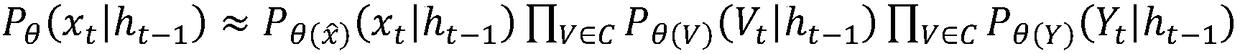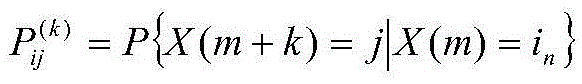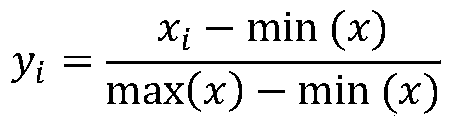Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
206 results about "Information science" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information science is a field primarily concerned with the analysis, collection, classification, manipulation, storage, retrieval, movement, dissemination, and protection of information. Practitioners within and outside the field study application and usage of knowledge in organizations along with the interaction between people, organizations, and any existing information systems with the aim of creating, replacing, improving, or understanding information systems. Historically, information science is associated with computer science, psychology, technology and intelligence agencies. However, information science also incorporates aspects of diverse fields such as archival science, cognitive science, commerce, law, linguistics, museology, management, mathematics, philosophy, public policy, and social sciences.
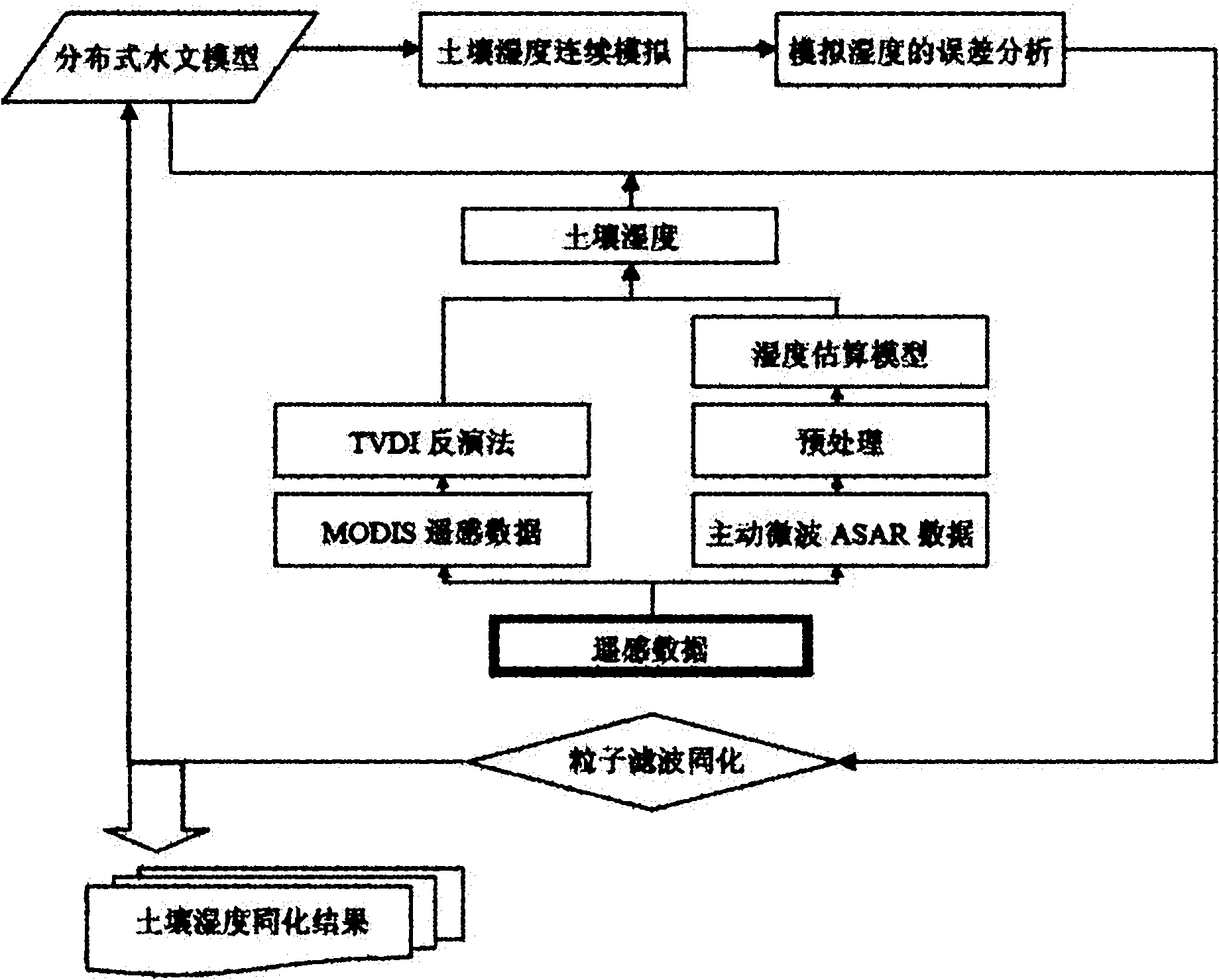
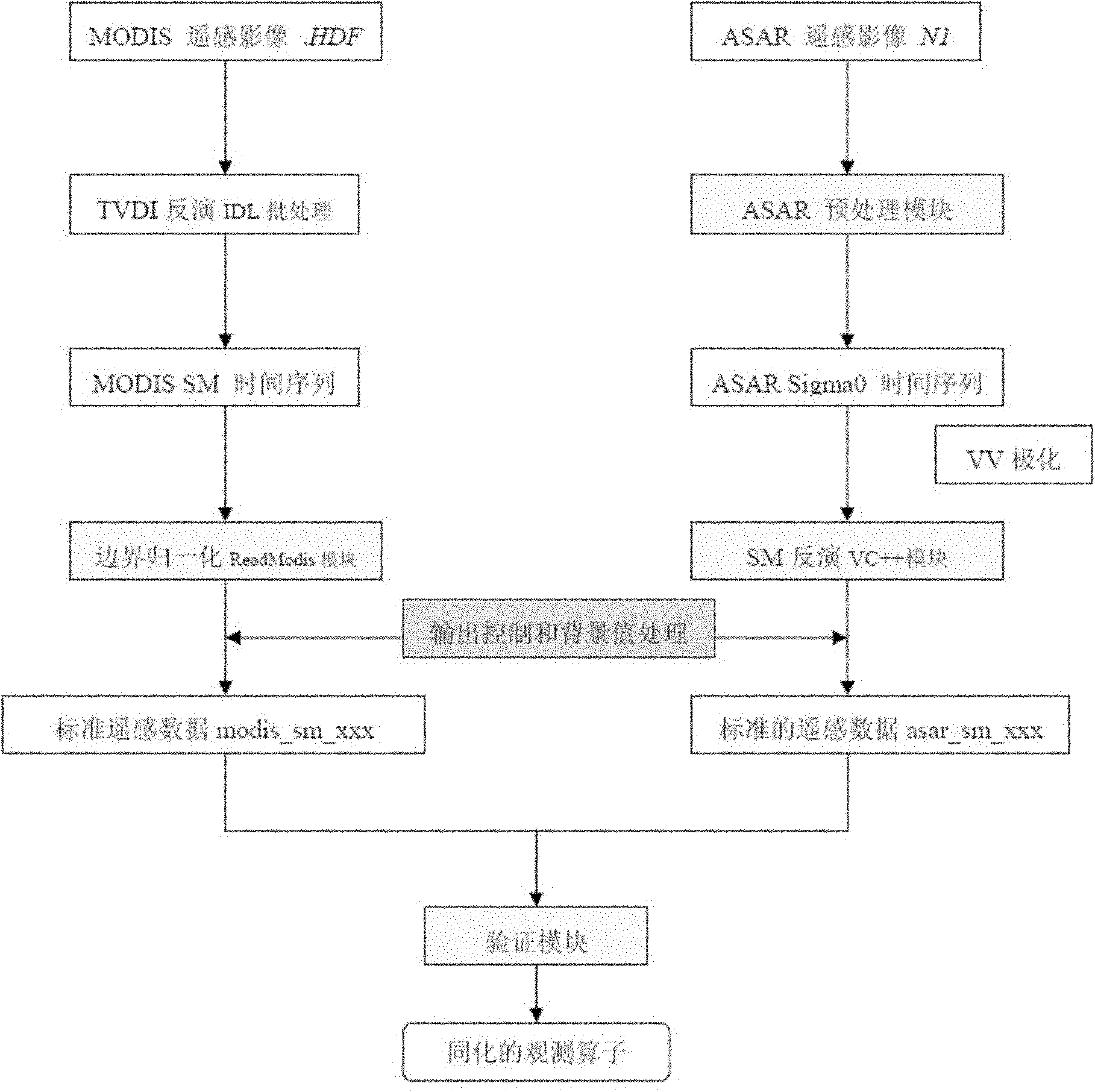
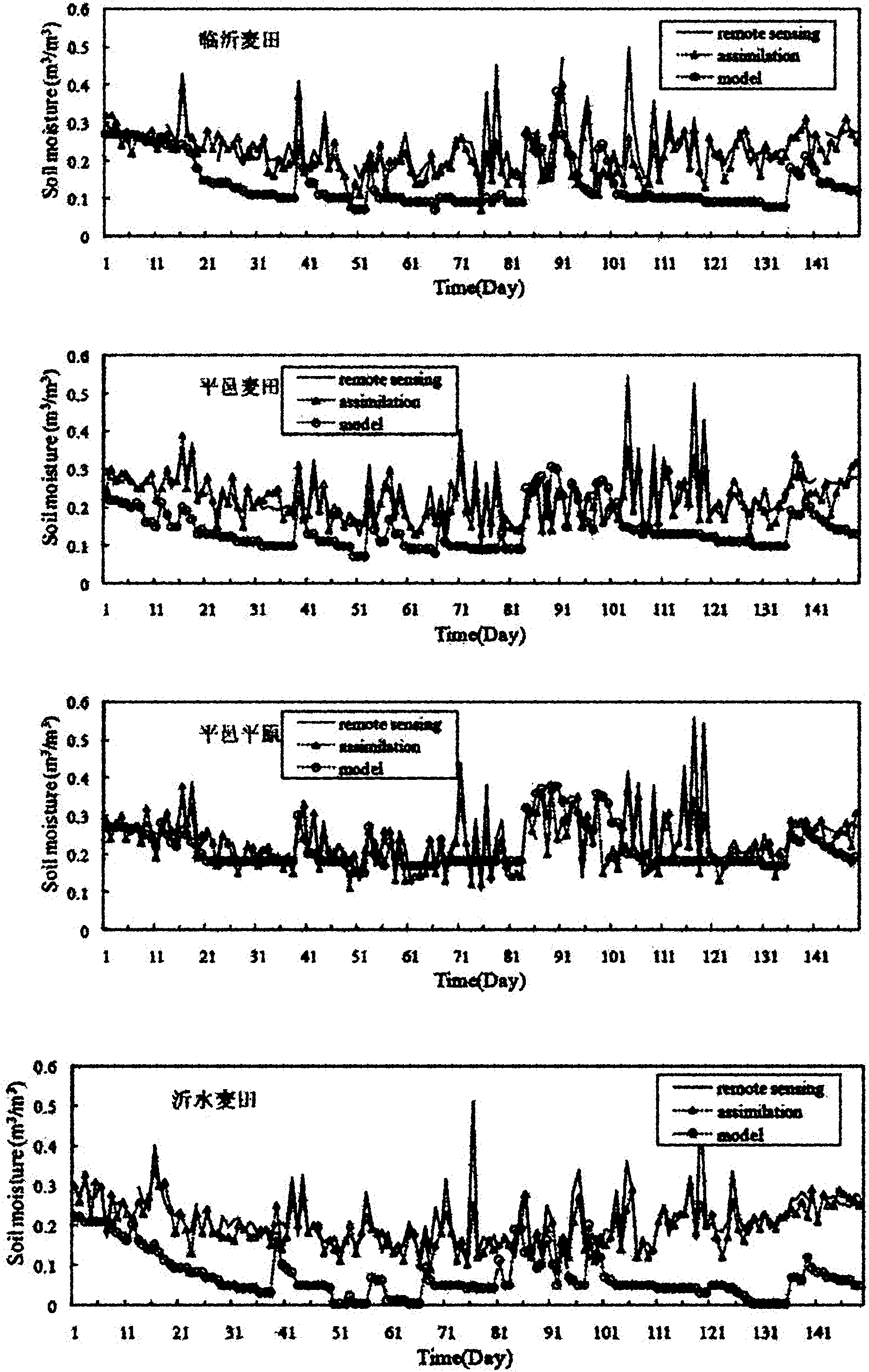
Method for assimilating remote sensing data of soil humidity in watershed scale
InactiveCN102034027AEfficient integrationGood day-to-day runoff simulationSpecial data processing applicationsSoil moisture contentDrainage basin
The invention provides a method for assimilating remote sensing data of soil humidity in a watershed scale. The method comprises the following steps of: improving a watershed runoff producing calculation module and developing a distributed hydrological model which is suitable for assimilating remote sensing soil humidity information and describes a soil hydrodynamic process; introducing a particle filtering sequence data assimilation method of information science, and continuously merging and assimilating new remote sensing observation data in a dynamic operation process of distributed hydrological process numerical simulation so as to acquire updated watershed soil humidity assimilated data during sequential assimilation; feeding the updated watershed soil humidity assimilated data back to a distributed hydrological model platform; and gradually estimating the time and space distribution pattern of watershed soil moisture content. Practices prove that by the method, not only high-precision and physically consistent watershed soil humidity data can be provided for research on hydrology, zoology, environment and agriculture, but also the foundation is laid for performing four-dimensional data assimilation processing on soil humidity data of an upper soil layer acquired by using remote sensing retrieval, and improving the precision of the model.
Owner:NANJING UNIV
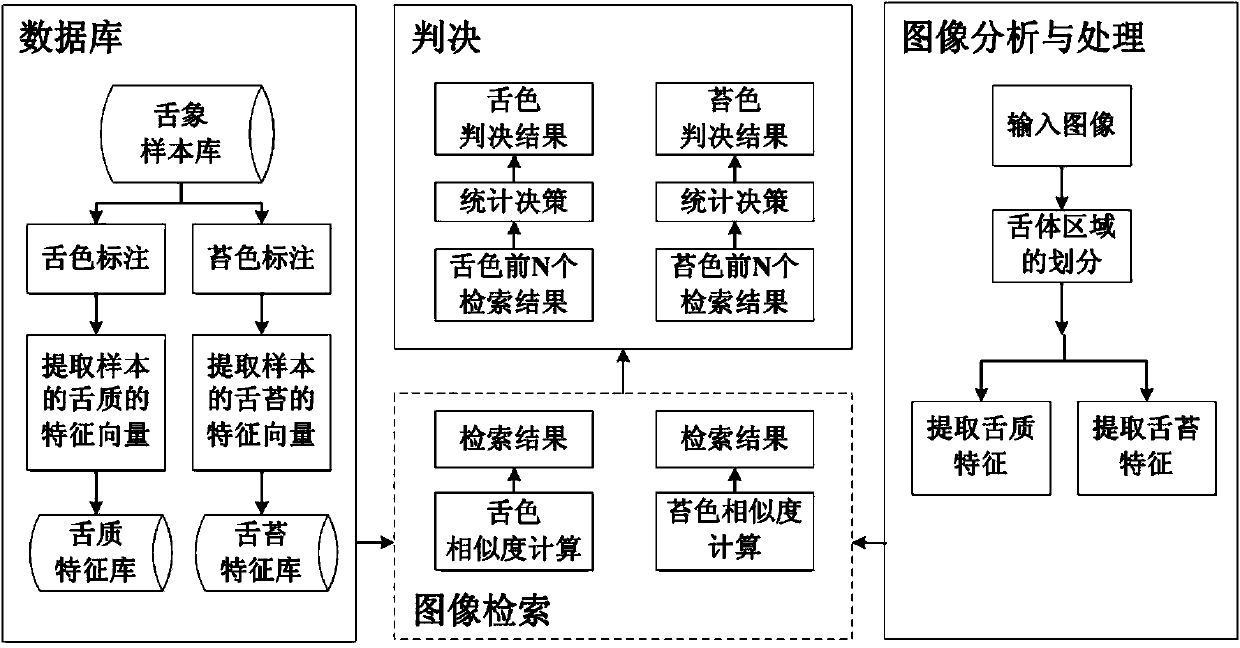
Automatic analysis method of tongue color and coating color in traditional Chinese medicine based on image retrieval
ActiveCN103745217AAccurate automatic classificationCharacter and pattern recognitionSpecial data processing applicationsCoated tongueImage retrieval
The invention discloses an automatic analysis method of a tongue color and a coating color in traditional Chinese medicine based on image retrieval, and belongs to the field of interdiscipline of information science and traditional Chinese medicine. In view of the characteristics that a result of tongue diagnosis in traditional Chinese medicine varies with different individuals, has strong subjectivity and lacks of normalization and standardization, the automatic analysis method of the tongue color and the coating color in the traditional Chinese medicine based on the image retrieval is designed. The automatic analysis method is characterized by comprising the following steps of inputting a tongue image to be analyzed by a user, firstly, segmenting a tongue body region through a tongue body segmentation technology, carrying out regional division on a tongue surface, distinguishing a tongue nature region and a coated tongue region, distinguishing a visual feature of the image in each region so as to form a feature vector, secondly, computing similarity of the feature vector and the feature of a tongue picture of a marked tongue image in a feature library, returning a most similar image as a retrieved result, and lastly, judging the retrieved result by utilizing a method of statistical decision, and respectively giving classification suggestions to the tongue color and the coating color in the tongue picture. According to the automatic analysis method, a classification result is more accurate and has a certain practical value.
Owner:BEIJING UNIV OF TECH
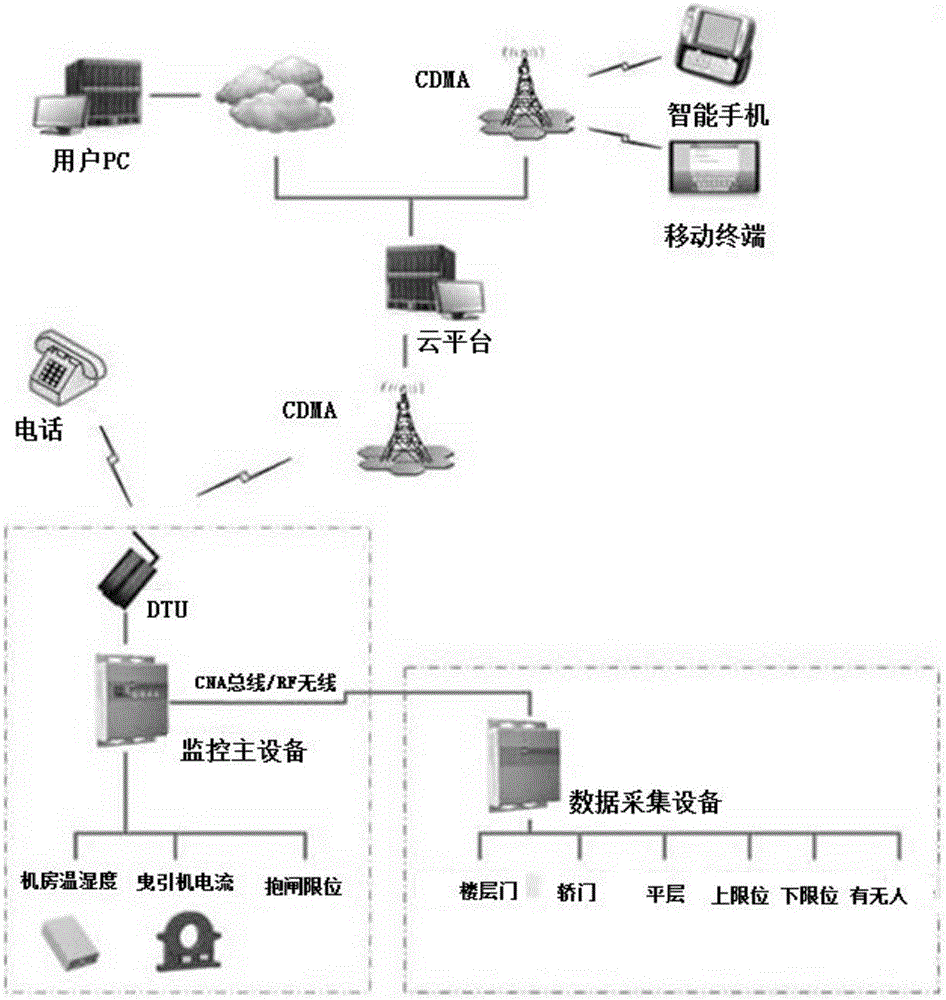
Intelligent monitoring system for elevator safe operation based on IOT (Internet of Things) technology
InactiveCN105035904AImprove your own securityEffectively guide productivityElevatorsInformatizationMonitoring system
The invention discloses an intelligent monitoring system for elevator safe operation based on IOT (Internet of Things) technology. The intelligent monitoring system is mainly designed for government regulation departments, maintenance units, manufacturers, property management companies and the like, and provides the above with a set of intelligent, platform-based total management system which supports wireless access and remote access, so that safe operation, management, maintenance and detection of an elevator can be more effectively realized. While daily needs are met, monitoring on the elevator is more normalized, institutionalized and scientized, so that elevator accidents are further reduced, and speed and quality for solving problems after an accident occurs are improved; by utilizing information for driving, the informatization management level of the intelligent monitoring system is improved through advanced and applicable technology and exploitation and construction pattern innovation by comprehensively utilizing information science and technology as well as decision making and management methods, and an emergency response system of elevator safety is favorably established.
Owner:JIESHOU XUNLIDA ELEVATOR CO LTD
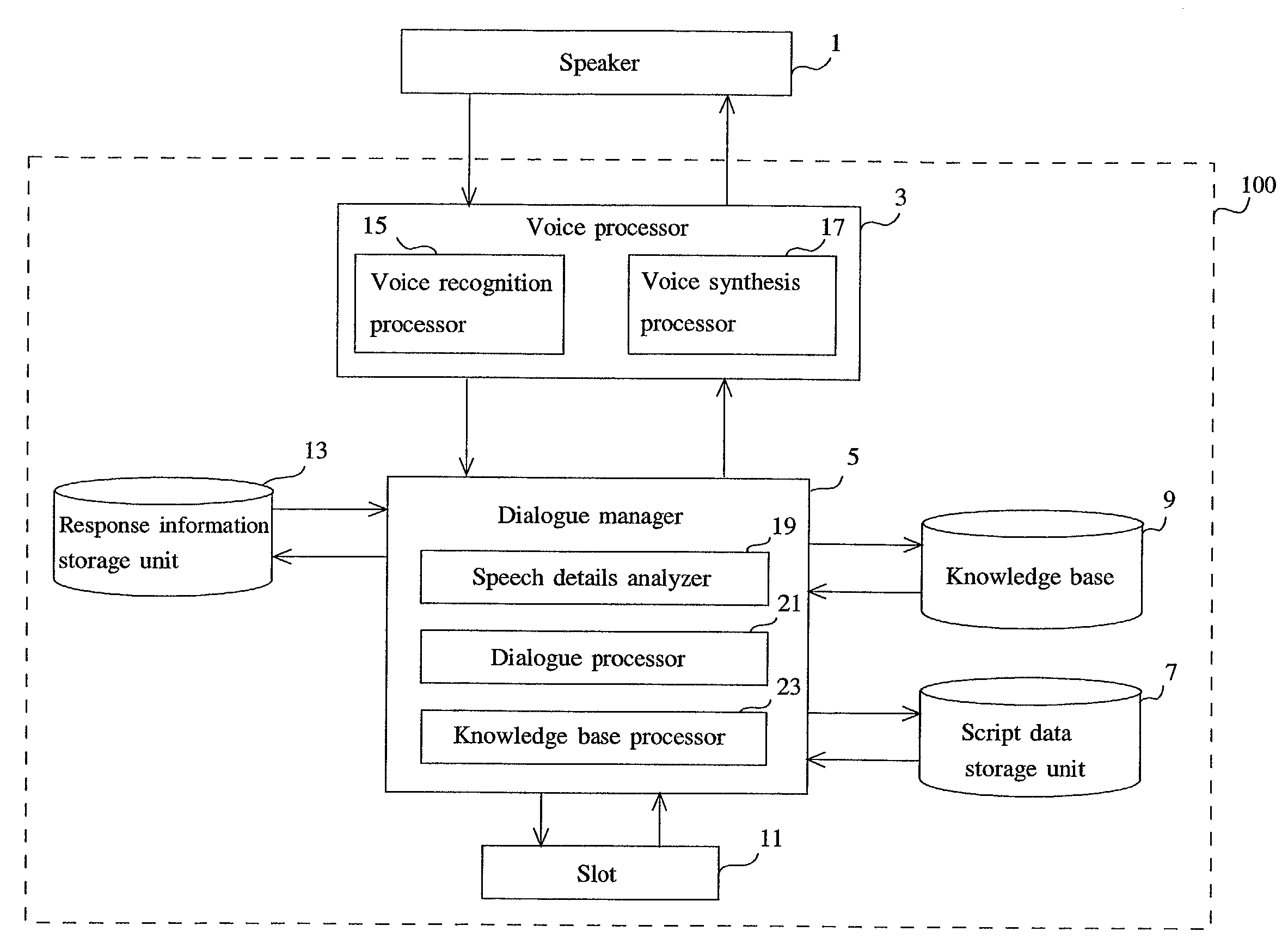
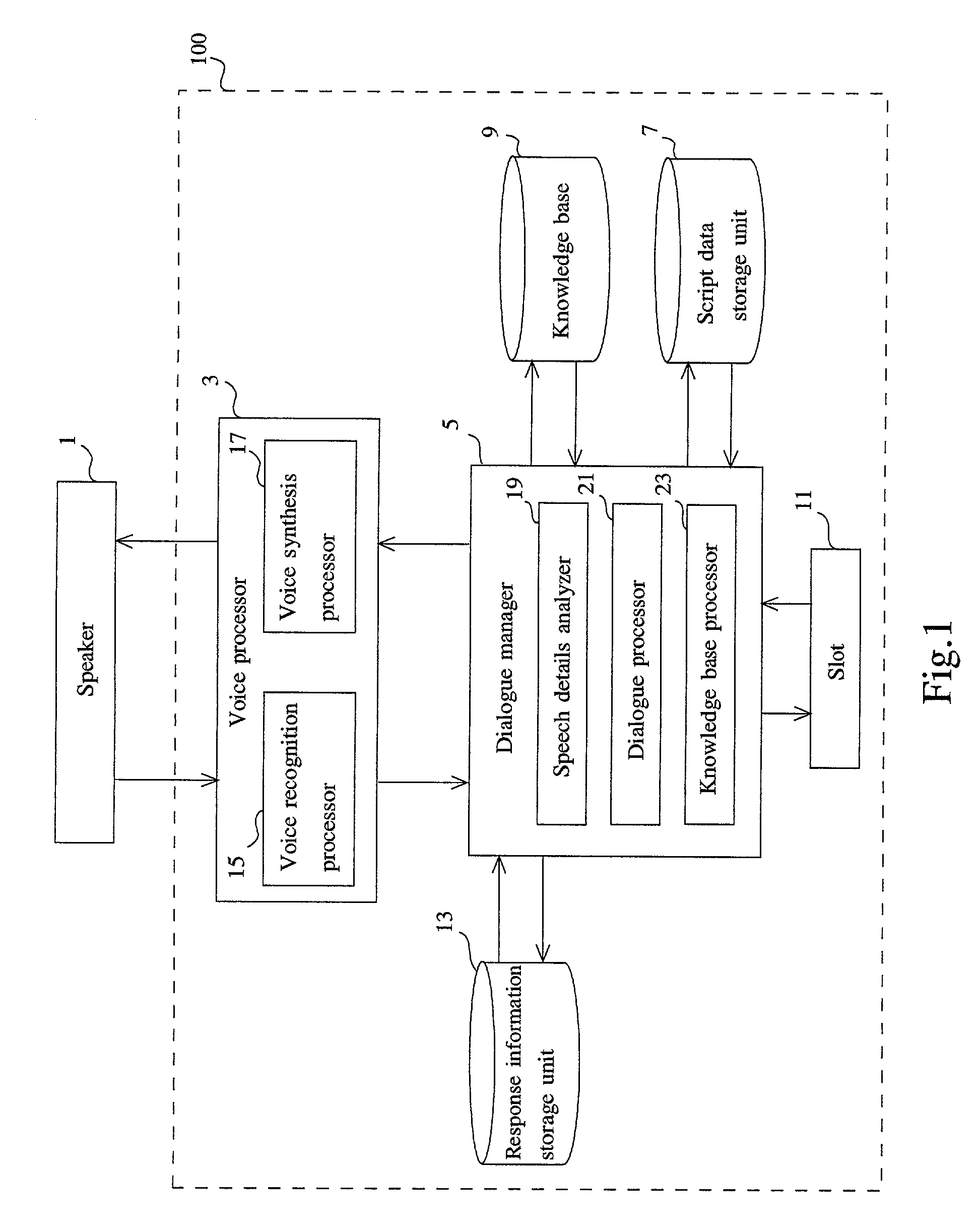
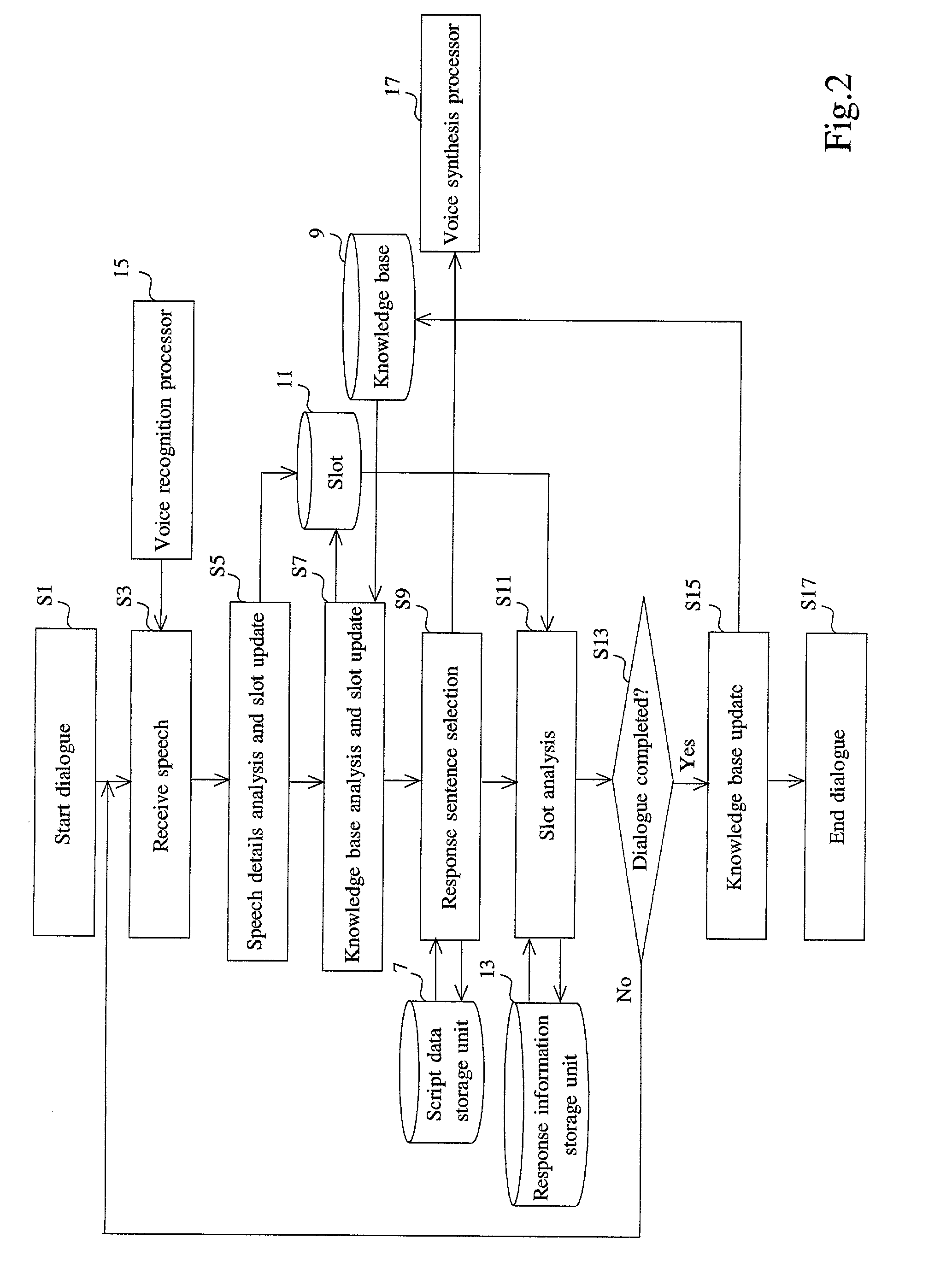
Dialogue processing system and method
InactiveUS7020607B2Simple configurationEfficient collectionSemantic analysisReservationsHandling systemHuman–computer interaction
An object of the present invention is to realize a natural dialogue with a system having a simple configuration. The dialogue processing system of the present invention to perform a dialogue with a user, comprises: a plurality of slots (slot 11), wherein each of the slots is a storage area storing a preset information item (for example, boarding date, departure point, destination, or flight name) that are required to achieve the purpose of the dialogue with the user (for example, an airline ticket reservation); an analyzer (the speech details analyzer 19) for extracting information corresponding to the information items from information (for example, free sentence entered in natural language) entered by the user in the dialogue and for storing the extracted information in the slot for that information item; and a response processor (the dialogue processor 21) for outputting response information (a sentence prompting the input of insufficient information) to the user in accordance with information storage state of the slots.
Owner:FUJITSU LTD
Distributed remote sensing data organization query method based on NoSQL database
InactiveCN103020325AEfficient storageEfficient managementSpecial data processing applicationsSensing dataUser input
The invention belongs to the technical field of zoology and remote sensing information science and relates to a distributed remote sensing data organization query method based on the NoSQL database. The method includes the steps: preprocessing an original remote sensing data file, and outputting an initial remote sensing image file according to an appointed format, extracting data of each pixel and data element information in the initial remote sensing image file; reconstructing the extracted data of each pixel and data element information as unstructured text data; storing the unstructured text data in the distributed NoSQL database, and setting up query indexes; and returning corresponding remote sensing data to users according to query conditions inputted by the users, and regenerating image files. The distributed remote sensing data organization query method based on the NoSQL database can be used for effectively storing and managing massive remote sensing data and can be applied to correlated fields of remote sensing ecological monitoring, species distribution forecast, remote sensing data inversion and the like.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
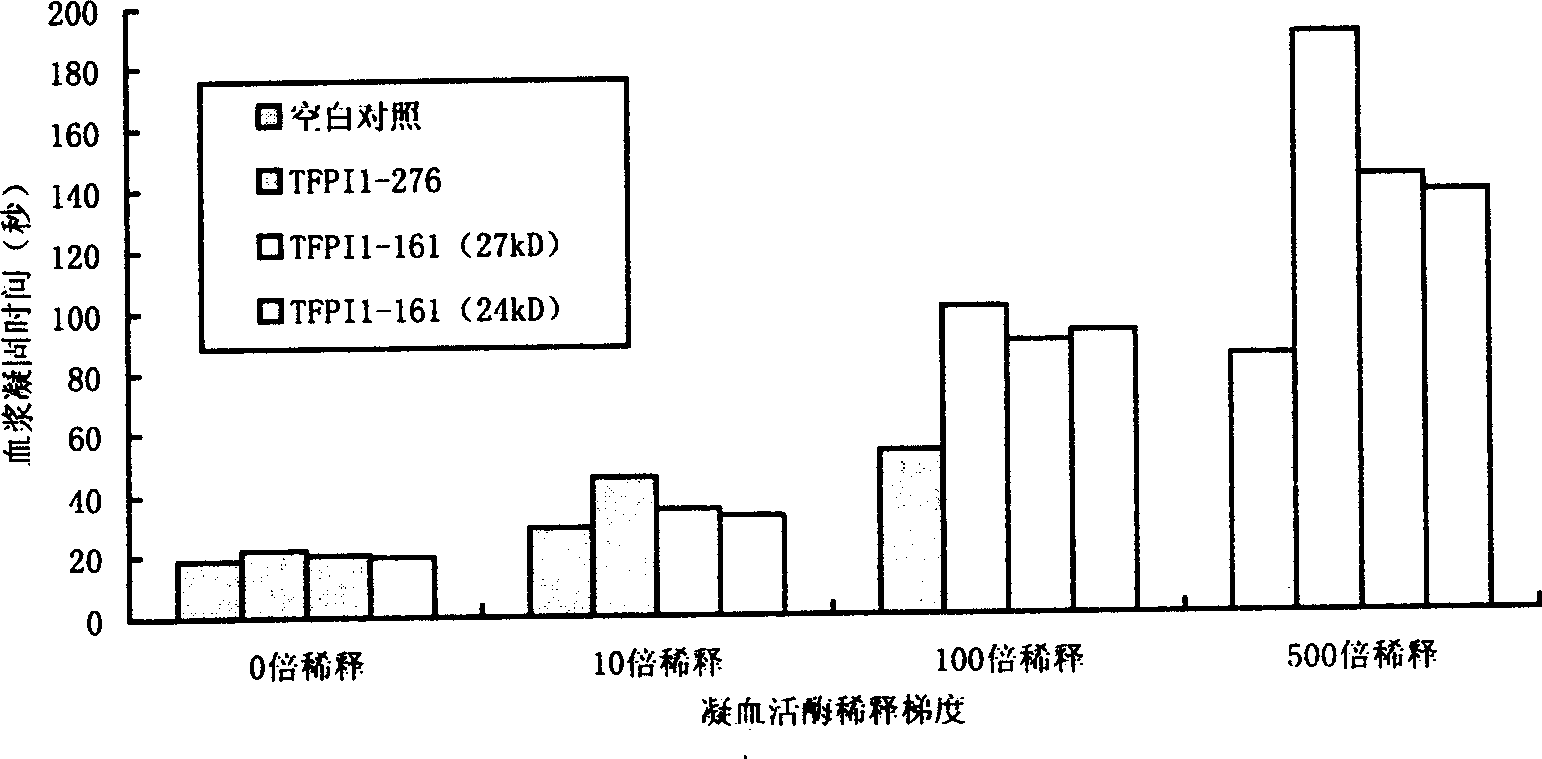
Long-acting reconbinant tissue factor channel inhibitor and preparing method thereof
InactiveCN1528894AExtended half-lifeHighly effective anticoagulantFermentationVector-based foreign material introductionBiotechnologyInclusion bodies
The invention belongs to biology technology field, which concretely refers to controlled release tissue factor path inhibitor (LTFPI) and the manufacturing method, and the application. The invention analyzes and experiments the biology information science and structure molecular biology science of tissue factor path inhibitor (TFPI) and its acceptor low density lipoprotein acceptor correspondent protein (LRP), it ascertains the part where the TFPI carboxy end combines with LRP and is eliminated. It designs TFPI carboxy end mutant, which is recombined with primary nucleus or eukarya expressing carrier after constructing LTFPI gene through PCR location, it converts bacillus coli or bici yeast, sifts the high expression project fungus. The primary project fungus are yeasted and expanded, crushed, then they are centrifugated and collects the inclusion body, purifies the LTFPI through molecular sift and ion interchanging two-step method; the eukarya project fungus are carried on with two-step purifying directly. The half-life are prolonged, it has good pour-depressant function.
Owner:海菲尔(辽宁)生物科技有限公司
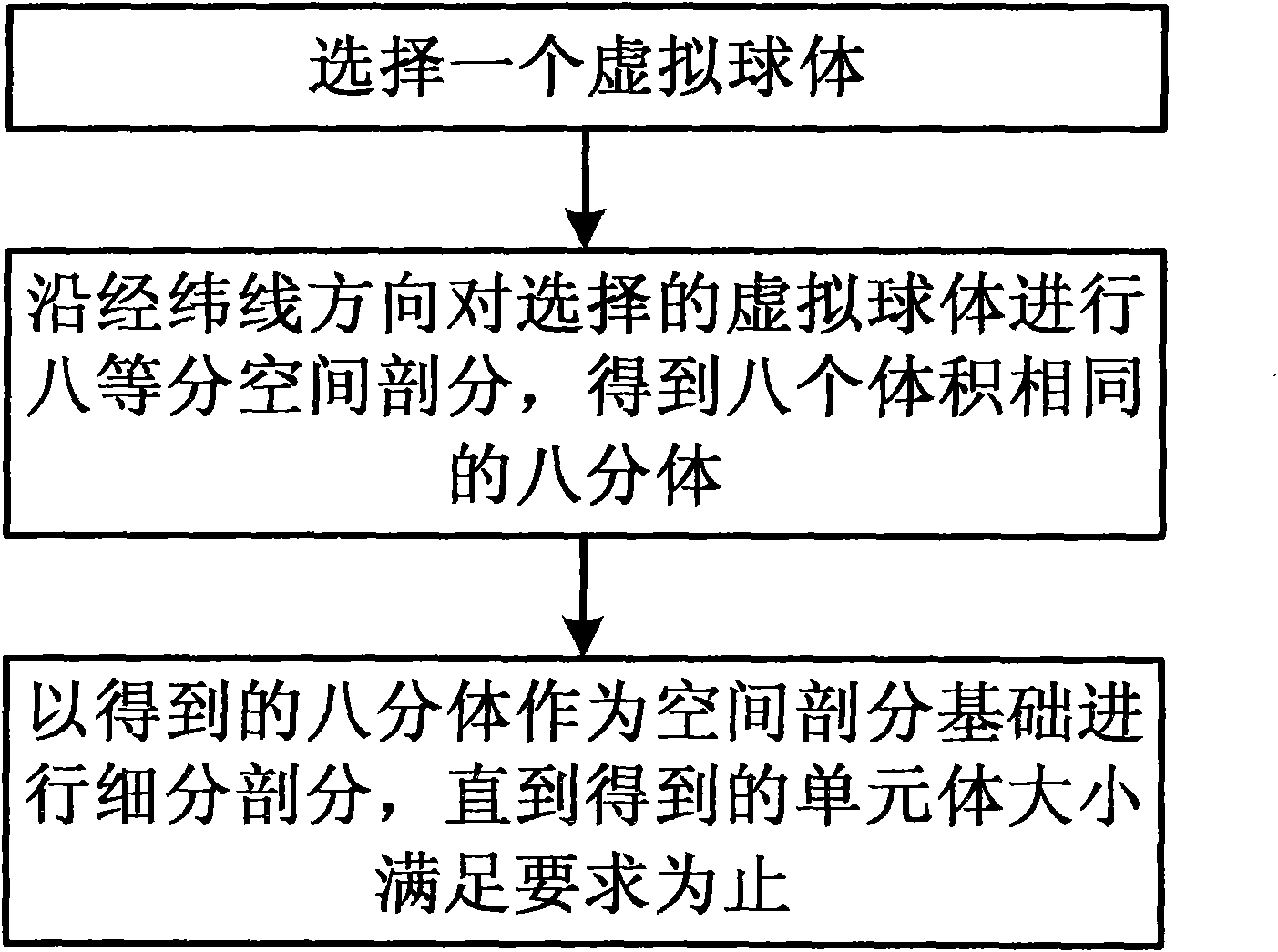
Method for realizing division of geospace three-dimensional grids
InactiveCN101599183ARealize multi-level overall division3D-image rendering3D modellingThree-dimensional spaceComputer science
The invention discloses a method for realizing division of geospace three-dimensional grids. The method comprises the following steps: selecting a virtual sphere; dividing the space of the virtual sphere into eight equal parts along the quadrillage direction to obtain eight octants with same volumes; performing degradation eight-ary tree recursive subdivision by taking the obtained octants as a space division basis until the size of the obtained unit body satisfies the requirement. The invention can realize the whole division to the geospace, fills the blank of the division of geospace three-dimensional grids and can build a global three-dimensional grid frame and be used in the key fields of geospace information sciences and technologies such as geospace data untied organization and code, geospace data integration management and shared utilization, global three-dimensional space multilayer model building and whole vision, and the like.
Owner:吴立新
Teaching experiment system based on alternating-current motor driving control method
ActiveCN102332223AWith over-current, short-circuit protectionWith short circuit protectionEducational modelsPermanent magnet synchronous motorData acquisition
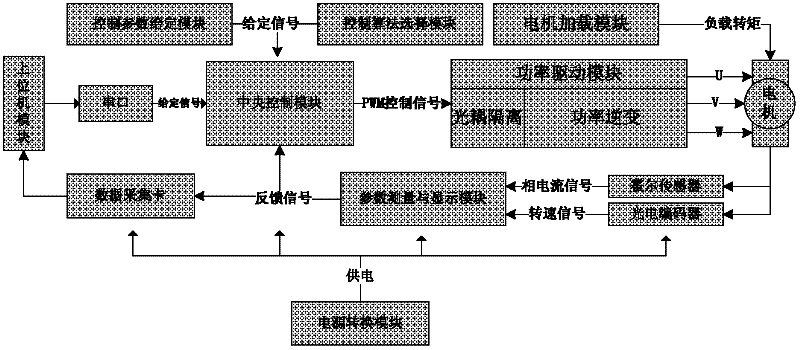
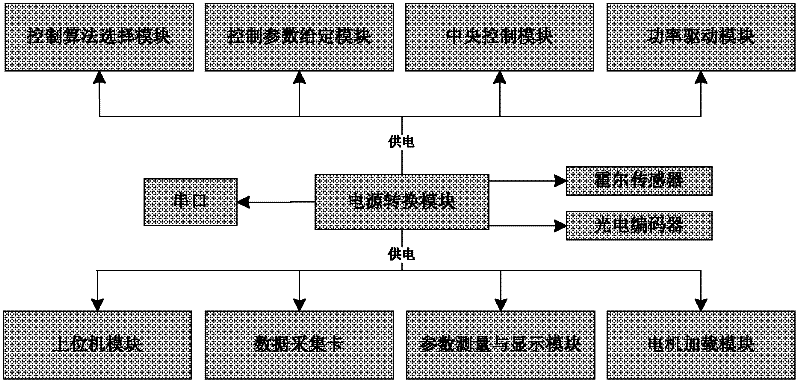
The invention belongs to the field of alternating-current motor control teaching instruments, and relates to the teaching of an advanced control algorithm of a permanent magnet synchronous motor and an asynchronous motor aiming at undergraduate students or postgraduate students, aiming to provide an alternating-current motor experiment teaching platform which is designed for undergraduate students or postgraduate students of the relevant majors, such as electrical engineering and automation of electrical and information science and technology, mechanical and electrical integration of colleges and universities of engineering courses. The teaching platform is tightly matched with teaching contents, can deepen the understanding of an alternating-current control theory and method for students, and simultaneously the operation ability of the students is strengthened. The experiment system comprises a power supply conversion module, a central control module, a power driving module, a control parameter set module, a control algorithm selection module, a parameter measuring and display module, a motor loading module, an upper computer module, a serial port, a data acquisition card, a hall sensor, a photoelectric encoder and a motor.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
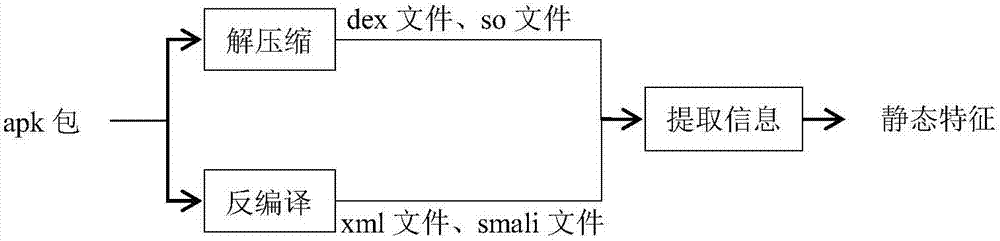
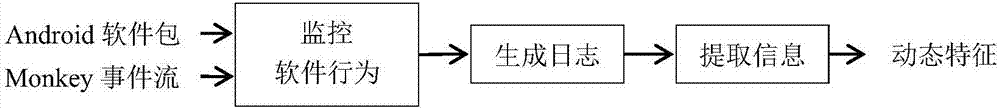
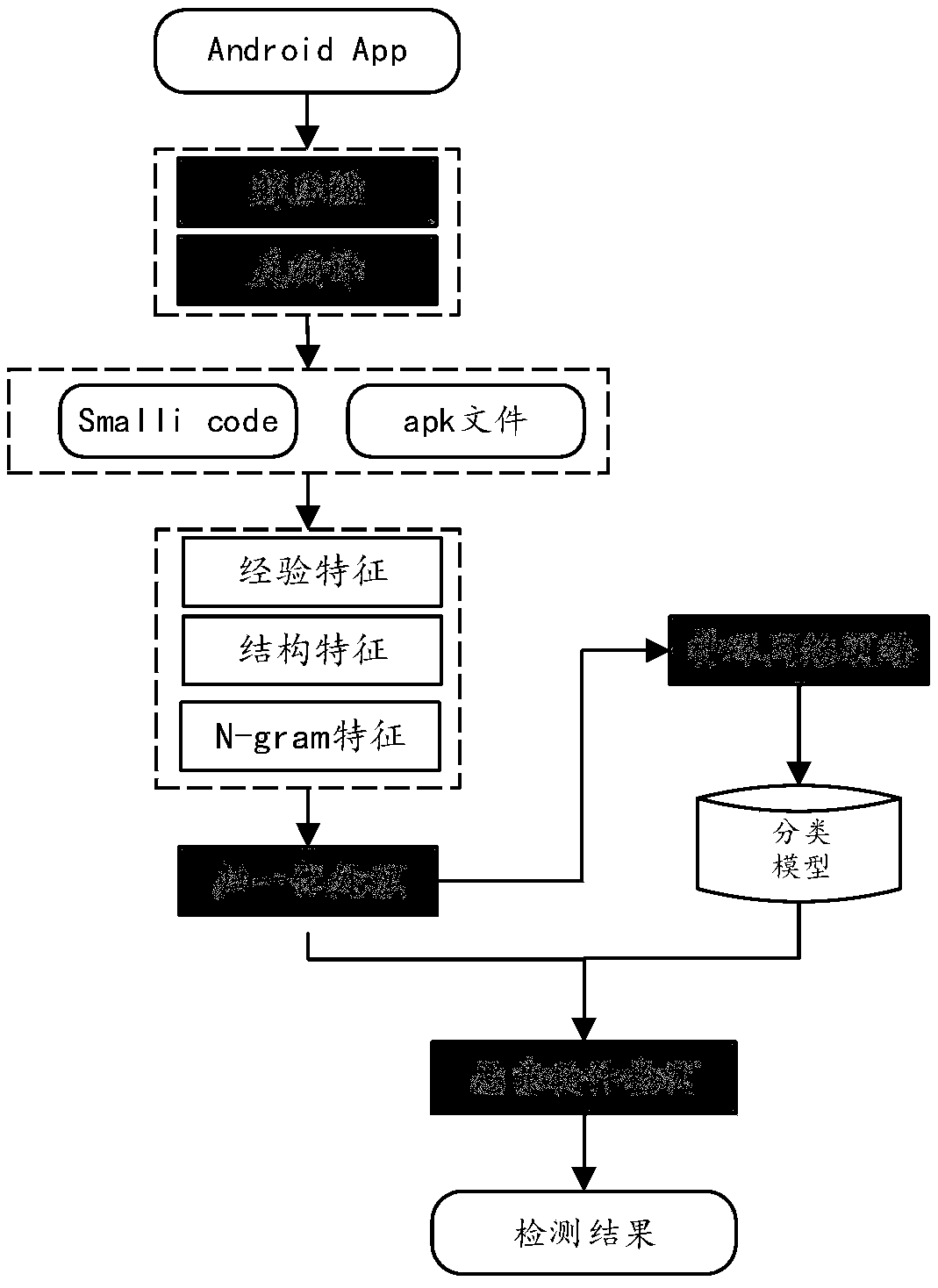
An Android unknown malicious software detection method based on dynamic behavior characteristics
InactiveCN107169351AWell representedImprove accuracyPlatform integrity maintainanceSoftware engineeringMalware
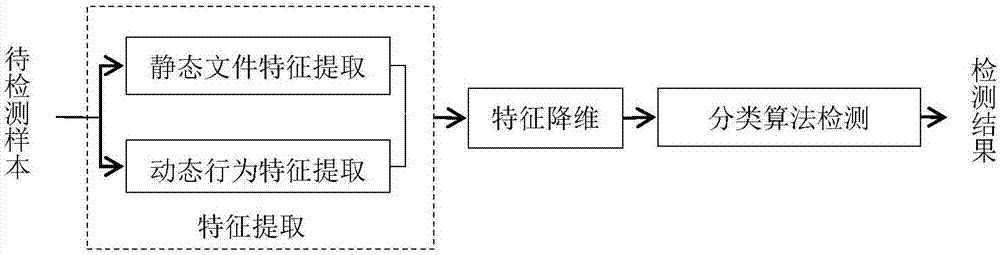
The invention relates to an Android unknown malicious software detection method based on dynamic behavior characteristics and belongs to the technical field of computers and information science. The method comprises the steps that to-be-detected software is input into a system; the system uncompresses and decompiles a software package and extracts static characteristics in a result file; at the same time, the system operates the software package in an Android simulator and monitors dynamic behavior of the software by using a behavior monitoring system based on an LKM (Loadable Kernel Module); the dynamic behavior is recorded in logs and the dynamic behavior characteristics of the software are extracted from the logs; the extracted dynamic and static characteristics are subjected to normalization processing and the results are input into a trained classification algorithm classification detection module; the module can automatically judge whether the detected software is malicious software or not according to the input dynamic and static characteristic data. The method has high detection efficiency and accuracy and can be applied to security detection of software platforms such as the Android application market.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
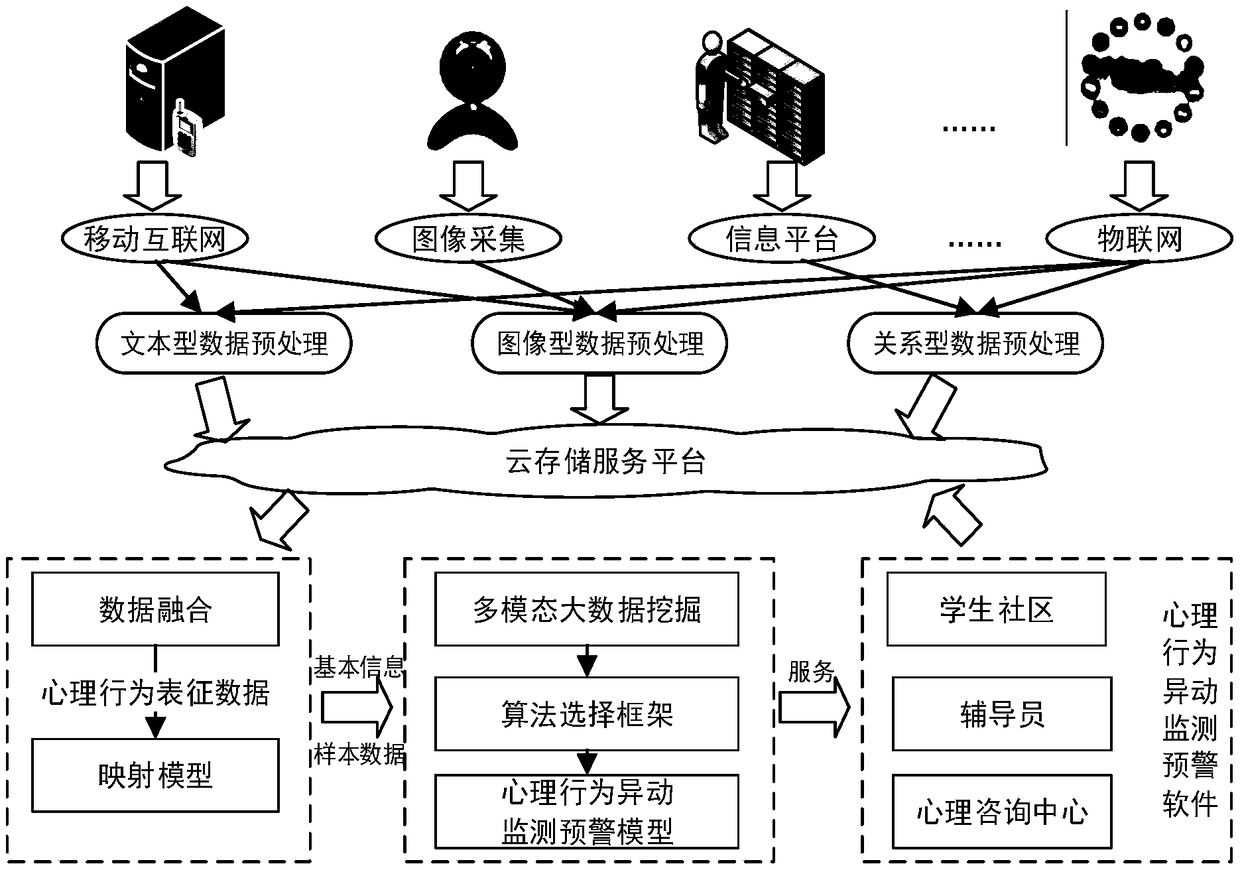
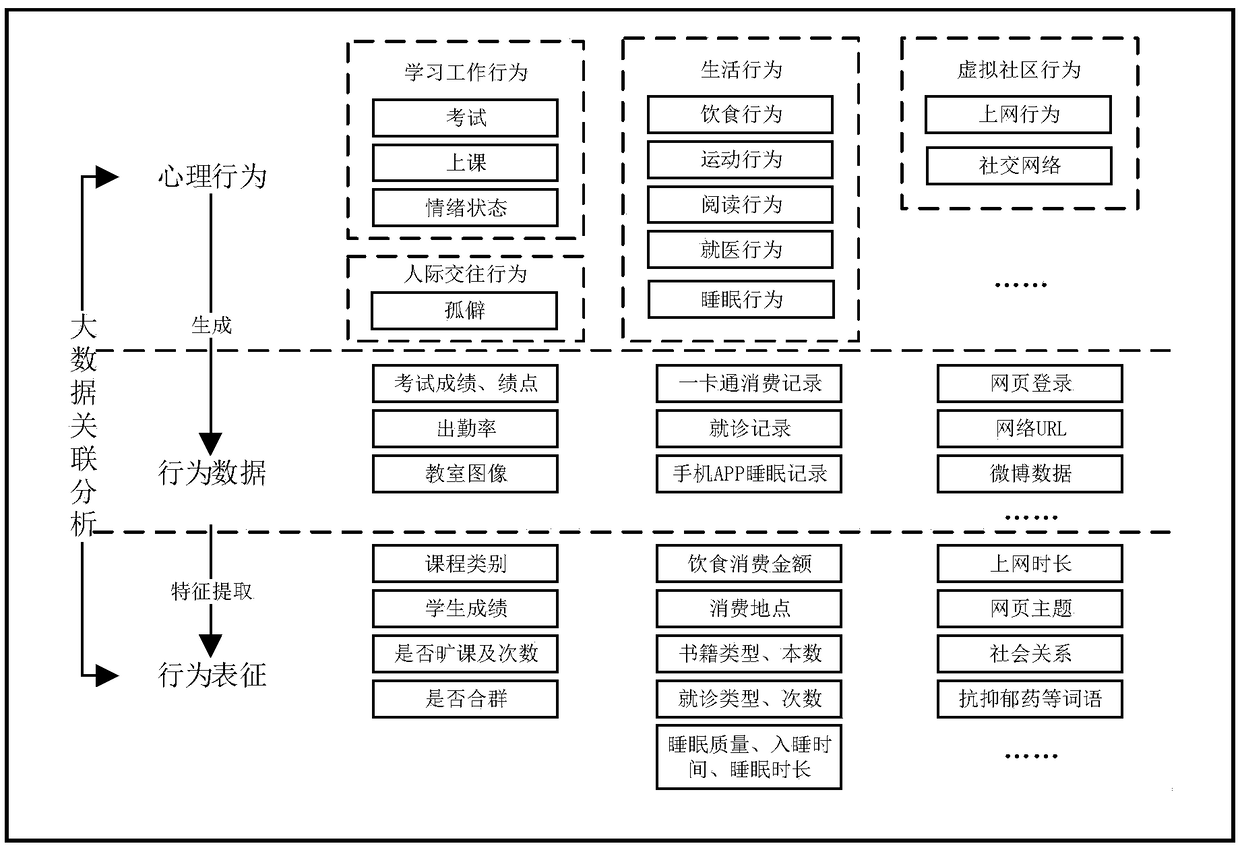
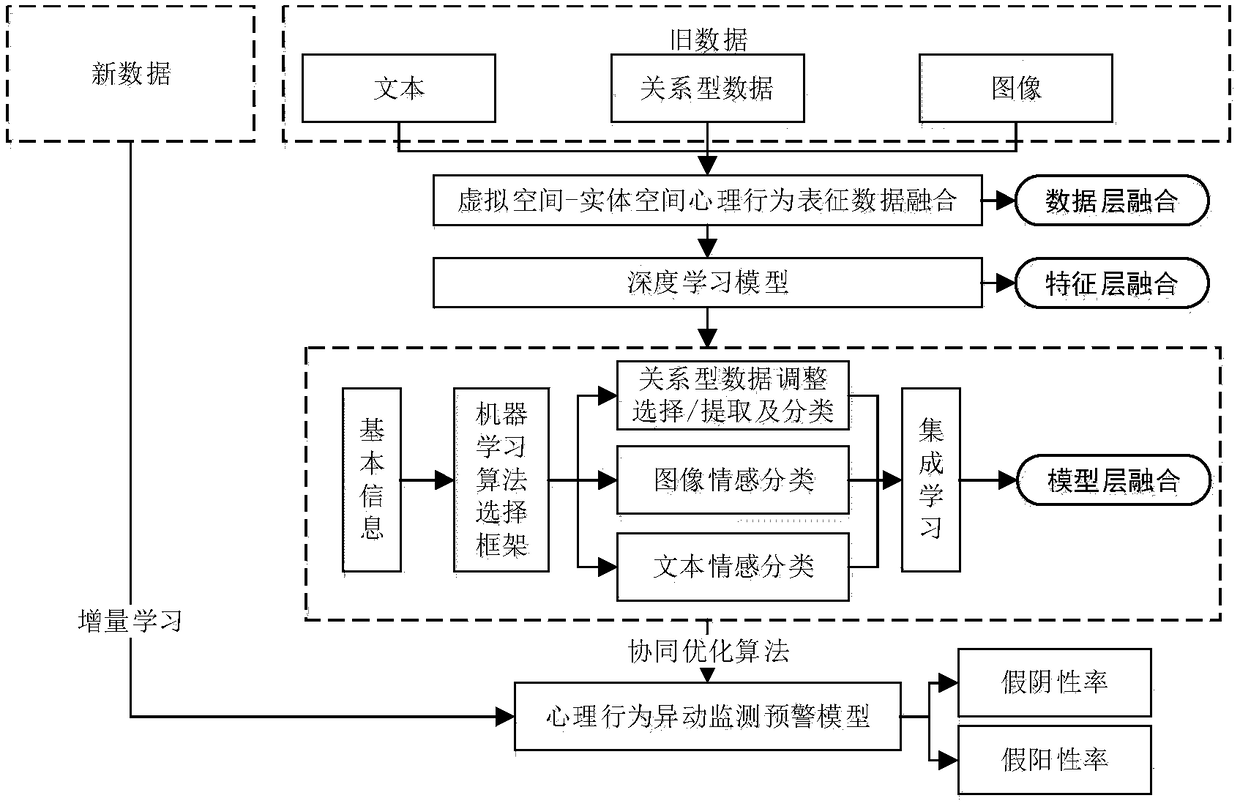
Big data-based collage students' psychological behavior abnormal change system scheme design method
InactiveCN109192310AComprehensive dataImprove accuracyMedical communicationMedical data miningText miningIncremental learning
The invention relates to a big data-based collage students' psychological behavior abnormal change system scheme design method. According to the method, multidisciplinary theories such as system science, information science, medicine and psychology are comprehensively applied; based on multi-source heterogeneous information fusion, virtual-reality space psychological behavioral representation information is pooled; by means of big data association analysis, a mapping relationship model between college students' psychological behaviors and behavioral representation information is established; through pooling smart campus big data, appropriate image processing, text mining, deep learning, incremental learning and other algorithms are selected to mine and establish a psychological behavior abnormal change monitoring and early warning model; and based on a Hadoop and Tensorflow big data analysis platform, college students' psychological behavior abnormal change monitoring and early warningsoftware is researched and developed. Compared with an existing system, the system of the invention scientifically detects individual students with psychological behavior abnormal changes, and has the advantages of high accuracy, good dynamic performance and the like.
Owner:TONGJI UNIV
Sci-tech expert information aggregation method based on semantic relation of knowledge organization
ActiveCN106909680AMeet academic authorityChoose objective and accurateSemantic analysisSpecial data processing applicationsKnowledge organizationKnowledge engineering
The invention discloses a sci-tech expert information aggregation method based on a semantic relation of knowledge organization, and relates to the technical fields of information science and knowledge engineering. The method provided by the invention has the advantages that the semantic aggregation, automatic discovery and dynamic updating of expert information are realized in a semantic relation framework of knowledge organization tools by semantically associating expert information with the knowledge organization tools, and the selection requirements for expert academic authority, professional correlation, research activity, dynamic update and peer avoidance are met, so that the experts can be selected more objectively and accurately.
Owner:INST OF SCI & TECHN INFORMATION OF CHINA
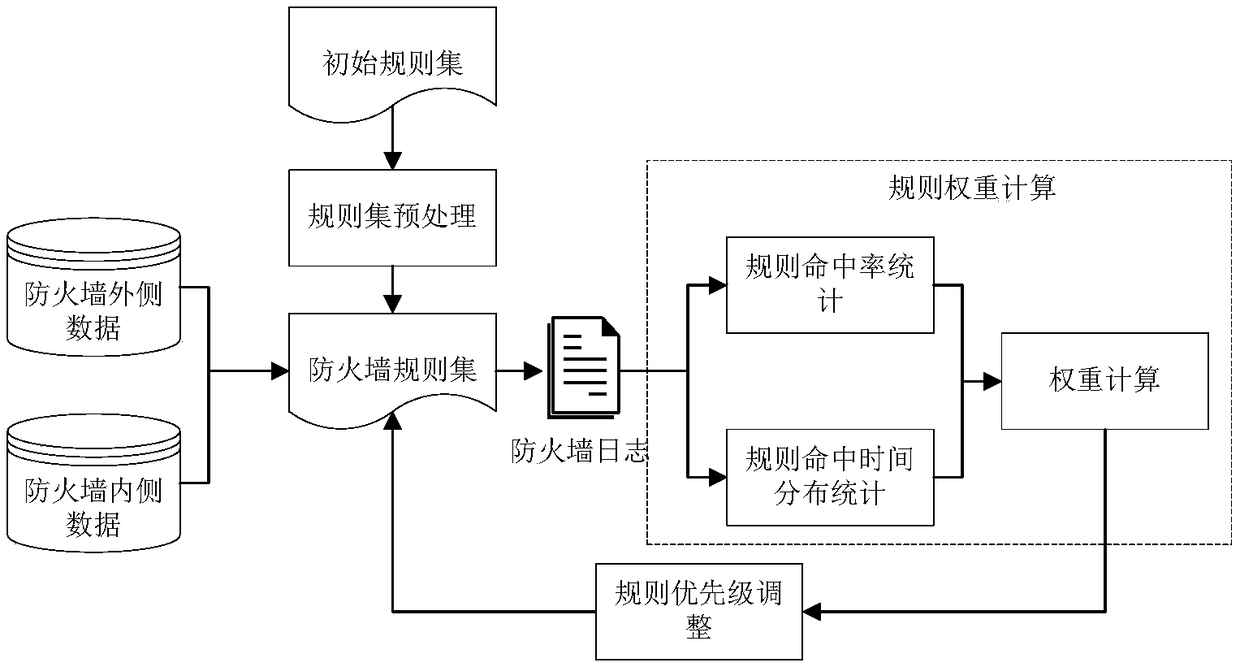
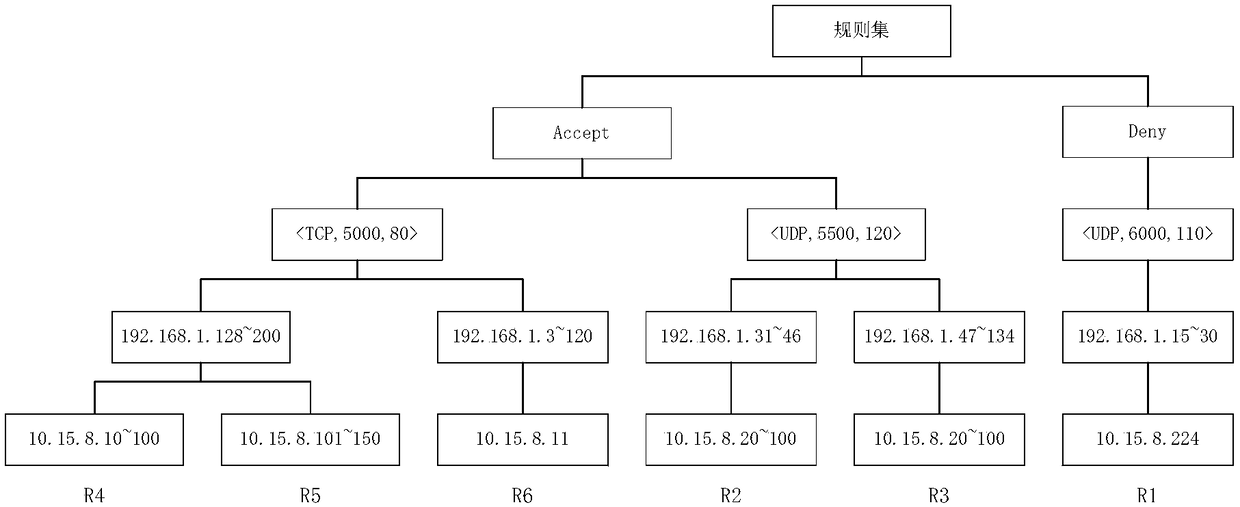
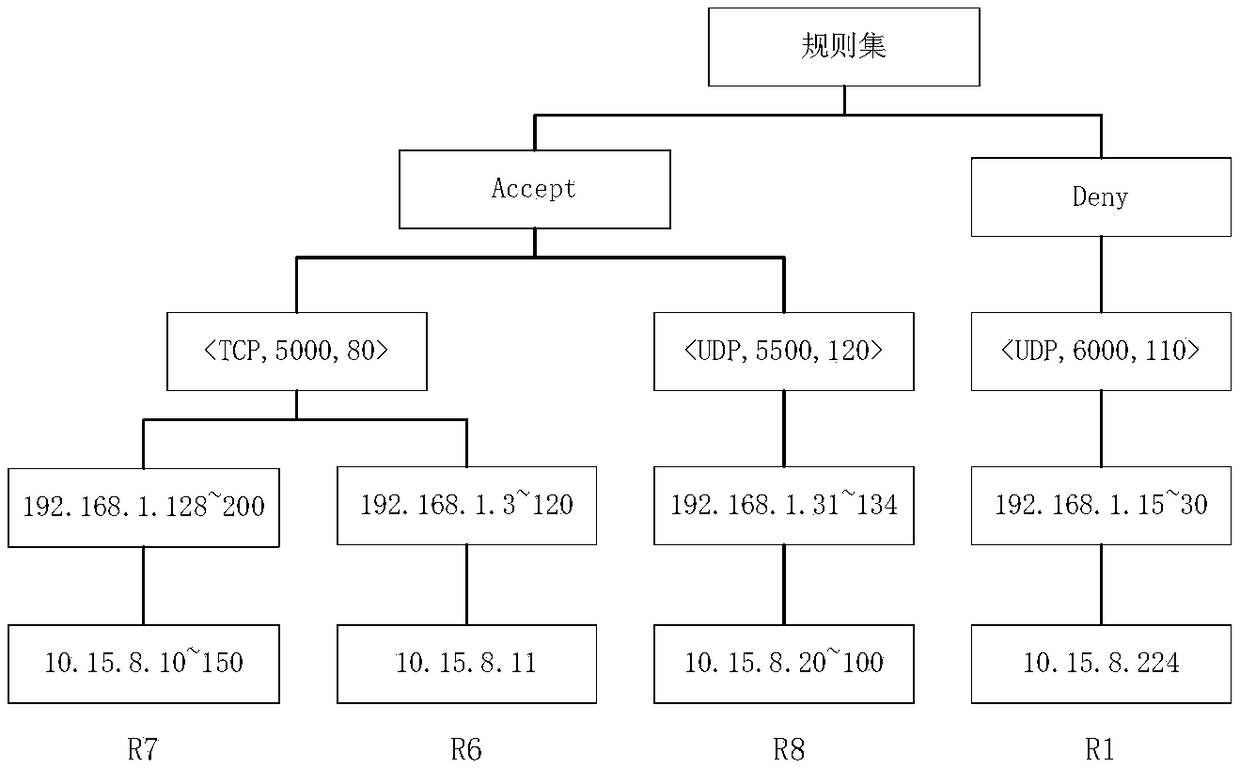
Firewall rule set optimization method based on rule matching hit rate and distribution variance
ActiveCN108462717AIncrease flexibilityImprove optimization effectTransmissionPacket filteringInformation science
The invention relates to a firewall rule set optimization method based on rule matching hit rate and distribution variance, belonging to the technical field of computer and information science. The method comprises the following steps: firstly preprocessing a firewall initialization rule set, wherein content of preprocessing comprises rule set exception detection, exception processing and rule combination, and obtaining a simplest firewall rule set without exceptional rules after preprocessing; then, collecting firewall logs of a period of time in real time, calculating rule weight according to the firewall log information, wherein rule weight calculation is divided into three parts including rule hit rate frequency statistic, rule hit time distribution statistic and a rule weight value calculated according to the two statistic data; finally, according to the calculated rule weight value, reordering the firewall rule set, and placing the rules with relatively higher weight values at positions with higher priority. Compared with the conventional firewall rule set optimization method, the method provided by the invention has better optimization effect, can enable a firewall to keep relatively higher data packet filtering rate and has relatively excellent flexibility and transportability.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
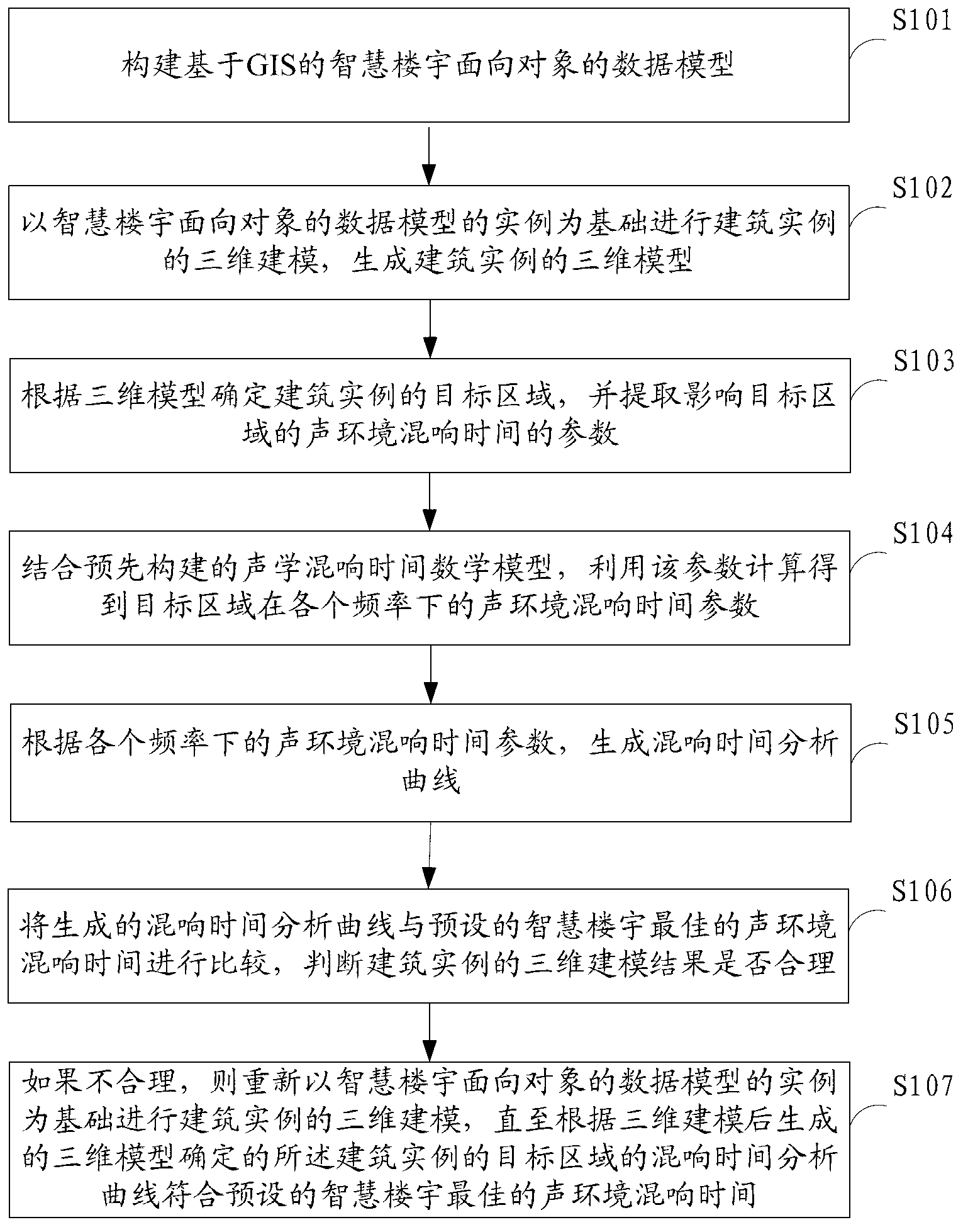
Method and device of achieving three-dimensional modeling of wisdom building
The invention is suitable for the technical field of wisdom buildings and geographic information science and provides a method and a device of achieving three-dimensional modeling of a wisdom building. The method of achieving 3D modeling of the wisdom building comprises that constructing a data model which is corresponding to the wisdom, carrying out a 3D modeling of a building example, generating the 3D modeling of the building example, confirming an object region of the building example, extracting parameters of a reverberation time of an acoustic environment influencing the object region, calculating the parameters of the reverberation time of the acoustic environment of the object region under each frequency, at last, forming a reverberation time analytical curve according to the parameters of the reverberation time of the acoustic environment under each frequency, comparing the reverberation time analytical curve with a best acoustic environment reverberation time, obtaining an acoustic environment reverberation time analysis result and updating the 3D modeling of the building example according to the analysis result. Due to the fact that a mathematical model simulation and a mathematical model analysis of the acoustic environment reverberation time is carried out on a result of all kinds of objects optimizing in a real building in order to choose best objects combination and therefore constructing requirements of the wisdom building is met.
Owner:SHANGHAI KEENSHINE ELECTRONIC TECH CO LTD
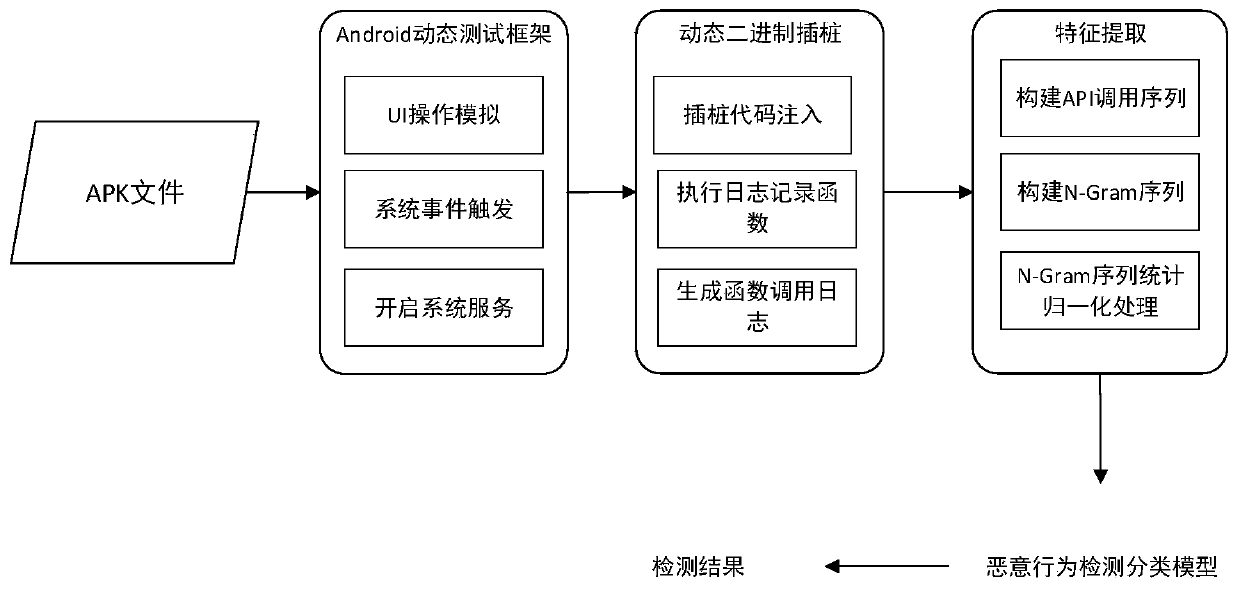
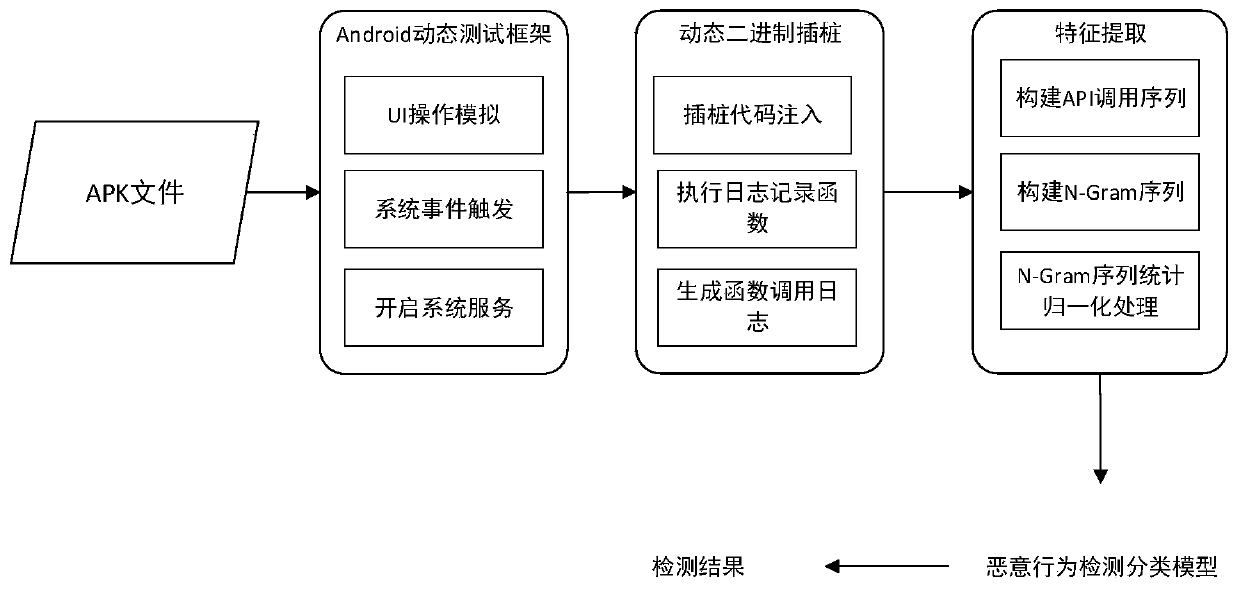
Android malicious behavior dynamic detection method based on binary dynamic instrumentation
InactiveCN109992968AImprove detection efficiencyImprove accuracyPlatform integrity maintainanceSoftware simulation/interpretation/emulationGranularityDynamic instrumentation
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
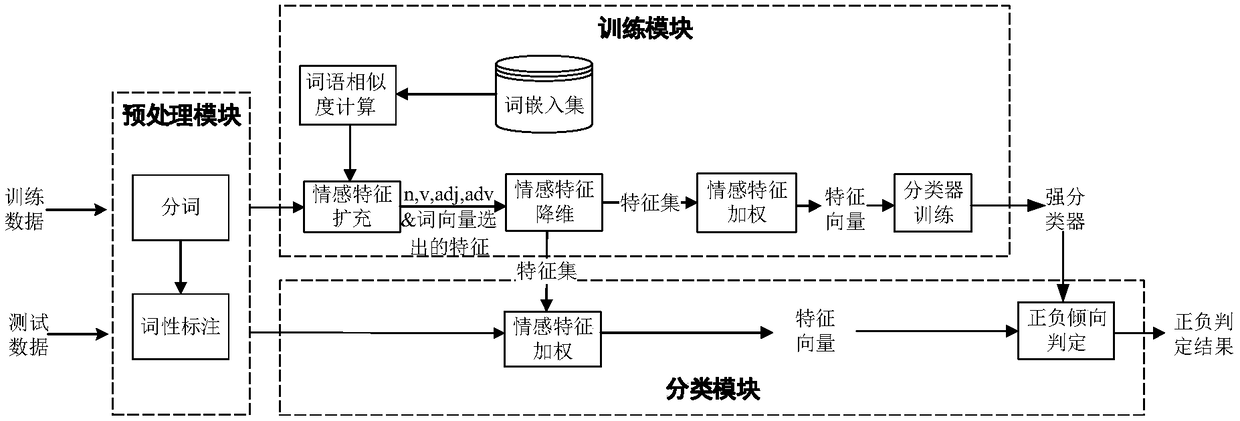
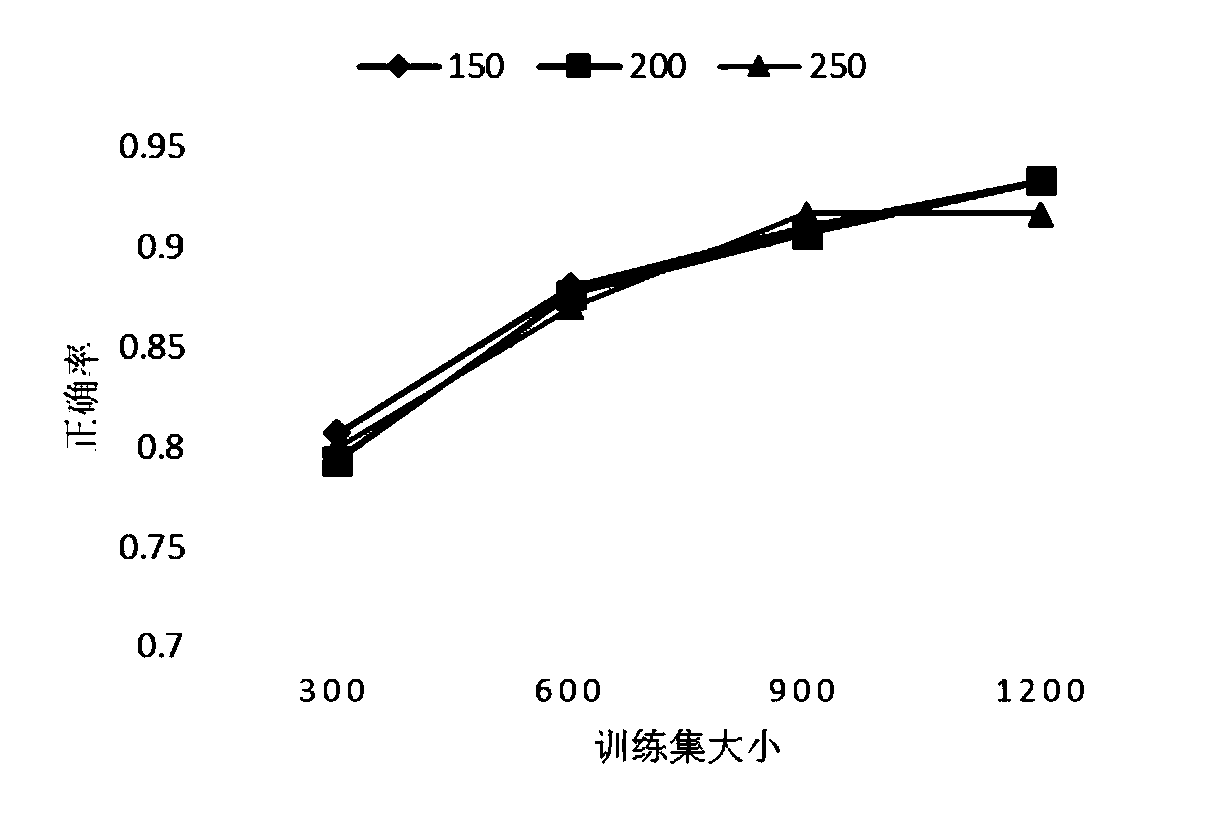
Sentiment word extension-based short text sentiment classifying method
InactiveCN108376133ASolve the problem of incomplete collection of emotional wordsImproving the performance of sentiment analysisNatural language data processingSpecial data processing applicationsPart of speechFeature vector
The invention relates to a sentiment word extension-based short text sentiment classifying method, and belongs to the technical field of computers and information science. The sentiment word extension-based short text sentiment classifying method comprises the following steps: first, segmenting a comment text into a sentence set, and dividing words and labelling parts of speech by utilizing a jieba word dividing tool to obtain a pre-processed result; then, aiming at each short text comment, acquiring the word vector of each word by using Wikipedia corpus training Glove, calculating the semantic similarity of other words and the primary sentiment features with the parts of speech of N, V, Adj and Adv by utilizing the word vectors, expanding the words with similar semantics to a primary sentiment feature set; next, proposing DF-TF-MI, performing feature dimension reduction by improving a conventional feature dimension reduction method by utilizing interlexical statistical features to obtain a low-dimension feature set, and weighting the sentiment features; finally, performing sentiment tendency classification on the obtained feature vectors through an RADA algorithm formed by weak classifier weighting. According to the sentiment word extension-based short text sentiment classifying method, the problem that unregistered words exit in a sentiment dictionary is solved, meanwhile, the problem of sparse sentiment features caused by few effective sentiment words of the short text comment is solved, and the performance and accuracy of sentiment tendency analysis are improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
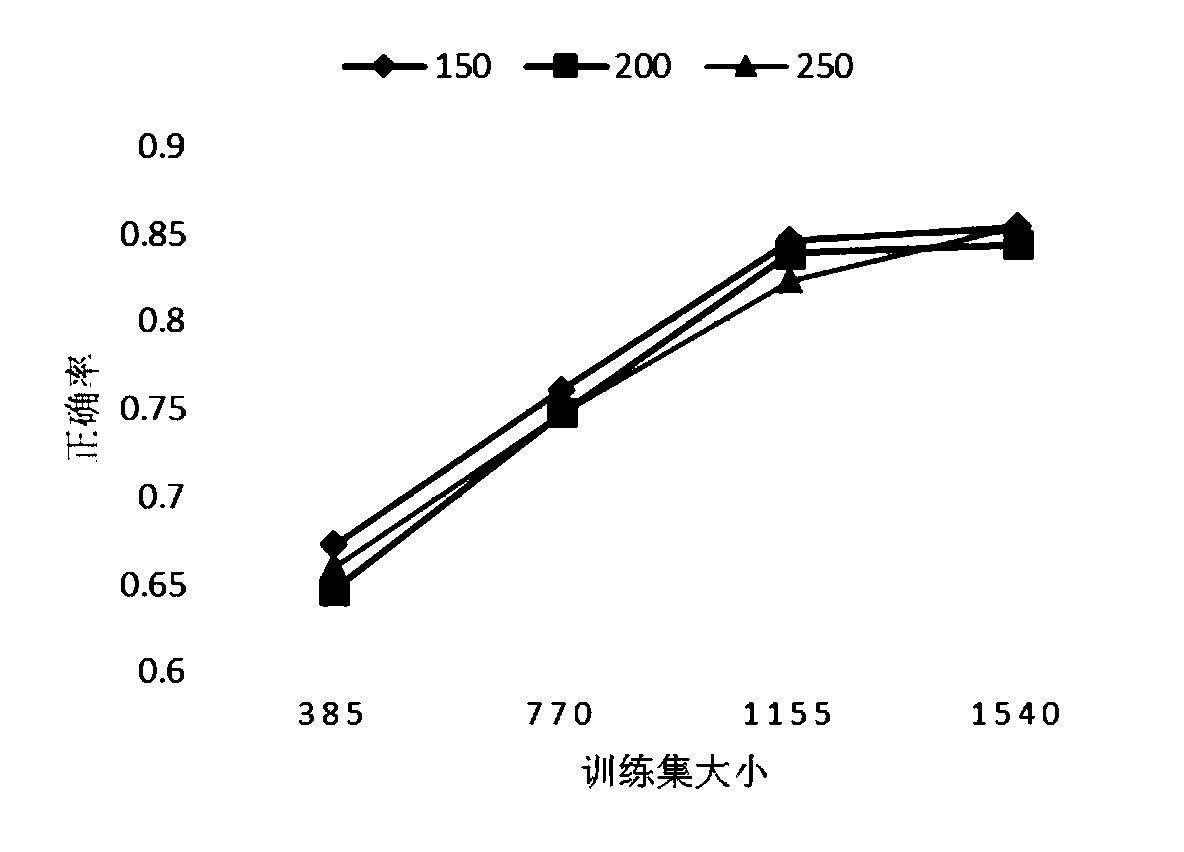
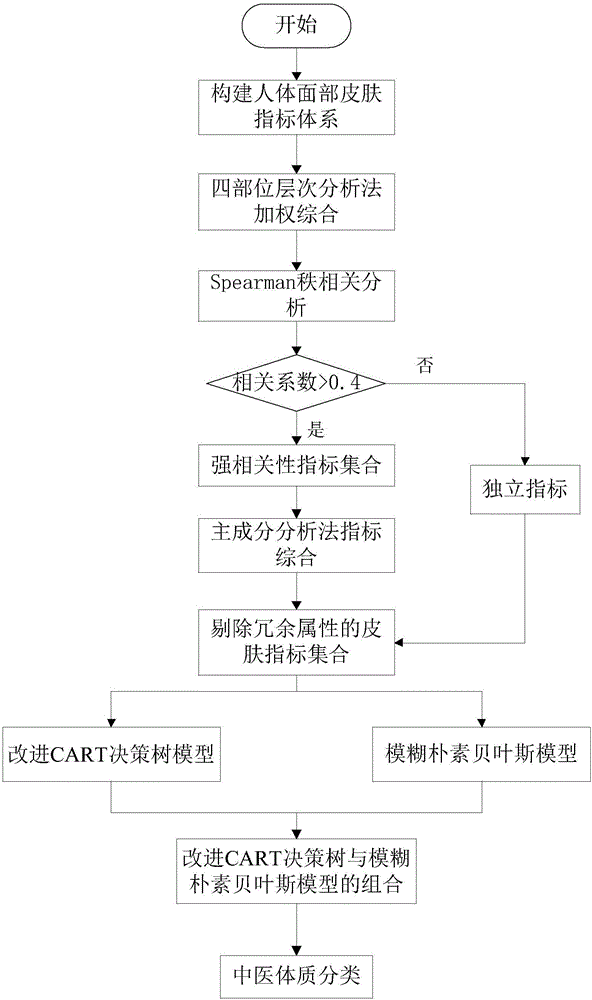
Traditional Chinese medicine constitution optimized classification method based on improved CART decision-making tree and fuzzy naive Bayes combined model
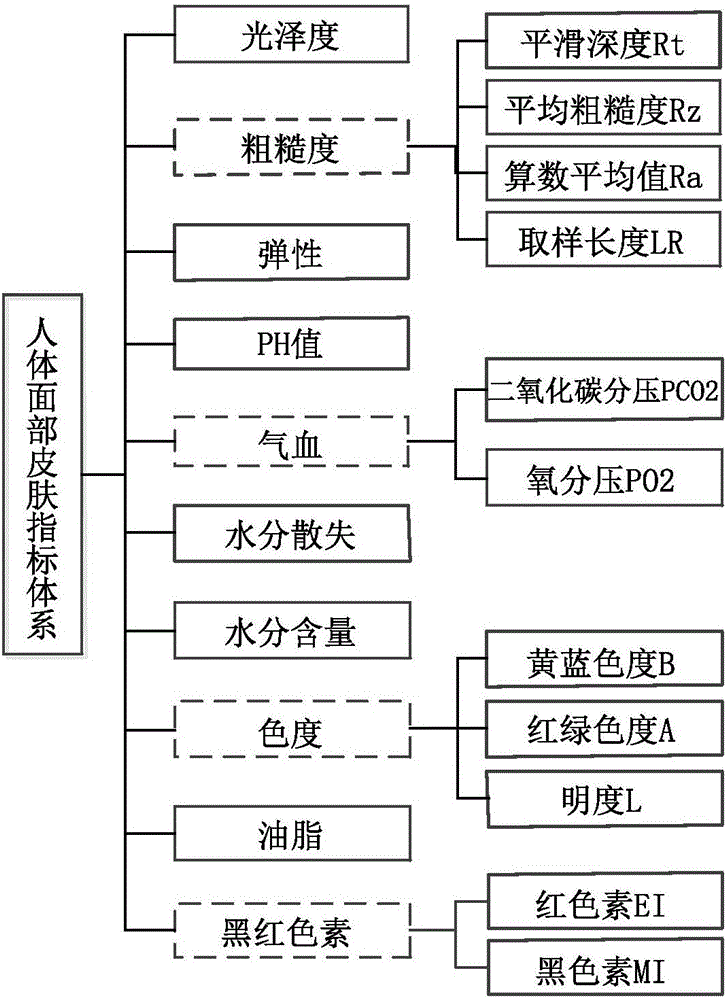
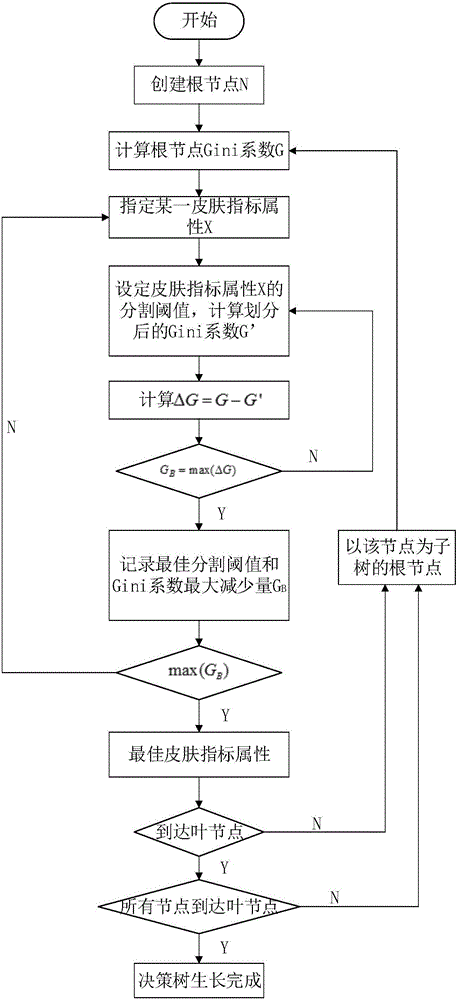
ActiveCN105956382AIncrease digging speedReduce test metricsCharacter and pattern recognitionMedical automated diagnosisHuman bodyClassification methods
The invention discloses a traditional Chinese medicine constitution optimized classification method based on an improved CART decision-making tree and a fuzzy naive Bayes combined model, and belongs to the field of engineering technology mixing and merging traditional Chinese medicine constitution science and information science technology. According to the method, a multi-dimensional human body face skin index system is built; a quite highly related index set is screened out; and according to different contribution degrees of each index, the original attribute is remained in a focused way so that redundant attributes are removed. By aiming at the classification requirement of needing to consider the interpretability and the accuracy at the same time, the advantages of the good induction characteristic of the decision-making tree on the attributes and the inter-class relationship under the condition of few training samples and of highest accuracy of the naive Bayes classification under the condition of many training samples are brought into full play; the traditional Chinese medicine constitution optimized classification method can be used for quantificationally studying the potential relationship between the skin and the traditional Chinese medicine constitution, and provides a certain scientific basis, data and a method support for the health care, conditioning and treatment of the skin.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
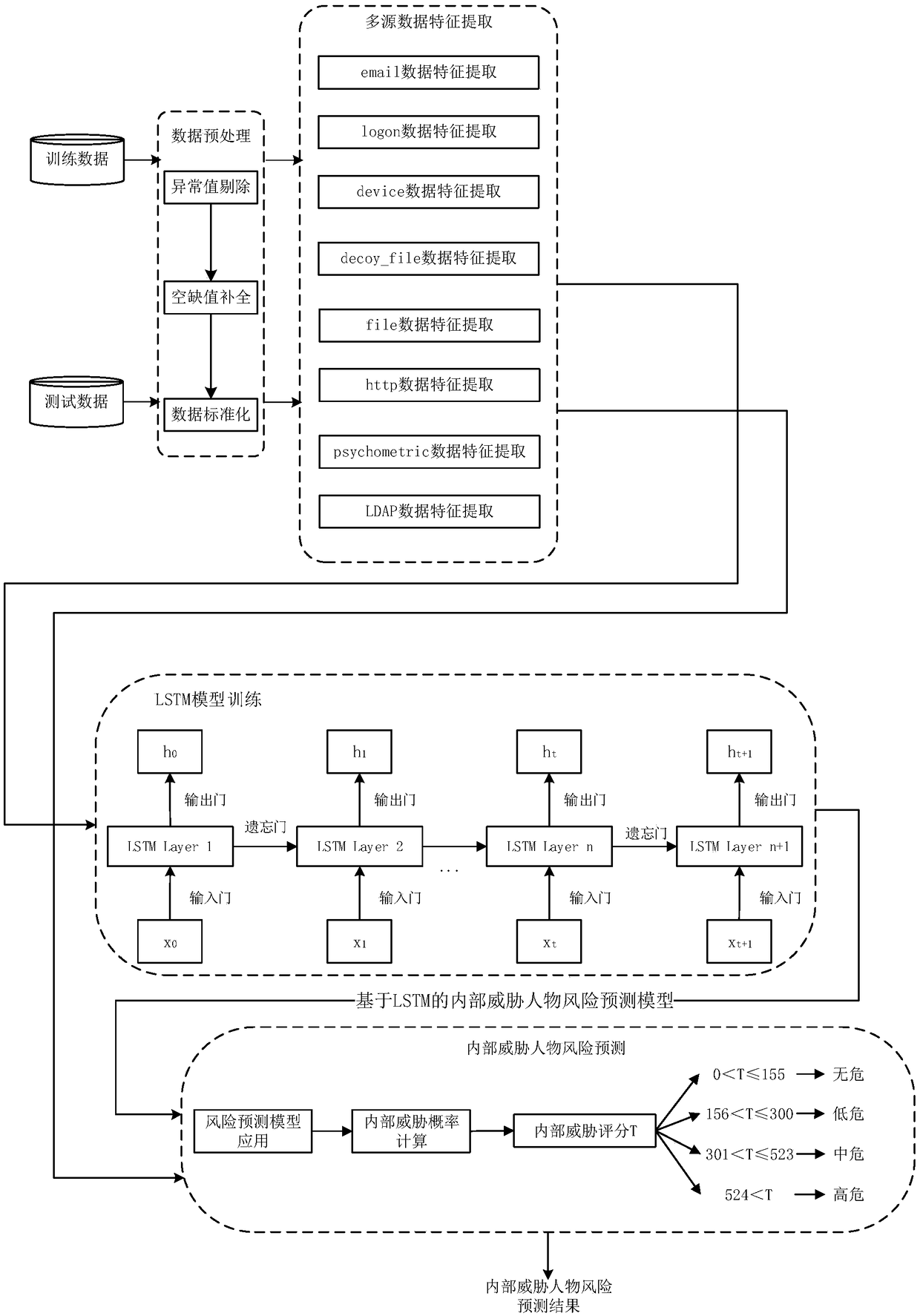
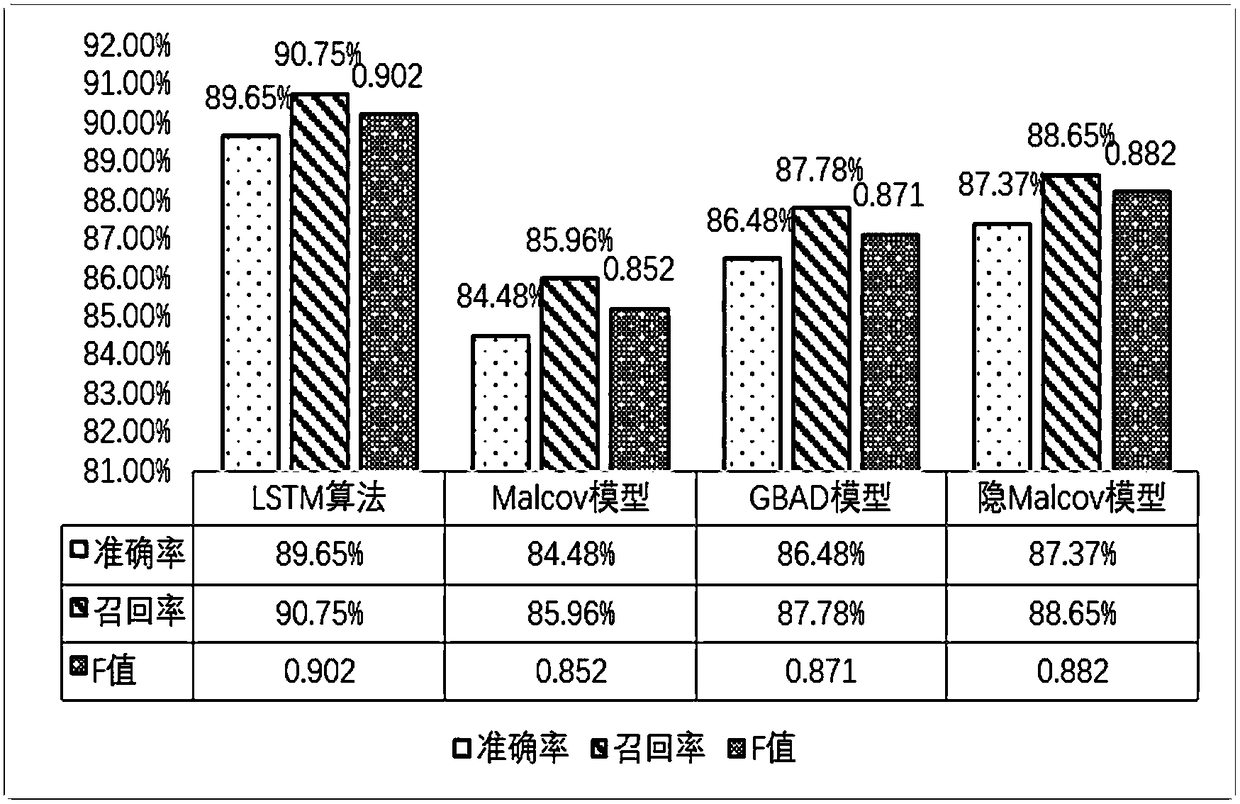
Interior threat figure risk prediction method based on personal behavior sequential characteristics
The invention relates to an interior threat figure risk prediction method based on personal behavior sequential characteristics, and belongs to the technical field of computer and information science.The method comprises the steps: carrying out the preprocessing and feature extraction of the accumulative historical behavior information of a figure, which comprises the quantitative sampling of figure information, pre-emphasis and windowing, and the extraction of the multi-domain heterogeneous figure data into corresponding digital characteristics; carrying out the synthesis training of an interior threat figure risk prediction model, and constructing an interior threat figure risk prediction model based on LSTM; and finally carrying out the risk prediction, estimation and early warning ofthe interior threat figure risk prediction model based on LSTM. Compared with other common methods, the method is higher in accuracy, provides a basis for the quantification of the interior threat foran enterprise, and provides a layered interior threat figure early-warning mode.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
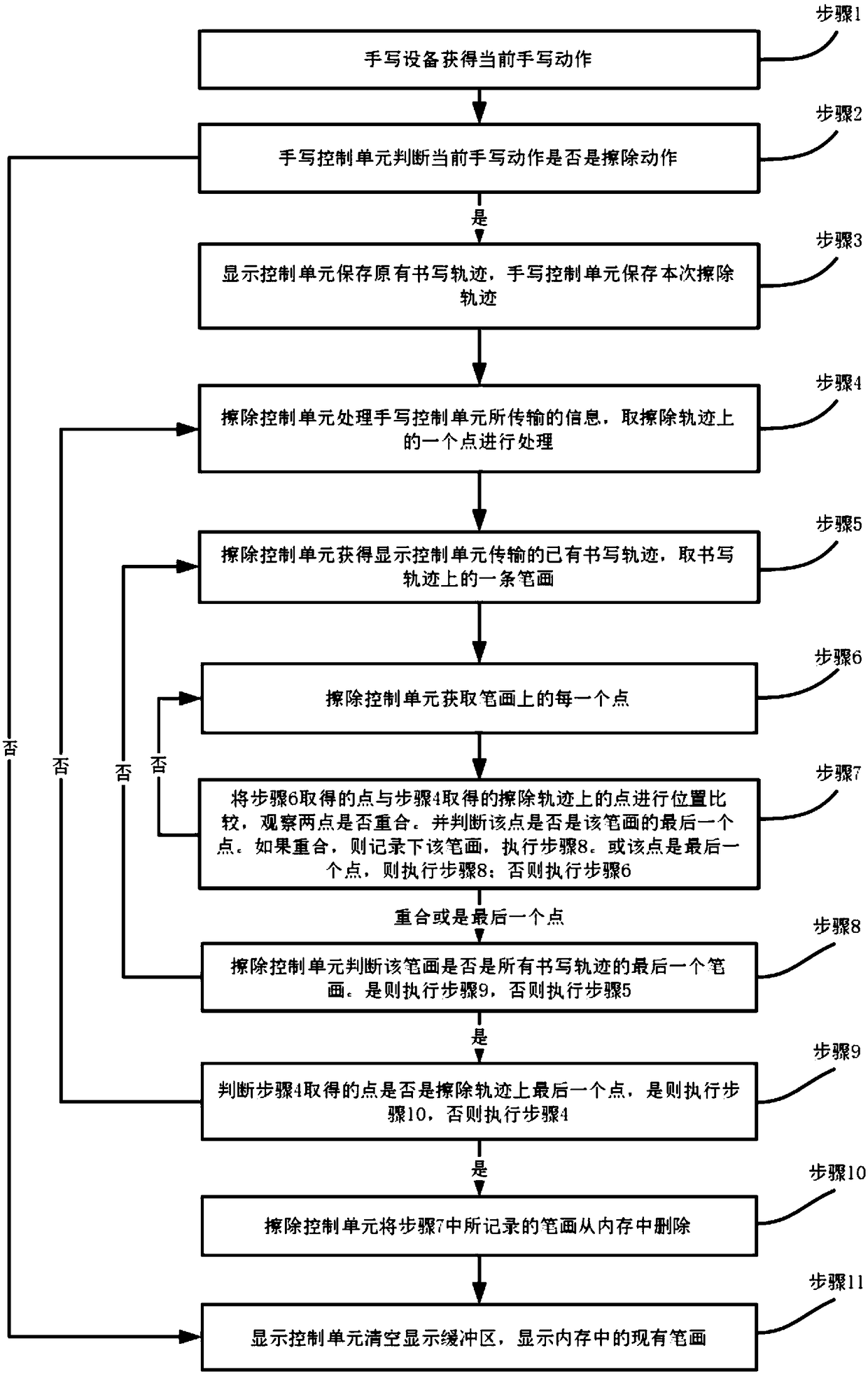
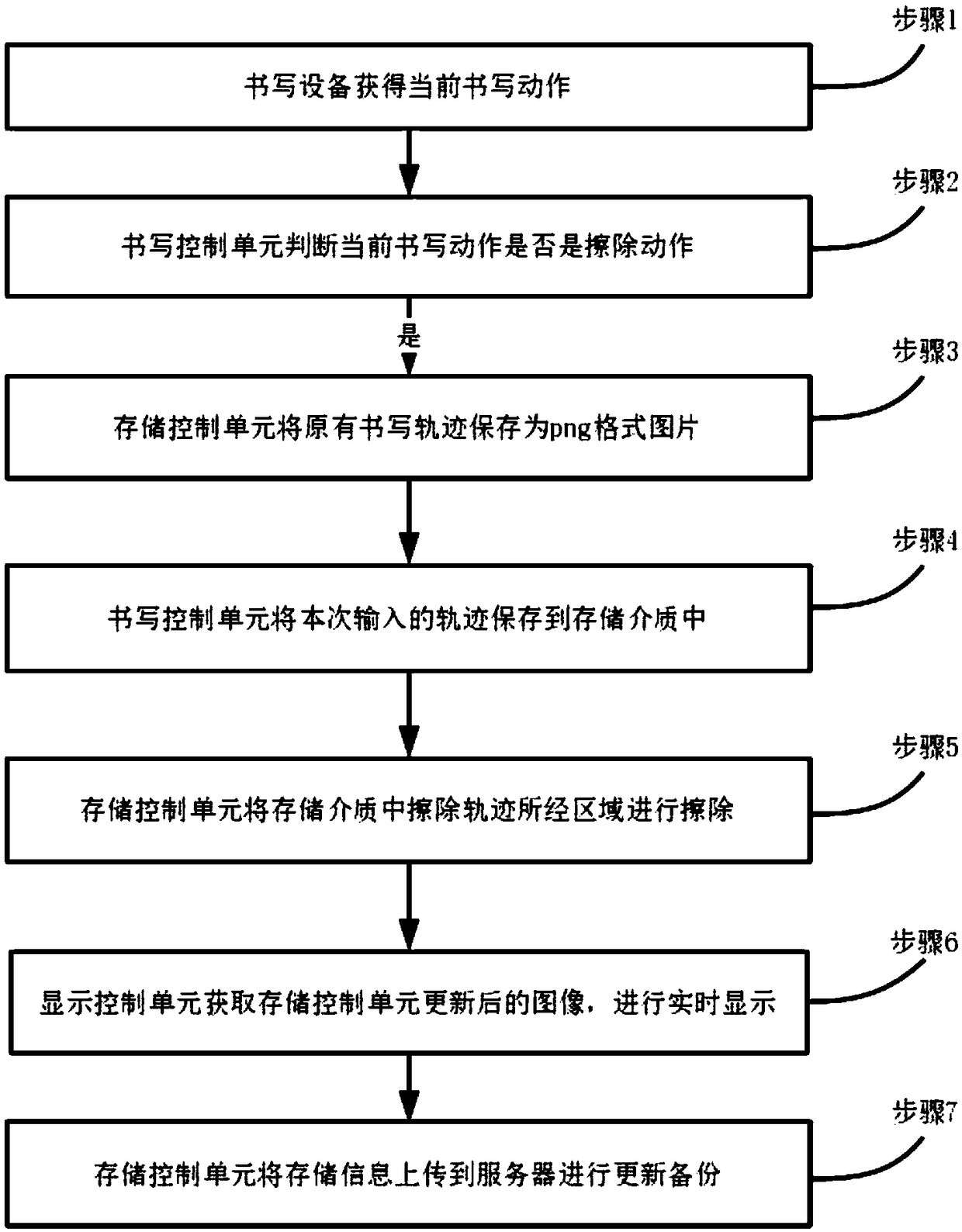
A method of deleting handwriting stroke information inputted by a user on a handwriting device
ActiveCN109445676ASatisfy erasure needsAchieve normal displayInput/output processes for data processingHandwritingInformation type
The invention discloses a method for deleting handwriting stroke information inputted by a user on a handwriting device, which relates to the field of information science and technology. The method comprises the following steps of after receiving the handwritten information input by the user, identifying the type of the information as erased information, comparing the existing information with thetrack information of the item, selecting the strokes to be erased and deleting the strokes, and displaying the modified handwriting information in real time by the display device. The invention has the following advantages that the handwriting device has a plurality of working modes, and the erasing method can automatically judge whether the current erasing action is an erasing action or not according to the input mode of the user; after reading and saving the erasing tracks, the handwriting passing through each track can be judged, so as to erase the corresponding strokes and satisfy the erasing requirements of some users; at the same time, the erasing effect of the strokes is displayed on the ink screen interface in real time, and the display speed is fast and the erasing efficiency ishigh.
Owner:宁波思骏科技有限公司
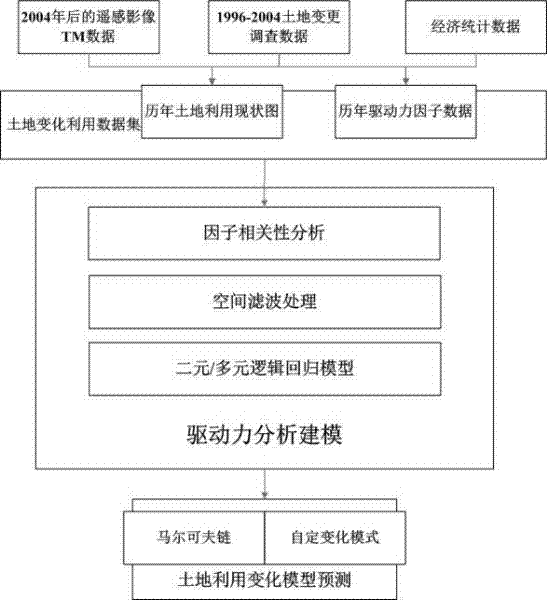
Land use change modeling method and system implemented in combination with spatial filtering
InactiveCN102646164AVerification accuracyImprove fitting accuracySpecial data processing applicationsData setAlgorithm
The invention discloses a land use change modeling method and system implemented in combination with spatial filtering and relates to the field of geographical information sciences. The method focuses on eliminating the spatial autocorrelation influence of data in the process of land use change modeling, and comprises the following steps: collecting original data, and preprocessing the original data so as to generate a data set sequence; determining the optimum distance of spatial filtering by using a variation function, and then splitting variable factors by using a Getis principle based a spatial filtering method; constructing a logistic regression model according to a filtered sample, and assessing the model by using methods such as fitting accuracies and ROC (receiver operating characteristic) curves; and finally, providing a Markov chain and a customized change pattern for forecasting the trend of land use change. According to the invention, based on a statistics mathematical model, a spatial filtering mode is adopted for making up the shortcomings and defects of the mathematical model in geo-spatial calculation, so that through the combination of the two, the fitting accuracy of the model is improved, and the model is more conform to the time and space characteristics of land use change.
Owner:黄波
Ecological resource bearing model method for urban and rural ecological planning
The invention discloses a method for quantitative partitioning by an ecological resource bearing model, which comprises the following steps: carrying out investigation and survey in a target area, and carrying out GIS (geographical information sciences) vectorization on results, establishing a unified coordinate system, and drawing the coordinate system into thematic maps; respectively grading by using preset classification standards; respectively calculating weight values by using an analytic hierarchy process; carrying out mutual superposition and merging on the thematic maps by using the GIS; and carrying out weighted averaging on single factors of water resources, single factors of land resources, single factors of forestry resources and single factors of mineral resources so as to obtain analysis results of an ecological resource bearing model, thereby completing the quantitative partitioning on the target area. According to the invention, the information in each aspect of ecological resources is integrally superposed through the GIS, and through optimizing the analytic hierarchy process and establishing a quantitative evaluation system, the inherent conditions of ecological resource bearing are expected to be studied simply and comprehensively, and implemented to the spatial publishing of urban planning.
Owner:TSINGHUA UNIV
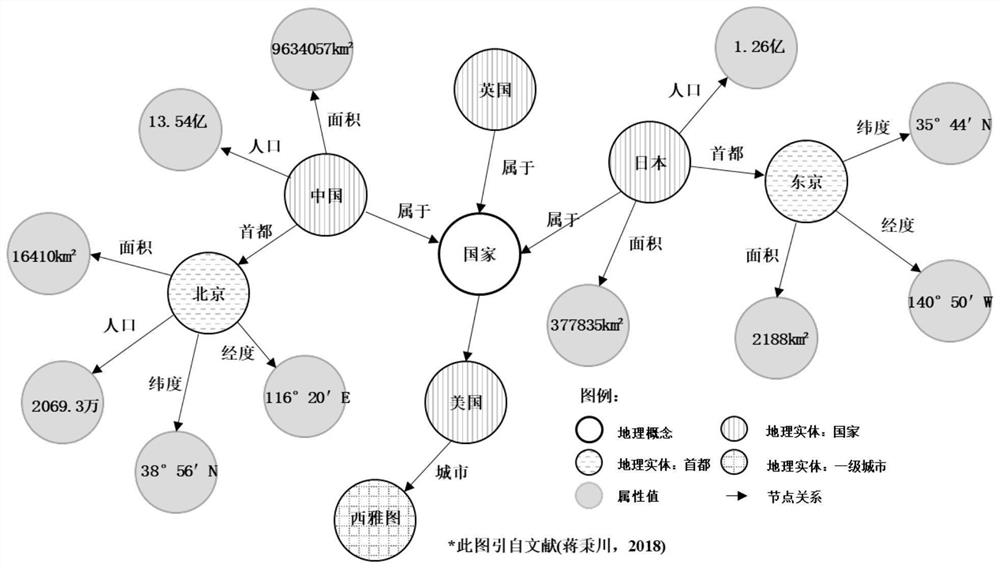
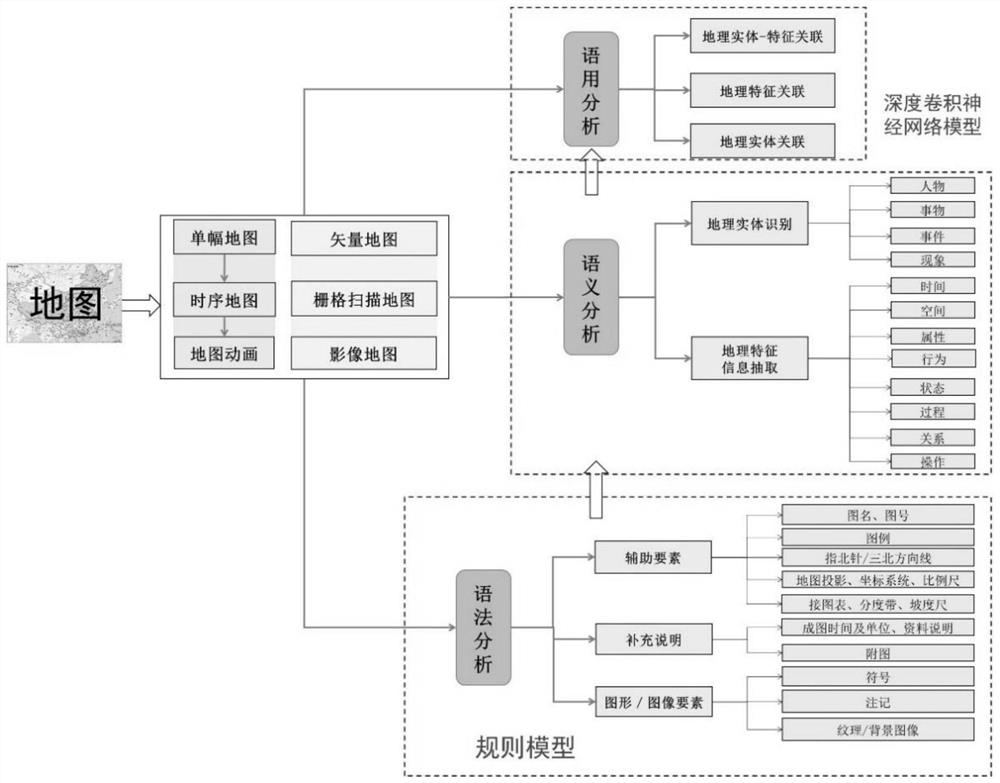
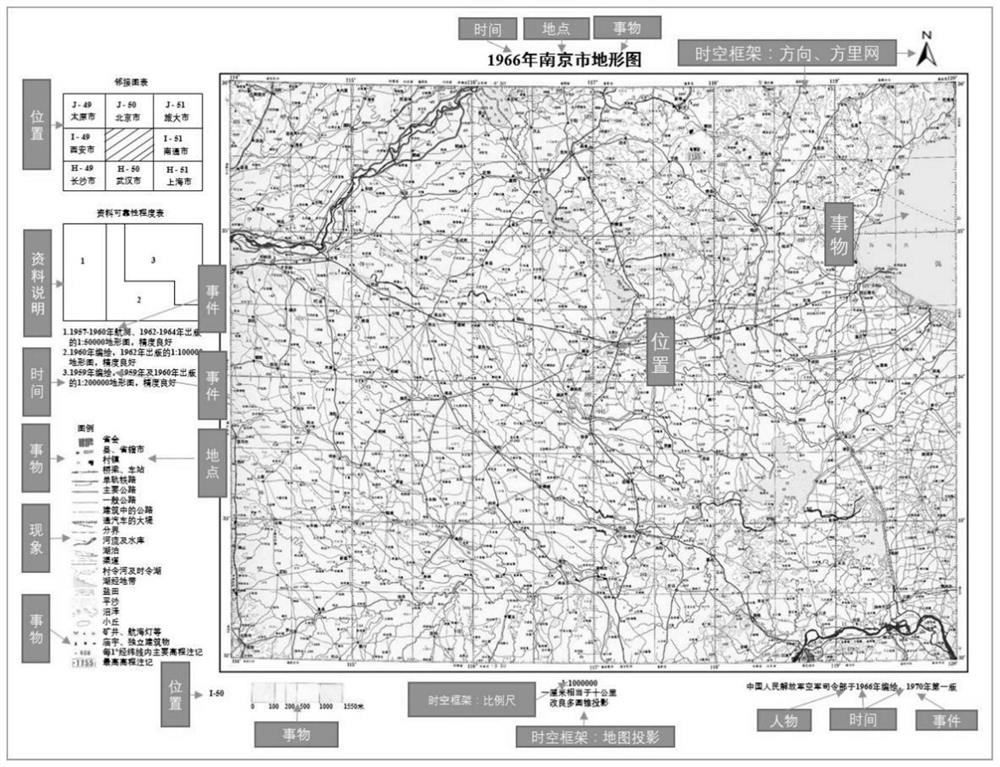
Geographic knowledge acquisition method
InactiveCN112256888ASolve basic theoretical problemsSemantic analysisGeographical information databasesGeoinformaticsA Graphics Language
The invention discloses a geographic knowledge acquisition method, which comprises the following steps of: 1, analyzing sources of geographic knowledge, and dividing the obtained sources of the geographic knowledge into a natural language and a graphic language; 2, carrying out feature analysis and concept modeling on the obtained geographic knowledge; 3, extracting geographic information from theobtained geographic knowledge, wherein the geographic information at least comprises identification of a geographic entity, extraction of feature information and association between the geographic entity and the feature information; and 4, generating a geographic knowledge graph. The invention aims to provide the geographic knowledge acquisition method, which can fill the blank of the existing geographic knowledge acquisition way and a method for converting the geographic knowledge acquisition way into a knowledge graph, essentially promotes the intellectualization, socialization and popularization of geographic information services, and further promotes the development of geographic information science theories and applications.
Owner:NANJING NORMAL UNIVERSITY
Magnesium particle macromolecule composite material and preparation method thereof
A magnesium particle macromolecule composite material is characterized in composed of macromolecule olefin polymer as substrate which is uniformly distributed with 0.5-50um magnesium alloy particles at the mass percentage of 0 C08L 23 / 06 C08L 23 / 12 C08L 27 / 06 C08K 3 / 08 1 5 1 2008 / 2 / 22 101235173 2008 / 8 / 6 000000000 Nanjing University of Information Science & Technology 210044 Zhao Haofeng Wang Ling luzhi bin 32200 The Patent Agency of the South-East University No.2 Sipailou, the City of Nanjing, Jiangsu Province 210018
Owner:NANJING UNIV OF INFORMATION SCI & TECH
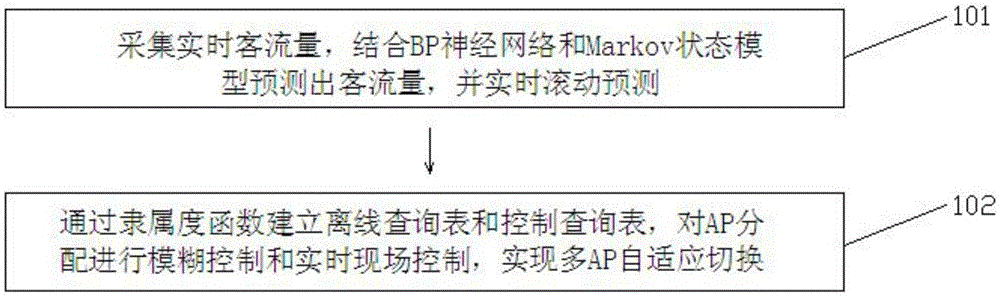
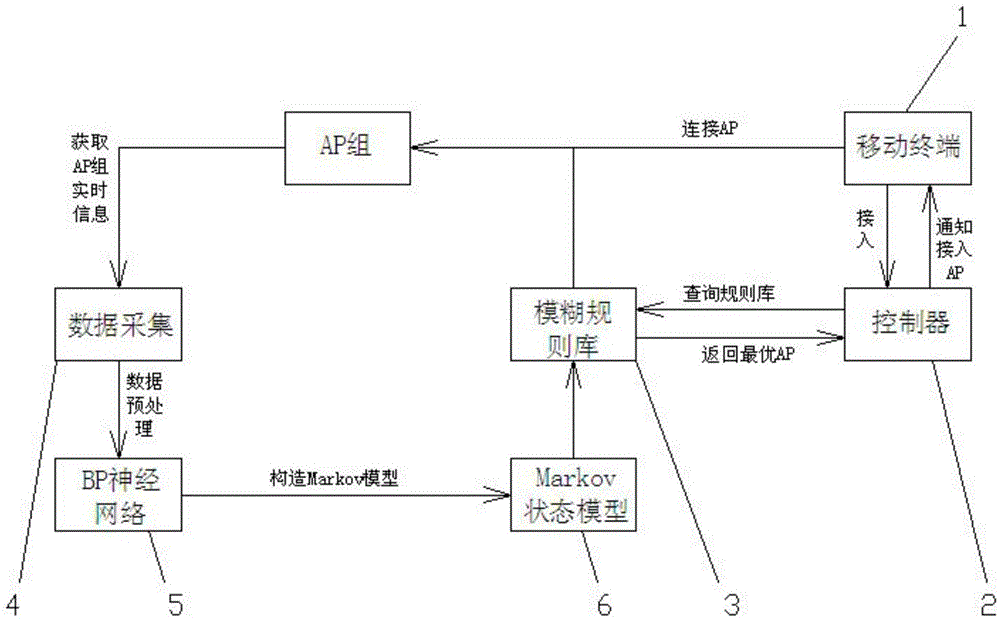
Multi-AP adaptive switching method based on Markov model
ActiveCN105657758AImplement adaptive switchingNo sense of Internet experienceWireless communicationQuality of serviceMathematical model
The invention discloses a multi-AP adaptive switching method based on a Markov model. The method comprises the following steps: 1) collecting a real-time passenger flow volume, predicating the passenger flow volume in combination with a BP neural network and the Markov state model, and rolling for predication in real time; and 2) establishing an offline query table and a control query table through a membership function, and carrying out fuzzy control and real-time site control on AP allocation to realize multi-AP adaptive switch. The multi-AP adaptive switching method based on the Markov model disclosed by the invention has the beneficial effects that: the multi-AP adaptive switch is a complicated system project that involves information science, geographical science, control science and system science and the like, the Markov model is introduced in the method to establish a passenger flow volume prediction model, and the AP having the least time consumption and the best quality of service is automatically switched in combination with the intelligent scheduling technology, a strict mathematical model is established, and senseless internet experience of users is realized.
Owner:HANGZHOU QUANWEI COMM SERVICES CO LTD
An erasing method and a system for writing trajectory
ActiveCN109407954AMeet usage habitsFeel goodDigital ink recognitionModifying/creating image using manual inputArray data structureHabit
The invention discloses an erasing method and a system for writing trajectory, which relate to the field of information science and technology. The method comprises the following steps: when the current action of the user is judged to be an erase action, the new trajectory is stored as a trajectory array object, the original writing trajectory dot array is drawn as a curve and save as a png formatpicture, and then the original writing trajectory picture is erased according to the region through which the input trajectory passes, and the processed writing trajectory is displayed in real time.The method has the advantages that: the writing device has a plurality of working modes, and the erasing method can automatically judge whether the erasing action is the erasing action or not according to the input mode of the user. It can erase part of the existing writing tracks, which conforms to the user's usage habit. It can be used for writing and displaying on the ink screen. The ink screenhas the characteristics of no eye injury and good hand feeling.
Owner:宁波思骏科技有限公司
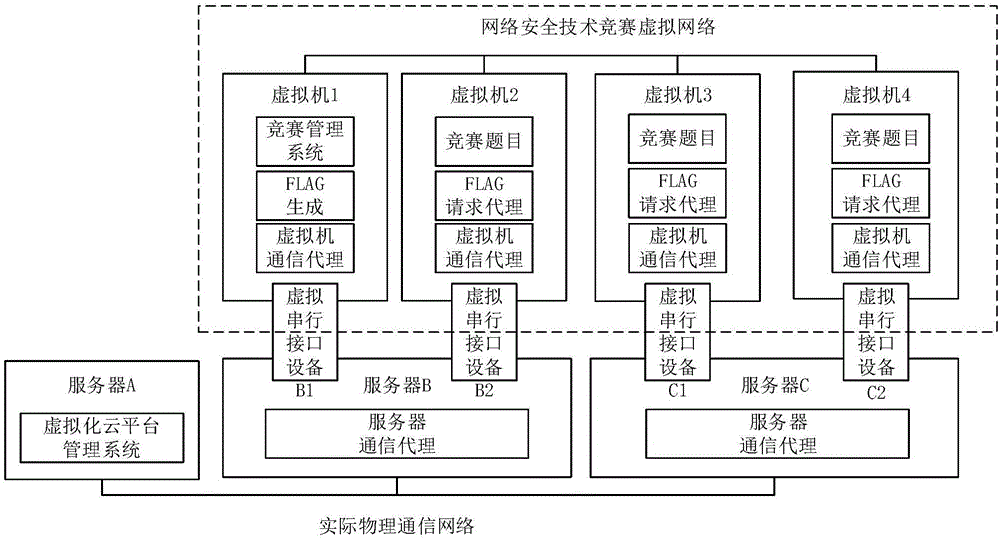
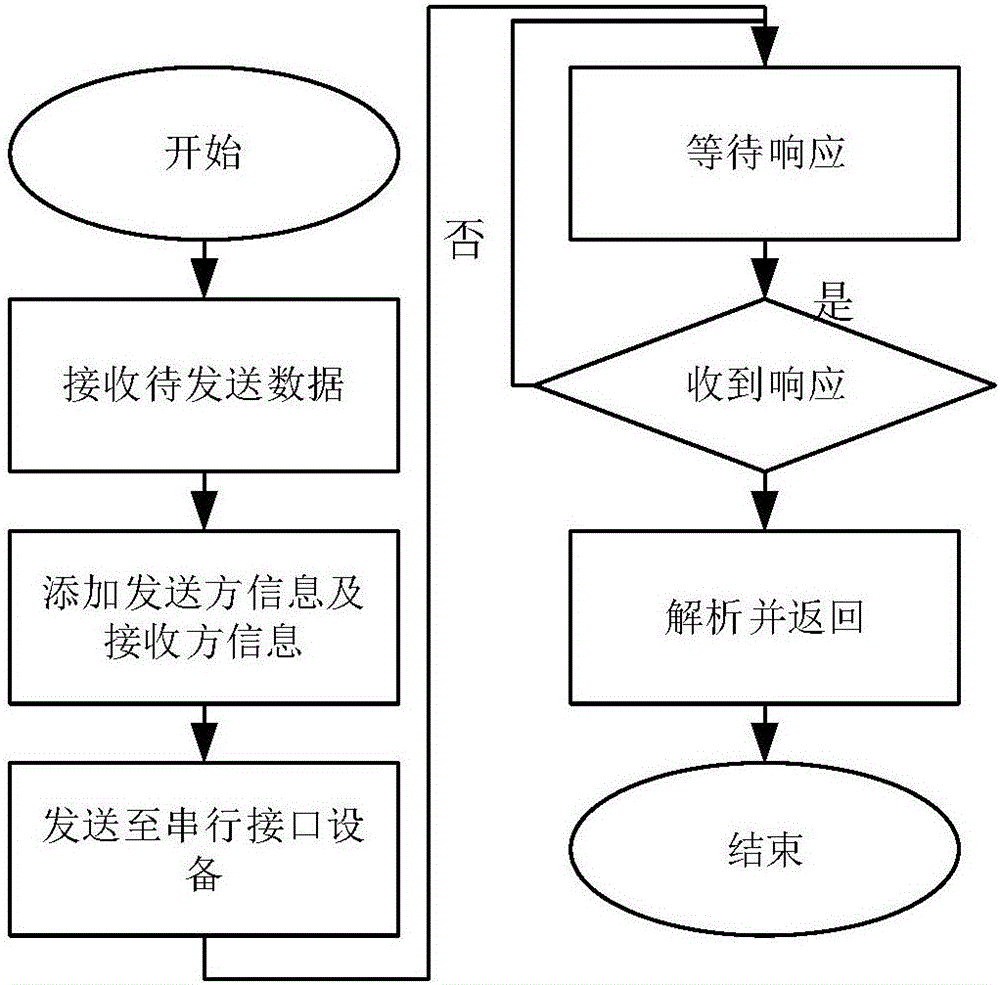
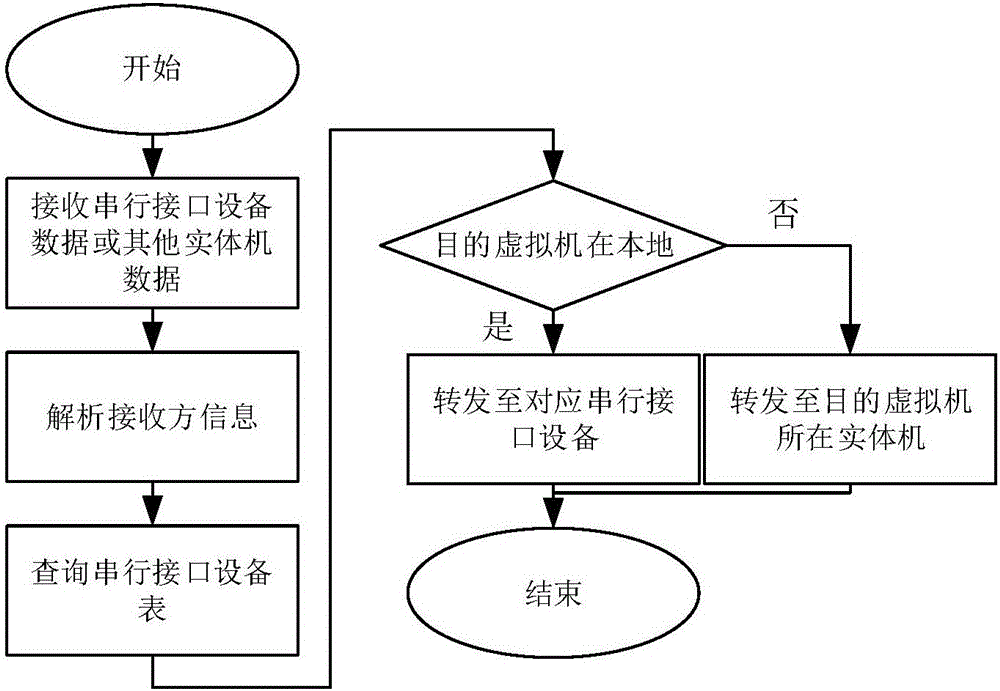
Network security technology competition dynamic FLAG management method
InactiveCN106254547ARealize control communicationIncrease flexibilityCosmonautic condition simulationsTransmissionVirtualizationData stream
The invention relates to a network security technology competition dynamic FLAG management method, relates to network security technology competition, and belongs to the technical field of computer and information science. According to the method, a network security technology competition system is configured and managed through a virtualized cloud platform, virtual machines needed by competition are built in a cloud platform environment to deploy a competition management system and examination questions, and a virtual network is constructed for competition as needed for competitors to access and answer questions. On the basis, serial interface communication equipment is added to a virtual machine to realize a special data interaction interface between the virtual machine and a real machine, communication between a question virtual machine and a management virtual machine is realized via the interface under the condition of not affecting the data flow of the competition virtual network, and thus, dynamic flag update and configuration is realized.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Boundary interaction-based area combination topological similarity measurement method
InactiveCN106446000ADistinguish topological relationshipsDistinguish the difference between its similaritiesGeographical information databasesSpecial data processing applicationsGeoinformaticsSpace object
The invention relates to the field of geographic information science, in particular to a boundary interaction-based area combination topological similarity measurement method. The method comprises the following steps of obtaining a boundary interaction record of complex entities by analyzing a topological relation between the complex entities based on a topological relation of area boundary interaction, and converting the interaction record into a binary sequence, thereby converting similarity assessment into a sequence calibration process; and representing a reference area combination and a candidate area combination by using CR and CP respectively, and then calculating topological similarity between the reference area combination CR and the candidate area combination CP by setting a weight of the similarity between a dimension sequence and a detail sequence. The method has the following advantages: 1), the topological relation between composite space objects, and the topological similarity difference can be well distinguished; and 2), various possible results are provided for users more visually.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
An Android malware detection method based on depth learning
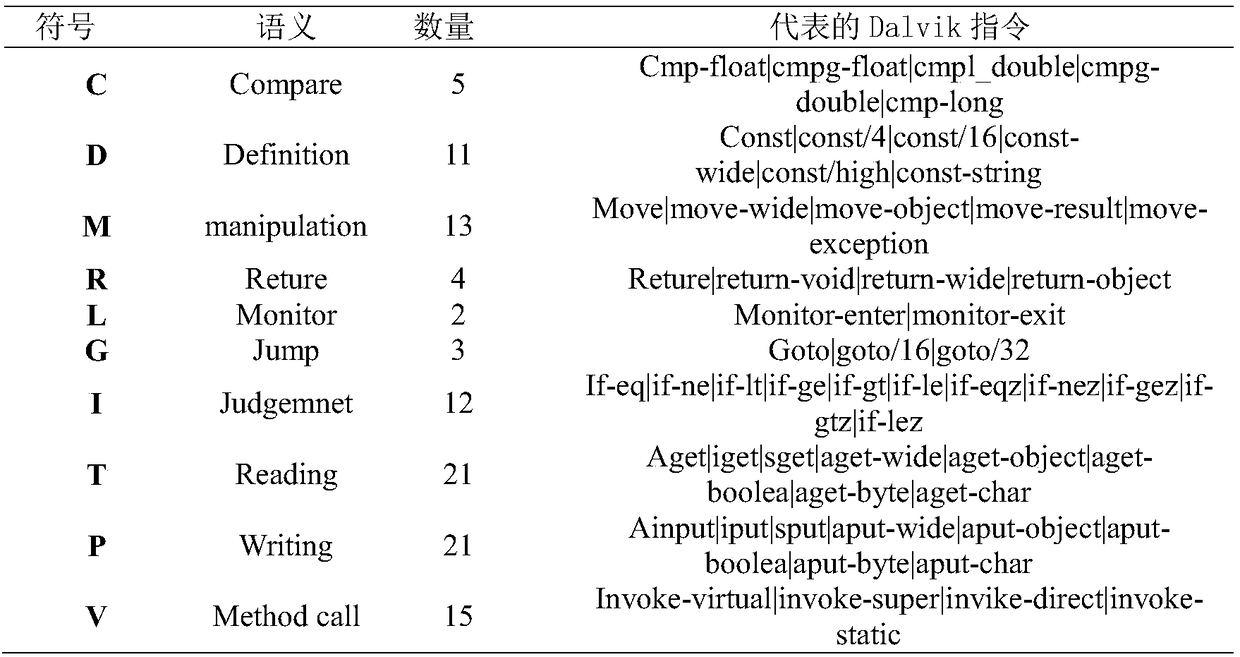
ActiveCN109271788ARich software featuresImprove detection accuracyCharacter and pattern recognitionPlatform integrity maintainanceConfusionInformation science
The invention relates to an Android malware detection method based on depth learning, belonging to the field of computer and information science and technology. The invention firstly extracts featuresof Android application software, and then extracts relevant security features by decompressing and decompressing Android application files. The extracted features include three aspects: file structure feature, security experience feature and N-Gram statistic characteristic. Then the extracted features are numerically processed to construct feature vectors. Finally, a DNN (Deep Neural Network) model is constructed based on the above extracted features. The new Android software is classified and identified by the constructed model. This method combines the analysis of instruction set and has the function of anti-malware confusion. At the same time, malware detection based on depth model can enhance the feature learning, can express the abundant information of big data, and can adapt to theevolving malware more easily.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Node risk assessment fusing ICT supply chain network topology and product business information
PendingCN111489065AImprove the accuracy of evaluationCharacter and pattern recognitionResourcesTopology informationData set
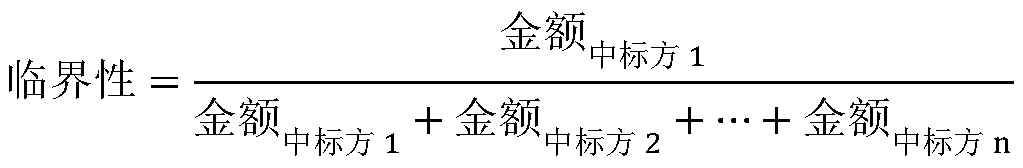
The invention relates to node risk assessment fusing ICT supply chain network topology and product business information, and belongs to the technical field of computer and information science. The invention is mainly used for solving the problem that an ICT supply chain network security risk assessment index system and an assessment method are incomplete. To solve the problem, the invention provides an ICT supply chain network node security risk assessment model which comprehensively considers ICT supply chain network topology information, supplier node product information and supplier node business information. The method comprises the following steps: firstly, quantizing 11-dimensional indexes; then, training the quantitative indexes through an ensemble learning stacking model; and finally, testing an output node security risk level and an F1 value by using the trained three-classification ensemble learning staging model. Experiments are carried out on an ICT bidding and tendering project data set, and a supplier node security risk rating task reaches a higher F1 value, which indicates that the supply chain network node security risk comprehensive evaluation method can well realize comprehensive evaluation of the supply chain network node security risk.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for hiding mass information by using remote sensing image
InactiveCN101840564AStrong concealmentAchieve hiddenWave based measurement systemsImage data processing detailsHidden dataComputer science
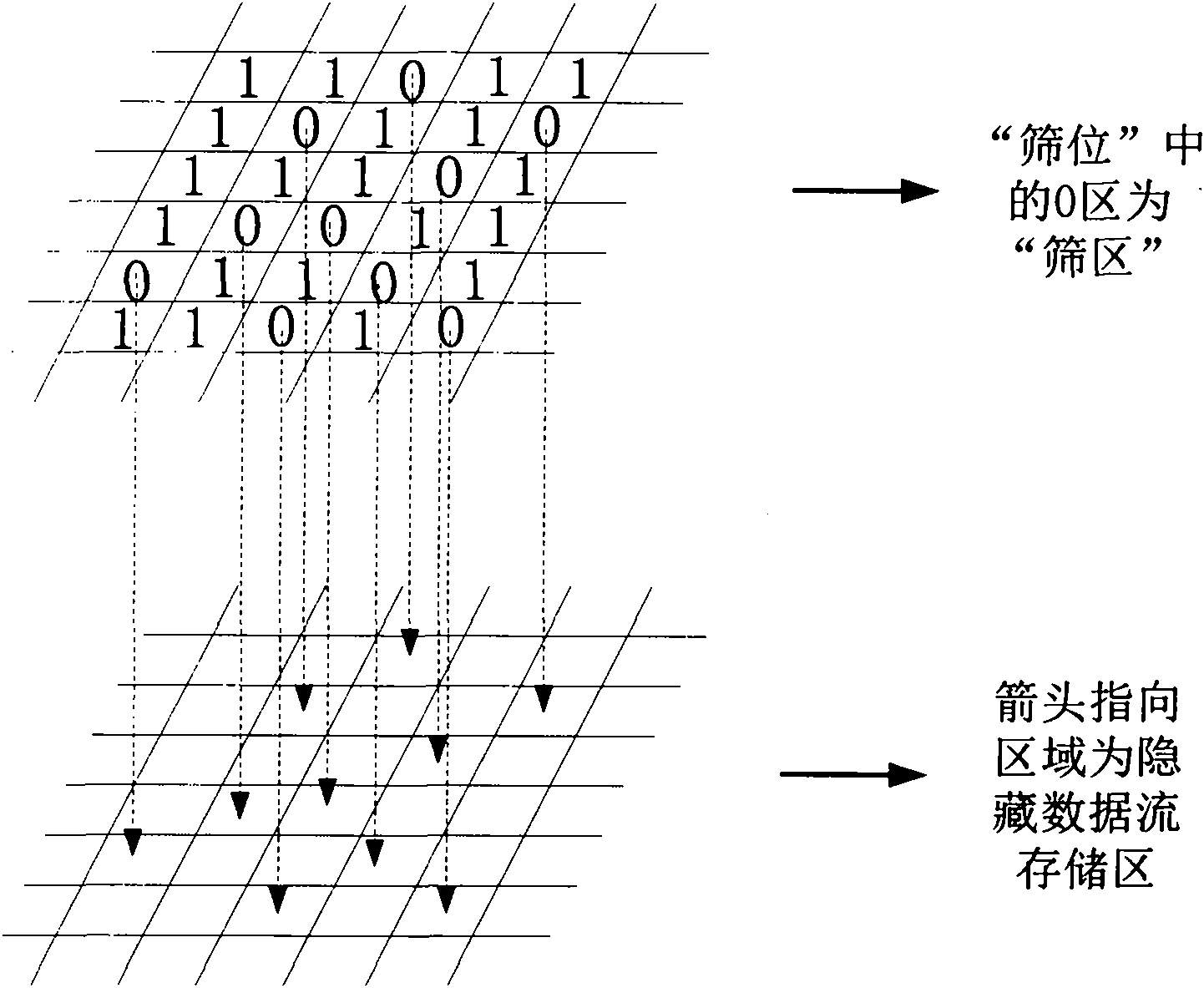
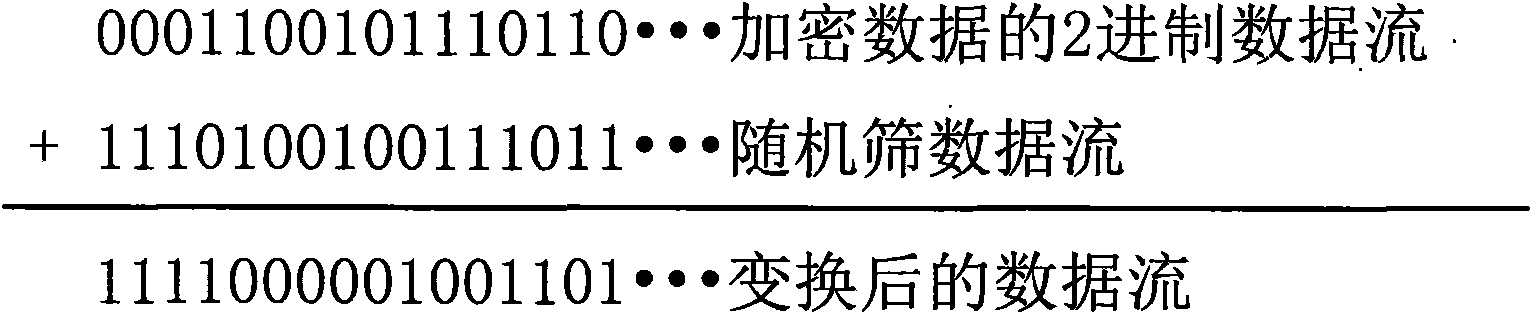
The invention relates to a method for hiding mass information by using a remote sensing image and belongs to the field of information hiding in pattern recognition and data encryption of information sciences. The method is characterized in that mass confidential files are stored in a remote sensing image file to have strong concealment; data is only stored in characteristic areas of the image file; and the hidden data is subjected to random encryption in advance and the encryption sites of an encrypted image still reserve the characteristics of an original image, so that the encrypted image has little appearance change to avoid being identified and decrypted and provide a security guarantee for the storage and transmission of private information. In addition, the invention also provides a method for extracting remote sensing image hidden information based on the method for hiding the mass information, which can effectively extract the hidden information and is simple and easy to implement.
Owner:NANJING UNIV
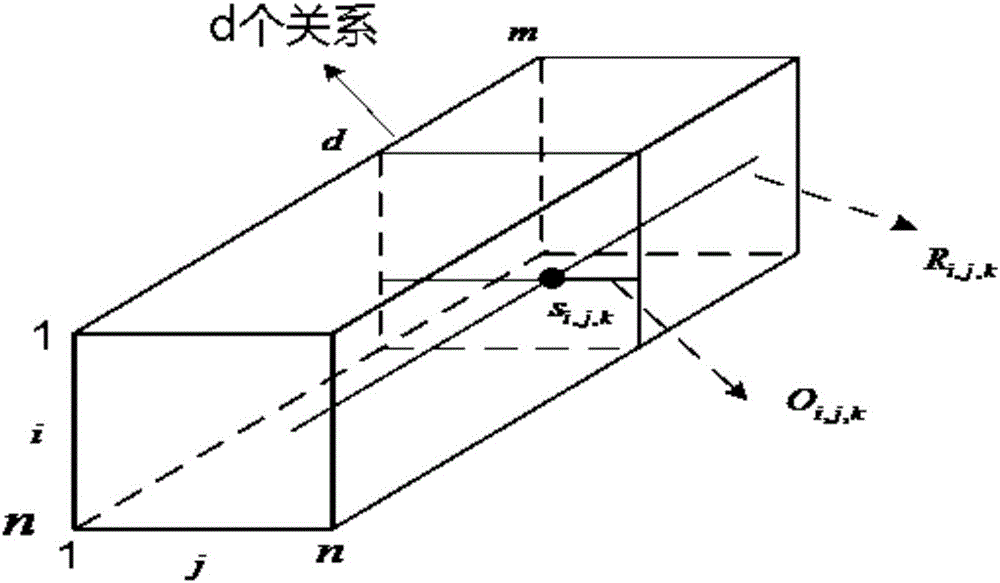
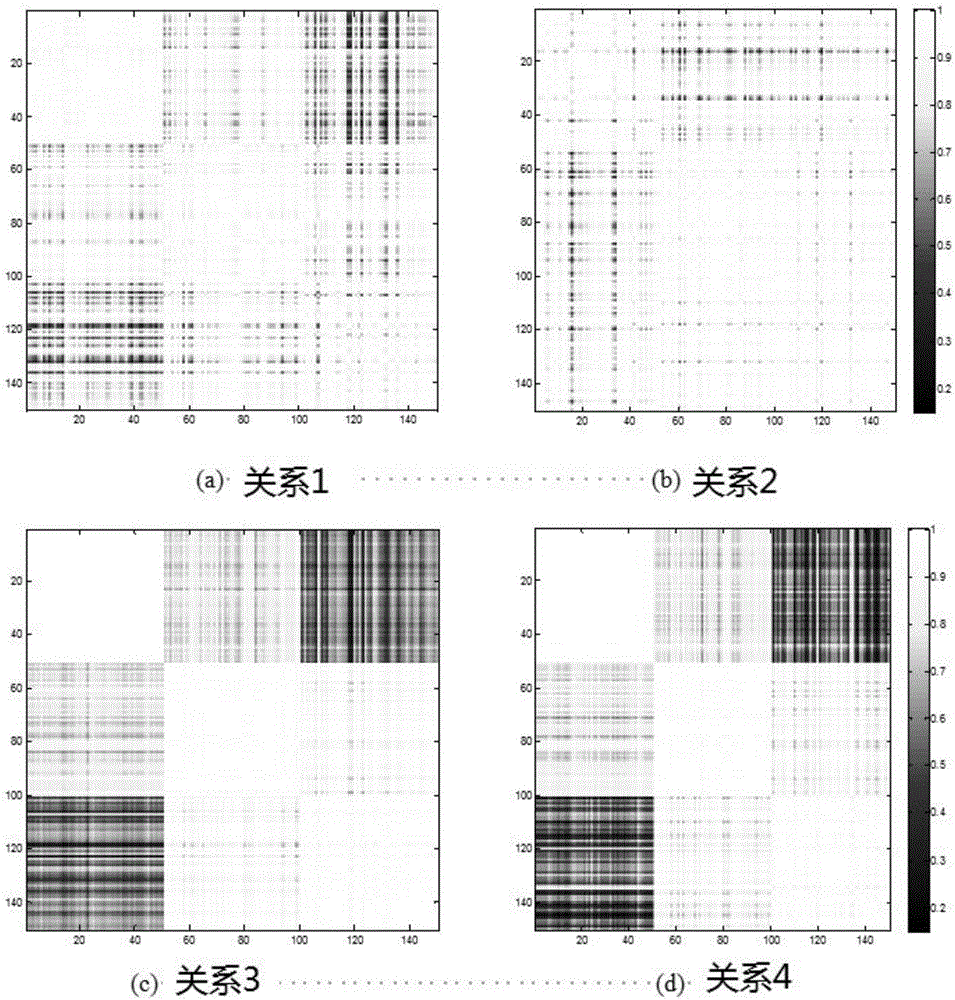
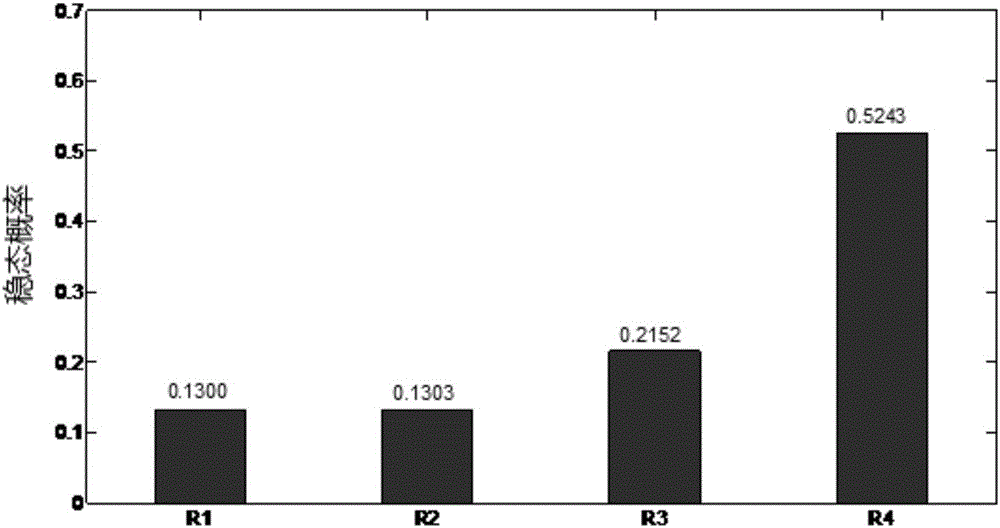
Heterogeneous social network-based detection method
The invention relates to the field of information science, and provides a detection method based on a heterogeneous social network, which maps the heterogeneous social network into a multidimensional matrix; determines the transition probability of the nodes and the transition probability of the relationship in the multidimensional matrix; uses random walk algorithm to obtain the balanced distribution of nodes and the balanced distribution of relationships; according to the balanced distribution of nodes and the balanced distribution of relationships, a weighted single-relationship social network is obtained; and using a single-relationship social network detection algorithm, based on the weighted single-relationship social network to obtain detection results of heterogeneous social networks. The present invention makes full use of the mutual influence of nodes and relationships in the heterogeneous social network, and fuses the heterogeneous network into a single-relationship social network with weights, and then utilizes the traditional single-relationship social network community detection method to Weighted single-relational networks for community detection.
Owner:南通弘数信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com