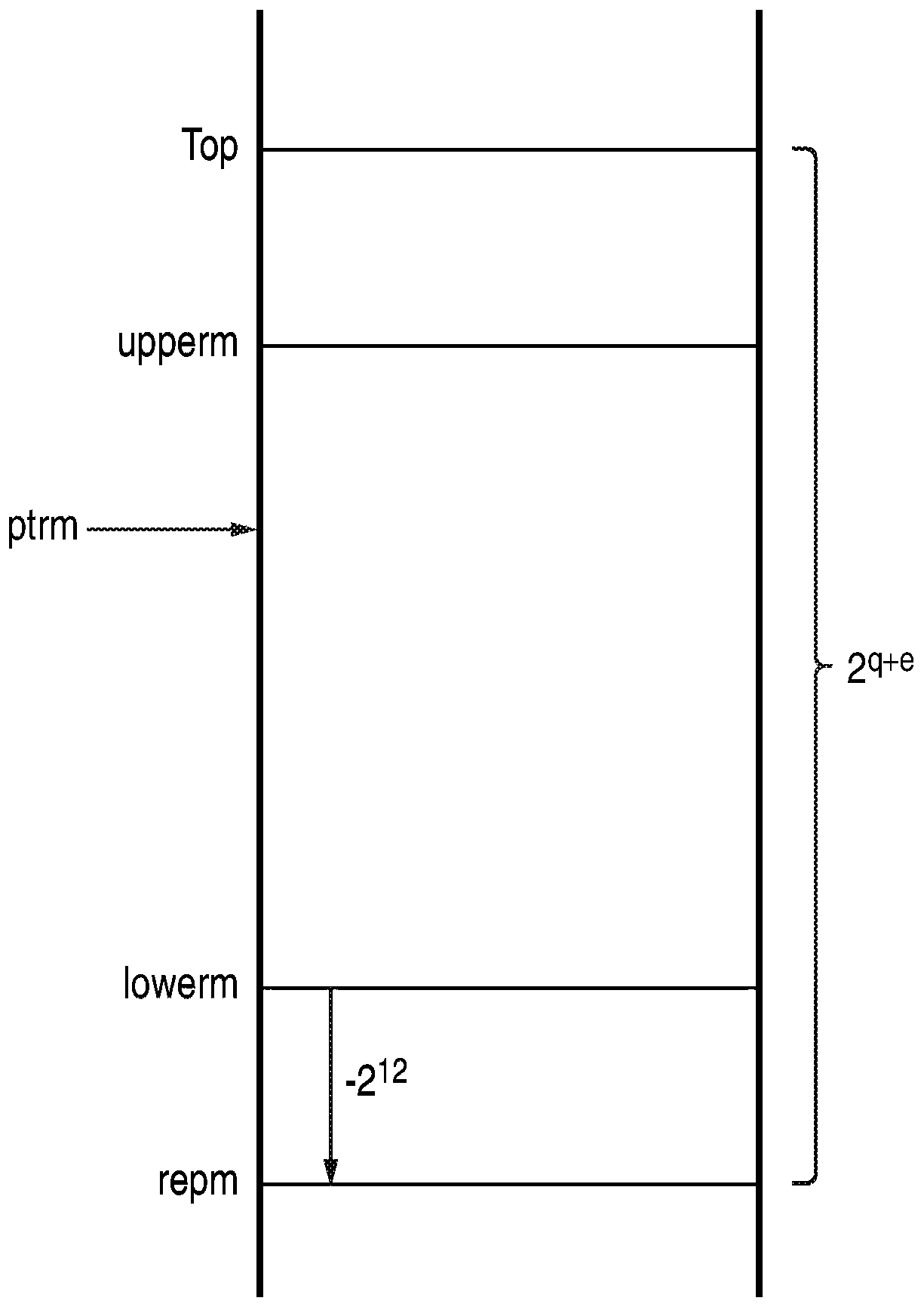
Bounds checking
ActiveCN110741552AMemory architecture accessing/allocationComputation using non-contact making devicesLower limitSoftware engineering
A data processing apparatus is provided, for performing a determination of whether a value falls within a boundary defined by a lower limit between 0 and 2 m and an upper limit between 0 and 2 m. Theapparatus includes storage circuitry that stores each of the lower limit and the upper limit in a compressed form as a mantissa of q < m bits and a shared exponent e. A most significant m-q-e bits ofsaid lower limit and said upper limit are equal to a most significant m-q-e bits of said value. Adjustment circuitry performs adjustments to the lower limit and the upper limit in compressed form andboundary comparison circuitry performs the determination on the value using the lower limit and the upper limit in the compressed form.
Owner:ARM LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com