Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Loadable kernel module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
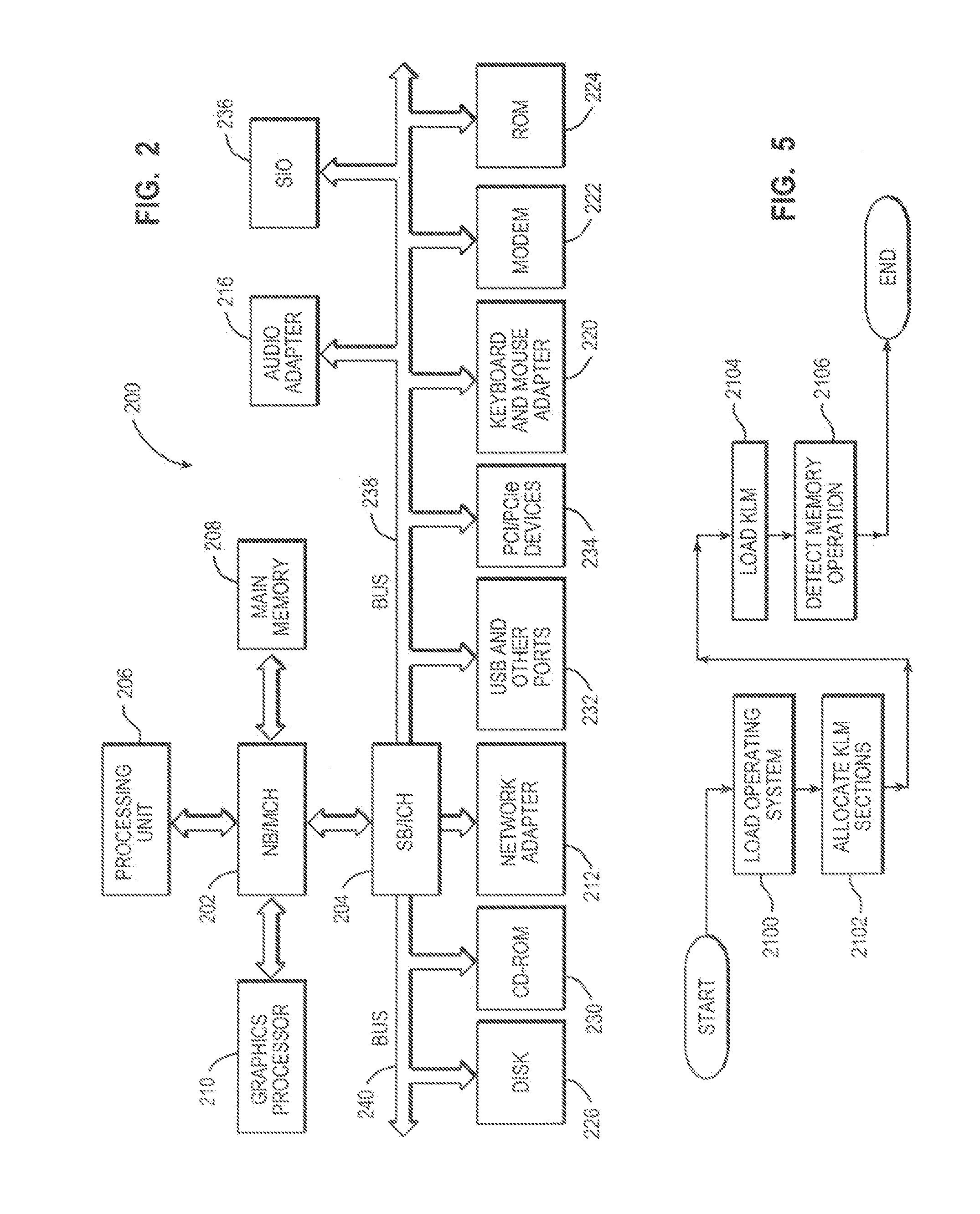
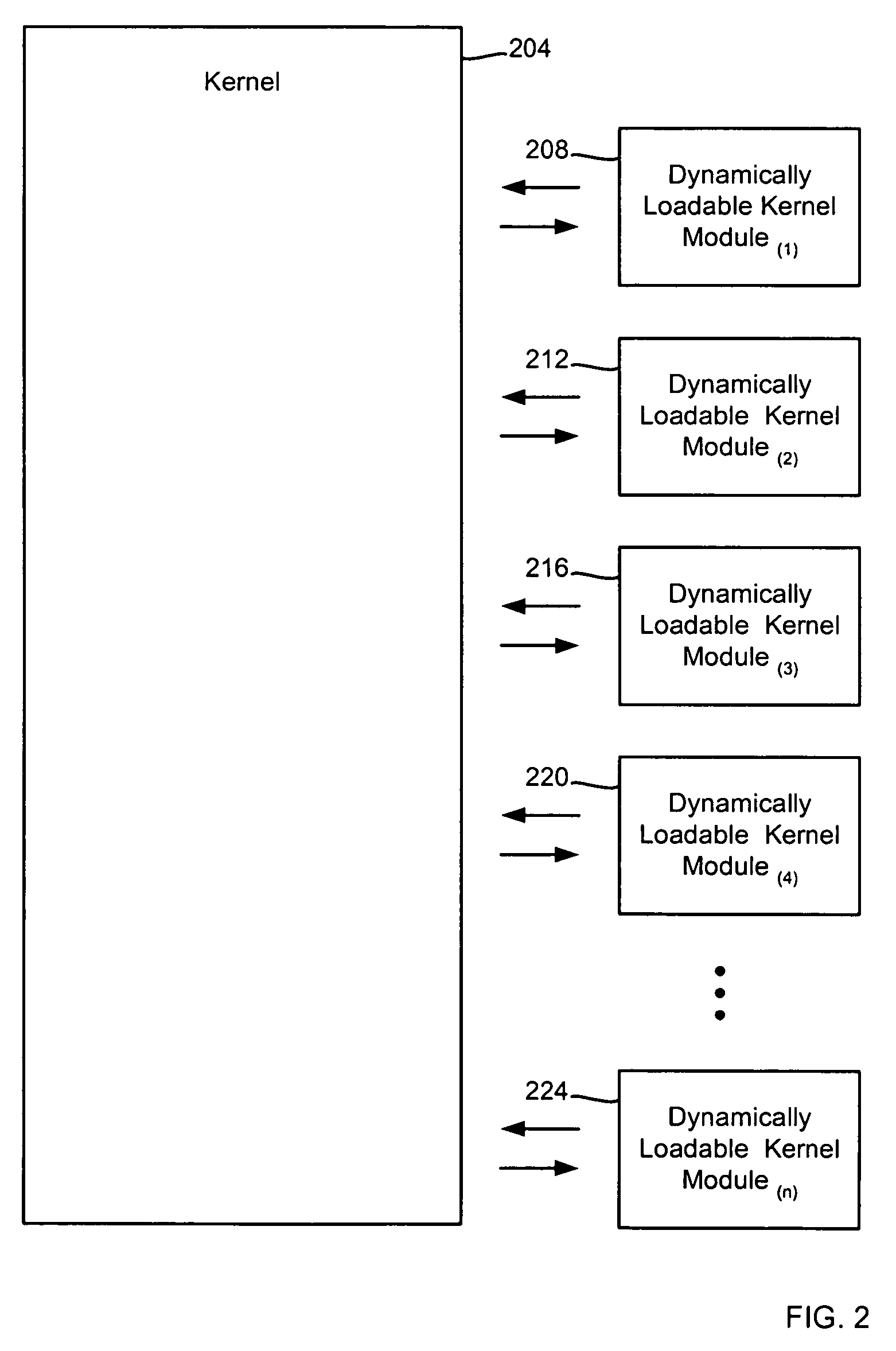
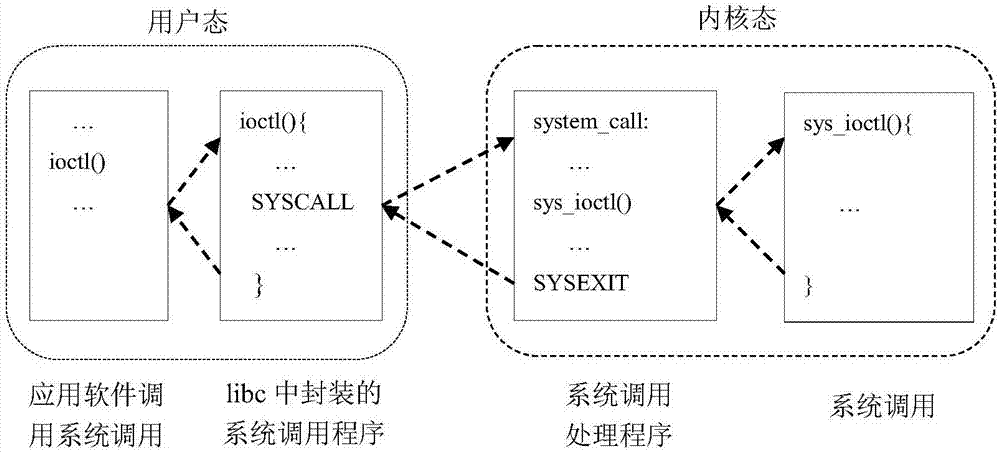
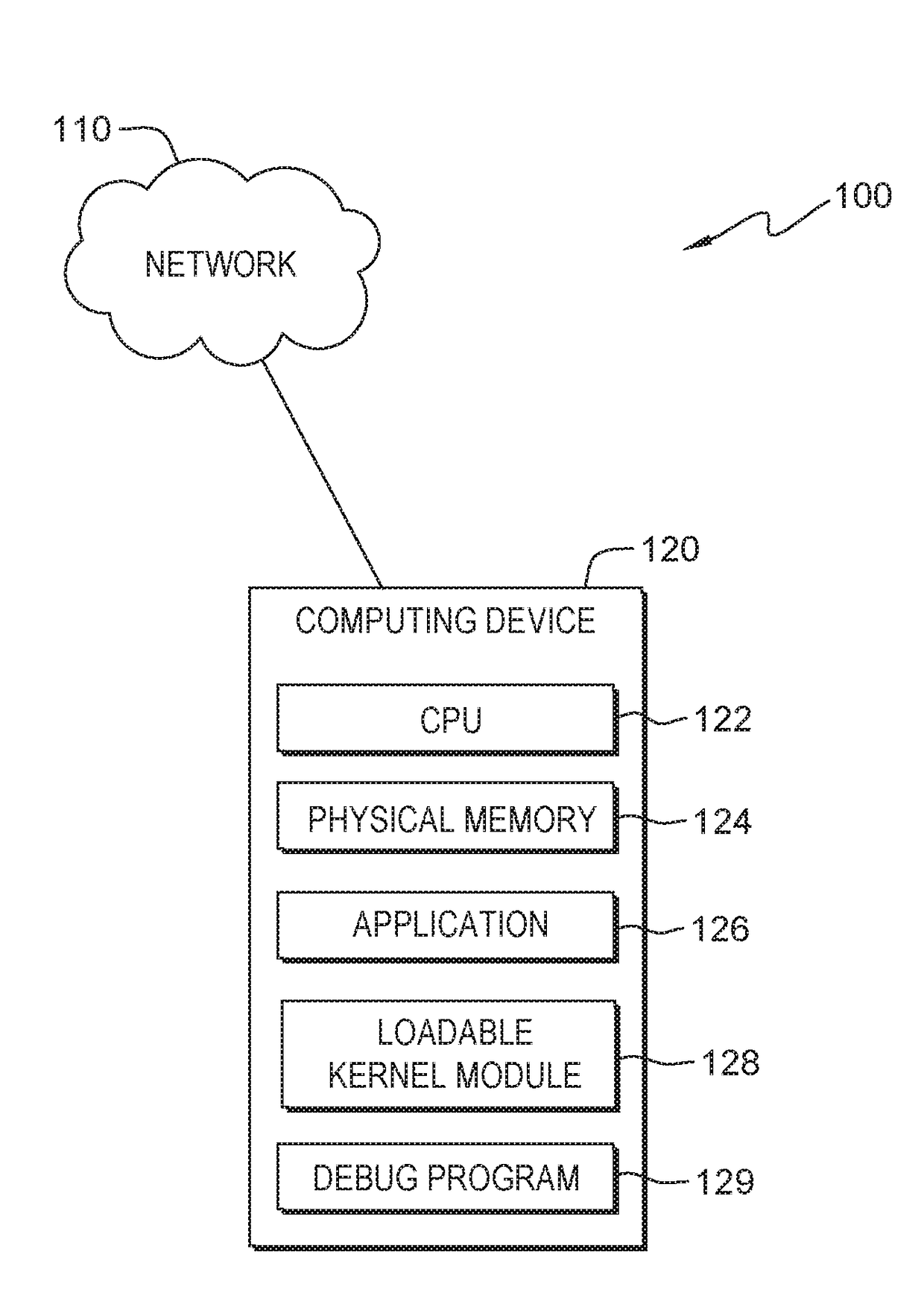
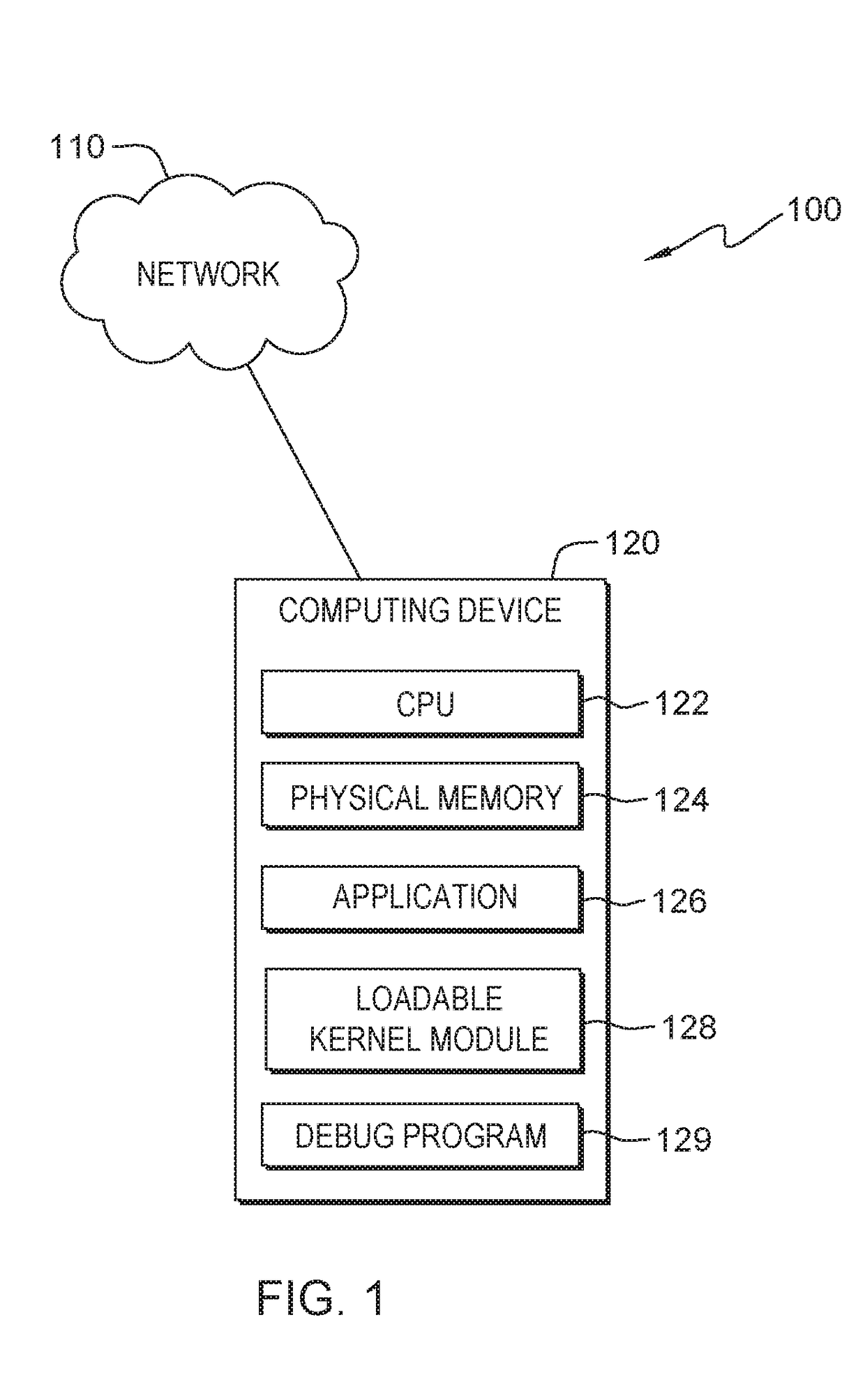
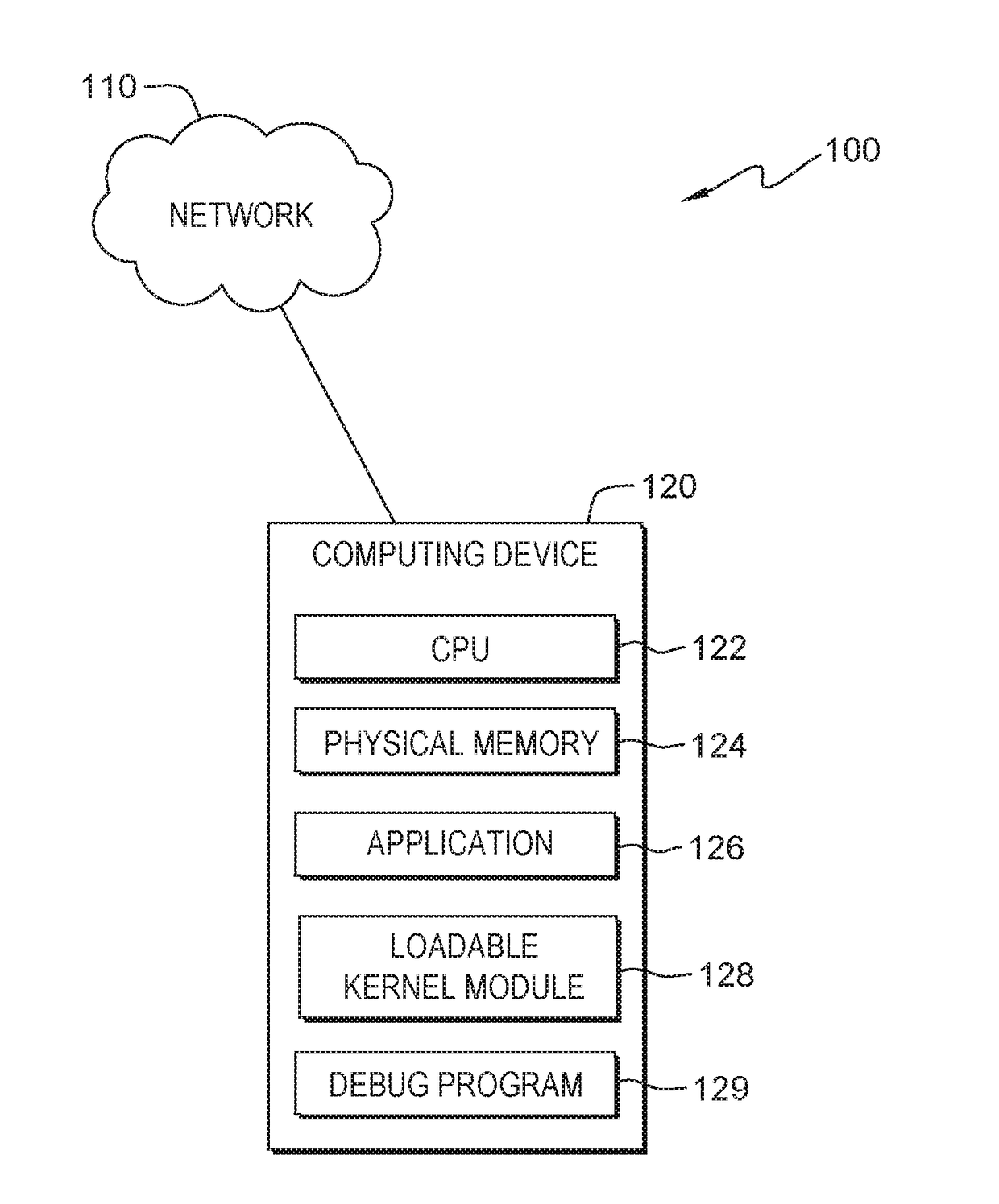
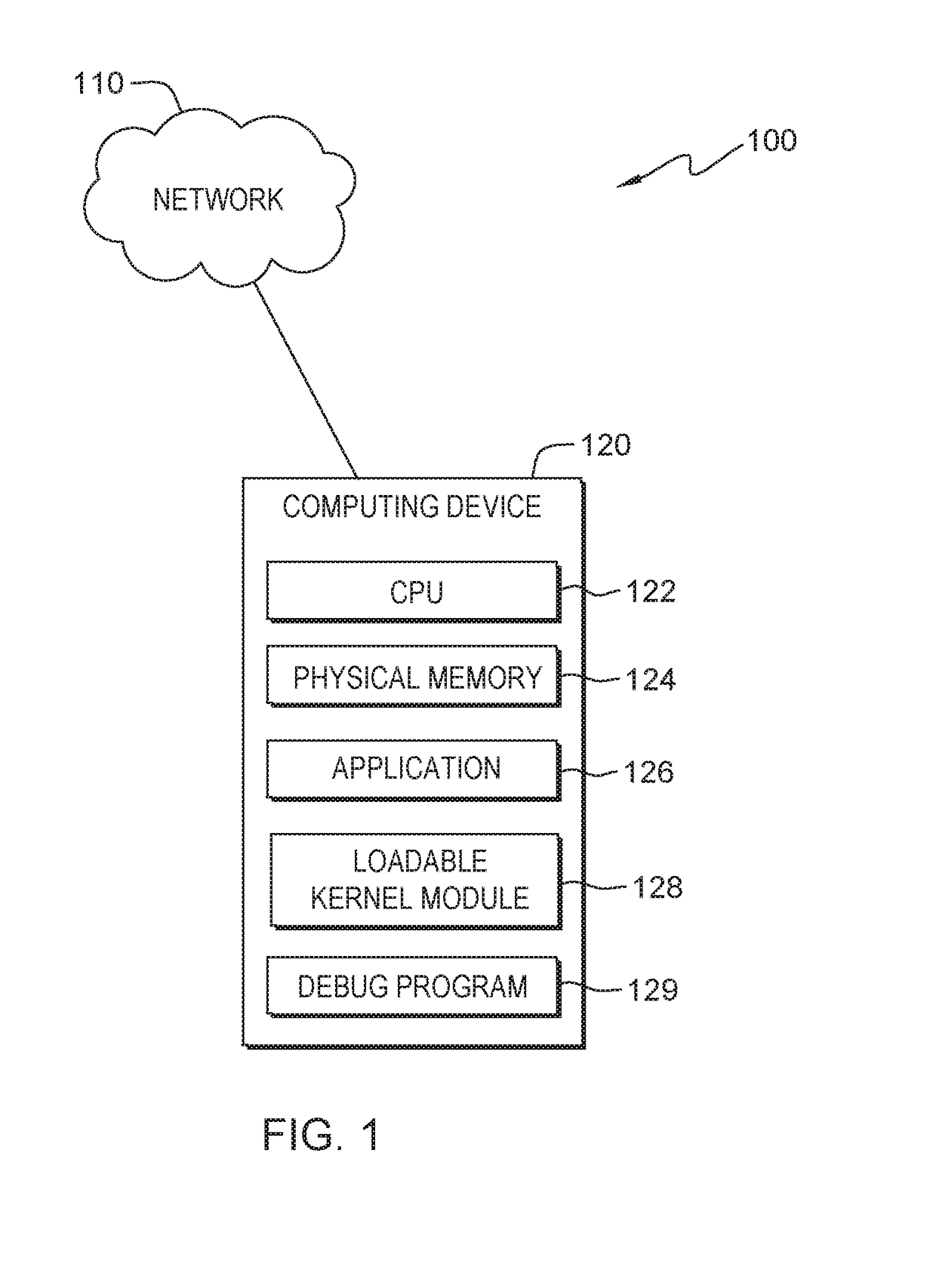
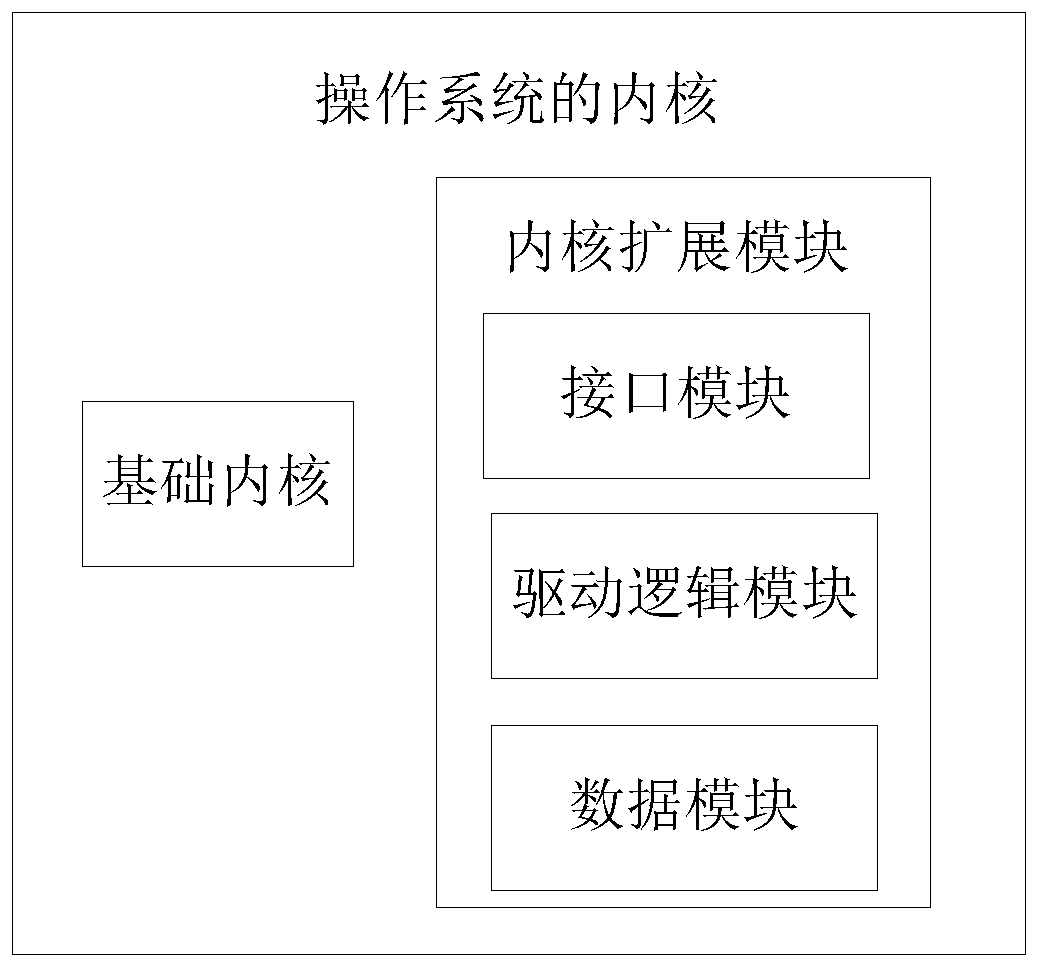
In computing, a loadable kernel module (LKM) is an object file that contains code to extend the running kernel, or so-called base kernel, of an operating system. LKMs are typically used to add support for new hardware (as device drivers) and/or filesystems, or for adding system calls. When the functionality provided by a LKM is no longer required, it can be unloaded in order to free memory and other resources.
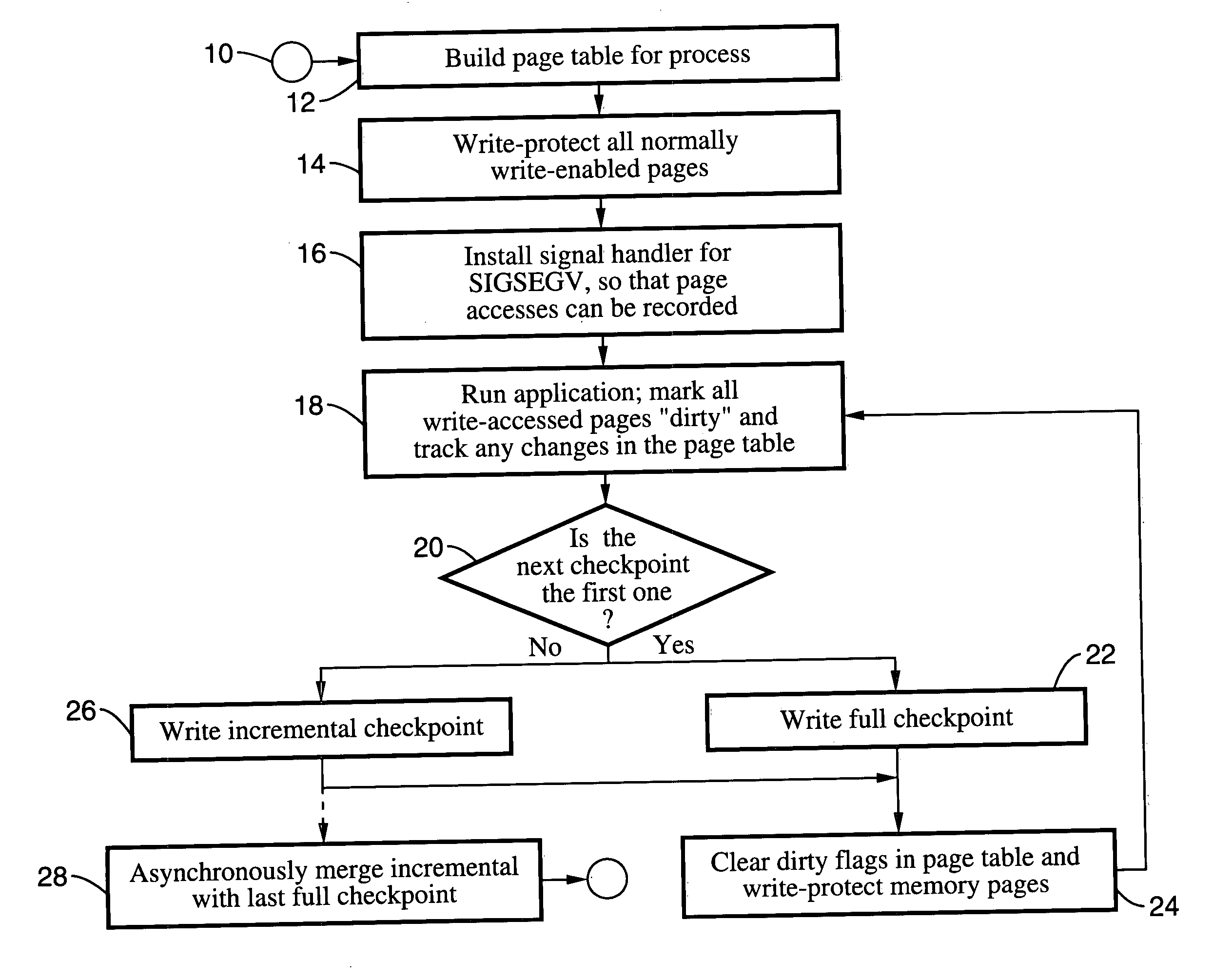
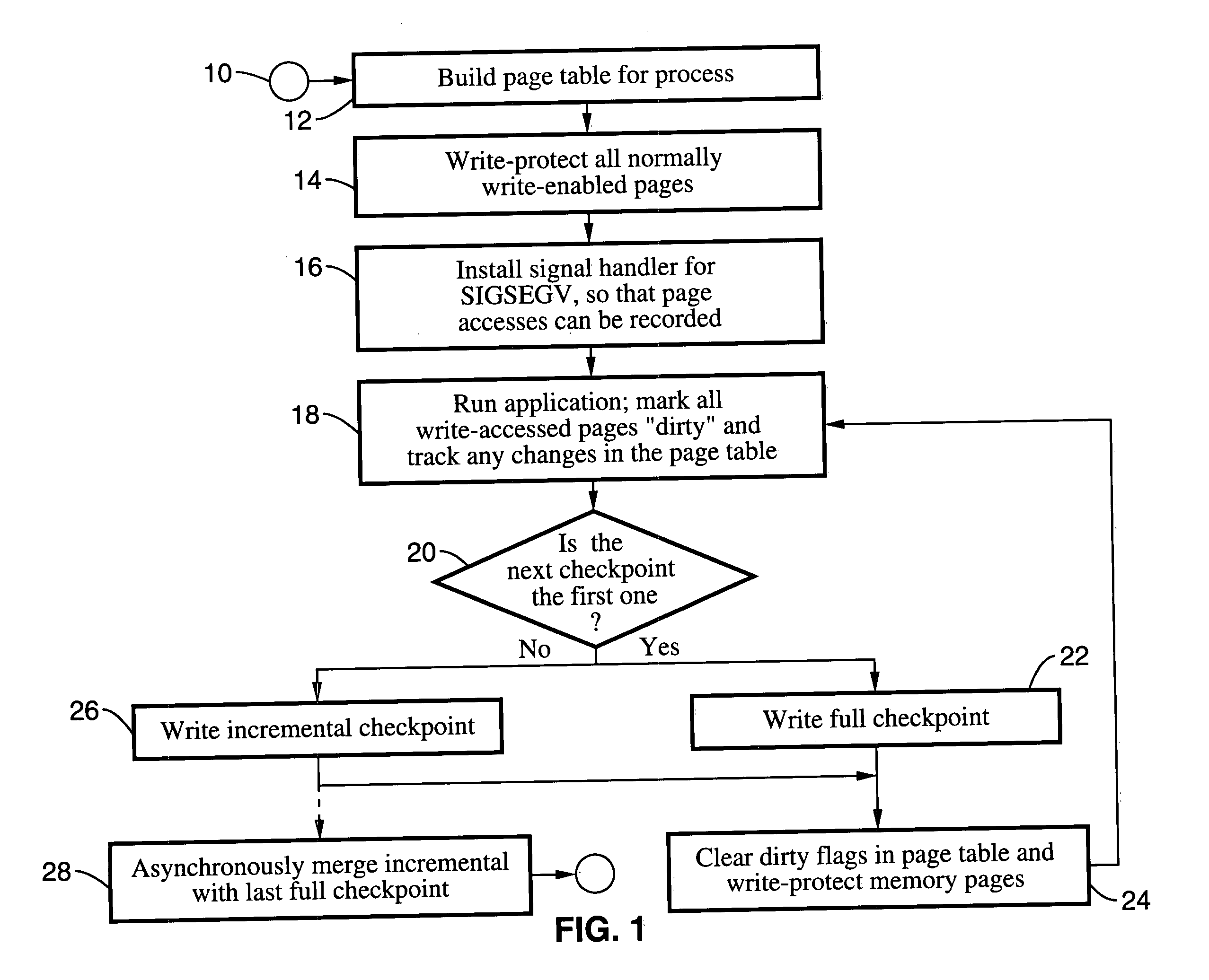
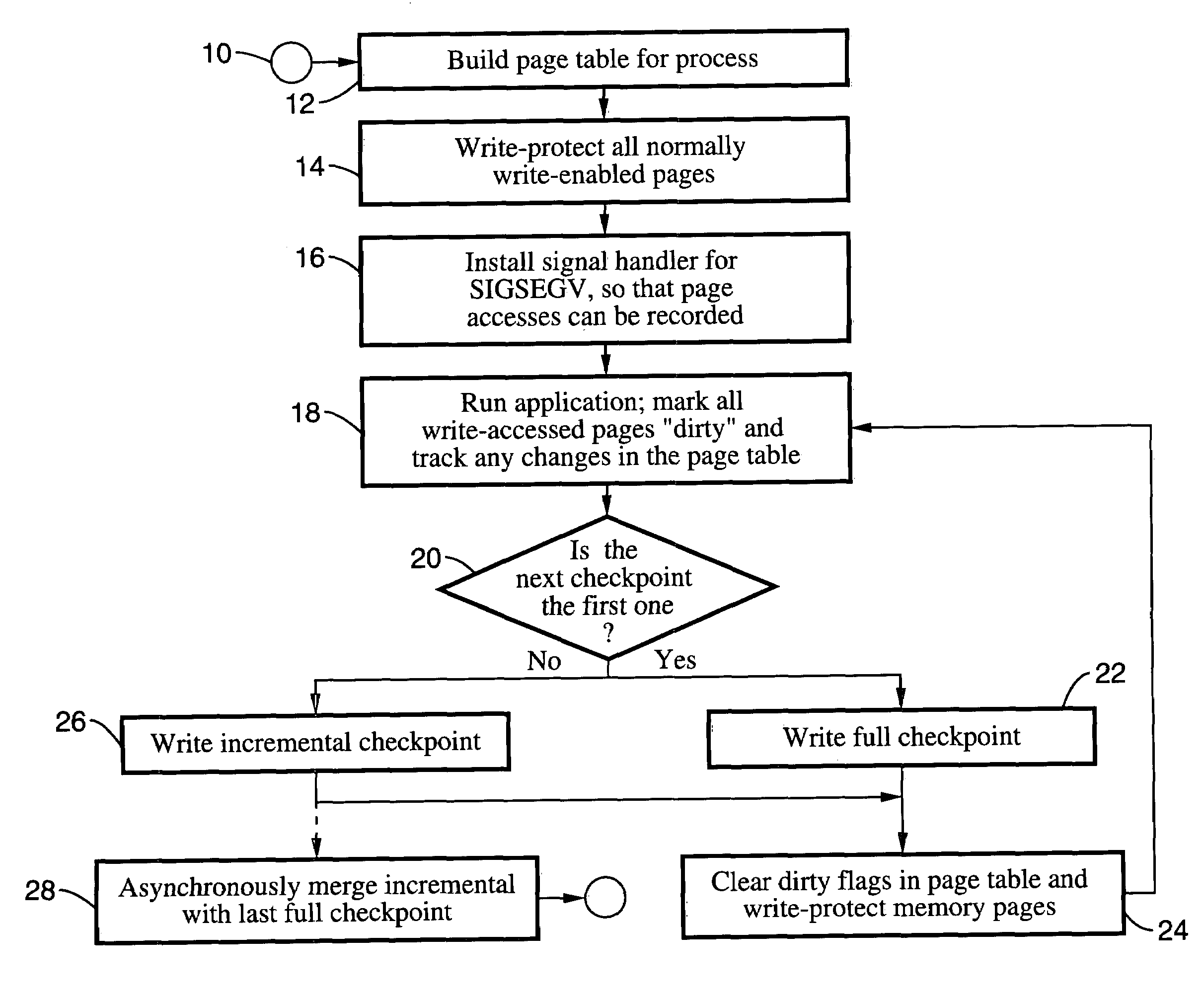
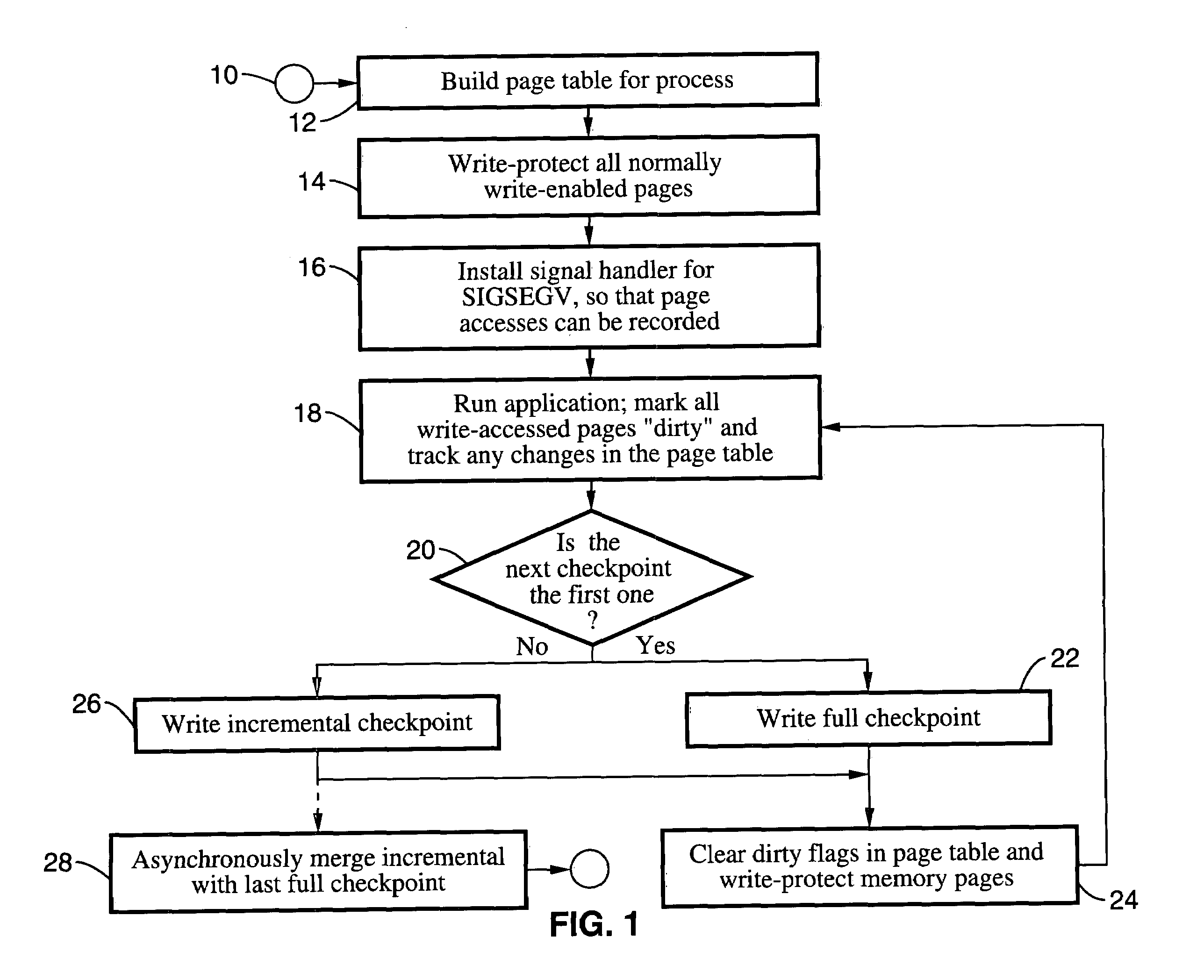
Method and system for providing transparent incremental and multiprocess checkpointing to computer applications
Incremental single and multiprocess checkpointing and restoration is described, which is transparent in that the application program need not be modified, re-compiled, or re-linked to gain the benefits of the invention. The processes subject to checkpointing can be either single or multi-threaded. The method includes incremental page-boundary checkpointing, as well as storage checkpointing of data files associated with applications to ensure correct restoration without the need to restore files for other application programs. Incremental and full checkpoints are asynchronously merged to ensure proper operation while reducing checkpointing delay. By way of example a user-level programming library is described for loading into the address space of the application in conjunction with a loadable kernel module (LKM) or device driver used to capture and restore process state on behalf of the application. These techniques are particularly well suited for use with high-availability (HA) protection programming.
Owner:RED HAT
Method and system for providing transparent incremental and multiprocess checkpointing to computer applications
Incremental single and multiprocess checkpointing and restoration is described, which is transparent in that the application program need not be modified, re-compiled, or re-linked to gain the benefits of the invention. The processes subject to checkpointing can be either single or multi-threaded. The method includes incremental page-boundary checkpointing, as well as storage checkpointing of data files associated with applications to ensure correct restoration without the need to restore files for other application programs. Incremental and full checkpoints are asynchronously merged to ensure proper operation while reducing checkpointing delay. By way of example a user-level programming library is described for loading into the address space of the application in conjunction with a loadable kernel module (LKM) or device driver used to capture and restore process state on behalf of the application. These techniques are particularly well suited for use with high-availability (HA) protection programming.
Owner:RED HAT
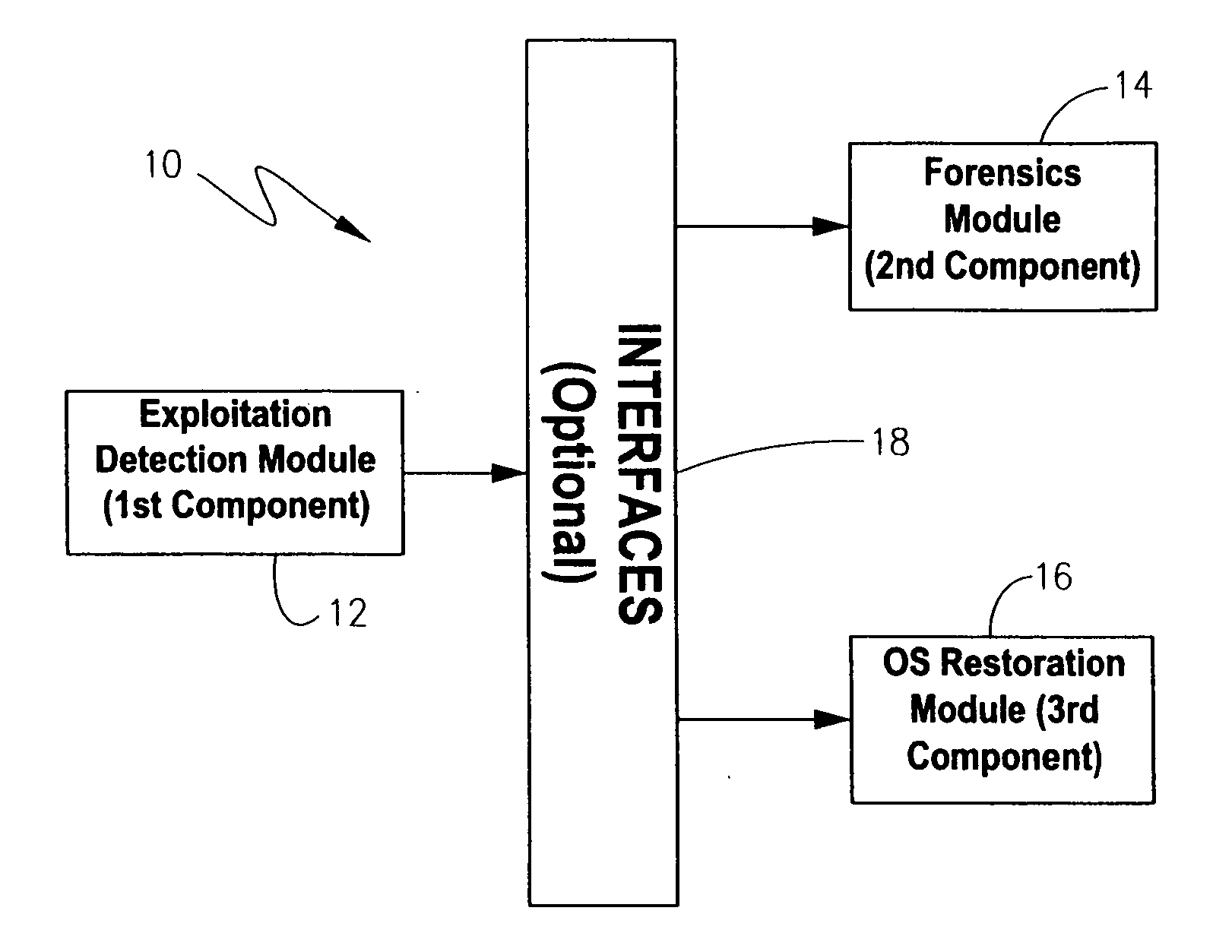
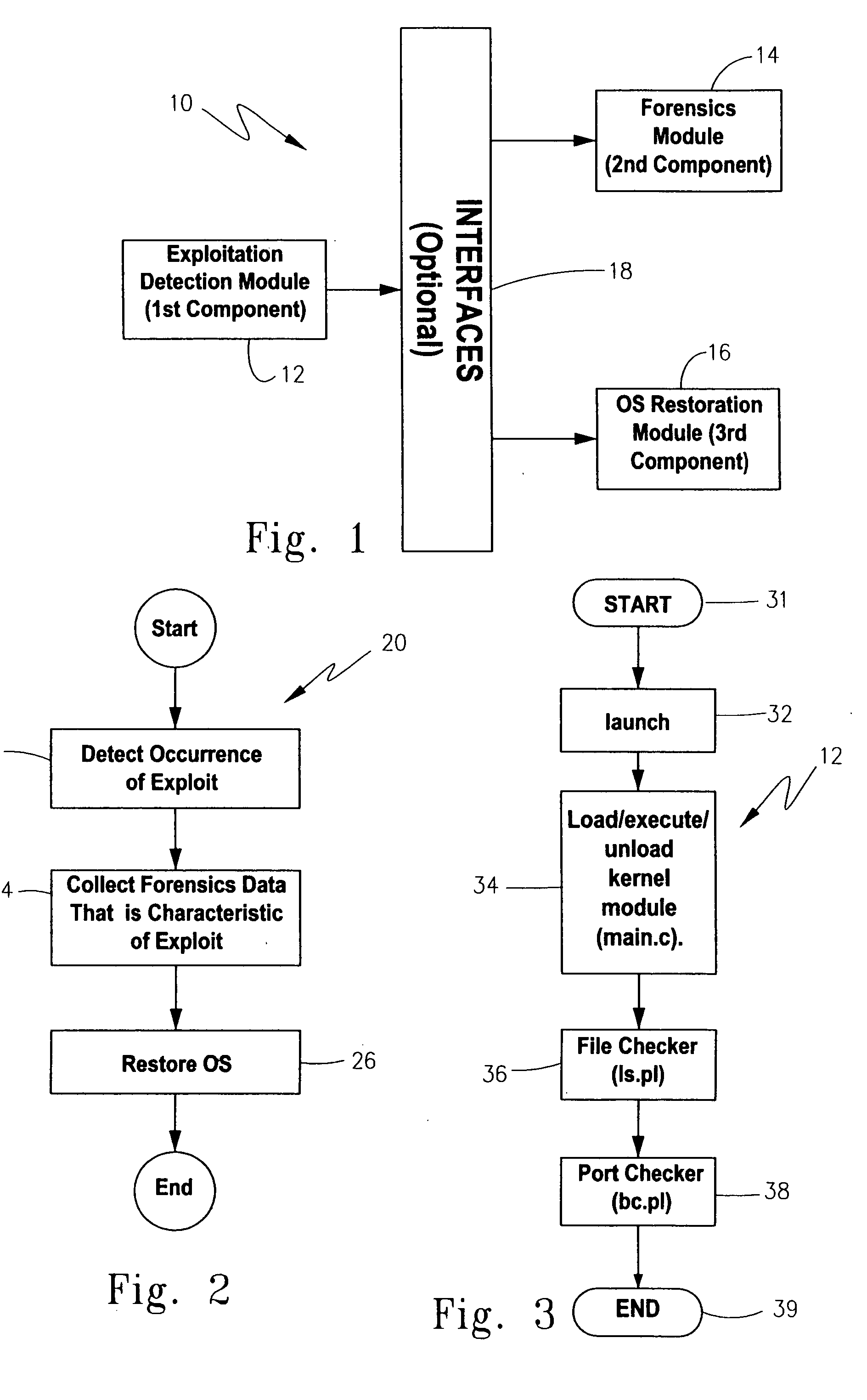
Methodology, system, and computer readable medium for detecting operating system exploitations
InactiveUS20050204205A1Error detection/correctionUnauthorized memory use protectionOperational systemOperating system
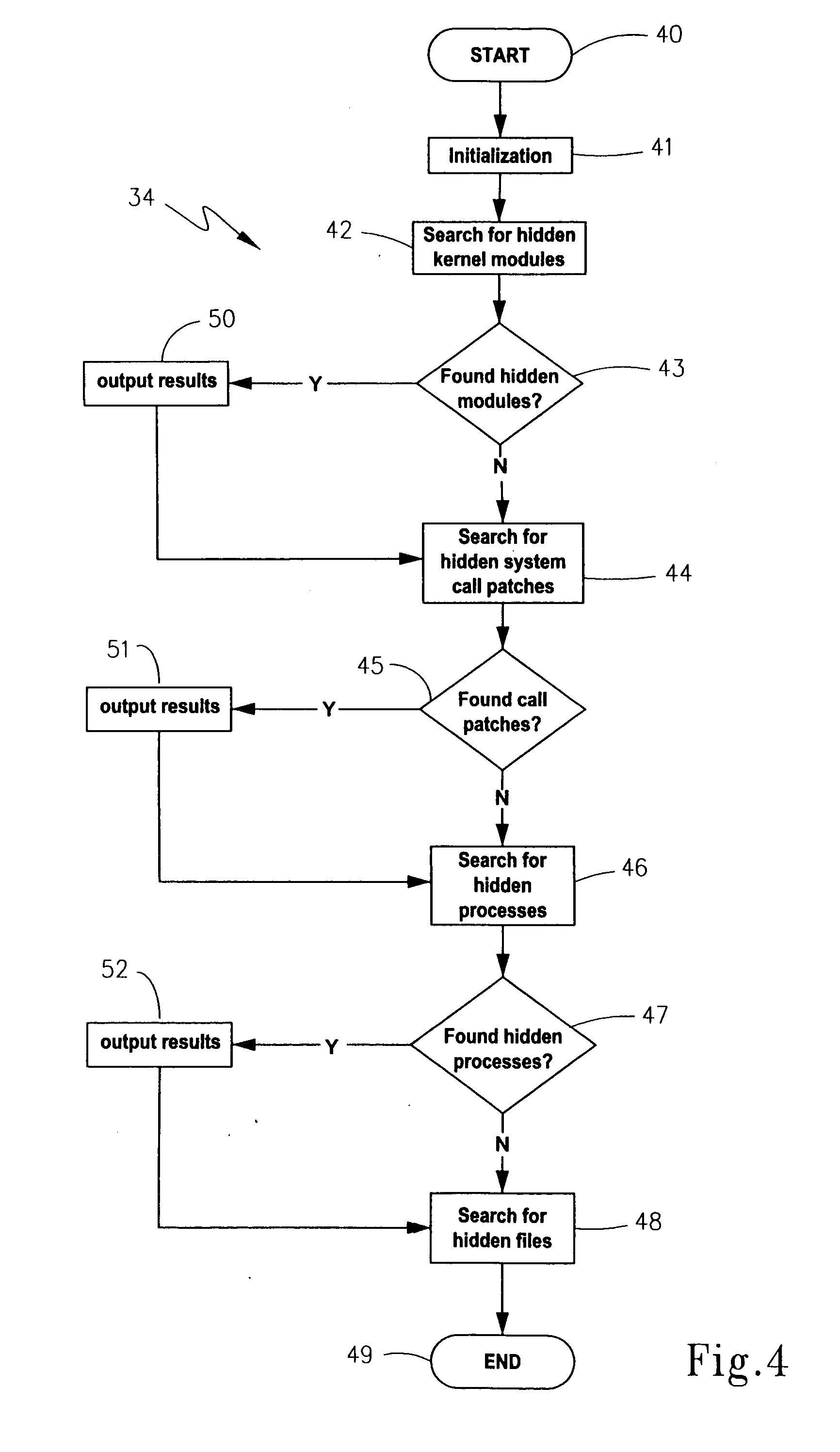
A system, computerized method and computer-readable medium are provided for the detection of an operating system exploitation, such as a rootkit install. The operating system is monitored to ascertain an occurrence of anomalous activity resulting from operating system behavior which deviates from any one of a set of pre-determined operating system parameters. Each parameter corresponds to a dynamic characteristic associated with an unexploited operating system. Output can then be generated to indicate any anomalous activity that is ascertained. The computer-readable medium may comprise a loadable kernel module for detecting hidden patches, processes, files or other kernel modules.
Owner:RING SANDRA E +1
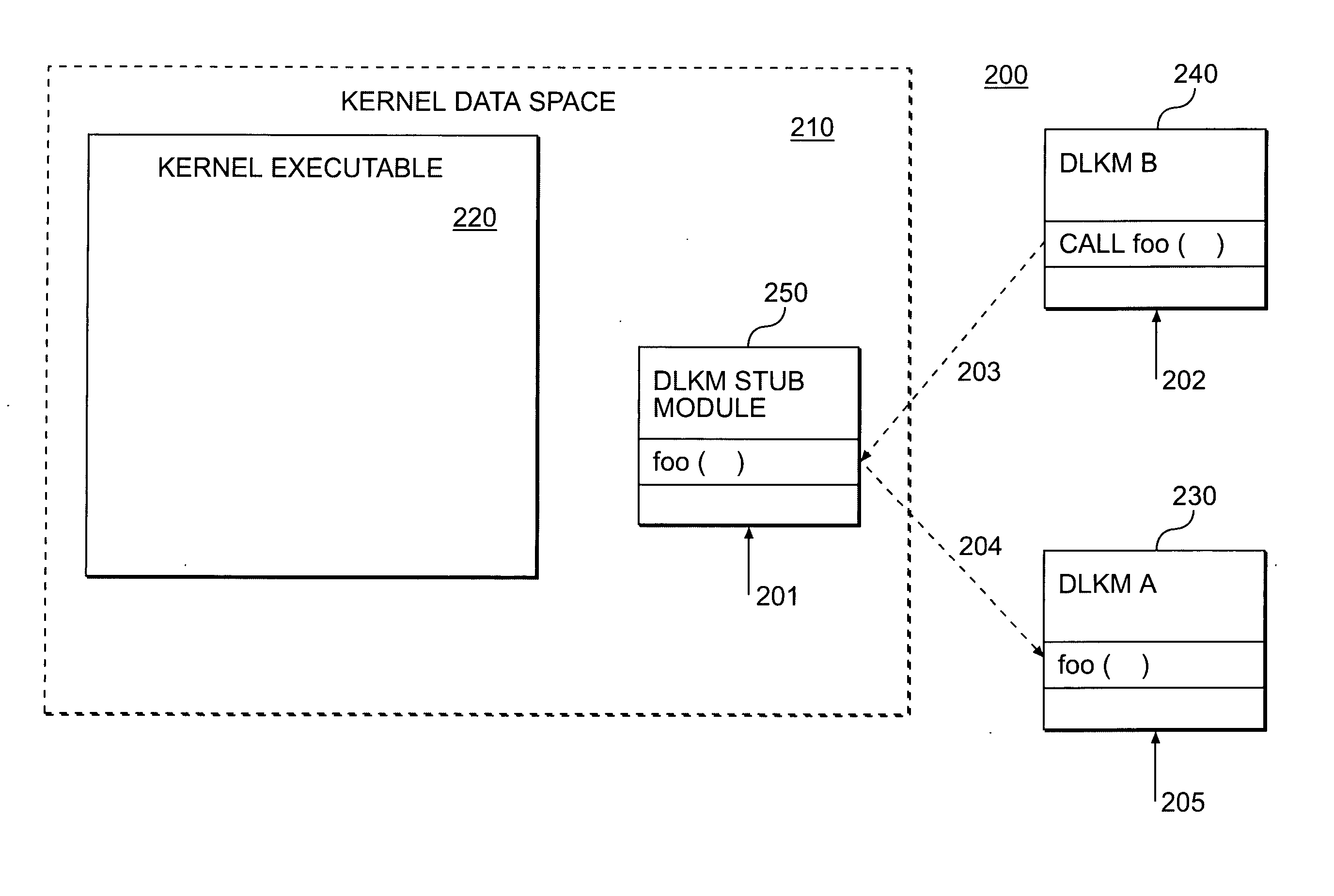
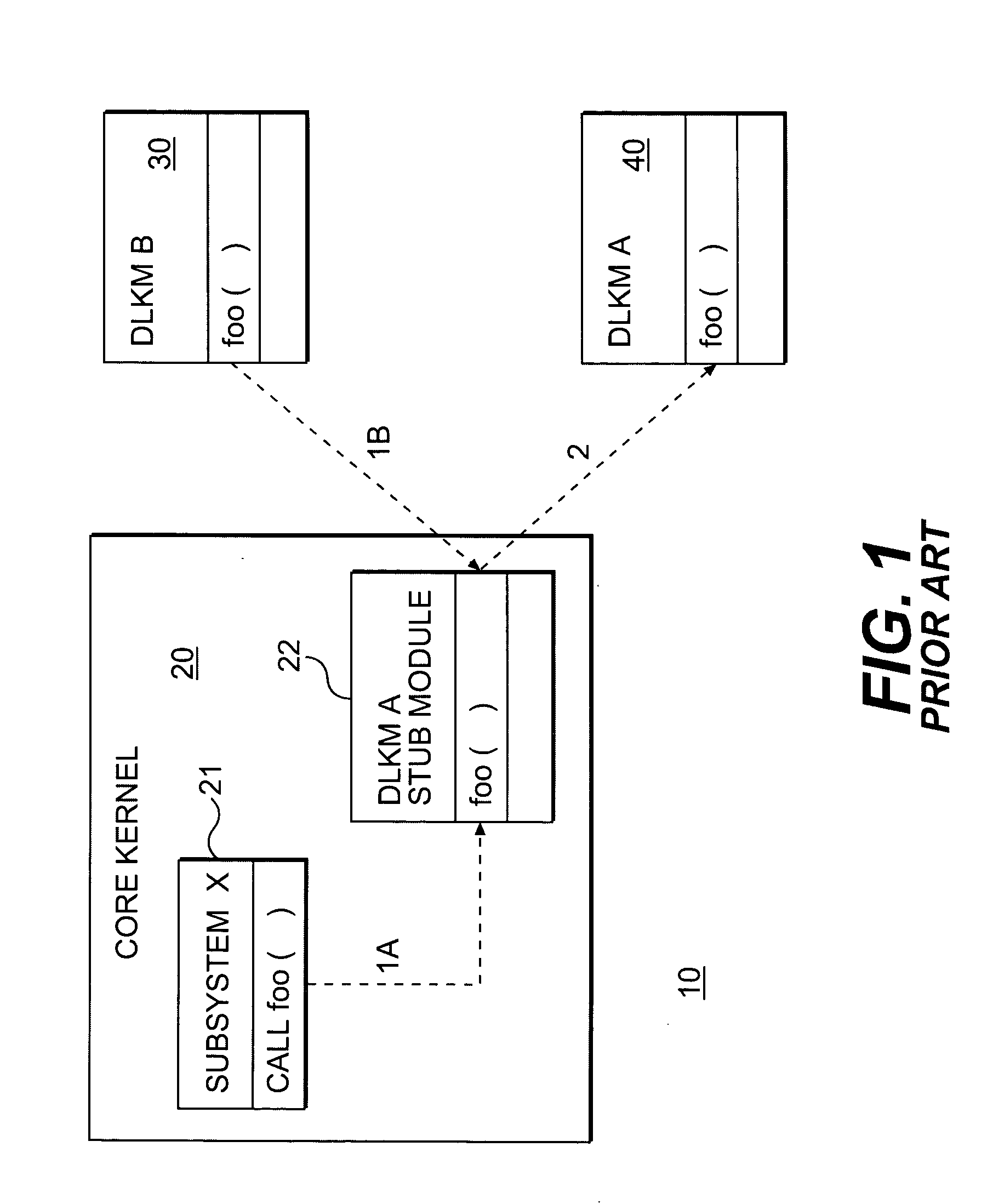
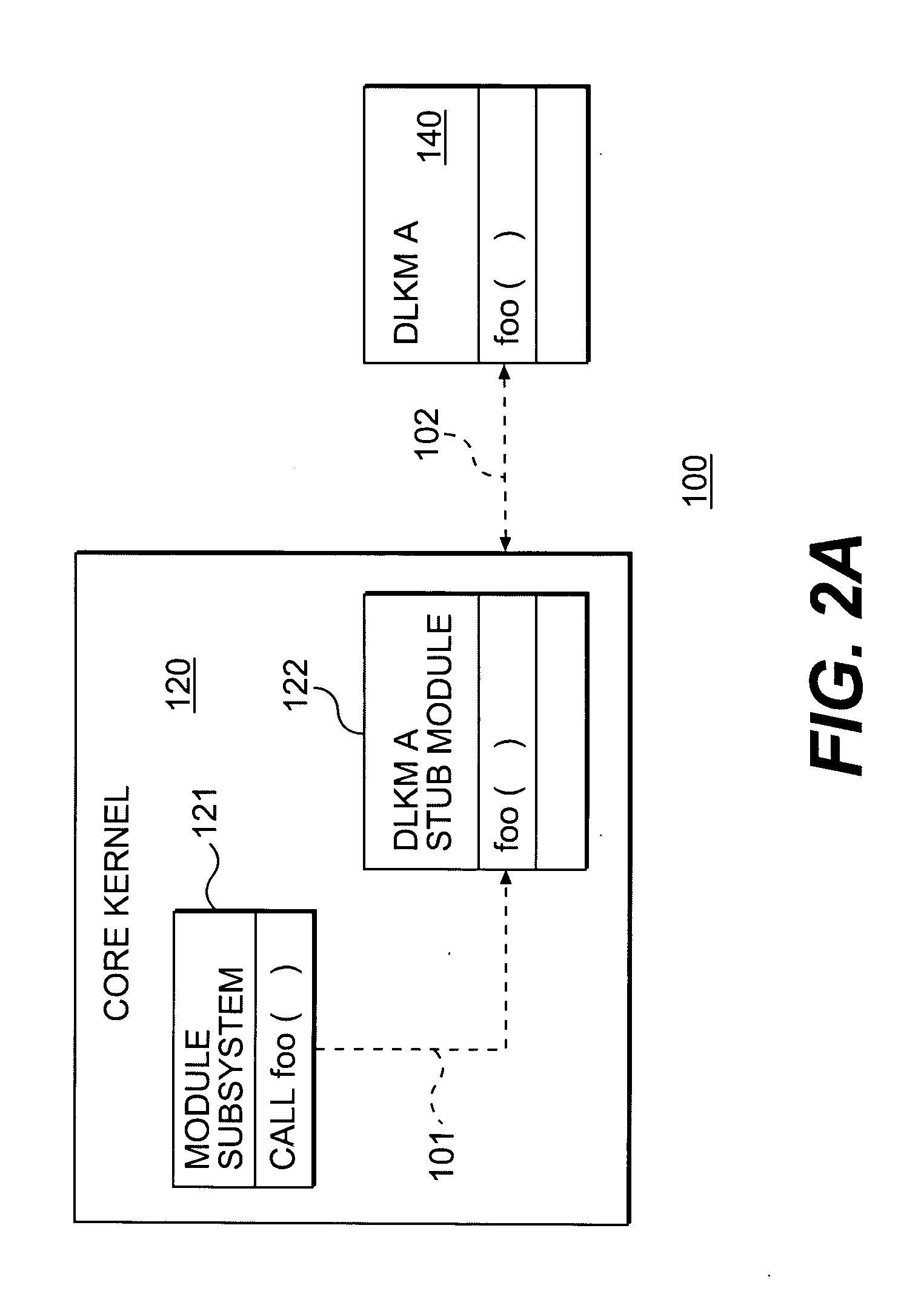
Dynamically loadable stub modules
InactiveUS20050071856A1Multiprogramming arrangementsProgram loading/initiatingComputer hardwareWrapper function
A dynamically loadable stub module, associated with a dynamically loadable kernel module (DLKM) includes a base stub module, means for defining DLKM data structures and wrapper functions, means for defining load and unload routines, means for defining metadata structures, means for allowing dynamic loading by DLKM infrastructures, and means for generating a dynamically loadable stub module object file.
Owner:HEWLETT PACKARD DEV CO LP
File systems accessing register dynamic collection method
InactiveCN101216850AImprove usabilityReduce sizeHardware monitoringSpecial data processing applicationsFile systemSystem testing
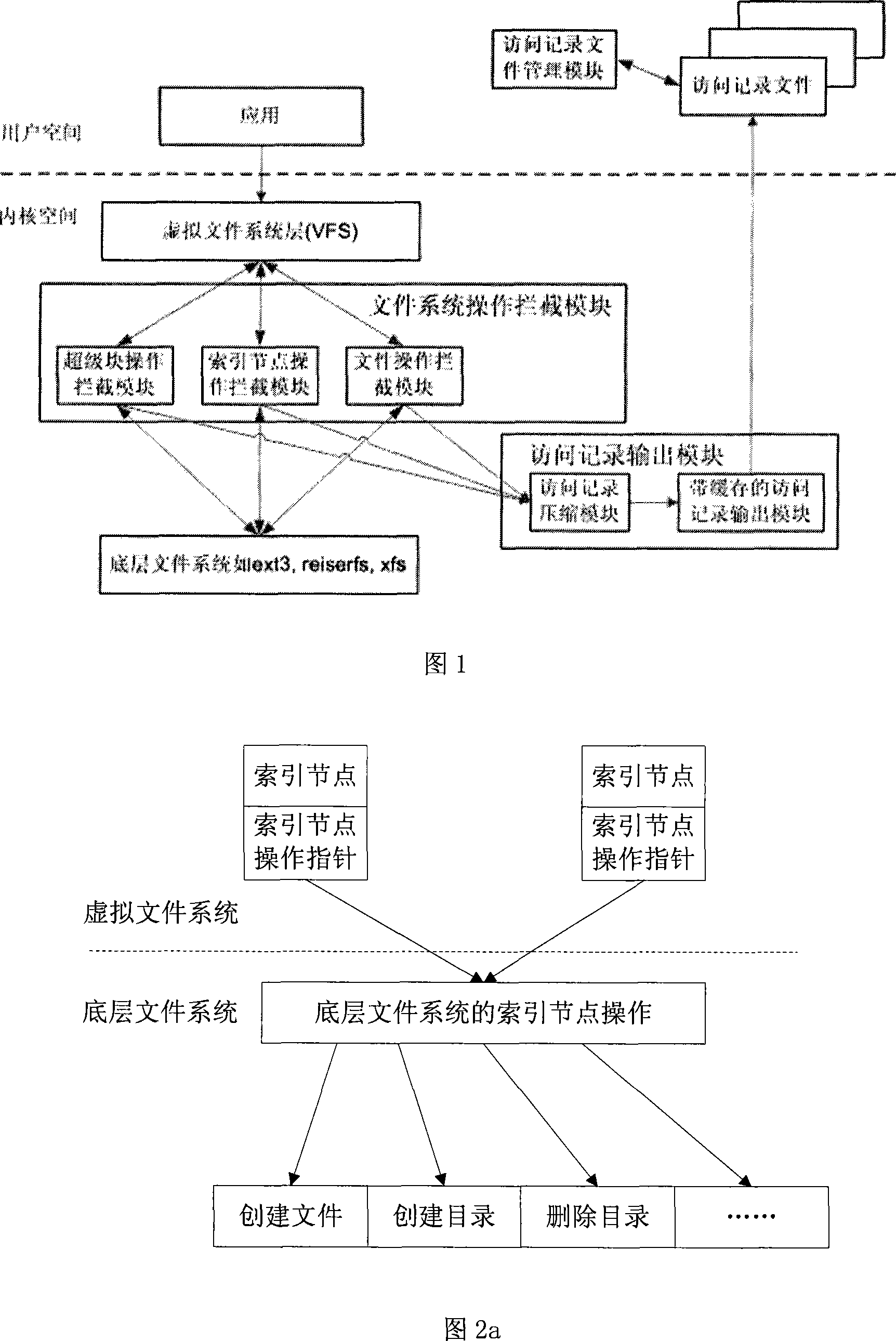
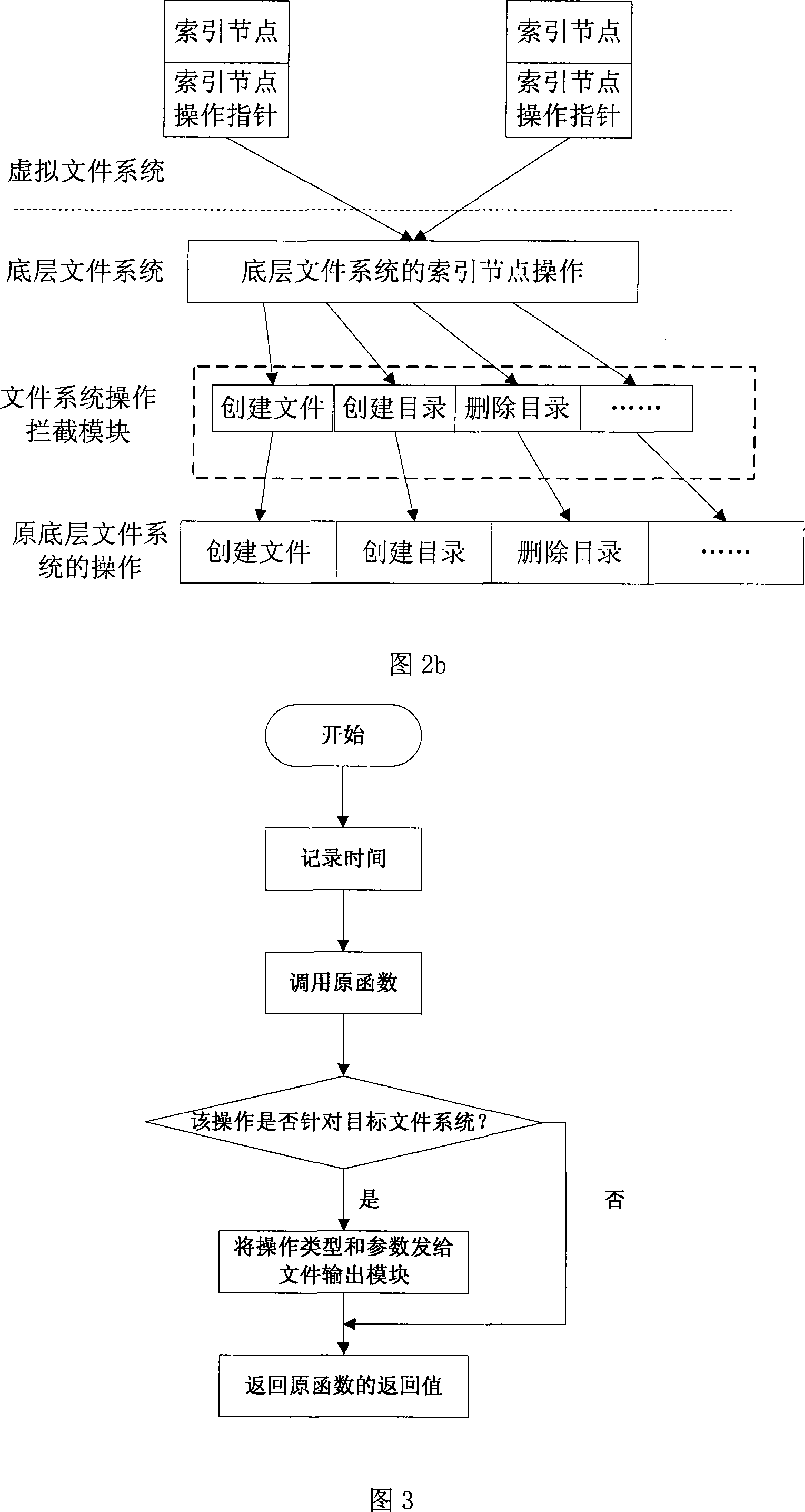
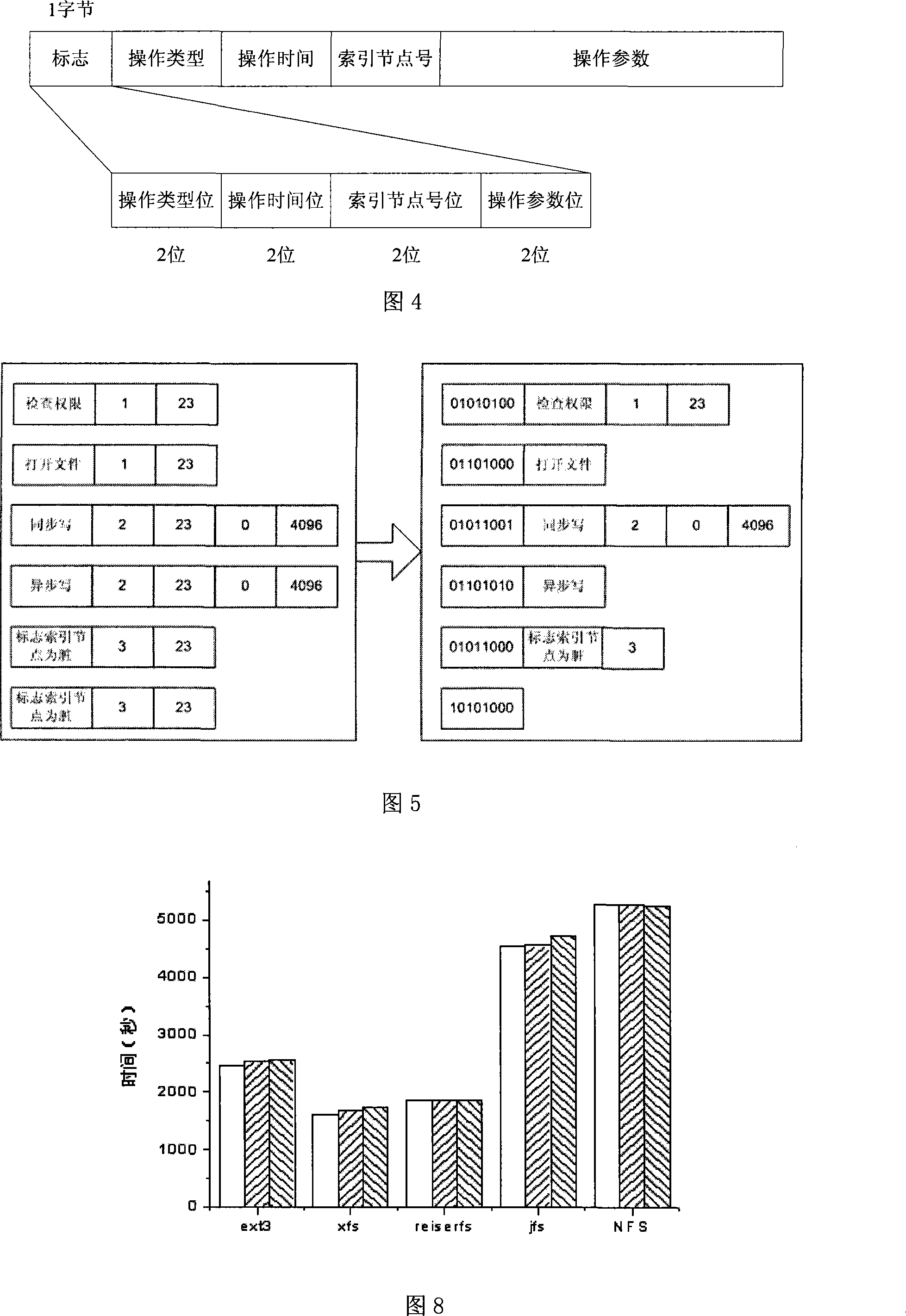
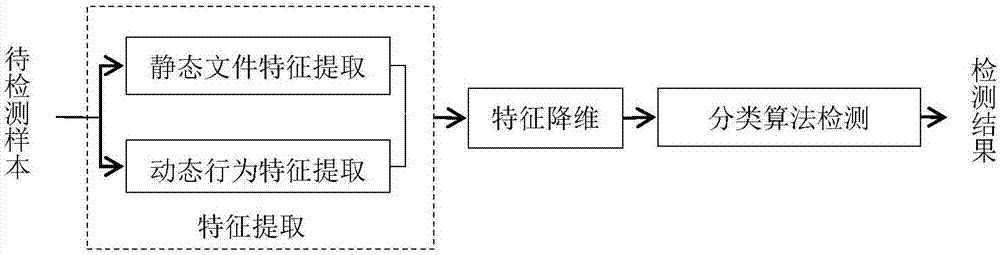
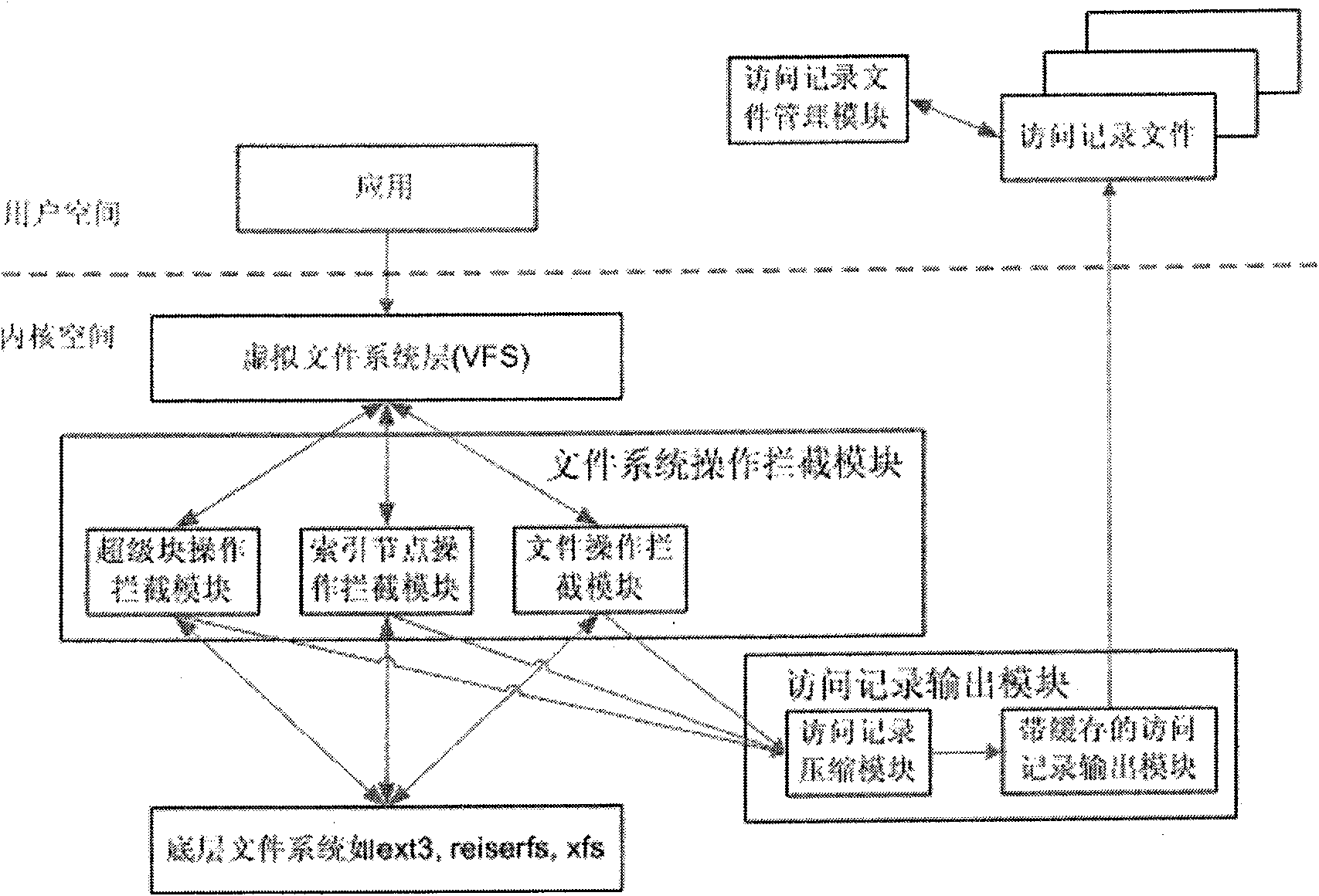
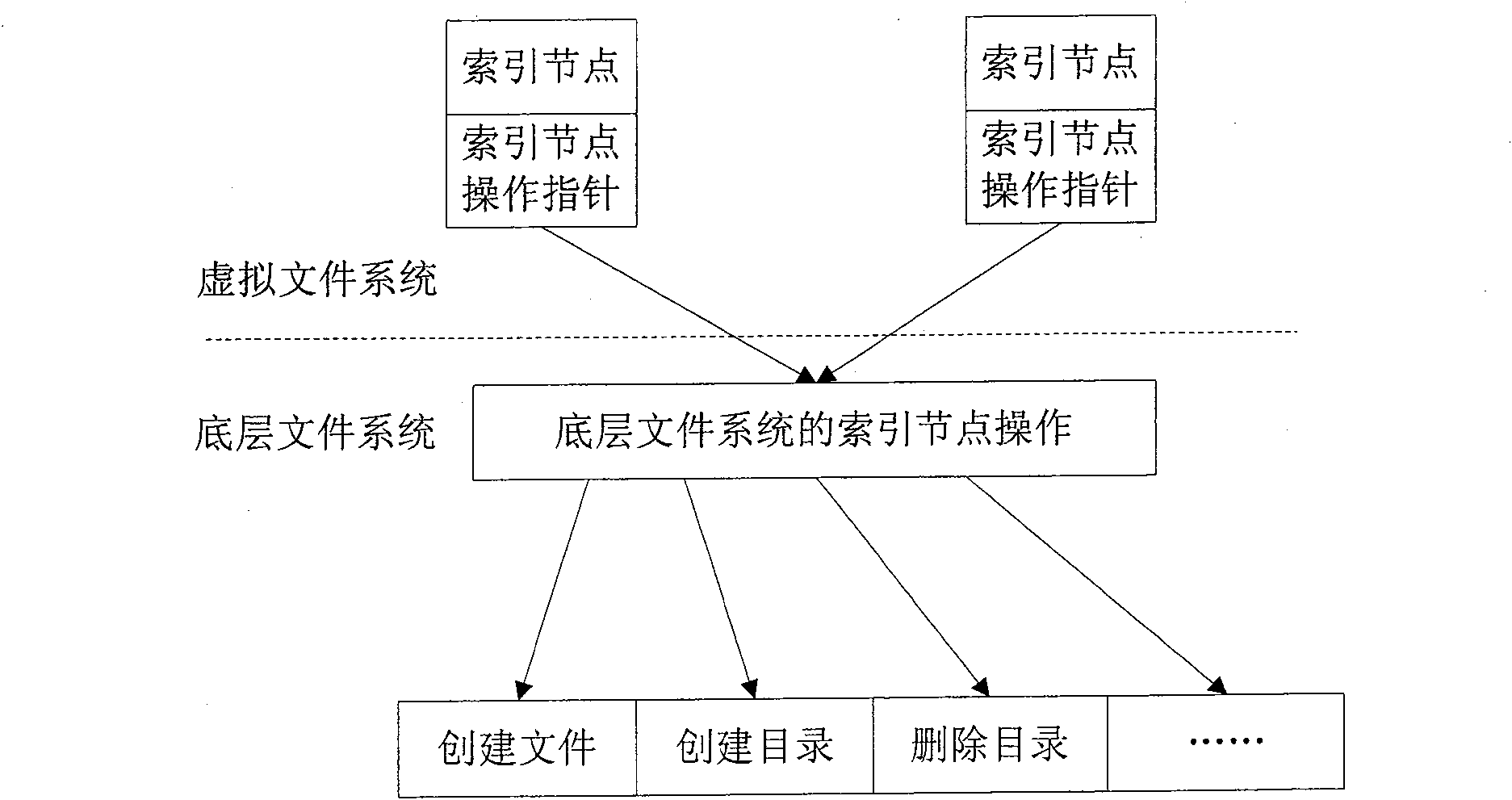
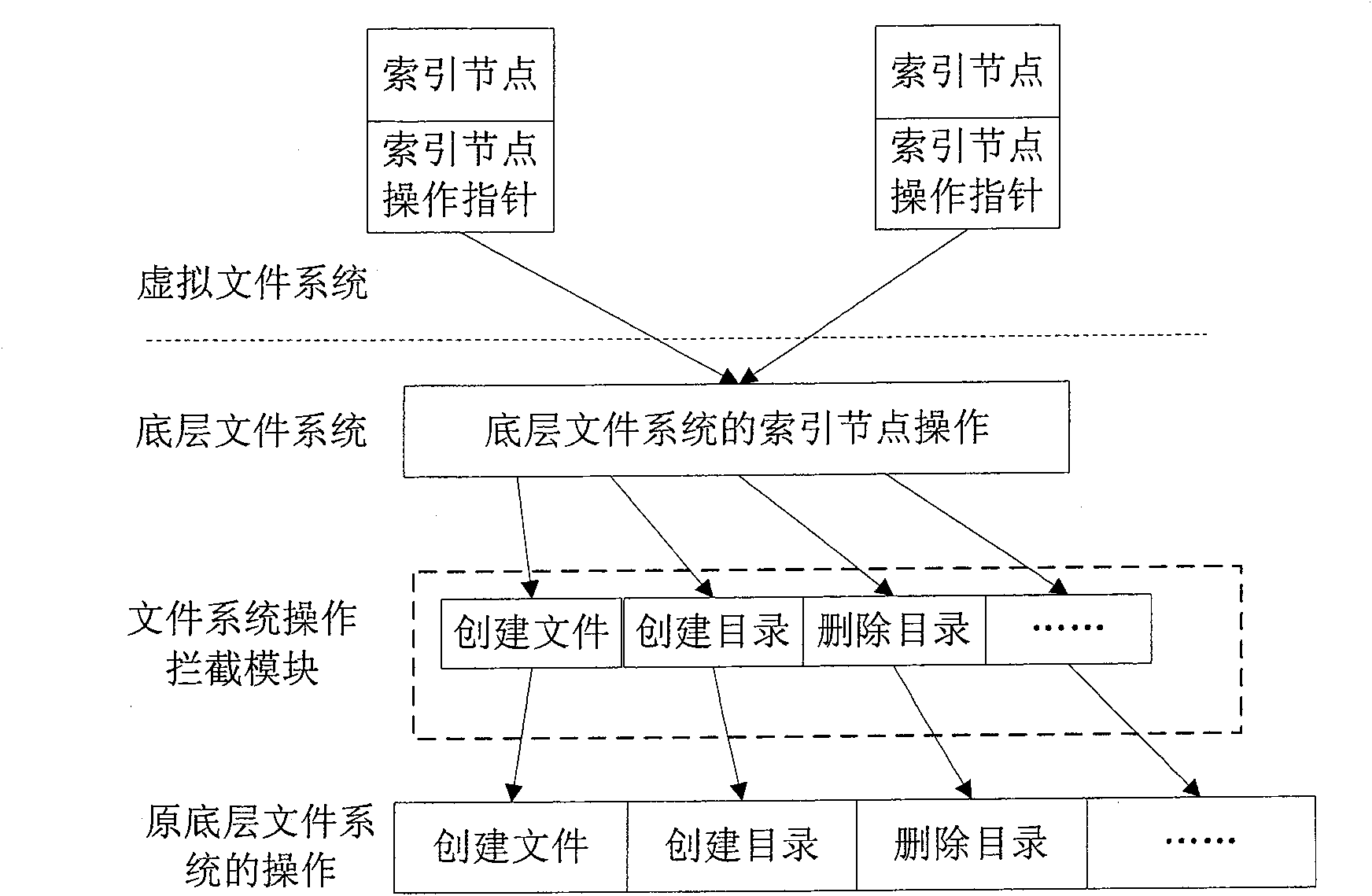
The invention discloses a dynamic acquisition method of file system access record, belonging to the field of storage system testing and performance analysis. The invention is characterized in that a kernel module can be loaded without the need of unloading the old file system, thus not needing to interrupt the working application. A file system operation interception module can dynamically intercept the underlayer file system operation by a substitution of corresponding functions in the interception module. While executing the underlayer file system operation, the functions output the operation type and parameters to an access record output module which compresses the file record and outputs a plurality of operation information at one time in a output record way of register. The access record output module controls the output file size to prevent the problems of difficult read and write and exceeding file system restriction. An access record file management module collects additional information and packages and transfers the access record according to the assignment of users, thus being convenient for users to manage. The test shows that the collection of access record has little impact on the application.
Owner:TSINGHUA UNIV
An Android unknown malicious software detection method based on dynamic behavior characteristics
InactiveCN107169351AWell representedImprove accuracyPlatform integrity maintainanceSoftware engineeringMalware
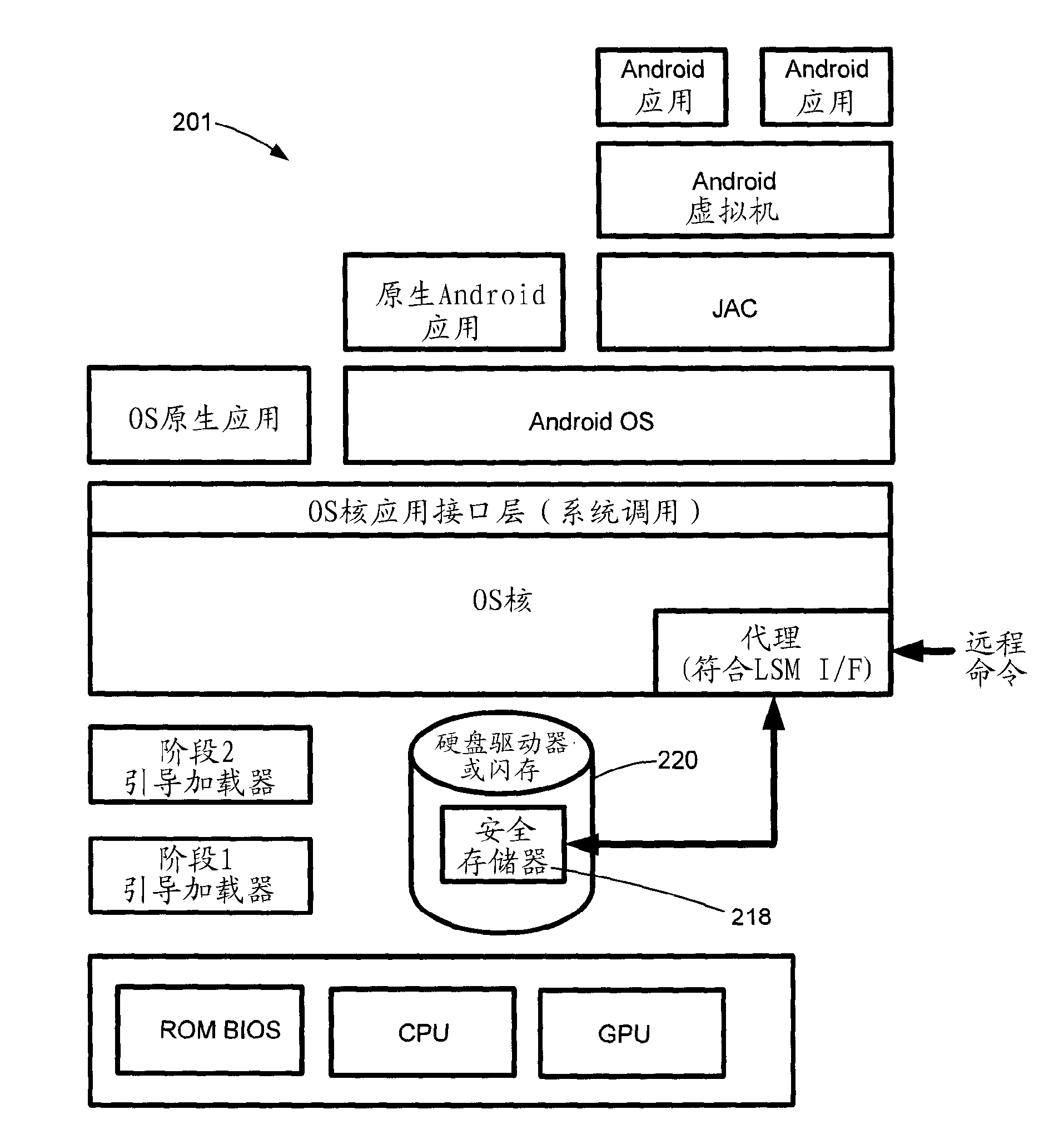
The invention relates to an Android unknown malicious software detection method based on dynamic behavior characteristics and belongs to the technical field of computers and information science. The method comprises the steps that to-be-detected software is input into a system; the system uncompresses and decompiles a software package and extracts static characteristics in a result file; at the same time, the system operates the software package in an Android simulator and monitors dynamic behavior of the software by using a behavior monitoring system based on an LKM (Loadable Kernel Module); the dynamic behavior is recorded in logs and the dynamic behavior characteristics of the software are extracted from the logs; the extracted dynamic and static characteristics are subjected to normalization processing and the results are input into a trained classification algorithm classification detection module; the module can automatically judge whether the detected software is malicious software or not according to the input dynamic and static characteristic data. The method has high detection efficiency and accuracy and can be applied to security detection of software platforms such as the Android application market.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Memory allocation with identification of requesting loadable kernel module
InactiveUS20120005445A1Error detection/correctionMemory adressing/allocation/relocationTerm memoryOperating system
Owner:IBM CORP
Methods and tools for executing and tracing user-specified kernel instructions
InactiveUS20060174229A1Error detection/correctionSpecific program execution arrangementsPresent methodParallel computing
Embodiments of the present invention present methods of tracing kernel functions of a kernel including: building a kernel tracing dynamically loadable kernel module (DLKM) wherein the kernel tracing DLKM contains user-specified kernel code; loading the kernel tracing DLKM on a target machine; invoking the kernel tracing DLKM on the target machine; and tracing kernel functions wherein trace variables are gathered. In some embodiments, the method may further include: creating user-specified kernel code wherein at least one kernel activity may be inspected or tested; creating at least one trace point corresponding to a point at which the kernel tracing DLKM is invoked; and compiling the kernel tracing DLKM.
Owner:HEWLETT PACKARD DEV CO LP
Method for implementing user mode drive program in embedded Linux
InactiveCN103593189AImprove encoding qualityIncrease overheadProgram loading/initiatingOperational systemGNU/Linux
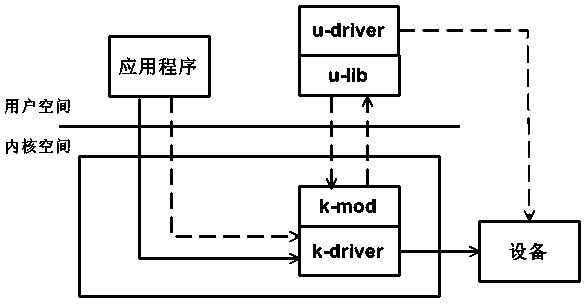
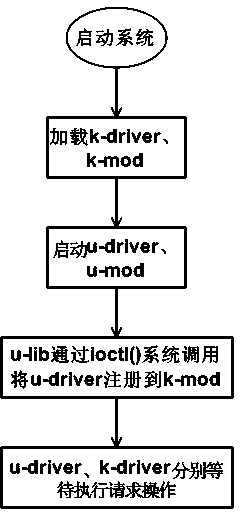
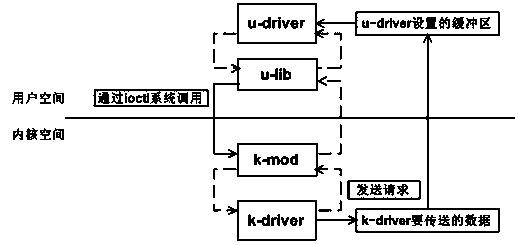
The invention relates to a method for implementing a user mode drive program in an embedded Linux, and belongs to the technical field of embedded operating systems. The method for implementing the user mode drive program in the embedded Linux comprises the specific steps of carrying out separation on a traditional kernel mode drive program to form a k-driver component running in a kernel mode and a u-driver component running in a user mode according to whether performance is related or not and priorities, building a dynamic loadable kernel module k-mod in the kernel mode, and building a dynamic link library u-lib in the user mode. According to a user mode programming tool, a programmer is allowed to use universal mature programming tools such as a code debugger when carrying out programming, and coding quality is improved; better performance is achieved, and performance, such as the throughput, the delay and the CPU overhead, is similar to performance of the traditional kernel mode device drive program; fault isolation is achieved, and a fault occurring on a user layer component cannot influence a kernel, namely, safe operation of a whole system cannot be influenced; compatibility is achieved, the method for implementing the user mode drive program in the embedded Linux is compatible with an existing embedded Linux system, and the same interfaces are provided.
Owner:KUNMING UNIV OF SCI & TECH
Real-time remote backup system and related method
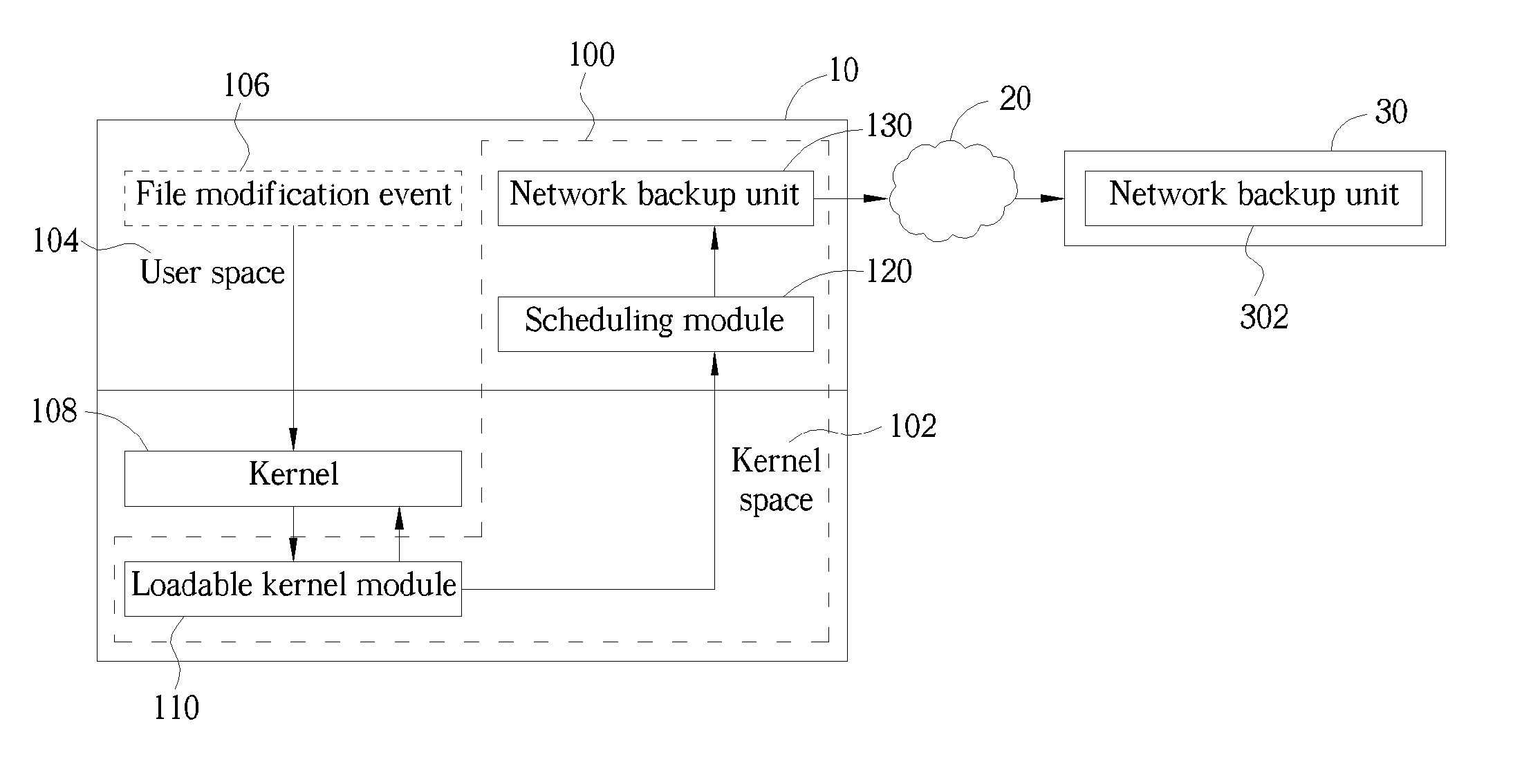
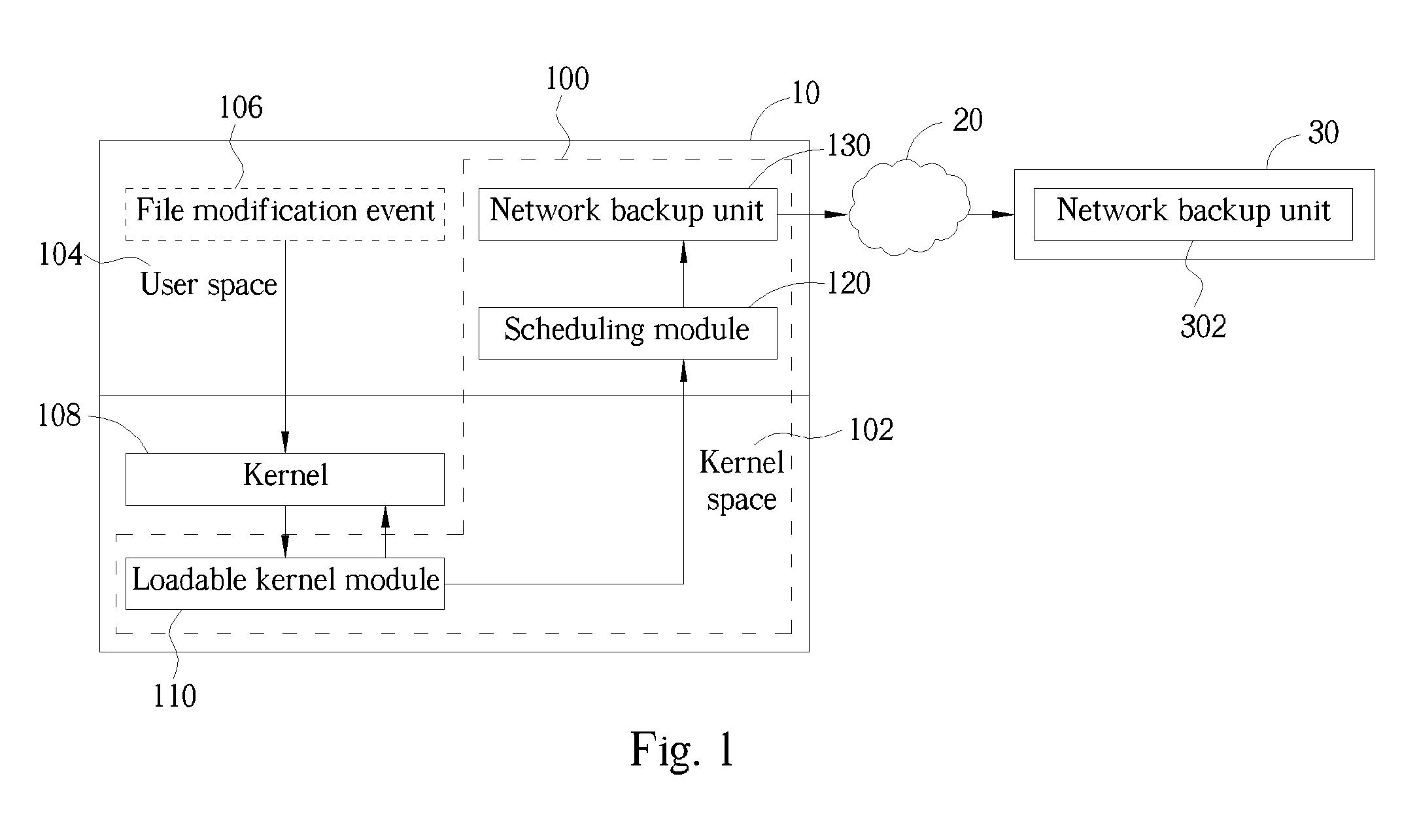
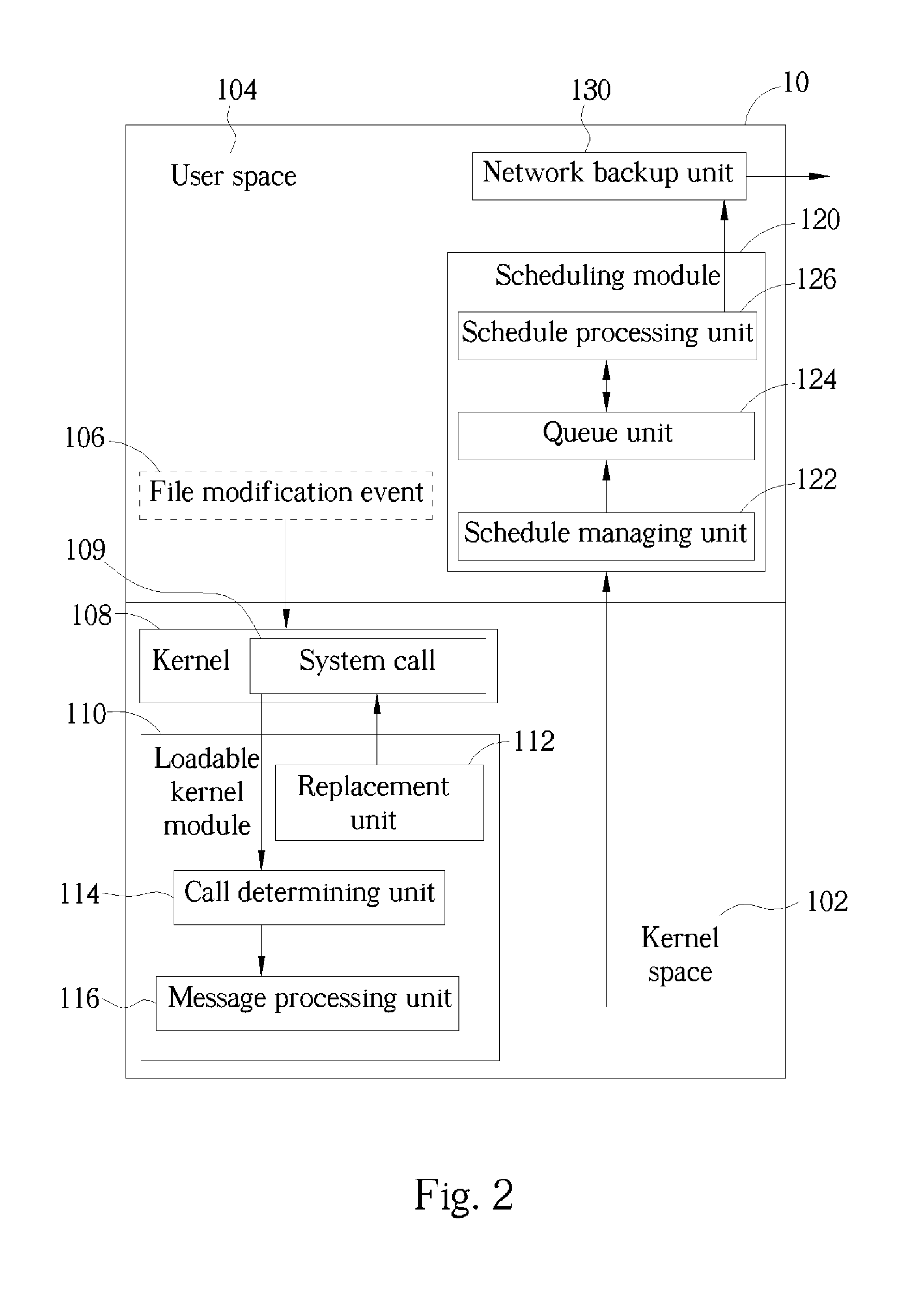
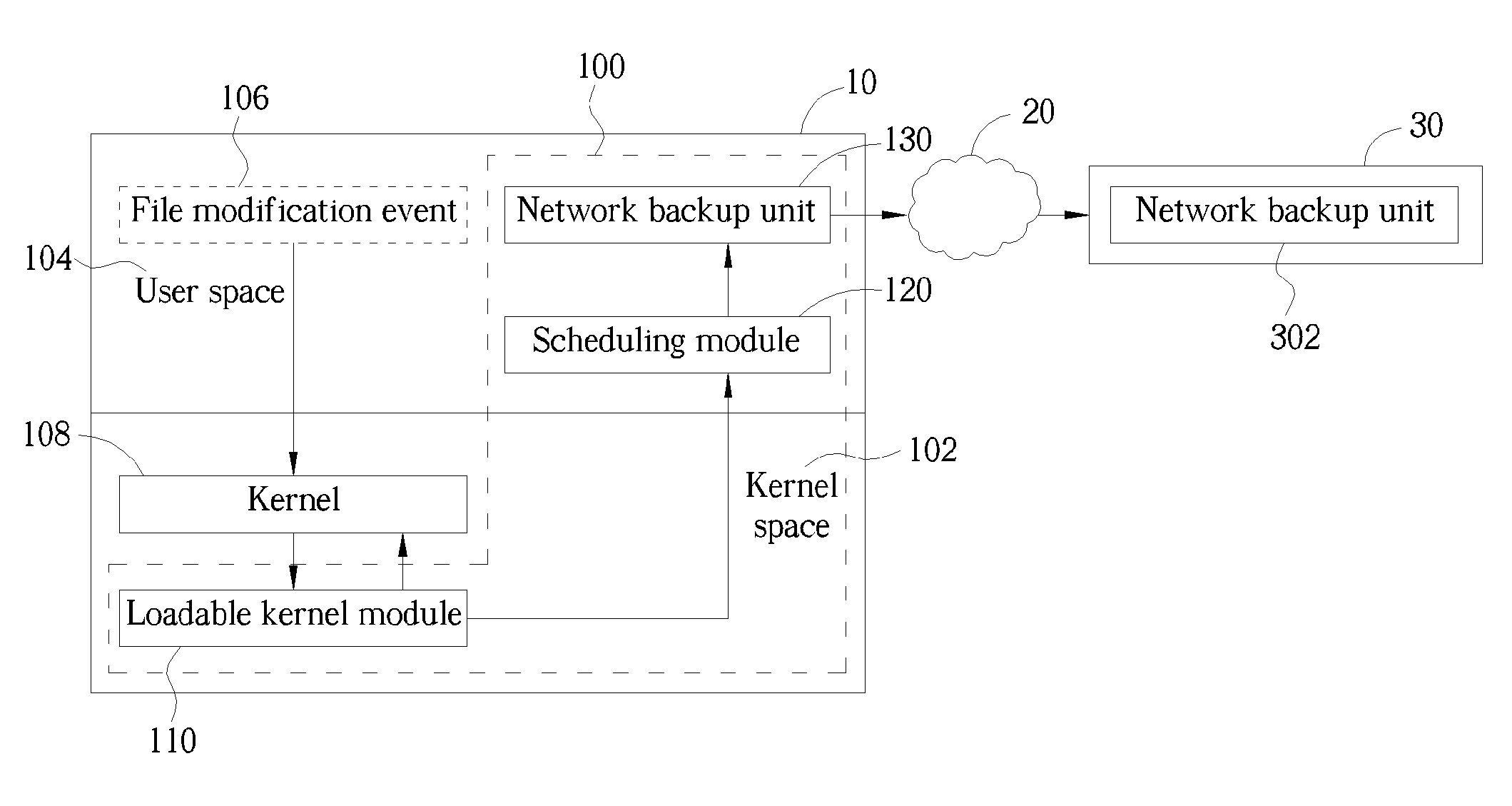
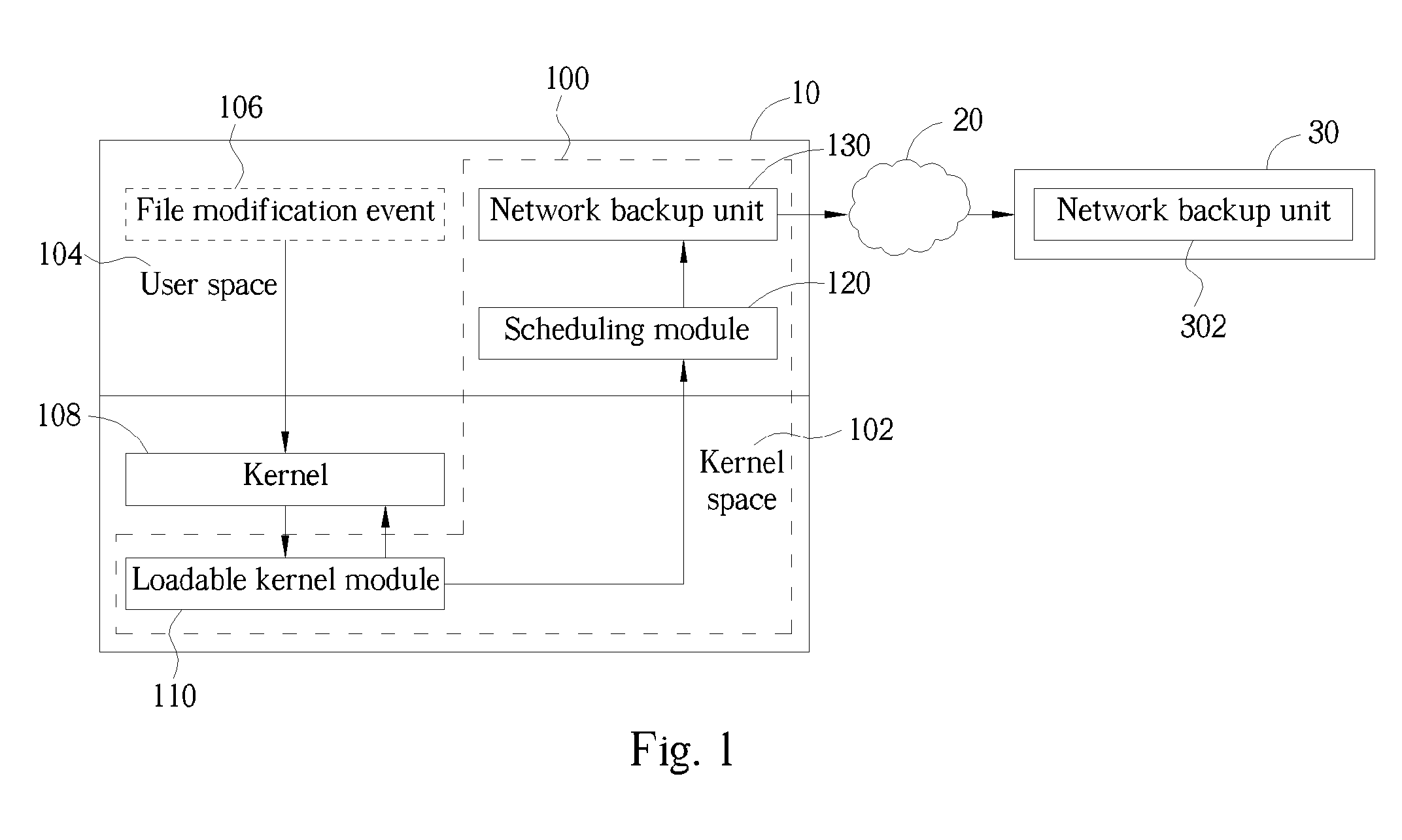
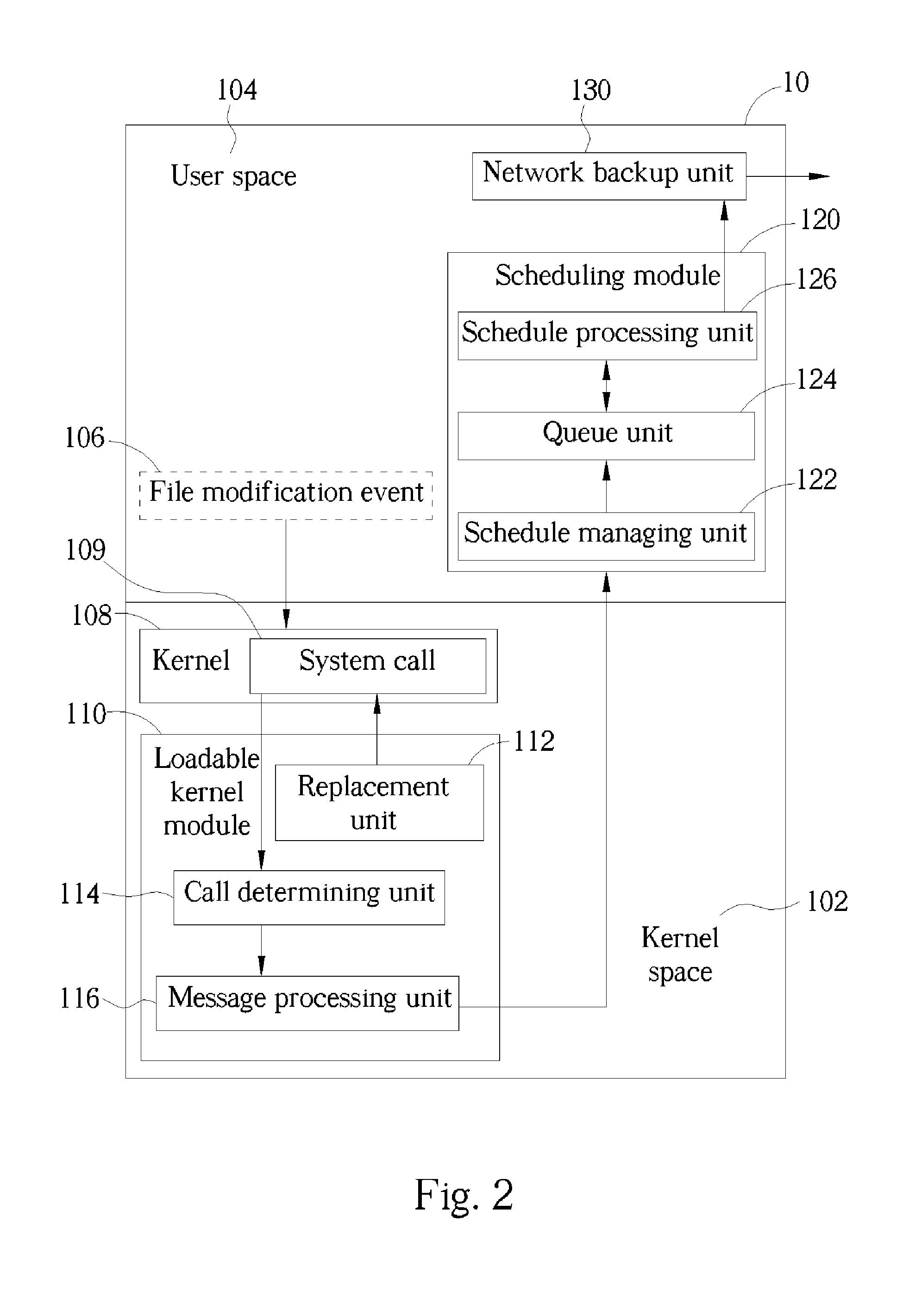
ActiveUS20050160313A1Reduce data loadFast transmissionData processing applicationsInput/output to record carriersComputer moduleComputerized system
A real-time remote backup system and related method used for a network system connecting at least one source computer system and one destination computer system is disclosed. The system includes a loadable kernel module capable of presetting up at least one specific system call in the kernel space of the source computer system. Besides the kernel software, the specific system call can notify the loadable kernel module to generate a corresponding file modification message when a file modification event occurs in the user space of the source computer system. A scheduling module sequentially queues and implements the file modification messages from the loadable kernel module, and then generates a corresponding backup command according to each said file modification message. And, a network backup unit installed in the source computer system is facilitated to directly back up variant part of the file through the network system to the destination computer system when receiving the backup command transmitted from the scheduling module.
Owner:QNAP SYST INC +1
Kernel mode Rootkit detection method based on system virtualization technology
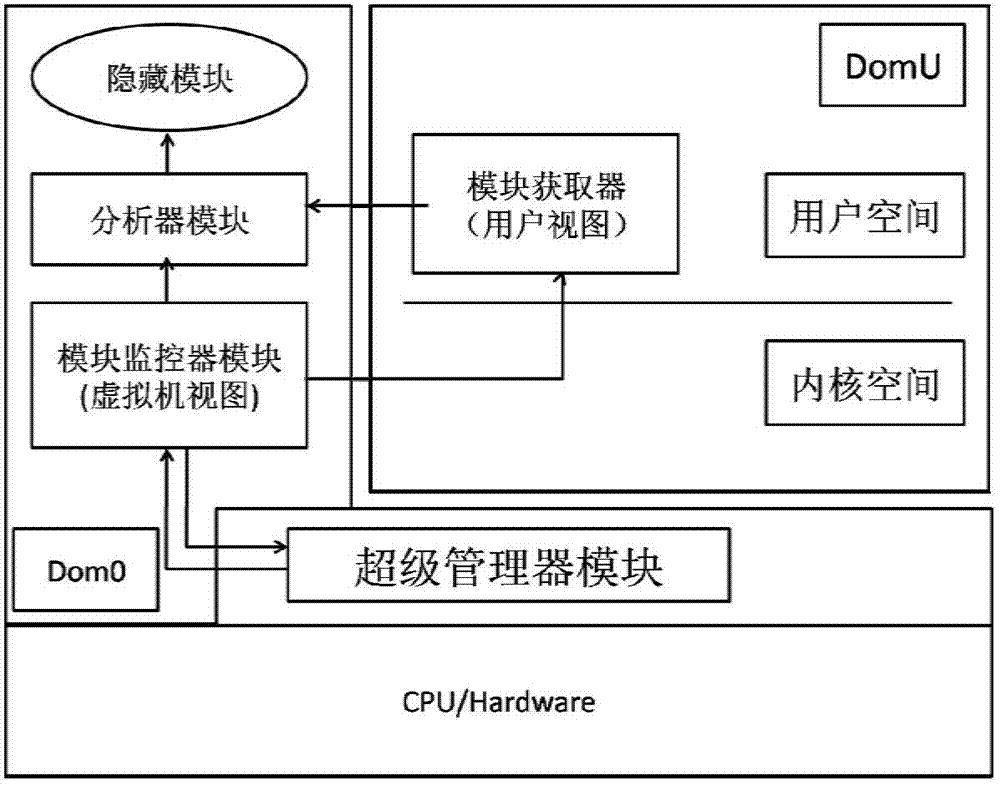
ActiveCN103310152AAvoid attackGuarantee authenticityPlatform integrity maintainanceVirtualizationSystem call
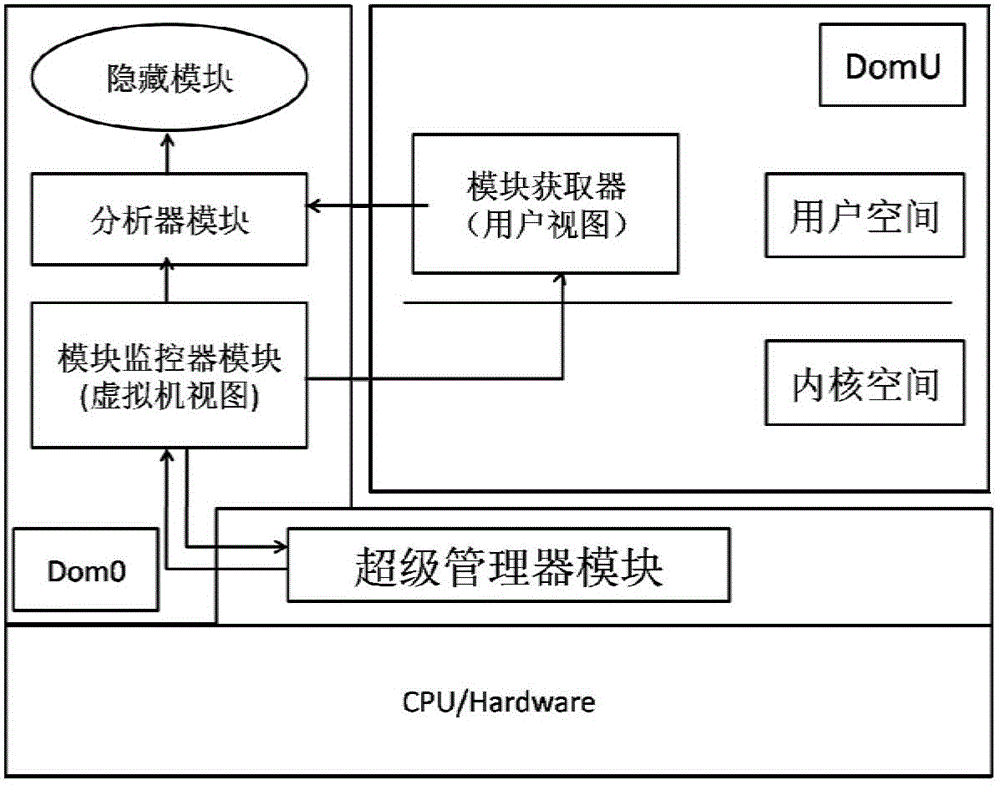
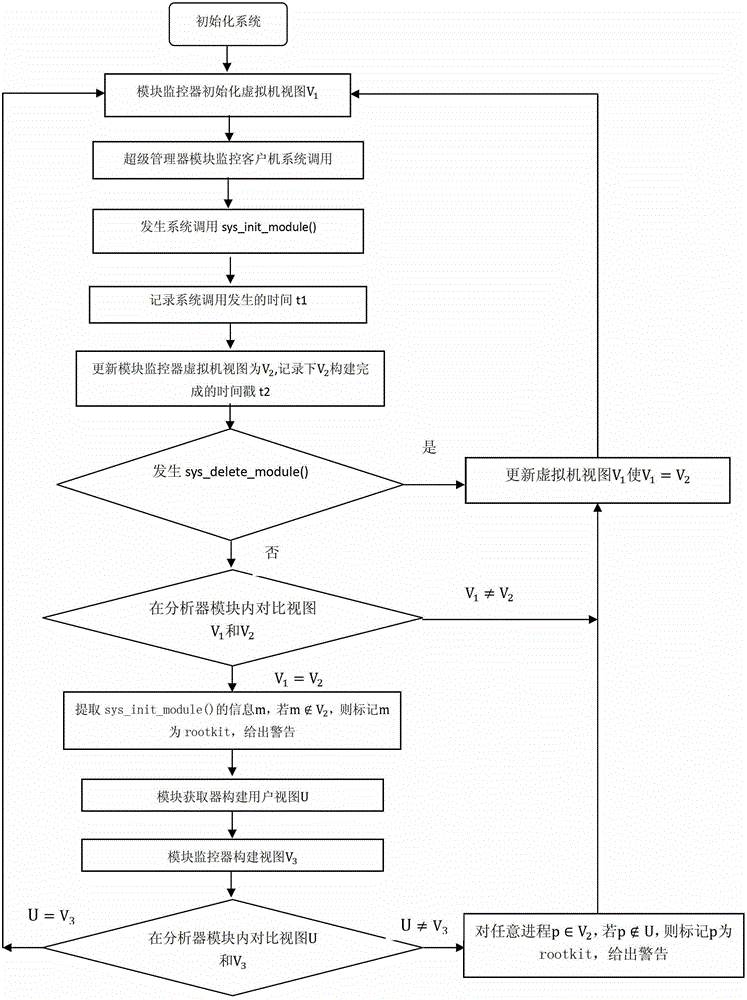
The invention provides a kernel mode Rootkit detection method based on system virtualization technology. A Rootkit principle, system calling and an LKM (Loadable Kernel Module) are analyzed deeply to obtain the behavior characteristic of hiding of own module information of kernel mode Rootkit. Specific to the characteristic, the Rootkit detection method based on cross view validation is designed. A Xen kernel is changed to intercept system calling, so that a credible view is constructed. An infected view is constructed by using a user mode tool of a target client. Hidden modules are found by comparing the credible view with the infected view.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
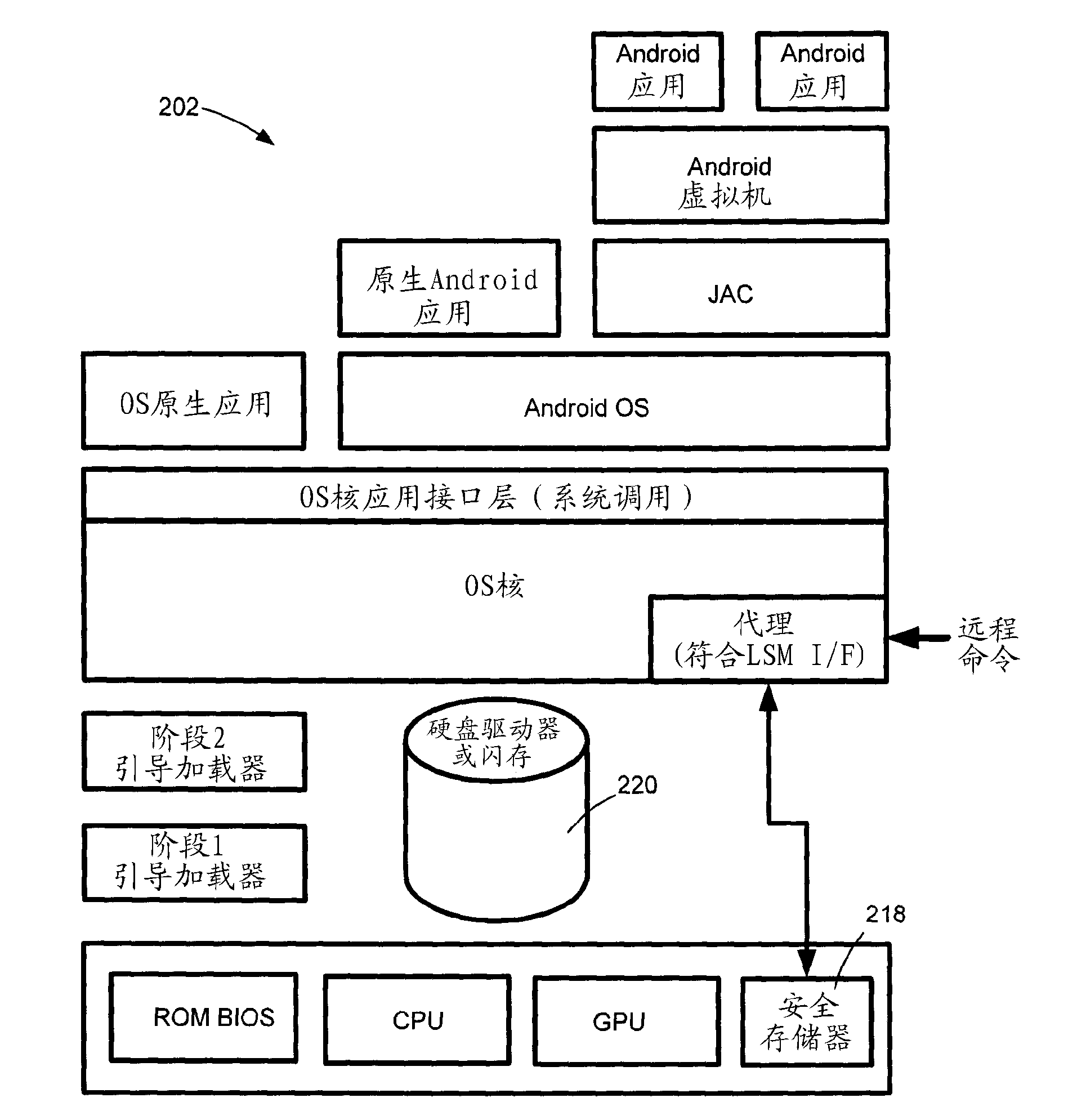
Method and system for preventing and detecting security threats
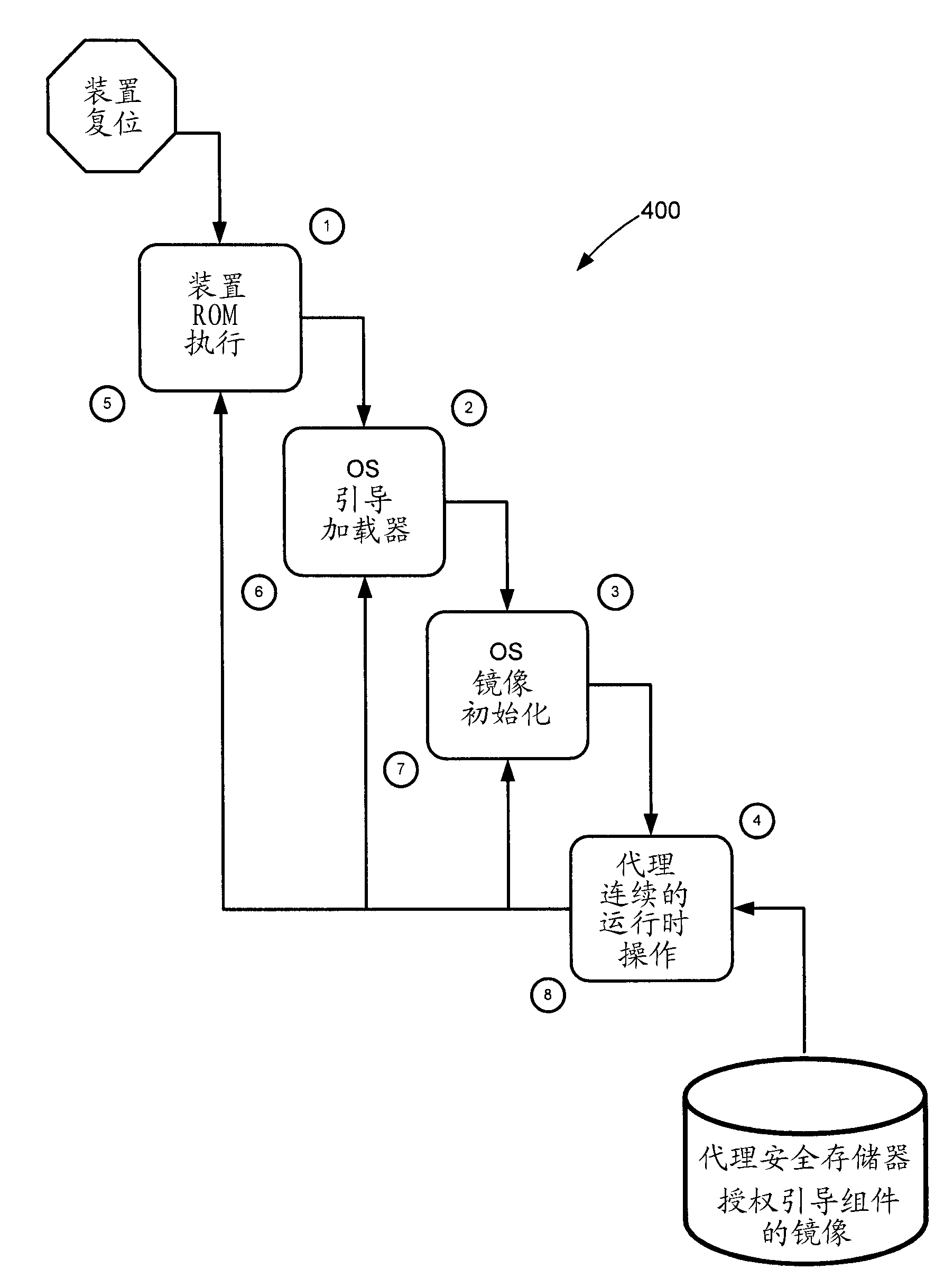
A system and method is provided for implementing platform security on a consumer electronic device having an open development platform. The device is of the type which includes an abstraction layer operable between device hardware and application software. A secured software agent is provided for embedding within the abstraction layer forming the operating system. The secured software agent is configured to limit access to the abstraction layer by either blocking loadable kernel modules from loading, blocking writing to the system call table or blocking requests to attach debug utilities to certified applications or kernel components.
Owner:IRDETO ACCESS
Malicious code analysis method and system under Linux platform
ActiveCN104102878AImplement dynamic loadingAccurate and useful monitoring informationPlatform integrity maintainanceVirtual file systemGNU/Linux
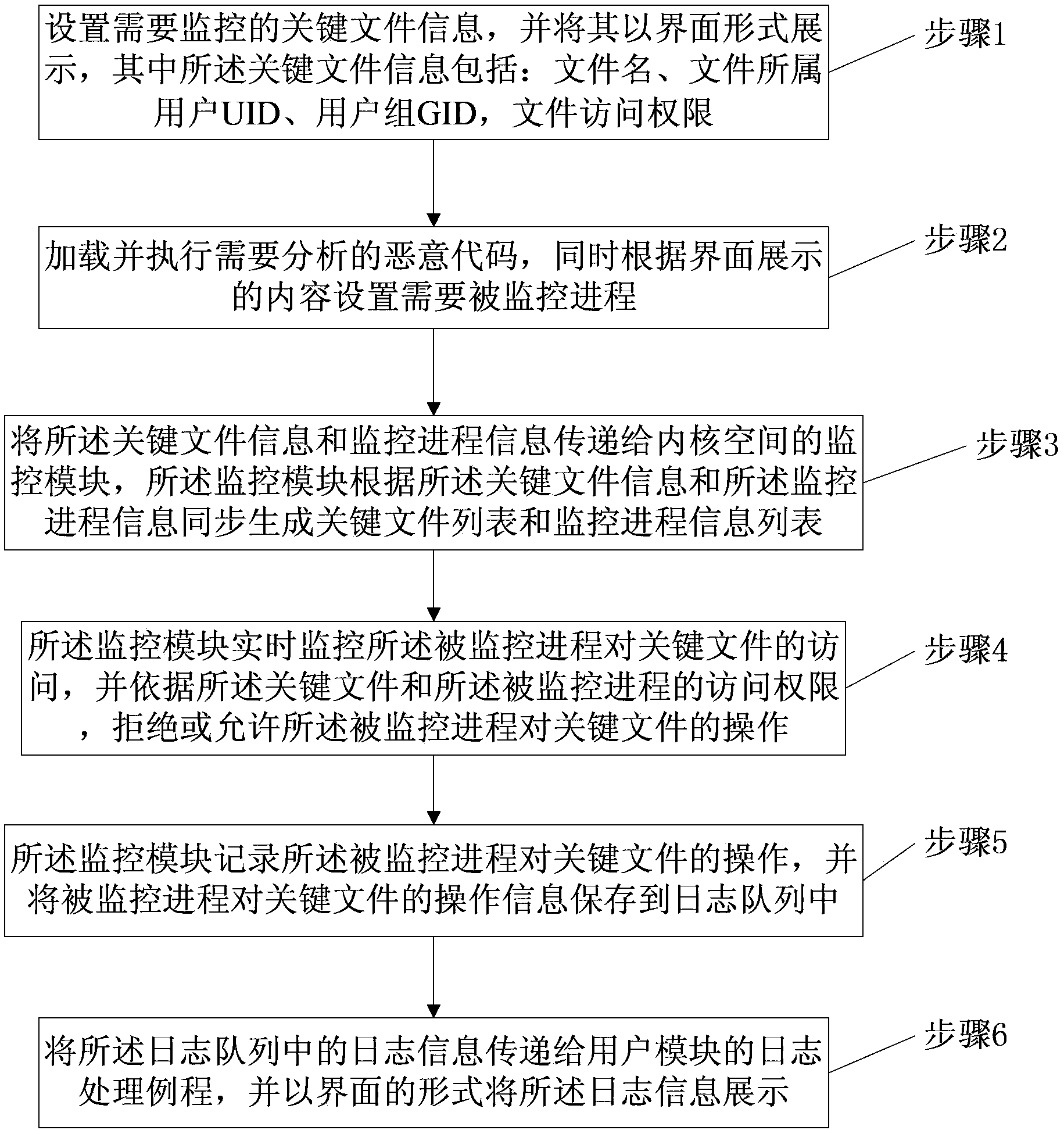
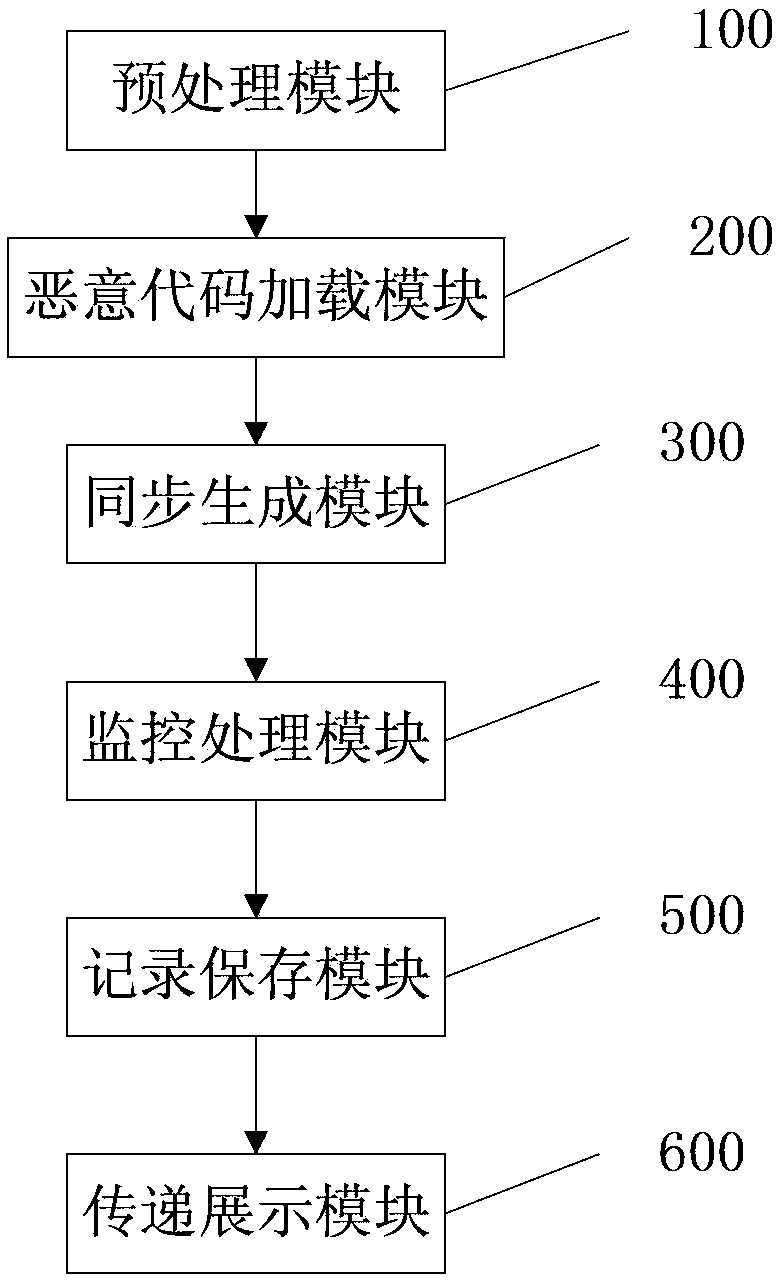
The invention provides a malicious code analysis method and system under a Linux platform. According to the method and the system provided by the invention, dynamic loading can be realized by using an LKM (Loadable Kernel Module) technology, a position of intercepting system call is positioned between a VFS (Virtual File system) layer and a detailed file system so as to acquire more information related to file operation and provide more accurate and useful monitoring information. The system call can be intercepted without the need of correcting a system call table, so that the potential safety hazards brought by the traditional method of correcting the system call table are avoided; a shared memory mechanism is adopted to increase the communication speed of a kernel module and a user progress, and the data volume of communication transmission; key files and progresses needing to be monitored are selected by a user so as to improve the usability, the flexibility and the high efficiency of the system, and the demands of the user on malicious code analysis are well met; the selected malicious code progresses and a plurality of important key files are monitored so as to avoid great performance loss of the system and improve the operation speed of the analysis system.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and device for loading kernel module
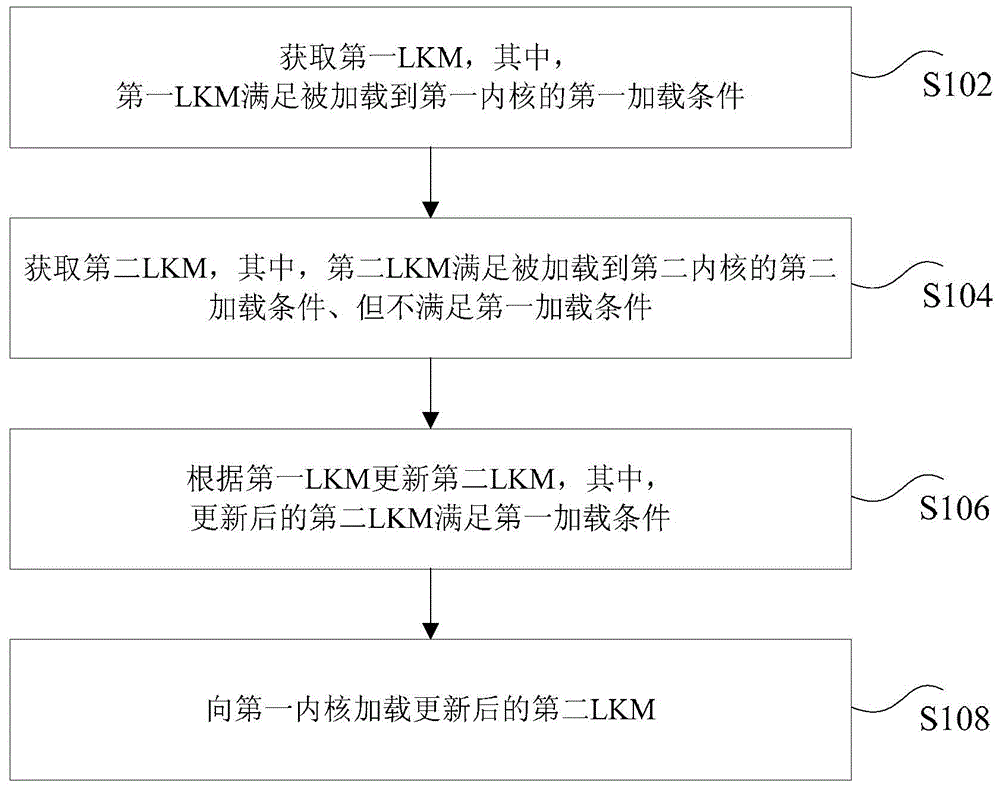
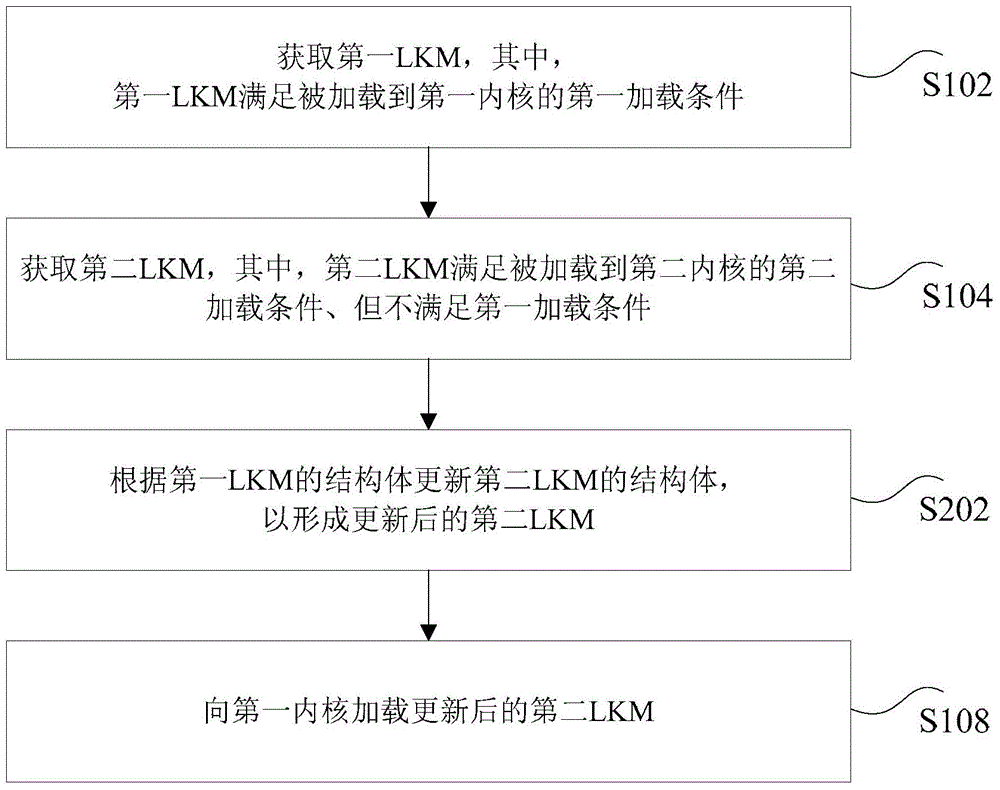
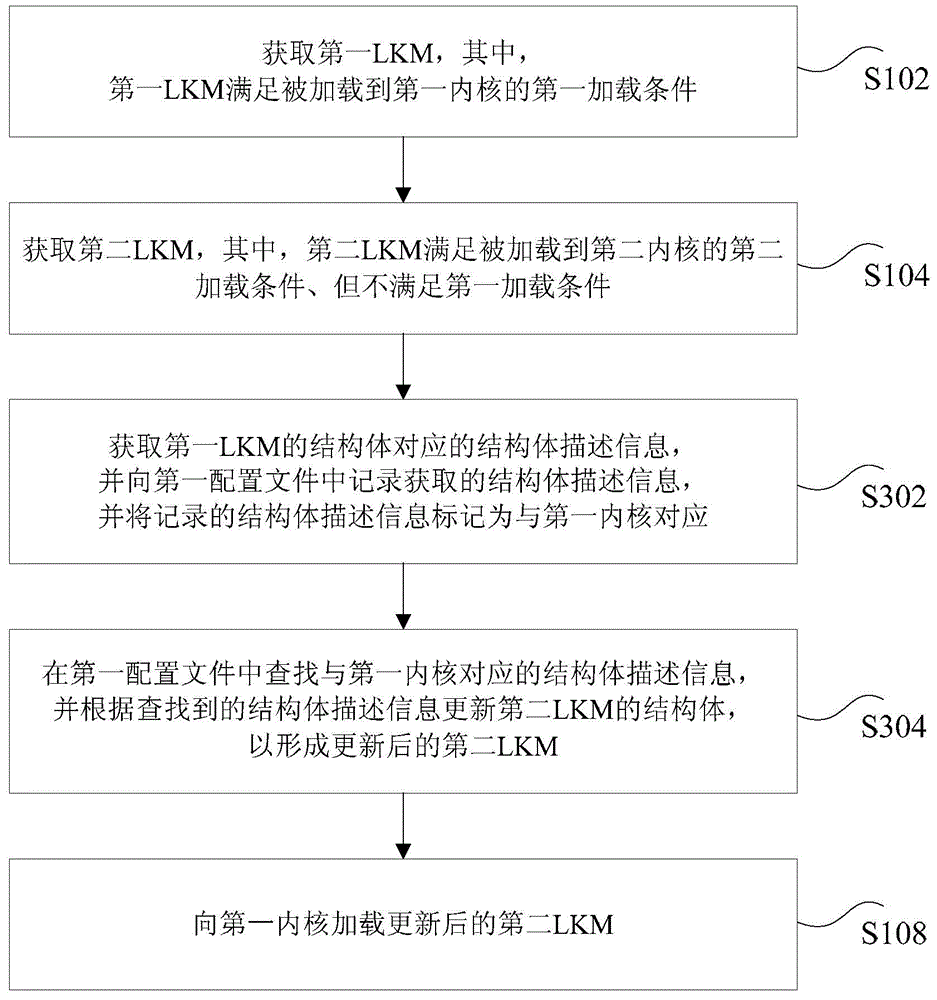
ActiveCN104679532ASolve technical problems that cannot be compatible with different kernelsProgram loading/initiatingComputer scienceLoadable kernel module
Method and Apparatus for loading kernel modules are disclosed. The method includes: obtaining a first loadable kernel module (LKM) and a second LKM, wherein the first LKM satisfies a first loading condition for being loaded into a first kernel, and the second LKM satisfies a second loading condition for being loaded into a second kernel different from the first kernel; identifying respective differences in one or more characteristic properties between the first and second LKMs; in accordance with the identified respective differences, modifying a respective one of the first and second LKMs; and loading the modified respective one of the first and second LKMs into the first kernel, wherein the modified respective one of the first and second LKM provides one or more functions in accordance with the second LKM.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and apparatus for kernel module testing
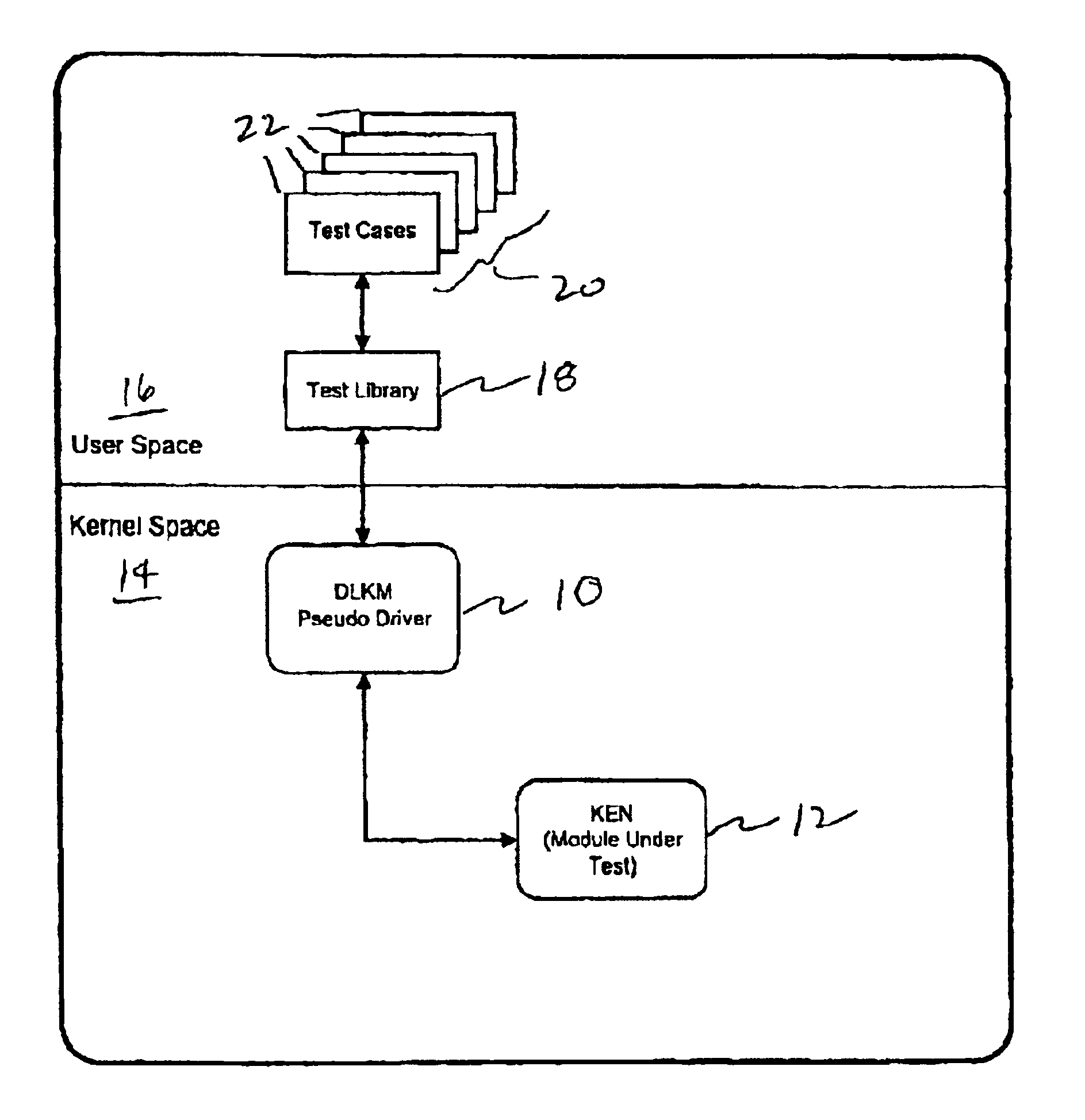
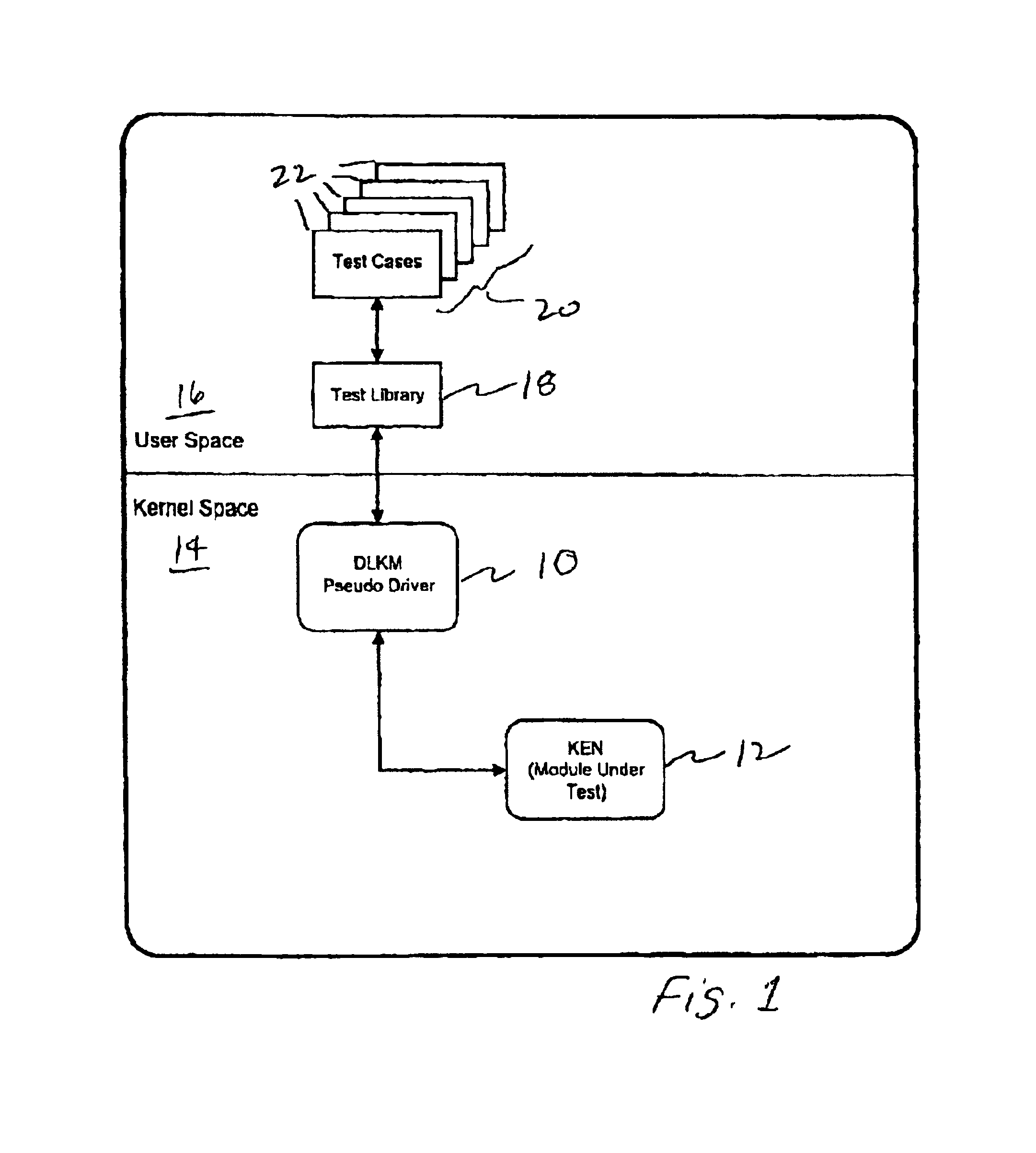
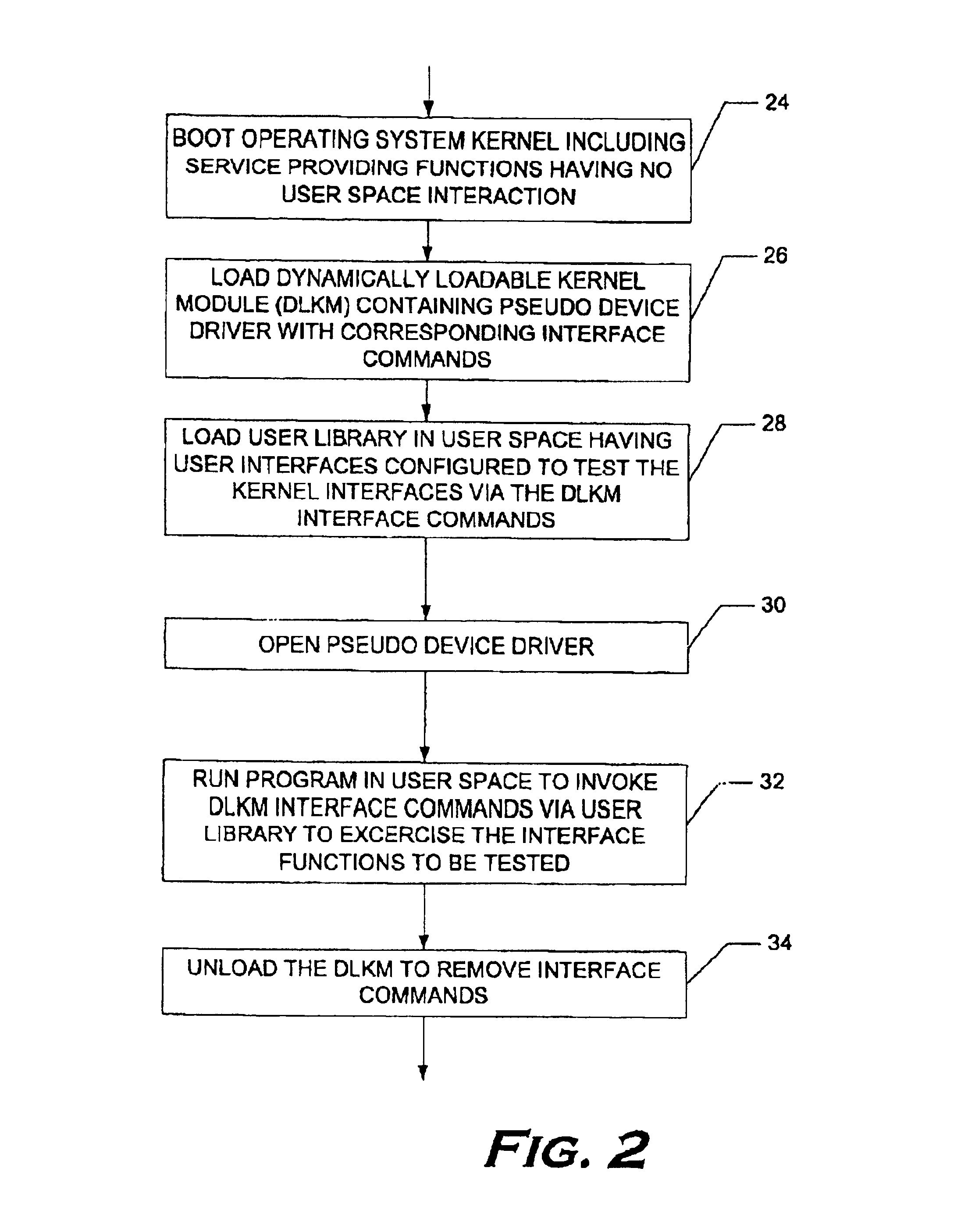
InactiveUS6950962B2Error detection/correctionEmergency protective arrangements for automatic disconnectionOperational systemComputer module
A method for testing a service that provides interface functions having no user space interaction and that is runs in a kernel space of an operating system. The method includes loading into the kernel space a dynamically loadable kernel module (DLKM) containing a pseudo device driver having interface commands corresponding to the interface functions of the service to be tested, invoking the interface commands to exercise the interface functions to be tested, and unloading the DLKM module.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Real-time remote backup system and related method
ActiveUS7315959B2Reduce data loadFast transmissionInput/output to record carriersData processing applicationsComputer moduleComputerized system
A real-time remote backup system and related method used for a network system connecting at least one source computer system and one destination computer system is disclosed. The system includes a loadable kernel module capable of presetting up at least one specific system call in the kernel space of the source computer system. Besides the kernel software, the specific system call can notify the loadable kernel module to generate a corresponding file modification message when a file modification event occurs in the user space of the source computer system. A scheduling module sequentially queues and implements the file modification messages from the loadable kernel module, and then generates a corresponding backup command according to each said file modification message. And, a network backup unit installed in the source computer system is facilitated to directly back up variant part of the file through the network system to the destination computer system when receiving the backup command transmitted from the scheduling module.
Owner:QNAP SYST INC +1
Equipment driving method for user mode and kernel mode driver cooperative processing framework
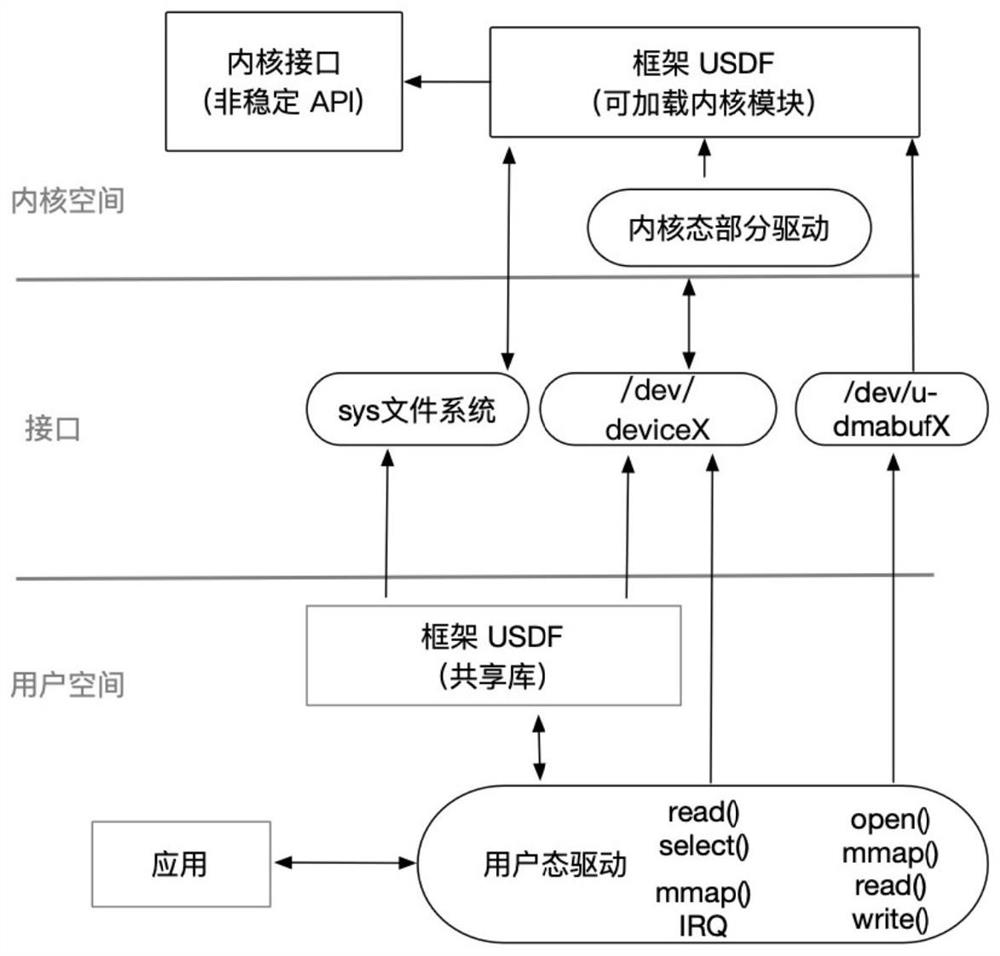
ActiveCN112231007ASimplify the development processSimplify the maintenance processBootstrappingComputer hardwareApplication procedure
The invention discloses an equipment driving method for a user mode and kernel mode-driver cooperative processing framework and the method comprises the steps: initializing the user mode and kernel mode driver cooperative processing framework, comprising a kernel mode driver as a loadable kernel module to operate in a kernel space used for providing a stable kernel mode driver development interface; and a user mode driver as a shared library, is located in the user space and used for providing an interface for user mode driver development; and when an application program in the user space calls the user mode driver, enabling the user mode driver to interact with the kernel mode driver by the user mode driver, or directly interact with the kernel mode driver by character equipment and DMA buffer equipment so that operation on specified equipment is completed. User mode and kernel mode driver cooperative processing can be achieved, interaction with hardware is jointly completed, the driver development and maintenance process can be greatly simplified, and the stability and reliability of the kernel are improved.
Owner:NAT UNIV OF DEFENSE TECH
Operating system and method for cloud server
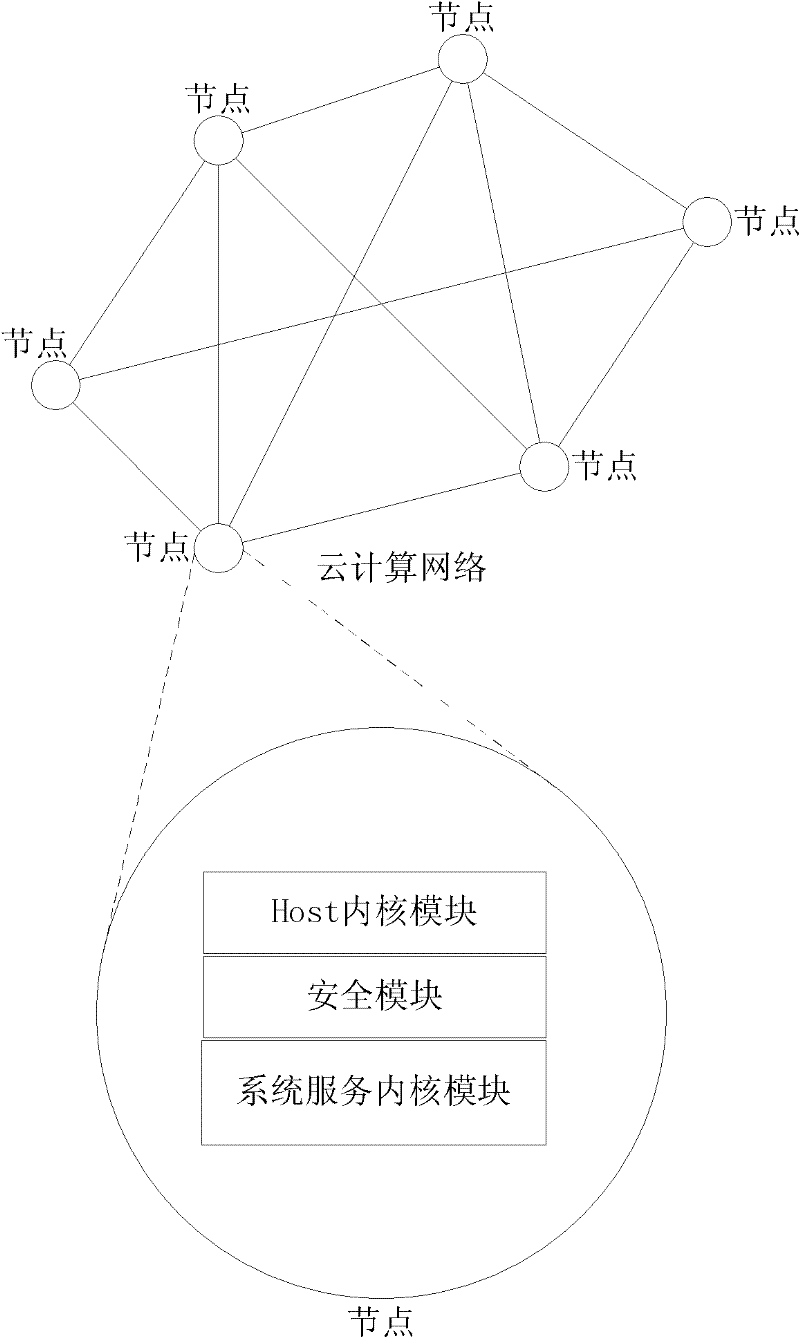
InactiveCN102541625ARun fastImprove efficiencyProgram initiation/switchingVirtualizationComputer module
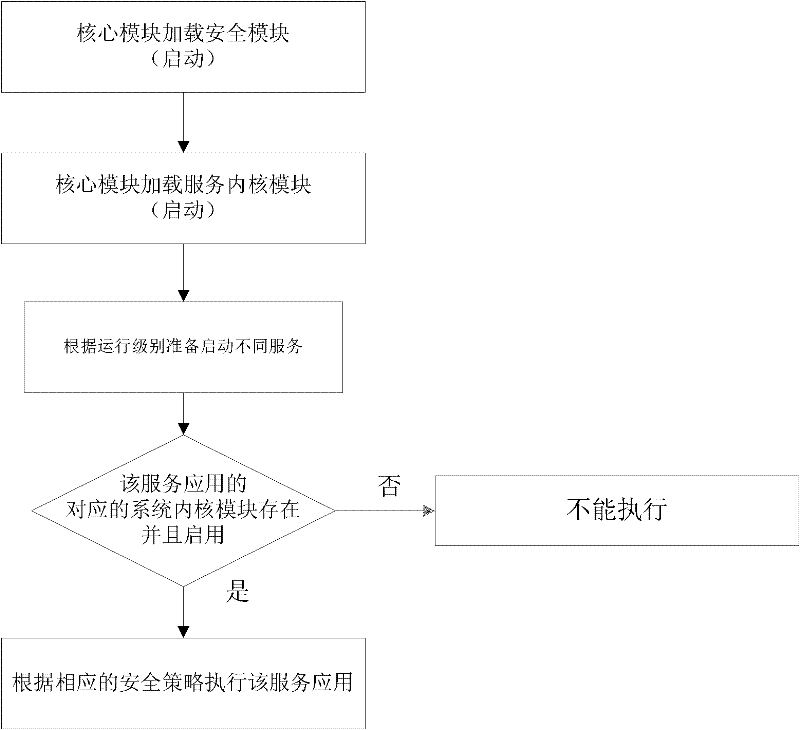
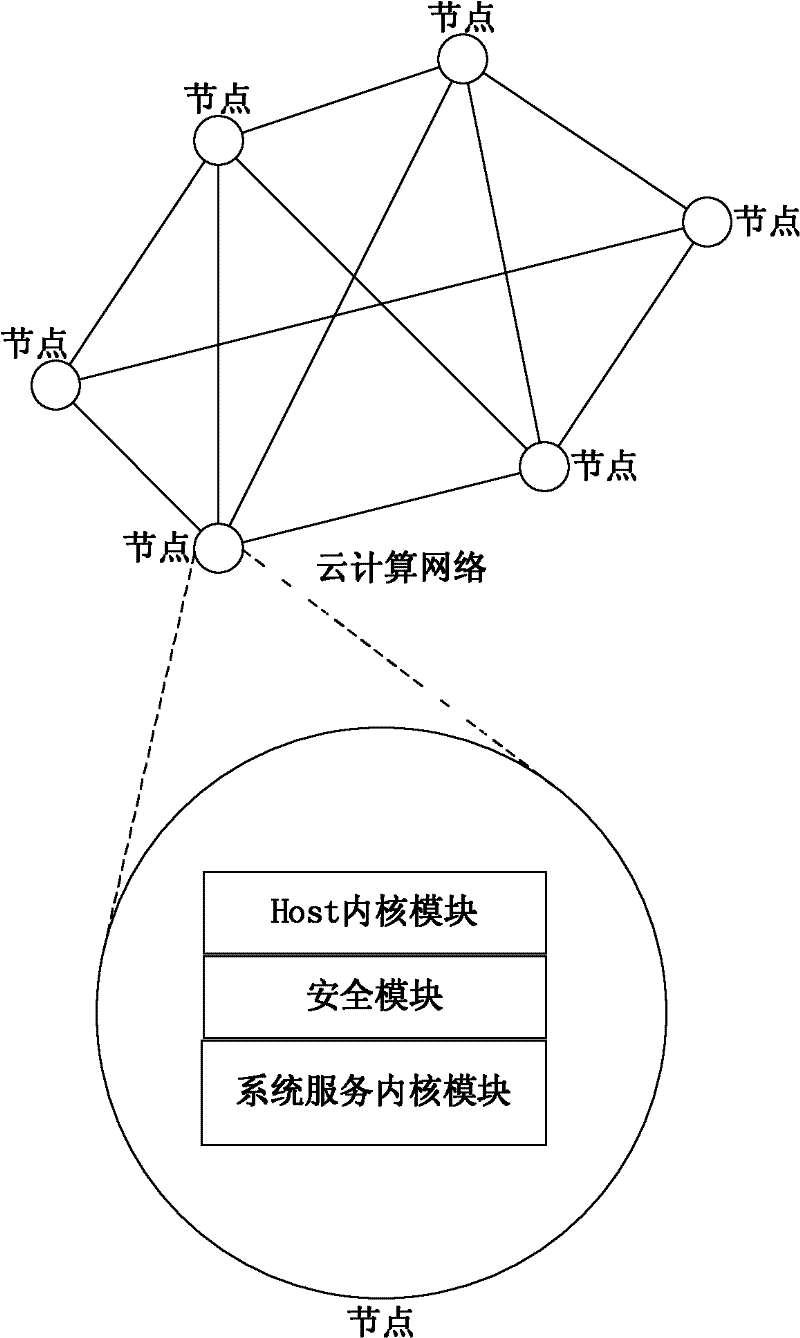
The invention discloses an operating system and an operating method for a cloud server. The system is arranged on a server of a cloud computing network, and comprises a Host kernel module, a security module and a system service kernel module, wherein the Host kernel module is a configurable multi-task operating system base layer, the security module is used for implementing a forced access control system and the system service kernel module is a loadable kernel module, wherein the system service kernel module directly runs a service program under the operating system on a cloud service operating system by loading different operating system plug-in modules. Under an operating system, service application of different operating systems can be simultaneously operated without performing virtualization and without installing different operating systems in each virtual environment; and when arranged on the server of the cloud computing network, the system can run the services of various operating systems at extremely high efficiency on the premise that other operating systems are not required to be installed.
Owner:SHANGHAI SHENGPAY E PAYMENT SERVICE CO LTD
Monitoring method for multi-level Android system malicious behaviors
InactiveCN107169354AThe results of the analysis are comprehensivePlatform integrity maintainanceOperating systemInformation science
The invention relates to monitoring for Android system malicious behaviors, and belongs to the technical field of computer and information science. Monitoring is implemented to system function calling in the Java layer, the Native layer and the Kernel layer of an Android system; while the malicious behaviors are prevented, a user is warned, and a log is recorded; the malicious behavior lists 1, 2 and 3 of each layer are output; and finally, through pairwise comparison of adjacent views, hidden behaviors (Java layer hidden behaviors and Native layer hidden behaviors) are analyzed, and a hidden behavior list is output. A process injection technology is adopted in the Java layer and the Native layer, and an LKM (Loadable Kernel Modules) technology is adopted in the Kernel layer.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
File systems accessing register dynamic collection method
InactiveCN100583099CImprove usabilityReduce sizeHardware monitoringSpecial data processing applicationsFile systemSystem testing
The invention discloses a dynamic acquisition method of file system access record, belonging to the field of storage system testing and performance analysis. The invention is characterized in that a kernel module can be loaded without the need of unloading the old file system, thus not needing to interrupt the working application. A file system operation interception module can dynamically intercept the underlayer file system operation by a substitution of corresponding functions in the interception module. While executing the underlayer file system operation, the functions output the operation type and parameters to an access record output module which compresses the file record and outputs a plurality of operation information at one time in a output record way of register. The access record output module controls the output file size to prevent the problems of difficult read and write and exceeding file system restriction. An access record file management module collects additional information and packages and transfers the access record according to the assignment of users, thus being convenient for users to manage. The test shows that the collection of access record has little impact on the application.
Owner:TSINGHUA UNIV
Method for debugging static memory corruption
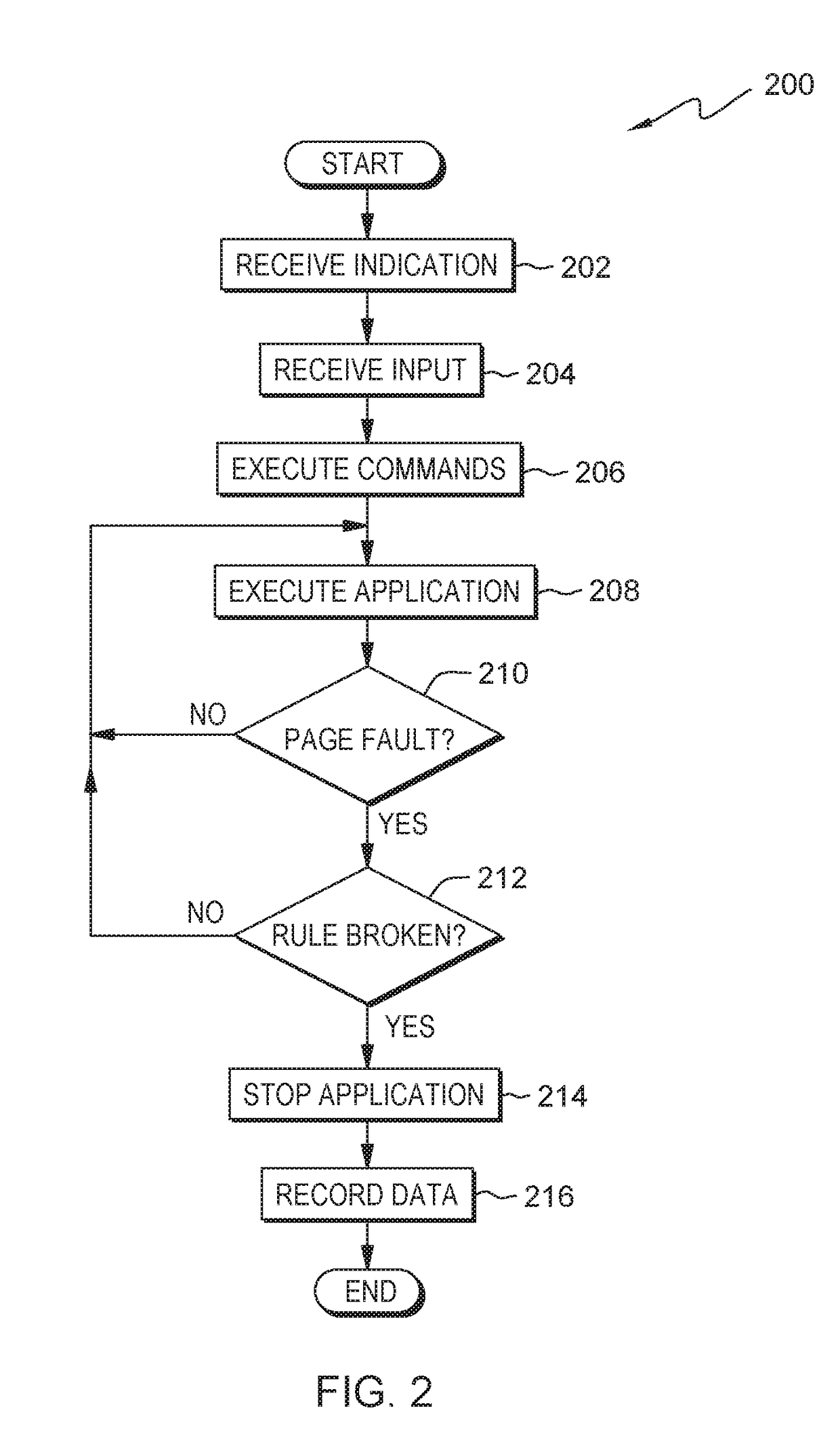
InactiveUS20170371732A1Memory architecture accessing/allocationMemory systemsLoadable kernel moduleVirtual storage
Owner:IBM CORP
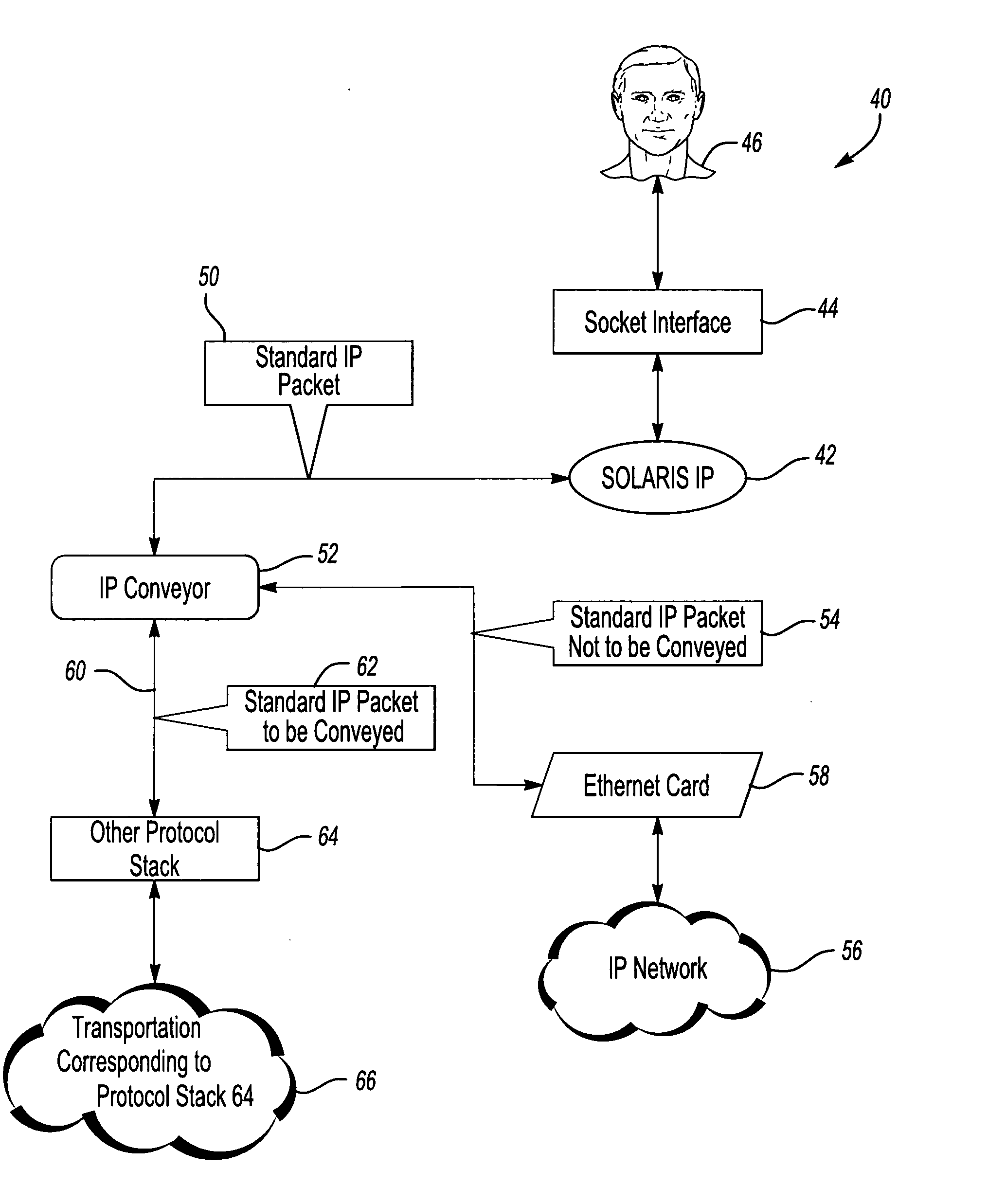
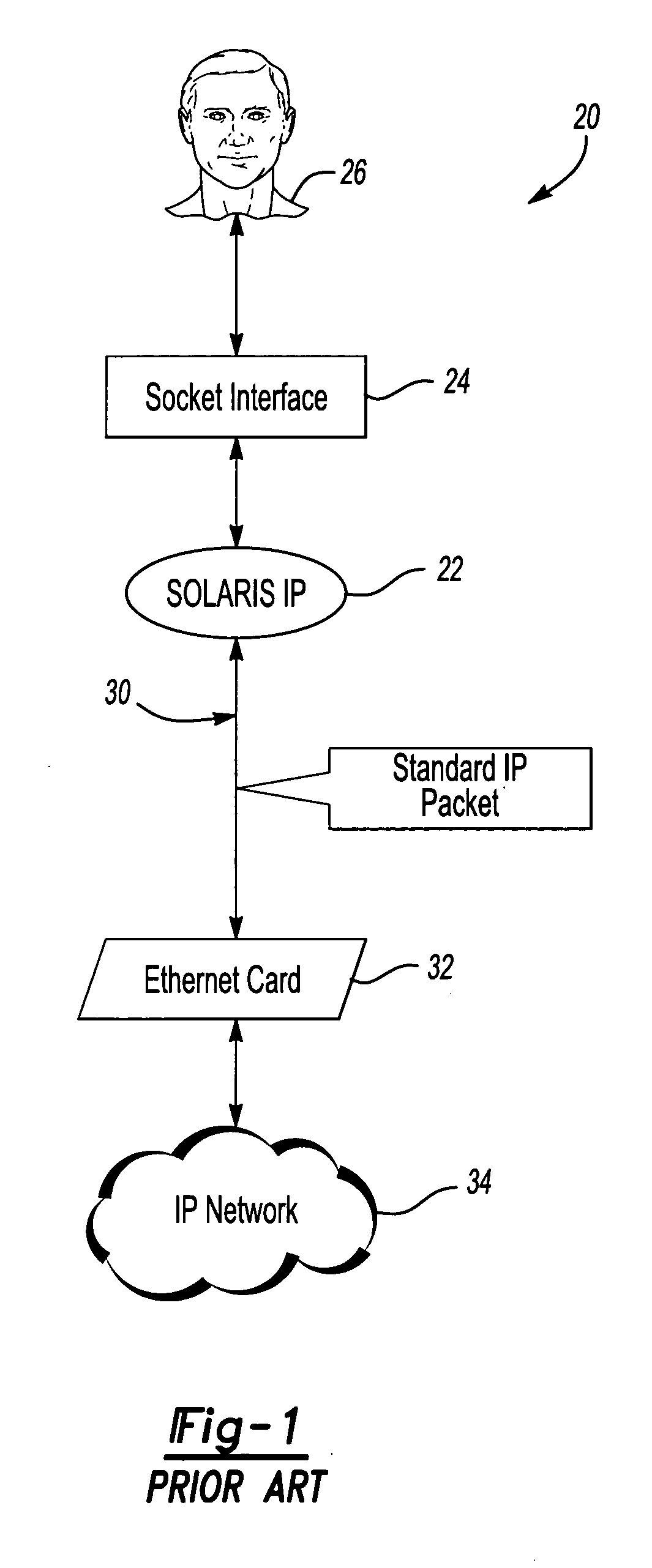
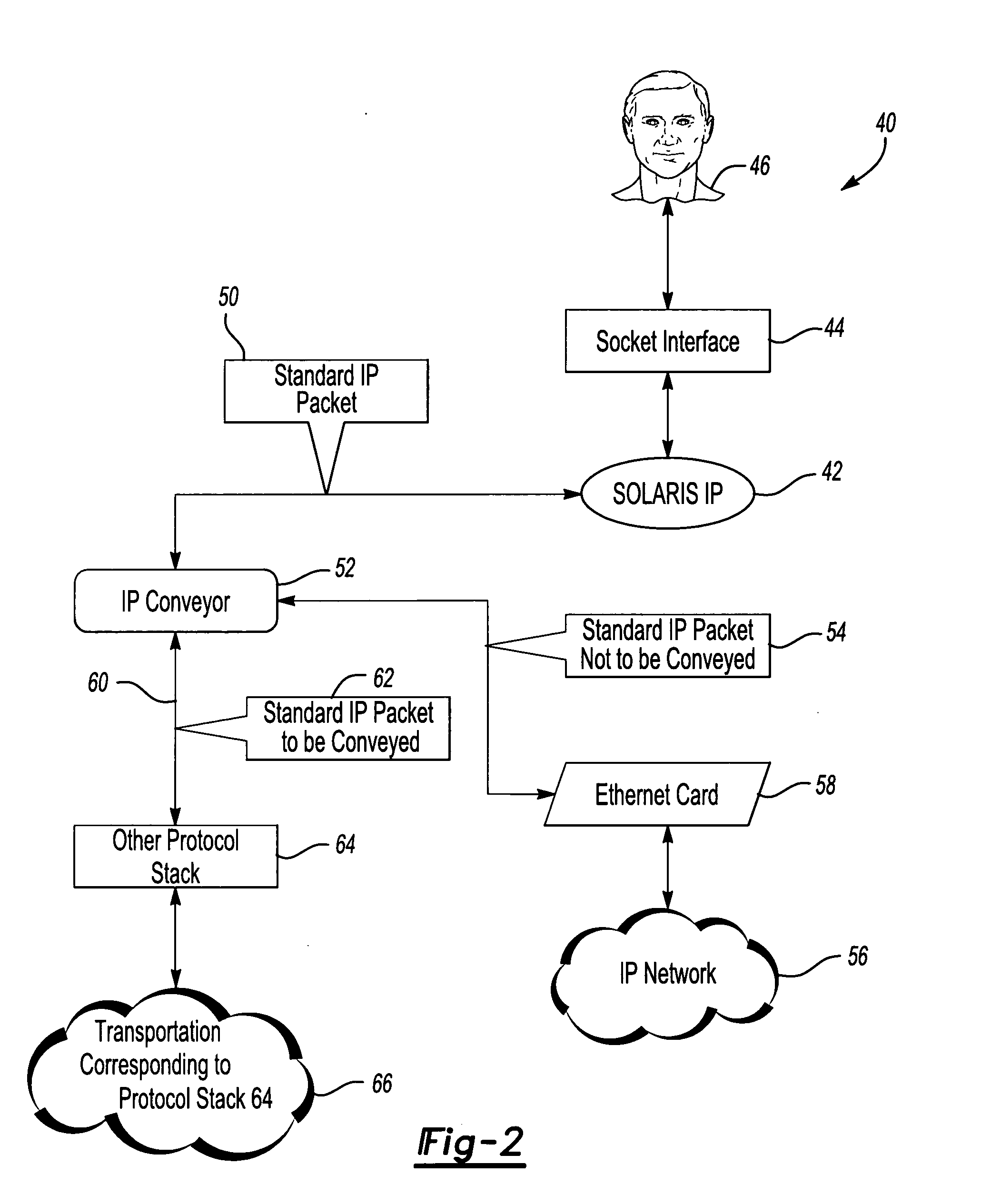
Internet protocol packet processing
A technique for processing Internet Protocol (IP) packets includes an IP conveyor portion as a loadable kernel module that includes user defined filtering criteria for recognizing at least one feature of an IP packet. When one of the user defined filtering criteria is satisfied, an IP packet can be directed along a desired communication path, processed using a desired protocol stack or both. Whenever an IP packet does not satisfy at least one of the filtering criteria, a default communication path is used for such a packet.
Owner:LUCENT TECH INC
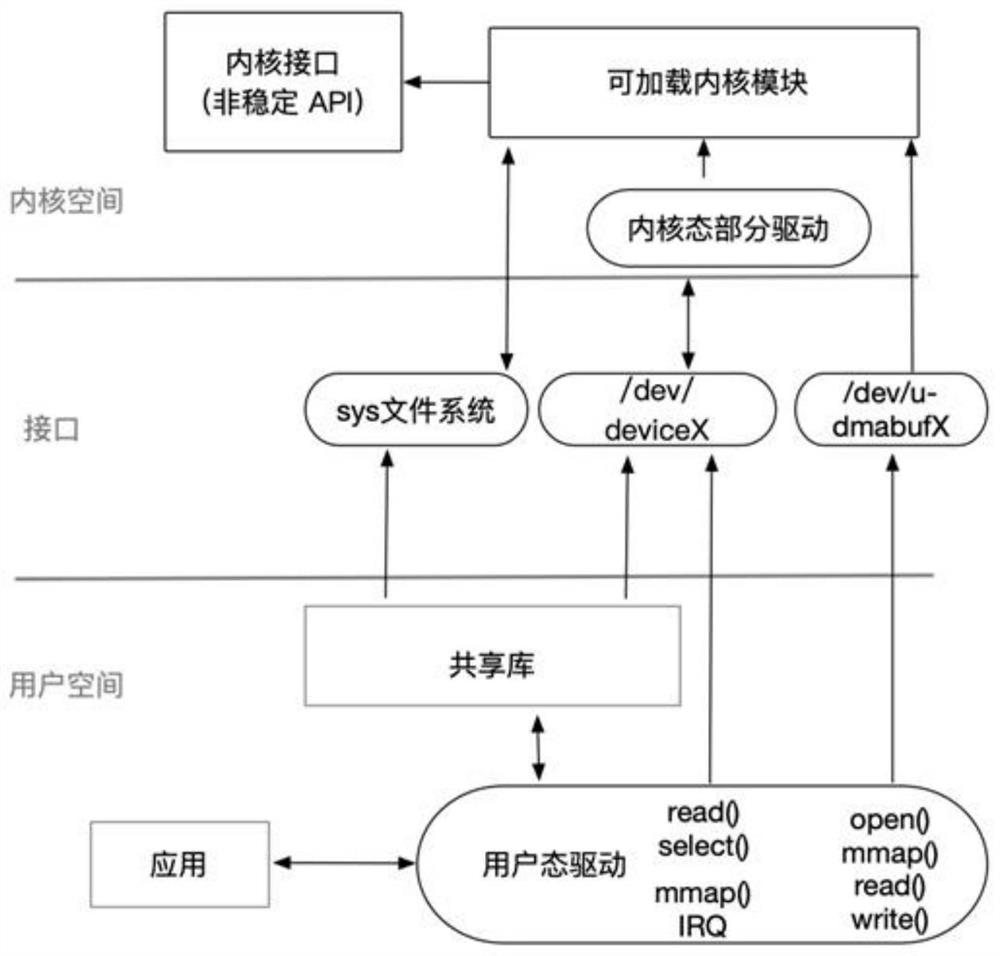
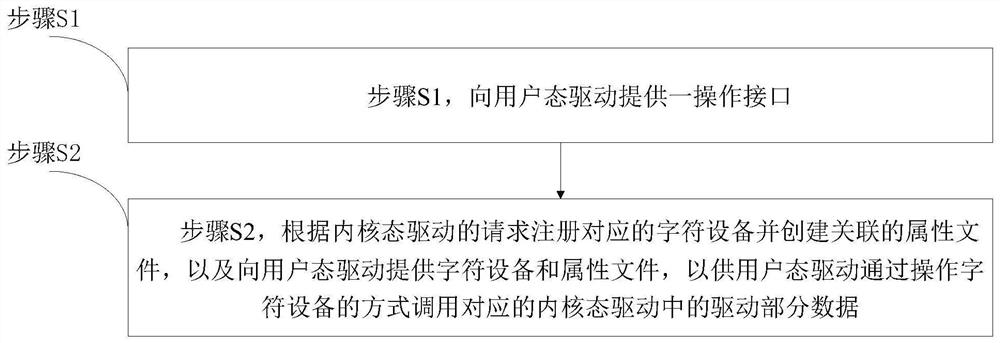
Cooperative work system and method of user mode drive and kernel mode drive
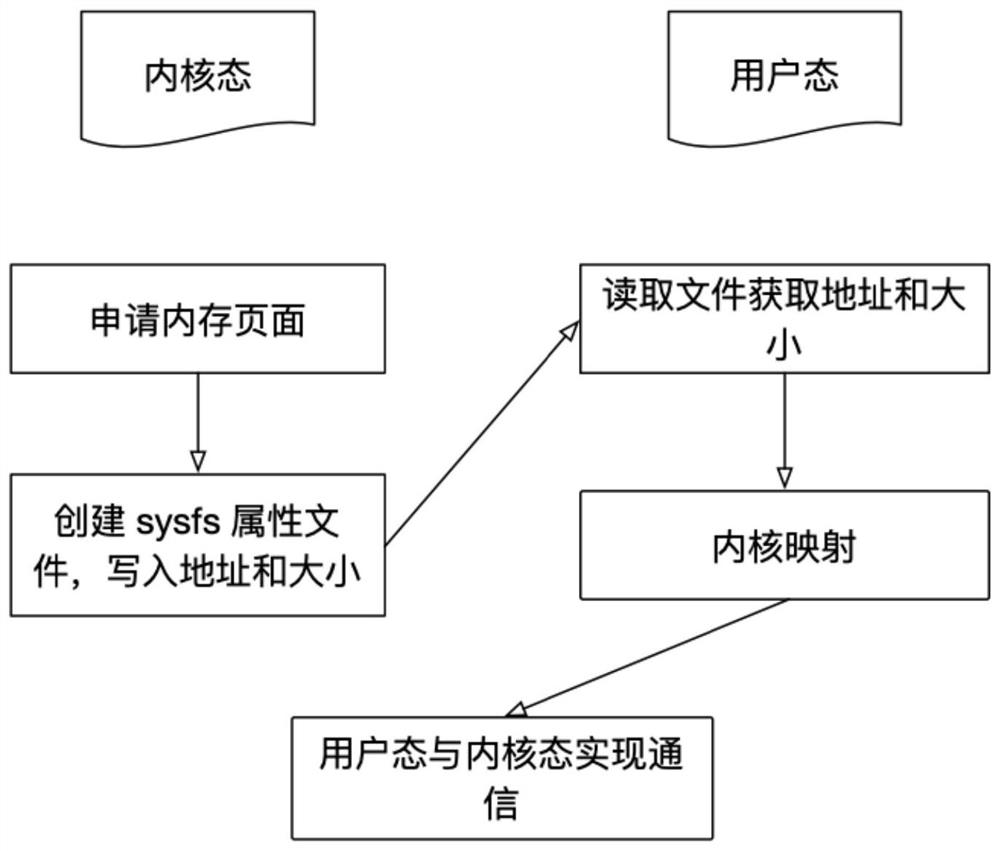
PendingCN112732344AImprove stabilityImprove reliabilityBootstrappingProgram loading/initiatingOperational systemControl engineering
The invention relates to the field of computer operating systems, in particular to a cooperative work system and method of a user mode drive and a kernel mode drive. The cooperative work system comprises a user mode driver, a kernel mode driver and a loadable kernel module, the loadable kernel module provides an operation interface for the user mode driver, and the loadable kernel module is used for registering corresponding character equipment according to a request of the kernel mode driver and creating an associated attribute file, and providing the character device and the attribute file for the user mode drive, so that the user mode drive calls the drive part data in the corresponding kernel mode drive by operating the character device. The technical scheme provided by the invention has the beneficial effects that the cooperative work system and method of the user mode drive and the kernel mode drive are provided, the cooperative processing of the user mode drive and the kernel mode drive can be achieved, the interaction with hardware is completed together, the drive development and maintenance process can be greatly simplified, and the stability and reliability of the kernel are improved.
Owner:ISOFT INFRASTRUCTURE SOFTWARE
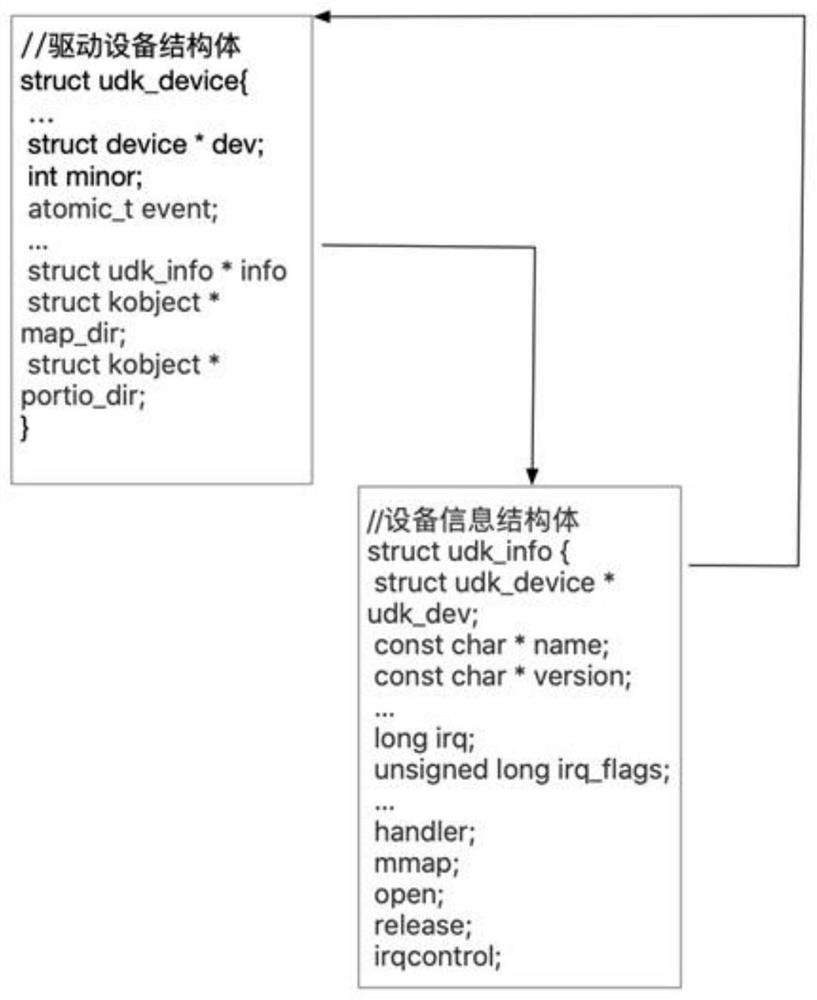
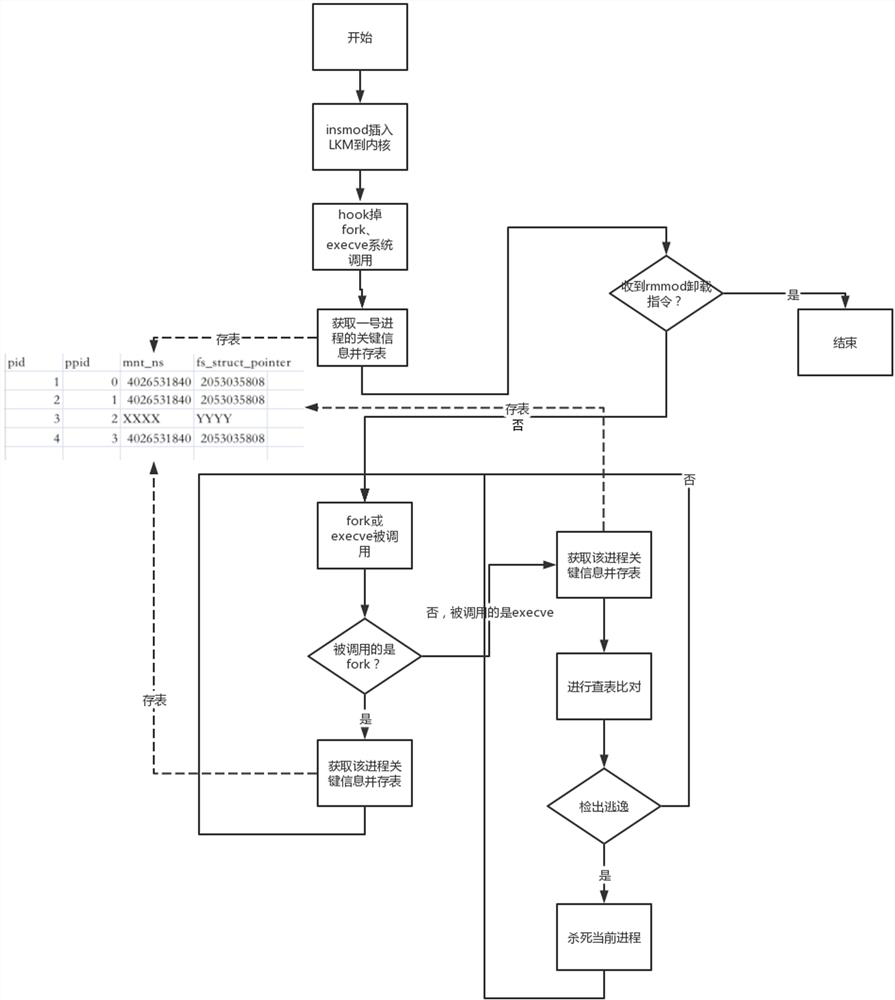
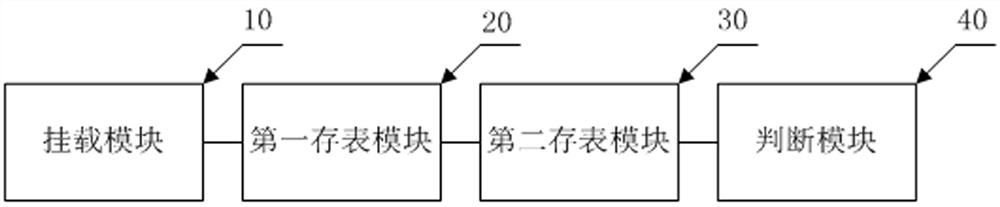
Container escape detection and blocking method, device and equipment and storage medium
ActiveCN114676424AReduce performance consumptionPrevent Bypass DetectionProgram initiation/switchingPlatform integrity maintainanceOperational systemOperating system
The invention discloses a container escape detection and blocking method, device and equipment and a storage medium, and relates to the technical field of safety environment detection.The method comprises the following steps that a dynamic loadable kernel module is loaded in a system, and the dynamic loadable kernel module is made to hook a fork function and an excve function; acquiring key information of a host machine process and storing the key information into a global table; when the fork function or the excve function is called by the container process, key information of the container process is obtained and stored in a global table; and searching the key information of the host machine process in the global table, comparing the key information with the key information of the container process to determine whether the container process escapes or not, and if so, blocking the container process. According to the method, the execution process of the process is supervised, and the process can be killed before the escape process executes malicious actions, so that blocking in the process is realized, and an operating system is protected to the maximum extent.
Owner:杭州默安科技有限公司
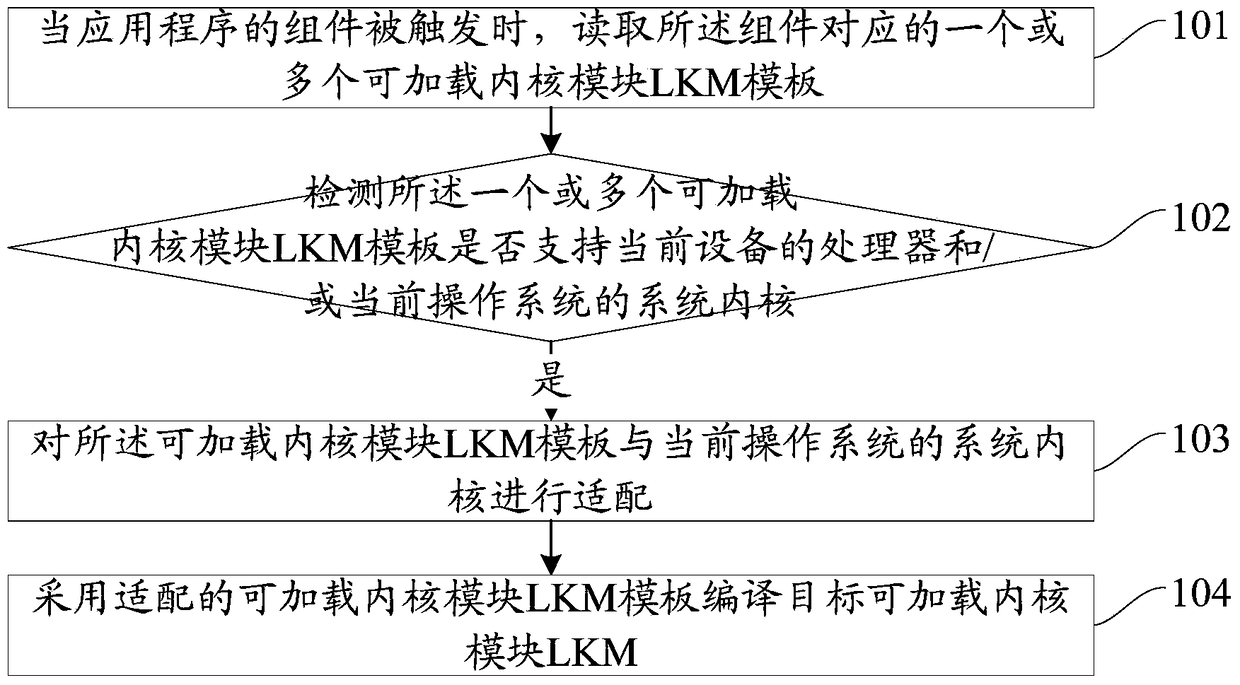
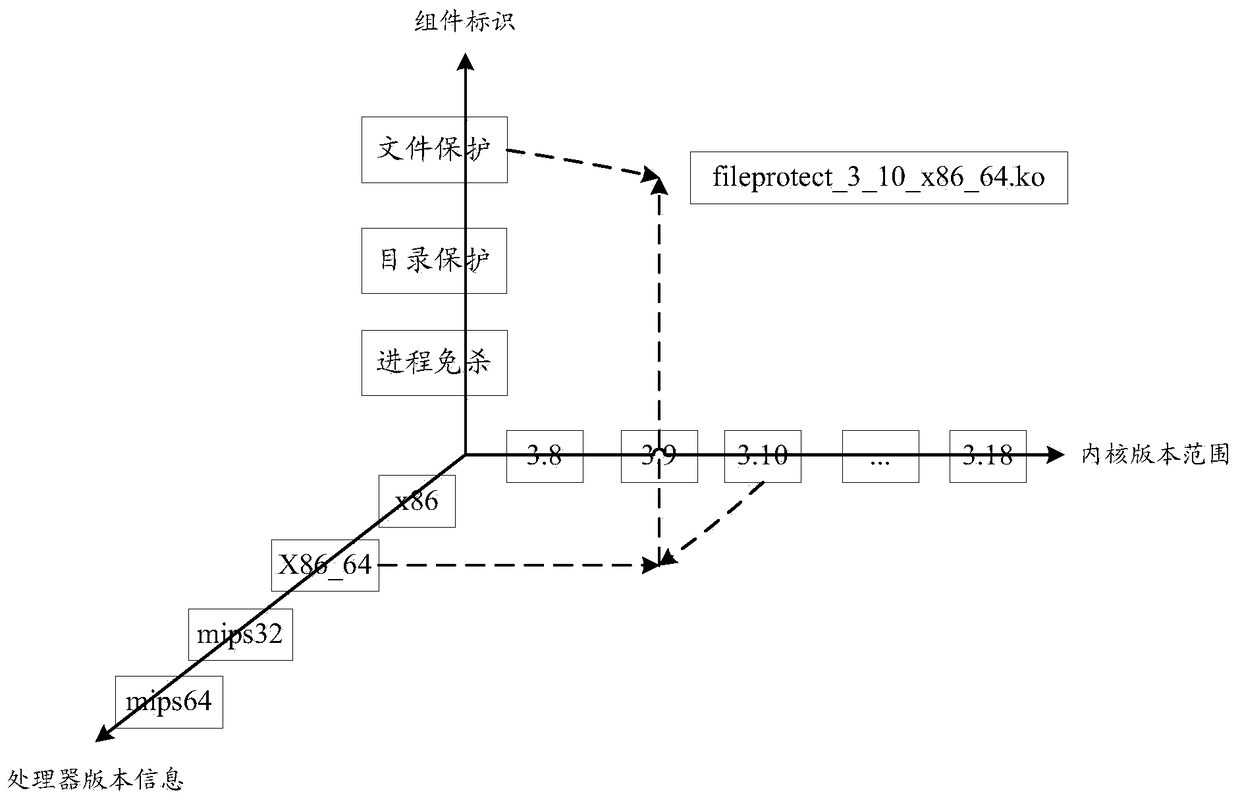
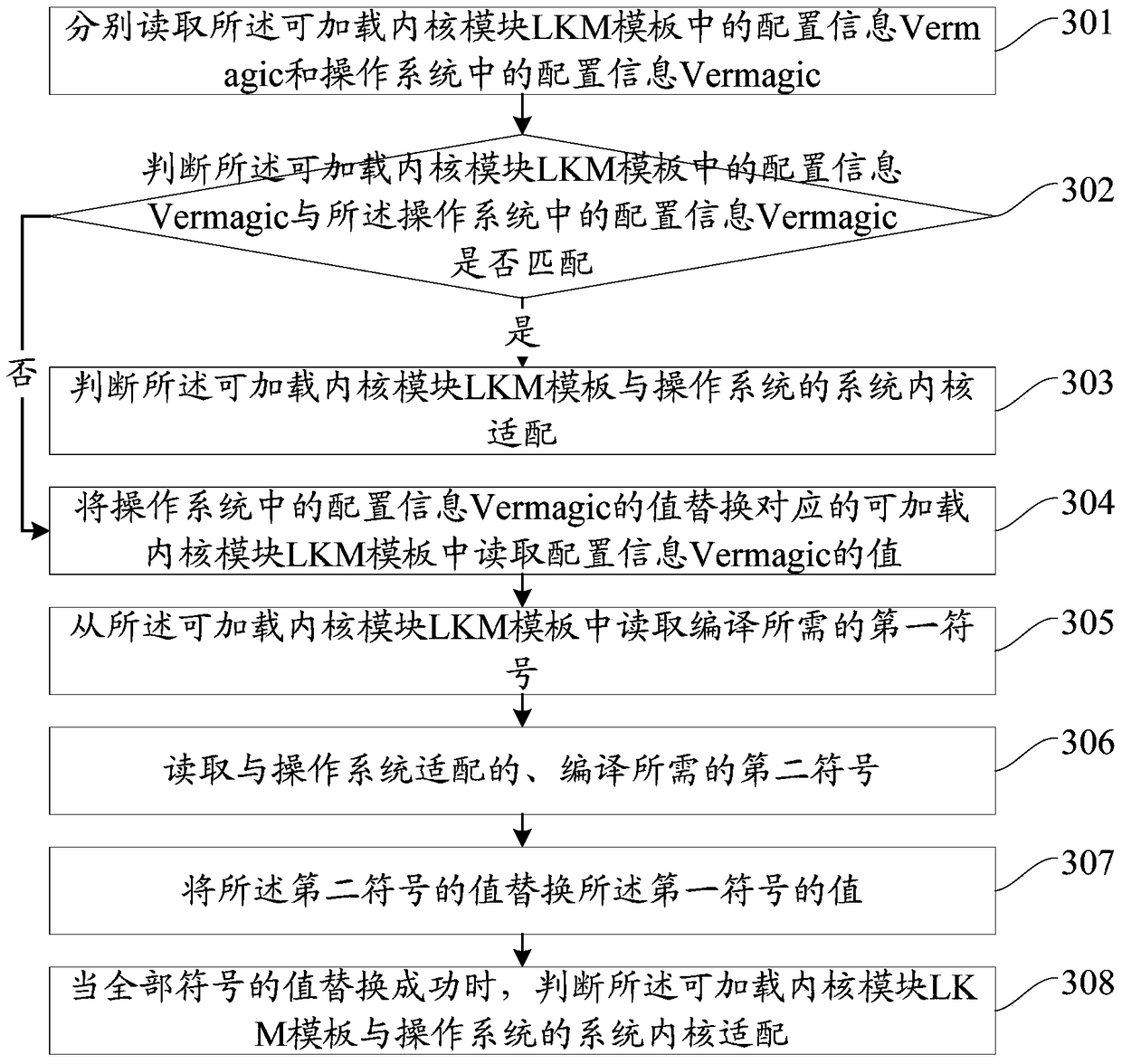
Compilation method and device for a loadable kernel module
ActiveCN104572235BReduce workloadLow costProgram loading/initiatingCode compilationComputer moduleWorkload
Owner:三六零数字安全科技集团有限公司
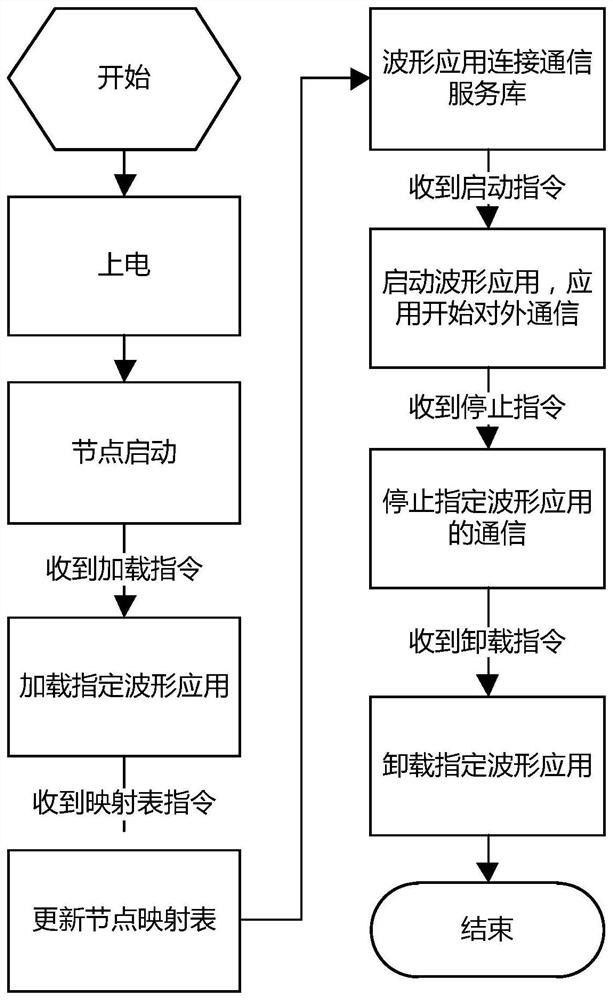
VxWorks real-time process-oriented modem hardware abstraction layer
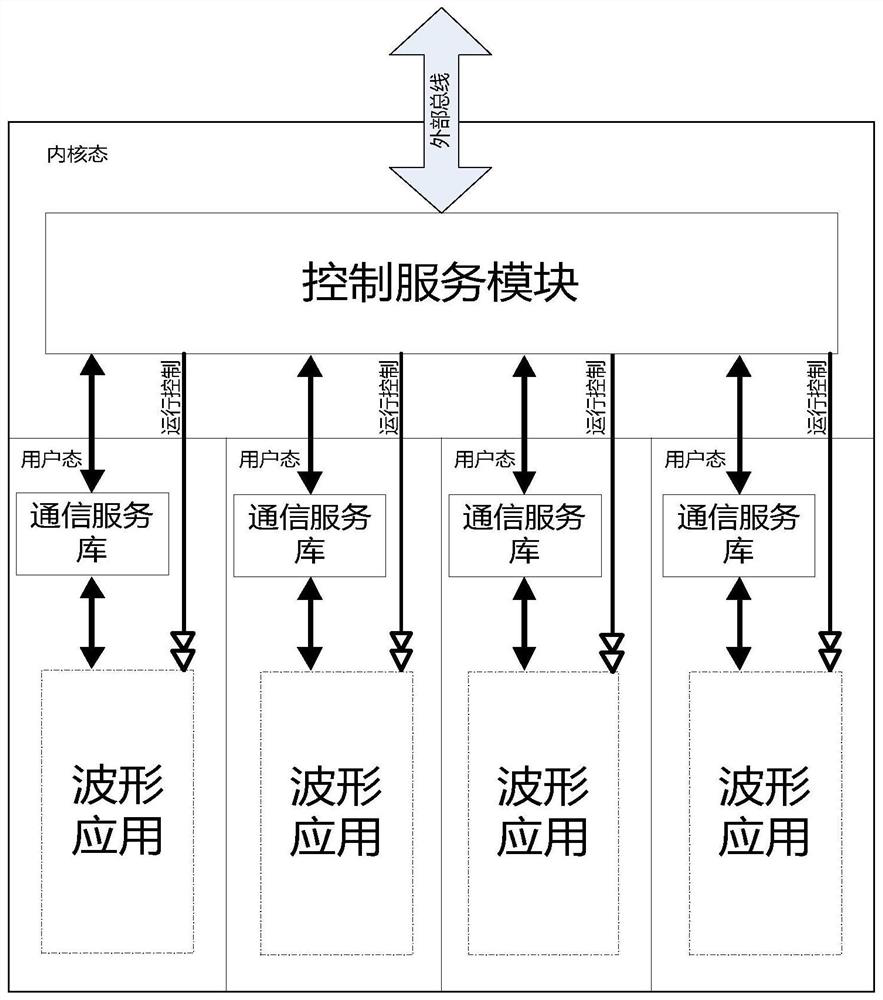
PendingCN113806106AHighly integratedReliable Multi-Waveform Deployment EnvironmentResource allocationInterprogram communicationAbstraction layerComputer architecture
The invention discloses a VxWorks real-time process-oriented modem hardware abstraction layer, which comprises a communication service library and a control service module, the communication service library exists in the form of a VxWorks application shared library, the kernel interface provided for the waveform application by the control service module is registered to an operating system as a system call, and packaged to a software interface according to the SCA standard, and the software interface is used for dynamic calling of waveform application in a real-time process form; and the control service module is loaded and resided in the VxWorks operating system in a VxWorks loadable kernel module form, provides various functions of modulating and demodulating the hardware abstraction layer, and provides a related kernel interface for a communication service library to register. The invention can solve the engineering problem that a single processor node deploys a plurality of applications, and improves the integration level of the system.
Owner:CHINESE AERONAUTICAL RADIO ELECTRONICS RES INST
Method and device for guaranteeing system security
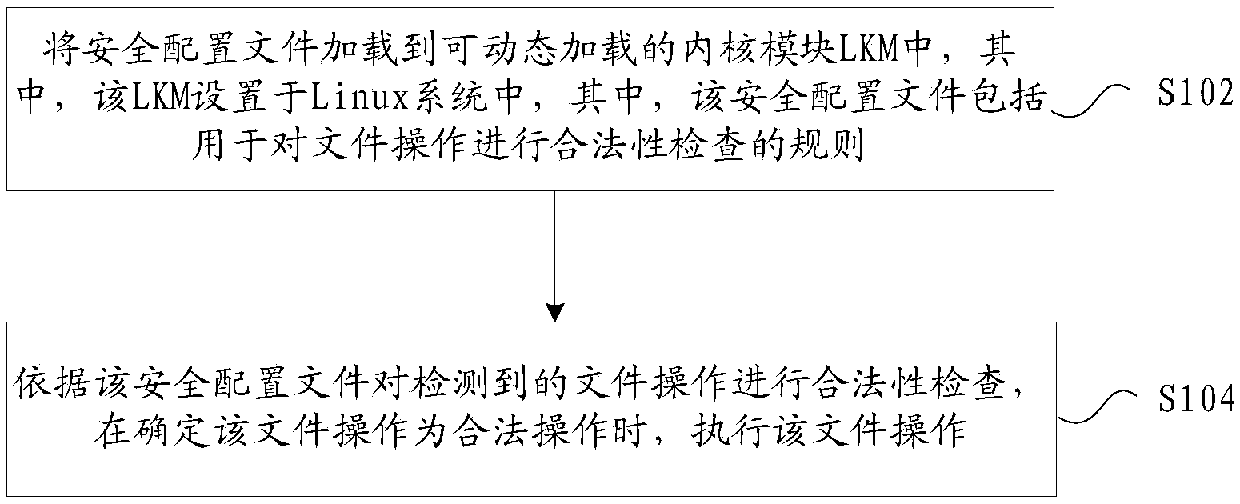
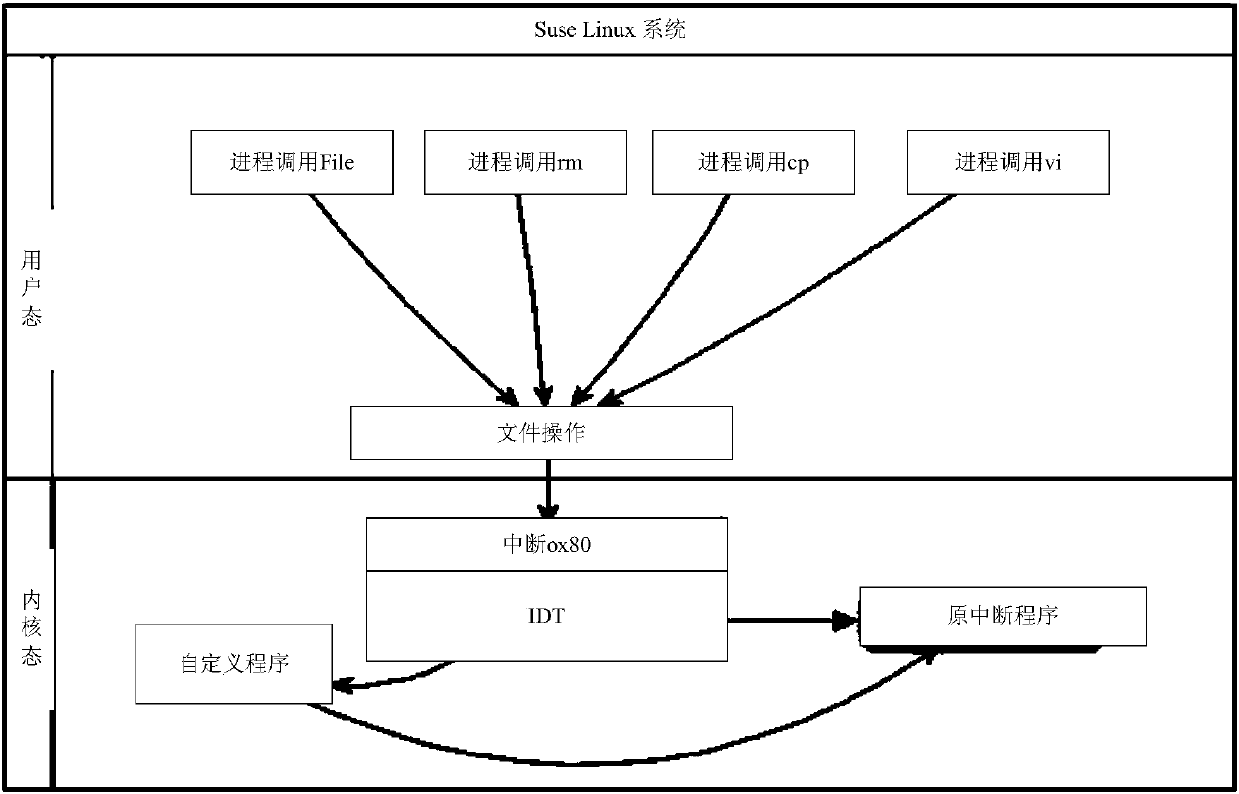
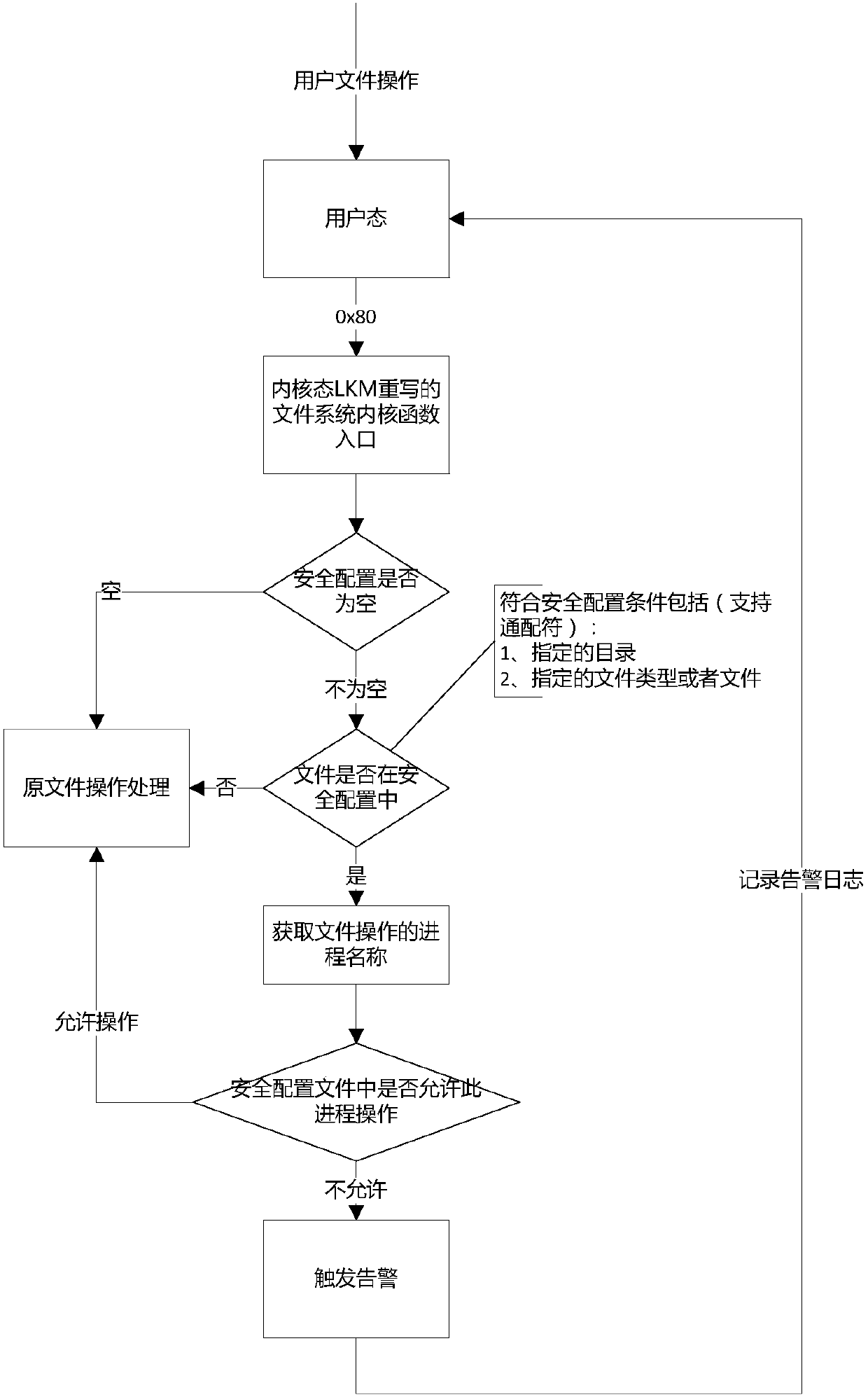
ActiveCN107818260ASolve the problem of low security levelImprove securityDigital data protectionDigital data authenticationComputer moduleSecurity level
The invention provides a method and device for guaranteeing the system security. The method includes the steps that a dynamic-loadable kernel module (LKM) is set in a Linux system of an EPG device, and preset security configuration files are loaded in the LKM; when file operation is carried out, whether the file operation is legal or not is detected according to the security configuration files; under the condition that the file operation is legal, the file operation is carried out, and if the file operation is illegal, the file operation is refused to be carried out. By means of the method and device for guaranteeing the system security in the technical scheme, the problem that the security level of the EPG device in the related technology is low is solved, and the security of the EPG device is greatly improved.
Owner:ZTE CORP
Method for debugging static memory corruption
InactiveUS20170364400A1Memory architecture accessing/allocationMemory systemsLoadable kernel moduleVirtual storage
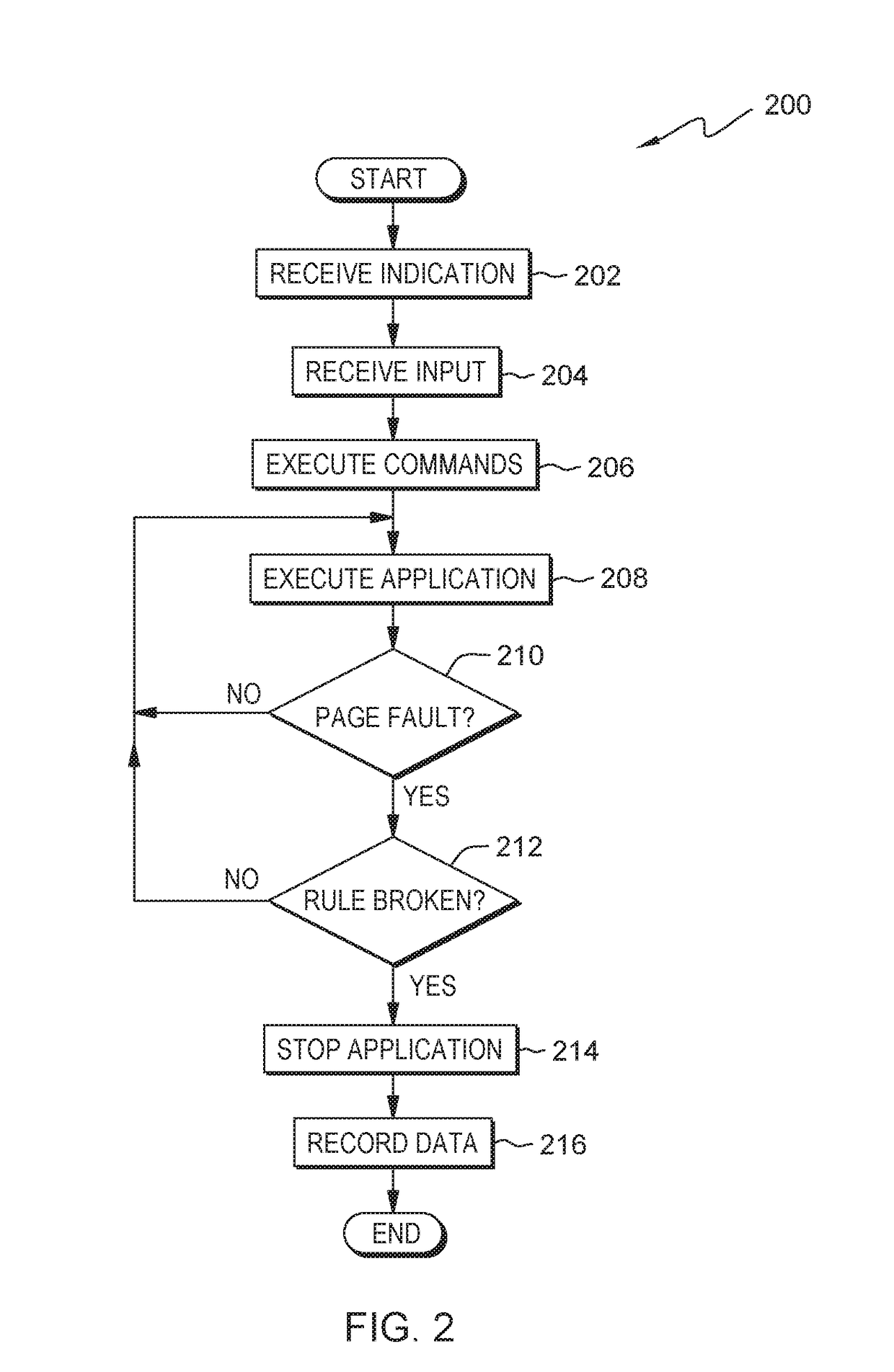
An indication is received. The indication is of an address in a first page in virtual memory used by an application with a static memory corruption. A loadable kernel module will monitor the address. Access to the first page in virtual memory is changed from read / write access to read only access. A second page in virtual memory is created with read / write access. Whether a page fault occurs on the first page in virtual memory during the execution of the application with the static memory corruption is determined.
Owner:IBM CORP
Kernel update method and device, computer equipment
ActiveCN107003880BShorten the timeSave time and costSoftware engineeringInterprogram communicationLogic moduleOperating system
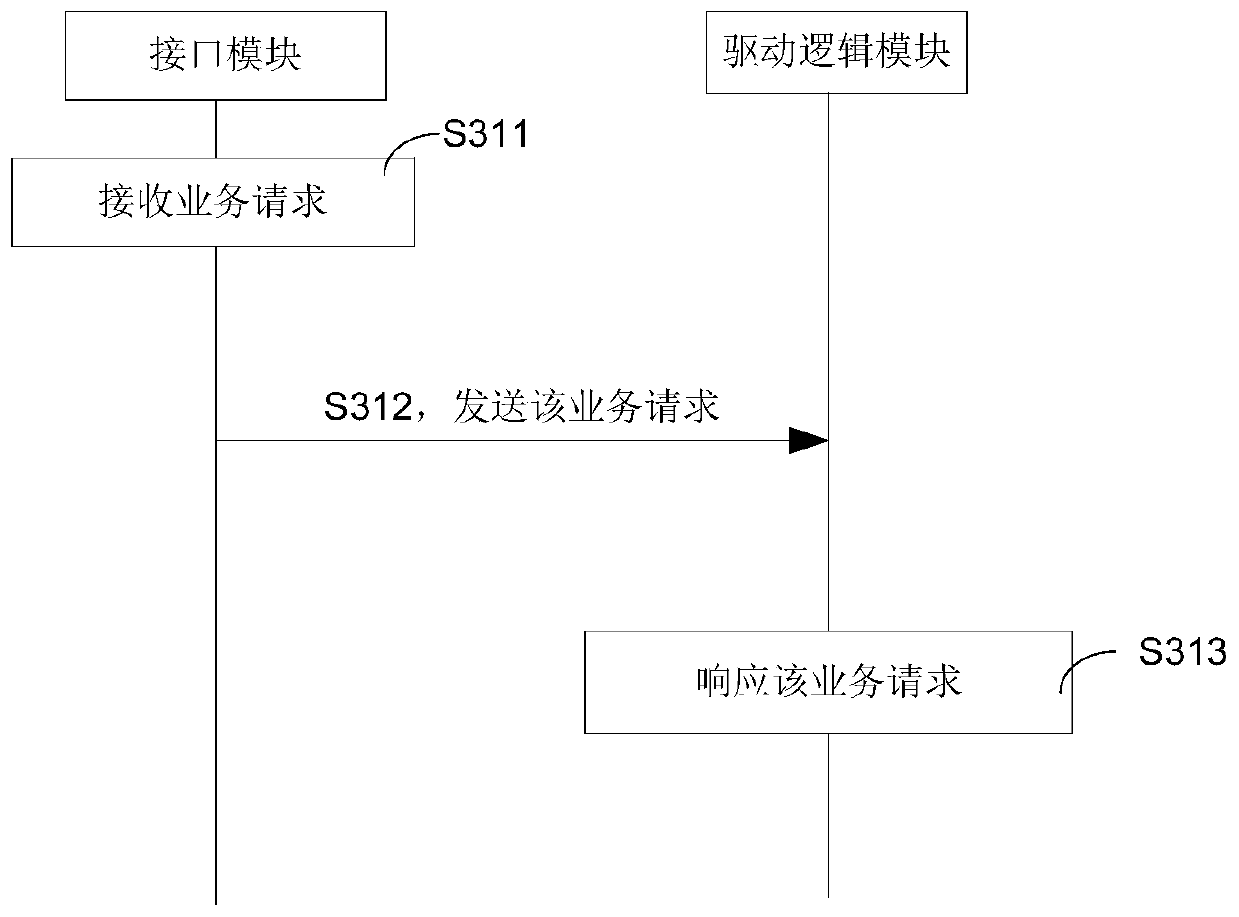
The invention relates to the computer field, and discloses a kernel update method and device, and computer equipment. The computer device executes the kernel update method to update the loadable kernel module in the kernel; firstly, the first interface mapping table is set to invalid, and the invalid first interface mapping table makes the interface module stop sending service requests of business applications to the first The driving logic of the driving logic module, so that the first driving logic module suspends providing driving services for business applications; then replace the first driving logic module in the loadable kernel module with the second driving logic module, and add it in the second interface mapping table Each interface in the interface module and the driving logic in the second driving logic module corresponding to the interface are recorded in . After the loadable kernel module is updated, the second driver logic module executes the driver logic on the new service request forwarded by the interface module according to the second interface mapping table, so as to resume providing driver services for business applications.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Kernel state rootkit detection method based on system virtualization technology
ActiveCN103310152BGuarantee authenticityTimely and effective detection of intrusionPlatform integrity maintainanceVirtualizationView based
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com